Patents
Literature
914results about How to "Reduce memory requirements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
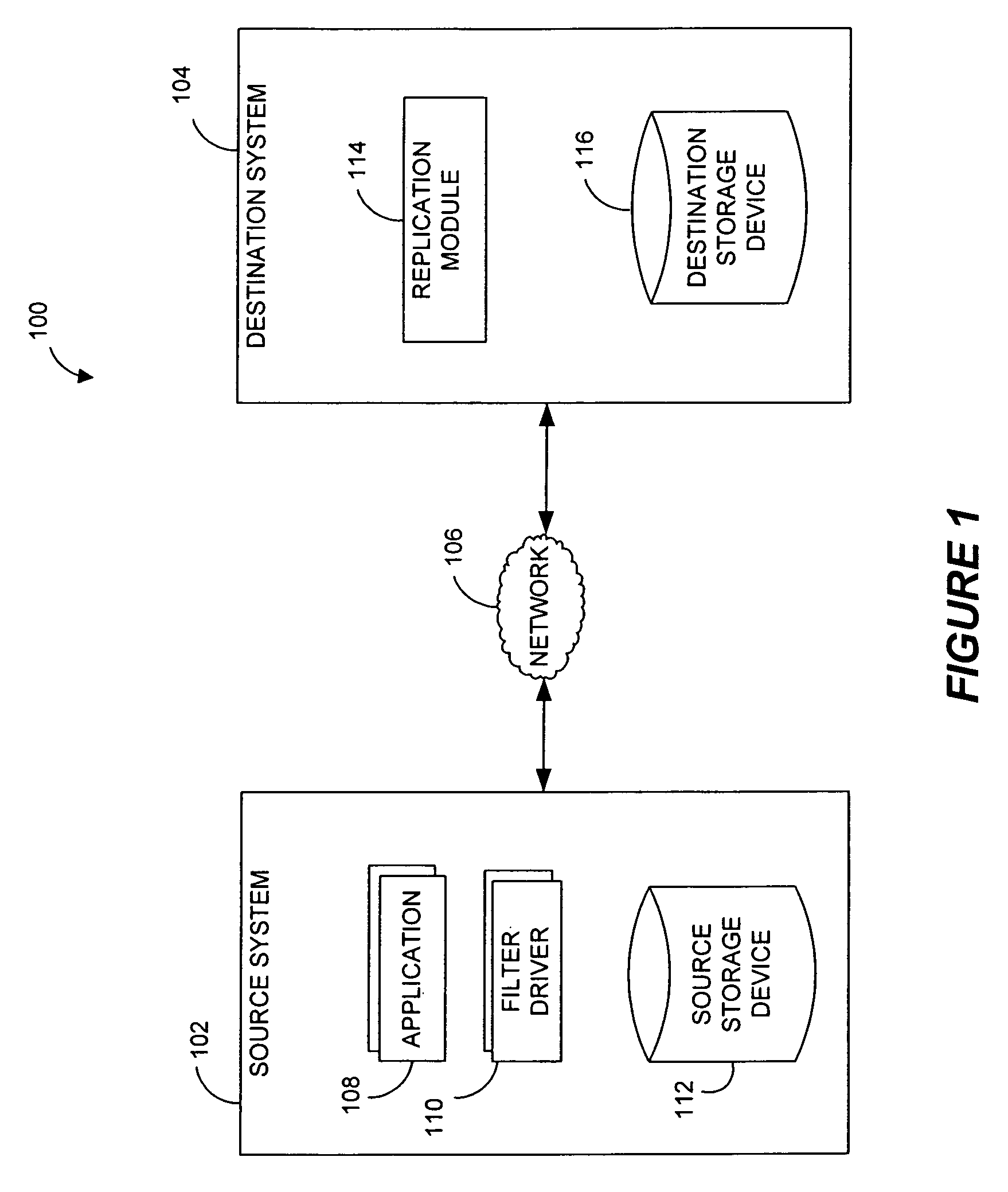
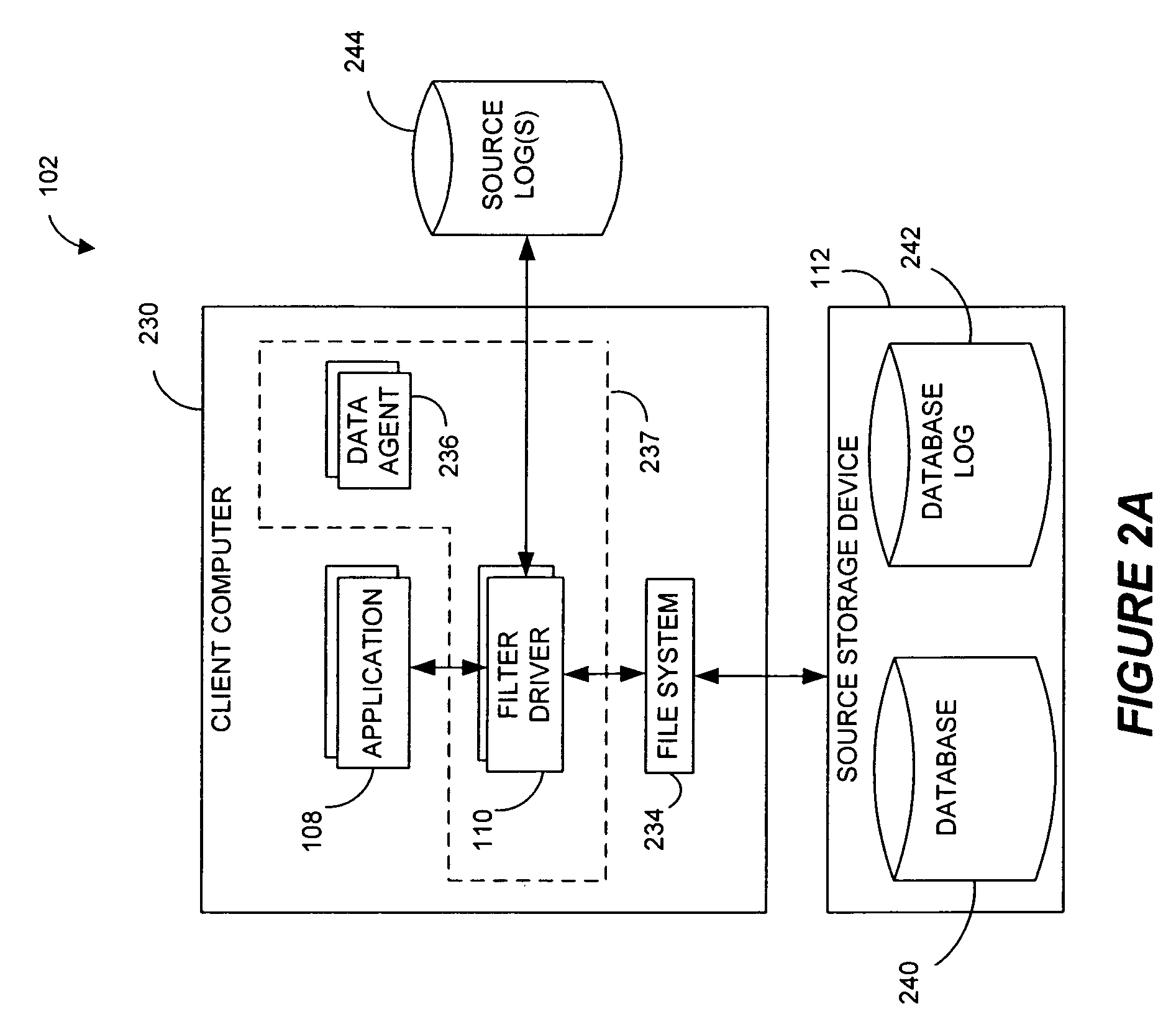
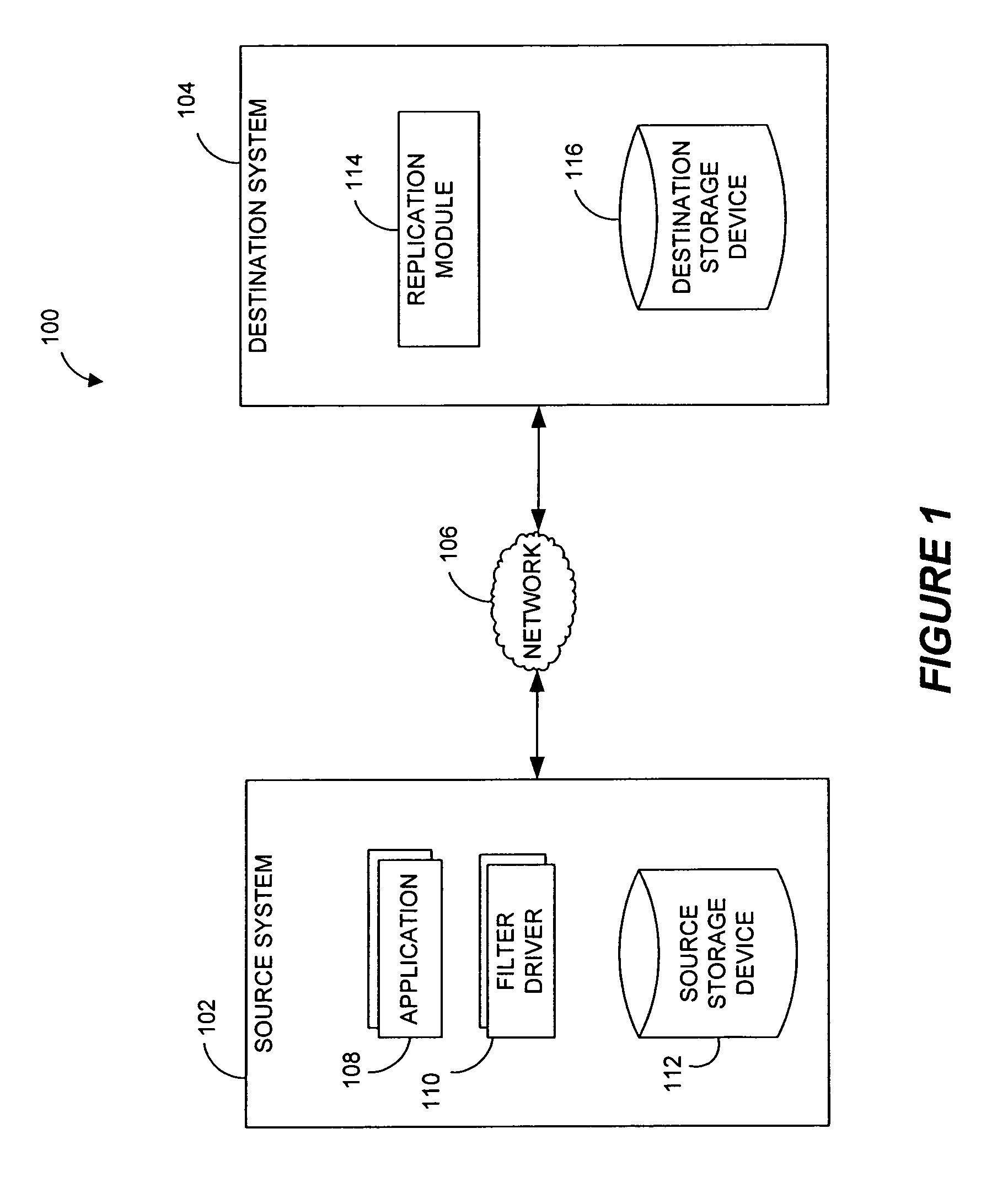
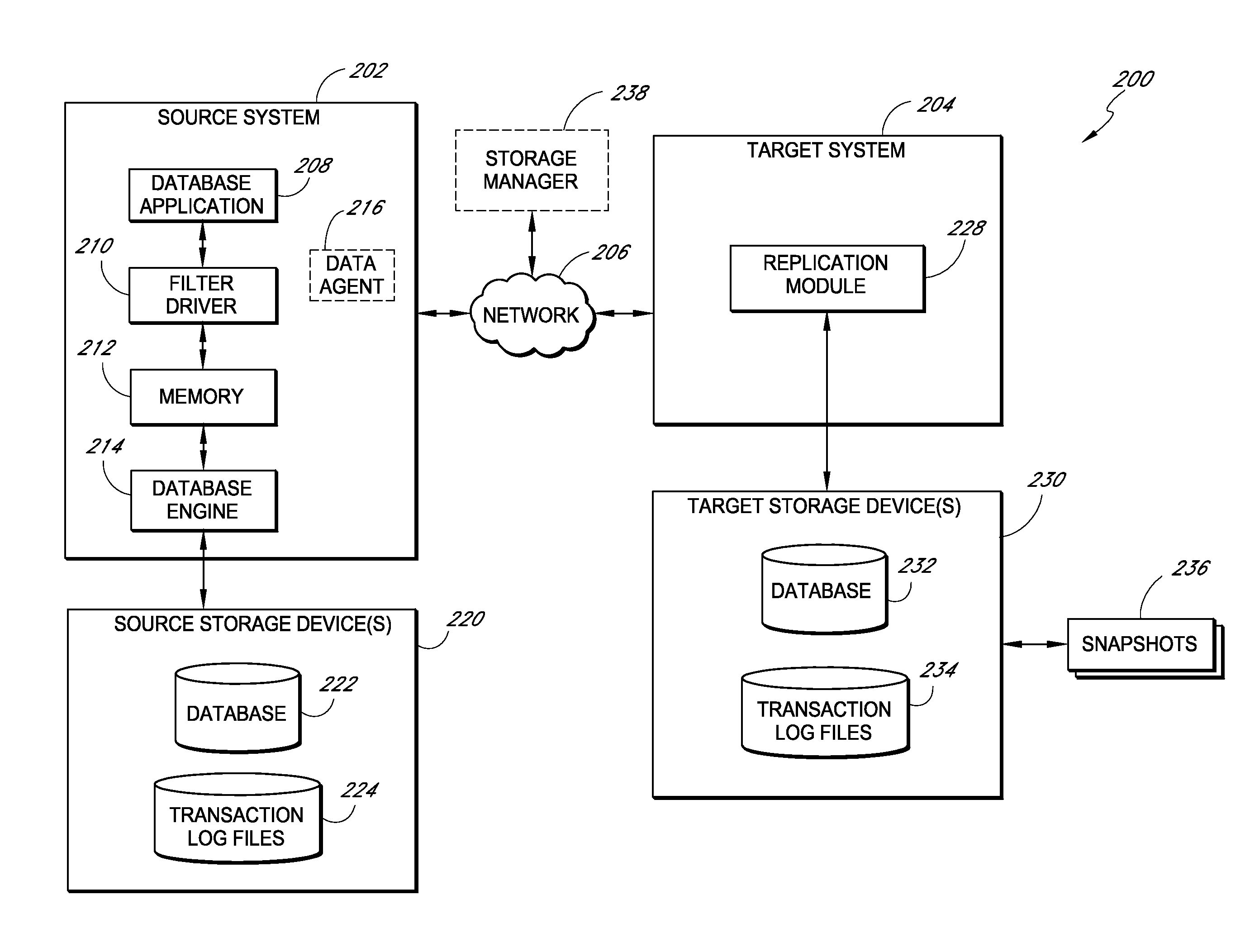
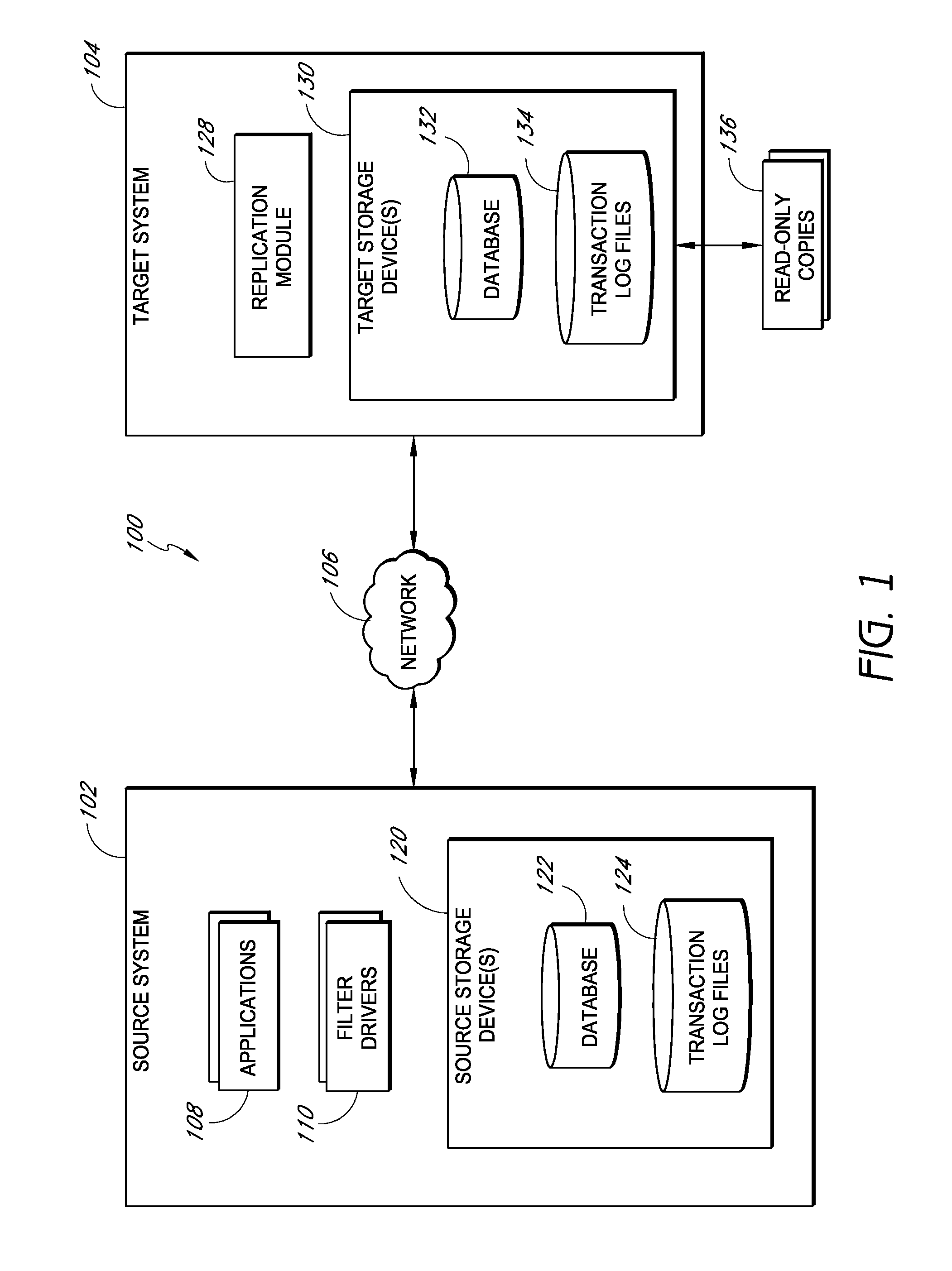
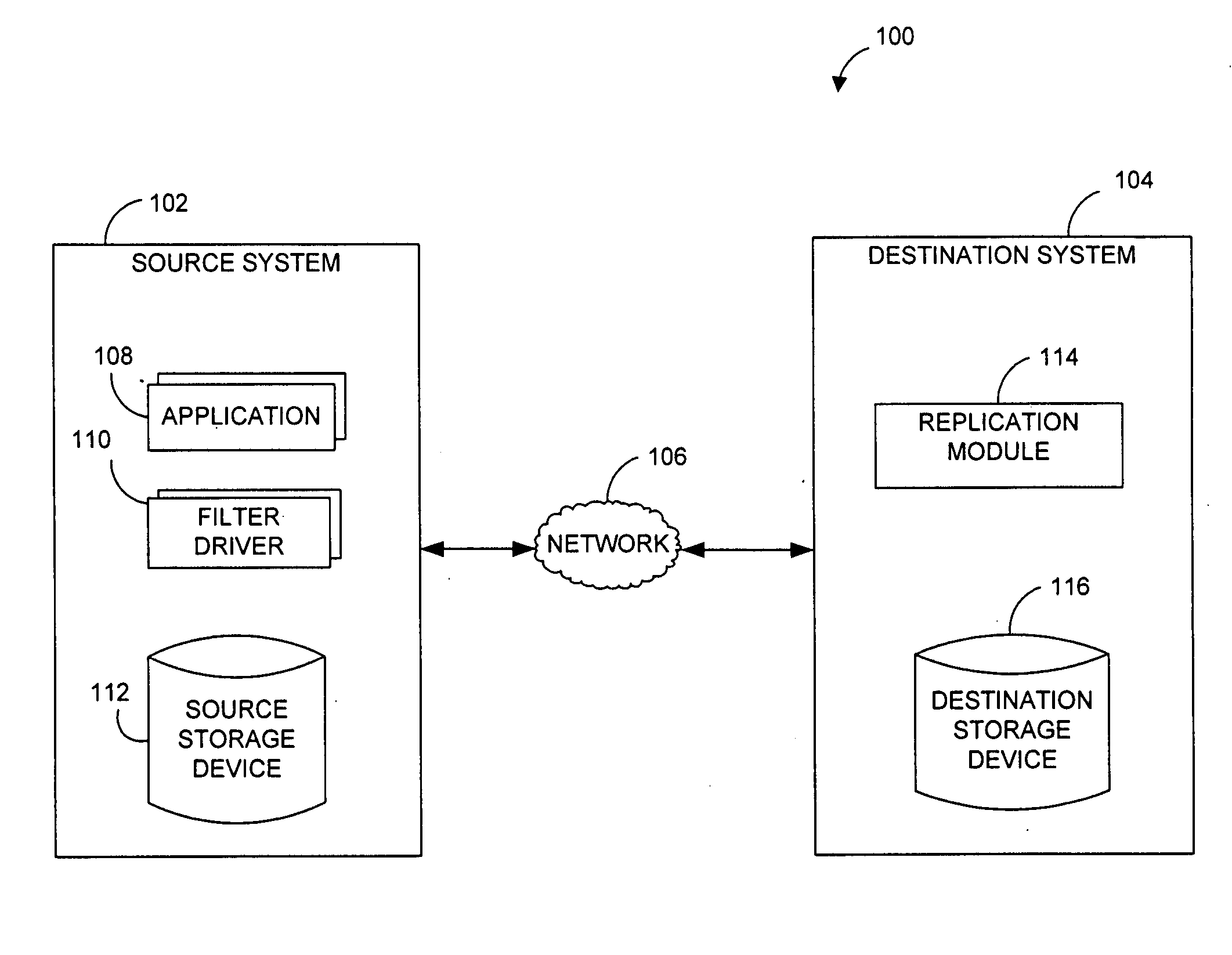
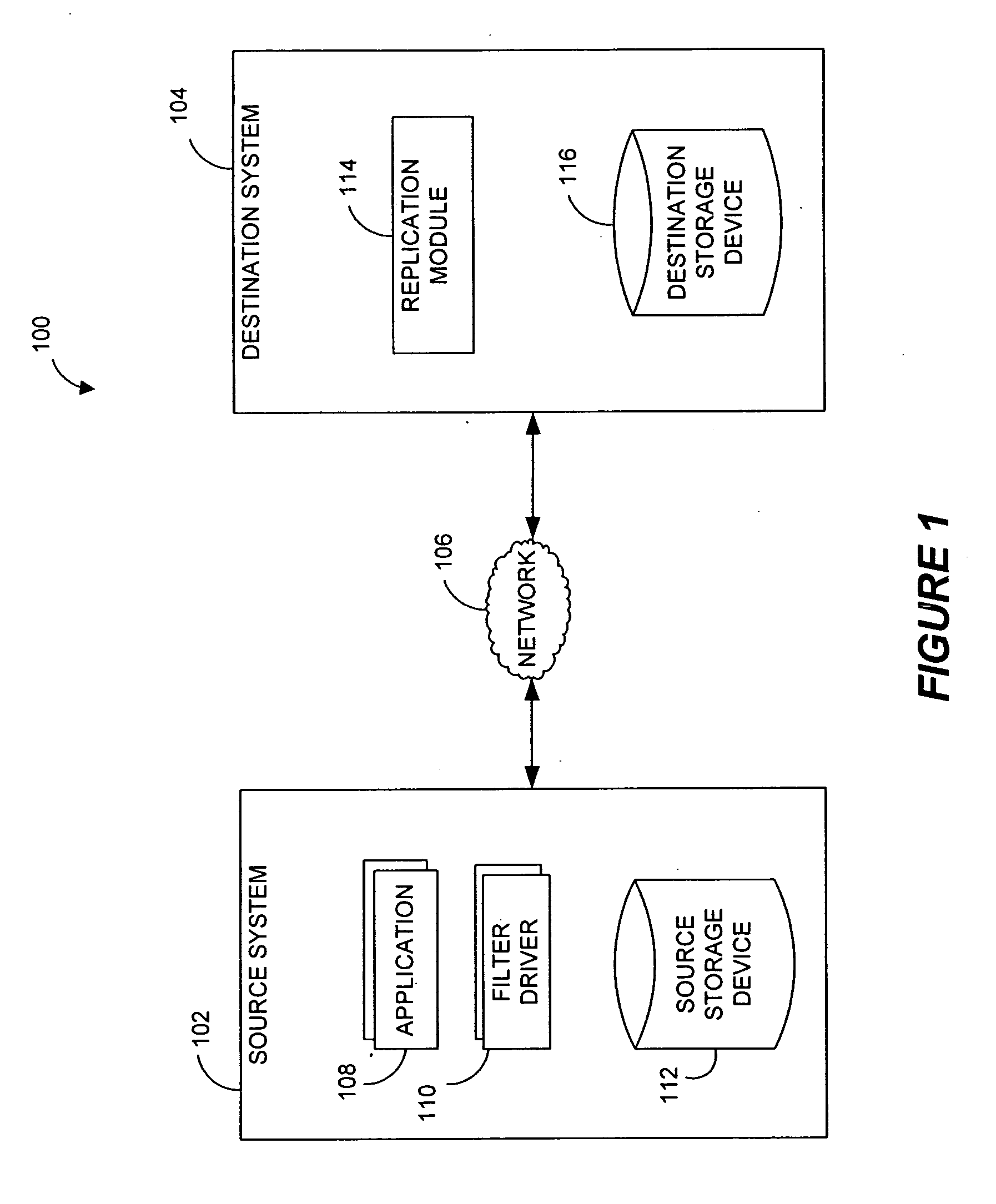
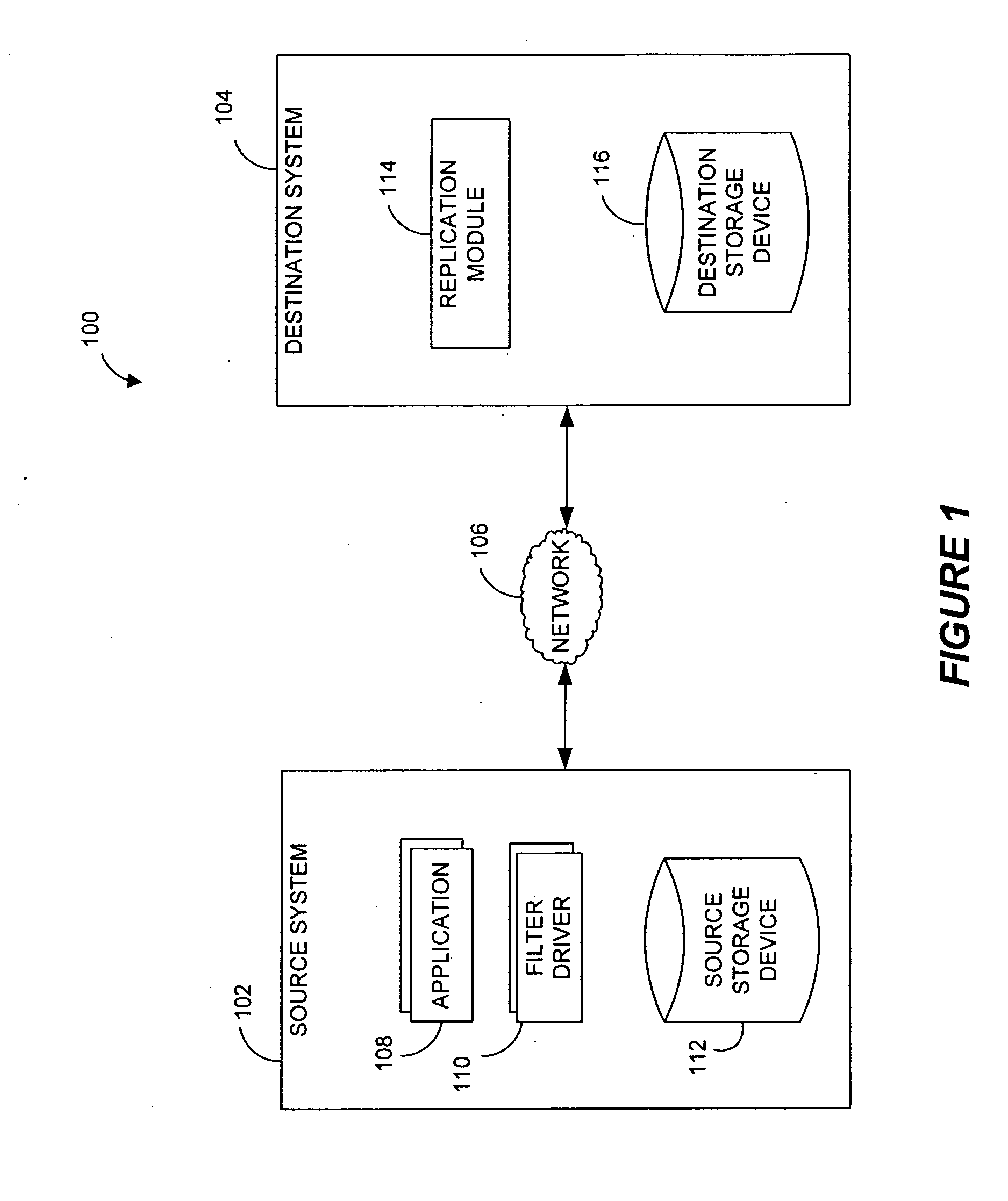
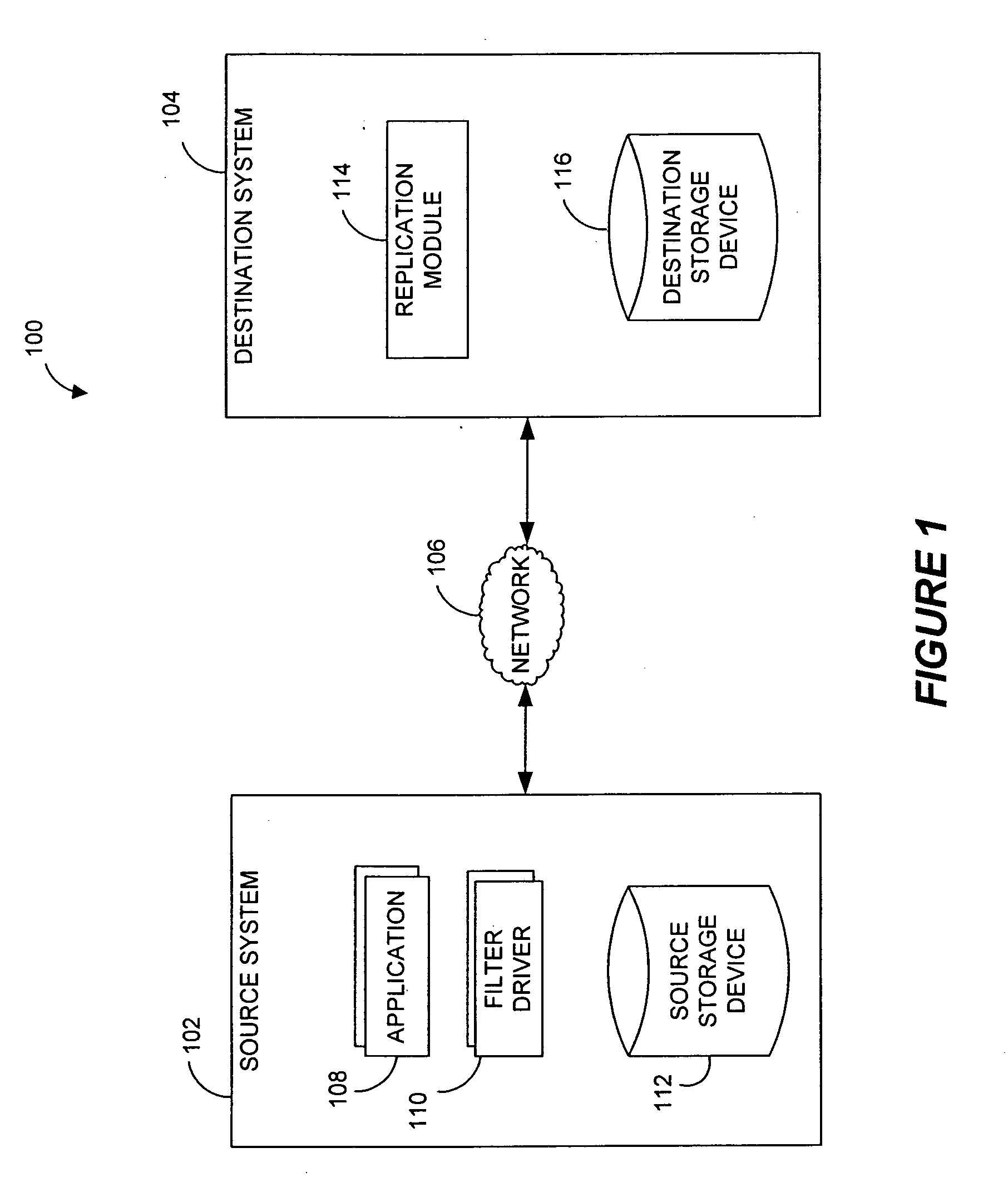
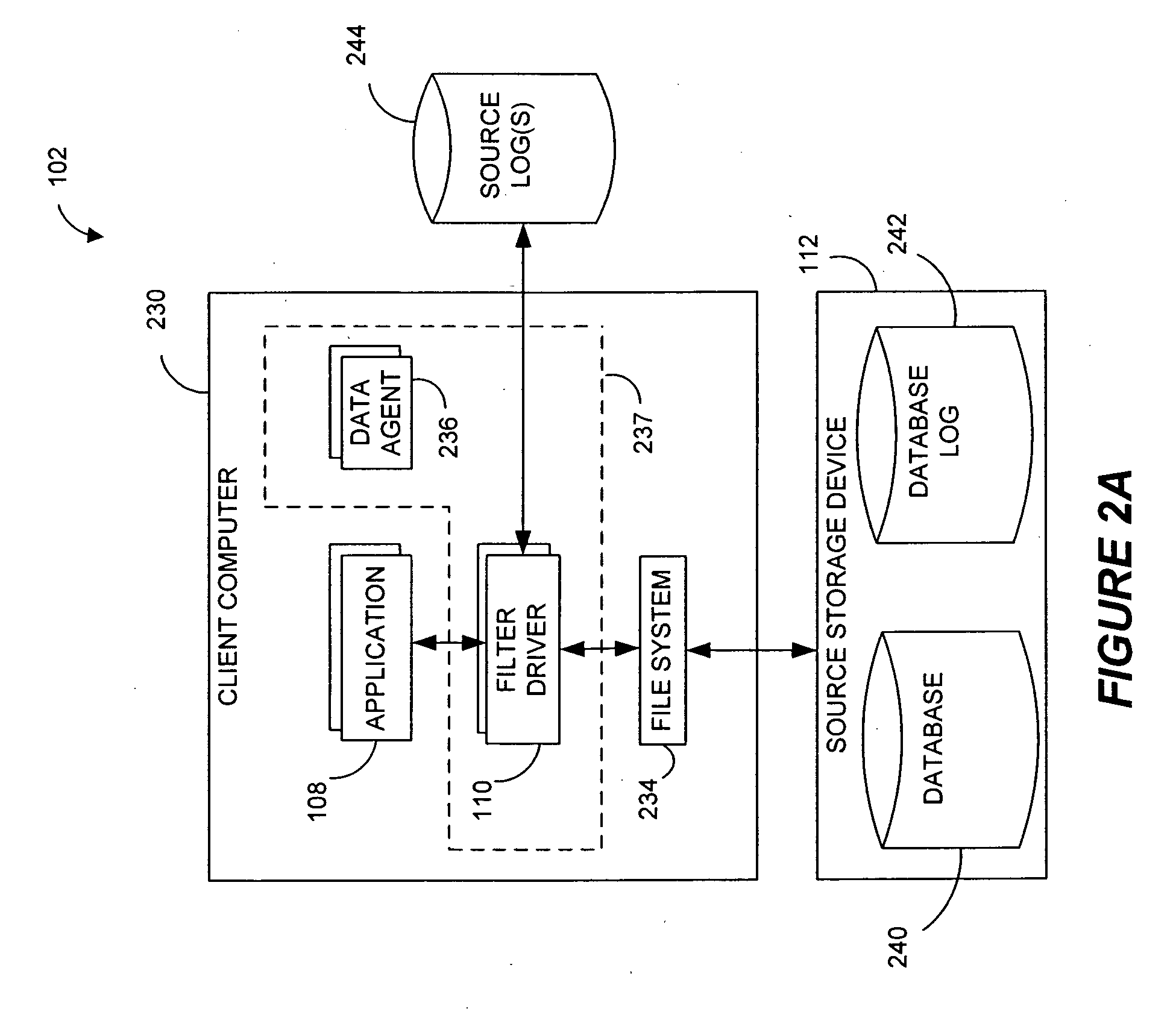
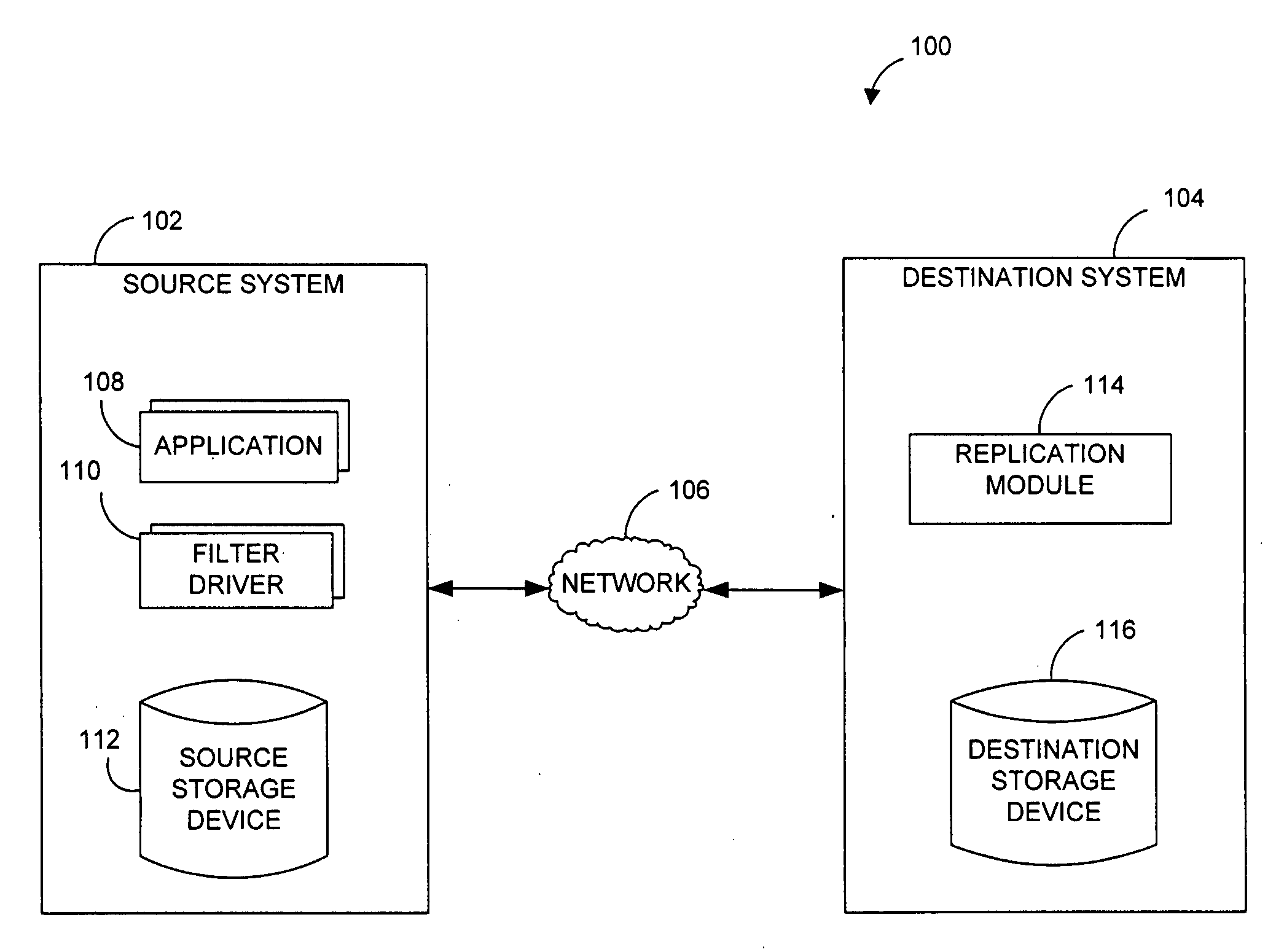
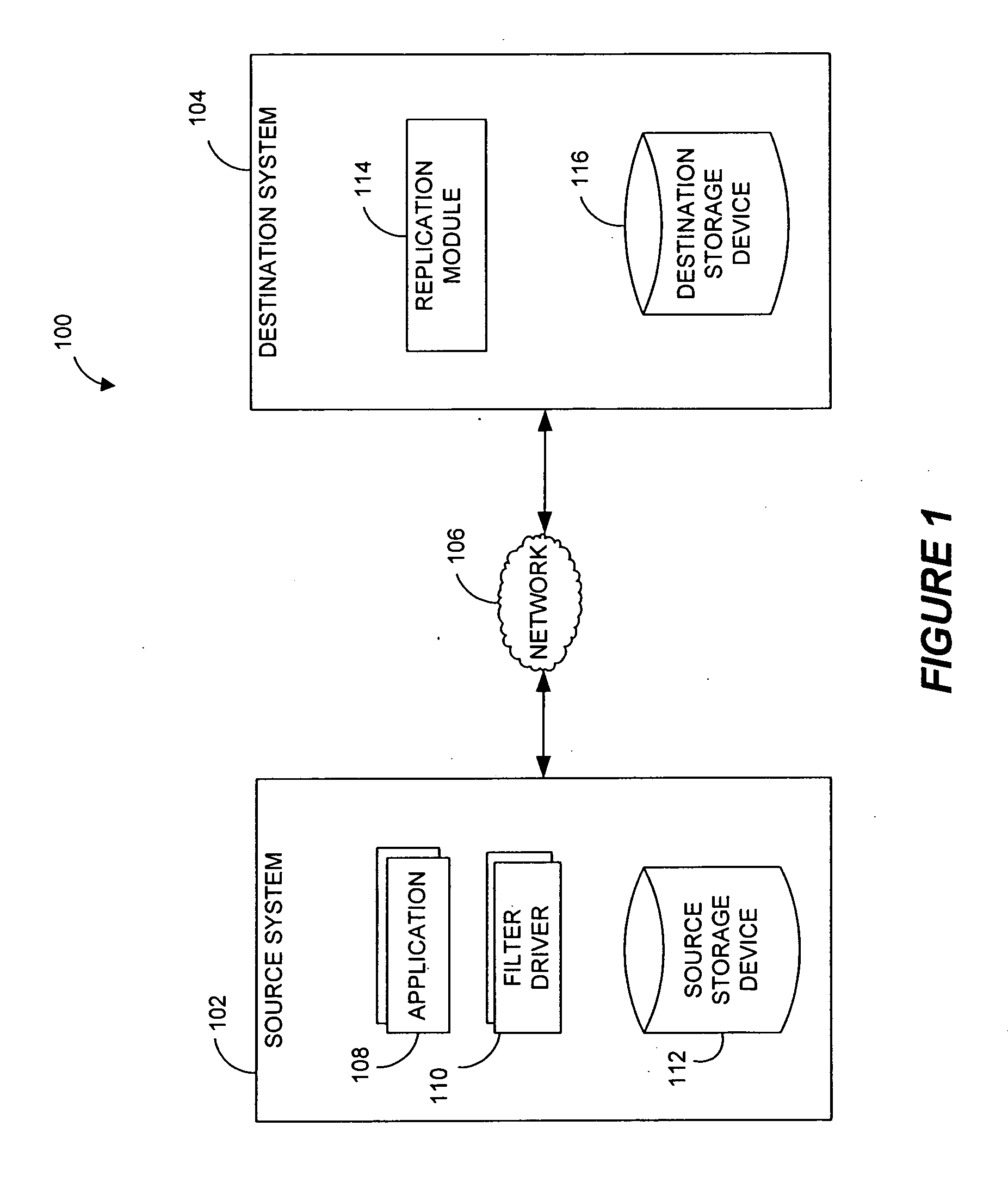
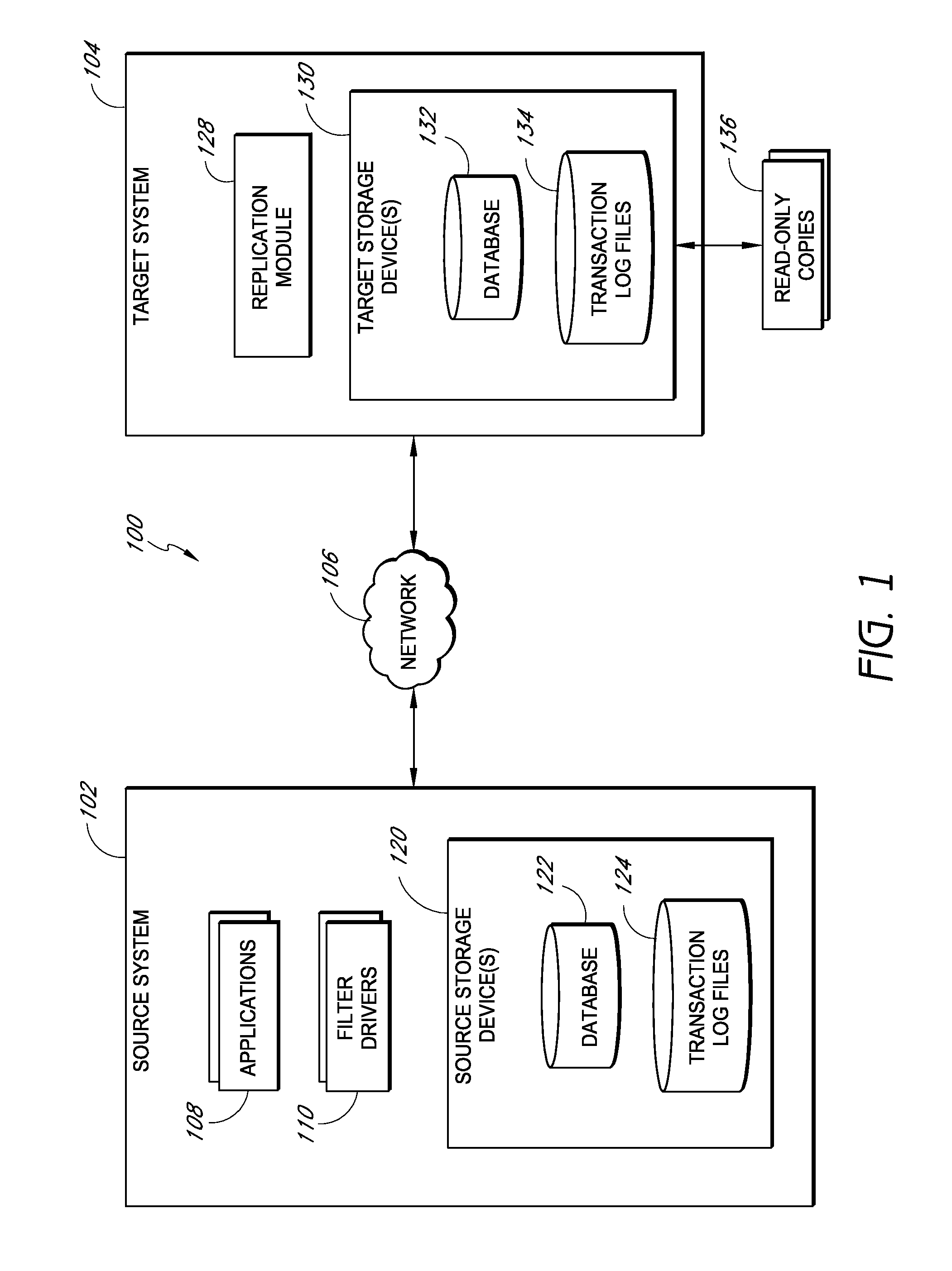
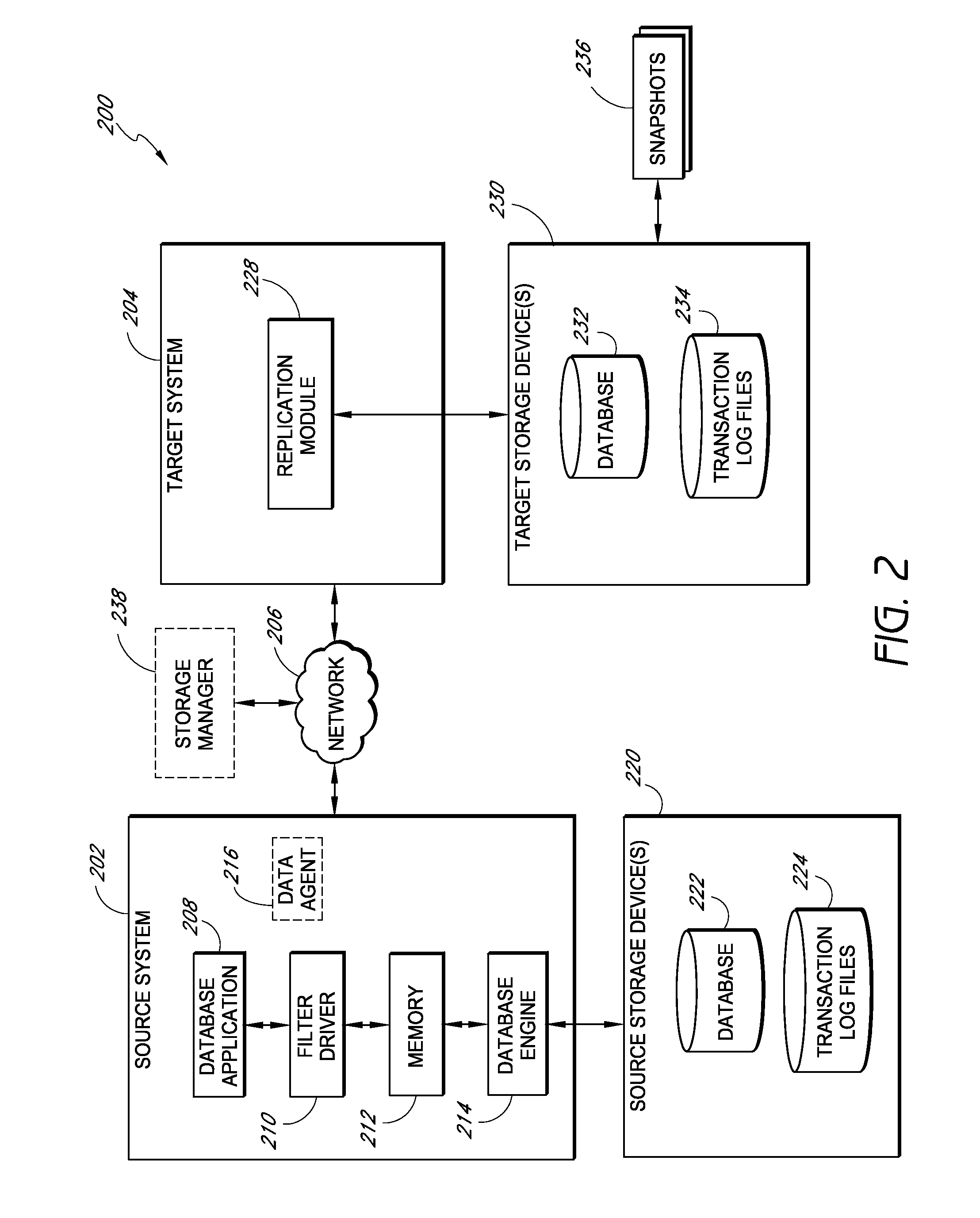
Systems and methods for monitoring application data in a data replication system
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
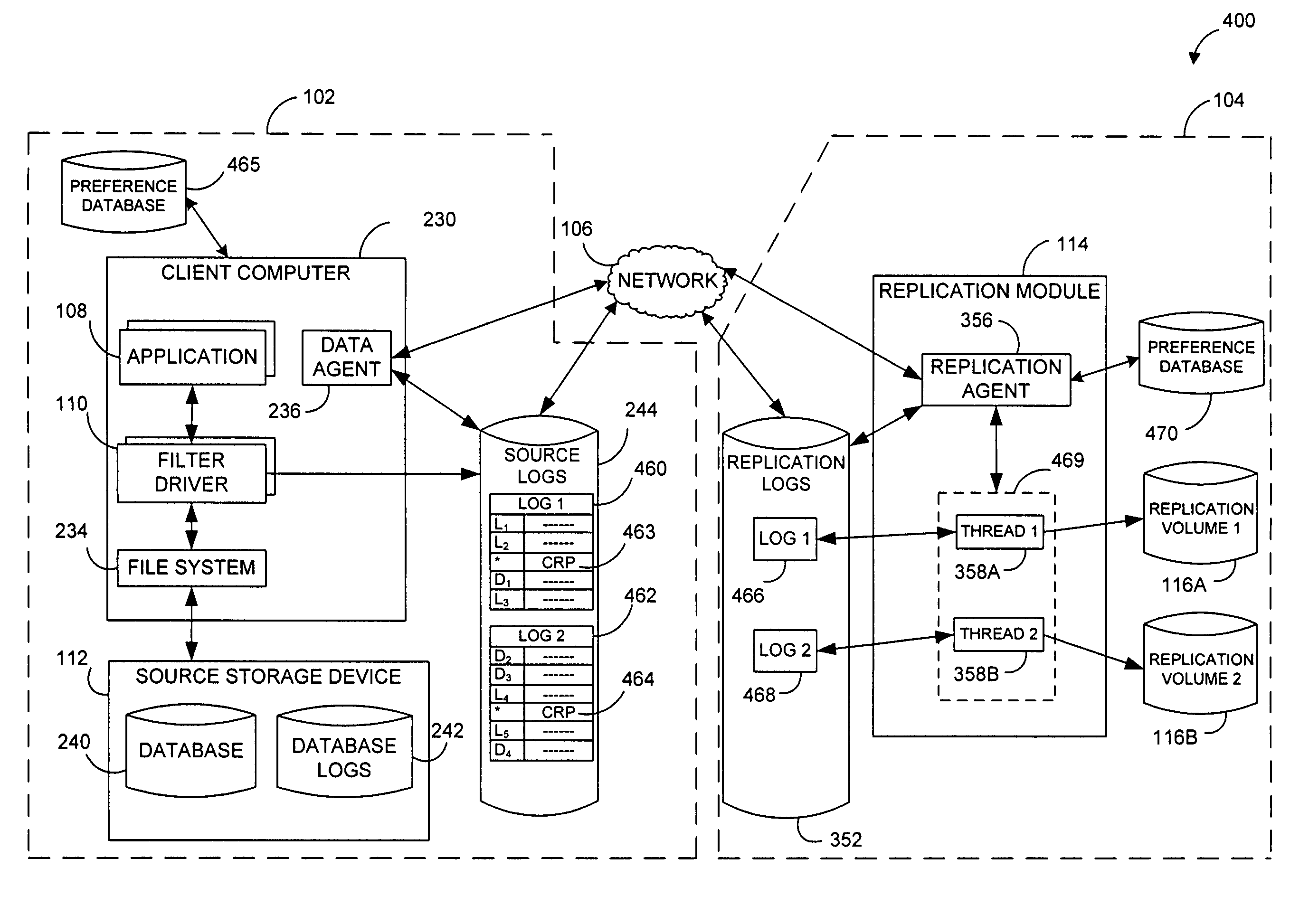
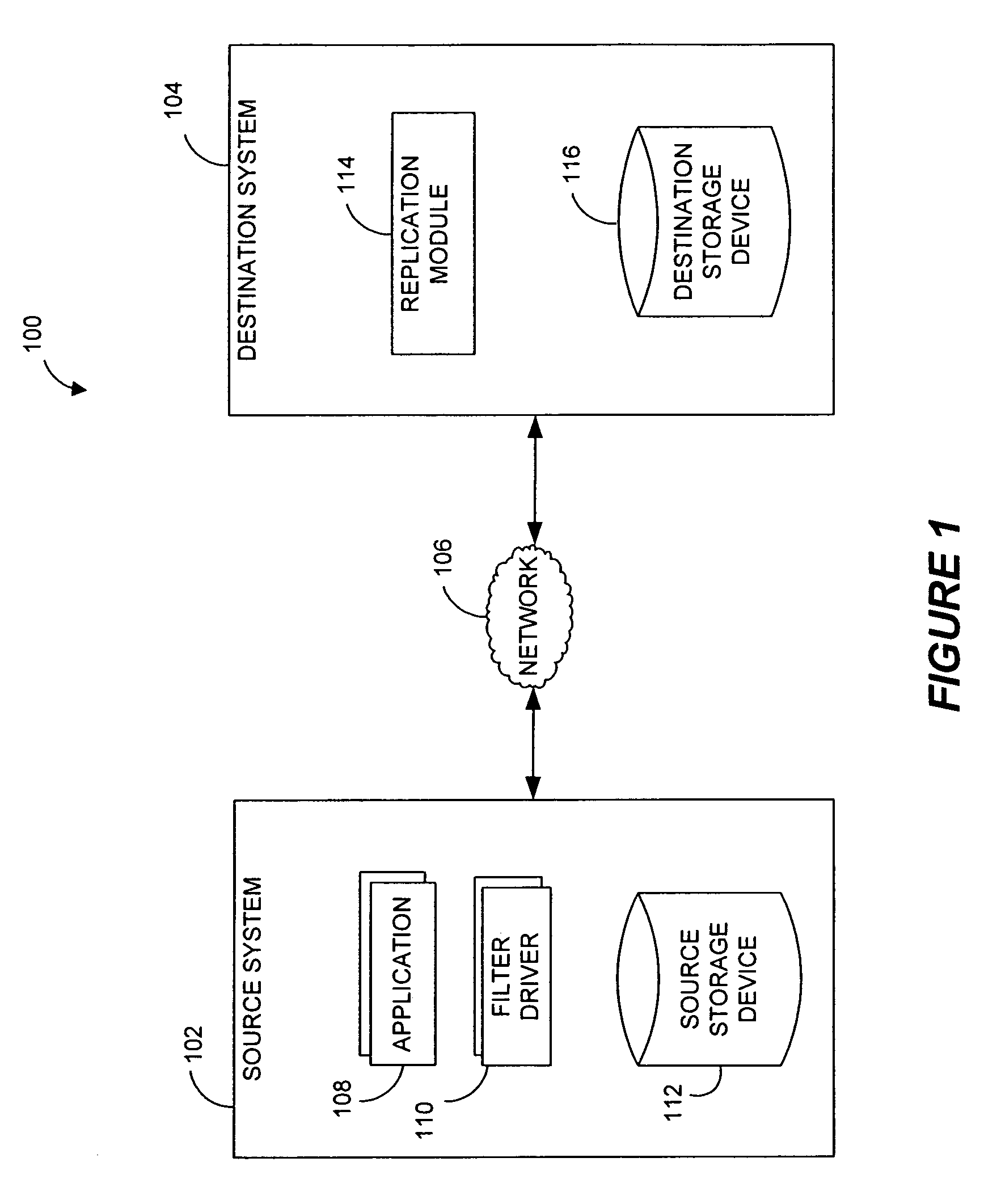
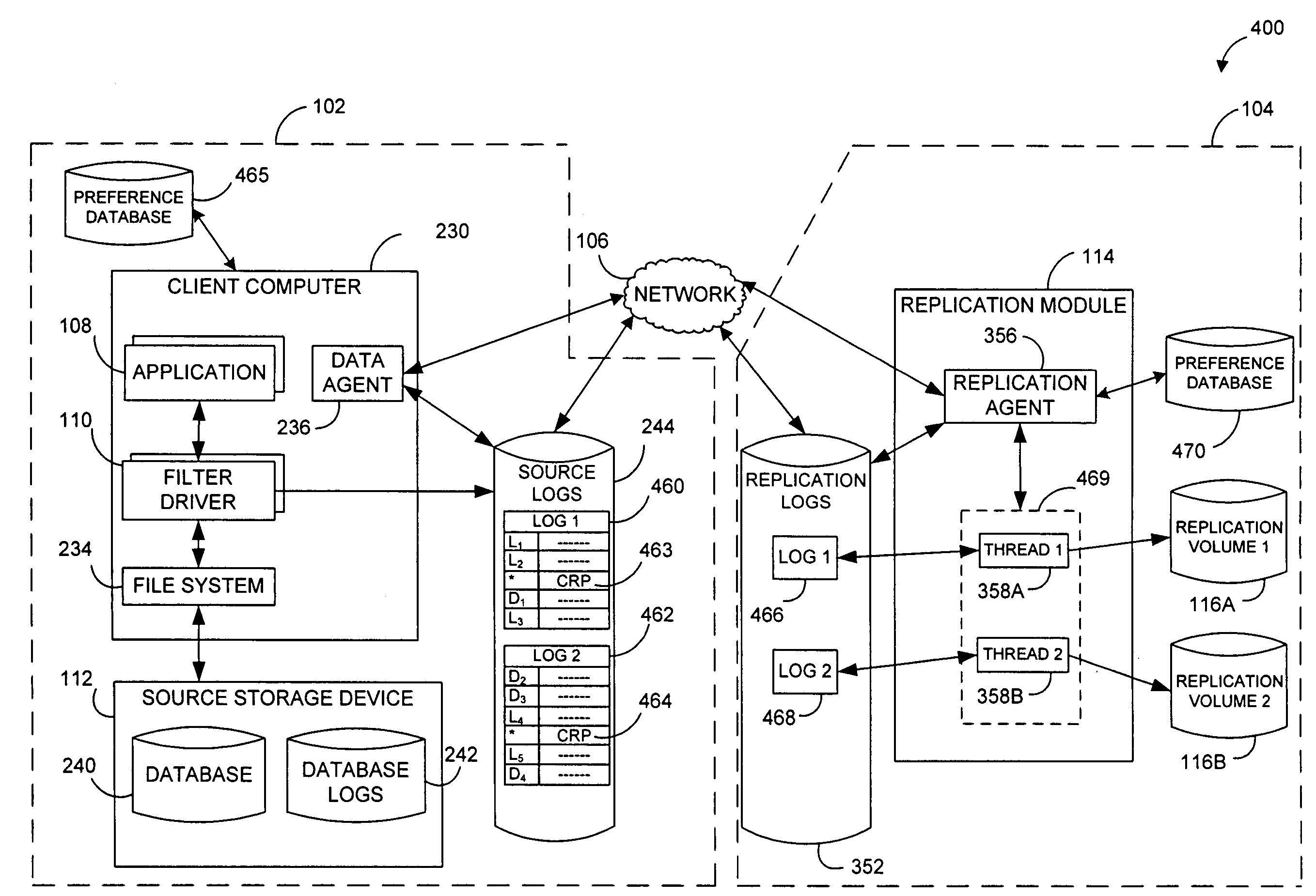
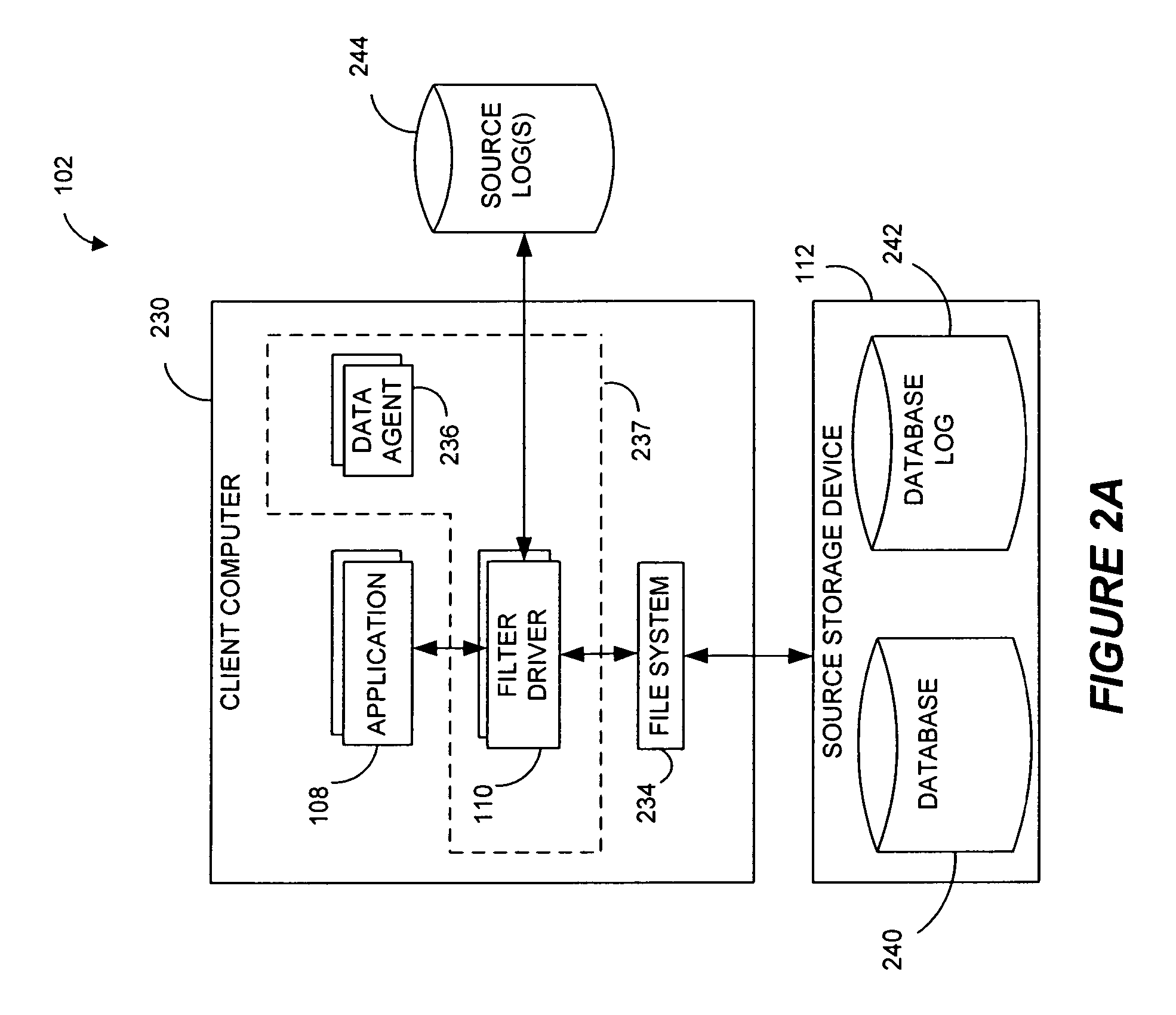
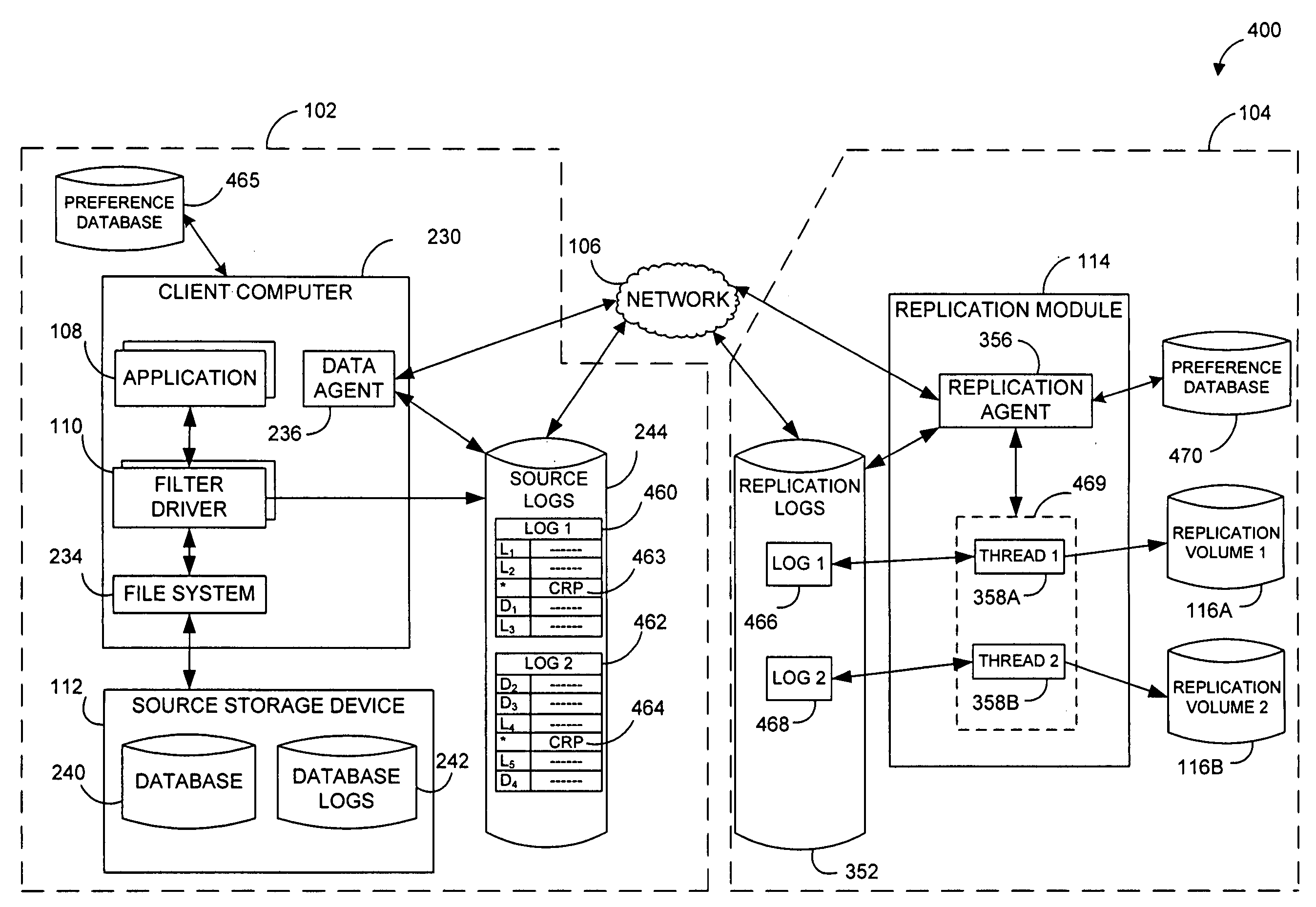
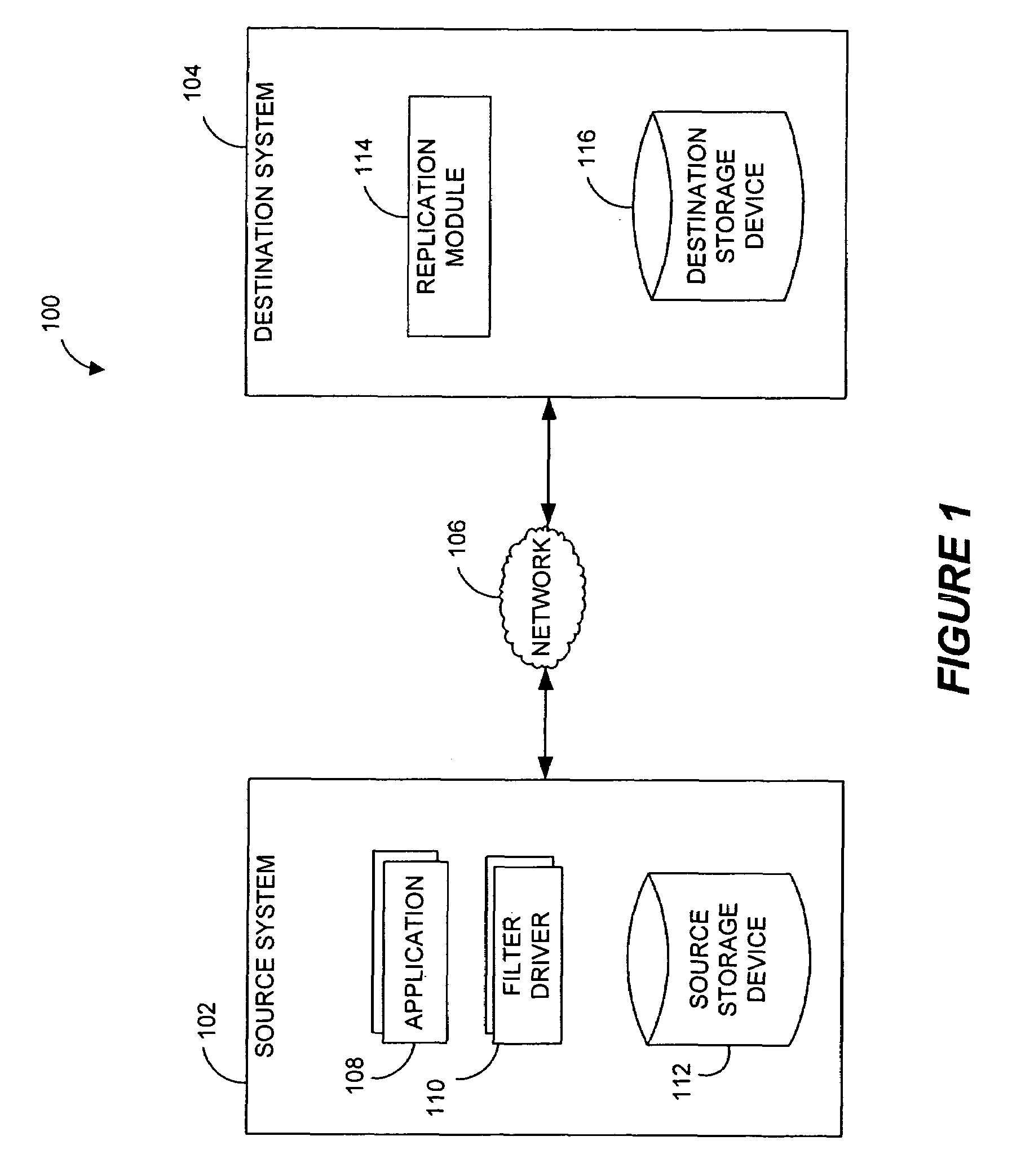
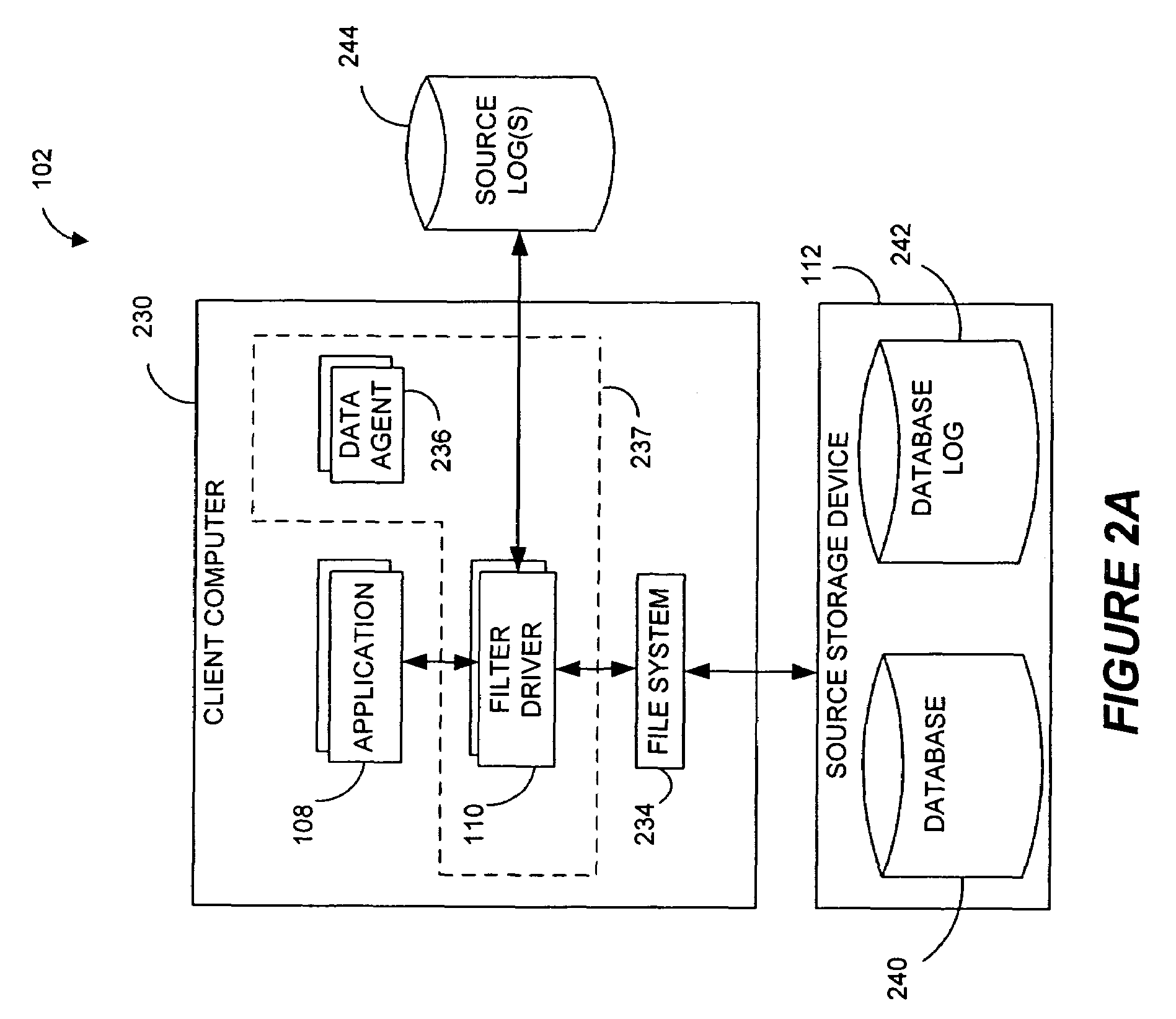
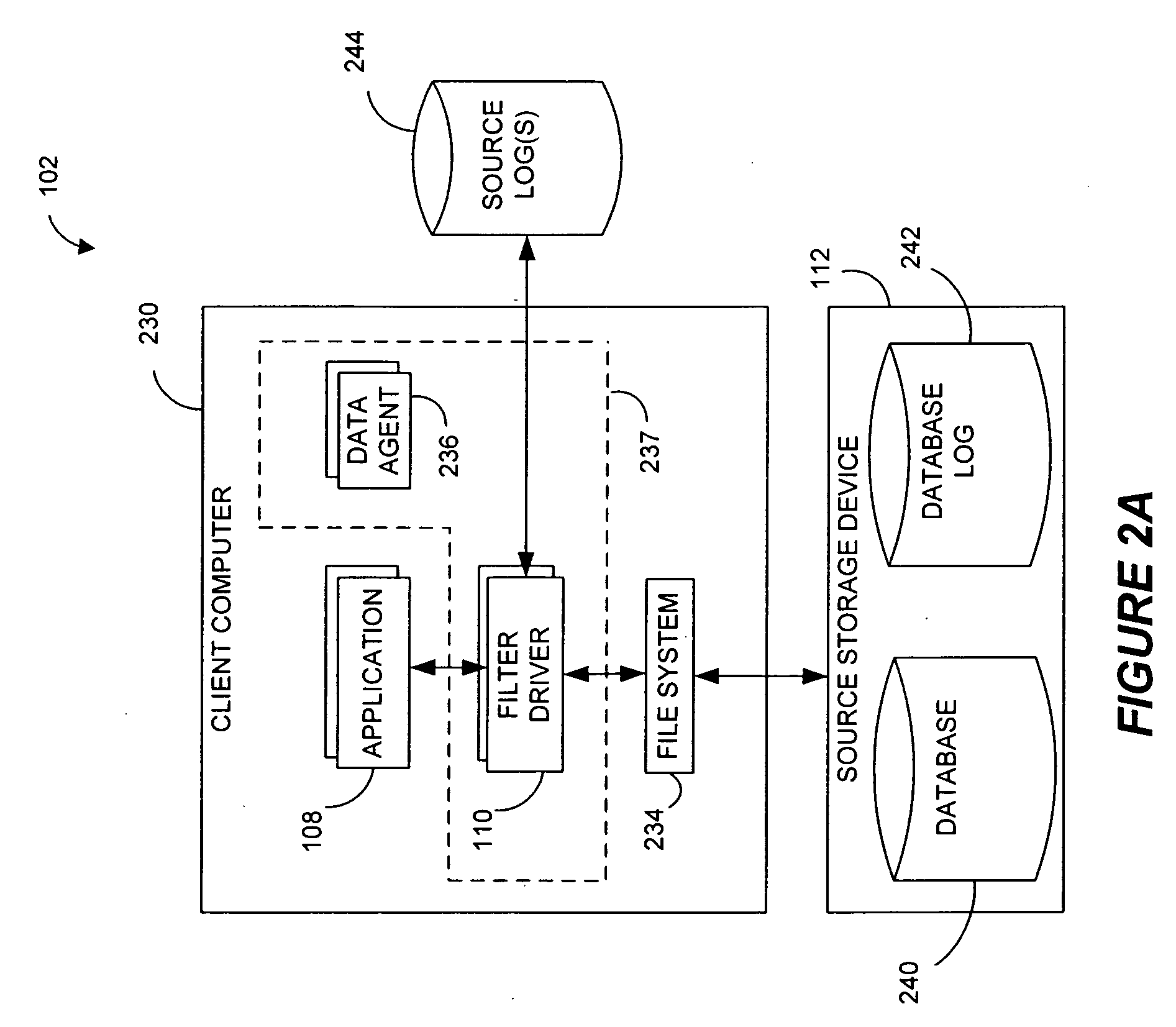
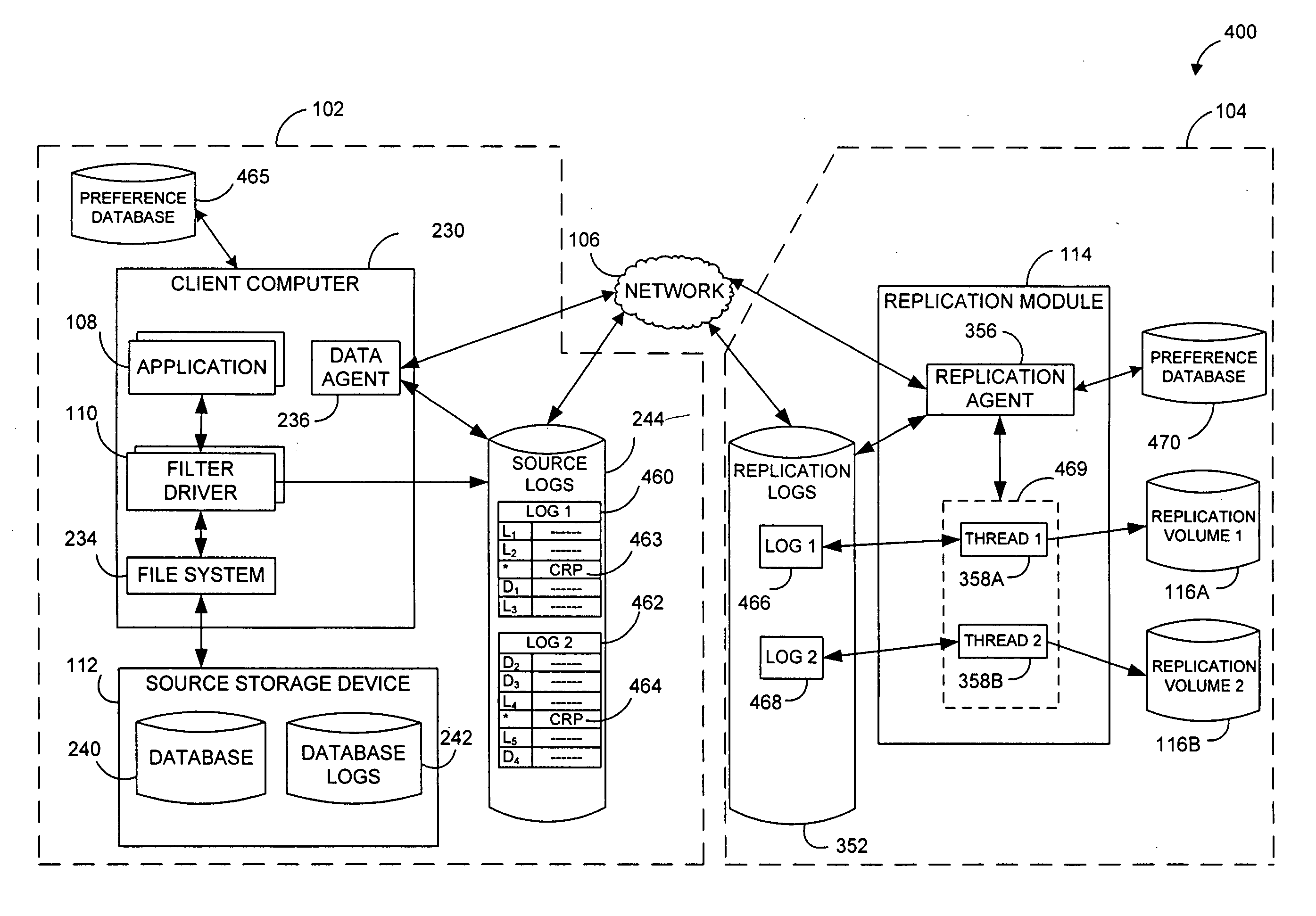
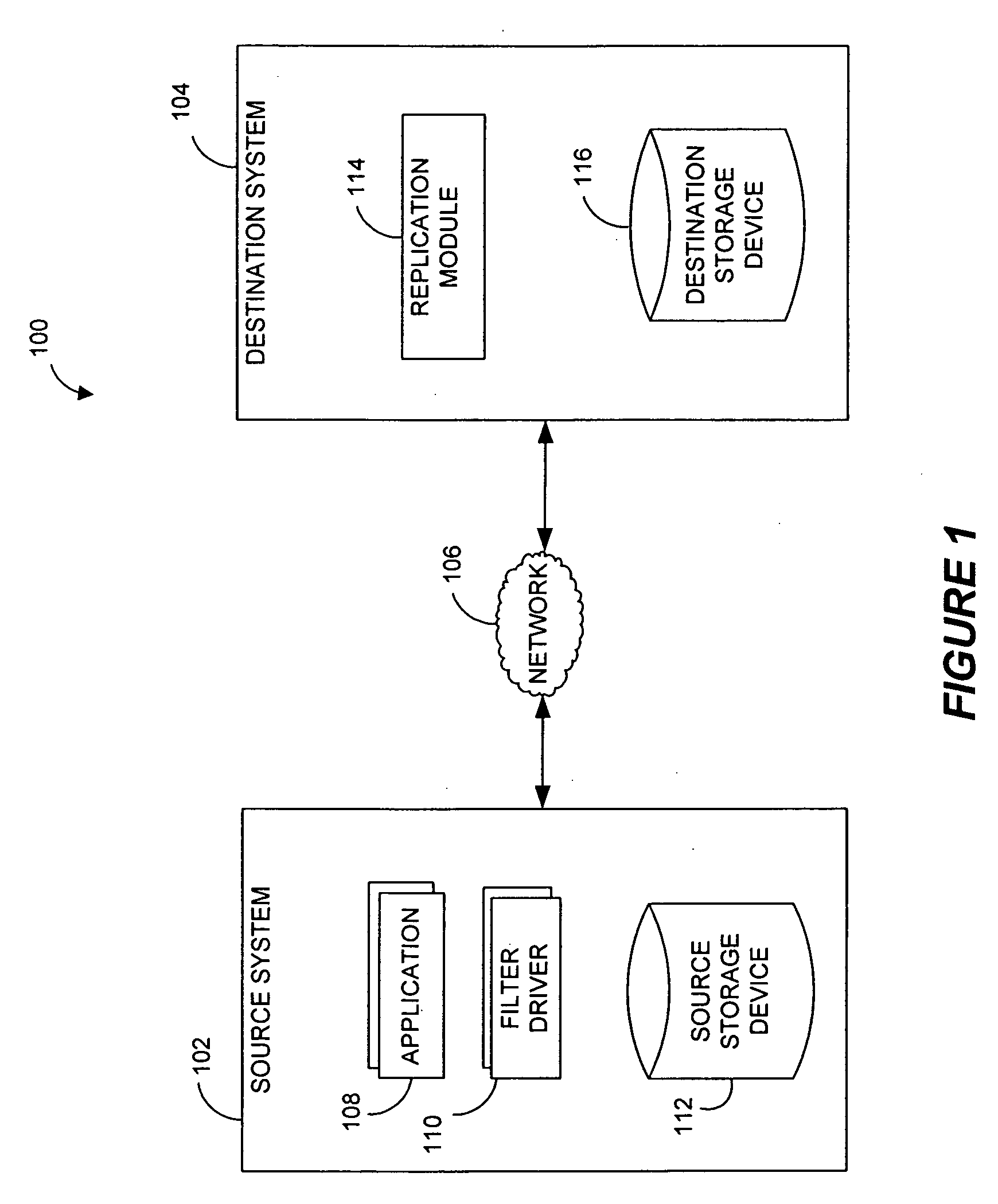
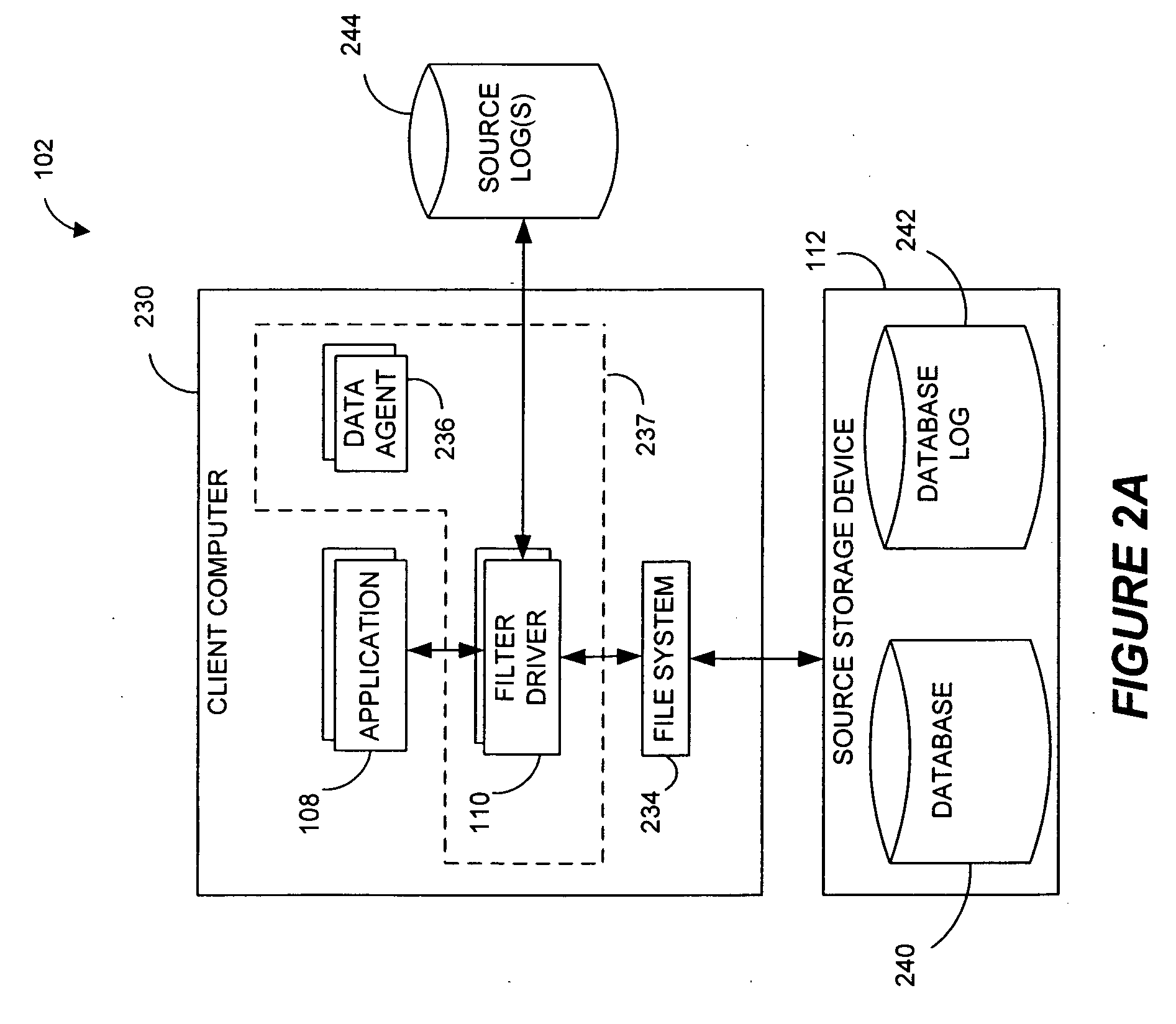
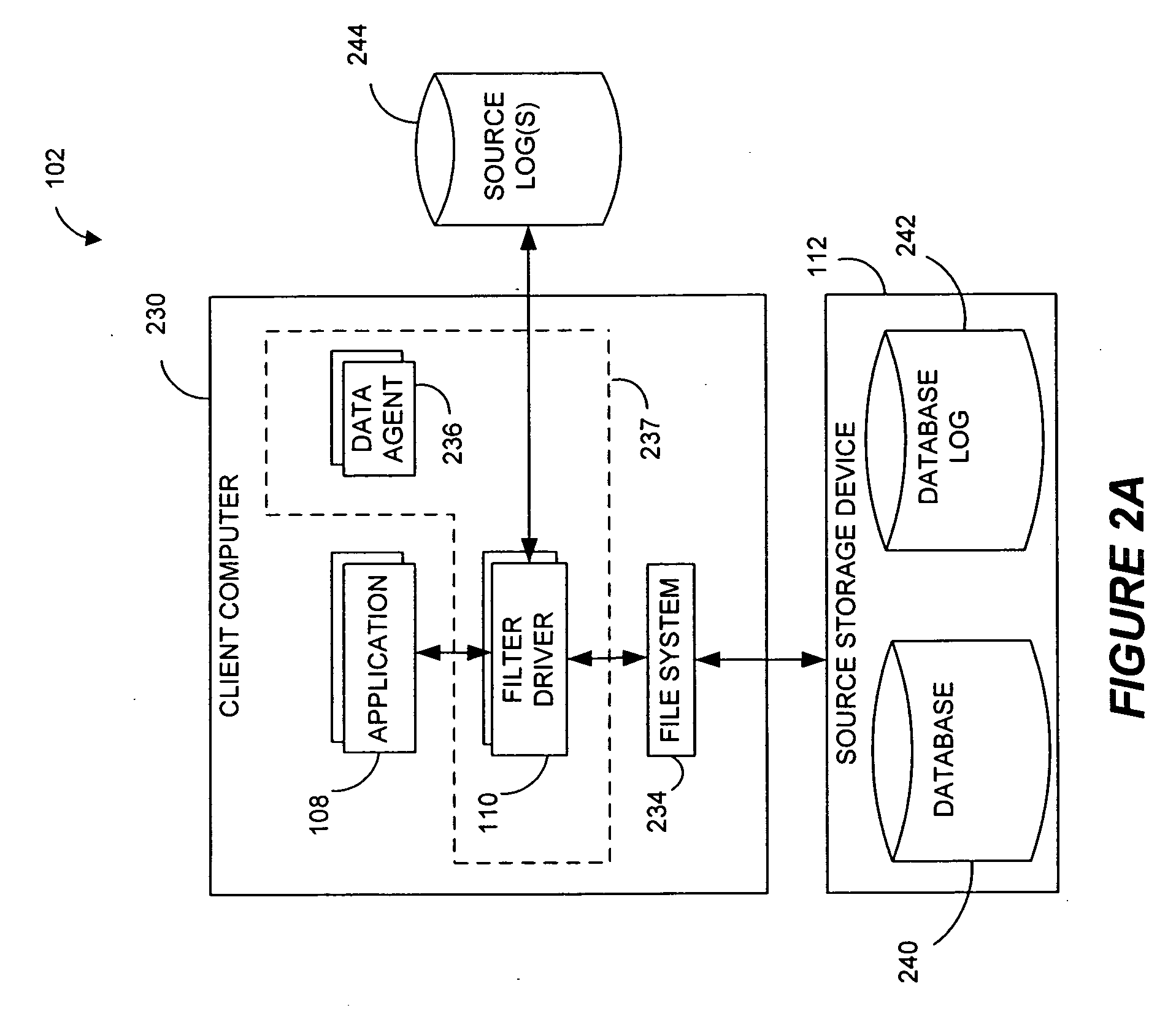
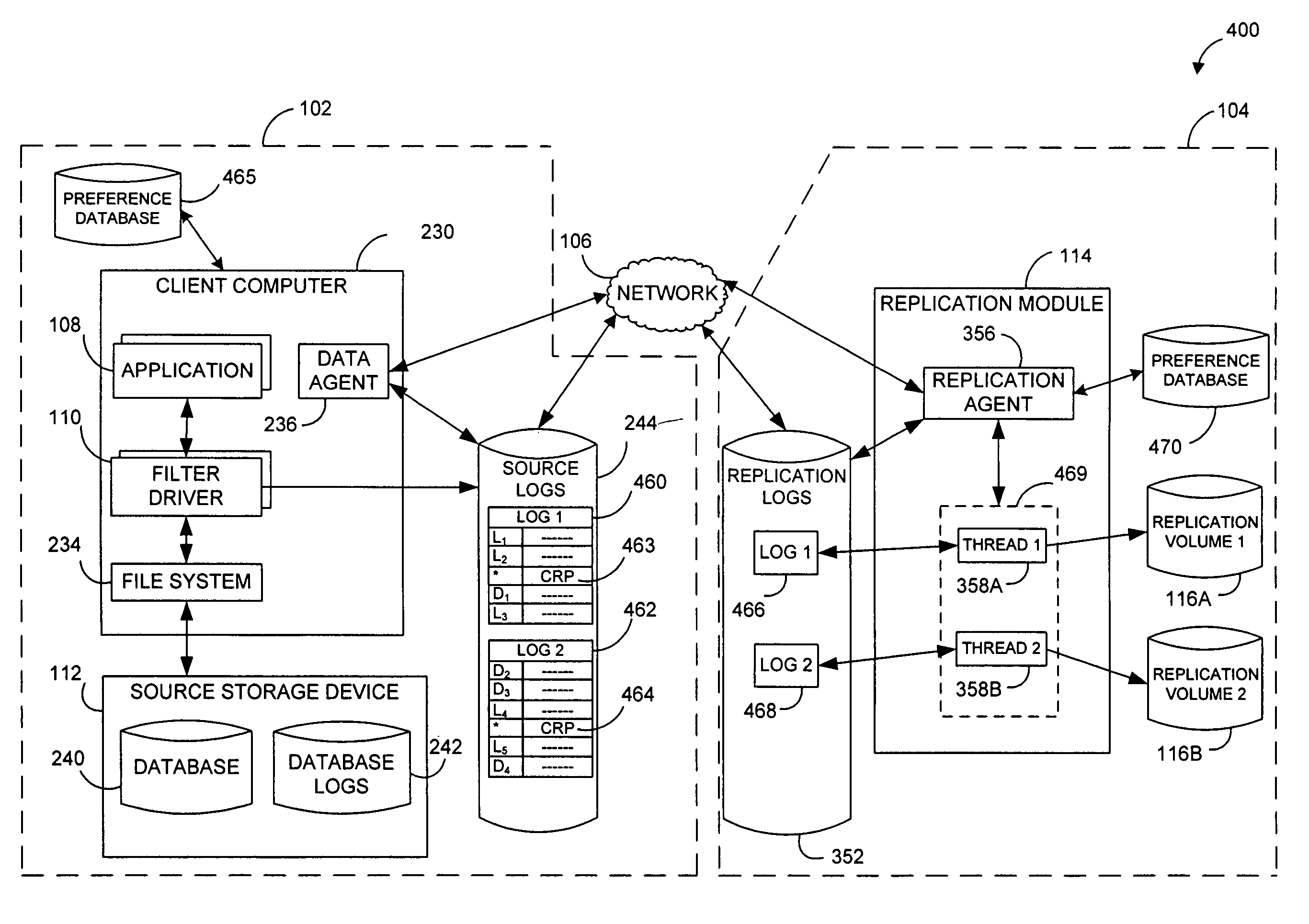
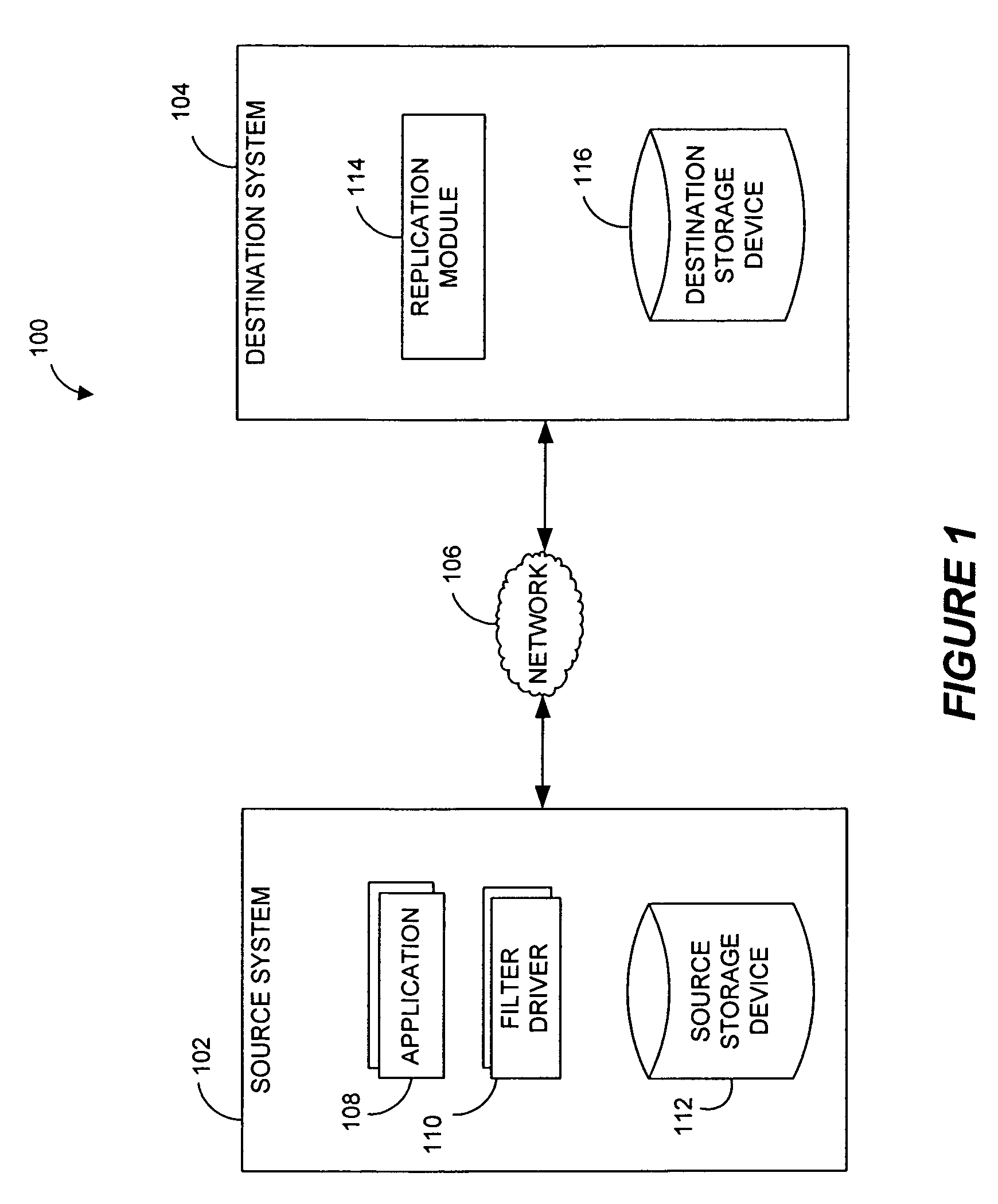
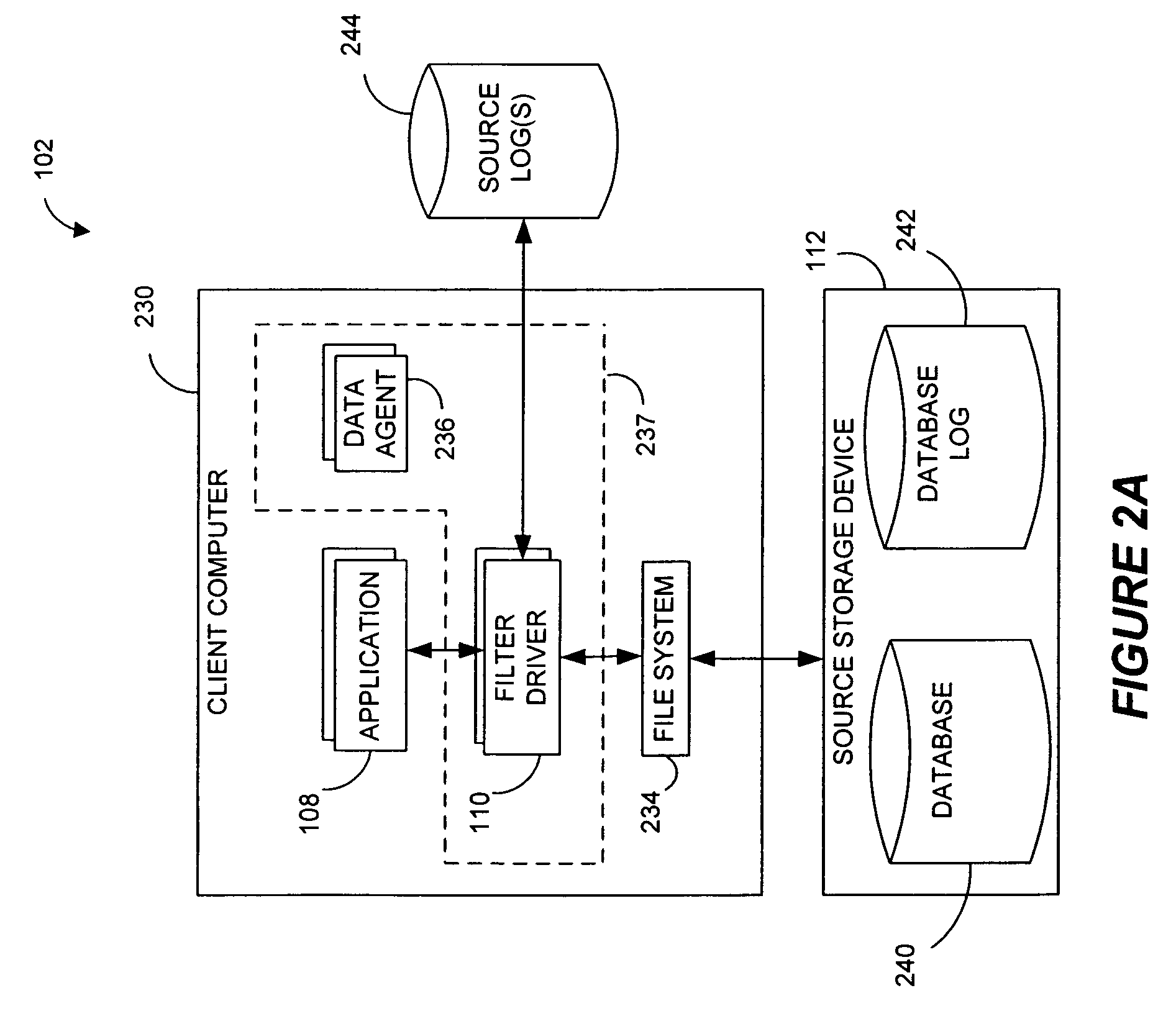
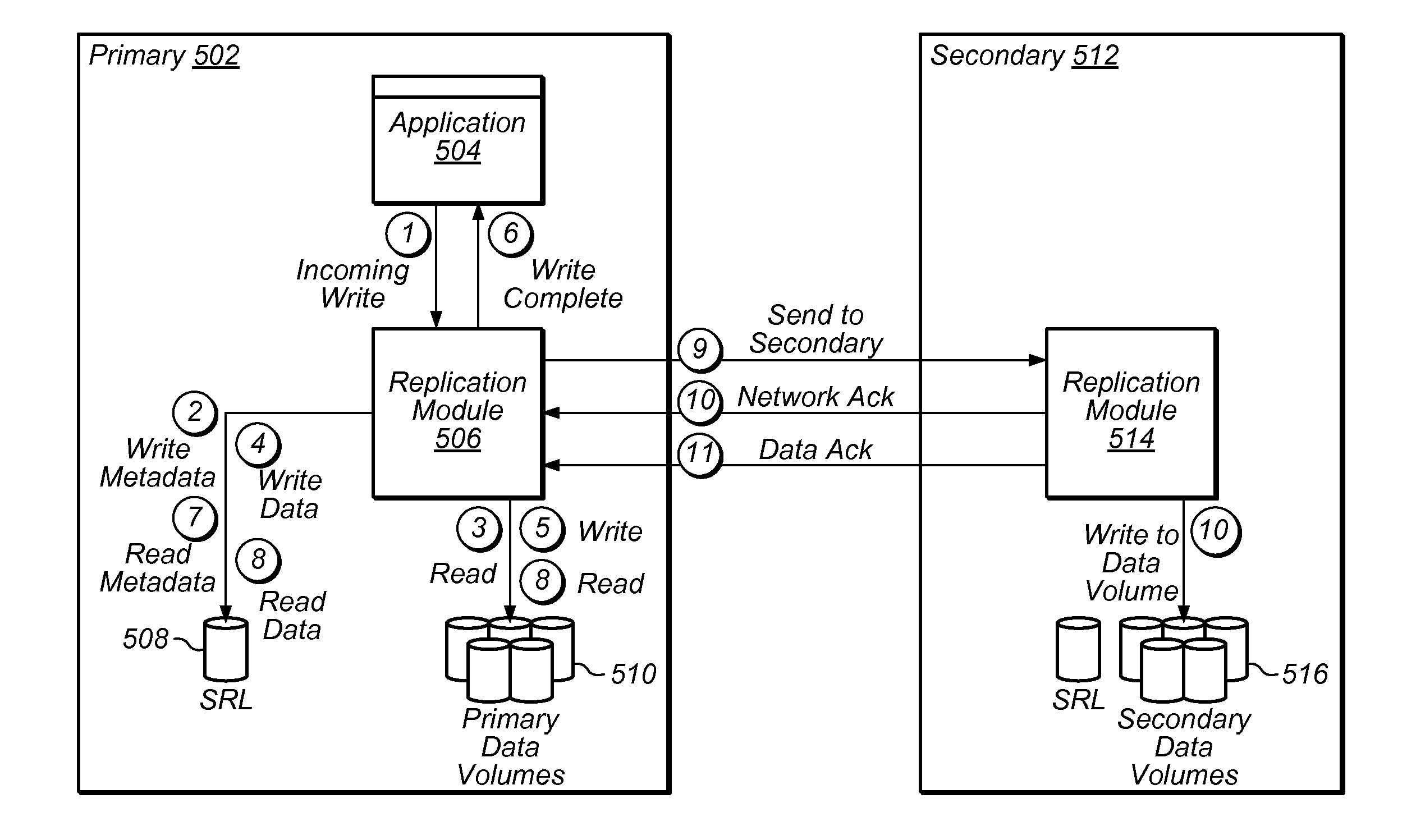
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
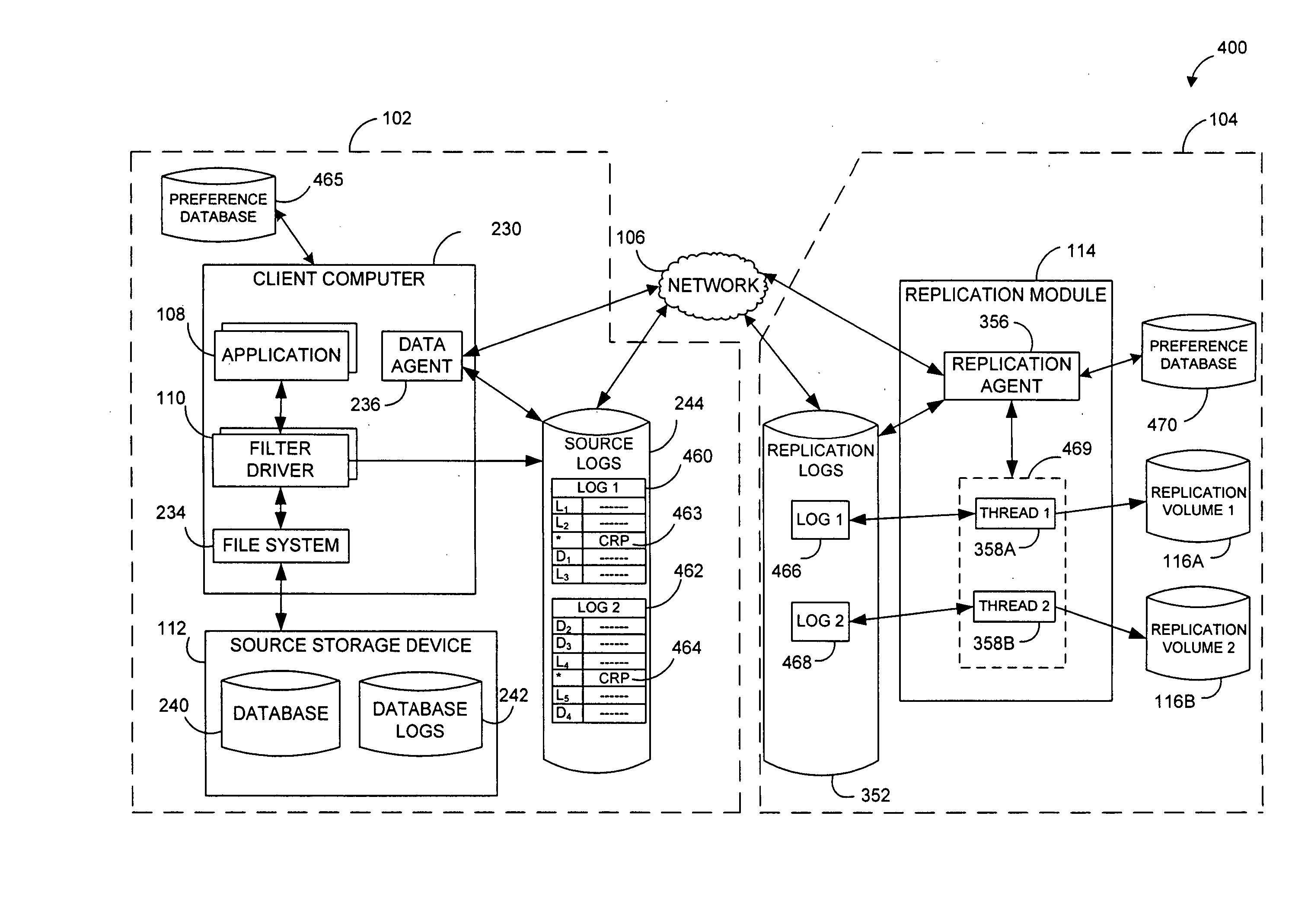
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
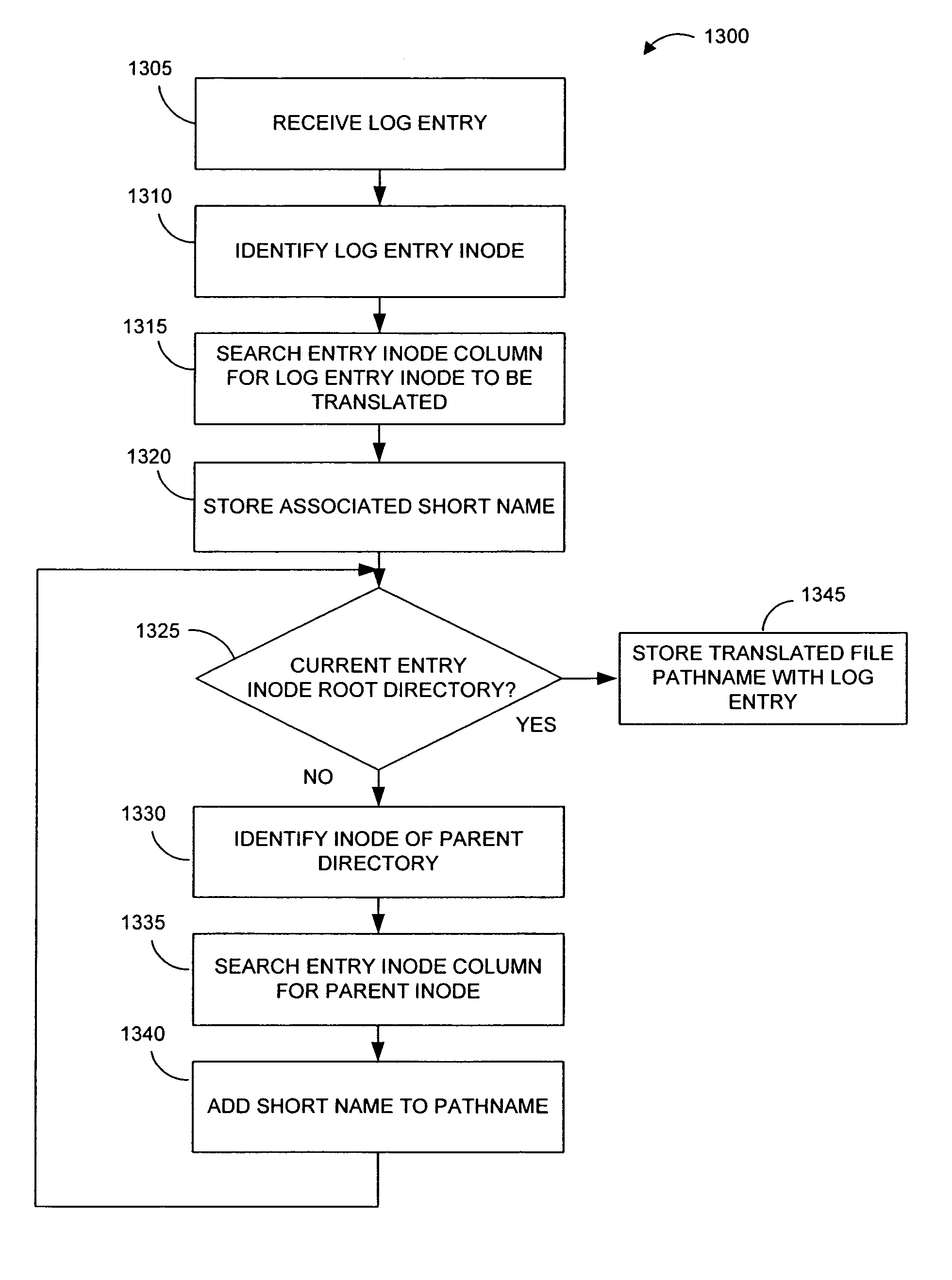
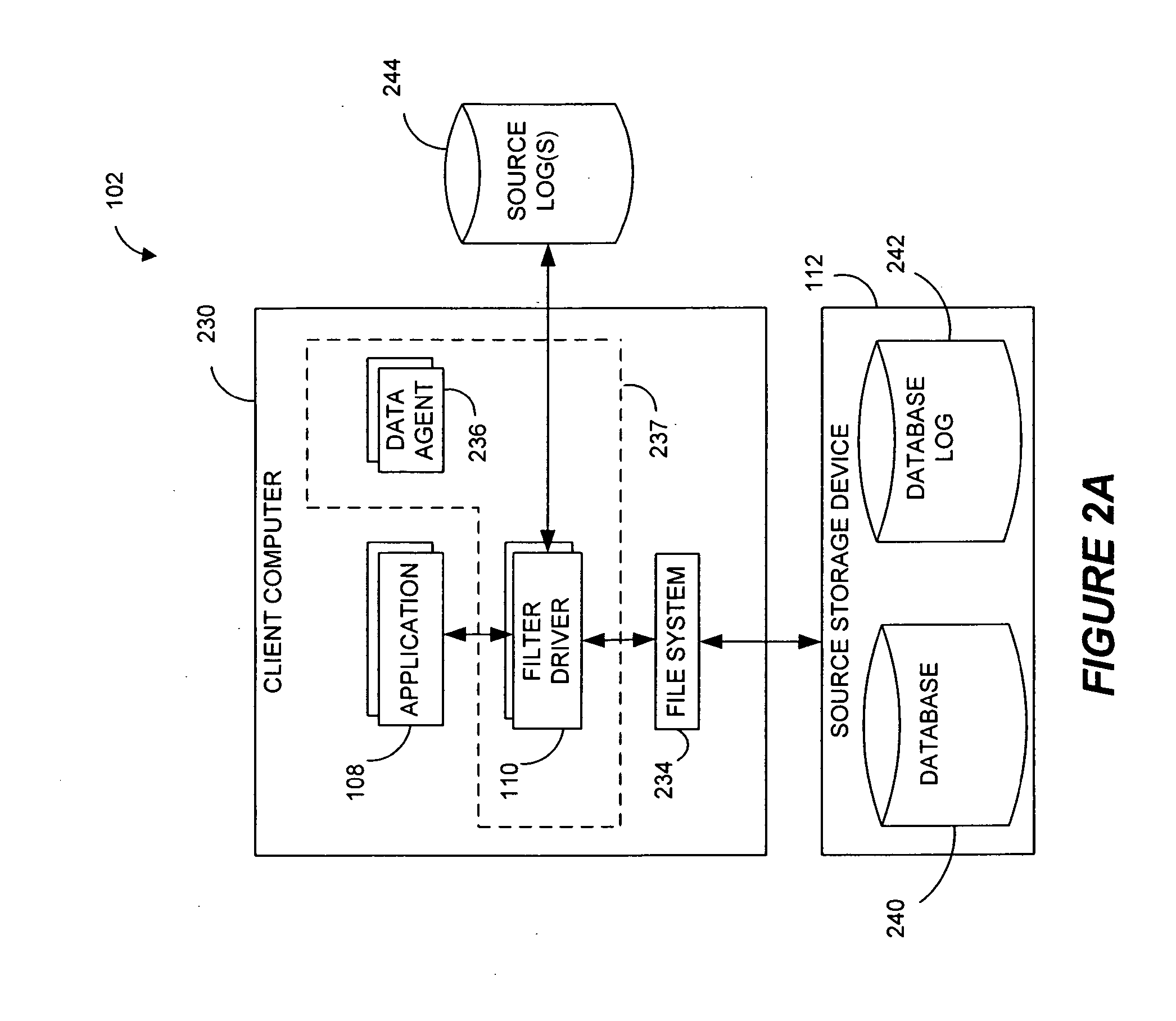
Pathname translation in a data replication system
InactiveUS7636743B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Owner:COMMVAULT SYST INC
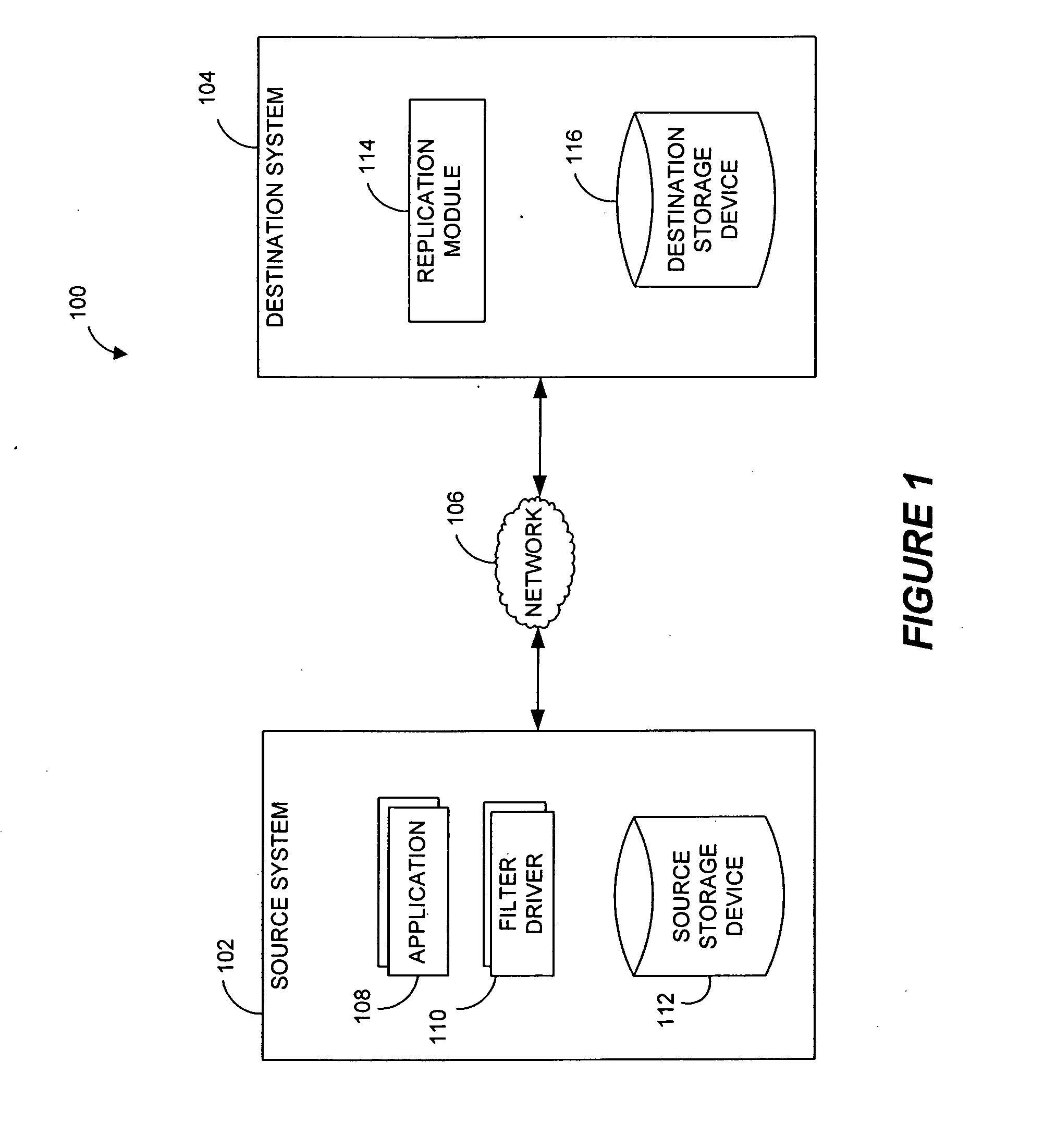
Destination systems and methods for performing data replication
InactiveUS7617253B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
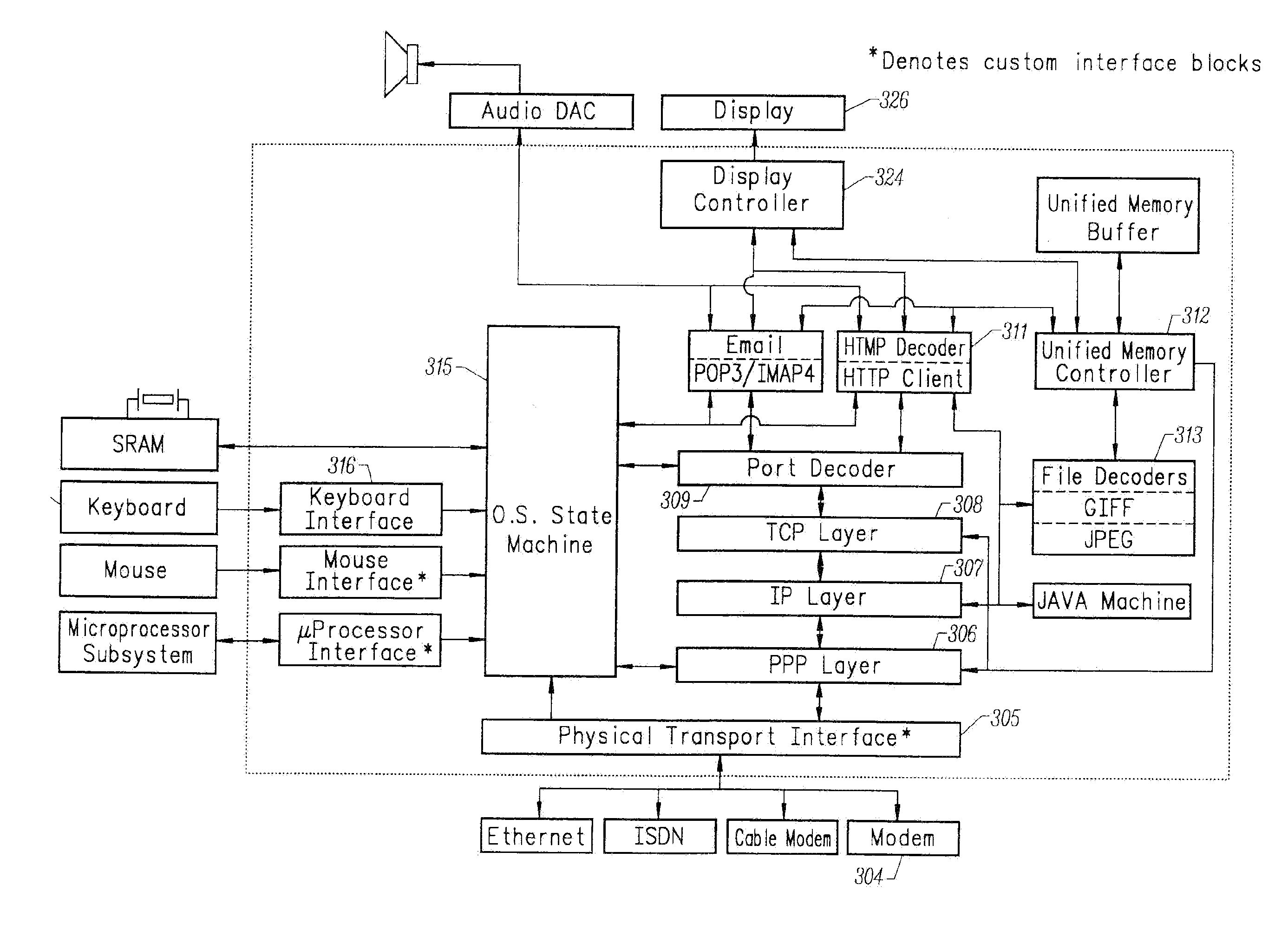
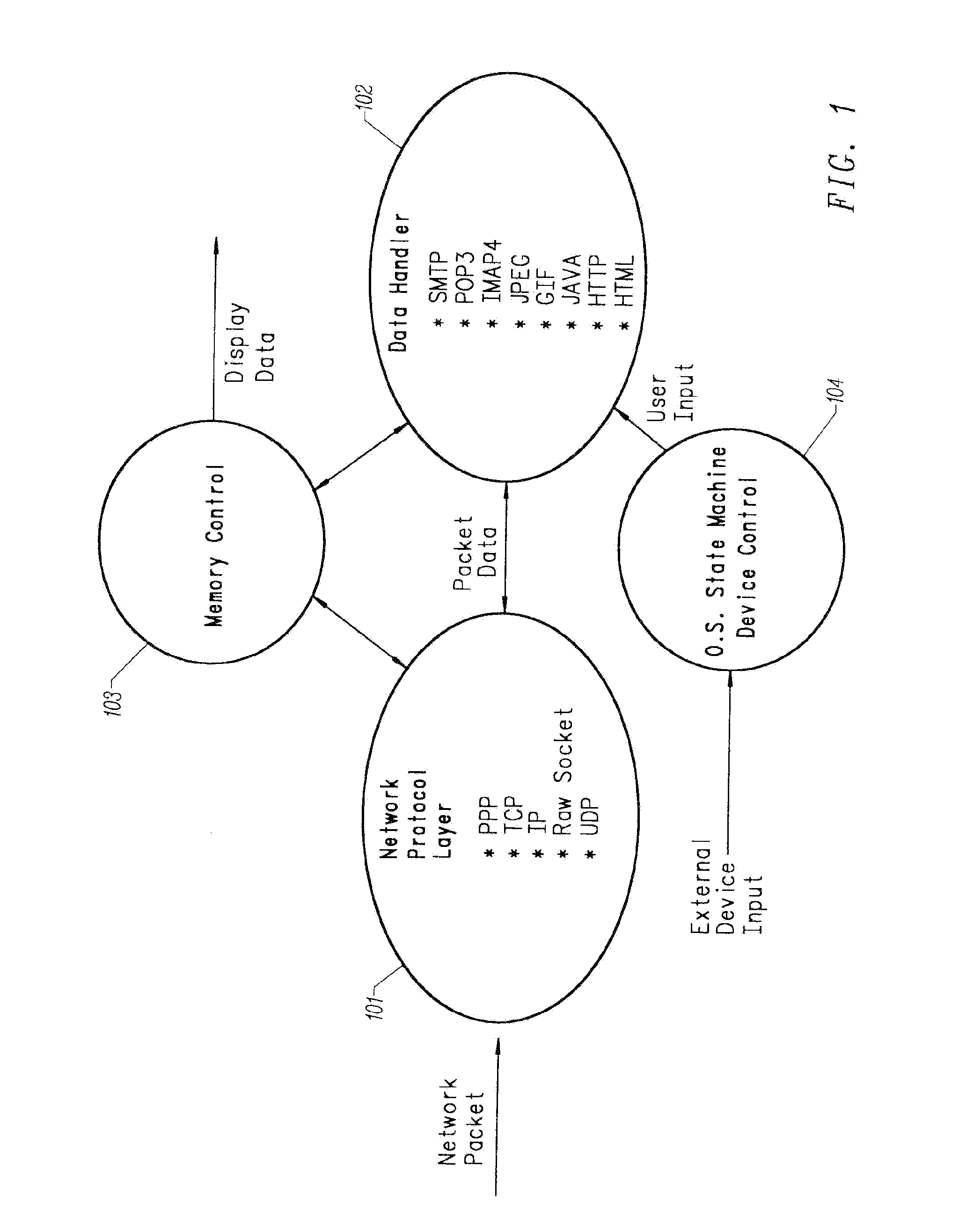
Multiple network protocol encoder/decoder and data processor
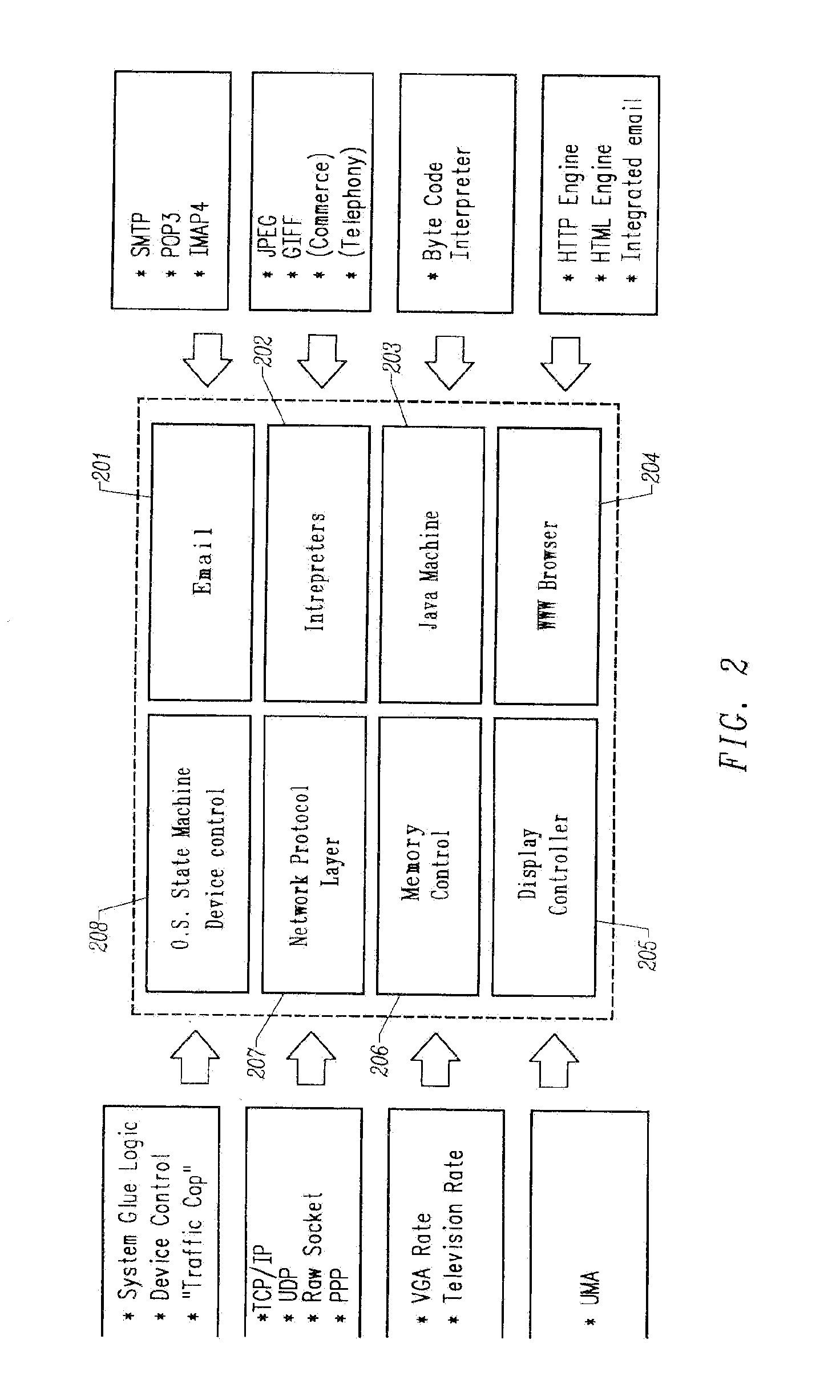
InactiveUS6034963AReduce system costLow costTime-division multiplexData switching by path configurationRaw socketByte
A multiple network protocol encoder / decoder comprising a network protocol layer, data handler, O.S. State machine, and memory manager state machines implemented at a hardware gate level. Network packets are received from a physical transport level mechanism by the network protocol layer state machine which decodes network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, and Raw Socket concurrently as each byte is received. Each protocol handler parses and strips header information immediately from the packet, requiring no intermediate memory. The resulting data are passed to the data handler which consists of data state machines that decode data formats such as email, graphics, Hypertext Transfer Protocol (HTTP), Java, and Hypertext Markup Language (HTML). Each data state machine reacts accordingly to the pertinent data, and any data that are required by more than one data state machine is provided to each state machine concurrently, and any data required more than once by a specific data state machine, are placed in a specific memory location with a pointer designating such data (thereby ensuring minimal memory usage). Resulting display data are immediately passed to a display controller. Any outgoing network packets are created by the data state machines and passed through the network protocol state machine which adds header information and forwards the resulting network packet via a transport level mechanism.
Owner:NVIDIA CORP
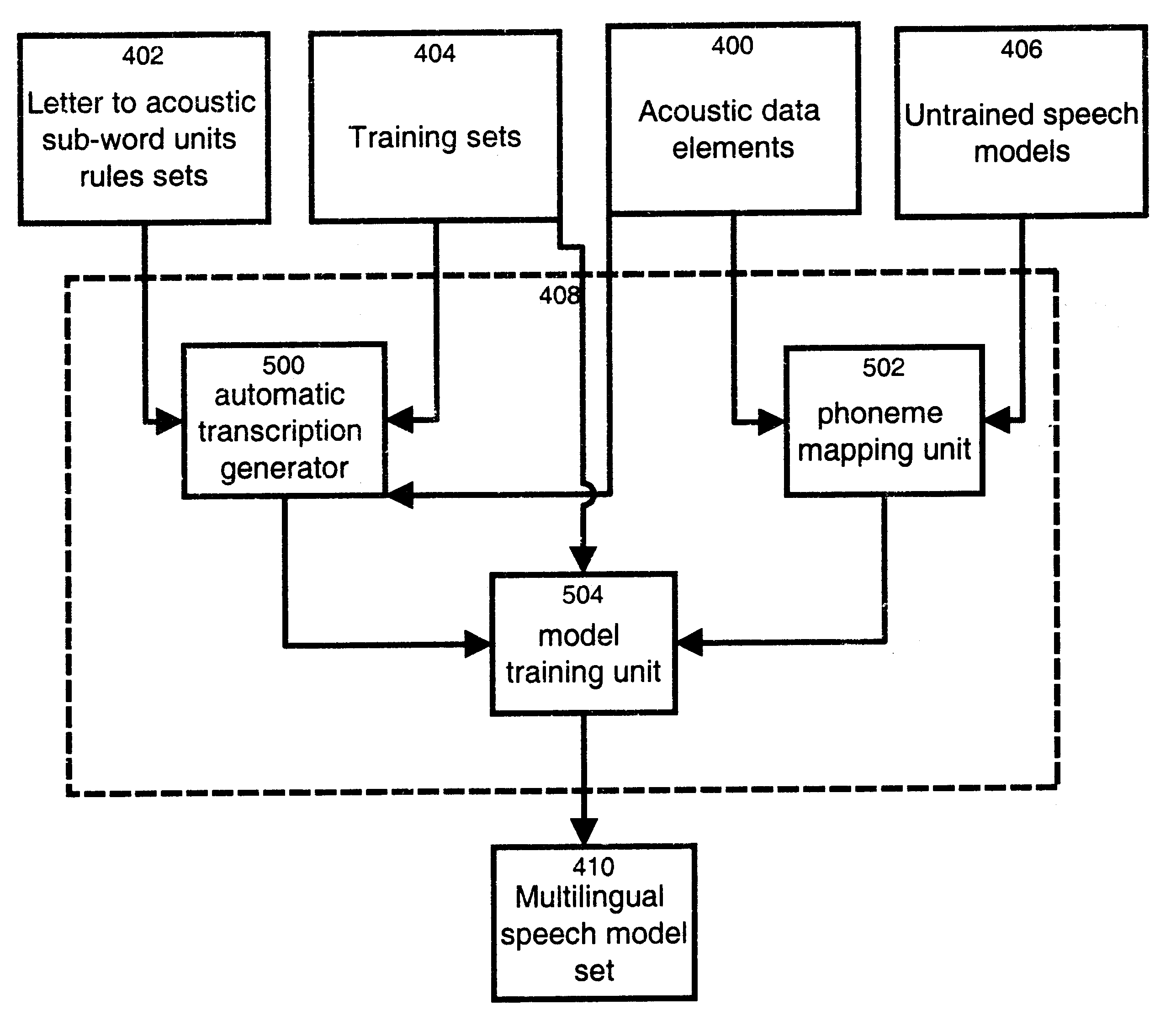
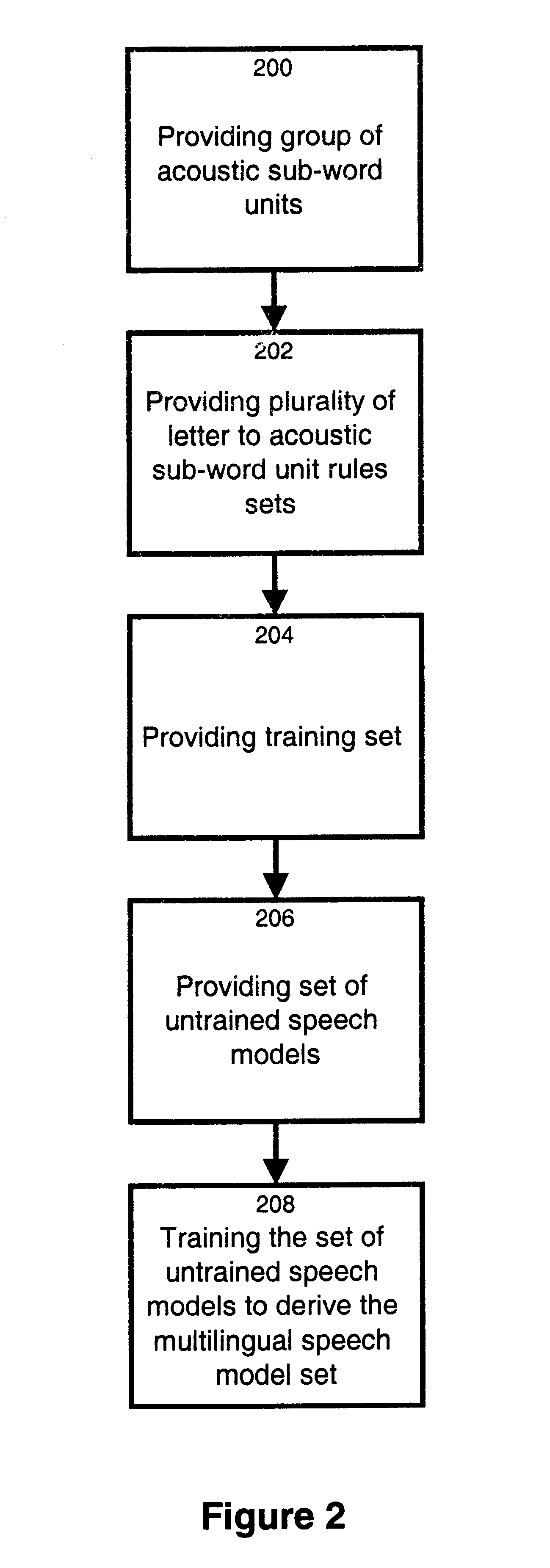
Method and apparatus for training a multilingual speech model set
InactiveUS6912499B1Reduce development costsShorten development timeSpeech recognitionSpecial data processing applicationsMore languageSpeech identification
The invention relates to a method and apparatus for training a multilingual speech model set. The multilingual speech model set generated is suitable for use by a speech recognition system for recognizing spoken utterances for at least two different languages. The invention allows using a single speech recognition unit with a single speech model set to perform speech recognition on utterances from two or more languages. The method and apparatus make use of a group of a group of acoustic sub-word units comprised of a first subgroup of acoustic sub-word units associated to a first language and a second subgroup of acoustic sub-word units associated to a second language where the first subgroup and the second subgroup share at least one common acoustic sub-word unit. The method and apparatus also make use of a plurality of letter to acoustic sub-word unit rules sets, each letter to acoustic sub-word unit rules set being associated to a different language. A set of untrained speech models is trained on the basis of a training set comprising speech tokens and their associated labels in combination with the group of acoustic sub-word units and the plurality of letter to acoustic sub-word unit rules sets. The invention also provides a computer readable storage medium comprising a program element for implementing the method for training a multilingual speech model set.
Owner:RPX CLEARINGHOUSE
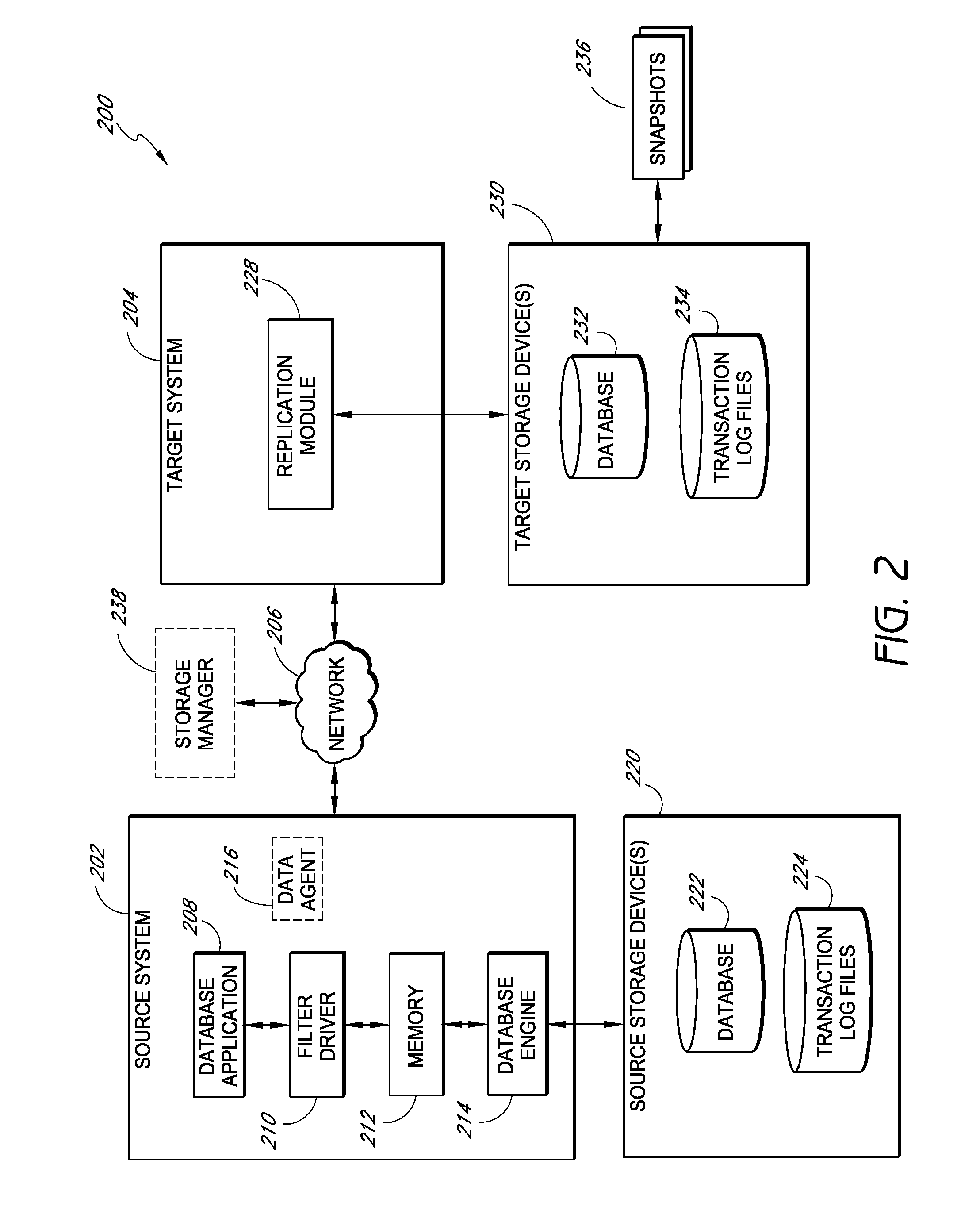
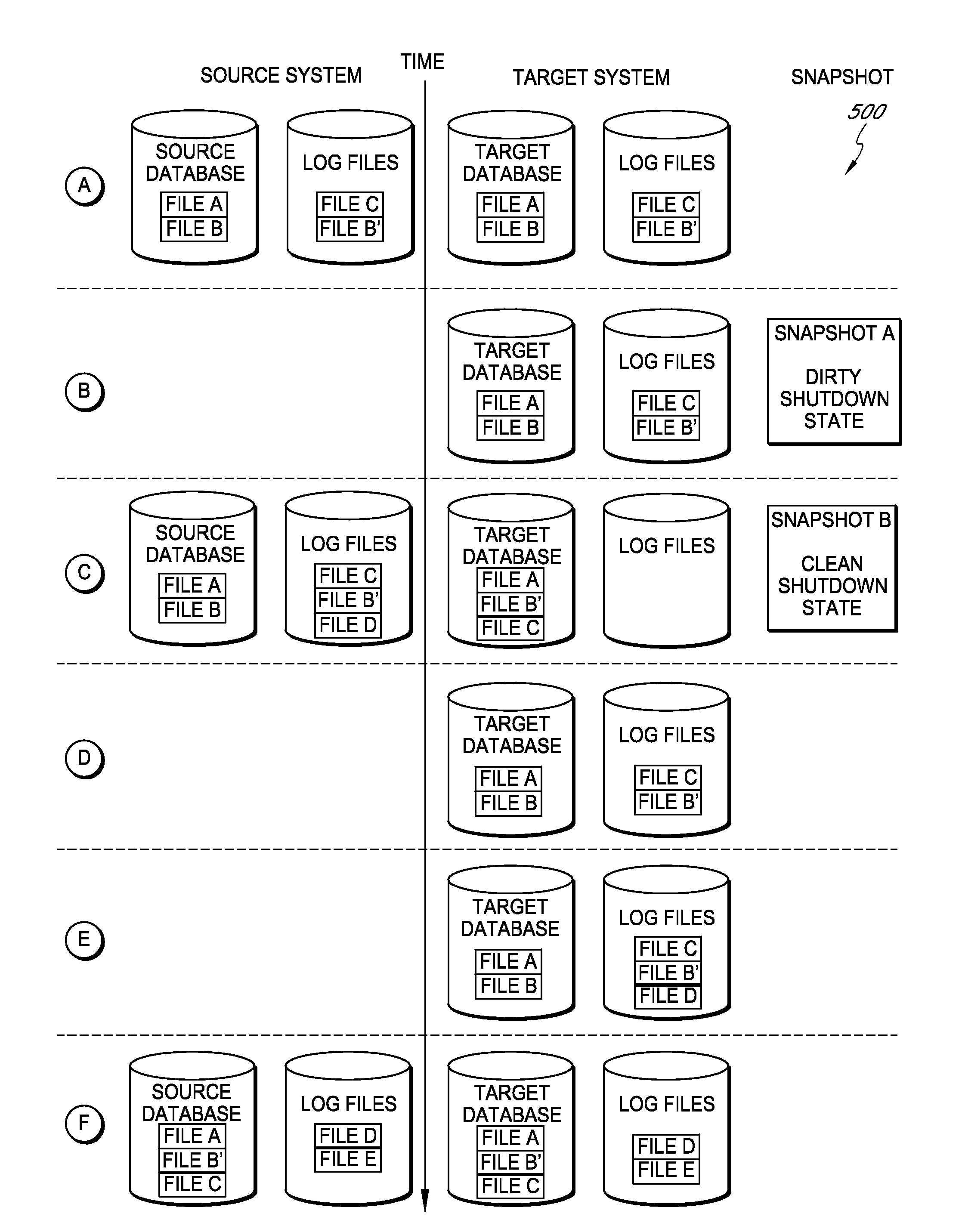
Systems and methods for managing replicated database data
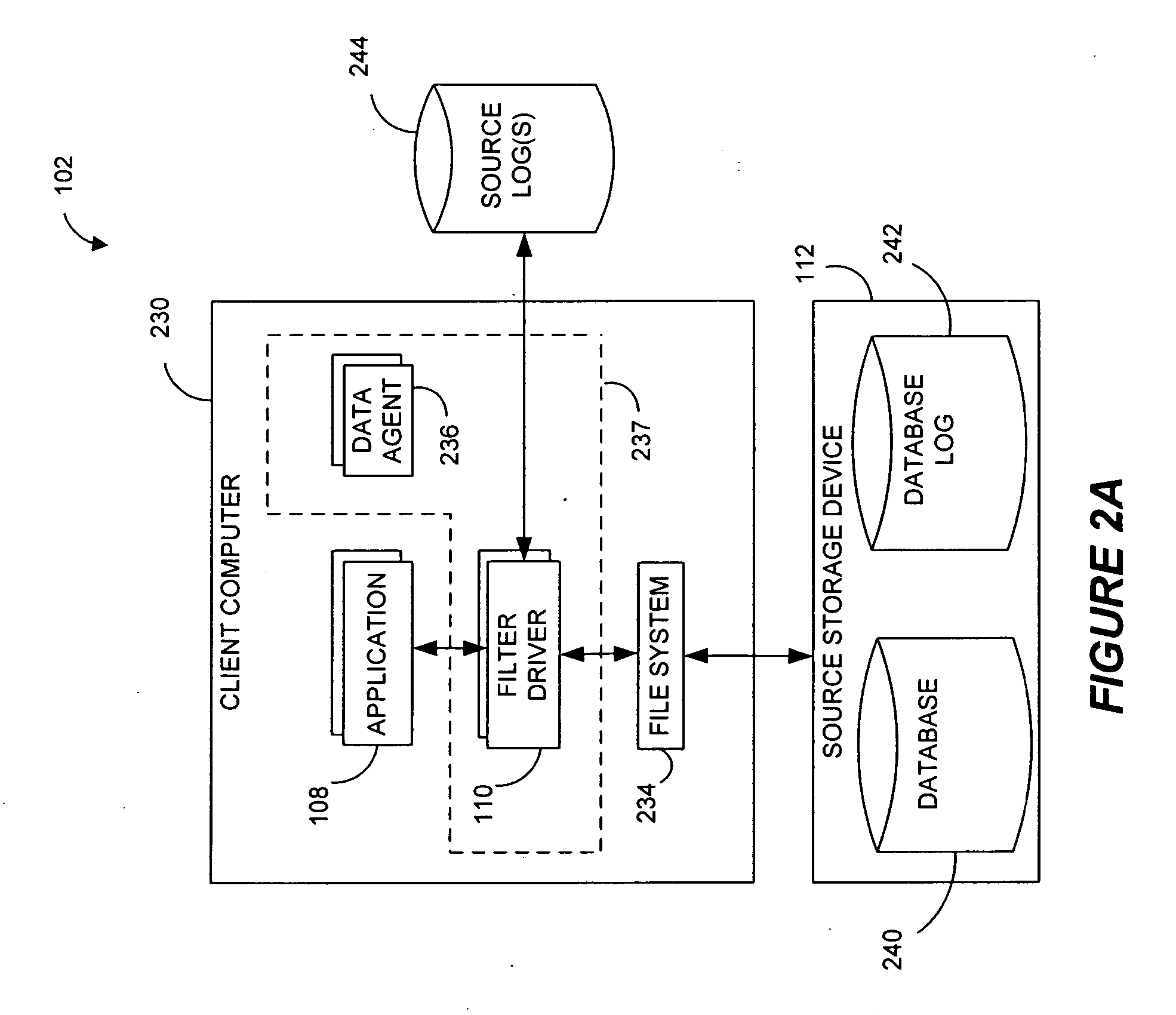
ActiveUS20100145909A1Reduce memory requirementsImprove performanceError detection/correctionDigital data processing detailsDatabase applicationApplication software
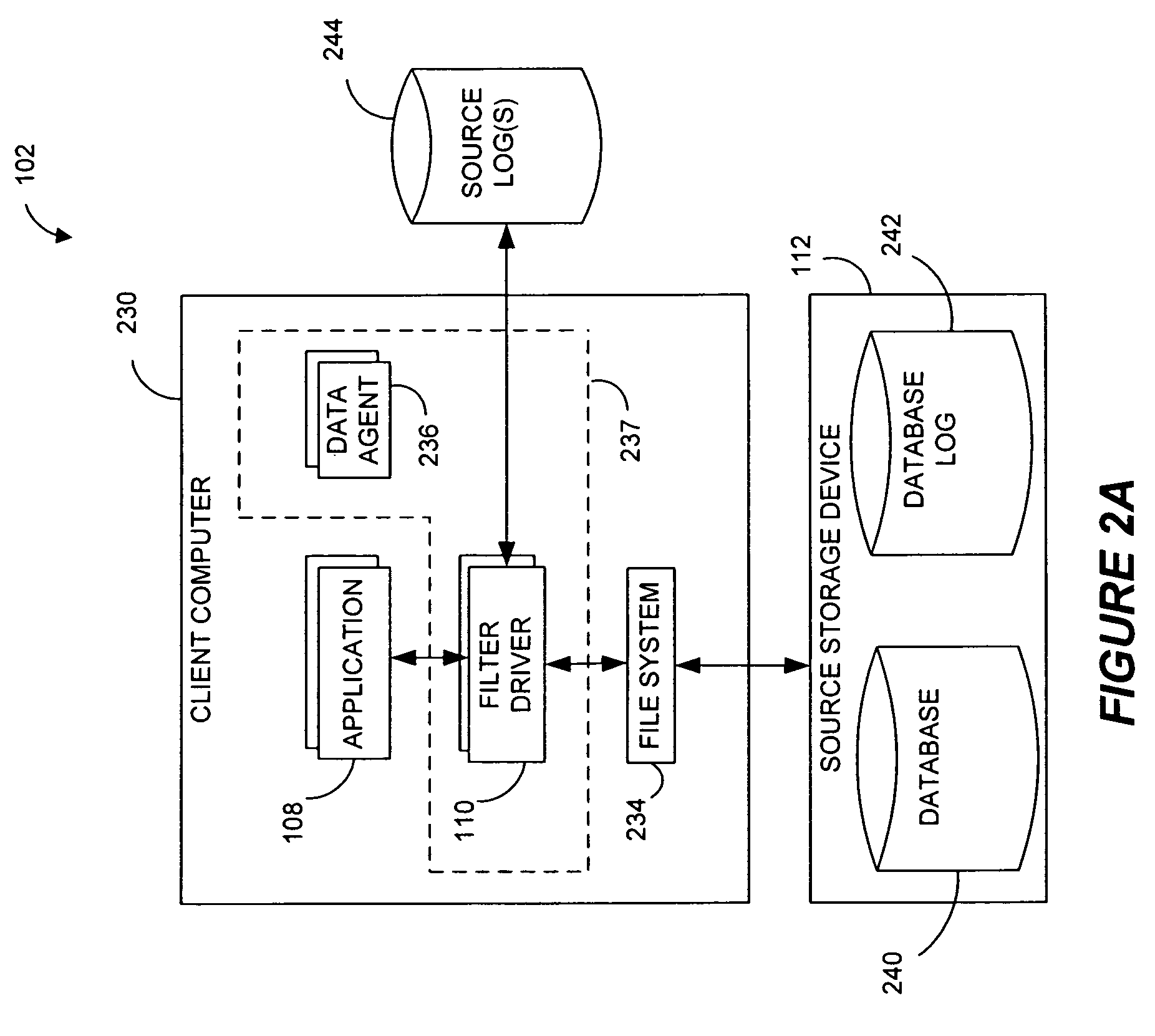
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
Systems and methods for performing data replication
ActiveUS20070185938A1Reduce impactReduce memory requirementsError detection/correctionDistillation separationGoal systemApplication software
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
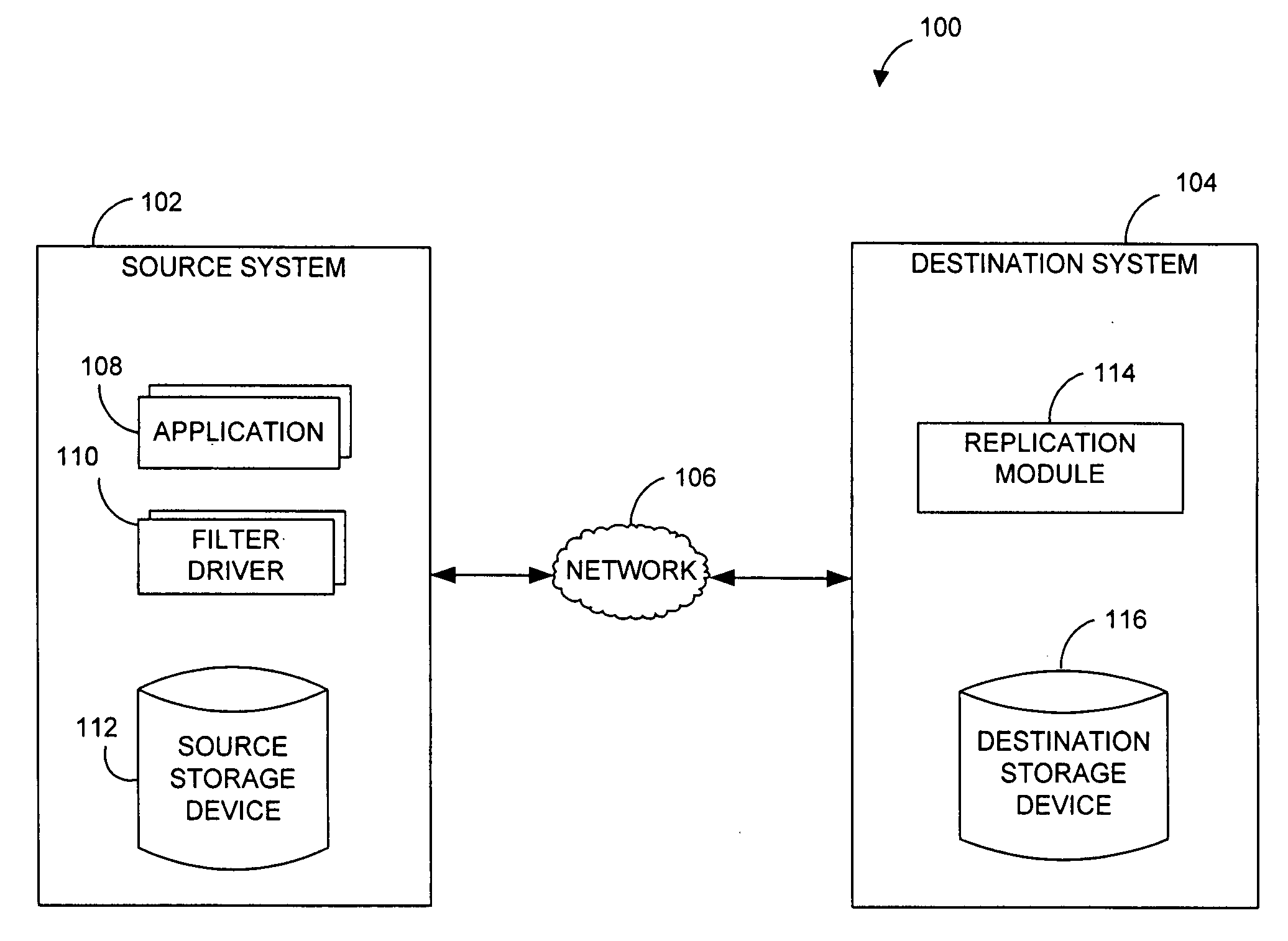
Network redirector systems and methods for performing data replication
ActiveUS20070186068A1Reduce impactReduce memory requirementsDigital data information retrievalMemory loss protectionNetwork redirectorDistributed computing
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
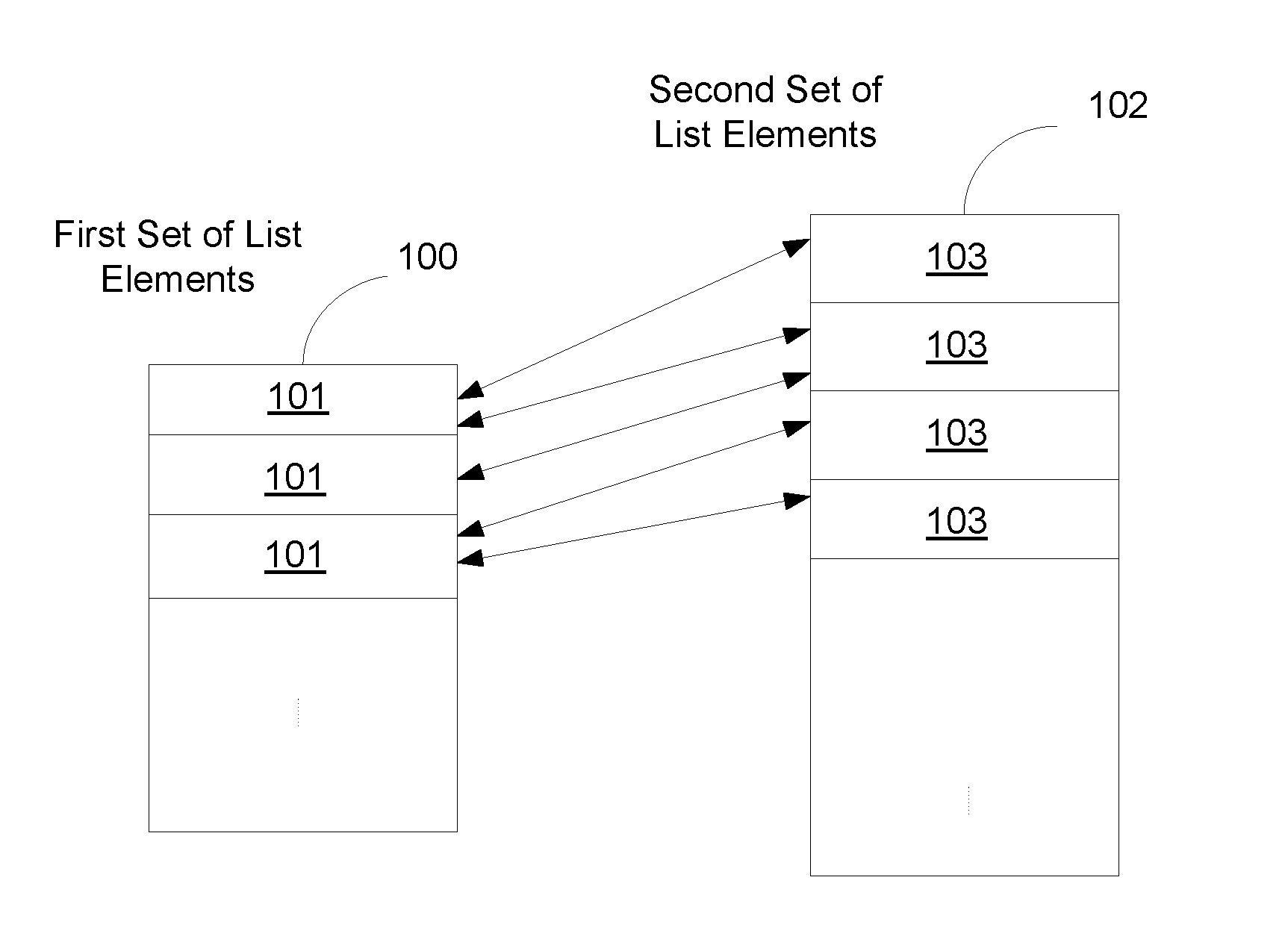
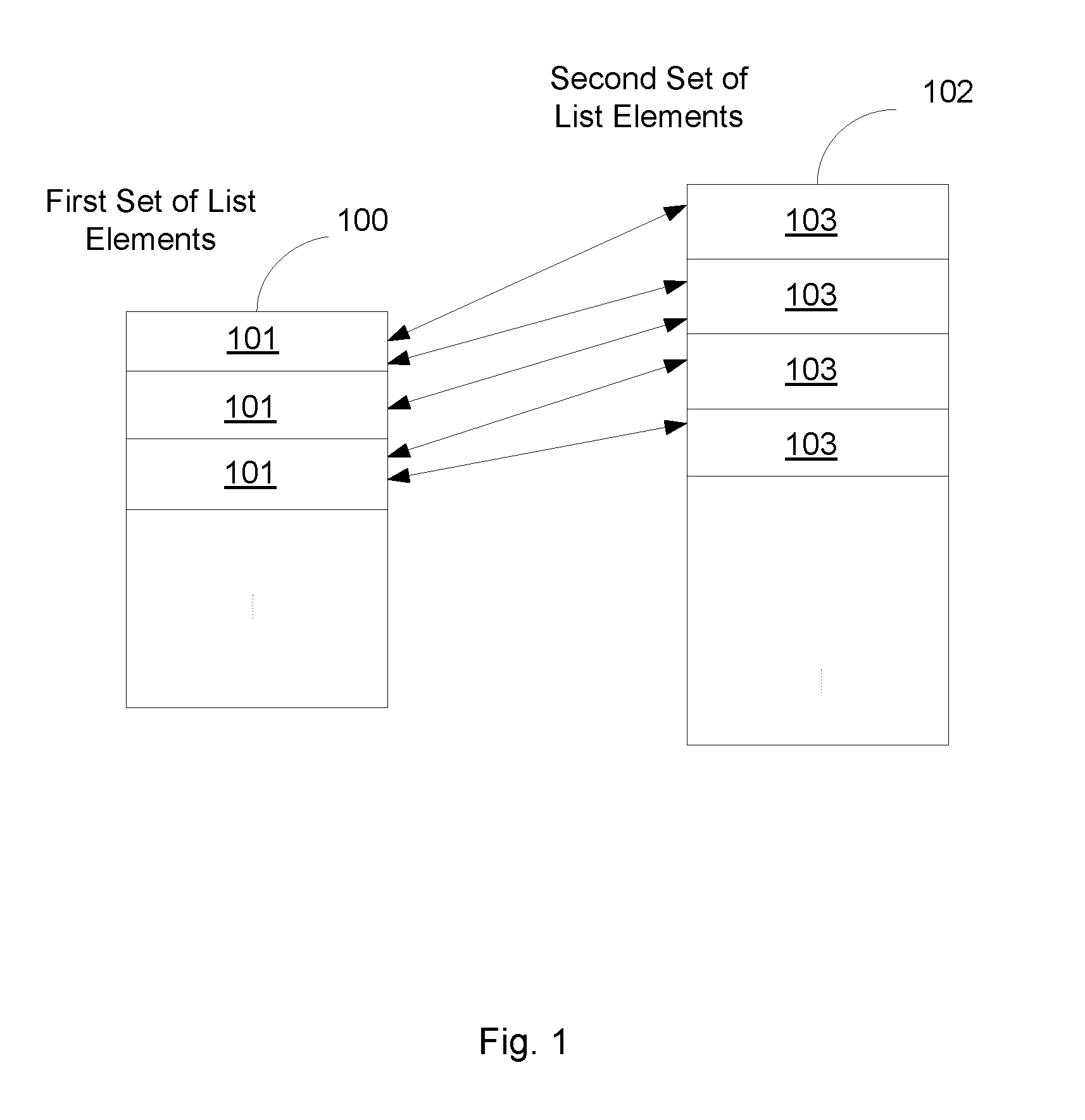
Speech Recognition Method for Selecting a Combination of List Elements via a Speech Input
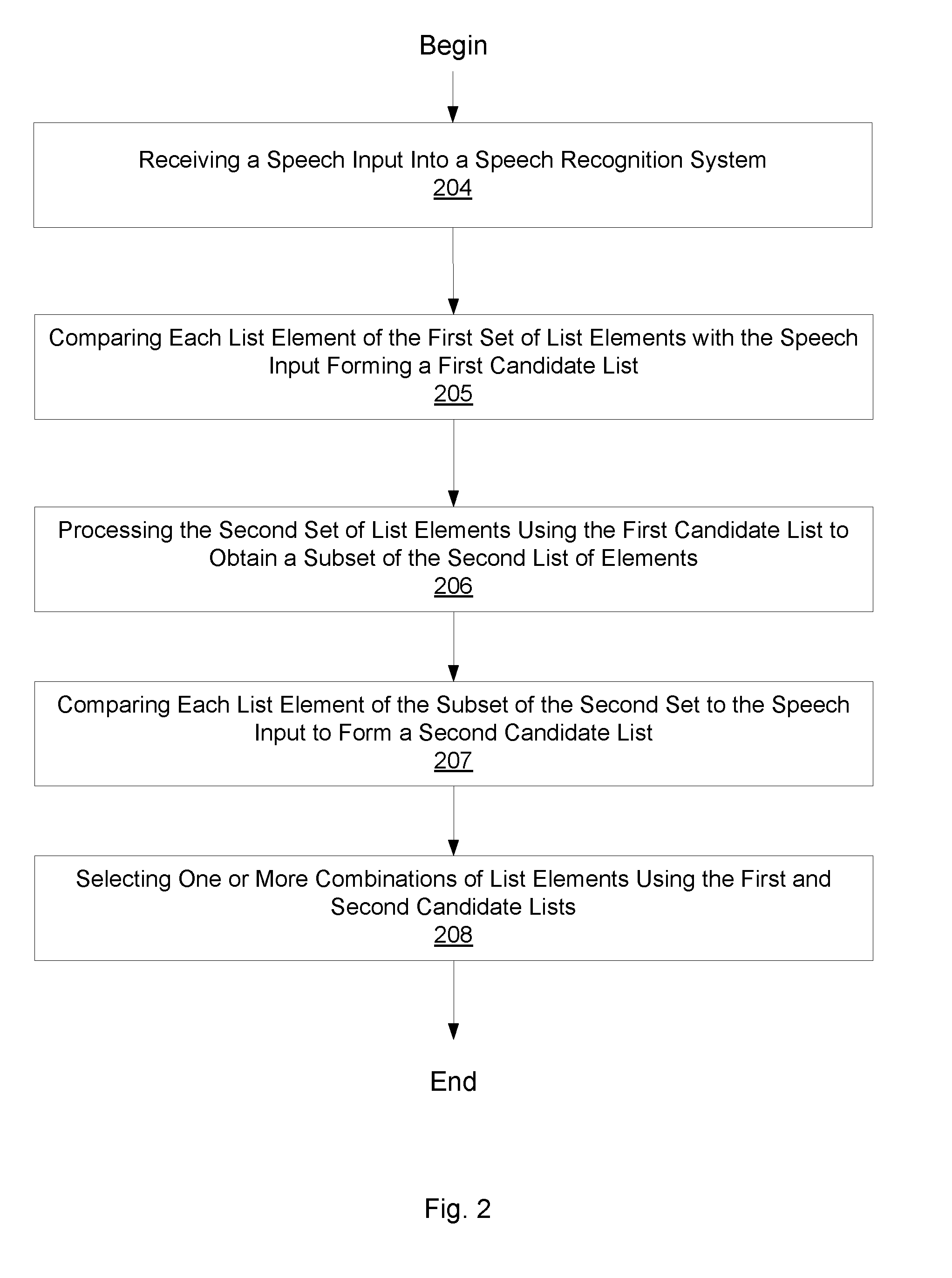
The invention provides a speech recognition method for selecting a combination of list elements via a speech input, wherein a first list element of the combination is part of a first set of list elements and a second list element of the combination is part of a second set of list elements, the method comprising the steps of receiving the speech input, comparing each list element of the first set with the speech input to obtain a first candidate list of best matching list elements, processing the second set using the first candidate list to obtain a subset of the second set, comparing each list element of the subset of the second set with the speech input to obtain a second candidate list of best matching list elements, and selecting a combination of list elements using the first and the second candidate list.
Owner:CERENCE OPERATING CO
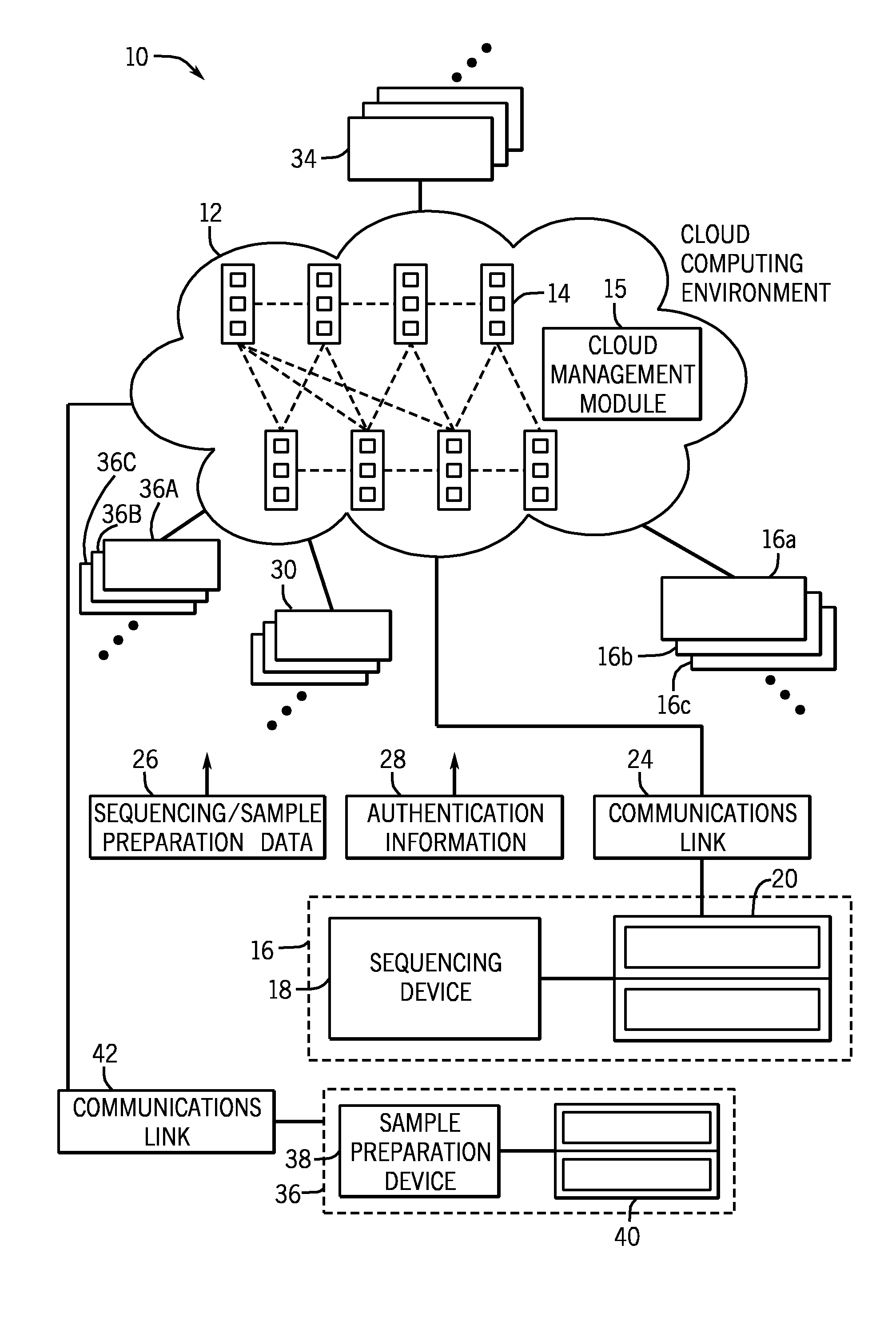
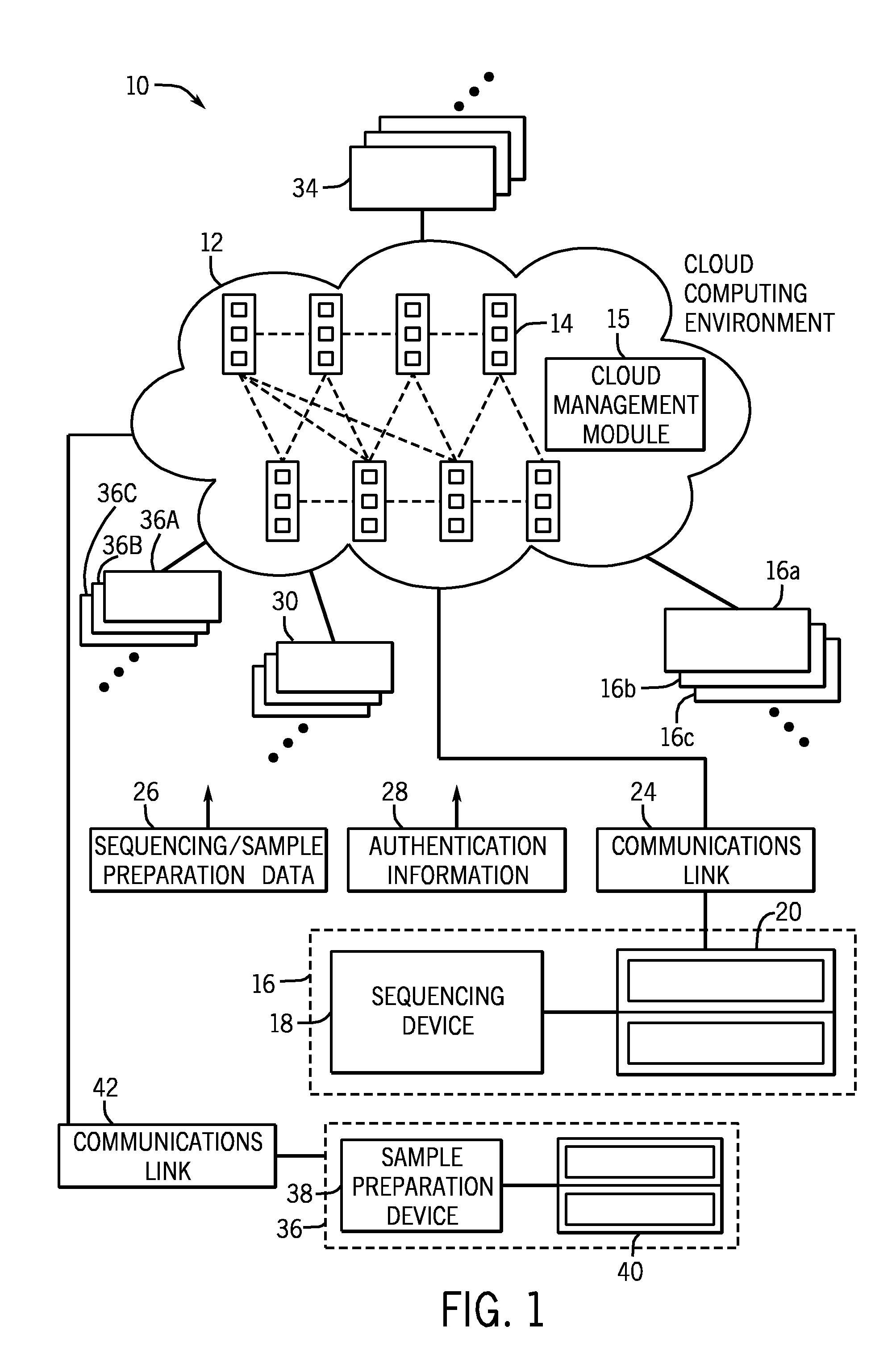
Methods and systems for using a cloud computing environment to share biological related data
ActiveUS20140214579A1Reduce processReduce storage burdenBuying/selling/leasing transactionsSequence analysisCloud baseAnalysis method
The present disclosure provides a novel approach for shifting or distributing various information (e.g., protocols, analysis methods, sample preparation data, sequencing data, etc.) to a cloud-based network. For example, the techniques relate to a cloud computing environment configured to receive this information from one or more individual sample preparation devices, sequencing devices, and / or computing systems. In turn, the cloud computing environment may generate information for use in the cloud computing environment and / or to provide the generated information to the devices to guide a genomic analysis workflow. Further, the cloud computing environment may be used to facilitate the sharing of sample preparation protocols for use with generic sample preparation cartridges and / or monitoring the popularity of the sample preparation protocols.
Owner:ILLUMINA INC
Destination systems and methods for performing data replication
InactiveUS20070185937A1Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Network redirector systems and methods for performing data replication
InactiveUS7962709B2Reduce impactReduce memory requirementsDigital data information retrievalDigital data processing detailsTemporal informationNetwork redirector
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Efficient Logging for Asynchronously Replicating Volume Groups
ActiveUS20110099342A1The process is compact and efficientReduce memoryMemory loss protectionError detection/correctionAuxiliary memoryData store
A system and method for logging for asynchronously replicating volume groups. A write request to write data to a location in a volume may be received. Metadata associated with the write request may be stored. It may be determined if the write request possibly overlaps with one or more earlier write requests to the volume that have not yet been replicated to a secondary storage. The data may be stored in a replication log only if the write request possibly overlaps with one or more earlier write requests to the volume. The data may not be stored in the replication log if the write request does not overlap with one or more earlier write requests to the volume. The data may be written to the location in the volume. Changes to the volume may periodically be replicated to the secondary storage using the replication log.
Owner:VERITAS TECH
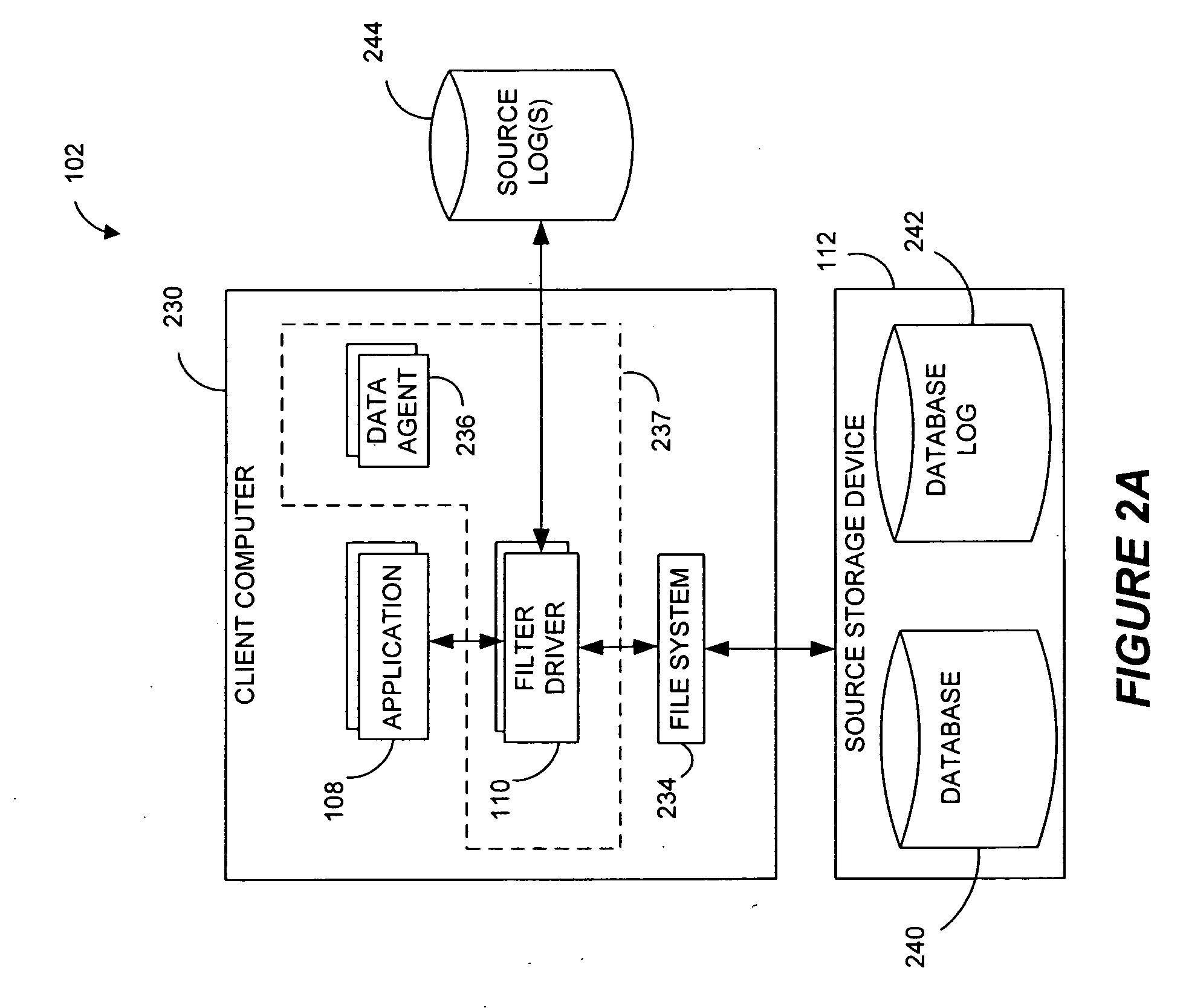
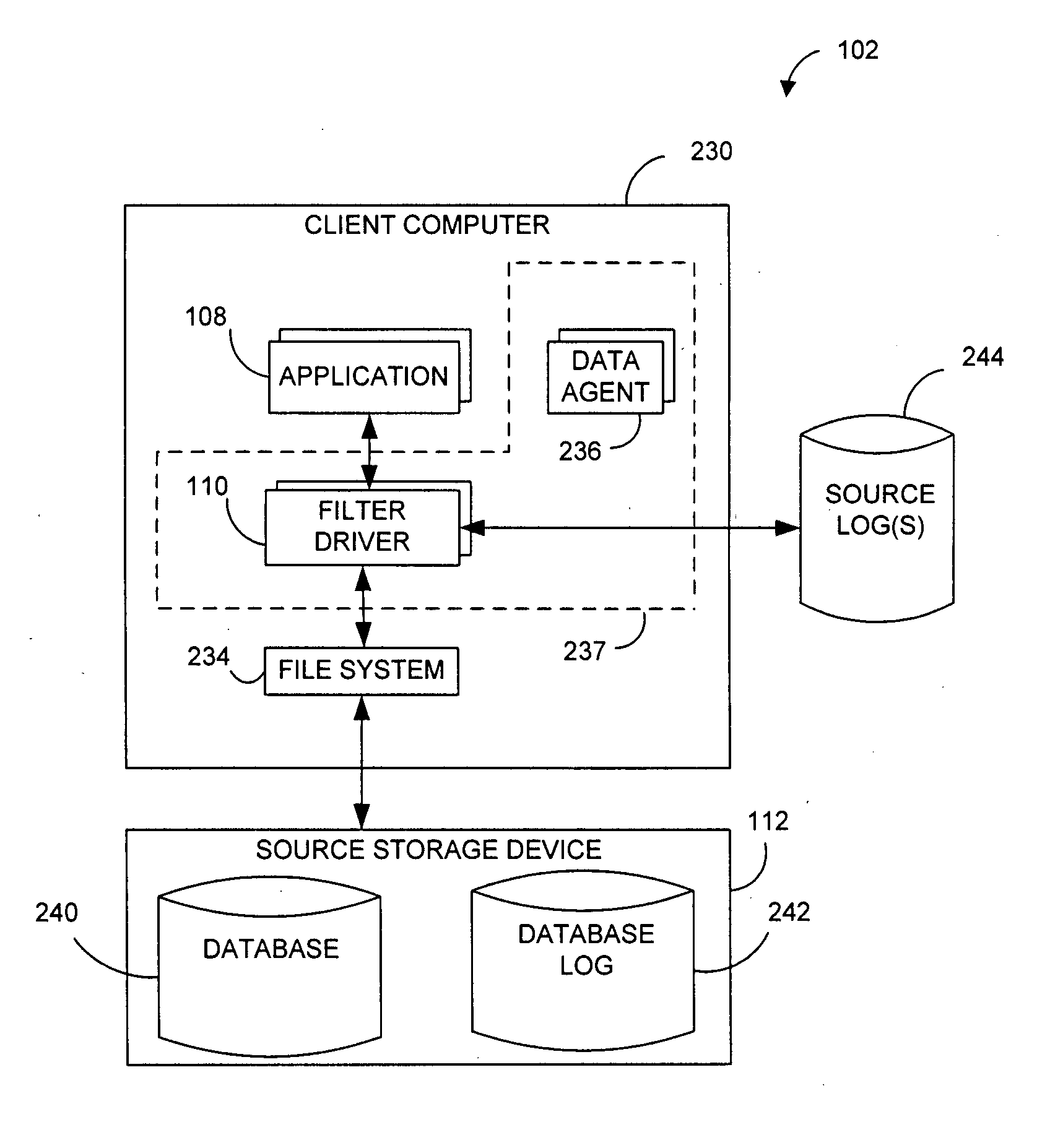
Systems and methods for monitoring application data in a data replication system
InactiveUS20070185939A1Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationGoal system
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
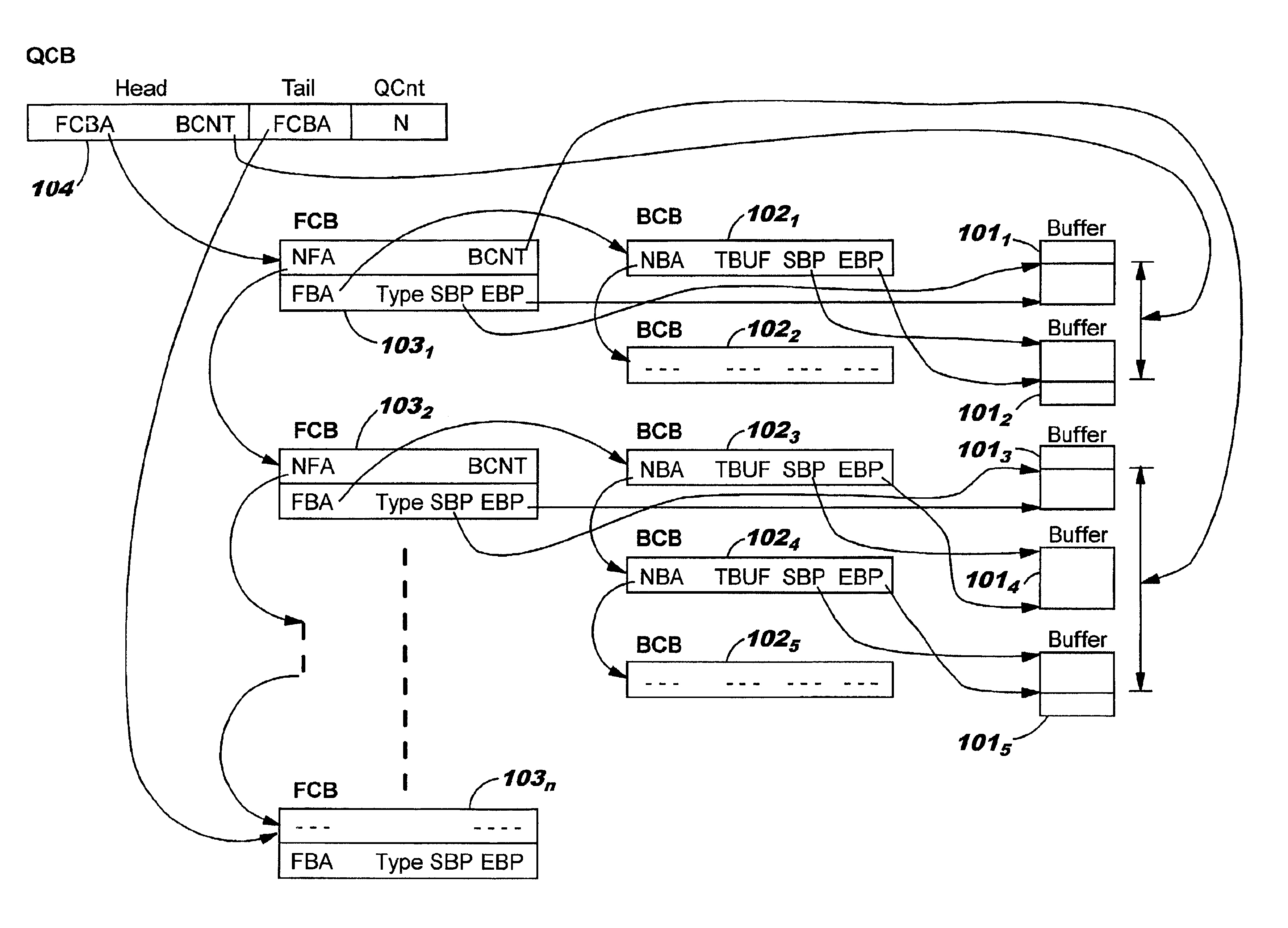
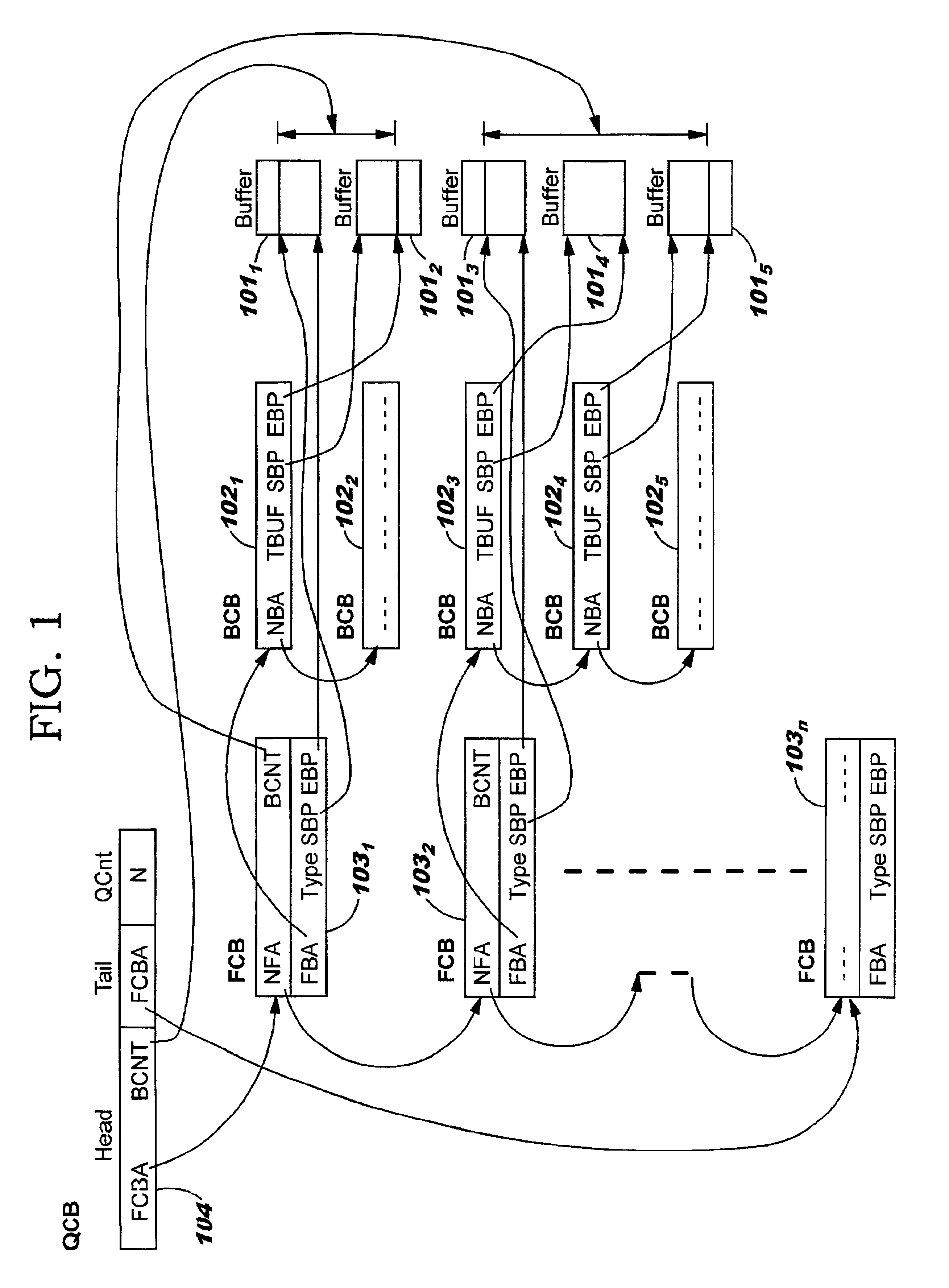
Buffer configuration for a data replication system
InactiveUS20070183224A1Reduce impactReduce memory requirementsError detection/correctionDatabase distribution/replicationTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Rolling cache configuration for a data replication system
InactiveUS20070226438A1Reduce impactReduce memory requirementsMemory loss protectionDigital data processing detailsTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
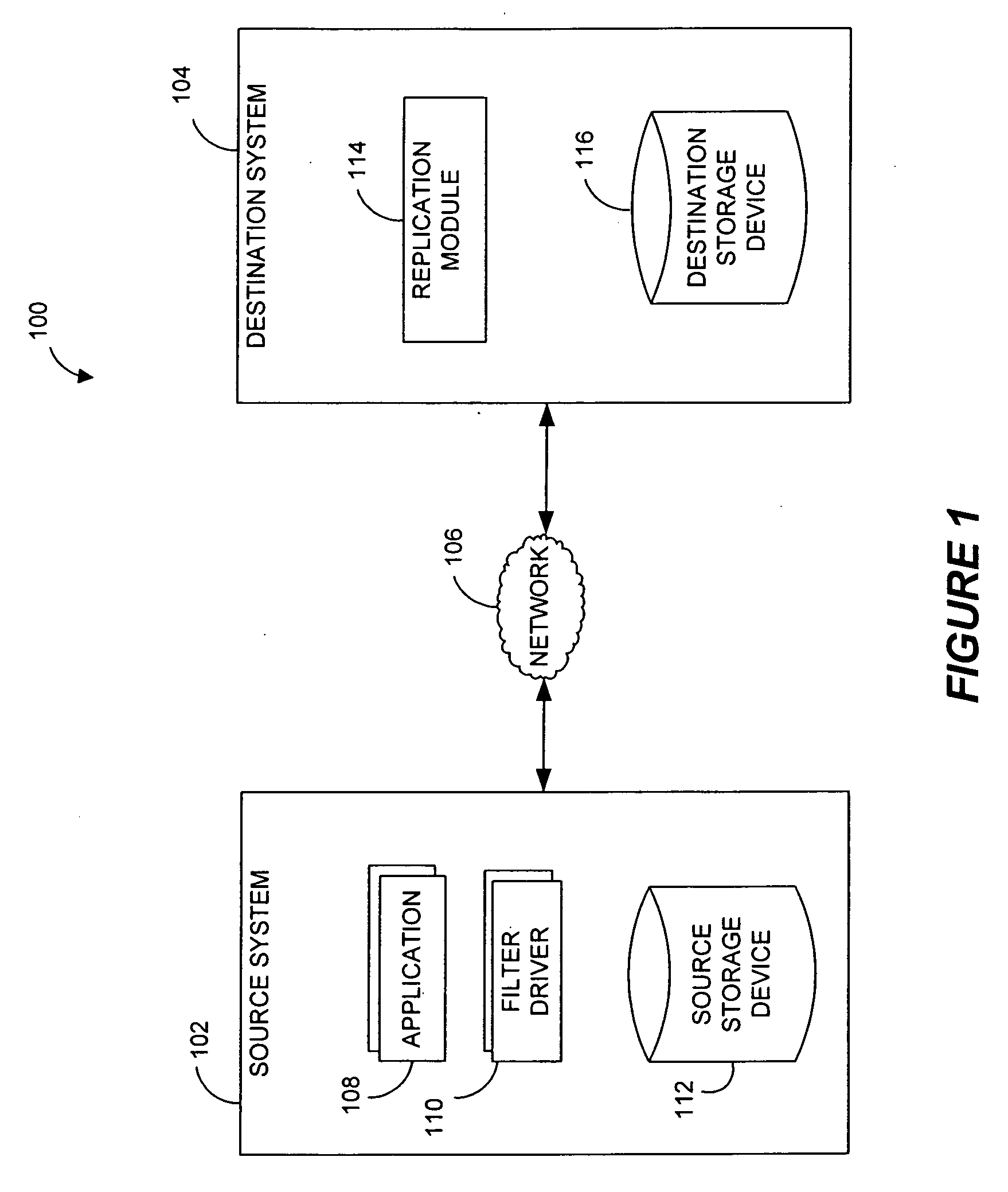
Pathname translation in a data replication system
InactiveUS20070185852A1Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationGoal system
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Data structures for efficient processing of multicast transmissions
InactiveUS6836480B2Reduce memory requirementsEliminate needSpecial service provision for substationTime-division multiplexArray data structureTransport system
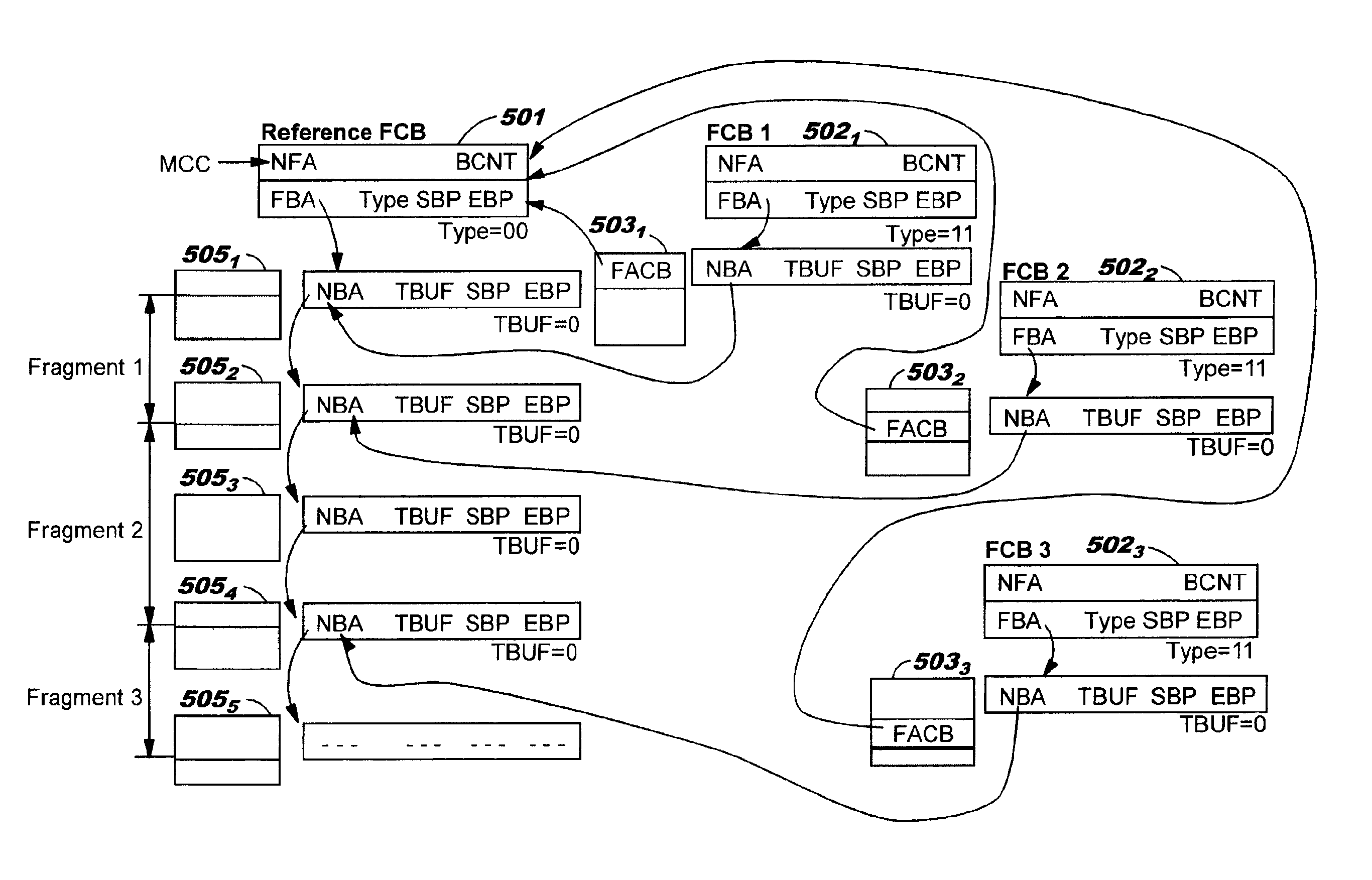
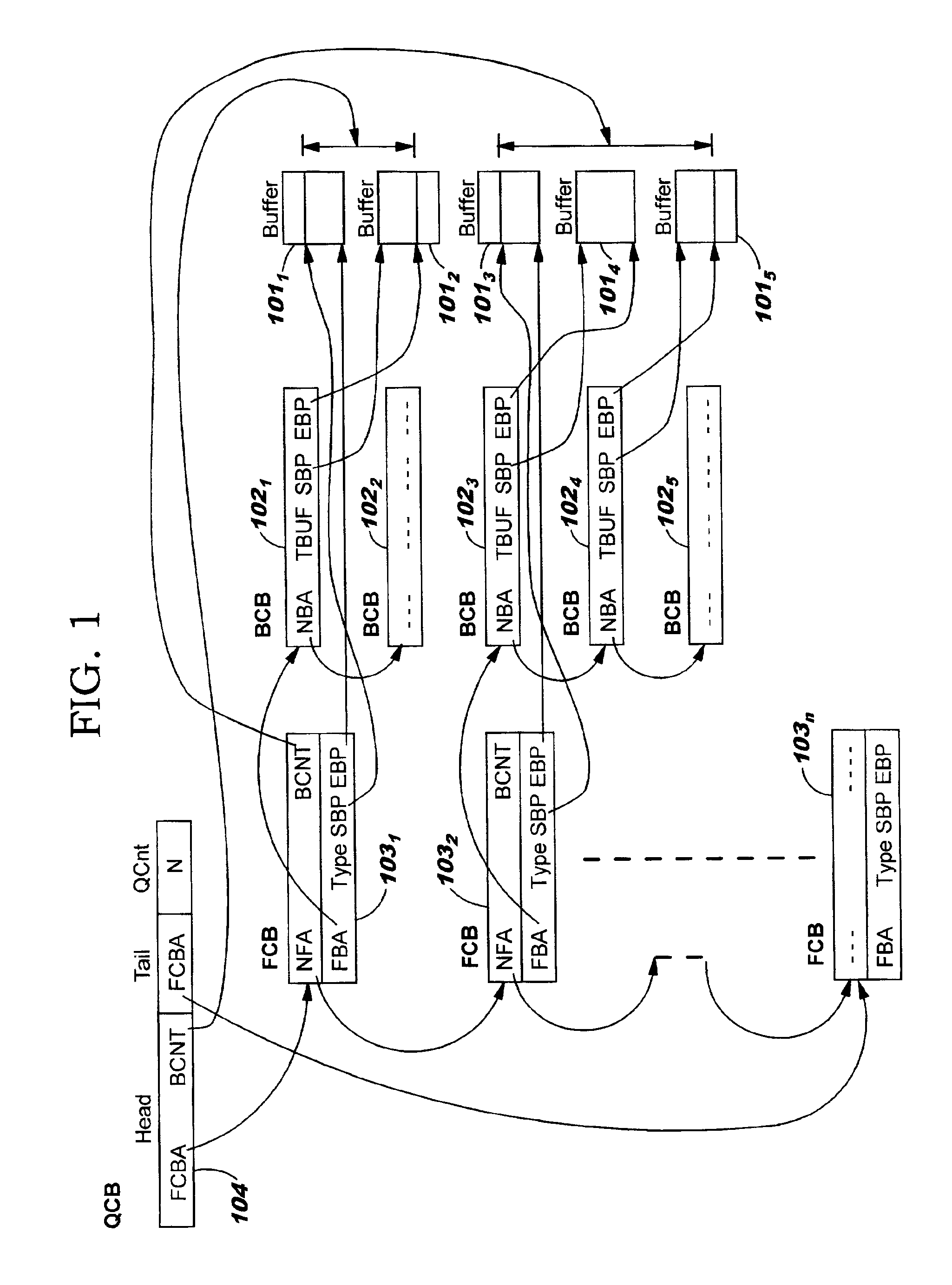
Data structures, a method, and an associated transmission system for multicast transmission on network processors in order both to minimize multicast transmission memory requirements and to account for port performance discrepancies. Frame data for multicast transmission on a network processor is read into buffers to which are associated various control structures and a reference frame. The reference frame and the associated control structures permit multicast targets to be serviced without creating multiple copies of the frame. Furthermore this same reference frame and control structures allow buffers allocated for each multicast target to be returned to the free buffer queue without waiting until all multicast transmissions are complete.
Owner:ACTIVISION PUBLISHING
Systems and methods for managing replicated database data
ActiveUS8204859B2Reduce memory requirementsImprove performanceDigital data processing detailsError detection/correctionDatabase applicationApplication software
Systems and methods for replicating database data and generating read-only copies of the replicated data in a clean shutdown state. For example, systems can include a tracking module (e.g., a filter driver) that monitors transactions from a database application to a source storage device to generate log entries having at least one marker indicating a known good state of the application. The systems further include a computer coupled to a target storage device comprising a database and log files. The computer processes the transactions, based on the log entries, to replicate data to the target storage device; performs a first snapshot on data stored in the database and log files; replays into the database data stored in the log files; performs another snapshot on the database; and reverts the database back to a state in which the database existed at the time of the first snapshot.
Owner:COMMVAULT SYST INC
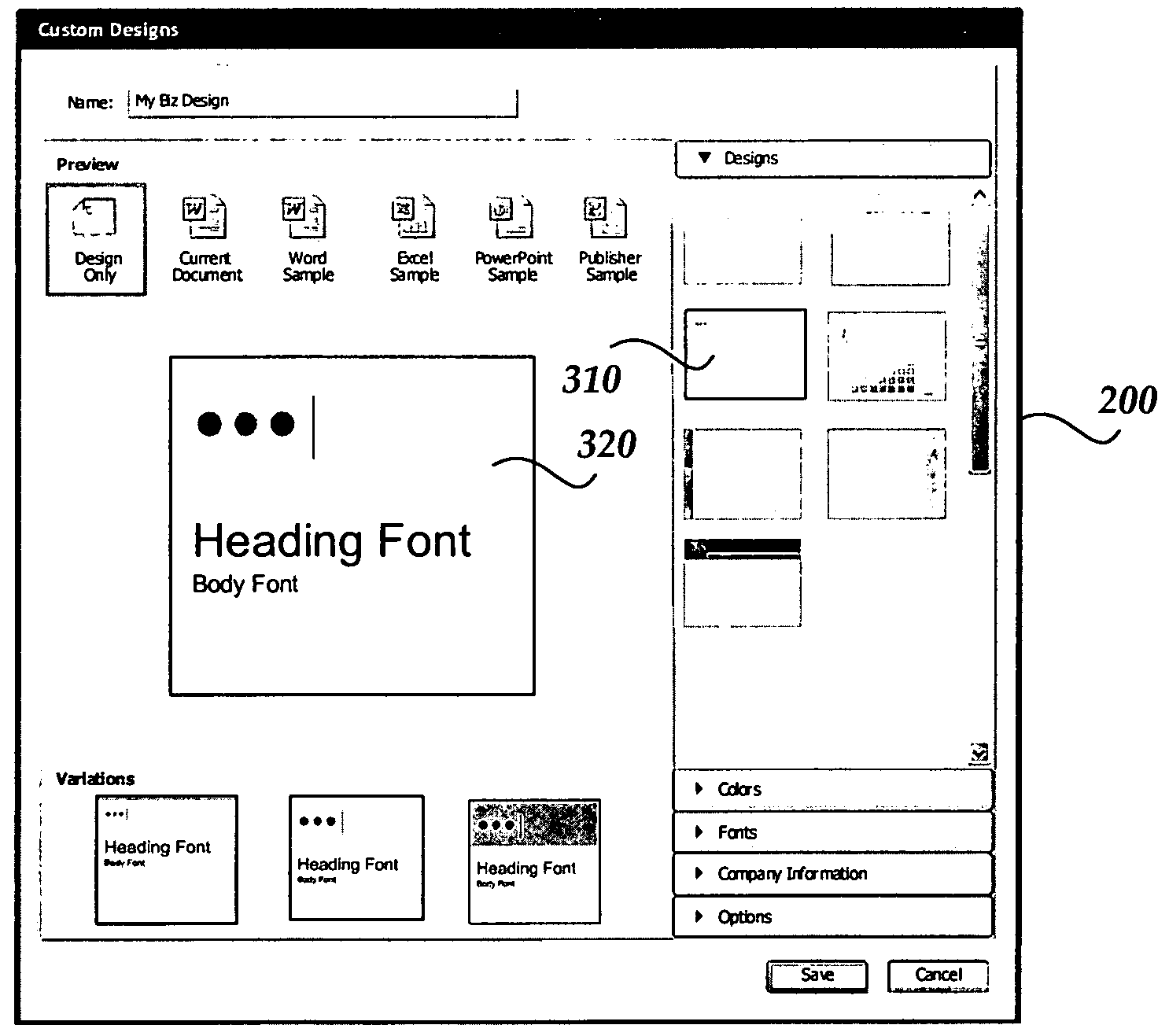
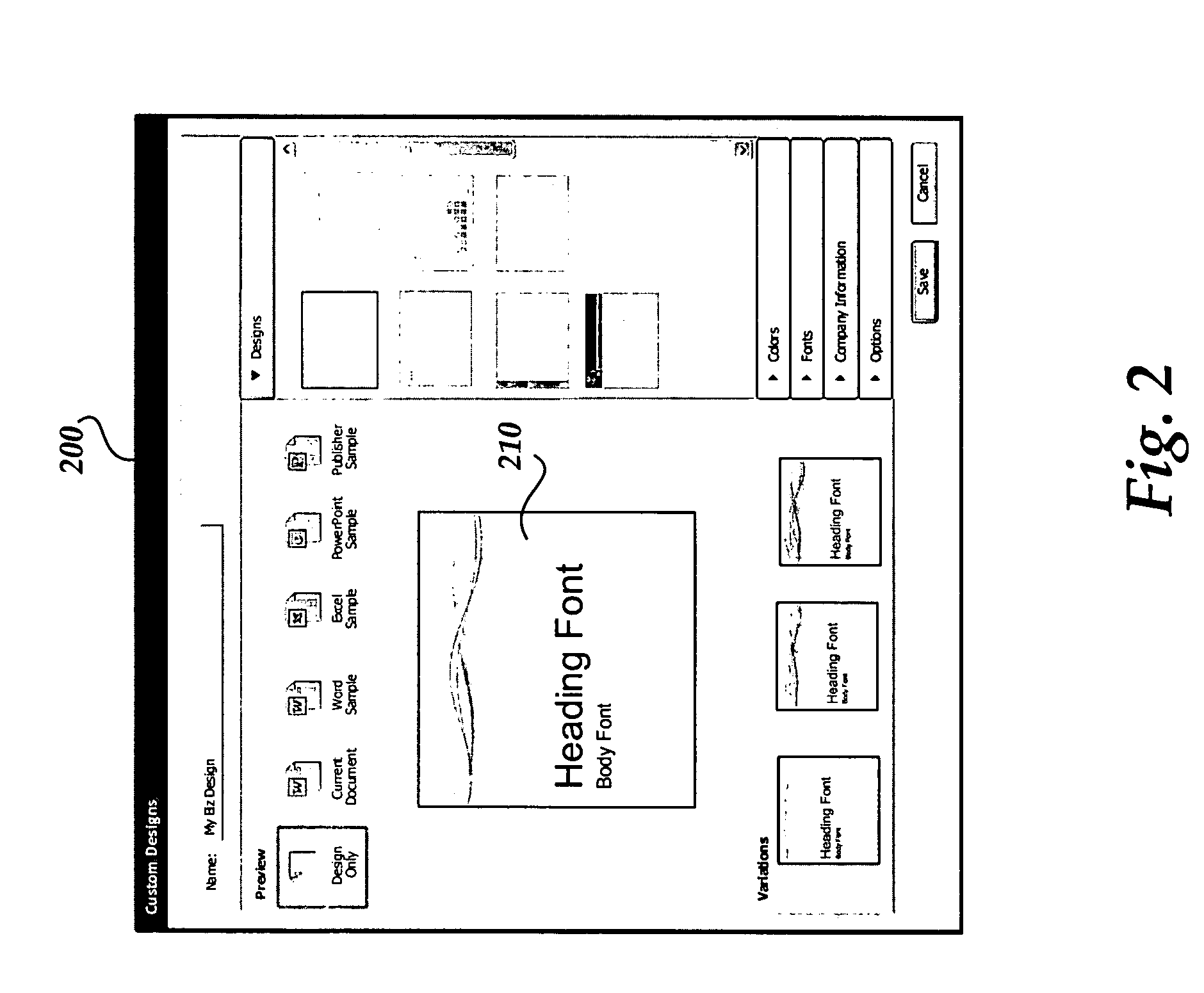
Dynamic document and template previews
InactiveUS7469380B2Improve performanceReduce memory requirementsNatural language data processingSpecial data processing applicationsDocumentation procedureDocument preparation
Methods and systems are provided for dynamically generating and displaying previews of documents or templates of interest to a user. As a user provides or selects customized designs or themes, including color themes, font types, images, and the like, previews of one or more documents or templates to which the user selected designs or themes are applied are dynamically generated and are displayed to allow the user to select an actual document or template for use.
Owner:MICROSOFT TECH LICENSING LLC
Methods for tag-grouping of blocks in storage devices
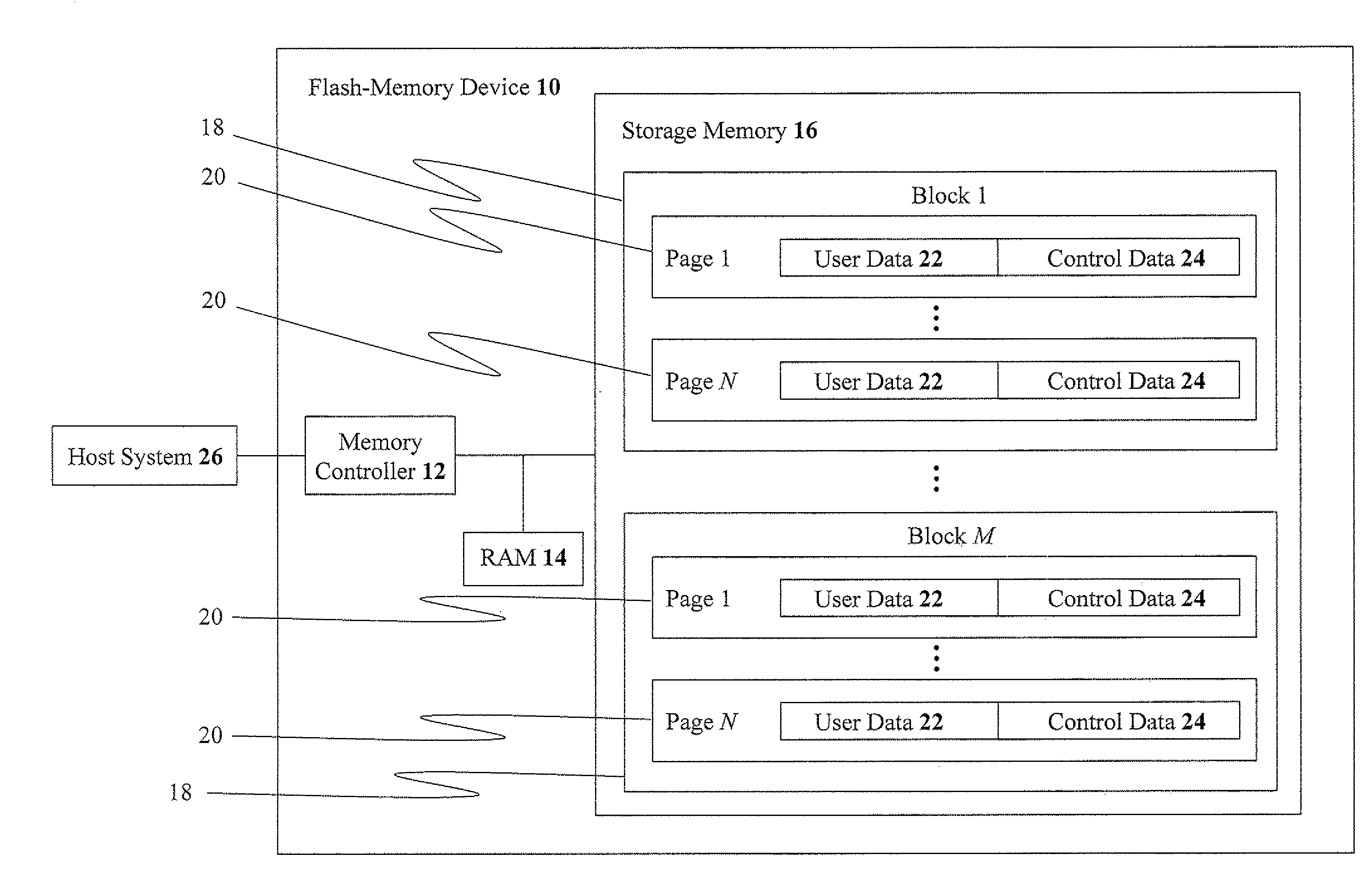
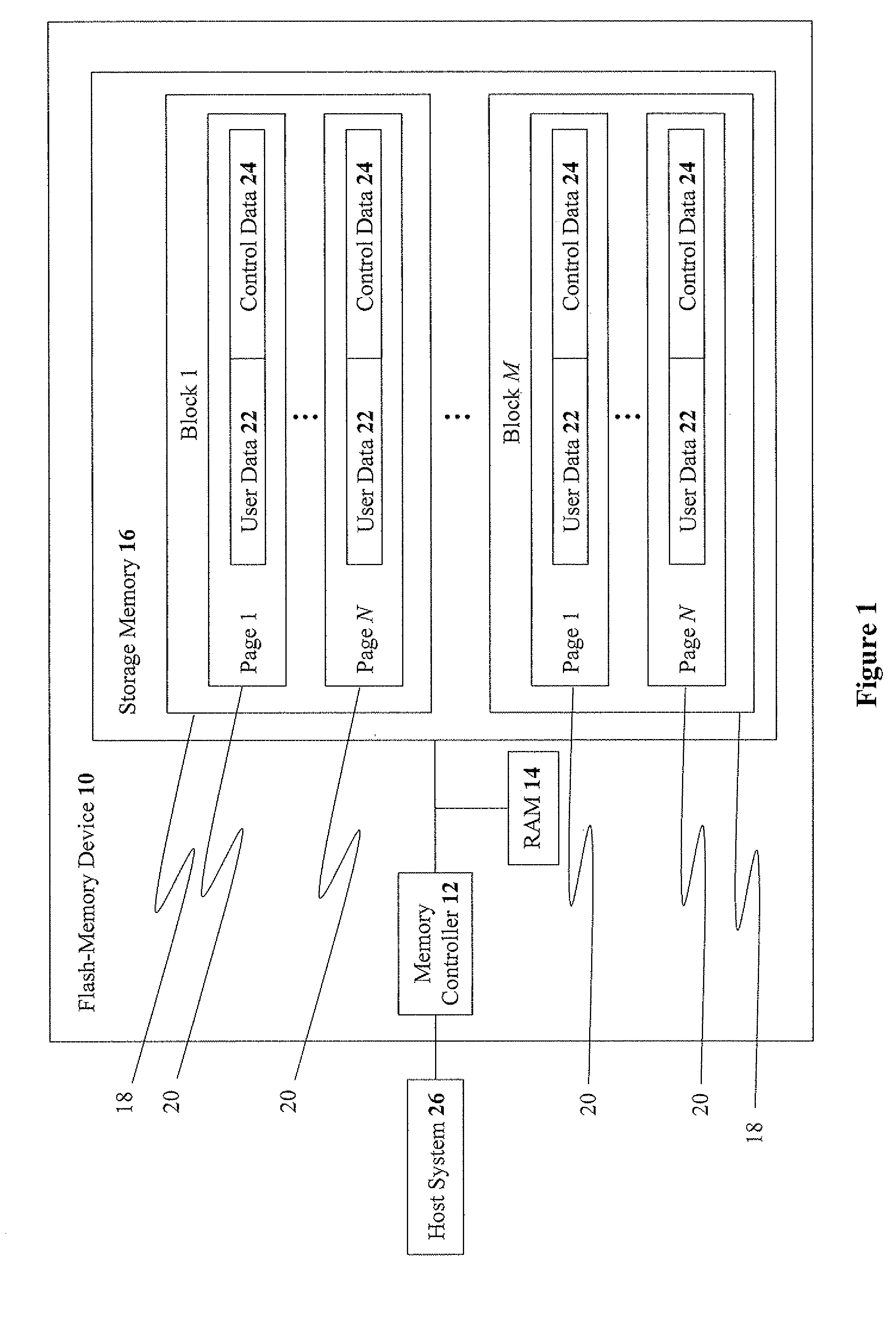
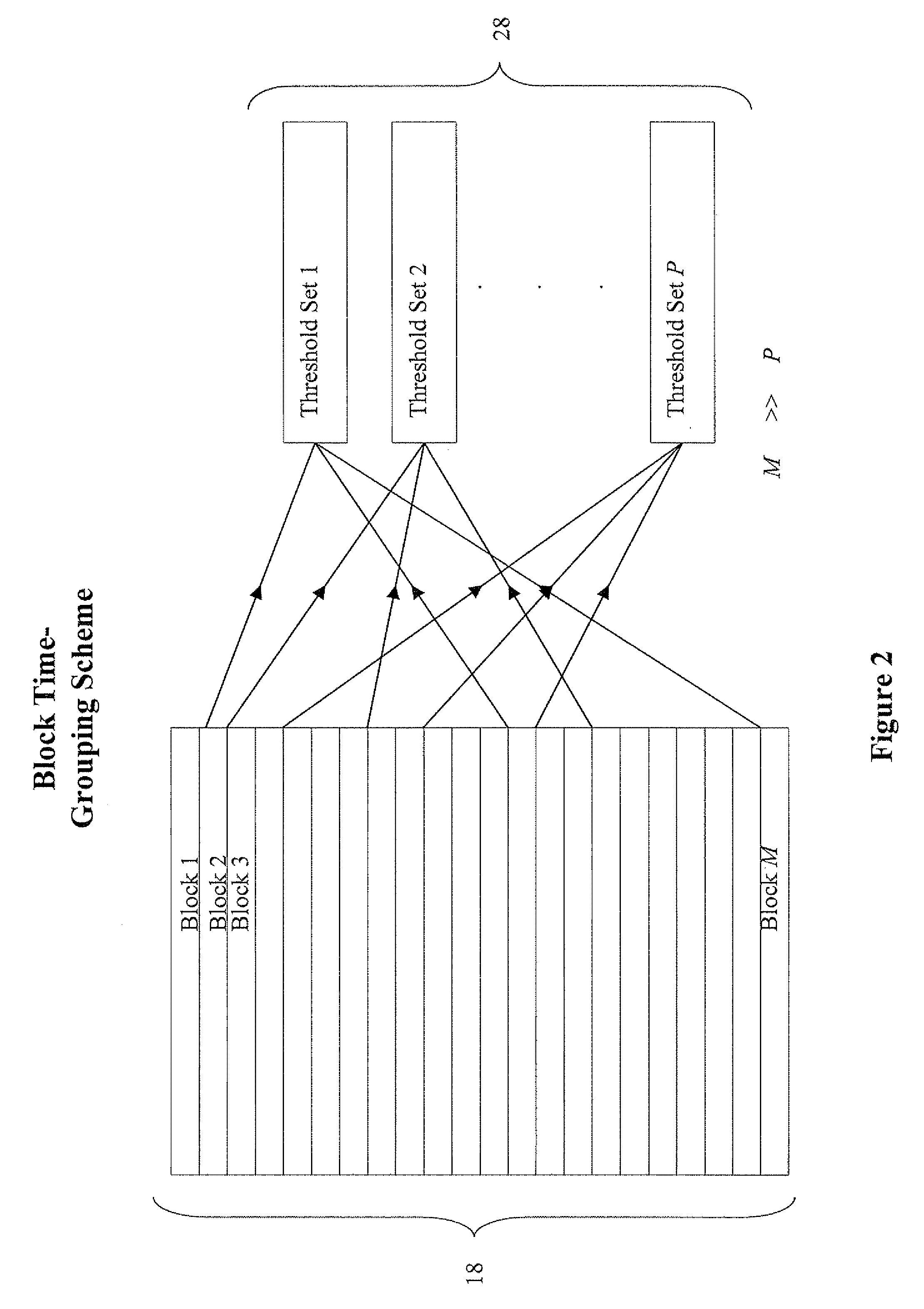
ActiveUS20100131697A1Improve accuracyAccuracy is compromisedMemory loss protectionError detection/correctionMetadataBlock group
Embodiments described herein disclose methods, devices, and media for storing data. Methods including the steps of: receiving data to be stored in a memory that includes at least three blocks, wherein each block, for storing the data, has at least one metadata value, associated with each block, that is dependent upon a writing time of each block; grouping at least three blocks into at least two block groups, wherein at least one block group contains at least two blocks; associating a respective metadata value with each block group; and associating the respective metadata value of a respective block group with each block storing the data contained in the respective block group, without storing a dedicated copy of at least one metadata value for each block. In some embodiments, at least one metadata value is stored in a block-group table.
Owner:SANDISK TECH LLC
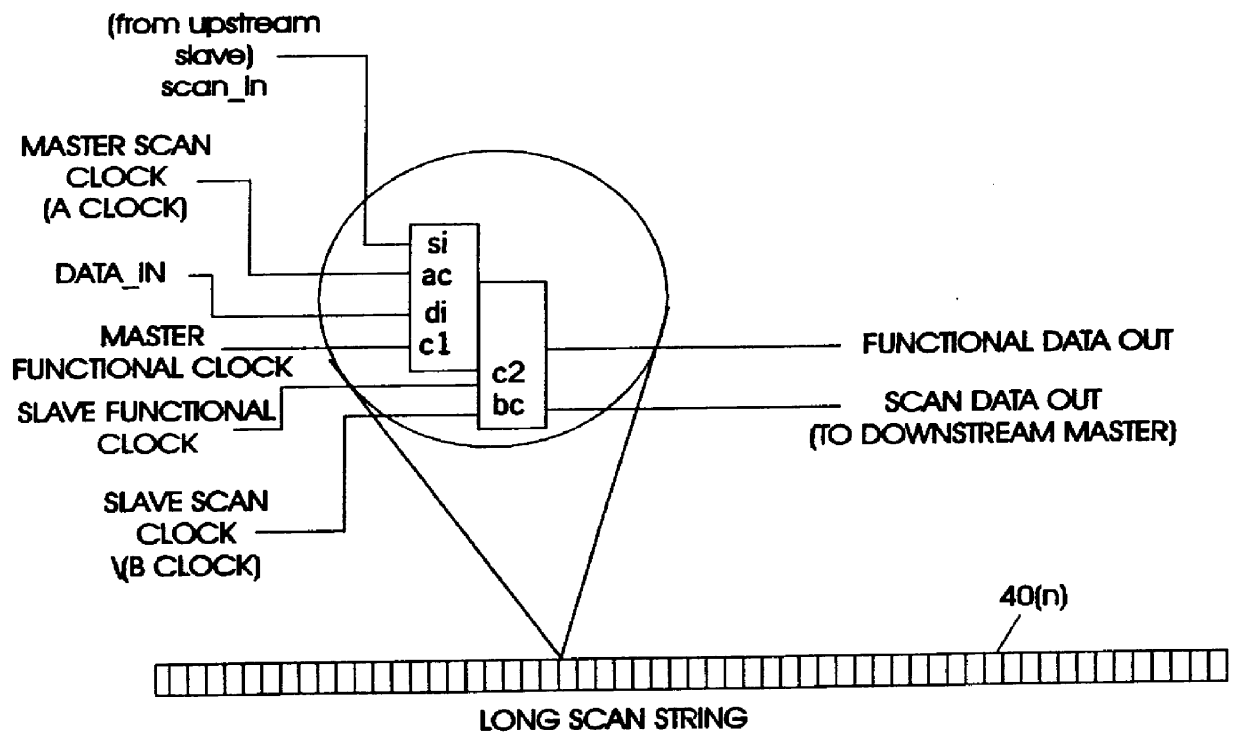
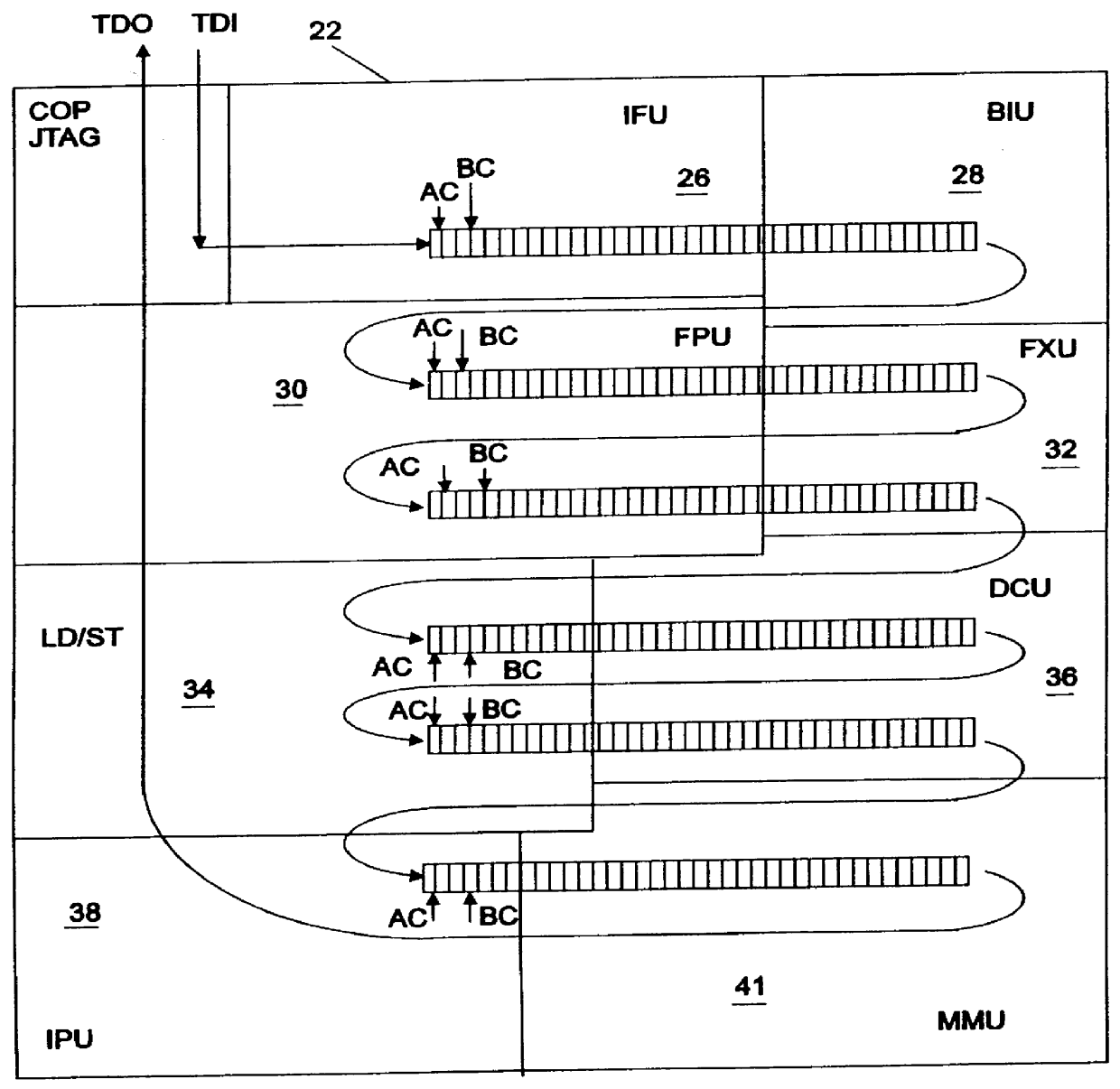
Apparatus and methods for testing a microprocessor chip using dedicated scan strings
InactiveUS6028983AReduce memory requirementsReduce scan timeElectronic circuit testingError detection/correctionTest inputJoint Test Action Group
A test apparatus and method for design verification of at least one microprocessor chip includes a compatible Joint Task Action Group (JTAG) terminal for access to a plurality of computer functional units contained in the chip. A test input terminal included in the JTAG terminal receives a scan string, the string being coupled to each computer functional unit through a first multiplexer. The scan input string is separated by the JTAG terminal under program control into a series of dedicated scan strings, each dedicated scan string being supplied to a selected functional unit through the first multiplexer. Each functional unit includes start and stop scan clocks for testing the functional under program control using the dedicated scan train for the functional unit. A test output terminal included in the JTAG terminal is coupled to each functional unit through a second multiplexer. The test results of the dedicated scan string under control of the scan clock are supplied to the output terminal through the second multiplexer. The compatible JTAG terminal includes further elements for controlling the scan clocks to select a targeted functional unit for testing purposes while the scan strings for non-targeted functional units remain in an inactive state.
Owner:GOOGLE LLC
Gigabit Ethernet Adapter
InactiveUS20070253430A1Fast communication speedCompact solutionWide area networksRaw socketSmall form factor
A gigabit Ethernet adapter provides a provides a low-cost, low-power, easily manufacturable, small form-factor network access module which has a low memory demand and provides a highly efficient protocol decode. The invention comprises a hardware-integrated system that both decodes multiple network protocols byte-streaming manner concurrently and processes packet data in one pass, thereby reducing system memory and form factor requirements, while also eliminating software CPU overhead. A preferred embodiment of the invention comprises a plurality of protocol state machines that decode network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, Raw Socket, RARP, ICMP, IGMP, iSCSI, RDMA, and FCIP concurrently as each byte is received. Each protocol handler parses, interprets, and strips header information immediately from the packet, requiring no intermediate memory. The invention provides an internet tuner core, peripherals, and external interfaces. A network stack processes, generates and receives network packets. An internal programmable processor controls the network stack and handles any other types of ICMP packets, IGMP packets, or packets corresponding to other protocols not supported directly by dedicated hardware. A virtual memory manager is implemented in optimized, hardwired logic. The virtual memory manager allows the use of a virtual number of network connections which is limited only by the amount of internal and external memory available.
Owner:NVIDIA CORP
System to monitor the health of a structure, sensor nodes, program product, and related methods
ActiveUS20070118301A1Reduce the amount requiredReduce bandwidth requirementsProgramme controlTesting/monitoring control systemsState of healthSensor node
A system to monitor the health of a structure, health monitoring sensor nodes, program product, and associated methods are provided. The system includes an array of health monitoring sensor nodes connected to or embedded within a structure to monitor the health of the structure. Each health monitoring sensor node includes sensor elements positioned to sense parameters of the structure and to provide data related to the parameters to a health monitoring sensor node interrogator. Each health monitoring sensor node includes a processor or other means reducing raw sensor data to thereby reduce communication bandwidth requirements, and can include memory or other storage for storing the reduced data and an antenna arrangement for providing the reduced data to the health monitoring sensor node interrogator.
Owner:LOCKHEED MARTIN CORP
Data structures for efficient processing of IP fragmentation and reassembly
InactiveUS6937606B2Requires minimizationReduce memory requirementsTime-division multiplexData switching by path configurationArray data structureIP fragmentation
Data structures, a method, and an associated transmission system for IP fragmentation and IP reassembly on network processors in order to minimize memory allocation requirements. Frame data for IP fragmentation or reassembly on a network processor is read into buffers to which are associated various control structures. The control structures permit IP fragmentation or reassembly to be accomplished without creating multiple copies of the frame or fragments.
Owner:IBM CORP
Object recognition with reduced neural network weight precision
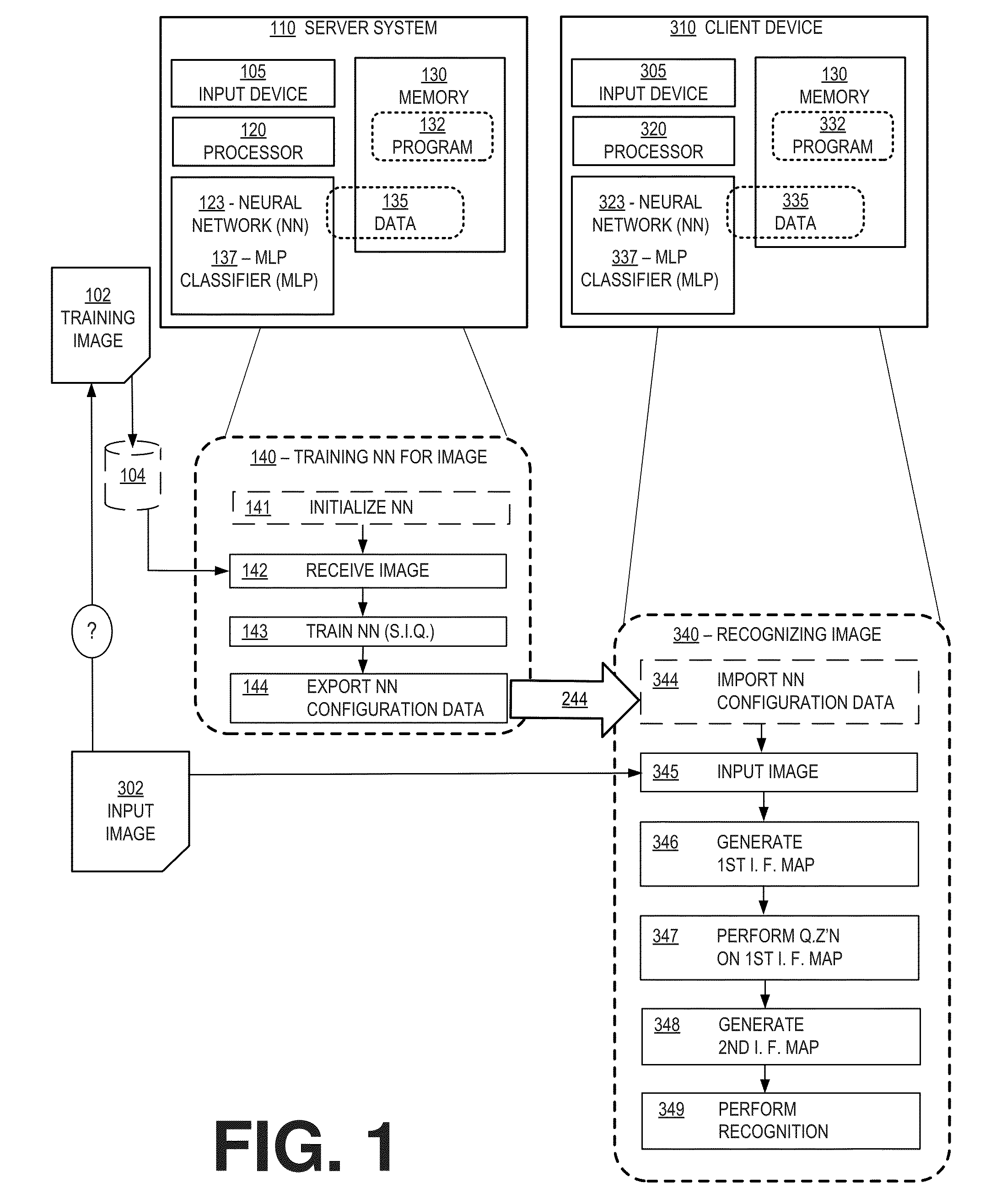
ActiveUS20160086078A1Conserve costReduce memory requirementsImage enhancementImage analysisCommunication interfaceNerve network
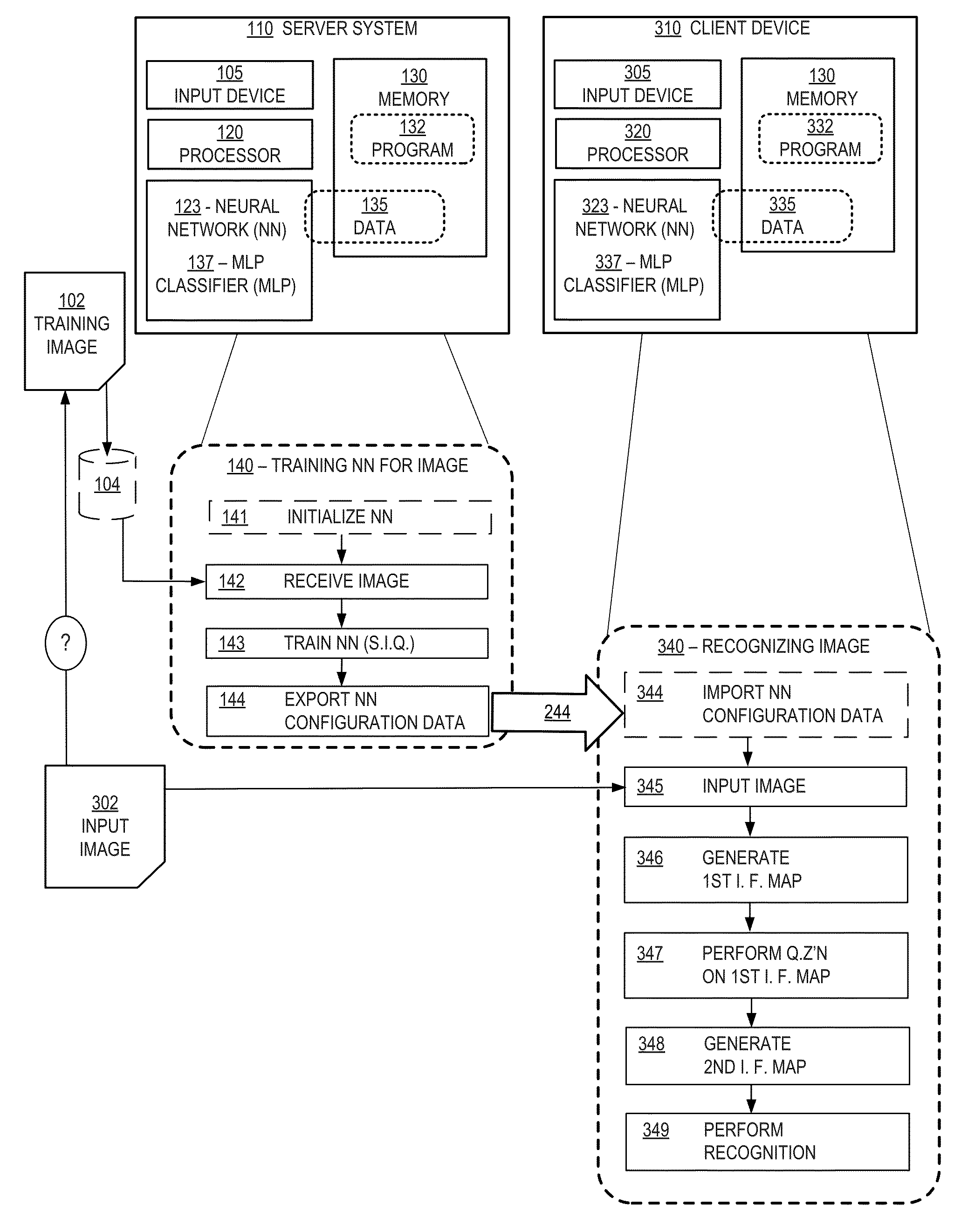
A client device configured with a neural network includes a processor, a memory, a user interface, a communications interface, a power supply and an input device, wherein the memory includes a trained neural network received from a server system that has trained and configured the neural network for the client device. A server system and a method of training a neural network are disclosed.
Owner:SAMSUNG ELECTRONICS CO LTD
Virtual message persistence service
InactiveUS7546284B1Reduce storageReduce memory requirementsDigital data information retrievalDigital data processing detailsDigital dataHigh availability
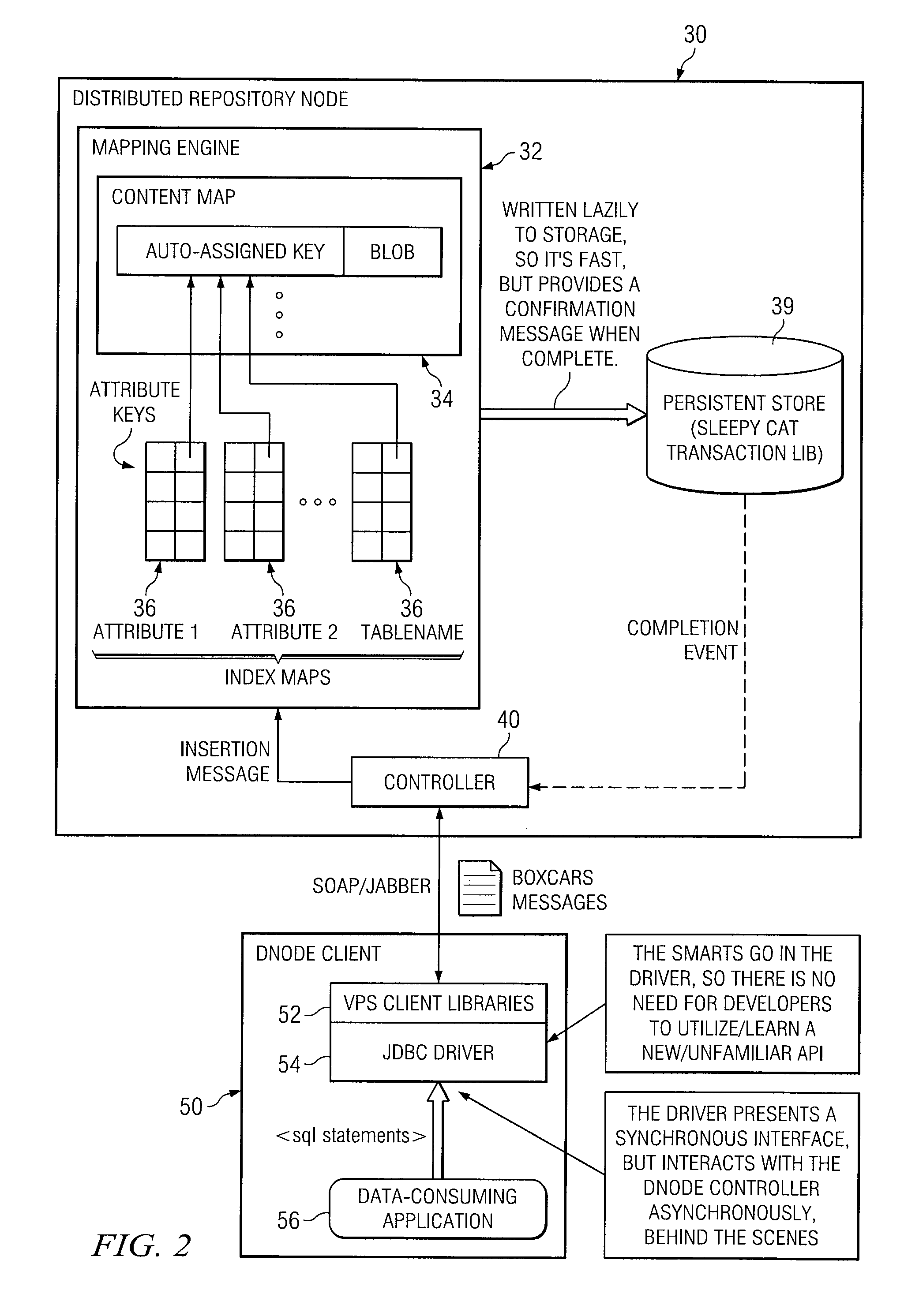
Methods, apparatuses and systems directed to a distributed data repository system including a plurality of symmetric data repository nodes. In certain embodiments of the present invention, the distributed data repository system is message-centric operative to store message payloads transmitted from client nodes. In certain embodiments, the distributed data repository system is BLOB-centric, maintaining binary data objects and indexes of attribute values that map to the binary data objects. Of course, the present invention can be utilized to store a great variety of digital data contained in message payloads. According to certain embodiments of the present invention, the attribute indexes are fully replicated across all data repository nodes, while the message payloads (e.g., data objects or other content) are exchanged across data repository nodes as needed to fulfill client queries. In this manner, each data repository node in the distributed system can fulfill any client request, while reducing the storage and memory requirements for each data repository node. The reduced storage and computational requirements enable each distributed data repository node to be hosted by an inexpensive hardware platform and, therefore, allow for the deployment of large numbers of distributed data repository nodes to achieve a distributed data repository system featuring high availability and reliability. In certain embodiments, each distributed data repository node is further equipped to act as an instant messaging (or other one-way messaging) server to allow client nodes to establish instant messaging connections with the data repository nodes in the distributed system.
Owner:AKANA
Apparatus and Method for Generating a Data File or for Reading a Data File
InactiveUS20080256431A1Reduced working memory requirementIncrease in file sizeMetadata audio data retrievalSpecial data processing applicationsData fileComputer science
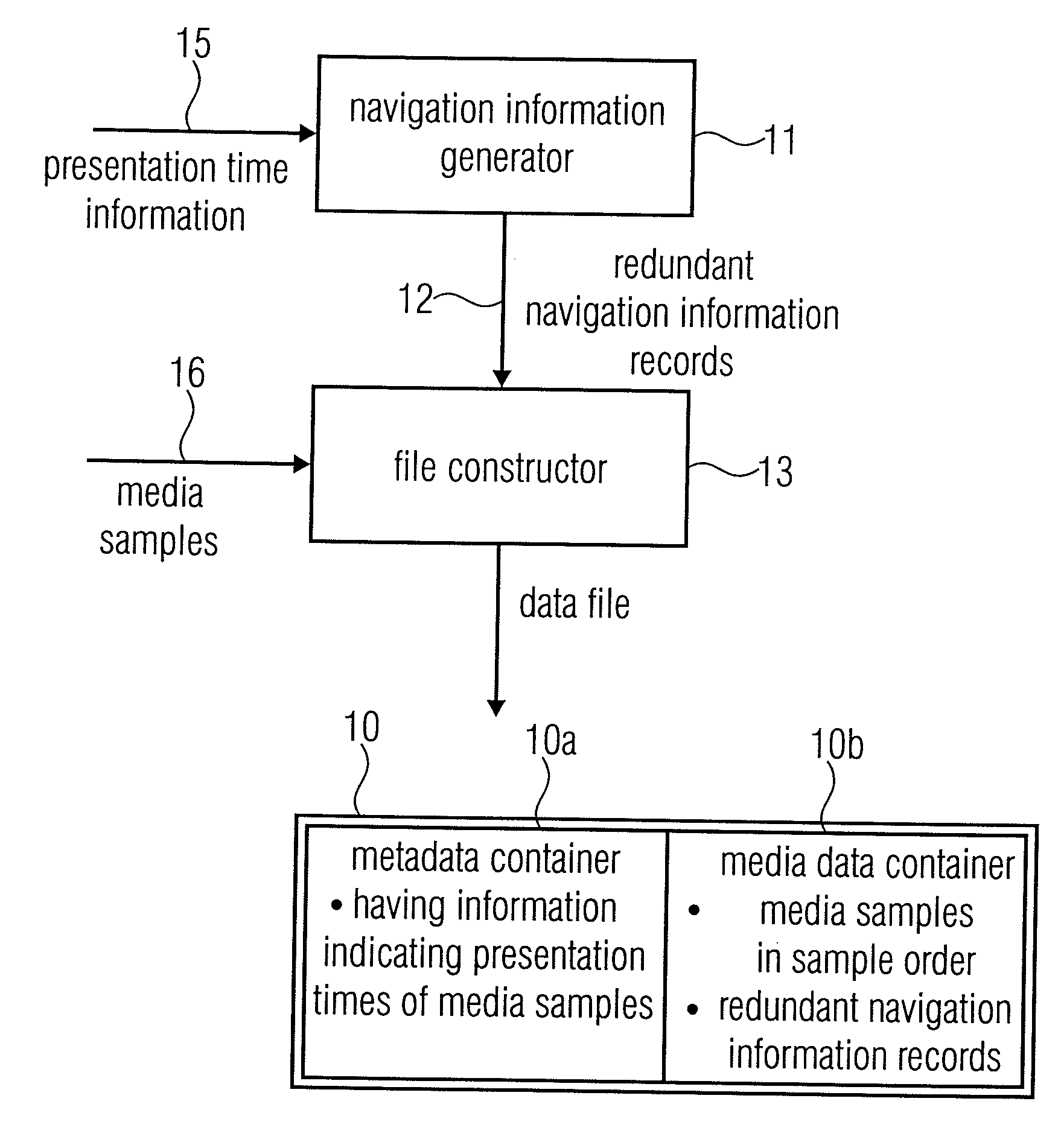
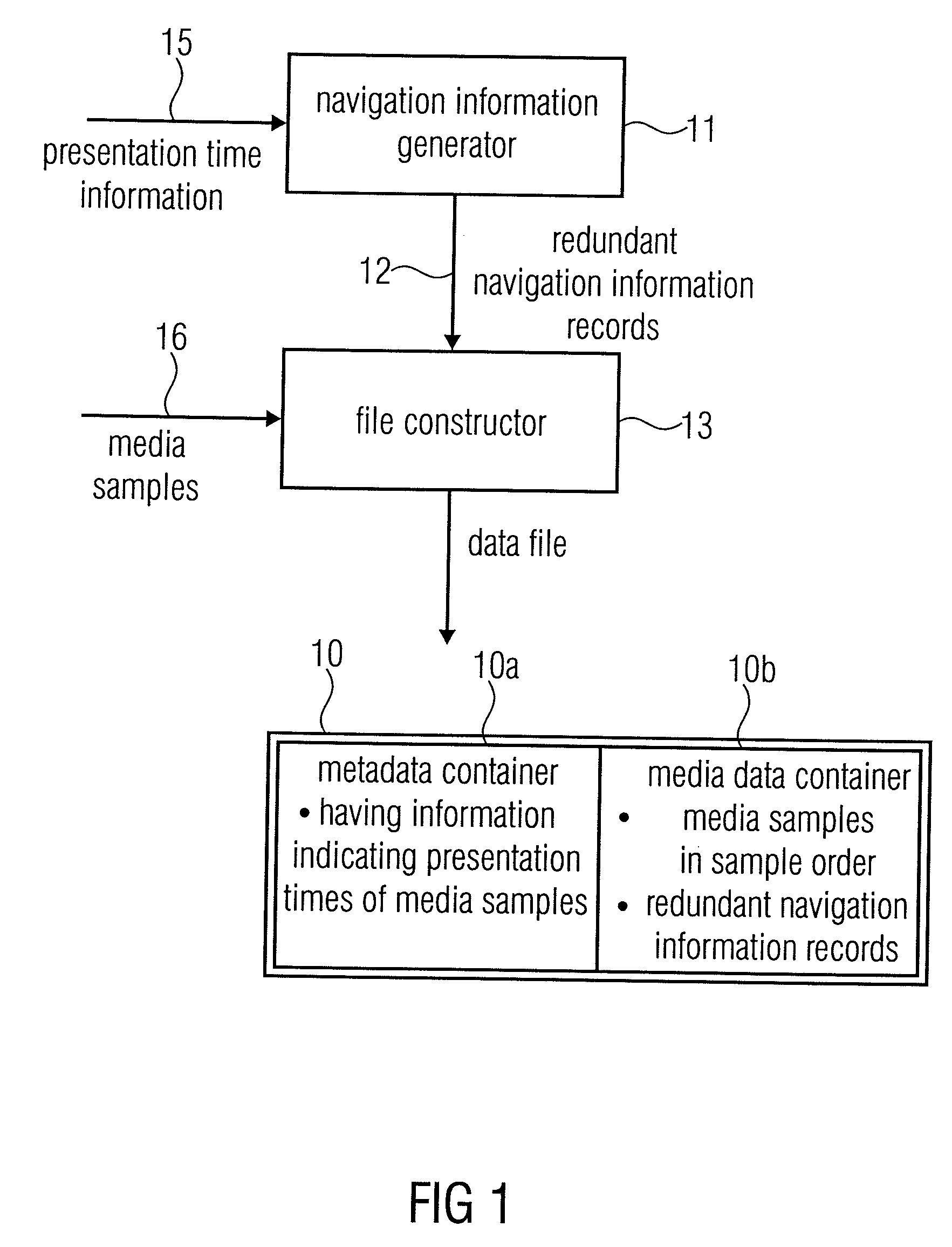
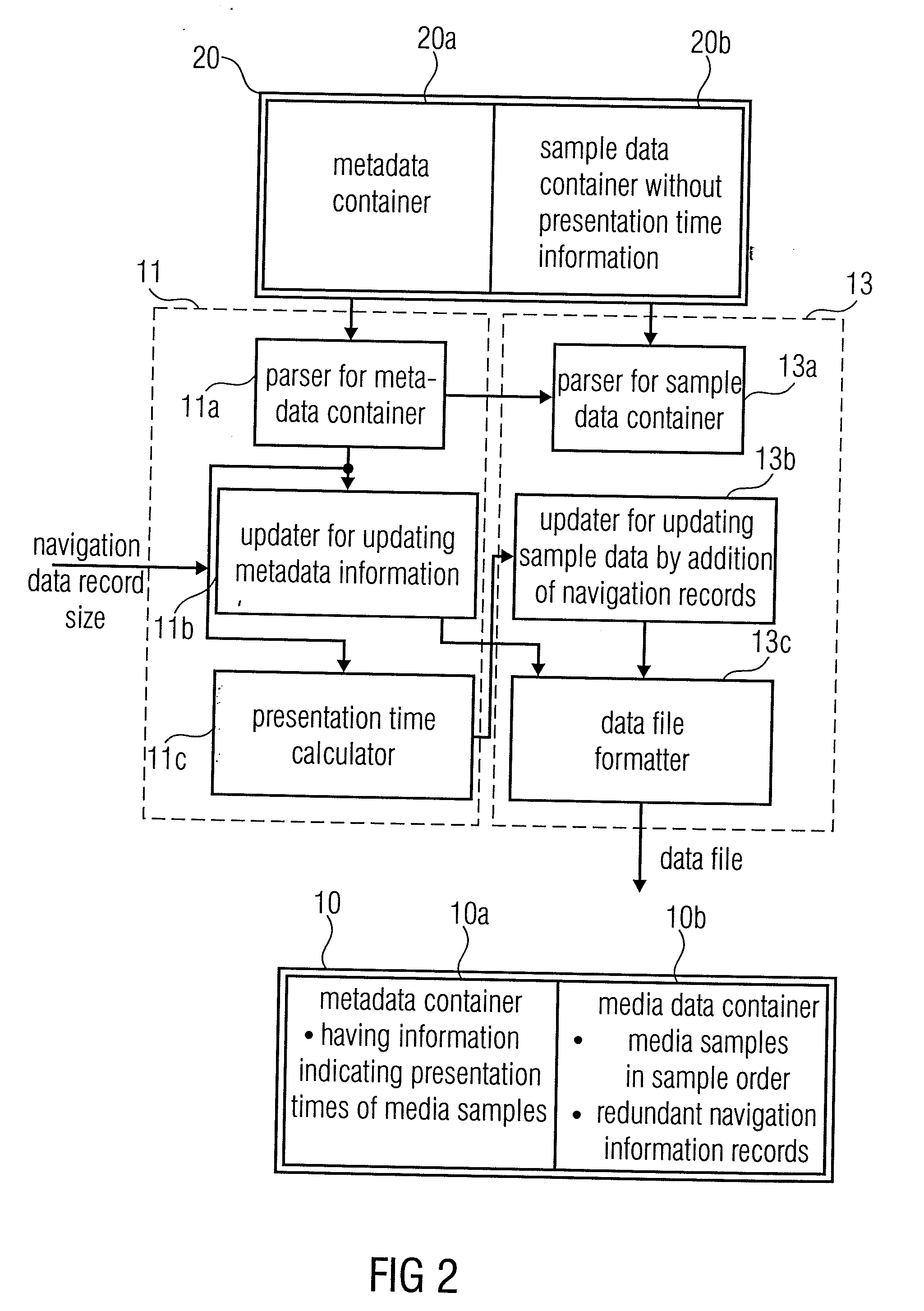
An apparatus for generating a data file has a navigation information generator and a file constructor. The file constructor constructs a file having a metadata container and a media data container. The metadata container comprises information indicating presentation times for a plurality of media samples, and the media data container includes these media samples. Additionally, the file constructor inserts redundant navigation information records into the media data container. A reader calculates presentation times of media samples based on these navigation information records in the media data container.
Owner:NERO AG
System and method for localization over a wireless network
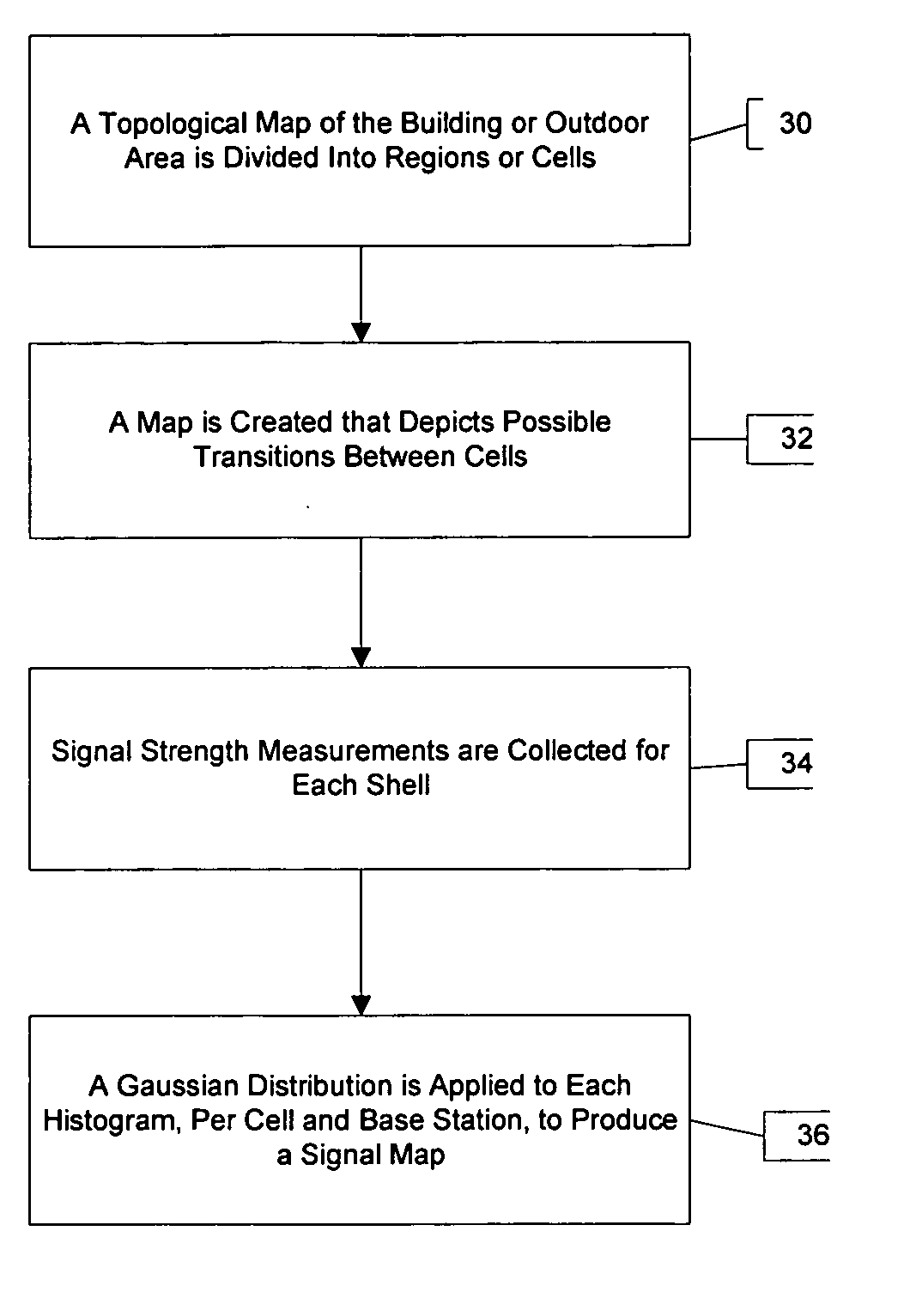
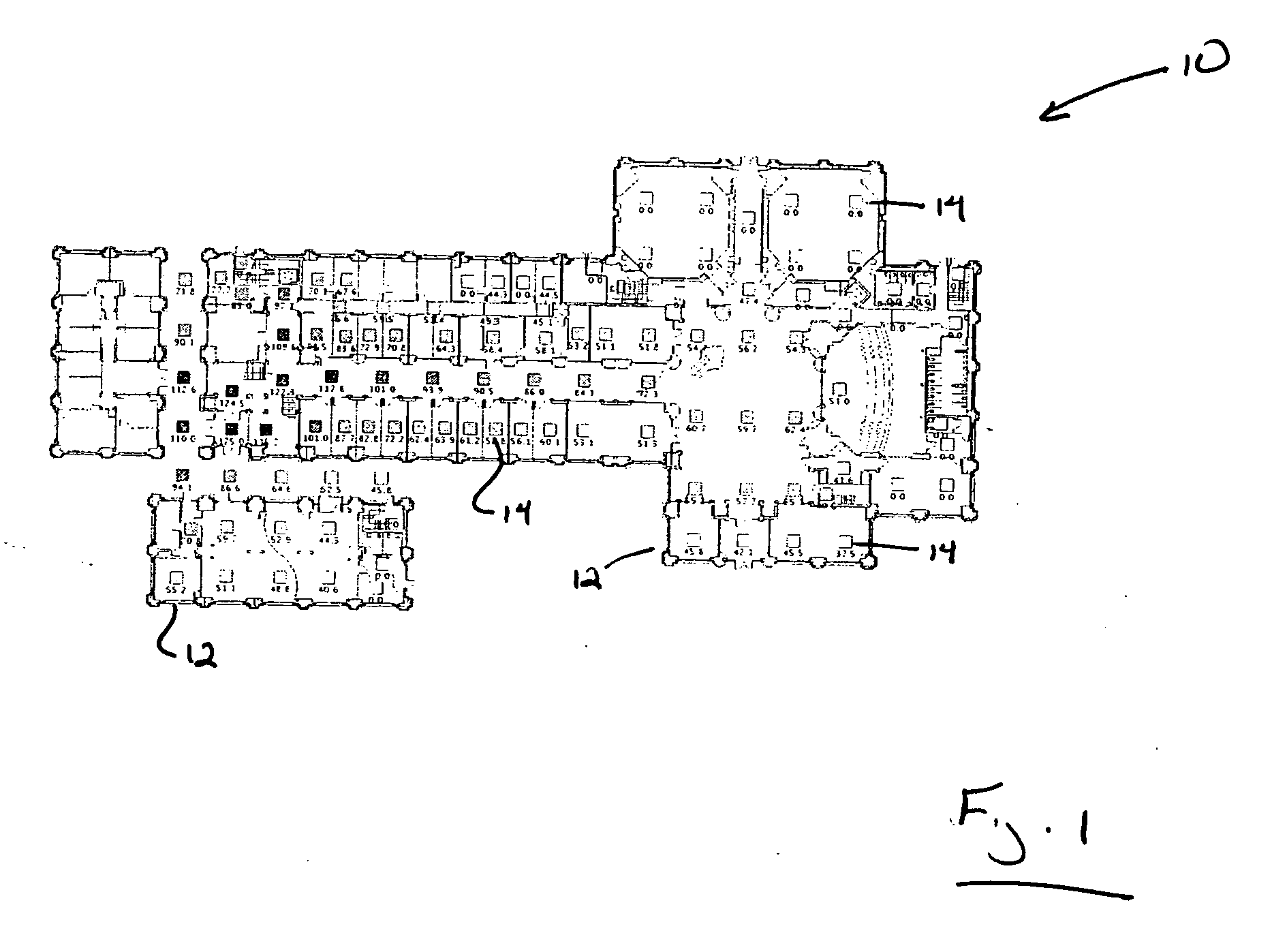
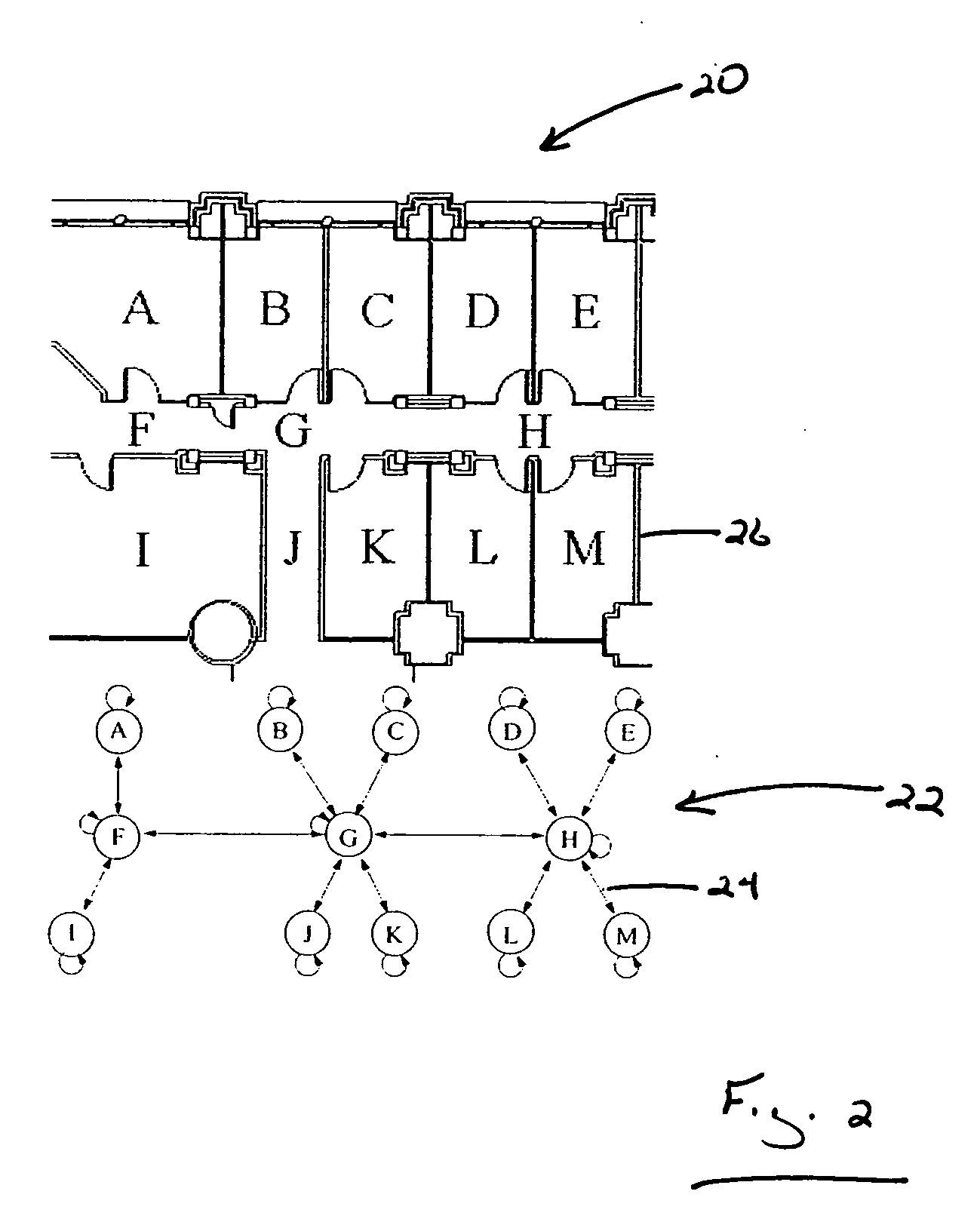
InactiveUS20060087425A1Reduce areaSufficient roomPosition fixationRadio/inductive link selection arrangementsOutdoor areaMarkov chain
A system for locating a wireless device involves the use of the measured signal strength of various base stations in the building or outdoor area under analysis. A topological map of the building or outdoor area under analysis is created. The map is divided into cells, and signal intensities are collected in each cell. For each cell, the signal from a particular base station is fit to a statistical distribution, such as a Gaussian distribution, and the parameters of the statistical distribution are estimated. After a device obtains a set of signal strength measurements, a probabilistic technique is employed to estimate the probability of the existence of the measurements in each of the cells of the building or area under analysis. The estimated location is the cell with the highest probability. A mobile user is tracked with the use of a Markov chain and the system can be calibrated to account for equipment and environmental variations.
Owner:RICE UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com