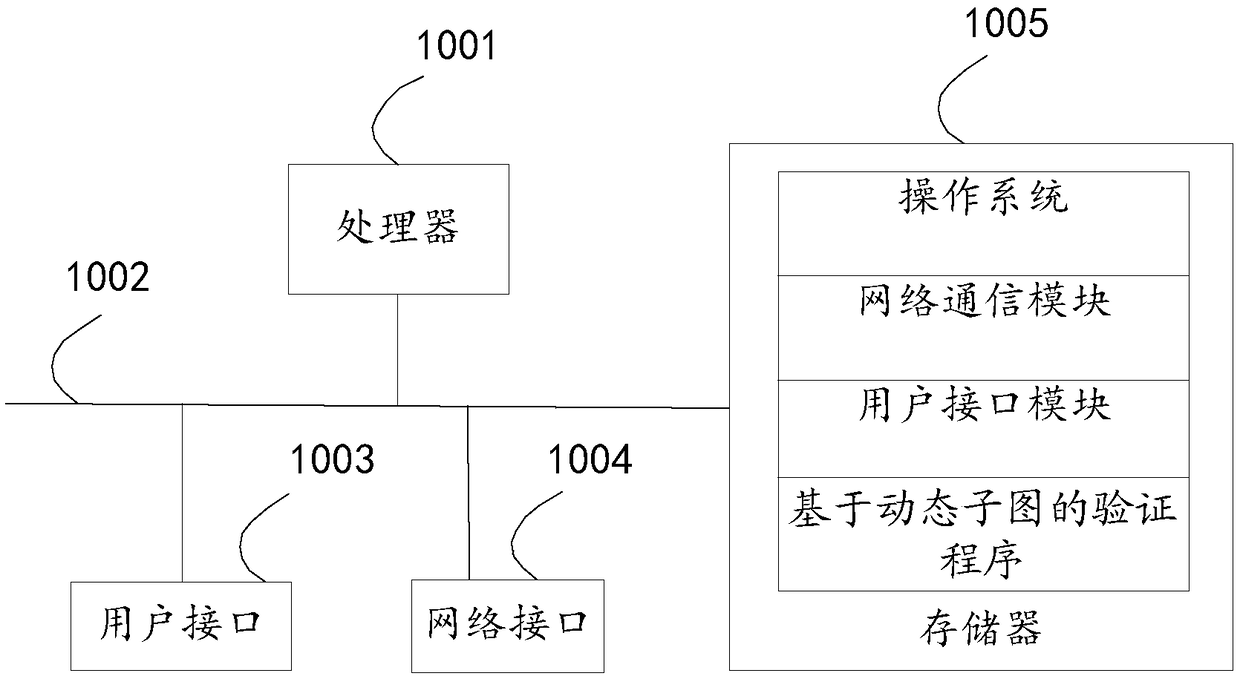
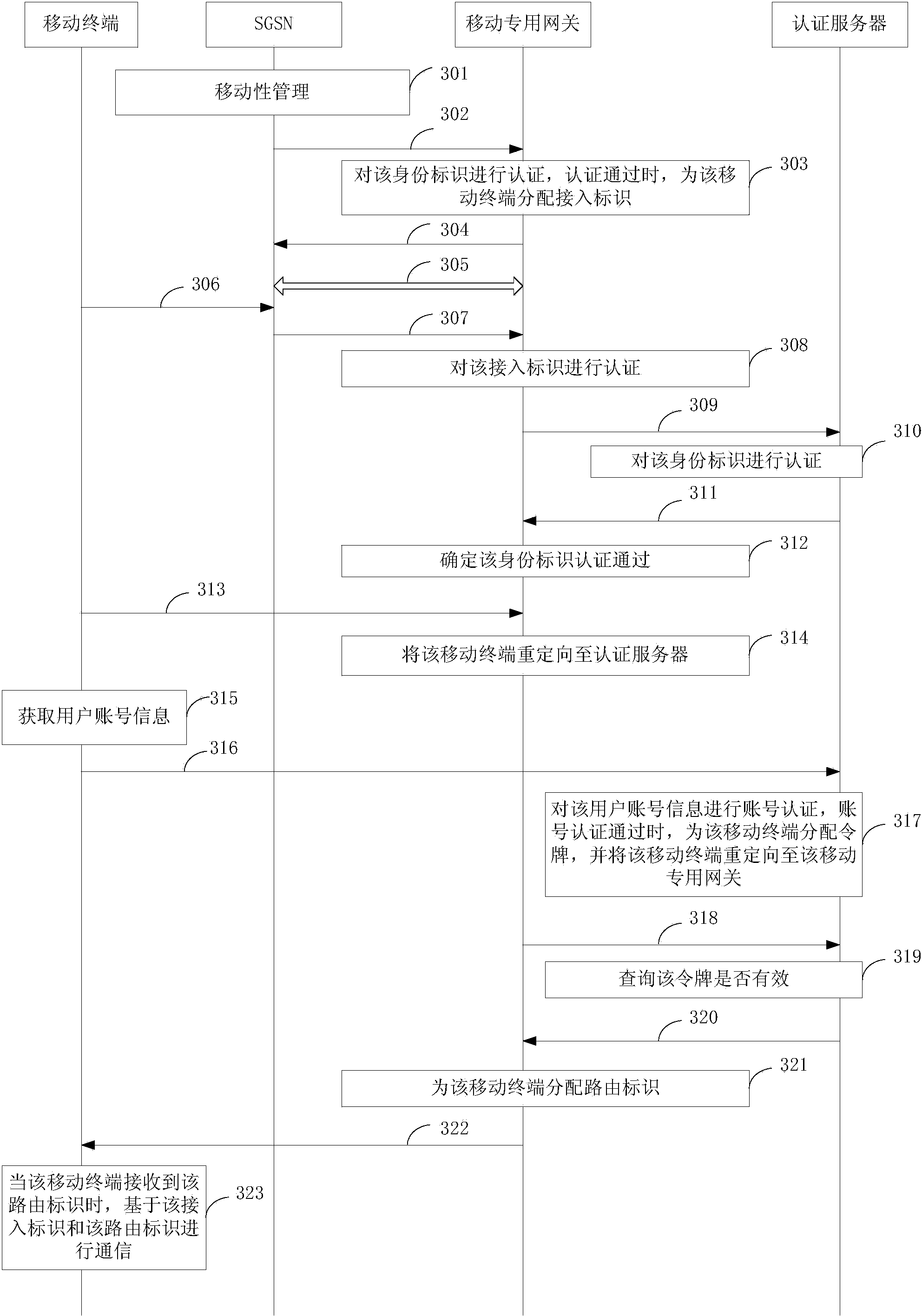Patents
Literature
64results about How to "Prevent cyber attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Domain name resolution agent method and system, and domain name resolution agent server
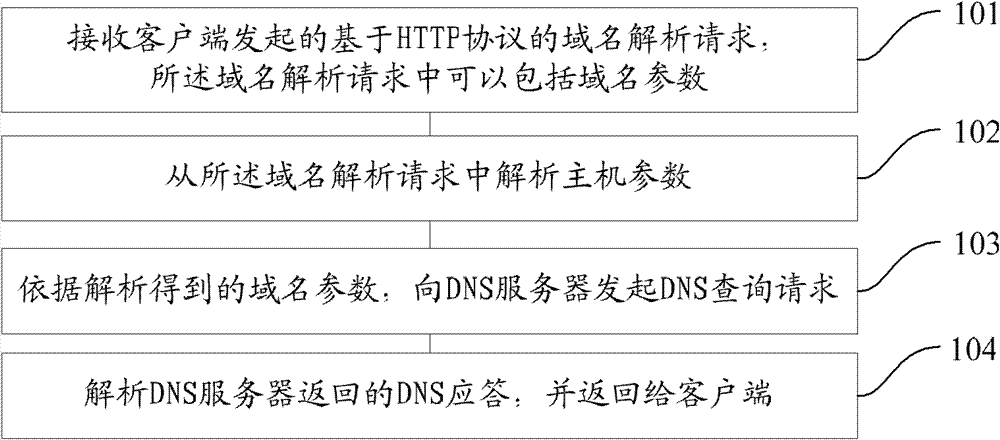
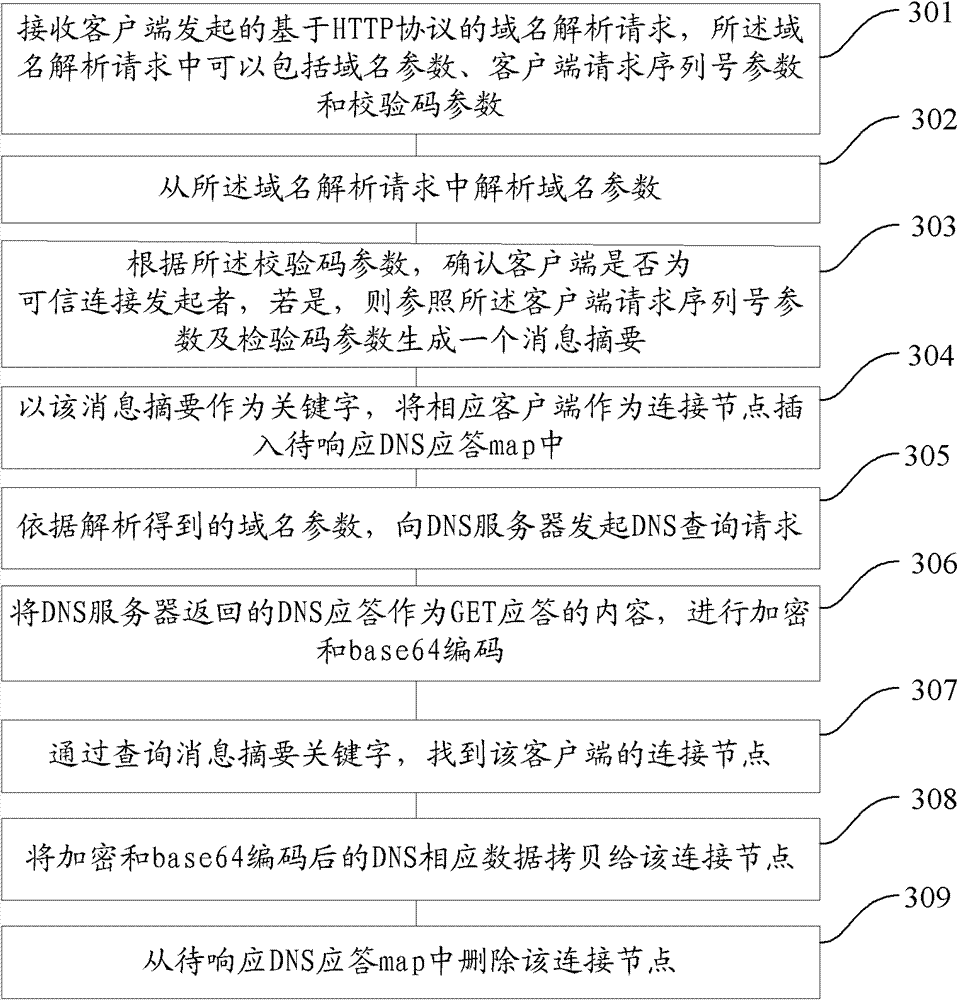
The invention provides a domain name resolution agent method and system, and a domain name resolution agent server, wherein the domain name resolution agent method specifically comprises the following steps: a client starts a domain name resolution request based on a hypertext transport protocol (HTTP), wherein the domain name resolution request comprises a domain name parameter; the domain name resolution request is received; the domain name parameter is resolved from the domain name resolution request; according to the resolved domain name parameter is obtained, a domain name server (DNS) query request is sent to the DNS; the DNS response returned by the DNS is resolved and then returned to the client. According to the invention, the domain name resolution can be conducted through the DNS agent resolution technology based on the HTTP, so that the safety of the domain name resolution is improved.
Owner:三六零数字安全科技集团有限公司
Data security protection method of enterprise management software
InactiveCN101923678APrevent cyber attacksPrevent leakageDigital data protectionData securityDatabase server
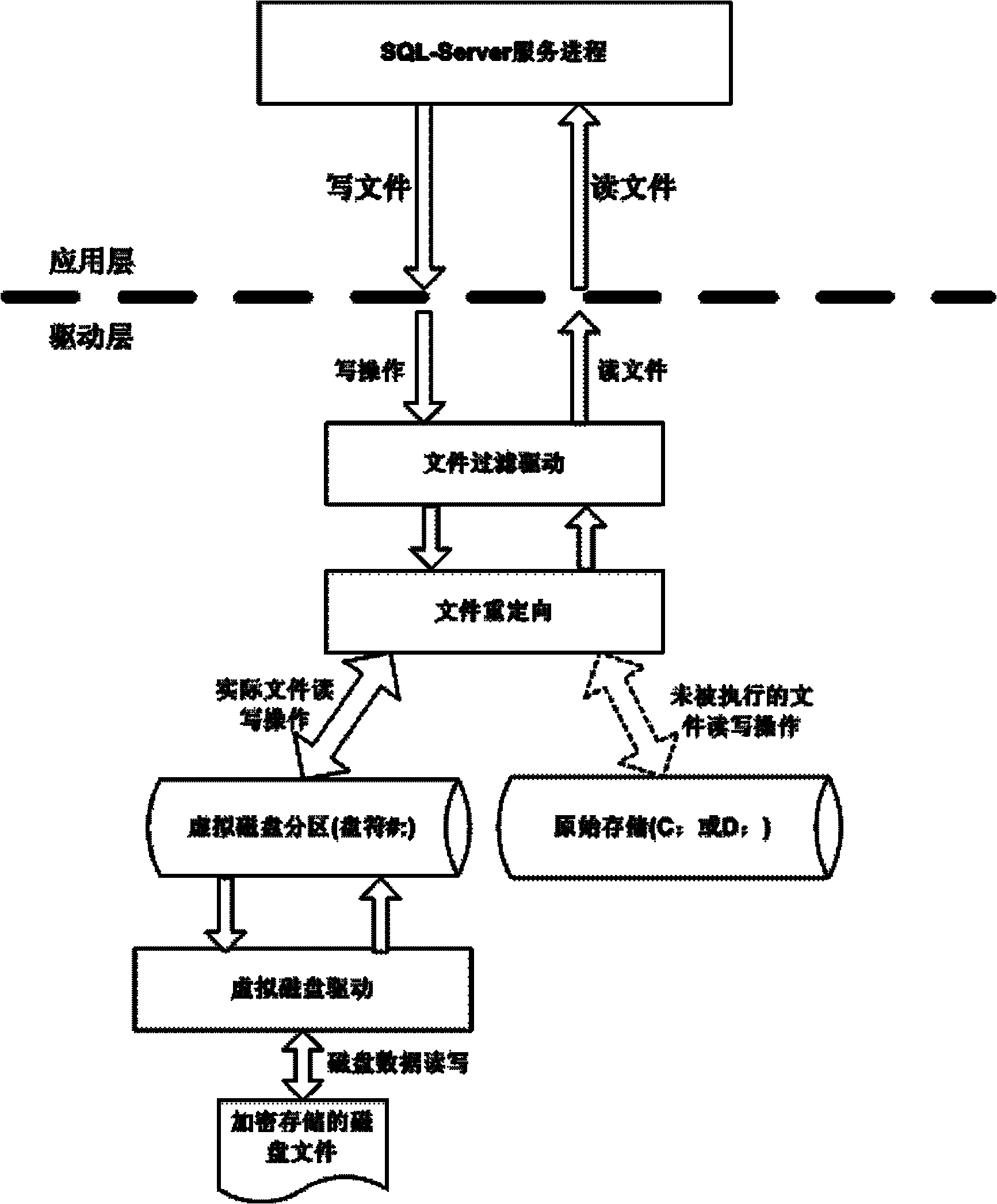
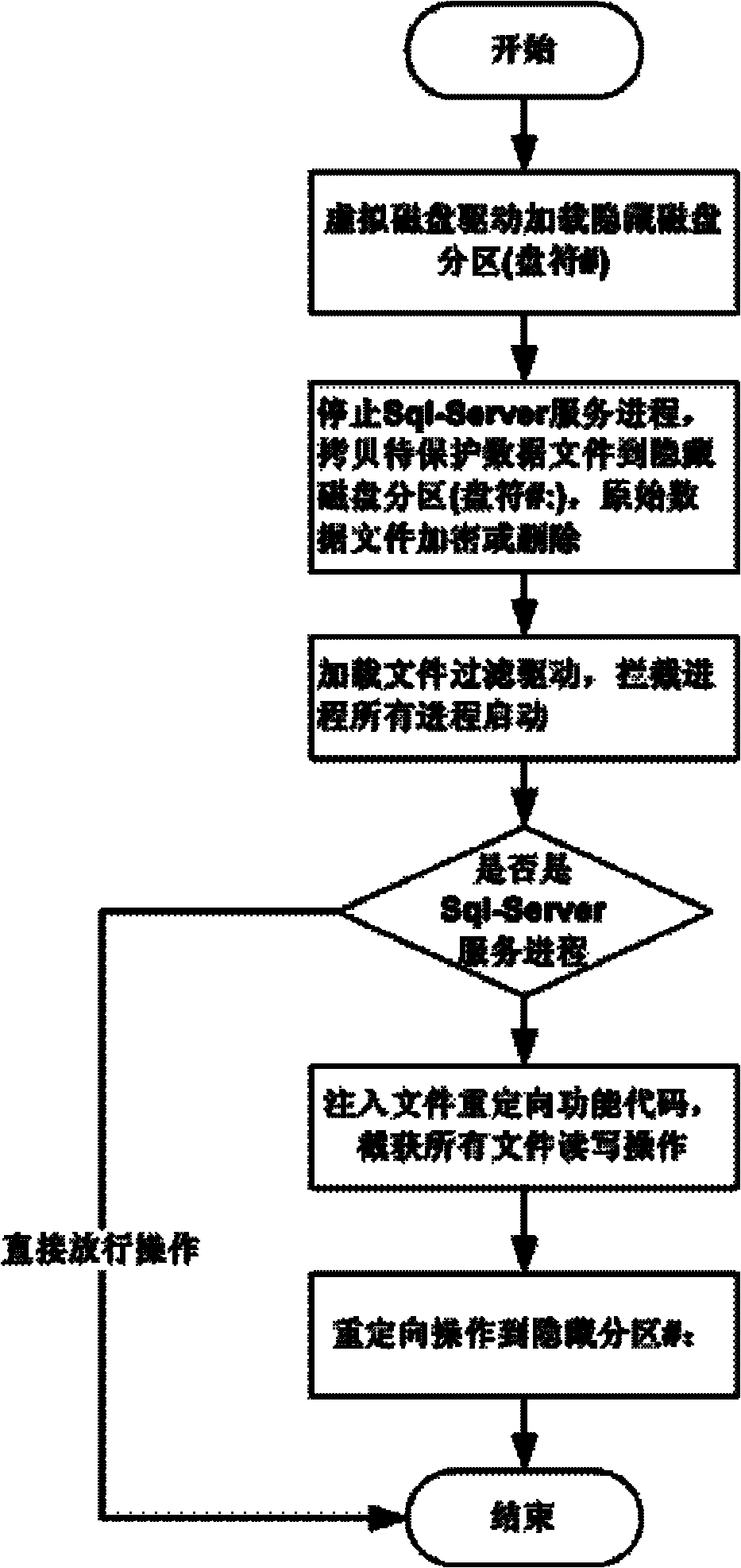
The invention discloses an enterprise management software security protection method and belongs to the field of information security. The method provided by the invention can protect the data security of enterprise confidential information without any influences on the application flow of enterprise management software. In the method, a database file which stores enterprise core confidential data is subjected to storage encryption to prevent secret leakage caused by copying the database file; for preventing password secret leakage from leading to network attack, the access to a database server is controlled, so that only specific terminals are allowed to access the database server after verification; and an enterprise management software system client is protected completely and intelligently, the output files are encrypted, and content copying, printing, screen capturing and any other operation which may lead to secret leakage are strictly controlled in a management software application process.
Owner:WUHAN TIANYU INFORMATION IND
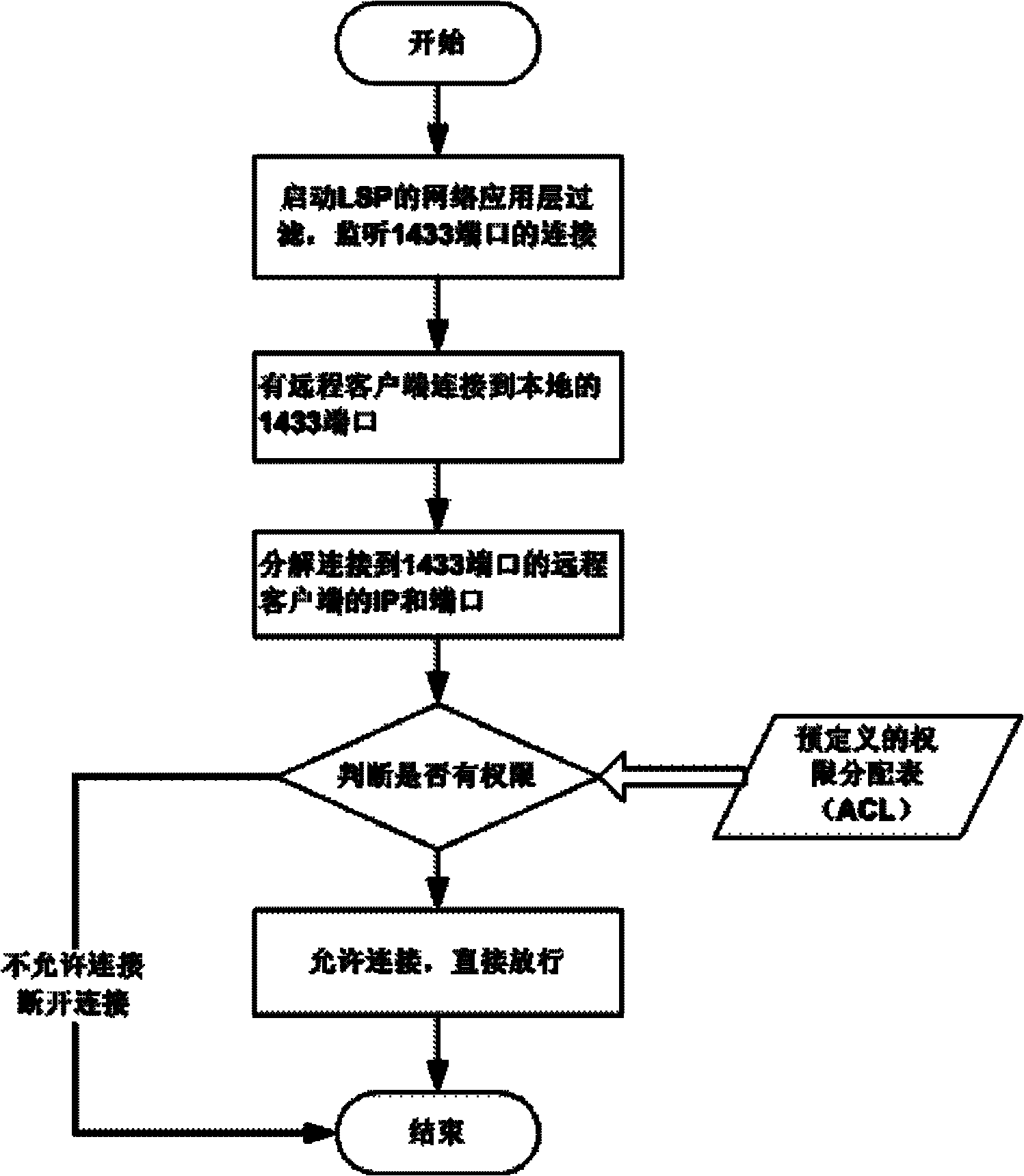
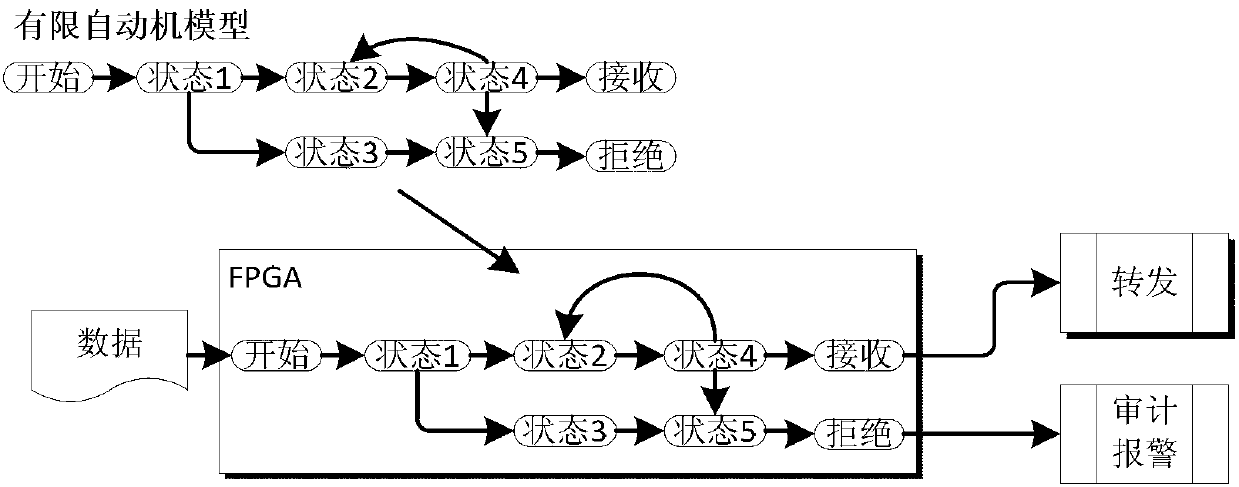
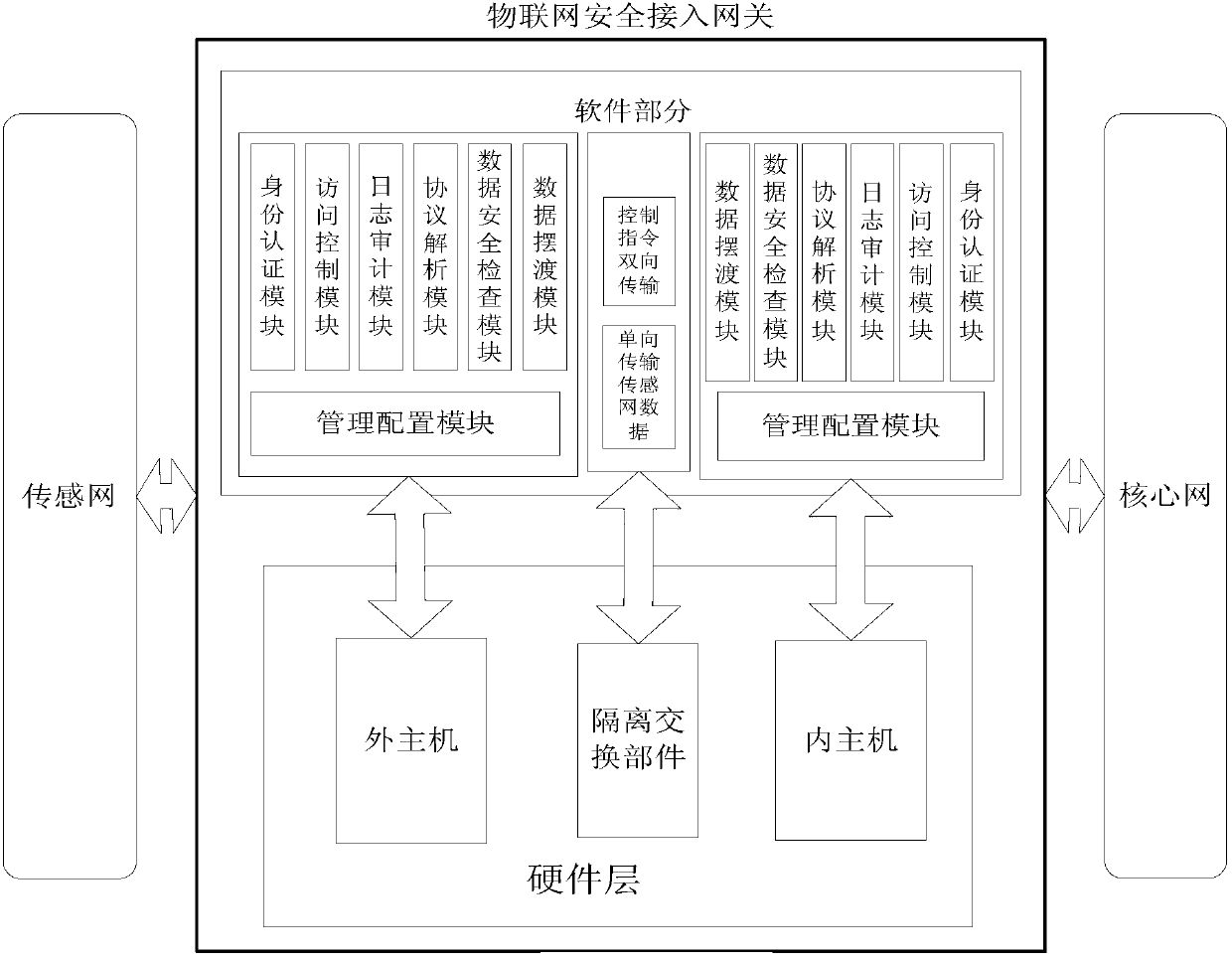
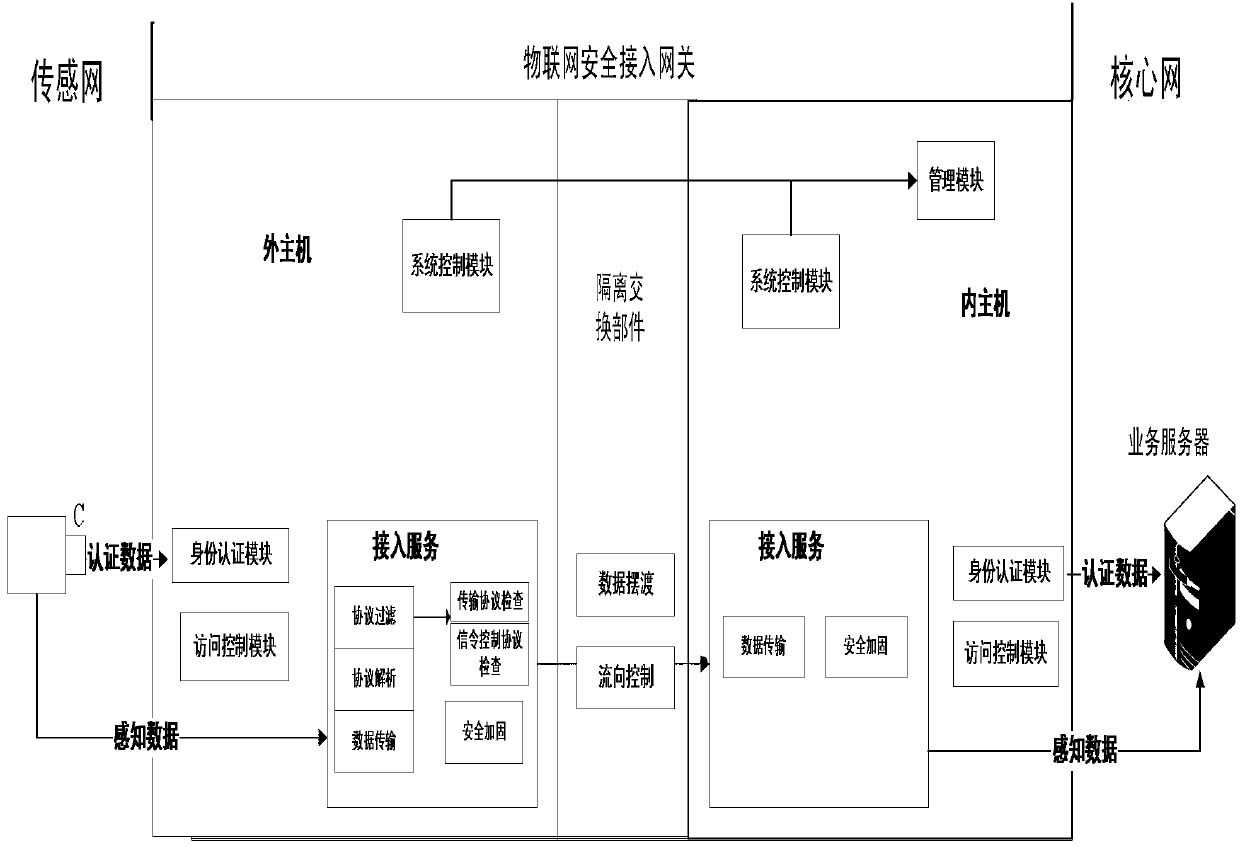
Internet of things security access gateway
InactiveCN103139058ARealize security border controlMeeting Multi-Protocol Complexity RequirementsNetwork connectionsGate arrayThe Internet
The invention discloses an internet of things security access gateway. A three component framework of 2+1 is adopted in a hardware layer of the gateway. The three component framework comprises an outer host machine, an isolation exchange component and an inner host machine. A filed programmable gate array (FPGA) card based on hardware serves as the isolation exchange component so that isolation of a network and safe and rapid exchange of data are achieved. Device certification, access control, protocol analysis, data security check, data ferry service and audit service are achieved through software layers on the inner host machine and the outer host machine and action of the services can be traced. The internet of things security access gateway has the advantages that relative requirements that data collected by an internet of things perception terminal is introduced to a core network safely are satisfied, network attack, Trojan horse virus transmission and denial of service attack are prevented from being launched through a sensing layer network with weak safety protection to the core network, safe exchange of data is achieved under the condition that the sensing network and the core network are in network isolation, and practical application of the internet of things is achieved under the condition that safety is guaranteed.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
Method and system for preventing IPv6 (Internet Protocol Version 6) from duplicate address detection attack
ActiveCN102082801APrevent cyber attacksImprove good performanceData switching networksComputer networkReachability
The invention relates to a method for preventing IPv6 (Internet Protocol Version 6) from duplicate address detection attack, which comprises the following steps: node equipment sends a neighbor solicitation (NS) message of duplicate address detection, appoints the source address of a received neighbor advertisement (NA) / NS message as the target address of the message after receiving the NA / NS message responding to duplicate address detection, sends an NS unicast reachability probe message and judges whether the response message is received; and if so, the node equipment ensures the configured IPv6 address to be in the duplicate state, otherwise, the node equipment ensures the configured IPv6 address to be in the available state. The invention also provides a system for preventing IPv6 from duplicate address detection attack. By applying the method and the system, the duplicate detection attack can be coped with and the network equipment can be protected.
Owner:ZTE CORP
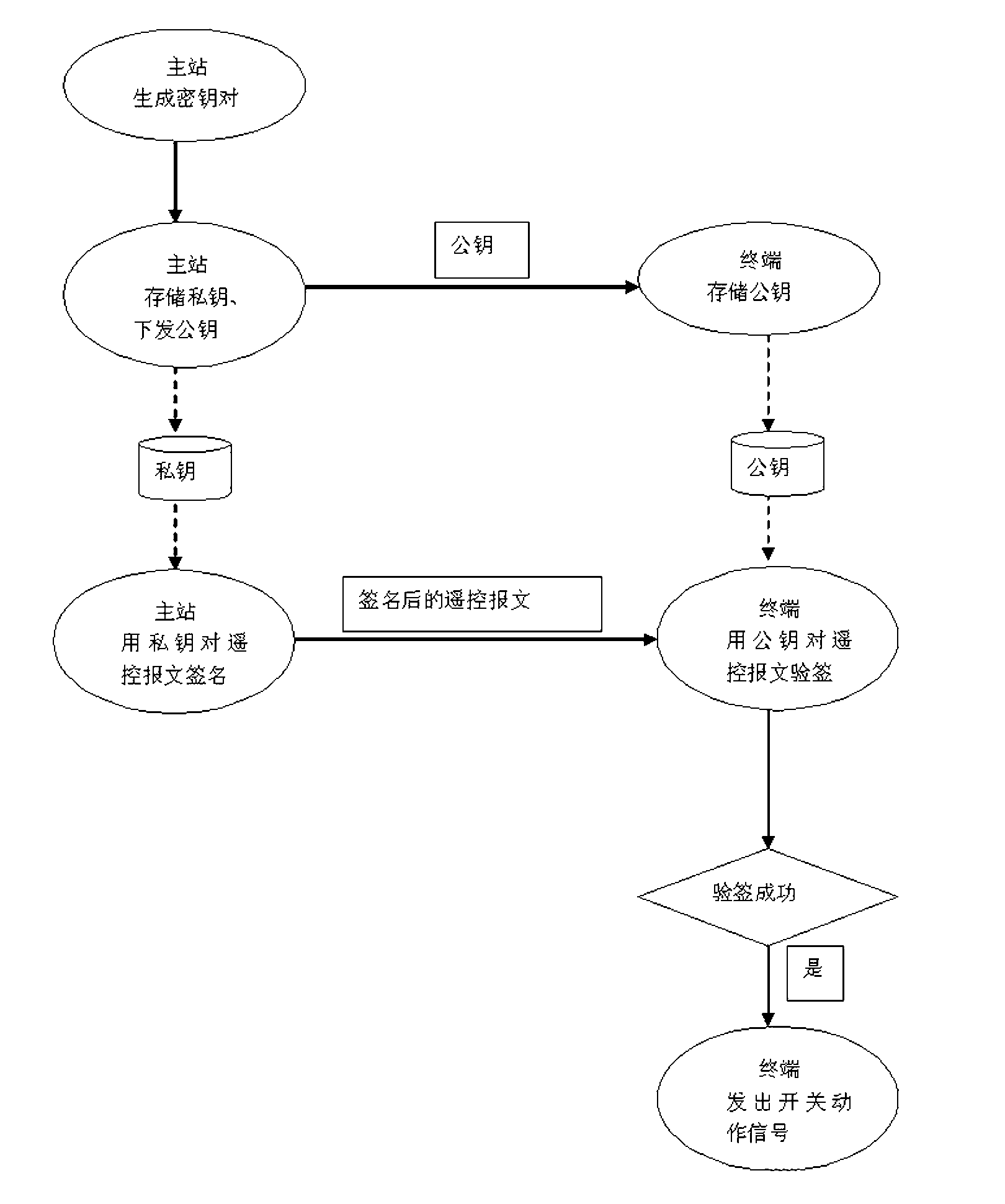
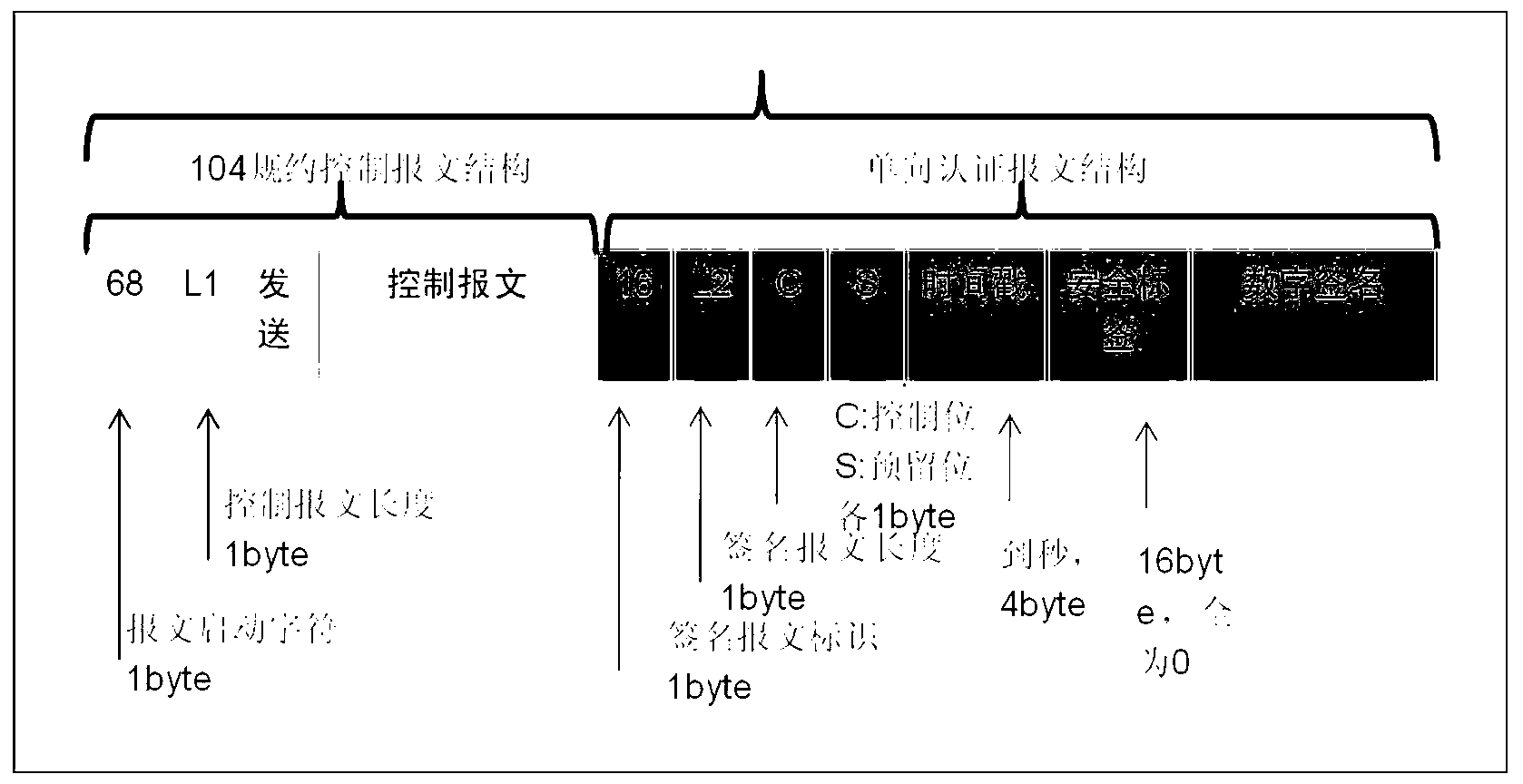
Method for realizing encrypted authentication of distribution automation remote control command
ActiveCN103178956APrevent cyber attacksIncrease the number ofKey distribution for secure communicationUser identity/authority verificationPrimary stationDigital signature
The invention discloses a method for realizing encrypted authentication of a distribution automation remote control command. The method comprises the following steps of: (1) digitally signing a remote control message, and generating a key pair by a main station; (2) storing a private key by the main station and issuing a public key to a power distribution terminal; (3) storing the public key by the power distribution terminal; (4) signing by using the private key by the main station; (5) verifying the signature by using the public key by the power distribution terminal; and (6) sending out an actuating signal from the distribution terminal to a switch. The method comprises that: the main station generates the key pair periodically or randomly through manual triggering by using an asymmetric cryptographic algorithm, stores the private key locally, and sends the public key to the power distribution terminal through a public network; the power distribution terminal stores the received public key locally; the main station when sending the remote control command to the power distribution terminal firstly generates a signature for the remote control message by using the private key, and then attaches the signature at the tail end of the remote control message; and the terminal when receiving the remote control command verifies the signature on the remote control message by using the public key, then carries out the switching action after the successful signature verification, and refuses the action if the signature verification is failed. The method for realizing encrypted authentication of the distribution automation remote control command has strong practicability, and enhances reliability and safety of the remote control.
Owner:CEEC HUNAN ELECTRIC POWER DESIGN INST
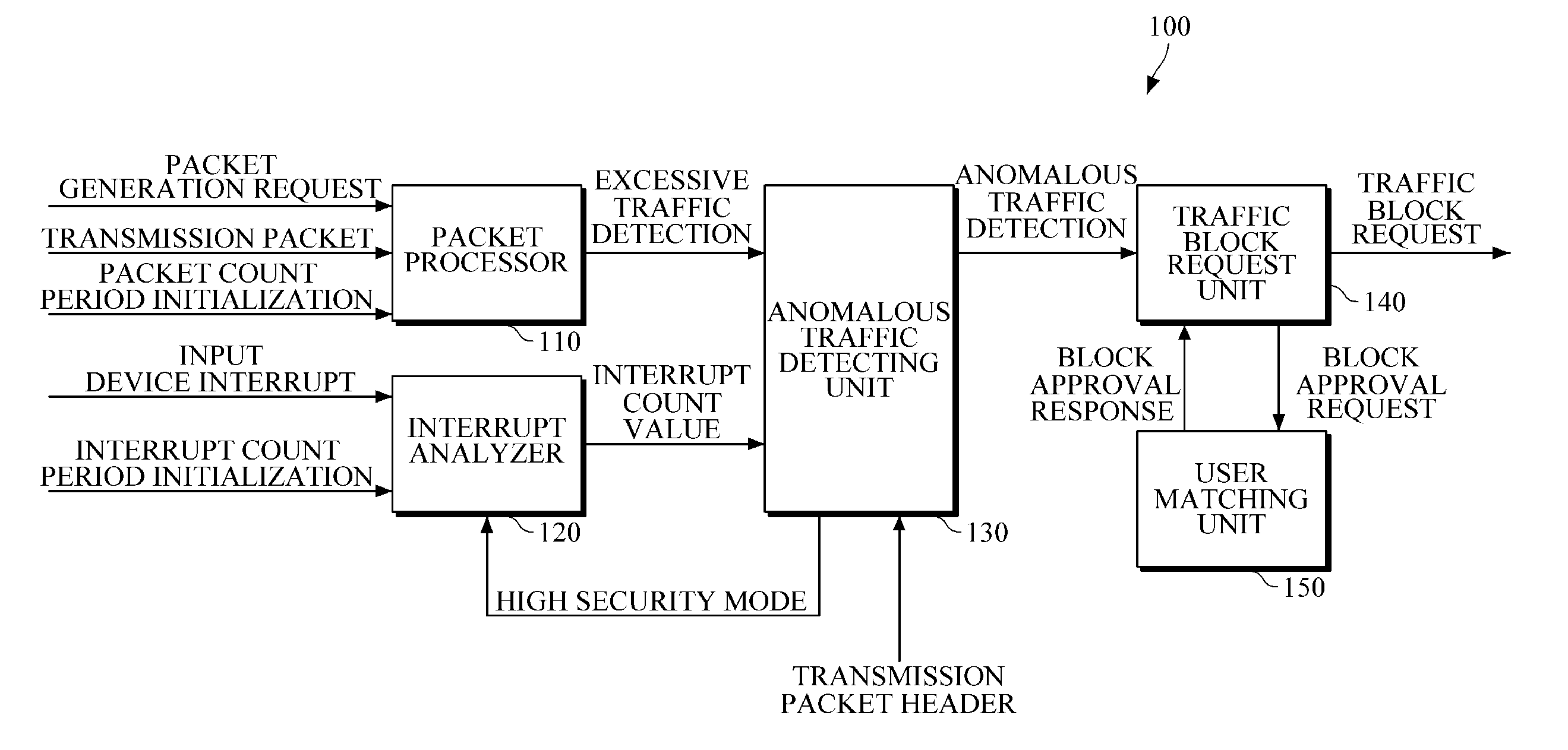
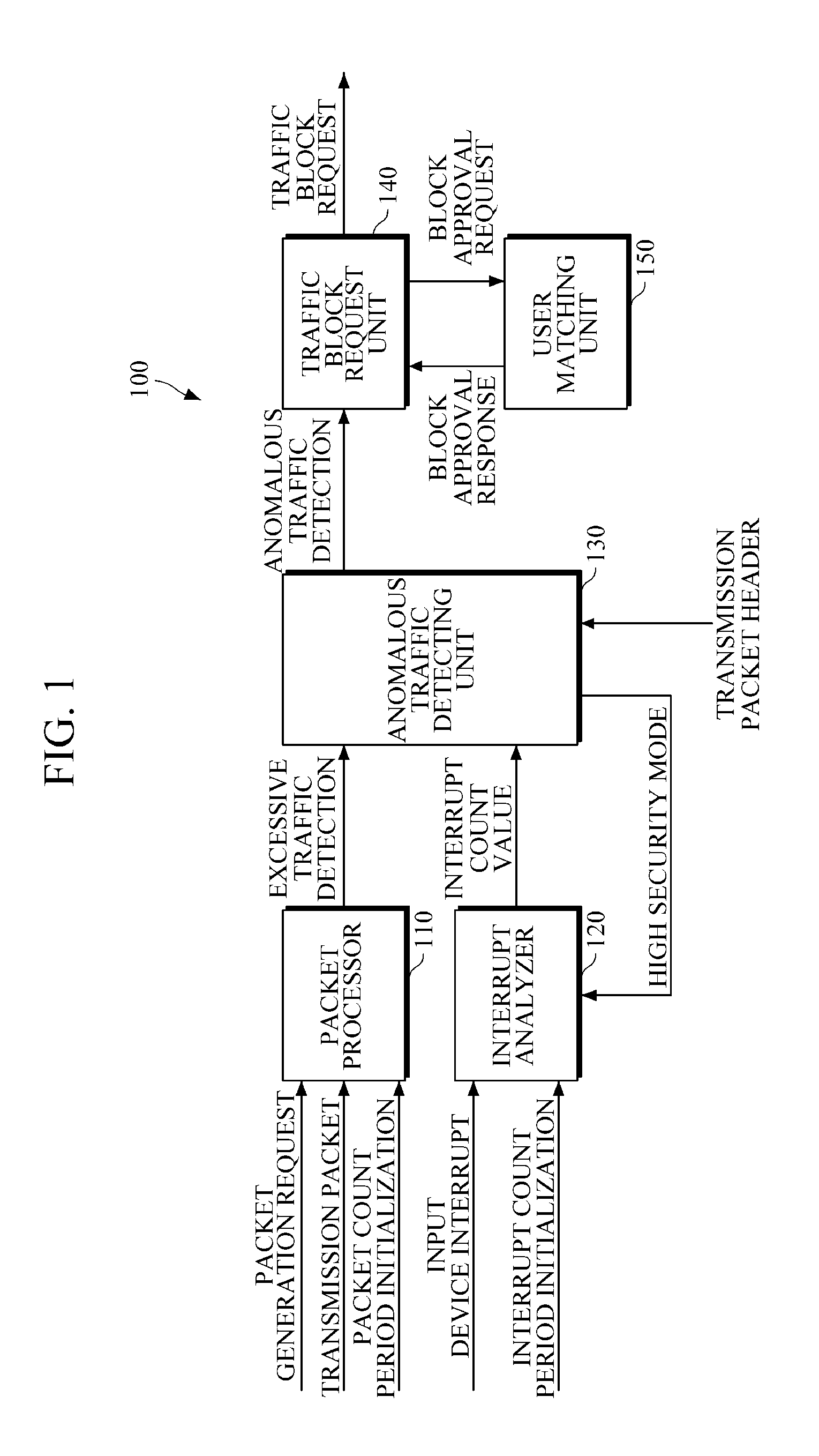
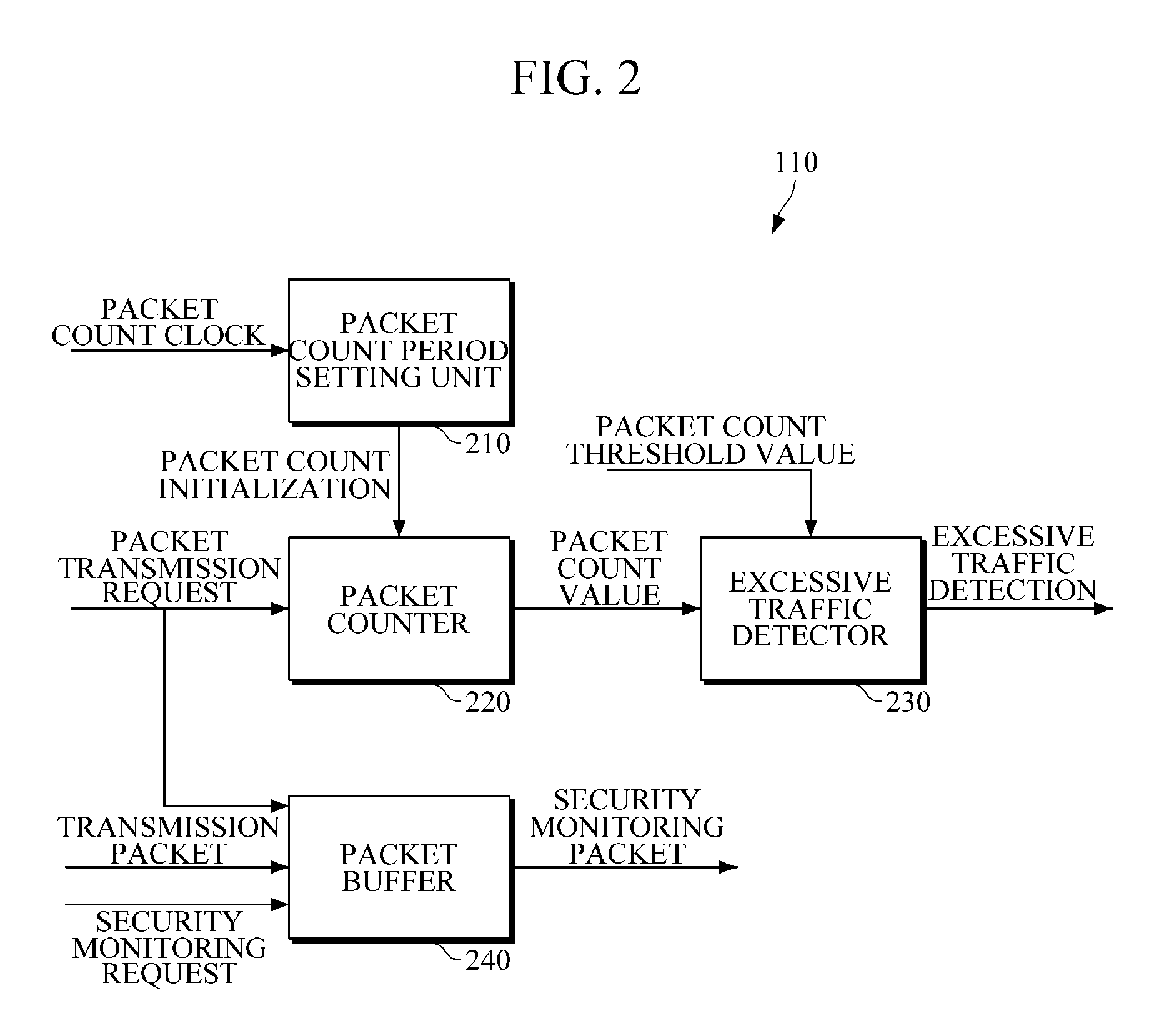
Apparatus and method for cyber-attack prevention
InactiveUS20130167219A1Avoid spreadingPrevent cyber attacksData taking preventionMultiple digital computer combinationsTraffic capacityCyber-attack
Provided are a method of preventing cyber-attack based on a terminal and a terminal apparatus therefor. The terminal apparatus includes: a packet processor configured to determine whether excessive traffic is generated by a transmission packet; an anomalous traffic detecting unit configured to determine whether anomalous traffic is generated, using a first condition of the excessive traffic being maintained for a first time period and a second condition of a generation count of the same kind of transmission packets exceeding a predetermined threshold value for a second time period; and a traffic block request unit configured to generate a traffic block request signal for requesting blockage of the transmission packet according to the result of determining whether anomalous traffic is generated.
Owner:ELECTRONICS & TELECOMM RES INST
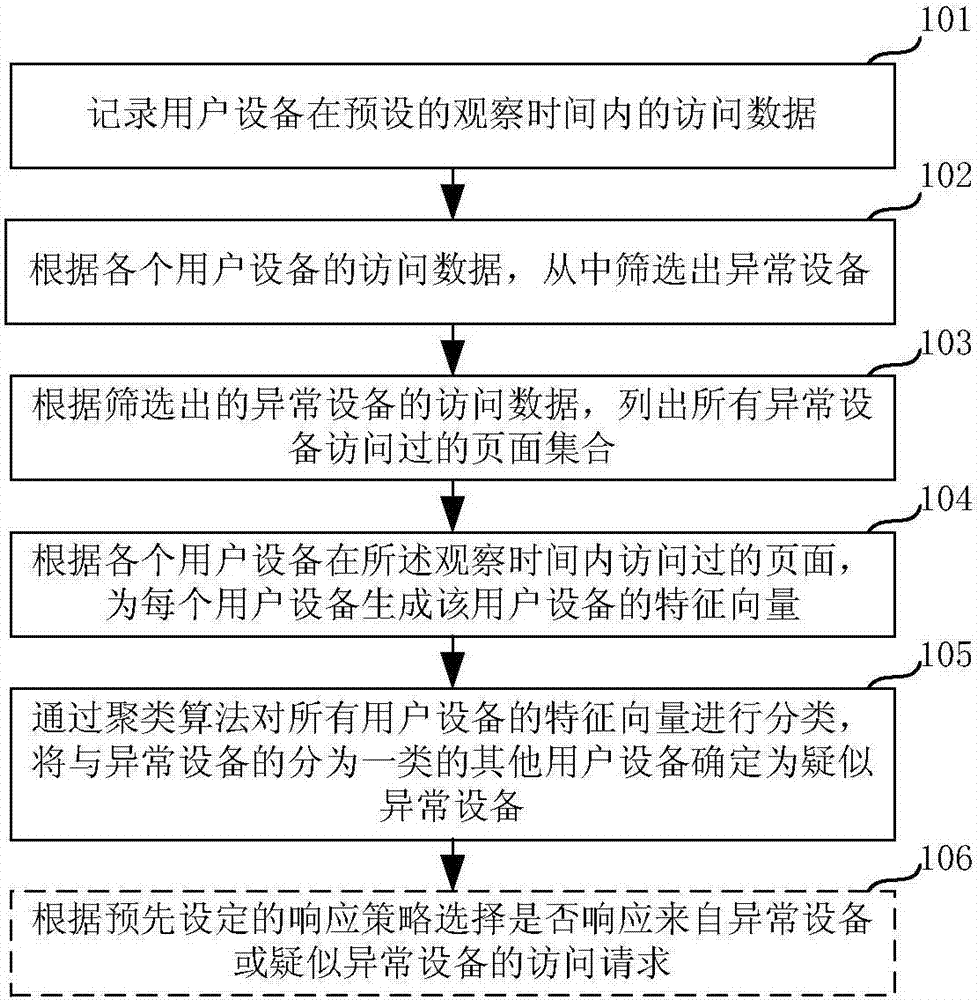
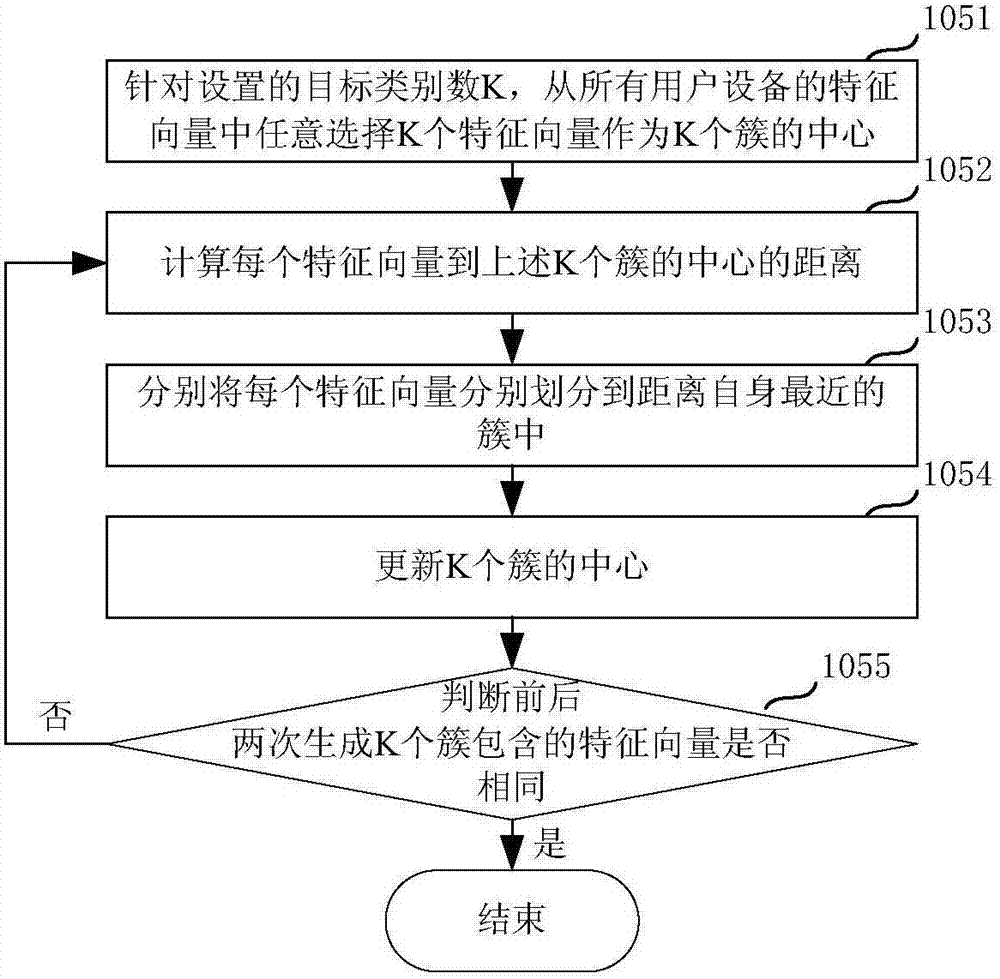
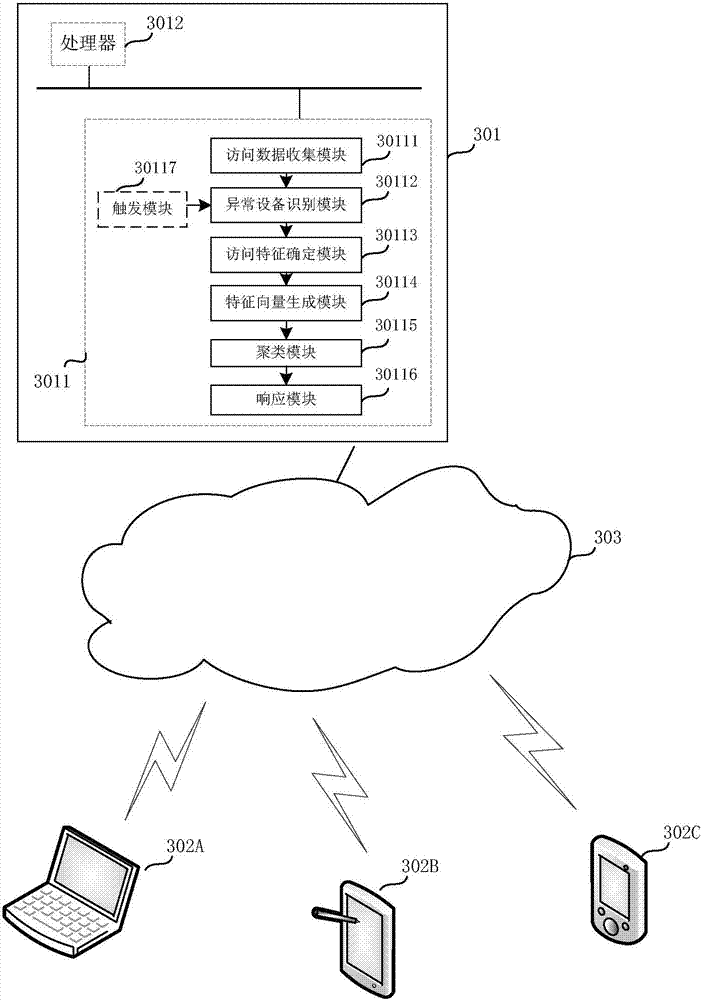
Abnormal equipment identification method and apparatus
The invention relates to an abnormal equipment identification method and apparatus. The abnormal device identification method comprises the following steps: recording access data of user equipment within a preset observation time; screening abnormal equipment according to the access data of the user equipment; listing the pages accessed by all abnormal equipment according to the screened access data of the abnormal equipment, and generating an abnormal equipment access page set; generating a feature vector of the user equipment for each user equipment according to the accessed page of each user equipment within the observation time, wherein feature values in the feature vector of the user equipment are in one-to-one correspondence with the pages in the abnormal equipment access page set; classifying the feature vectors of call user equipment via a clustering algorithm; and determining the user equipment that is classified as the same category as the abnormal equipment as suspected abnormal equipment. By adoption of the abnormal equipment identification method and apparatus, the abnormal equipment and the suspected abnormal equipment can be identified, thereby effectively avoiding the network attack from the abnormal equipment.
Owner:TENCENT TECH (SHENZHEN) CO LTD
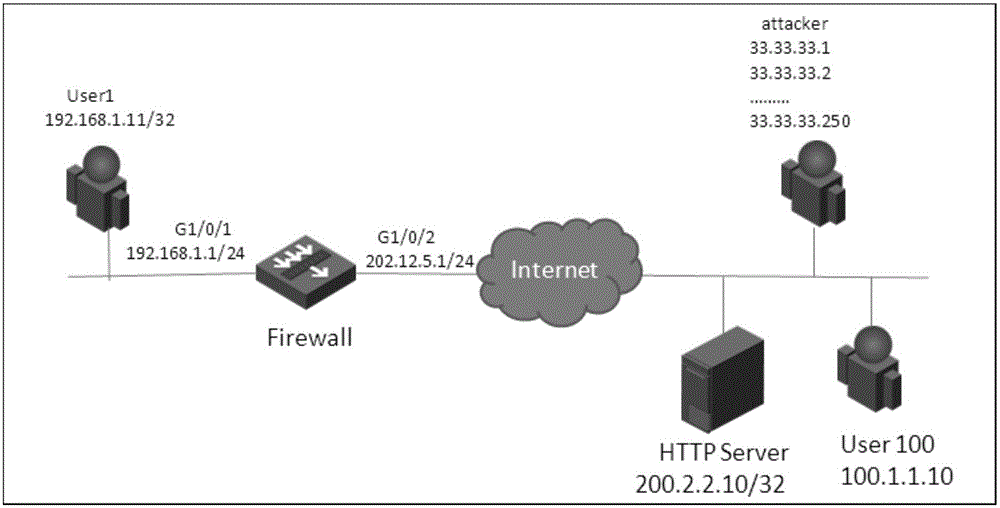
Method and network address translation device preventing network attacks
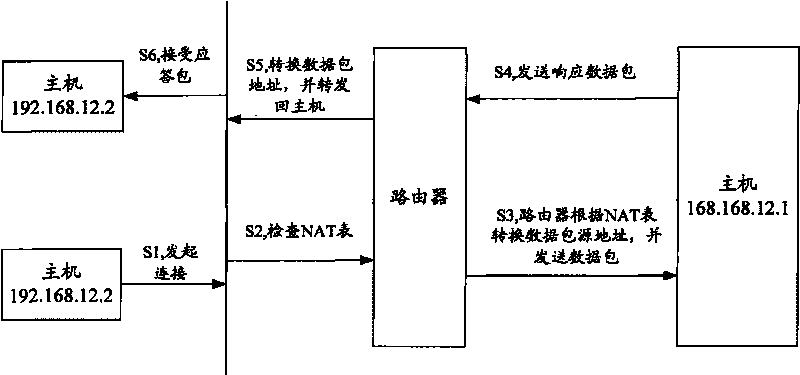
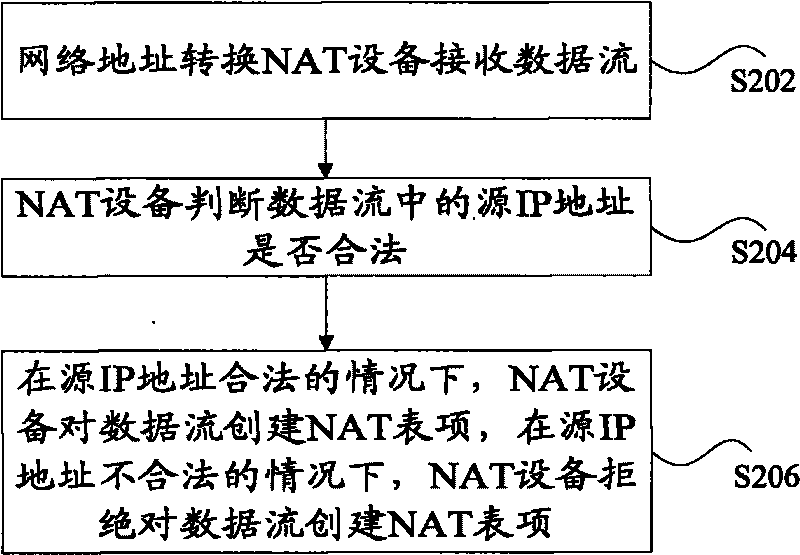
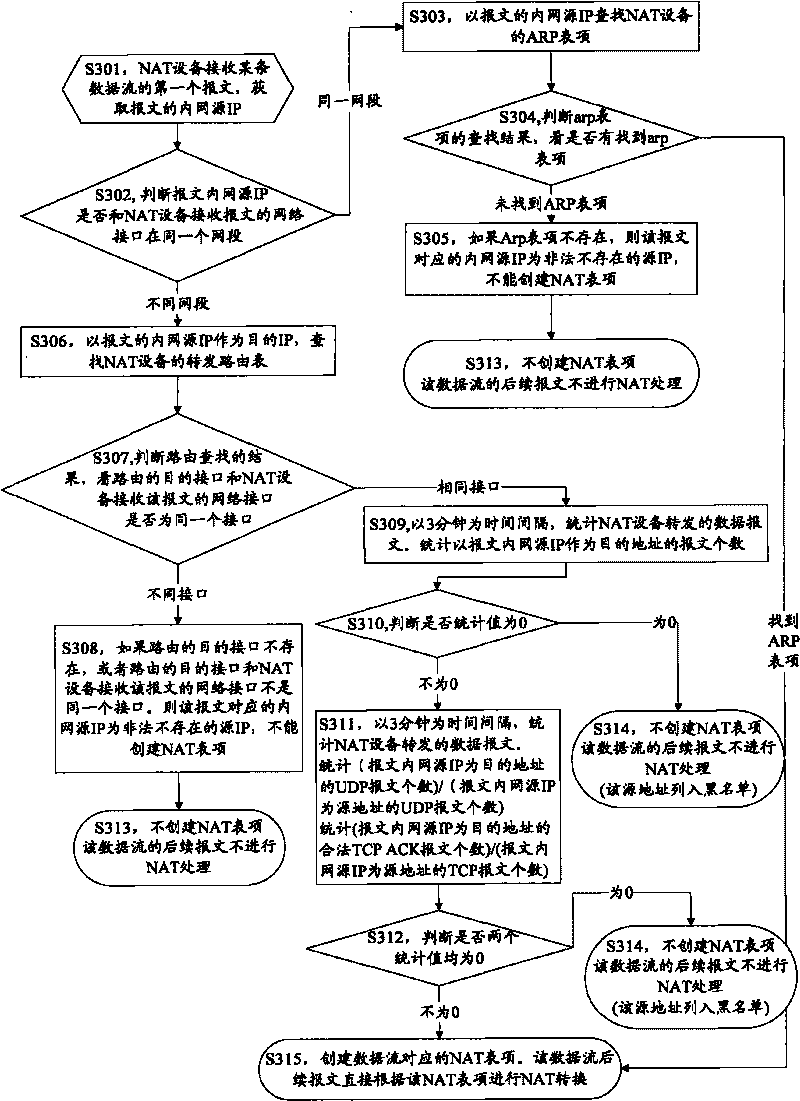
InactiveCN101753637ASolve the problem that cannot be forwardedPrevent cyber attacksTransmissionData streamIp address
The invention discloses a method and a network address translation device preventing network attacks, wherein the method comprises the following steps: the network address translation device receives a data stream; the NAT device judges whether a source IP address in the data stream is legitimate or not; and the NAT device creates an NAT table entry for the data stream under the situation that the source IP address is legitimate, and the NAT device refuses to create the NAT table entry for the data stream under the situation that the source IP address is illegitimate. The method can protect the NAT table entry of the NAT device and further prevent the network attacks.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
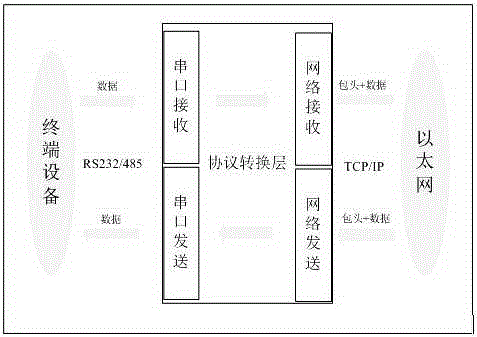
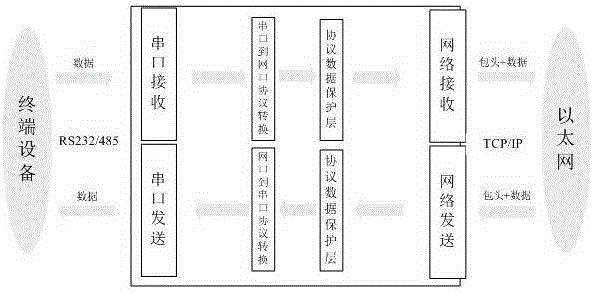
Communication protocol security defending system for electric power serial server
ActiveCN105245555AAdd security detection functionEnsure safetyTransmissionService modelNetwork Communication Protocols
The invention discloses a communication protocol security defending system for an electric power serial server. A protocol data security defending system is provided in an internet access protocol to serial port protocol and a serial port protocol to internet access protocol, and any protocol data and access requests sent to an internet access and a serial port will pass security certification and detection of the security defending system. The communication protocol security defending system is characterized by being composed of a communication protocol data analytical reduction and formatting processing module, a protocol data analysis detection system and a communication protocol data service model security policy definition system. The problems that an existing electric power serial server does not have the security protection function on a communication protocol layer for various kinds of connected electric power industrial control equipment, an electric power telecommunication service protocol protection layer is provided on a protocol conversion layer (the internet access protocol to serial port protocol and the serial port protocol to internet access protocol) in a serial server software control system and used of preventing attackers from illegally operating and attacking various kinds of electric power control equipment connected in the electric power serial server.
Owner:HUAIAN OF JIANGSU ELECTRIC POWER COMPANY POWER SUPPLY +2
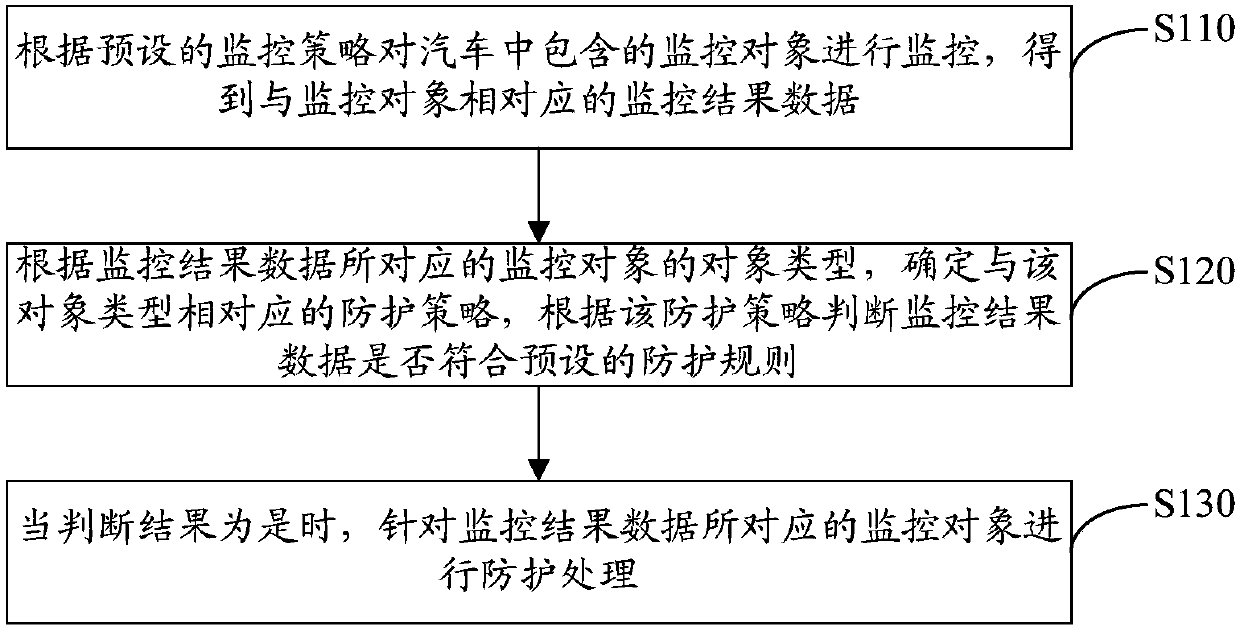
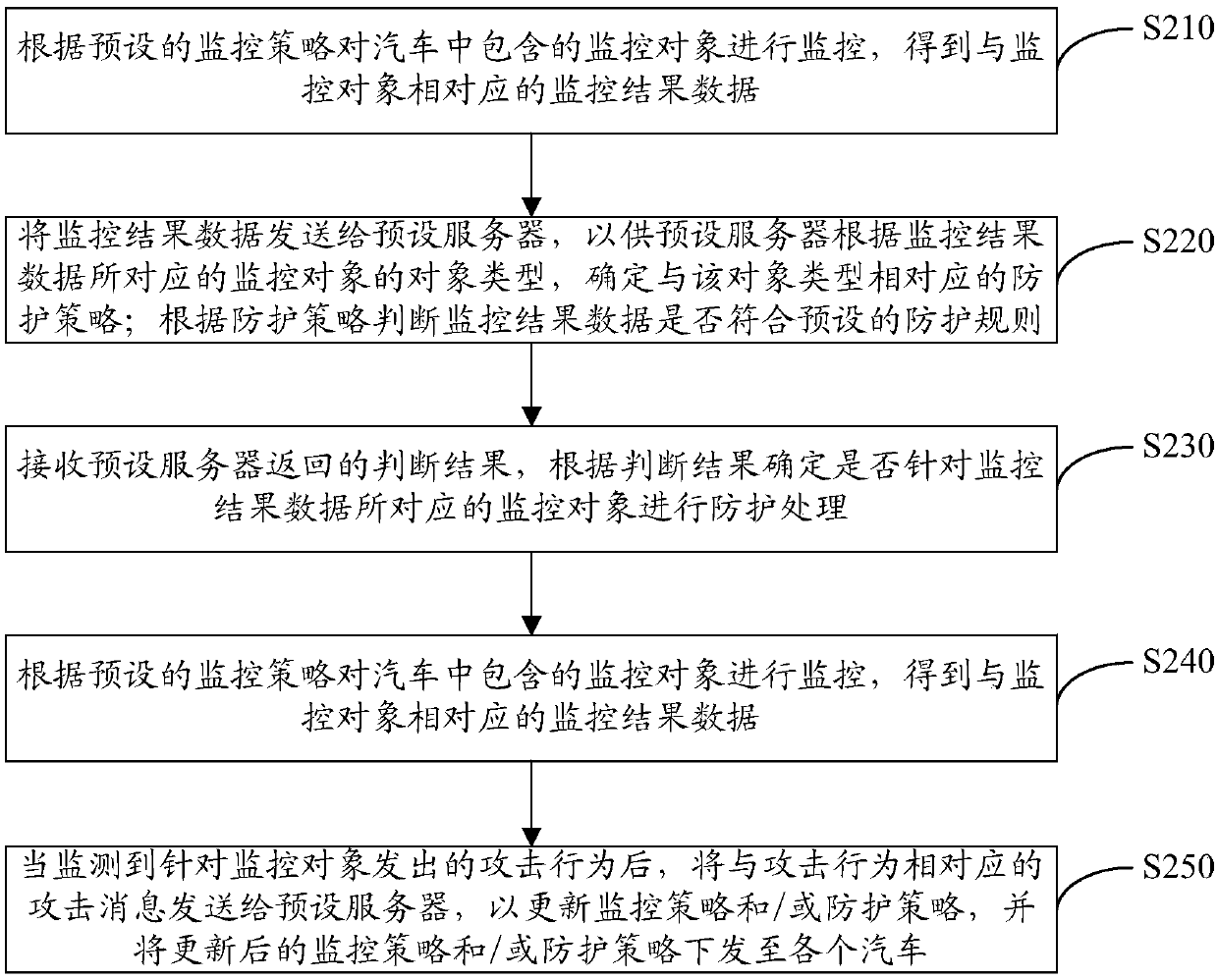
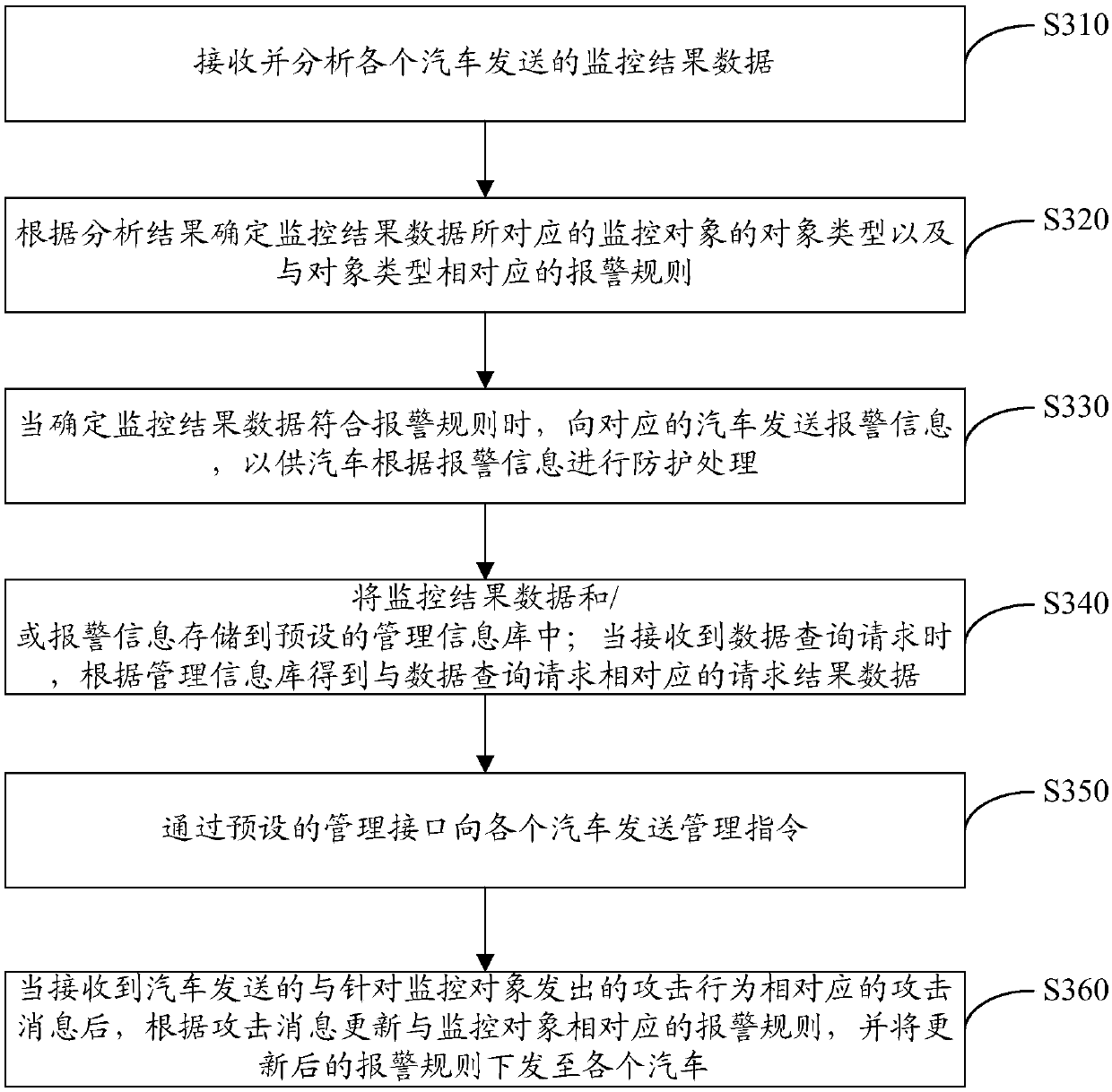
Car-based protection method, device and system
ActiveCN107634959AImprove securityPrevent cyber attacksTransmissionNetwork attackReal-time computing
The invention discloses a car-based protection method and device. The method comprises the following steps: monitoring a monitored object contained in a car according to a preset monitoring strategy to obtain monitoring result data corresponding to the monitored object; determining a protection strategy corresponding to an object type according to the object type of the monitored object corresponding to the monitoring result data; judging whether the monitoring result data meets a preset protection rule according to the protection strategy; if the monitoring result data meets the preset protection rule, performing protection processing on the monitored object corresponding to the monitoring result data. Visibly, each monitored object in the car can be monitored through the protection method disclosed by the invention, thereby acquiring the corresponding monitoring result data; the preset protection strategy is used for performing the protection, thereby preventing the car from being subjected to network attacked, and the security of the car is improved.
Owner:三六零数字安全科技集团有限公司
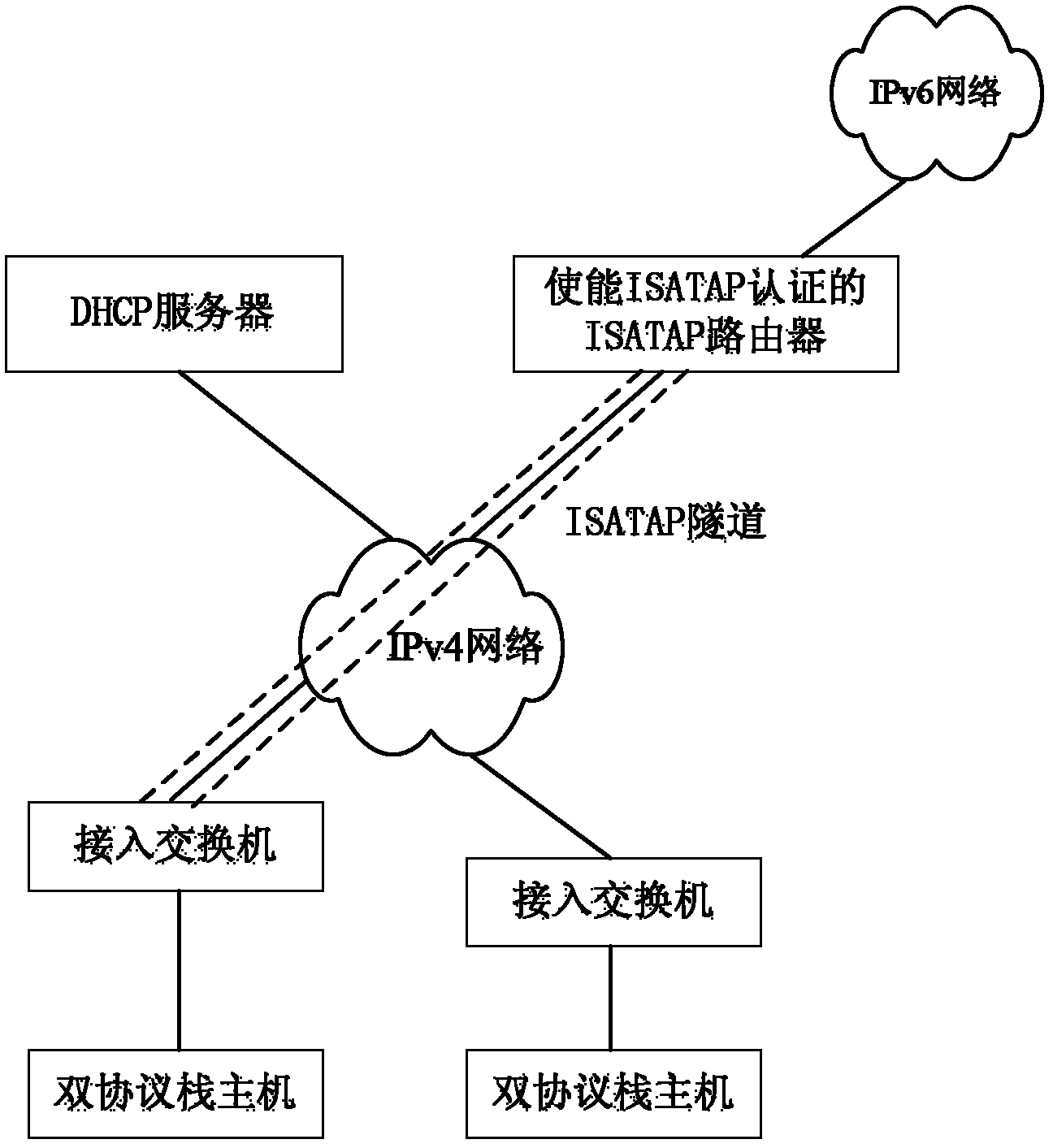
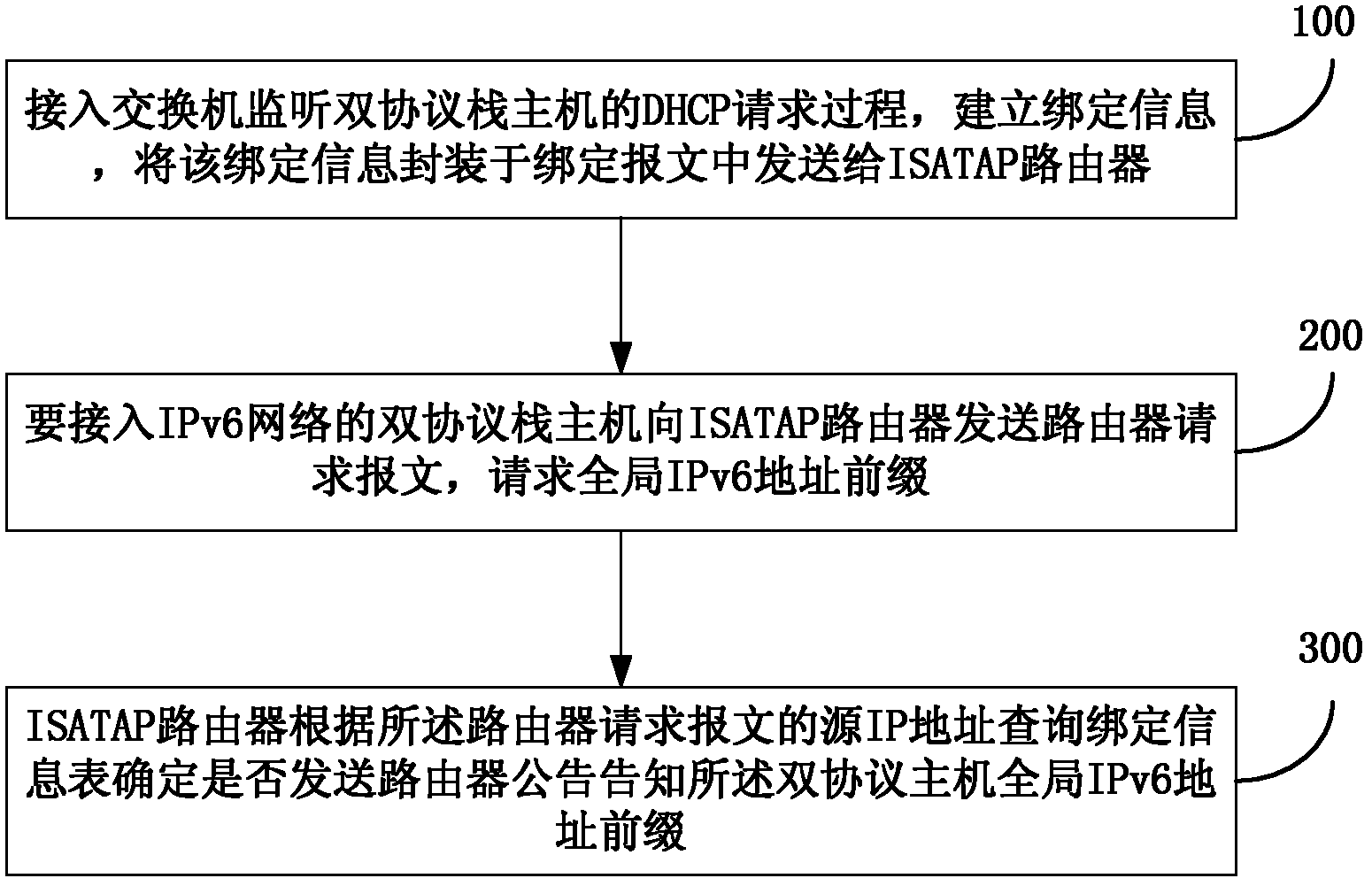
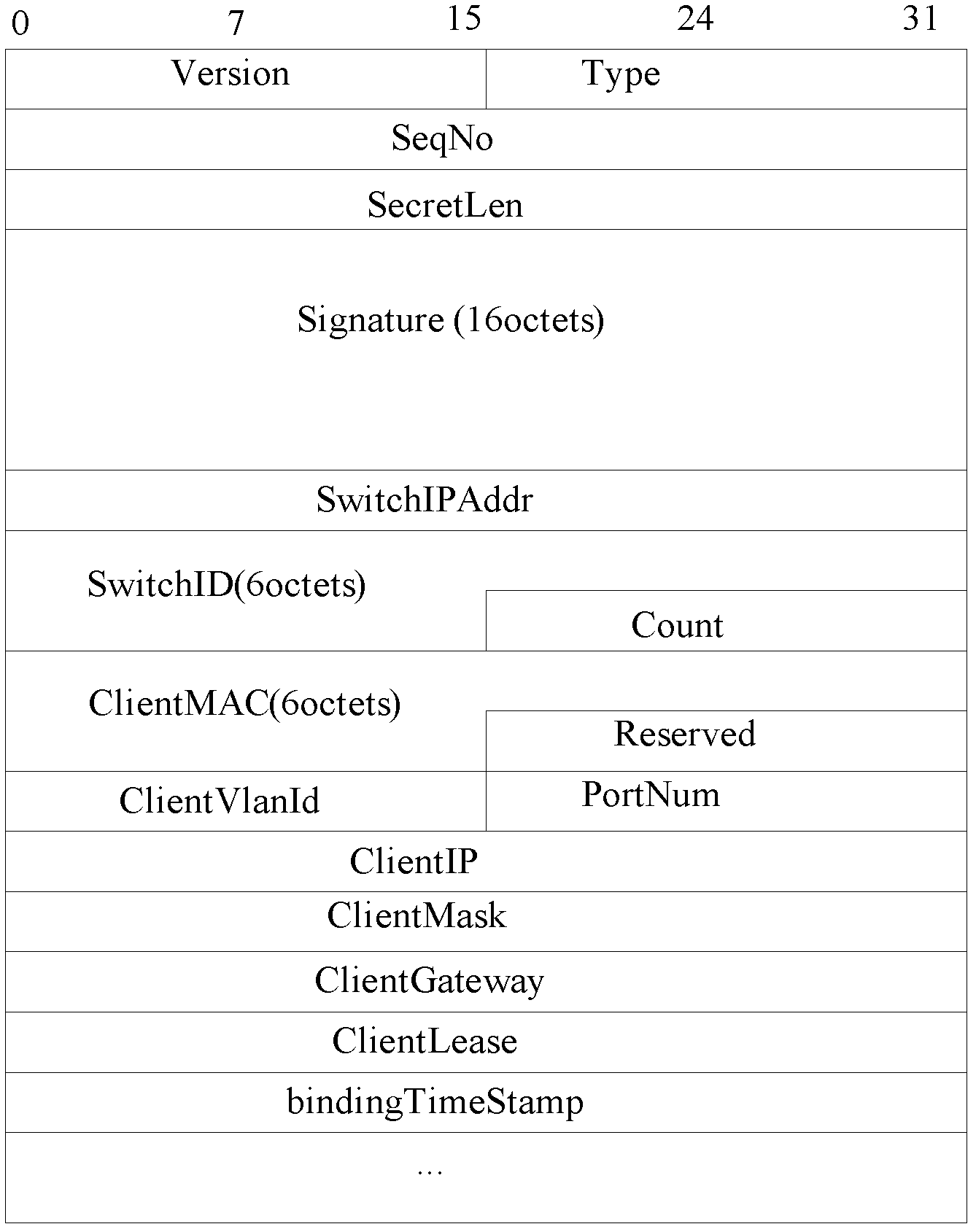
Method and system for authenticating intra-site automatic tunnel addressing protocol (ISATAP) tunnels based on dynamic host configuration protocol (DHCP) monitoring
The invention discloses a method and a system for authenticating intra-site automatic tunnel addressing protocol (ISATAP) tunnels based on dynamic host configuration protocol (DHCP) monitoring. The method includes that A an access switch monitors DHCP request processes of an internet protocol version 4 / internal protocol version 6 (IPv4 / IPv6) double-protocol stack host, binding information containing a media access control (MAC) address, an internet protocol (IP) address, a tenancy, a virtual local area network identifier and a port number of the double-protocol stack host is built, the binding information is packaged in a binding message, and the binding message is sent to a ISATAP router; B the double-protocol stack host to be accessed in a IPv6 network sends a router request message to the ISATAP router to request a prefix of a global IPv6 address; and C the ISATAP router inquires the binding information to determine whether a router advertisement is sent to notify the double-protocol stack host of the prefix of the global IPv6 address according to the IP address of the double-protocol stack host in the router request message.
Owner:北京神州数码云科信息技术有限公司
Biological characteristic-based security verification method, client and server
ActiveCN106330850APrevent replay attacksImprove securityMultiple keys/algorithms usagePublic key for secure communicationUser inputClient-side
The invention discloses a biological characteristic-based security verification method, a client and a server. The method includes the following steps that: a client sends an authentication request to a server; after receiving the authentication request, the server returns an authentication request reply message; the client receives a fingerprint image for verification inputted by a user, obtains a corresponding biometric characteristic template ID, compares the biometric characteristic template ID with a locally-stored biometric characteristic template ID in an enabling record, generates an authentication response message containing the acquired biometric characteristic template ID, and sends the authentication response message to the server; the server receives the authentication response message and compares the biometric characteristic template ID in the authentication response message with a locally-stored biometric characteristic template ID in a corresponding user record; if the biometric characteristic template ID in the authentication response message is matched with the locally-stored biometric characteristic template ID in the corresponding user record, verification is successful, otherwise, an error is reported. The present invention also provides a client and a server corresponding to the above method. With the biological characteristic-based security verification method, the client and the serve of the invention adopted, the risk of personal biological characteristic leakage when personal biological characteristics are uploaded to a network can be avoided, and the network traffic of network transmission can be decreased, and therefore, higher security can be achieved.
Owner:ADVANCED NEW TECH CO LTD
Authentication method and device based on GPRS network and integrated identification network
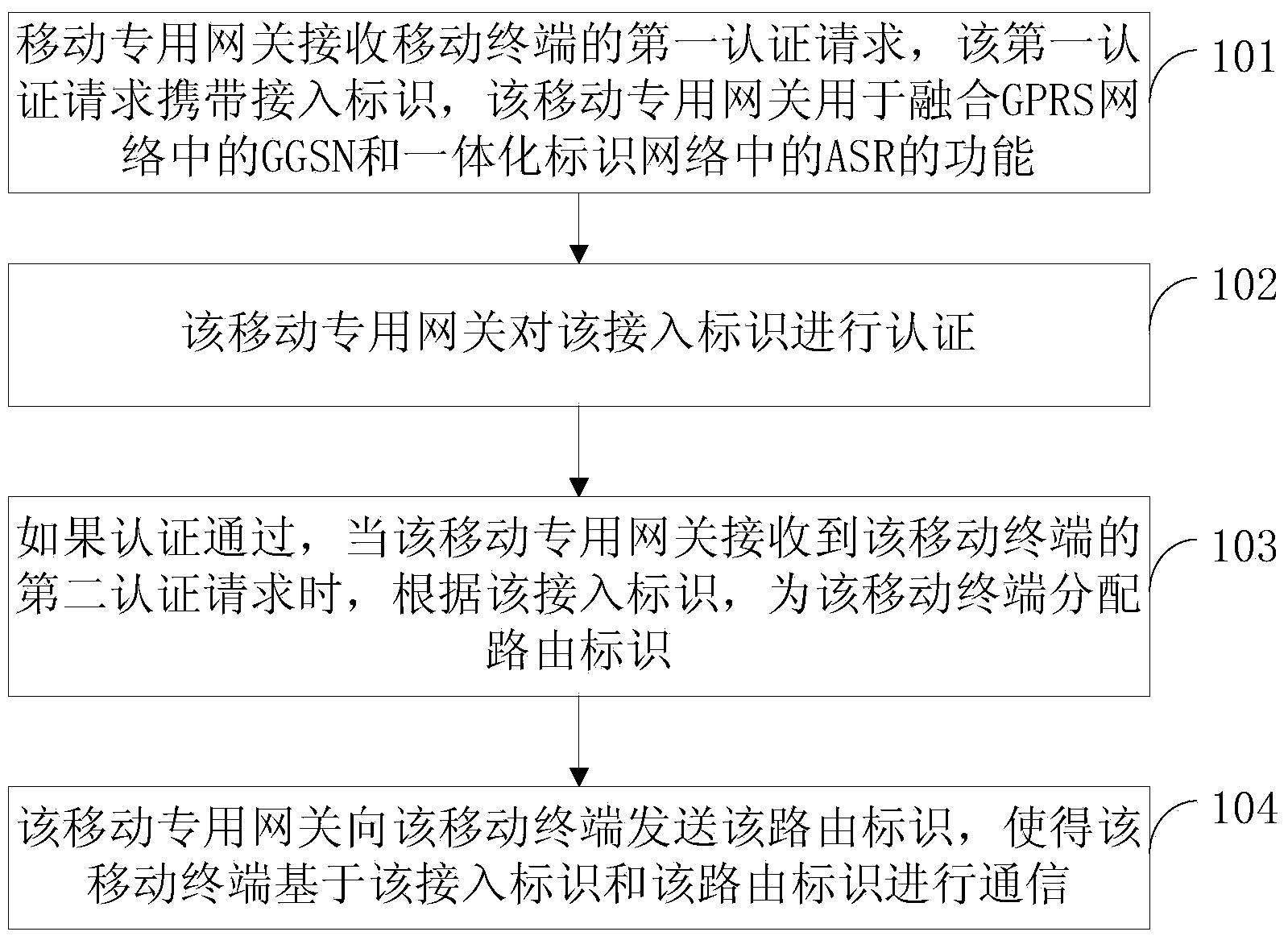
InactiveCN104168564APrevent cyber attacksImprove securitySecurity arrangementEngineeringNetwork attack
The invention discloses an authentication method and a device based on a GPRS network and an integrated identification network, belonging to the network technology field. The method comprises: receiveing a first authentication request of a mobile terminal by a mobile exclusive gateway, wherein the first authentication request carries an accessing identifier, performing authentication on the accessing identifier, if the authentication is passed, distributing a rout identifier to the mobile terminal according to the accessing identifier when the mobile exclusive gateway receives a second authentication request of the mobile terminal, and transmitting the rout identifier to the mobile terminal to enable the mobile terminal to communicate with the rout identifier based on the accessing identifier. The invention integrates the GGSN function in the GPPS network and the ASP function in the integrated network, enables the mobile terminal to communicate with the rout identifier based on the accessing identifier, and distributes the rout identifier to the mobile terminal when the authentication of the accessing identifier is passed, so that the possible network attack can be avoided and the safety is greatly improved.
Owner:BEIJING JIAOTONG UNIV
Method and device for preventing network attack based on Web authentication technology
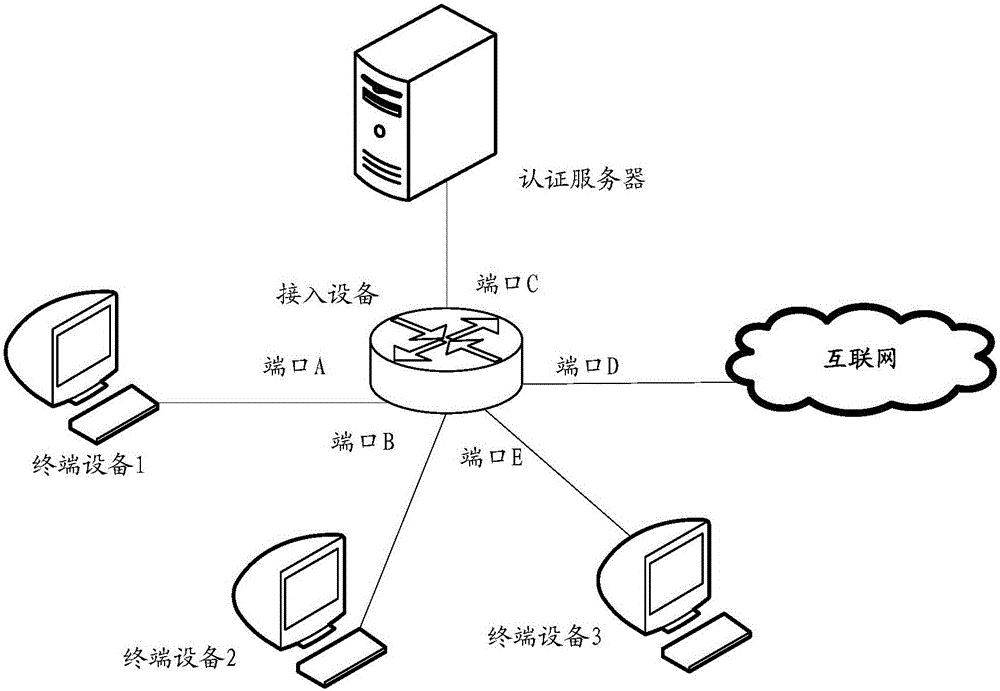
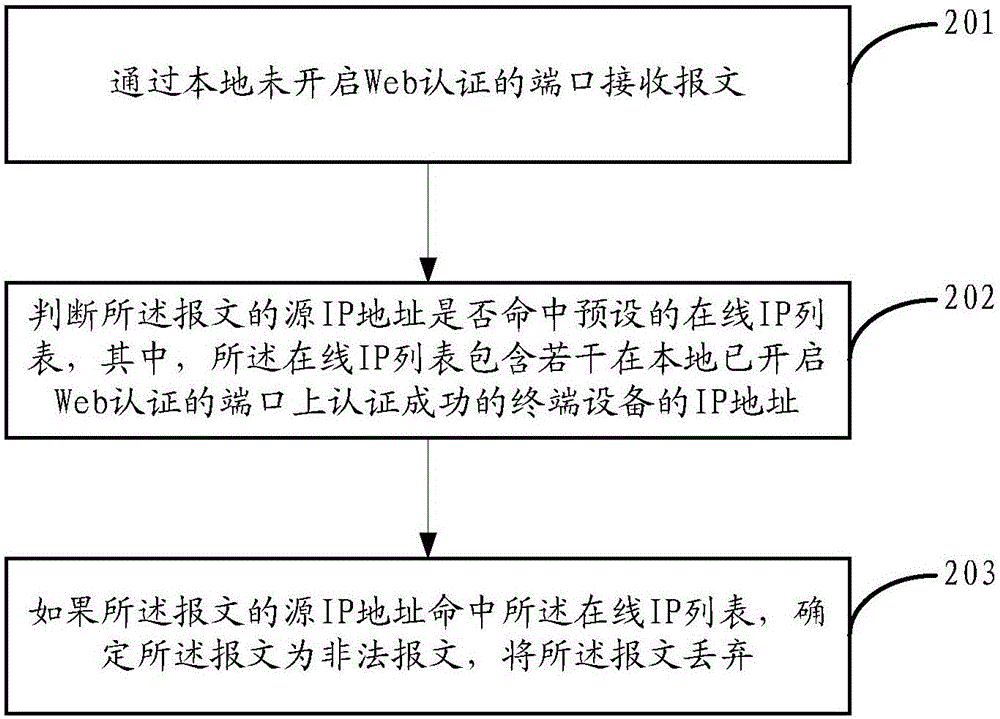
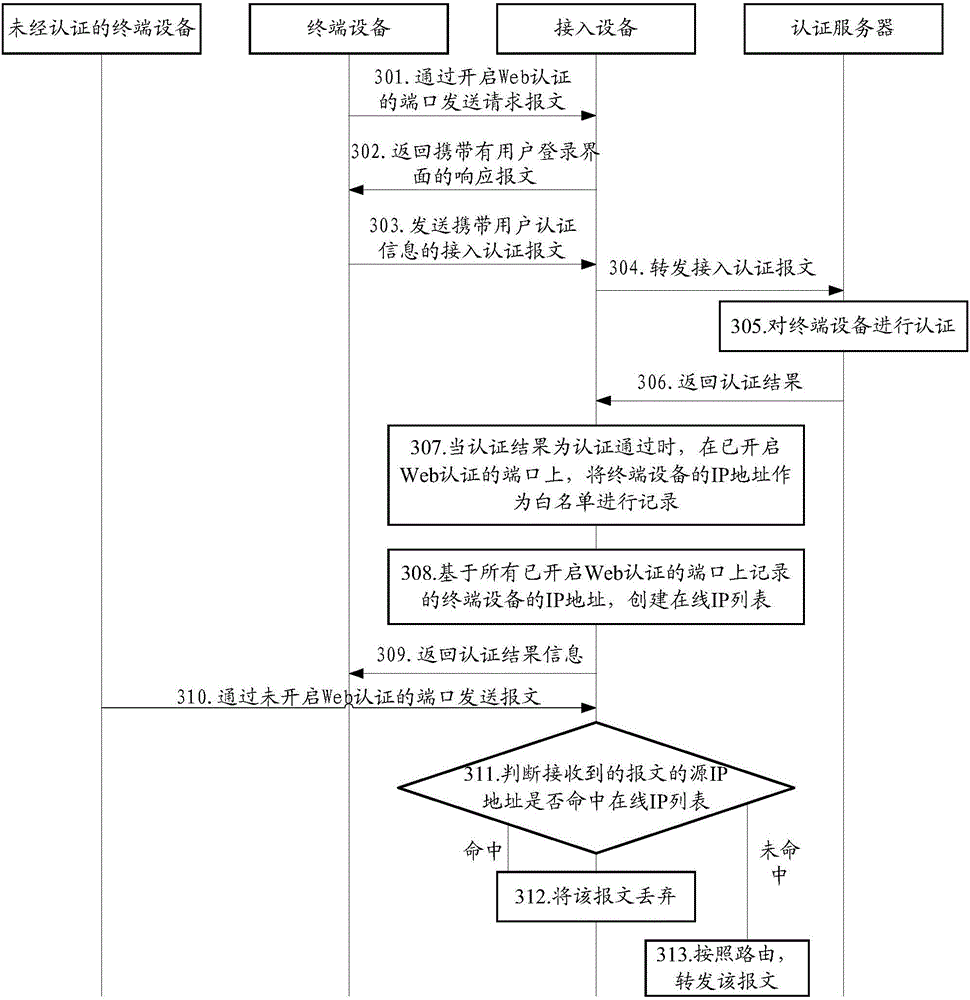
InactiveCN106230781APrevent cyber attacksPrevent cyberattacksTransmissionWeb authenticationIp address
The invention provides a method and a device for preventing network attack based on a Web authentication technology. The method comprises the steps of receiving a message through a port which does not open Web authentication locally; judging whether a source IP address of the message hits a preset online IP list or not, wherein the online IP list contains a plurality of IP addresses of terminal equipment which are already successfully authenticated on a port which already opens Web authentication locally; and determining the message is an illegal message if the source IP address of the message hits the online IP list, and discarding the message. By applying the embodiment of the invention, access equipment can be prevented from initiating a network attack behavior through embezzling an IP address of terminal equipment which passes Web authentication.
Owner:HANGZHOU DPTECH TECH
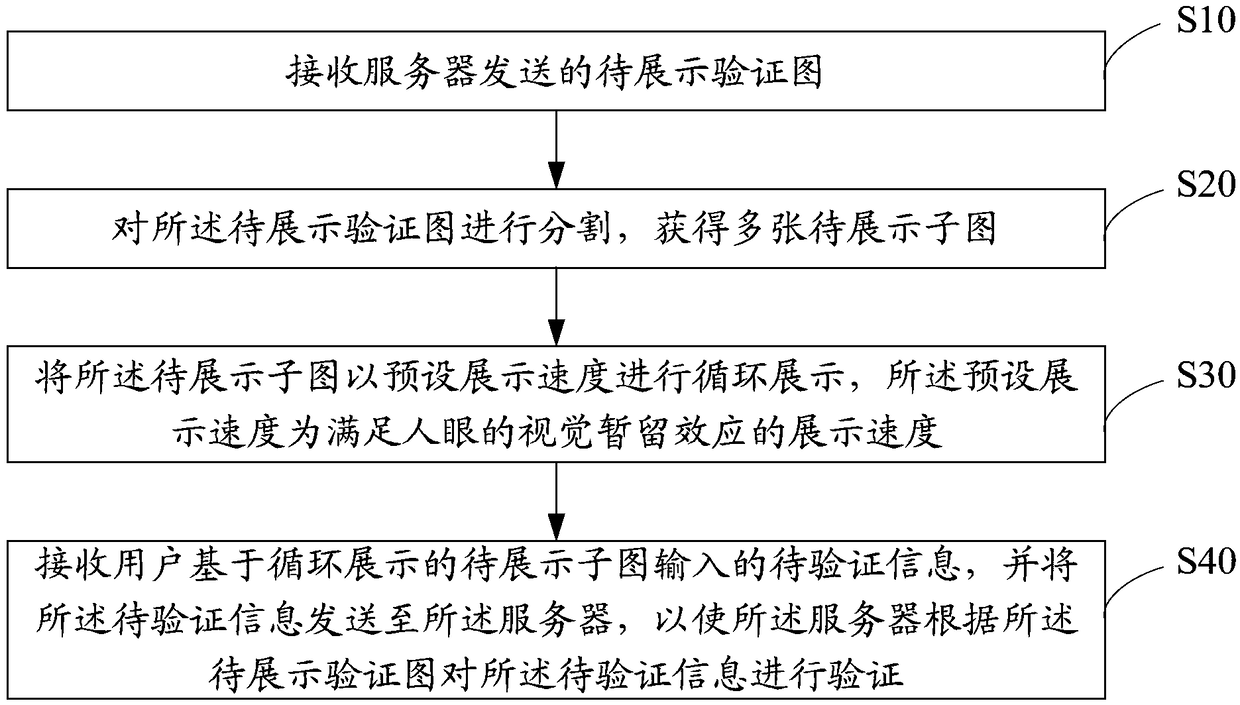
Dynamic subgraph-based authentication method, device, user equipment and storage medium
InactiveCN109388933AAvoid illegal registrationPrevent cyber attacksCharacter and pattern recognitionDigital data authenticationValidation methodsUser input
The invention discloses an authentication method, a device, a user equipment and a storage medium based on a dynamic sub-graph. As that verification map to be displayed is segmented, a plurality of sub-images to be displayed are obtained, the sub-image to be displayed is cyclically displayed at a display speed satisfying the visual retention effect of the human eye, Then the information to be verified inputted by the user is sent to the server, and the server verifies the information to be verified, which can ensure that the image interception technology and the image recognition technology can not obtain the effective information from a single sub-image to be displayed, and can effectively avoid various illegal registration and network attacks.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
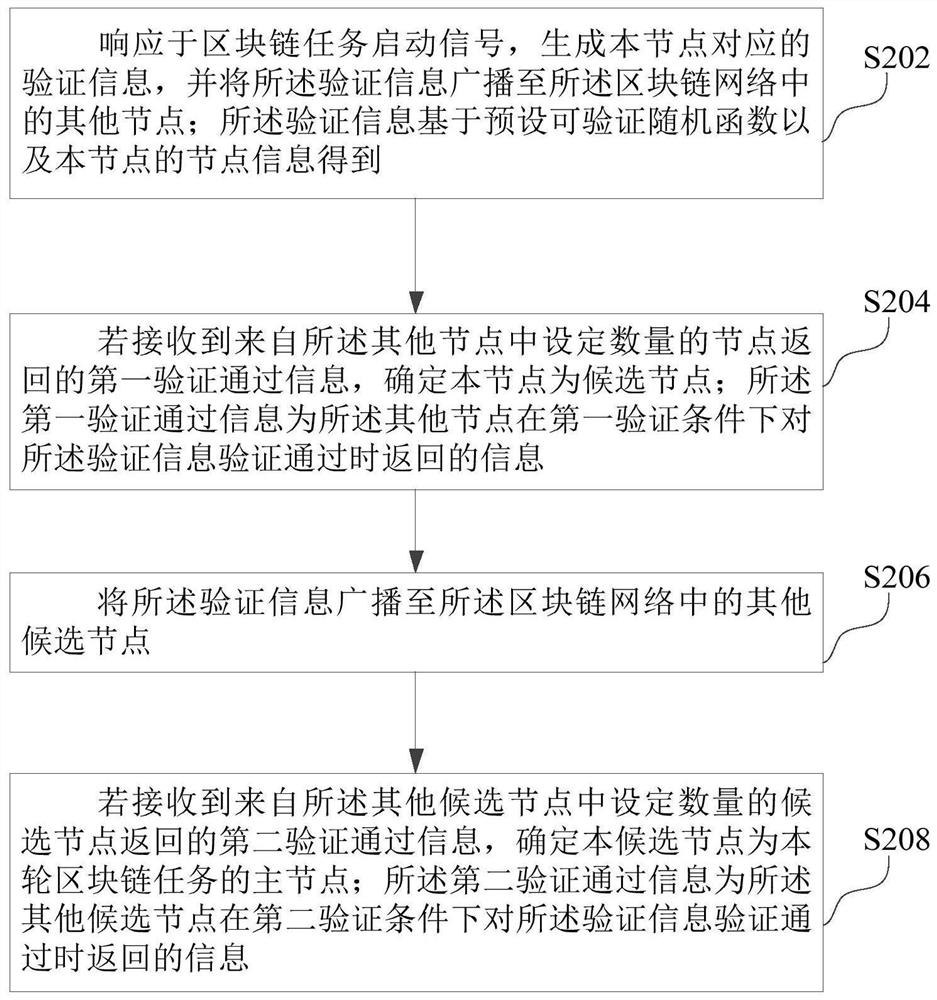
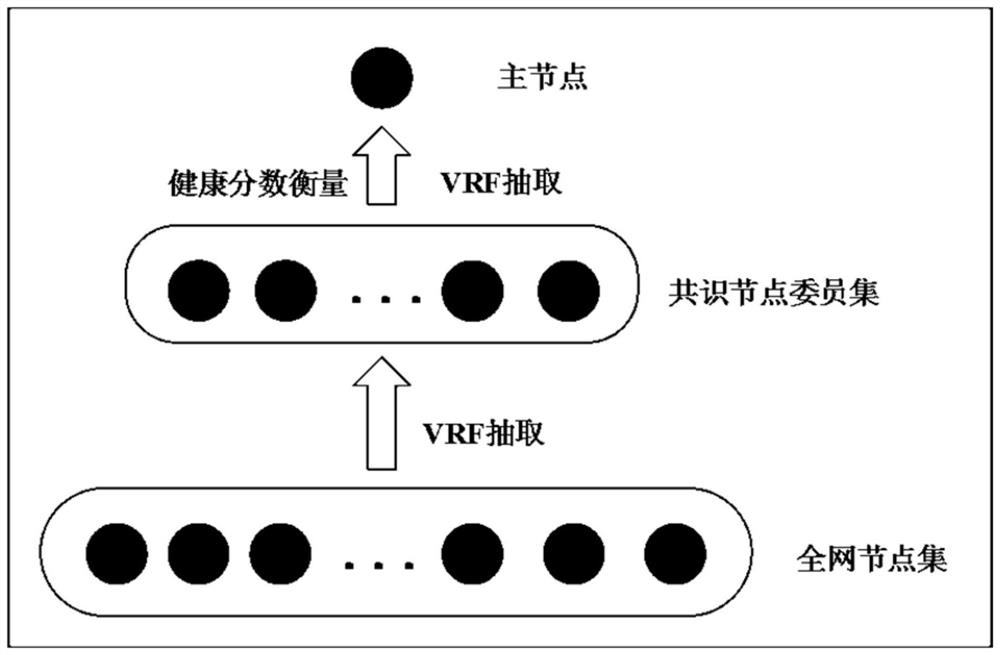
Block chain consensus node selection method and device, computer equipment and storage medium
ActiveCN113301114AIncrease randomnessImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer networkConsensus
The invention relates to a block chain consensus node selection method and device, computer equipment and a storage medium. The method comprises the steps of broadcasting verification information of the node to other nodes in the block chain, and when a set number of first verification passing information is received, determining the node as a candidate node; and when the node is a candidate node, broadcasting verification information of the candidate node to a plurality of candidate nodes in the candidate node set, and when a set number of second verification passing information is received, determining that the candidate node is a main node. Compared with a traditional method for selecting nodes through proven of rights and interests or a practical Byzantine fault-tolerant algorithm, according to the scheme, multiple rounds of verification are carried out by utilizing verification information formed based on various node information and a verifiable random function, the randomness of node selection is improved, network attacks carried out through predicted nodes are prevented, and the effect of improving the node security is achieved.
Owner:GUANGDONG POWER GRID CO LTD +1
Information processing device, information processing method, and recording medium
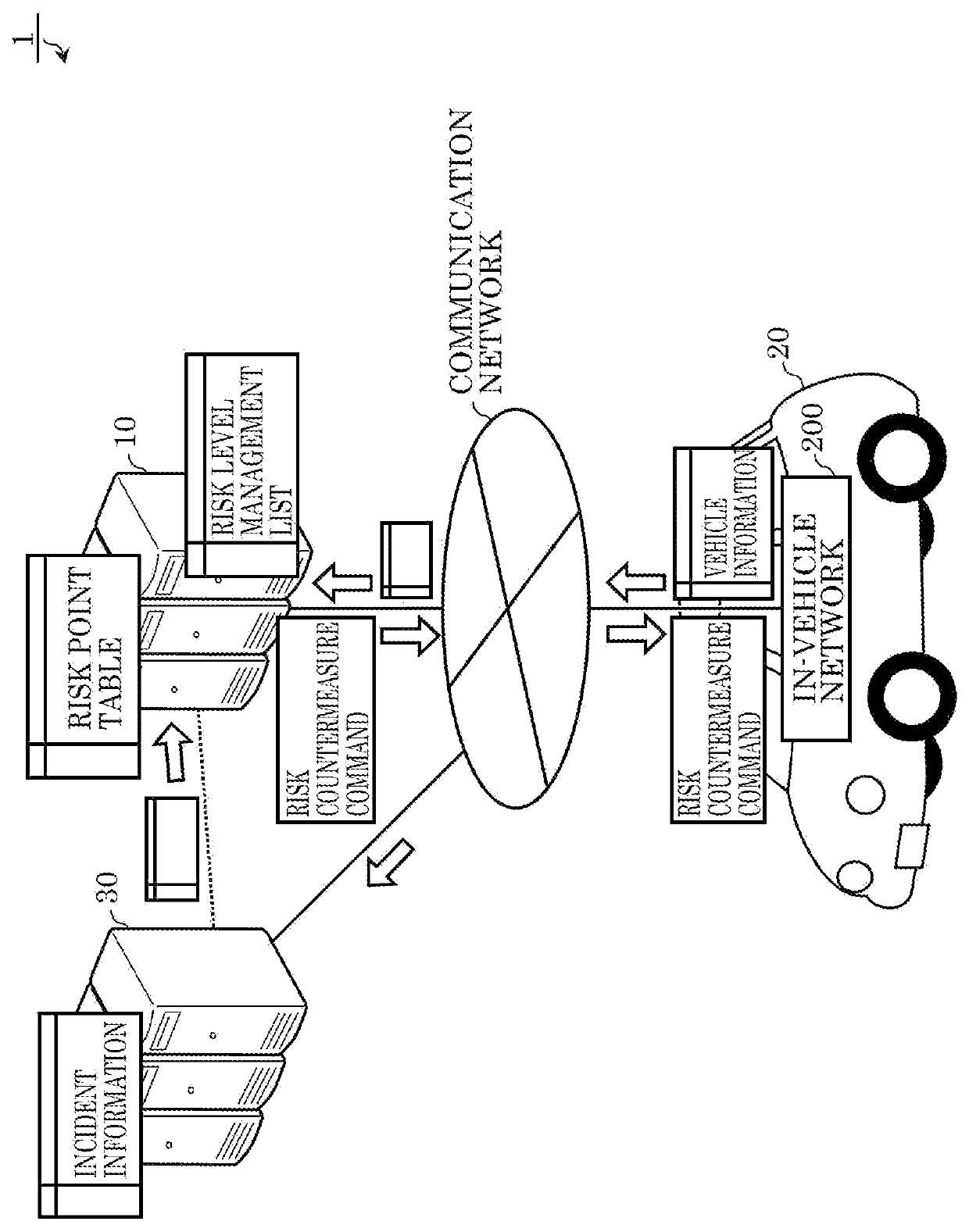
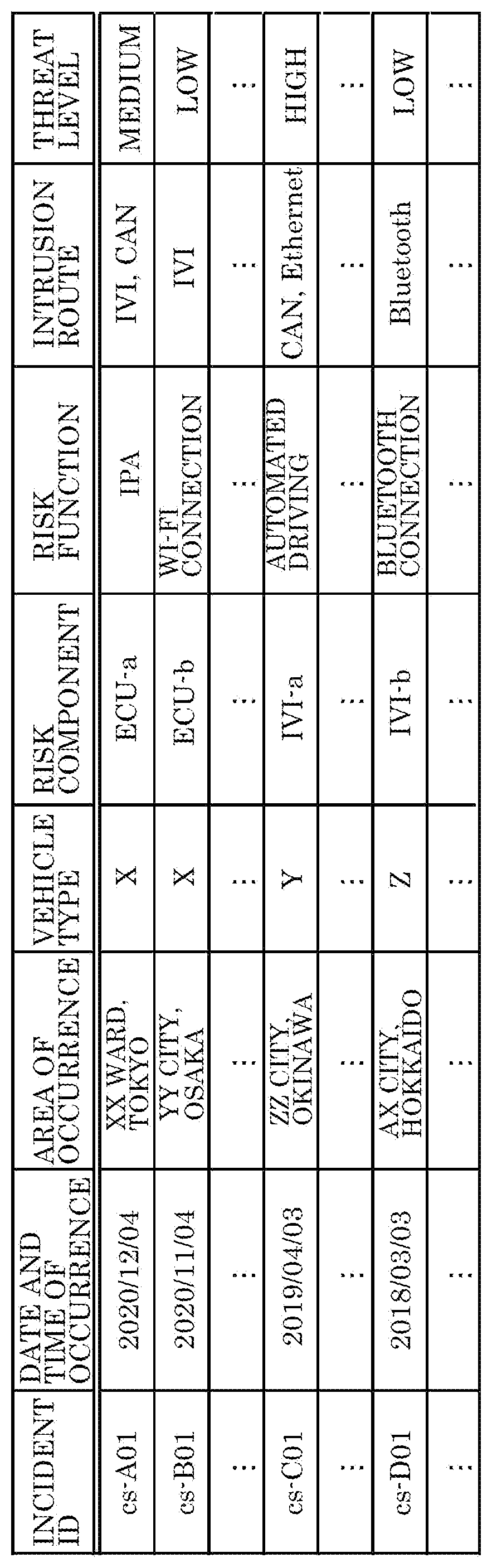
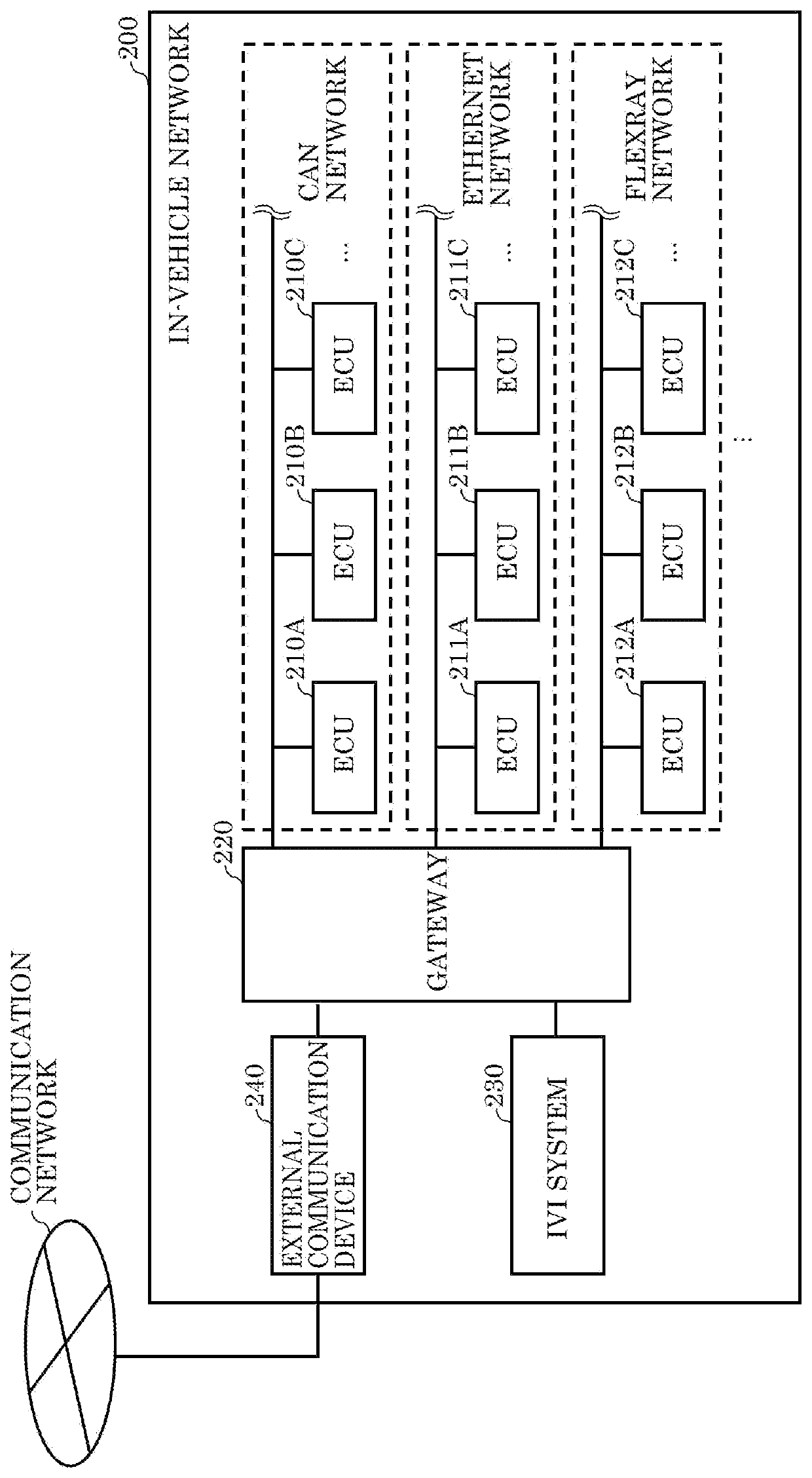
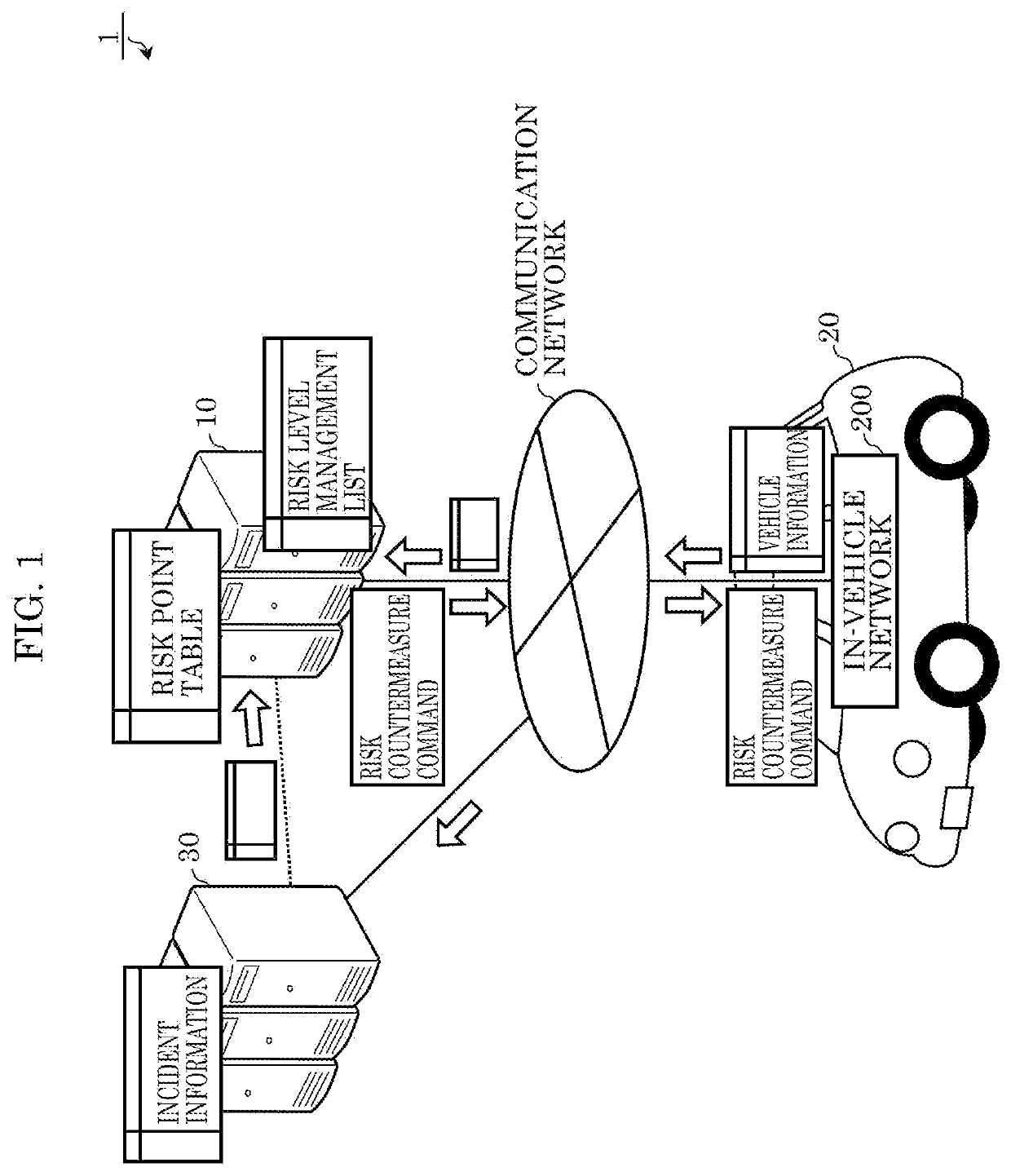
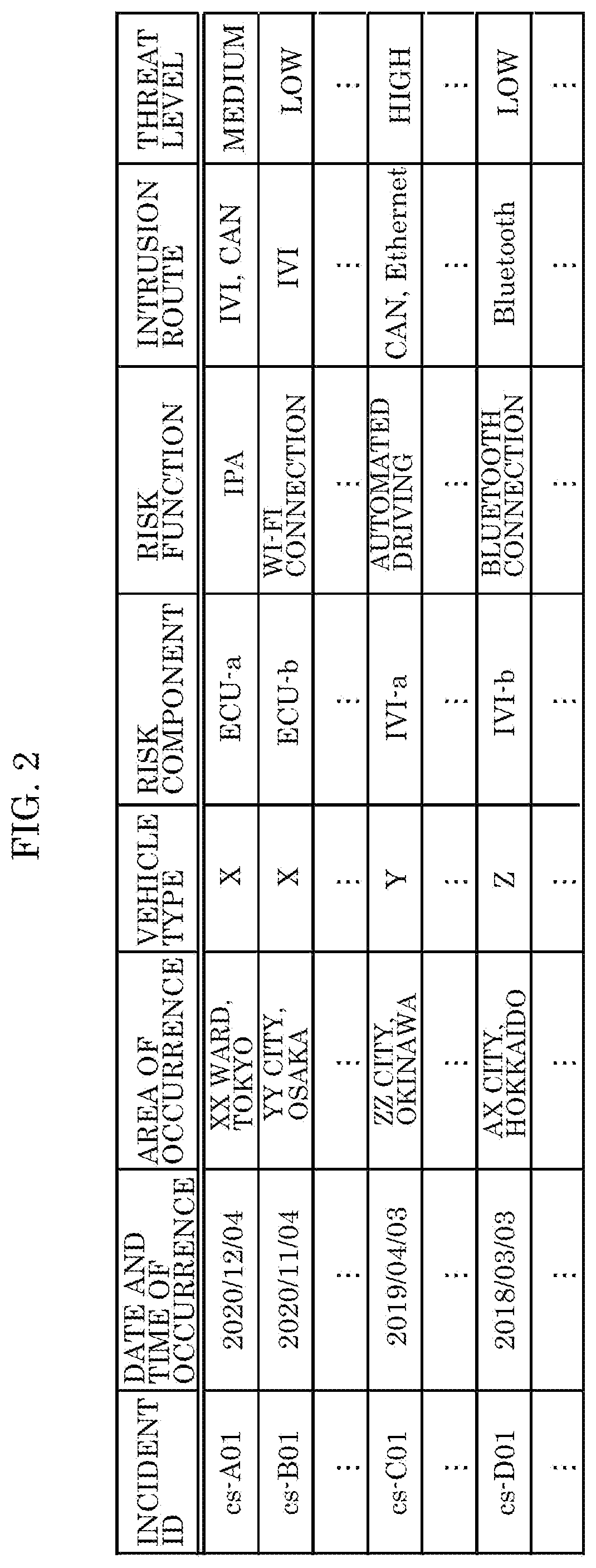
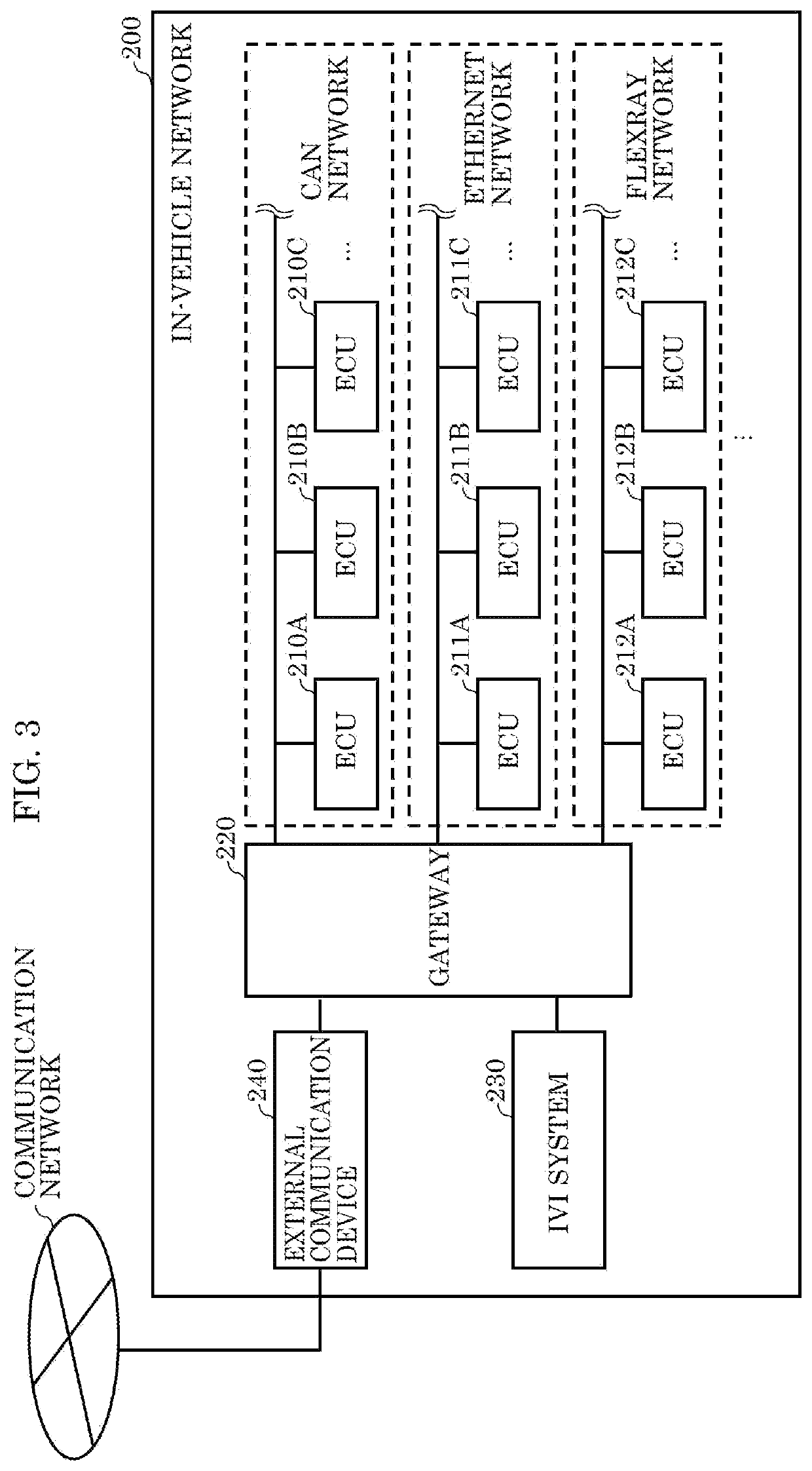
PendingUS20210232687A1Avoid damagePrevent intrusionAnti-theft devicesData switching by path configurationRisk levelInformation processing
An information processing device includes: a processor; and a memory including at least one set of instructions that, when executed by the processor, causes the processor to perform operations. The operations include: obtaining incident information about an incident of a cyberattack that occurred in a vehicle; obtaining first vehicle information about a state of a first vehicle; storing, in the memory, the incident information and the first vehicle information; determining a risk level of a vehicle function of the first vehicle, based on a degree of matching between the incident information and the first vehicle information stored in the memory, the vehicle function of the first vehicle being one among one or more vehicle functions of the first vehicle; generating a function restriction command for restricting the vehicle function, when the risk level is higher than a first criterion; and outputting the function restriction command.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
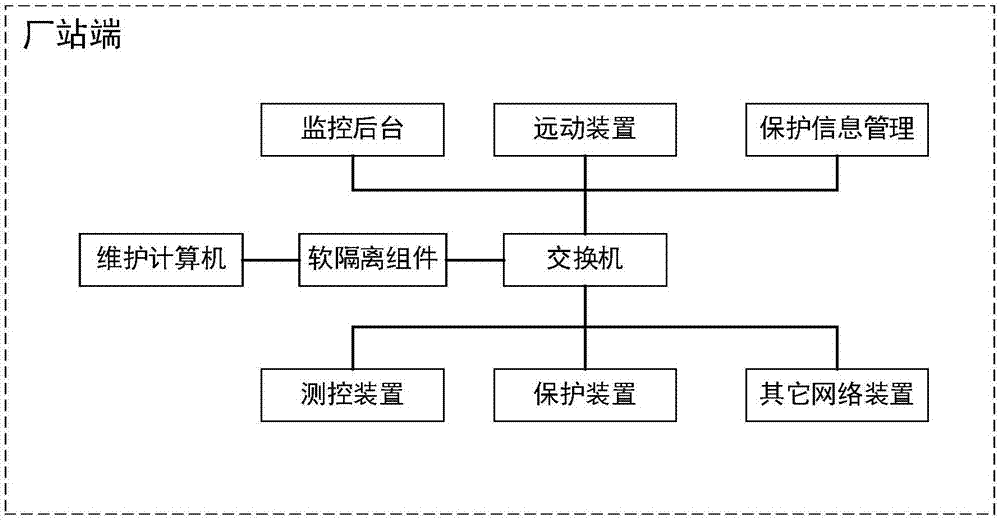
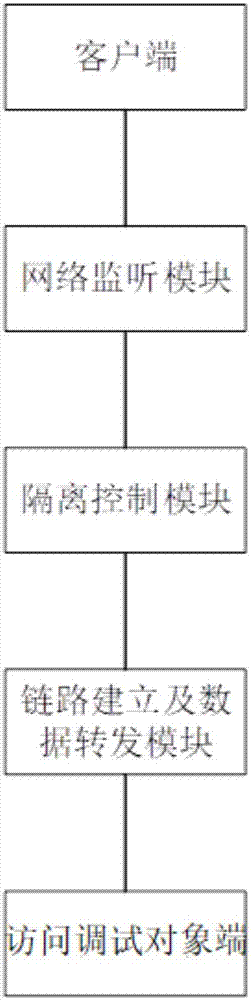
Soft isolation assembly for network access debugging and using method thereof
InactiveCN108011748AMaintenance isolationPrevent cyber attacksData switching networksNetwork structureStructure of Management Information
The invention provides a soft isolation assembly for network access debugging and a using method thereof. A network monitoring module, an isolation control module and a link establishment and data forwarding module are included; the network monitoring module is responsible for monitoring a debugging port information network to access debugging port information and submitting client link establishment information and transmitted data to the isolation control module; the isolation control module analyzes the link information and the transmitted data and compares the information with a pre-configured authorized access condition, the network data belonging to an allowable access range are submitted to the link establishment and data forwarding module, and the network data not belonging to theallowable access range are blocked. In a condition of not changing a network structure and debugging object parameters, isolation, monitoring and control on a maintenance computer and a device are carried out when an operation and maintenance person accesses and debugs the device, device access by the operation and maintenance person in excess of authority and network attacks on the device by themaintenance computer can be avoided, and the safety operation of a substation network and the device is ensured.
Owner:南京捷安信息科技有限公司
Information processing device, information processing method, and recording medium
PendingUS20210240838A1Avoid damagePrevent intrusionRoad vehicles traffic controlAnti-theft devicesInformation processingRisk level
An information processing device comprising: a processor; and a memory including at least one set of instructions that, when executed by the processor, causes the processor to perform operations. The operations include: obtaining incident information about an incident of a cyberattack that occurred in a vehicle; obtaining second vehicle information about a state of a second vehicle via communication with the second vehicle; determining a risk level of a vehicle function of the second vehicle based on a degree of matching between the incident information and the second vehicle information; generating a function restriction command for restricting a vehicle function of a first vehicle corresponding to the vehicle function of the second vehicle, when the risk level is higher than a first criterion, the vehicle function of the first vehicle being one among one or more vehicle functions of the first vehicle; and outputting the function restriction command.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Method for implementing improving success ratio of access authentication of AAA server
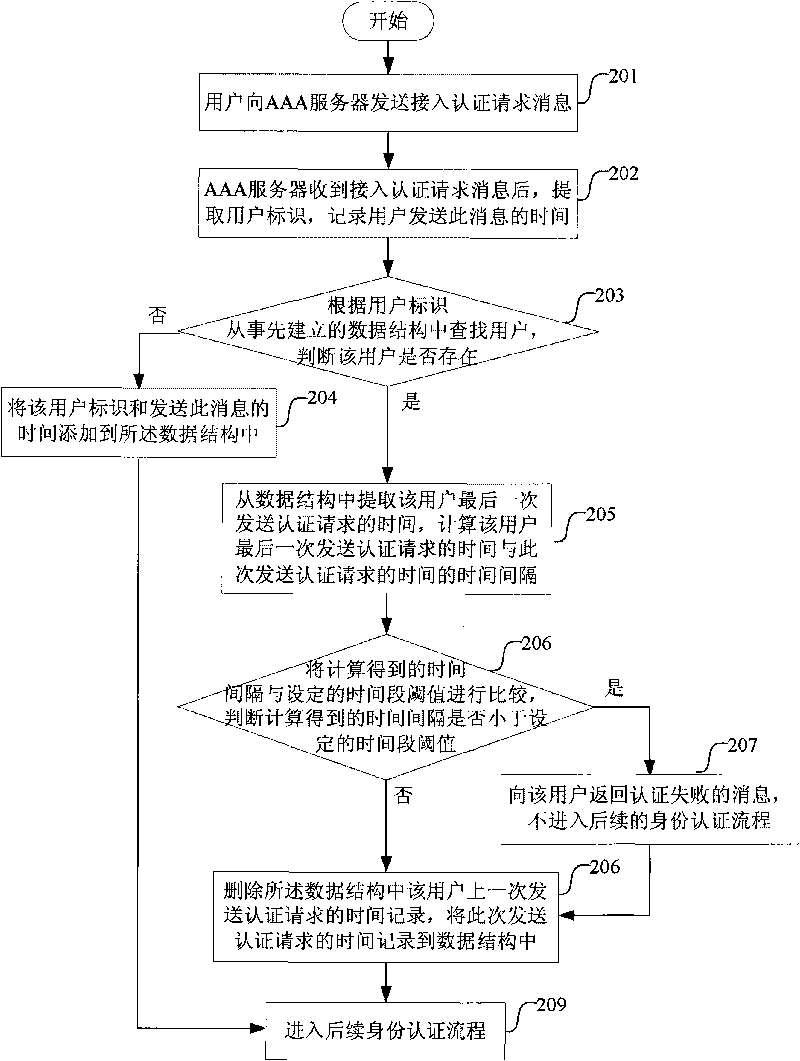
InactiveCN101729504AImprove access authentication success ratePrevent cyber attacksUser identity/authority verificationTime conditionDigest access authentication
The invention discloses a method for implementing improving a success ratio of access authentication of an AAA server, which improves the success ratio of access authentication service under the condition of not changing hardware equipment. The method comprises the following steps that: after the AAA server receives an access authentication request sent by a user each time, the AAA server calculates the time interval between the time of the access authentication request and the time of a last access authentication request, compares the time interval with preset time conditions, makes the user which satisfies the conditions enter subsequent identity authentication and processing flow, and directly refuses the access authentication request of the user which does not satisfy the conditions.
Owner:ZTE CORP
Single packet authorization method and system
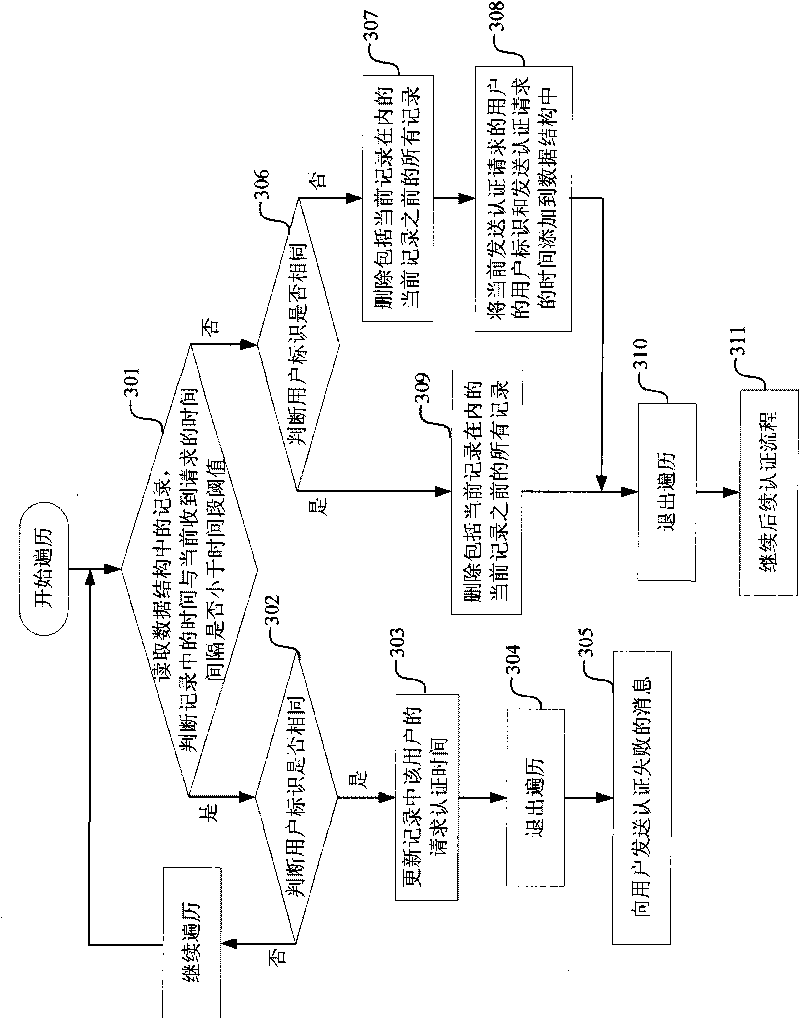
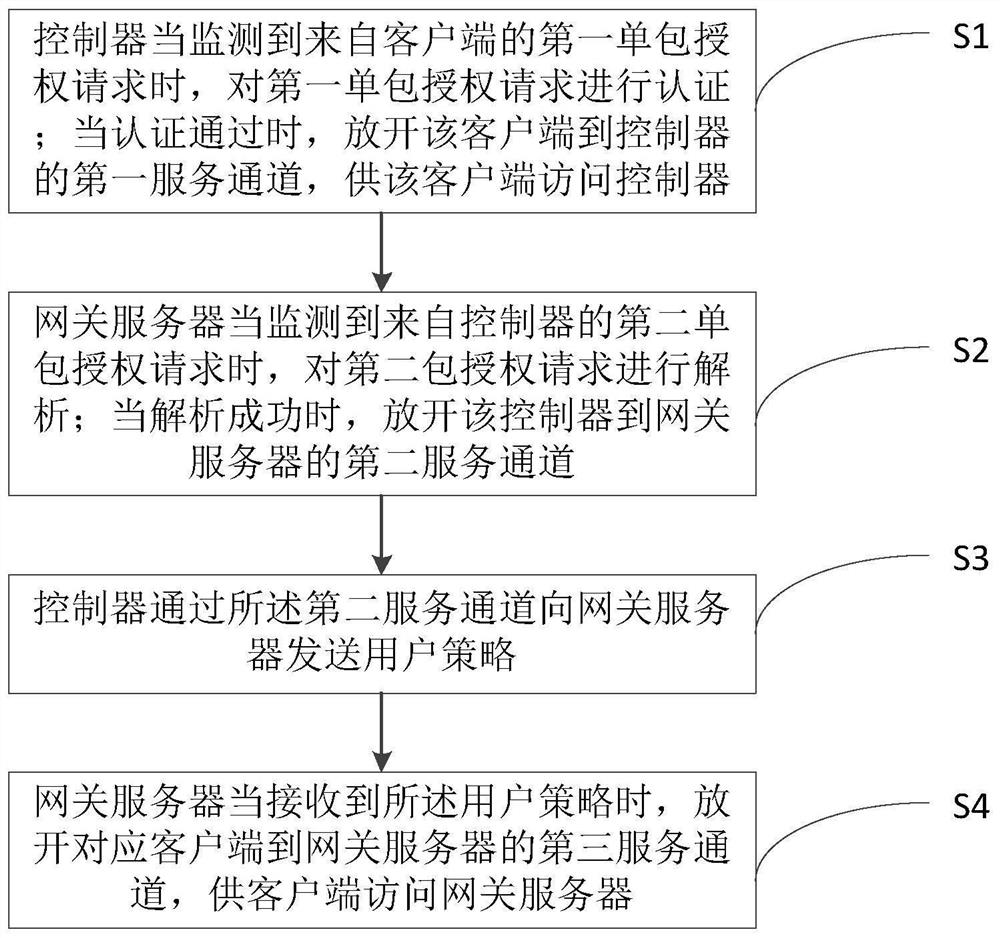
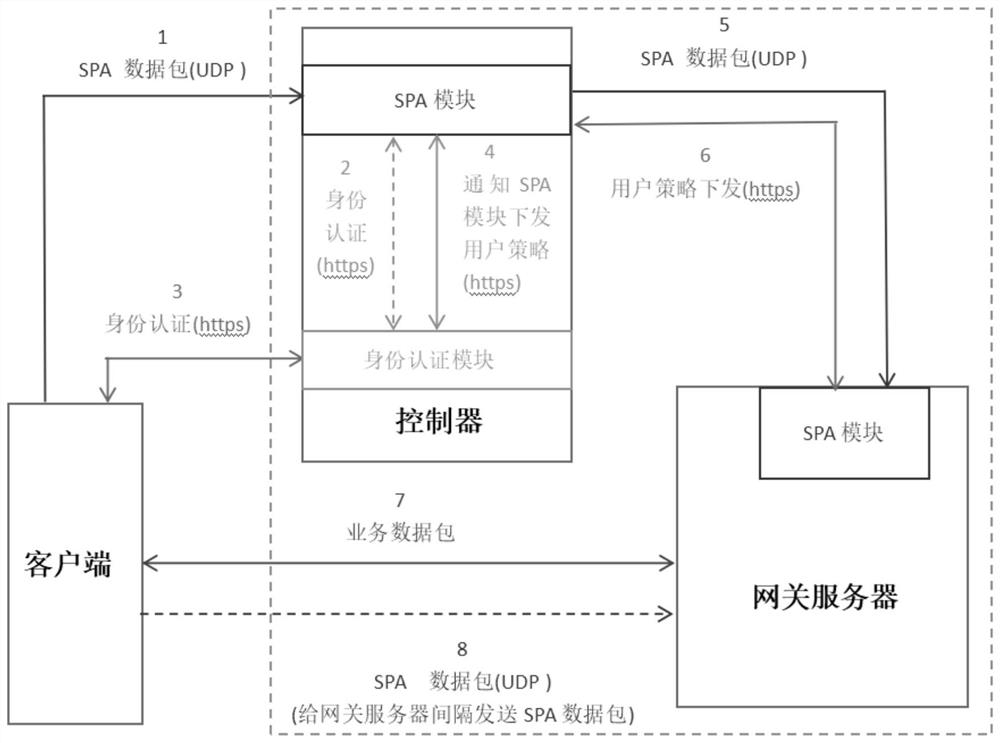
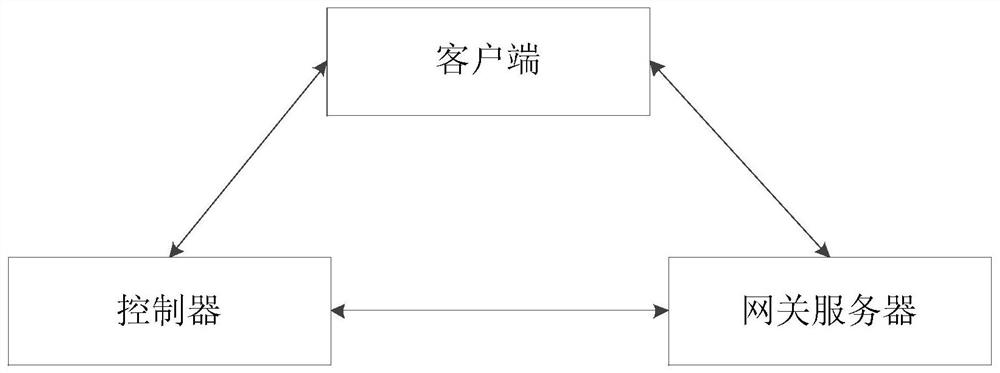
The invention provides a single packet authorization method and system. The method comprises the following steps: a controller carries out the authentication of a first single packet authorization request when monitoring the first single packet authorization request from a client; when the authentication is passed, a first service channel is released from the client to the controller for the client to access the controller; a gateway server analyzes a second packet authorization request when monitoring the second single packet authorization request from the controller; when the analysis is successful, a second service channel is released from the controller to the gateway server; the controller sends a user strategy to a gateway server through the second service channel; when receiving theuser strategy, the gateway server releases a third service channel from the corresponding client to the gateway server, and therefore the client can access the gateway server. The method can preventmost network attacks.
Owner:SHENZHEN LEAGSOFT TECH
Method of guarding network attack
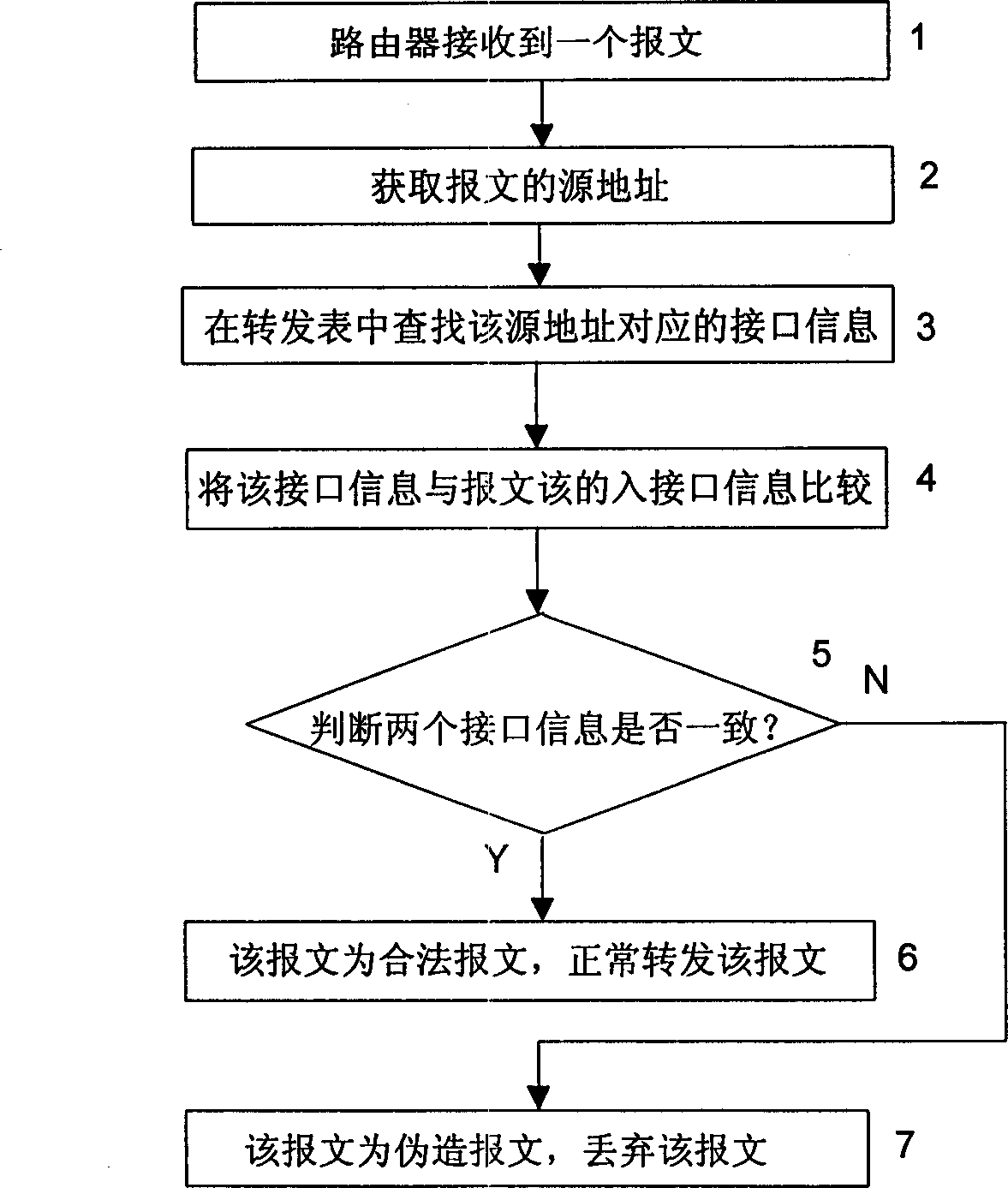
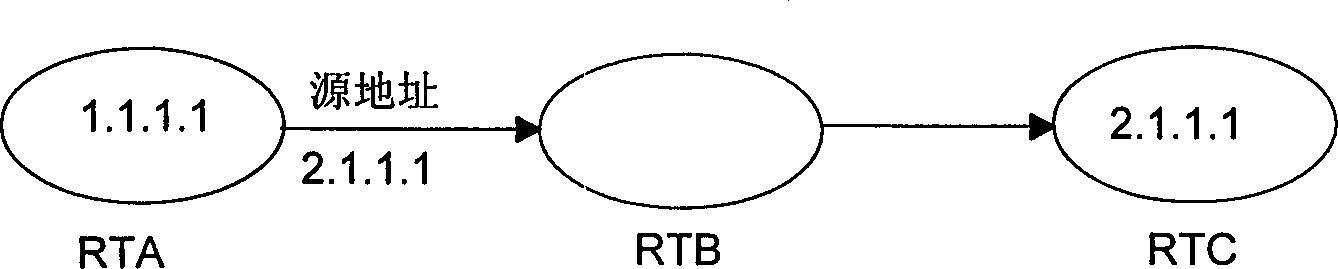
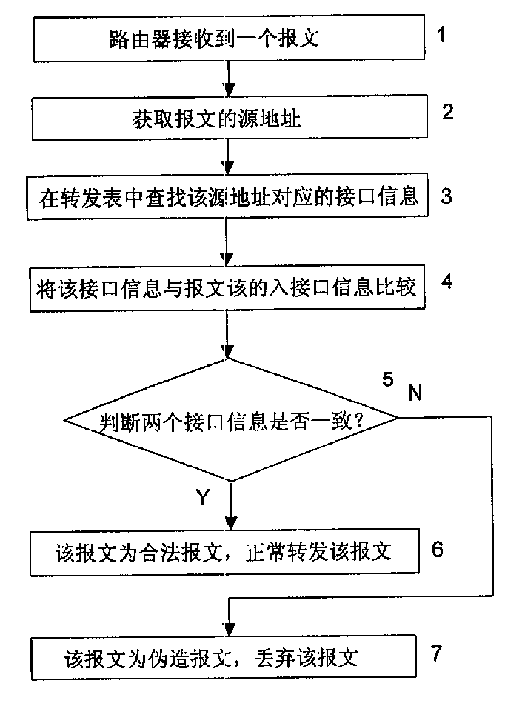
InactiveCN1152517CEnsure safetyPrevent cyber attacksData switching networksSecuring communicationNetwork addressingNetwork address
This invention relates to a method for preventing network from attack includes firstly, setting network address and interface information correspondent relationship list in network equipment, namely, network addresses of other network equipment connected with the said network equipment interface and applied interface information correspondent relation list of other network equipment connected on the said network; the route transferred list can be used in a router then the network equipment looks for the said correspondent relationship list according to the original address of the received message and makes judgment in terms of the result it is fake to determine the addressability of the message.
Owner:HUAWEI TECH CO LTD
Transaction information exchange method and system between internal and external networks in financial industry
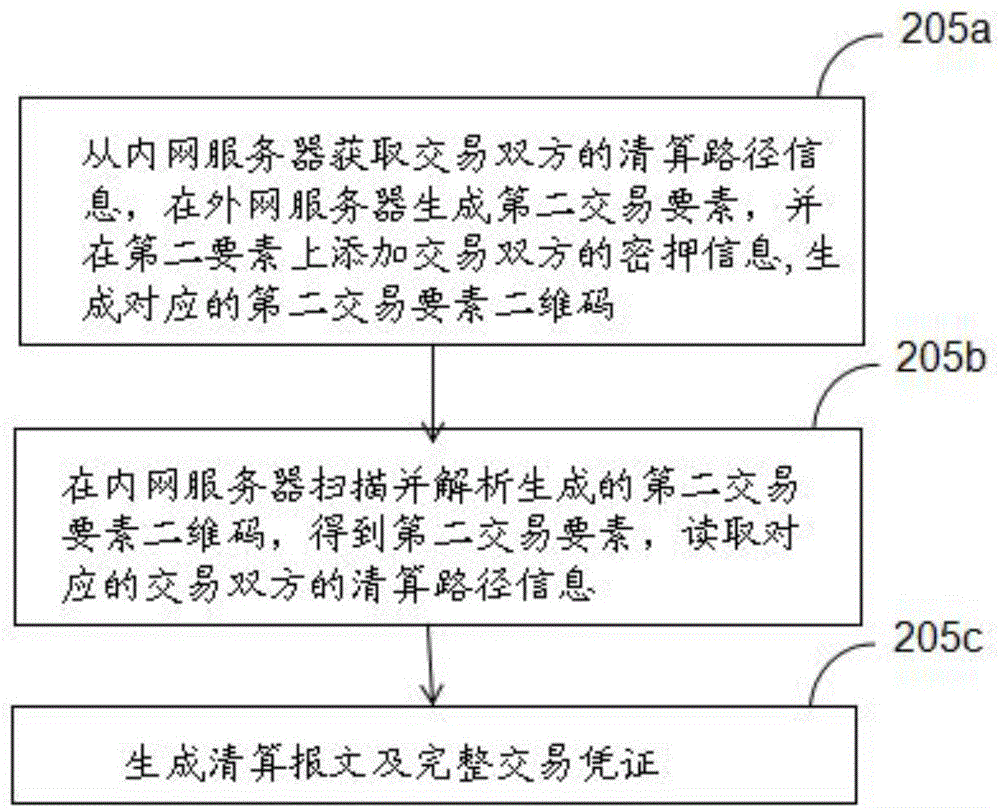
ActiveCN107437102AAvoid Intranet Information LeakageImprove accuracy and safetyFinanceCo-operative working arrangementsComputer securityCounterparty
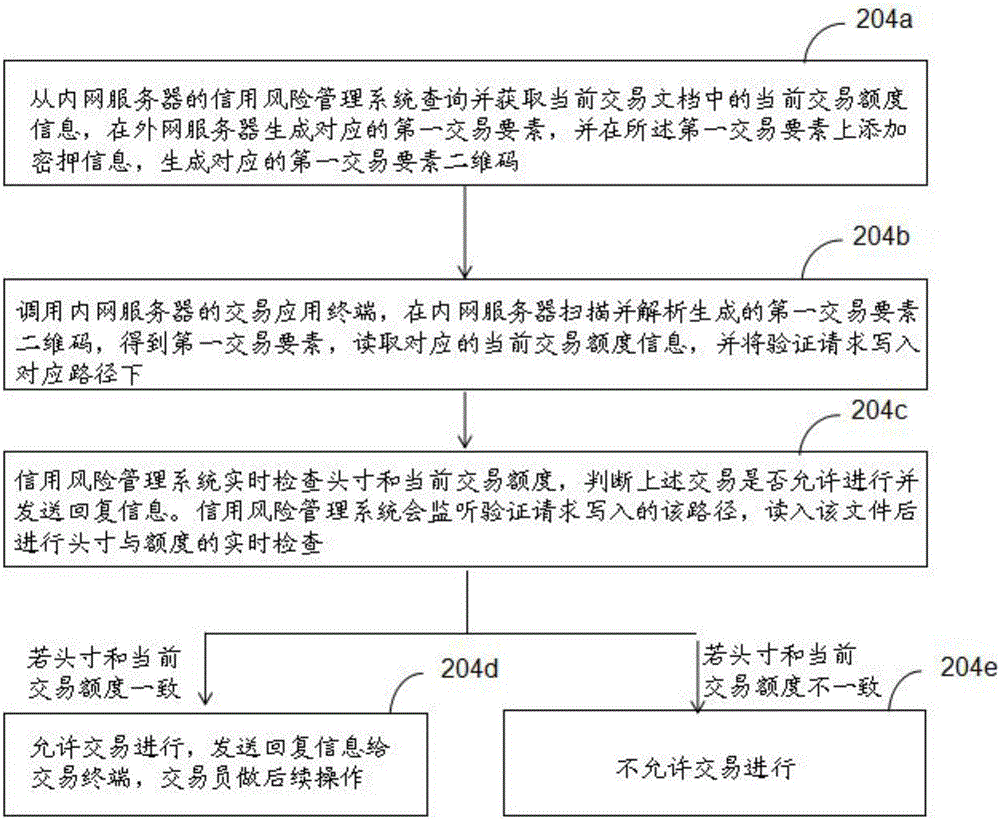
The invention discloses a transaction information exchange method between the internal and external networks in the financial industry. The method comprises steps that the quota information of each transaction opponent or a transaction kind is acquired from an internal network server, the test key information is further added, and a corresponding quota information two-dimensional code is generated; the corresponding quota information two-dimensional code is scanned and analyzed through an external network server, the corresponding quota information of files is updated; the transaction essential factor information is generated in the external network server, the test key information is further added, a corresponding transaction essential factor two-dimensional code is generated, the transaction essential factor two-dimensional code is scanned and analyzed through the internal network server, and the corresponding transaction information of the files is updated. The invention further discloses a transaction information exchange system between the internal and external networks in the financial industry. The method is advantaged in that information interaction between the mutually-separated internal and external networks is carried out through the two-dimensional code, hidden safety trouble caused by network attack and virus infection during communication of the internal and external networks can be avoided, and transaction compliance management and safe transaction are realized.
Owner:苏州凯联信息科技有限公司
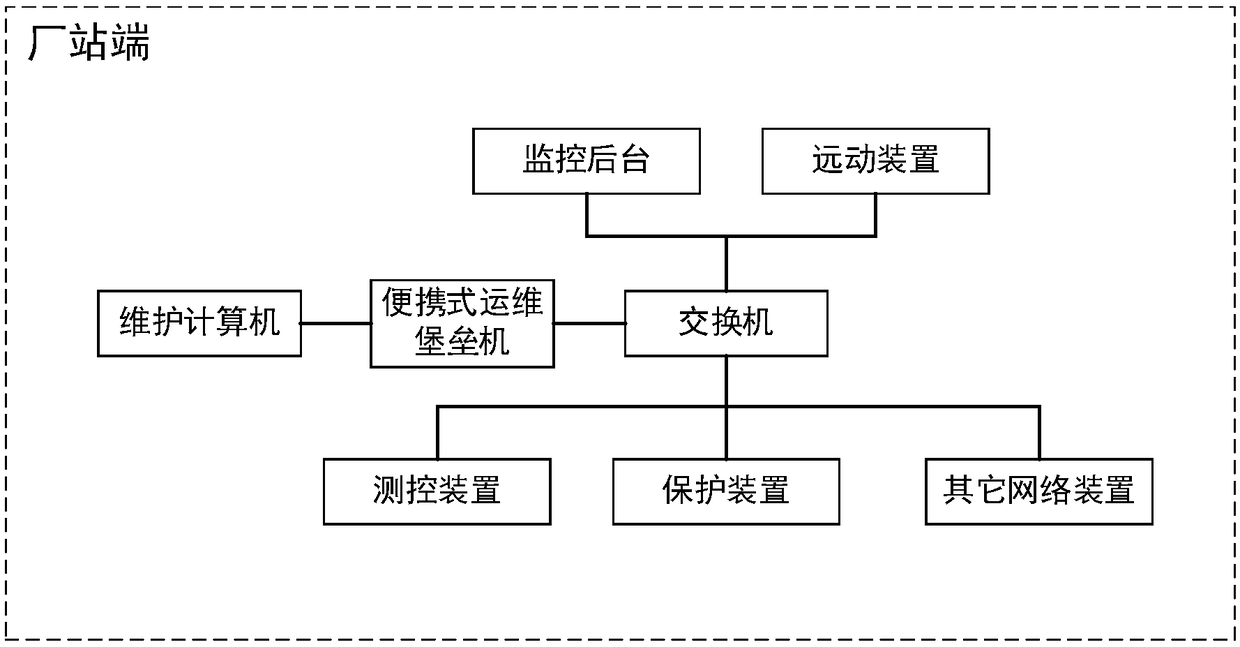
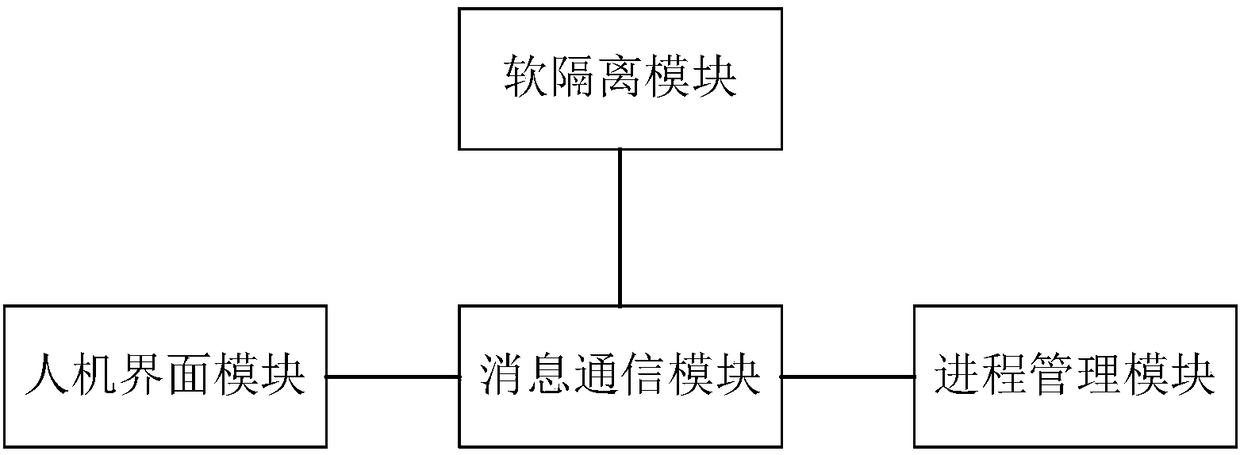
Portable operation and maintenance bastion host system
ActiveCN108551400ASimple structureEasy to useData switching networksHuman–machine interfaceNetwork link
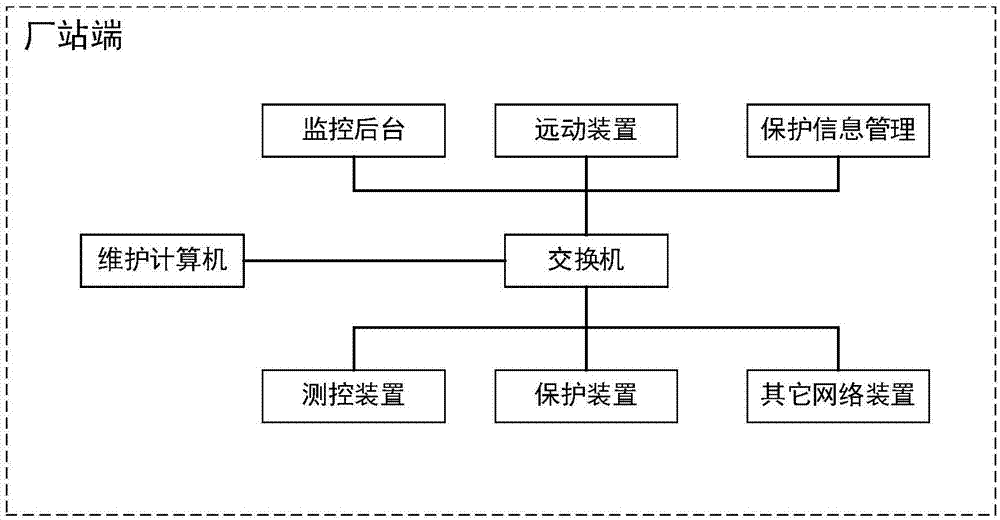
The invention relates to a portable operation and maintenance bastion host system comprising a soft isolation module, a process management module, a message communication module and a human-computer interface module, wherein the soft isolation module, the human-computer interface module and the process management module are separately connected with the message communication module. The portable operation and maintenance bastion host system is relatively concise in framework, and relatively simple for user; the monitoring and guard on each process can be achieved, the communication interactionof each process in the operation and maintenance bastion host can be achieved, and a dedicated human-computer interface can be provided for electric power maintenance; the access behavior of accessing and debugging transformer substation running equipment via a network is monitored and controlled, when the operation and maintenance personnel accesses the other network equipment in an unauthorizedmanner, the operation and maintenance personnel can be blocked and warning can be provided; an unauthorized network link initiated by a computer can be blocked and maintained, and the maintenance computer can be prevented from initiating a network attack to the operation and maintenance equipment.
Owner:南京捷安信息科技有限公司
Offline identity authentication system and device and computer readable storage medium
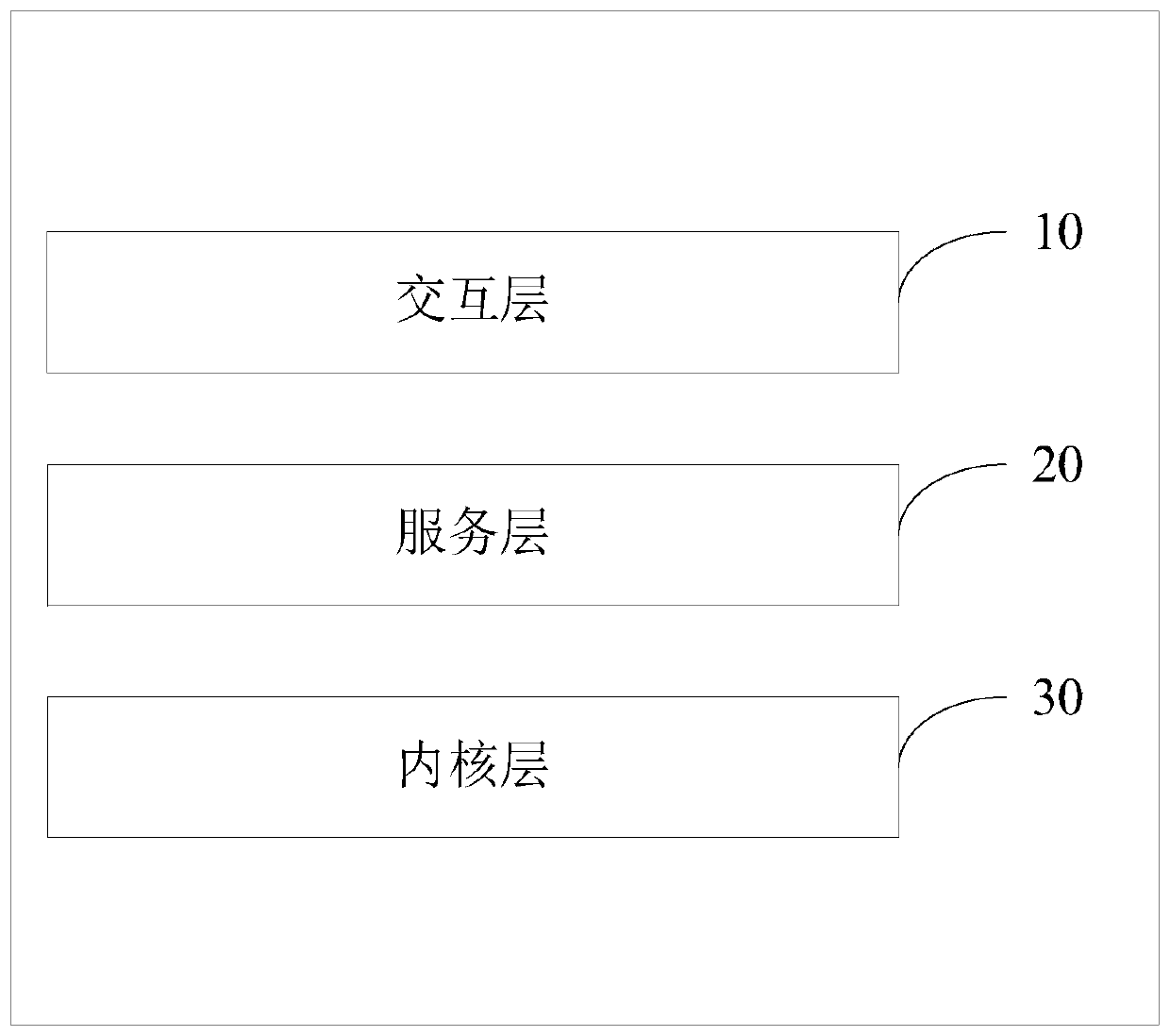
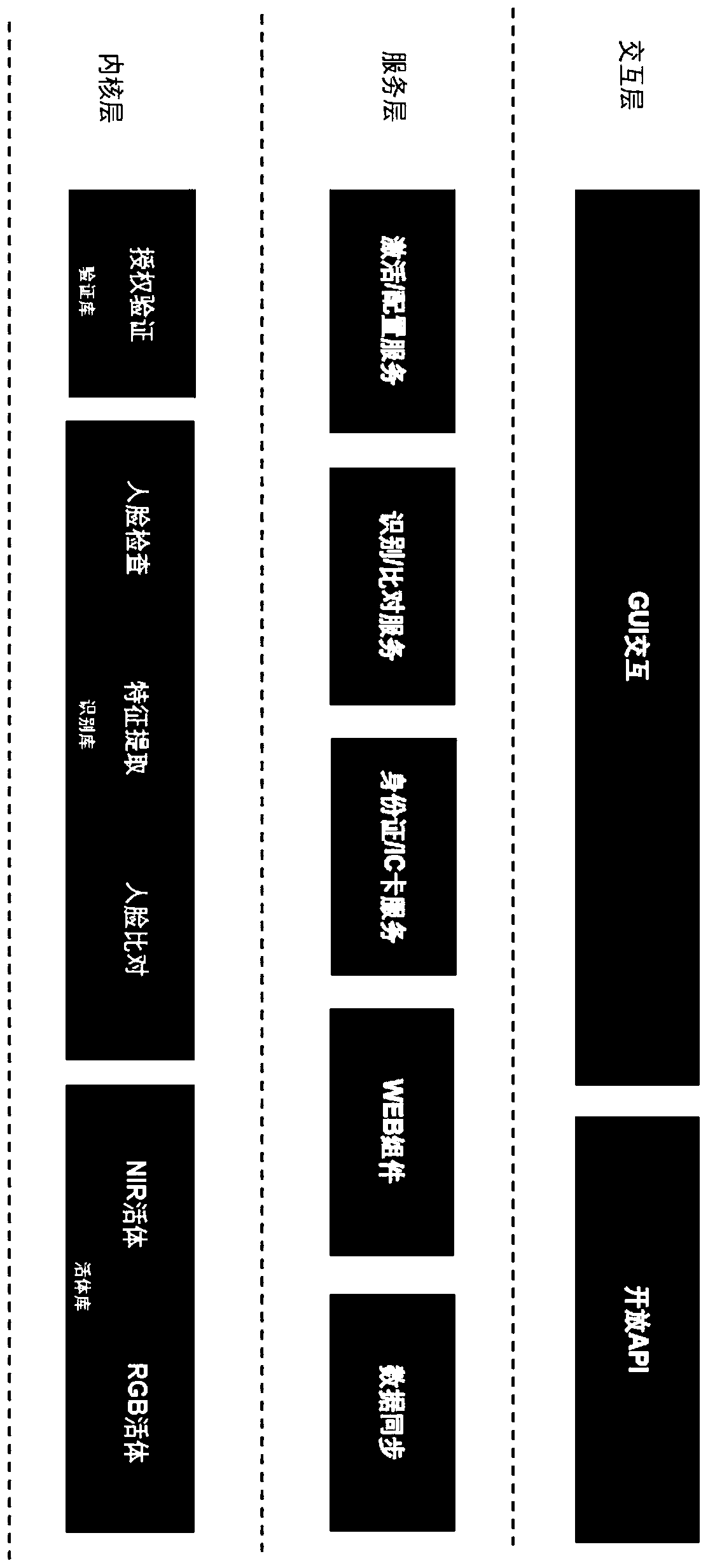
ActiveCN109885994AProtect privacy and securityPrevent cyber attacksDigital data authenticationInteraction layerFeature extraction
The invention discloses an offline identity authentication system and device and a computer readable storage medium. The system comprises an interaction layer, a service layer and a kernel layer, wherein the interaction layer is used for providing an interaction interface and receiving an interaction operation obtained by the interaction interface; the service layer is used for packaging businessfunctions into corresponding services, and the business functions comprise locally preloading a feature data set of admission personnel, performing feature extraction and feature comparison operationin real time in an offline state, and performing verification and identification operation on a target object in the offline state, and the kernel layer is used for executing operation and logic taskprocessing. According to the scheme, an identity authentication scheme with high security, quick response, stability and flexibility is realized.
Owner:SHENZHEN HEILS ZHONGCHENG TECH CO LTD
Network security processing method and device
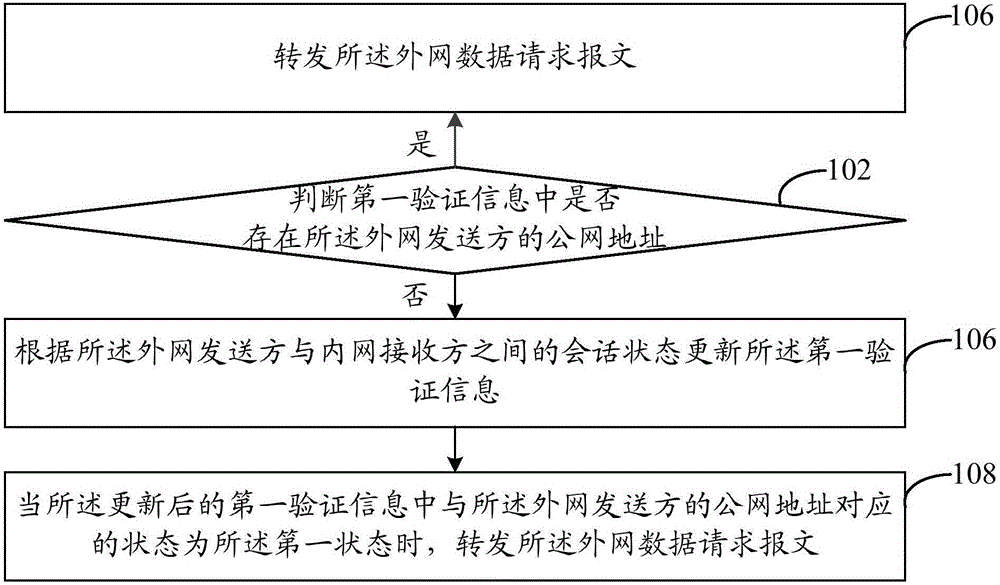
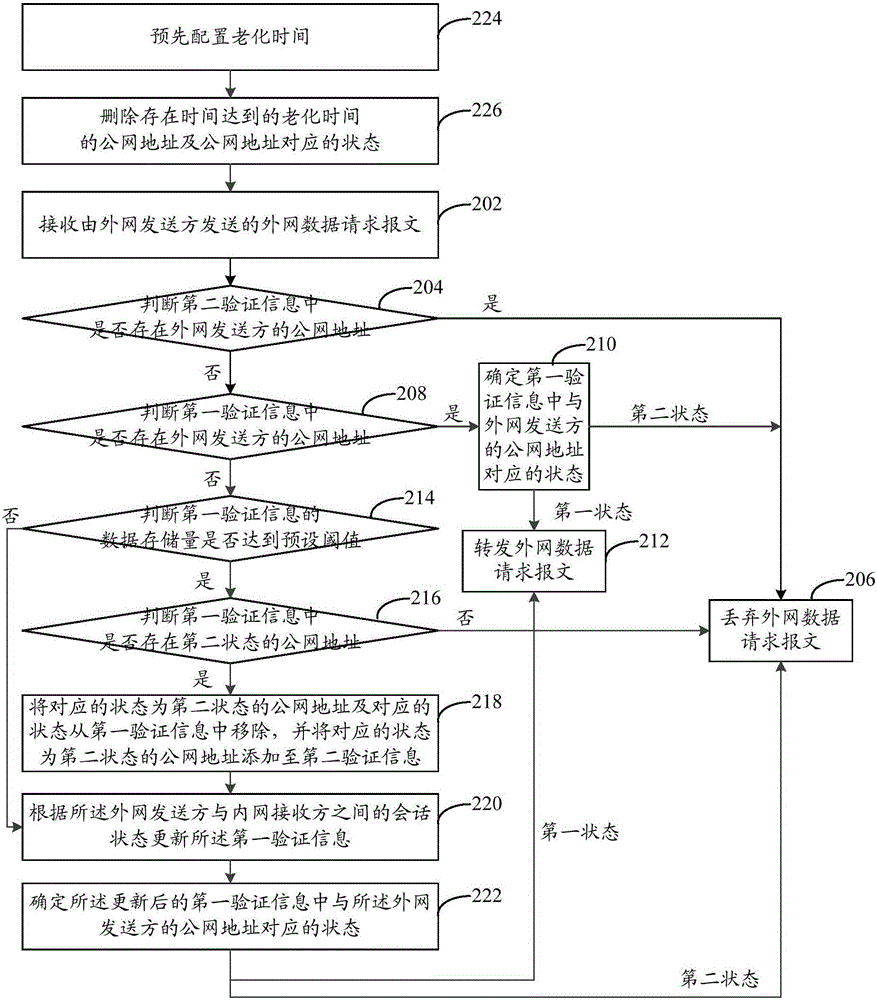
ActiveCN106131063AAvoid visitingPrevent cyber attacksTransmissionNetwork address translationDistributed computing
The invention provides a network security processing method and device. The method comprises the steps of judging whether a public network address of an external network sender exists in first verification information or not when an external network data request message sent by the external network sender is received; forwarding the external network data request message if the public network address exists in the first verification information and the state corresponding to the public network address of the external network sender in the first verification information is a first state; updating the first verification information according to a session state between the external network sender and an internal network sender if the public network address does not exist in the first verification information; and forwarding the external network data request message when the state corresponding to the public network address of the external network sender in the updated first verification information is the first state. Through application of the method and the device, the problem that in an existing NAT (Network Address Translation) scheme, an attacker can easily carry out a network attack on an internal network host through NAT table items is solved.
Owner:NEW H3C TECH CO LTD
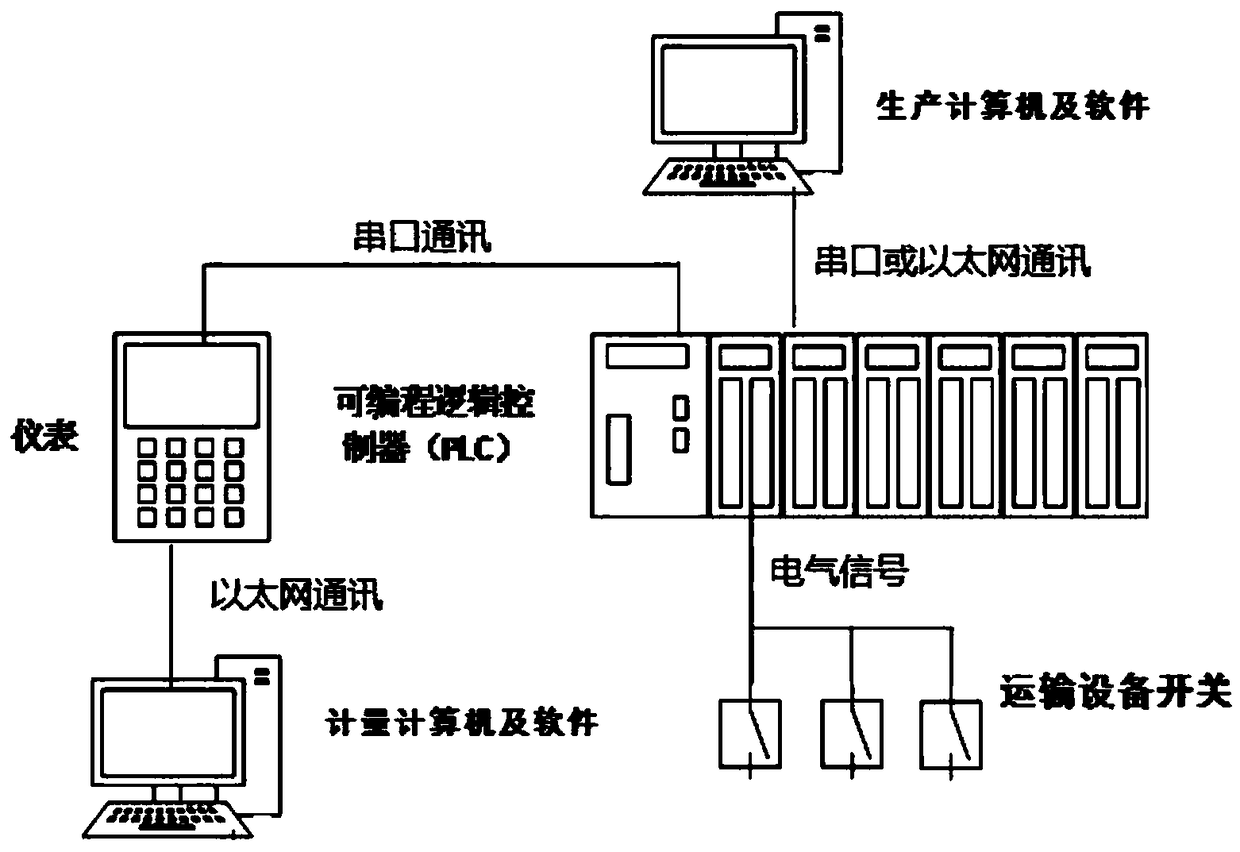
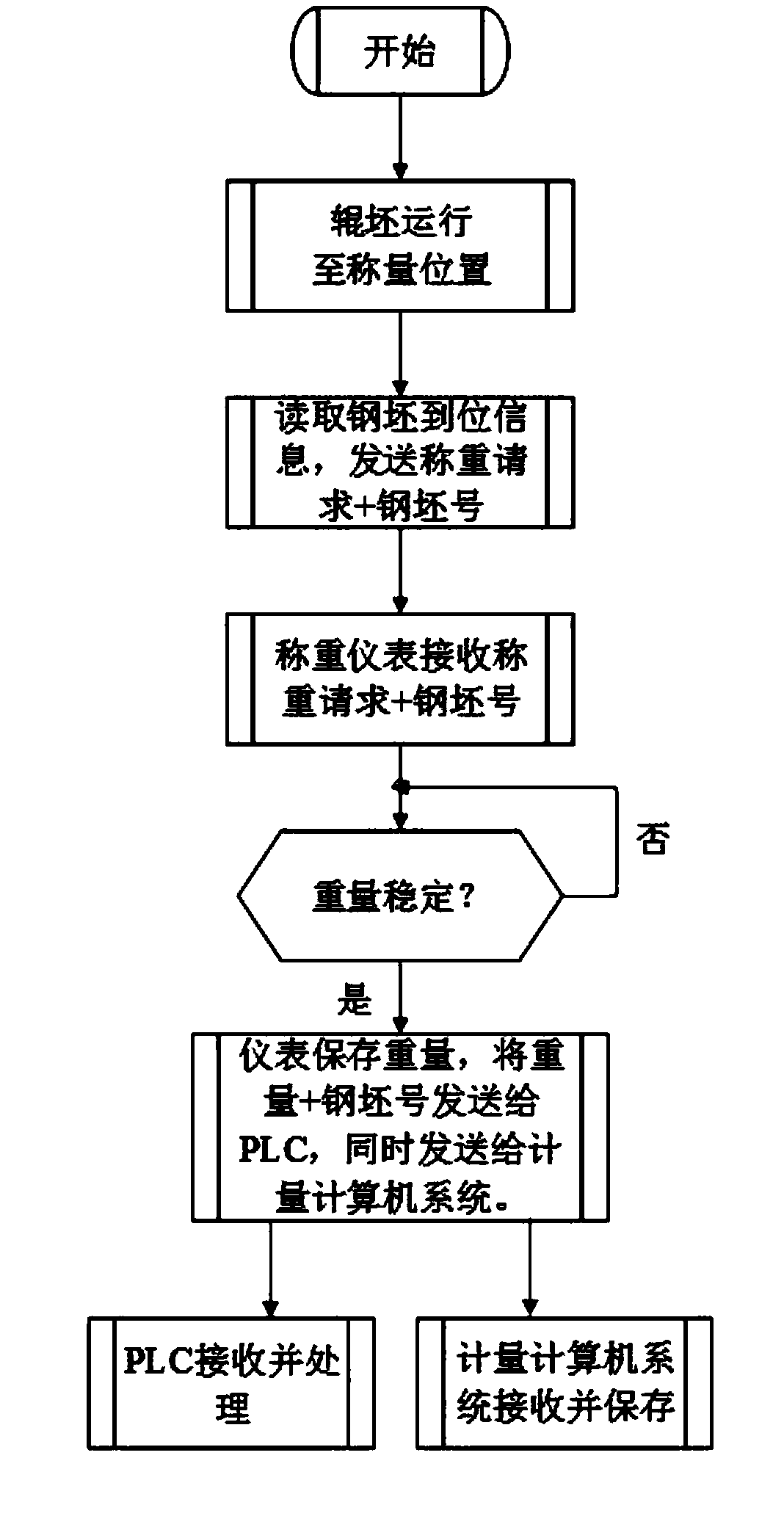
Automatic metering system of roller scale based on weighing controller and method thereof
InactiveCN109238418AAvoid delivery errorsPrevent virus spreadWeighing auxillary devicesProgramme control in sequence/logic controllersInformation transmissionProgrammable logic controller
The invention relates to an automatic metering system of a roller scale based on a weighing controller and a method thereof. The automatic metering system comprises a steel billet transportation roller table, a roller scale, a programmable logic controller, a weighing controller, a position switch, a production computer system and a metering computer system. The metering method comprises the following steps: transporting a steel billet to a weighing position, i.e., the transportation roller table above the roller scale; judging information indicating that the steel billet is put in place; starting to weighing by the weighing controller after reception of a weighing request and a steel billet number; judging whether the weighing condition is satisfied or not; and after the metering computersystem receives the steel billet number and weight, carrying out a saving action. Through adoption of the automatic metering system, steel billet metering and complete steel billet information transmission functions can be finished automatically without manual participation; information transmission errors in steel billet metering caused by manual operation errors or untimeliness are avoided, andphysical isolation is realized between a production automation network and a metering network, thereby completely avoiding virus transmission and network attacks between the production network and metering network.
Owner:SD STEEL RIZHAO CO LTD
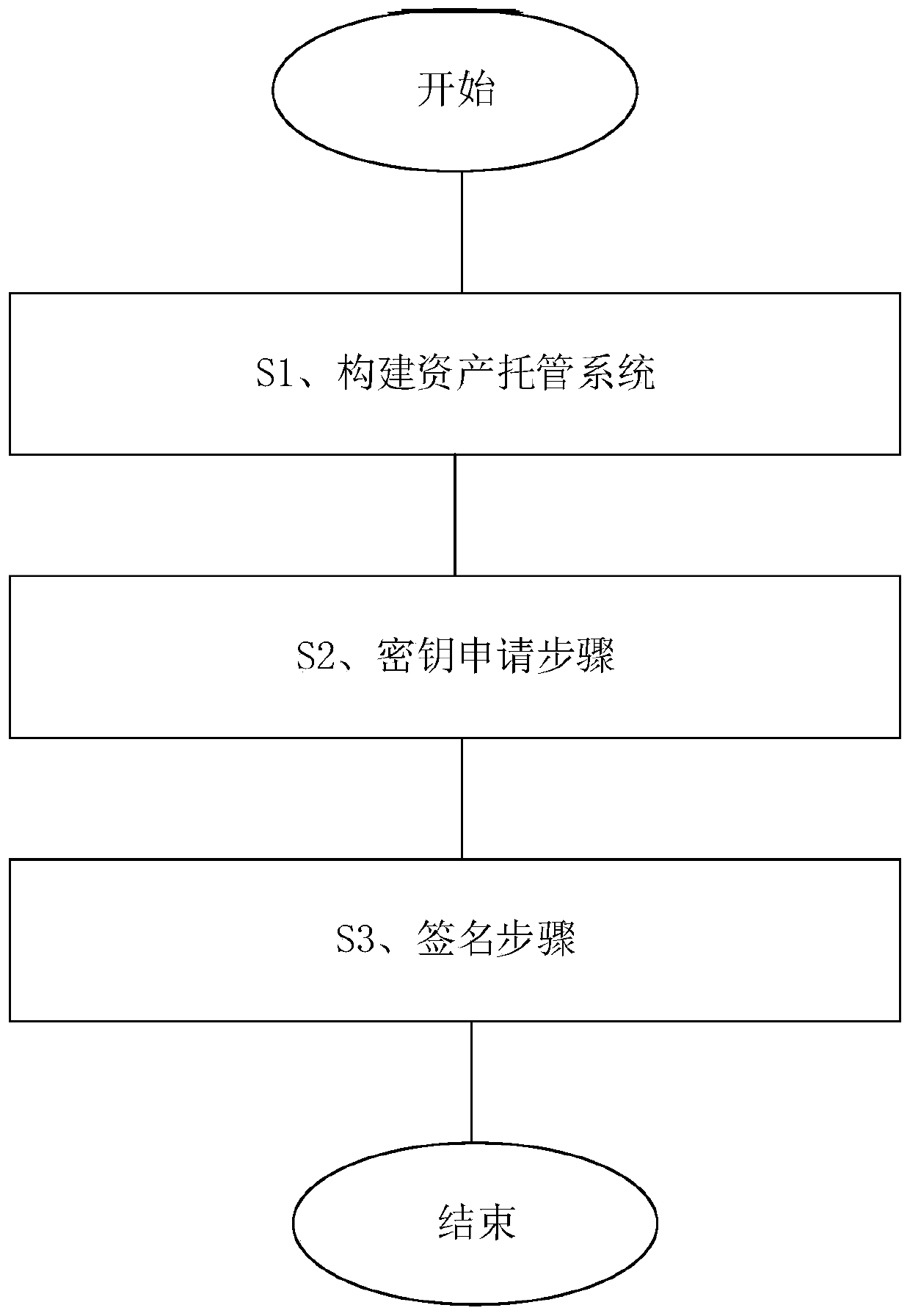
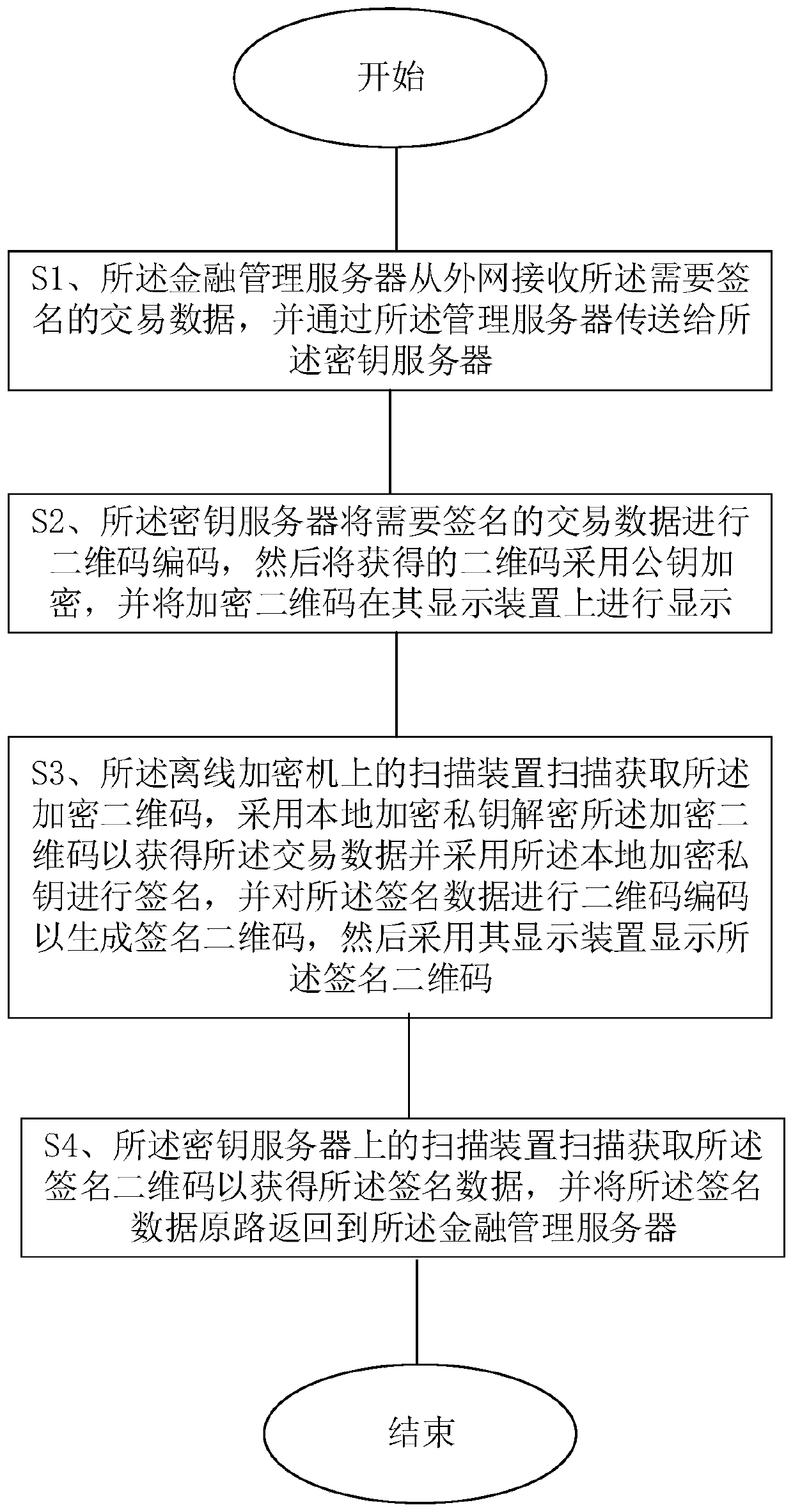
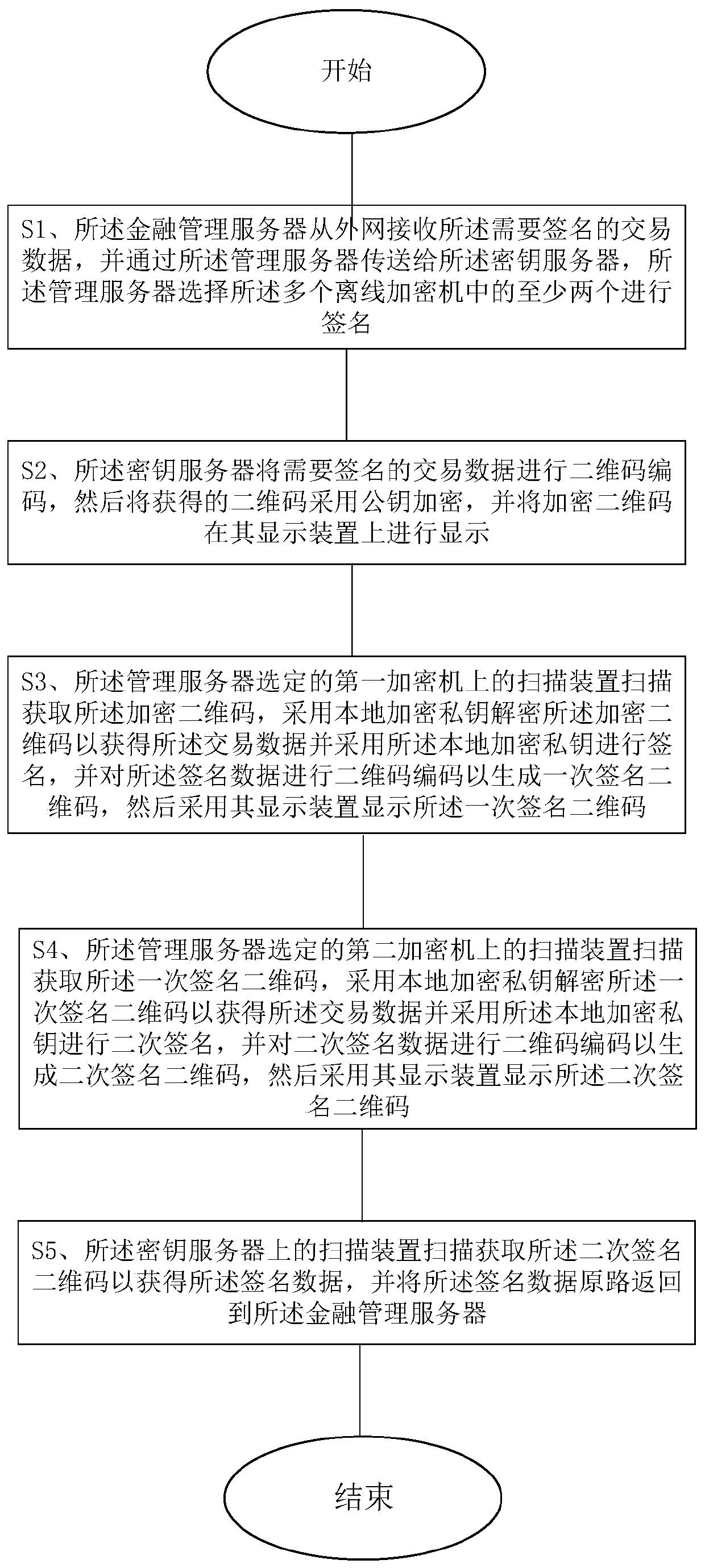
Digital asset hosting method and system
PendingCN111144885AEnsure safetyPrevent cyber attacksFinanceUser identity/authority verificationDigital assetKey server
The invention relates to a digital asset trusteeship method. The method comprises a step of constructing an asset trusteeship system, a key application step and a signature step. The invention also relates to a digital asset hosting system. The asset trusteeship system comprises a financial management server communicating with an external network, a management server communicating with the financial management server through a first communication channel, a secret key server communicating with the management server through a second communication channel, and an offline encryption machine communicating with the secret key server through a third communication channel. According to the digital asset trusteeship method and system, the private key is stored in the offline encryption machine, and the signature is also carried out in the offline encryption machine, so that the security of the key is ensured, and the defects of network attacks, relatively large potential safety hazards and information leakage risks are avoided through multi-layer network isolation.
Owner:杜晓楠
Clock calibration method and network security protection method and device based on clock synchronization
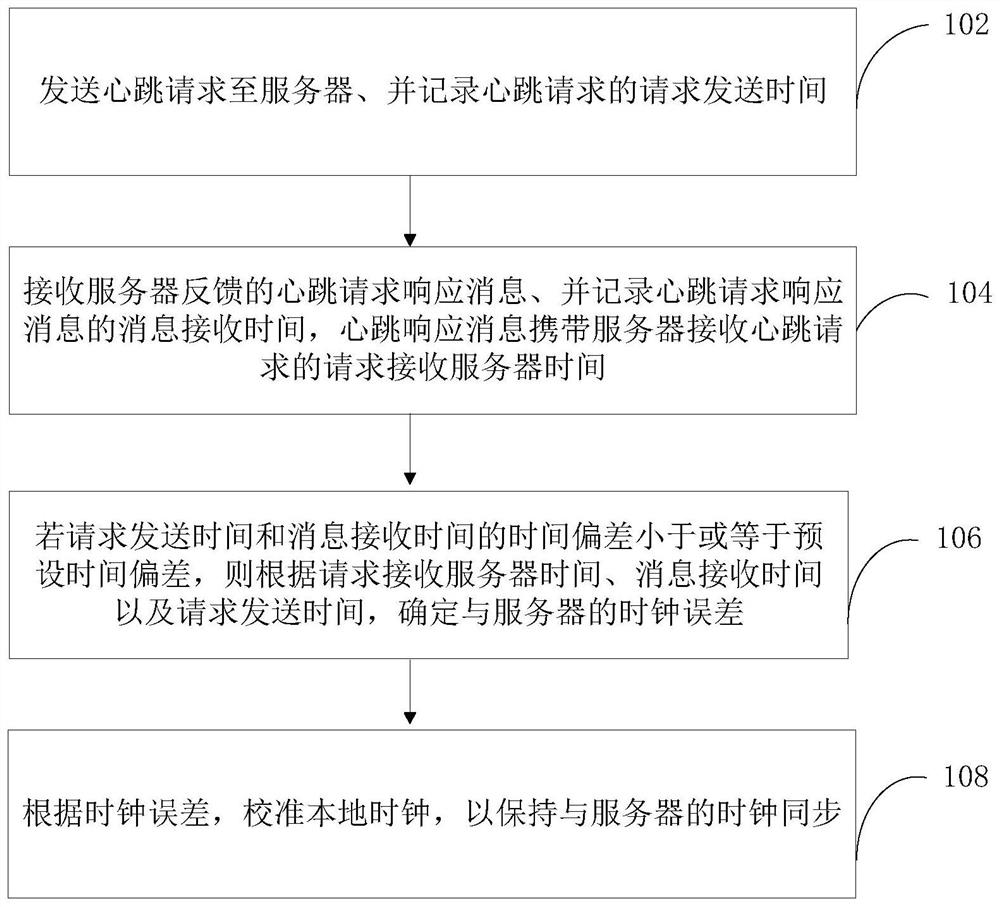
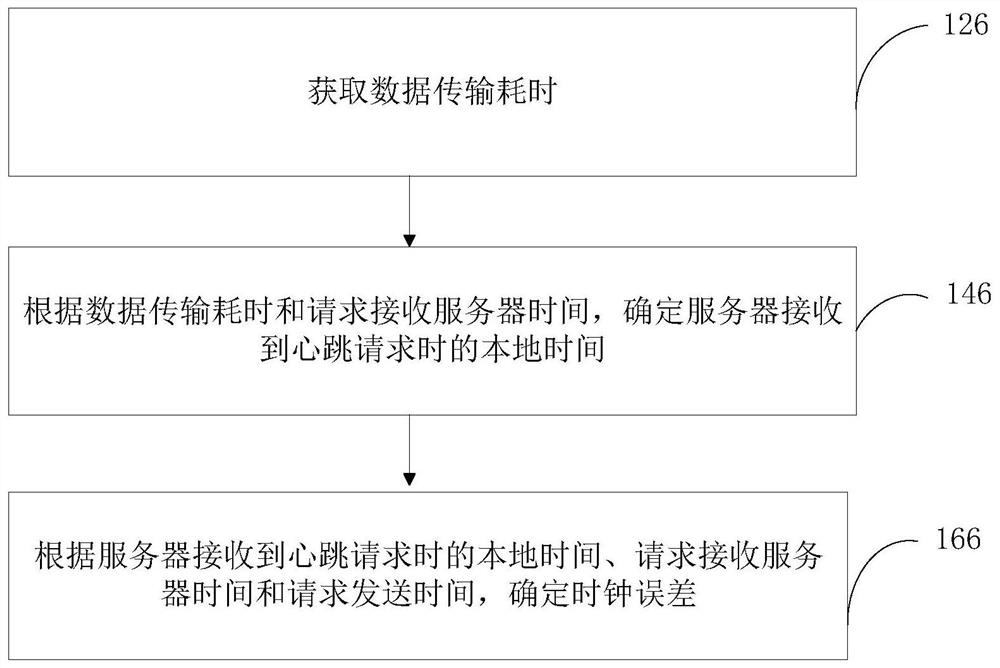
PendingCN113556200APrevent cyber attacksImprove network securityTime-division multiplexData switching networksEmbedded systemClock error
The invention relates to the technical field of security monitoring, and provides a clock calibration method and a network security protection method and device based on clock synchronization. The clock calibration method comprises the following steps: sending a heartbeat request to a server, recording request sending time of the heartbeat request, receiving a heartbeat request response message which is fed back by the server and carries request receiving server time for receiving the heartbeat request, and recording message receiving time; and if time deviation between the request sending time and the message receiving time is less than or equal to preset time deviation, determining a clock error relative to the server, and calibrating a local clock according to the clock error. By adopting the method, clock calibration efficiency can be improved. The network security protection method based on clock synchronization comprises the following steps: receiving a heartbeat request which is sent by a user terminal and carries request initiation time, recording request receiving time, and filtering the heartbeat request in which the time deviation between the request initiation time and the request receiving time exceeds the preset time deviation. The method can realize efficient network protection.
Owner:PING AN ASSET MANAGEMENT CO LTD
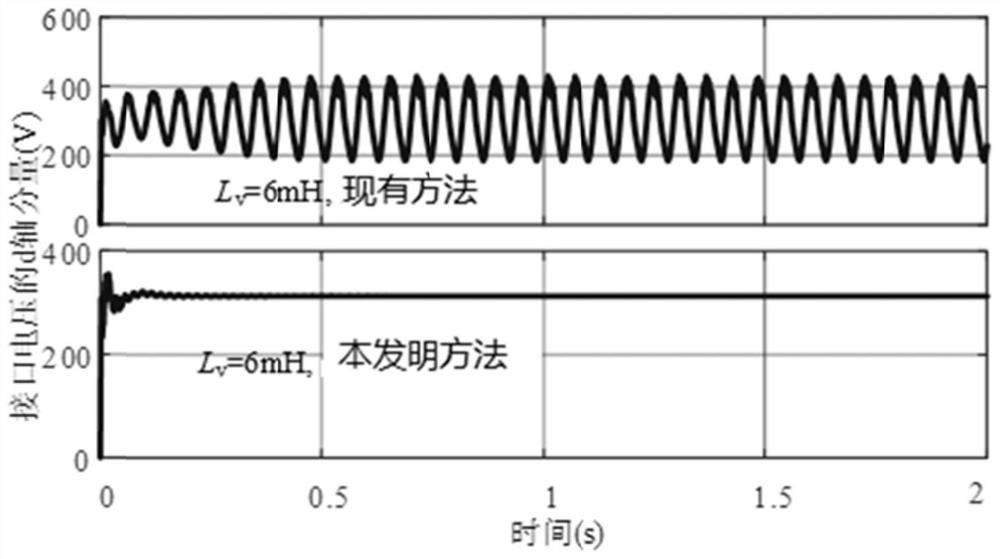
Island micro-grid system and interactive oscillation suppression method and system thereof
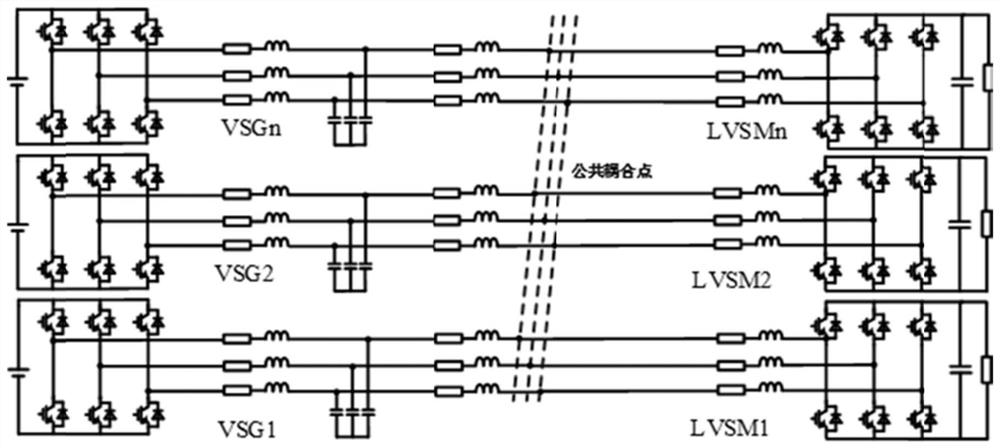
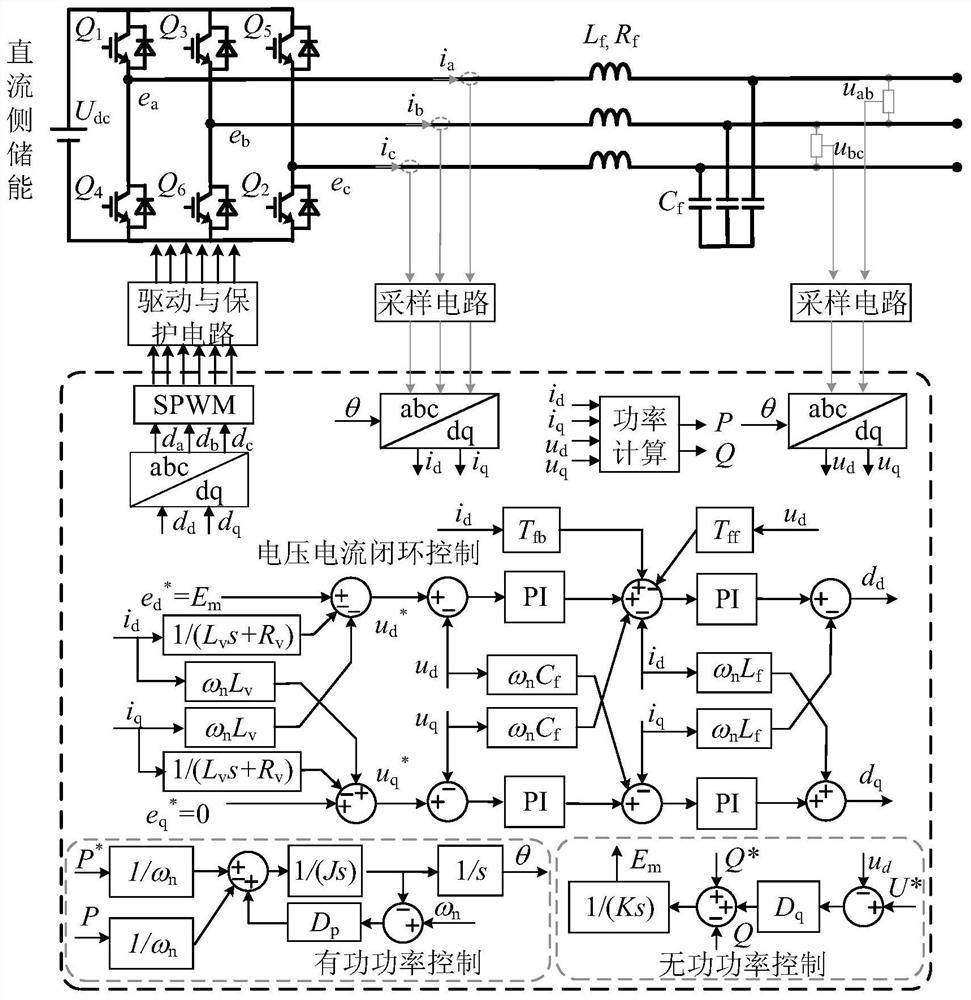
PendingCN114024309ASuppression of reciprocal oscillationsGuaranteed stabilityFlicker reduction in ac networkSingle network parallel feeding arrangementsIslandingEngineering
The invention discloses an island micro-grid system and an interactive oscillation suppression method and system thereof. A source side virtual synchronous machine and a load side virtual synchronous machine are combined to provide virtual inertia and damping. The invention provides a d-axis inductive current feedforward control and d-axis voltage feedback control method to remodel the impedance of the VSG so as to reduce the impedance amplitude of the VSG. Therefore, the low-frequency interaction between the VSG and the LVSM can be suppressed. The method can be used for solving the problem of interactive oscillation of the alternating current island micro-grid composed of the multi-source-load virtual synchronous machine.
Owner:GUANGDONG ZHICHENG CHAMPION GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com