Method for resisting abnegation service aggression
A denial of service attack and server technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as connection interruption and gateway failure, and achieve the effect of improving access speed and system efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
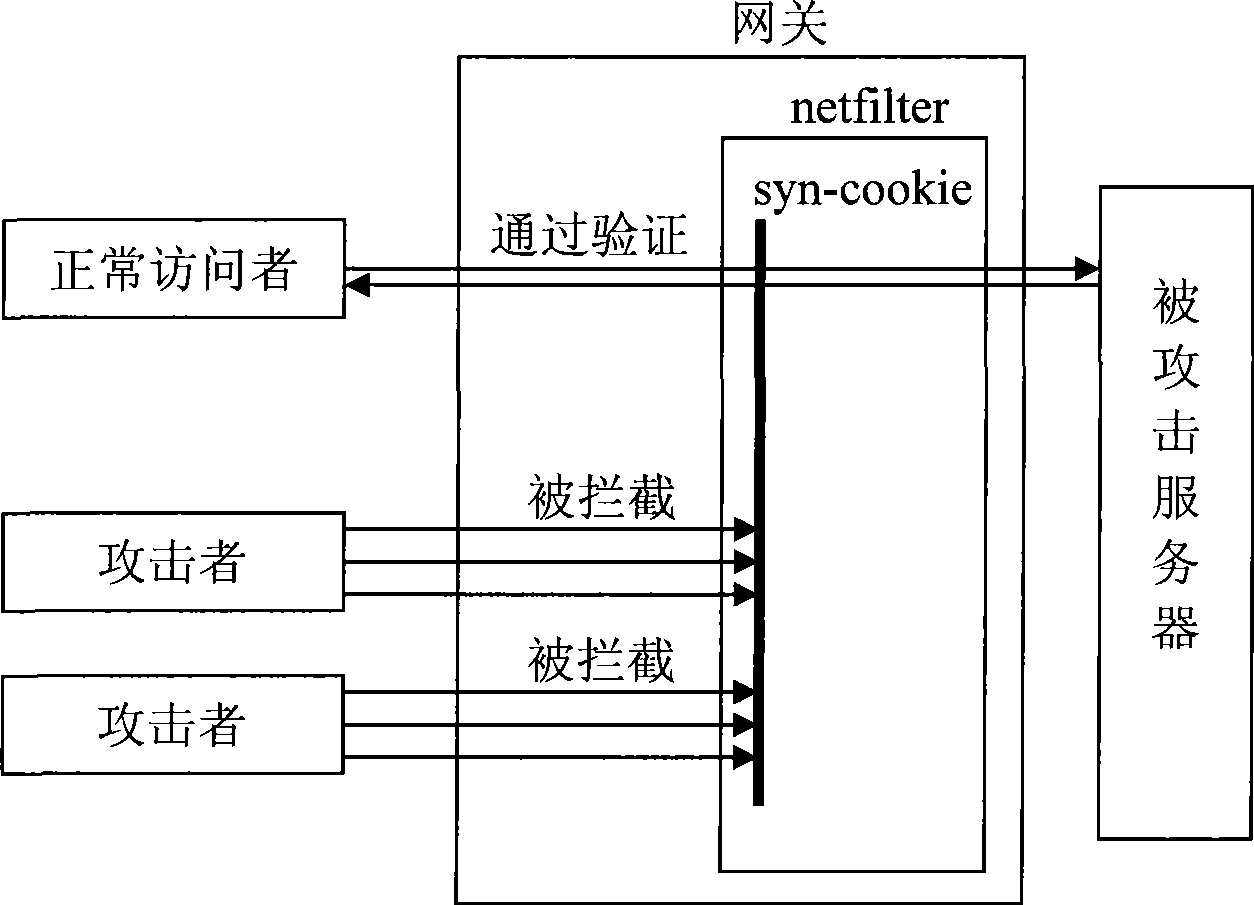
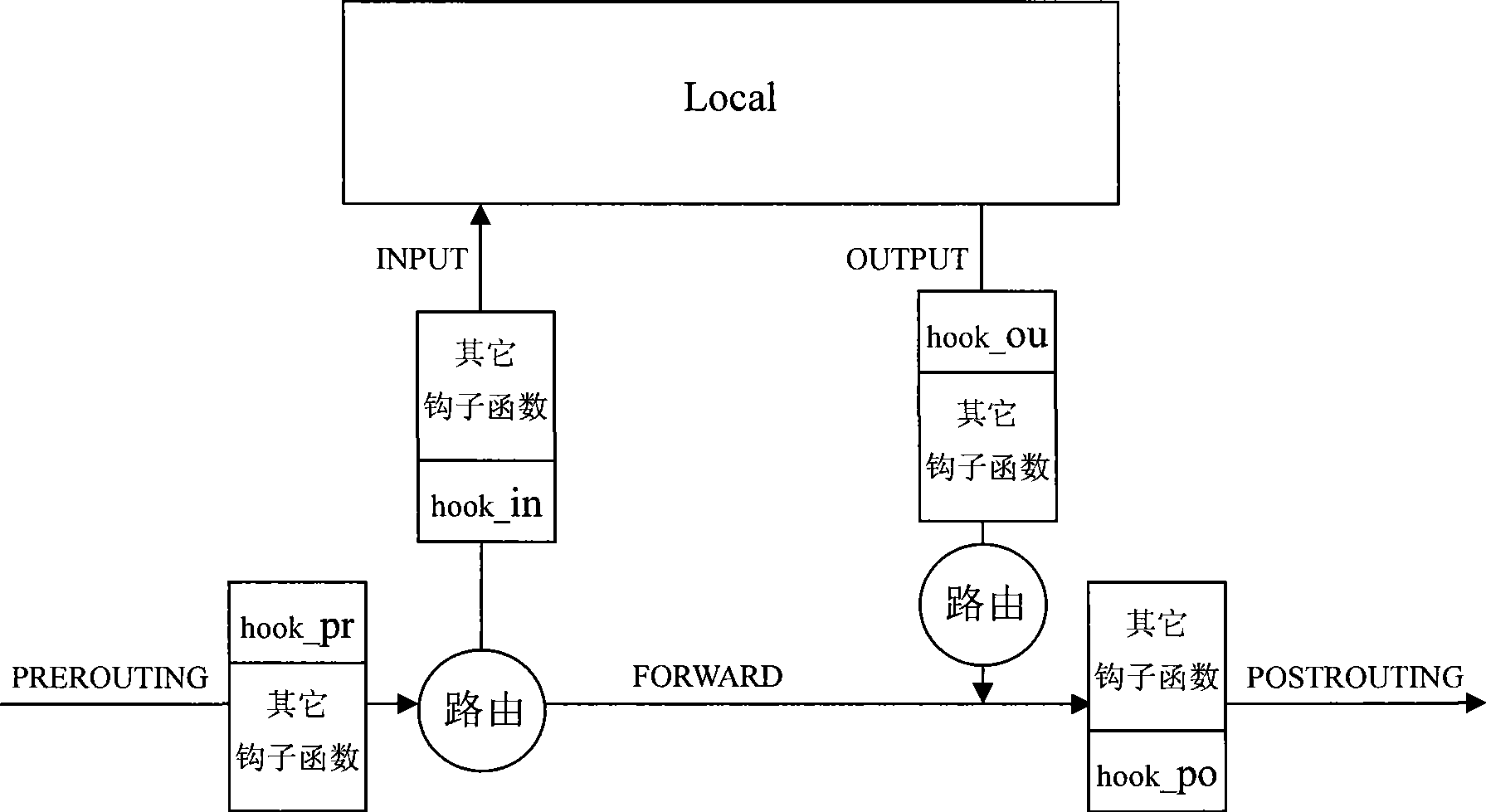
[0036] figure 1 Shows the configuration that realizes the method for resisting denial of service attack of the present invention, from figure 1 As can be seen in the figure, the present invention sets a device for resisting denial of service attack in the gateway, and uses the device to resist denial of service attack.
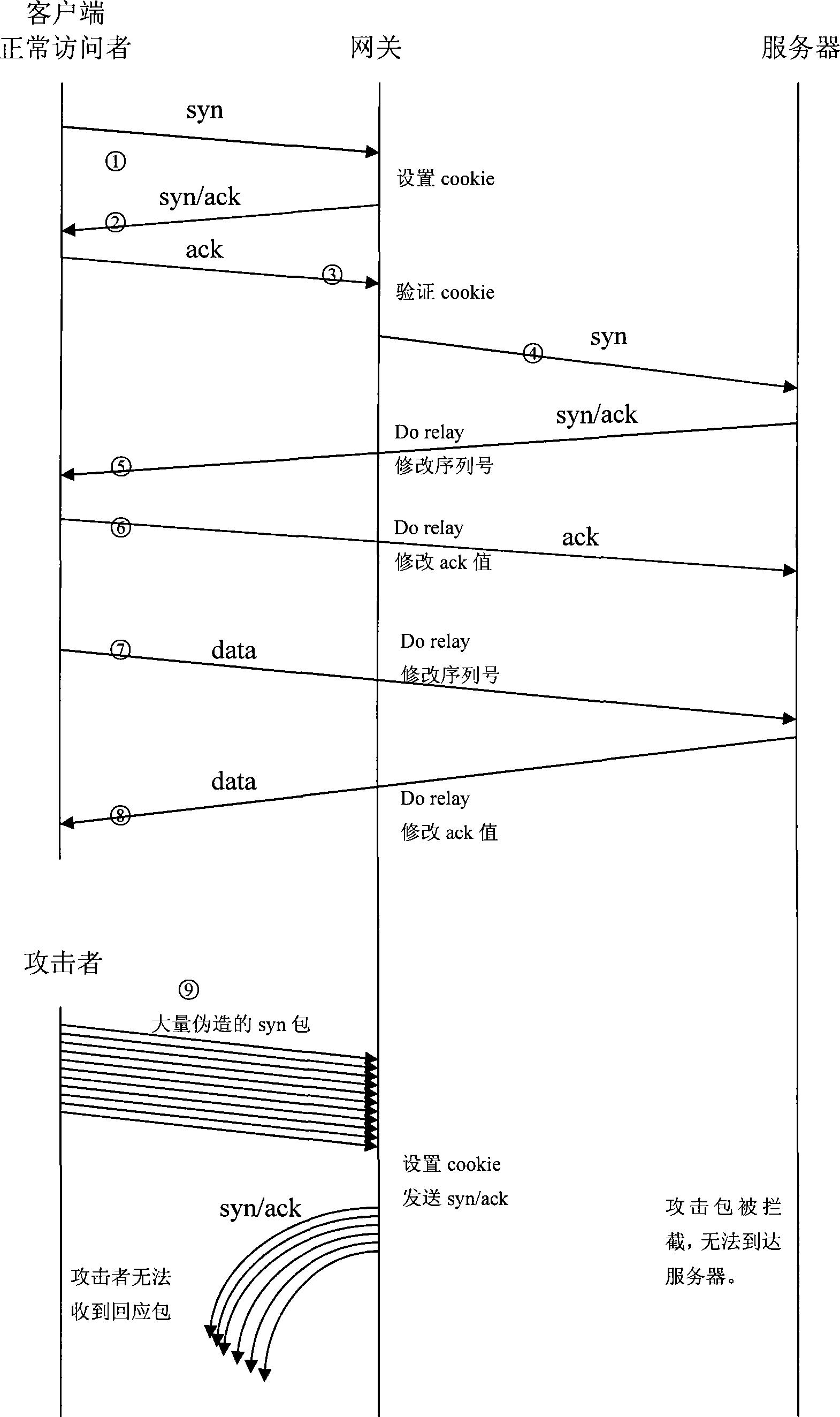
[0037] Such as image 3 As shown, the device of the denial of service attack resists the denial of service attack by performing the following steps:
[0038] (1) Intercept the syn connection request sent by the client that includes source IP, source port, destination IP, destination port, and TCP serial number;
[0039] (2) for the syn connection request, utilize a local key to generate a proxy TCP serial number x associated with the syn;
[0040] (3) return the syn / ack data packet that comprises proxy TCP serial number to client;
[0041] (4) receiving the ack data packet containing the serial number x+1 which is responded by the client after receiving th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com