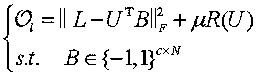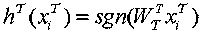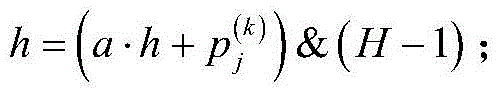Patents
Literature
309results about How to "Reduce memory overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
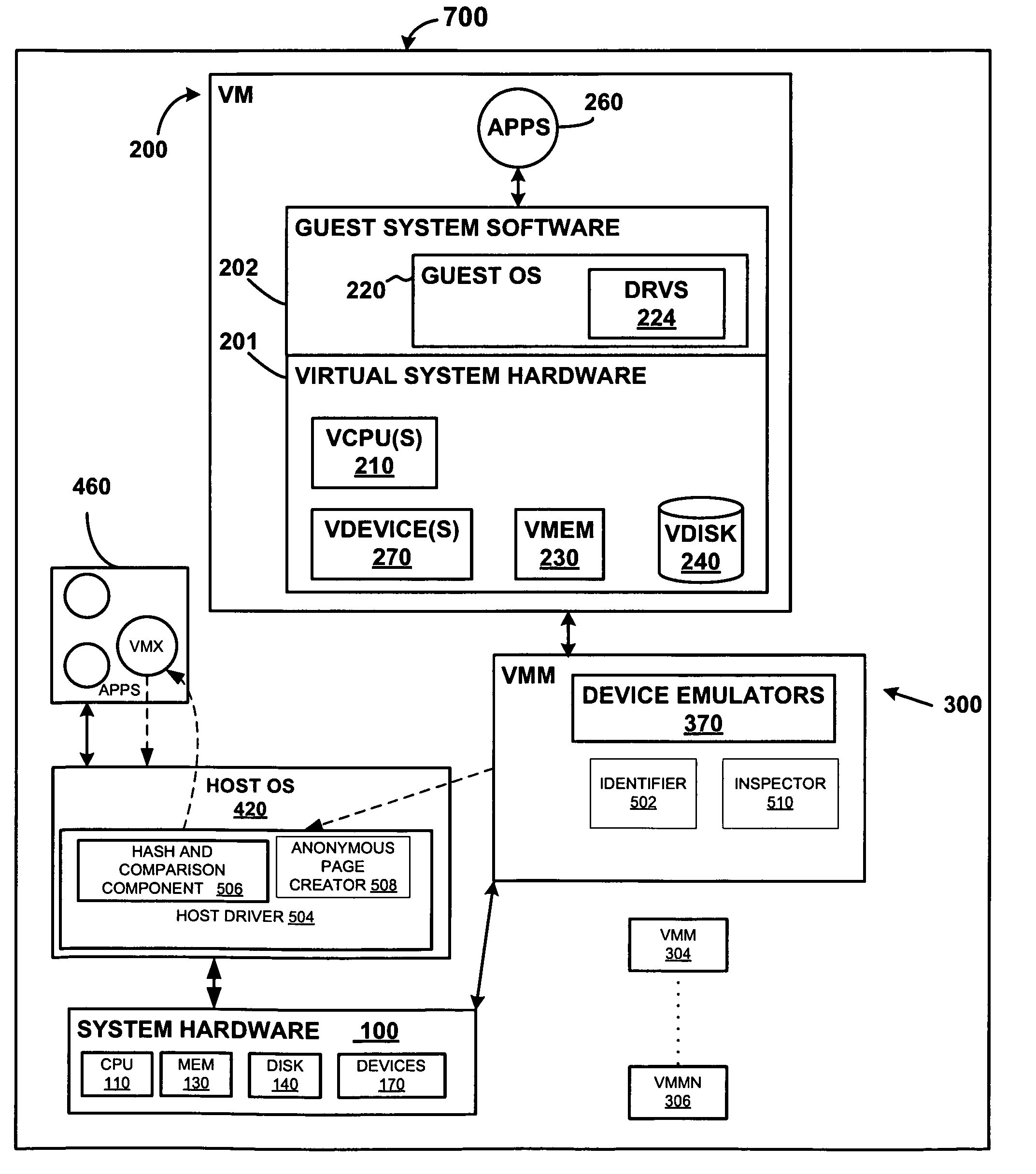
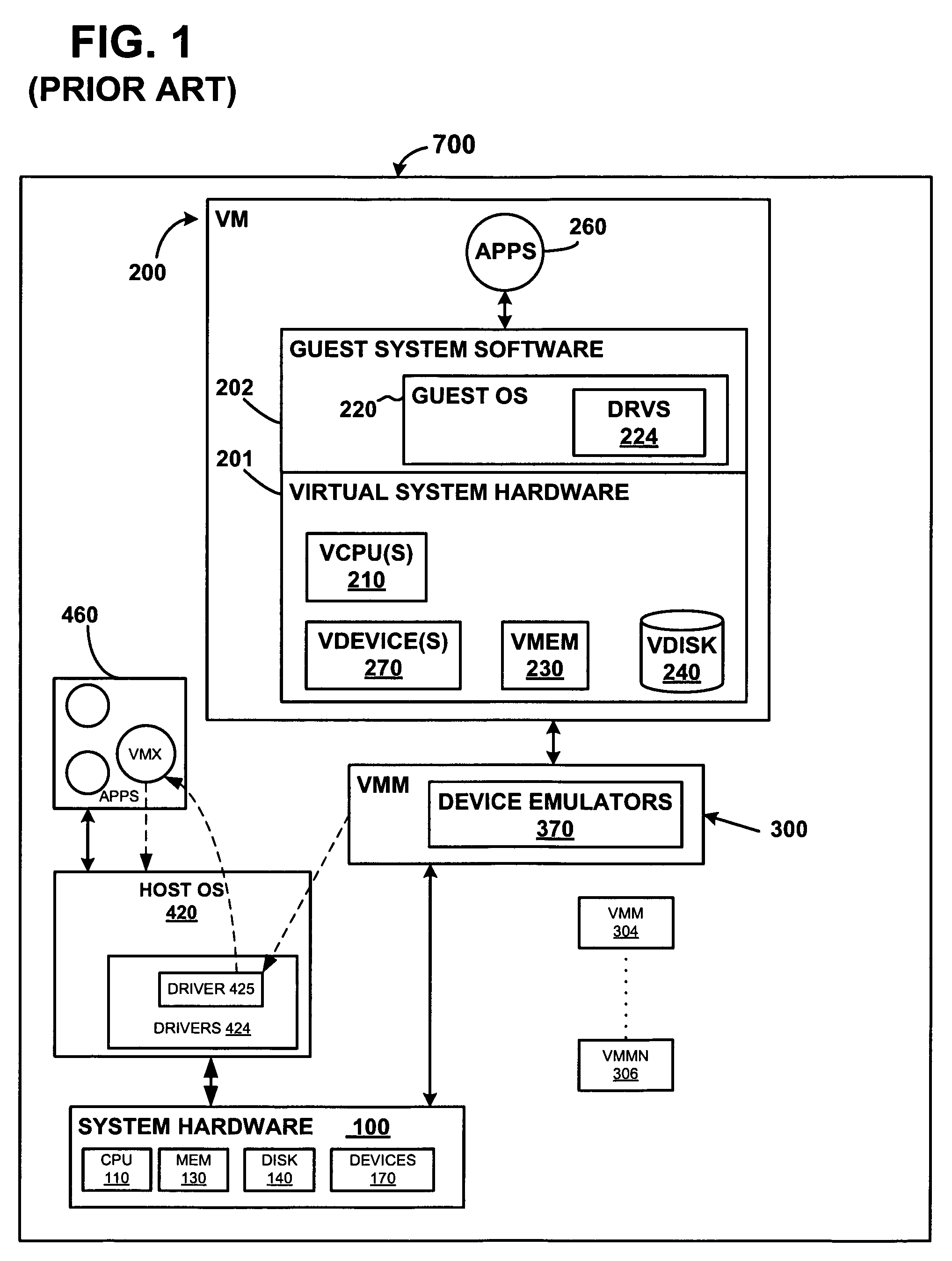
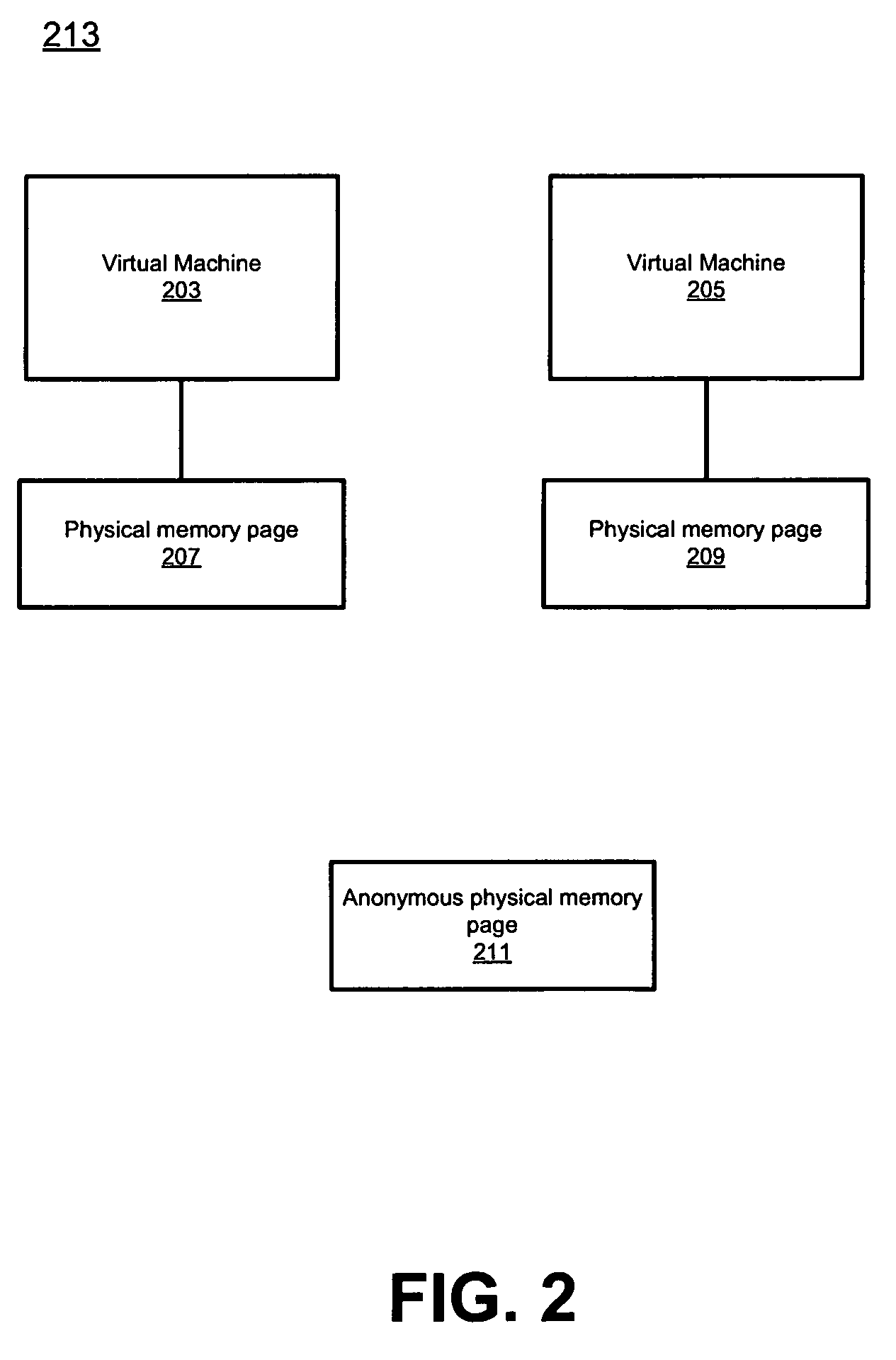
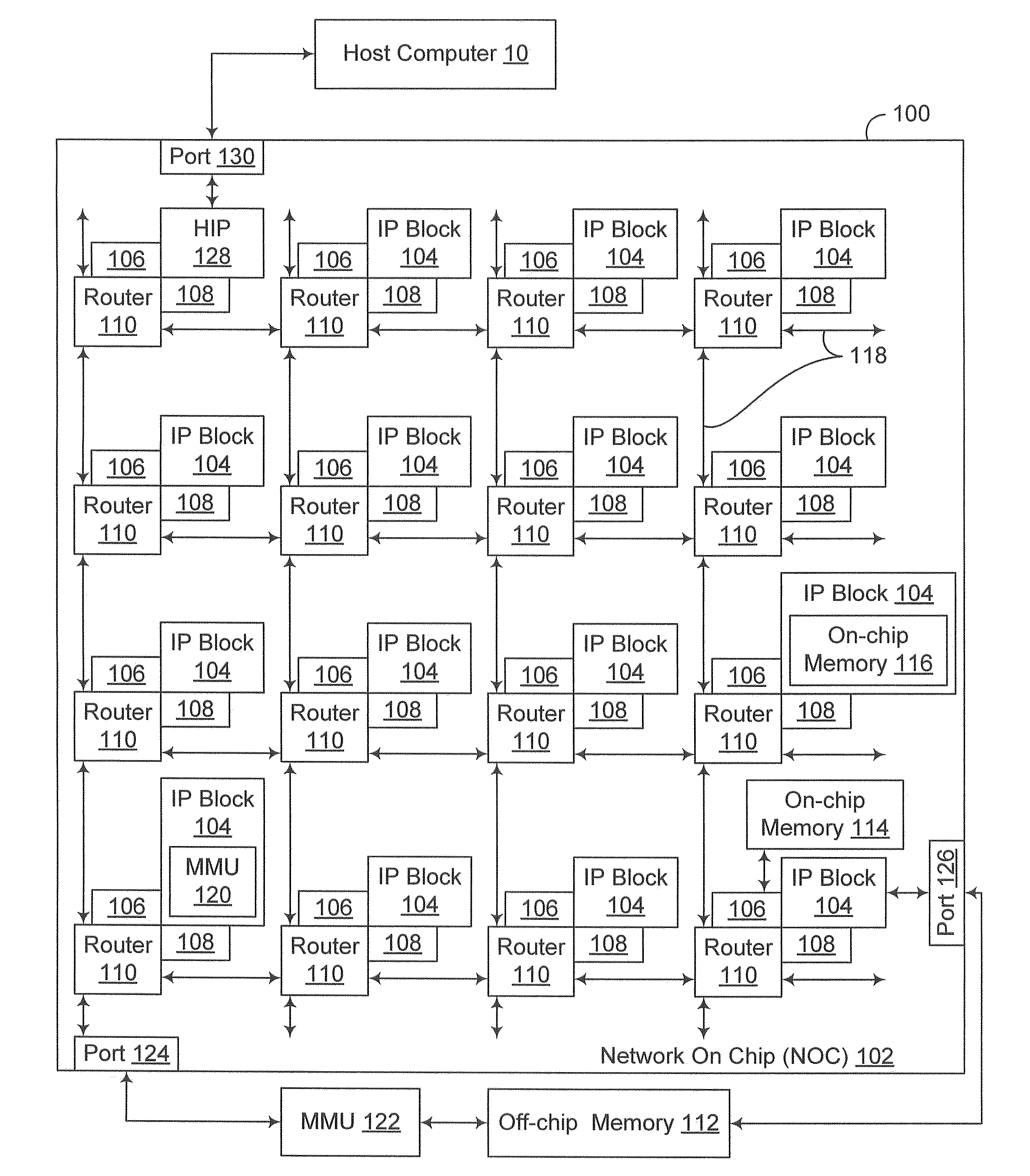
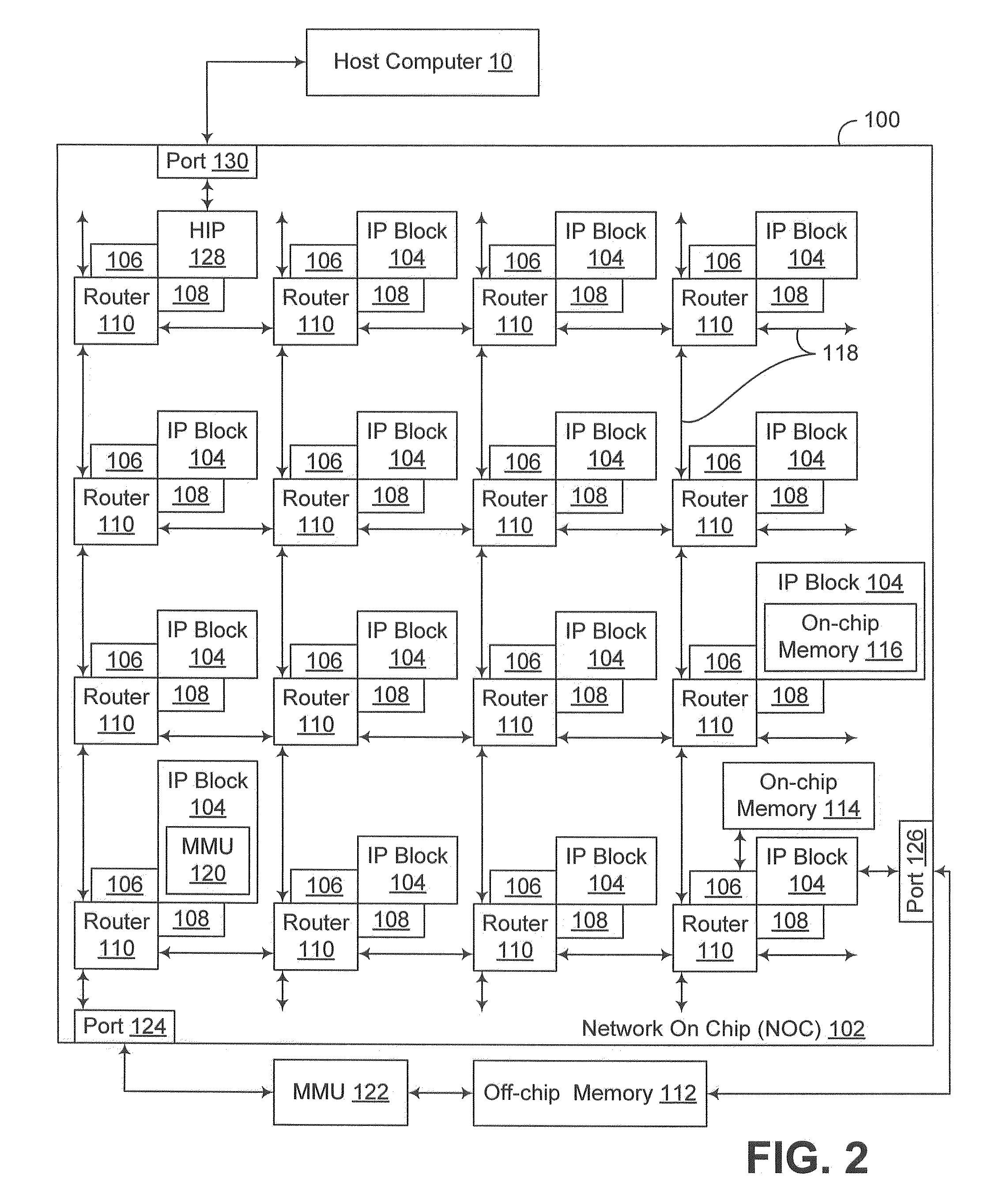
Transparent page sharing on commodity operating systems
ActiveUS7500048B1Reduce memory overheadMemory architecture accessing/allocationComputer security arrangementsOperational systemShared memory
Owner:VMWARE INC
Data de-duplication method based on combination of similarity and locality
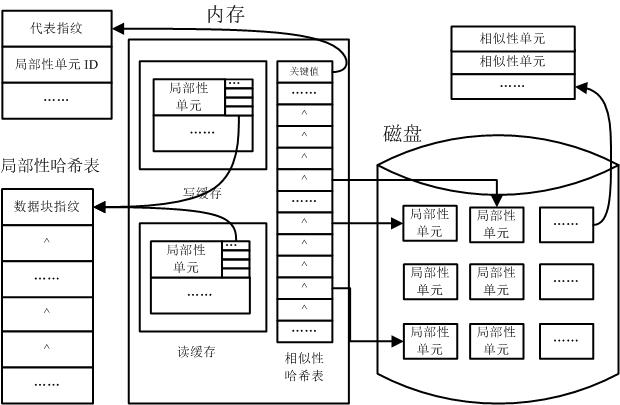
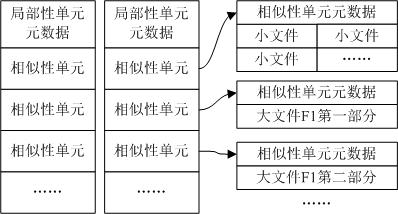
ActiveCN102222085AAvoid putting inReduce memory overheadSpecial data processing applicationsData streamData mining
The invention provides a data de-duplication method for combining the similarity and the locality of data, with less system memory expense and high data de-duplication efficiency. The method comprises the steps of: firstly partitioning and grouping files in a data stream, determining a similarity unit and a representative fingerprint of every data group, and storing the representative fingerprint in a memory; and traversing all the data groups and performing a similarity determination to determine which data in data groups are completely duplicate data and which data in data groups have non-duplicate data. If the non-duplicate data exists in the data groups, the locality determination can be continued to further determine which data in the data groups is the duplicate data. According to the method, the representative fingerprint is only stored in the memory, thus the memory expense is greatly reduced; supplement can be performed after the similarity determination by mining the locality of the data stream and caching the locality of the data stream in the memory, thus more duplicate data can be found, and simultaneously, frequent access to a disk index can be avoided and the utilization rate of the memory can be enhanced.
Owner:HUAZHONG UNIV OF SCI & TECH
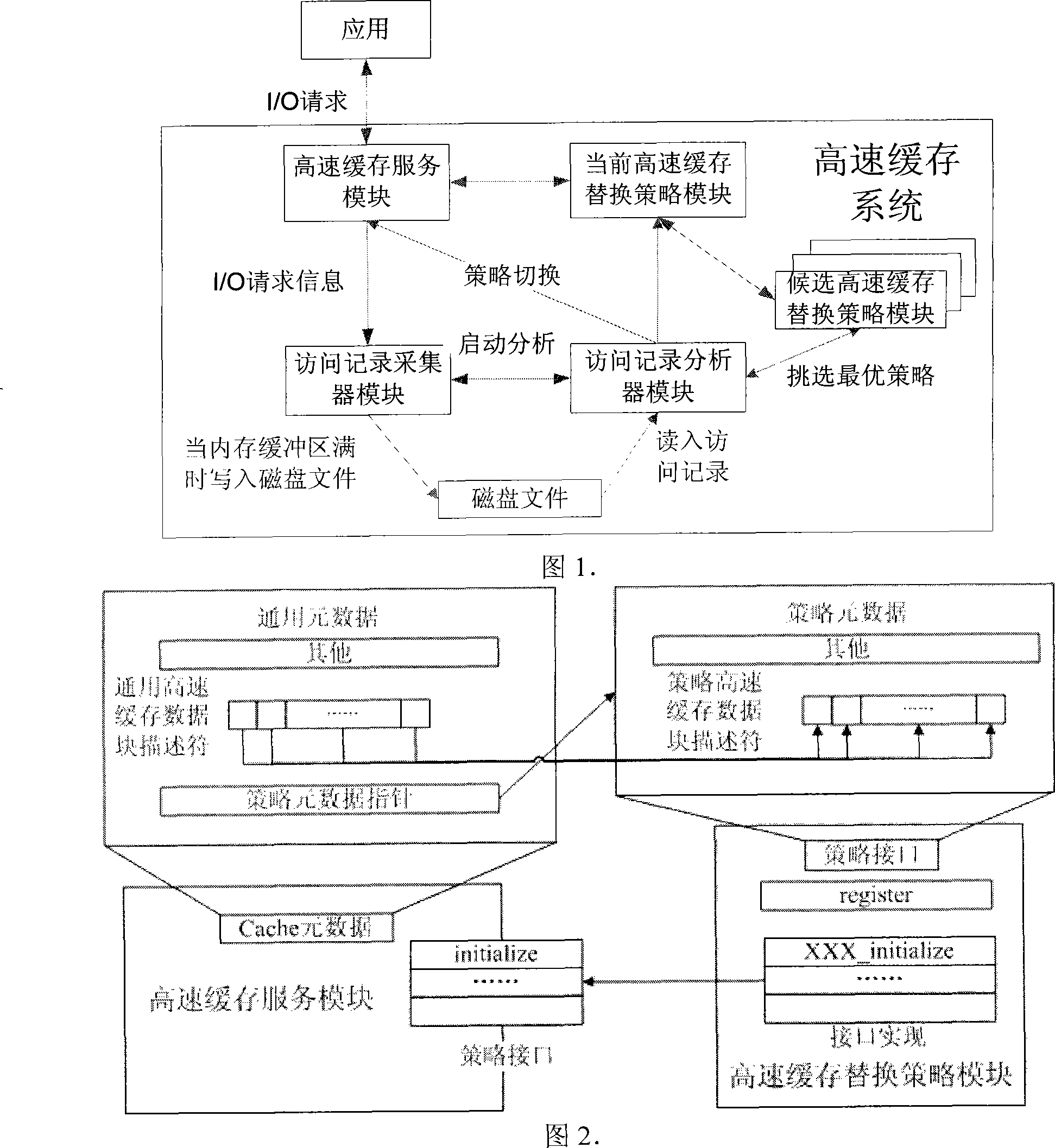
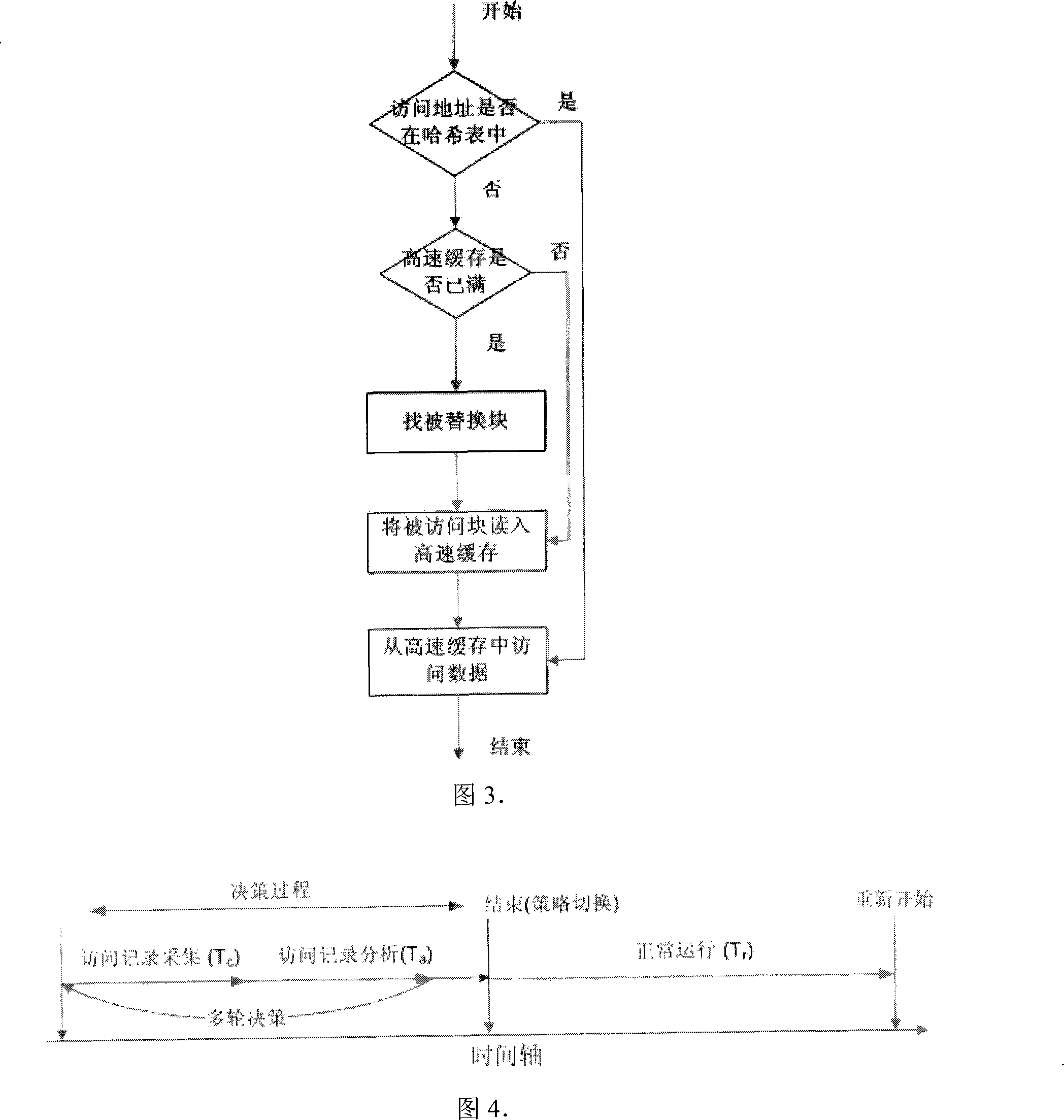
High speed cache replacement policy dynamic selection method
InactiveCN101236530AReduce CPU and memory overheadLower average response timeMemory adressing/allocation/relocationModularityDecision-making
The invention relates to a dynamic selection method for cache replacement policies, belonging to the memory system cache filed. The invention is characterized in that: the cache replacement policies are modularized through uniform interfaces, thereby online switching can be performed on any two cache replacement policies and novel cache replacement policies can be disposed; assess, record, acquisition and analysis are performed asynchronously, thereby CPU and memory overheads are small and affection on application is small; accurate decision-making results can be obtained as soon as possible through multi-run of policy selection, thereby not only the results are guaranteed to be brought into use quickly but also method overheads are reduced as much as possible.
Owner:TSINGHUA UNIV
Method and system for caching address translations from multiple address spaces in virtual machines
InactiveUS7363463B2Low costEfficient detectionMemory architecture accessing/allocationMemory systemsVirtualizationPage table
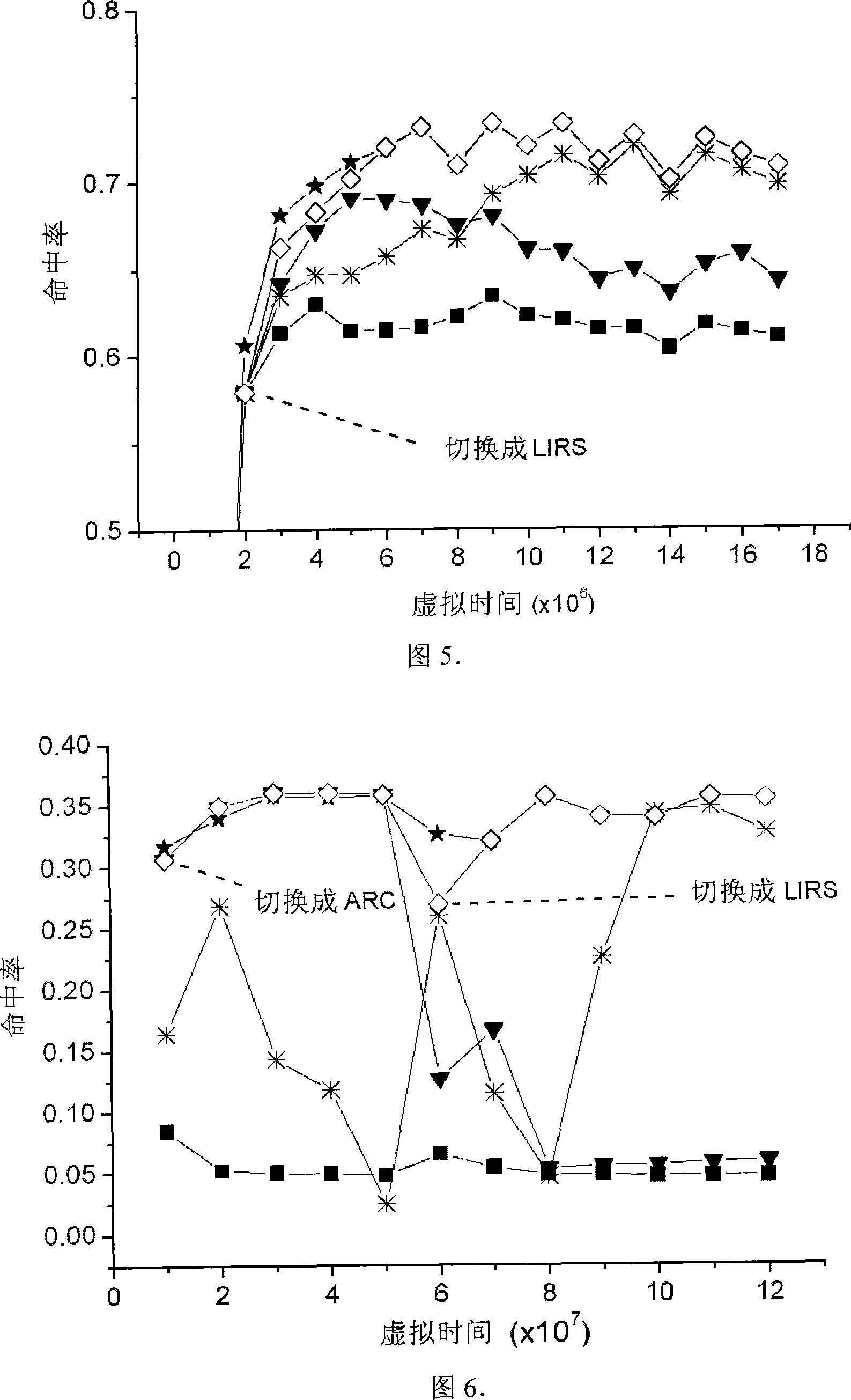
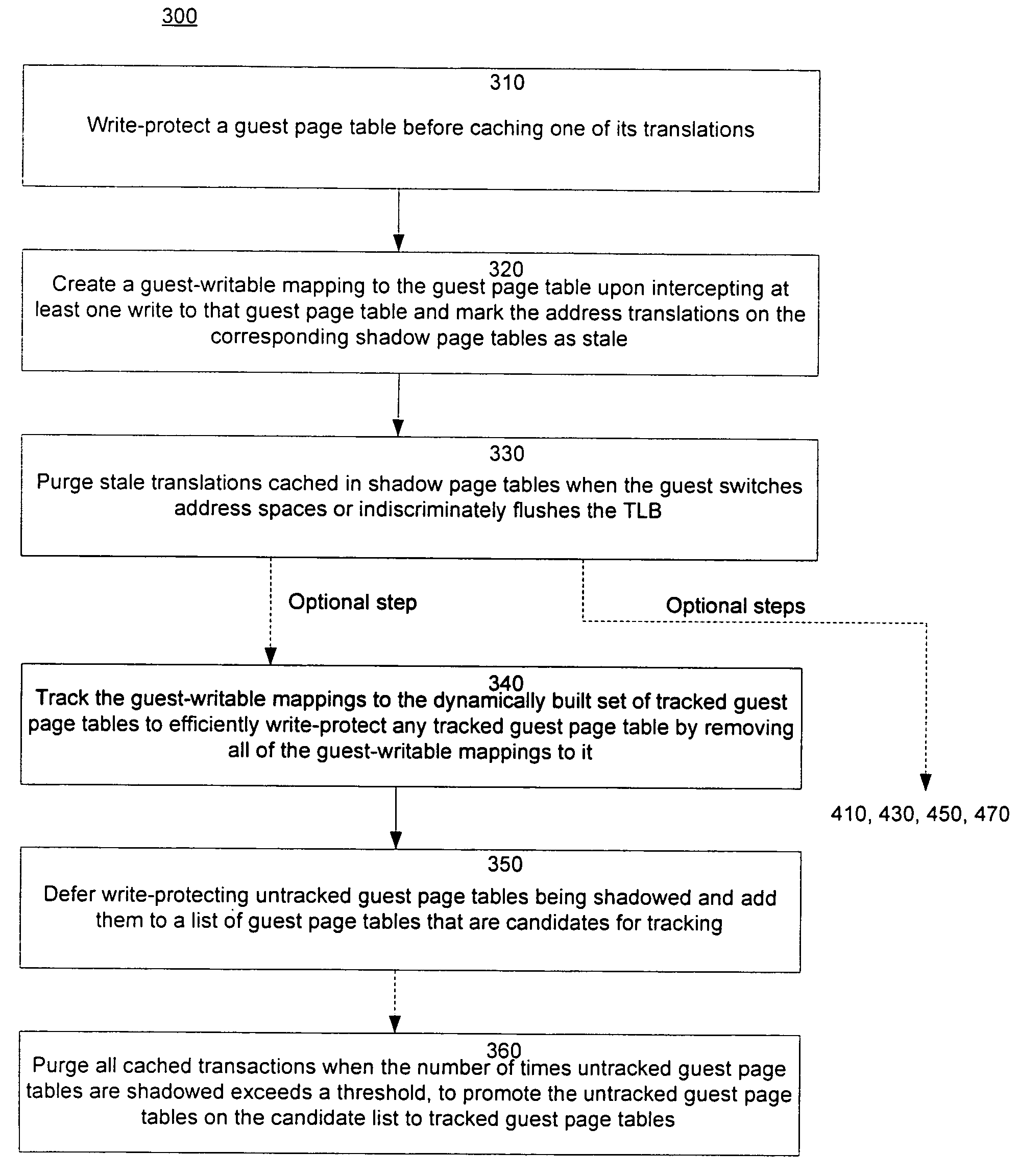
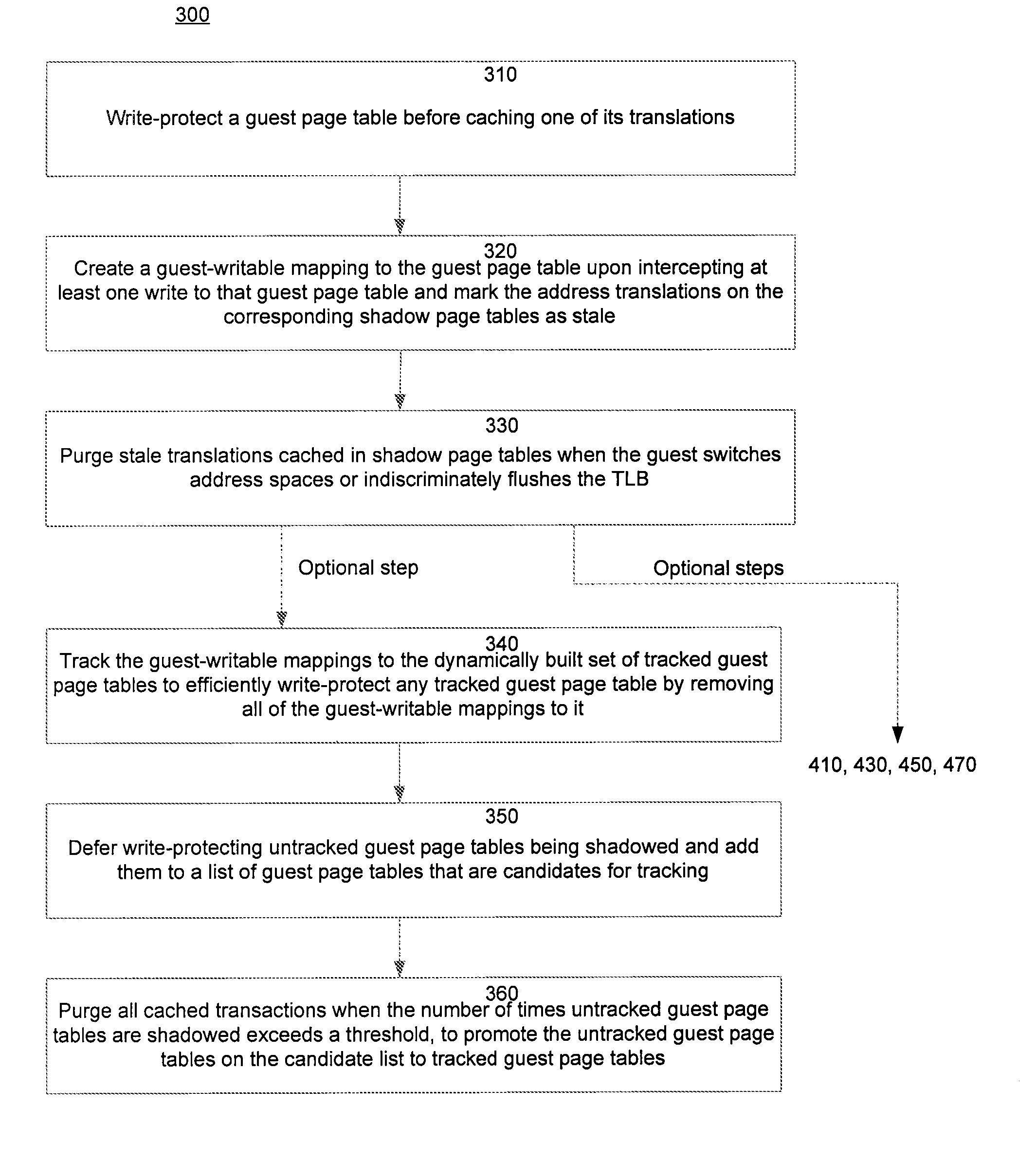
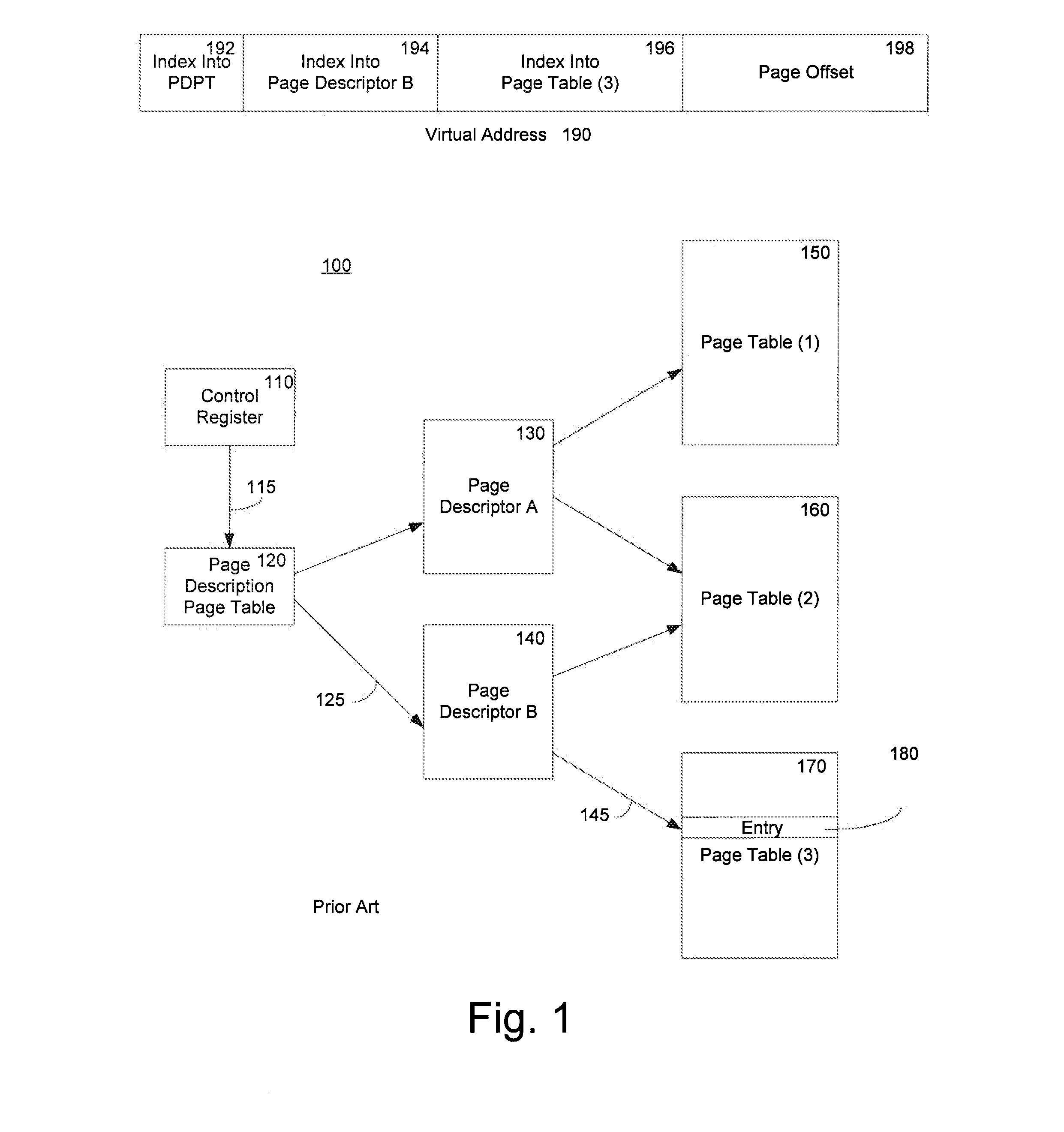
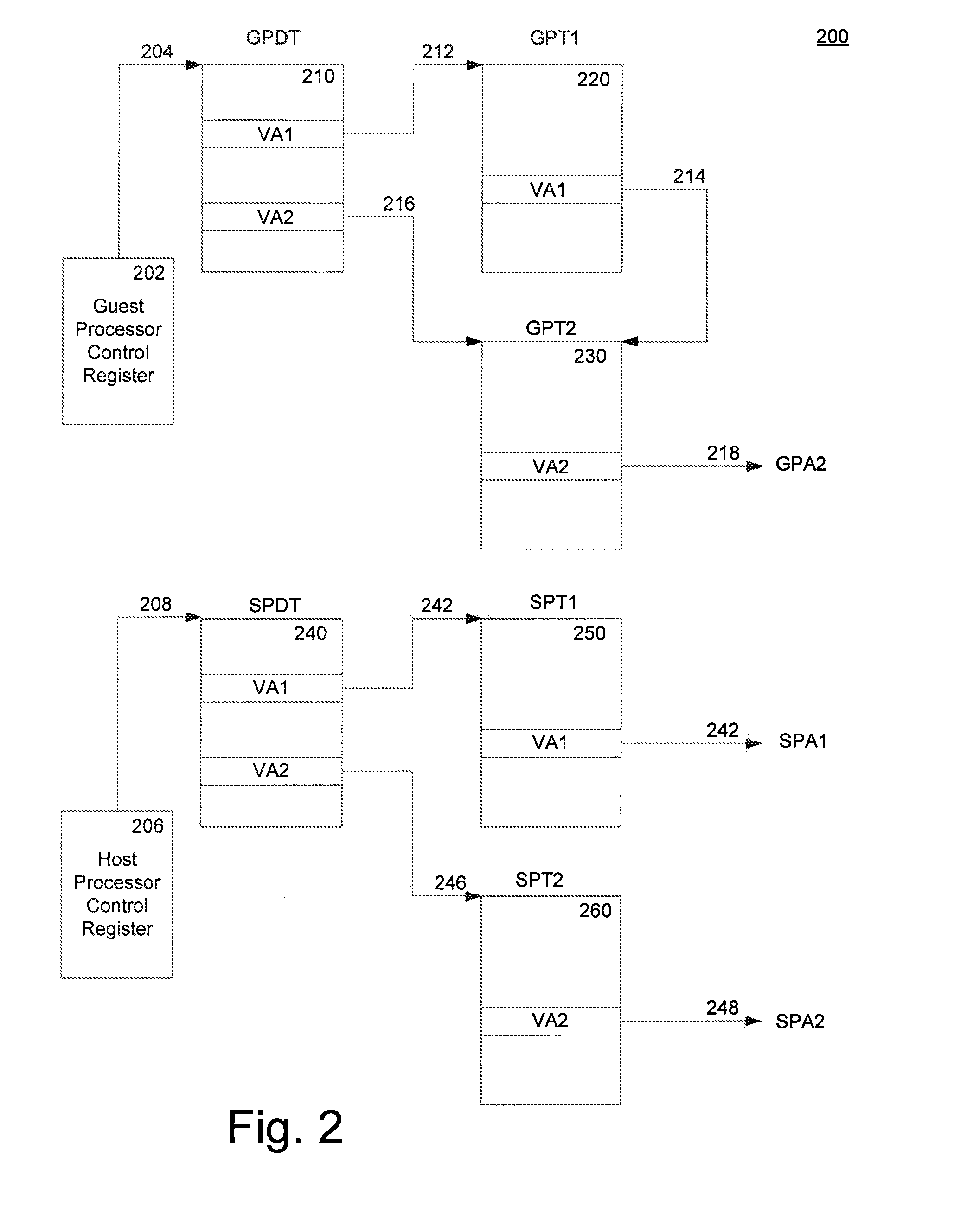
A method of virtualizing memory through shadow page tables that cache translations from multiple guest address spaces in a virtual machine includes a software version of a hardware tagged translation look-aside buffer. Edits to guest page tables are detected by intercepting the creation of guest-writable mappings to guest page tables with translations cached in shadow page tables. The affected cached translations are marked as stale and purged upon an address space switch or an indiscriminate flush of translations by the guest. Thereby, non-stale translations remain cached but stale translations are discarded. The method includes tracking the guest-writable mappings to guest page tables, deferring discovery of such mappings to a guest page table for the first time until a purge of all cached translations when the number of untracked guest page tables exceeds a threshold, and sharing shadow page tables between shadow address spaces and between virtual processors.
Owner:MICROSOFT TECH LICENSING LLC
Method and System For Caching Address Translations From Multiple Address Spaces In Virtual Machines
ActiveUS20080215848A1Low costEfficient detectionMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationPage table
A method of virtualizing memory through shadow page tables that cache translations from multiple guest address spaces in a virtual machine includes a software version of a hardware tagged translation look-aside buffer. Edits to guest page tables are detected by intercepting the creation of guest-writable mappings to guest page tables with translations cached in shadow page tables. The affected cached translations are marked as stale and purged upon an address space switch or an indiscriminate flush of translations by the guest. Thereby, non-stale translations remain cached but stale translations are discarded. The method includes tracking the guest-writable mappings to guest page tables, deferring discovery of such mappings to a guest page table for the first time until a purge of all cached translations when the number of untracked guest page tables exceeds a threshold, and sharing shadow page tables between shadow address spaces and between virtual processors.
Owner:MICROSOFT TECH LICENSING LLC
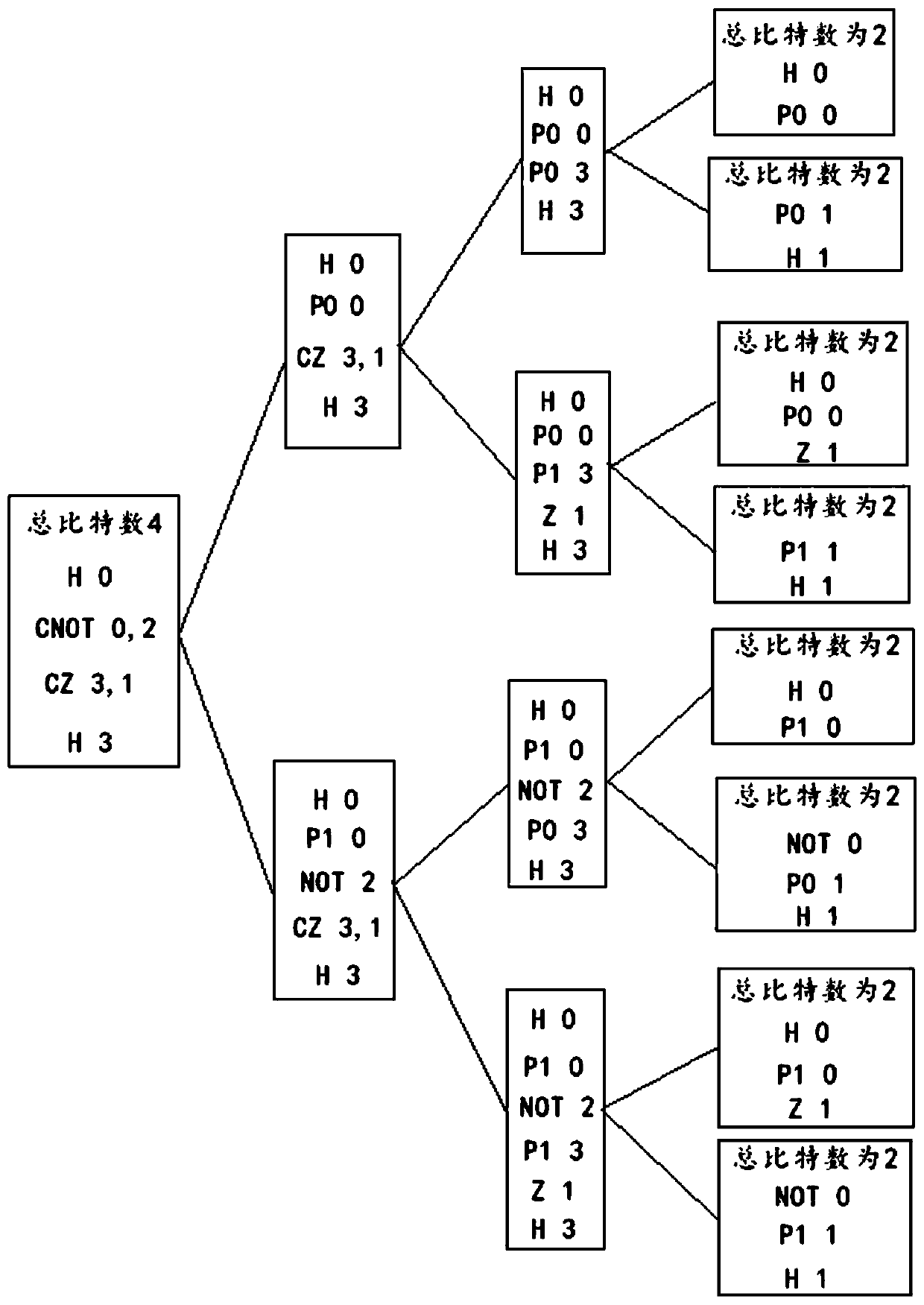
Quantum computing simulation method and device, storage medium and electronic device
ActiveCN110188885AReduce complexityQubit count reductionQuantum computersDesign optimisation/simulationQuantum computerSimulation methods
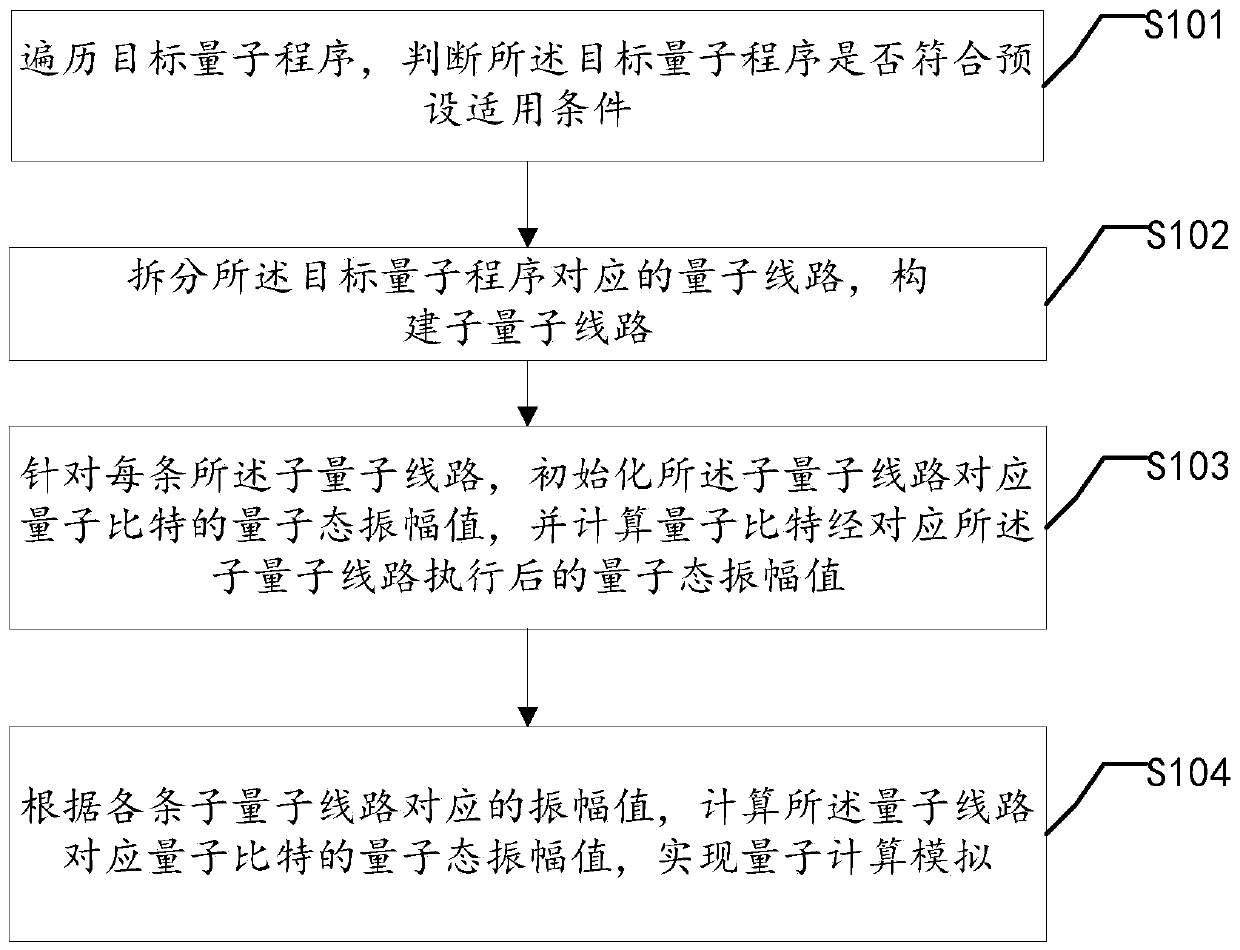
The invention discloses a quantum computing simulation method and device, a storage medium and an electronic device, and the method comprises the steps: traversing a target quantum program, and judging whether the target quantum program meets a preset application condition or not; if yes, splitting a quantum line corresponding to the target quantum program, and constructing a sub-quantum line; foreach sub-quantum line, initializing a quantum state amplitude value of a quantum bit corresponding to the sub-quantum line, and calculating the quantum state amplitude value of the quantum bit executed by the corresponding sub-quantum line; and according to the amplitude value corresponding to each sub-quantum line, calculating the quantum state amplitude value of the quantum bit corresponding tothe quantum line, and realizing quantum calculation simulation. By utilizing the embodiment of the invention, the simulation efficiency of quantum calculation can be improved.
Owner:HEFEI ORIGIN QUANTUM COMP TECH CO LTD
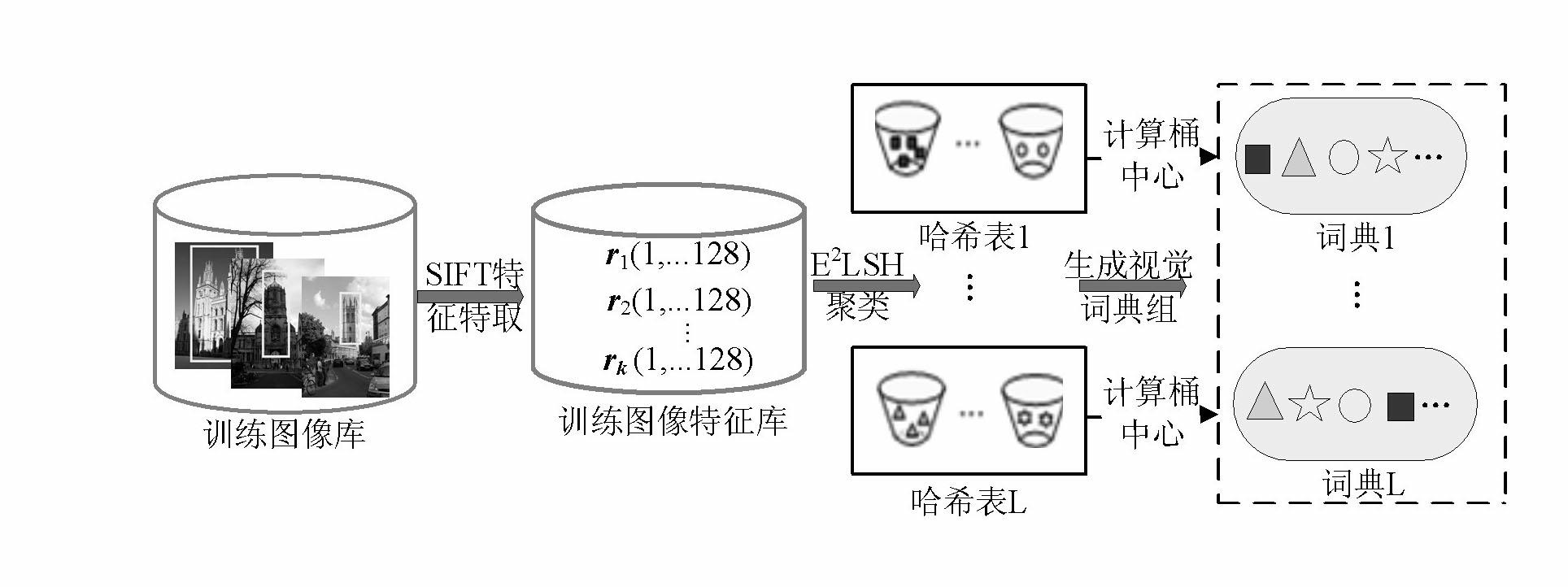
Target retrieval method based on group of randomized visual vocabularies and context semantic information
InactiveCN102693311AAddressing operational complexityReduce the semantic gapCharacter and pattern recognitionSpecial data processing applicationsImage databaseSimilarity measure
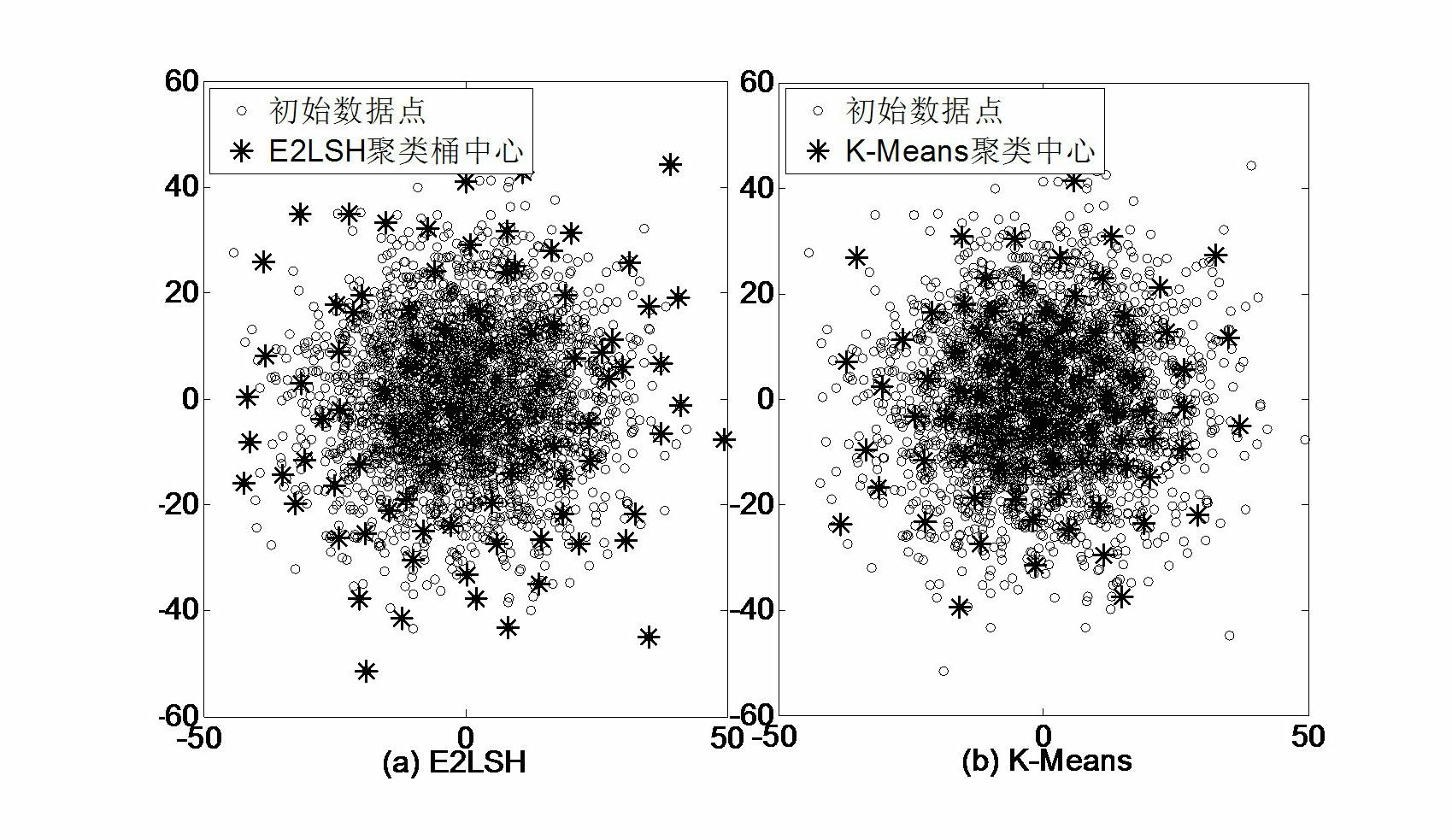
The invention relates to a target retrieval method based on a group of randomized visual vocabularies and context semantic information. The target retrieval method includes the following steps of clustering local features of a training image library by an exact Euclidean locality sensitive hash function to obtain a group of dynamically scalable randomized visual vocabularies; selecting an inquired image, bordering an target area with a rectangular frame, extracting SIFT (scale invariant feature transform) features of the inquired image and an image database, and subjecting the SIFT features to S<2>LSH (exact Euclidean locality sensitive hashing) mapping to realize the matching between feature points and the visual vocabularies; utilizing the inquired target area and definition of peripheral vision units to calculate a retrieval score of each visual vocabulary in the inquired image and construct an target model with target context semantic information on the basis of a linguistic model; storing a feature vector of the image library to be an index document, and measuring similarity of a linguistic model of the target and a linguistic model of any image in the image library by introducing a K-L divergence to the index document and obtaining a retrieval result.
Owner:THE PLA INFORMATION ENG UNIV
Discrete supervision cross-modal hashing retrieval method based on semantic alignment
ActiveCN107729513AImprove performanceBridging the Heterogeneous GapSpecial data processing applicationsHash functionSemantic alignment
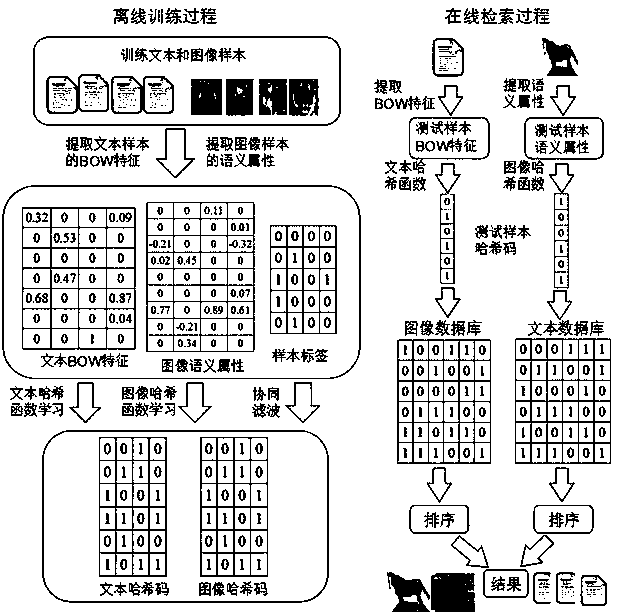
The invention discloses a DSAH (discrete semantic alignment hashing) method based on semantic alignment for cross-modal retrieval. In the training process, a heterogeneous gap is reduced by the aid ofimage attributes and modal alignment semantic information. In order to reduce memory overhead and training time, a latent semantic space is learned by synergistic filtering, and the internal relationbetween a hash code and a label is directly built. Finally, in order to decrease quantization errors, a discrete optimization method is proposed to obtain a hash function with better performances. Inthe retrieval process, samples in a testing set are mapped to a binary space by the hash function, the Hamming distance between a binary code of a query sample and a heterogeneous sample to be retrieved is calculated, and front ranked samples are returned according to the sequence from small to large. Experimental results of two representative multi-modal data sets prove superior performances ofDSAH.
Owner:LUDONG UNIVERSITY
Vector register file caching of context data structure for maintaining state data in a multithreaded image processing pipeline
ActiveUS20130044117A1Easy accessMinimize memory bus utilizationRegister arrangementsProgram control using wired connectionsGraphicsGeneral purpose
Frequently accessed state data used in a multithreaded graphics processing architecture is cached within a vector register file of a processing unit to optimize accesses to the state data and minimize memory bus utilization associated therewith. A processing unit may include a fixed point execution unit as well as a vector floating point execution unit, and a vector register file utilized by the vector floating point execution unit may be used to cache state data used by the fixed point execution unit and transferred as needed into the general purpose registers accessible by the fixed point execution unit, thereby reducing the need to repeatedly retrieve and write back the state data from and to an L1 or lower level cache accessed by the fixed point execution unit.
Owner:SAMSUNG ELECTRONICS CO LTD
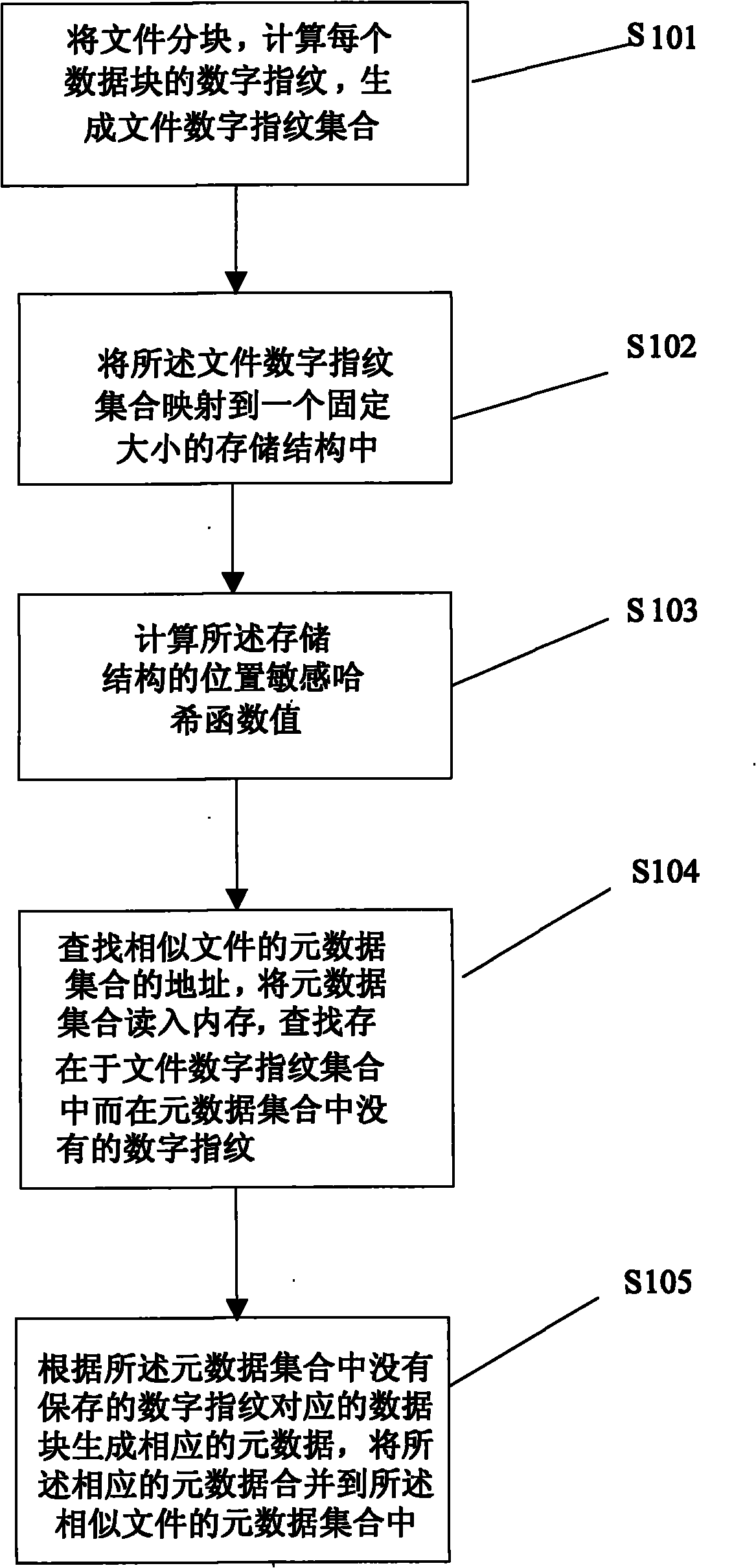
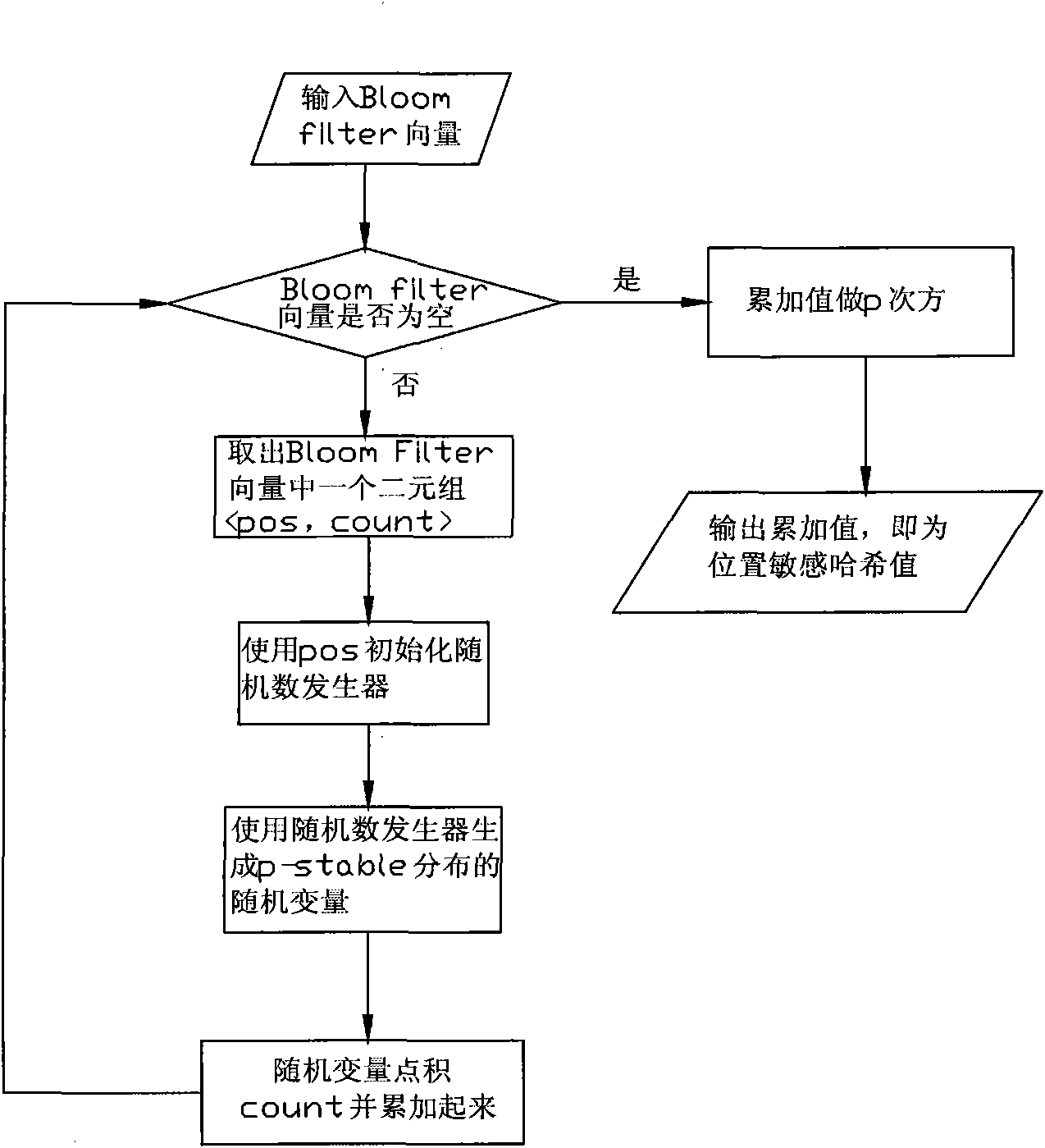
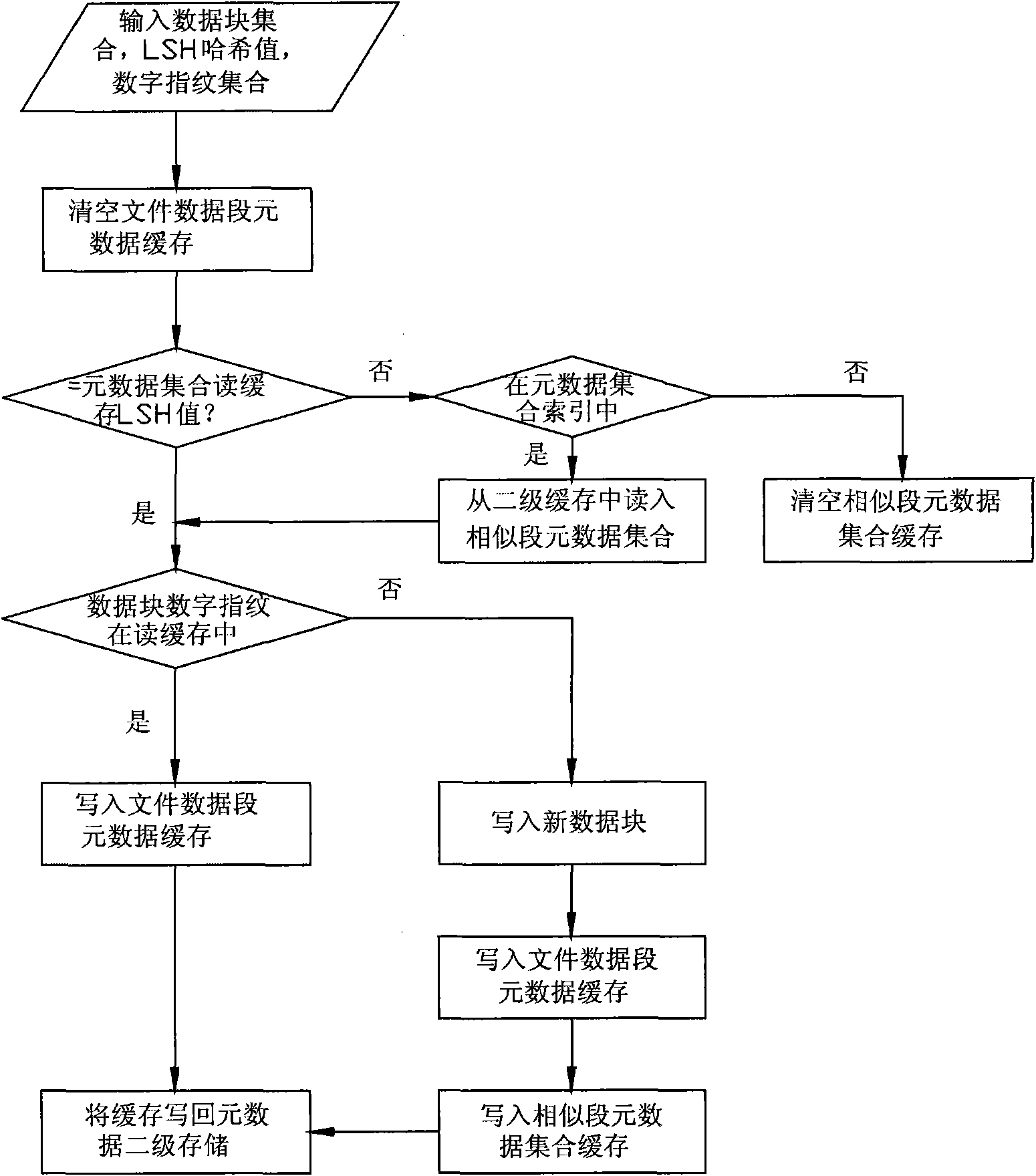
Method for managing metadata of redundancy deletion and storage system based on location sensitive Hash
ActiveCN101963982AImprove redundancyQuick and accurate identificationSpecial data processing applicationsSystem requirementsMetadata management
The invention discloses a method for managing metadata of redundancy deletion and storage system based on location sensitive Hash, which combines the metadata of a similar file data block together rapidly by a location sensitive Hash function, so that when a data block is written into the redundancy deletion and storage system, the method can quickly search whether the data block has existed in the system, improves the metadata search performance of the redundancy deletion and storage system and finally improves the throughput rate of the system. In the method, the query speed, the memory overhead and the redundancy deletion effect of a metadata management system are changed by setting the number of the used location sensitive Hash functions and adjusting the identification rate of similar files. The method can lead the metadata management to be suitable for different demands of the redundancy deletion and storage system, can improve the identification rate of similar files by using a plurality of Hash functions, improves the redundancy deletion capability of the redundancy deletion and storage system and reduces the memory overhead of the metadata index.
Owner:TSINGHUA UNIV
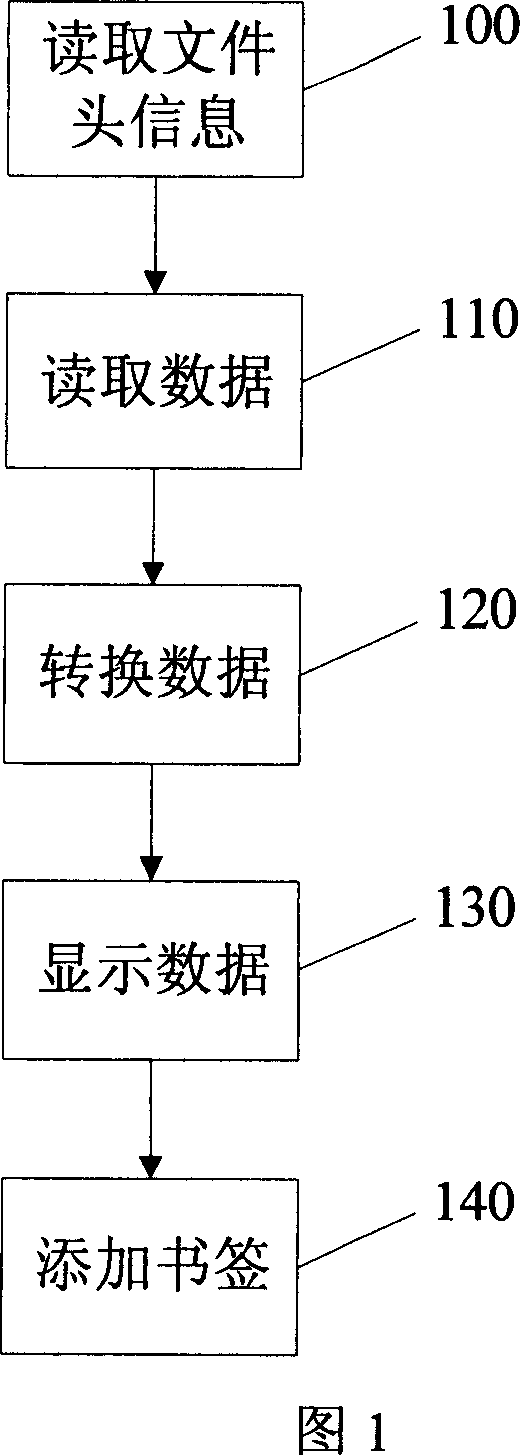
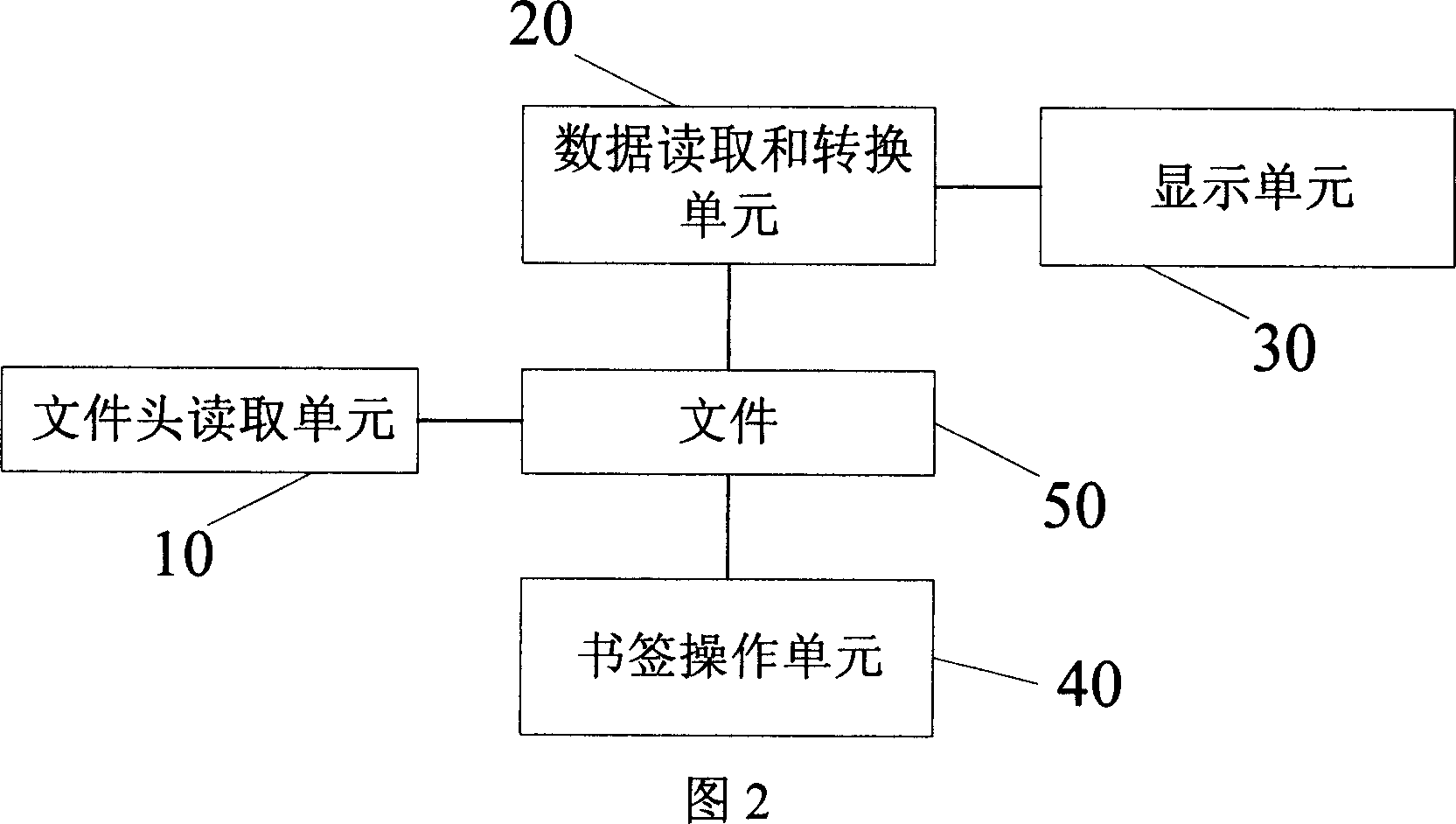
Method and apparatus for displaying electronic book on mobile phone
InactiveCN101059800AEasy to manageReduce memory overheadSpecial data processing applicationsElectronic bookDocument format
The invention discloses a method for displaying electric book on a mobile phone, characterized in that reading and displaying the data in fixed length in each time, recording bookmark information at the tail of document. The invention also disclose a relative device, comprising a document head reader for reading the information of document head and finding document format, a data reading and converting unit for reading the data in fixed length and converting the data into Unicode, a display unit for displaying the read and converted data, and a bookmark operator for adding bookmark information at the tail of the document. The invention uses segmented read method in limited device as mobile terminal to reduce memory consumption, support ultra-large document, realize paging, and jump or the like, and inserts bookmark data into the tail of document, to directly correlate the bookmark and the document to support the management of bookmark data, as document deletion and bookmark data elimination.
Owner:SHANGHAI CHENXING ELECTRONICS SCI & TECH CO LTD
Stream type repetitive data detection method
ActiveCN102253820AFlexible and Efficient DetectionMaintain stabilityData conversionInternal memoryExtensibility
The invention provides a stream type repetitive data detection method. According to the method, a TBFA (Timing Bloom Filter Array) is constructed for flexibly and efficiently detecting repetitive data in a sliding window model, wherein the TBFA consists of a plurality of TBFs (Timing Bloom Filters) with the same structure, each TBF comprises a bloom filter and a separated timer array used for storing timestamps, the whole TBFA works in a looped first-in first-out mode and gets rid of old elements removed from a data stream monitoring window while recording new elements. The stream type repetitive data detection method is implemented under the sliding widow model, element monitoring is correct to one element, therefore the statistic result based on the stream type repetitive data detectionmethod has good stability; in addition, a part of the timer arrays in the TBFA can be unloaded into a disc, therefore the overhead of an internal memory can be reduced. Theoretical analysis and experimental data show that more than 95% of query efficiency can be maintained when DCBA (Detached Counting Bloom filters Array loads less than 10% of data contents to the internal memory, therefore the method provided by the invention is superior to the traditional technical scheme in space efficiency and expandability.
Owner:HUAZHONG UNIV OF SCI & TECH
Neural network optimizing method and device
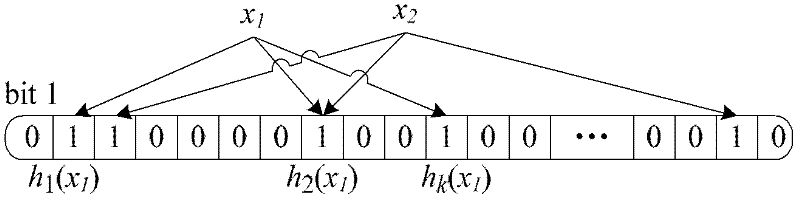
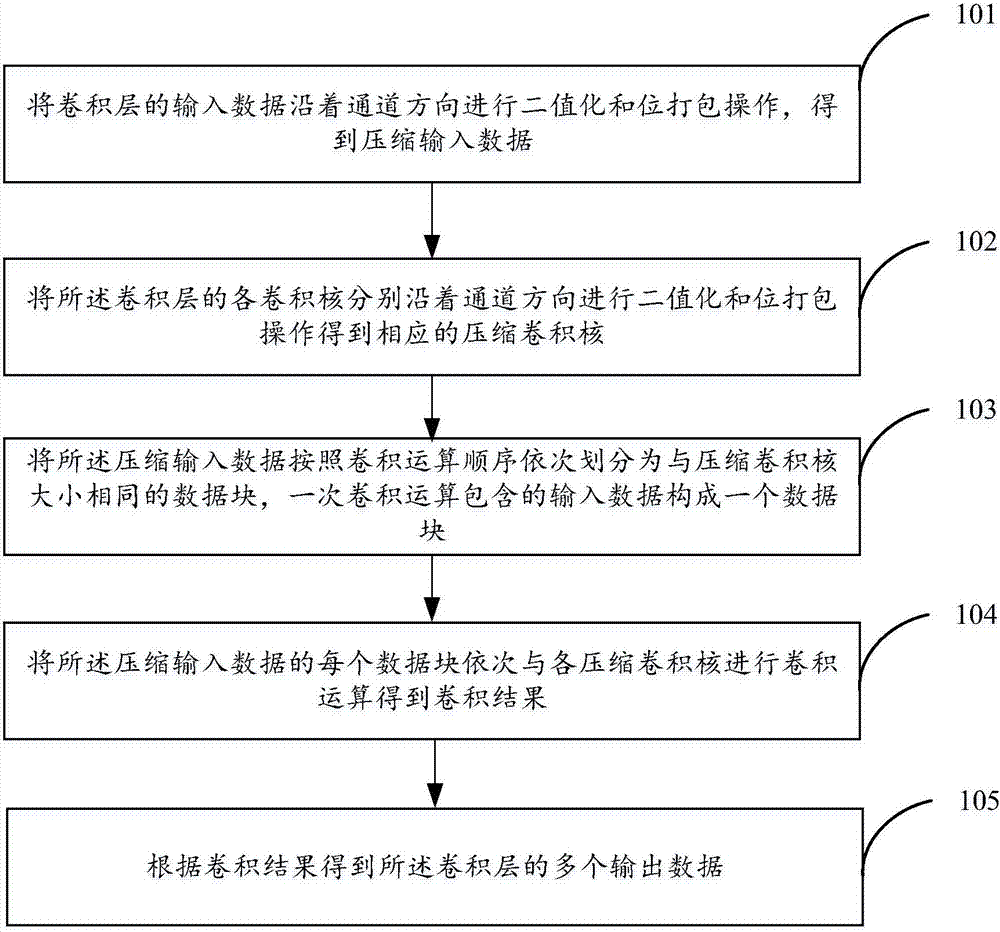
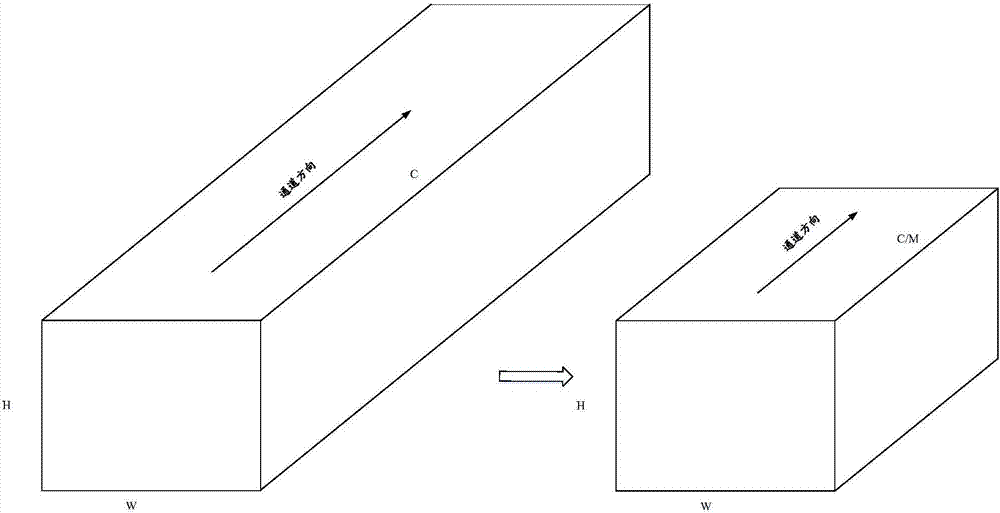
ActiveCN107145939ABitwise operations are good atHeavy computationKernel methodsCode conversionNerve networkAlgorithm
The invention discloses a neural network optimizing method and a device to solve the problems in the prior art of neural network technology that the calculation speed is low, and that the timeliness is poor. The method comprises: performing binarization to the convolution layer inputted data along the channel direction and packaging the bits to obtain the zipped data; performing binarization to the convolution kernels of the various convolution layers and packaging the bits to obtain the corresponding zipped convolution kernels; dividing the zipped input data into data blocks of the same sizes as the convolution kernels according to the calculation order in a succession manner with the input data contained in one convolution calculation forming a data block; performing convolution calculations to each data block of the zipped input data successively with the zipped convolution kernels to obtain the convolution result; and according to the convolution result, obtaining a plurality of output data for the convolution layers. The technical schemes of the invention are able to make the neural network calculation more speedy and more timely.
Owner:BEIJING TUSEN ZHITU TECH CO LTD
Label-based black box detection method and system for privacy disclosure of Android user
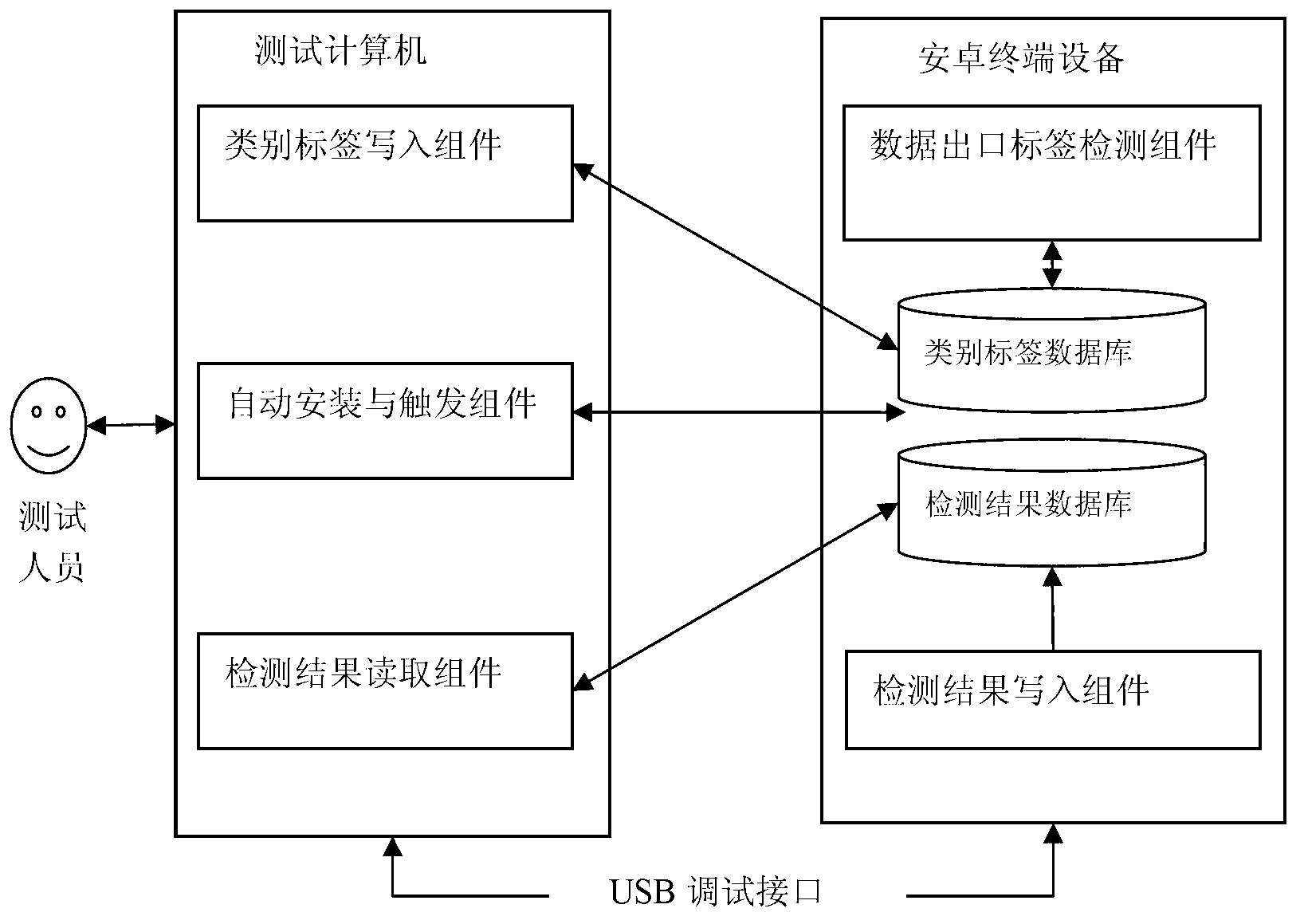
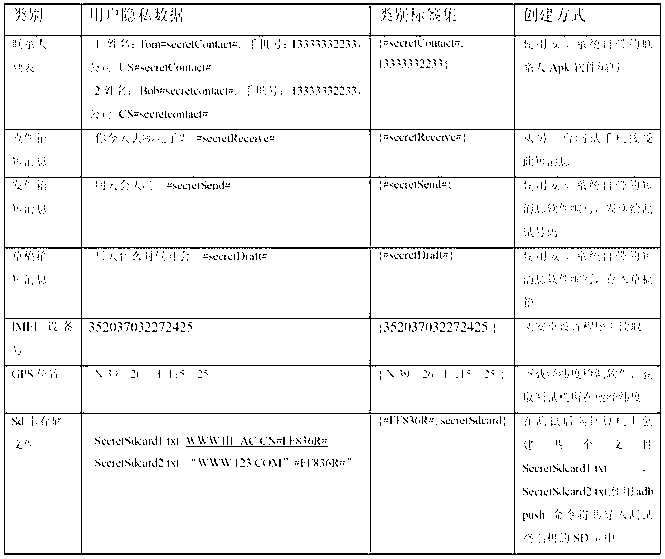
InactiveCN103309808AShorten the timeReduce memory overheadDigital data protectionSoftware testing/debuggingInternet privacyNetwork packet
The invention relates to a label-based black box detection method and system for privacy disclosure of an Android user. The detection steps are as follows: 1), user privacy data are created for an Android user terminal and category labels are added to the user privacy data; 2), at least one to-be-detected application program is mounted in the Android user terminal and is triggered; 3), the category labels carried in data packets sent by the application program are detected at an network exit of the Internet, a Bluetooth or a short message; and 4), privacy data categories are judged according to category labels carried in the data packets, and results are recorded. Analysis of a large number of orders and stain spreading time is saved, variables in all orders of the application program and intermediate variables during calculation are avoided, and a large amount of memory expenditure is saved at the same time.
Owner:HUAWEI TECH CO LTD +1
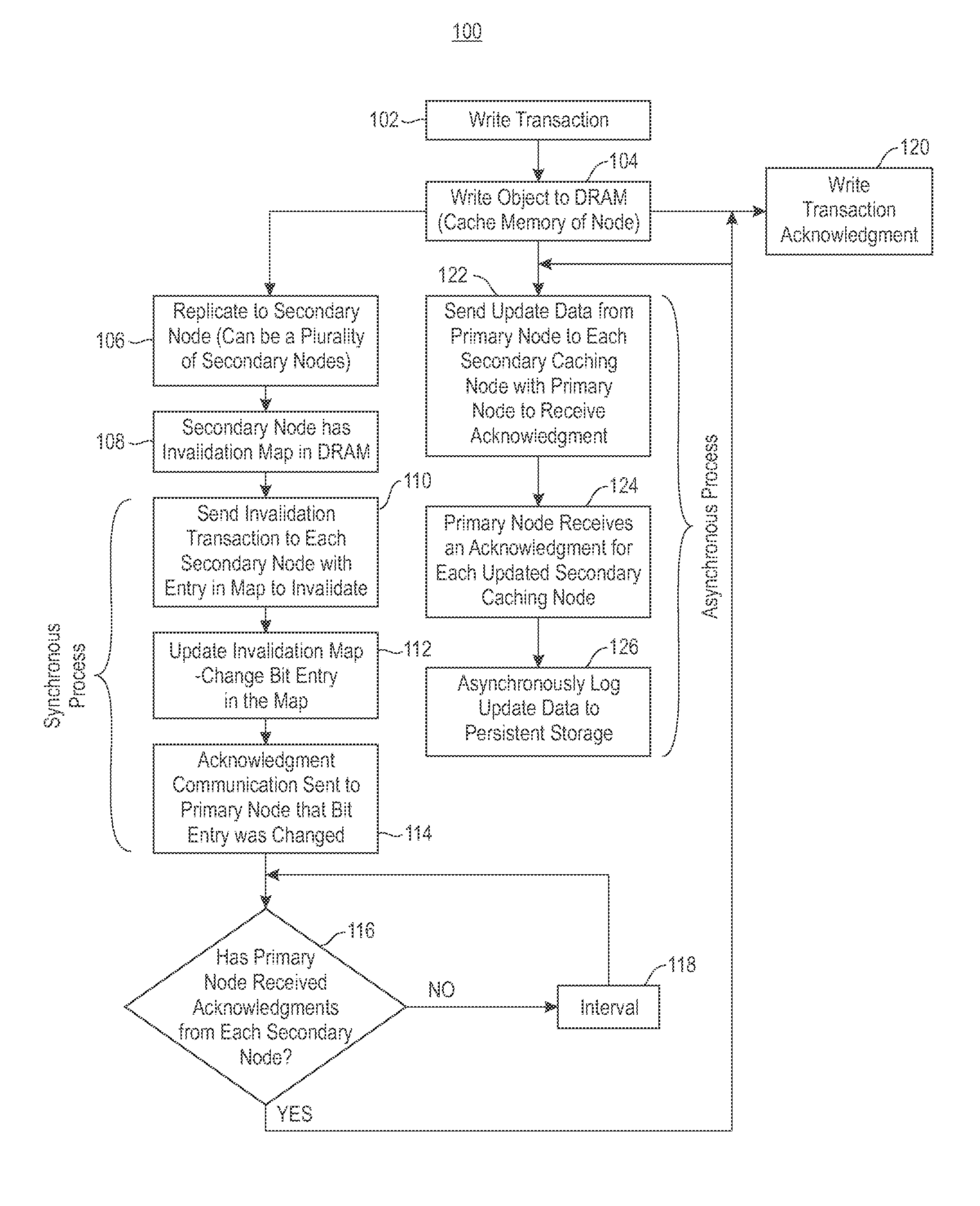
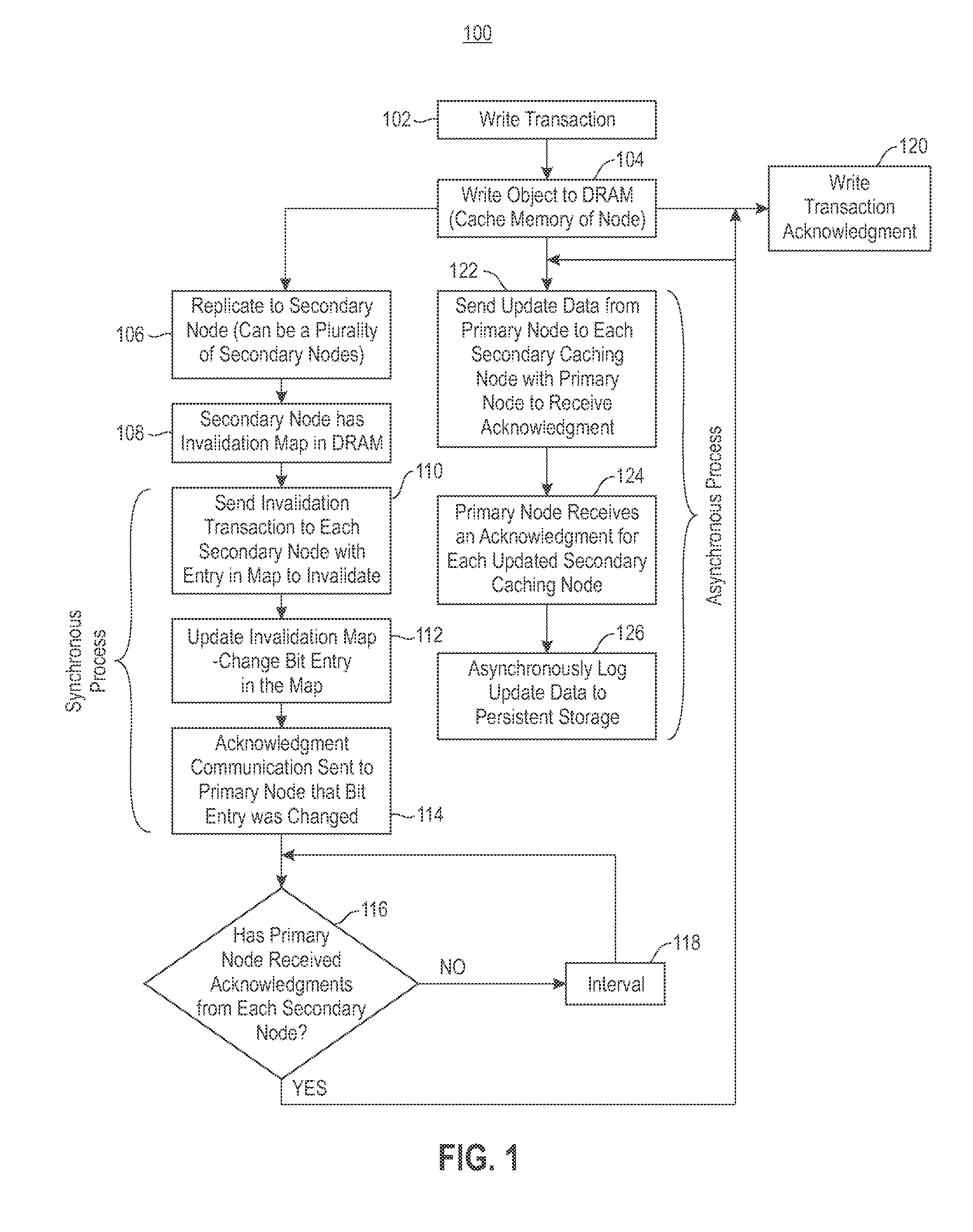
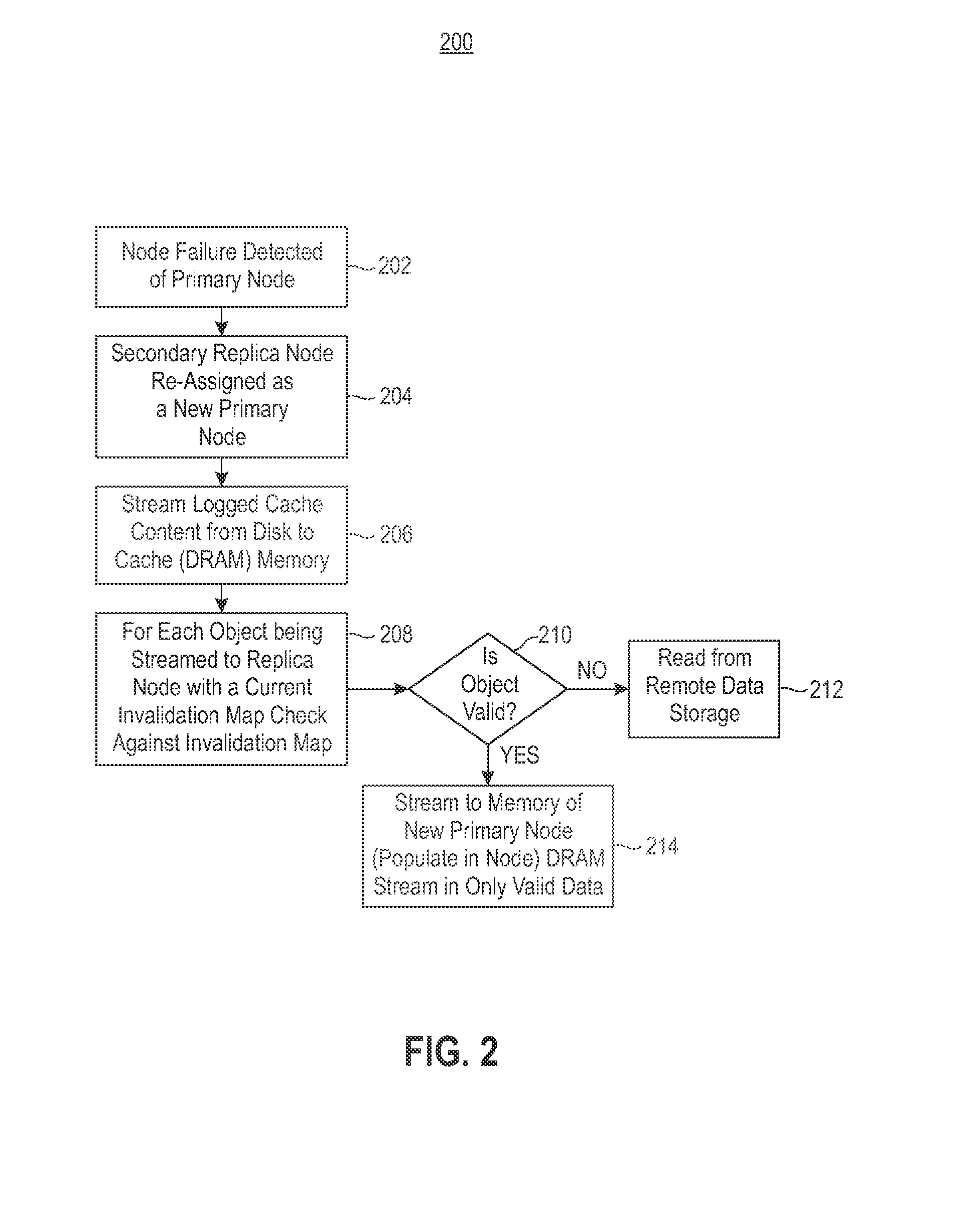
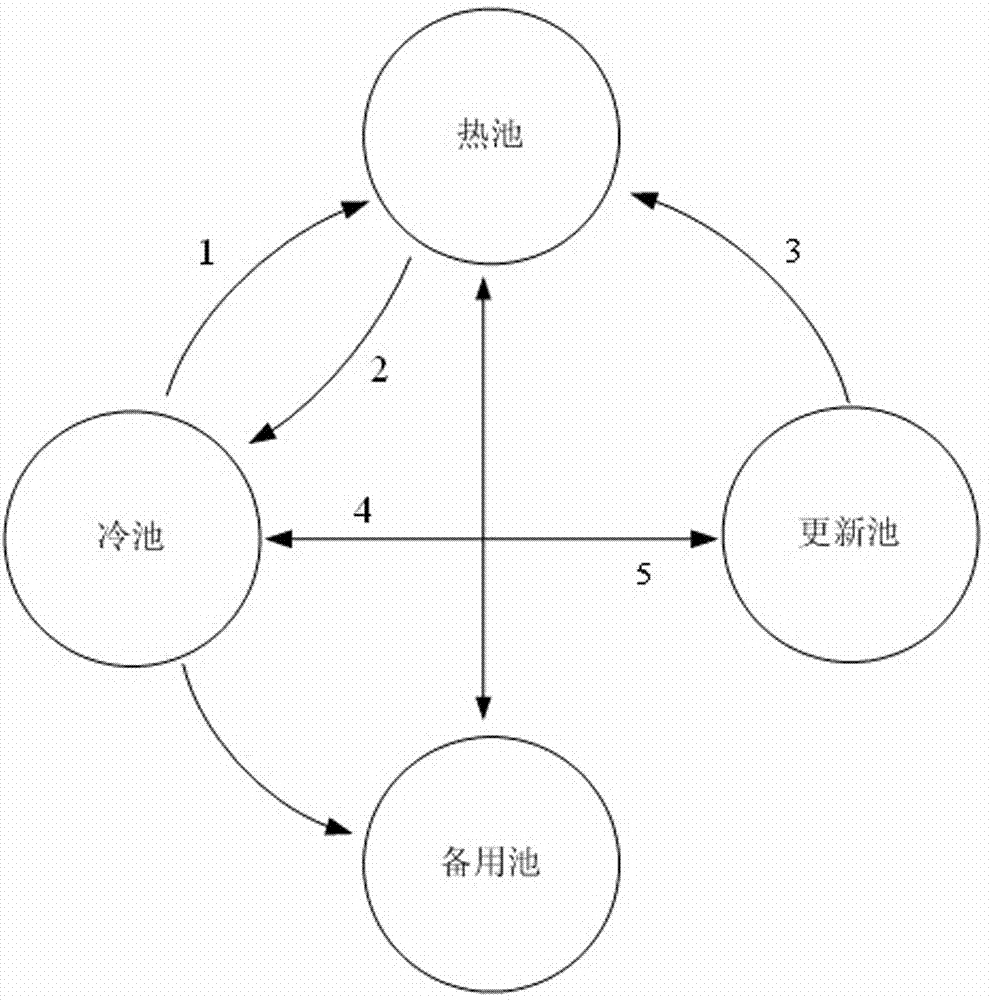
Reducing Memory Overhead of Highly Available, Distributed, In-Memory Key-Value Caches
InactiveUS20140115251A1Reduce memory overheadImprove usabilityMemory architecture accessing/allocationMemory loss protectionHigh availabilityComputer science
Maintaining high availability of objects for both read and write transactions. Secondary copies of cached objects are created and maintained on disks of a secondary caching node and in remote data storage. In response to an update request, the secondary copies of cached objects are updated. Secondary cached objects are synchronously invalidated in response to the update request, and the update is asynchronously propagated to a secondary caching node.
Owner:IBM CORP
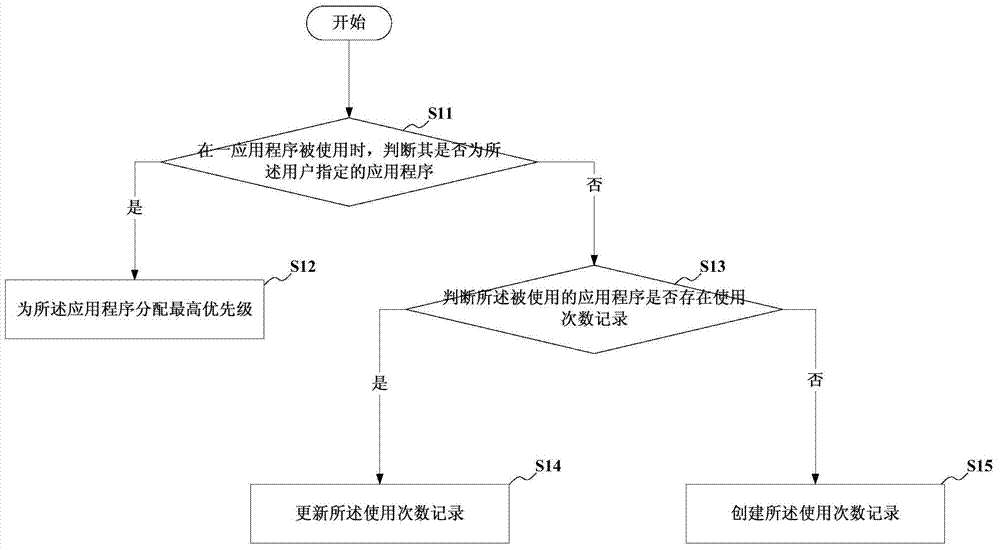
Mobile terminal application management system and method and use time record generating method
ActiveCN104750550AEasy to operateImprove experienceMultiprogramming arrangementsComputer terminalApplication software
The invention provides a mobile terminal application management system and method and a use time record generating method. The use time record generating method is that the use times of each application program in a mobile terminal is recorded to calculate the use frequency of the each application program; different priority levels are distributed for the corresponding application programs according to different use frequency; the application program with high priority level is configured to enter the state of using earlier than the application program with low priority level. With the adoption of the use time record generating method, the application program interested by a user can be analyzed according to the application program use frequency of the user; the application program interested by the user cannot be easily removed during operating the background program and can be quickly accessed through a lock screen; in addition, the notification bar and list sequence of the application program interested by the user are sequenced in the top so that the user can view conveniently. The method has the advantages that the independence on hardware equipment is avoided, the positioning can be rapidly performed, and some commonly-used application programs can be accessed; the memory input is reduced; the user can operate conveniently, and thus the user experience can be increased.
Owner:北京佐敦网络科技有限公司
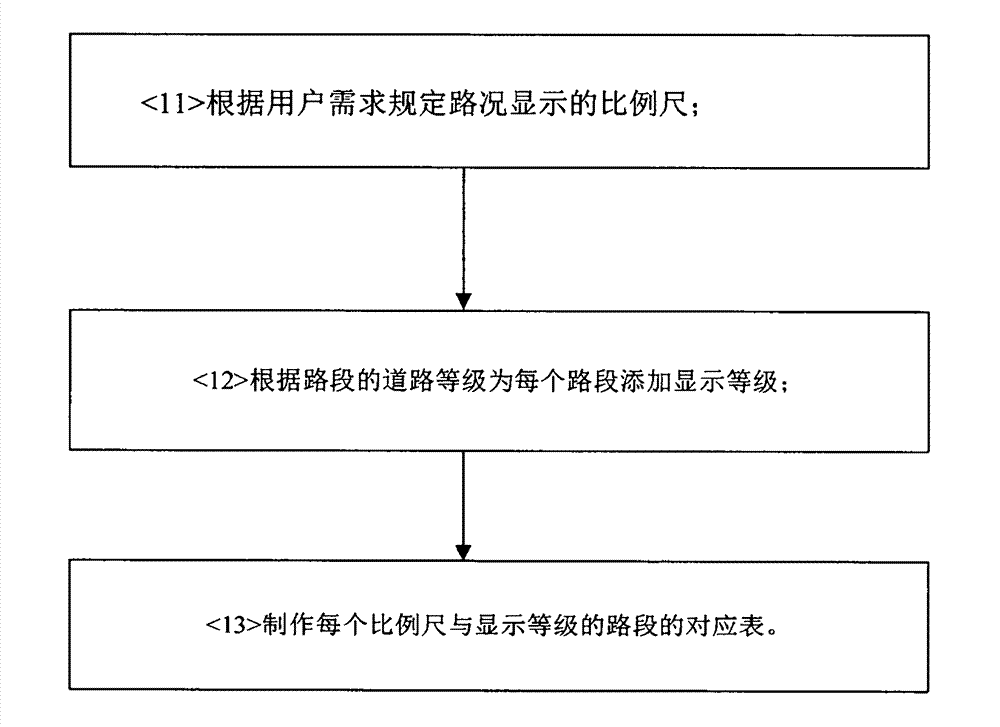
Data hierarchy and organization method and device capable of fast displaying road conditions
InactiveCN102818571ARapid positioningReduce memory overheadInstruments for road network navigationEngineeringData mining
A data hierarchy and organization method capable of fast displaying road conditions includes defining display levels of different road sections in map data according to road hierarchy information; then, combining the road sections with same index identifications into a road section according to index identifications of a road section coding schedule in the map data and performing thinning; establishing code corresponding indexes which can be rapidly and mutually searched between road condition display data and the road section coding schedule according to a unique index of road condition information; and finally, generating road condition display data according to the established code corresponding indexes and subjecting the road condition display data to partitioning organization to display the area road conditions.
Owner:BEIJING QIANTU FANGYUAN SOFTWARE TECH
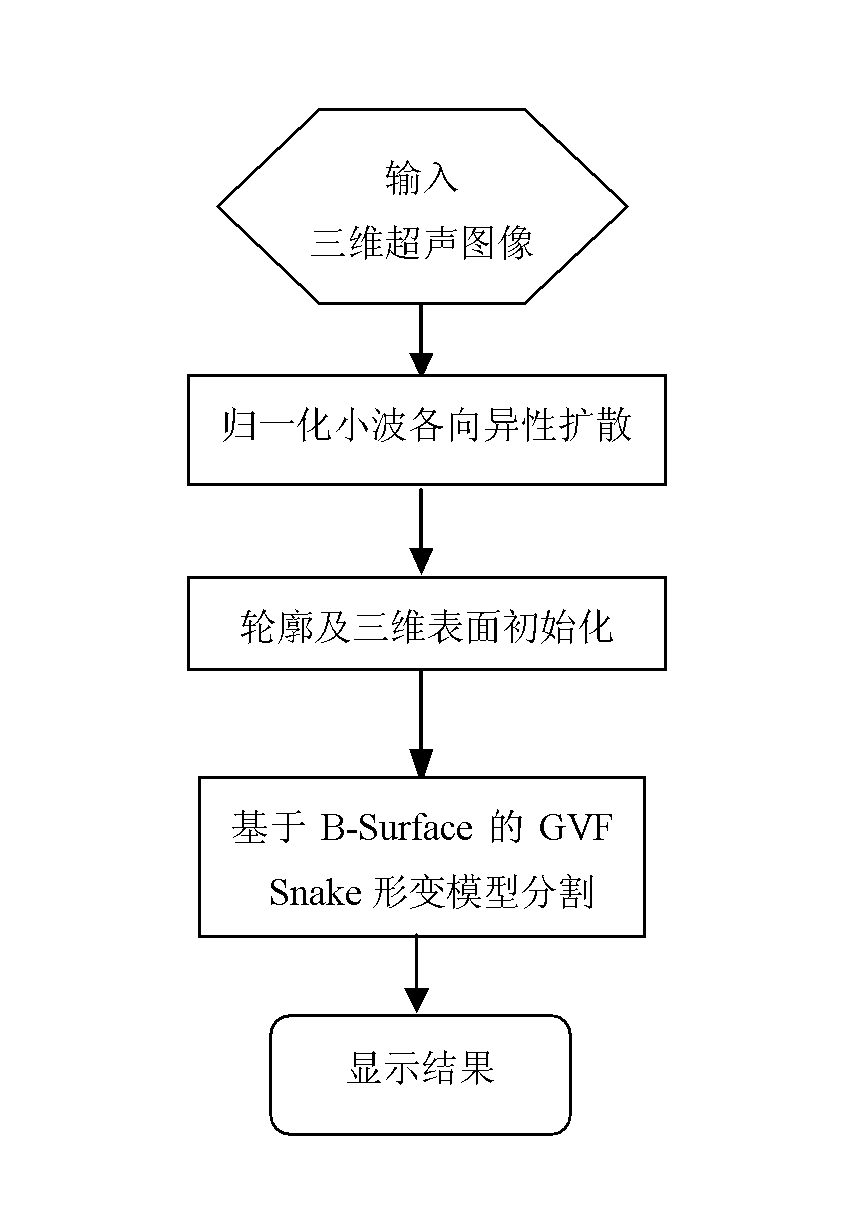
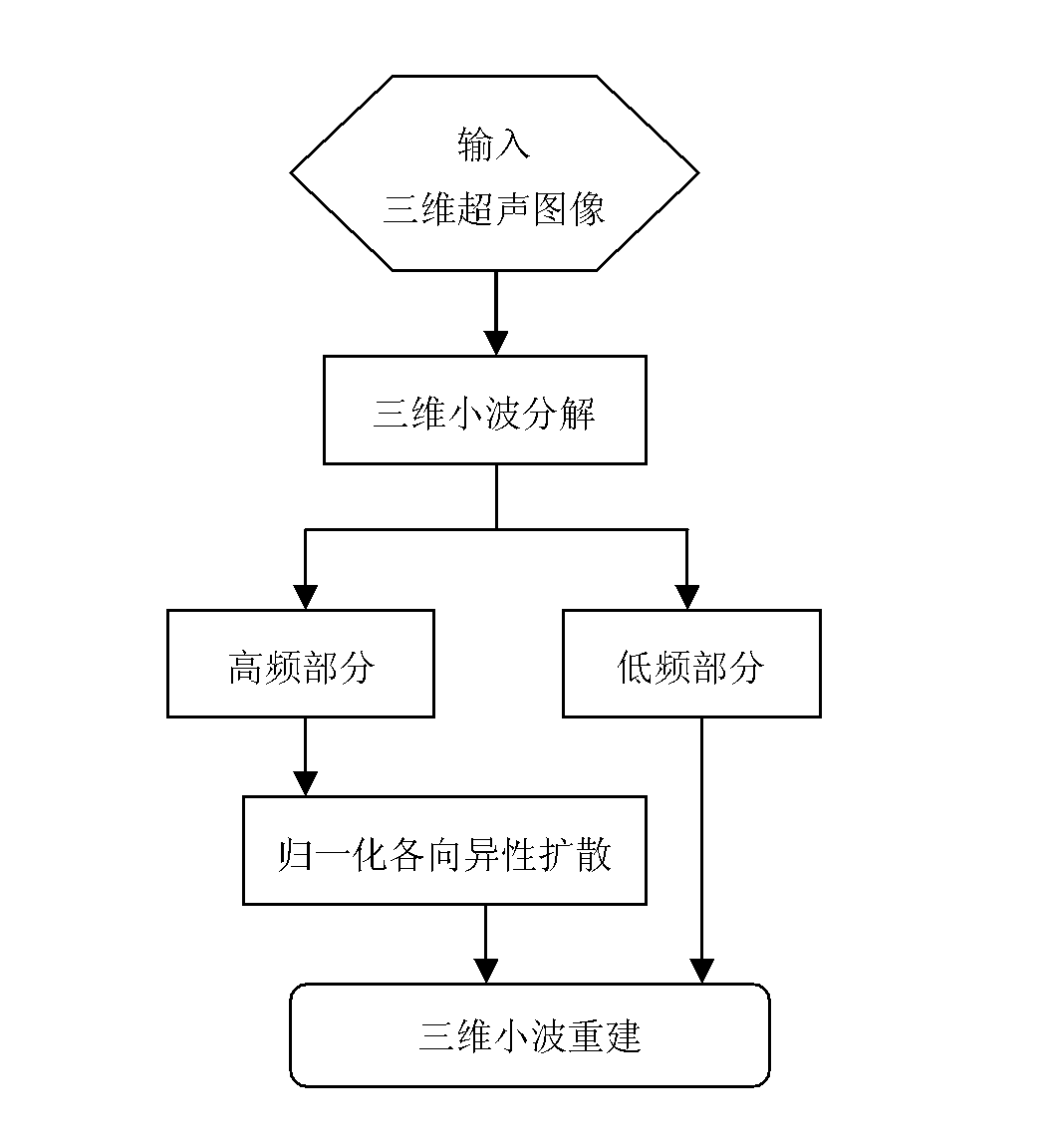
Method for segmenting three-dimensional ultrasonic image
InactiveCN102402788AEffective smoothingAccurate segmentationImage enhancementImage analysisComputed tomographyResonance
The invention discloses a method for segmenting a three-dimensional ultrasonic image, belonging to the technical field of the digital image processing. The method comprises the following steps: (1) preprocessing spots of the three-dimensional ultrasonic image by adopting a normalized anisotropic diffusion method of a three-dimensional wavelet according to the characteristics of the three-dimensional ultrasonic image to remove spot noise; (2) initializing the preprocessed three-dimensional ultrasonic image by adopting a Canny edge detection operator; and (3) segmenting the three-dimensional ultrasonic image three-dimensionally by using a B-Surface and GVF Snake based three-dimensional deformation model. The method disclosed by the invention can be used to rapidly and accurately segment the three-dimensional ultrasonic image and particularly has strong noise robustness. The method for automatically segmenting the three-dimensional ultrasonic image can be also used for segmenting other three-dimensional images such as CT (computed tomography) images, MRI (magnetic resonance images) and PET (position-emission tomography) images, thereby having high application value.
Owner:SOUTH CHINA UNIV OF TECH
Webpage rendering method and related equipment
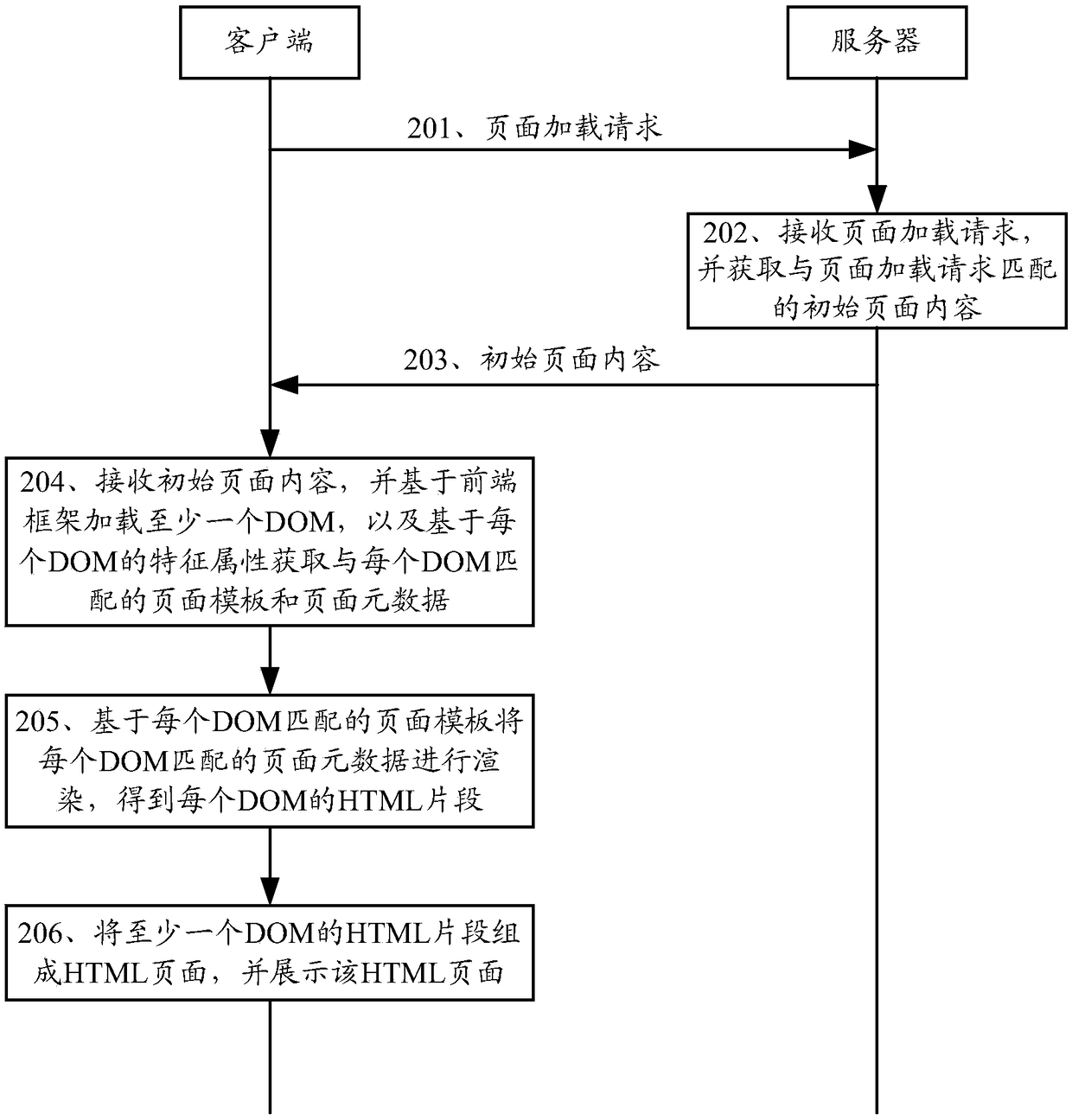
InactiveCN108334517AImprove efficiencyImprove system performanceText processingWebsite content managementClient-sideDatabase
The embodiment of the invention discloses a webpage rendering method and related equipment. The method includes the steps that after a server receives a page loading request of a client side, initialpage content matched with the page loading request can be obtained and returned to the client side, wherein the initial page content includes a front-end framework and at least one DOM; the client side can load the DOMs based on the front-end framework and obtain page templates and page metadata matched with the DOMs based on feature attributes of all the DOMs, and therefore the page metadata is rendered based on the page templates to obtain HTML fragments of all the DOMs; finally, all the HTML fragments form an HTML page, and the HTML page is displayed. According to the embodiment, page rendering is conducted by the client side, in a high-concurrence scene, the hardware deployment cost, pressure and memory overhead of the server can be reduced, and the page rendering efficiency and the system performance are improved.
Owner:HUAWEI TECH CO LTD
Method and System to Space-Efficiently Track Memory Access of Object-Oriented Language in Presence of Garbage Collection
InactiveUS20100114999A1Reduce storage overheadReduce memory overheadError detection/correctionMemory adressing/allocation/relocationProcess memoryObject based
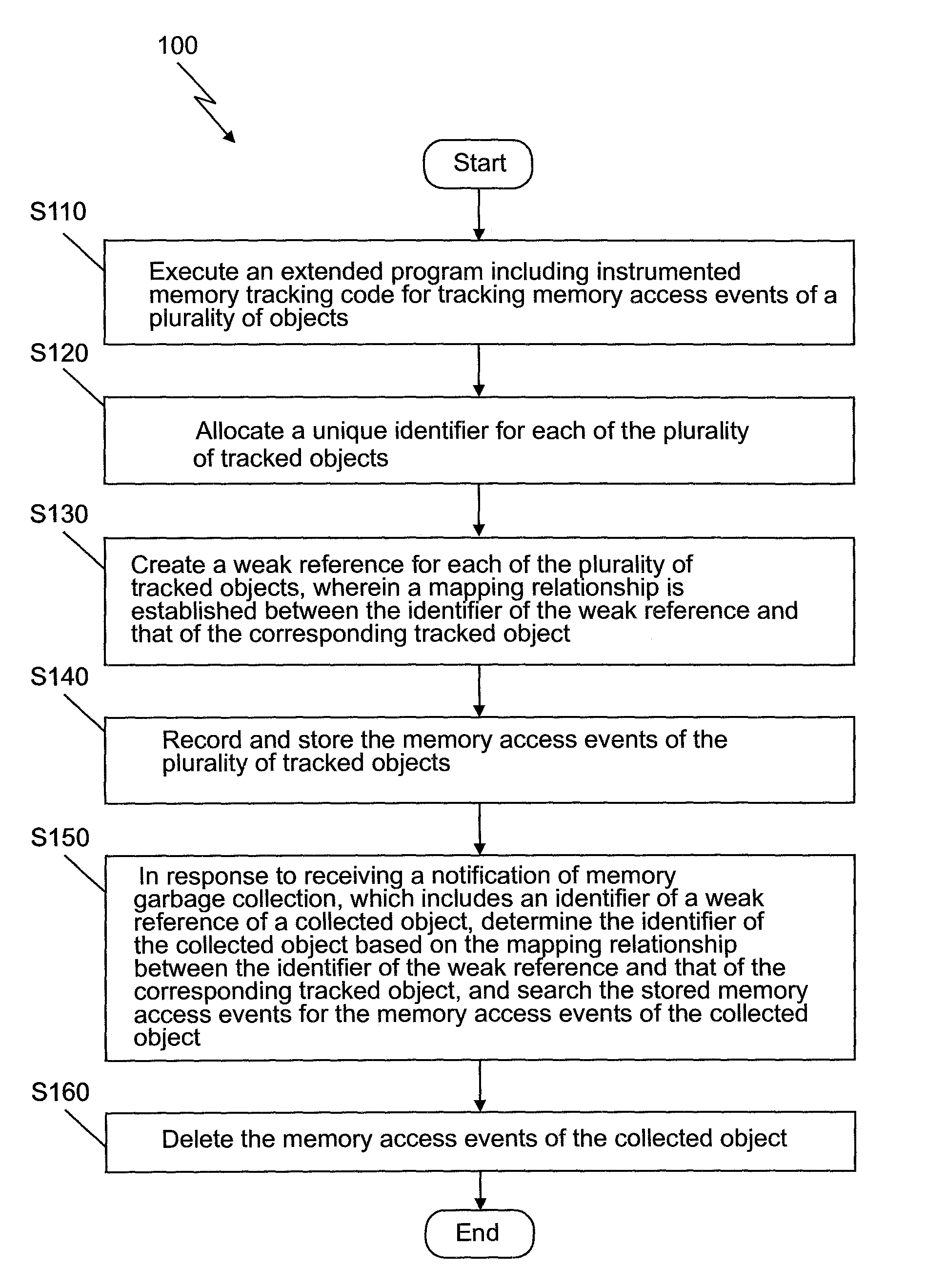
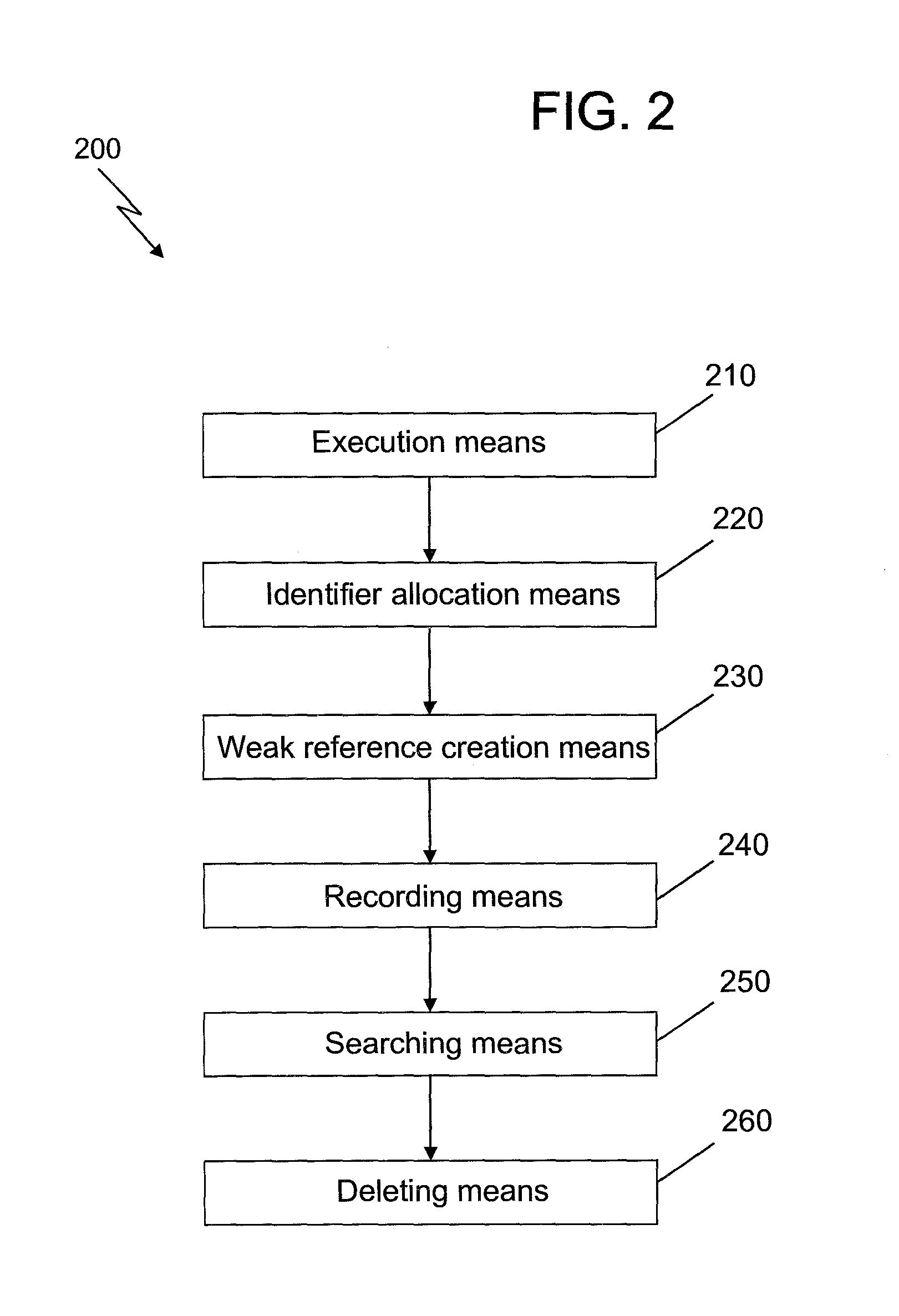
The present invention provides a method and system for processing memory access events. The method comprises: executing an extended program including instrumented memory tracking code for tracking memory access events of a plurality of objects; allocating a unique identifier for each of the plurality of tracked objects; creating a weak reference for each of the plurality of tracked objects, wherein a mapping relationship is established between the identifier of the weak reference and that of the corresponding tracked object; recording and storing the memory access events of the plurality of tracked objects; in response to receiving a notification of memory garbage collection which includes an identifier of a weak reference of a collected object, determining the identifier of the collected object based on the mapping relationship between the identifier of the weak reference and that of the corresponding tracked object, and searching the stored memory access events for the memory access events of the collected object; and deleting the memory access events of the collected object. The storage overhead may be reduced according to the above method of the present invention.
Owner:IBM CORP
Method and apparatus for automated patient severity ranking in mass casualty incidents
InactiveUS20160328530A1Attenuation bandwidthReduce total powerMedical data miningElectrocardiographyNODALMass Casualty
A single disaster could leave hundred thousands of people injured or even dead. In order for the rescue team to reach this knowledge they should send one of the team members to investigate the scene. Body Sensor Networks are emerging systems that can be easily used to measure patient's physiological data and communicate relevant data to other patient using their smart phones. We propose to use Bloom filters, a space efficient probabilistic data structure, for efficiently collecting the dynamic status of patients in a mass casualty scenario. The collected data is disseminated to all nodes in the network to make it available to the rescue team wherever they arrive. In particular, we show that the members of the most urgent cases found at each node are found to be very close to the set of the actual urgent cases.
Owner:UMM AL QURA UNIVERISTY
Zigbee wireless sensor network of master and slave tree types, construction method and routing protocol
InactiveCN101868041AScale upProlong survival timeEnergy efficient ICTNetwork topologiesRouting tablePoint counting
The invention discloses a Zigbee wireless sensor network of master and slave tree types, a construction method and a routing protocol. The method comprises the following steps of: dividing a whole network into a master network and a plurality of salve networks; forming the master network by using a master coordinator and related nodes; and constructing the plurality of salve networks by using peripheral isolated nodes and a plurality of routers in the master network serving as slave coordinators so as to construct the network with a master and slave tree type structure. The traditional tree type routing protocol is improved so that the routing protocol can be applied to the network of the master and slave tree types. The method has the advantages of enlarging the scale of the traditional tree type network, facilitating elimination of the isolated node number in the network, facilitating reduction of overhead of energy and memory of the routers caused by constructing a routing table and improving the survival time of the network by adopting the improved tree type routing protocol, and ensuring the compatibility with the primary protocol without any modification on the frame structure of the primary Zigbee protocol.
Owner:NANJING HANZHIXIAN ELECTRONICS TECH
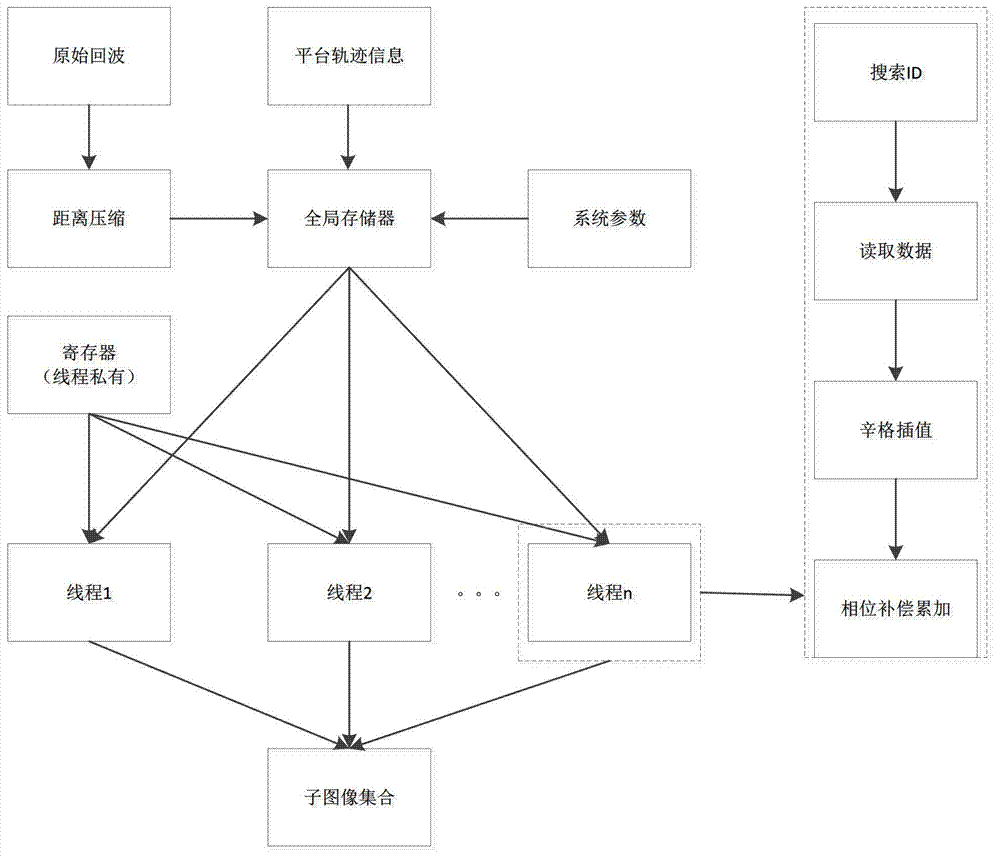
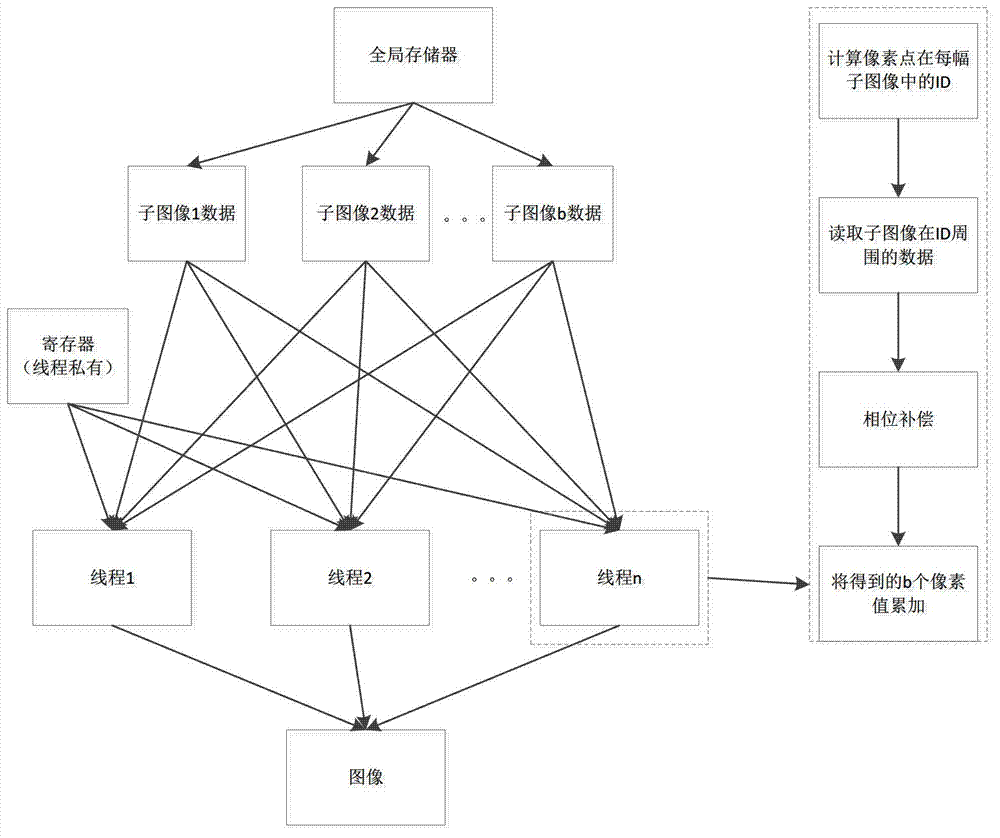
Imaging method of bistatic SAR (synthetic aperture radar) based on GPU (graphics processing unit) back projection
InactiveCN102854507AEnables fast imagingReduce memory overheadRadio wave reradiation/reflectionSynthetic aperture radarInverse synthetic aperture radar
The invention discloses an imaging method of a bistatic SAR (synthetic aperture radar) based on GPU (graphics processing unit) back projection. Classification parameters of traditional rapid factorization back projection are optimized and imaging processing efficiency is improved compared with the traditional rapid factorization back projection. Imaging tasks are divided into a plurality of unrelated subtask groups to facilitate parallel processing of the subtask groups by a GPU, and processing unit is improved again through novel parallel strategies. Compared with existing bistatic SAR imaging methods, advantages, such as low internal memory overhead and easy motion compensation, of time domain methods are kept, fast imaging with large data throughput of the bistatic SAR is achieved, processing efficiency is also improved greatly, and high-quality imaging is achieved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
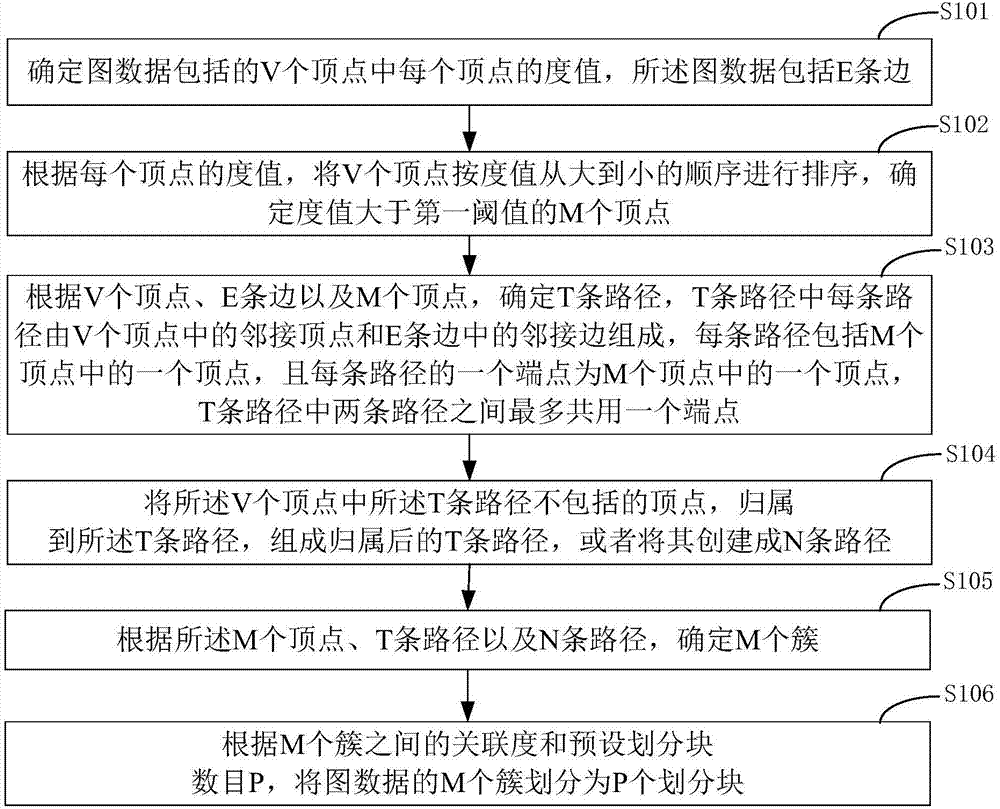
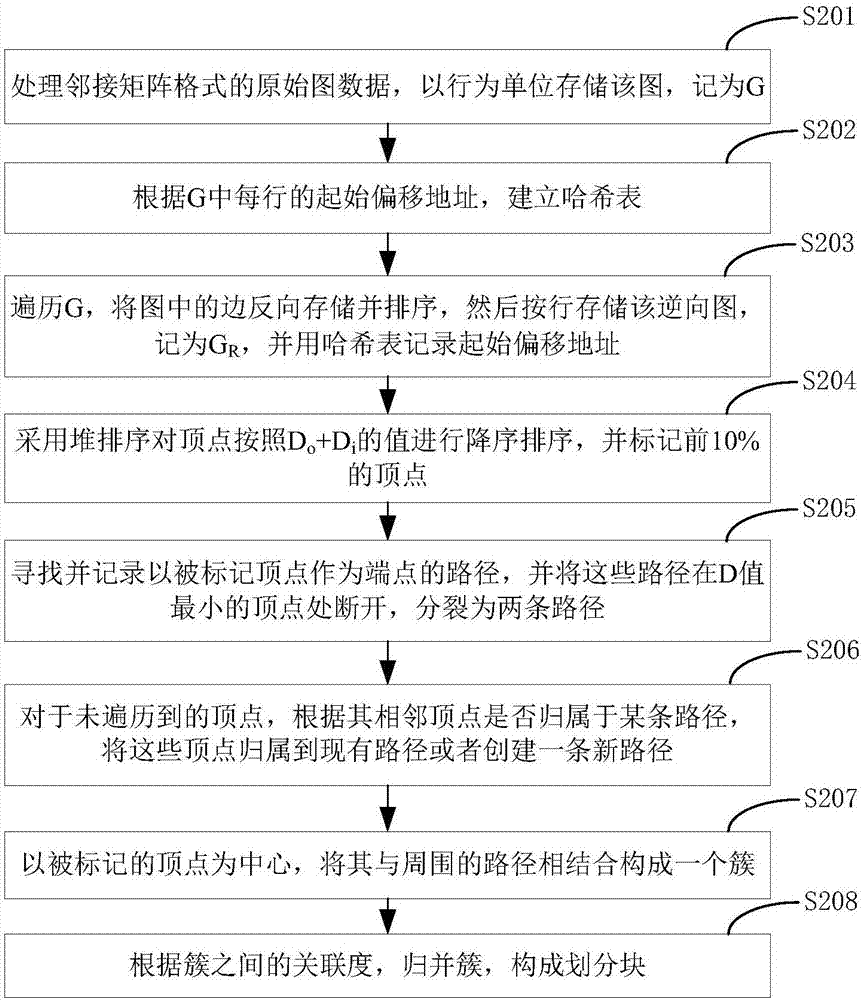
Cluster-based graph data division method
InactiveCN107193896AReduce memory overheadMaintain integritySpecial data processing applicationsCluster basedAlgorithm
The invention discloses a cluster-based graph data division method. The method comprises the steps of determining a degree value of each vertex in V vertexes comprised in graph data, wherein the graph data comprises E edges; according to the degree value of each vertex, sorting the V vertexes according to a degree value sequence from big to small, and determining M vertexes with the degree values greater than a first threshold; according to the V vertexes, the E edges and the M vertexes, determining T paths; attributing the vertexes which T paths do not comprise in the V vertexes to the T paths, forming the T paths after the attribution, or creating N paths by the T paths; according to the M vertexes, the T paths and the N paths, determining M clusters; and according to an association degree among the M clusters and a preset divided block number P, dividing the M clusters of the graph data into P divided blocks. According to the method, the vertexes with the relatively big degree values serve as end pintos of the paths, so that the repetition rate of graph data division can be reduced; the graph scale is reduced by taking the paths as units, so that the memory overhead is reduced; and large-scale graph data can be processed.
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for space-efficient multi-pattern matching
ActiveCN104881439AReduce memory requirementsSolve space problemsSpecial data processing applicationsHash functionPattern matching
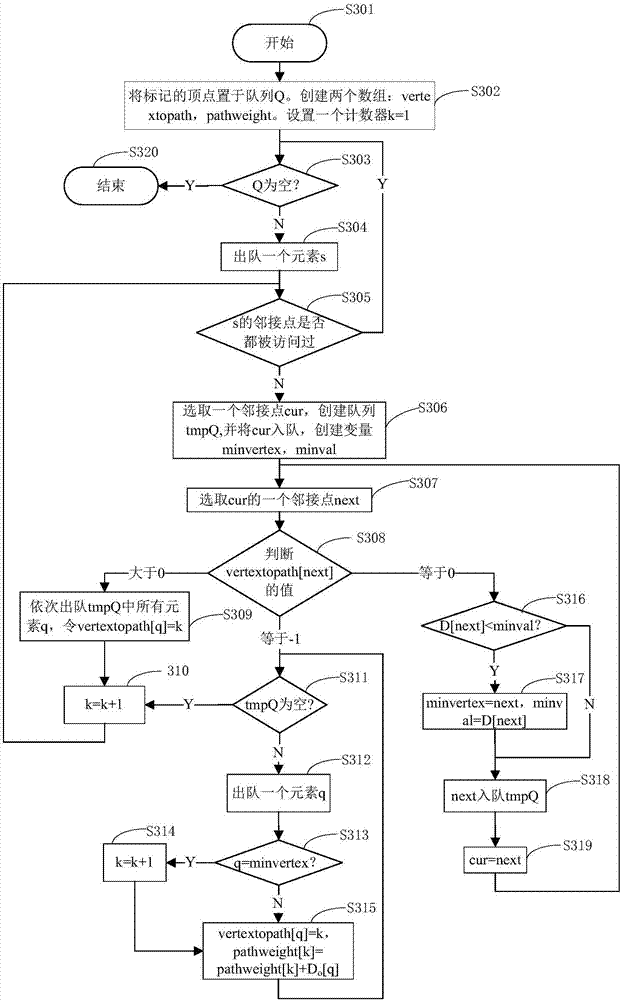
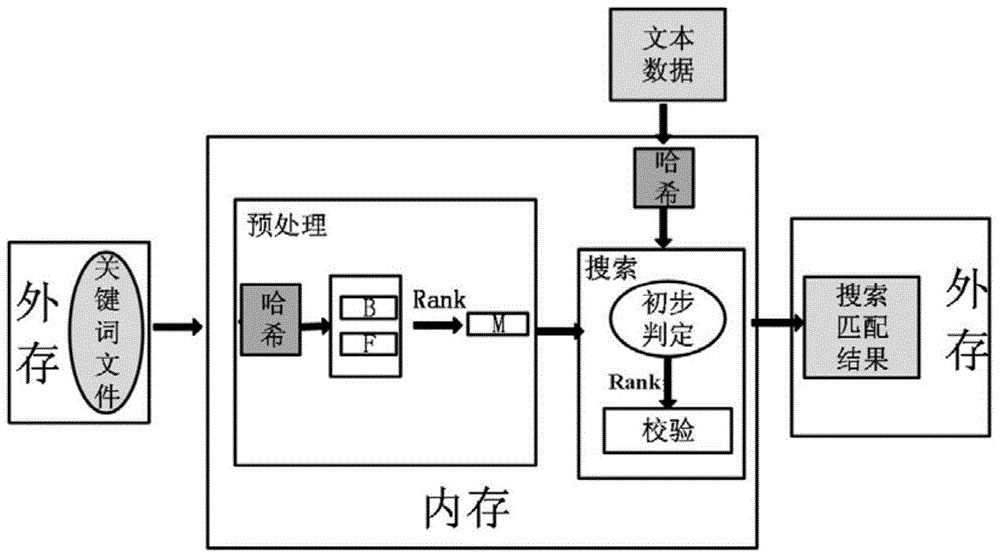
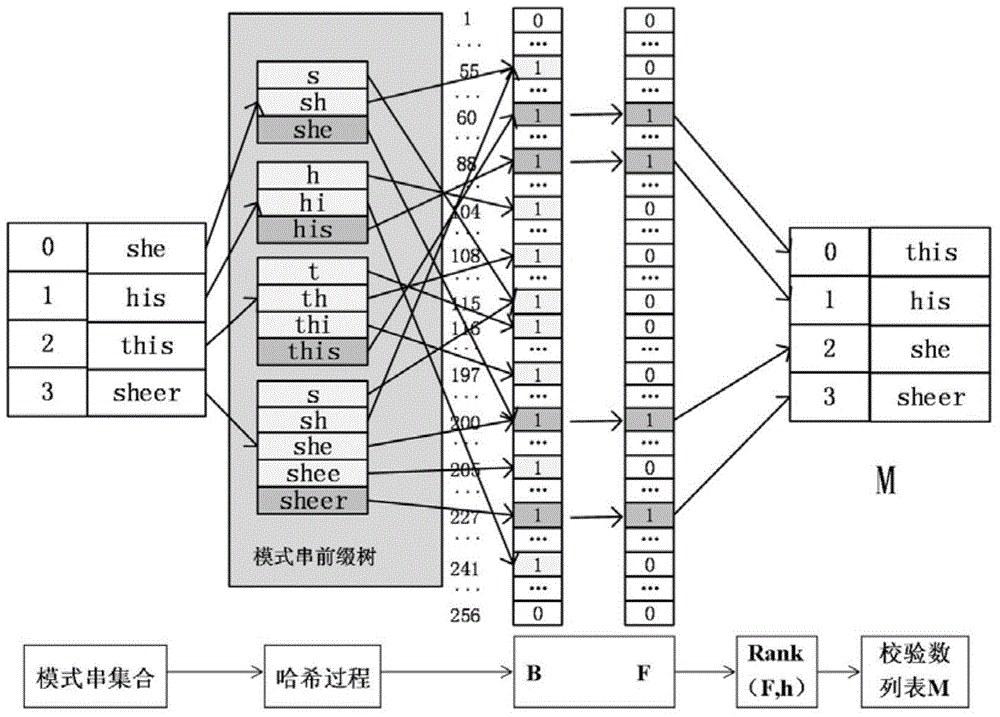
The invention relates to a method and a system for space-efficient multi-pattern matching. Firstly, a novel data structure HashTrie for storing pattern string is proposed, in which an original pattern string matrix is stored in the form of one-dimensional table by using a bit vector table, thus avoiding the problem of state transition matrix of conventional method memory automations; resolving the special bit vector table by using the method of recursive Hash function so as to save memory space; in the process of calculating the Hash function, converting the Hash function into a simple and efficient bit operation by using bit operation; the adoption the Rank technology in HashTrie construction and key word searching increases space and time efficiency of search. The method and system herein markedly reduce memory overhead and pretreatment time, can meet the need of timelessness as required by a real-time intrusion detection system as for when rules come into effect, and is more suitable for handling multi-pattern real-time matching which features in comparatively large scale of pattern string collection and comparatively short length of pattern string.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Cache stashing processor control messages
InactiveUS7774522B2Extra memory accessImprove execution performanceMemory systemsInput/output processes for data processingEmbedded systemPeripheral
A system and method have been provided for pushing cacheable control messages to a processor. The method accepts a first control message, identified as cacheable and addressed to a processor, from a peripheral device. The first control message is allocated into a cache that is associated with the processor, but not associated with the peripheral device. In response to a read-prompt the processor reads the first control message directly from the cache. The read-prompt can be a hardware interrupt generated by the peripheral device referencing the first control message. For example, the peripheral may determine that the first control message has been allocated into the cache and generate a hardware interrupt associated with the first control message. Then, the processor reads the first control message in response to the hardware interrupt read-prompt. Alternately, the read-prompt can be the processor polling the cache for pending control messages.
Owner:MACOM CONNECTIVITY SOLUTIONS LLC
Method for reducing random access memory (RAM) expense in abrasion balanced processing
ActiveCN103092770AReduce memory overheadSave memoryMemory adressing/allocation/relocationRedundant data error correctionError correctingComputer science
The invention discloses a method for reducing random access memory (RAM) expense in abrasion balanced processing. The method comprises the steps of establishing an abrasion balanced table, recording error correction digits of each available block and error correcting codes of each available block in an NAND flash memory, updating the abrasion balanced table in NAND flash memory operation, and preferentially using the available block with less error correction digits in the abrasion balanced processing. According to the method, the RAM expense can be effectively reduced in abrasion balance.
Owner:SHANDONG SINOCHIP SEMICON
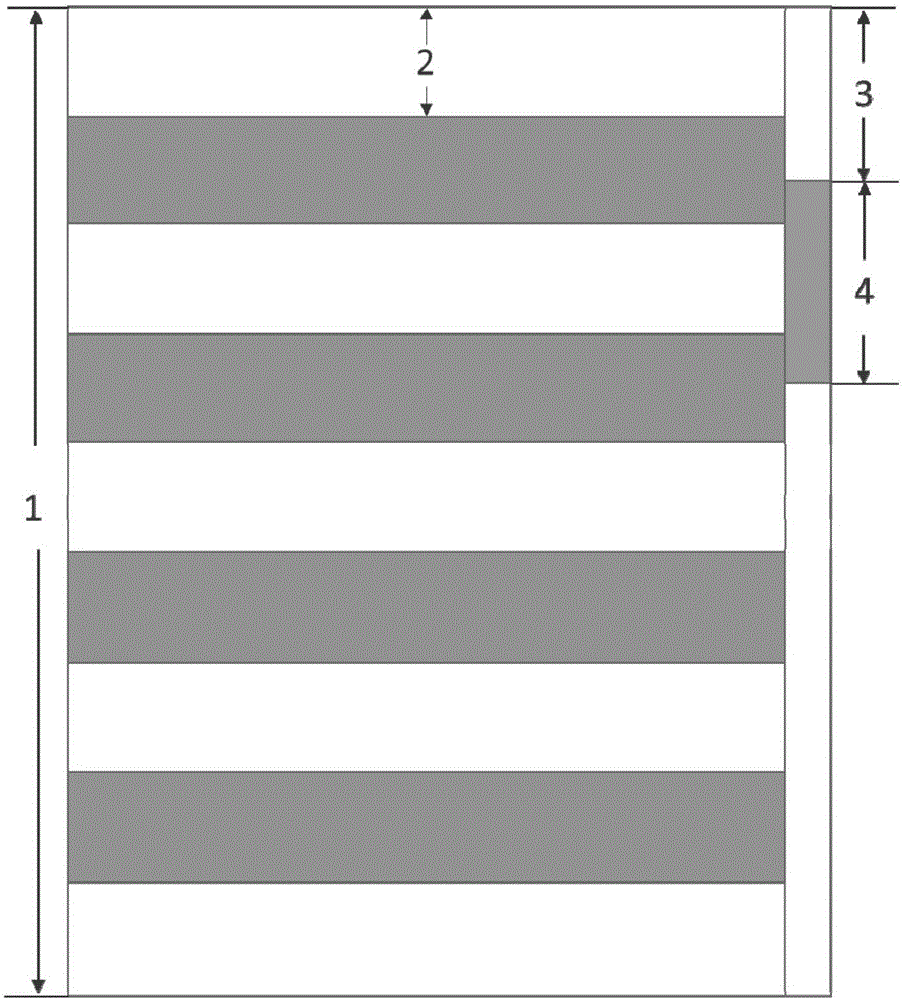
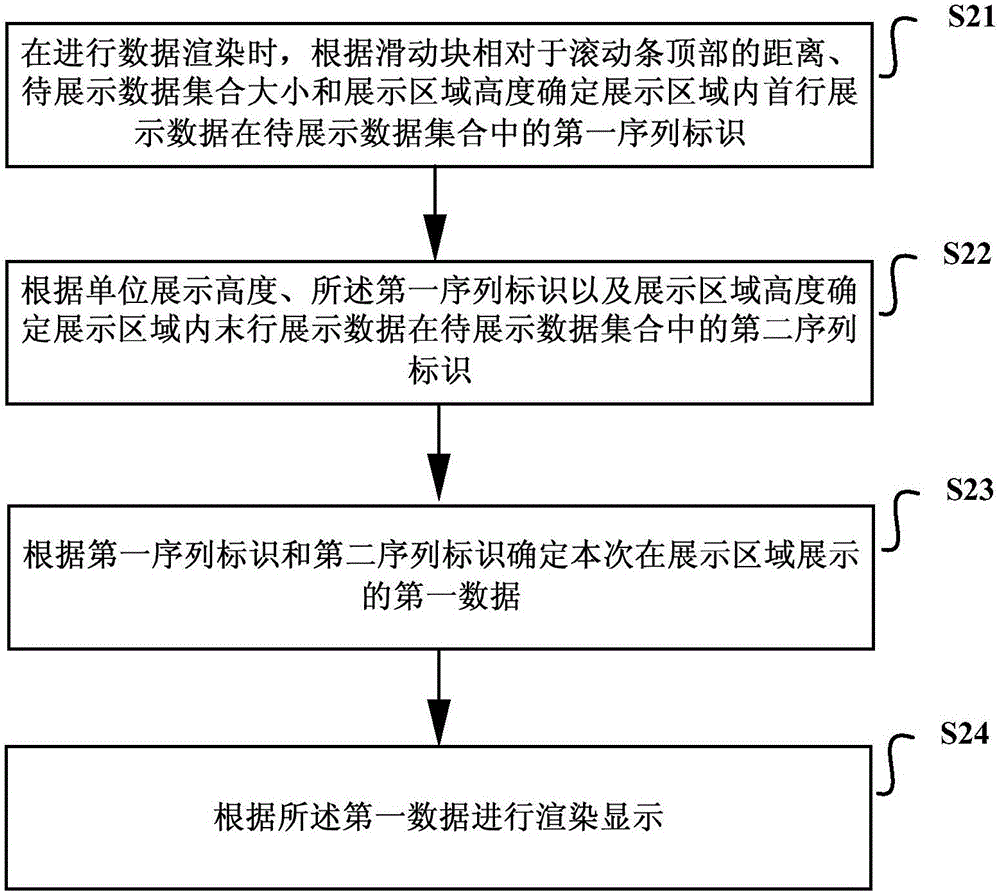
Data rendering method and device
ActiveCN106570142AImprove experienceImprove accuracySpecial data processing applicationsData displayData set
The invention discloses a data rendering method and device. The method comprises following steps: when data rendering is carried out, a first sequence identification of first row display data in a data set to be displayed within a display area is determined according to the relative distance between a slide block and a scroll bar top part, the size of the data set to be displayed and the height of the display area; a second sequence identification of terminal row display data in the data set to be displayed within the display area is determined according to the unit height of displaying, the first sequence identification and the height of the display area; first data displayed in the display area this time is determined according to the first sequence identification and the second sequence identification. Rendering display is carried out according to the first data; by means of the method of the invention, as little DOM nodes as possible are adopted to render massive data, which saves memory consumption and increases user experience.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +2
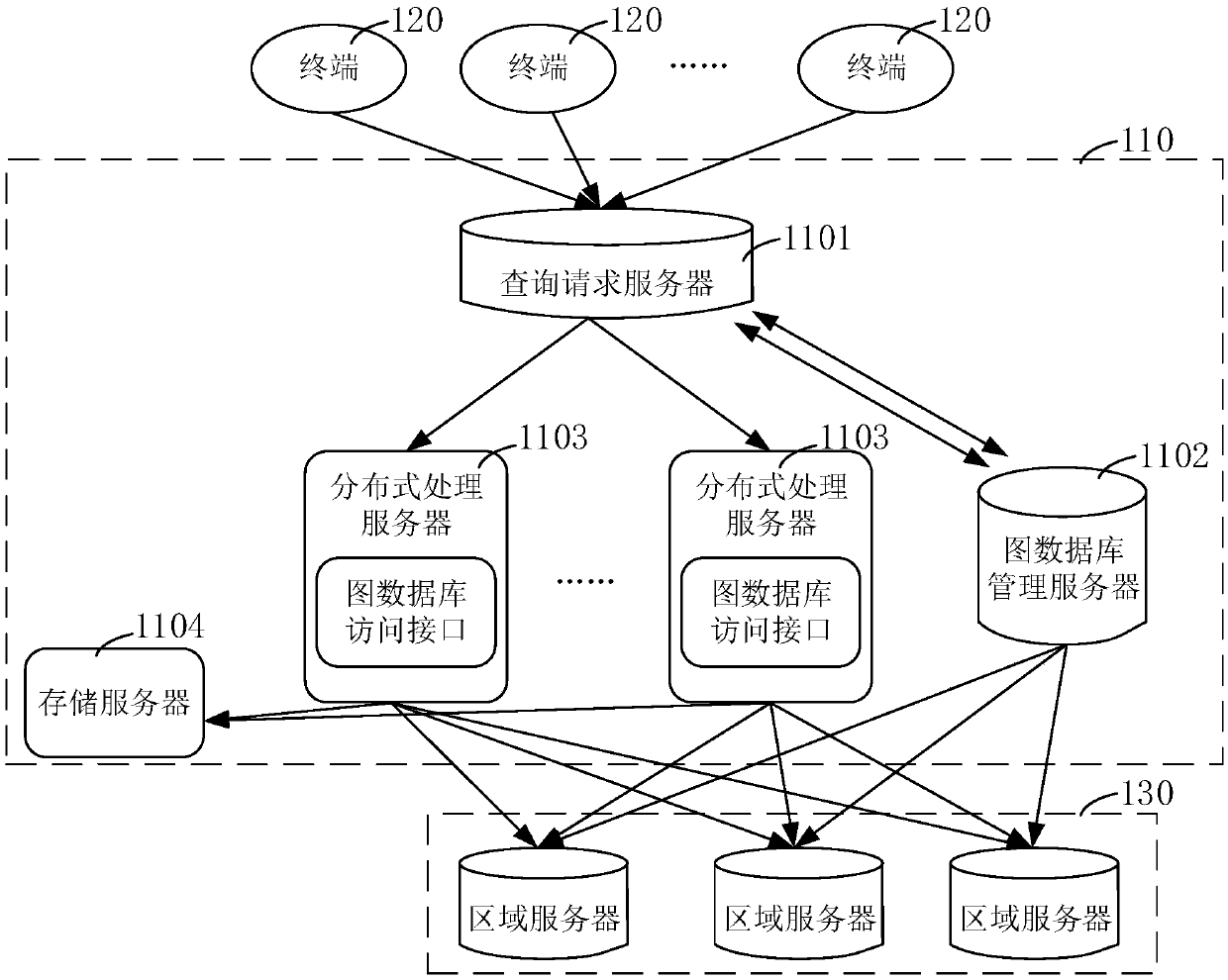
Graph database query method and system, computer equipment and readable storage medium
ActiveCN110309334AImprove query efficiencyReduce time consumptionStill image data indexingMetadata still image retrievalData miningMetadata
The invention relates to a graph database query method and system, computer equipment and a readable storage medium. The method comprises the following steps: a query request server receives at leastone query condition sent by a terminal, analyzes each query condition, obtains an analysis result, and sends the analysis result to a graph database management server; the graph database management server obtains corresponding metadata according to the analysis result and sends the metadata to the query request server; the query request server receives the metadata, generates query requests corresponding to the query conditions according to the metadata, and then distributes the query requests to the distributed processing server; and the distributed processing server calls a pre-configured graph database access interface and queries the graph database according to the distributed query request to obtain a query result. According to the method, the query response time and memory overhead of the graph database management server are saved, and the query efficiency of the graph database is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
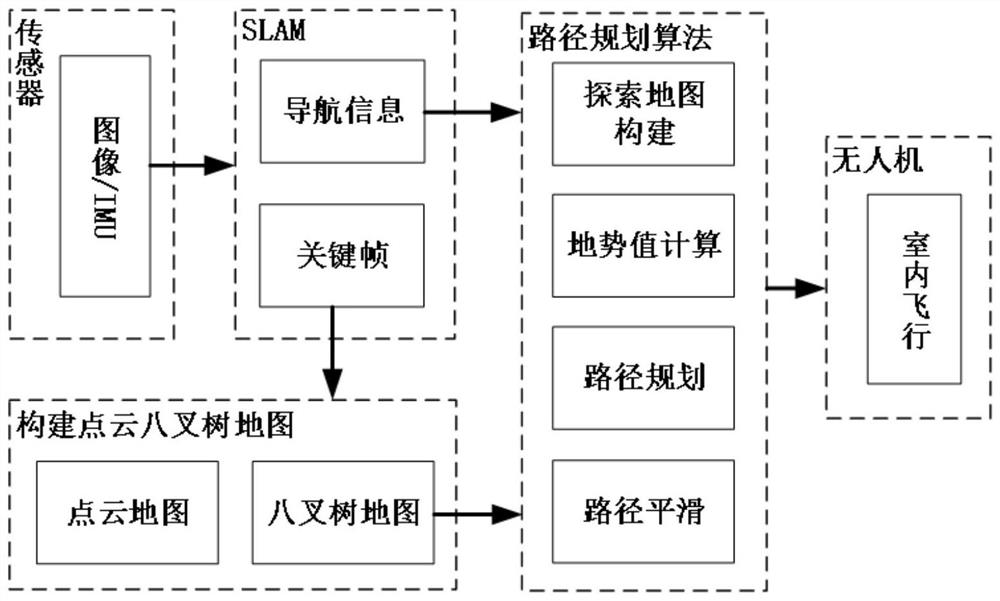
Vision-based indoor unmanned aerial vehicle path planning method
ActiveCN112747736AStrong real-timeReduce memory overheadImage enhancementImage analysisPoint cloudUncrewed vehicle
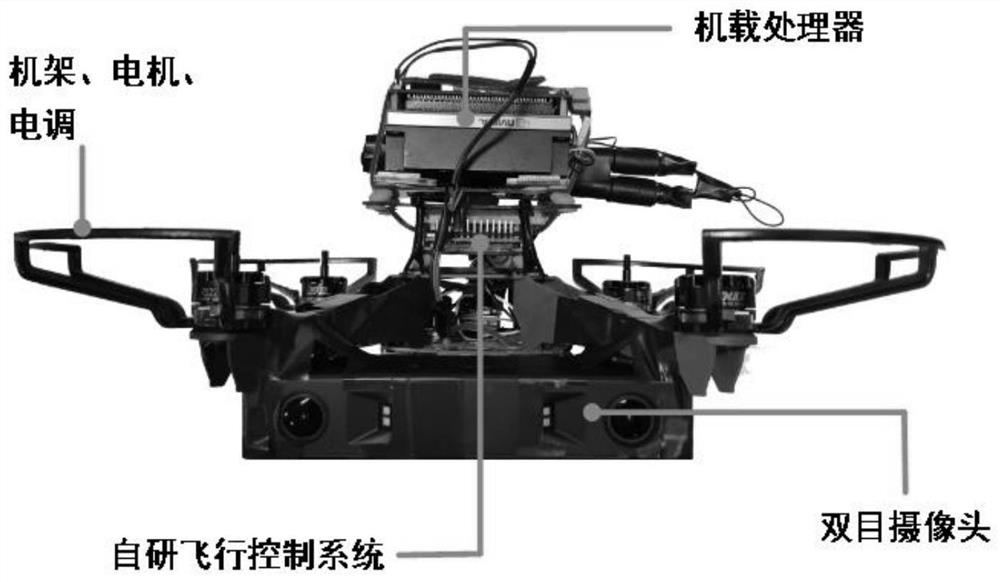
The invention discloses a vision-based indoor unmanned aerial vehicle path planning method, which comprises the following steps of: firstly, constructing a point cloud map, and then carrying out point cloud filtering and downsampling to improve the precision of the point cloud map; then constructing an octree map and an exploration map, and carrying out terrain value calculation; then planning a real-time path, finally forming an exploration map required by the real-time path planning through the construction of the map, and ensuring the correctness of a path planning algorithm through the conversion of the position and the path point of the unmanned aerial vehicle between a navigation coordinate system and an exploration map coordinate system; and finally, conducting real-time path smoothing. The method has the advantages of small calculation amount, high real-time performance, capability of unknown environment exploration and path planning at the same time and the like. Precise local path planning can be carried out in an explored area, and global path direction guidance can be carried out in an unexplored area; and rapid response to sudden obstacles can be realized.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com