Method for realizing encrypted authentication of distribution automation remote control command
A technology of power distribution automation and remote control commands, applied in the field of electrical engineering, to prevent network attacks, enhance key security, and avoid remote control failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
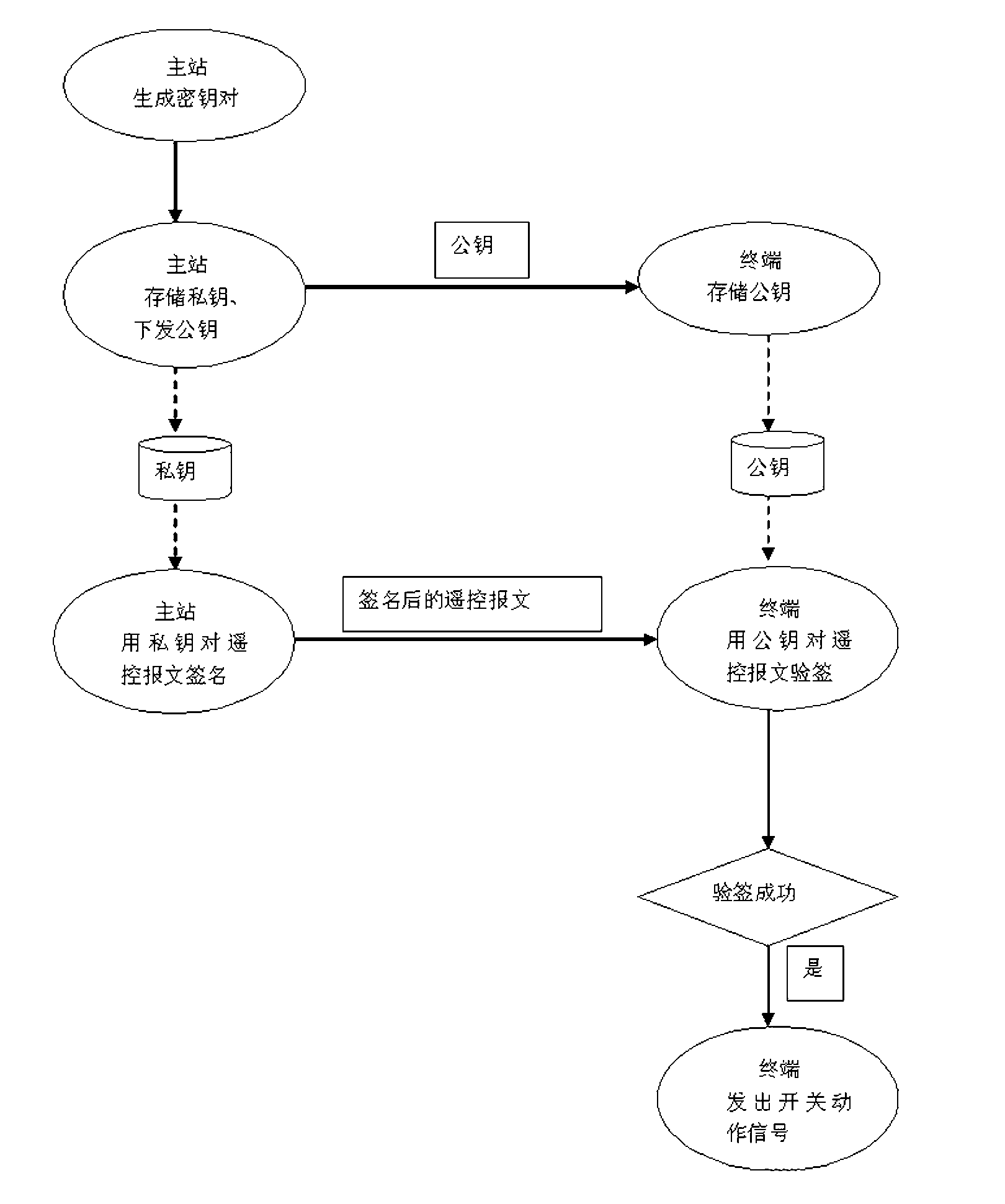
[0015] refer to figure 1 — Figure 4 , the method to realize the encryption and authentication of distribution automation remote control commands consists of the following steps: (1) Digitally sign the remote control message and generate a key pair by the master station; (2) The master station stores the private key and issues the public key to the power distribution (3) The power distribution terminal stores the public key; (4) The master station uses the private key to sign; (5) The power distribution terminal uses the public key to verify the signature; (6) The power distribution terminal sends an action signal to the switch.
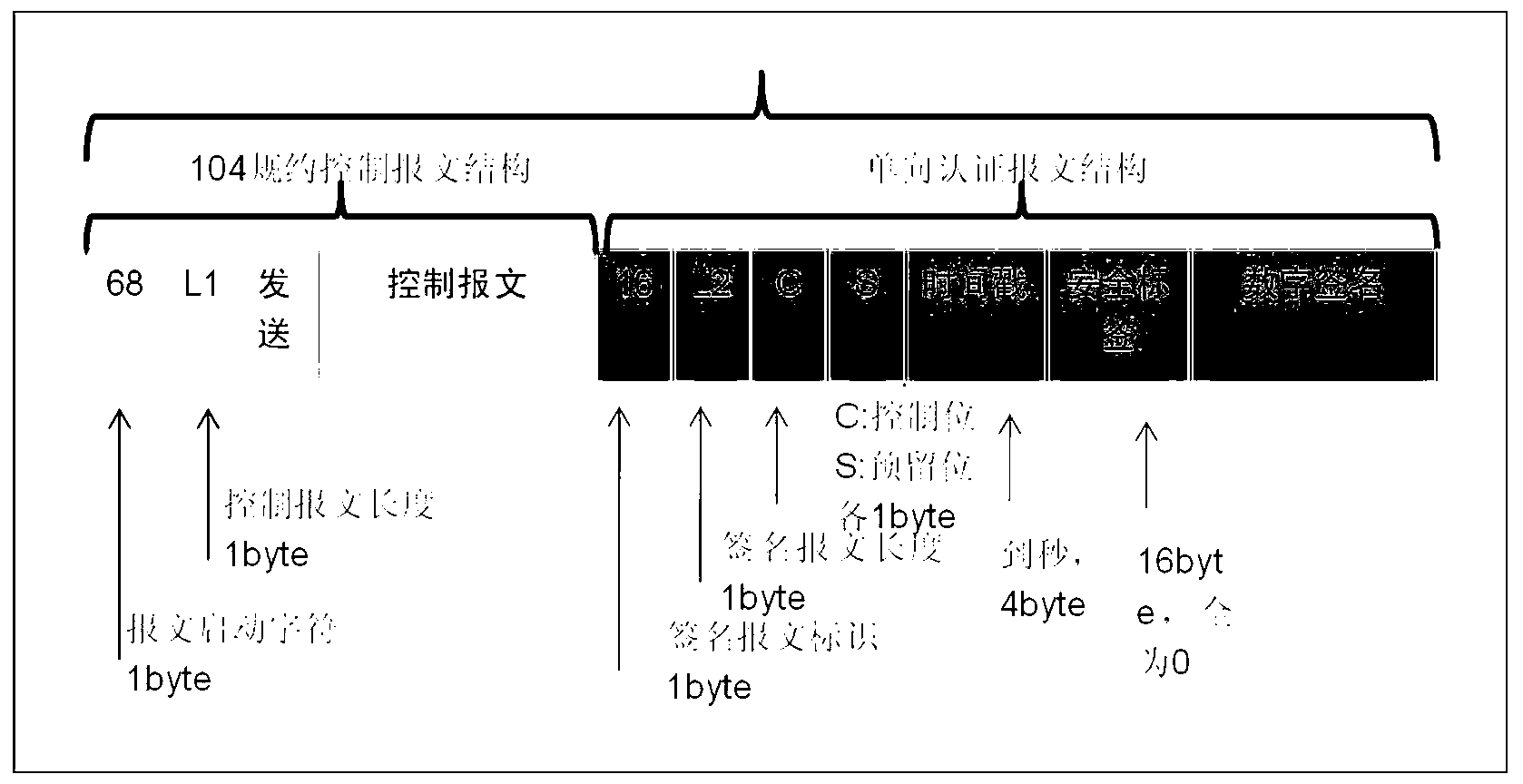
[0016] The digital signature process of the distribution network master station is as follows: the master station sends a link start message, the power distribution terminal replies with a link start confirmation message, and the master station issues a public key file (ECC method) according to the encryption method used by the power distribution ter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com