Application program accessing method and device
An application and user technology, applied in the field of information security, can solve problems such as malicious acquisition of user information, and achieve the effect of preventing malicious access to applications and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
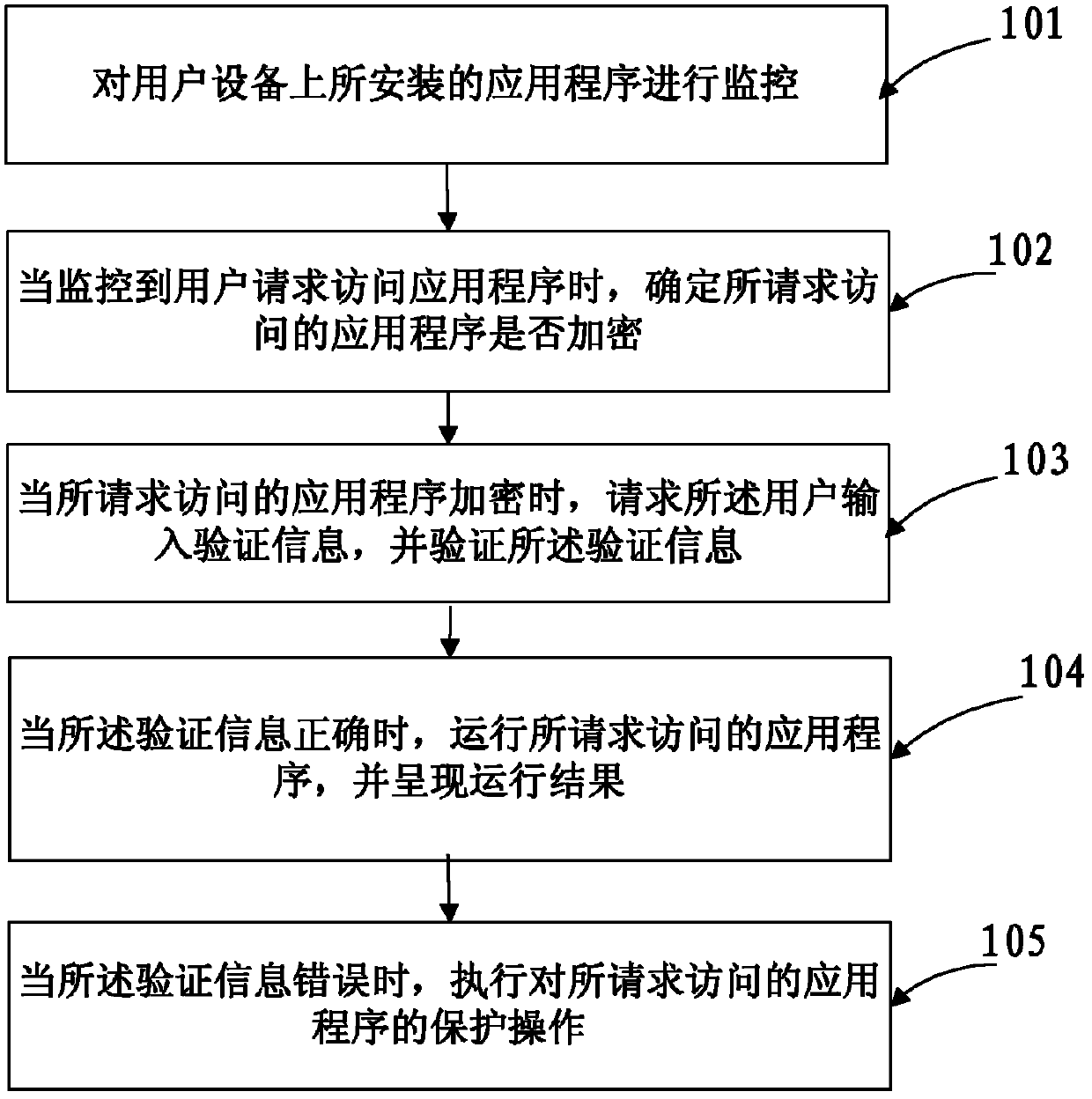
[0048] see figure 1 , a method of accessing an application that includes:
[0049] Step 101: Monitor the application programs installed on the user equipment;
[0050] Step 102: When it is monitored that the user requests to access the application program, determine whether the requested application program is encrypted;
[0051] Step 103: When the requested application is encrypted, request the user to input verification information, and verify whether the verification information is correct;
[0052] Step 104: When the verification information is correct, run the requested application program and present the running result;
[0053] Step 105: When the verification information is incorrect, perform a protection operation on the application program requested for access.
[0054] The beneficial effect brought by the technical solution provided by the embodiment of the present invention is: when the user requests to access the application program, verify the verification info...
Embodiment 2
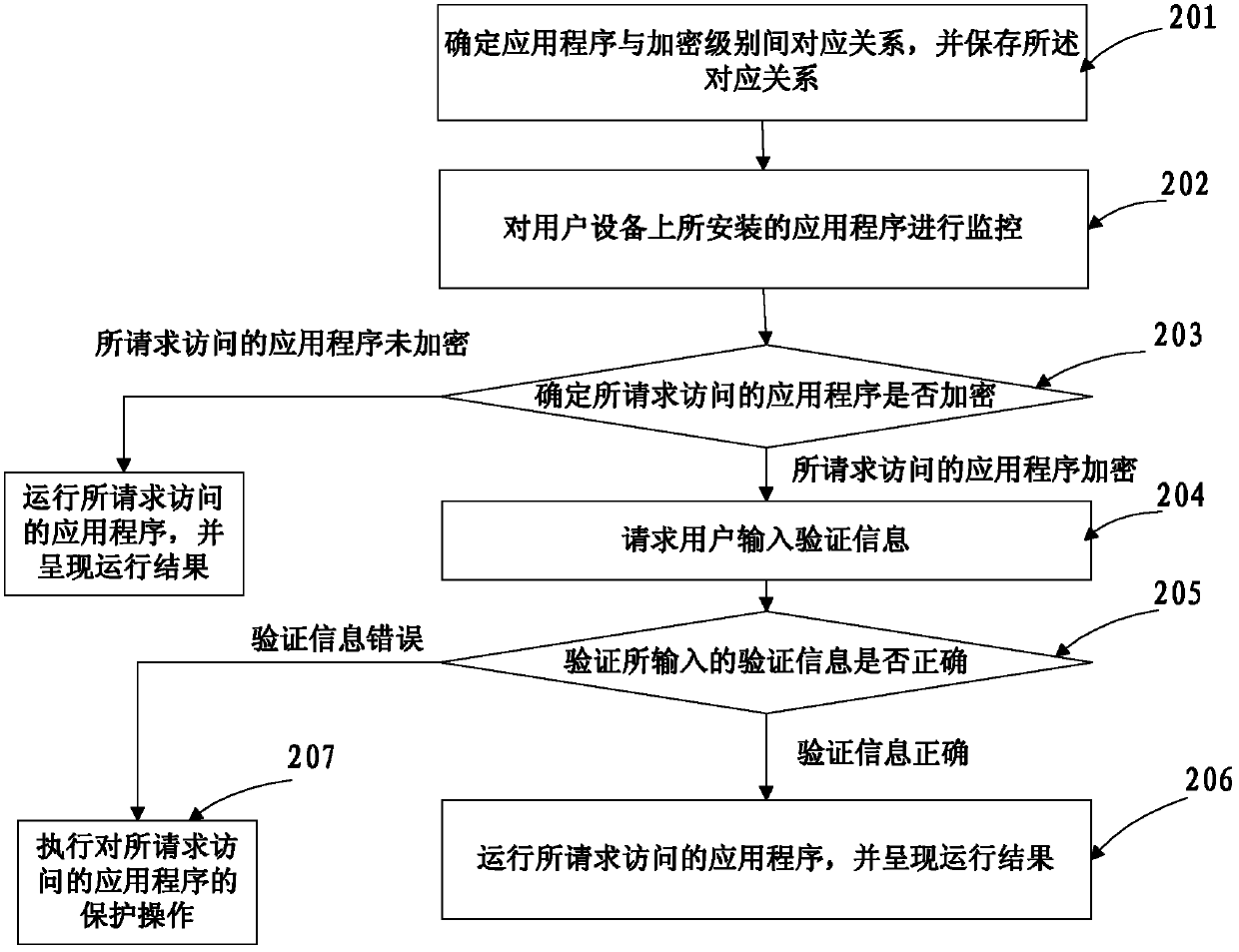
[0056] see figure 2 , a method for accessing an application program, the execution subject of the method is a user device, further, the method may be implemented by a client application program (such as a program lock) installed on the user device, wherein the user device may include But not limited to mobile phones, tablet computers or PDA (Personal Digital Assistant, personal digital assistant) and other devices, specifically include the following:
[0057] Step 201: Determine the corresponding relationship between the application program and the encryption level, and save the corresponding relationship, wherein the encryption level is used to indicate whether the application program is encrypted, which may specifically include: unencrypted, encrypted, hidden, or encrypted and hidden;
[0058]When this step is specifically implemented, it may include:
[0059] Receive a request from the user to access the program lock, wherein the program lock is used to manage the applica...
Embodiment 3
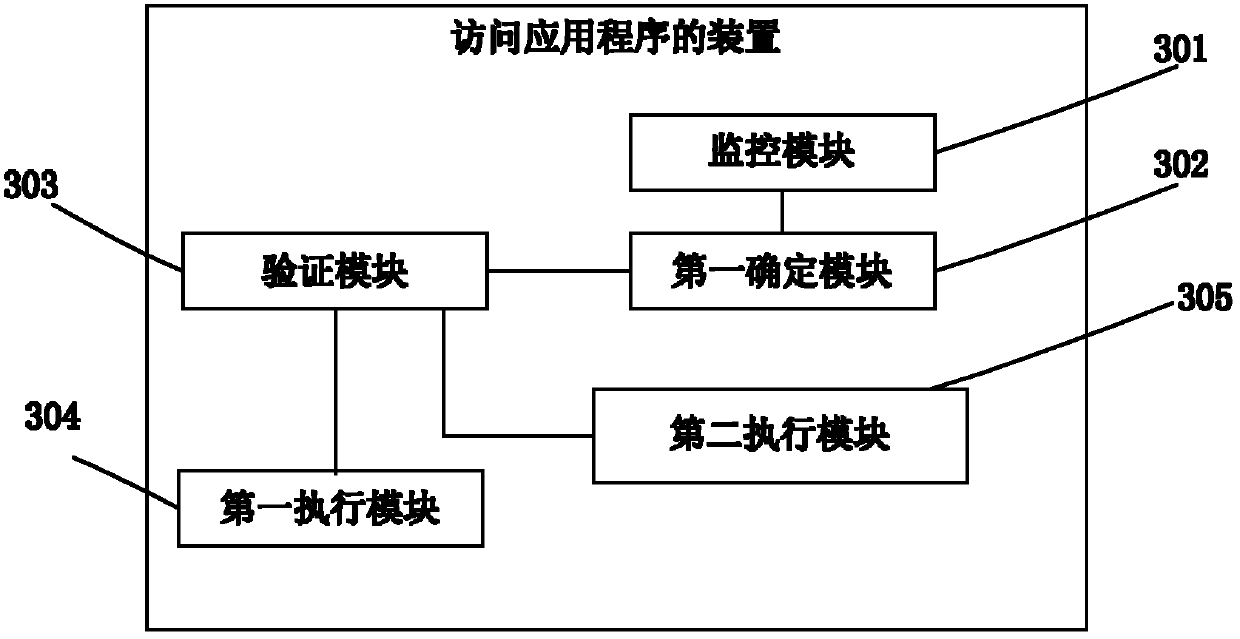
[0093] see image 3 , an apparatus for accessing an application program, comprising: a monitoring module 301, a first determination module 302, a verification module 303, a first execution module 304, and a second execution module 305;
[0094] A monitoring module 301, configured to monitor the application programs installed on the user equipment;
[0095] The first determination module 302 is configured to determine whether the requested application program is encrypted when monitoring the user's request for access to the application program;
[0096] A verification module 303, configured to request the user to input verification information when the requested application program is encrypted, and verify whether the verification information is correct;
[0097] The first executing module 304 is configured to run the requested application program and present the running result when the verification information is correct;
[0098] The second execution module 305 is configure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com