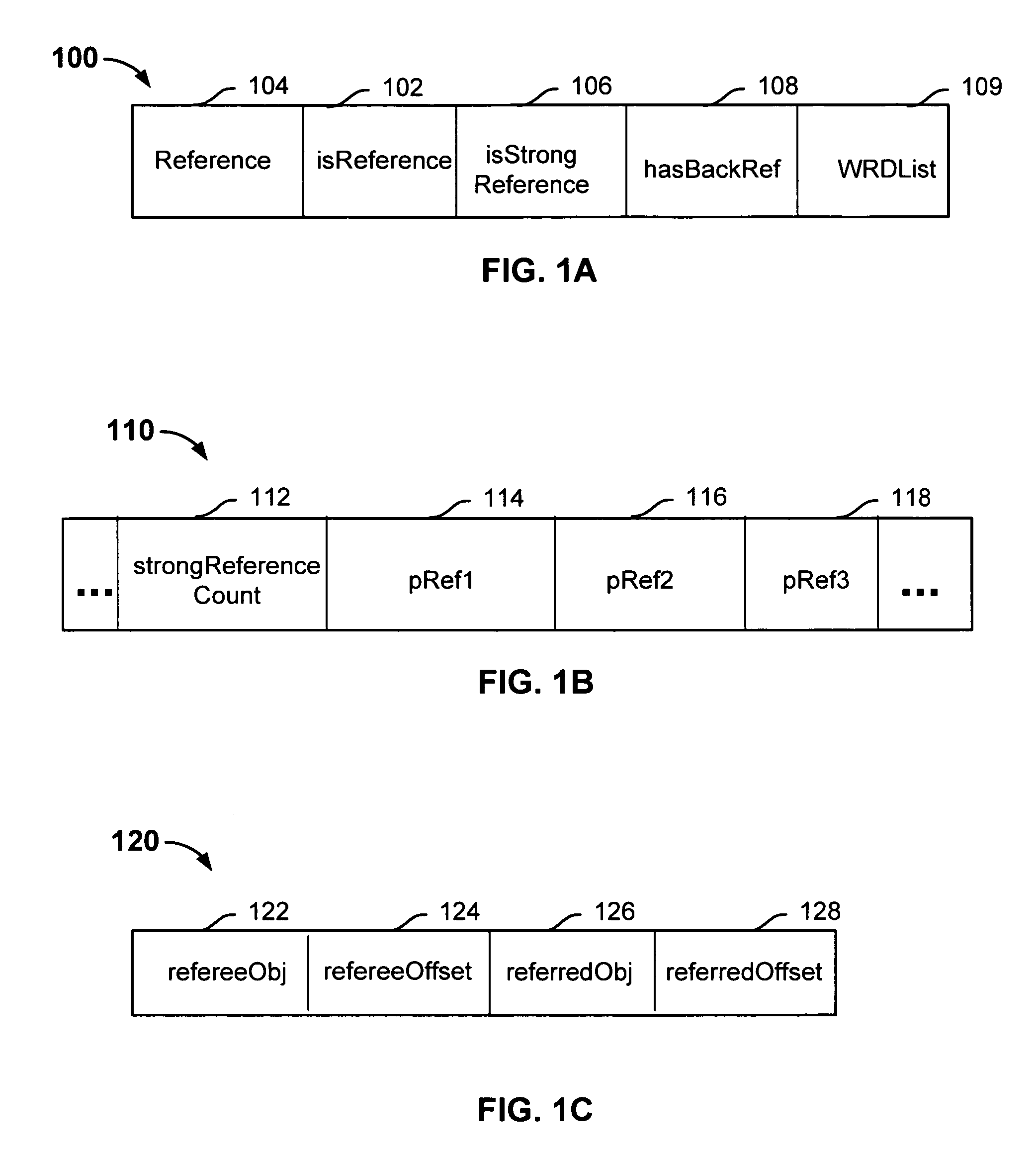
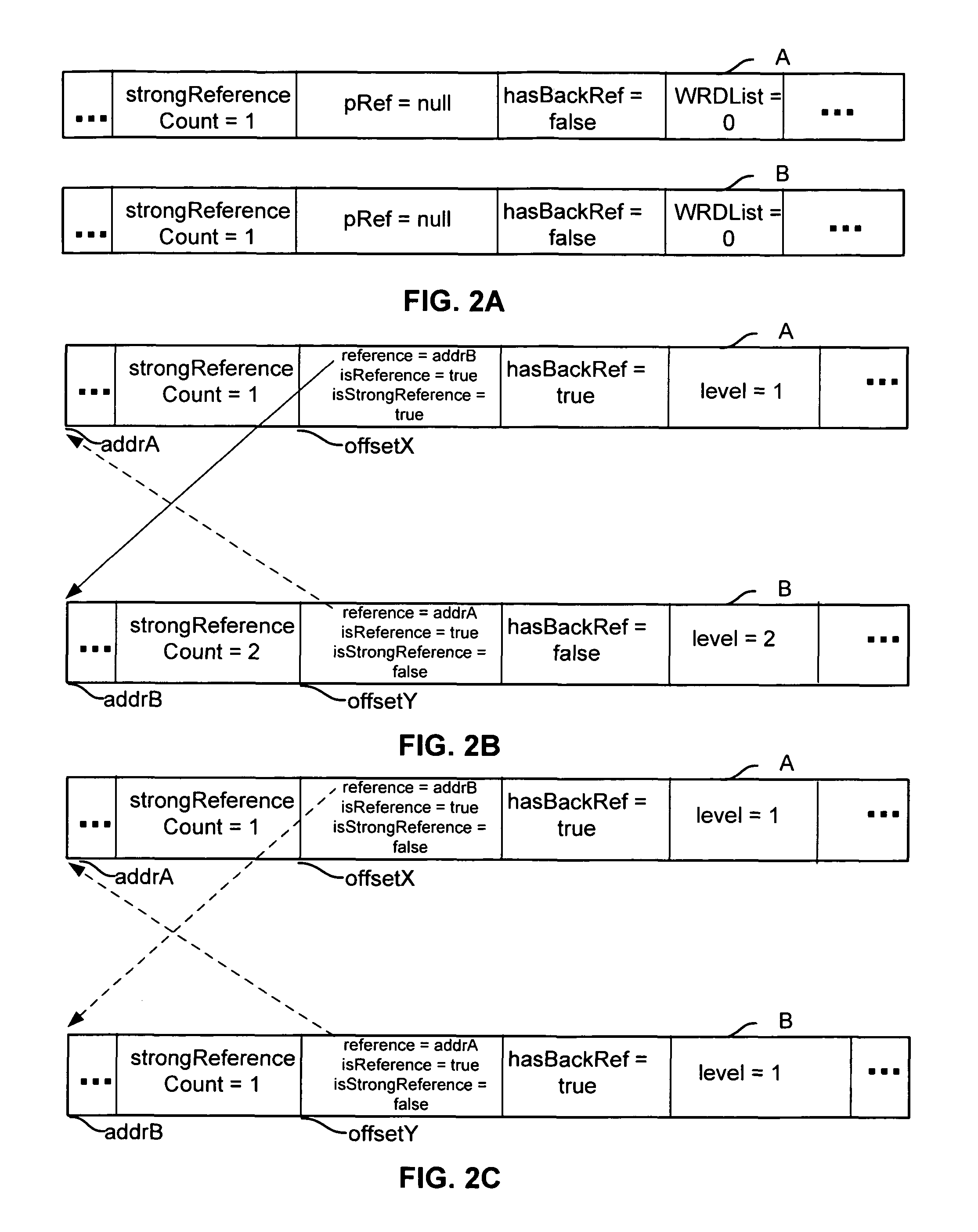
Patents
Literature
49 results about "Weak reference" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
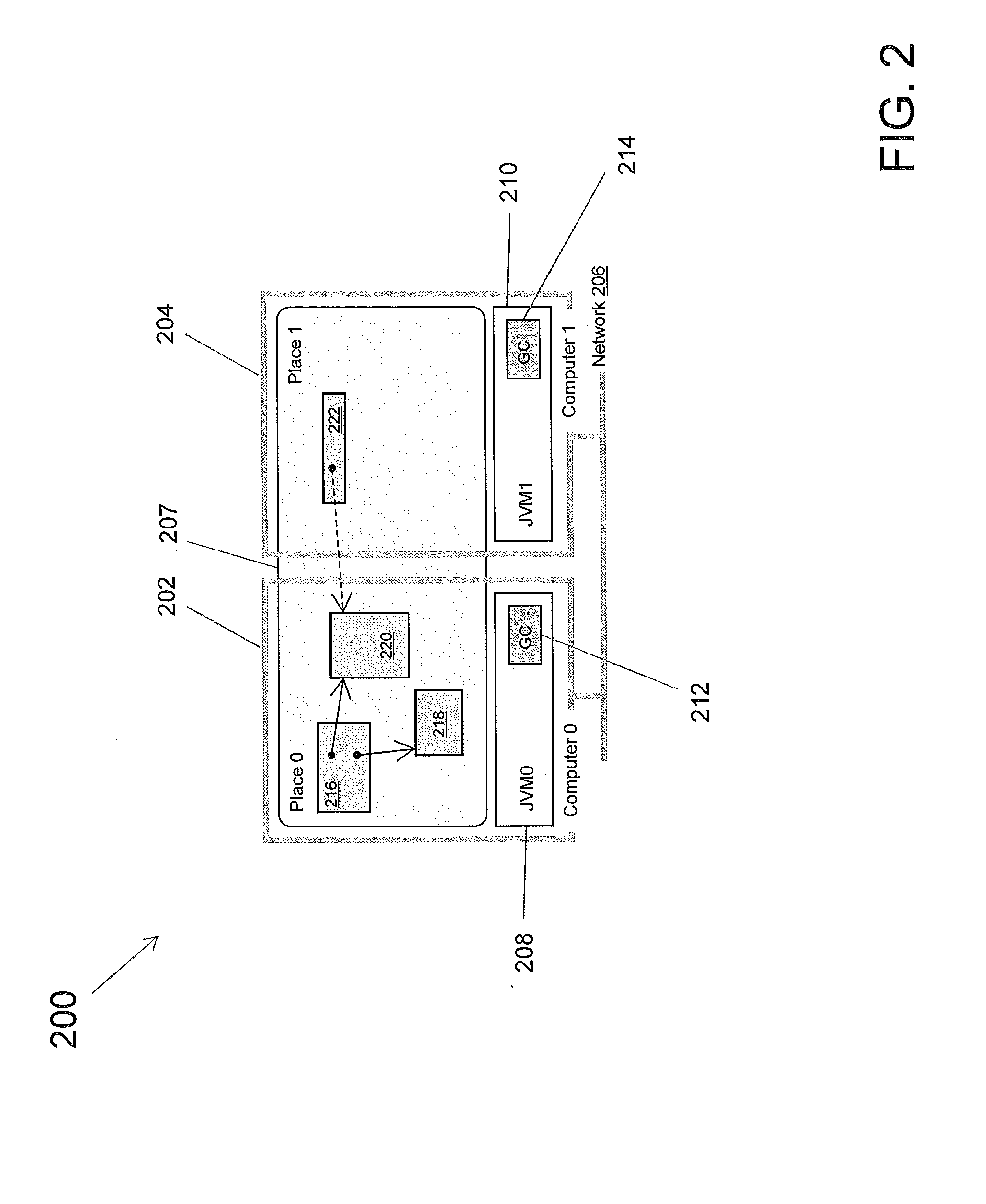
In computer programming, a weak reference is a reference that does not protect the referenced object from collection by a garbage collector, unlike a strong reference. An object referenced only by weak references – meaning "every chain of references that reaches the object includes at least one weak reference as a link" – is considered weakly reachable, and can be treated as unreachable and so may be collected at any time. Some garbage-collected languages feature or support various levels of weak references, such as C#, Java, Lisp, OCaml, Perl, and Python.
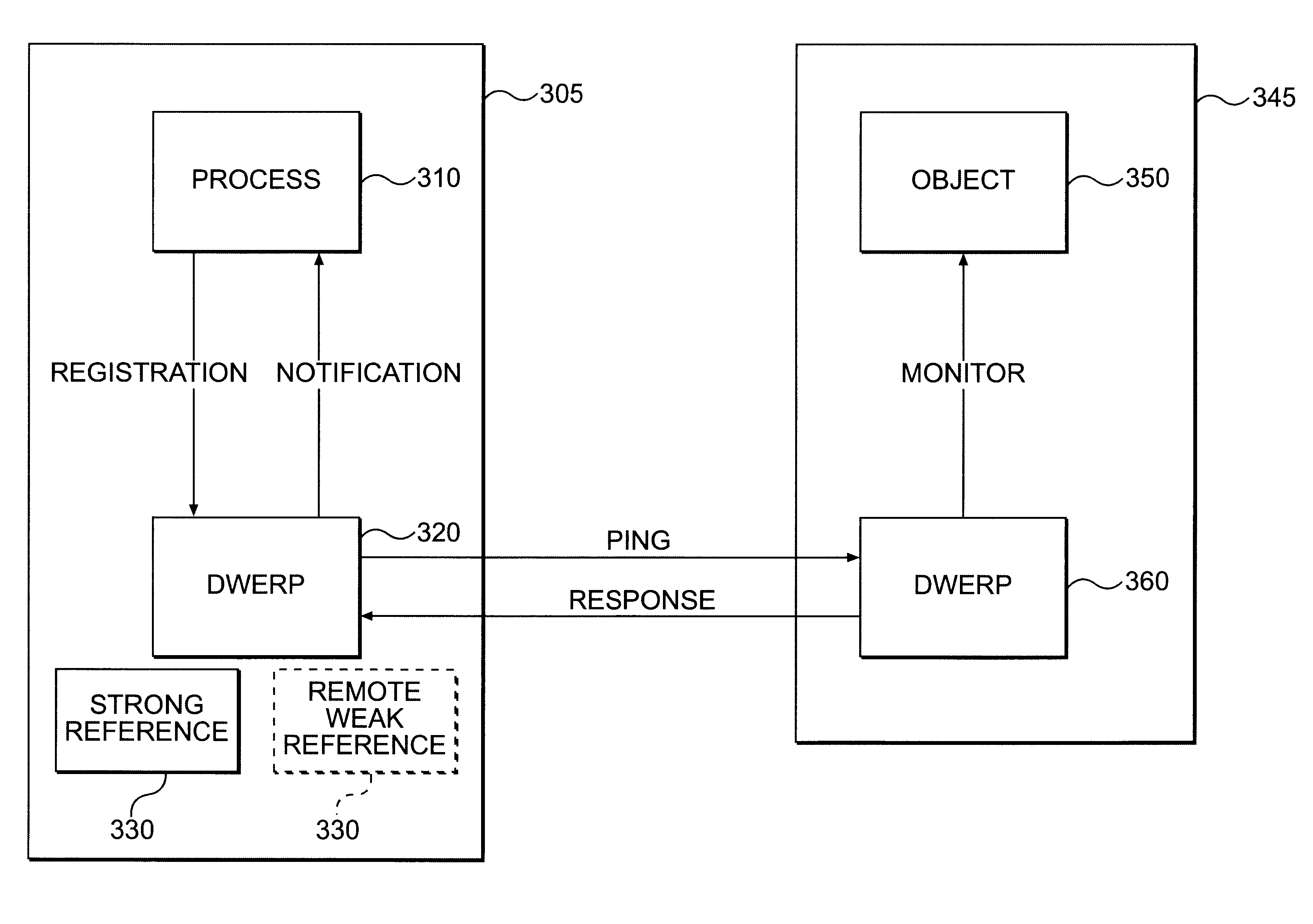
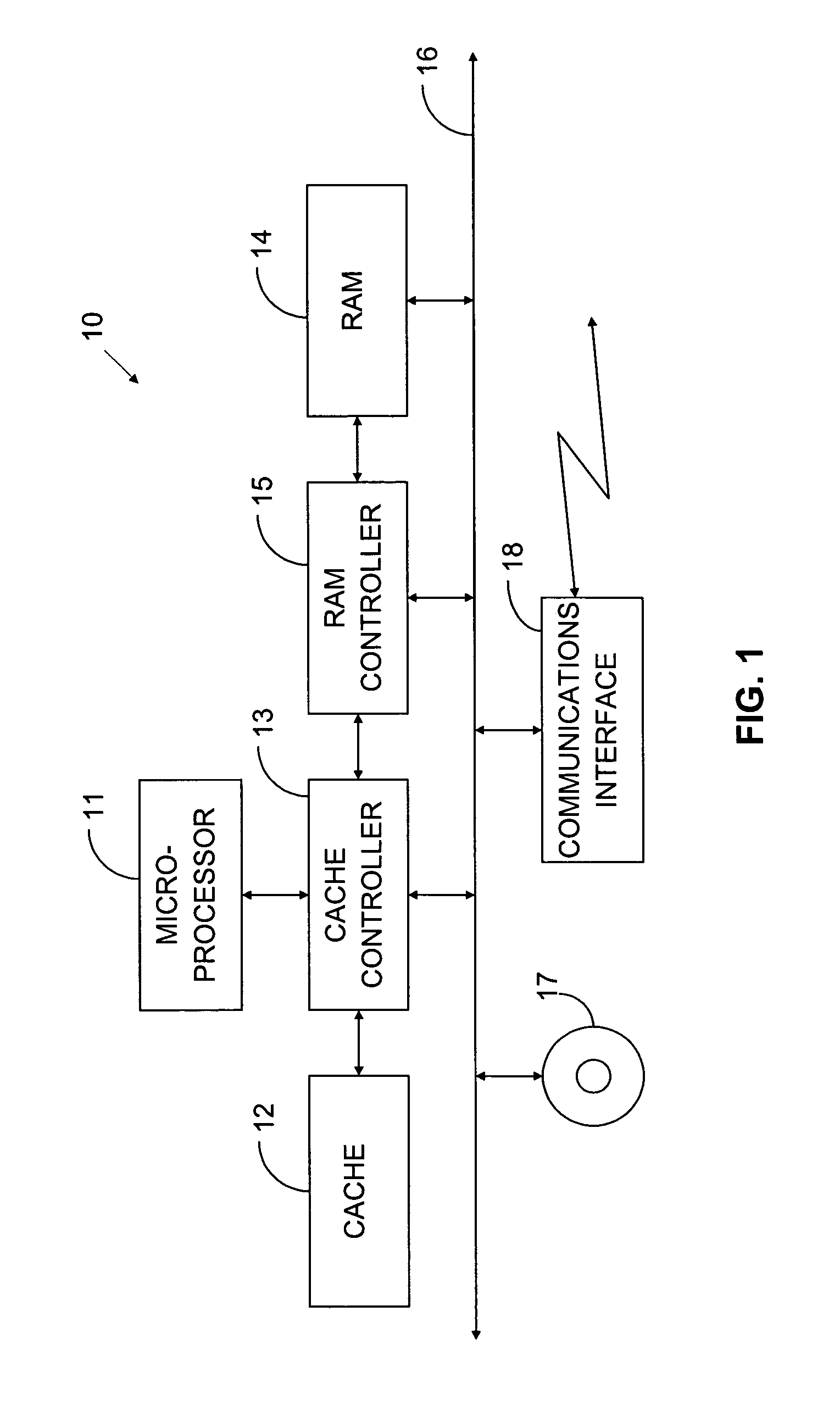
Method and apparatus for determining status of remote objects in a distributed system
InactiveUS6598094B1Memory adressing/allocation/relocationMultiprogramming arrangementsDistributed computingWeak reference
Systems consistent with the present invention a method and apparatus is provided for selectively supplying a state change associated with remote objects in a distributed system. The method involves registering a request from a computational entity to receive notification as to a state change associated with a remote object. Registration of a notification request causes the creation of a remote weak reference to the remote object including an identifier of a location of the remote object. Periodically, a request is sent to a location based on the identifier of the remote weak reference. When it is determined that a state change associated with the remote object has occurred, the registered computational entity is notified accordingly.
Owner:ORACLE INT CORP
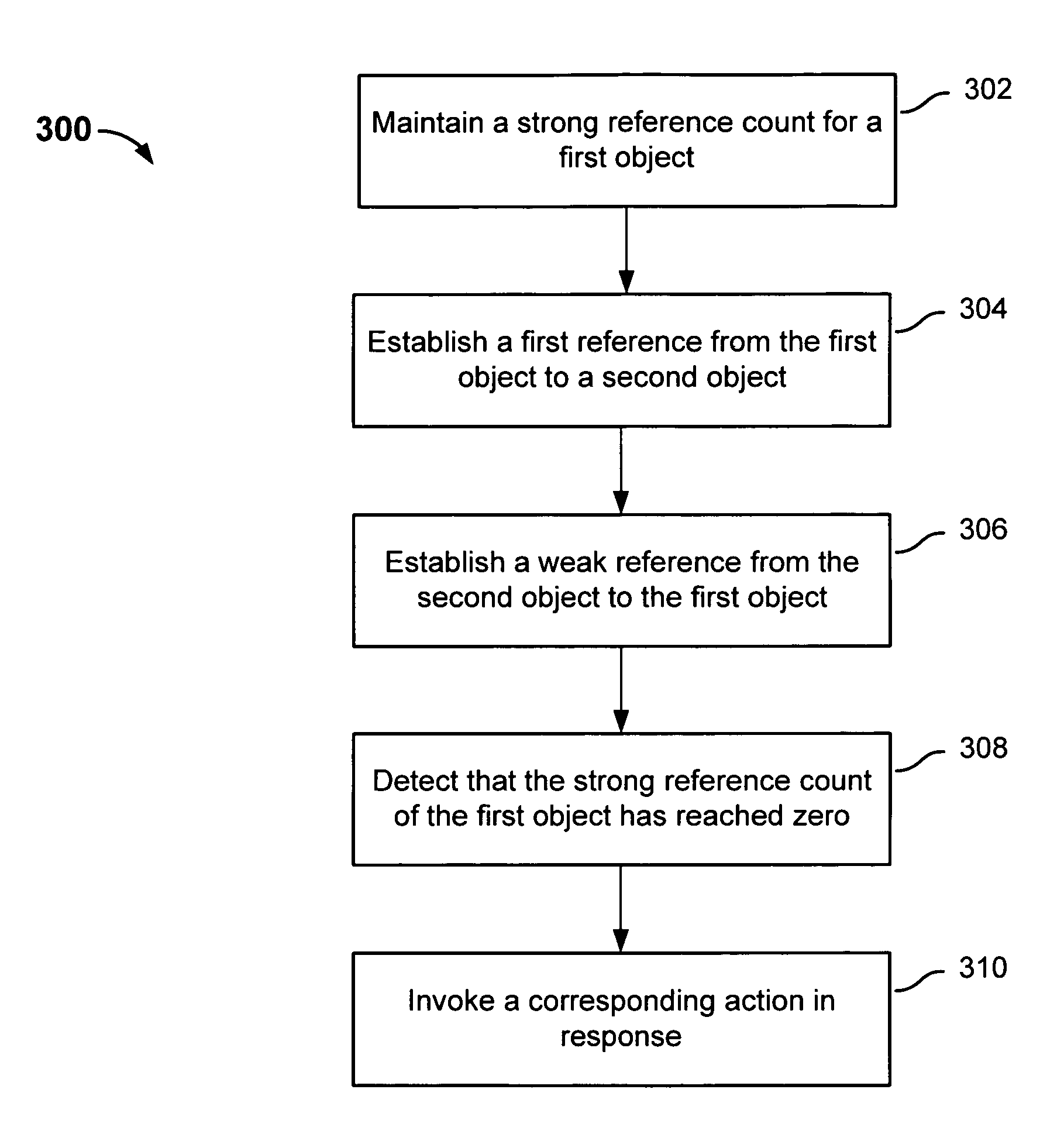
Hardware-protected reference count-based memory management using weak references
ActiveUS8838656B1Memory architecture accessing/allocationDigital data information retrievalStrong referenceMemory management unit
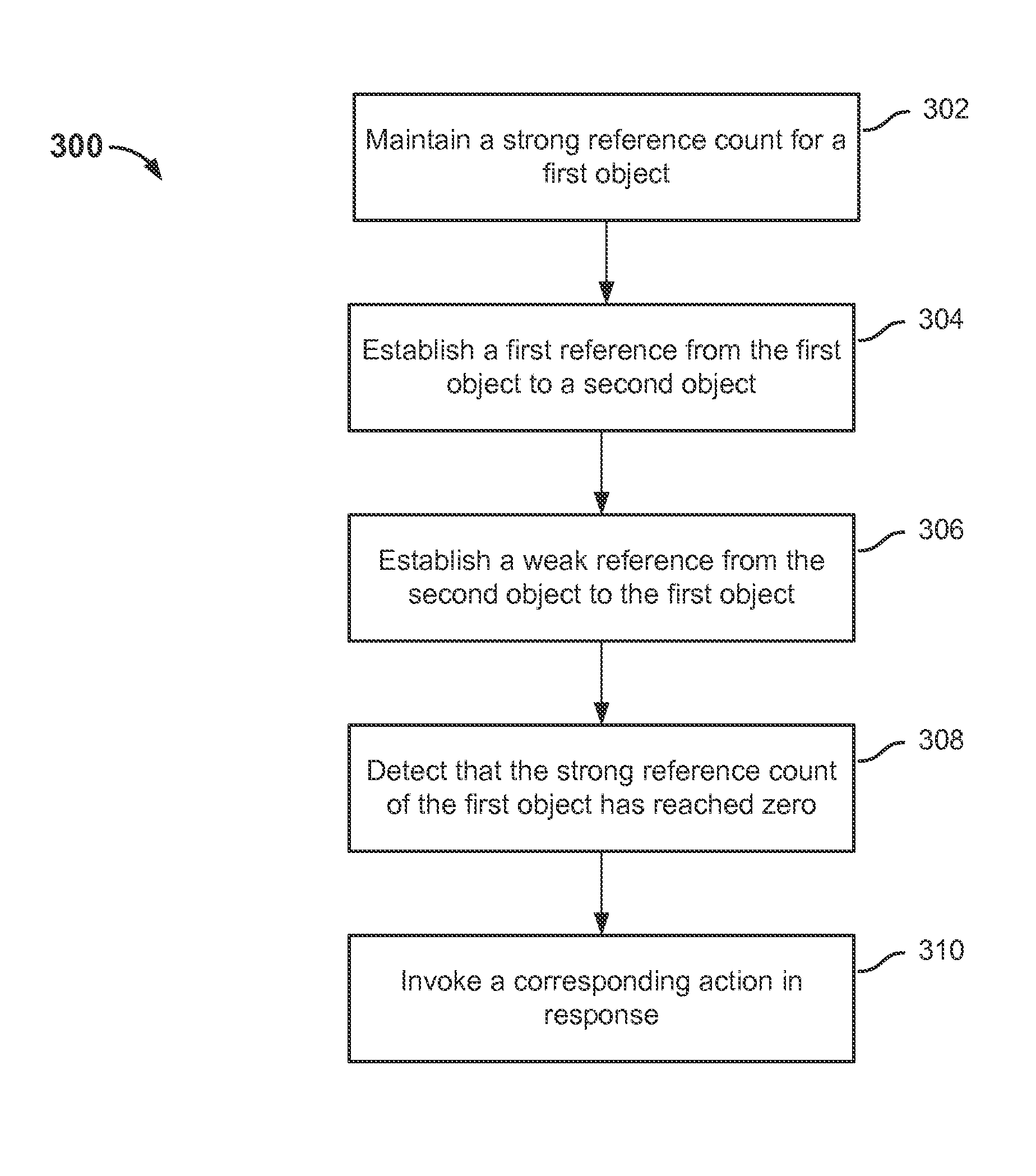
A method for managing memory, comprising: maintaining a strong reference count for a first object; establishing a first reference from the first object to a second object; establishing a second reference from the second object to the first object, wherein the second reference is a weak reference that does not increase the strong reference count of the first object; detecting that the strong reference count of the first object has reached zero; in response to detecting that the strong reference count has reached zero, invoking a corresponding action.
Owner:INTEL CORP
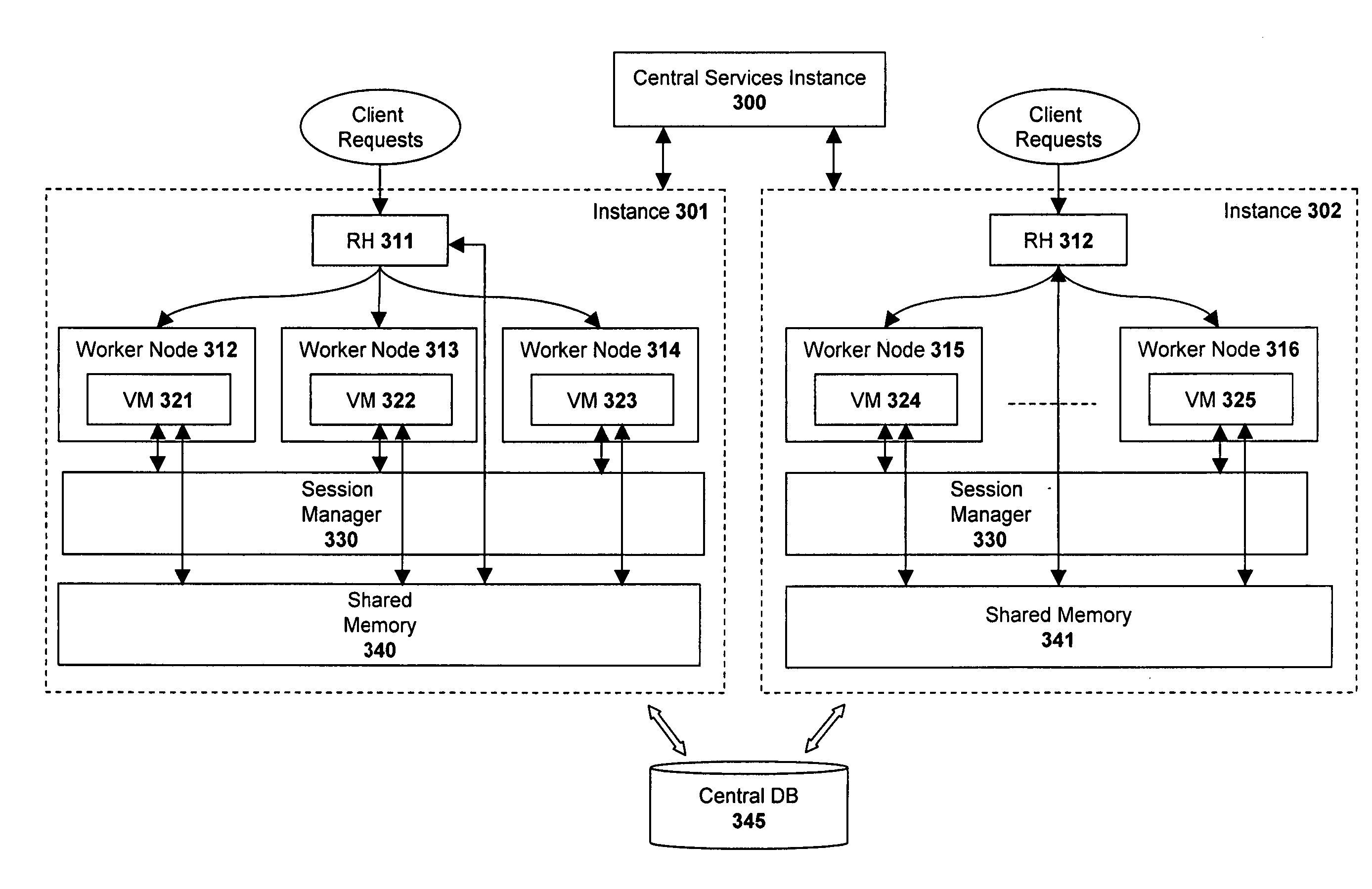
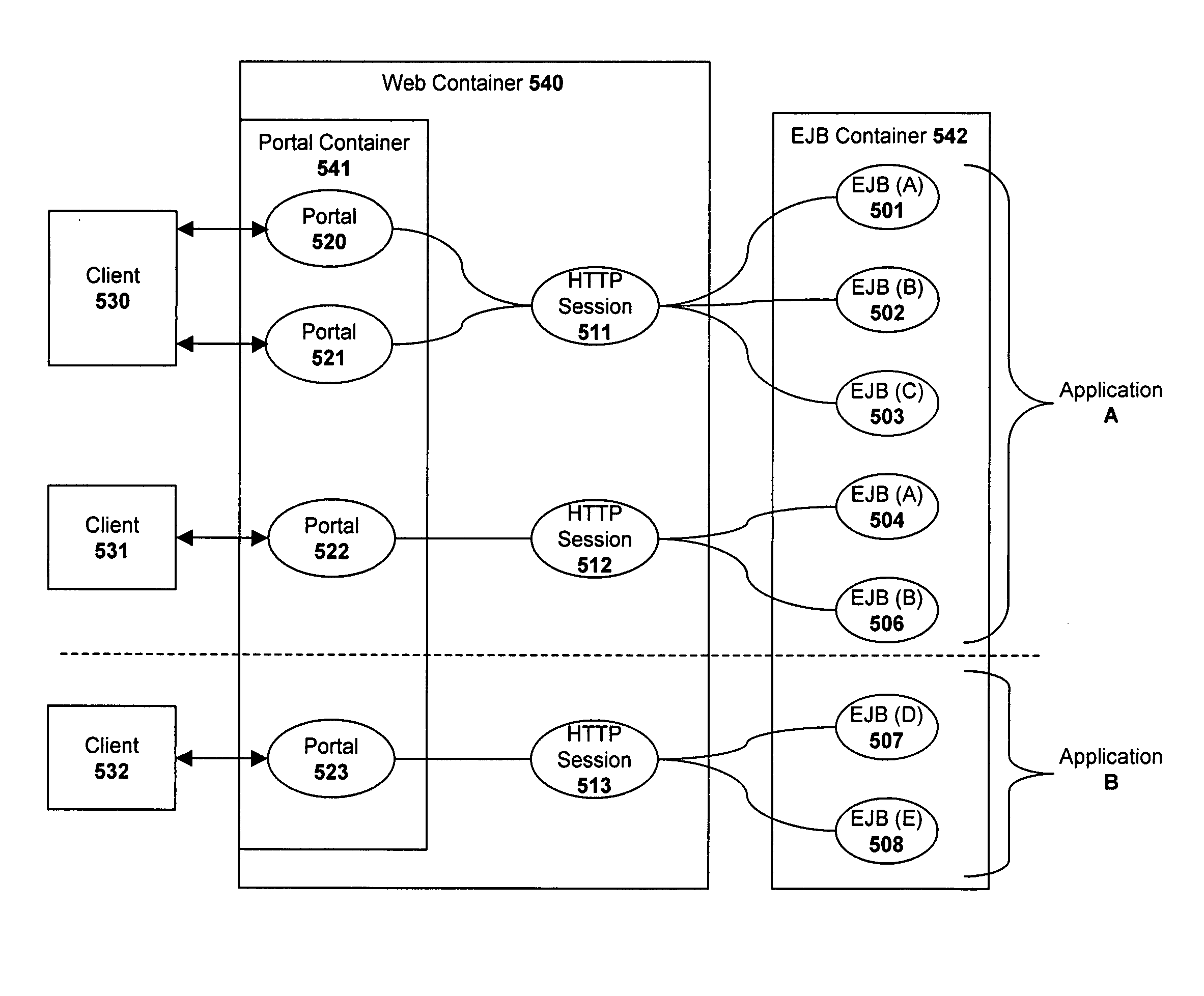
Session lifecycle management within a multi-tiered enterprise network
ActiveUS20060155756A1Multiple digital computer combinationsTransmissionApplication lifecycle managementObject based
A system and method are described for managing session lifecycles within a multi-tiered enterprise network. In one embodiment, a plurality of session objects are generated at different layers of the enterprise network in response to a client request. Each of the session objects store session data defining a state of interaction with the client. In addition, one embodiment of the invention manages the lifecycle of a first session object based on corresponding lifecycles of one or more related session objects and also the type of relationship existing between the first session object and the one or more related session objects. In one embodiment, the defined relationship types include strong references, weak references, and soft references.
Owner:SAP AG
Handling method and system for memory access events
InactiveCN101727355AReduce overheadReduce storage overheadResource allocationError detection/correctionUnique identifierOperating system
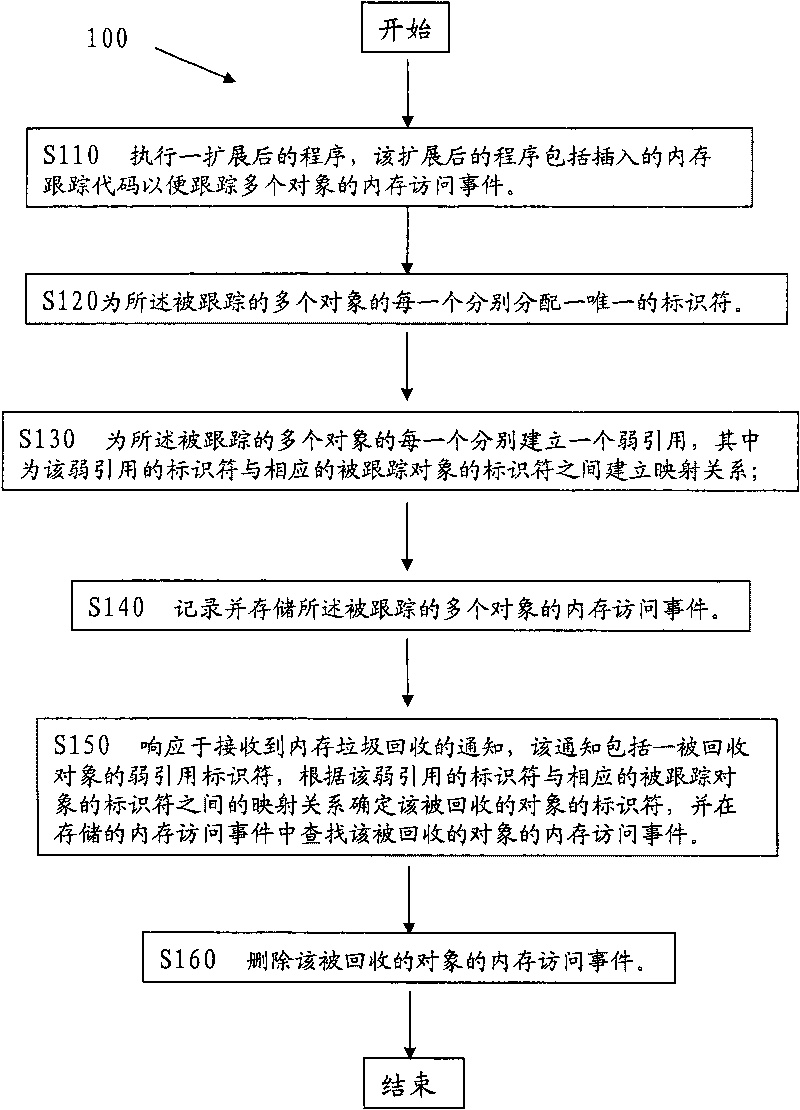
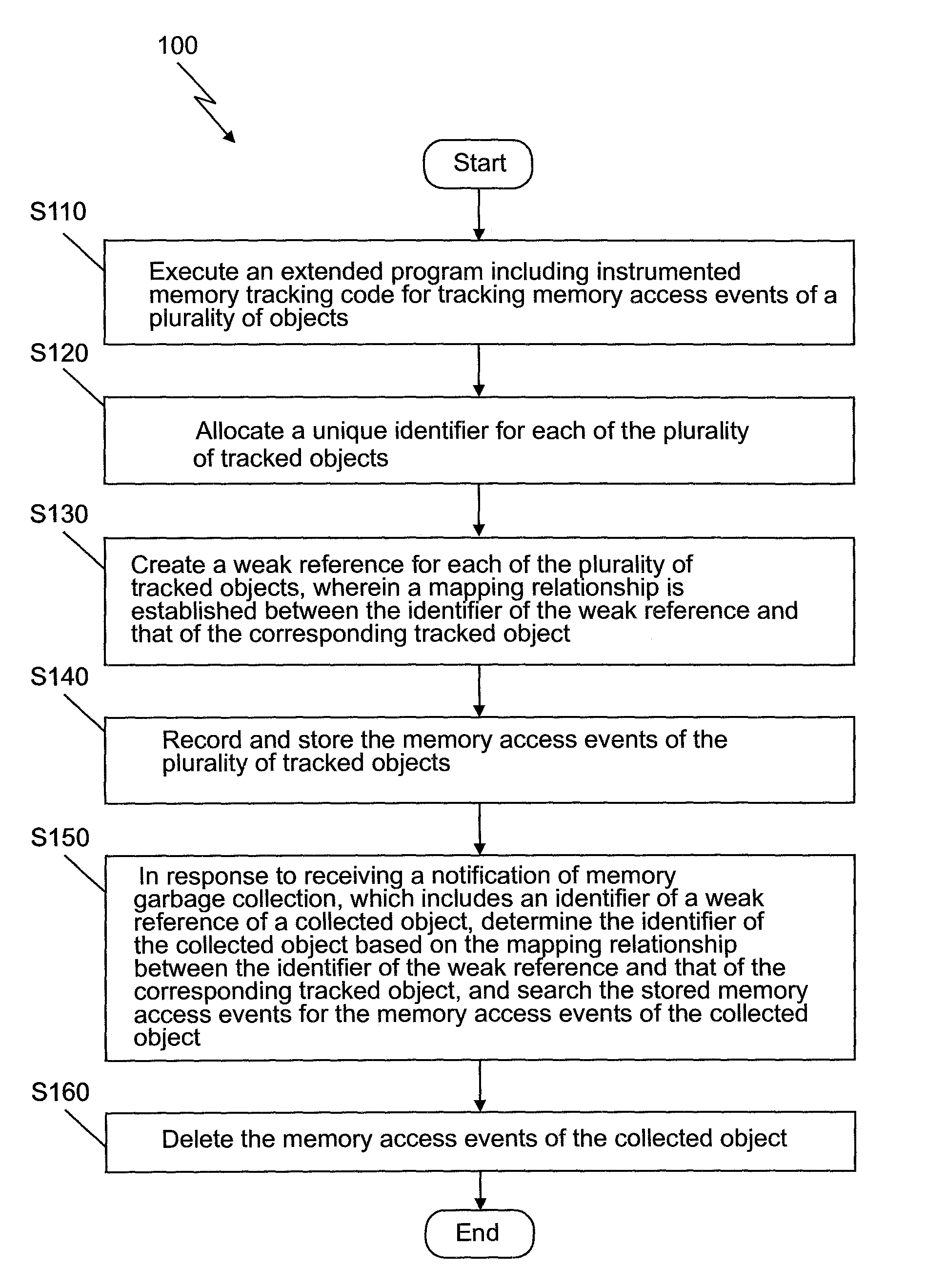
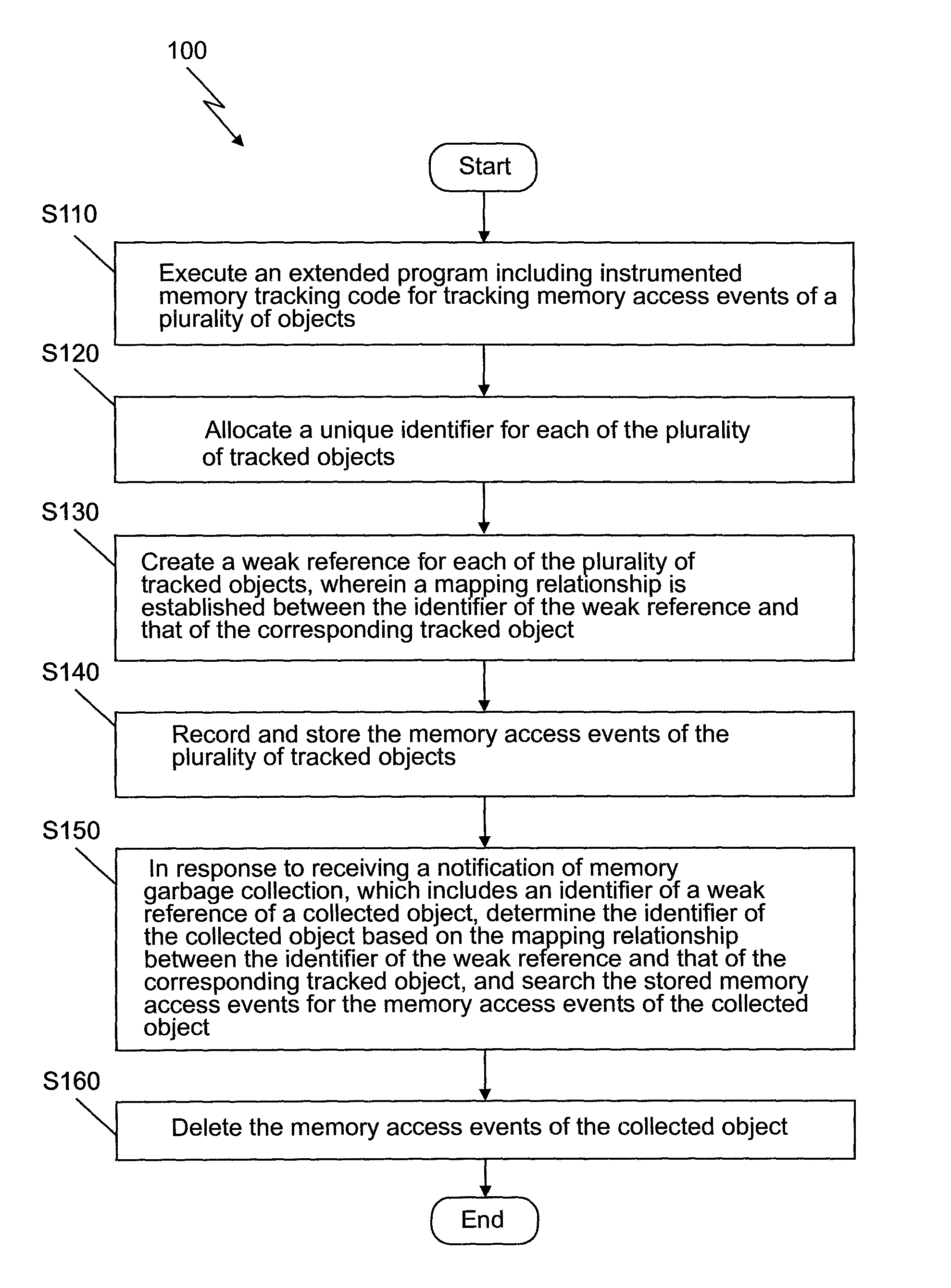
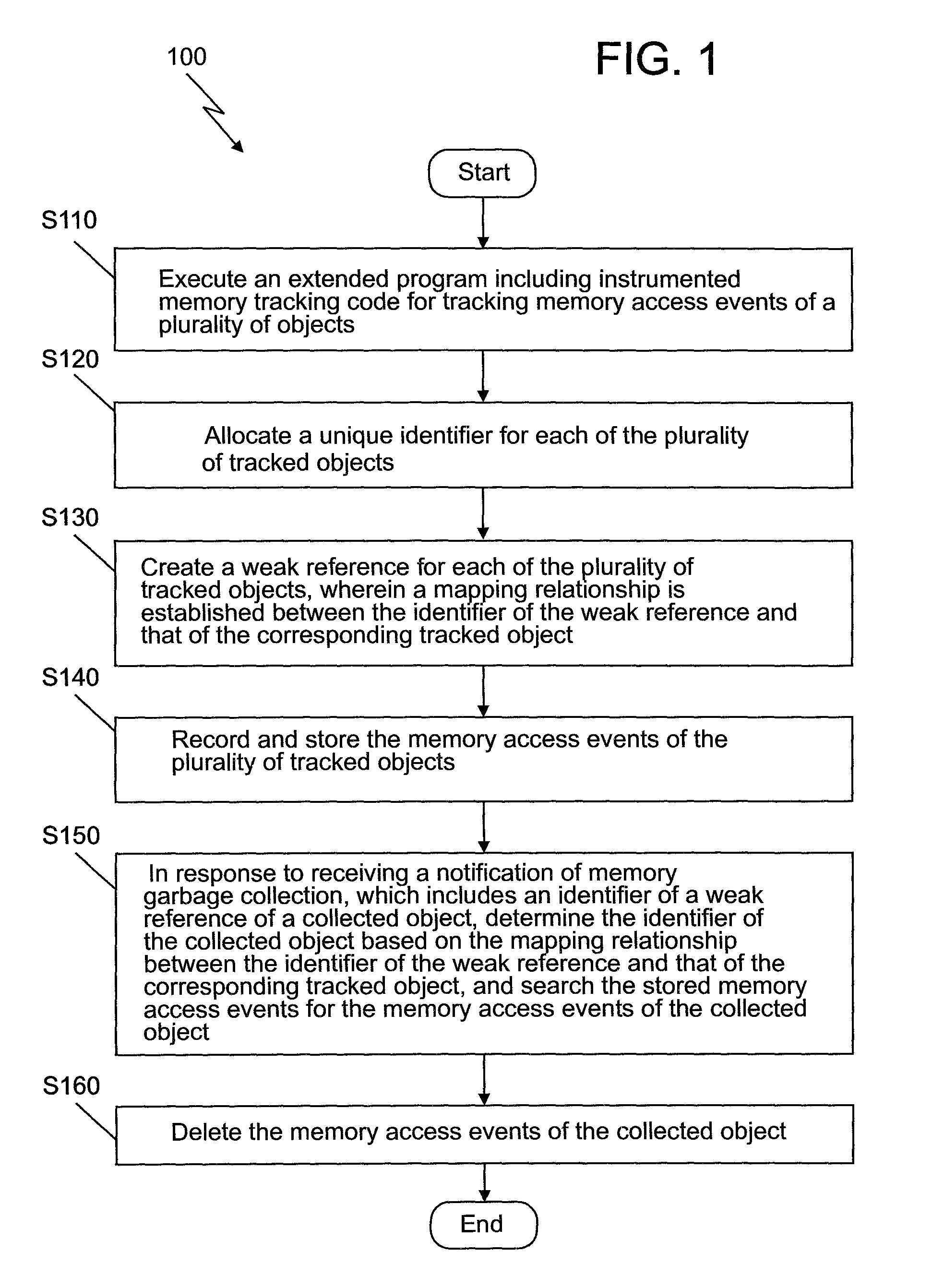
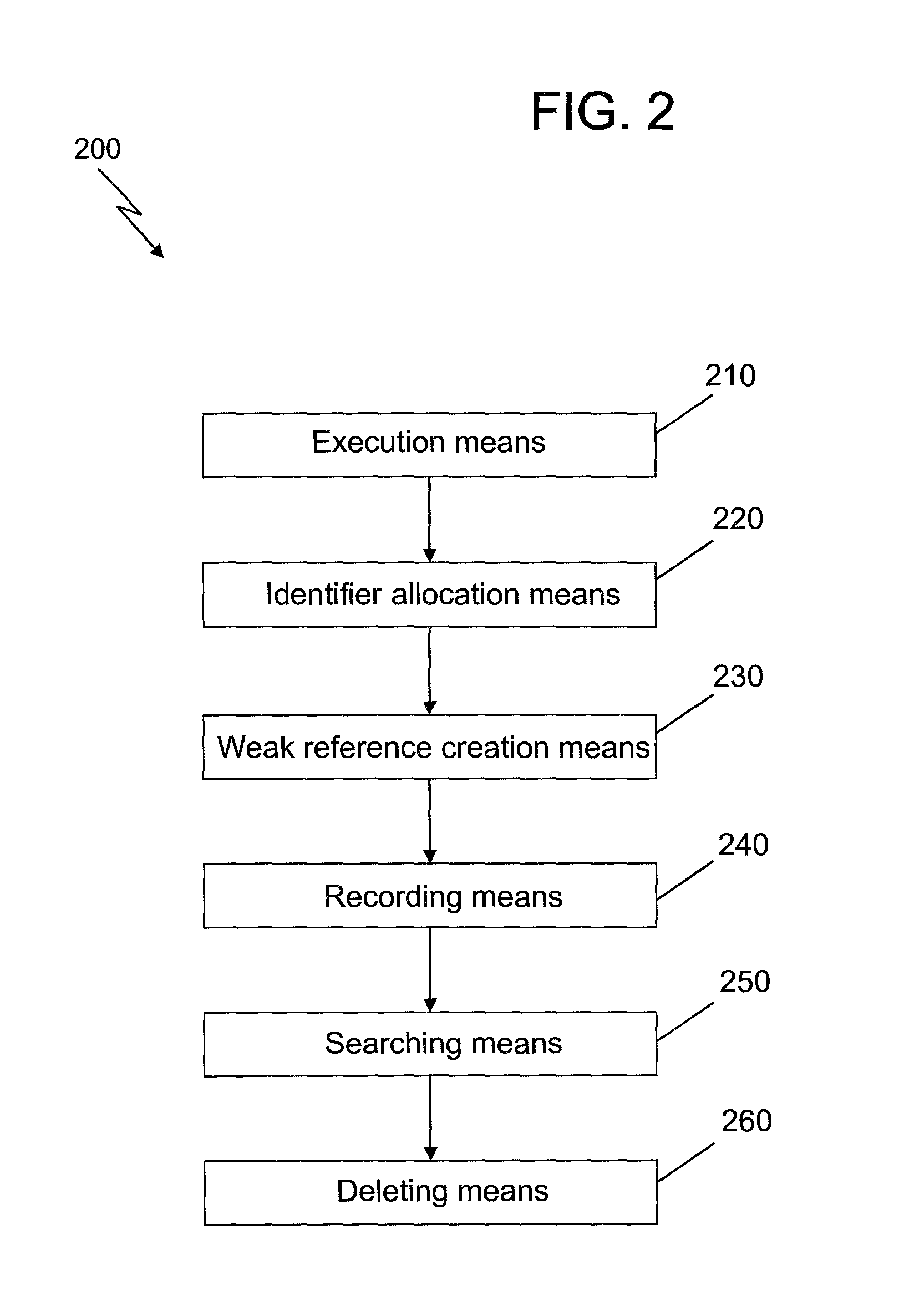
The invention provides a handling method and a system for new memory access events; the method comprises the following steps: an expanded procedure is carried out, and the expanded procedure comprises an inserted memory tracking code to track memory access events of a plurality of objects conveniently; unique identifiers are respectively distributed on a plurality of the tracked objects; weak references are respectively built for a plurality of the tracked objects, and mapping relation is built between the identifier for weak reference and the corresponding identifier of the object which is tracked; the memory access events of a plurality of the objects care recorded, stored and tracked; a notice for memory rubbish recovery, which is received, is responded, the notice comprises a weak reference identifier for a recycled object, the identifier of the recycled object is determined according to the mapping relation between the weak reference identifier and the corresponding identifier ofthe tracked object, and the memory access events of the recycled object are searched in the stored memory access events; and the memory access events of the recycled object are deleted; by adopting the method, the memory overhead can be reduced.
Owner:INT BUSINESS MASCH CORP
Method and System to Space-Efficiently Track Memory Access of Object-Oriented Language in Presence of Garbage Collection
InactiveUS20100114999A1Reduce storage overheadReduce memory overheadError detection/correctionMemory adressing/allocation/relocationProcess memoryObject based
The present invention provides a method and system for processing memory access events. The method comprises: executing an extended program including instrumented memory tracking code for tracking memory access events of a plurality of objects; allocating a unique identifier for each of the plurality of tracked objects; creating a weak reference for each of the plurality of tracked objects, wherein a mapping relationship is established between the identifier of the weak reference and that of the corresponding tracked object; recording and storing the memory access events of the plurality of tracked objects; in response to receiving a notification of memory garbage collection which includes an identifier of a weak reference of a collected object, determining the identifier of the collected object based on the mapping relationship between the identifier of the weak reference and that of the corresponding tracked object, and searching the stored memory access events for the memory access events of the collected object; and deleting the memory access events of the collected object. The storage overhead may be reduced according to the above method of the present invention.
Owner:IBM CORP
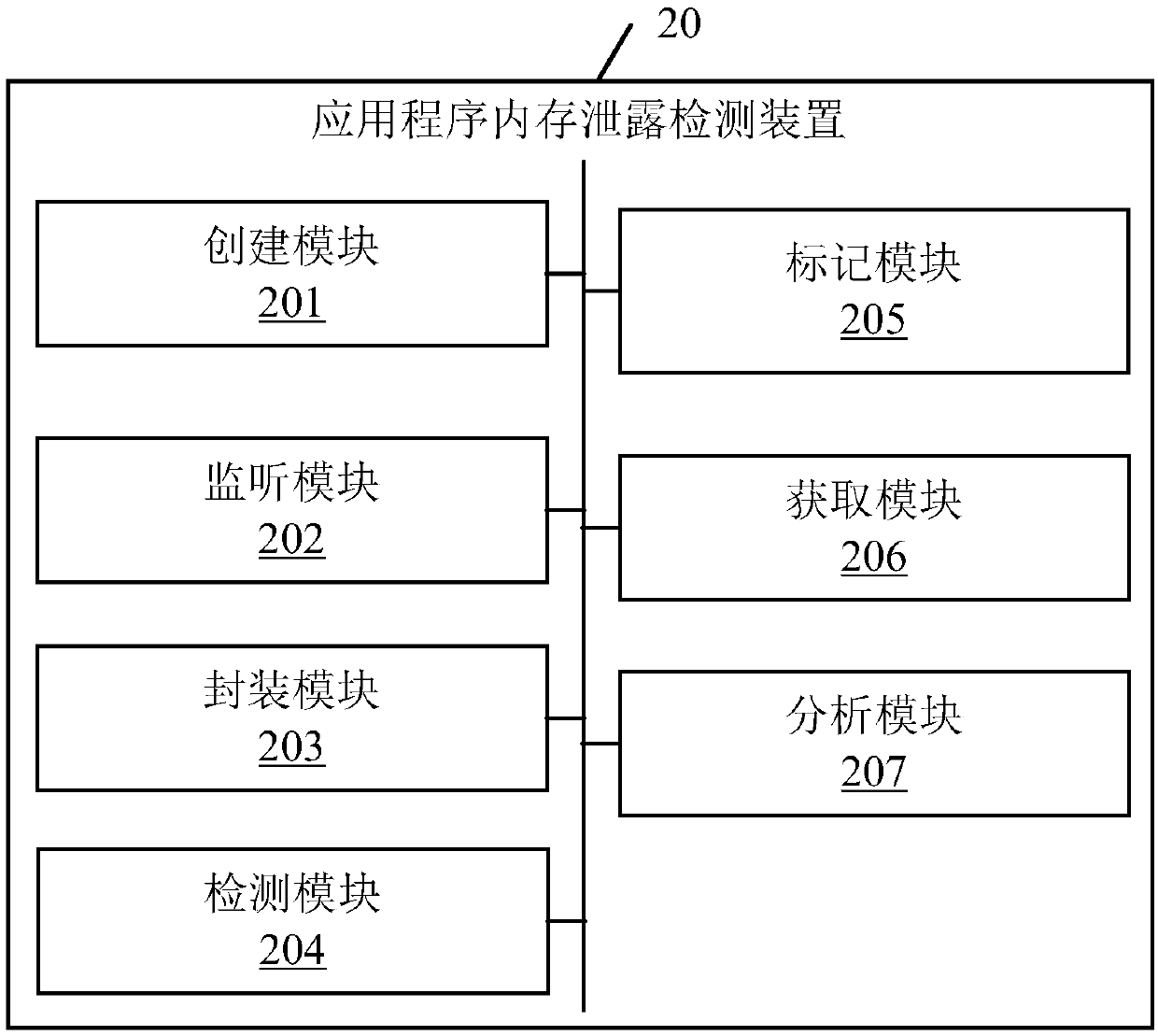
Application memory leakage detection method and device, electronic equipment and storage medium
PendingCN109558308AImprove experiencePrecise positioningResource allocationSoftware testing/debuggingSecurity monitoringMemory leak detection
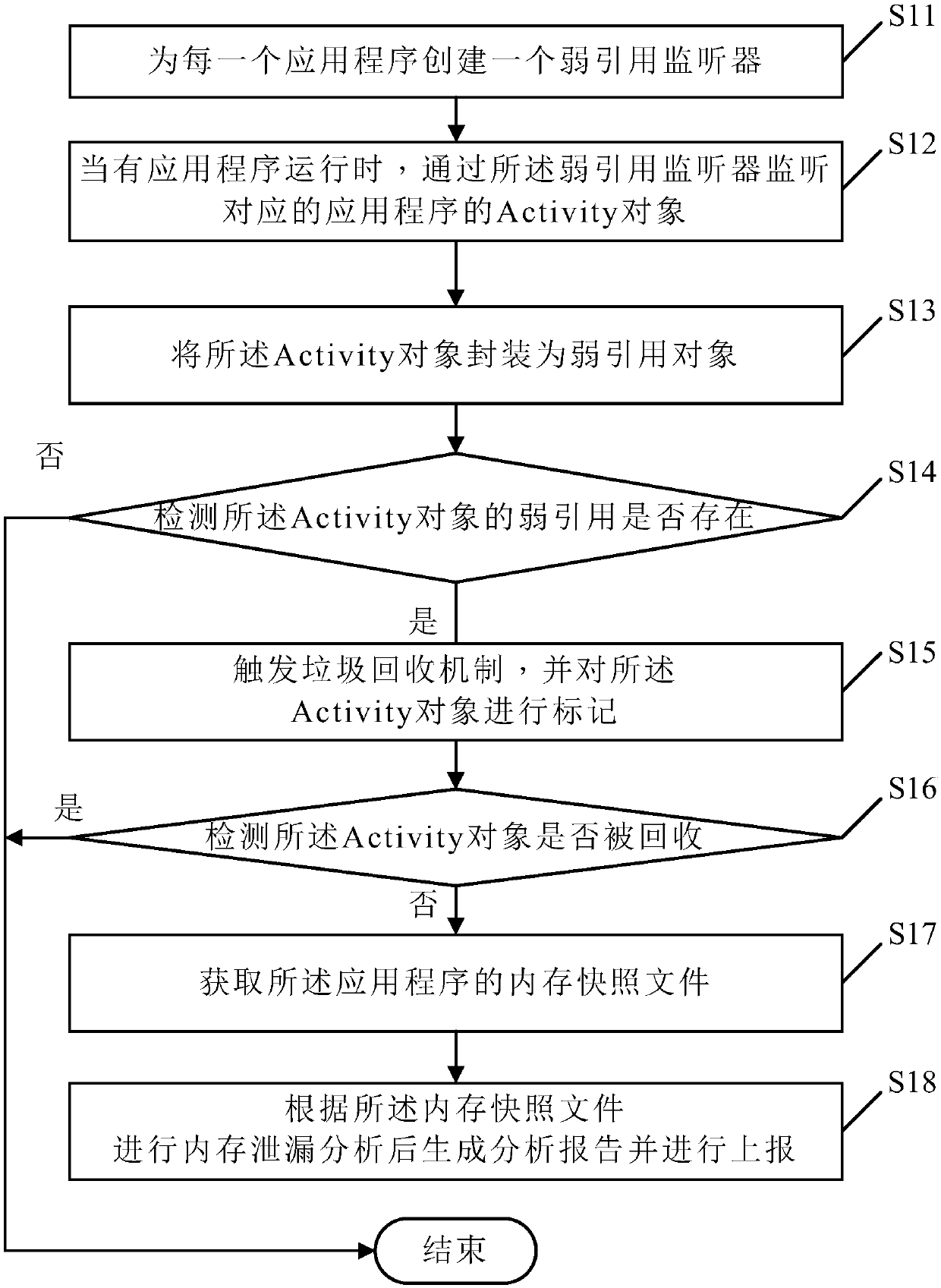
The invention discloses an application program memory leakage detection method. The method comprises the following steps of creating a weak reference monitor for each application program; when an application program runs, monitoring an Activity object of the corresponding application program through the weak reference monitor; packaging the Activity object as a weak reference object; detecting whether the weak reference of the Activity object exists or not; when it is determined that the weak reference of the Activity object exists, triggering a garbage collection mechanism, and marking the Activity object; detecting whether the Activity object is recovered or not; when it is detected that the Activity object is not recovered, obtaining a memory snapshot file of the application program; and analyzing memory leakage according to the memory snapshot file, generating an analysis report and reporting the analysis report. The invention further provides an application program memory leak detection device, electronic equipment and a storage medium. The invention belongs to the technical field of security monitoring, can accurately and quickly locate the memory leakage problem of an application program, and improves the efficiency and accuracy of application program memory optimization.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
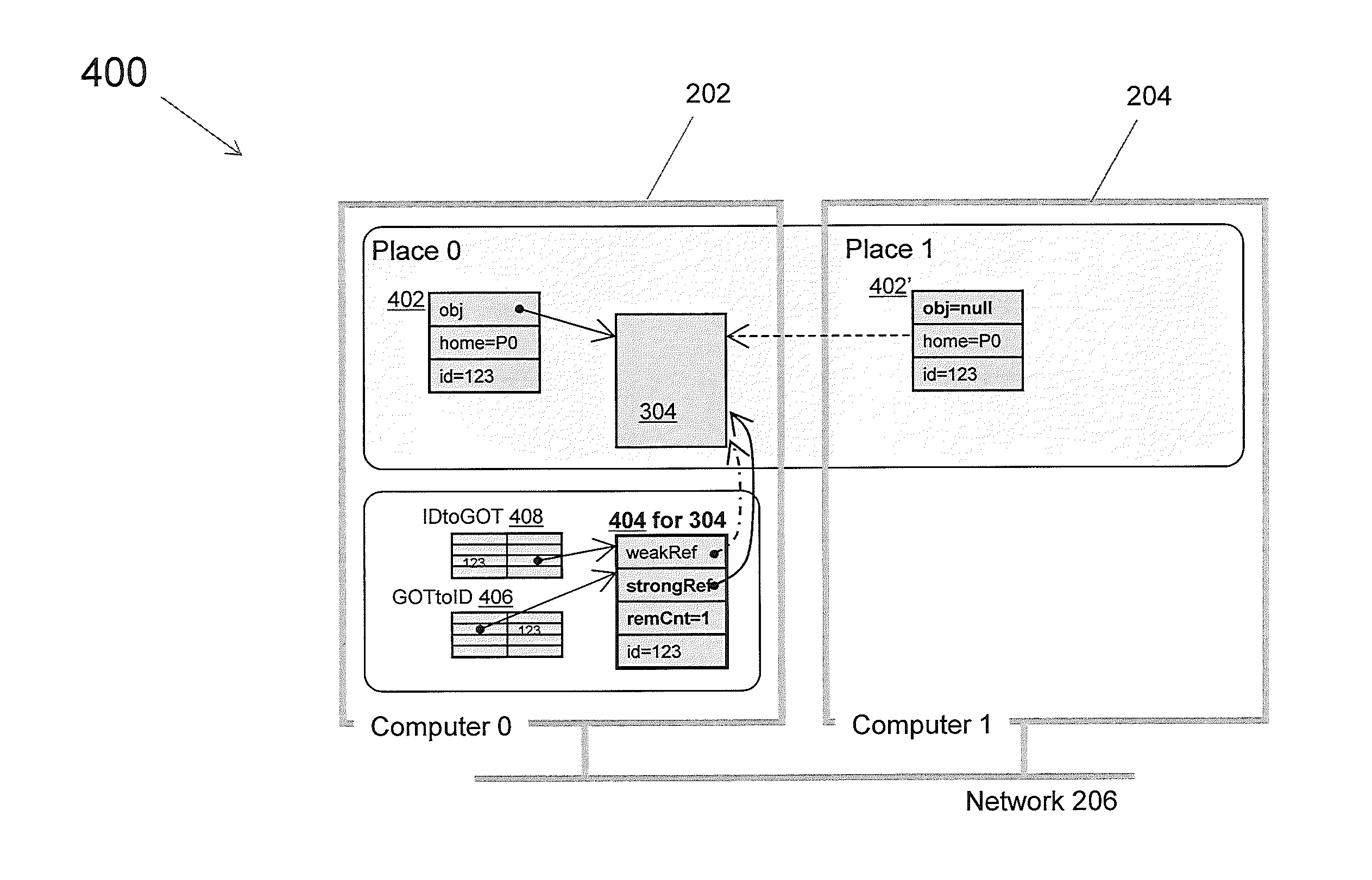
Garbage collection of an object
InactiveUS20140040327A1Prevent garbage collectionStrong referenceMemory architecture accessing/allocationProgram controlProgramming languageRefuse collection
One or more embodiments are directed to creating a structure comprising a weak reference to an object, a strong reference to the object, a count of remote references to the object, and an identifier for the object, incrementing the count when a remote reference is created to the object and decrementing the count when a remote reference is removed, setting the strong reference in response to the count being greater than a first threshold in order to avoid a garbage collection of the object, clearing the strong reference in response to the count being less than a second threshold to enable a garbage collection of the object, and removing the structure and related resources based on a recognition of the object's collection through the weak reference.
Owner:IBM CORP
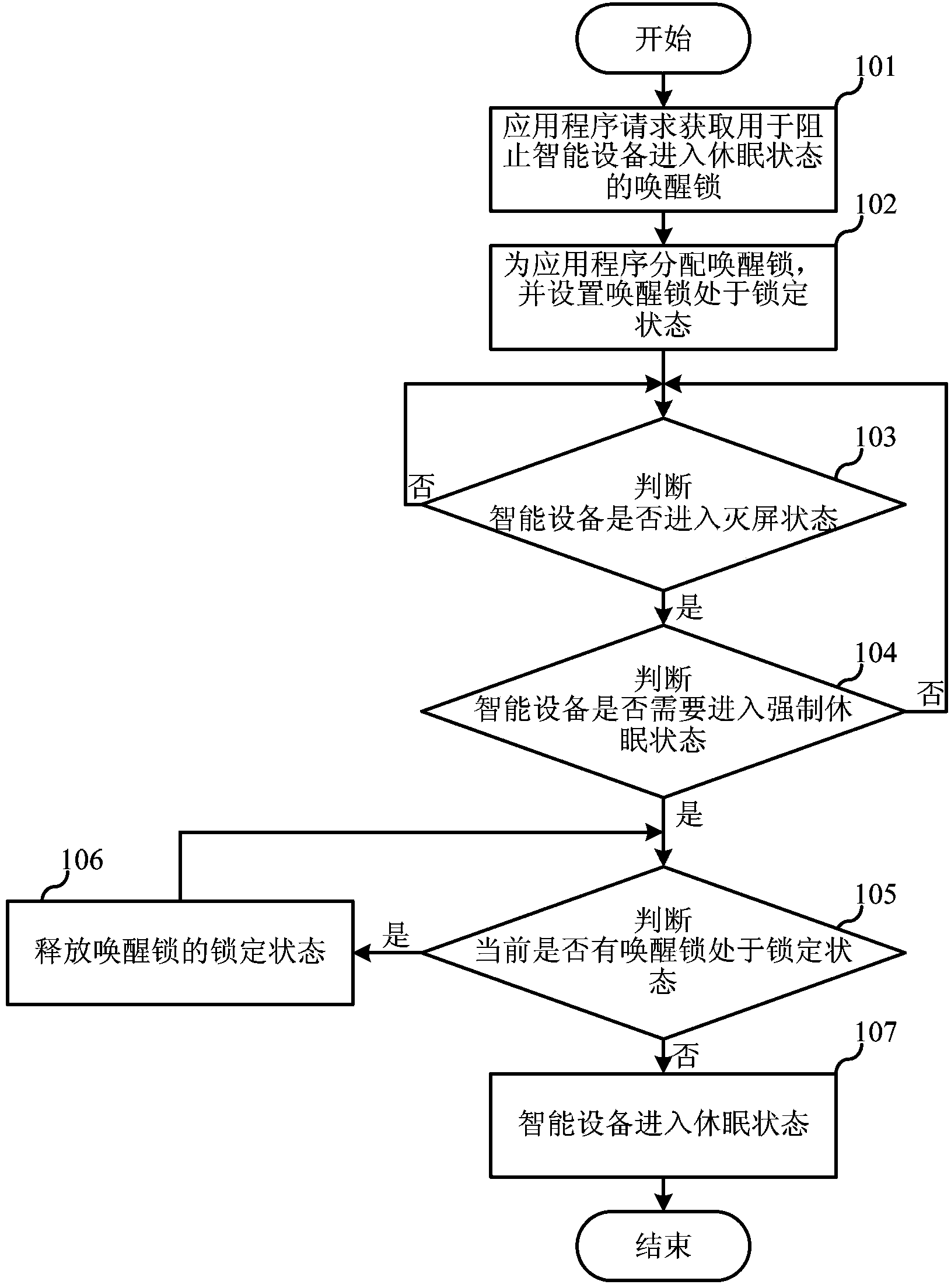
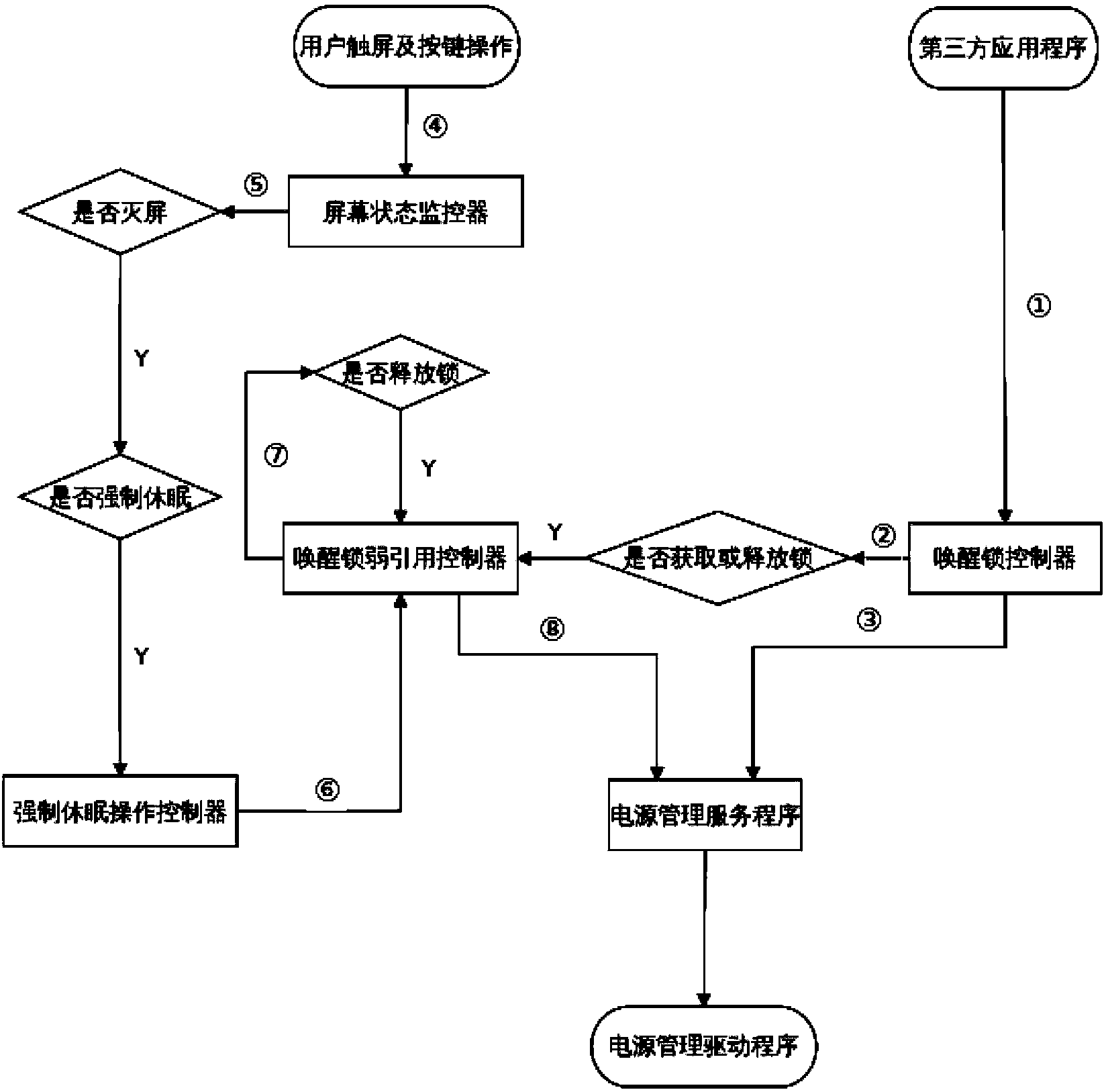
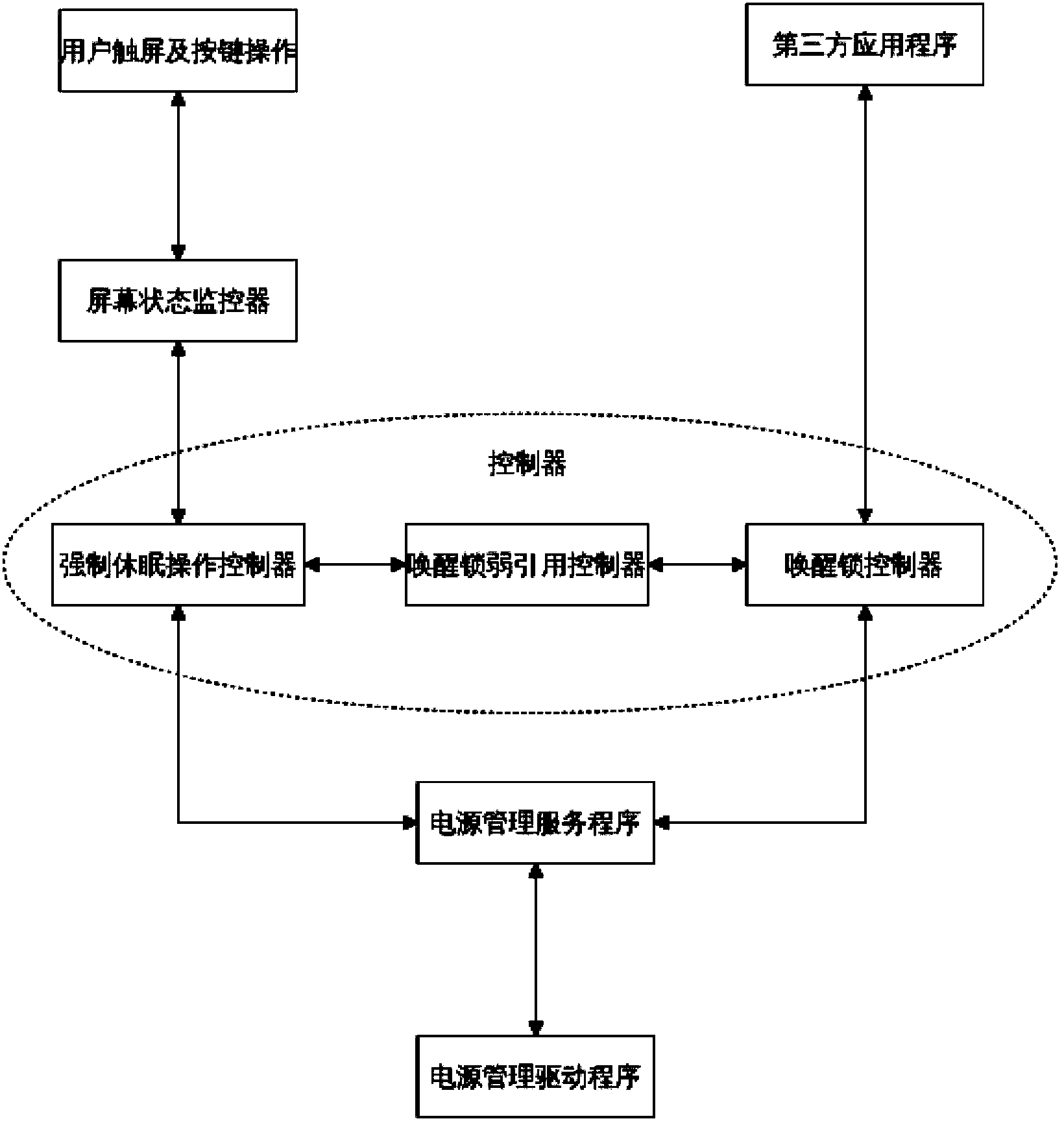
Dormancy method and dormancy system for intelligent equipment
ActiveCN103885565AGuaranteed uptimeImprove experiencePower supply for data processingComputer scienceIntelligent equipment
The invention relates to intelligent equipment and discloses a dormancy method and a dormancy system for the intelligent equipment. The dormancy method includes that by distributing awakening locks for application programs, when the intelligent equipment needs to enter a forced dormancy state, locking states of all awakening locks are released, so that no matter current equipment is in any state, the intelligent equipment can enter a dormancy state as long as a user has the need. In addition, by performing weak reference backing-up on the awakening locks when distributing the awakening locks and realizing operation on the awakening locks through operation on weak reference of the awakening locks, stability and reliability in running of the intelligent equipment can be guaranteed.
Owner:SHANGHAI SIMCOM LTD
Automated memory management of indexed data using weak references
InactiveUS20120066270A1Not be preventDigital data processing detailsSpecial data processing applicationsWaste collectionMemory management unit
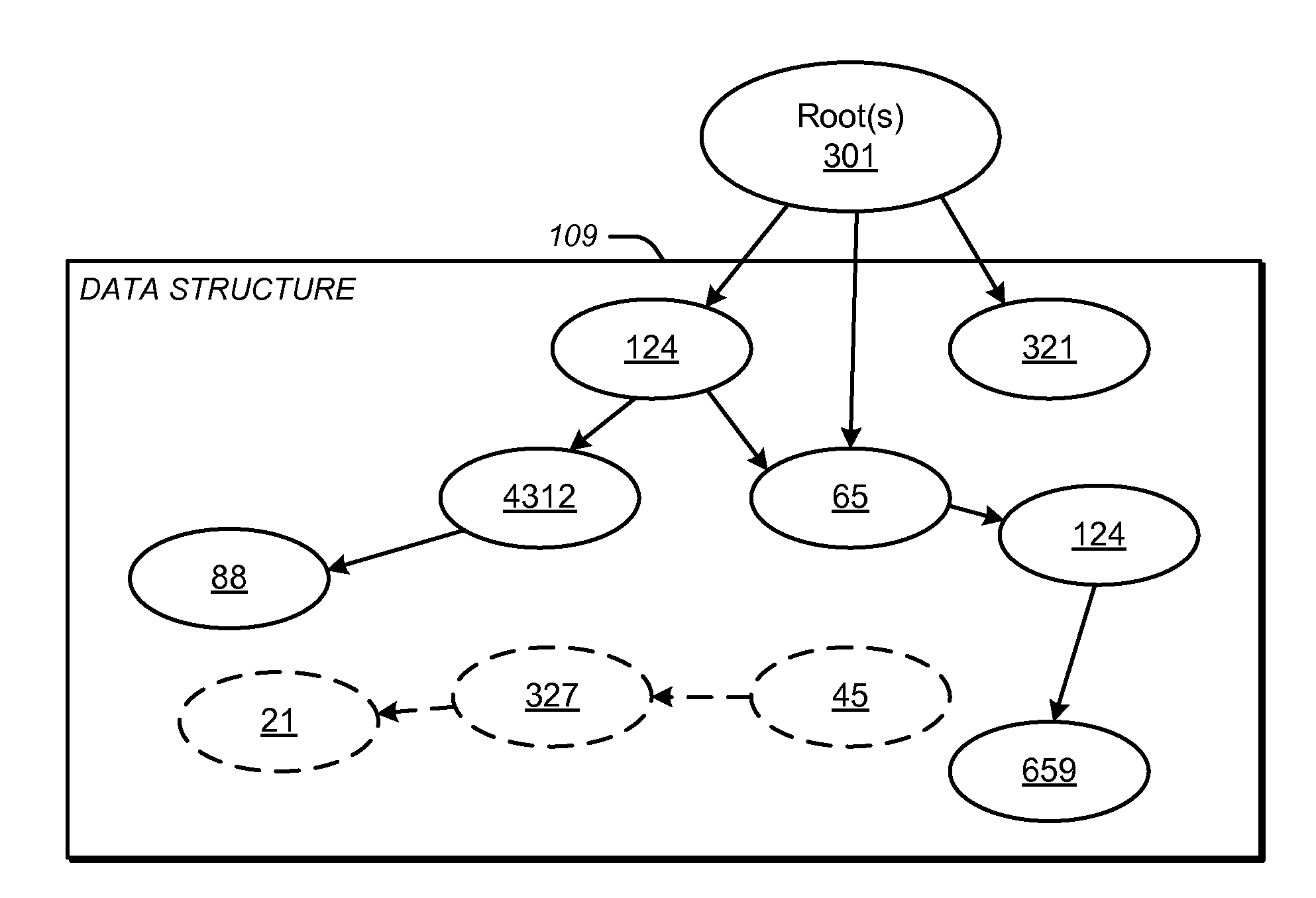
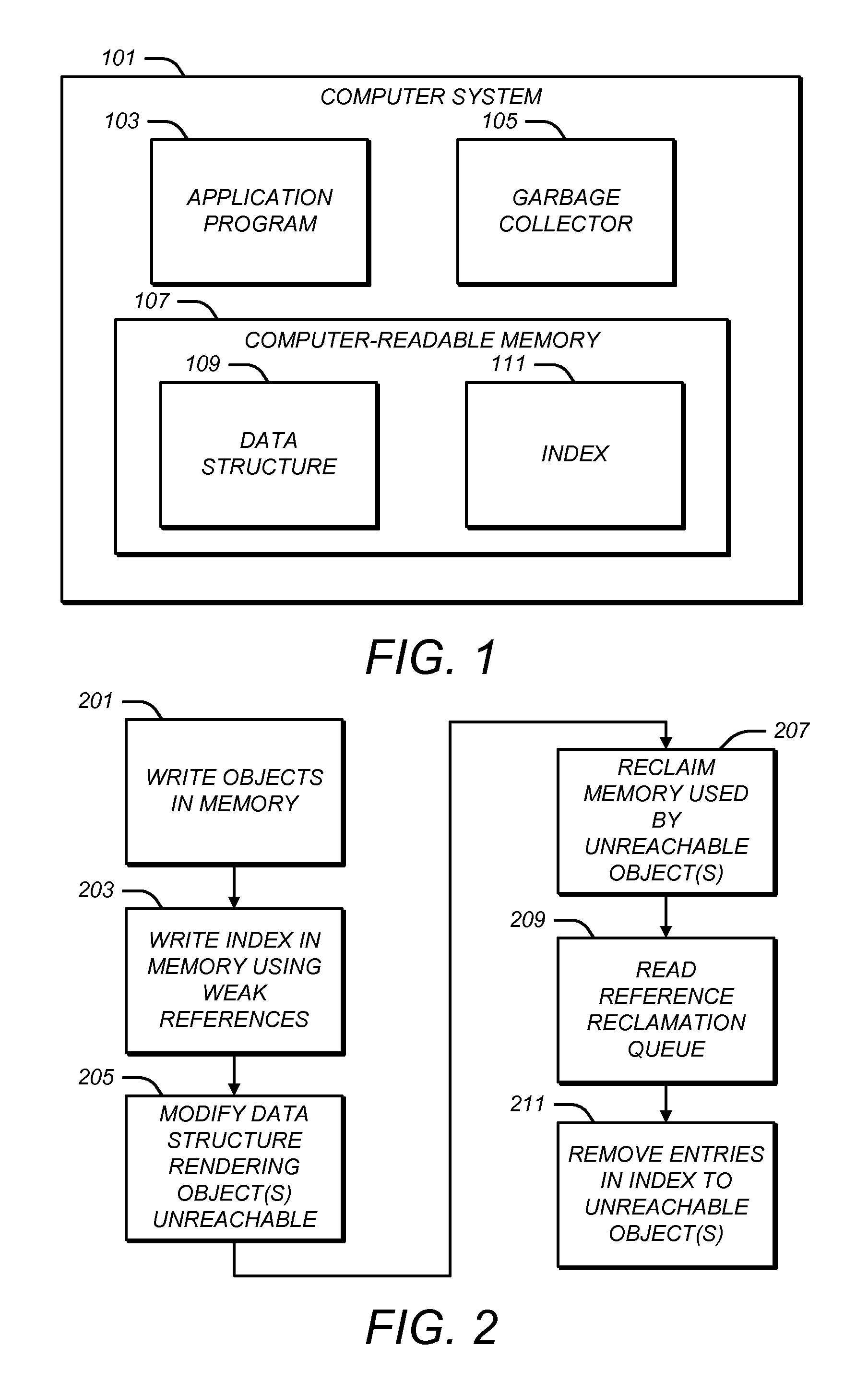
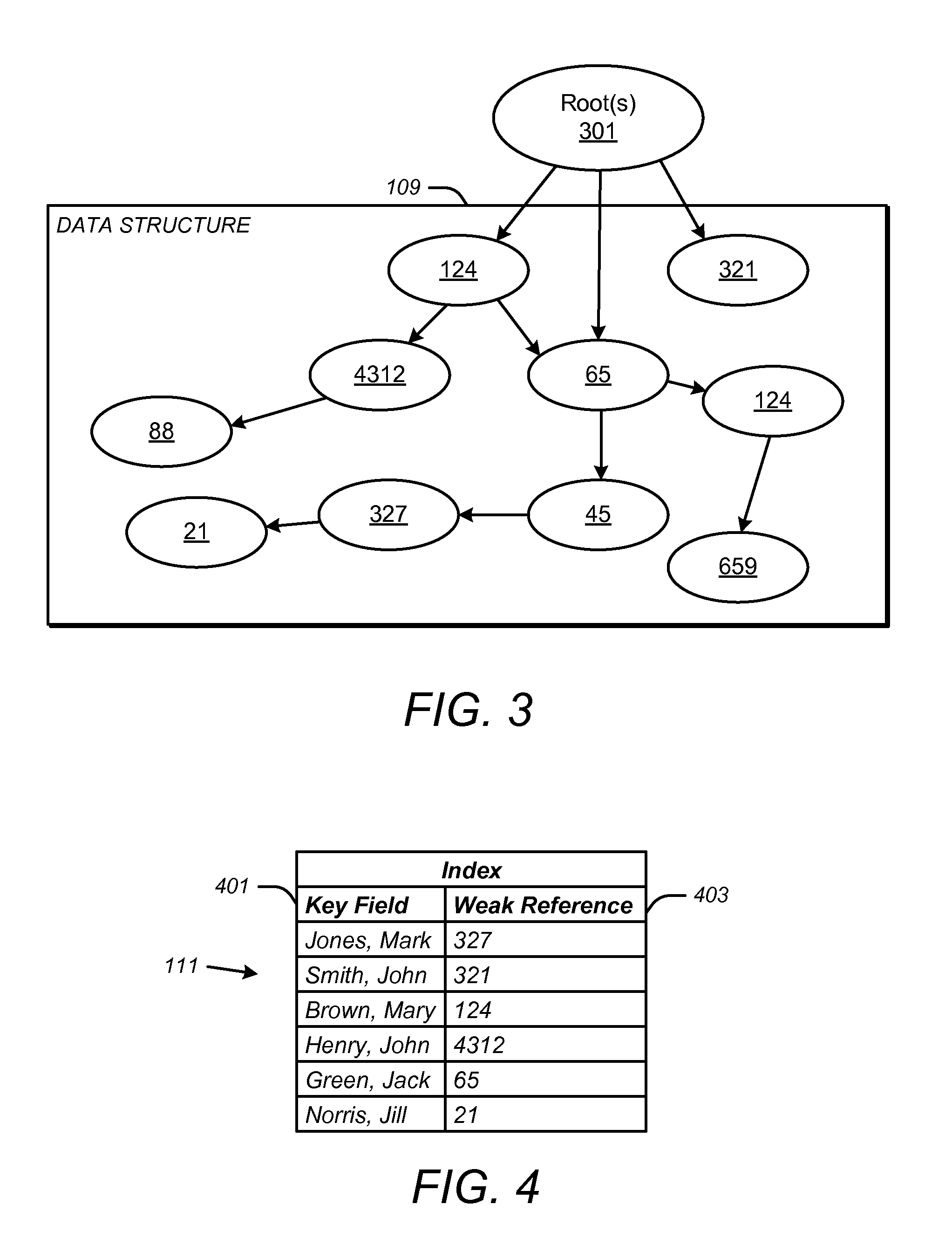
Memory may be managed by a garbage collector. The memory may contain a data structure and an index. The data structure may include a plurality of objects. The index may index a plurality of the objects in the data structure. For each object which it indexes, the index may contain a key field and a weak reference to the object. The key field may be indicative of an attribute of the object. The weak reference to the object may be associated with the key field. The weak reference may have a configuration which is not followed by a pointer tracer of the garbage collector when the garbage collector seeks to determine which of the objects in the data structure are no longer reachable from outside of the data structure during a memory reclamation process. This may insure that the index does not prevent the memory occupied by any unreachable object in the data structure from being reclaimed by the garbage collector during the memory reclamation process, even though the object is still referenced by the index. References in a reference reclamation queue generated by the garbage collector may be used to identify and remove entries in the index to objects whose memory has been reclaimed by the garbage collector.
Owner:ALELO
Better placement of dying objects in a generation managed by the train algorithm
ActiveUS7519640B1Avoid expensive I/O operationDigital data processing detailsMemory systemsWaste collectionWell placement
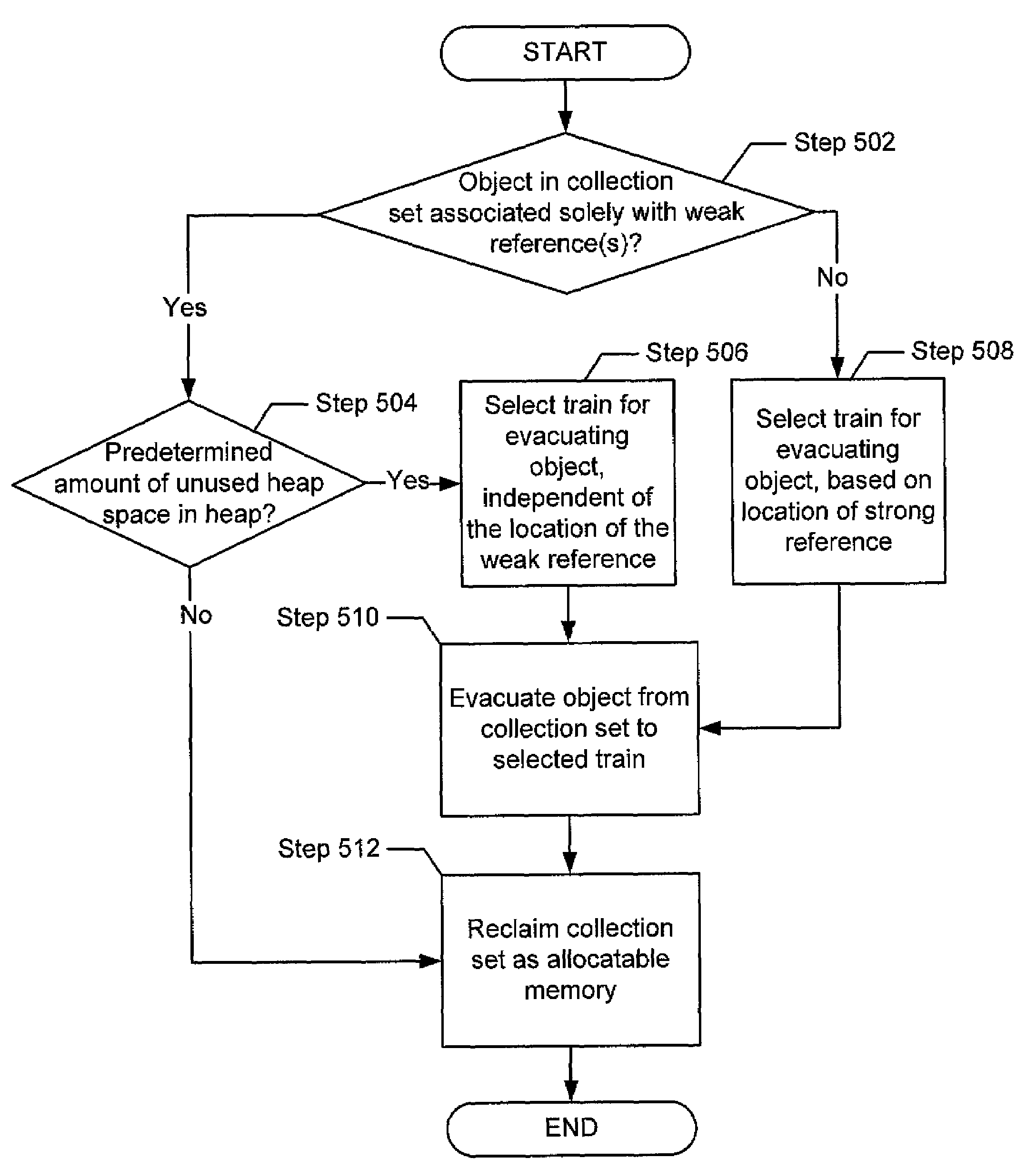
In a garbage collector that employs the train algorithm, some objects in the collection set are evacuated from the collection set, even though they are referred to only by weak references, in order to keep the data that they contain available for post-mortem processing. The destinations to which at least some such objects are evacuated are chosen independently of where the weak references to them are located.
Owner:ORACLE INT CORP
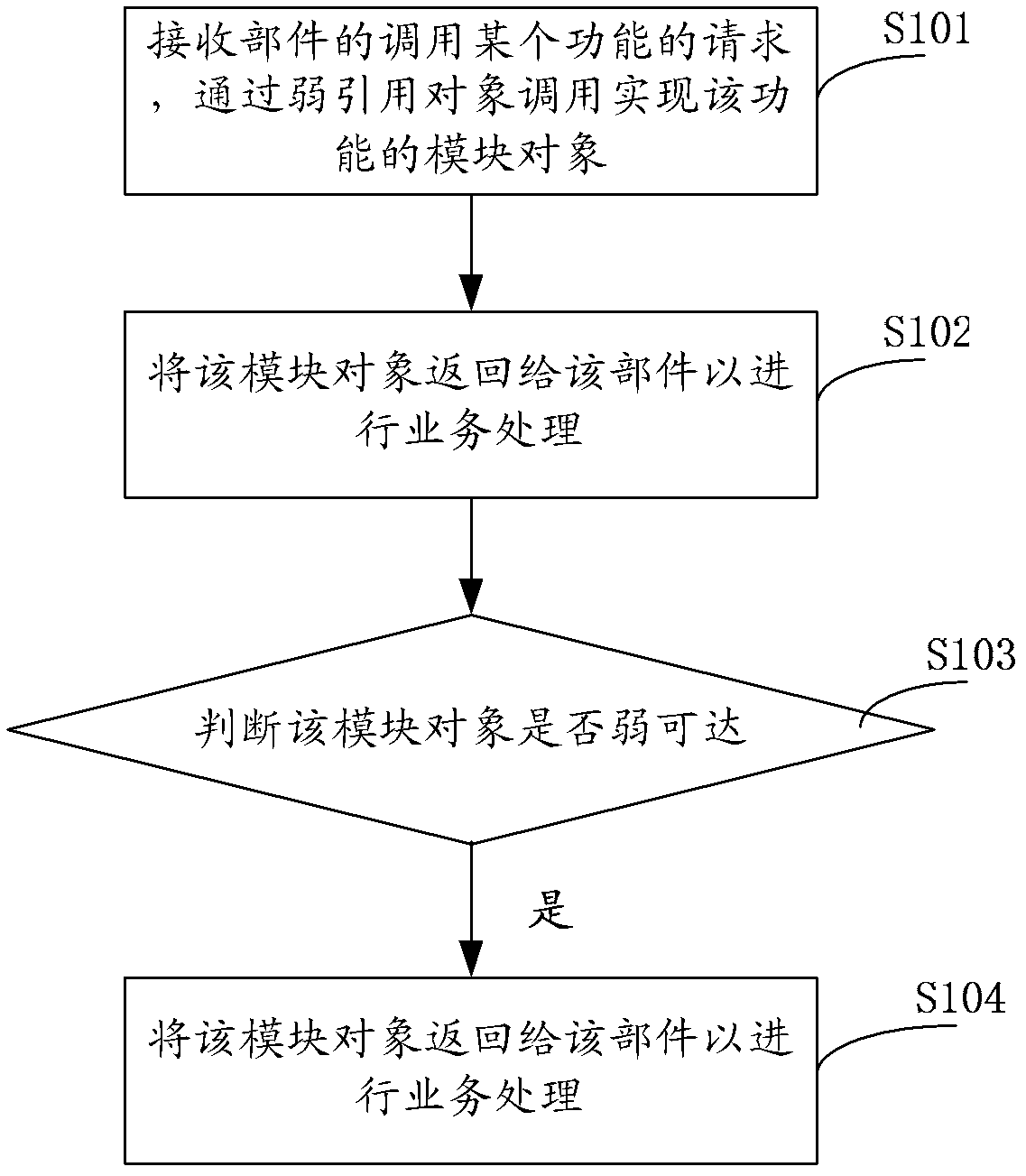
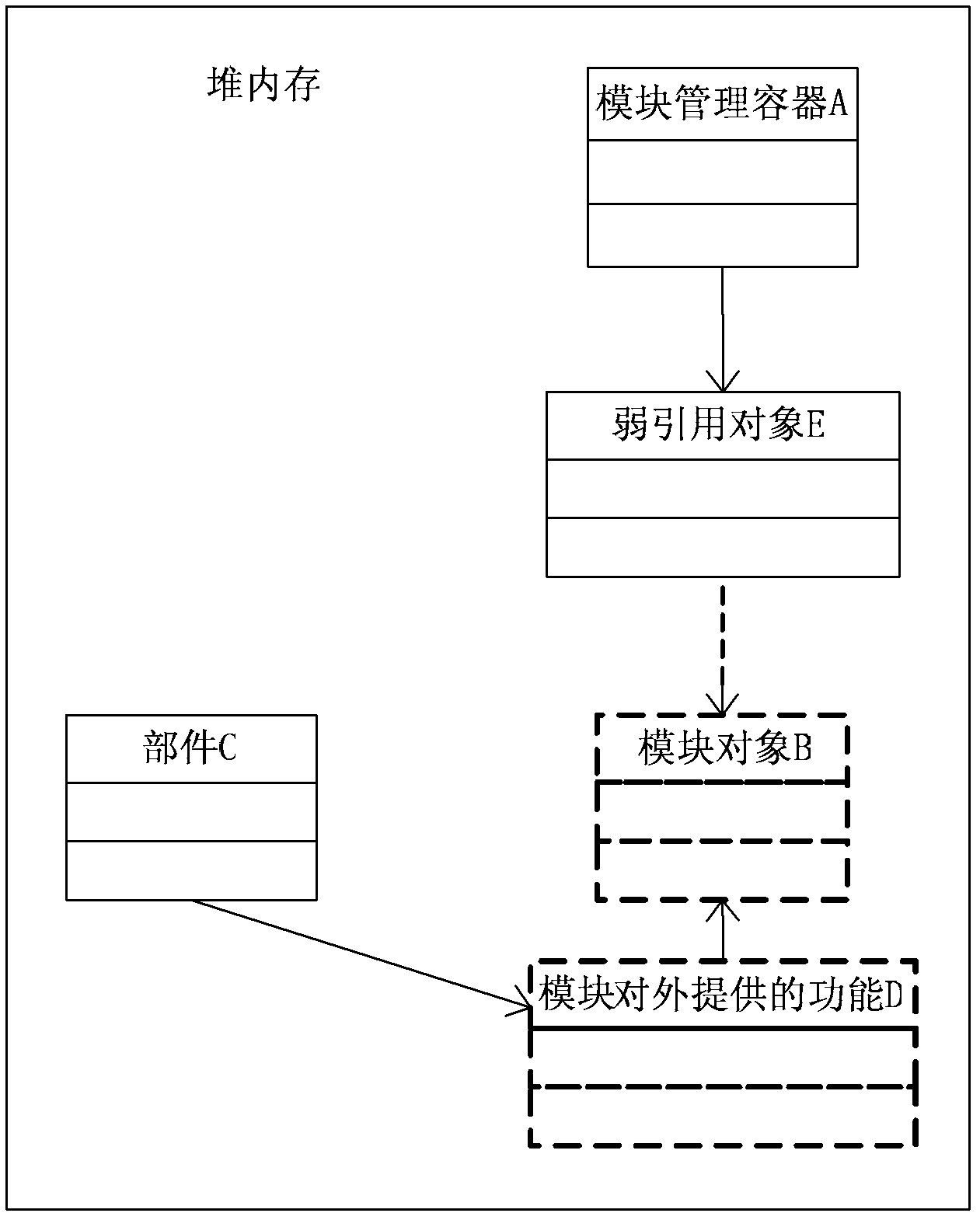
Transaction processing method and Java virtual machine
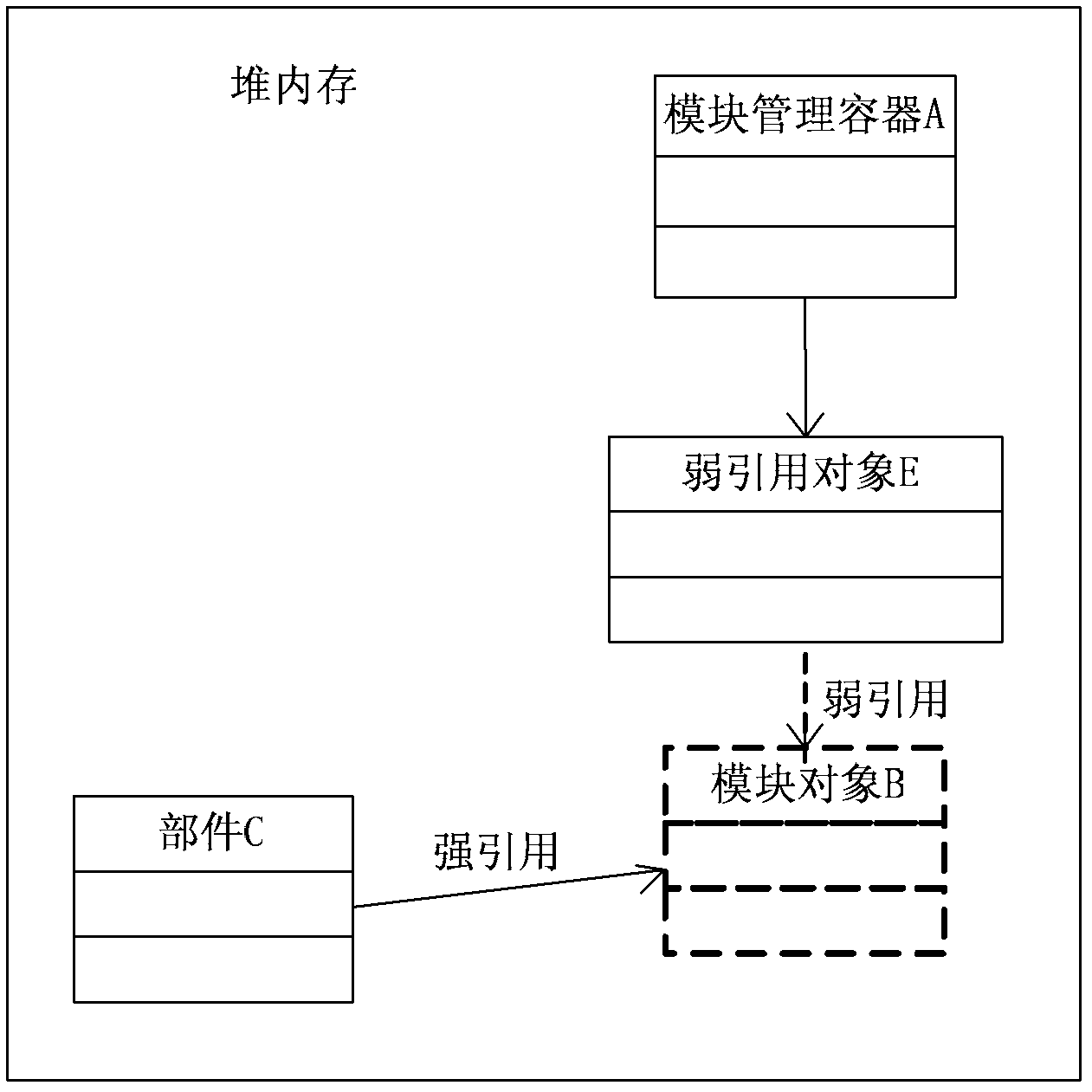
InactiveCN102253854ATimely releaseSave memory resourcesProgram loading/initiatingSoftware simulation/interpretation/emulationSoftware engineeringTransaction processing system
The embodiment of the invention provides a transaction processing method and a Java virtual machine. The method comprises the steps of: receiving a request of a unit for calling a certain function, and calling a module object capable of realizing the function through a weak reference object; returning the module object to the unit so as to carry out transaction processing; and judging whether the module object is weakly reachable, if so, clearing the module object. According to the transaction processing method and the Java virtual machine provided by the embodiment of the invention, when a module management container receives the request for calling a set-up function sent by the unit, the module object capable of realizing the set-up function is called through the weak reference object, and after the unit calls the module object to perform transaction processing, if the module object is weakly reachable, the module object can be cleared by the virtual machine, so that the memory resource occupied by the module can be released in time, and the memory resource is saved.
Owner:HUAWEI TECH SERVICE
View refreshing method and view refreshing device
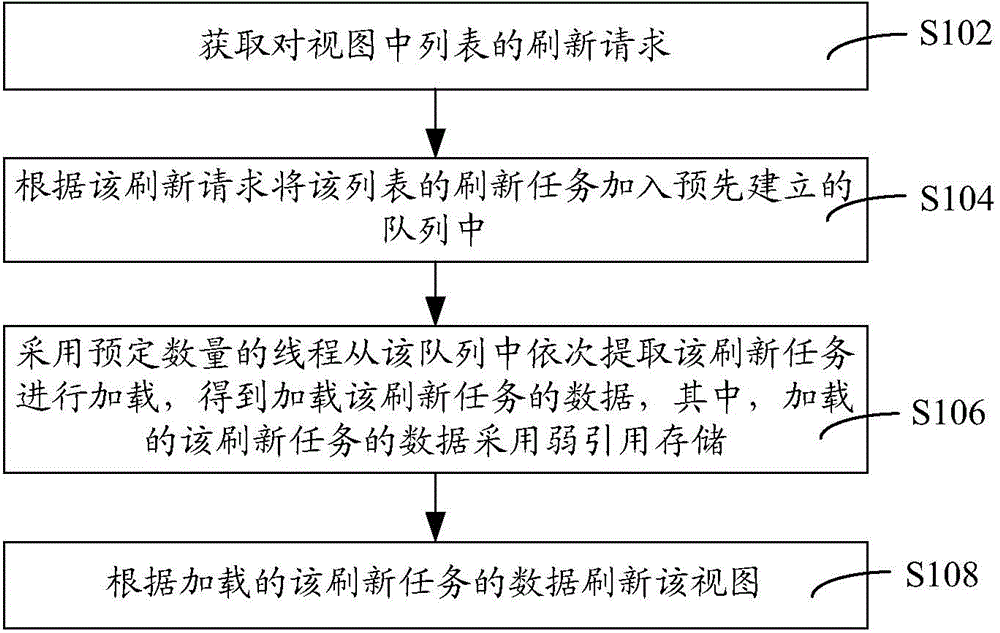
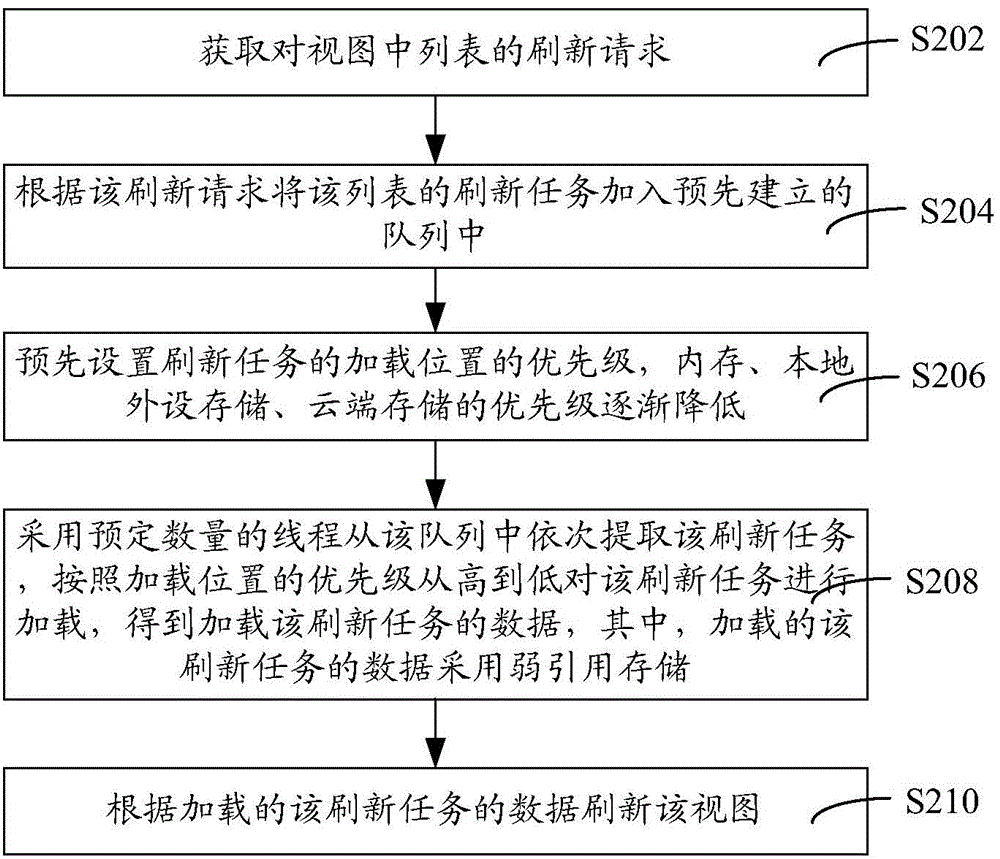
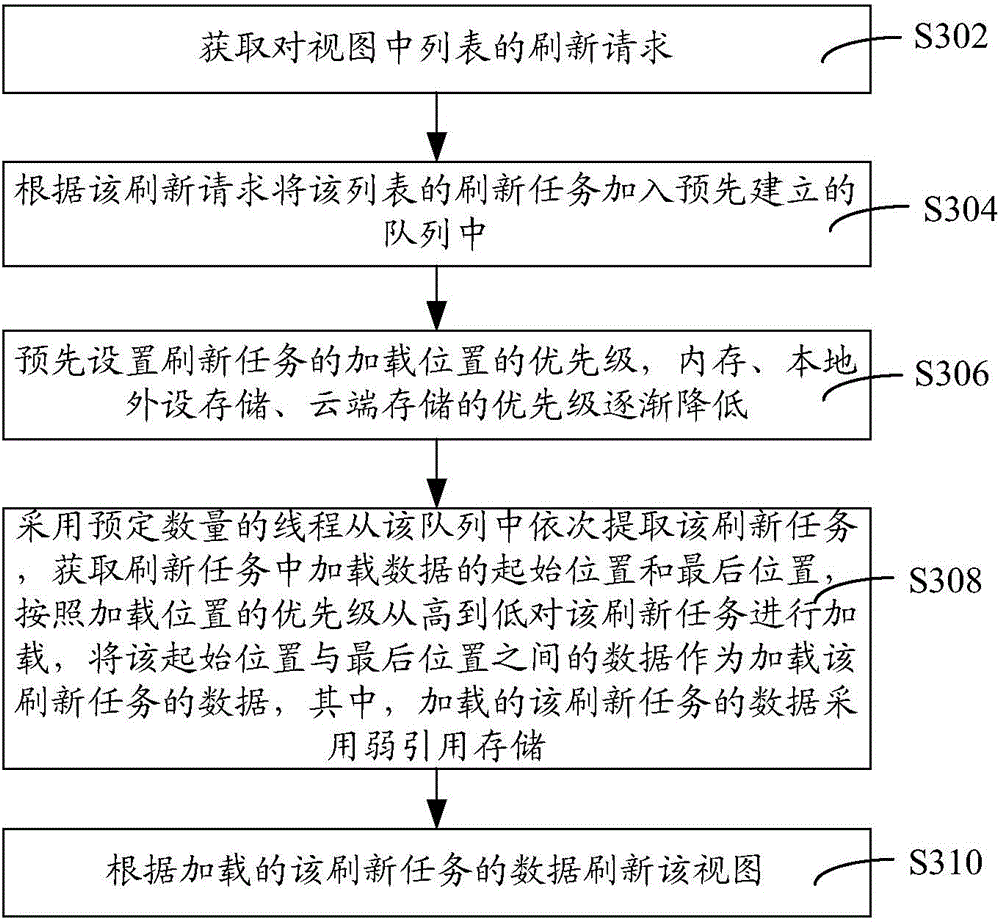
ActiveCN104423996AReduce occupancyRefresh smoothResource allocationProgram loading/initiatingOccupancy rateWeak reference
The invention relates to a view refreshing method and a view refreshing device. The method comprises the following steps of acquiring a refreshing request on a list in a view; adding refreshing tasks of the list to a queue established in advance according to the refreshing request; sequentially extracting the refreshing tasks from the queue and loading the refreshing tasks by using a defined amount of threads to obtain data on loading of the refreshing tasks; and refreshing the view according to the loaded refreshing tasks. The data of the loaded refreshing tasks are stored in a weak reference manner. The cost on establishment of a new thread of each refreshing task is reduced due to the defined amount of threads, the data which are stored in the weak reference manner can be recycled at any time, internal storage space occupied by the data can be released, the occupancy rate of system resources such as an internal storage device and a CPU (central processing unit) is reduced, pages are refreshed smoothly, and the integrity of the data is guaranteed with the aid of the queue.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Session lifecycle management within a multi-tiered enterprise network
ActiveUS8281014B2Multiple digital computer combinationsTransmissionApplication lifecycle managementObject based
A system and method are described for managing session lifecycles within a multi-tiered enterprise network. In one embodiment, a plurality of session objects are generated at different layers of the enterprise network in response to a client request. Each of the session objects store session data defining a state of interaction with the client. In addition, one embodiment of the invention manages the lifecycle of a first session object based on corresponding lifecycles of one or more related session objects and also the type of relationship existing between the first session object and the one or more related session objects. In one embodiment, the defined relationship types include strong references, weak references, and soft references.
Owner:SAP AG
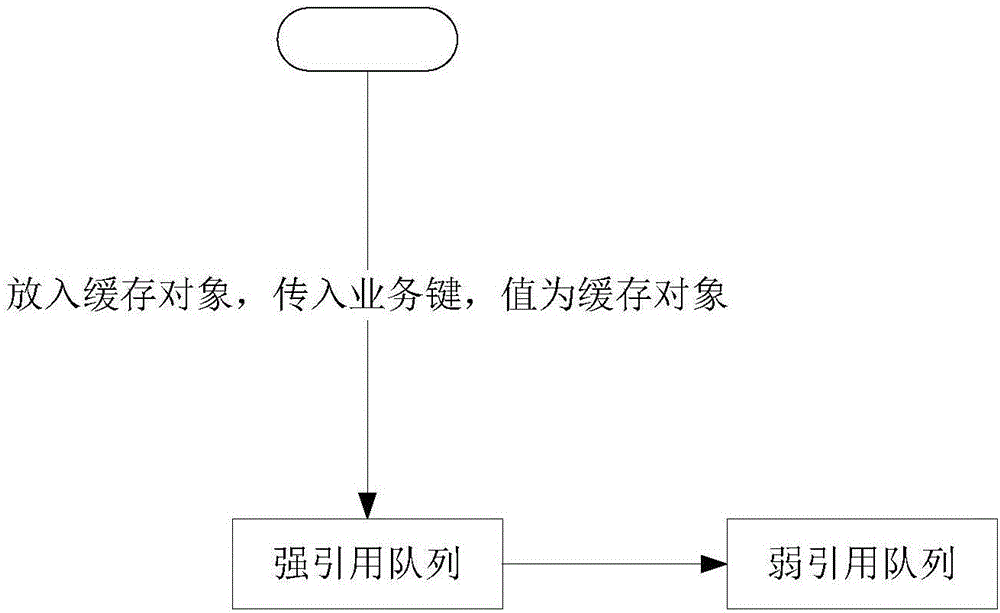
Automatic management method of object cached in memory
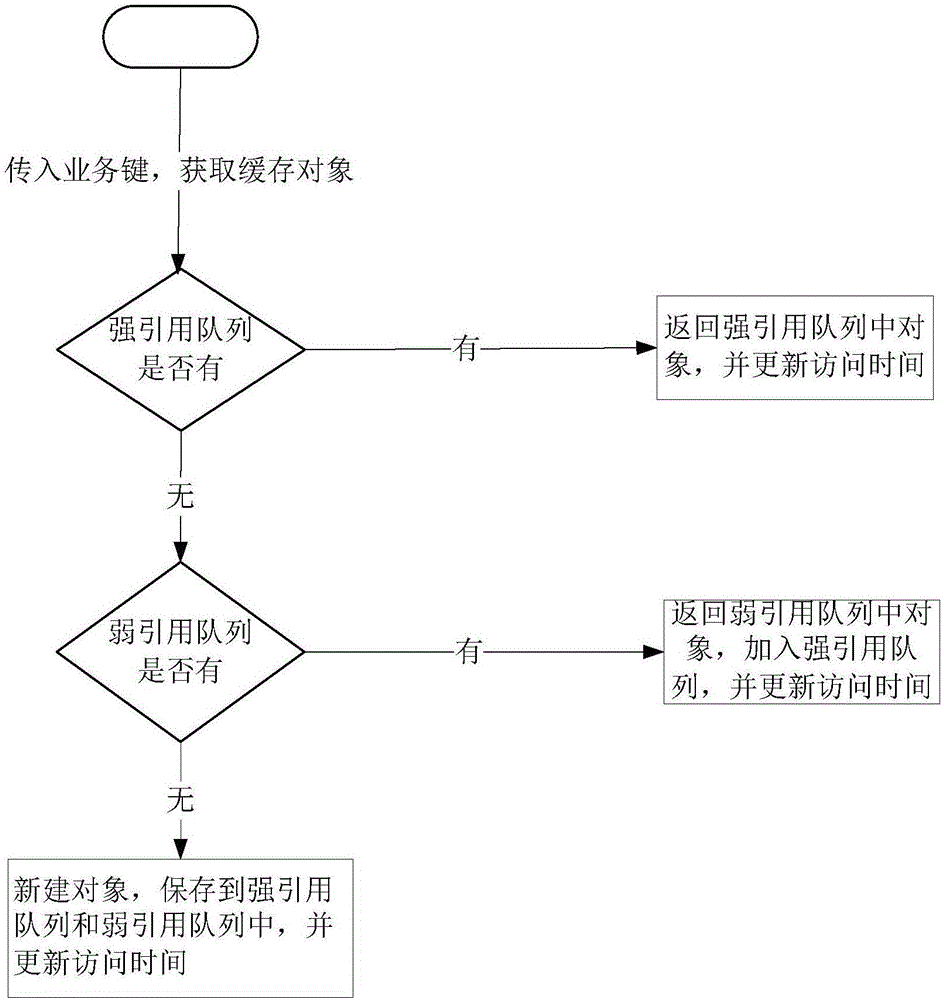
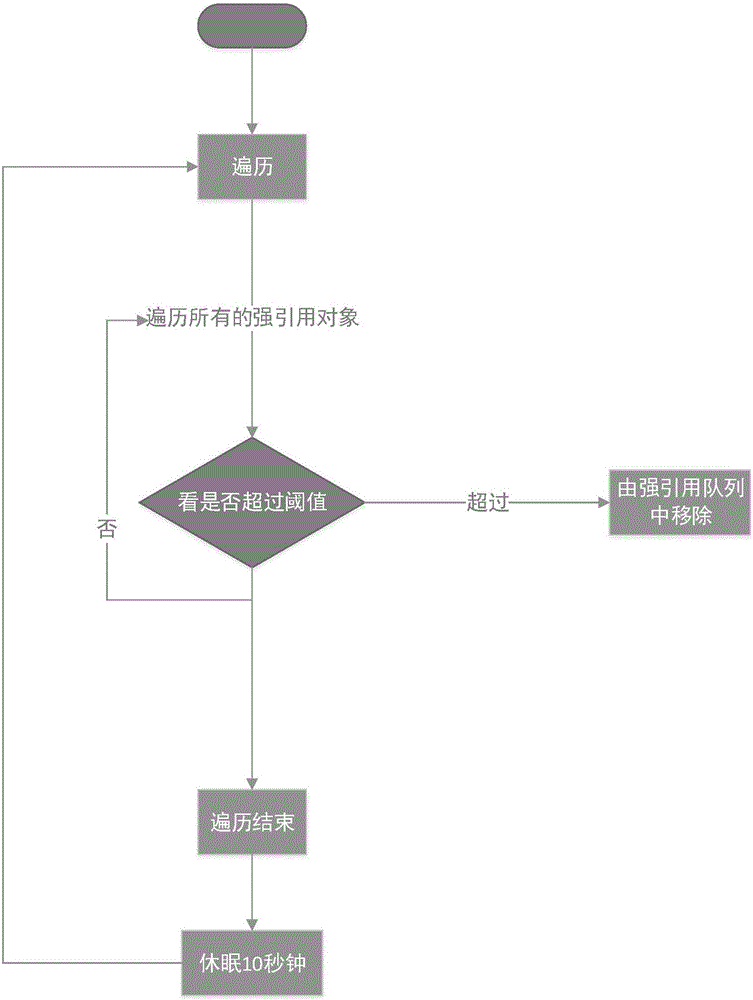
InactiveCN106528444AAvoid duplicate creationMemory adressing/allocation/relocationPattern recognitionStrong reference
The invention discloses an automatic management method of an object cached in a memory. The automatic management method comprises the following steps: simultaneously putting the object, which is put into a memory cache, into a strong reference queue and a weak reference queue; when accessing the object, searching whether the object exists in the strong reference queue first, and if the object exists in the strong reference queue, returning; if the object does not exist in the strong reference queue, continuously searching whether the object exists in the weak reference queue; if the object is searched in the weak reference queue, adding the object from the weak reference queue into the strong reference queue; and if the object is not searched in the weak reference queue, establishing the object, and caching the object into the strong reference queue. According to the method disclosed by the invention, only one object exists in the memory within the same time, so that re-establishment of the object is avoided. The invention provides an automatic recycling mechanism of the memory; and no object is actively released from outside. By means of monitoring the weak reference queue, the object with memory leak can be found.
Owner:BEIJING JINHER SOFTWARE
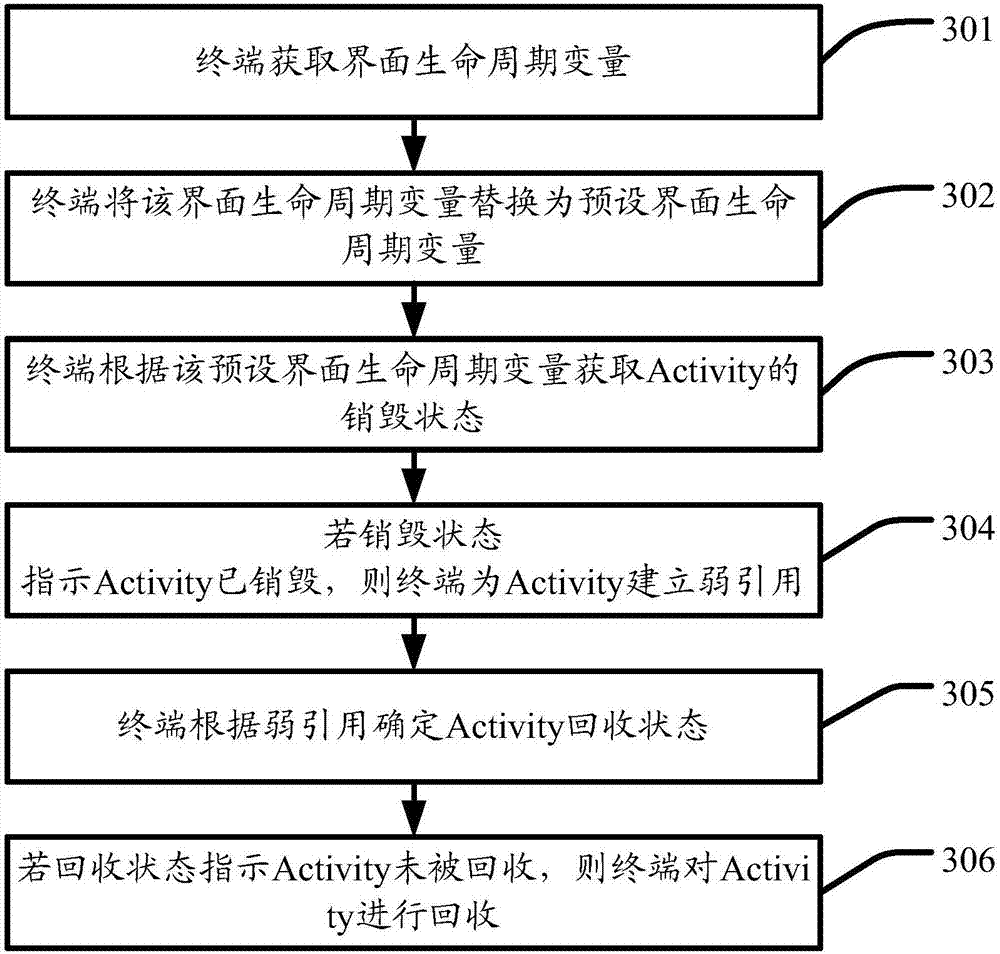
Interface element Activity processing method and terminal
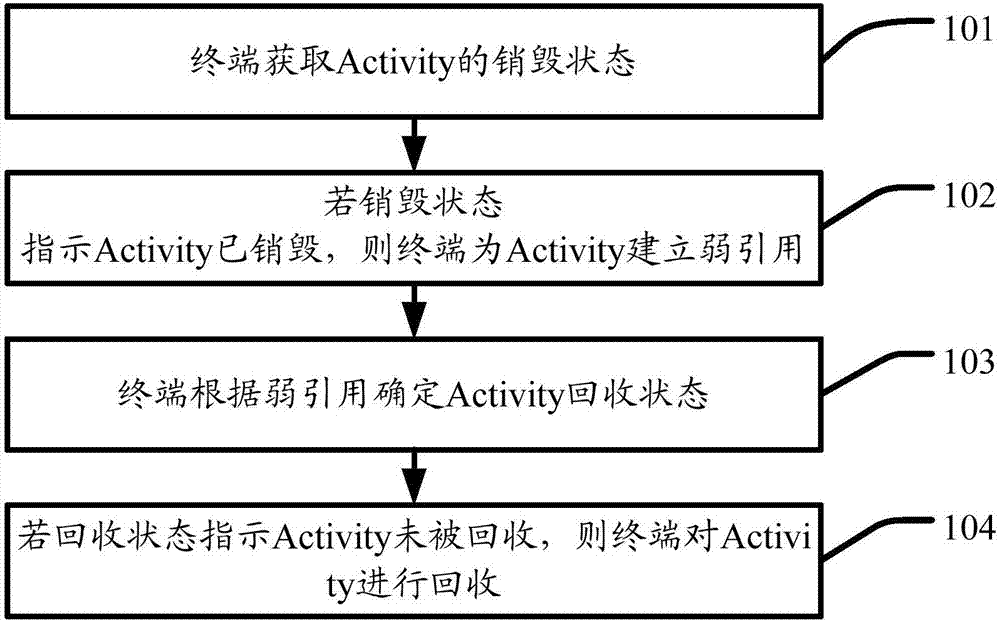
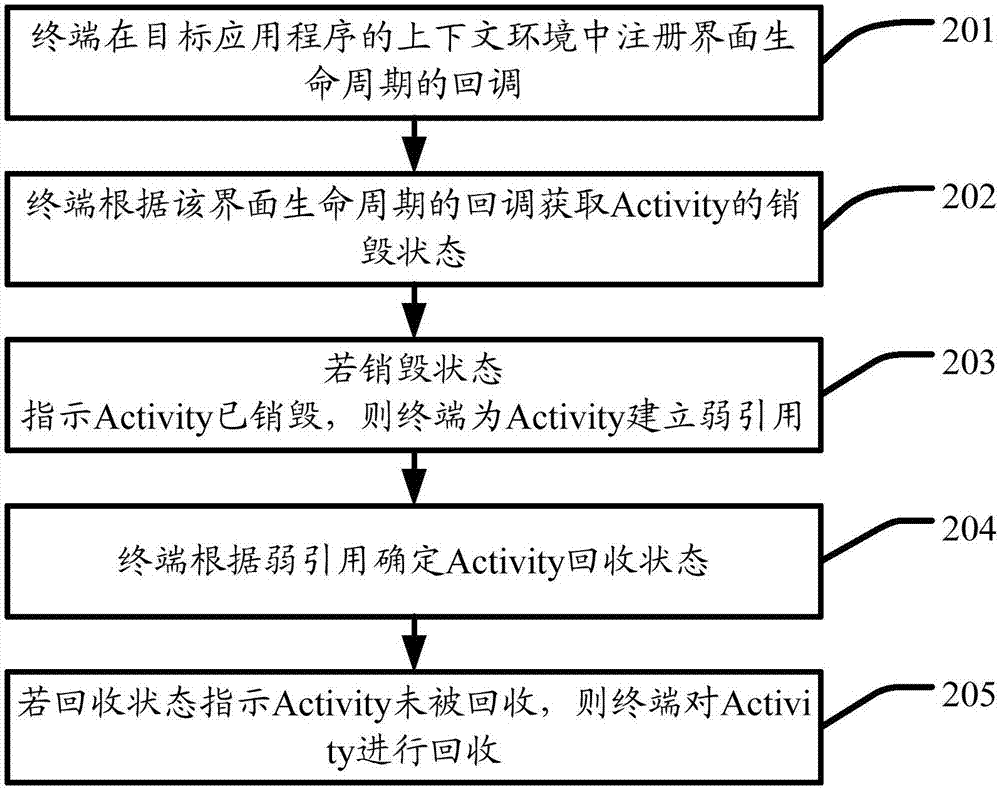
InactiveCN106886413AReduce memory usageReduce CatonExecution for user interfacesReal-time computingWeak reference
Embodiments of the invention disclose an interface element Activity processing method and a terminal. The method is used for the terminal, can monitor a recovery state of a destroyed Activity in real time, and timely reminds the terminal to recover the Activity when the Activity is not recovered, so that the memory occupation of the terminal is reduced and the jamming of the terminal is relieved. The method comprises the steps that the terminal obtains a destruction state of the Activity; if the destruction state indicates that the Activity is destroyed, the terminal establishes a weak reference for the Activity; the terminal determines the recovery state of the Activity according to the weak reference; and if the recovery state indicates that the Activity is not recovered, the terminal recovers the Activity.
Owner:TENCENT TECH (SHENZHEN) CO LTD
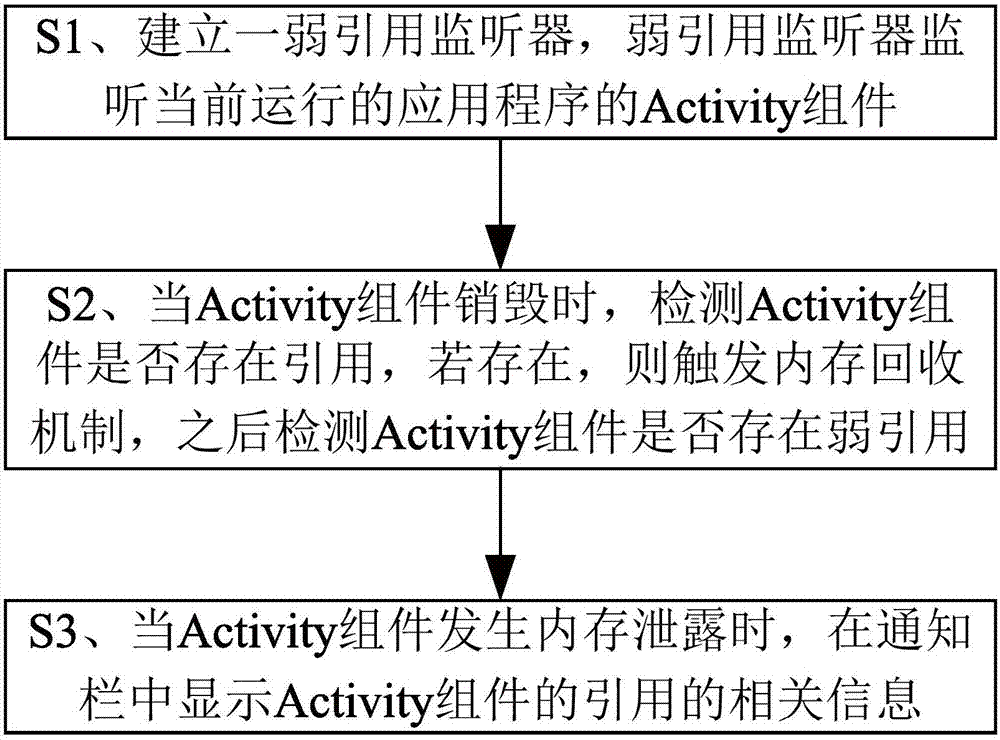
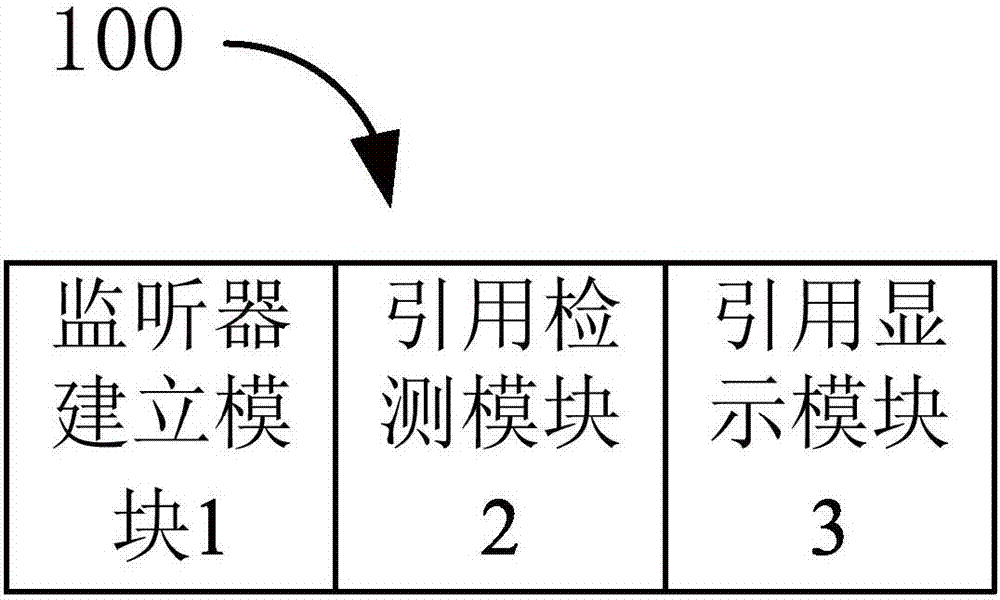
Memory leakage detection method and apparatus for Android application
InactiveCN107239394AEasy to monitorImprove robustnessSoftware testing/debuggingApplication softwareAndroid application
The present invention discloses a memory leakage detection method and apparatus for an Android application. The memory leakage detection method comprises: establishing a weak reference audio monitor, wherein the weak reference audio monitor monitors the Activity component of the currently running application; and when the Activity component is destroyed, detecting whether there is a reference to the Activity component, if so, triggering a memory recovery mechanism, and detecting whether there is a weak reference to the Activity component. Beneficial effects of the method and apparatus disclosed by the present invention are that, by arbitrarily setting a monitor object, monitoring of the memory leakage in the application development can be facilitated; and the method and apparatus are simple and flexible, so that not only the robustness of the application is improved, and the development efficiency of the engineer is improved.
Owner:卓望数码技术(深圳)有限公司
Memory optimization method, apparatus and system, and computer readable storage medium
ActiveCN108021445AImplement life cycle managementEasy to shareResource allocationVisual/graphical programmingProgramming languageBusiness process
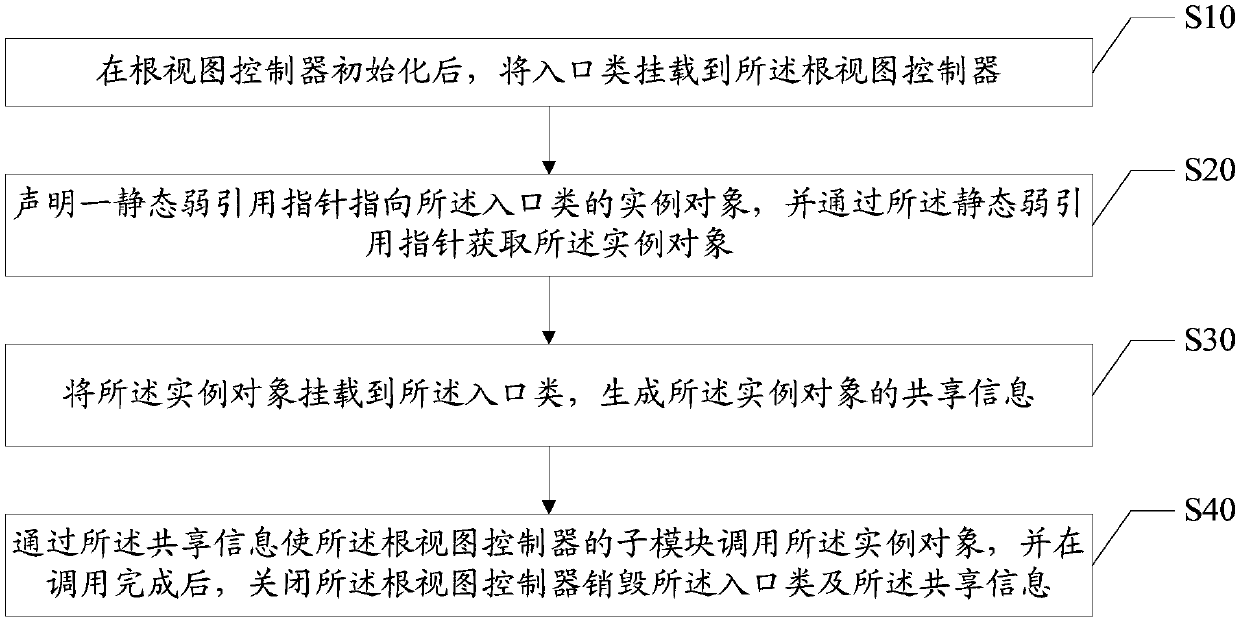
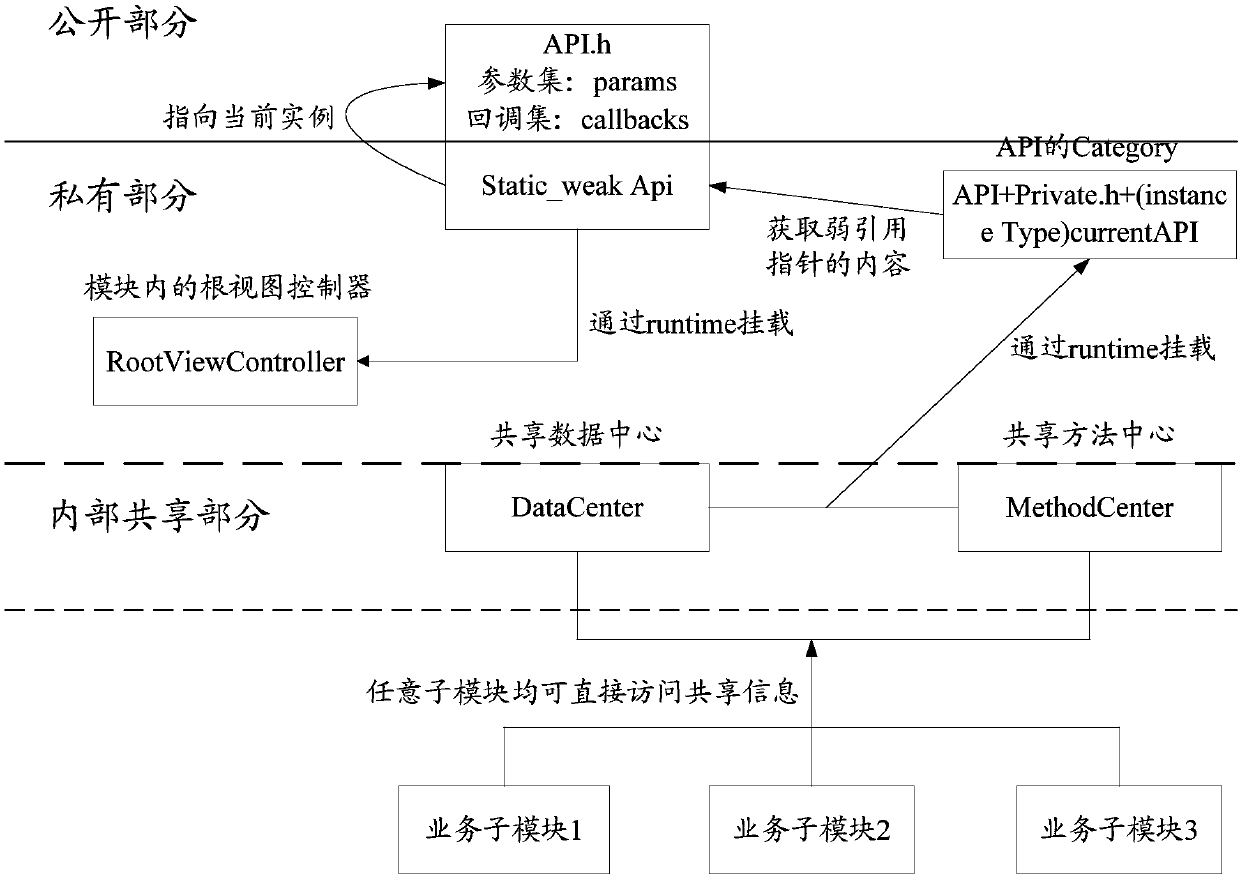
The invention discloses a memory optimization method. The method comprises the steps of mounting an entry class to a root view controller after the root view controller is initialized; declaring a static weak reference pointer to point to an instance object of the entry class, and through the static weak reference pointer, obtaining the instance object; mounting the instance object to the entry class, and generating shared information of the instance object; and through the shared information, enabling a sub-module of the root view controller to call the instance object, and after the call isfinished, disabling the root view controller and destroying the entry class and the shared information. The invention furthermore discloses a memory optimization apparatus and system, and a computer readable storage medium. By self-defining enabling and disabling of a life cycle of a business process, the beneficial effect of managing the life cycle of the business process is achieved.
Owner:GUANGZHOU PINWEI SOFTWARE
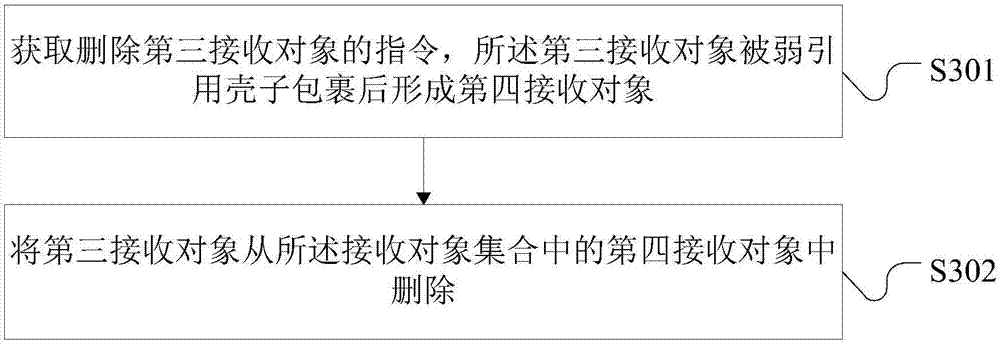
Memory management method and apparatus, and electronic device
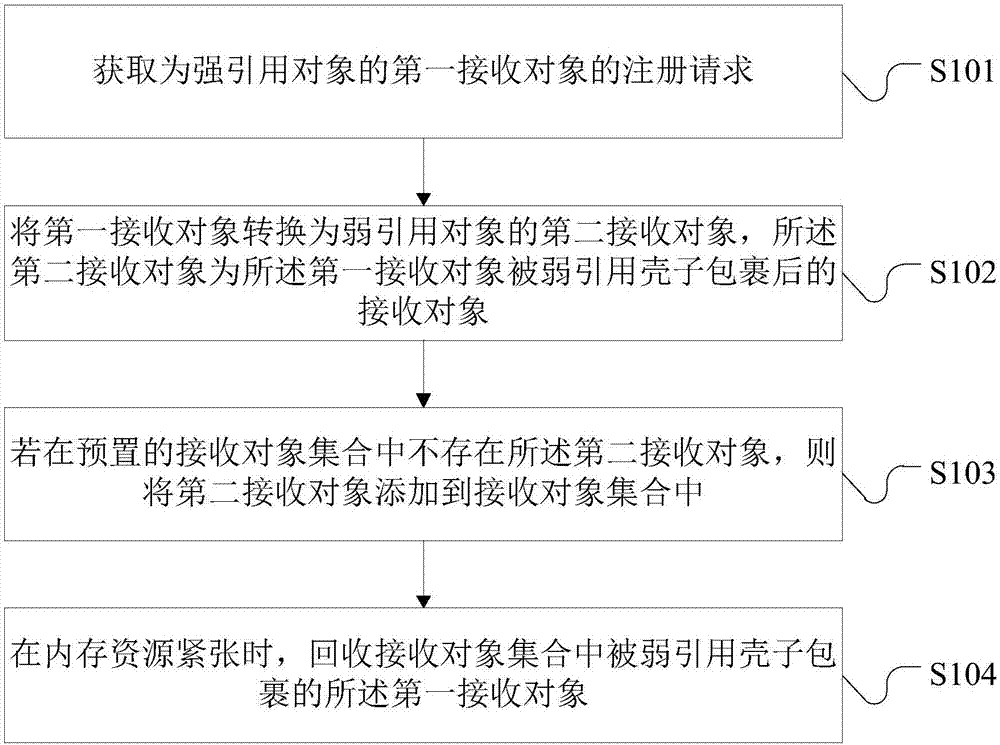
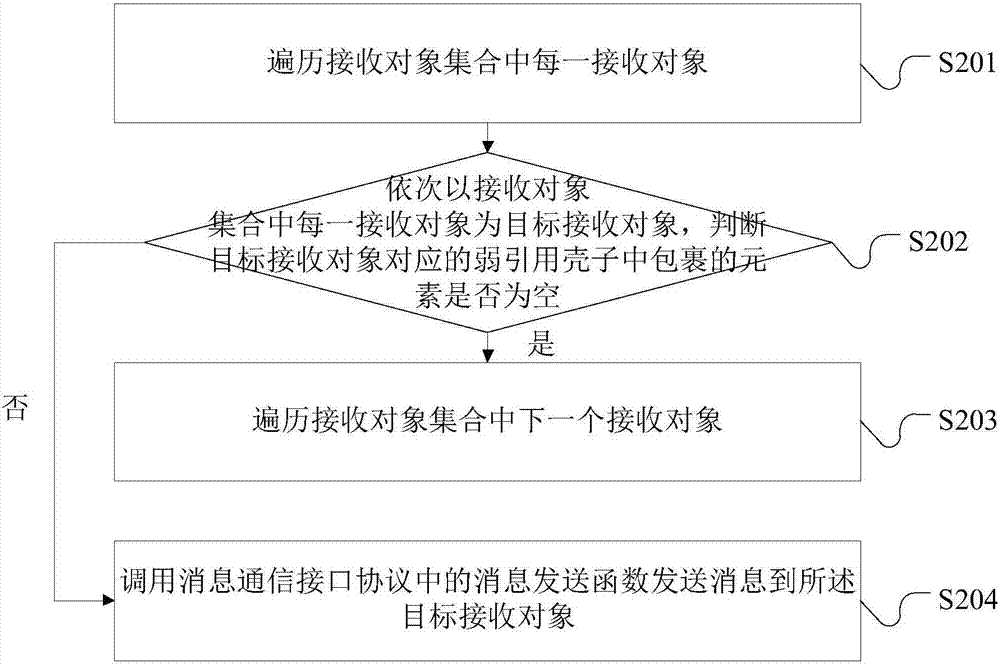
Embodiments of the invention disclose a memory management method and apparatus, and an electronic device. The method comprises the steps of obtaining a registration request of a first receiving objectas a strong reference object; converting the first receiving object into a second receiving object as a weak reference object, wherein the second receiving object is a receiving object after the first receiving object is wrapped with a weak reference shell; if the second receiving object does not exist in a preset receiving object set, adding the second receiving object to the receiving object set; and when memory resources are in shortage, recovering the first receiving object wrapped with the weak reference shell in the receiving object set. A monitor as a message receiving object is converted into the weak reference object; and when the memory resources are in shortage, the message receiving object can be recovered, so that the message receiving object not subjected to de-registrationstill can ensure that a system can perform memory recovery on the message receiving object at a moment, and the purpose of solving the problem of memory leakage is achieved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
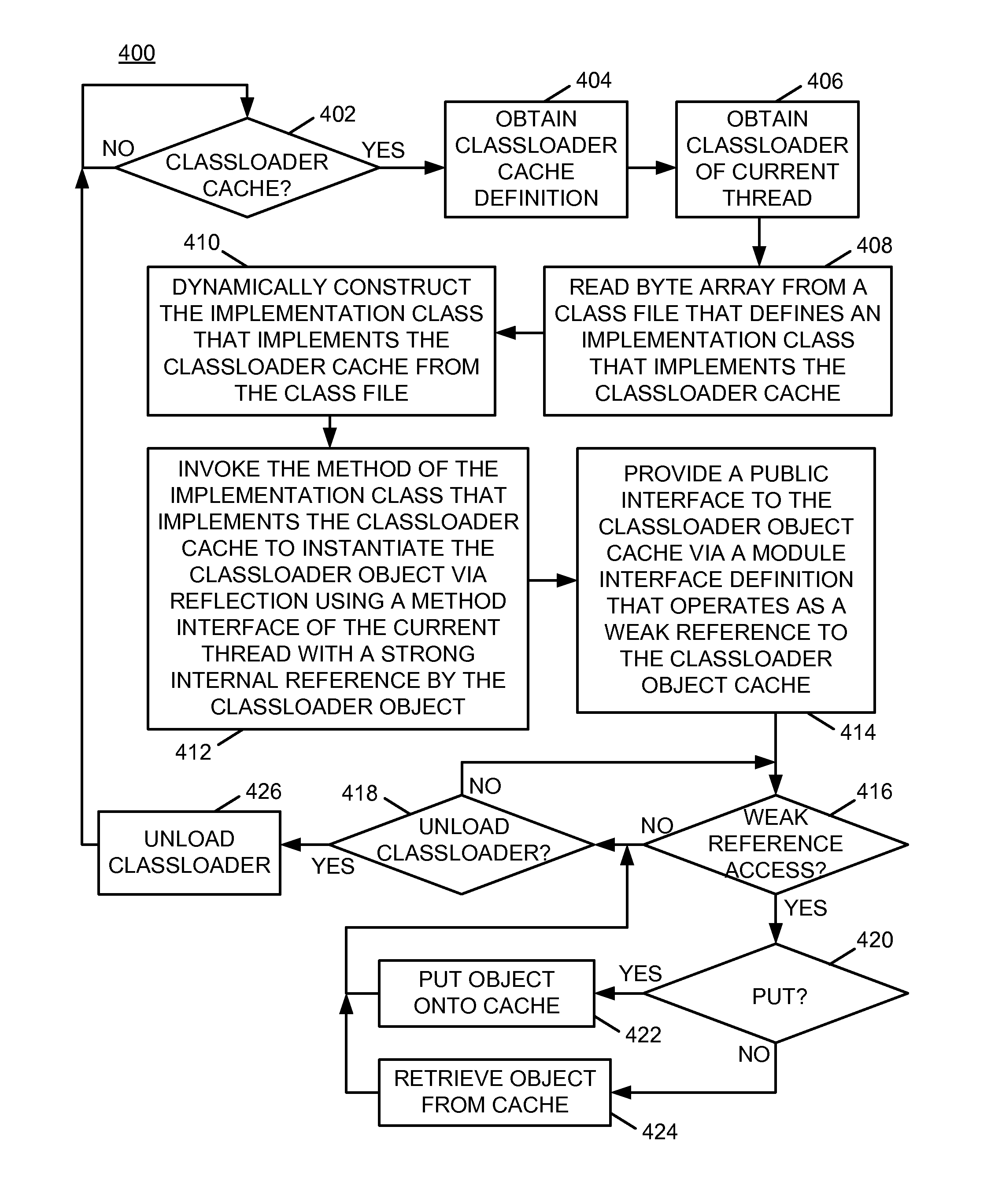
Prevention of classloader memory leaks in multitier enterprise applications
InactiveUS20130080706A1Improves classloader related memory issueAlleviates code developer burdenMemory adressing/allocation/relocationSoftware metricsBusiness enterpriseParallel computing
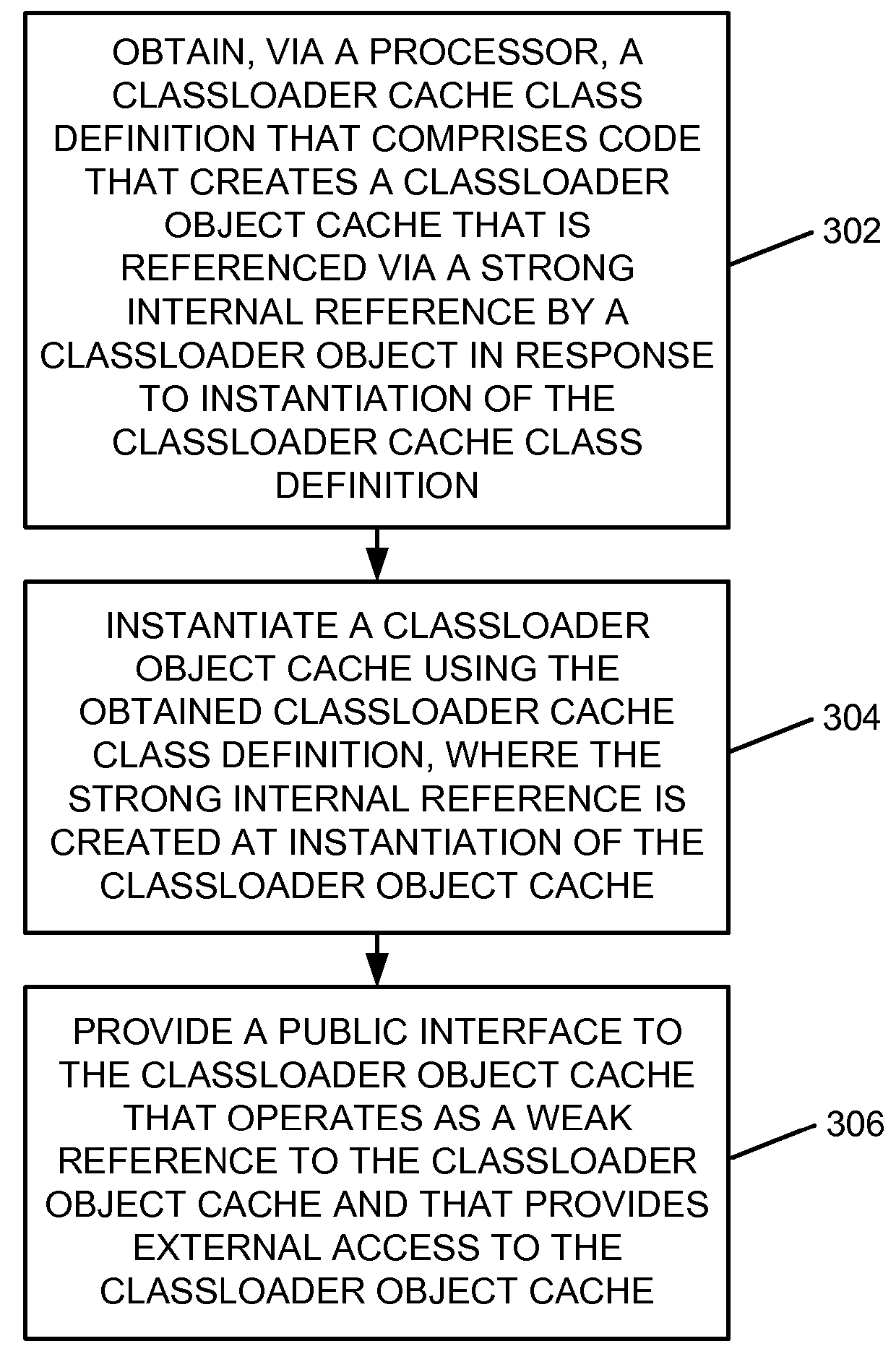
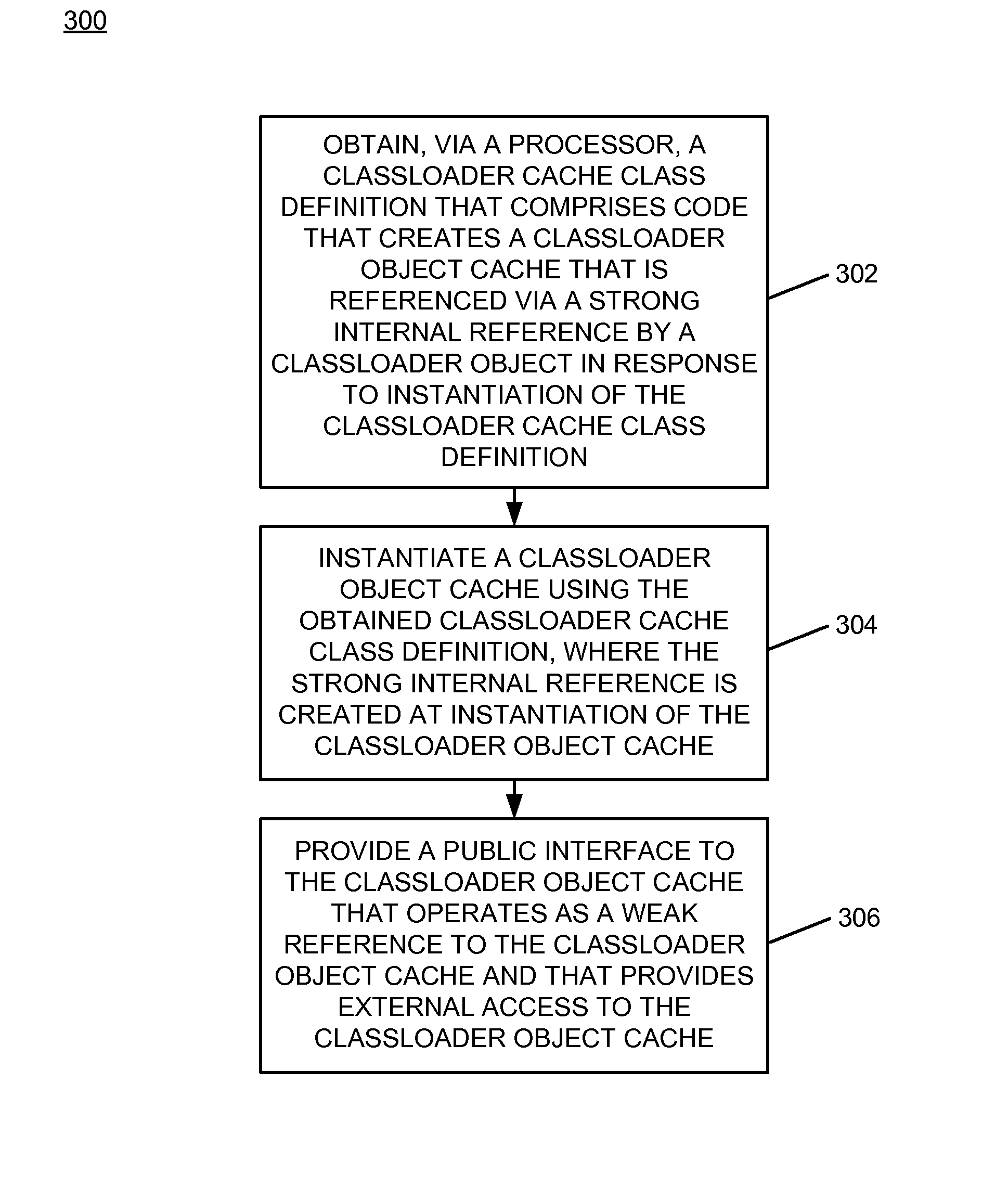
A classloader cache class definition is obtained by a processor. The classloader cache class definition includes code that creates a classloader object cache that is referenced by a strong internal reference by a classloader object in response to instantiation of the classloader cache class definition. A classloader object cache is instantiated using the obtained classloader cache class definition. The strong internal reference is created at instantiation of the classloader object cache. A public interface to the classloader object cache is provided. The public interface to the classloader object cache operates as a weak reference to the classloader object cache and provides external access to the classloader object cache.
Owner:IBM CORP
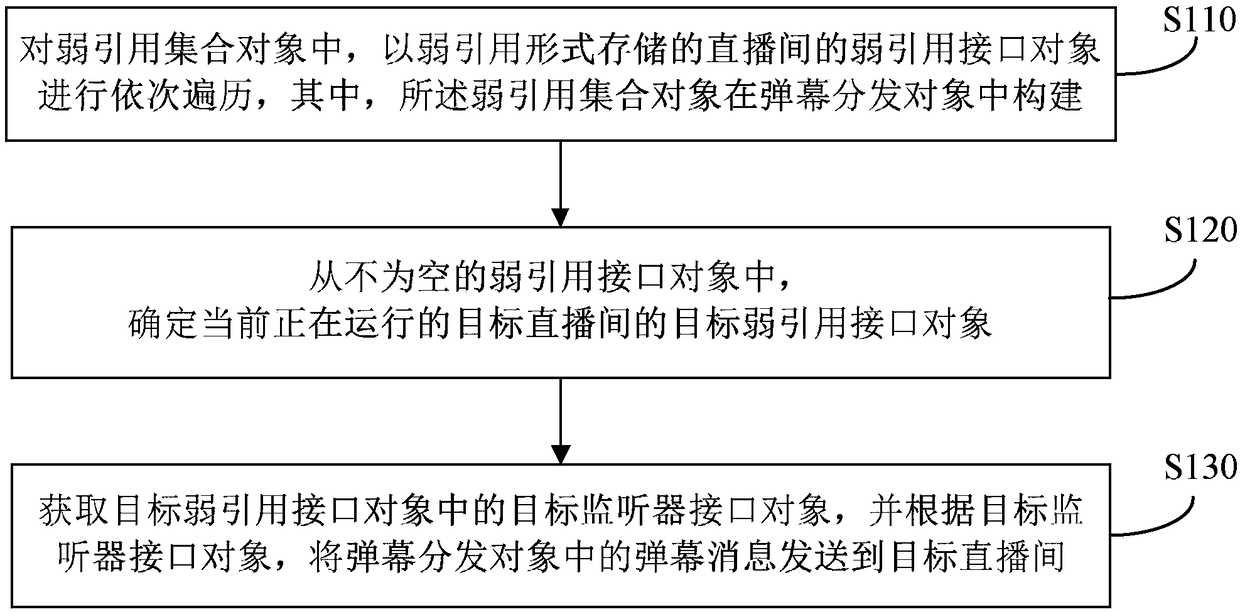
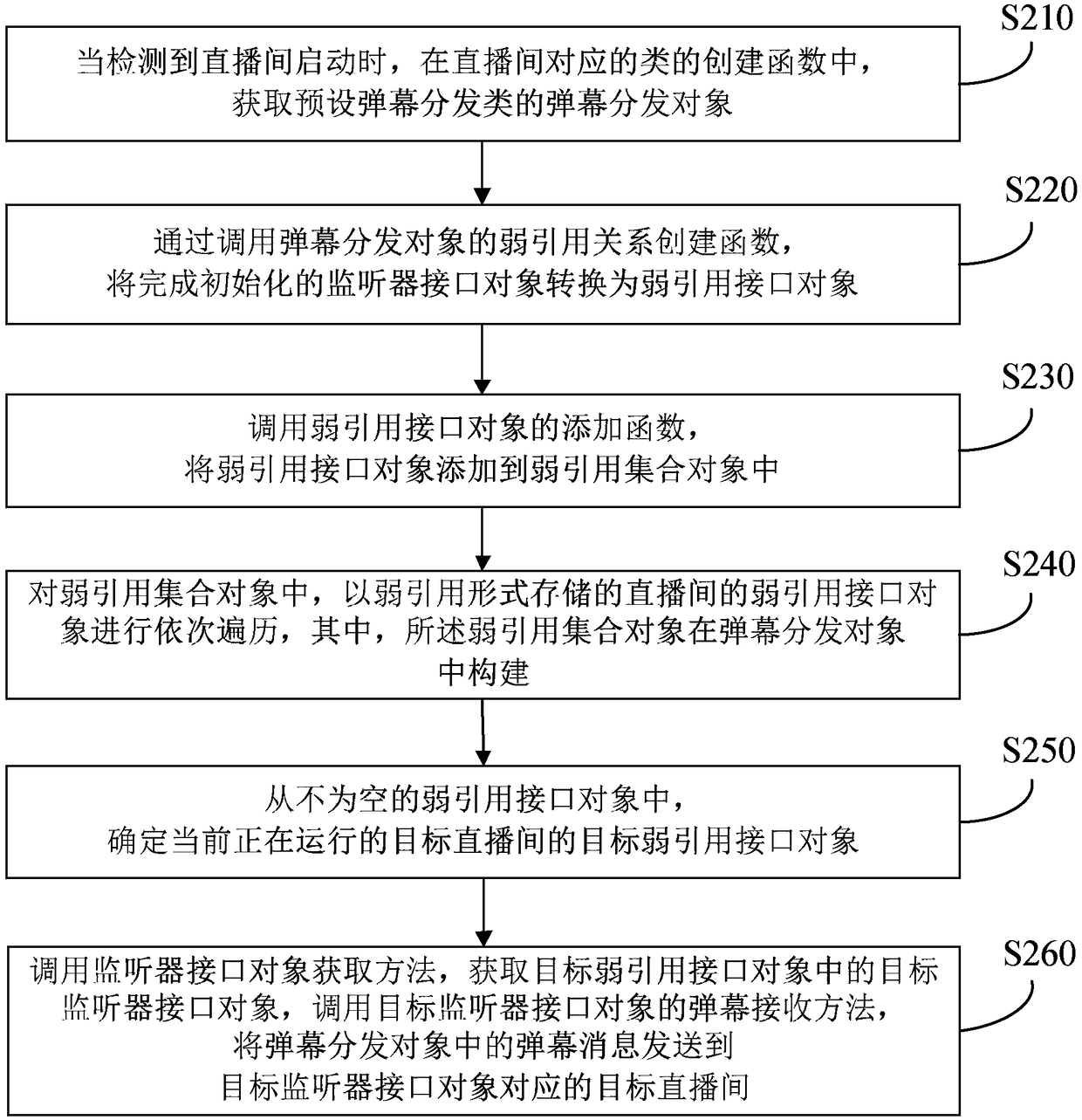
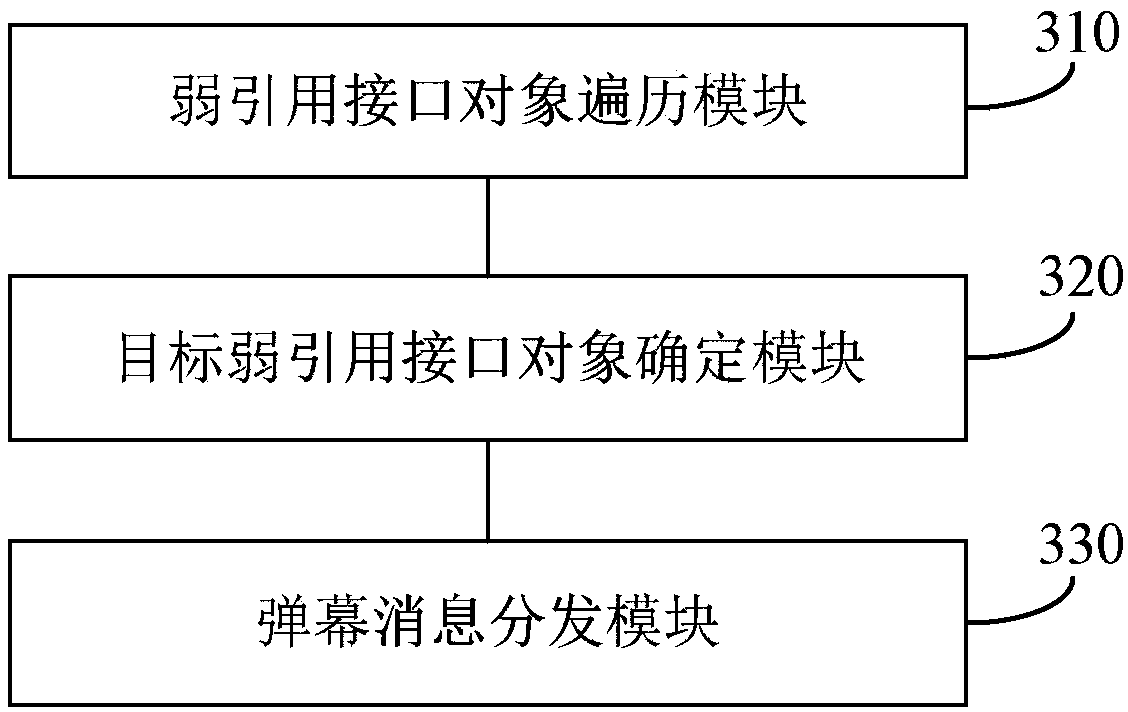
Method and apparatus for distributing bullet screen message, terminal and storage medium
ActiveCN109302639ASolve the problem of memory leakSelective content distributionComputer hardwareObject store
Owner:WUHAN DOUYU NETWORK TECH CO LTD
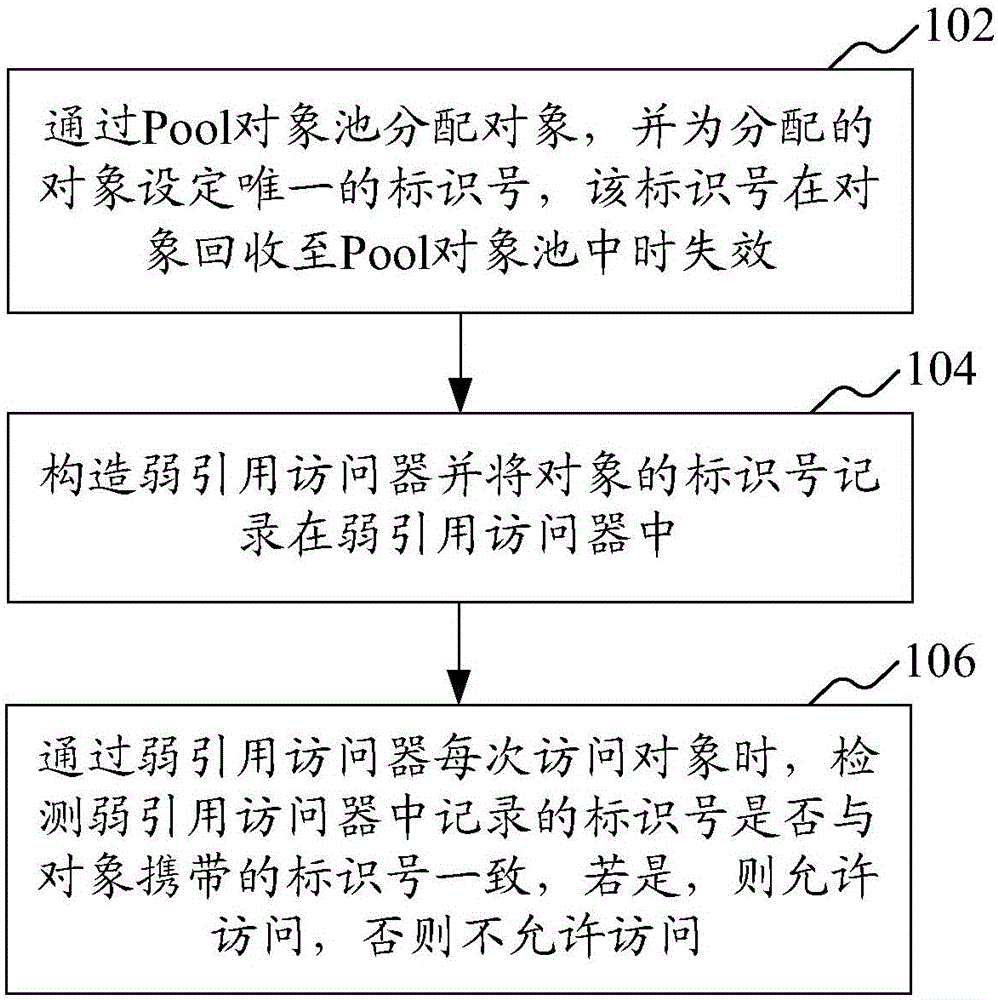
Weak reference implementation method and device oriented to Pool object
ActiveCN106020822AImplement weak reference mechanismProgramming languages/paradigmsSoftware designPattern recognitionDistributed object
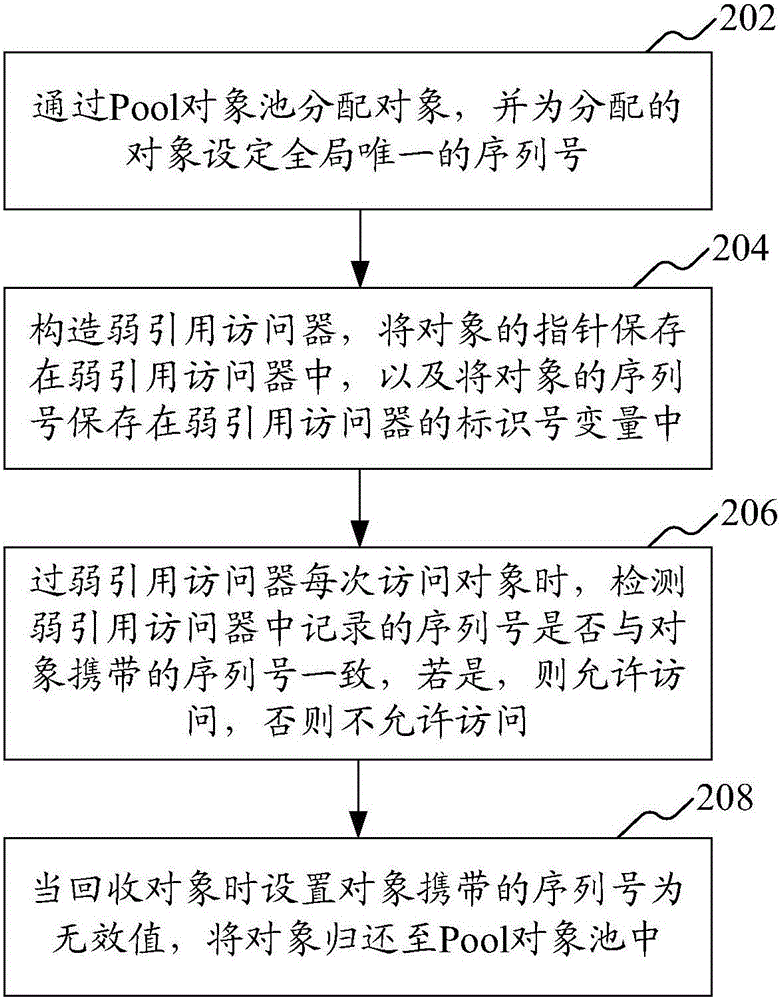
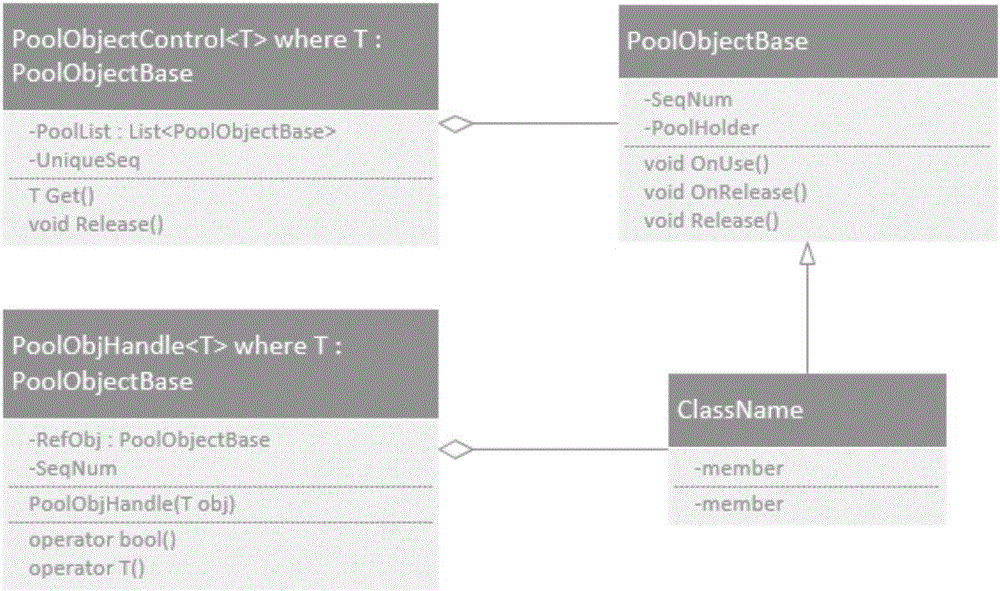
The invention relates to a weak reference implementation method oriented to a Pool object. The method comprises the following steps: through a Pool object pool, distributing an object, and setting a unique identification number for the distributed object, wherein the identification number fails when the object is recovered to the Pool object pool; constructing a weak reference accessor, and recording the identification number of the object in the weak reference accessor; and when the object is accessed by the weak reference accessor each time, detecting whether the identification number recorded in the weak reference accessor is consistent with the identification number carried by the object, permitting to access if the weak reference accessor is consistent with the identification number carried by the object, and otherwise, forbidding to access. The method can be adopted to realize a weak reference mechanism on the Pool object. In addition, the invention also provides a weak reference implementation device oriented to the Pool object.
Owner:TENCENT TECH CHENGDU
Prevention of classloader memory leaks in multitier enterprise applications
InactiveUS9229743B2Memory adressing/allocation/relocationSoftware metricsPublic interfaceParallel computing
A classloader cache class definition is obtained by a processor. The classloader cache class definition includes code that creates a classloader object cache that is referenced by a strong internal reference by a classloader object in response to instantiation of the classloader cache class definition. A classloader object cache is instantiated using the obtained classloader cache class definition. The strong internal reference is created at instantiation of the classloader object cache. A public interface to the classloader object cache is provided. The public interface to the classloader object cache operates as a weak reference to the classloader object cache and provides external access to the classloader object cache.
Owner:INT BUSINESS MASCH CORP
Image based repeated data deletion method and apparatus
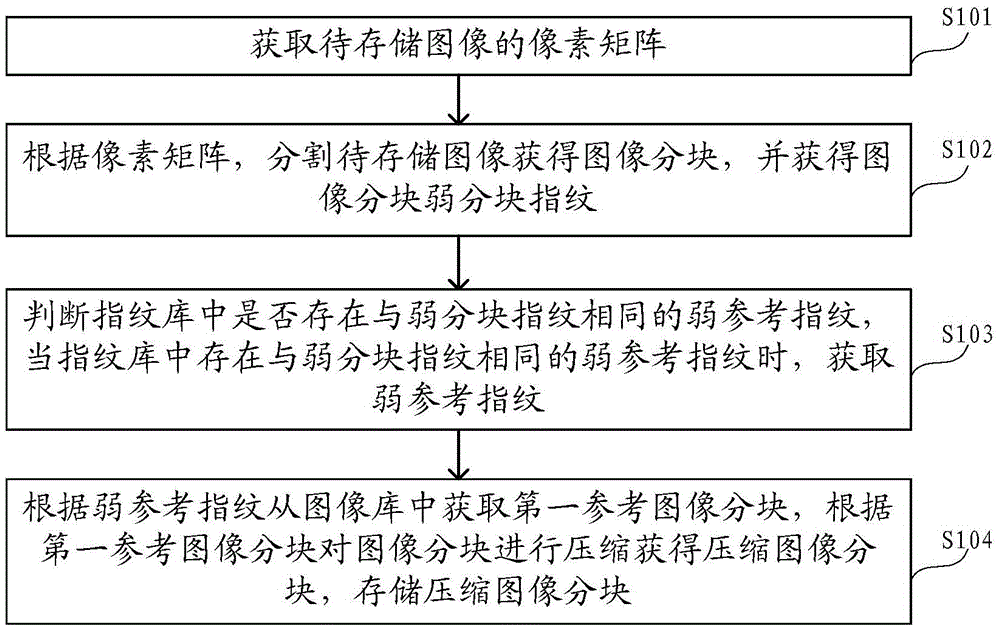
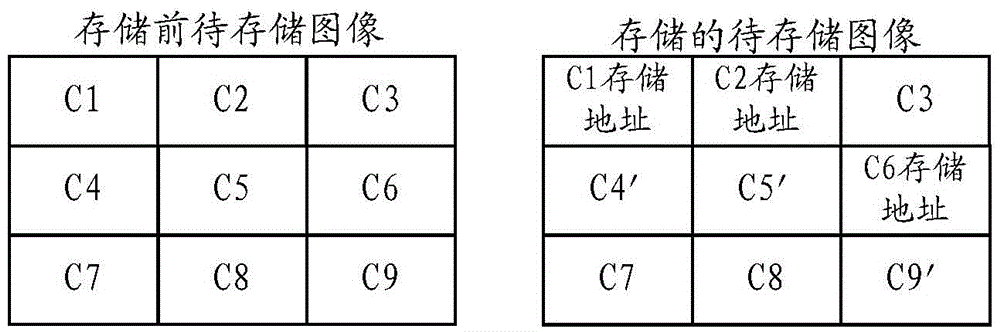
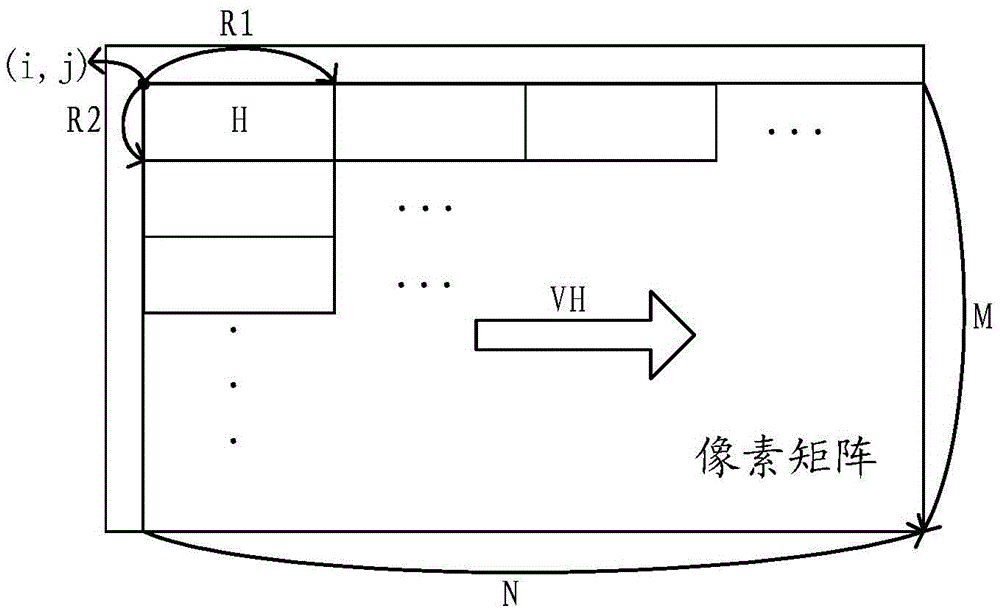
InactiveCN105550352AIncrease reduction ratioReduce storageImage analysisStill image data indexingPattern recognitionReference image
The invention relates to an image based repeated data deletion method and apparatus. The method provided by an embodiment of the invention comprises the steps of obtaining a pixel matrix of a to-be-stored image; according to the pixel matrix, segmenting the to-be-stored image to obtain image blocks, and obtaining weak block fingerprints of the image blocks; judging whether weak reference fingerprints as same as the weak block fingerprints exist in a fingerprint library or not, and when the weak reference fingerprints as same as the weak block fingerprints exist in the fingerprint library, obtaining the weak reference fingerprints; according to the weak reference fingerprints, obtaining first reference image blocks from an image library; according to the first reference image blocks, compressing the image blocks to obtain compressed image blocks, and storing the compressed image blocks; and when the weak reference fingerprints as same as the weak block fingerprints do not exist in the fingerprint library, storing the weak block fingerprints as new weak reference fingerprints in the fingerprint library, and storing the image blocks in the image library. According to the image based repeated data deletion method and apparatus provided by the invention, the deletion rate of repeated data of the image is increased, the reduction ratio of the image is increased, and the storage, transmission and processing speeds of the image are increased.
Owner:HUAWEI TECH CO LTD
Prevention of classloader memory leaks in multitier enterprise applications
InactiveUS20130080707A1Improves classloader related memory issueAlleviates code developer burdenMemory adressing/allocation/relocationSoftware metricsEngineeringWeak reference
A classloader cache class definition is obtained by a processor. The classloader cache class definition includes code that creates a classloader object cache that is referenced by a strong internal reference by a classloader object in response to instantiation of the classloader cache class definition. A classloader object cache is instantiated using the obtained classloader cache class definition. The strong internal reference is created at instantiation of the classloader object cache. A public interface to the classloader object cache is provided. The public interface to the classloader object cache operates as a weak reference to the classloader object cache and provides external access to the classloader object cache.
Owner:IBM CORP
Method and system to space-efficiently track memory access of object-oriented language in presence of garbage collection
InactiveUS8326894B2Reduce storage overheadReduce memory overheadError detection/correctionSpecial data processing applicationsProcess memoryObject based
The present invention provides a method and system for processing memory access events. The method comprises: executing an extended program including instrumented memory tracking code for tracking memory access events of a plurality of objects; allocating a unique identifier for each of the plurality of tracked objects; creating a weak reference for each of the plurality of tracked objects, wherein a mapping relationship is established between the identifier of the weak reference and that of the corresponding tracked object; recording and storing the memory access events of the plurality of tracked objects; in response to receiving a notification of memory garbage collection which includes an identifier of a weak reference of a collected object, determining the identifier of the collected object based on the mapping relationship between the identifier of the weak reference and that of the corresponding tracked object, and searching the stored memory access events for the memory access events of the collected object; and deleting the memory access events of the collected object. The storage overhead may be reduced according to the above method of the present invention.
Owner:INT BUSINESS MASCH CORP
Managing snapshotting of a dataset using an ordered set of b+ trees
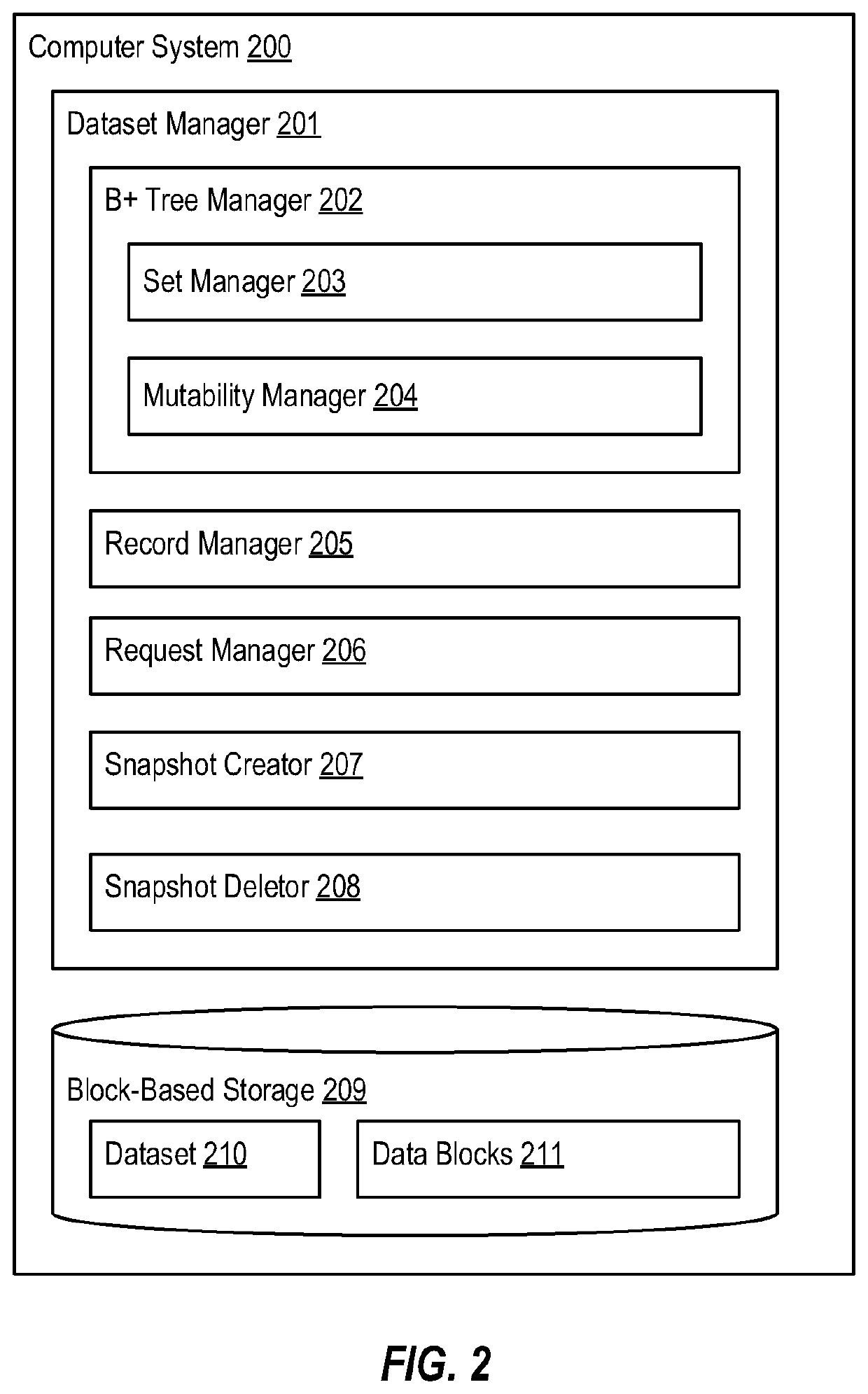
ActiveUS20210349850A1Improve performanceSemi-structured data mapping/conversionFile system administrationData setAlgorithm
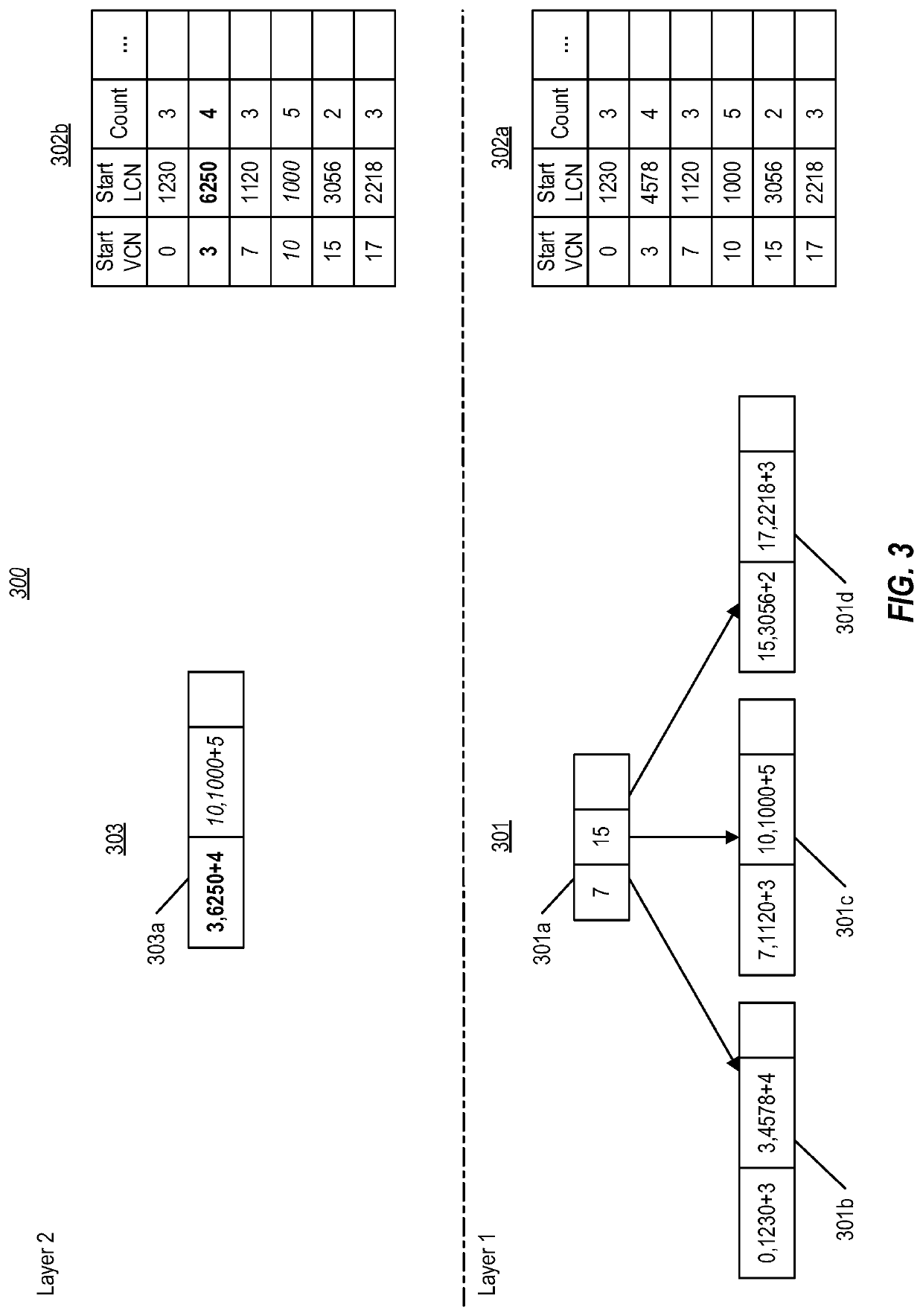
A current state of a dataset is represented by a mutable B+ tree, while each snapshot of the dataset is represented by an immutable B+ tree. An ordering of B+ trees in the ordered set logically arranges those B+ trees into layers, with the mutable B+ tree representing the current state of the dataset being logically arranged as an upper layer, and with immutable B+ trees representing snapshots of the dataset being progressively arranged as lower layers with the oldest snapshot being a lowest layer. Each B+ tree stores dataset records with a strong or a weak reference state; strong records are independent of any lower-layer record, while weak records are dependent on at least one lower-layer record. A snapshot deletion includes merging the snapshot's corresponding B+ tree with its highest neighbor B+ tree, including merging overlapping records based on their weak vs. strong reference state.
Owner:MICROSOFT TECH LICENSING LLC
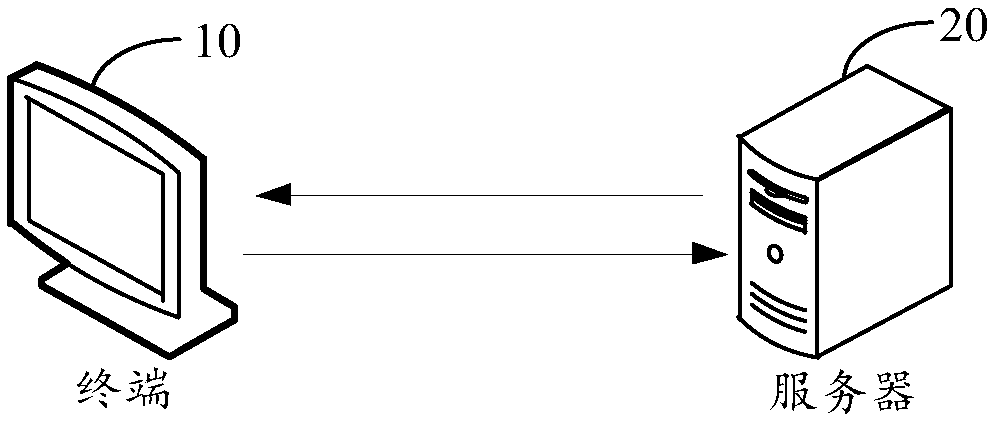
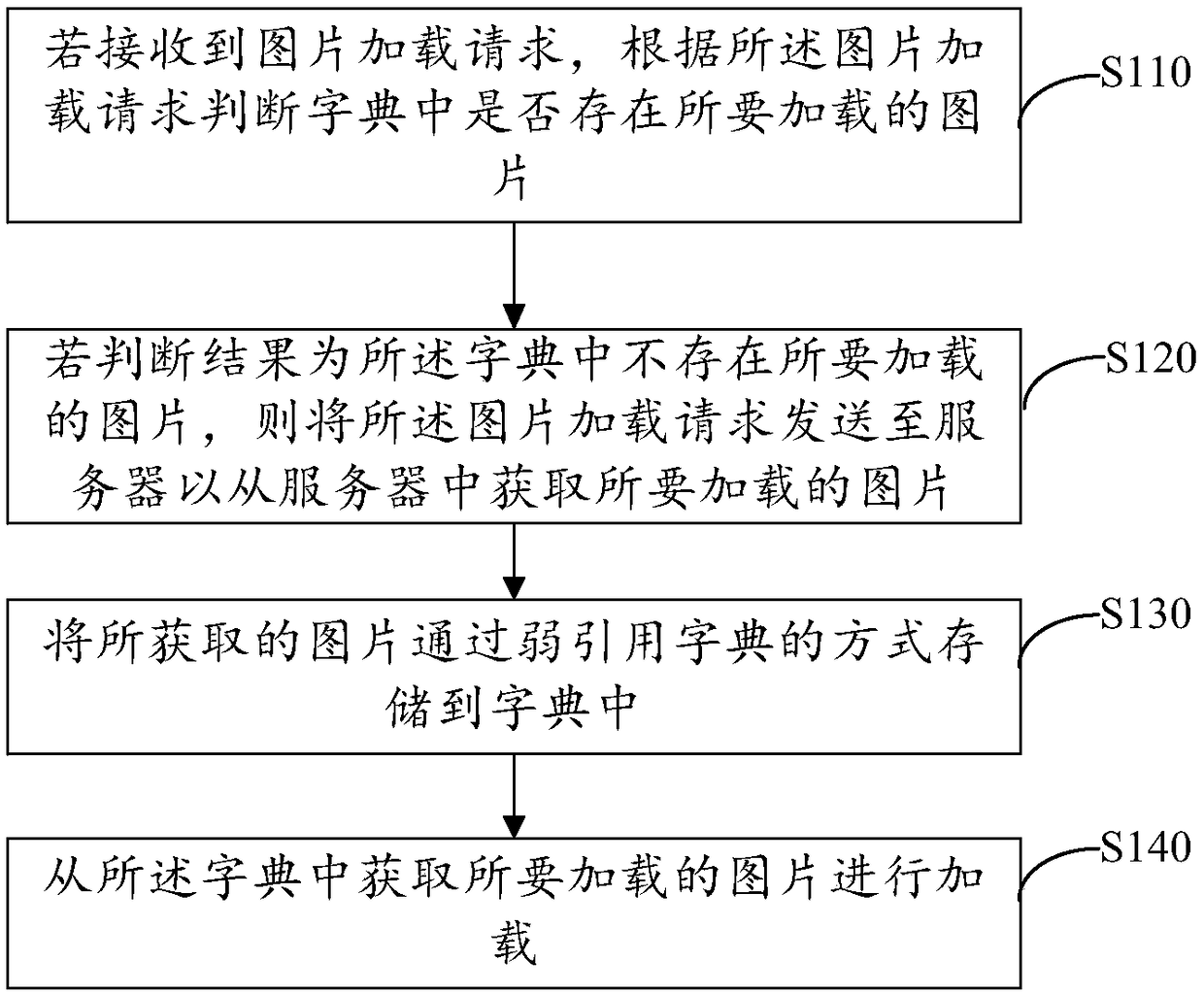
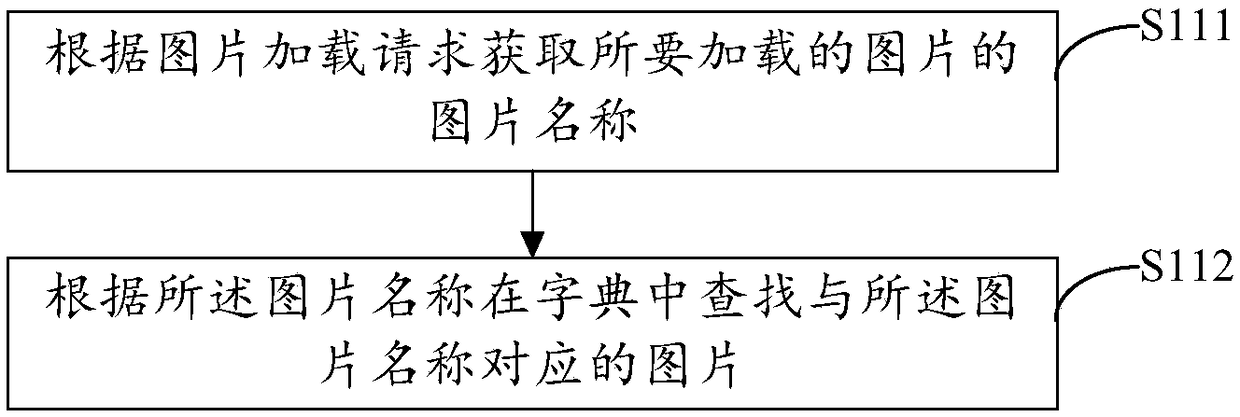
Picture loading method, device, computer device, and storage medium
PendingCN109388459ASave memoryResource allocationExecution for user interfacesComputer engineeringWeak reference
The embodiment of the invention discloses a picture loading method, a device, a computer device and a storage medium. The method comprises the following steps: if a picture loading request is received, judging whether a picture to be loaded exists in a dictionary according to the picture loading request; If it is judged that there is no picture to be loaded in the dictionary, sending the picture loading request to the server to obtain the picture to be loaded from the server; The obtained picture is stored in the dictionary by weak reference dictionary. A picture to be loaded is obtained fromthe dictionary for loading. By implementing the method of the embodiment of the present invention, it is possible to obtain pictures in the cache without repeatedly loading the pictures, and the pictures can be destroyed so as to save memory.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
System and method for solving memory leak in proxy mode
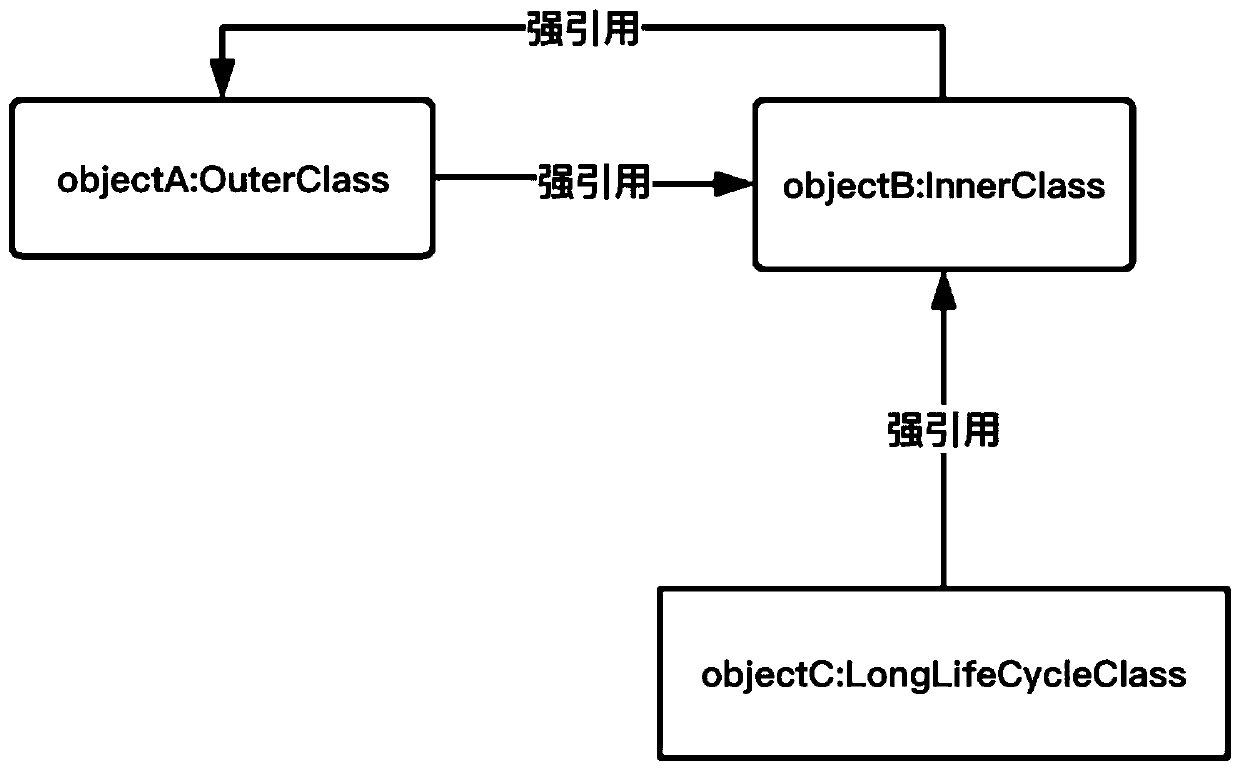
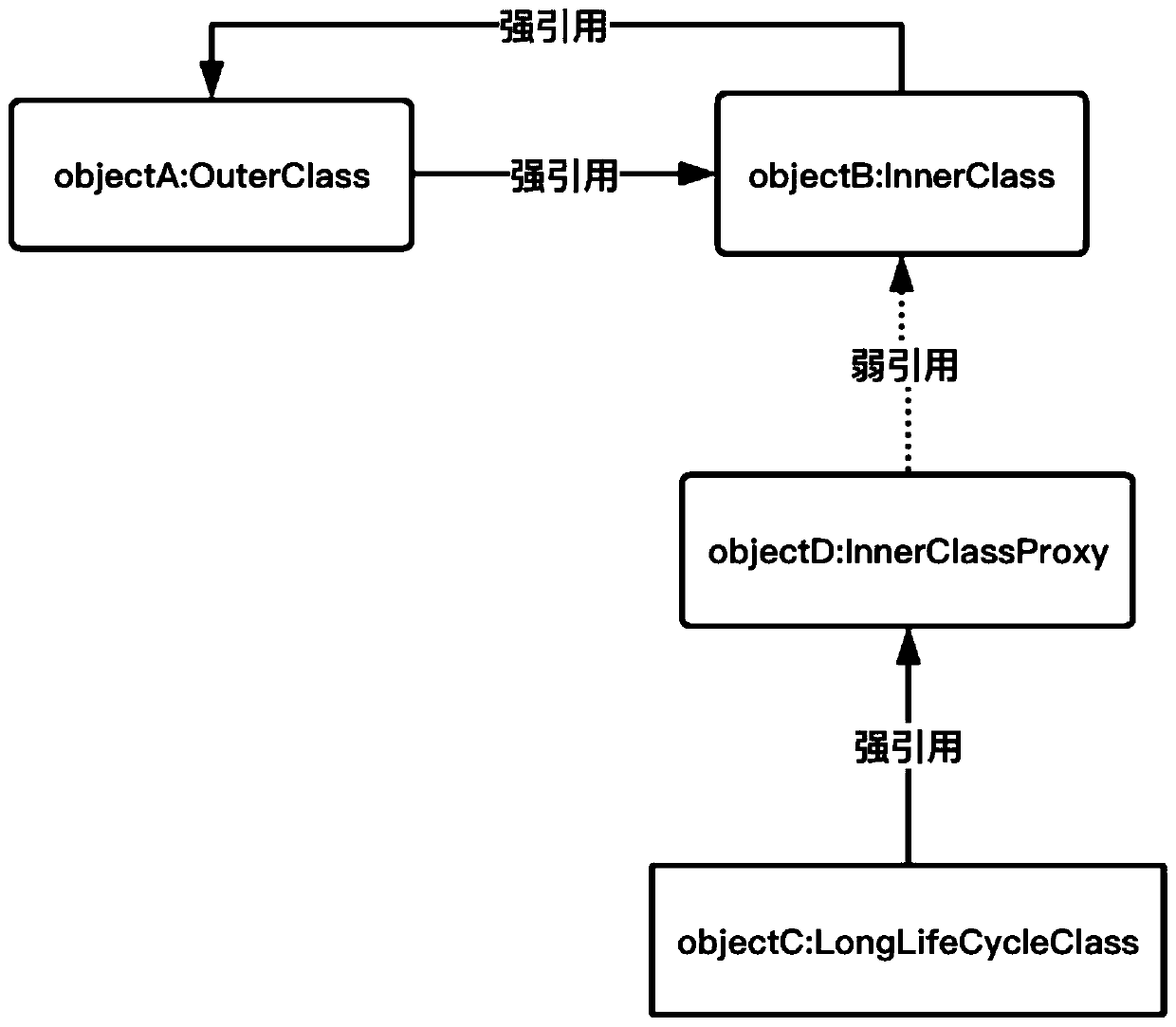
ActiveCN110457152AWriting Convenience PreservesBreak strong citationsNon-redundant fault processingStrong referenceSimulation
The invention discloses a system and method for solving memory leak by using an agent mode, and the system comprises a judgment module which is used for judging two non-static internal classes with astrong reference relation, wherein at least one non-static internal class is a non-static internal class with a long life cycle; an agent module is used for inserting an agent non-static internal class between the two non-static internal classes; a strong reference setting module used for setting a strong reference relationship between a non-static internal class and an agent non-static internalclass with a long life cycle; and a weak reference setting module used for setting a weak reference relationship between the agent non-static internal class and the other non-static internal class except the non-static internal class with the long life cycle. The mutual strong reference of the external class and the internal class is relieved by utilizing the agent mode and the weak reference object, so that the writing convenience of the non-static internal class is kept.
Owner:贵阳语玩科技有限公司
Query access method, apparatus and system based on CIM model
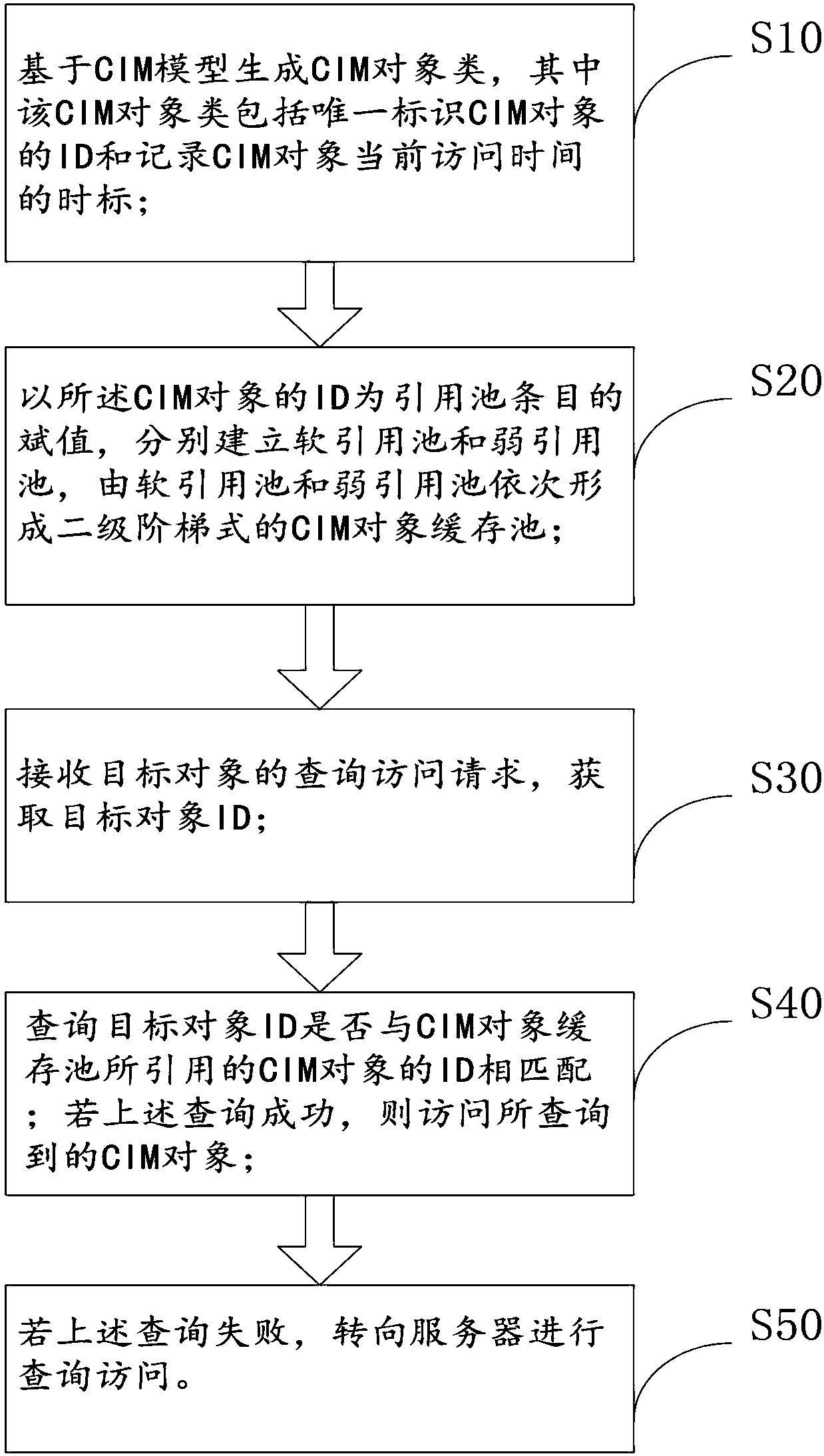
ActiveCN107908470ASolve dynamic cache data transmissionSolve processingResource allocationSoftware simulation/interpretation/emulationObject ClassTimestamp
The present invention discloses a query access method, apparatus and system based on a CIM model, and belongs to the technical field of data transmission. The method comprises: generating a CIM objectclass based on a CIM model, wherein the CIM object class comprises an ID that uniquely identifies the CIM object and a timestamp that records the current access time of the CIM object, and the ID ofthe CIM object is the value of a reference pool entry; creating a two-level ladder-type CIM object cache pool formed by a soft reference pool and a weak reference pool; receiving a query access request of a target object, and obtaining the target object ID; querying whether the ID of the target object is matched with the ID of the CIM object referenced by the CIM object cache pool; if the query issuccessful, accessing the queried CIM object; and if the query fails, returning to a server for query access. According to the technical scheme of the present invention, problems of excessive interaction with the server due to short-term frequent access to the CIM object and garbage collection failing to release the referenced CIM object are solved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com