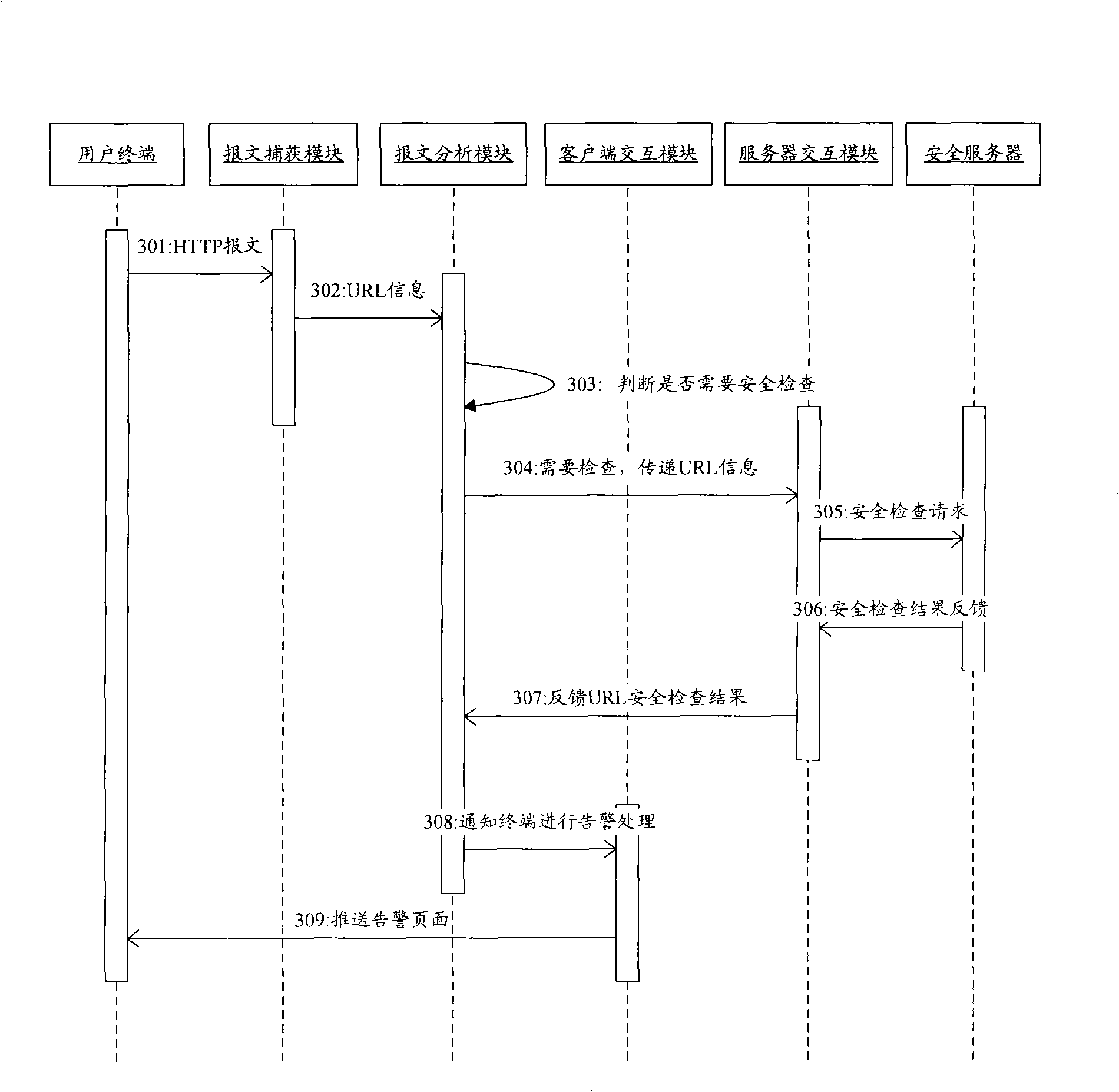
Patents
Literature
519results about How to "Avoid visiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
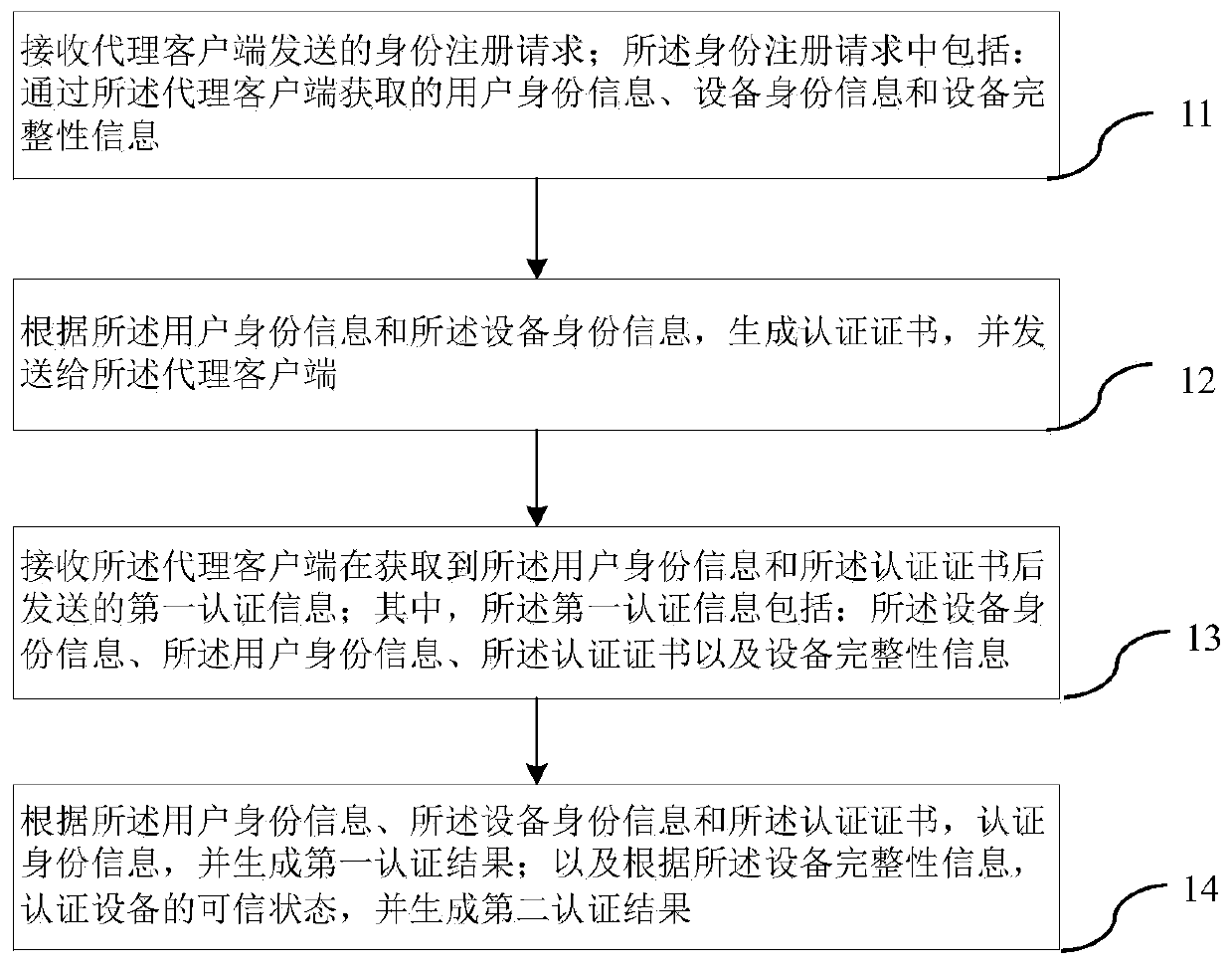
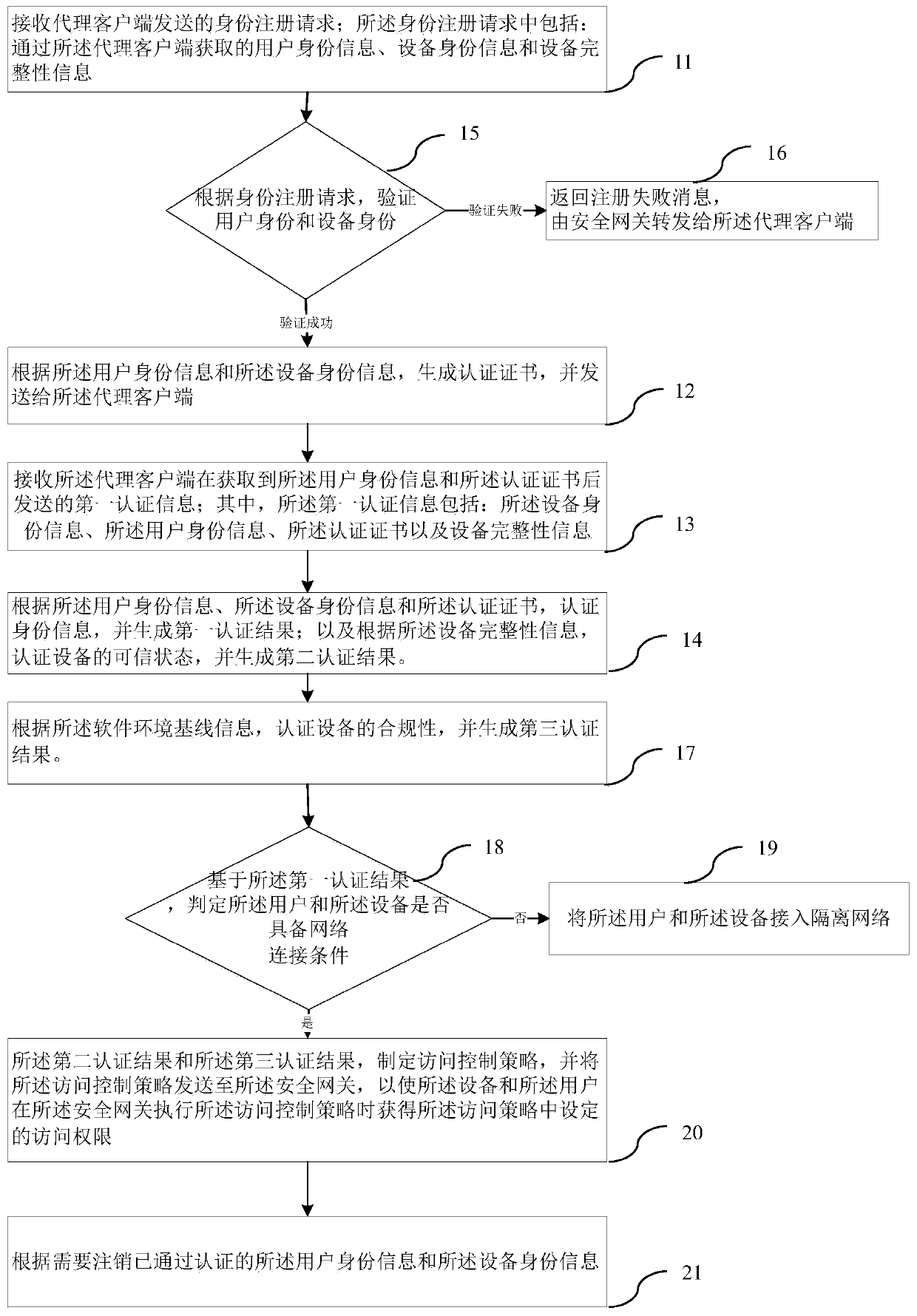
Patent Type
Patent Status
Application Year
Inventor
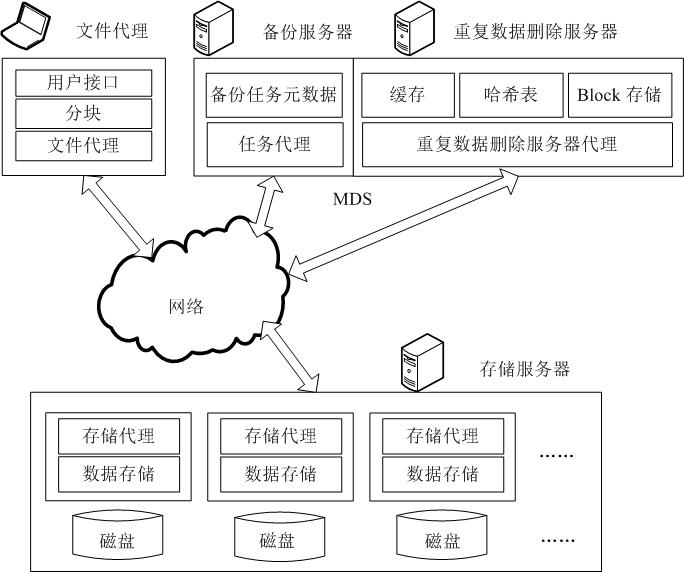
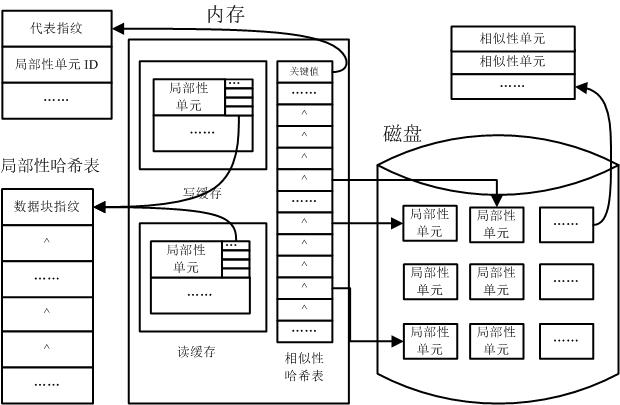
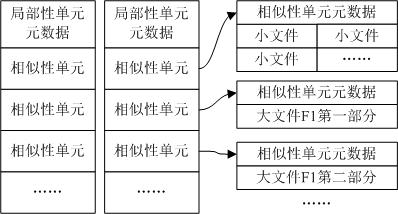
Data de-duplication method based on combination of similarity and locality
ActiveCN102222085AAvoid putting inReduce memory overheadSpecial data processing applicationsData streamData mining
The invention provides a data de-duplication method for combining the similarity and the locality of data, with less system memory expense and high data de-duplication efficiency. The method comprises the steps of: firstly partitioning and grouping files in a data stream, determining a similarity unit and a representative fingerprint of every data group, and storing the representative fingerprint in a memory; and traversing all the data groups and performing a similarity determination to determine which data in data groups are completely duplicate data and which data in data groups have non-duplicate data. If the non-duplicate data exists in the data groups, the locality determination can be continued to further determine which data in the data groups is the duplicate data. According to the method, the representative fingerprint is only stored in the memory, thus the memory expense is greatly reduced; supplement can be performed after the similarity determination by mining the locality of the data stream and caching the locality of the data stream in the memory, thus more duplicate data can be found, and simultaneously, frequent access to a disk index can be avoided and the utilization rate of the memory can be enhanced.
Owner:HUAZHONG UNIV OF SCI & TECH
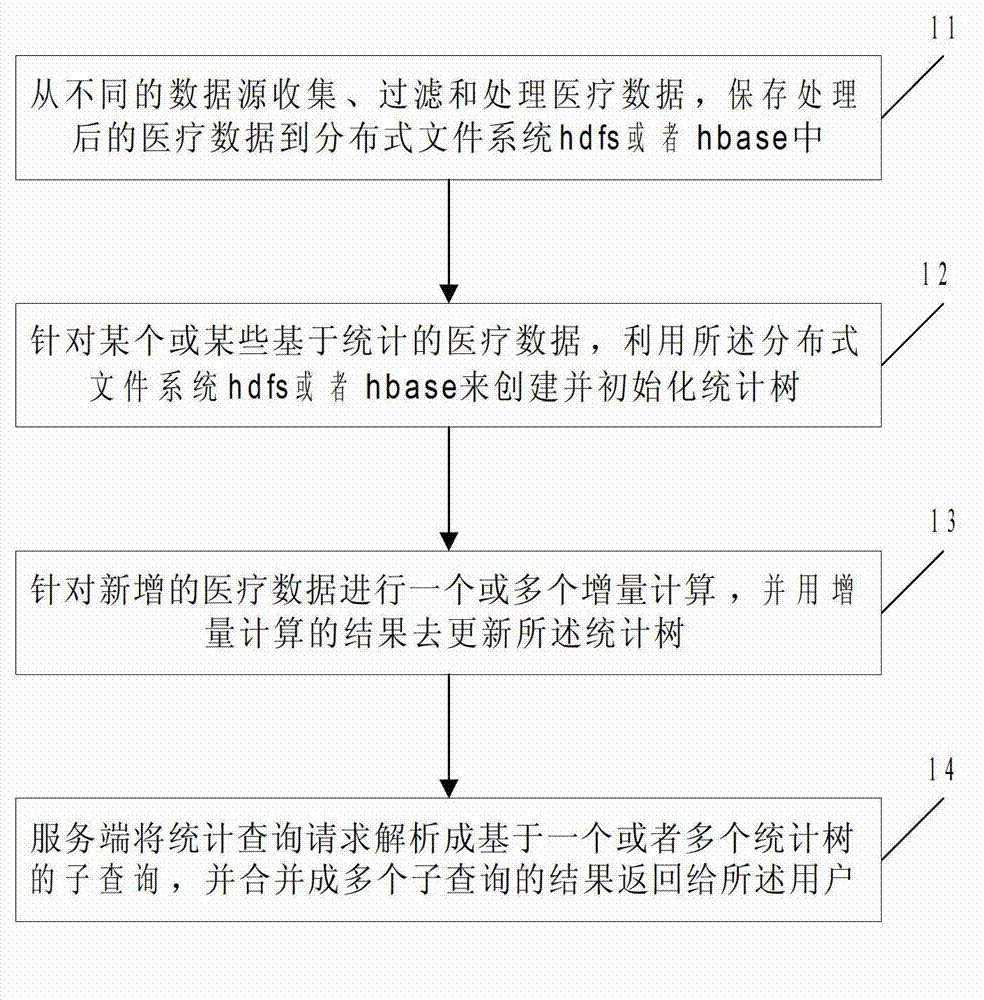
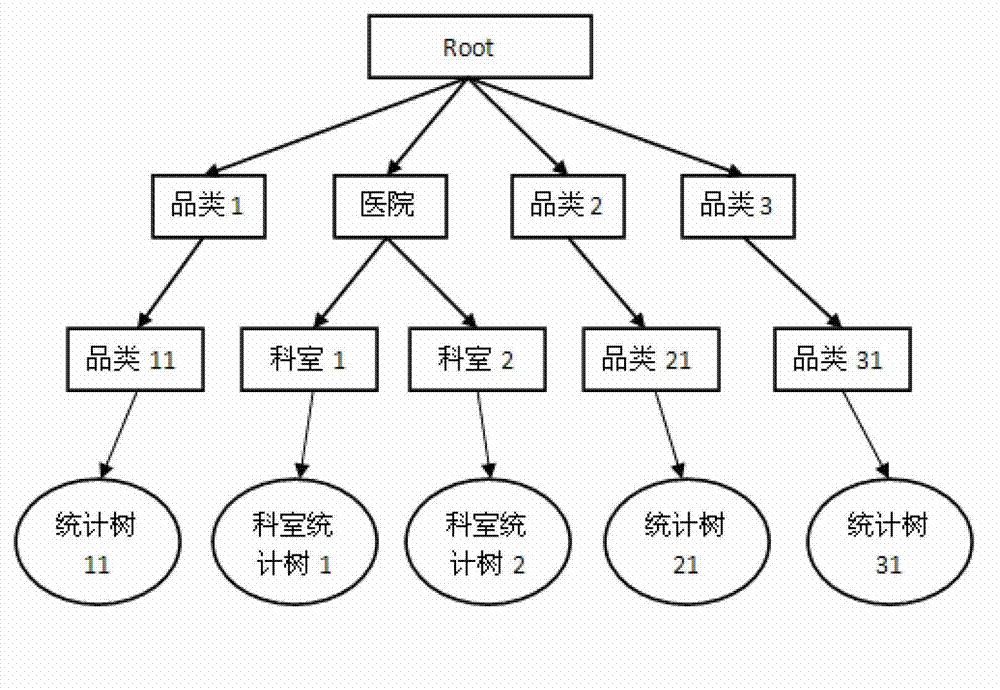
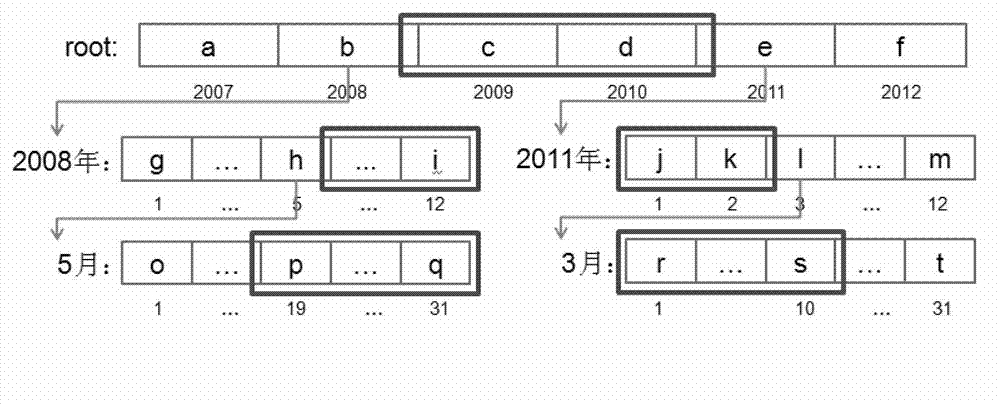
Fast statistical query method for mass medical data
ActiveCN103049556AAvoid visitingRapid positioningSpecial data processing applicationsDistributed File SystemDatasource
The invention discloses a fast statistical query method for mass medical data. The method includes: firstly, collecting, filtering and processing medical data from different data sources, and storing processed medical data into an HDFS (Hadoop distributed file system) or HBase; using the HDFS or HBase to create and initialize statistics trees for one or certain statistics-based medical data; subjecting the newly added medical data to single or multiple incremental computations, and updating the statistics tree by results of the incremental computations; allowing a server to respond to a statistical query request from a user according to the one or a plurality of created statistics trees, to analyze the statistical query request into sub-queries based on one or the plurality of statistics trees, and to combine into a plurality of sub-query results fed back to the user. The position of statistical data can be located quickly by the method, access to mass data is avoided, system load is lightened, and query efficiency and access concurrency are increased.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Method, device and system for realizing resource sharing
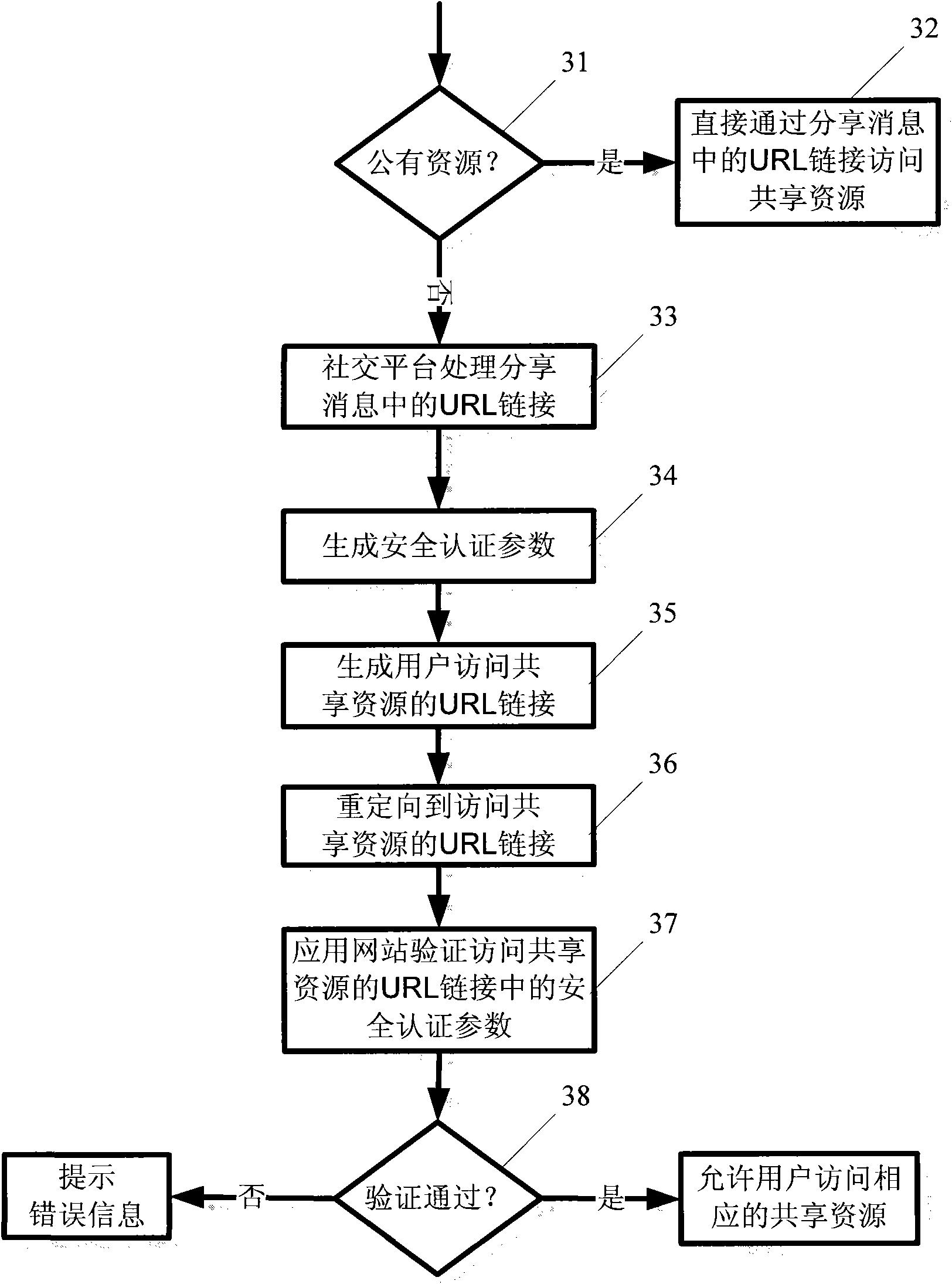
ActiveCN101771532AAvoid visitingKey distribution for secure communicationData switching networksResource informationInformation access
Owner:HUAWEI TECH CO LTD
Method and system for mini-station to access cloud, and access management equipment
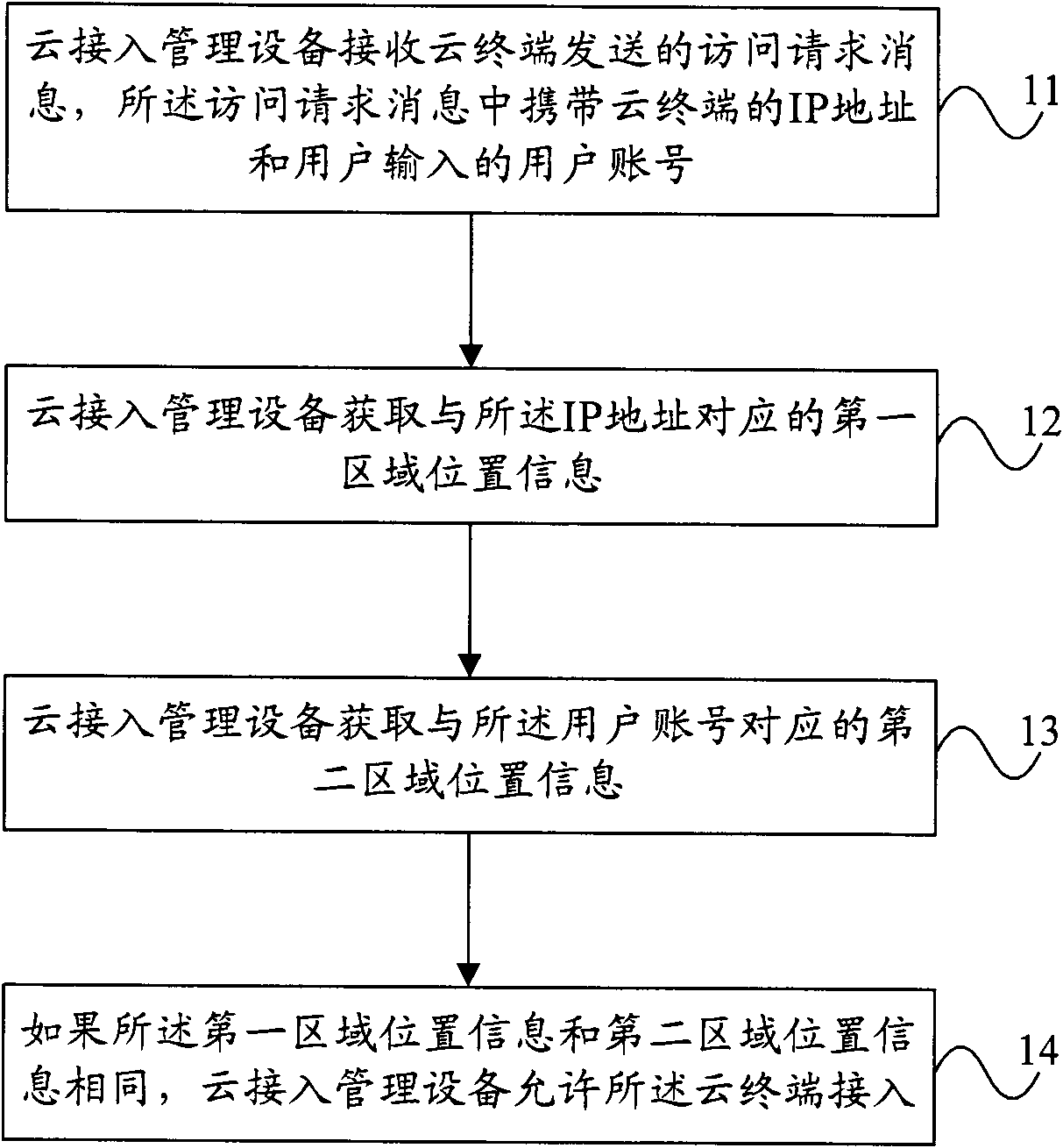
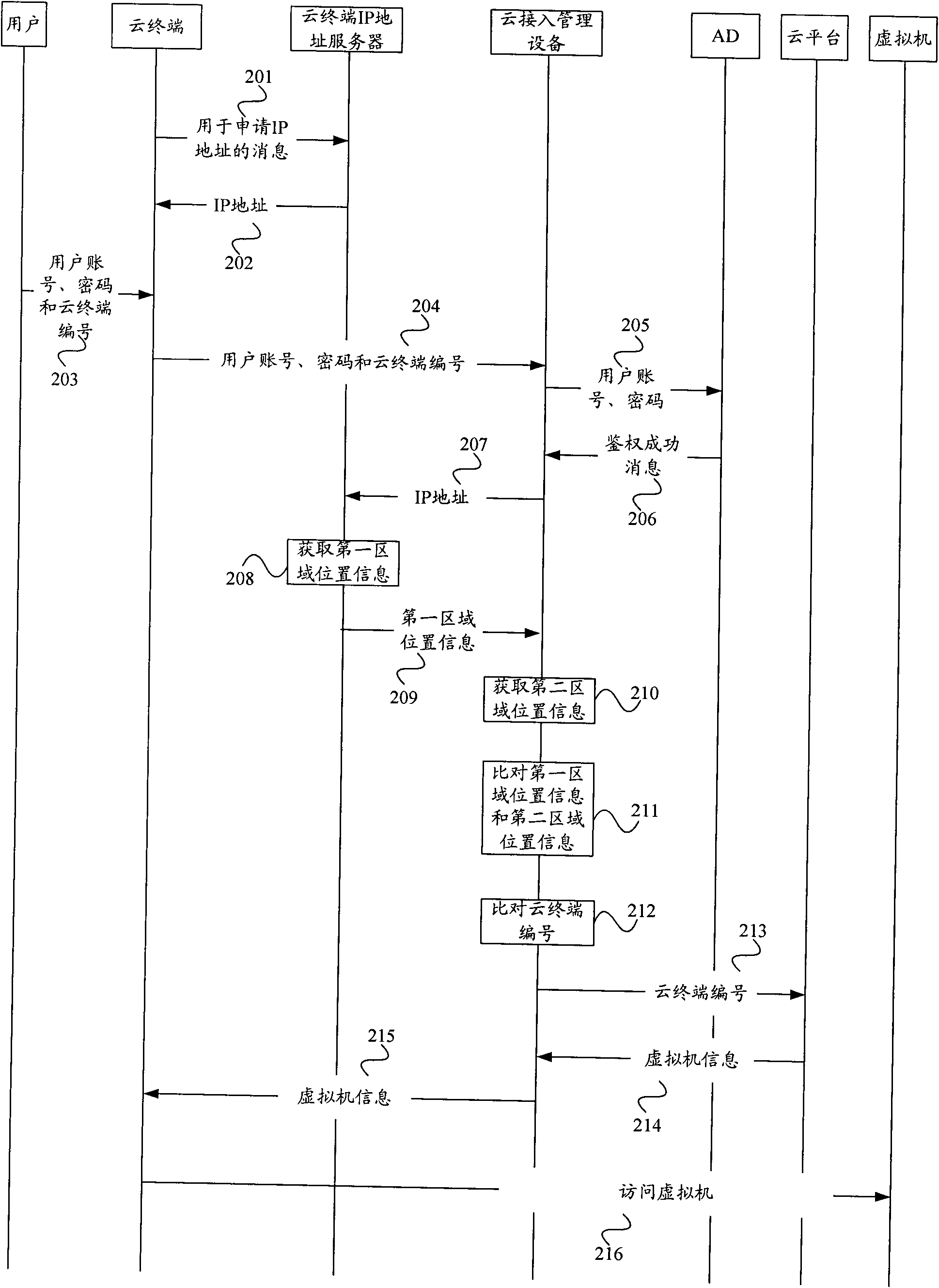
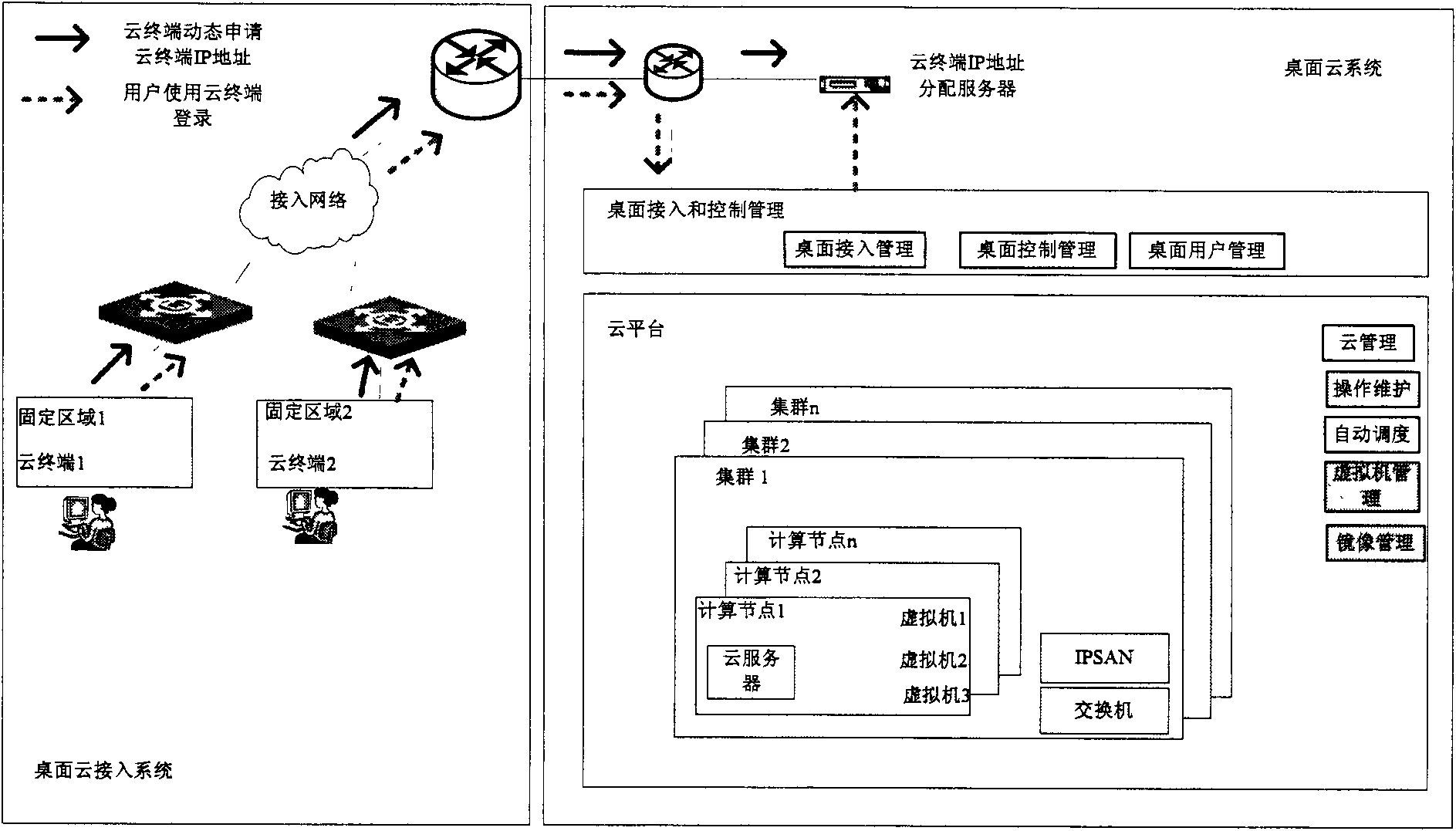
The invention provides a method and a system for a mini-station to access cloud, and access management equipment. The method comprises the following steps of: receiving an access request message from the mini-station, wherein the access request message carries an Internet protocol (IP) address of the mini-station and a user account input by a user; acquiring first area position information corresponding to the IP address; acquiring second area position information corresponding to the user account; and if the first area position information is the same as the second area position information, allowing the accessing of the mini-station. The embodiment of the invention can realize area-based cloud accessing.
Owner:HUAWEI TECH CO LTD
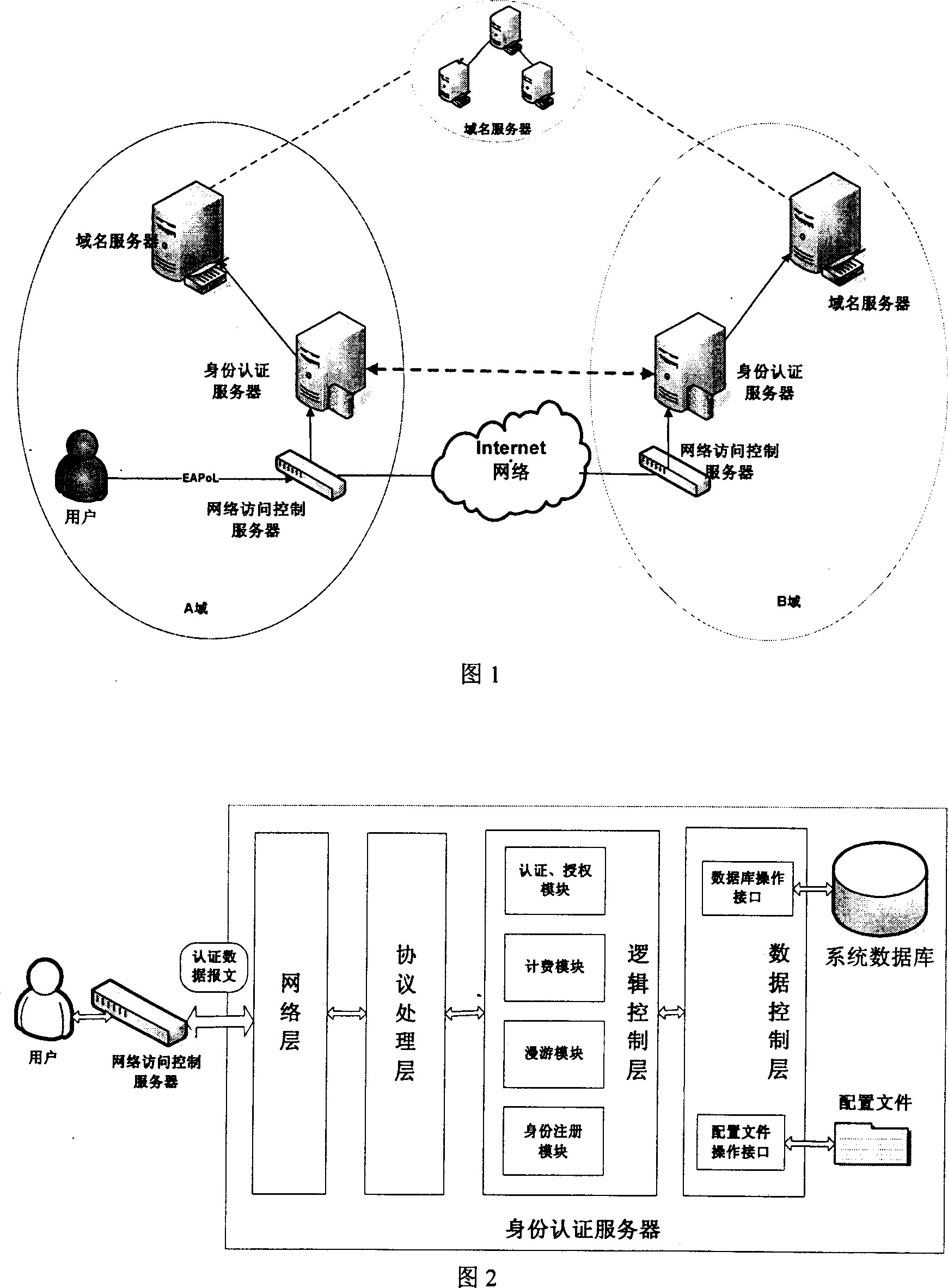
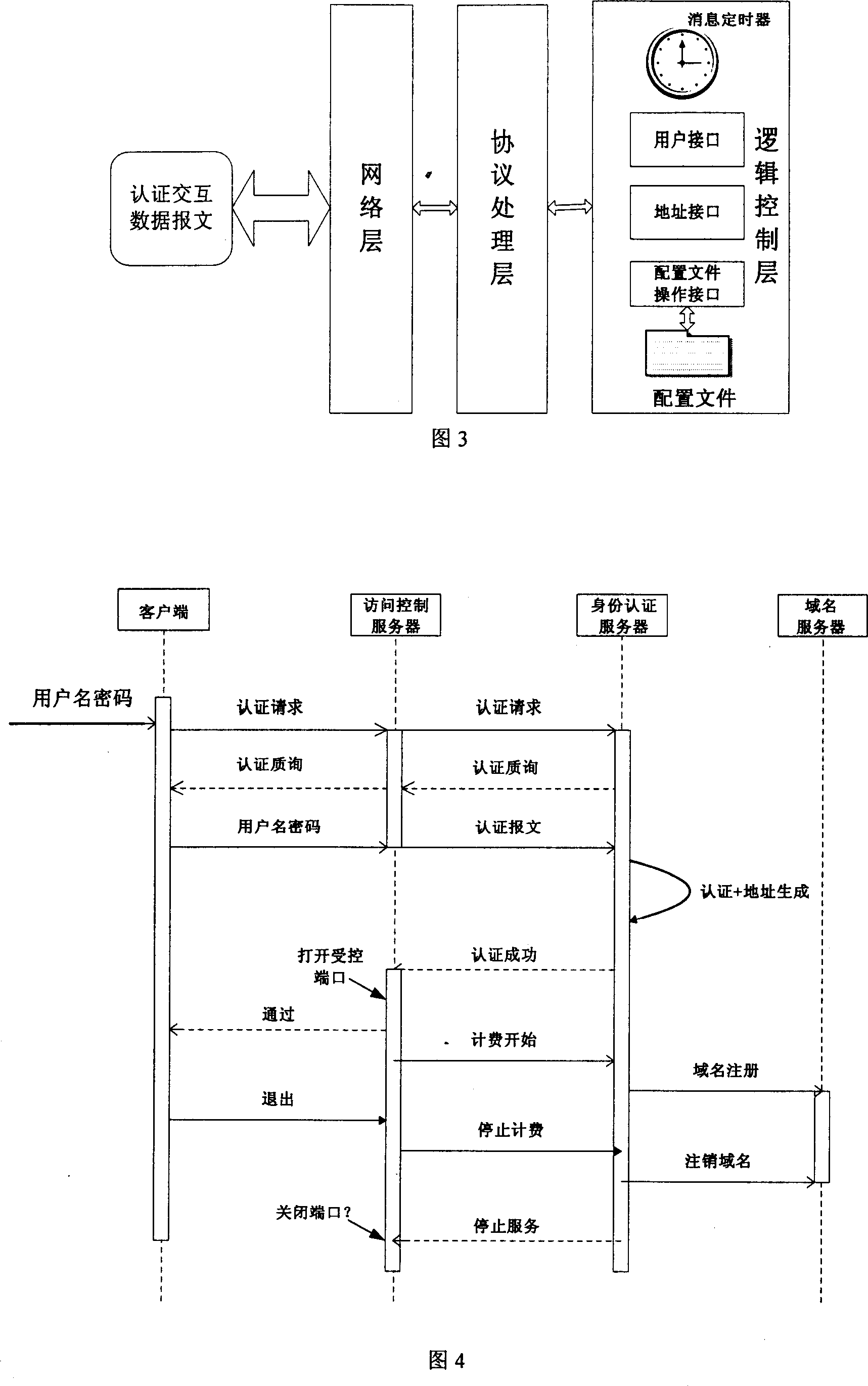
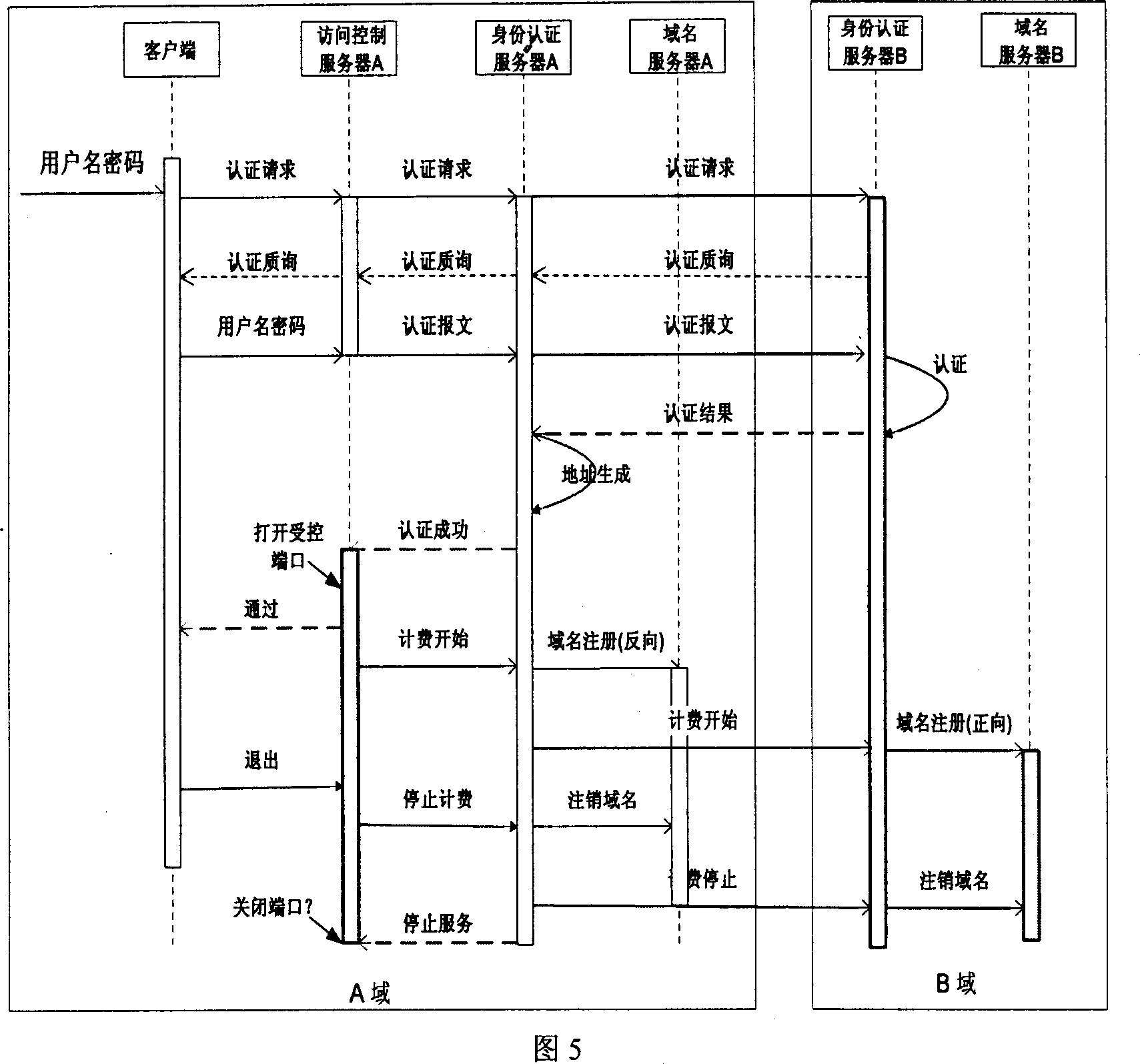
Domainname-based unified identification mark and authentication method
InactiveCN1937499AGood scalabilityAvoid visitingUser identity/authority verificationData switching by path configurationVerification systemMAC address
This invention utilizes the good architecture design presented by the latest Internet protocol IPv6, combines with safety domain name (DN) service, extends the existed ID verification system functions, realizes the bounding relation between the user ID and recent real IPv6 address to offer a reliable security service for the upper application. In the user management domain, there are a net access control server (NACS), an ID authentication server (IDAS) and a DN server. NACS recognizes the registered user via a 3-element group consisted of user computer source MAC address, the source IPv6 address and the port. IDAS authenticates the user ID recognition and defines related accessing priority. DN server establishes the positive-negative direction relations between user private DN and IPv6 address. This invention provides more effective ID authentication means and possesses a great extendable function to meet the requirement of the future Internet application development.
Owner:TSINGHUA UNIV
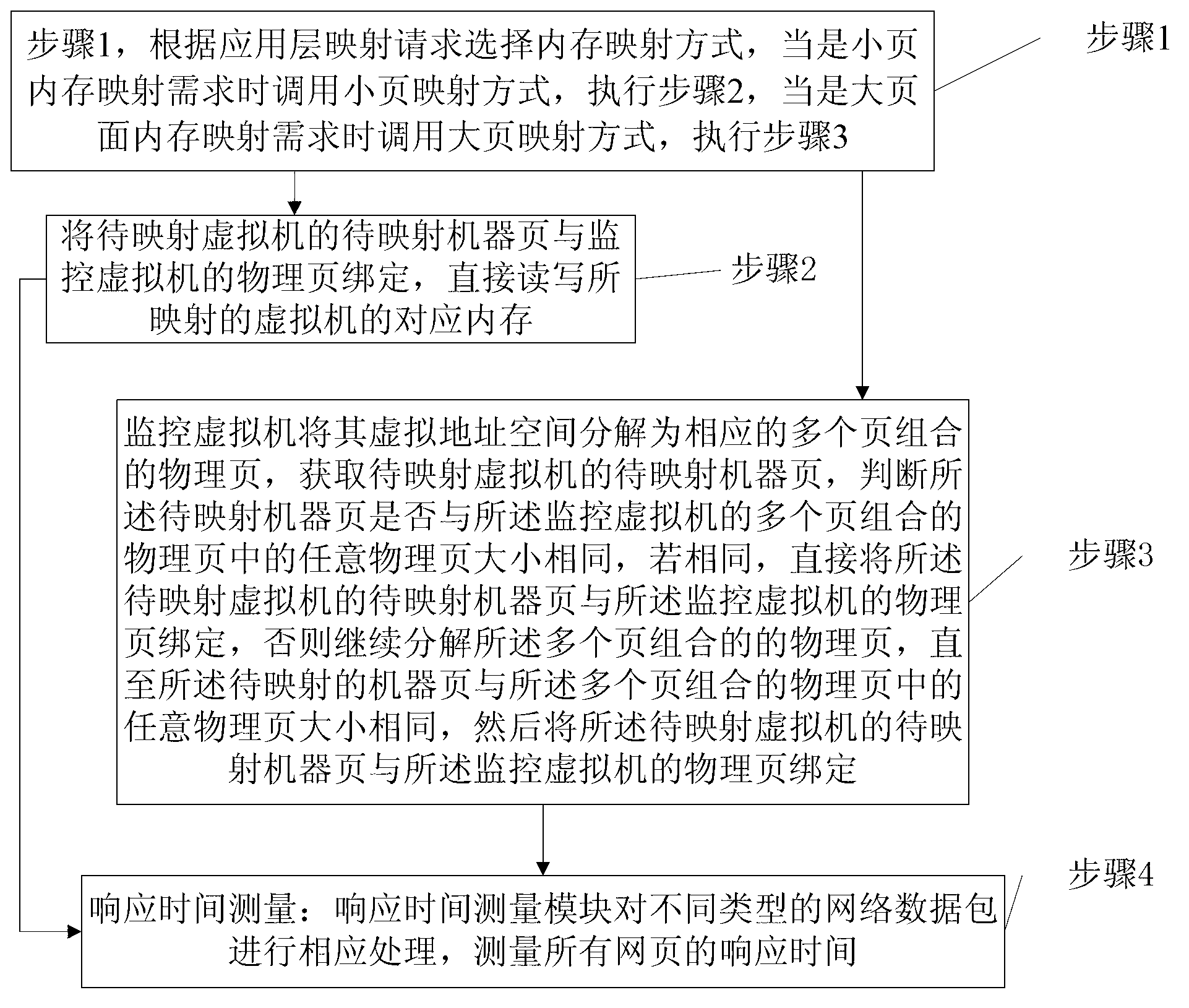
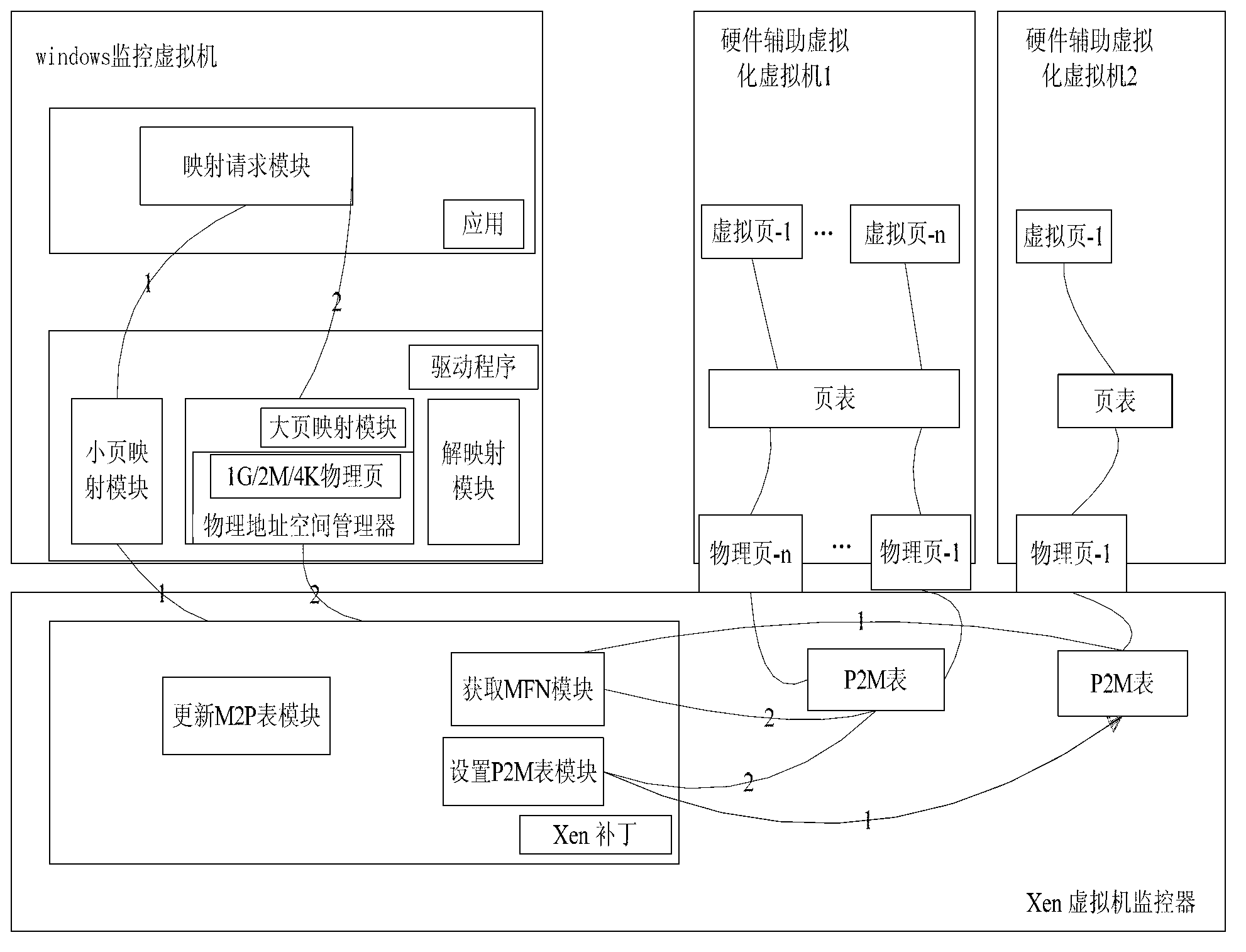
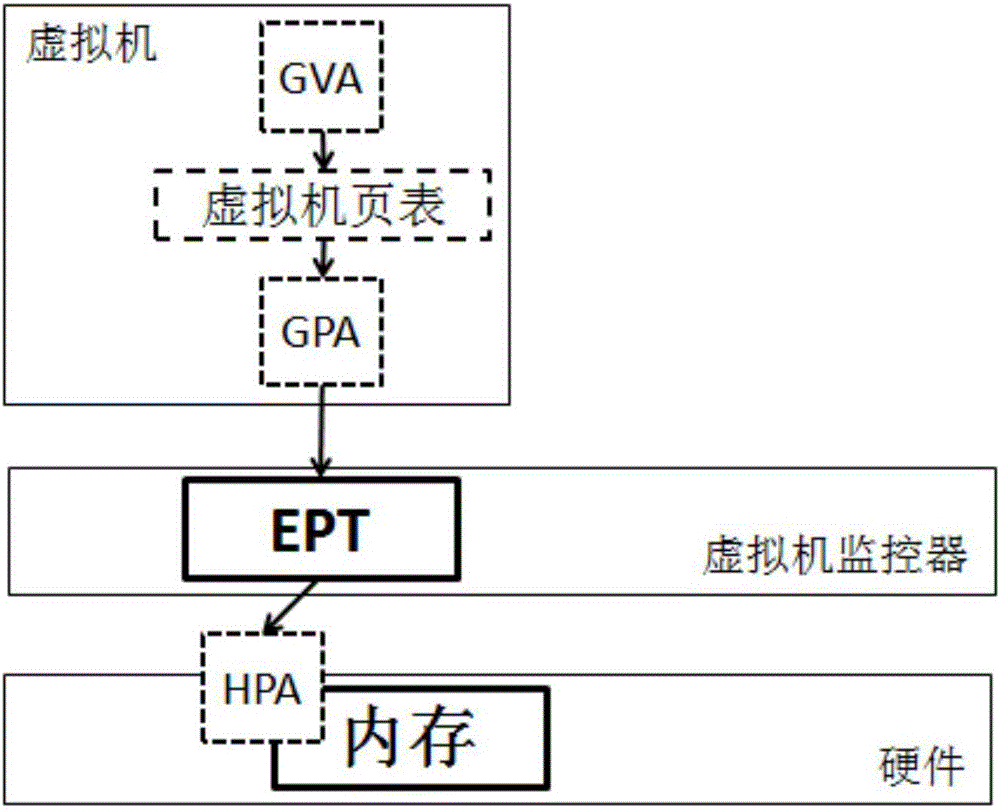
Virtual machine memory mapping method and system
InactiveCN103257929AAvoid visitingMeet the needs of specific applicationsMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationProtocol ApplicationVirtual address space
The invention provides a virtual machine memory mapping method and a system, wherein the method comprises step 1 of selecting a memory mapping method according to an application layer mapping request, and executing step 2 or step 3; step 2 of binding machine pages to be mapped of a virtual machine to be mapped and physical pages of a monitoring virtual machine, directly reading and writing corresponding memory corresponding to the mapped virtual machine, and executing step 4; step 3 of enabling the monitoring virtual machine to decompose a virtual address space into corresponding physical pages combined by a plurality of pages after the monitoring virtual machine processes unused physical memory in the physical memory, obtaining the machine pages to be mapped of the virtual machine to be mapped, carrying out corresponding processing after judgment, then binding the physical pages of the monitoring virtual machine and the machine pages to be mapped of the virtual machine to be mapped, and executing step 4; step 4 of releasing the memory of the monitoring virtual machine corresponding to the mapping memory of the virtual machine to be mapped after mapping, setting a mapping list from the machine pages of the monitoring virtual machine to the physical pages, and setting a corresponding item to be an invalid machine page.
Owner:SHANGHAI YINGLIAN SOMATOSENSORY INTELLIGENT TECH CO LTD
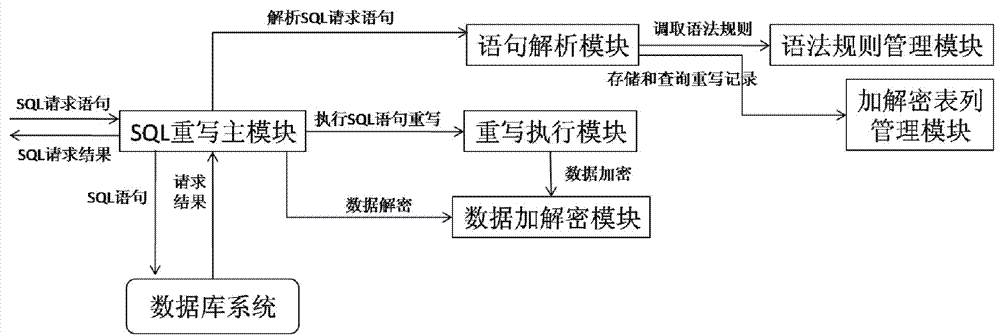
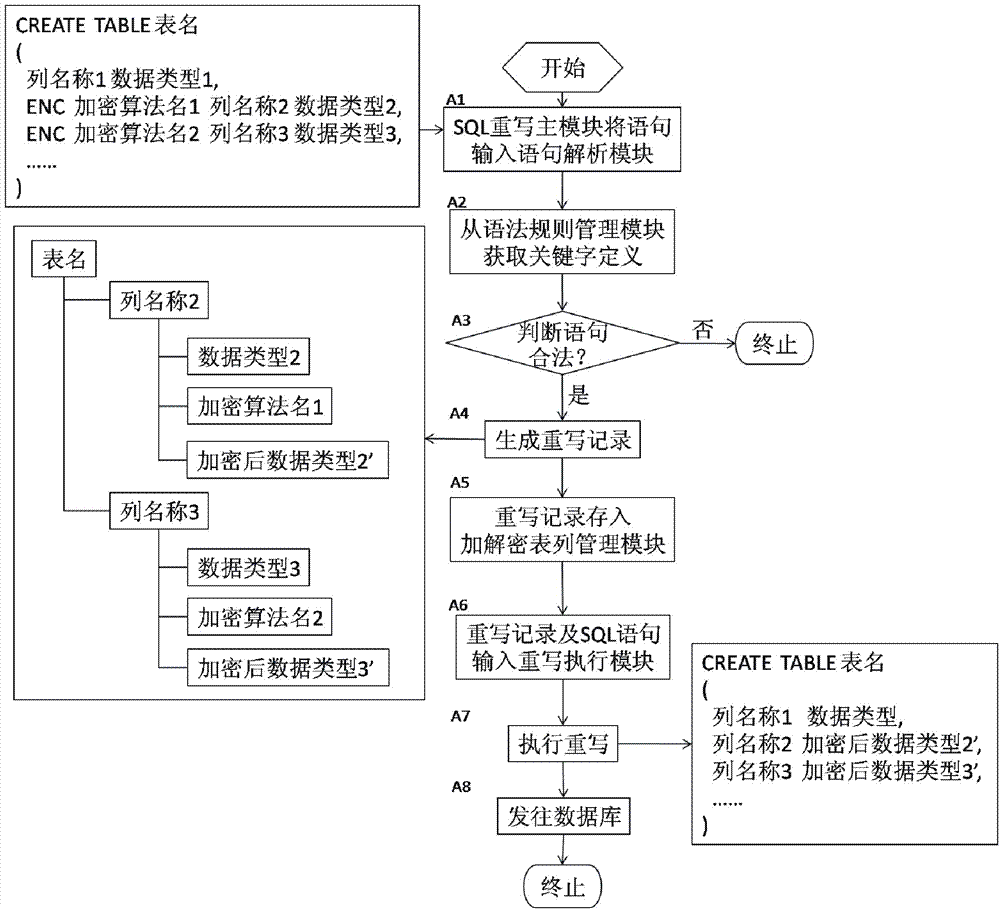
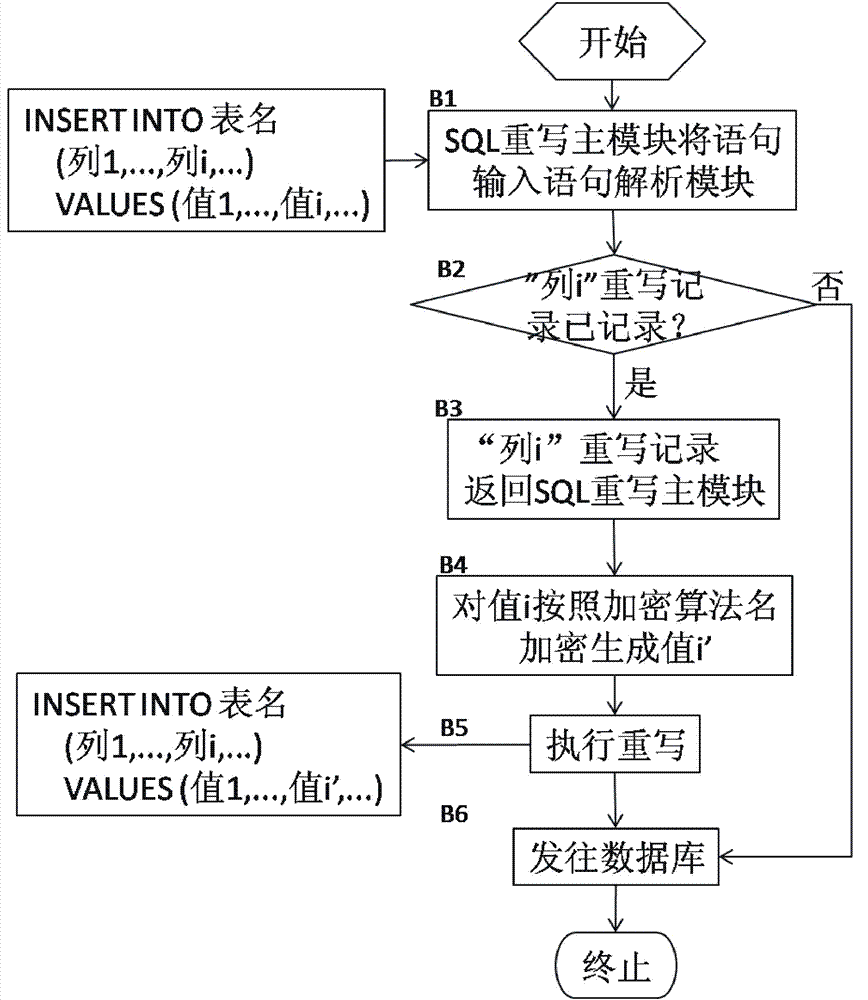
Structured query language (SQL) rewrite based database external encryption/decryption system and usage method thereof
ActiveCN102902932AAvoid encryption and decryption overheadAvoid visitingDigital data protectionSpecial data processing applicationsDatabase encryptionData query
The invention provides an SQL rewrite based database external encryption / decryption system and a usage method thereof. The system comprises an SQL rewrite main module, a statement parsing module, a grammatical rule management module, an encryption / decryption table management module, a rewrite execution module and a data encryption / decryption module. The method comprises the steps of executing a rewritten data sheet creation process, a rewritten data insertion process and a data query process. According to the system and the method, an SQL rewrite technology is used, and data are encrypted and decrypted outside a database system, so that encryption / decryption costs of the database system are avoided.
Owner:武汉华工安鼎信息技术有限责任公司
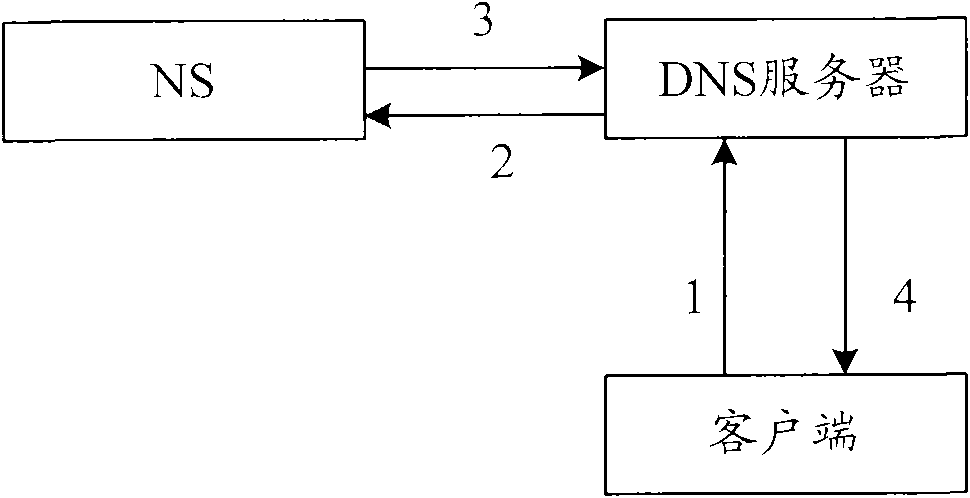
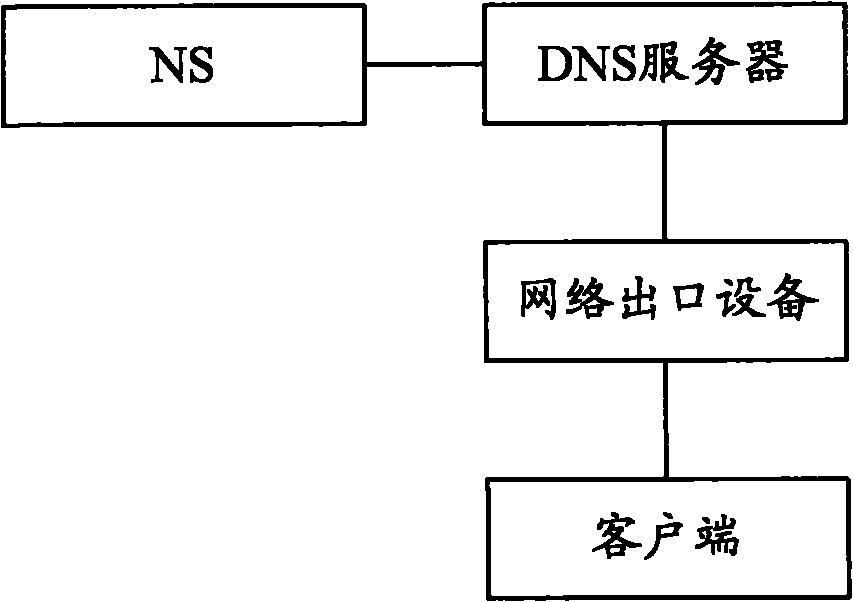
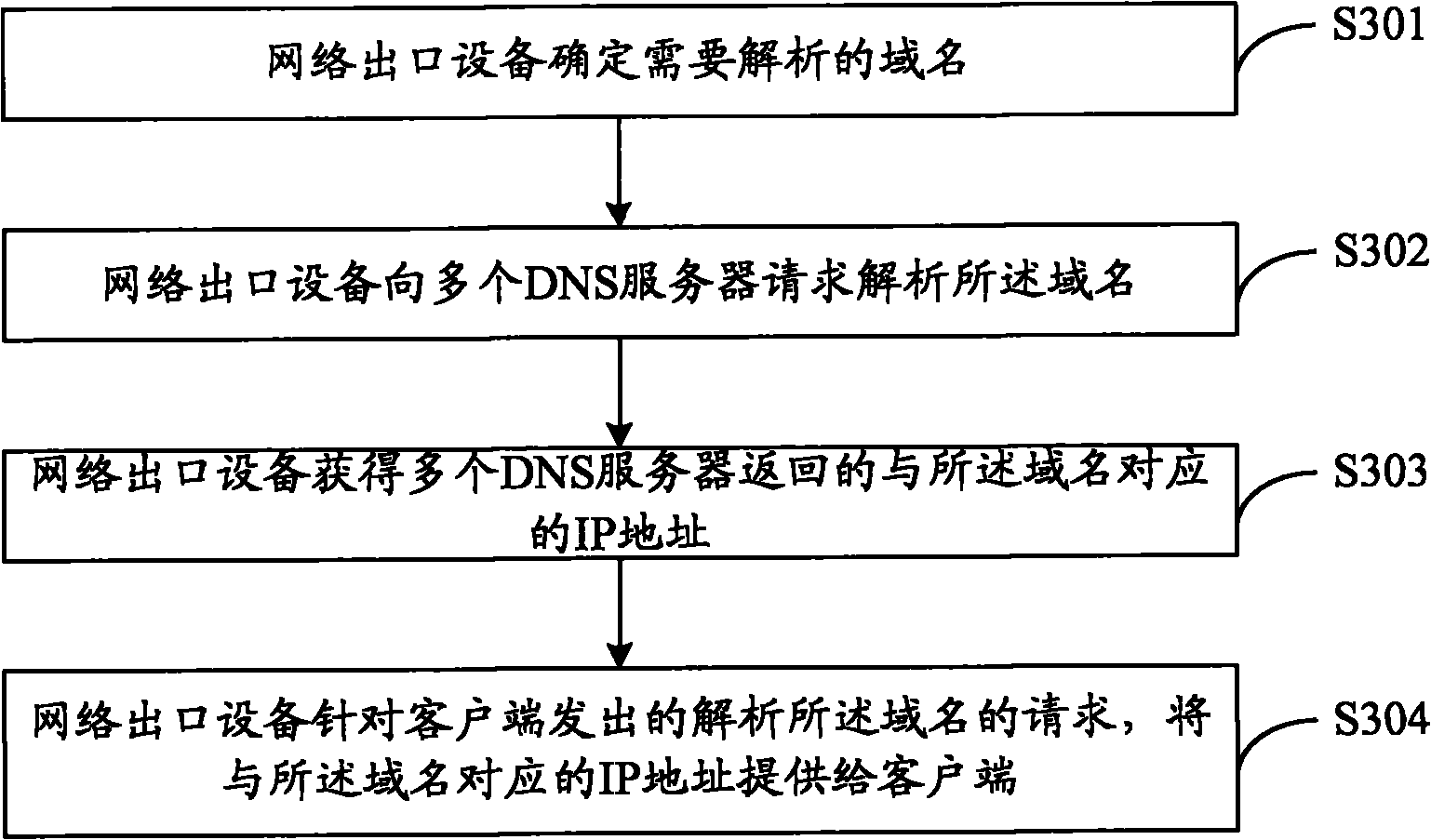
Defense method for domain name system server buffer infection and network outlet equipment
The invention provides a defense method for DNS (Domain Name System) server buffer infection, which is applicable for a network environment in which network outlet equipment is arranged between a client and a DNS server. The method comprises the following steps that the network outlet equipment determines a domain name to be analyzed, requests a plurality of DNS servers to analyze the domain names, acquires IP addresses which are returned by the DNS servers and correspond to the domain names and provides the IP addresses corresponding to the domain names aiming at the request transmitted by the client for analyzing the domain names. The invention also provides the network outlet equipment. The invention can avoid the phenomenon that the DNS servers provide illegal IP addresses for the client under the condition that the DNS server buffer is infected, so that the client accesses to network entities corresponding to the illegal IP addresses.
Owner:BEIJING LEADSEC TECH
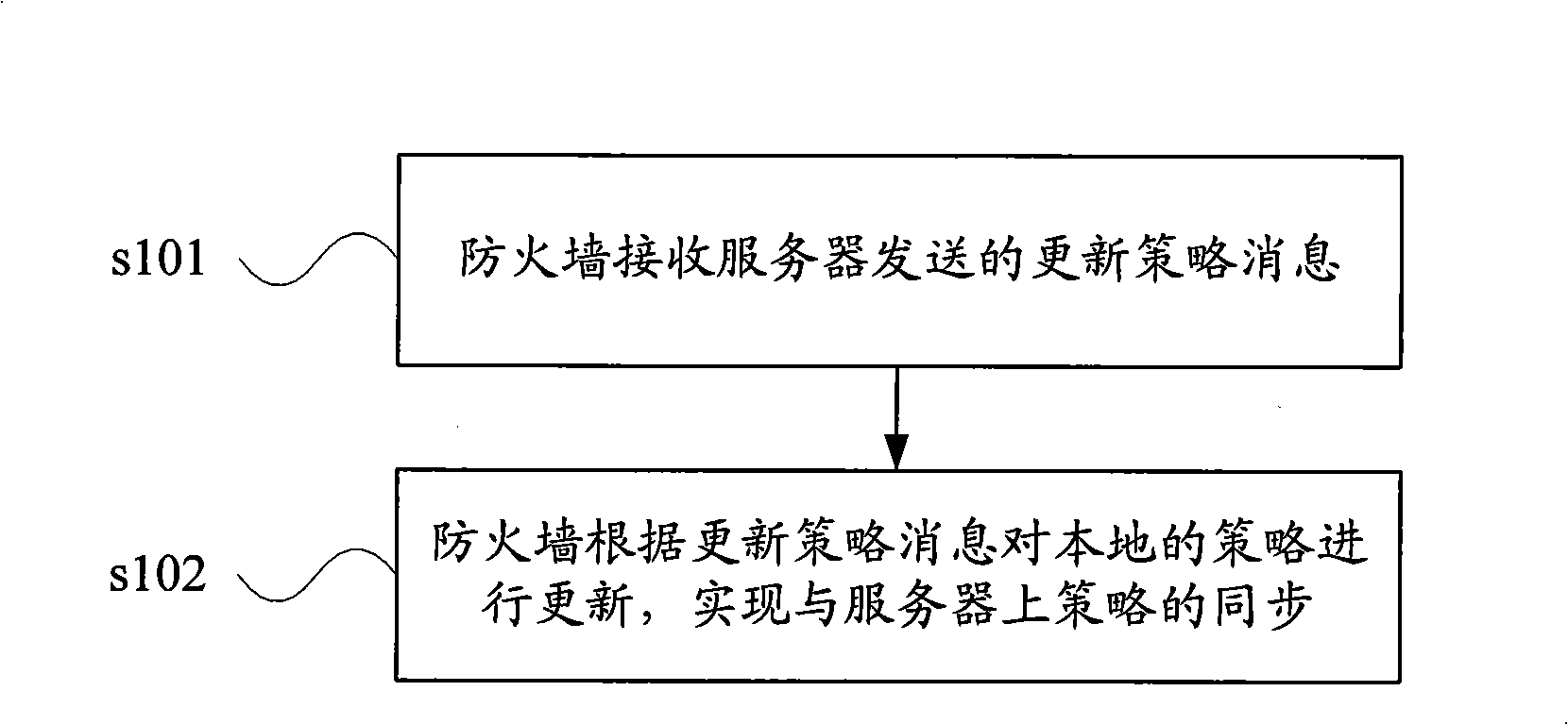
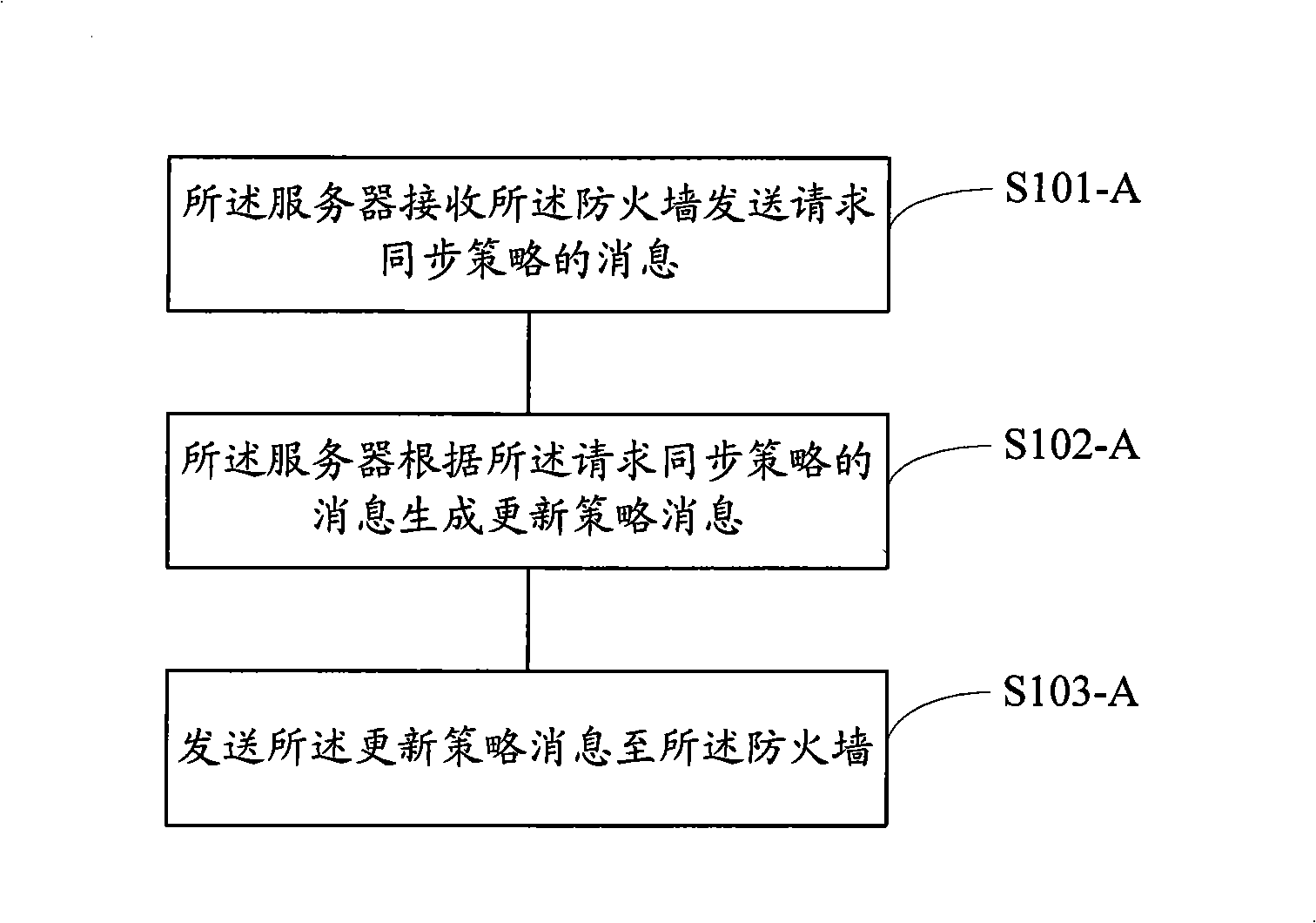
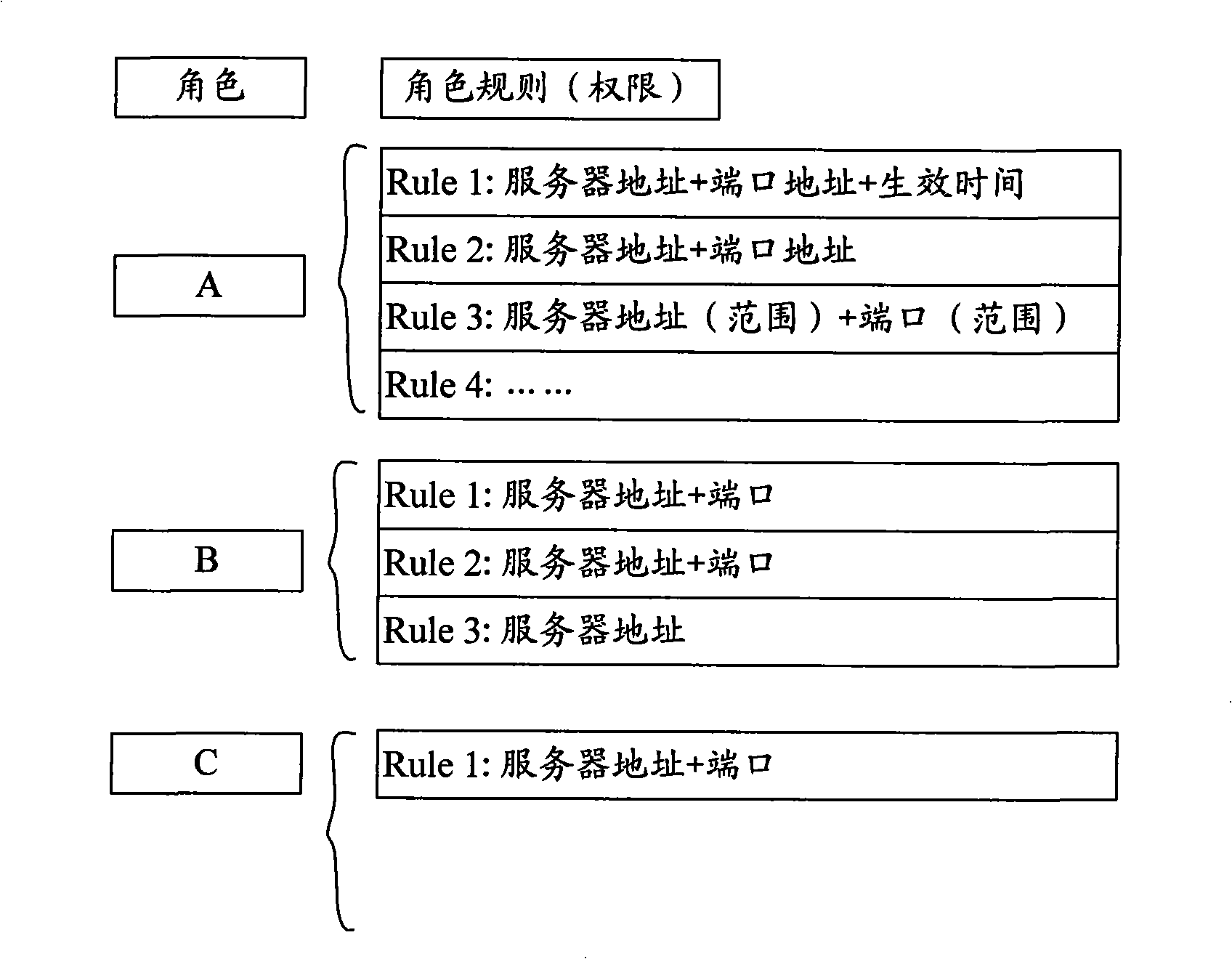
Fireproof wall and server policy synchronization method, system and apparatus
ActiveCN101340444AControl accessAvoid visitingError prevention/detection by using return channelData switching networksDistributed computing
The embodiment of the invention discloses a strategy synchronization method, a system and a device. The method comprises that: a firewall receives an updating strategy message which is sent by a server; the firewall carries out the updating of a local strategy according to the updating strategy message, thereby realizing the strategy synchronization on the server. By adopting the embodiment of the invention, the dynamic synchronized firewall and ACL rules on the server can rapidly update role rules which are bound by a user terminal and the synchronization of more strategies and the switch of authorities of the user terminal can be rapidly realized without the manual configuration on the firewall.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Equipment for controlling access of facilities according to the type of application
InactiveCN1536842AAvoid visitingUnauthorized memory use protectionData switching by path configurationMemory addressProtection mechanism
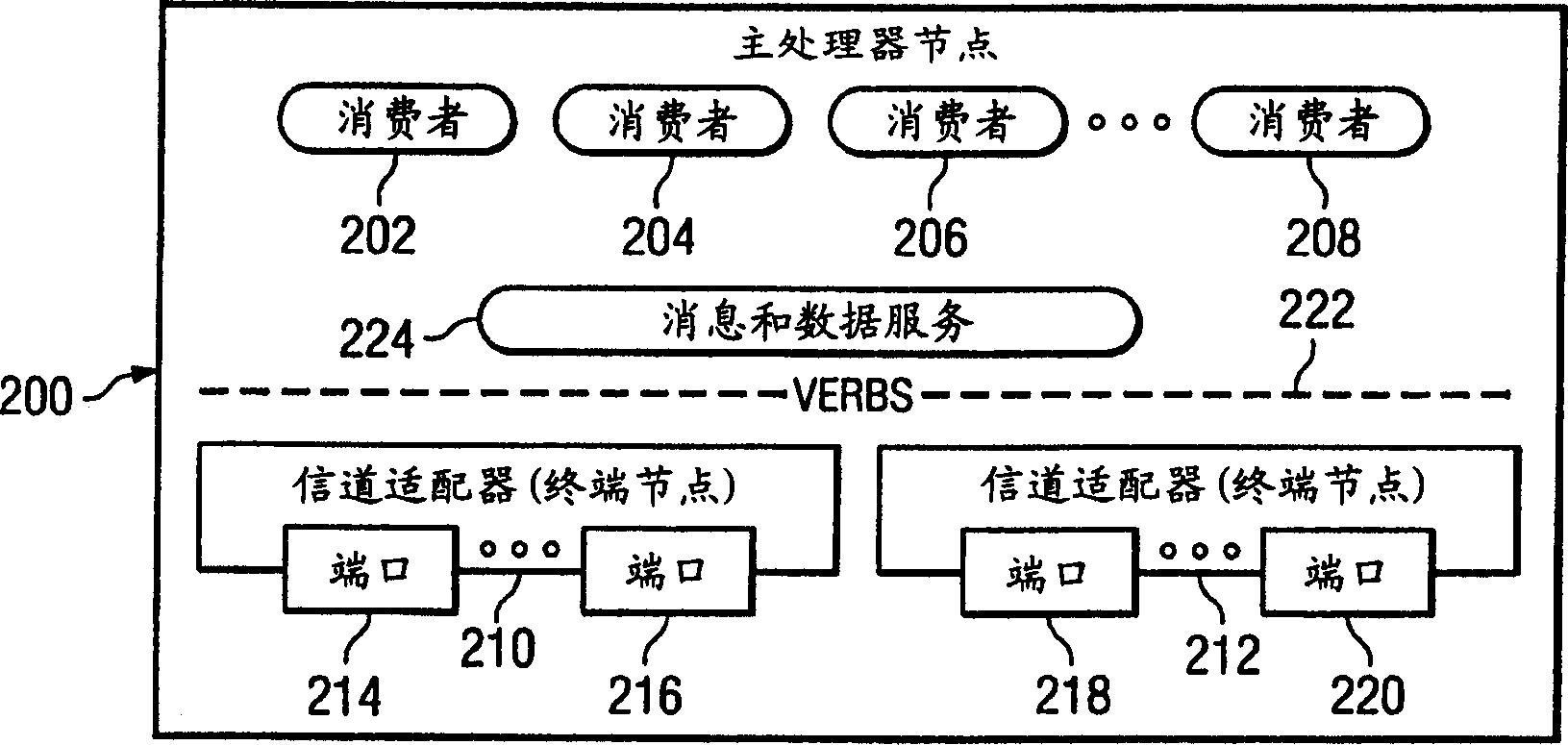
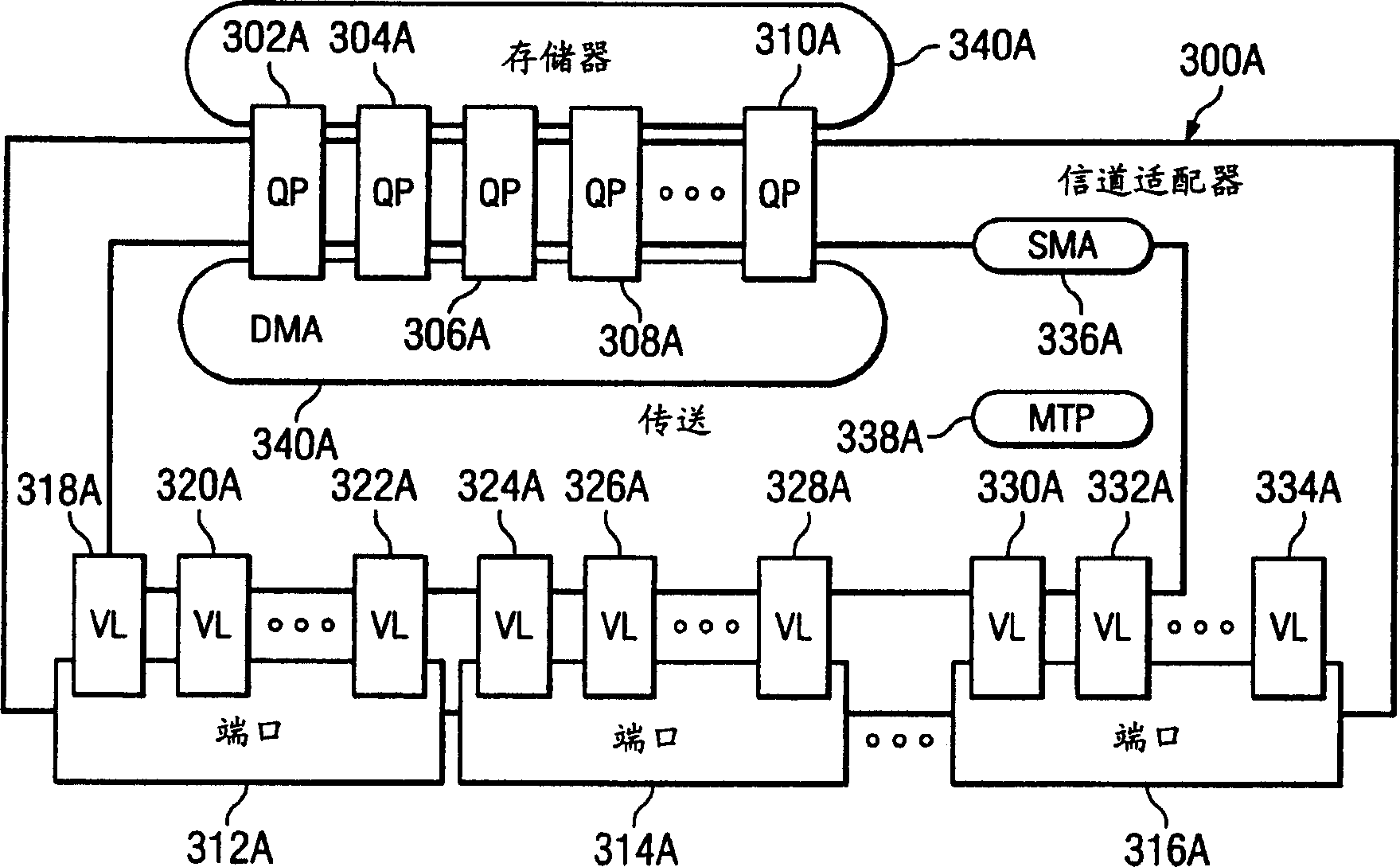
An apparatus, system and method for controlling access to facilities based on usage class of a requestor are provided. With the apparatus, system and method, a two level protection mechanism is provided for protecting host channel adapter (HCA) facilities from unauthorized access. With the present invention, a first level of access is provided through virtual address translation and a mechanism for determining if the requestor of access may access a system memory address space page associated with a real address to which the virtual address maps. A second level of access is provided through the allocation of usage classes and determining a required usage class for accessing an HCA facility.
Owner:IBM CORP
Security network attachment device and method for block chain
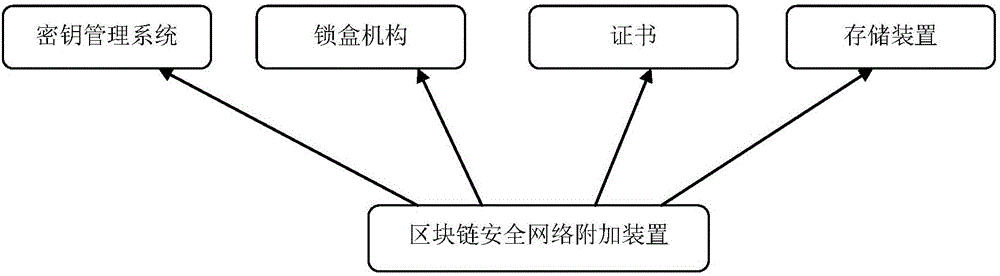
ActiveCN106330452AAvoid visitingAvoid potential threatsUser identity/authority verificationOriginal dataData file
The present invention provides a security network attachment device for a block chain. The security network attachment device for the block chain comprises a key management system, a box locking mechanism, a certificate and a storage device; the key management system is used for providing a decryption key; the box locking mechanism is used for storing a key, wherein the key is stored in a unique trusted server and is supplied to a user who accesses a file; the certificate is used for managing an authorized user; and the storage device is used for storing the non-linear checksum of original data and an encrypted result. The user can verify whether the file is modified when the file is stored through the storage device. The user can verify the integrity of writing through verifying and analyzing the metadata file of the key body of the file and verifying a provided digital signature. With the security network attachment device and method of the invention, based on data encryption, decryption is carried out a client only, so that any unauthorized users can be prevented from accessing data, and potential threats caused by accesses threatening a system administrator and physical capture for a magnetic disk can be avoided.
Owner:广东中云智安科技有限公司
Method and server for controlling multilevel access authority of access user
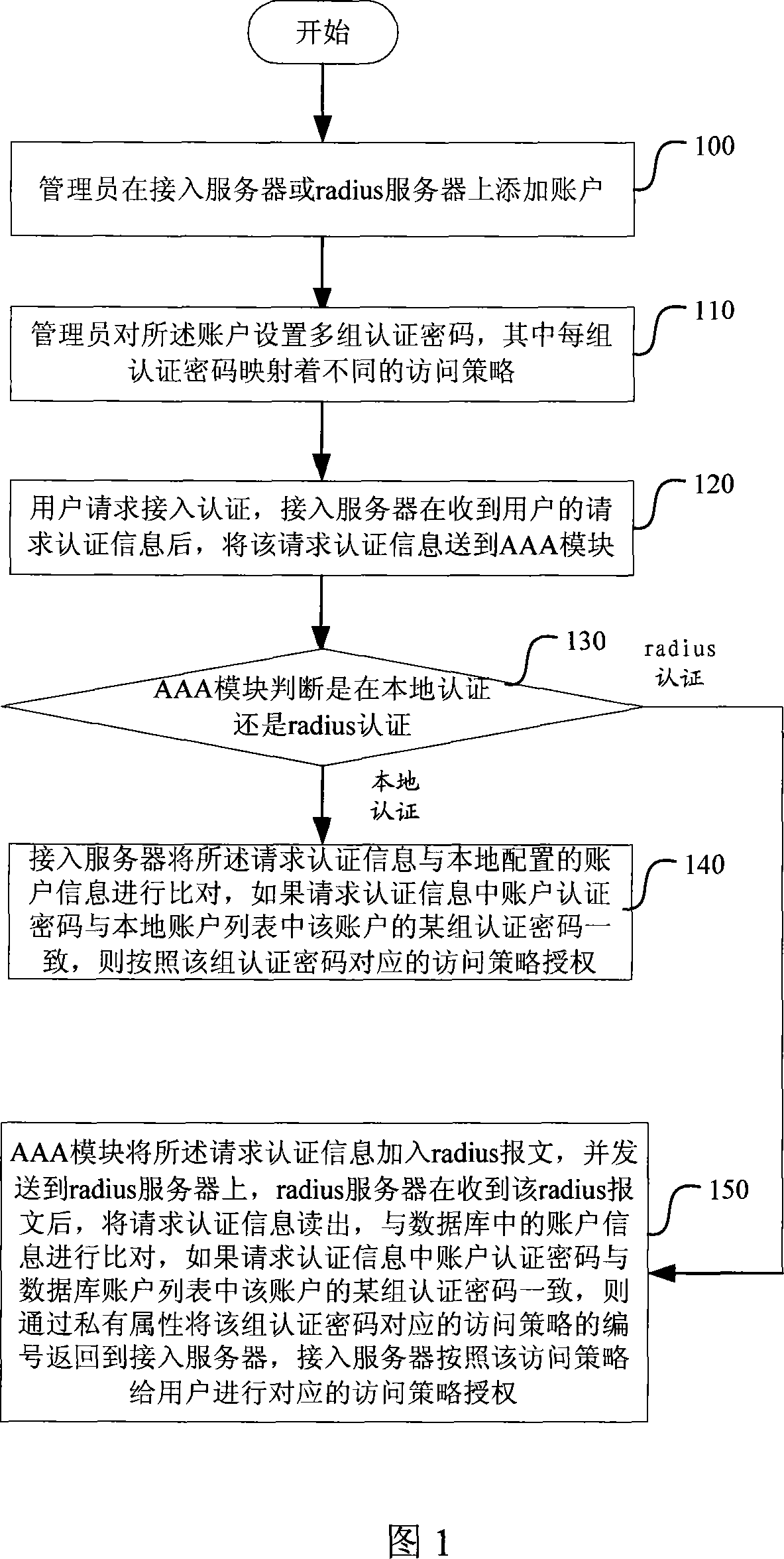
ActiveCN101247336AGuaranteed use requirementsAvoid visitingData switching by path configurationUser verificationUser authentication
The present invention discloses a method and server of controlling multi-class access authorization of a linking account, including that: administrators adds accounts on the access server or remote dial user authentication server, sets plural groups of identification codes for the accounts, each of which reflects different access strategies; when the users request dialing-in identification, the access server compares the required identification information of the user with the account information if the dialing-in identification is local identification, and then Authorize the access strategy corresponding to the group of identification codes if the code of the required identification information is identical with the one of the code in the account of local account list. The invention supplies an access technical means, which not only confirm the web requirement of the adult but prevent the children accessing the bad information in the web. Only one account is needed for a family, so it is very economical.
Owner:ZTE CORP
Double-factor identity verification method based on intelligent equipment
InactiveCN103986584AEnsure safetyImprove securityUser identity/authority verificationApplication serverValidation methods
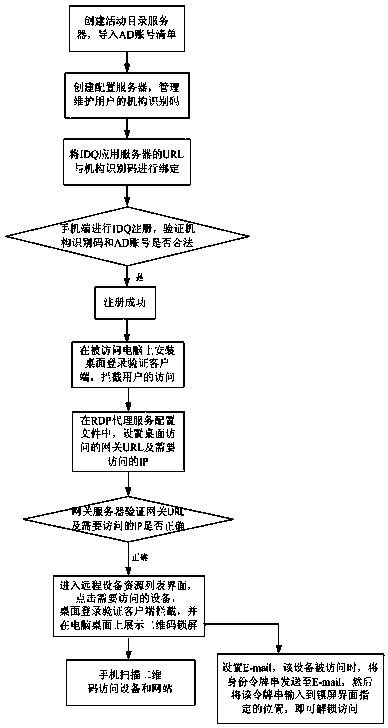
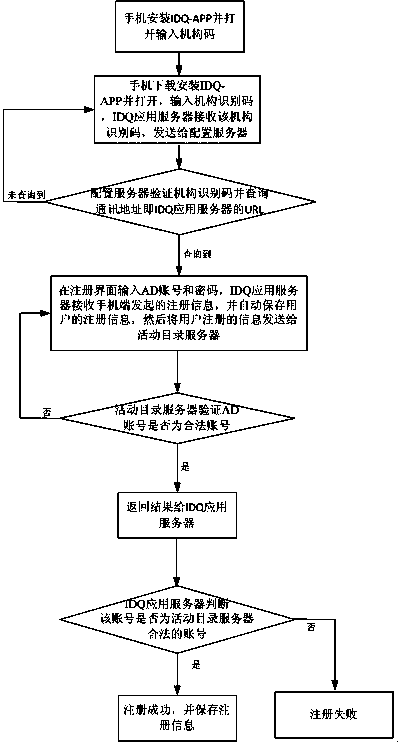
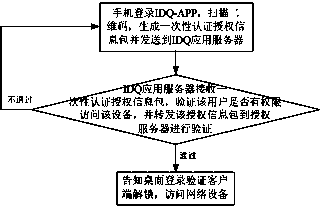
The invention discloses a double-factor identity verification method based on intelligent equipment, which is used for solving the problems of inconvenient operation and low safety of user account numbers and network equipment caused by inputting account numbers and passwords during logging in a long-distance website in the prior art. The double-factor identity verification method based on the intelligent equipment comprises the following steps: establishing an active directory server, and guiding an AD (Active directory) account number list into the active directory server; establishing a configuration server, and managing and maintaining an organization identifying code of a user; binding a URL (Uniform Resource Locator) of an IDQ (internet data query) application server and the organization identifying code; and carrying out IDQ registration at a mobile phone terminal, verifying whether the organization identifying code and the AD account number are legal, if the organization identifying code and the AD account number are legal, registering successfully, otherwise, registering unsuccessfully; and visiting the equipment and a website by using a mobile phone. The double-factor identity verification method has the advantages that the mobile phone is used for scanning real-time alteration two-dimension codes generated by using a verification server so as to carry out login access of network resources, a conventional login manner of inputting the account numbers and the passwords by using a conventional keyboard is replaced, and the safety of the user account numbers and network equipment is greatly guaranteed.
Owner:上海金融云服务集团安全技术有限公司
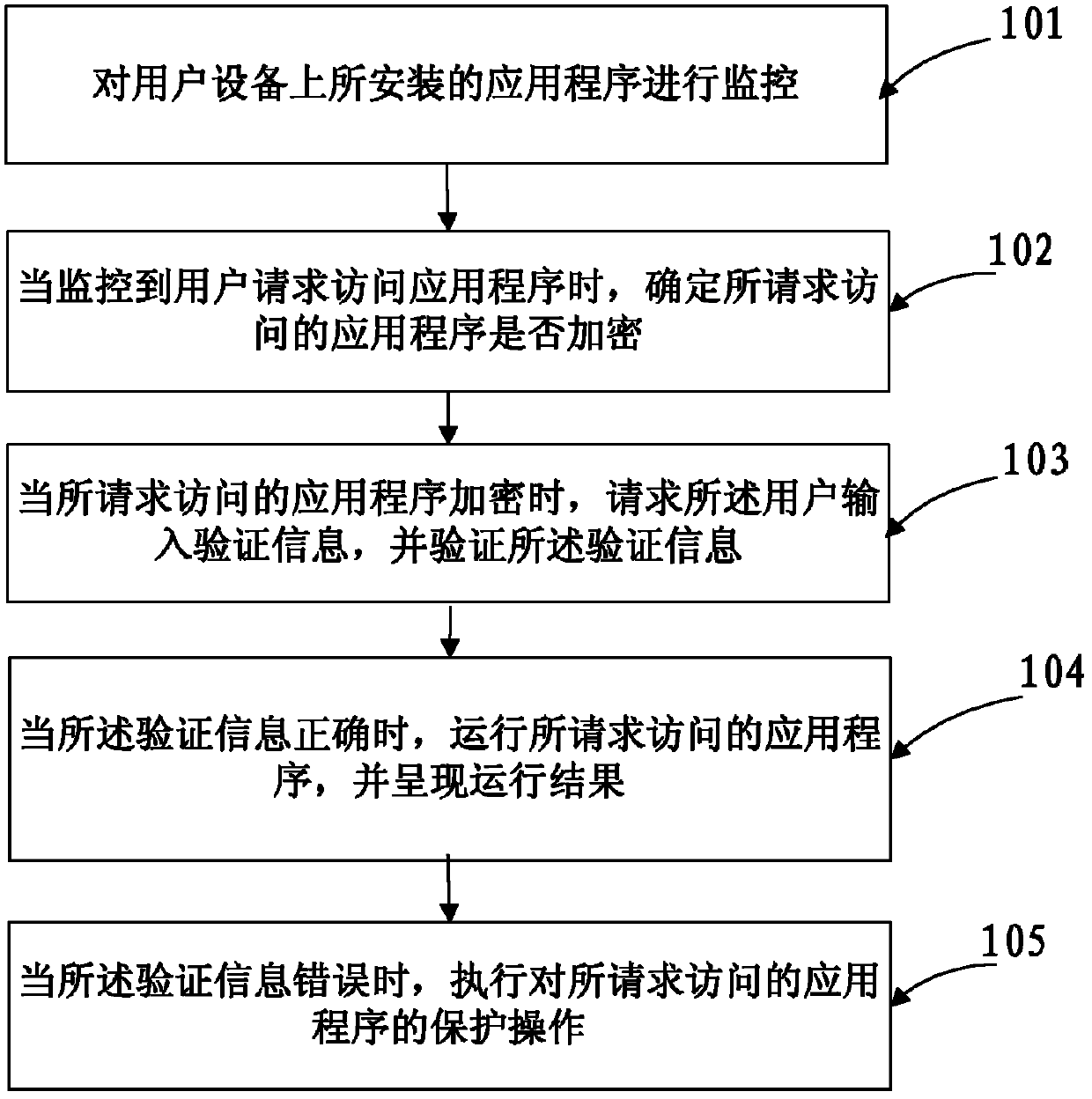
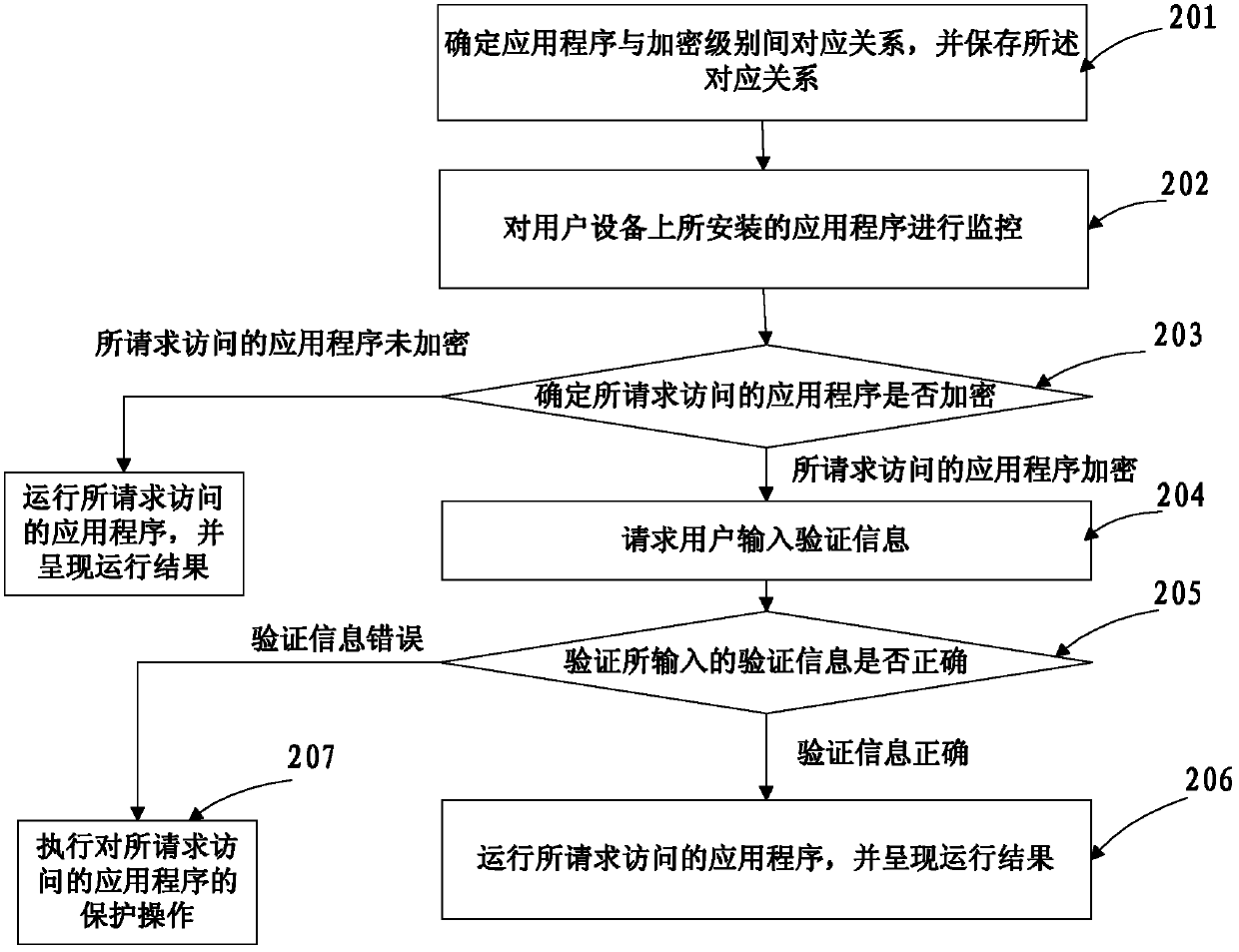
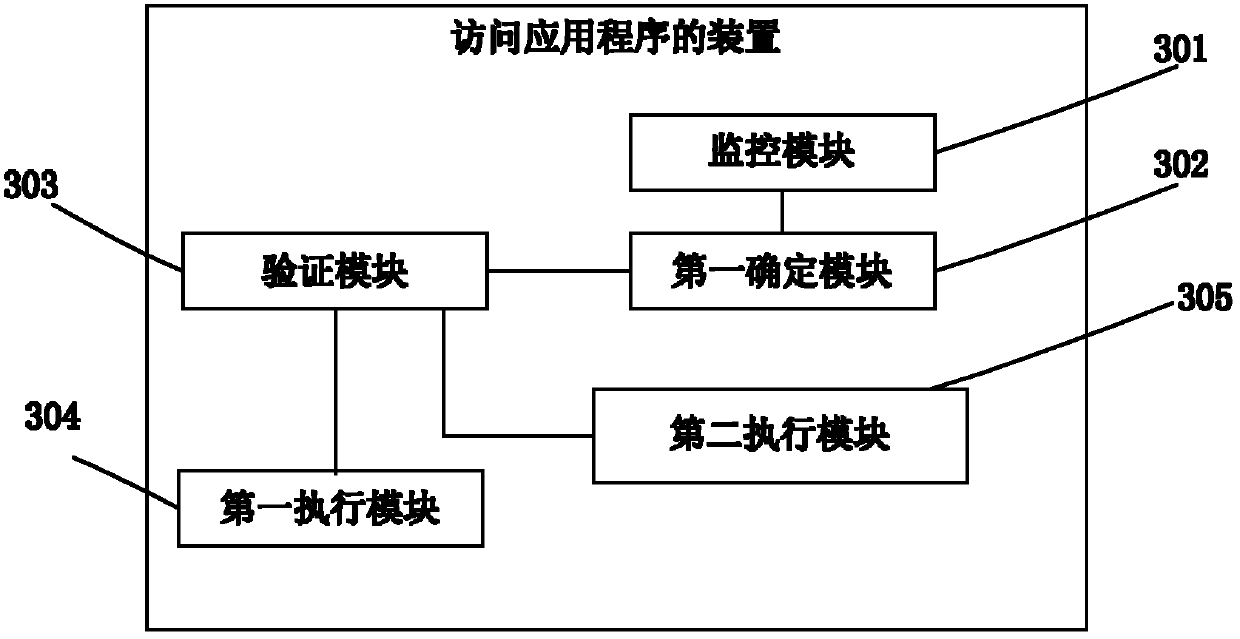
Application program accessing method and device
ActiveCN103377332AAvoid visitingDatabase updatingDigital data authenticationUser deviceApplication procedure
Disclosed are a method and an apparatus for accessing an application, which relate to the technical field of information security. The method comprises: monitoring an application installed on a user equipment; when it is detected that a user requests to access an application, determining whether the application whose access is requested is encrypted; when the application whose access is requested is encrypted, requesting the user to input authentication information, and authenticating whether the authentication information is correct; when the authentication information is correct, running the application whose access is requested, and presenting a running result; and when the authentication information is incorrect, executing a protection operation for the application whose access is requested. In this way, a malicious access to the application by someone can be effectively prevented, thereby effectively ensuring the security of user information in the application.
Owner:TENCENT TECH (SHENZHEN) CO LTD
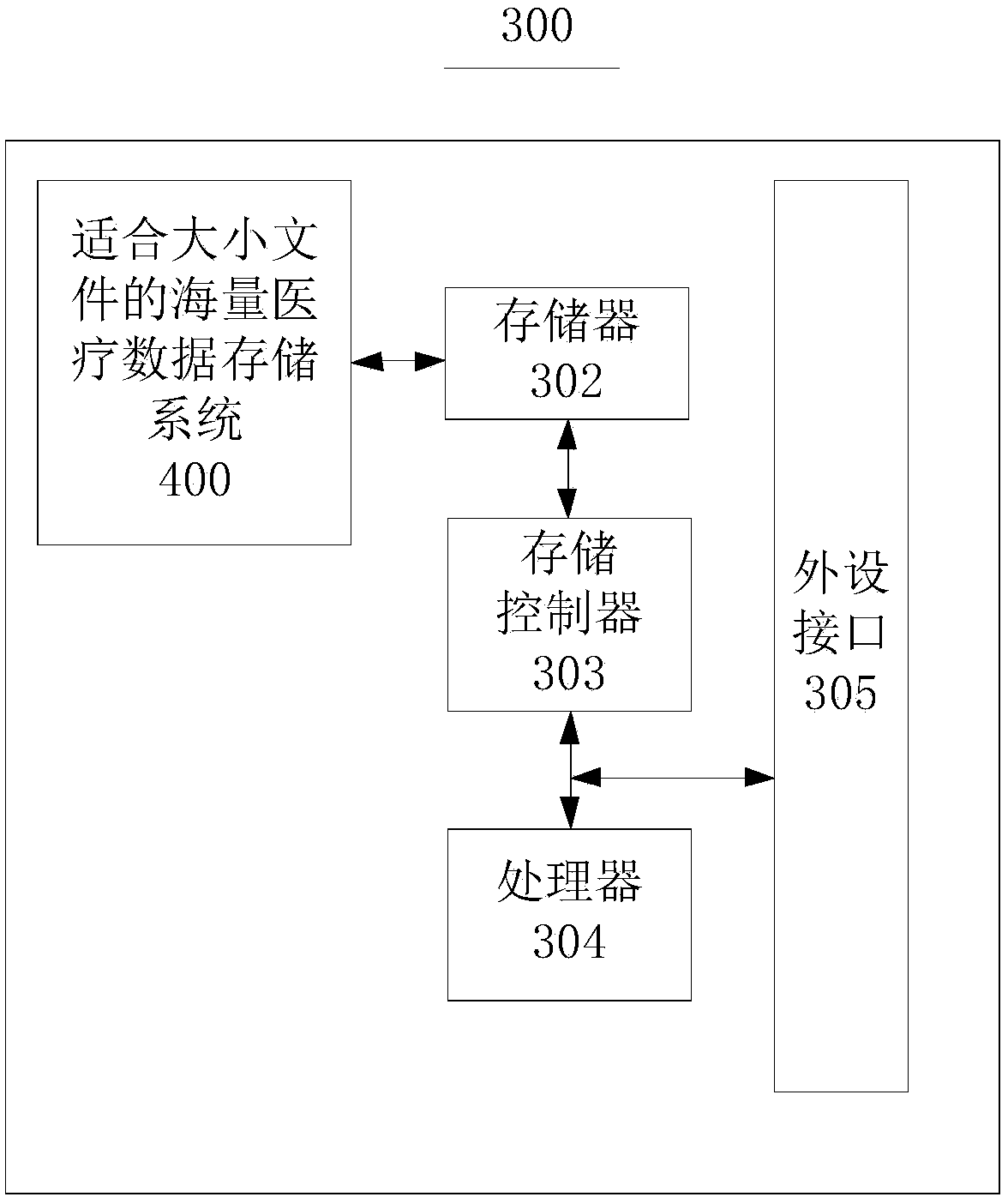
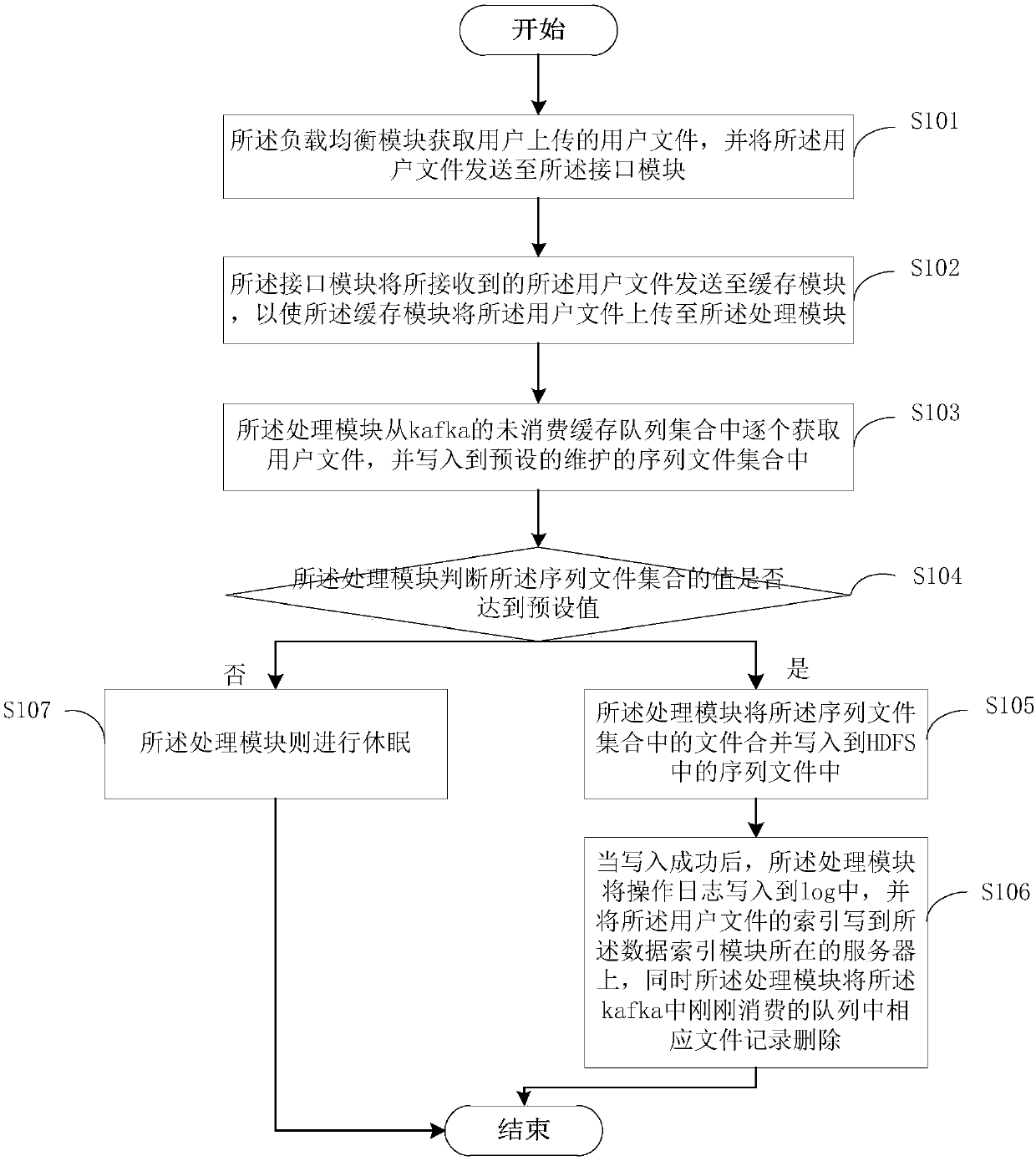
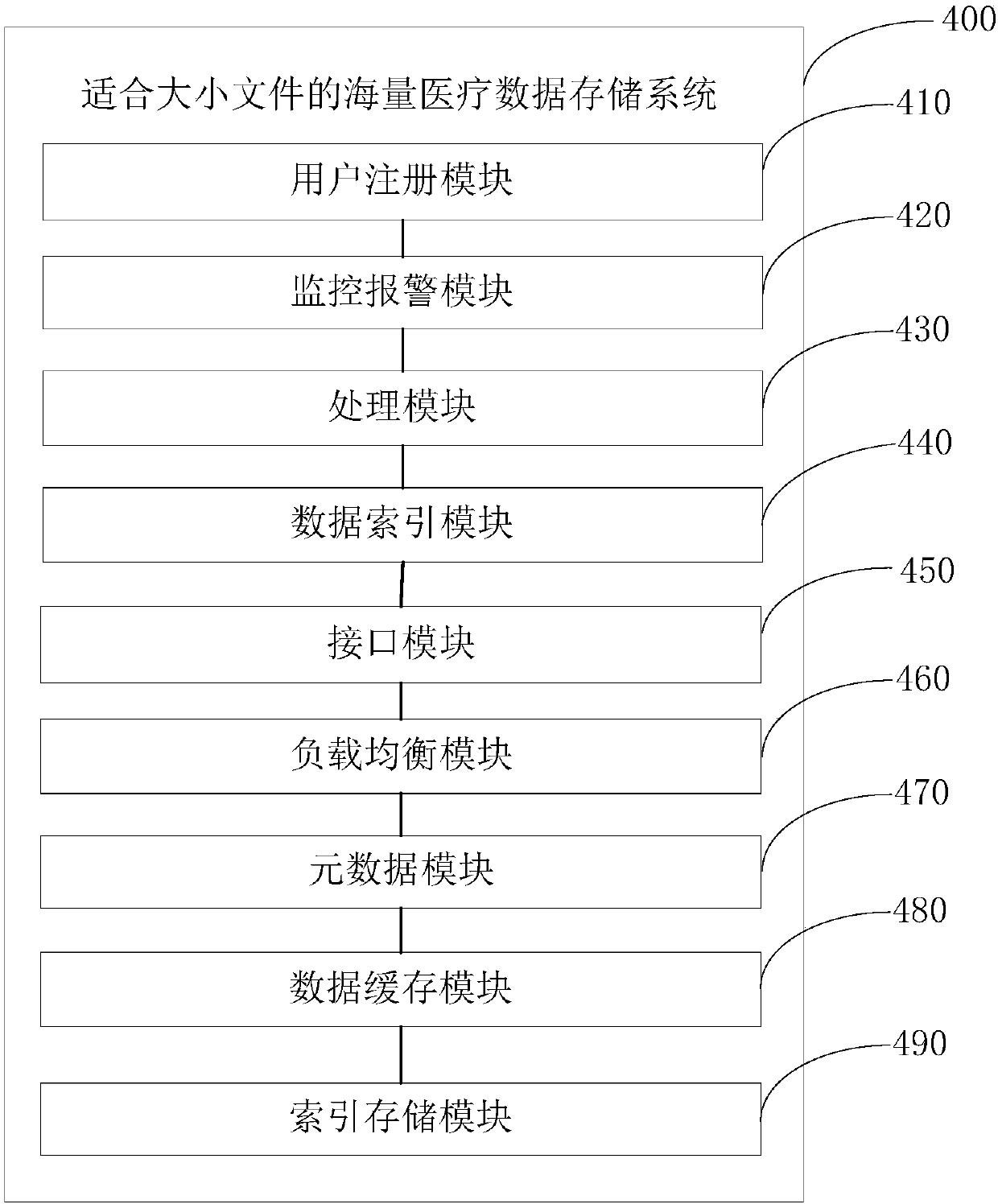
Mass medical data storage system and data storage method suitable for files of different sizes
ActiveCN108053863AAvoid visitingAvoid registrationPatient healthcareFile access structuresRelational databaseInstability
An embodiment of the invention provides a mass medical data storage system and a data storage method suitable for files of different sizes and belongs to the technical field of data storage. Aiming atapplication scenes with coexistence of mass large files and small files in the medical field, the system solves a problem that a traditional relational database is not suitable for unstructured data,a problem that redis is not suitable for mass data storage, a problem of system instability when only hbase is adopted for storage and problems of inadaptability to large files and inconvenient fileretrieval when hdfs is adopted merely for solving a problem of small file storage.
Owner:THE FIRST AFFILIATED HOSPITAL OF THIRD MILITARY MEDICAL UNIVERSITY OF PLA
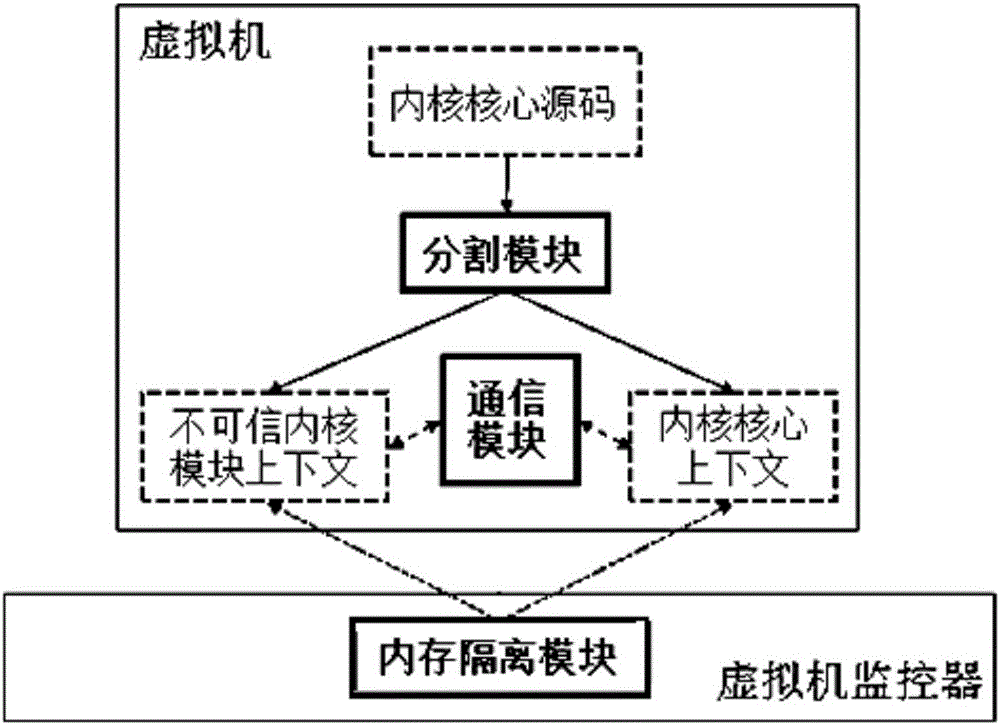
Virtual hardware characteristic-based system and method for efficiently isolating kernel modules
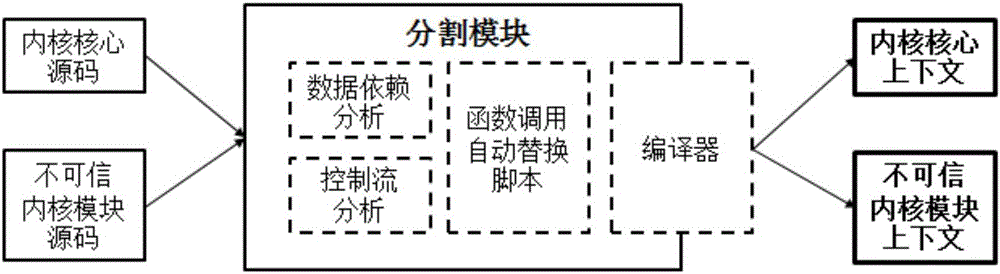
InactiveCN106203082AEffective segmentationEffective isolationInternal/peripheral component protectionPlatform integrity maintainanceVirtualizationControl flow
The invention provides a virtual hardware characteristic-based system and method for efficiently isolating kernel modules. According to the system and method, a secure and efficient strong isolation mechanism aiming at incredible kernel modules is designed, so that the present requirements for the security and functionality can be satisfied. Compared with the existing solutions, the system and method has better performance, stronger isolation and higher backward compatibility. The designed mechanism is easy to deploy in the present mainstream cloud computing platforms, so that considerable social benefit and economic benefit can be provided. In the mechanism, when the incredible kernel modules need to call functions of kernel cores or the kernel cores need to call functions in the incredible kernel modules, a secure and efficient virtual hardware characteristic-based control flow transformation mechanism is established, so that more attack surfaces are not exposed in the switching.
Owner:SHANGHAI JIAO TONG UNIV
Encryption and decryption method and system of terminal data
ActiveCN103259651AAvoid visitingKey distribution for secure communicationDigital data protectionComputer terminalData storing
The invention provides an encryption and decryption method and system of terminal data, and relates to encryption techniques in the field of data safety. The encryption and decryption method and system solves the problem that in the prior art, enterprise data stored on a mobile terminal have safety hidden risks. The encryption and decryption method includes the steps: a client receives a private secret key set by a terminal user, the private secrete key set by the terminal user is submitted to a server end, the server end produces a system secret key corresponding to the terminal user and stores the system secret key, when the terminal user carried out data encryption and decryption operations, the client submits the private secret key of the terminal user to the server end, the server end returns to the corresponding system secrete key after the private secrete key passes verification, and the client carries out encryption and decryption operations on data by means of the private secrete key and the corresponding system secrete key.
Owner:MAIPU COMM TECH CO LTD
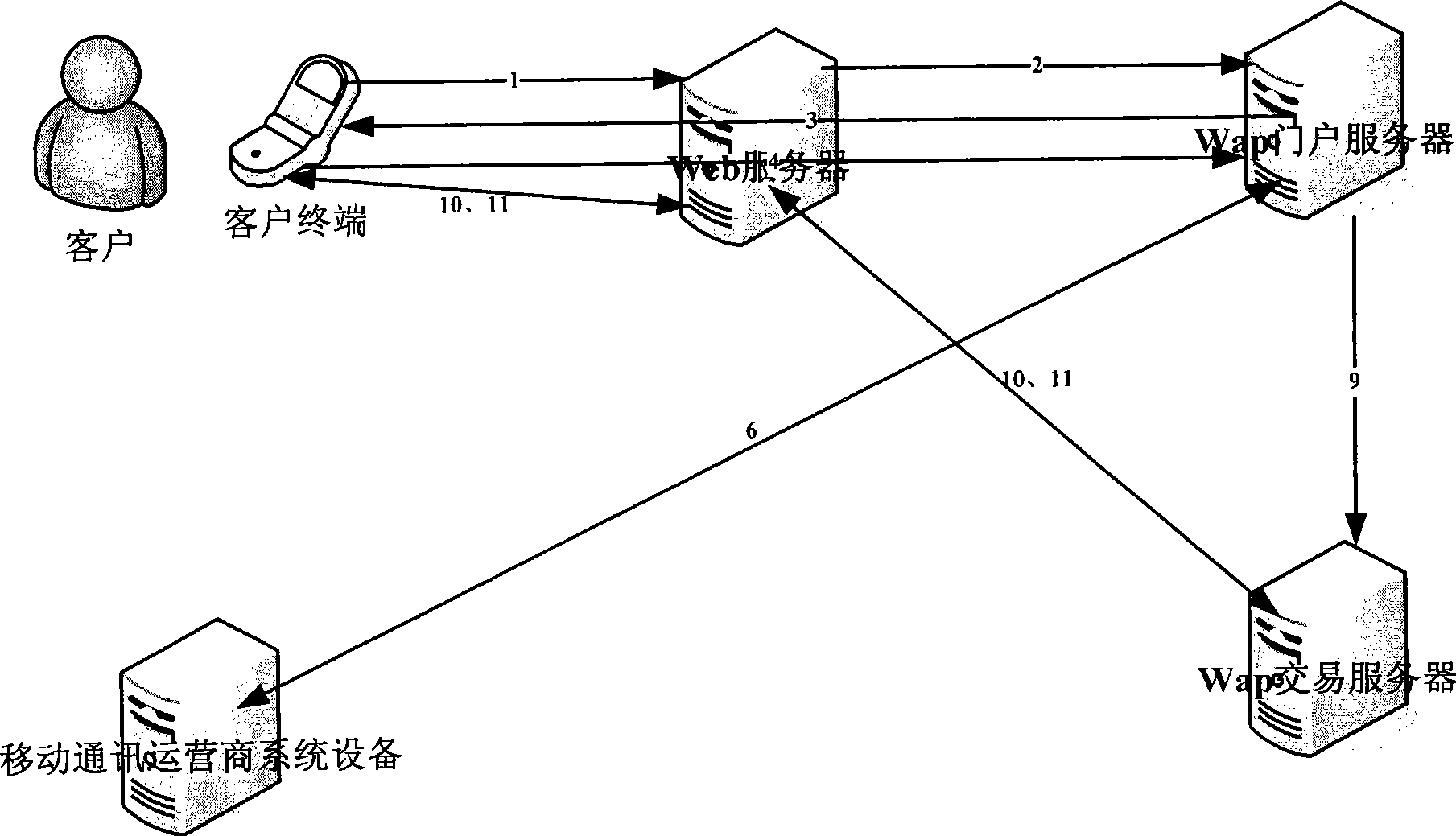
System for realizing WAP mobile banking transaction security control and method thereof
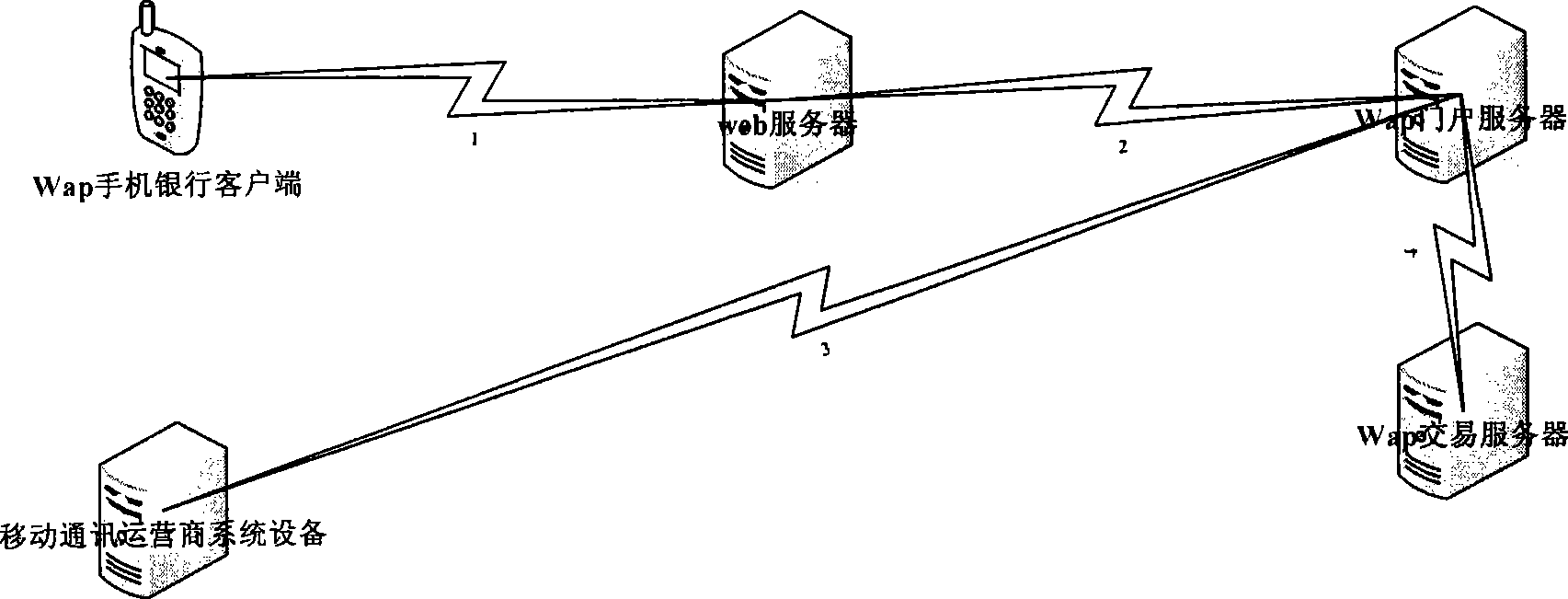
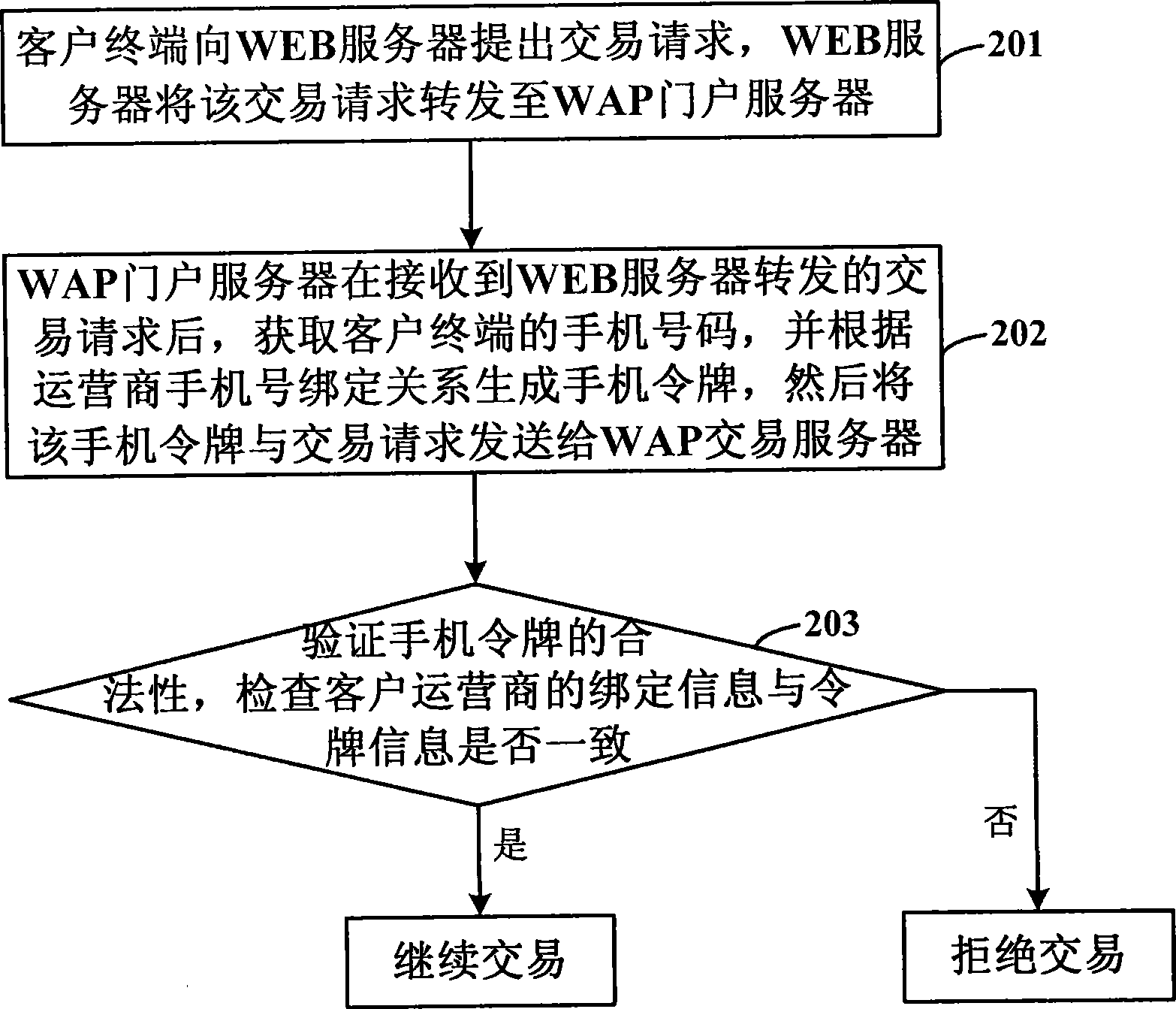
ActiveCN101448001AImprove securityAvoid visitingPayment architectureTransmissionDomain nameMobile Telephone Number
The invention discloses a system for realizing WAP mobile banking transaction security control and a method thereof. The system comprises a user terminal, a WEB server, a WAP portal server, a WAP transaction server and mobile communication operator system equipment, wherein, the WEB server is used for providing domain name address service and transferring a transaction request received from the user terminal to the WAP portal server; the WAP portal server is used for acquiring the mobile phone number of the user terminal, generating a mobile token according to operator mobile phone binding relations and sending the mobile token and the transaction request to the WAP transaction server; the WAP transaction server is used for verifying validity of the mobile token and checking whether user operator binding information is consistent with token information; the mobile communication operator system equipment is used for providing an interface to the WAP portal server and the WAP portal server acquires the mobile phone number by communicating with the mobile communication operator system equipment. By adopting the invention, the user can be prevented from visiting the WAP mobile banking by the internet, thereby effectively improving security of visiting the mobile banking.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Memory space management and memory access control method and device
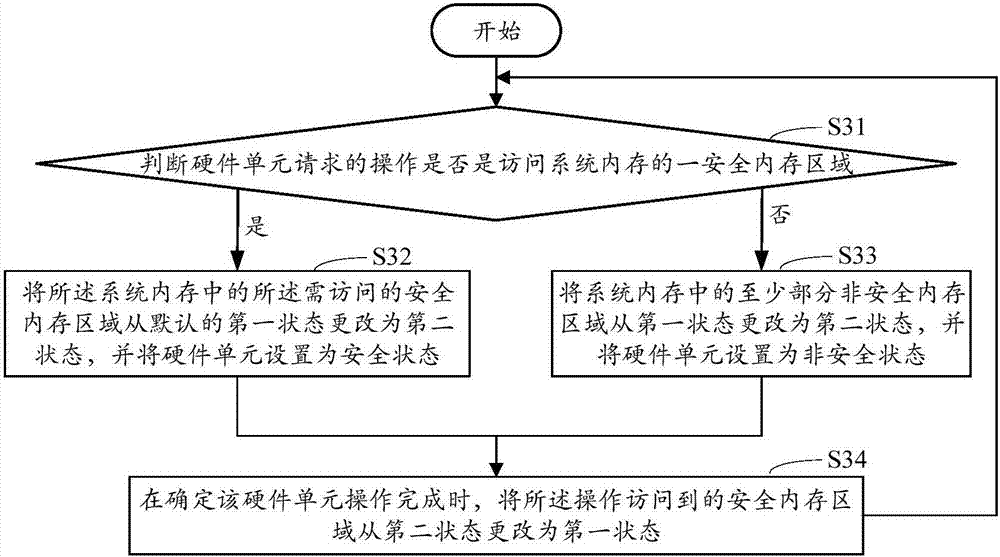
InactiveCN107220189AEnsure safetyAvoid visitingMemory architecture accessing/allocationUnauthorized memory use protectionSpace managementAccess control
The invention discloses a memory space management and memory access control method and device. The method comprises the steps that when access requests are received, access addresses and visitor identifiers in the access requests are obtained; current states of the memory space pointed by the access addresses are checked, and first check results are obtained, wherein the states of the memory space comprise a first state and a second state; searches are conducted to determine whether or not the visitor identifiers belong to an access permission collection corresponding to the checked results in multiple access-permitted collections; an instruction is generated according to the search results, wherein the instruction is used for allowing or not allowing a visitor to access the memory space. Through the above approach, the memory space management and memory access control method is capable of reducing waste of memory resources and reducing system costs.
Owner:MSTAR SEMICON INC
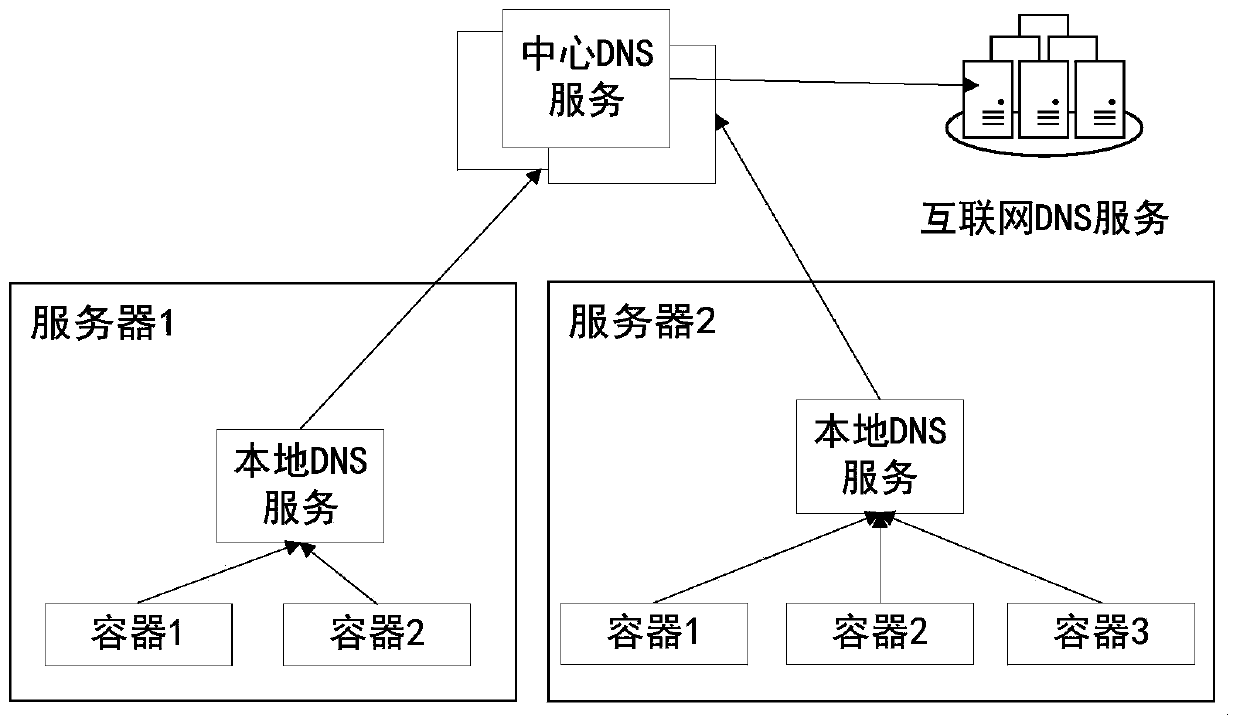
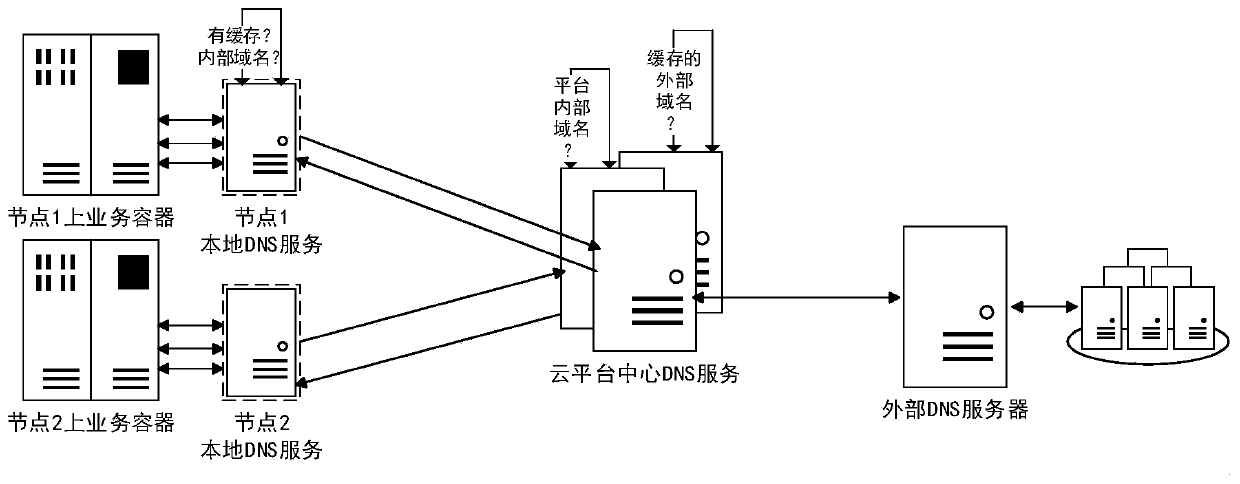
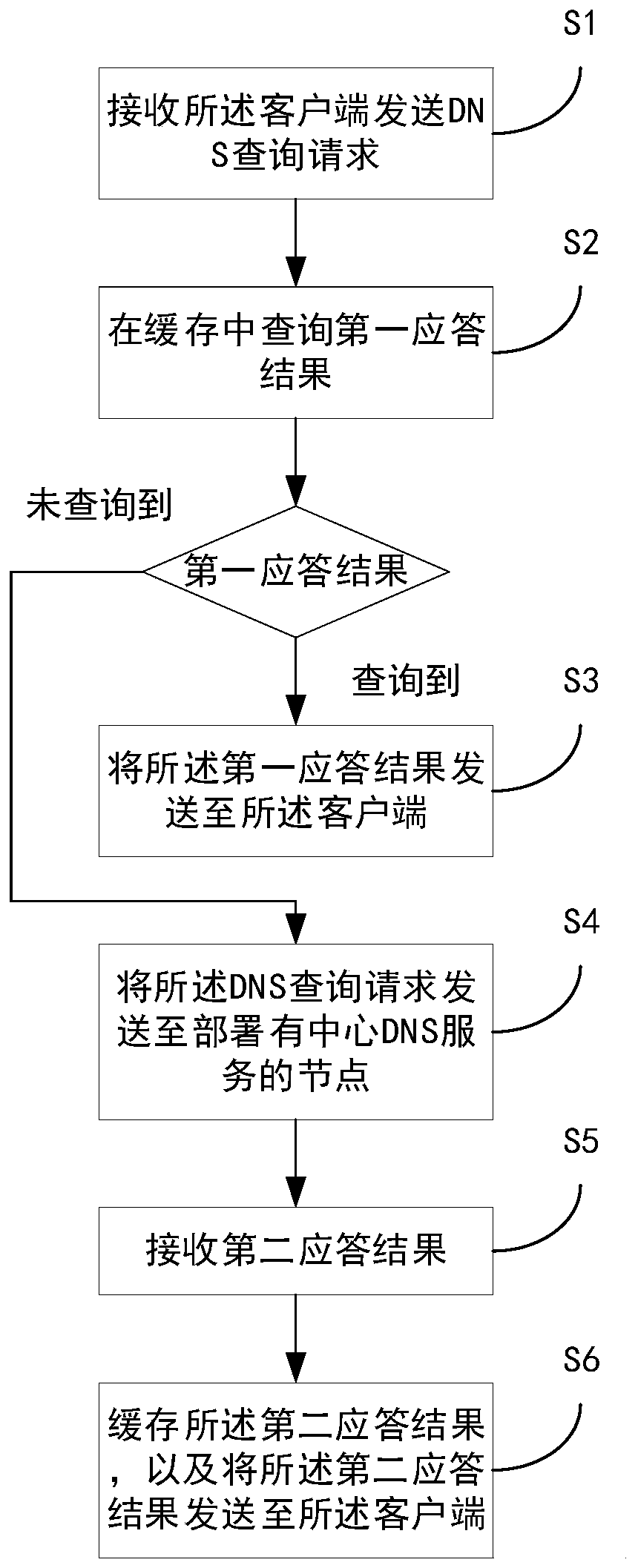
Distributed local DNS system and domain name query method
The invention provides a distributed local DNS system and a domain name query method. The system comprises a local DNS service and a central DNS service which are deployed on a plurality of nodes. Theserver nodes corresponding to the local DNS service can provide domain name resolution service for the containers on the respective nodes, query response results in the nodes cache after receiving DNS query requests, and the response results are directly returned to the client if the response results are queried; and if the response results are not queried, the central DNS service is queried, soas to obtain the IP address corresponding to the DNS query request through the central DNS service and send the IP address to the client, thereby reducing the dependence of each service on the cloud platform on the platform centralized DNS system. According to the invention, the local DNS service can be automatically configured and automatically switched when a fault occurs, so that the influenceof the fault of the DNS system on the service can be alleviated, and the situation that the upper layer service accesses the basic DNS service across servers can be avoided.
Owner:JUHAOKAN TECH CO LTD
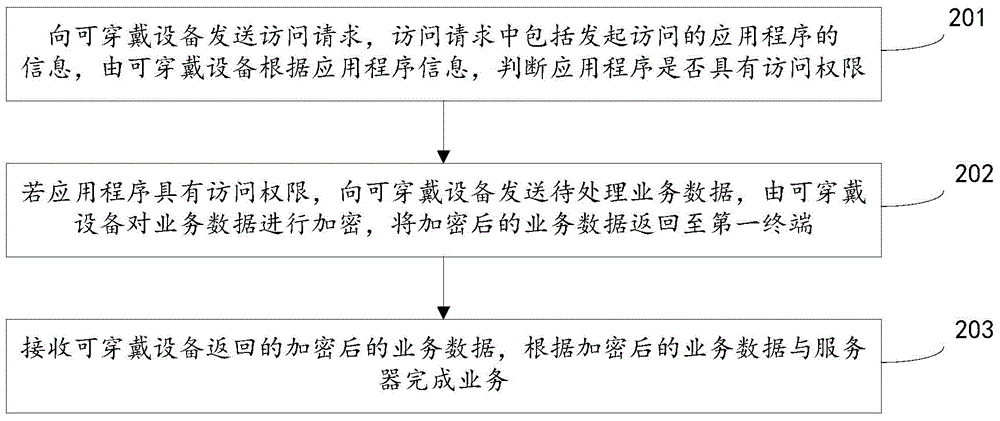
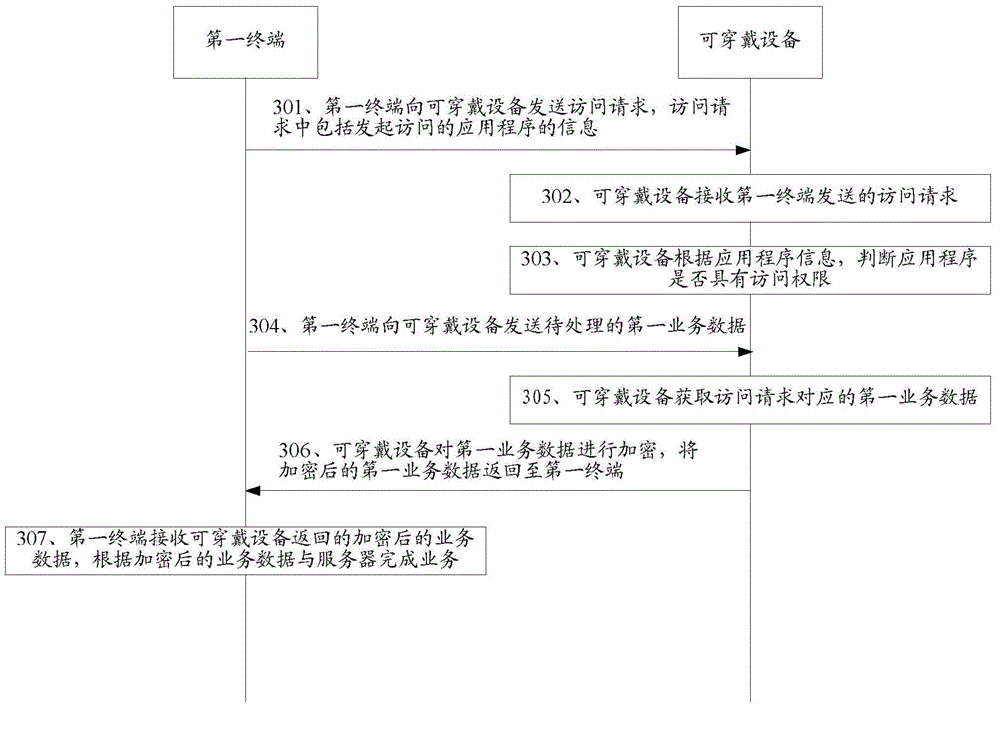
Business processing method and device and terminal
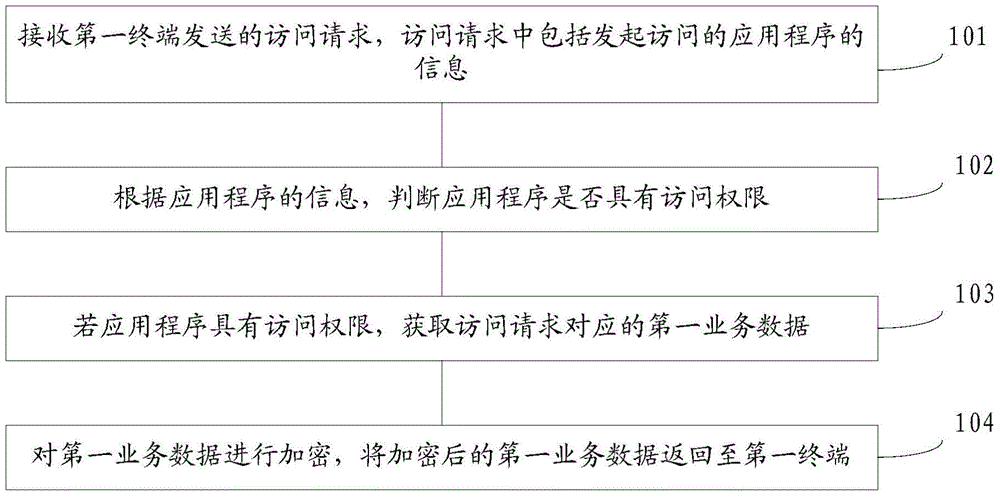
ActiveCN104618330AImprove securityAvoid visitingNear-field transmissionDigital data protectionBusiness dataComputer terminal
The invention relates to a business processing method and device and a terminal and belongs to the technical field of communication. The method comprises receiving an access requirement sent by a first terminal; determining whether an application program has an access right according to application program information; obtaining first business data corresponding to the access requirement if the application program has the access right; encrypting the first business data and returning the encrypted first business data to the first terminal. By means of the method, the device and the terminal, the first business data to be processed are encrypted, the encrypted first business data are returned to the first terminal, and the first terminal complete businesses with a server through the encrypted first business data; access of unauthorized applications can be prevented, so that the business processing security is high; besides, remote businesses between the server can be processed, so that the business processing flexibility is high, and the effect is good.
Owner:上海鸿米信息科技有限责任公司
Block chain service device, block chain service system and communication method thereof
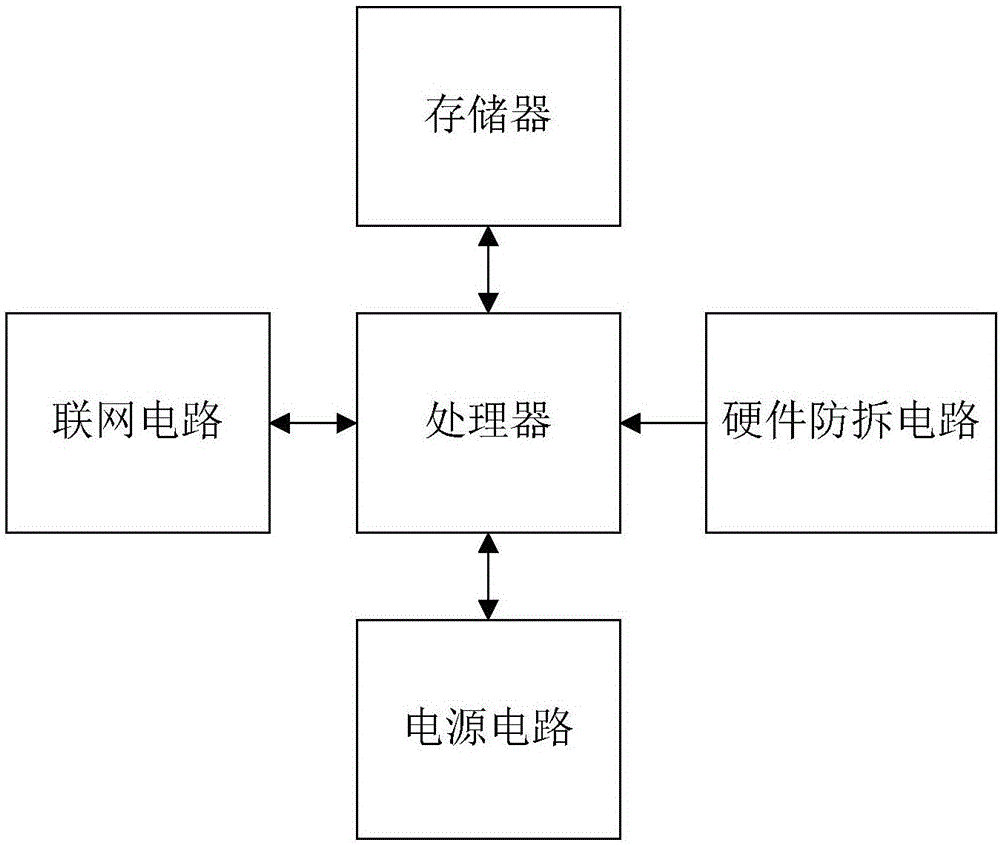
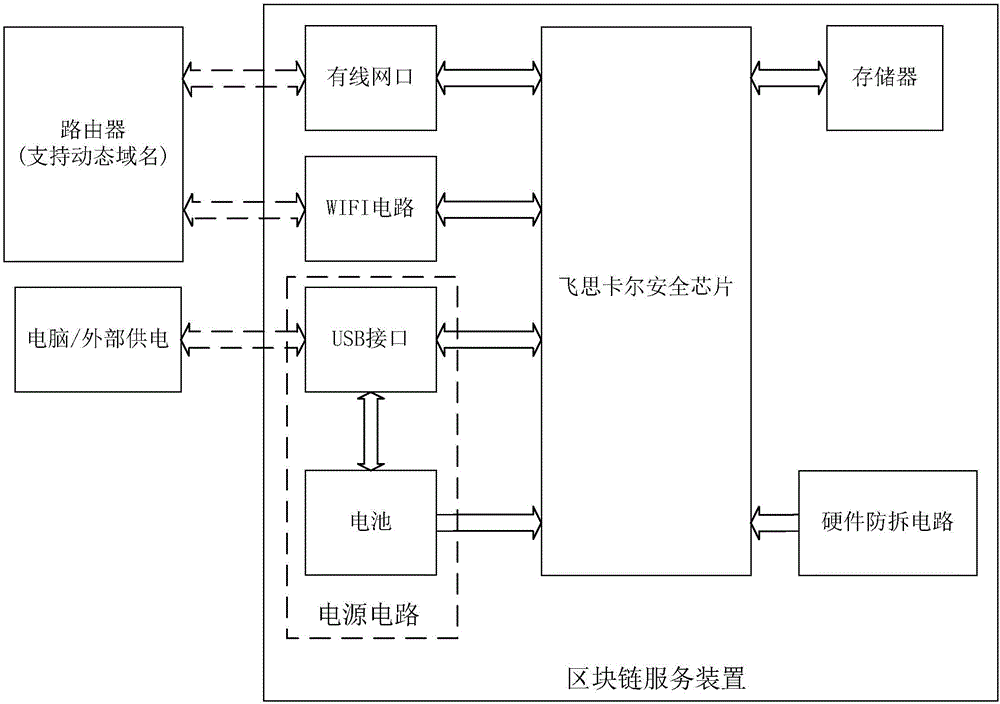
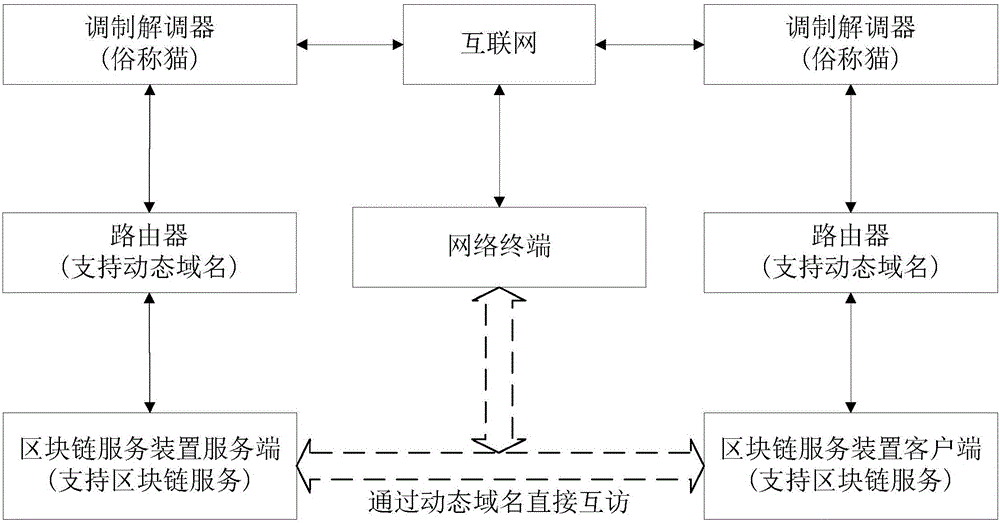
ActiveCN106789875AAvoid visitingEnsure safetyDigital data protectionTransmissionNetwork terminationComputer terminal
The invention discloses a block chain service device which comprises a processor, a networking circuit, a power supply circuit, a memory and a hardware dismounting prevention circuit. The invention further discloses a block chain service system, which comprises a plurality of network terminals and a plurality of block chain service devices, wherein at least one block chain service device acts as a block chain service device server, and at least one block chain service device acts as a block chain service device client. The invention also provides a communication method of the block chain service system. According to the invention, block chain data of the block chain service device is stored in the block chain service device, access can only be available through authorization, no delete interface is provided, the power consumption is small, and the block chain service device can operate for 24 hours. The block chain service system and the communication method thereof realize point-to-point block chain services by relying on the block chain service device and need not rely on a computer to act as an intermediary. The block chain service device, the block chain service system and the communication method thereof can be widely applied to the field of block chains.
Owner:SHENZHEN XINGUODU PAYMENT TECH CO LTD
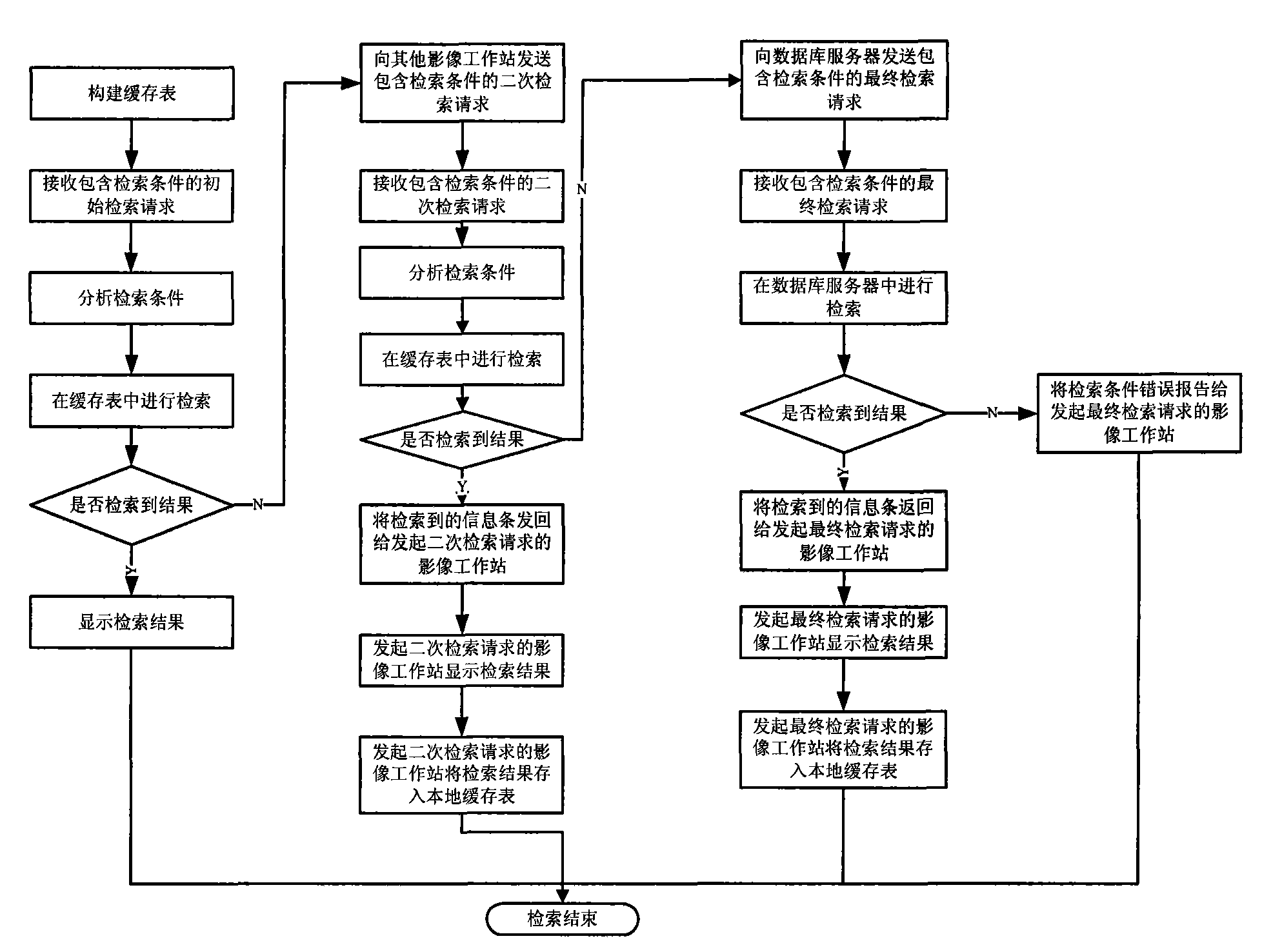
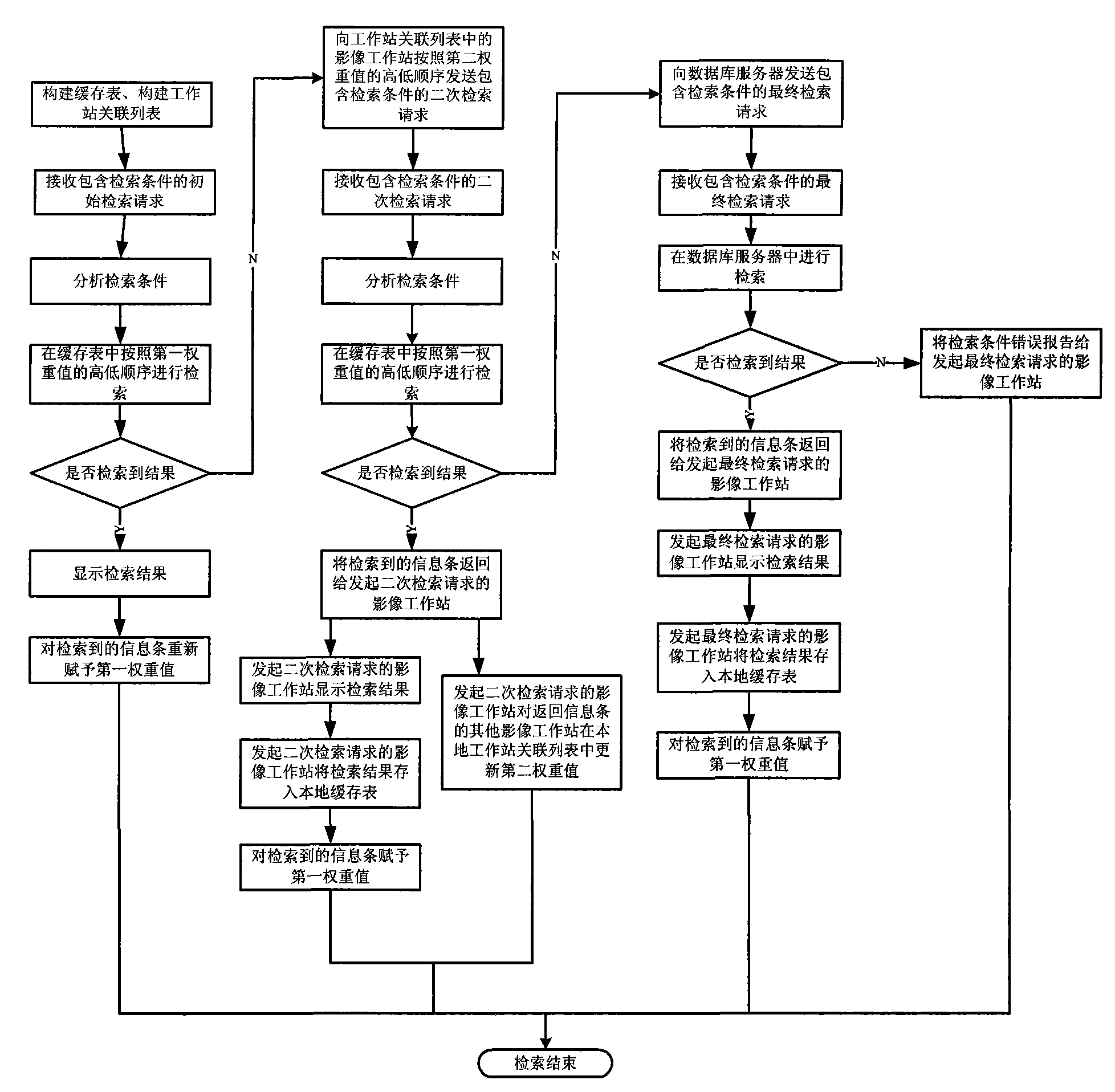
Caching technology based medical image database searching method and searching system
ActiveCN101604334AImprove retrieval speedAvoid visitingSpecial data processing applicationsImage databaseDatabase server
Aiming at the problems in the prior art that when searching image data in a PACS system having a plurality of data, especially searching simultaneously in a plurality of image workstation, workload of a database server is sharply raised, system speed is declined, and the overall cost is added, the invention provides a caching technology based medical image database searching method, which comprises: after receiving an initial searching request, searching firstly in a local caching list; sending final searching request to the database server if not searching it, transmitting it to a local image workstation if the database server searches it, reporting the searching result to the local image workstation if not searching it in the database server. By using the method, the image data searching speed is quickened, the workload of the database server is lightened, and the working efficiency of the PACS system is improved. The invention also provides a a caching technology based medical image database searching system, which is used for guaranteeing implementation and application of the method in actual system.
Owner:北京美智医疗科技有限公司
Identity authentication method and device
ActiveCN110417776AAvoid visitingAvoid issues such as leaksDigital data authenticationTransmissionAuthentication systemSystem safety
The invention discloses an identity authentication method and device. The method is applied to a server of an identity authentication system, and comprises the following steps: performing identity registration according to user identity information and equipment identity information in an identity registration request, equipment integrity information reflecting an equipment operation state and thelike, and binding equipment and a user through identity registration to generate an authentication certificate; when a system access request exists, authenticating identities of a user and equipmentand equipment operation state information and realizing multi-level identity authentication; further, formulating multi-level and multi-combination access control strategy through comprehensively authenticating the identity and the equipment state, thus the network system safety is effectively increased. In the identity authentication method, the user identity is authenticated based on the multi-factor technology, the equipment identity is authenticated based on trusted computing, and the equipment integrity is authenticated, so that a zero-trust identity authentication system is realized, andthe security of the network system is effectively improved.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
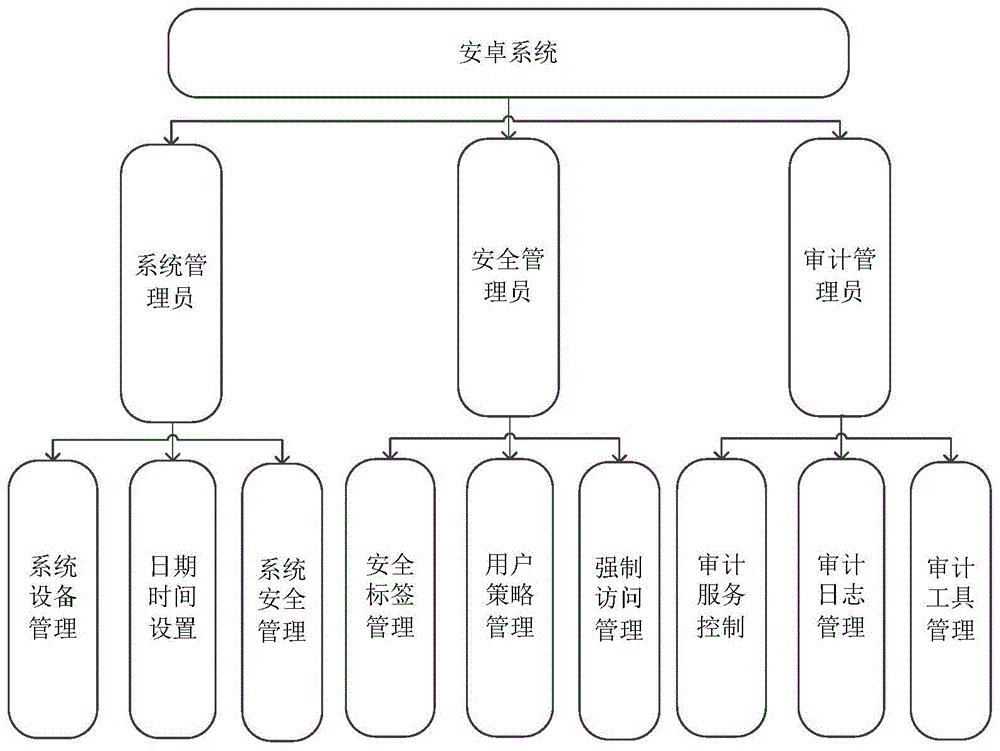
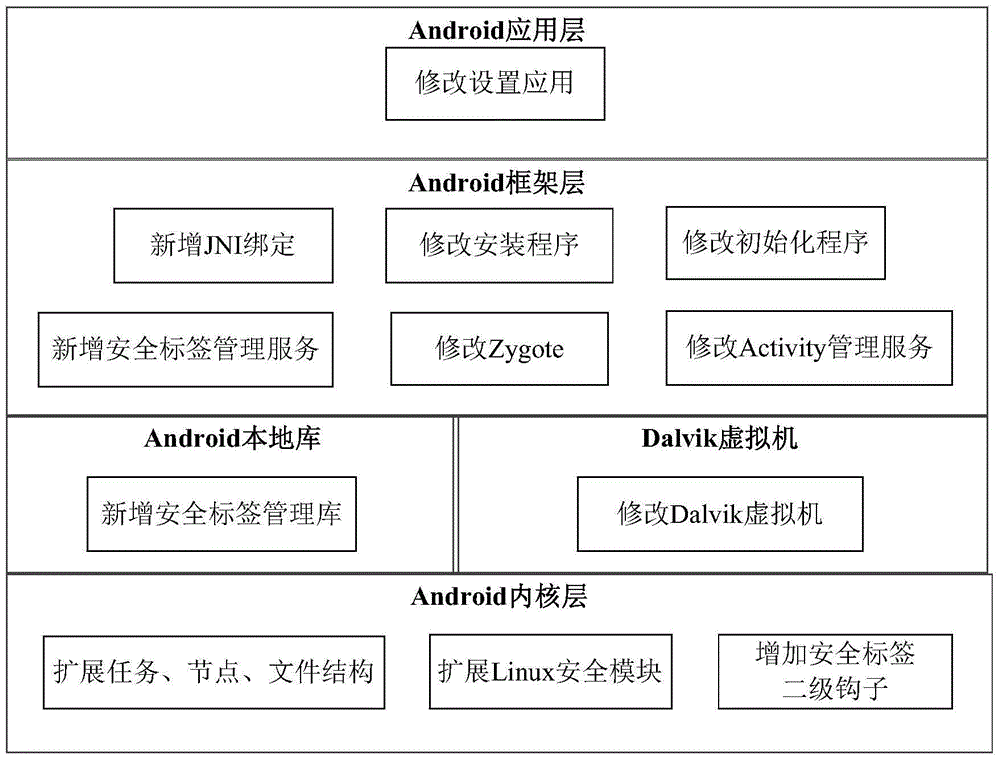
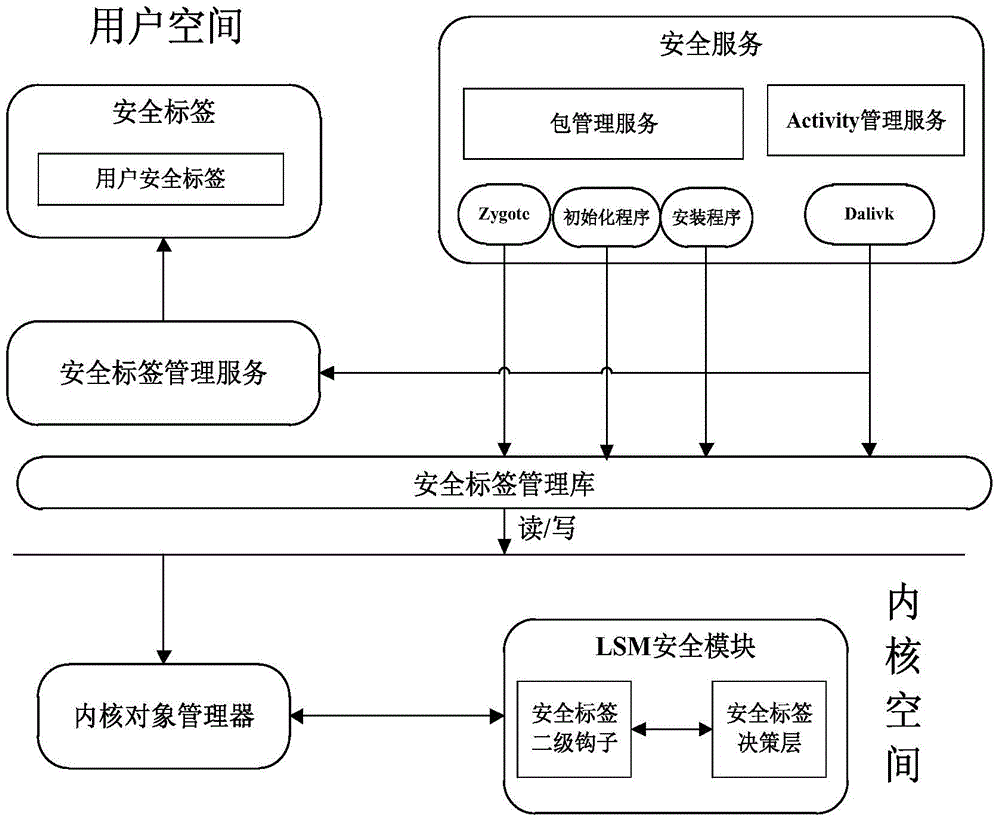
Resource access method of Android system
ActiveCN105046146AAvoid visitingImprove securityPlatform integrity maintainanceComputer securityDiscretionary access control
The invention discloses a resource access method of an Android system, and belongs to the technical field of a mobile system. The resource access method of the Android system aims at solving the technical problem that in the existing Android system, the security and the completeness of resources of a user can be threatened. The resource access method of the Android system comprises the following steps of: sequentially performing DAC (Discretionary Access Control) permission checking and MAC (Mandatory Access Control) permission checking on a resource accessing process; if the process passes the DAC permission checking and the MAC permission checking, obtaining a security label of the process and a security label of the resources; matching the security label of the process and the security label of the resources; and if the security label of the process and the security label of the resources are matched, allowing the process to access the resources.
Owner:CHINA STANDARD SOFTWARE
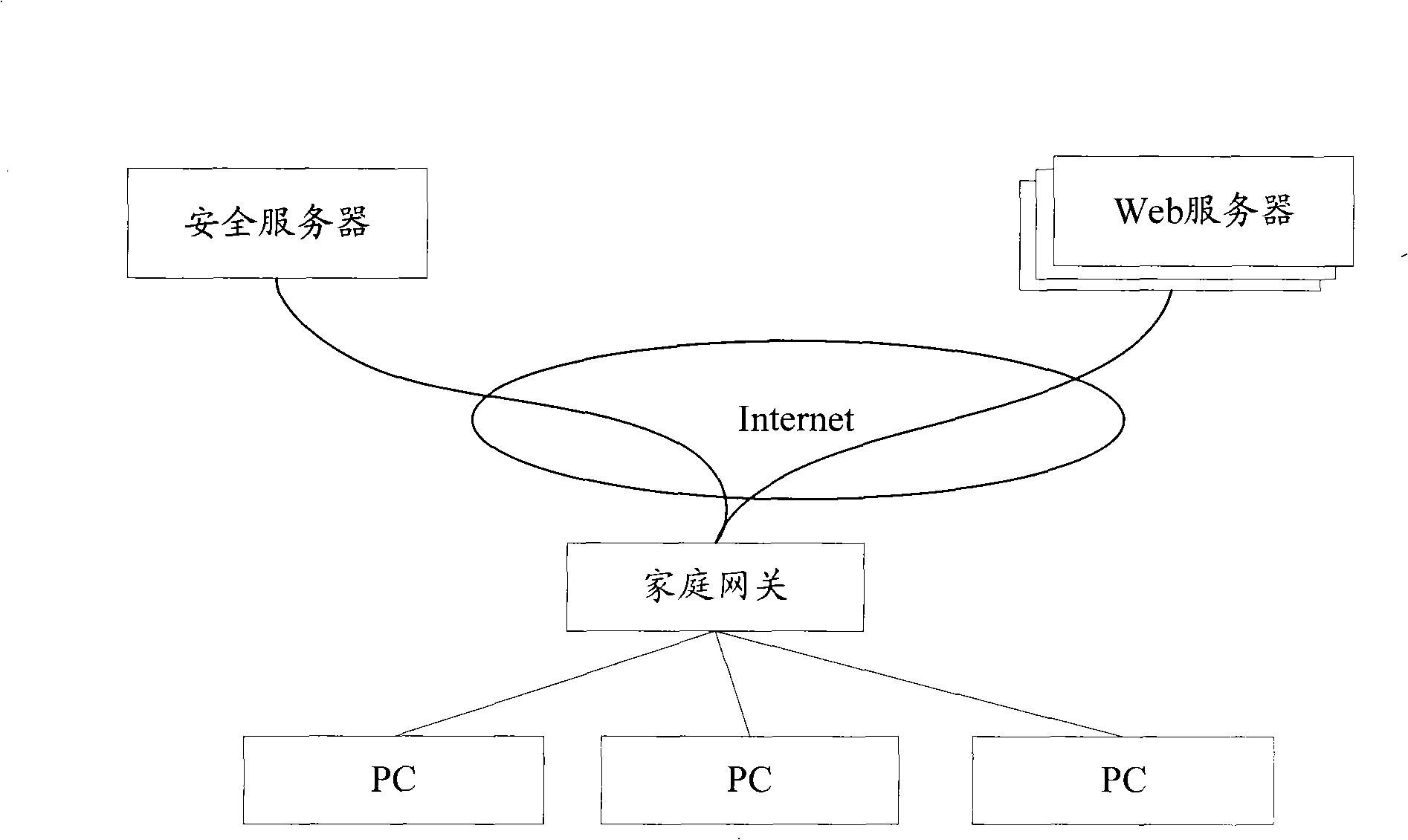
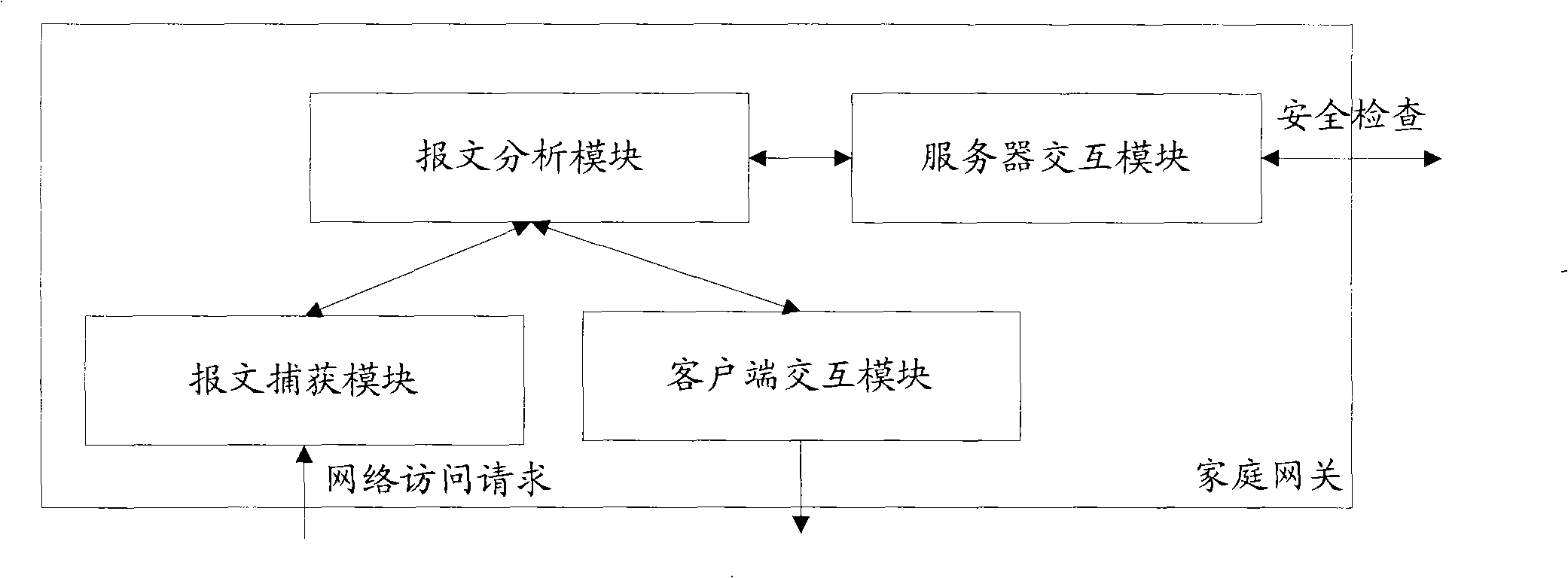
Anti-virus method on the basis of household gateway and device thereof
The invention discloses an anti-virus method based on household gateway and a device thereof, which are used for solving technical problems, such as high requirements, complex installation and configuration and the like, of single-machine virus and anti-attack software. The invention employs resource of household gateway and uses a method which captures key information of contents accessed by users and inquires a security server, so as to prevent users from accessing network stations with viruses and hostile attacks, thereby improving safety of household network. The anti-virus method also avoids problems caused by direct installation of a firewall software on a user PC.
Owner:ZTE CORP
Method, device, client and server for detecting malicious APK
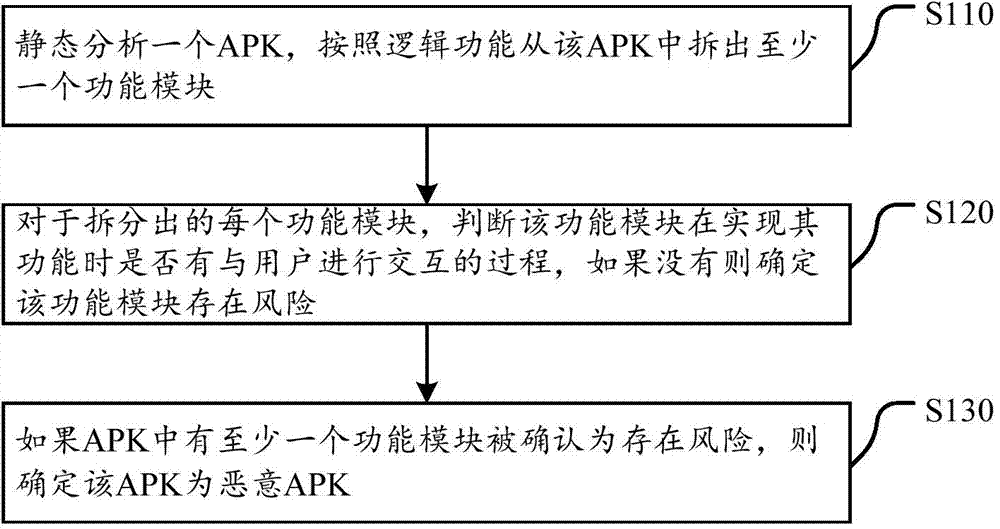
ActiveCN104517054AImprove experiencePrevent peepingPlatform integrity maintainanceFunctional moduleStatic analysis
The invention discloses a method, a device, a client and a server for detecting a malicious APK. The method comprises the following steps: statically analyzing one APK; disassembling at least one functional module from the APK according to a logic function; with regard to the functional module, judging whether the functional module has a process of interacting with a user or not when realizing the function; if not, determining that the functional module has risks; and if so, determining that at least one functional module in the APK has risks, namely determining the APK to be the malicious APK. The operation rule is carried out based on the malicious APK under the condition that a user does not know the condition, and whether each functional module of the APK is interacted with the user or not is judged so as to determine the safety grade of the APK. The method, which can be used for heuristically and directly detecting the malicious APK, is provided, and the detection of the unknown APK can be realized.
Owner:三六零数字安全科技集团有限公司
Safety access method and system based on fire wall policy
ActiveCN103561002AAvoid configuration problems and dangersReduce manual operationData switching networksSecurity policyEngineering
The invention discloses a safety access method and system based on a fire wall policy, and relates to the technical field of computer information security. According to the safety access method and system, configuration problems and dangerousness of the fire wall policy because of habits or unexpected errors of managers can be avoided through the dynamic open configuration according to needs. Furthermore, after equipment is accessed according to needs, a fire wall can close service access states according to fire wall poly instructions, and therefore the equipment can be effectively protected against external accesses and invasions which do not accord with service protocols. Through the dynamic starting-stopping configuration of the fire wall policy, the service protocols of the fire wall are started and stopped, manual operation of the managers is reduced, and therefore losses caused by operation errors can be avoided. A one-to-one safe configuration method between the fire wall safety policy and the equipment is achieved according to network safety check each time, access needs can form an access period, a safe closed ring from access needs to access to access stop is formed, and therefore the target equipment can be effectively protected against network threats in real time.
Owner:ULTRAPOWER SOFTWARE
Method of checking the performance of a flow cytometer instrument and apparatus for executing said method as well as a standard kit therefore
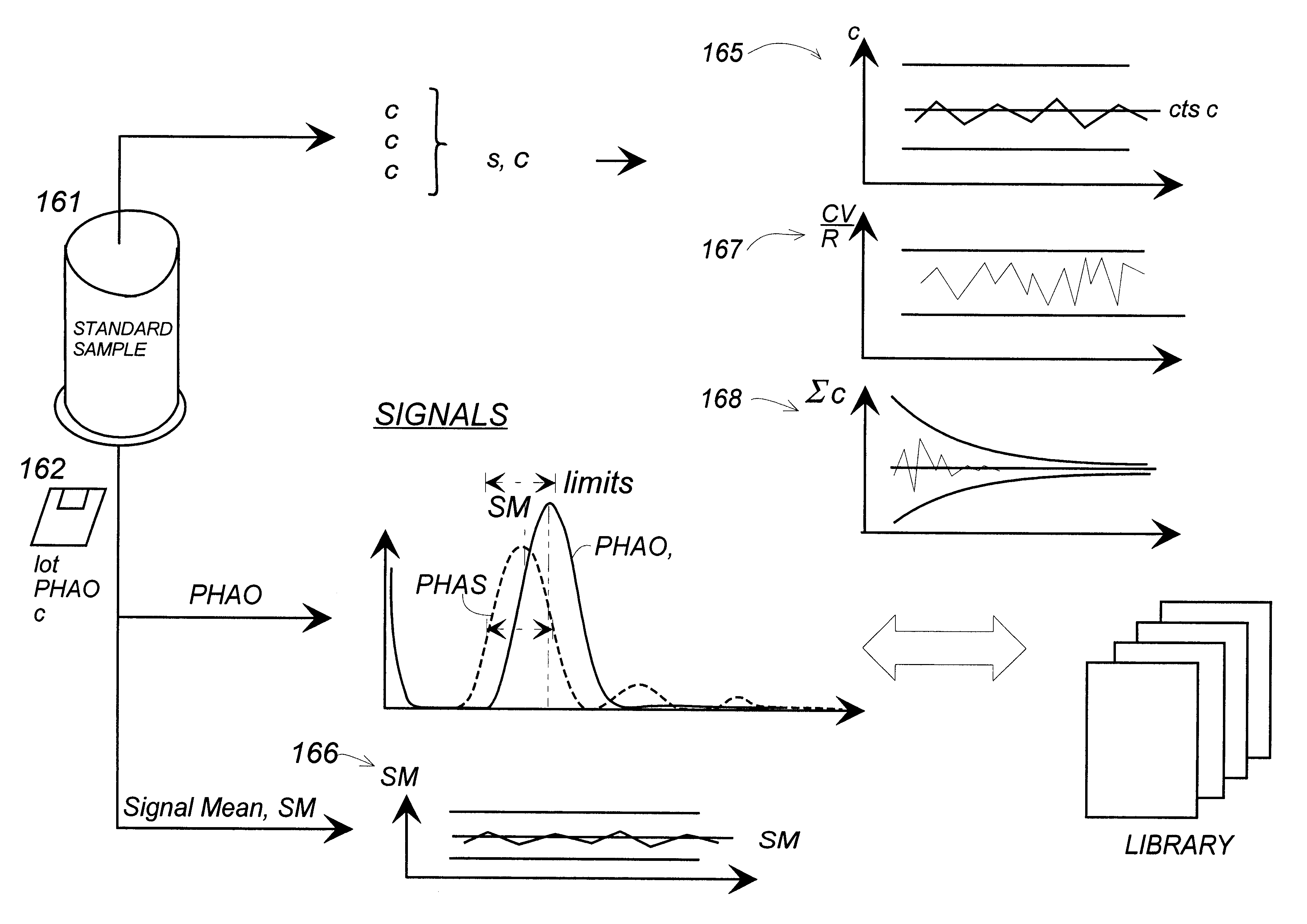
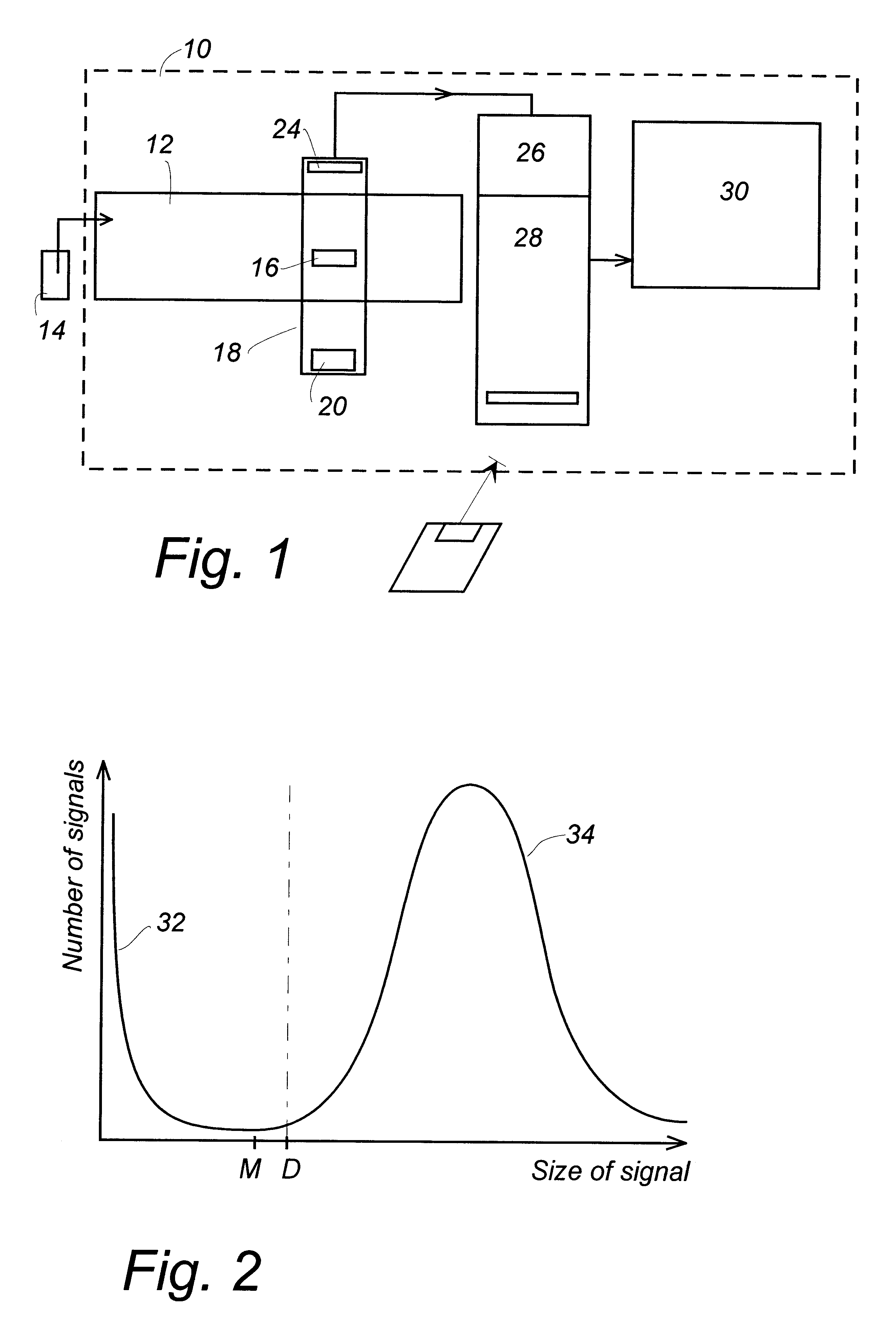
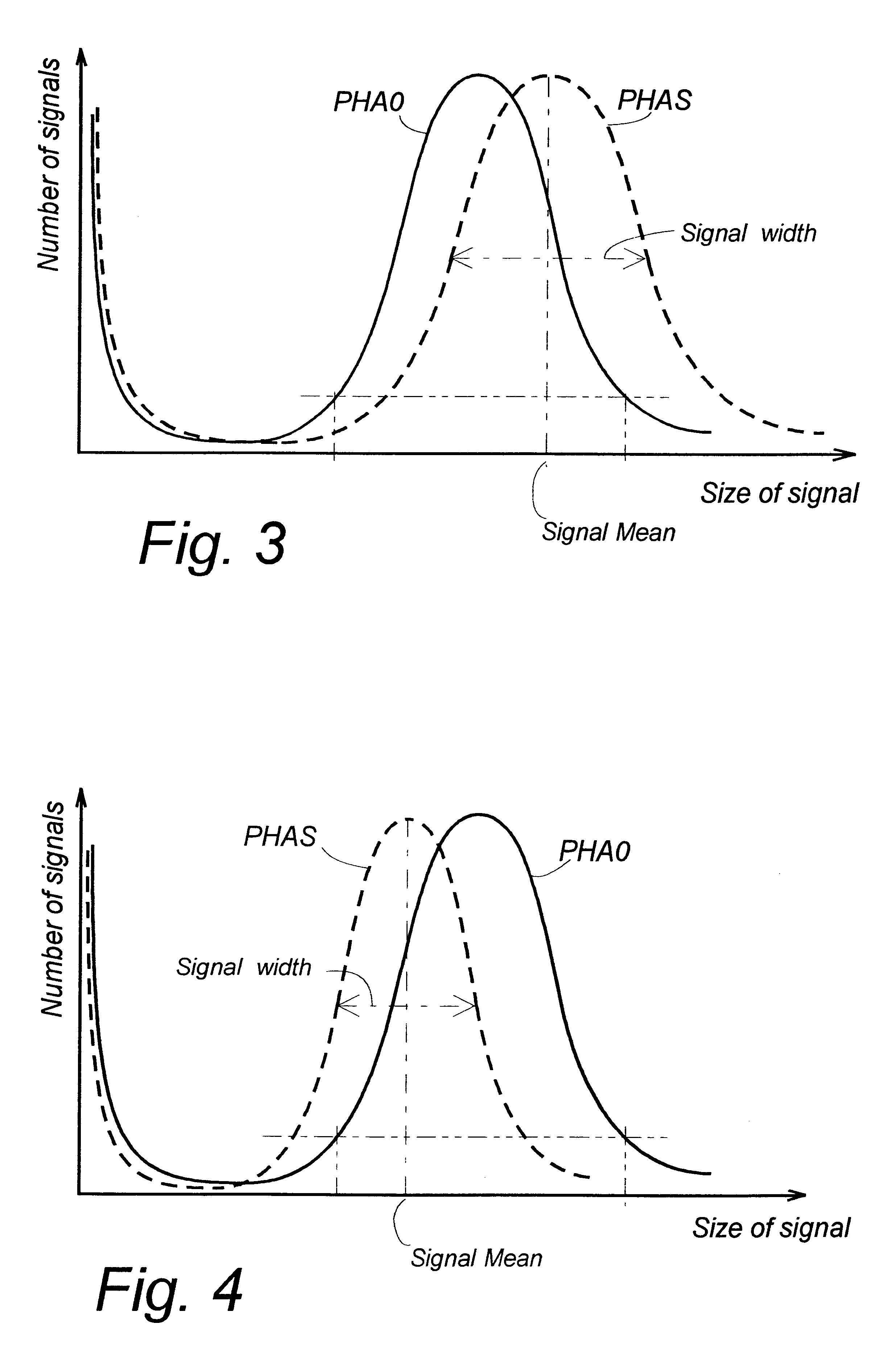
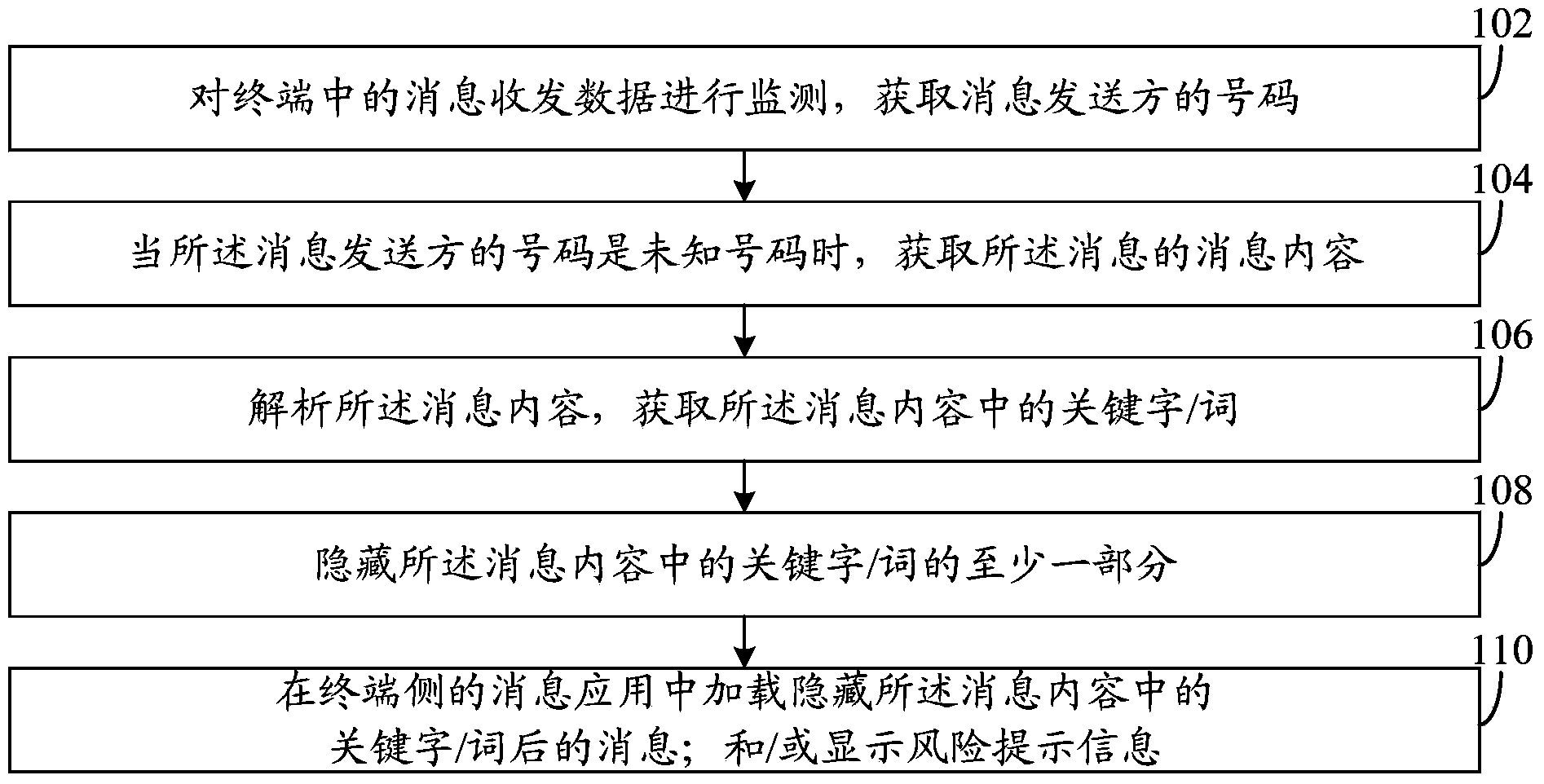
InactiveUS6542833B1Easily informedEasy to useVolume/mass flow measurementIndividual particle analysisStandard samplesSignal Width
A method for correcting the settings of a flow cytometer, designed for fast sample handling and counting, allowing about 500 samples per hour to be counted. The counting is based on the provision of data representing a PHA diagram (Pulse Height Analysis) of registered pulses, each indicating a passed cell or particle. To check the settings the user measures a standard sample of uniform microbeads 161 on the flow cytometer, and inserts information on a disk 162 in a computer arranged to process the measured data and to calculate: a plurality of particle counts on the same sample, a mean count, a standard deviation s and / or Coefficient of Variation CV, a signal mean value SM, a signal width (width of the bell-curve in the PHA-diagram). The parameters are compared to pre-set limits (165, 166, 167, 168) and the PHAS curve is compared to an ideal curve PHA0. A user help program for adjusting the flow cytometer is arranged to display typical symptoms on a computer screen, to indicate the possible defects and to recommend actions to remedy the problems, based on information in a library stored in the computer. Thereby a visit by a service engineer can often be avoided.
Owner:FOSS ELECTRIC
Message processing method and system
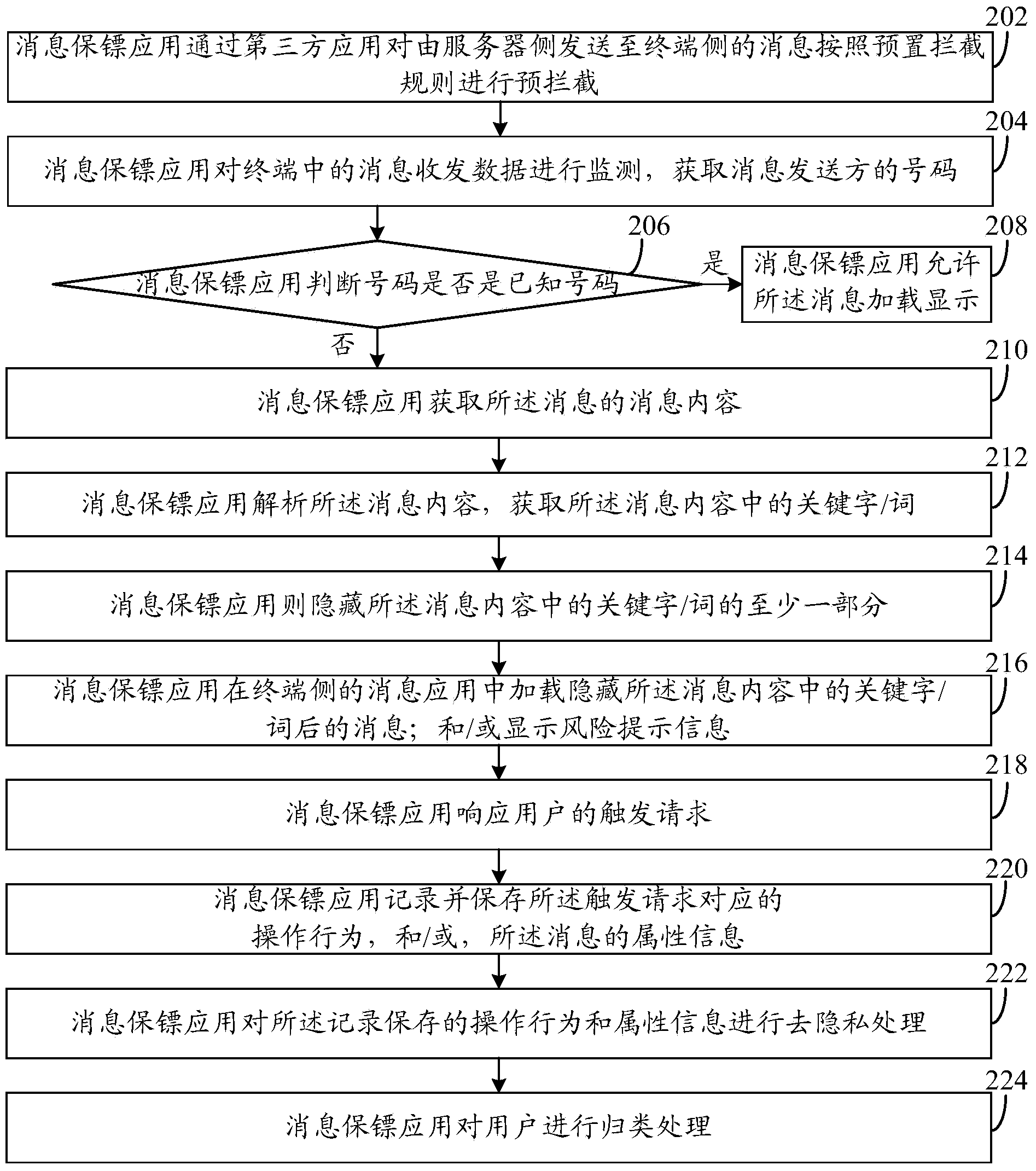
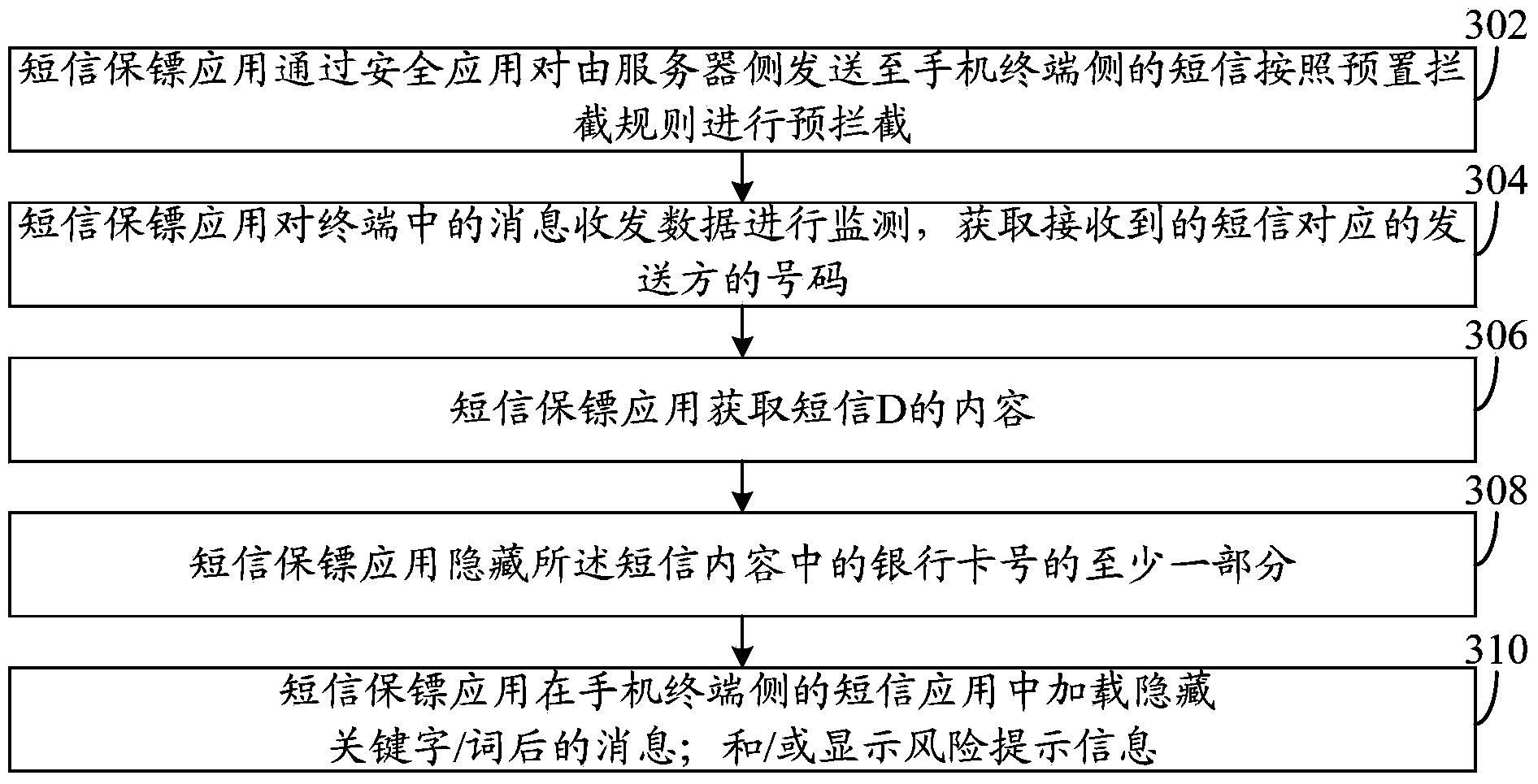
InactiveCN104079475AAvoid direct manipulationAvoid human judgmentMessaging/mailboxes/announcementsData switching networksComputer terminalMessage processing
The invention discloses a message processing method and system. The method includes the steps that message receiving and sending data in a terminal are monitored, and the number of a message sender is acquired; when the number of the message sender is an unknown number, the content of a message is acquired; the content of the message is analyzed, and keywords in the content of the message are acquired; if the keywords in the content of the message meet a preset interception policy, at least part of the keywords in the content of the message are concealed; the message with the concealed keywords in the content of the message is loaded into message application on the side of the terminal, and / or risk prompt information is displayed. Through the message processing method and system, the problems about how to improve accuracy of information judgment and prevent a user from having access to false and fraud information are solved.
Owner:BEIJING QIHOO TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com