Soft isolation assembly for network access debugging and using method thereof
A technology for isolating components and network access. It is used in data exchange networks, electrical components, digital transmission systems, etc., and can solve unauthorized access by operation and maintenance personnel, network equipment isolation access monitoring and access control, computers carrying viruses or network attacks on running equipment. and other issues to ensure safe operation and avoid network attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
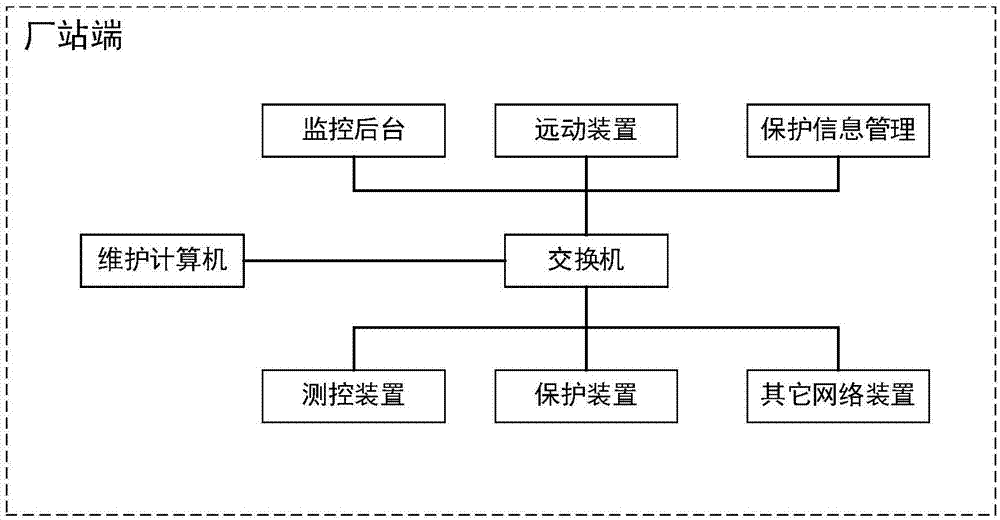
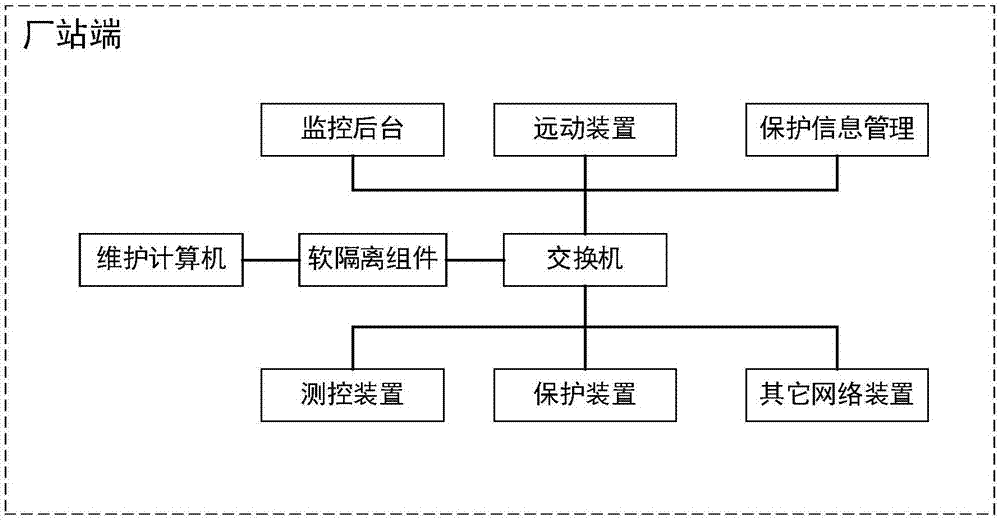
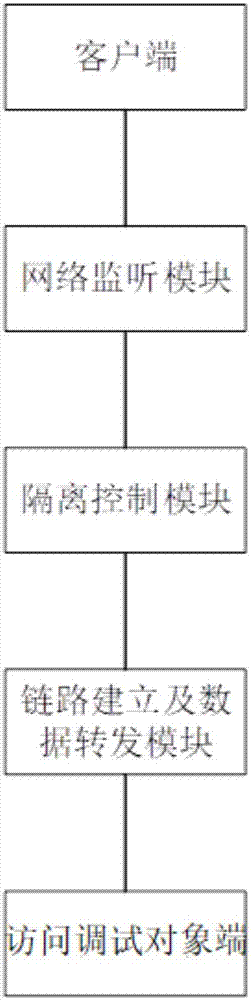
[0032] combine figure 2 and image 3 , the present invention provides a soft isolation component for network access debugging, including a client, a network monitoring module, an isolation control module, a link establishment and data forwarding module, and an access debugging object end; the client is connected to the network monitoring module; the network The monitoring module is connected with the isolation control module; the isolation control module is connected with the link establishment and data forwarding module; the link establishment and data forwarding module is connected with the access debugging object end.
[0033] The client is connected to the maintenance computer; the maintenance computer and the client establish a link to the soft isolation component; the maintenance computer provides the client with IP and debugging port information.
[0034] The invention provides a soft isolation method for network access debugging, comprising the following steps:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com