Flood attack prevention method and device
A flooding attack and illegal technology, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problems of normal traffic packet discarding, exceeding, and the total amount of ARP packets sent
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] Such as Figure 5 As shown, this embodiment provides a method for preventing flooding attacks, including:
[0036] Step 501: Carry out CAR restrictions on packets sent from different IP addresses, and set CAR channels respectively.
[0037] In step 501, according to the rate range of the normal traffic packets sent by the same IP address, CAR restrictions are performed on the packets sent by each IP address, and the CAR channel is set. The threshold of the CAR channel limitation is set according to the rate range of normal traffic packets sent by the same IP address, so as to filter attack traffic packets exceeding the rate range of normal traffic packets. The rate range of normal traffic packets sent by the same IP address can be calculated according to specific application situations. Taking the ARP application as an example, for an IP address with a subnet mask of 255.255.255.0, up to 254 hosts can share one IP address. Since the length of a single ARP message is g...
Embodiment 2
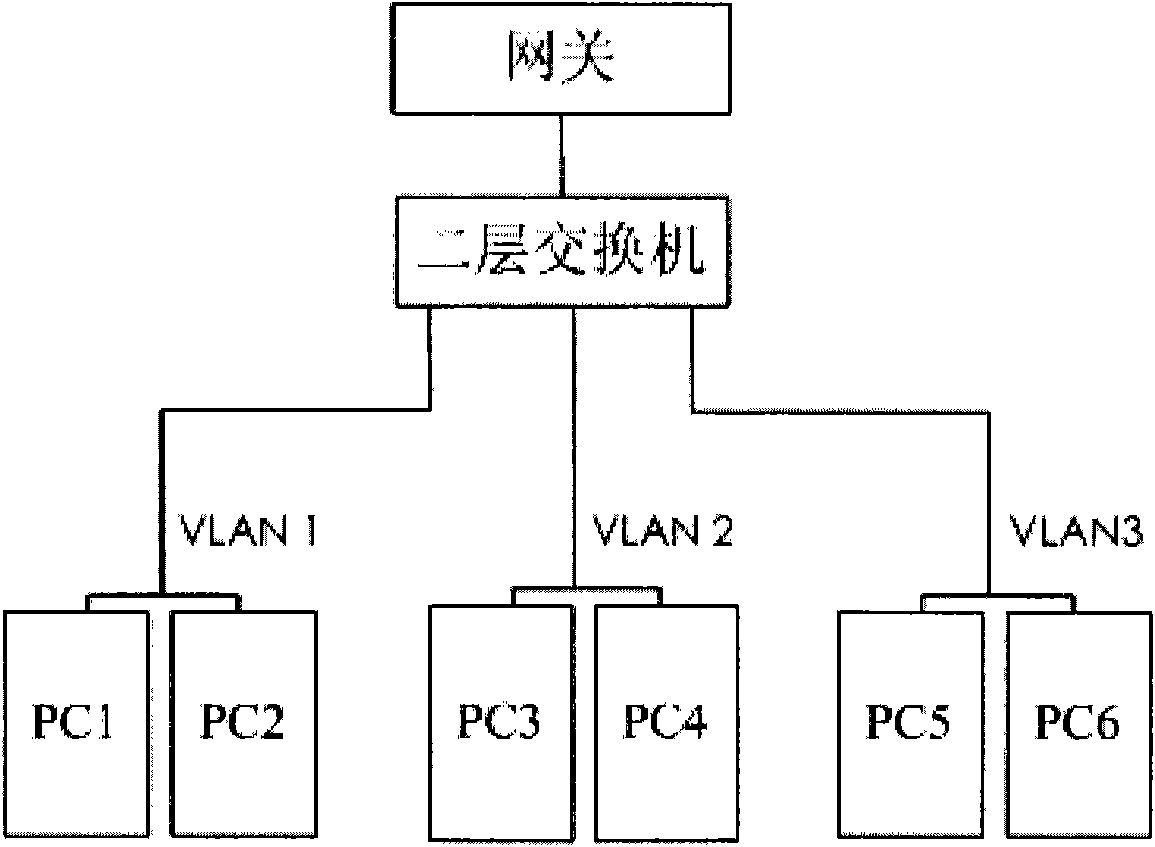
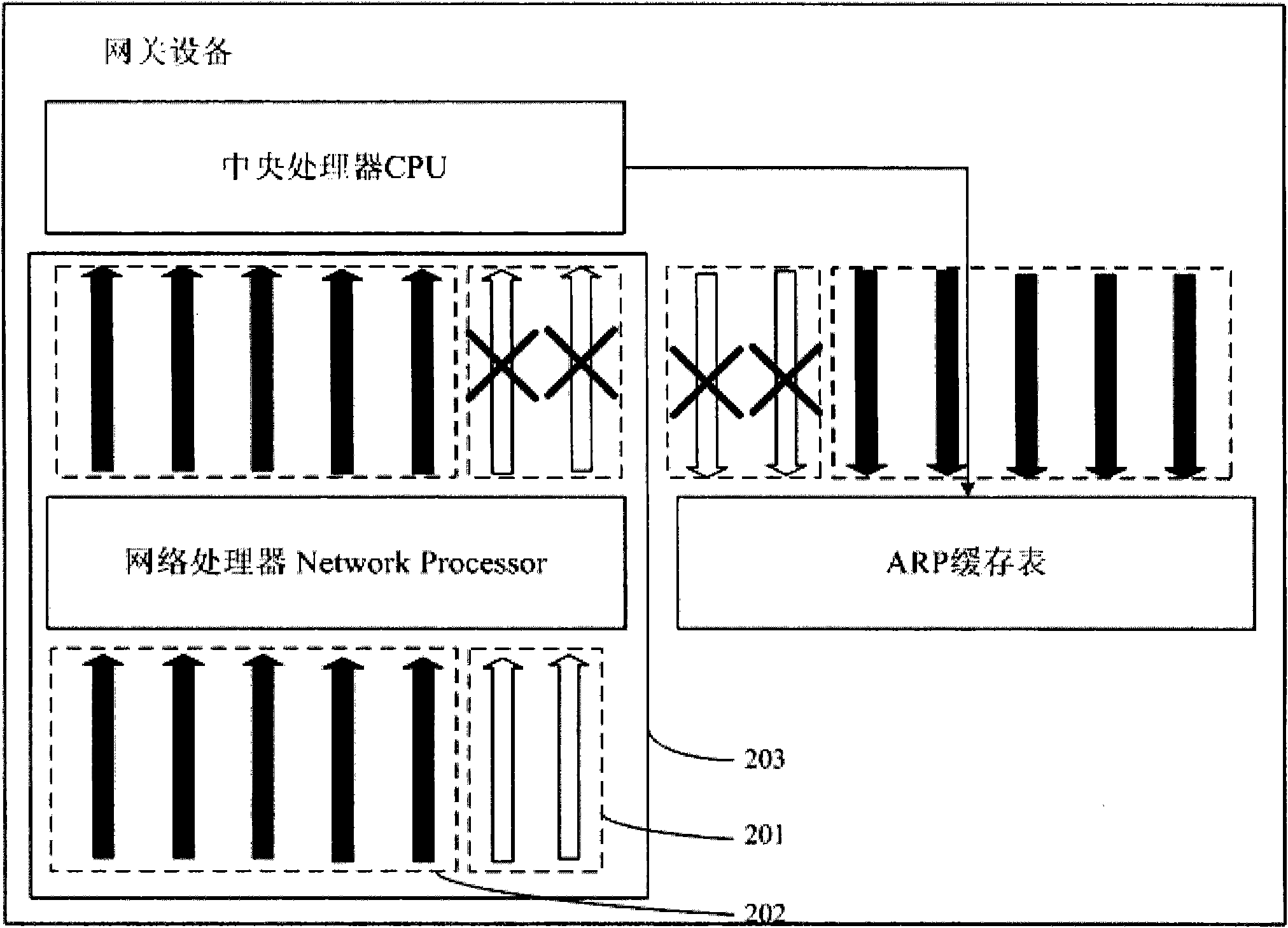
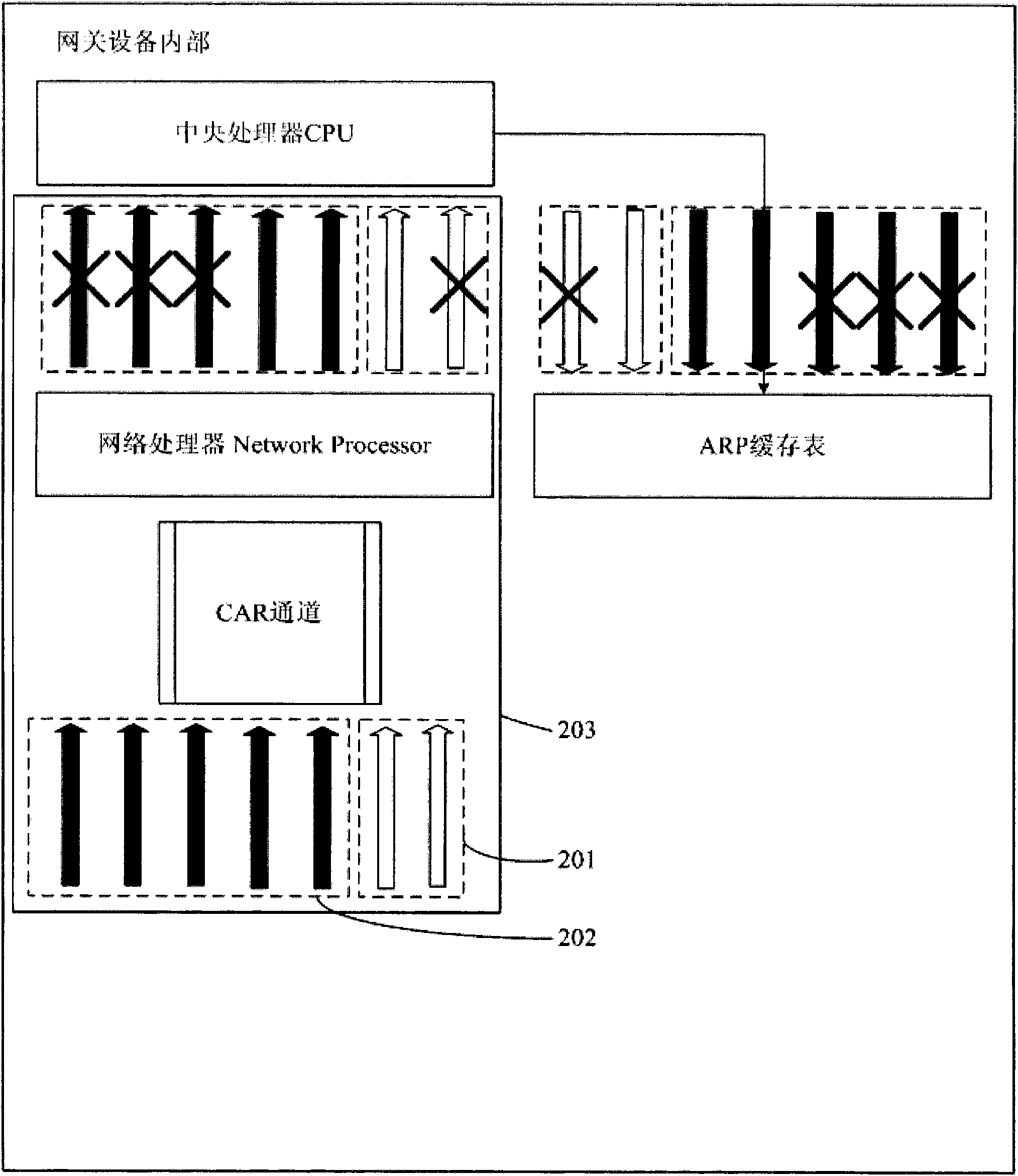
[0046] This embodiment provides a method for preventing flooding attacks, and its application scenario is an ARP packet flooding attack. Such as figure 1 As shown, the terminals PC1 and PC2 form a virtual local area network VLAN1, the terminals PC3 and PC4 form a virtual local area network VLAN2, and the terminals PC5 and PC6 form a virtual local area network VLAN3. Each terminal is aggregated to the gateway device through a layer 2 switch. The internal situation of the gateway device is as follows: figure 2 As shown, including the central processing unit CPU, the network processor Network Processor, and the ARP cache table. Such as Figure 8 As shown, the flood attack prevention method provided in this embodiment includes:
[0047] Step 801: Check the validity of the sent ARP message.
[0048] In step 801, the network processor first checks the validity of the ARP message, and preliminarily filters some illegal ARP messages. The legality check includes presetting the ca...
Embodiment 3
[0067] This embodiment provides a method for preventing flooding attacks, and its application scenario is the situation of ICMP message flooding attacks. Such as figure 1 As shown, the terminals PC1 and PC2 form a virtual local area network VLAN1, the terminals PC3 and PC4 form a virtual local area network VLAN2, and the terminals PC5 and PC6 form a virtual local area network VLAN3. Each terminal is aggregated to the gateway through a layer 2 switch, and the gateway device includes a central processing unit CPU and a network processor NetworkProcessor. Such as Figure 10 As shown, the flood attack prevention method provided in this embodiment includes:
[0068] Step 1001: Check the validity of the ICMP message sent.
[0069]In step 1001, the network processor first checks the validity of ICMP messages, and preliminarily filters some illegal ICMP messages. The legality check includes presetting the category of the illegal ICMP message, and judging whether the ICMP message b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com