Patents
Literature
81 results about "Transfer control protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
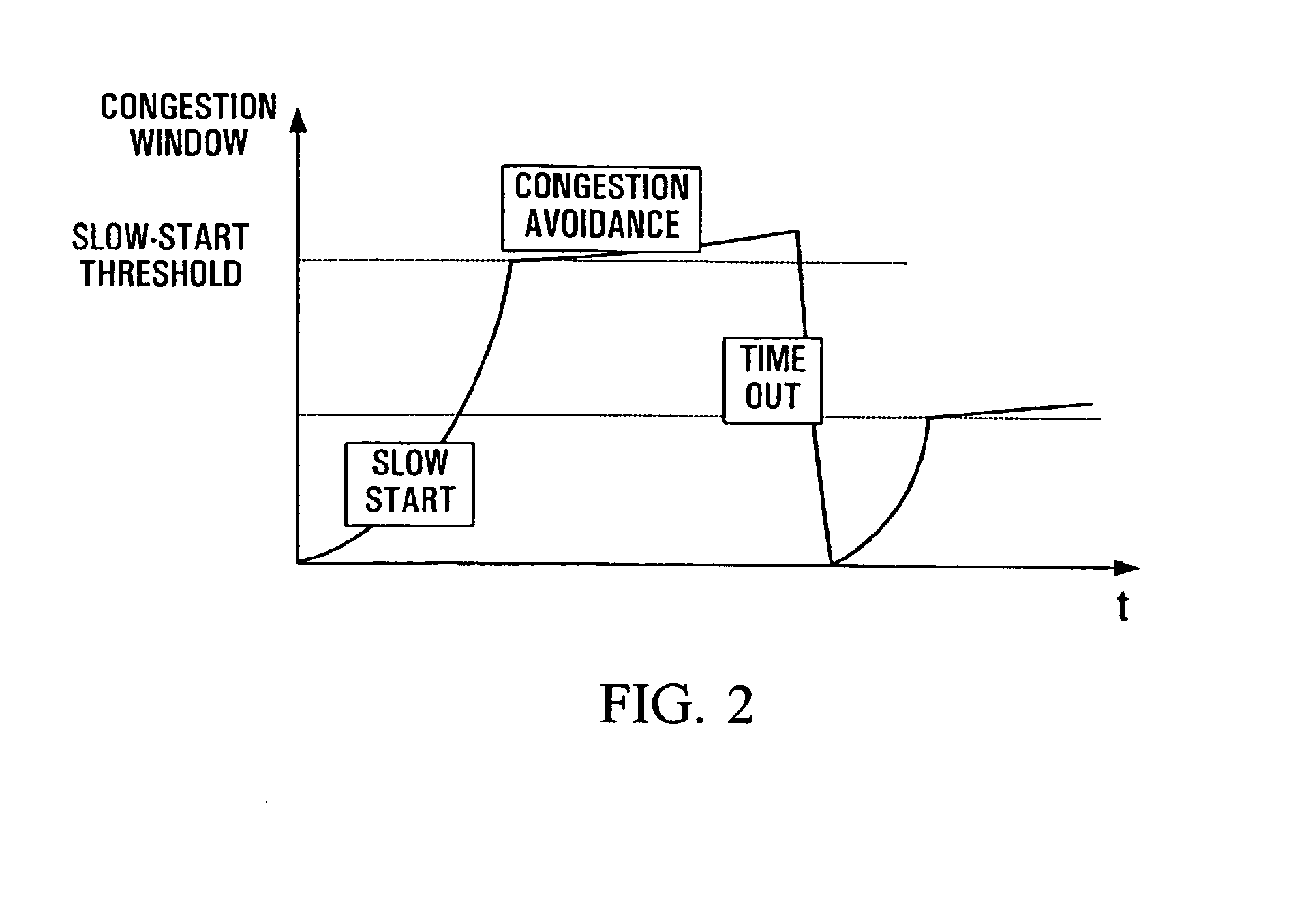
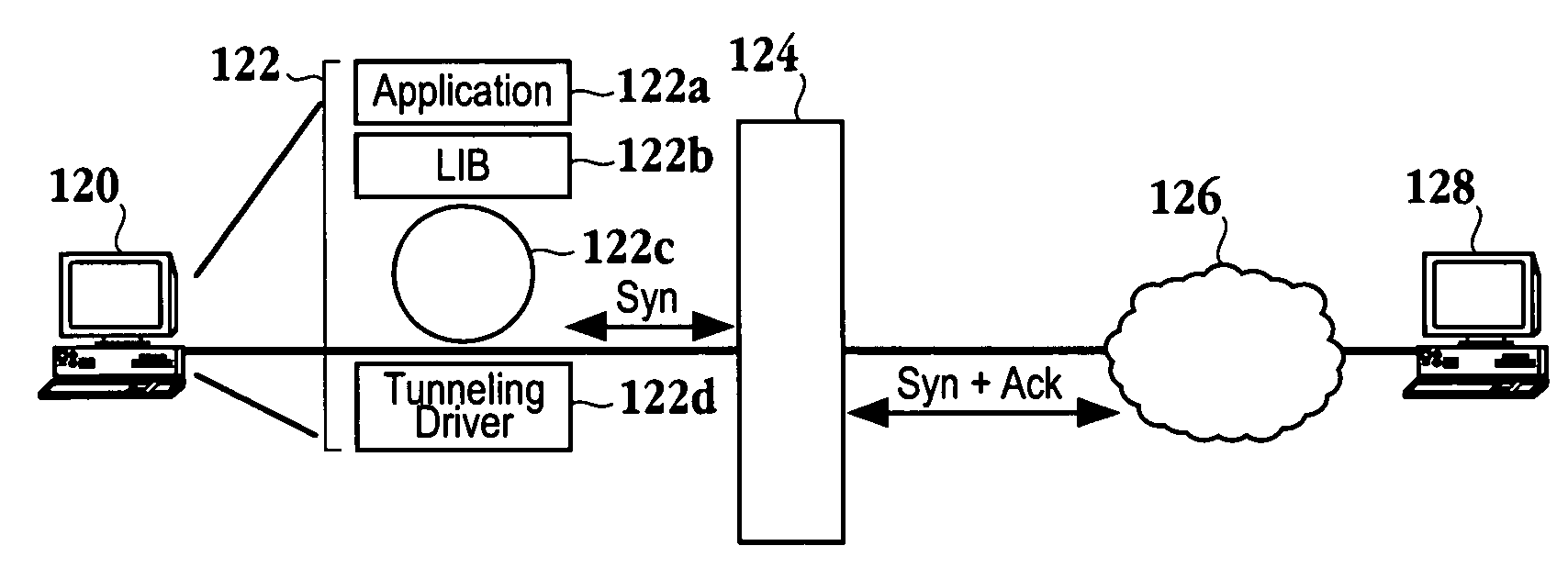
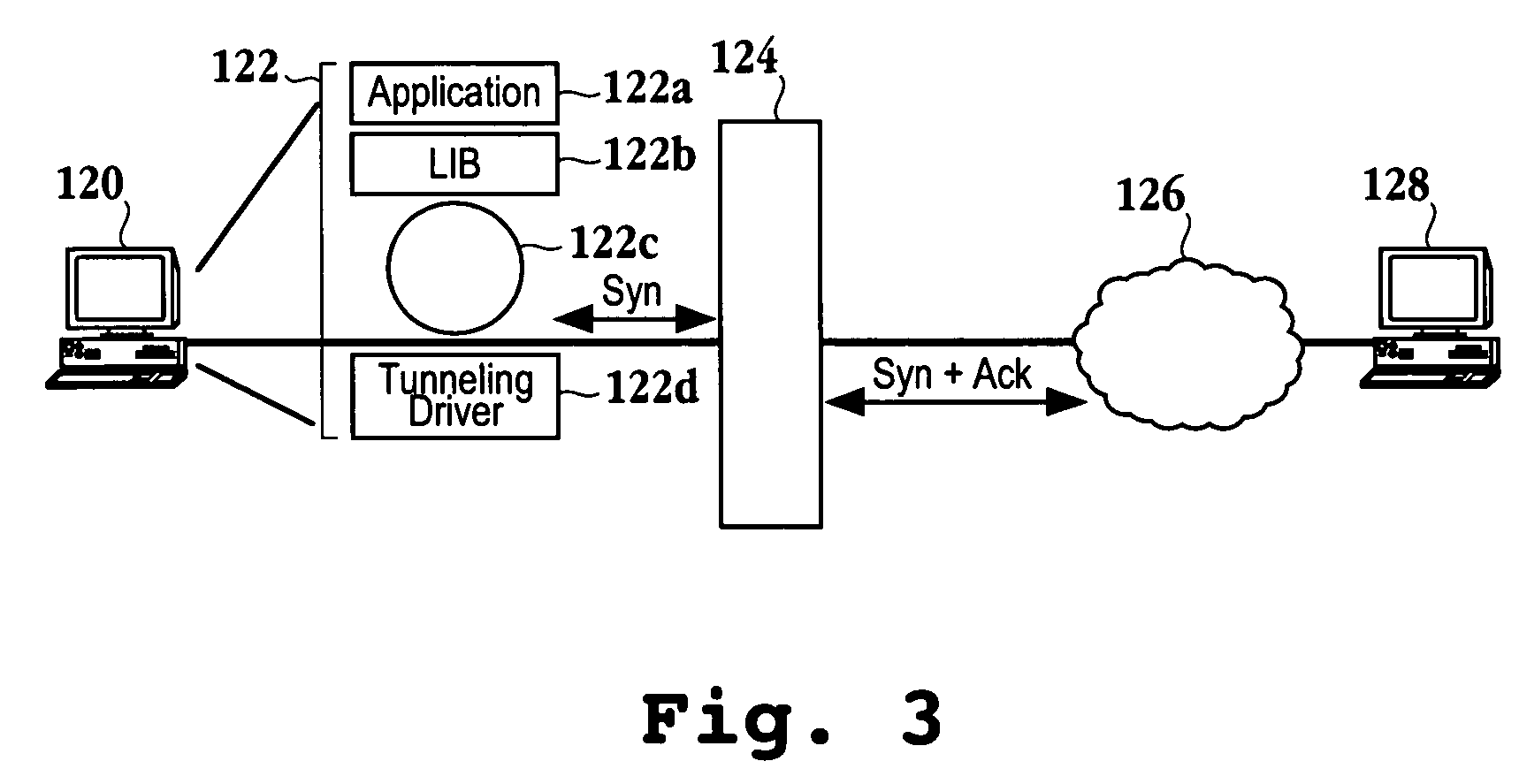
Transfer Control Protocol or Transmission Control Protocol (TCP) is one of the core protocols of the Internet Protocol suite, TCP is one of the two original components of the suite, complementing the Internet Protocol (IP), and therefore the entire suite is commonly referred to as TCP/IP.
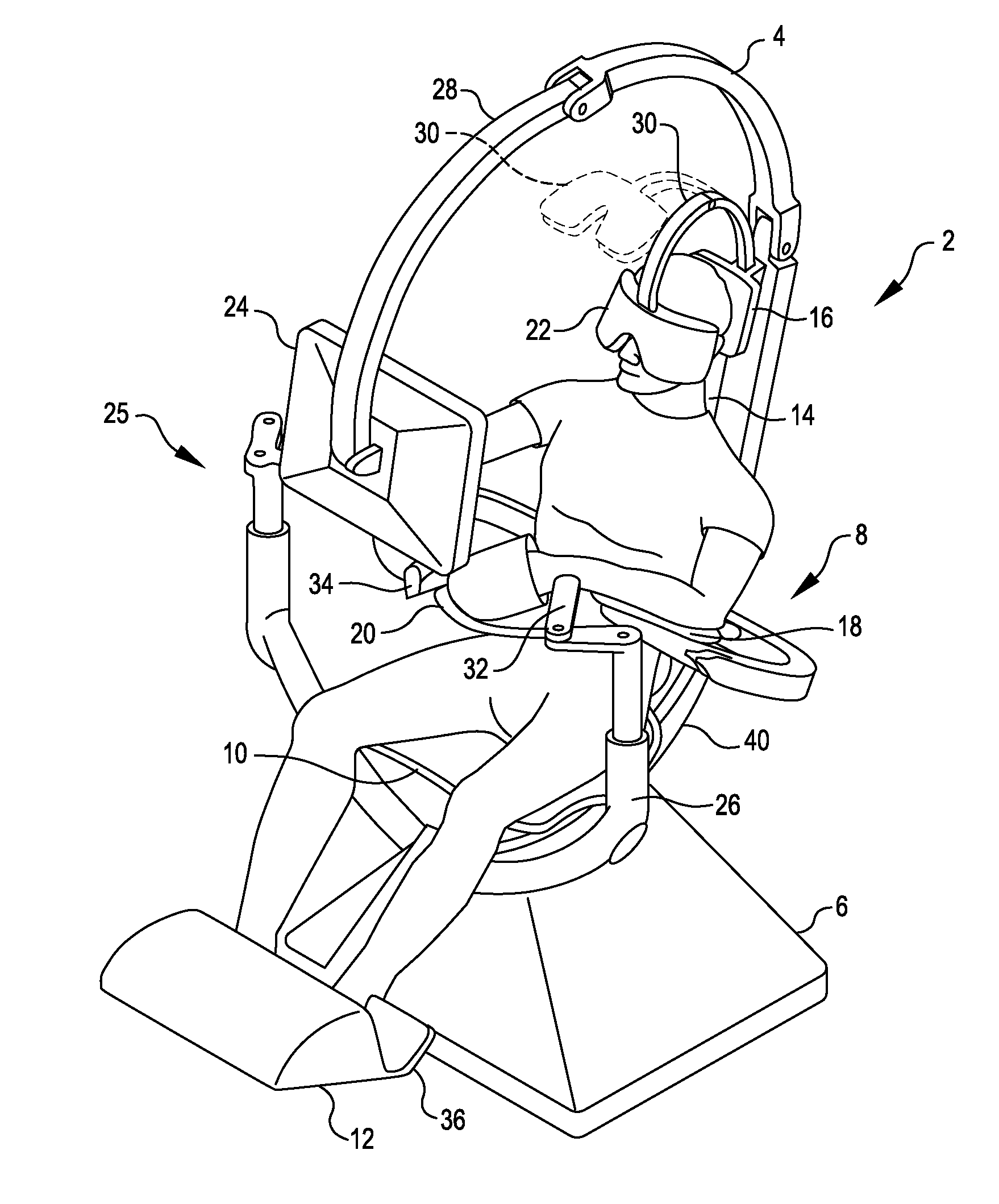
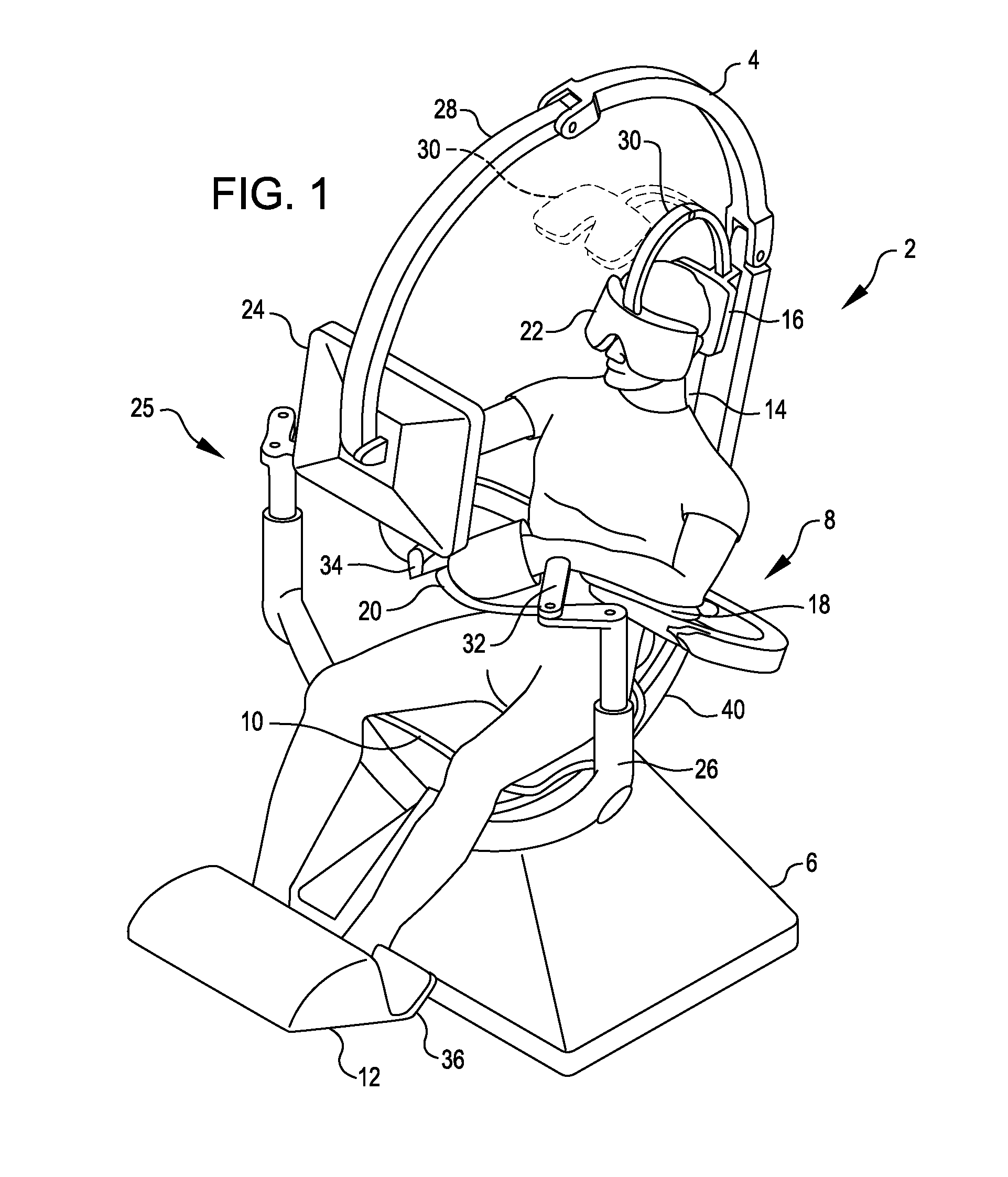
Surgical Cockpit Comprising Multisensory and Multimodal Interfaces for Robotic Surgery and Methods Related Thereto
InactiveUS20110238079A1Accurately respondEnhanced Situational AwarenessMedical communicationMechanical/radiation/invasive therapiesRemote surgeryCommunications system
Local surgical cockpits comprising local surgical consoles that can communicate with any desired remote surgical module (surgical robot), for example via a shared Transmission Control Protocol / Internet Protocol (TCP / IP) or other unified open source communication protocol or other suitable communication system. The systems and methods, etc., herein can also comprise a modular approach wherein multiple surgical consoles can network supporting collaborative surgery regardless of the physical location of the surgeons relative to each other and / or relative to the surgical site. Thus, for example, an operator operating a local surgical cockpit can teleoperate using a remote surgical module on a patient in the same room as the surgeon, or surgeons located in multiple safe locations can telemanipulate remote multiple surgical robots on a patient in or close to a war zone.
Owner:SPI SURGICAL
Communications network quality of service system and method for real time information
InactiveUS7142536B1Efficient qualityLower latencyTime-division multiplexCircuit switching systemsQuality of serviceTime information
The present invention provides efficient and effective quality of service for information that is time sensitive (e.g., real time data). An intermediate network communication system and method (e.g., a router) of the present invention performs cut through switching to reduce latency problems for time sensitive information. In one embodiment of the present invention, communication packet header information is encoded with a time sensitive identifier that identifies the information as time sensitive. In one exemplary transfer control protocol / internet protocol TCP / IP implementation of the present invention, time sensitive indication is provided in the link layer information. In one embodiment of the present invention, time sensitive information is dropped if the intermediate network device can not communicate the information within specified timing constraints. In one embodiment of the present invention time sensitive information is cut through routed on a virtual channel and pre-empts non time sensitive information. In one embodiment a communication path probe is cut through routed via intermediate network devices to establish a communication path before other information is communicated from a originating source to a final destination. In one embodiment the present invention leverages previously collected information to establish a communication path. In one embodiment the present invention, an intermediate network device establishes a second communication link if a first communication link is unavailable.
Owner:GOOGLE LLC
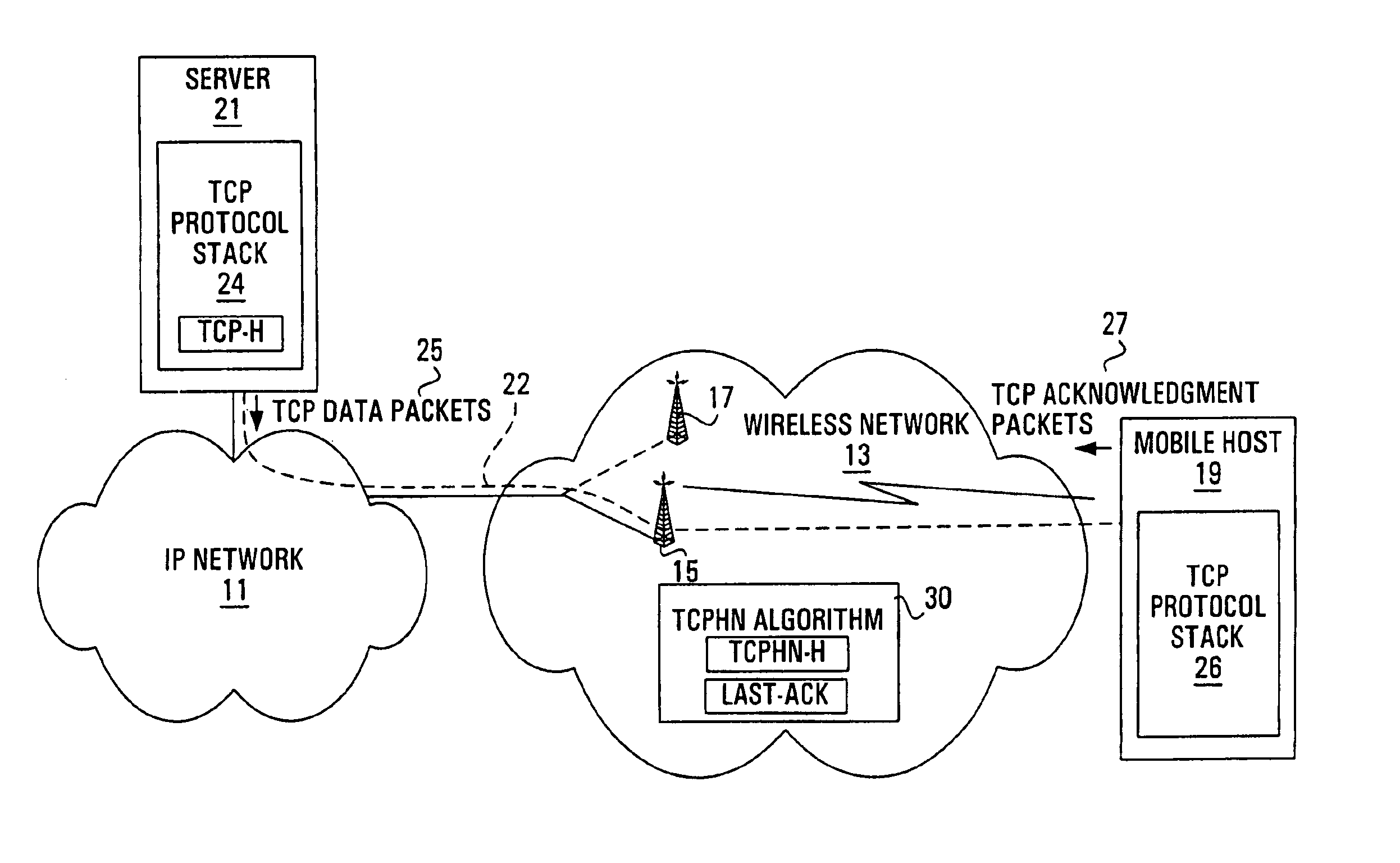
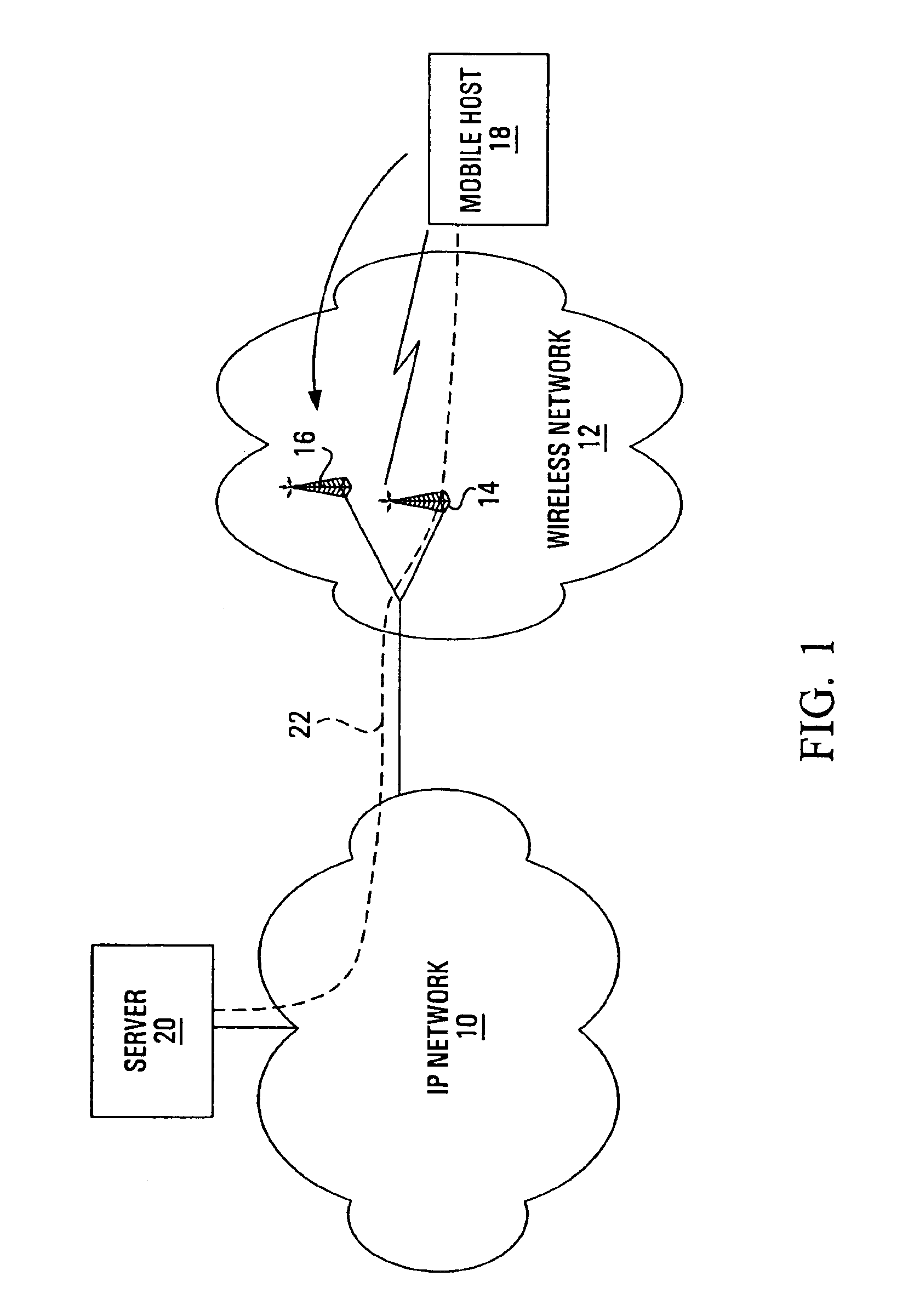
Transmission control protocol handoff notification system and method
InactiveUS6876639B1Promote recoveryReduce in quantityError prevention/detection by using return channelWireless network protocolsMobile serverNotification system
The present invention provides a transfer control protocol handoff notification (TCPHN) mechanism for a wireless network by which hosts connected through the wireless network via a transfer control protocol (TCP) connection can be notified in the event a handoff occurs. The TCPHN mechanism allows hosts connected in TCP to avoid TCP timeouts and reduce any adverse effect on transmission performance. The TCPHN mechanism of the present invention can be used in relation to any TCP connection between any transmitting and receiving host where at least one of the transmitting and receiving hosts is mobile and subject to handoffs. In one embodiment for example, the TCPHN mechanism is used in relation to a TCP connection between a mobile host in a wireless network and a non-mobile server host in a connecting Internet protocol (IP) network.
Owner:APPLE INC
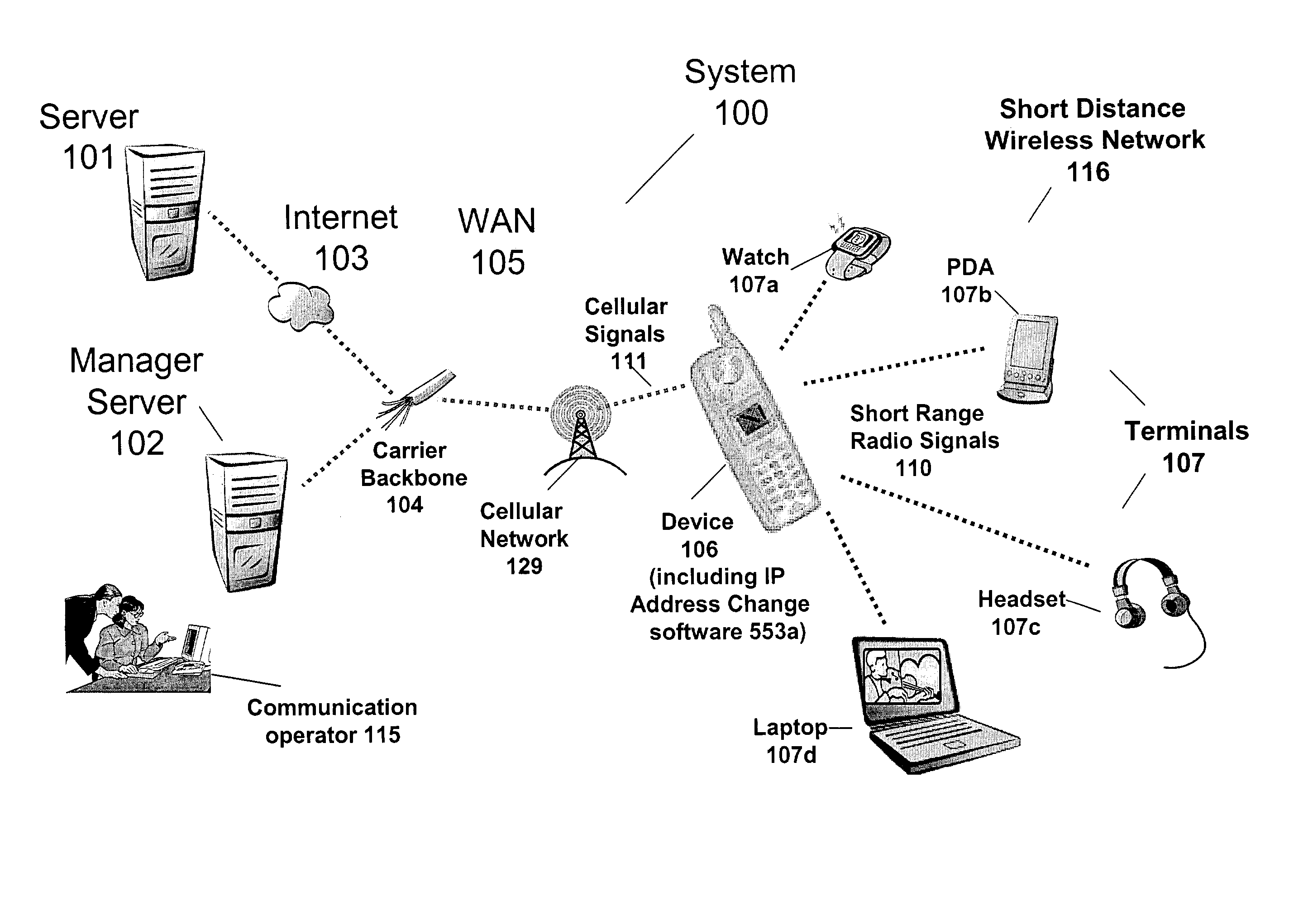
Device, system, method and computer readable medium for fast recovery of IP address change
InactiveUS7016334B2Promote recoveryNetwork traffic/resource managementNetwork topologiesPrivate IPIp address
A device, method, system and computer readable medium allows for a fast recovery of a communication connection in response to a newly assigned Wide Area Network (“WAN”) Internet protocol (“IP”) source address. In an embodiment of the present invention, a device provides communication between a WAN and a short distance wireless network. The device comprises a memory to store a first and a second WAN address for the device and a router software component. The processor and router software component transfers a first plurality of packets between the device and the wide area network using the first wide area network address. The processor and router software component discontinues the transfer of the first plurality of packets responsive to receiving the second wide area network address and transfers a second plurality of packets between the device and the wide area network using the second wide area network address. The second newly assigned WAN address may have been assigned by the WAN after a disconnection of communication between the device and a server in the WAN. In an embodiment of the present invention, the router software includes a plurality of private IP addresses for respective terminals, in the short distance wireless network, associated with the WAN IP address. In an embodiment of the present invention, a Point-to-Point (“PPP”) connection or Transfer Control Protocol (“TCP”) connection is discontinued and then initiated in response to a newly assigned WAN IP address in order to quickly recover a communication connection between terminals in the short distance wireless network and the WAN.
Owner:IXI IP LLC +1
Method and apparatus for tunneling data using a single simulated stateful TCP connection
InactiveUS7392323B2Data switching by path configurationMultiple digital computer combinationsComputer networkPage header
Owner:SEIKO EPSON CORP
Data transmission method and virtual peer-to-peer network for data transmission
InactiveCN101699801AReduce transmission delayLow bandwidth resourceData switching networksIp addressData transmission time
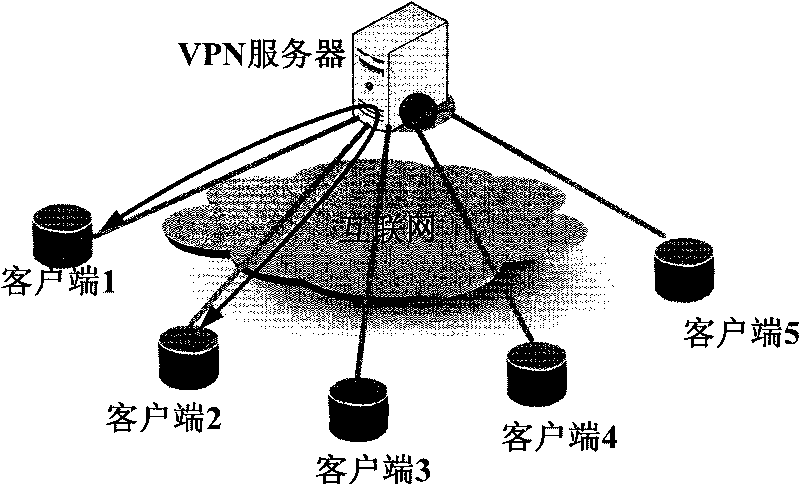
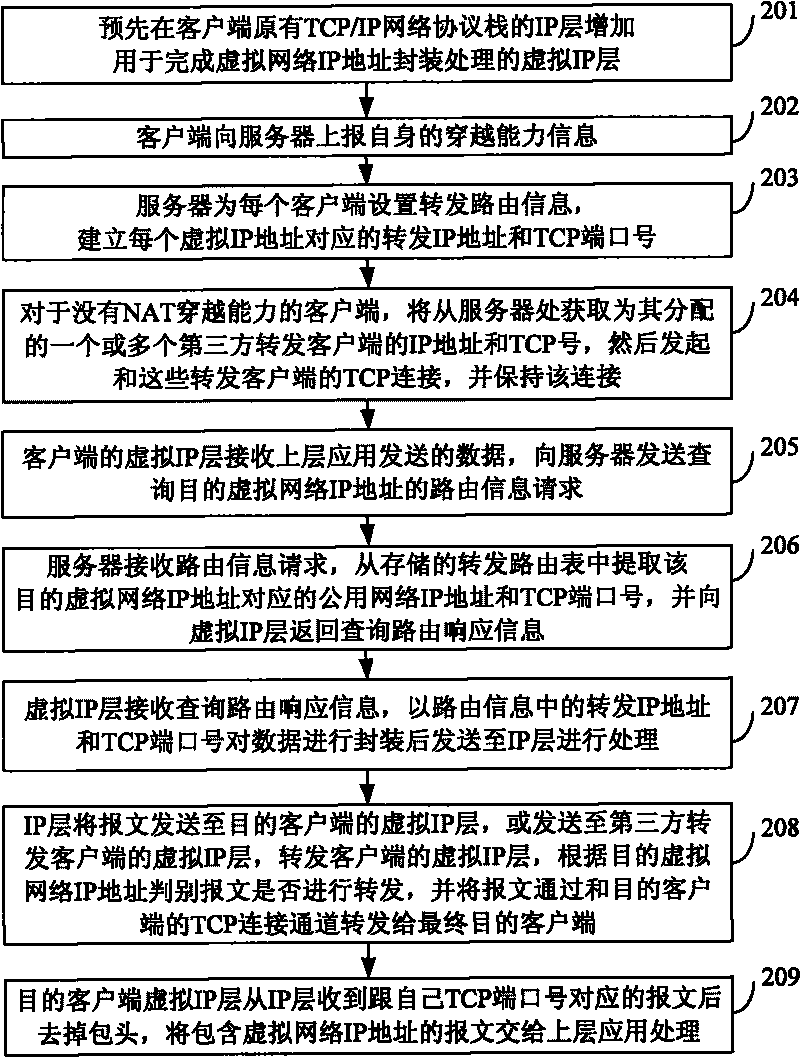
The invention discloses a data transmission method and a virtual peer-to-peer network for data transmission, and the data transmission method comprises the following steps: increasing a virtual IP layer at an IP layer of an original (TCP / IP, Transfer Control Protocol / Internet Protocol) network protocol stack of a client, thereby obtaining the public network IP address which corresponds to the virtual network IP address from a server and packaging the virtual network IP address as the corresponding public network IP address when taking the virtual network IP address as the target network IP address; and obtaining routing path information to the public network IP address from a routing information table stored in the server and carrying out the corresponding treatment according to the obtained routing path information. When a VPN network is constructed by applying the invention, the server does not need to forward data any longer, thereby reducing the data transmission time delay, simplifying the requirements on the performances of the server and the bandwidth and improving the network transmission efficiency.
Owner:孙喜明 +1
Remote real machine debugging method and system of mobile terminal application software
InactiveCN103268288APrecise positioningEasy to findSoftware testing/debuggingTest efficiencyApplication software
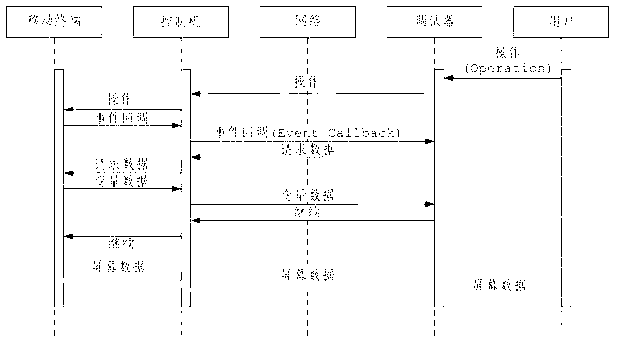
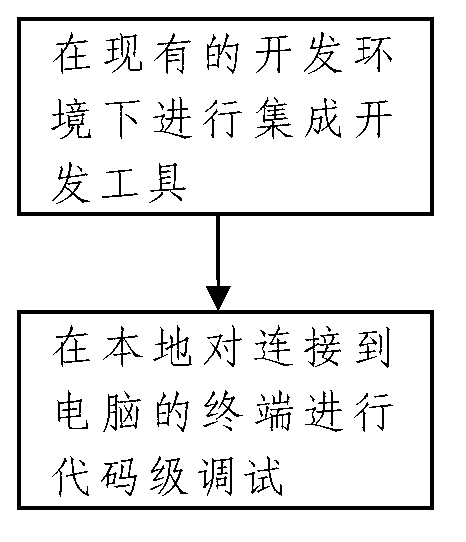
The invention provides a remote real machine debugging method and system of mobile terminal application software. The method comprises the following steps that a mobile terminal is connected to a control machine, and the control machine is connected and communicated with a client debugger through a TCP / IP (Transfer Control Protocol / Internet Protocol) protocol; a TCP / IP protocol forwarding layer and a terminal control layer are additionally arranged between a development tool and hardware, the application is deployed to a remote terminal, and the remote terminal is controlled; the control machine forwards the debugging commands from the client debugger to the terminal; the debugging data returned from the terminal is forwarded to the client debugger; and through the manipulation of real machine, a client adds a breakpoint to a correlation function, and carries out debugging in the source code environment. According to the technical scheme provided by the invention, developers can execute breakpoint hit, single step running, variable value checking and other operations on the remote terminal in the local source code environment, so that the positioning and checking of problems in the debugging process are greatly facilitated, and the testing efficiency of application software is improved.
Owner:BEIJING YUNCE INFORMATION TECH CO LTD
Tcp/ip reception process circuit and semiconductor integrated cirtuit having the same
InactiveUS20060265517A1Reduce loadMultiple digital computer combinationsTransmissionCommunication endpointComputer network
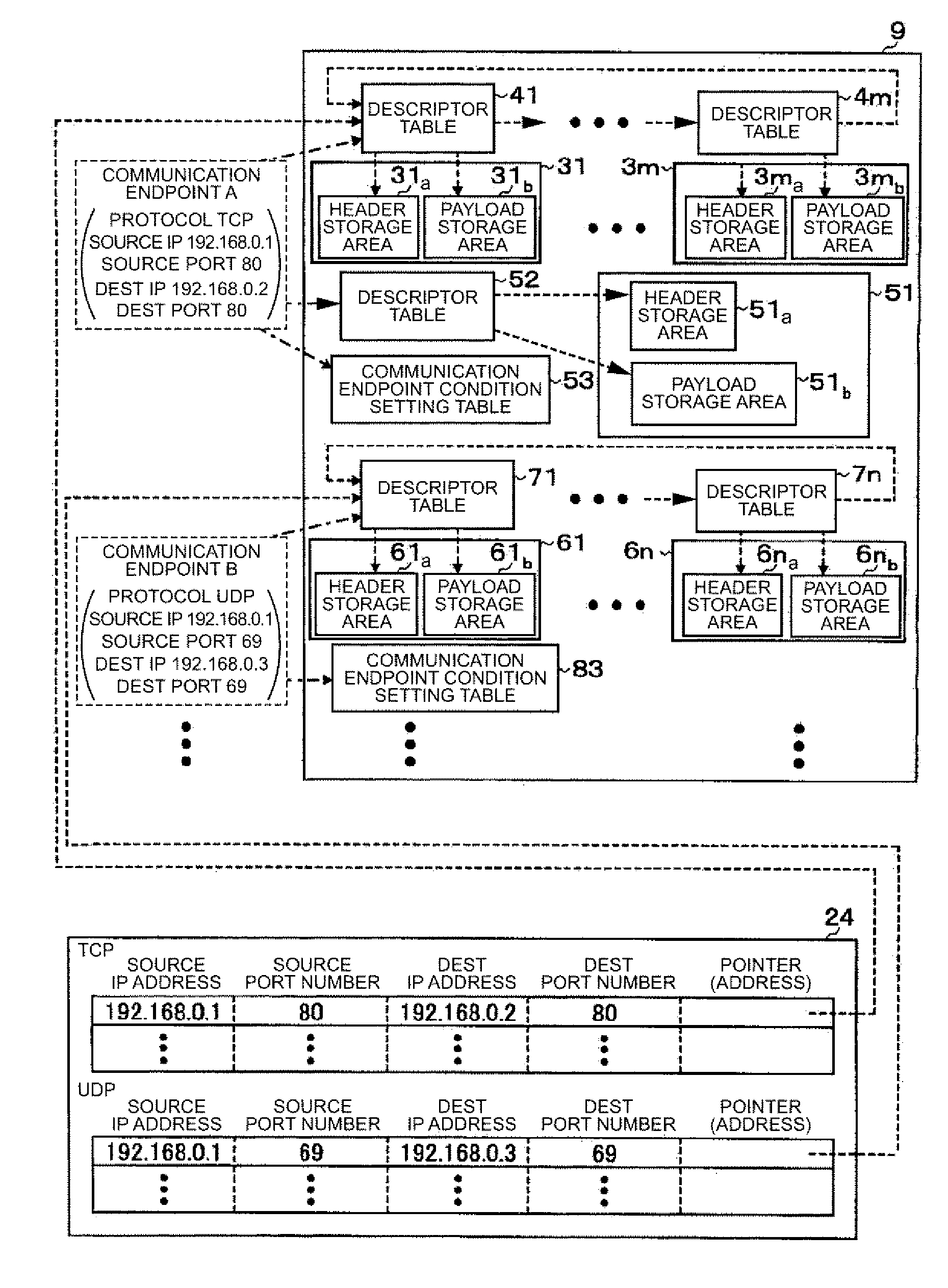
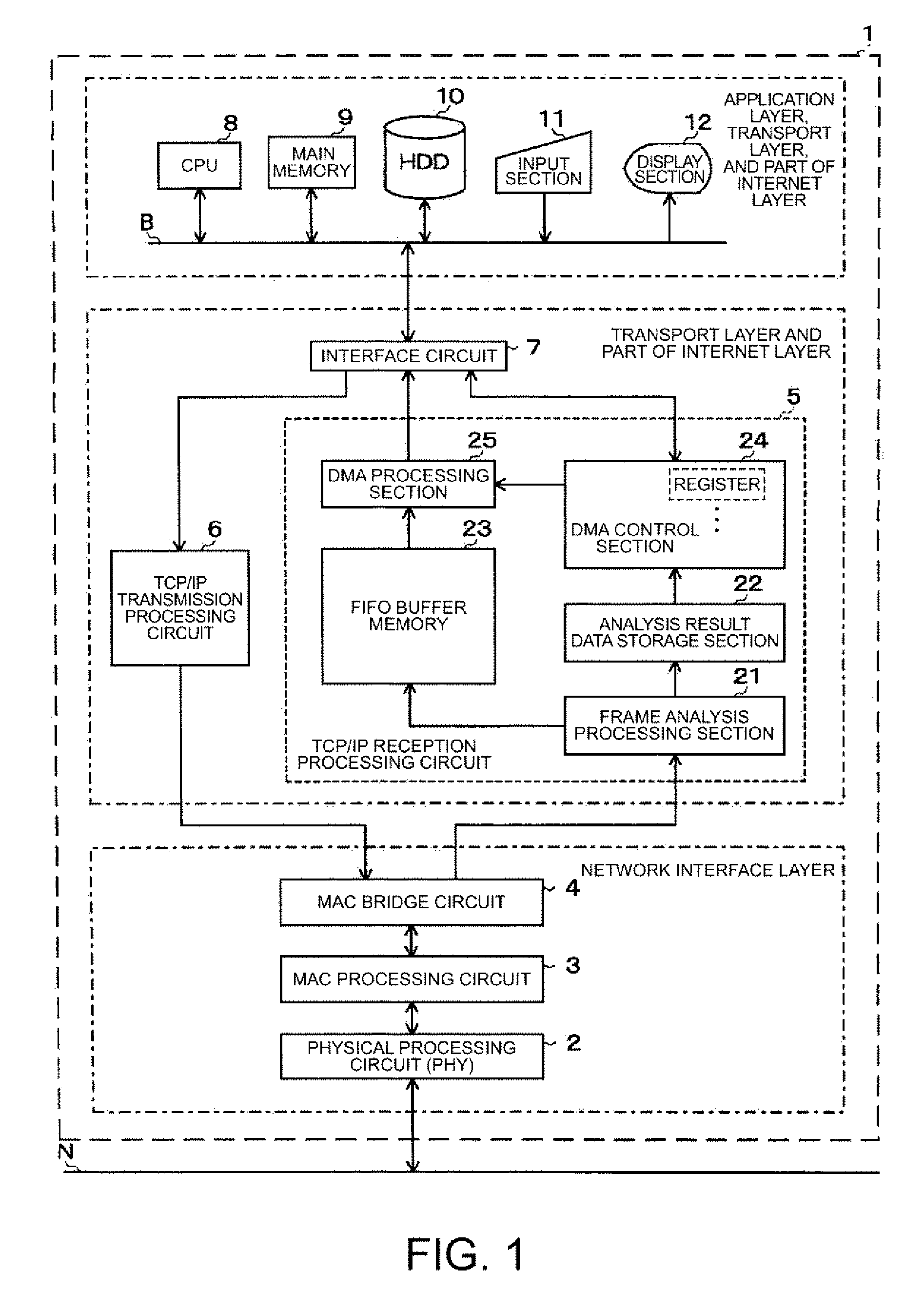
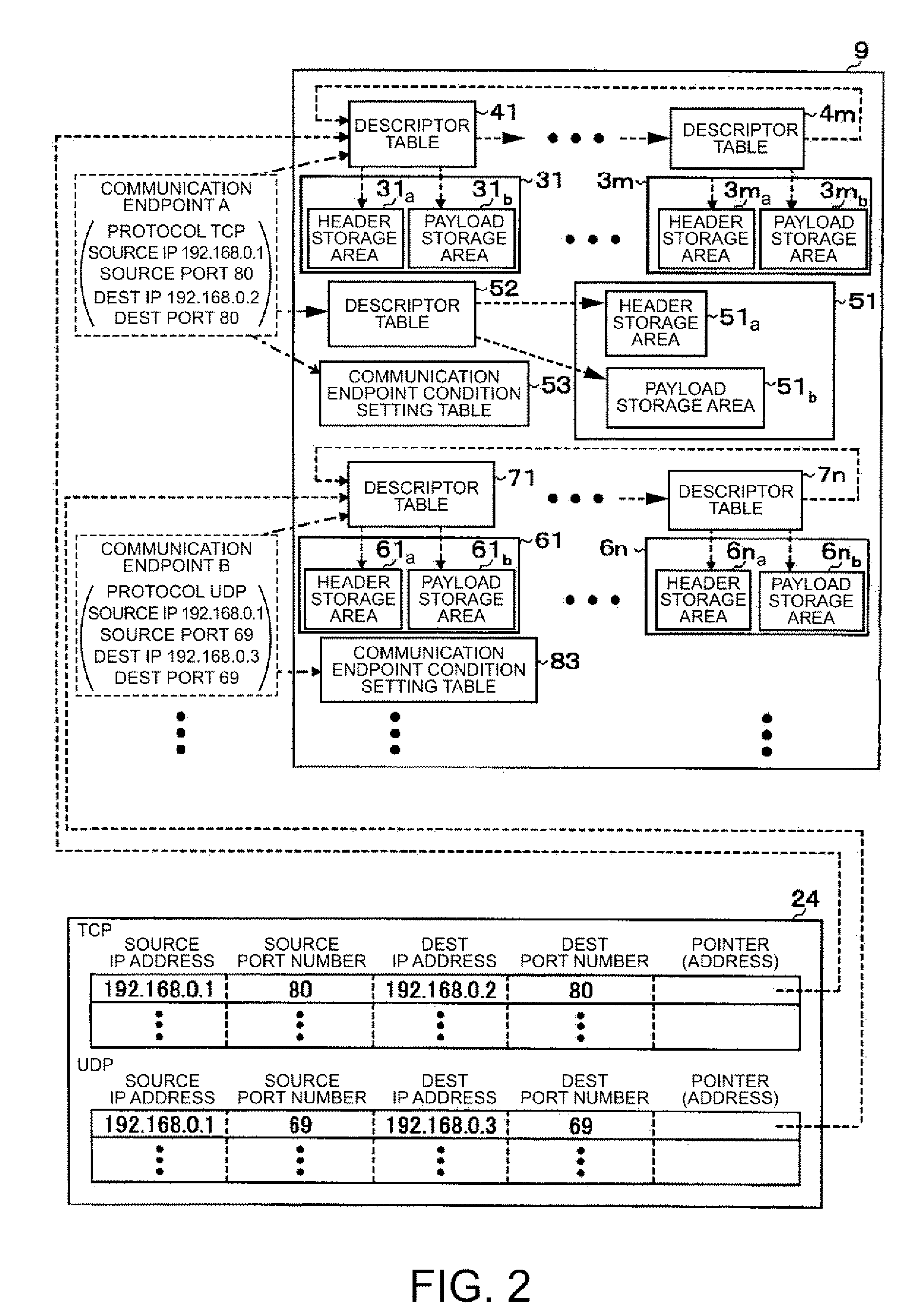
A transmission control protocol / Internet protocol (TCP / IP) reception processing circuit that transmits a packet included in a frame and received from a lower layer to memory accessible by an upper layer, in that: the memory includes: a communication endpoint information area which contains a plurality of packet storage areas, with each packet storage area storing a plurality of packets addressed to a predetermined communication endpoint, and which contains a plurality of descriptor tables linked to a first pointer included in each packet storage area, with each descriptor table having a second pointer that points out the packet storage area and having packet writable / non-writable information that indicates whether or not the packet can be written into the packet storage area pointed out by the second pointer; and, if a packet included in a frame and received from the lower layer is a packet addressed to the predetermined communication endpoint, one out of the plurality of descriptor tables that points out the packet storage area into which the packet can be written is determined by using the first pointer and the packet writable / non-writable information, and the packet included in the frame and received from the lower layer is transferred into the packet storage area pointed out by the second pointer in this descriptor table.
Owner:SEIKO EPSON CORP
Network speed test method and network speed test system
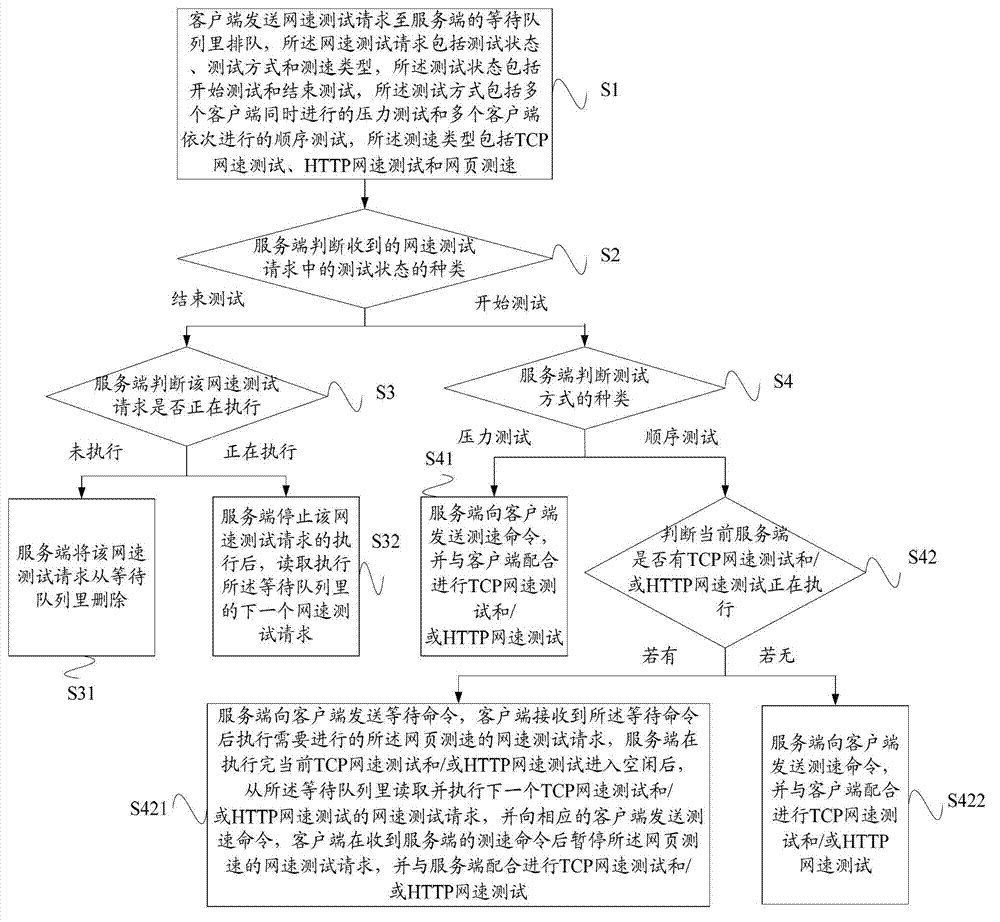
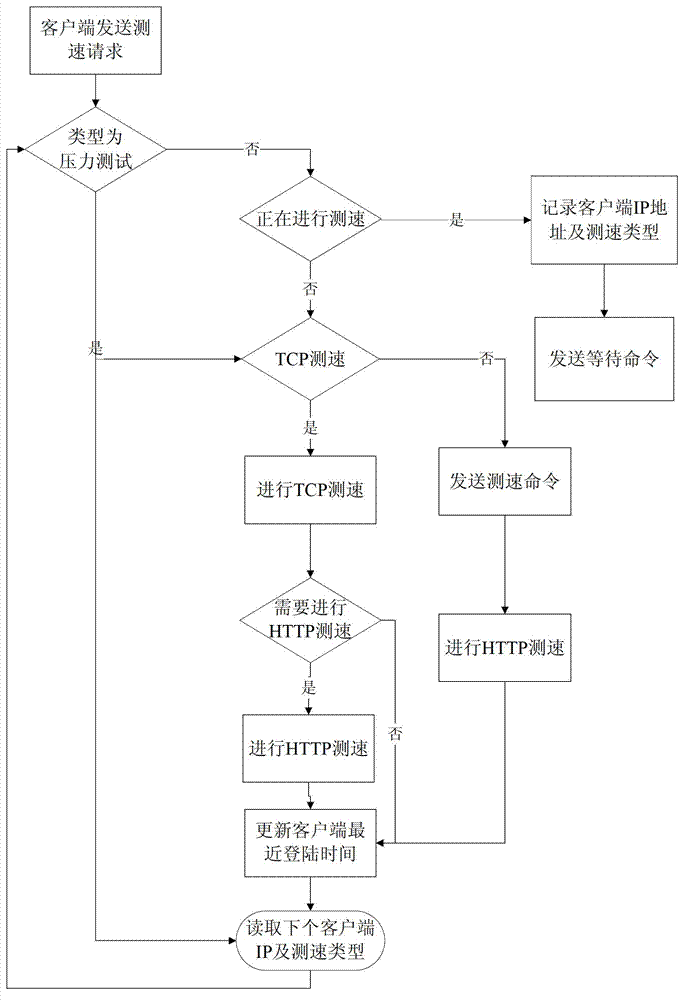
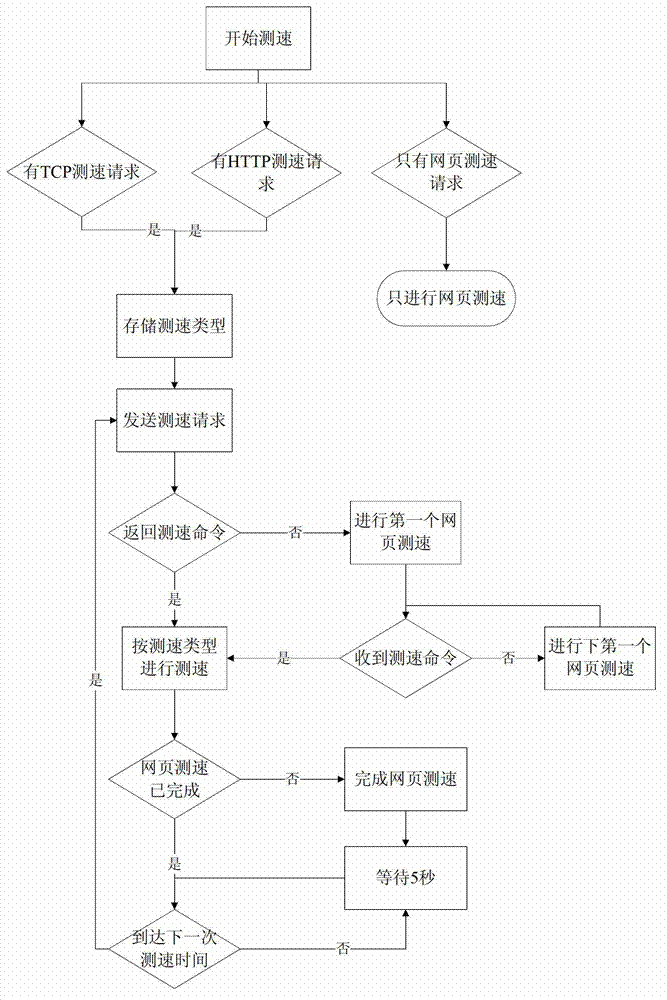
ActiveCN103051498AIntuitive and objective detectionAccurate Bandwidth DataData switching networksSpeed testClient-side
The invention relates to a network speed test method and a network speed test system. The method includes the following steps: a network speed test request is sent into a waiting queue of a server by a client to be queued; if the judgment result of the server is test starting, then the server judges the variety of a test mode; if the test mode is pressure test, then the server sends a speed-testing command to the client, and cooperates with the client to carry out a TCP (transfer control protocol) network speed test and / or an HTTP (hypertext transfer protocol) network speed test; if the test mode is sequence test, whether the TCP network speed test and / or the HTTP network speed test are / is executed by the current server is judged, if so, then a waiting command is sent to the client, and if not, then the server cooperates with the client to carry out the TCP network speed test and / or the HTTP network speed test. The invention can visually and objectively test the speed of all broadband networks to provide reliable technical support for users to obtain accurate bandwidth data of operators.
Owner:上海泰峰检测认证有限公司
Processing method and system for remote process call, client end and server
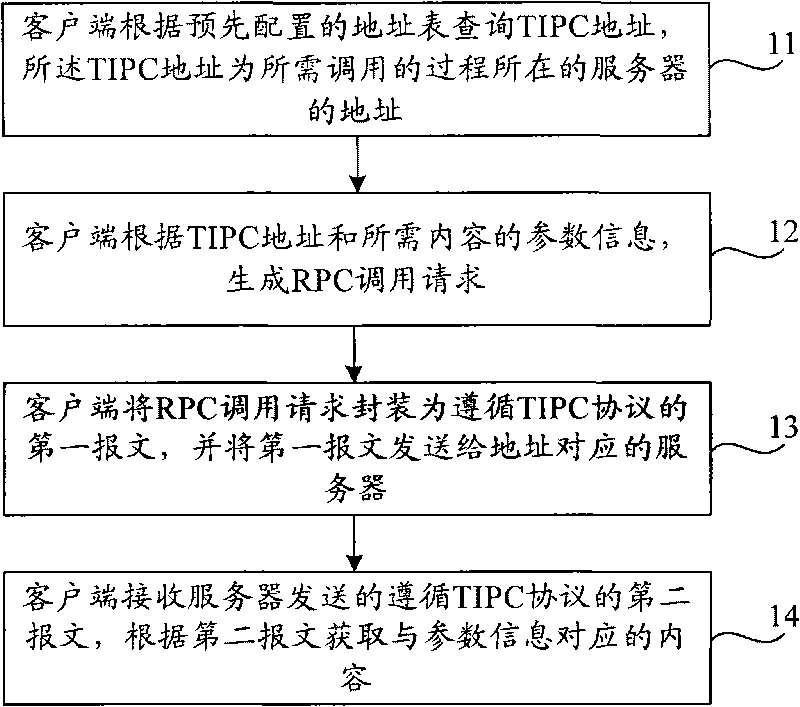
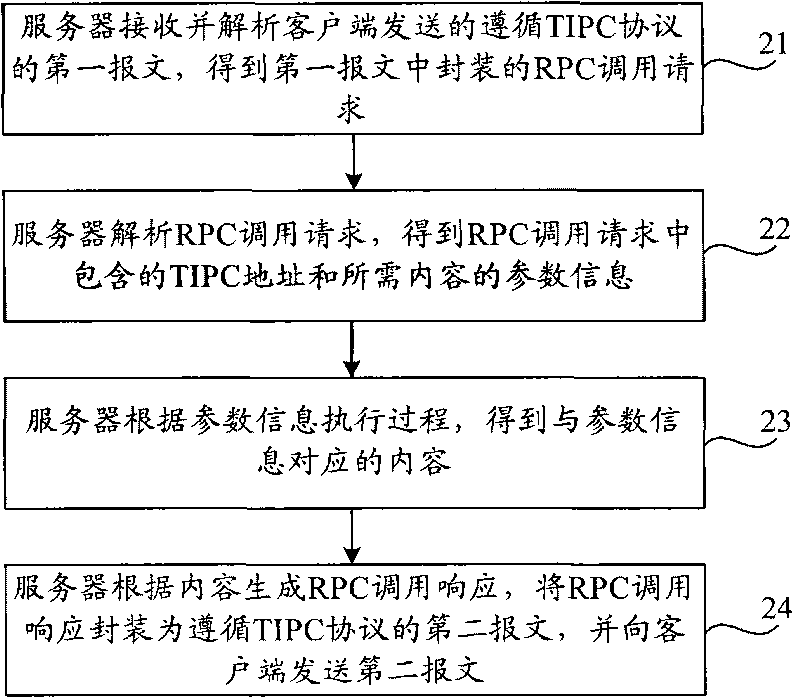
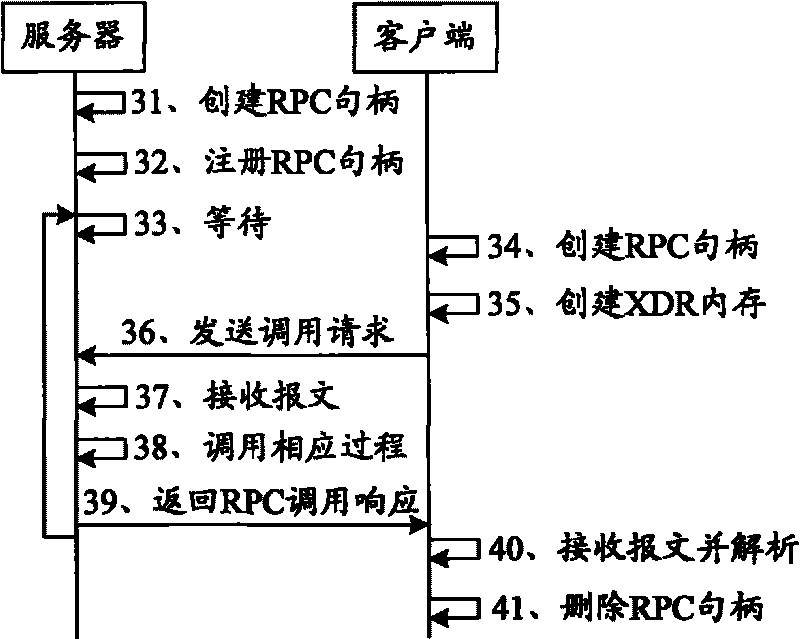
InactiveCN101764843AOvercoming Quantitative ProblemsTransmissionInter-process communicationClient-side
The invention provides a processing method and a system for remote process call, a client end and a server, wherein the method comprises the following steps of: inquiring a TIPC (Transparent Inter-Process Communication) address by the client end according to a preconfigured address list, wherein the TIPC address is the address of the server of a process to be called; generating a RPC (Remote Procedure Call) call request according to the TIPC address and the parameter information of a required content; packaging the RPC call request into a first message following a TIPC protocol and sending the first message to the server; and receiving a second message which is sent by the server and follows the TIPC protocol and obtaining the content corresponding to the parameter information according to the second message. In the processing method and the system for remote process call, the client end and the server provided by the invention, RPC is realized on the basis of the TIPC protocol, thereby solving the problem that a traditional RPC mechanism supporting a (TCP Transfer Control Protocol) or UDP (User Datagram Protocol) protocol is limited by the quantity of famous ports of the server.
Owner:RUIJIE NETWORKS CO LTD
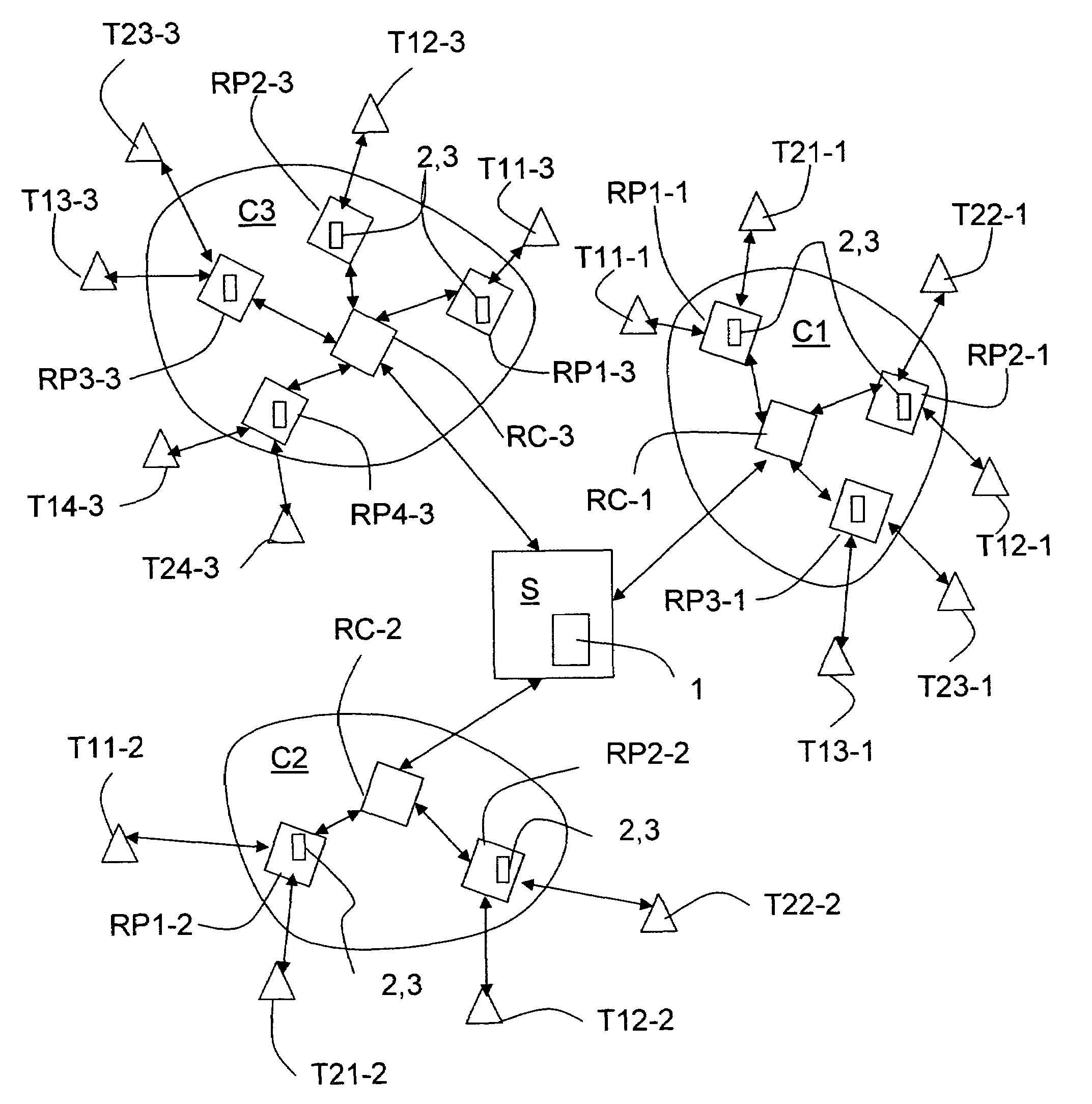
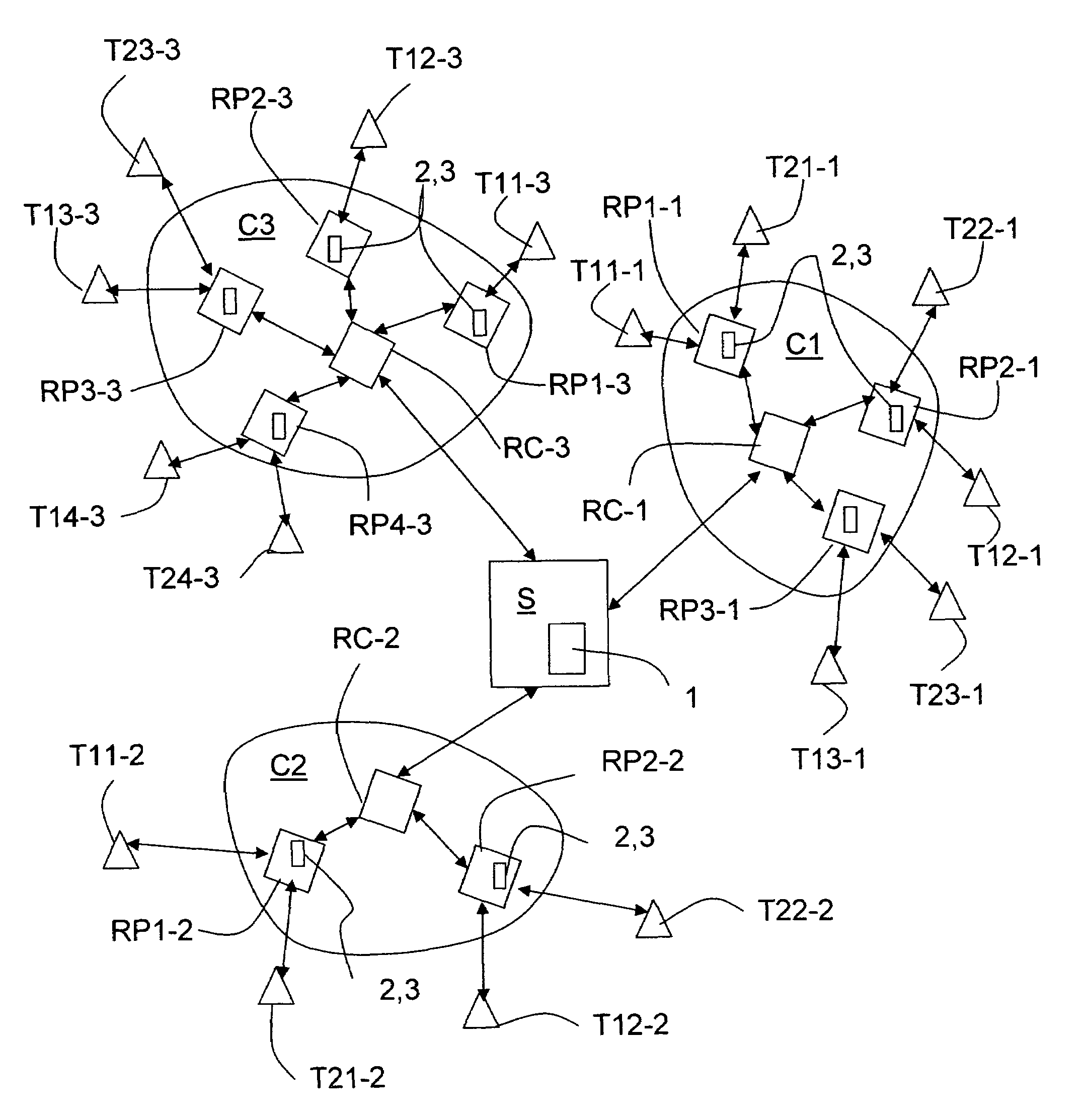
Method and system for generating an annotated network topology
A method of generating an annotated network topology of a network is described. The method includes determining available bandwidth “B” of a network on a network path connecting a pair of endpoints by performing Transfer Control Protocol (TCP) flows between the pair of endpoints, the network having a plurality of network paths, identifying a bottleneck link in the network path, and annotating all edges in a network path, wherein available bandwidth annotation of links inside the network is determined using end-to-end network measurements. A system for generating the annotated network topology of a network is also described.
Owner:IBM CORP
Integrated on-line system with enchanced data transfer protocol
ActiveUS7065547B2Digital data processing detailsUnauthorized memory use protectionComputer hardwareExchange protocol
The integrated on-line system with enhanced data transfer protocol enables dissimilar computers to instantly interchange data and integrate applications over a transfer control protocol / internet protocol (TCP / IP) network. The system is based on a client-server architecture in which multiple clients exchange data through a data transfer server using the enhanced data transfer protocol. The server acts as a post office for transferring data and provides verification of the sender's identity, the receiver's identity, verification of data transfers, electronic mailbox facilities, an audit trail, and inquiry and reporting functions. The protocol implements a socket to socket data interchange protocol on a preassigned port. Communications require validation of a header and permit send and receive sessions, receive sessions, or and end to end session. Optionally, the system provides a dual key encryption system, including a header key and a data encryption key.
Owner:PERSELS CONRAD G +1
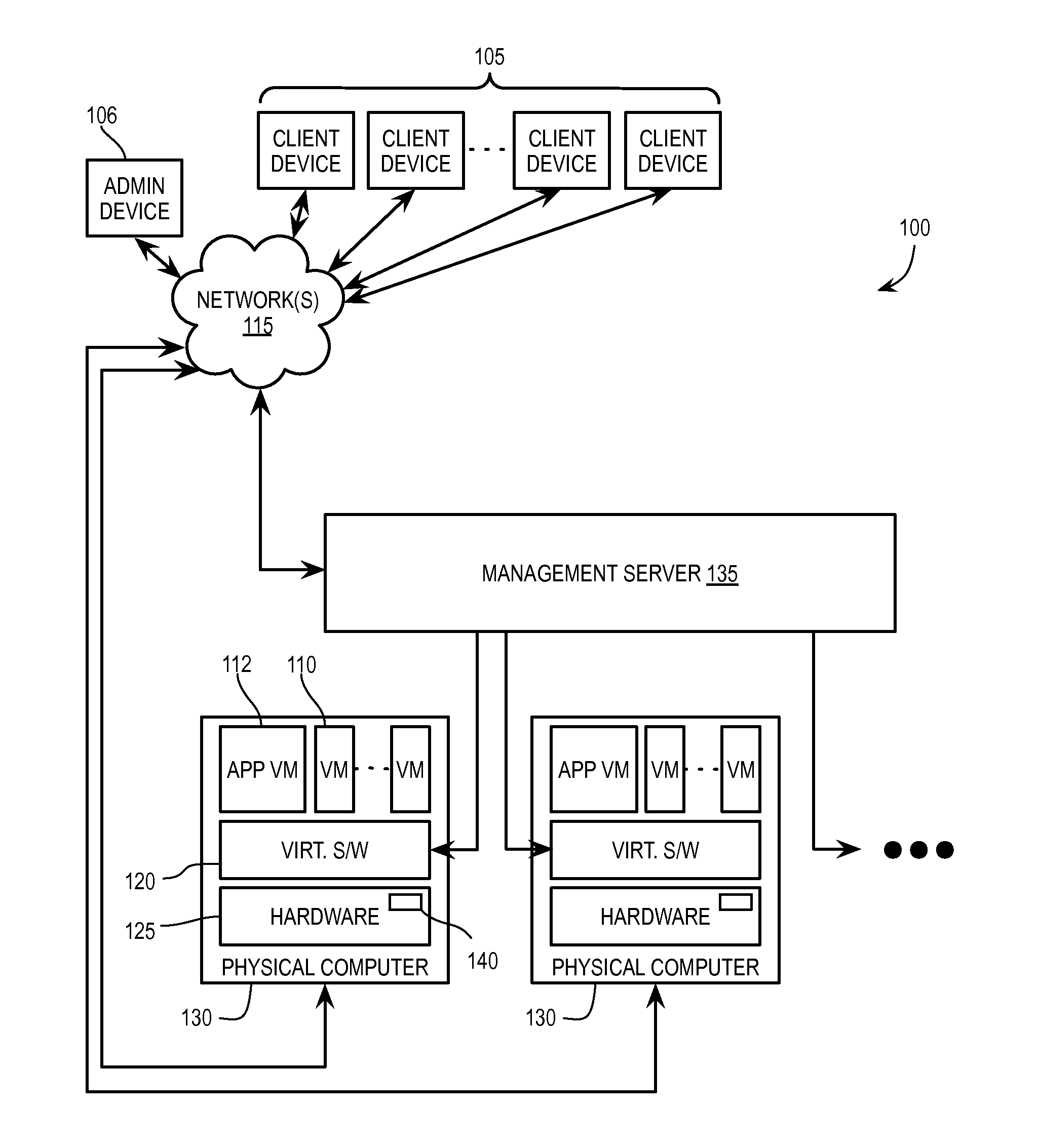
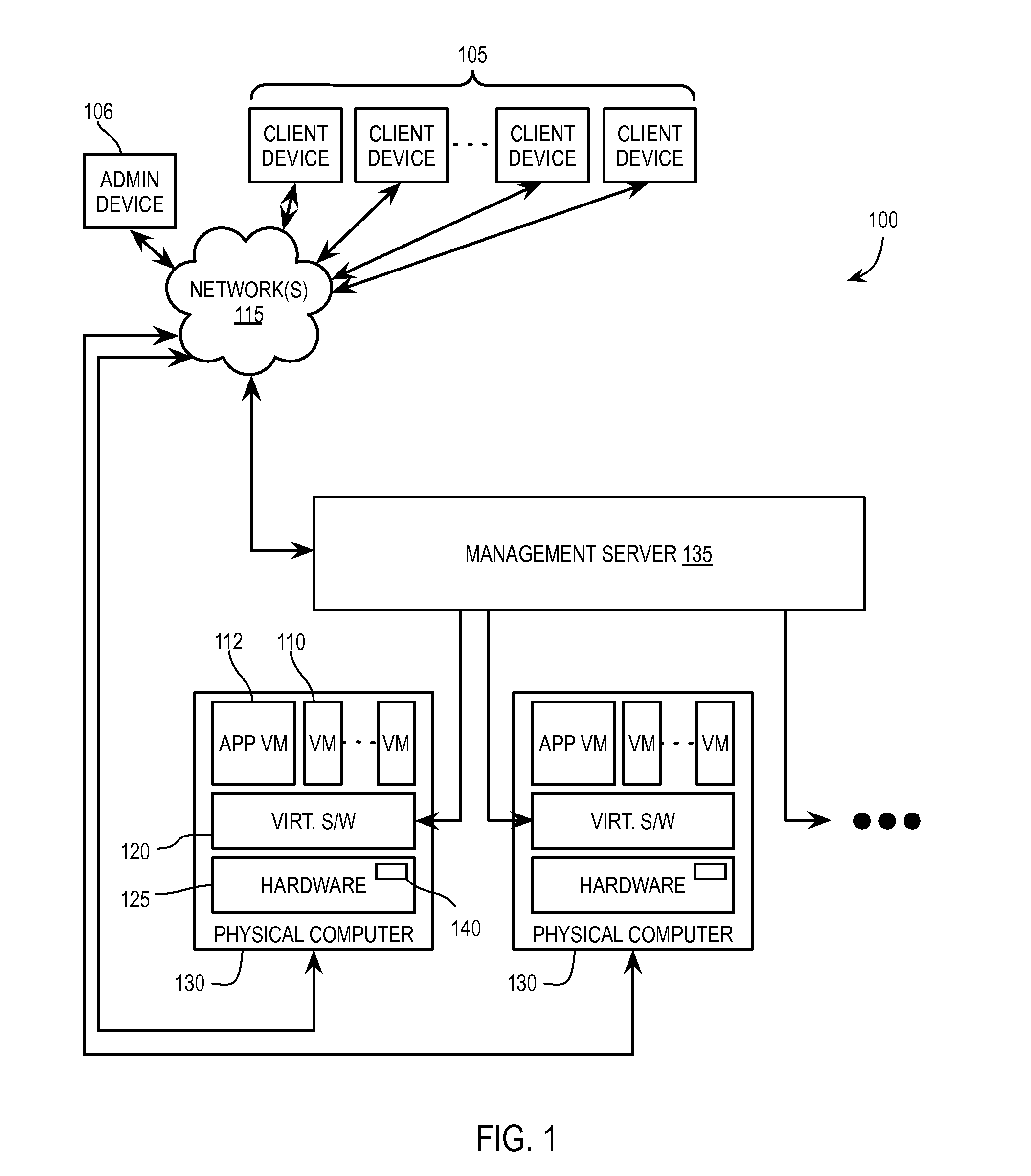
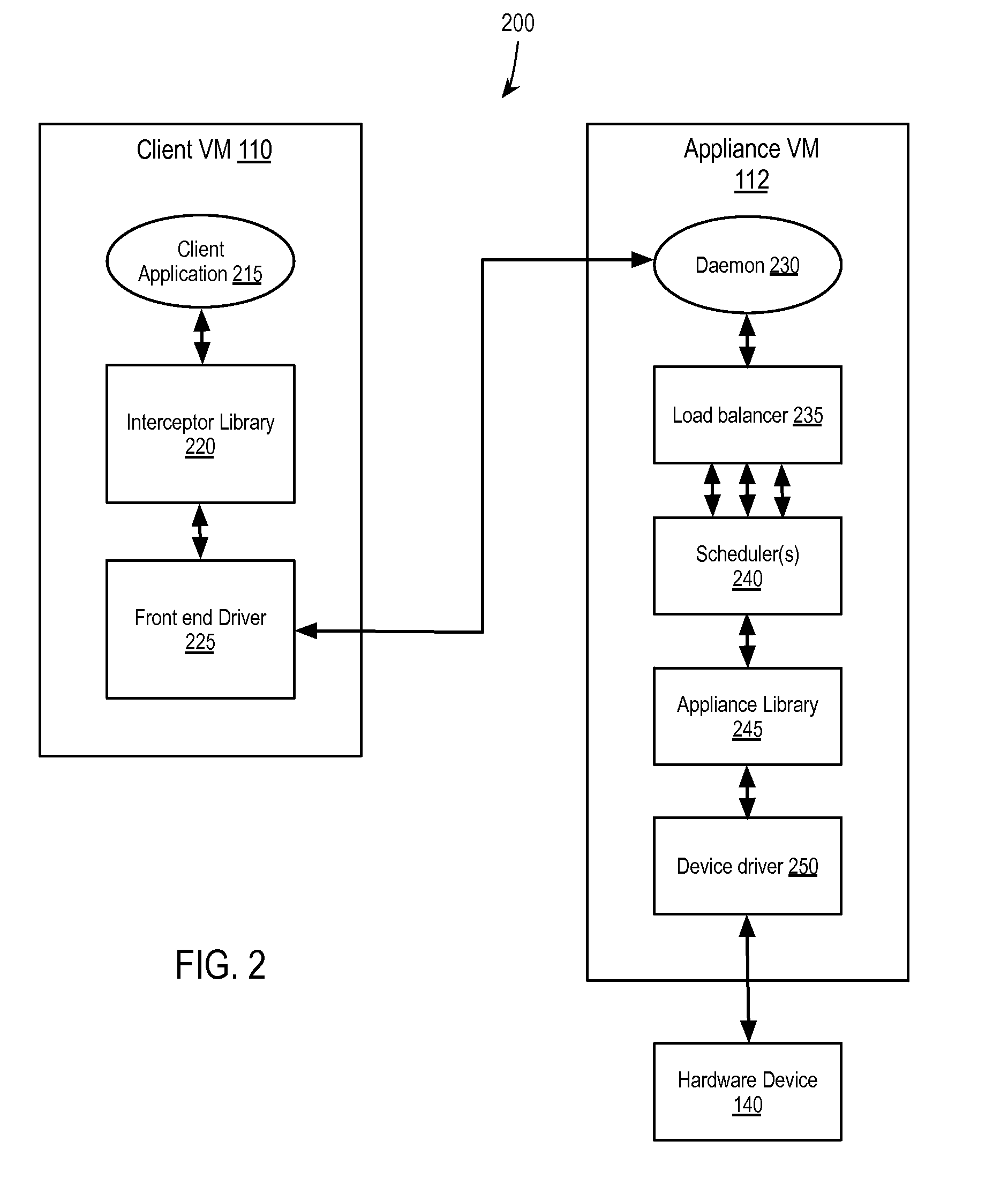
High-performance processing in a virtualization environment
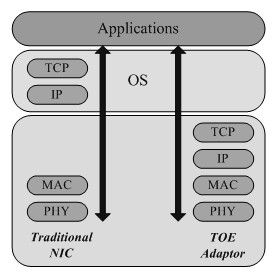
ActiveUS20140359614A1Software simulation/interpretation/emulationMemory systemsTransmission protocolVirtualization
Exemplary methods, apparatuses, and systems include a client virtual machine processing a system call for a device driver to instruct a physical device to perform a function and transmitting the system call to an appliance virtual machine to execute the system call. The client virtual machine determines, in response to the system call, that an established connection with the appliance virtual machine has switched from a first protocol to a second protocol, the first and second protocols including a high-performance transmission protocol and Transmission Control Protocol and Internet Protocol (TCP / IP). The client virtual machine transmits the system call to the appliance virtual machine according to the second protocol. For example, the established connection may switch to the second protocol in response to the client virtual machine migrating to the first host device from a second host device.
Owner:VMWARE INC
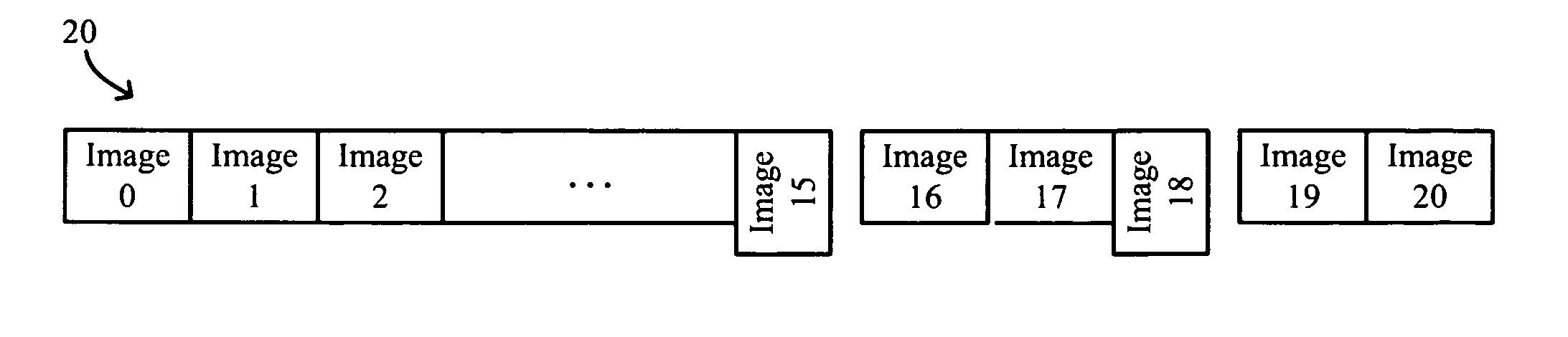
Transferring, processing and displaying multiple images using single transfer request
ActiveUS7890858B1Digital data information retrievalSpecial data processing applicationsWeb browserComputer graphics (images)
Systems and methods for transferring, processing and displaying multiple images using a single transfer request such as a Transfer Control Protocol / Internet Protocol (TCP / IP) transfer request are disclosed. The method may generally include requesting a document, e.g., an HTML document, that references a composite image containing multiple image portions, splitting the composite image into the multiple image portions, determining a layout of the image portions in a client browser, e.g., a web page browser, and laying out the image portions in the client browser according to the determined layout. The splitting of the composite image into the multiple image portions may utilize Cascading Style Sheets (CSS), e.g., using a CSS clip function for each image portion, and may use absolute positioning of the image portions within the composite image. The determining the layout and the laying out of the multiple image portions may be implemented utilizing JavaScript.
Owner:GOOGLE LLC
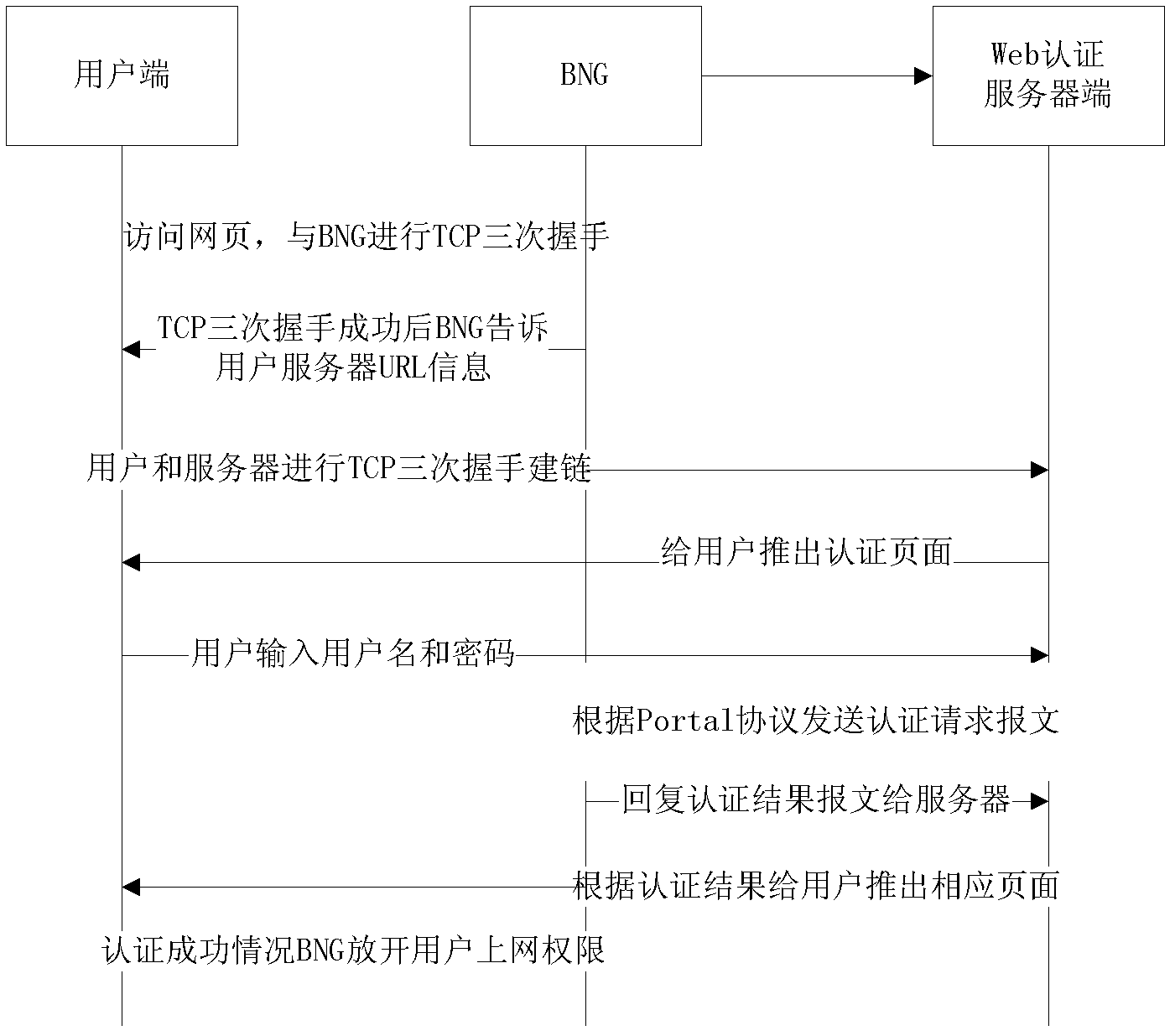
Method and device for releasing transfer control protocol resources
The invention provides a method and a device for releasing transfer control protocol (TCP) resources. The method comprises the steps as follows: after three times of handshake connection between a band net gate (BNG) and user equipment (UE), the BNG sends a detection message to the UE; the BNG acquires the receiving status of the response message from the UE, wherein the response message is the response message of the detection message; and the BNG releases the TCP resources occupied by the UE according to the acquired receiving status. By adopting the technical scheme provided by the invention, the technical problem that the WEB identification of a normal user is affected because a technical scheme for affectively releasing the TCP resources is unavailable in a relative technique is solved, so that limited TCP resources is effectively utilized, and the normal user can normally carry out WEB identification.
Owner:ZTE CORP
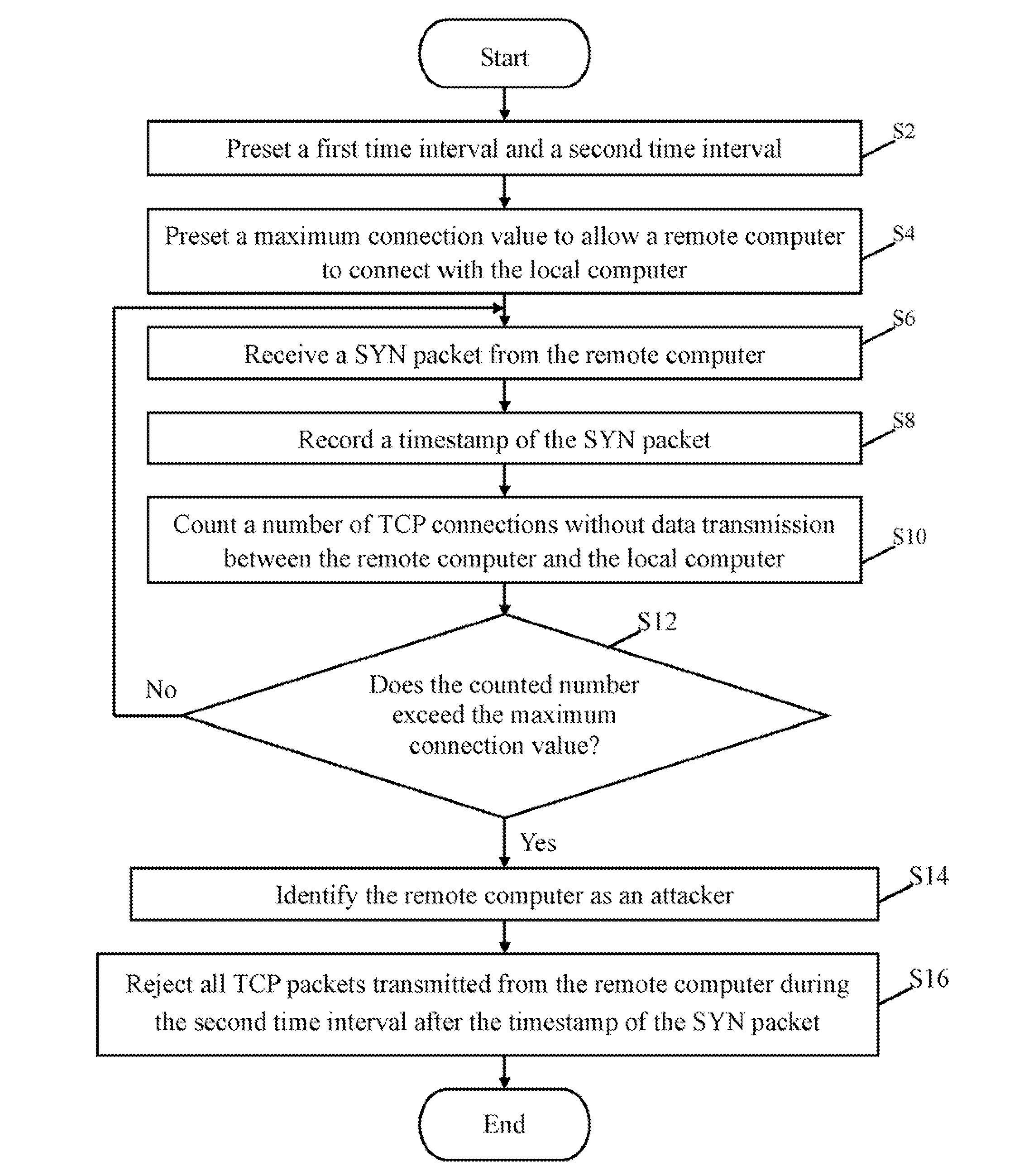
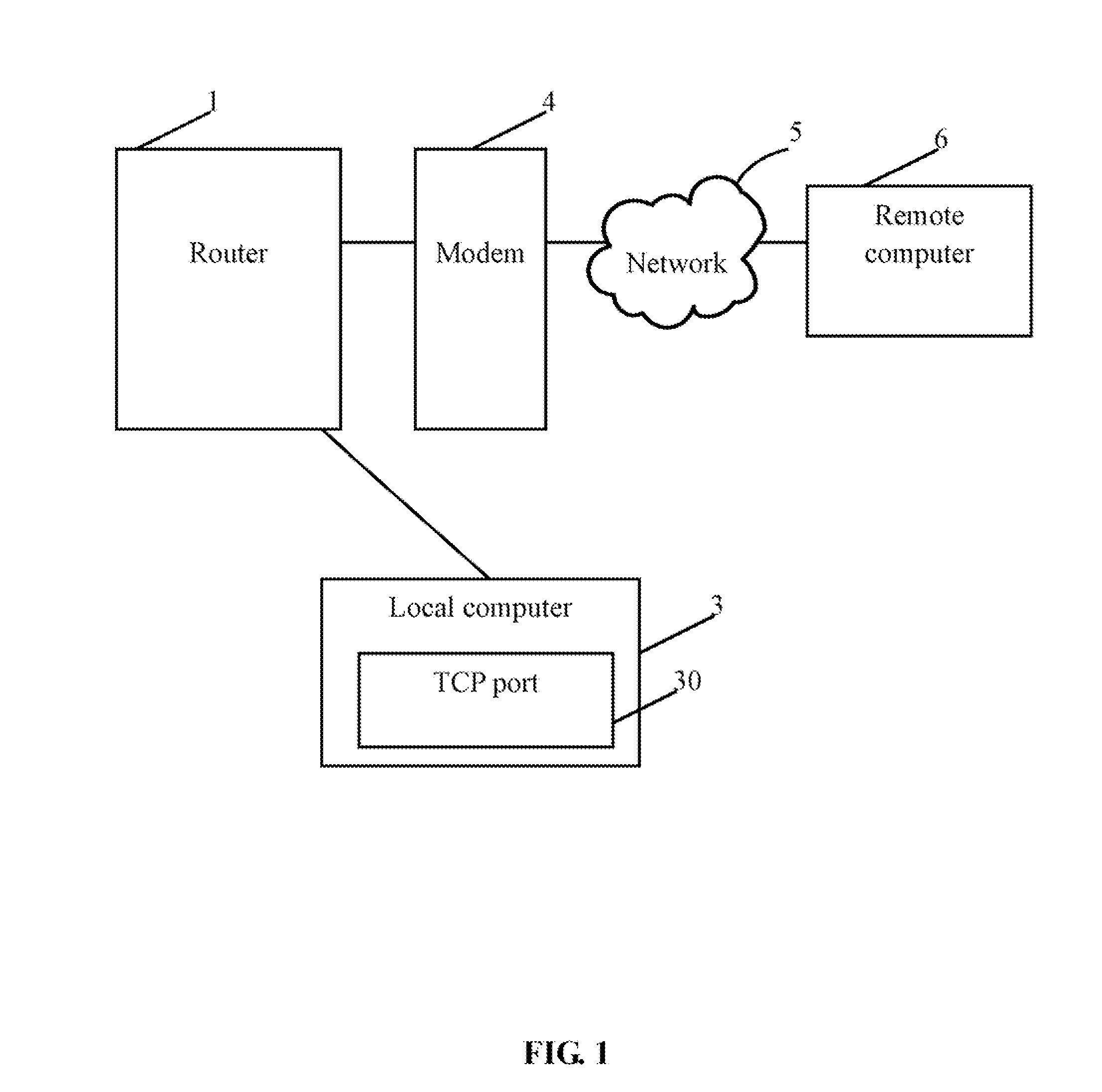
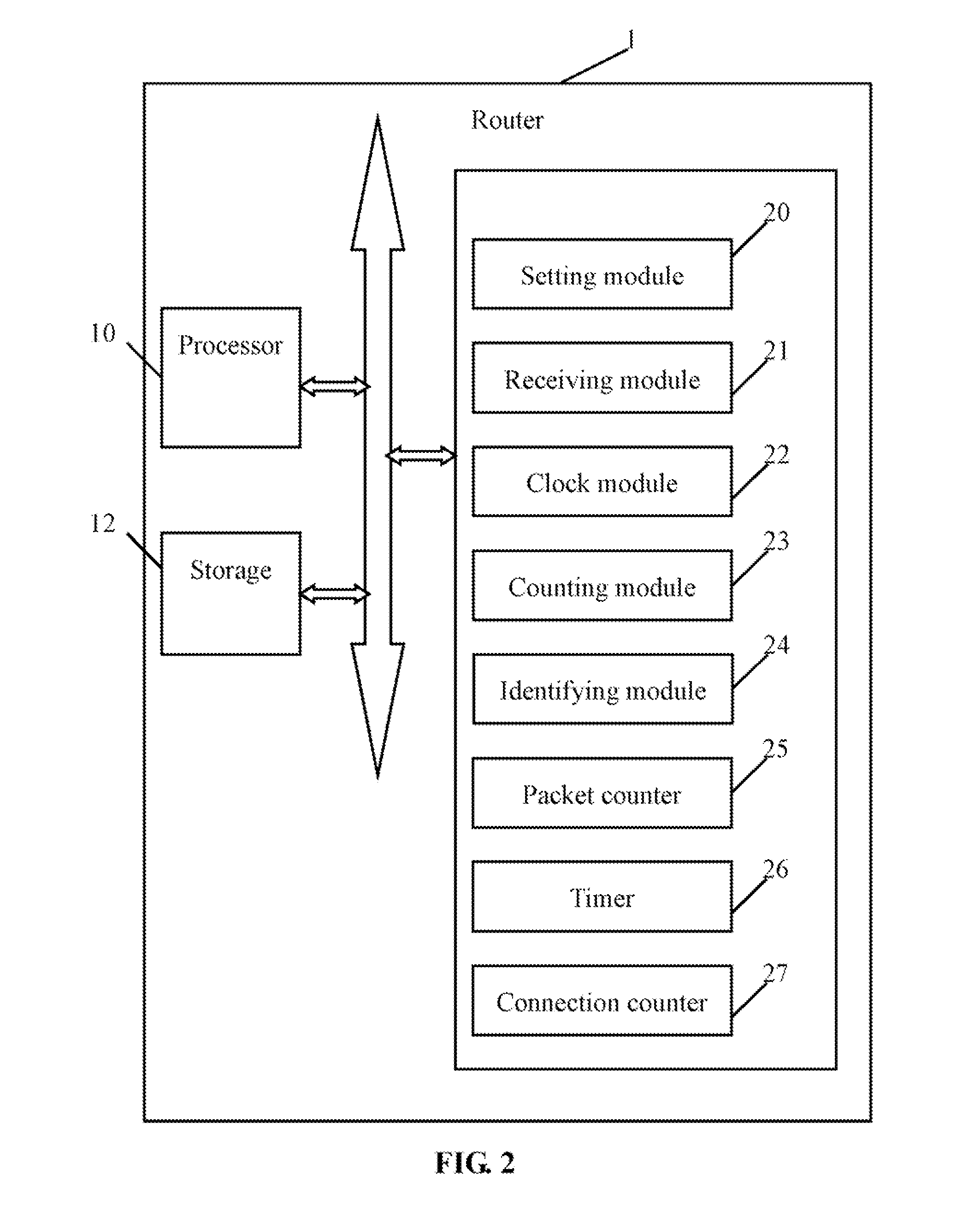
Router and method for protecting TCP ports utilizing the same
InactiveUS20110093946A1Computer security arrangementsMultiple digital computer combinationsTimestampNetwork packet
A router and method for protecting transfer control protocol (TCP) ports of a local computer include receiving a SYN packet from a remote computer, recording a timestamp of the SYN packet, and counting a number of suspicious TCP connections established during a first time interval before the timestamp of the SYN packet. The router and method further include identifying the remote computer as an attacker if the counted number exceeds a preset maximum connection value, and rejecting all TCP packets transmitted from the remote computer during the second time interval after the timestamp of the SYN packet.
Owner:HON HAI PRECISION IND CO LTD
Web access cloud architecture and access method
ActiveCN102143218AImprove processing efficiencyImprove securityTransmissionWeb serviceStructure of Management Information
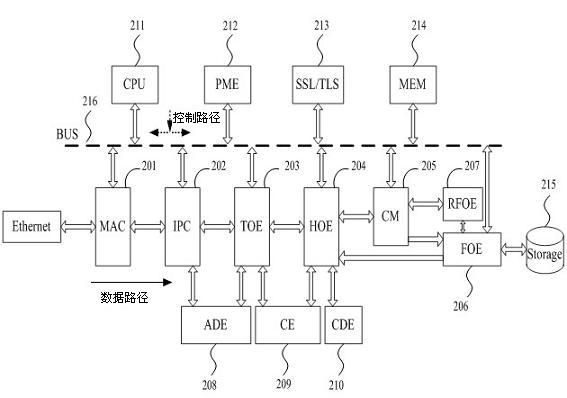
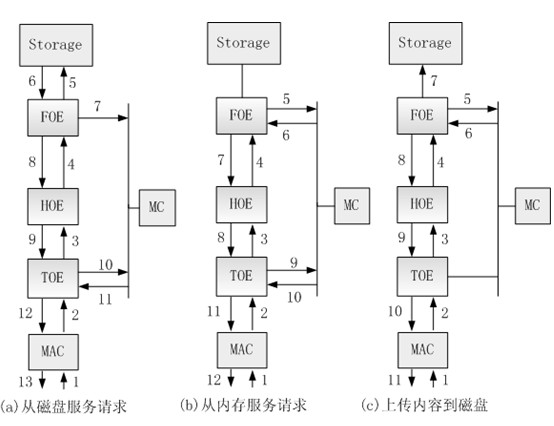
The invention relates to a web access cloud architecture and an access method. The web access cloud architecture comprises an IP (internet protocol) packet classification engine IPC, a DoS protection engine ADE, an SSL (security socket layer) / TLS (transport layer security) engine, a TCP (transfer control protocol) / IP offload engine TOE, an HTTP (hypertext transfer protocol) offload engine HOE, a file system offload engine FOE, a remote file system offload engine RFOE, a power consumption management engine PEM, a content management engine CM, a CryptoEngineCE and a compression / decompression engine CDE, and also comprises control storage components: a CPU (central processing unit), an on-chip bus and an on-chip memory, wherein the on-chip bus is connected with the CPU, the on-chip memory, the power consumption management engine PEM and the IP packet classification engine IPC, the TCP / IP offload engine TOE, the HTTP offload engine HOE, the content management engine CM, the file system offload engine FOE and the SSL / TLS engine, and the CPU controls the components mounted on the on-chip bus, so that the processing efficiency and security of the existing Web server can be greatly improved, and the power consumption is reduced.
Owner:SHANGHAI REDNEURONS +1
Communication standard of automated testing for monitoring system
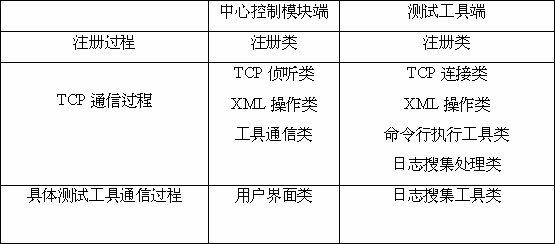
The invention discloses a communication standard of automated testing for a monitoring system, which is characterized in that: a test tool is communicated with a central control module, firstly, the test tool is registered, and then establishes a TCP (Transfer Control Protocol) communication with the central control module, and is finally interacted with a specific command of a user interface. The TCP communication flow of the central control module and the test tool is divided into three layers for processing: for an XML (extensible markup language) operation layer, when sending data, the XML operation layer receives the specific command of a tool communication layer, the specific data is packaged as XML data, and then the XML data is transferred to a TCP interception layer for sending; when receiving the data, the XML operation layer receives the original XML data of the TCP interception layer to parse the original XML data to get a specific result, and then transfers the specific result to the tool communication layer for processing; and the cross-layer operation is realized by callback and call between the layers. The communication standard of automated testing for the monitoring system is used for intensively controlling a plurality of test tools to concurrently work, accordingly, the test speed is quickened up, the test quality is improved, and the object of faster and better development of software products is achieved.
Owner:NALONG SUZHOU INFORMATION TECH
Method for generating an annotated network topology
A method of generating an annotated network topology of a network is described. The method includes; deriving a network topology by performing a route tracing utility between each pair of endpoints to determine the route taken by packets; initially annotating each network path with an initial value; determining the available bandwidth of a path connecting a pair of endpoints by performing Transfer Control Protocol (TCP) flows between the pair of endpoints; identifying a bottleneck link in the network path, and annotating all edges to generate an annotated network topology wherein available bandwidth annotation of links inside the network is determined using end-to-end network measurements.
Owner:INT BUSINESS MASCH CORP
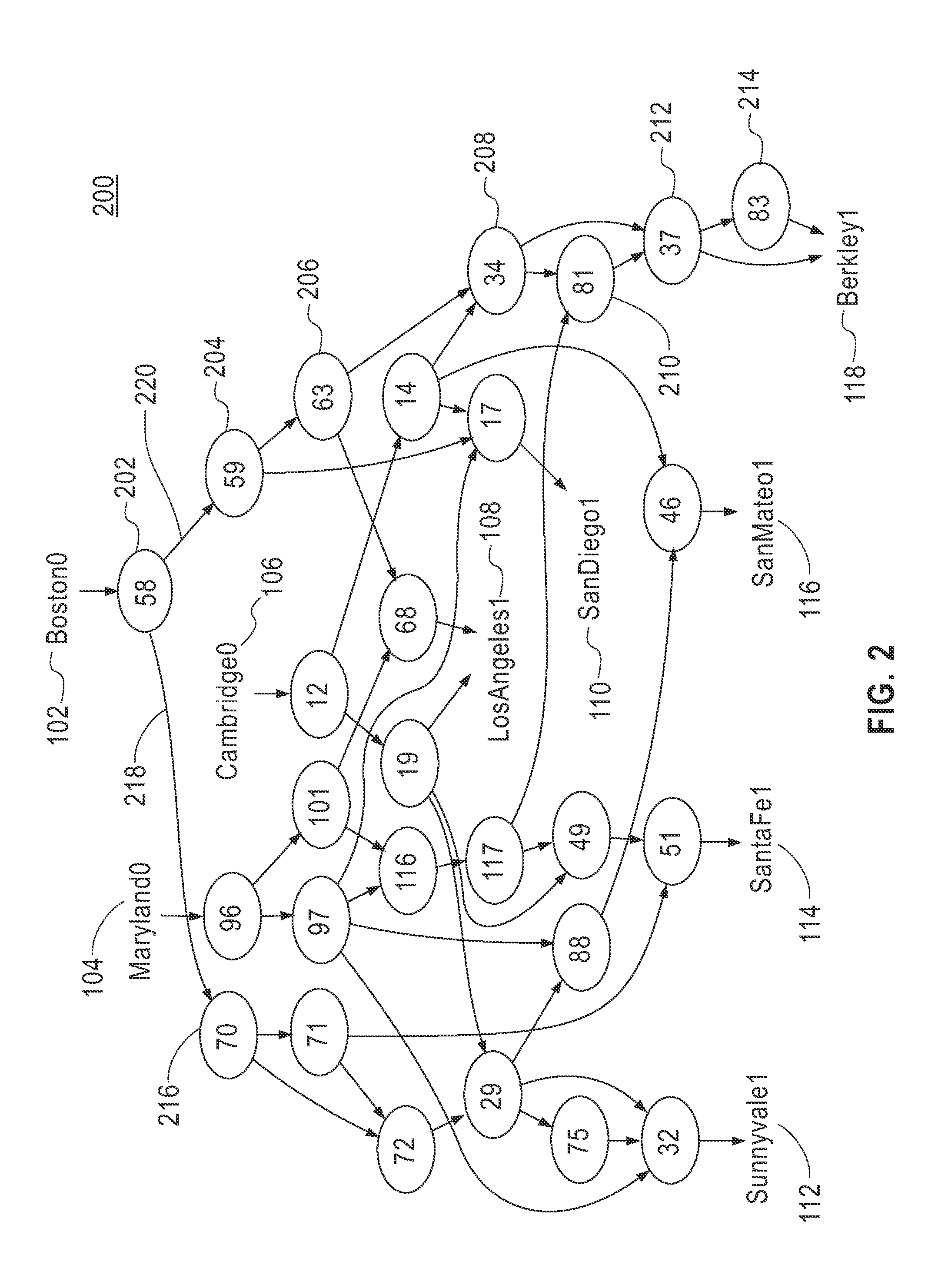
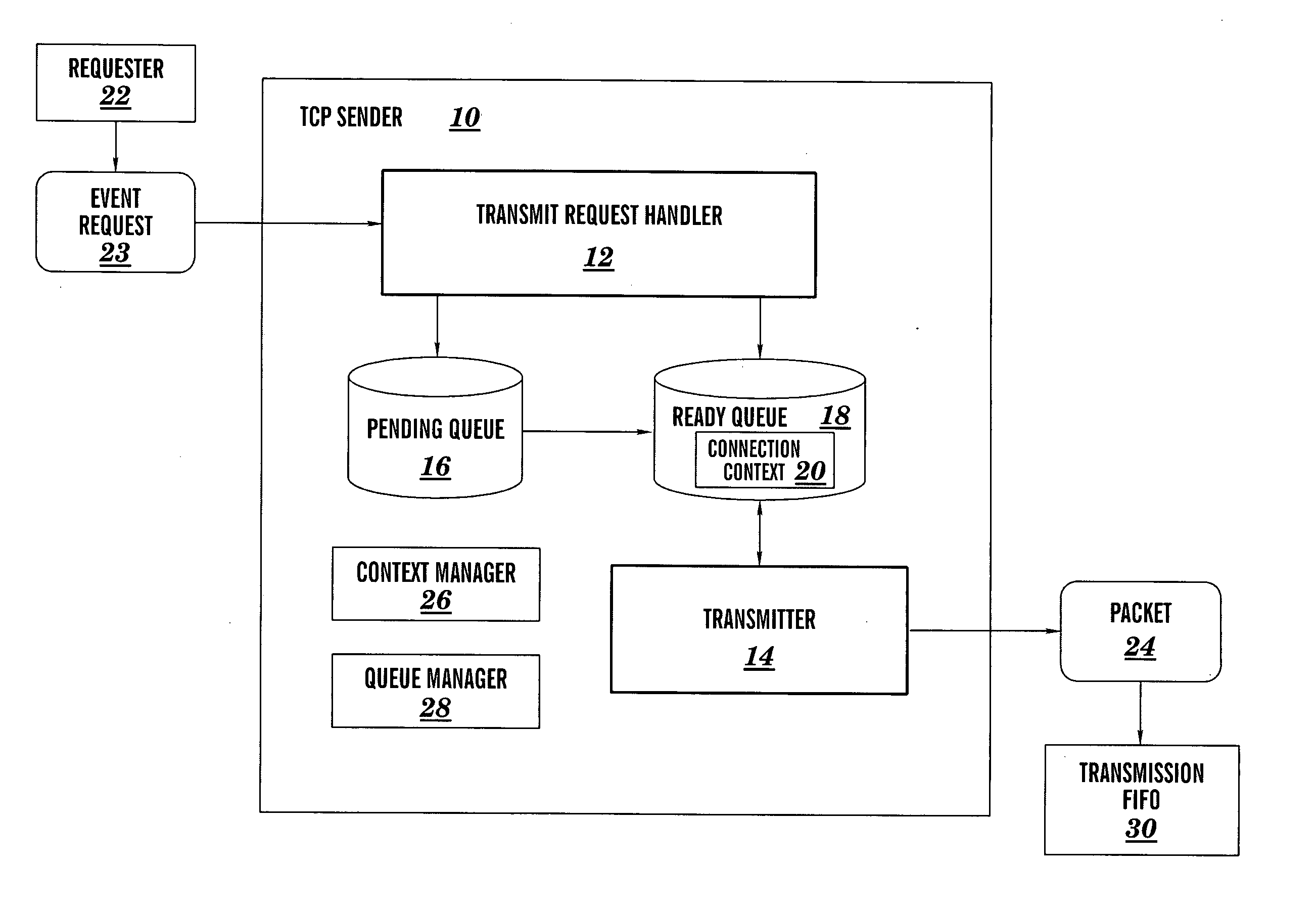
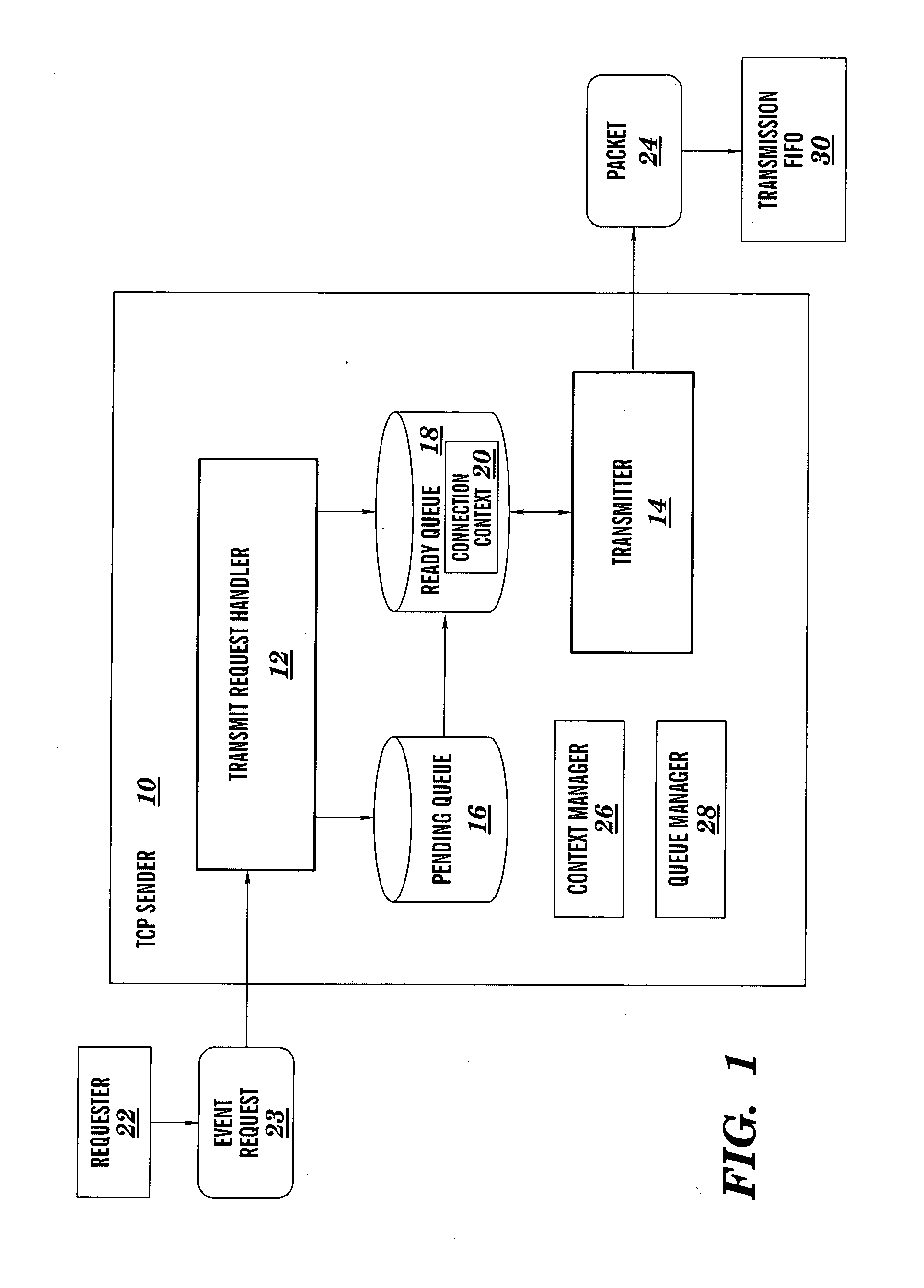
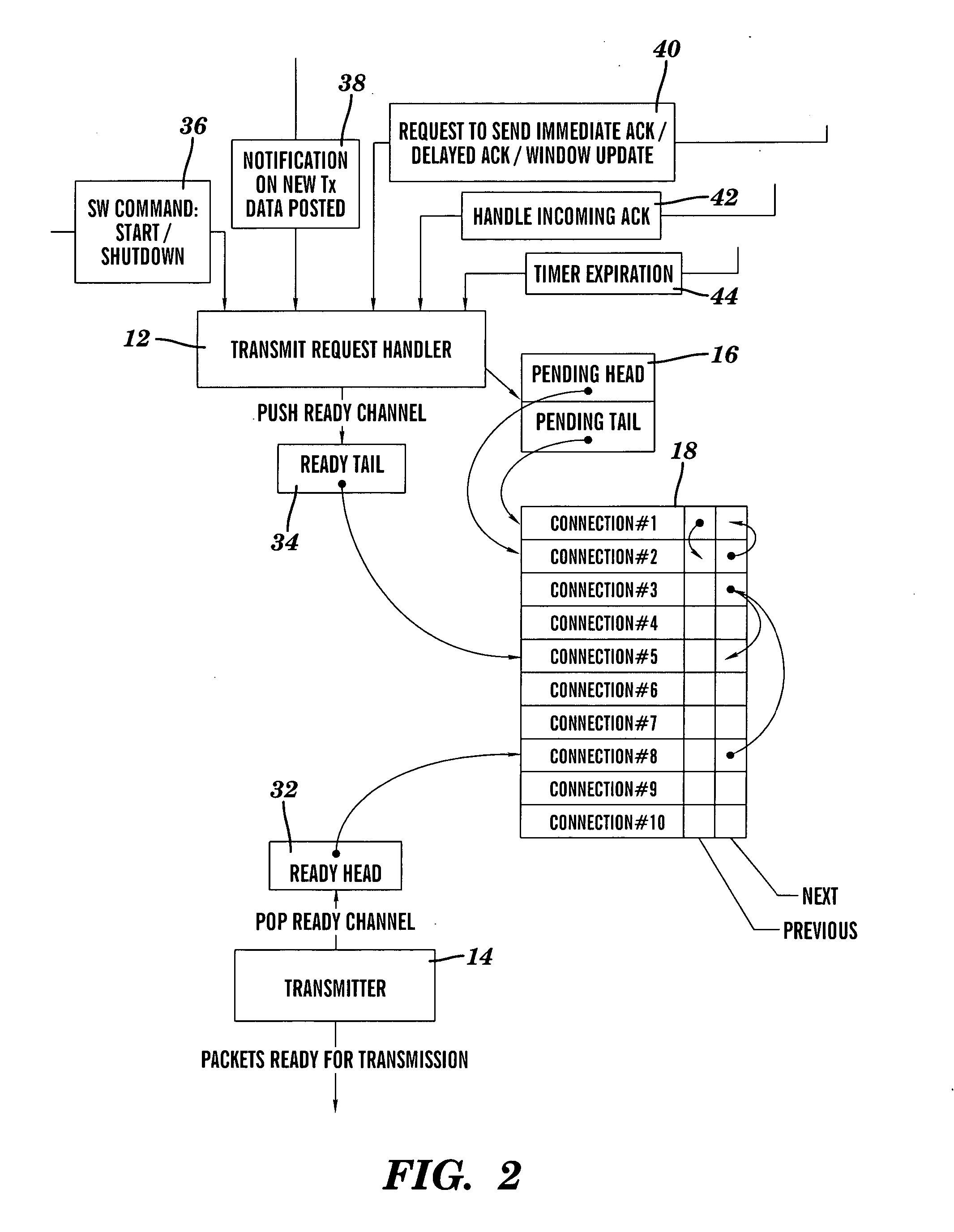
Parallel TCP sender implementation
InactiveUS20050117582A1Digital computer detailsData switching by path configurationData packTransfer system
A system and method for providing parallel implementation of a TCP sender comprising a transmit request handler and a transmitter. A transfer control protocol (TCP) transmission system is provided, comprising: a transmit request handler that receives request events, records the event information into a connection context and either schedules a connection in a ready queue or places the connection in a pending queue; and a transmitter that operates in parallel with the transmit request handler, wherein the transmitter dequeues connections from the ready queue and prepares packets for transmission based on information recorded in the connection context.
Owner:IBM CORP
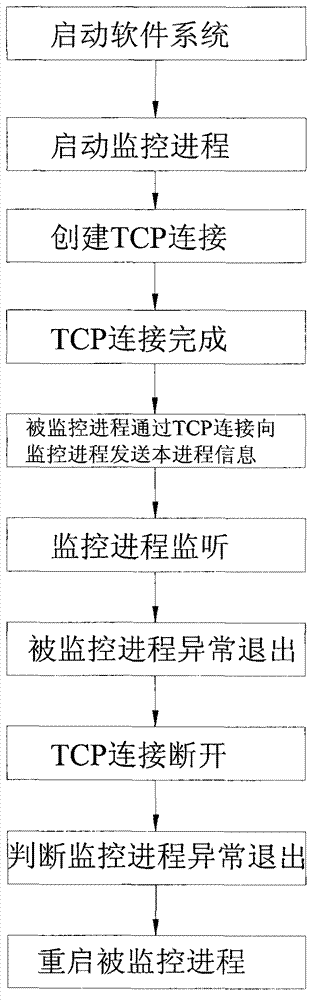
Method for implementing software watchdog in software system
The invention discloses a method for monitoring the stability of a software system, and particularly relates to a method for implementing a software watchdog in the software system. The method comprises the following steps of: creating TCP (Transfer Control Protocol) connection, receiving a TCP connection request of a monitored process; sending the process information to a monitoring process through the TCP connection by the monitored process, and monitoring the state of TCP connection between the monitoring process and all the monitored processes by the monitoring process; when the monitoring process abnormally exits, disconnecting the corresponding TCP connection, and determining whether the corresponding monitored process abnormally exits or not; and restarting the monitored process, so that the software system returns to normal. The method provided by the invention has the following beneficial effects that the method that the system state is monitored by utilizing the TCP connection in the software system is adopted, so that the system automatically restores when the process truly and abnormally exits, and thus the stability of the software system is greatly improved, and the method can be implemented very simply and reliably by using the standard TCP connection.
Owner:TAICANG T&W ELECTRONICS CO LTD
Method and system fpor transferring data to improve responsiveness when sending large data sets
ActiveUS20170078205A1Without impacting responsivenessReliable estimateData switching networksWide areaTimestamp
Most of the internet traffic today is carried out via the Transmission Control Protocol (TCP). The main advantage of TCP is that it provides reliable data transfer to the application layer and simplifies programming. The protocol maximizes data throughput but may also lead to noticeable transmission delay in wide area networks (WAN). A client-server based medical image viewing system is disclosed that achieves high data throughput over TCP without impacting responsiveness. Special timestamp messages inserted into the data stream allow the system to detect situations where network latency increases noticeably and to obtain a reliable estimate of sustained transfer bandwidth. The system applies a feedback scheme that avoids network delays by limiting send bandwidth. In addition other parameters, in particular image compression settings, are dynamically adjusted depending on current network quality.
Owner:PME IP
Method for realizing firewall in household gateway
The invention discloses a method for realizing a firewall in a household gateway, and relates to a method preventing an internet access in the manner of detecting the internet access through an SPI (stateful packet inspection). The SPI-typed firewall means that each connecting information (including socket pairs which comprises a source address, a destination address, a source port and a destination port, a protocol type, a TCP (transfer control protocol) connection state, an overtime hour and the like) is detected for judging whether the firewall filters a data packet. By the adoption of the method, besides finishing the work of packet filtering of a simple packet filtering firewall, a table of a tracing and connecting state is maintained in the own internal memory, thus the firewall is provided with higher safety compared with the simple packet filtering firewall.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
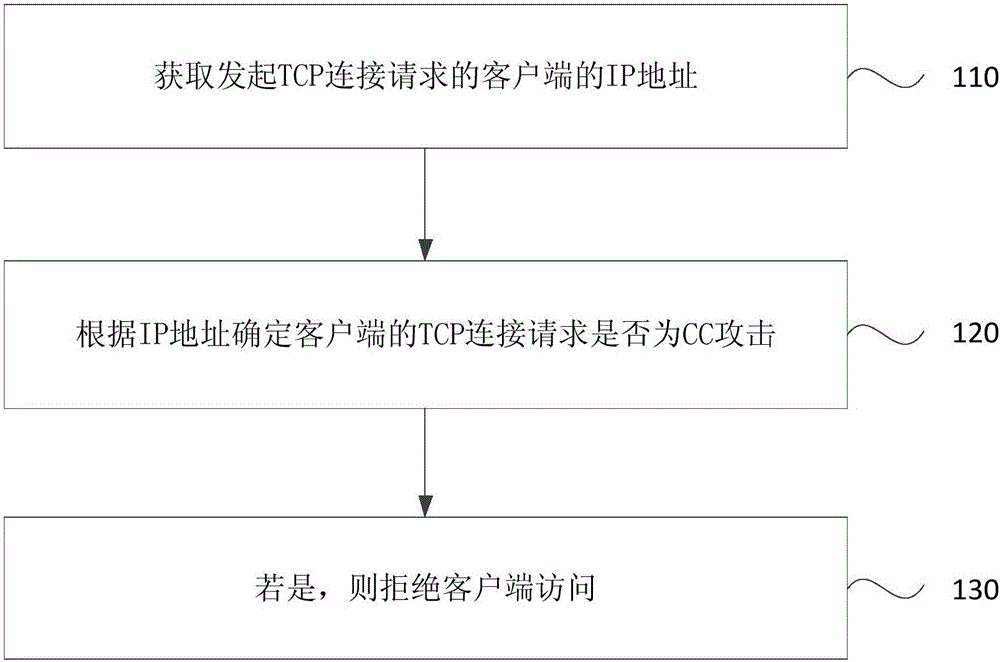
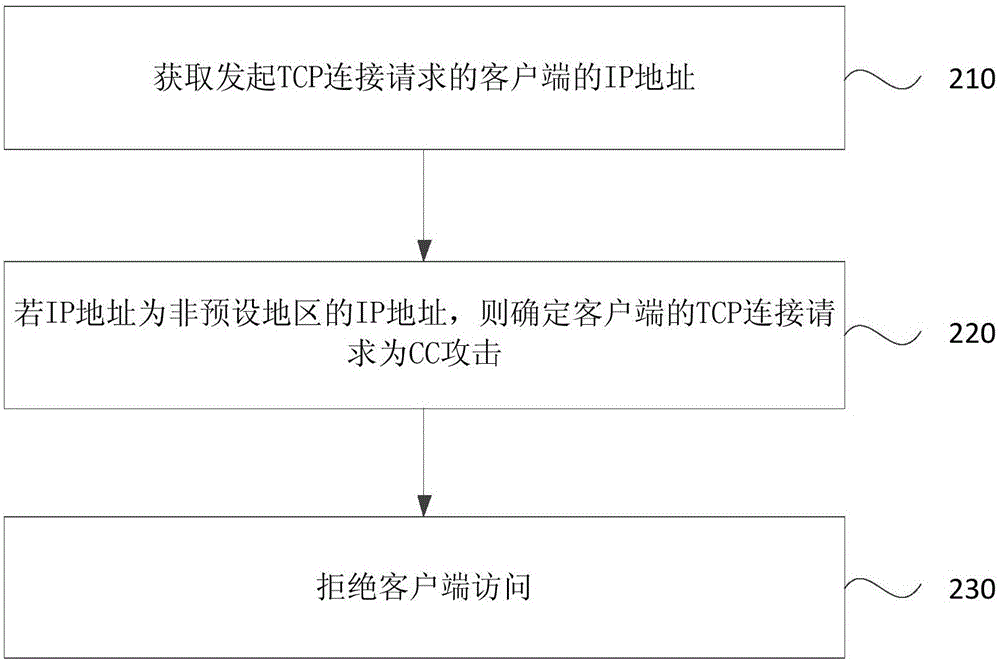
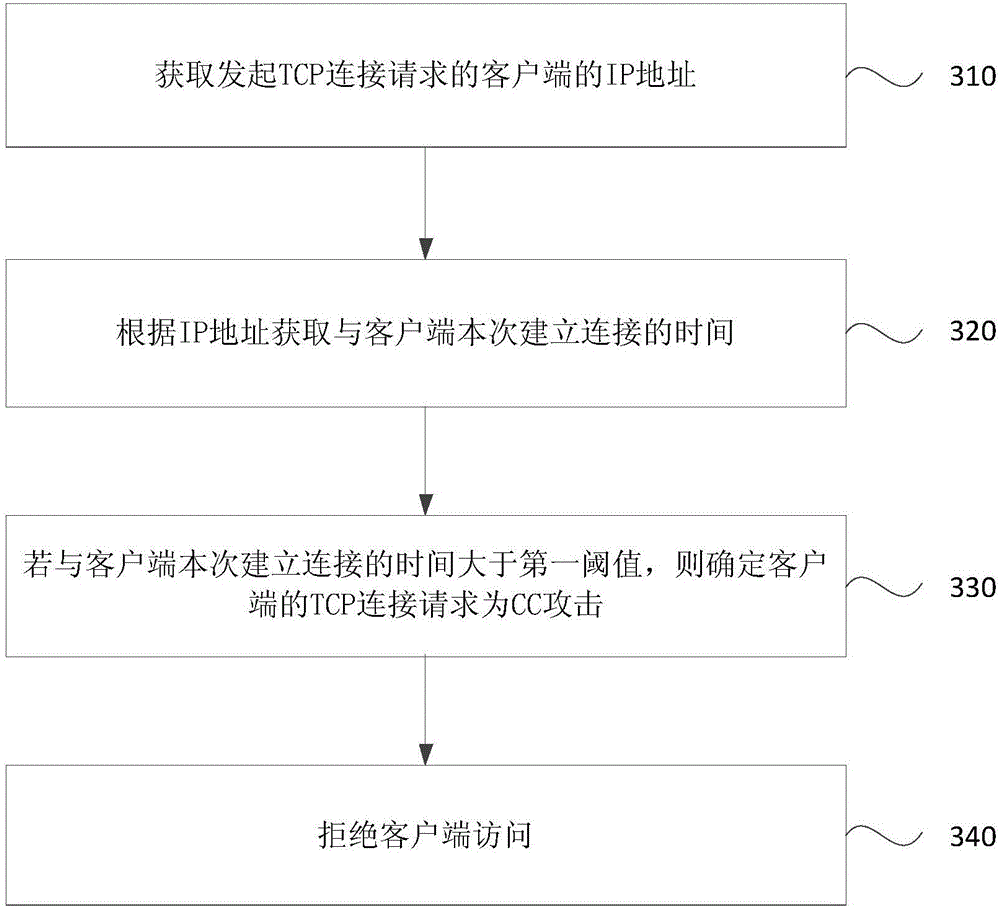
CC (Challenge Collapsar) attack protection method and device
InactiveCN106330911AImprove the protective effectReduce usageTransmissionIp addressProtocol for Carrying Authentication for Network Access
The invention discloses a CC (Challenge Collapsar) attack protection method and device. The method comprises the steps of obtaining IP (Internet Protocol) address of a client which initiates a transmission control protocol TCP connection request; determining whether the TCP connection request of the client is a CC attack or not according to the IP address; and rejecting an access of the client if the TCP connection request of the client is the CC attack. According to the technical solution provided by the embodiment of the method and the device, the request initiated by an abnormal client can be recognized and filtered, thereby rejecting the access of the client, reducing the use of server resources and improving a CC attack protection effect.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
Method for intercepting control data, in particular quality of service data, and associated device
InactiveUS7478155B2Error preventionFrequency-division multiplex detailsQuality of serviceReal-time data
A device comprises interception means (2) capable, in the case of transfer of data packets between at least two remote terminals (Tij-k), via a communications network, of intercepting at least certain of the control packets during the transfer, and of determining amongst the intercepted control packets those which are formatted according to a chosen real-time data transfer control protocol, and management means (3) capable of duplicating at least part of each intercepted control packet, and of generating data, representing the duplicated part, intended to be communicated to control means (1) located in a control application (S) of the network.
Owner:ALCATEL LUCENT SAS
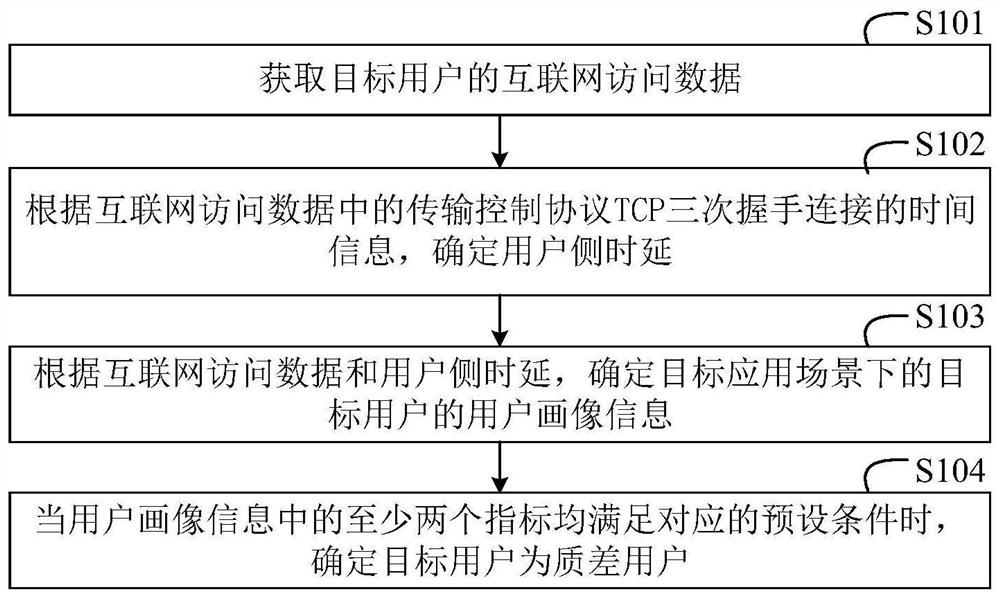
User identification method, device and equipment and computer storage medium
InactiveCN111953563AImprove positioning accuracyResourcesData switching networksData packTime information
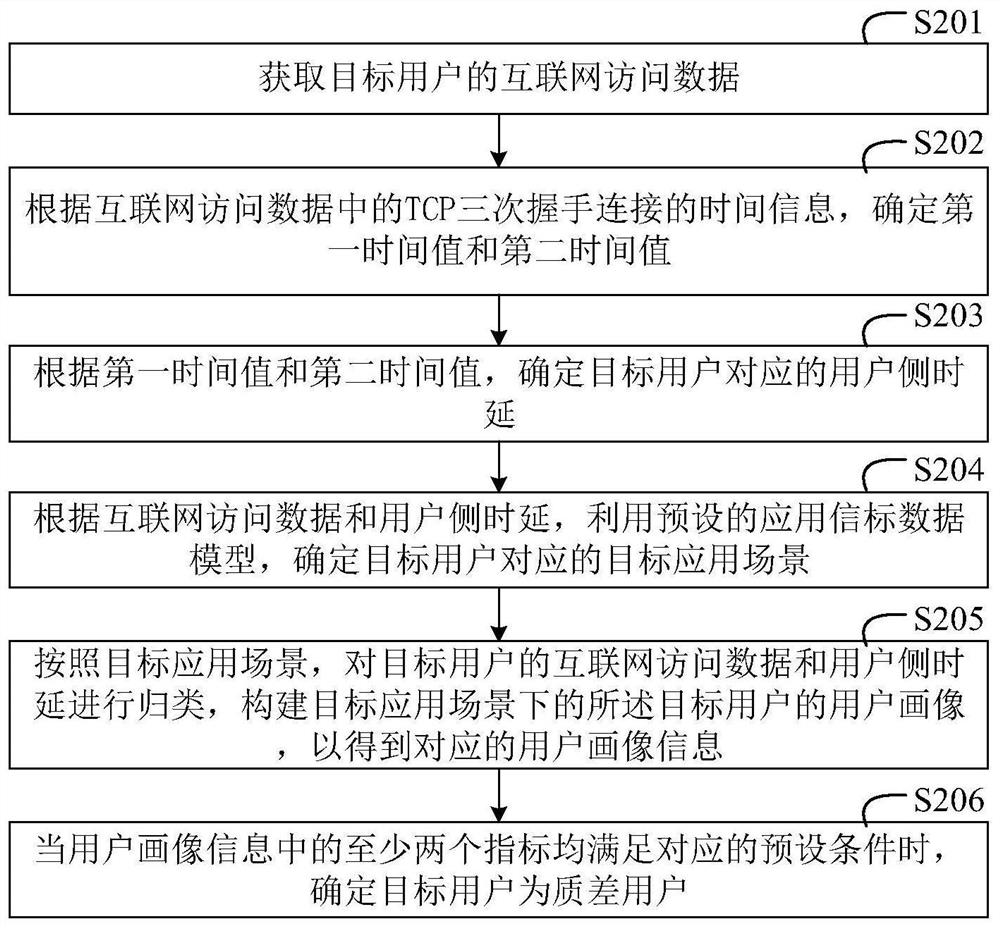
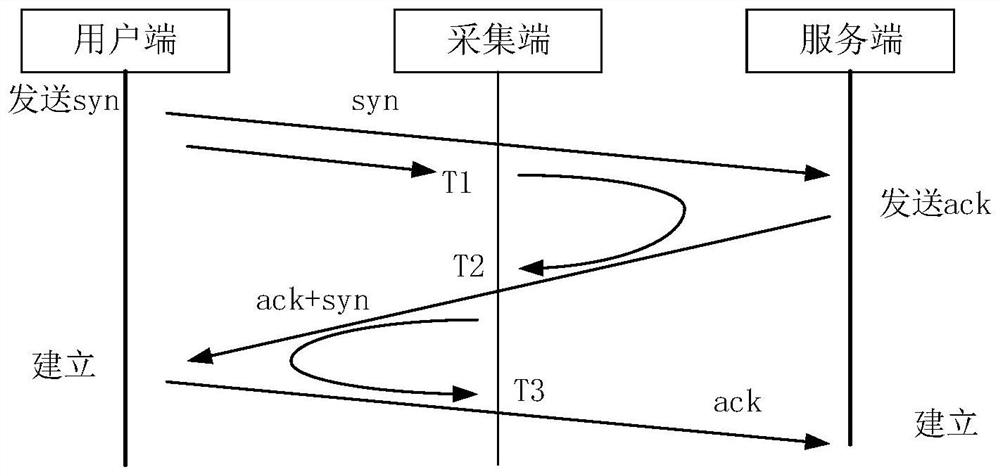
The invention discloses a user identification method, apparatus and device, and a computer storage medium, and the method specifically comprises the steps: obtaining Internet access data of a target user, the Internet access data comprising at least two indexes; determining user side time delay according to time information of three-way handshake connection of a transmission control protocol TCP in the Internet access data; determining user portrait information of the target user in the target application scene according to the Internet access data and the user side time delay, the user portrait information comprising at least two indexes; and when at least two indexes in the user portrait information meet corresponding preset conditions, determining that the target user is a poor-qualityuser. According to the embodiment of the invention, the network quality condition of the user side can be deeply mined, and the positioning accuracy of the user with poor network perception quality isimproved.
Owner:CHINA MOBILE GROUP JIANGSU +1
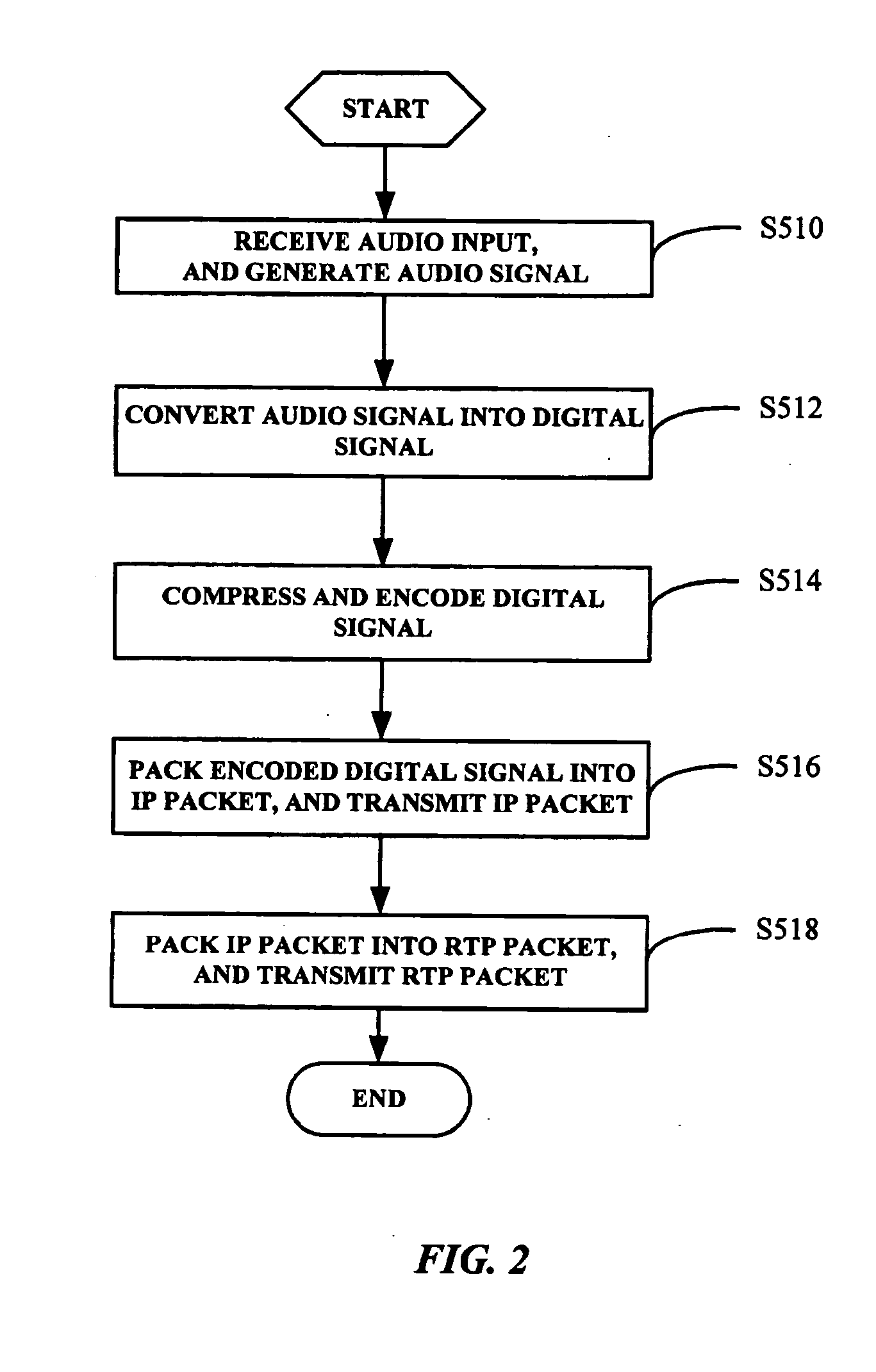
Network telephony system with enhanced interconversion of audio signals and IP packets
InactiveUS20050013305A1Reliable and low-cost communicationError preventionFrequency-division multiplex detailsSession Initiation ProtocolBoard support package
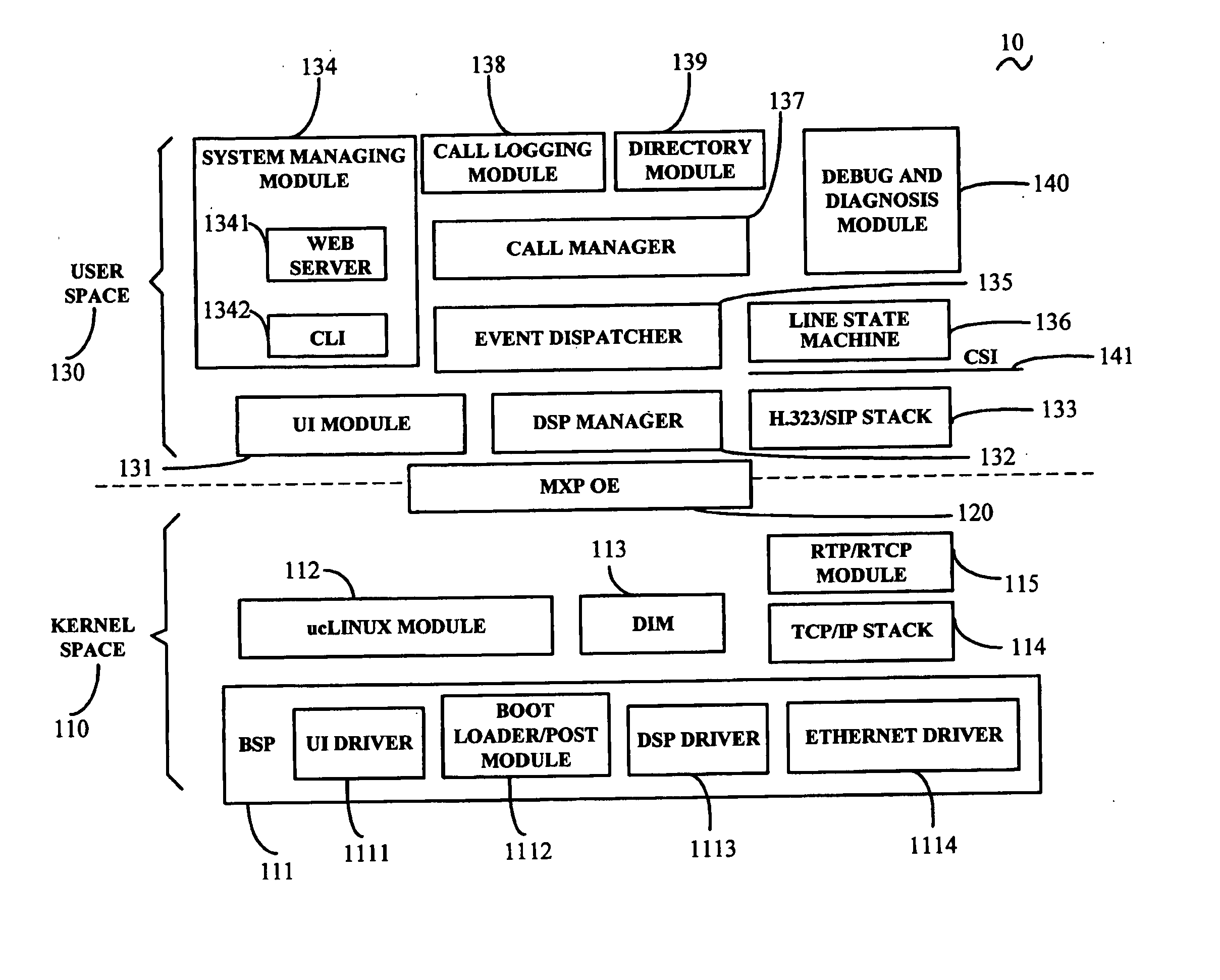
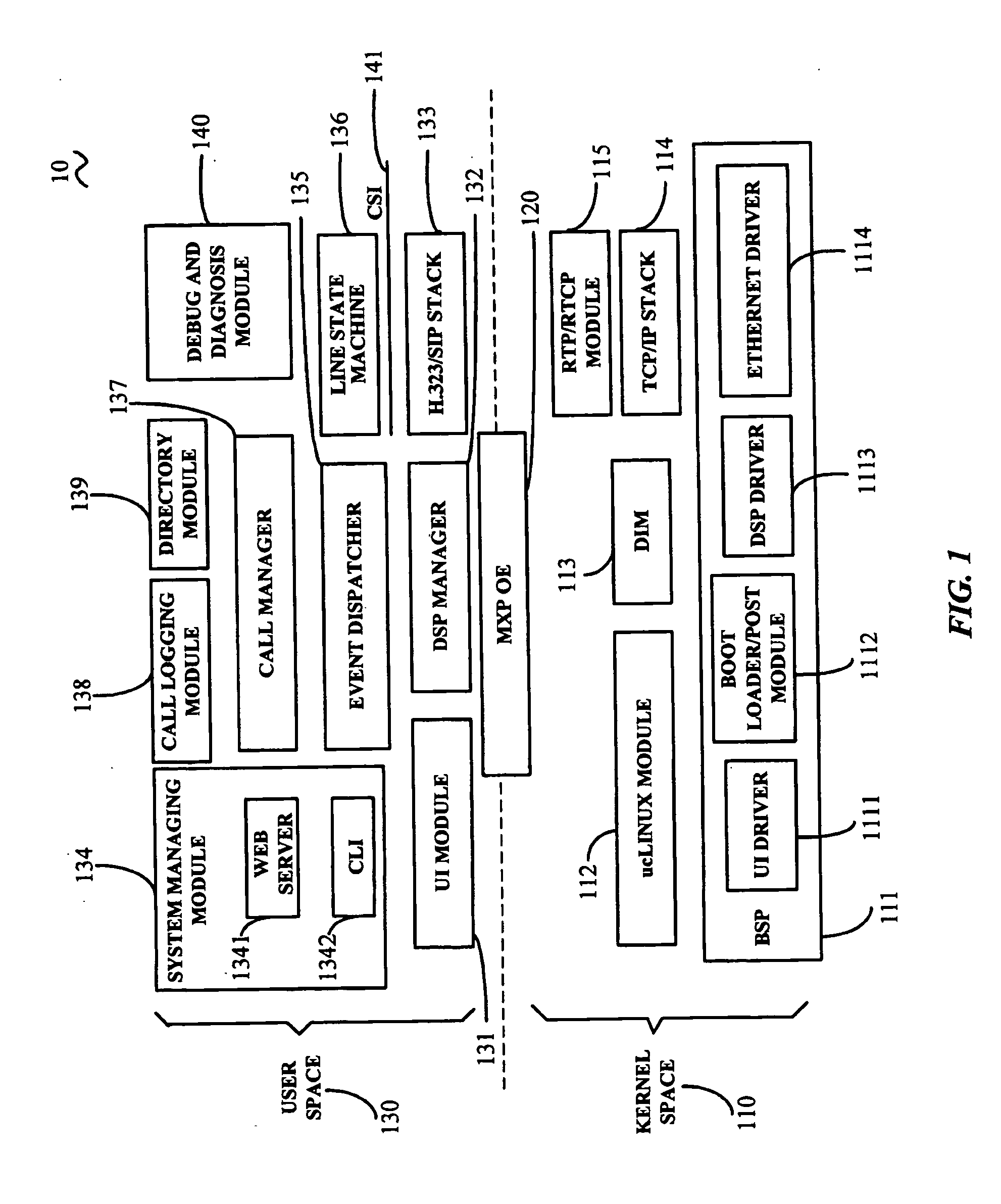
A telephony system (10) for communication over a network includes a kernel space (110), a media express processor operating environment (120) for providing a set of software facilities for task synchronization, and a user space (130). The kernel space includes a board support package (111), a ucLinux module (112), a digital signal processor interface module (113), a transfer control protocol / Internet protocol (TCP / IP) stack (114) for performing TCP / IP, and a real-time transport protocol / real-time transport control protocol module (115). The user space includes a digital signal processor manager (132), an H.323 / session initiation protocol (H.323 / SIP) stack (133) for performing H.323 protocol or SIP, a system managing module (134), an event dispatcher (135), a line state machine (136), a call manager (137), a call logging module (138), and a directory module (139) for storing, editing, searching and removing contact information of users.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
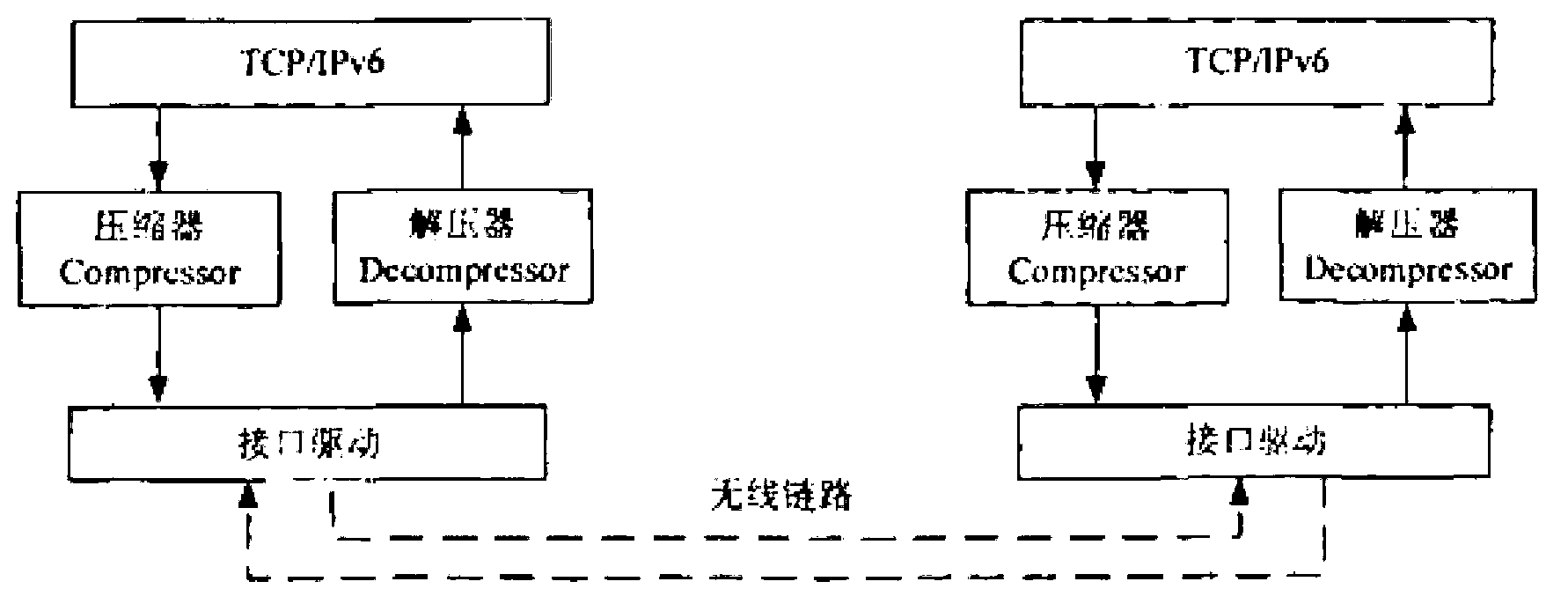
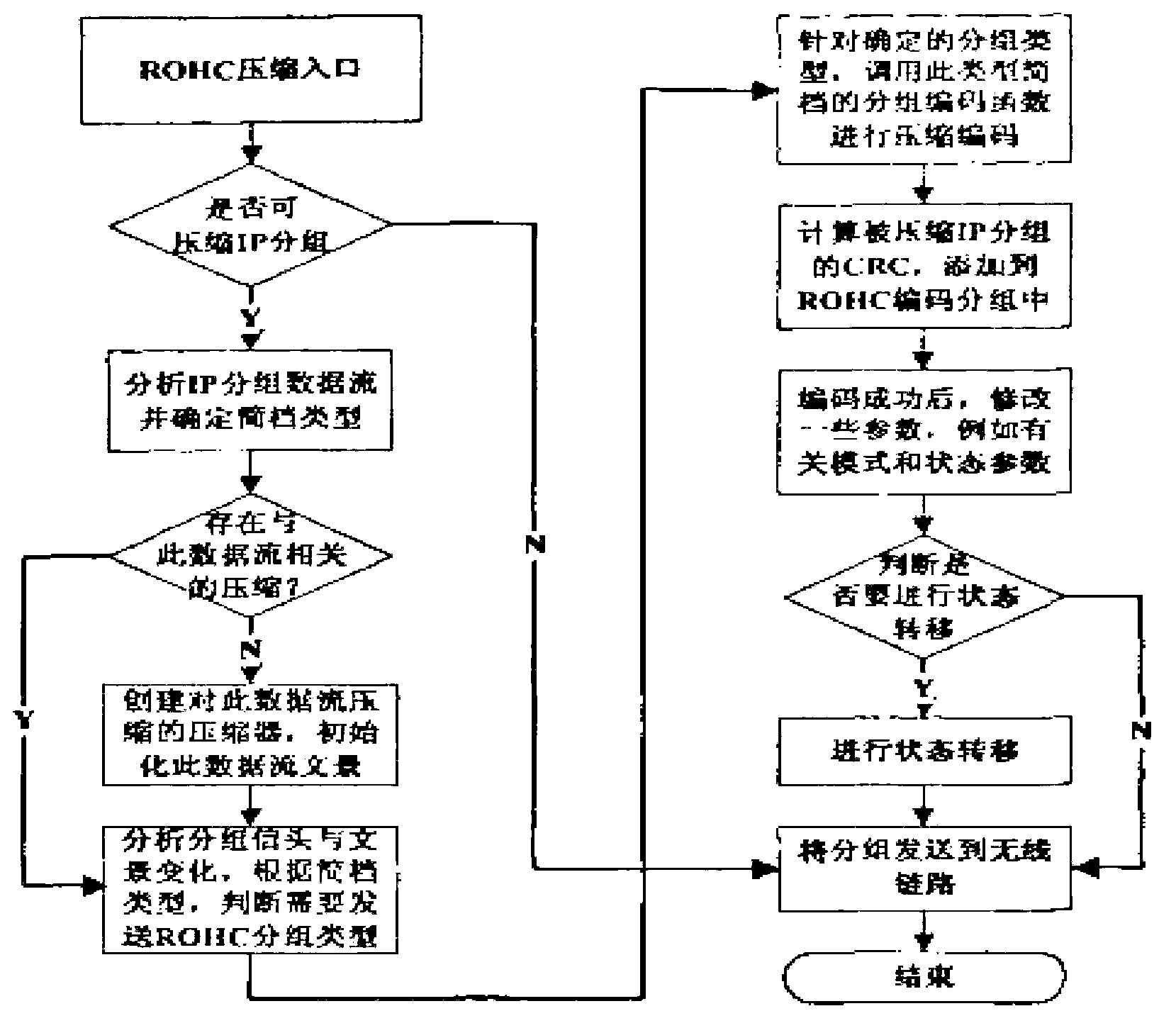
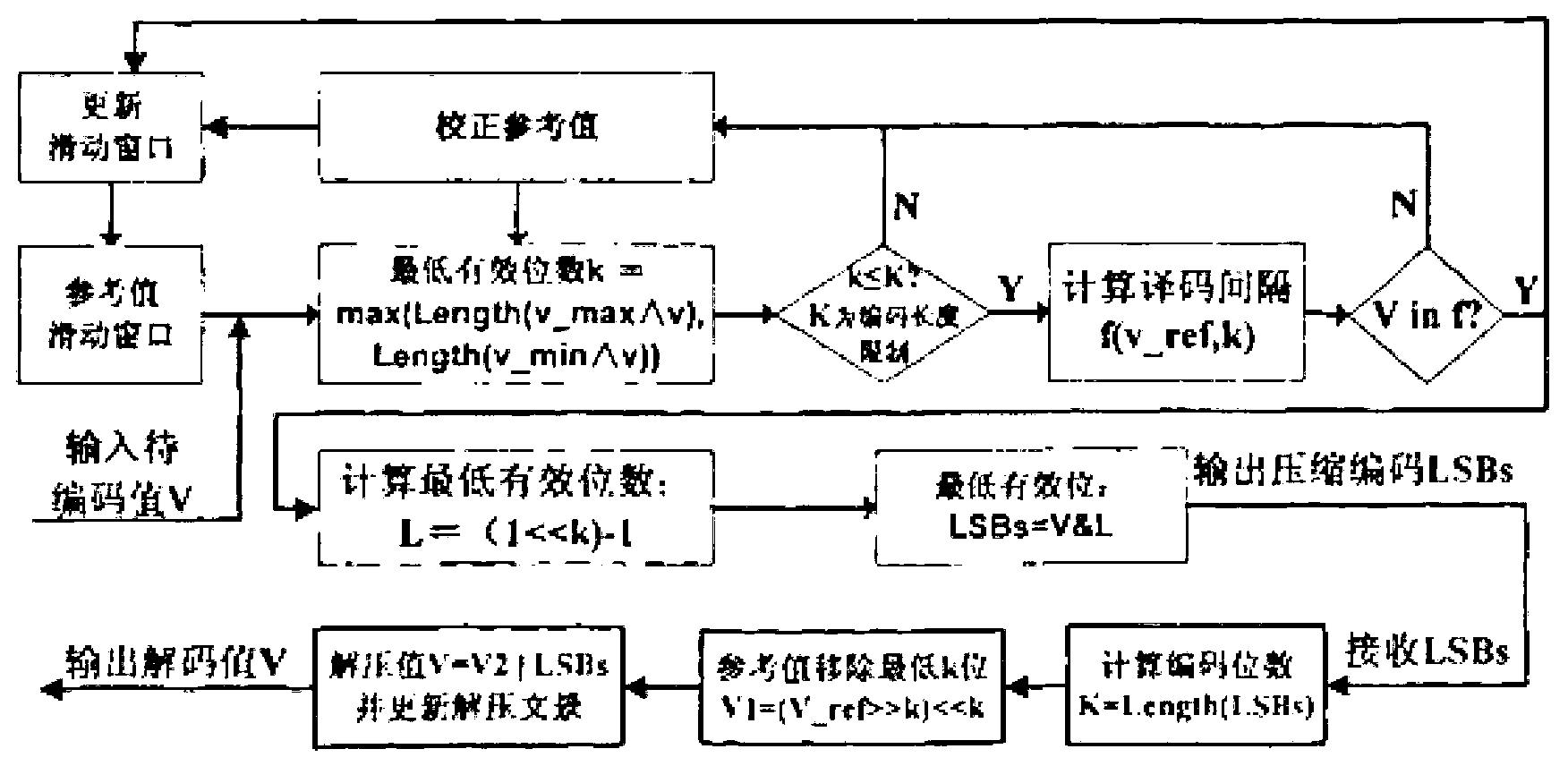
TCP (transmission control protocol) header compression method in wireless IPv6 (internet protocol version 6) network
InactiveCN103067971AParity compressionCalibration functionNetwork traffic/resource managementComputer hardwareInternet protocol suite
The invention discloses a TCP (transmission control protocol) header compression method in wireless IPv6 network, belonging to the technical field of improving the compression ratio and robustness of a wireless link. The invention emphasizes the three compression states, three working modes, W-LSB (window-based least significant bit) algorithm and the like of ROHC (robust header compression). A classification mode of the TCP header field is provided, and the profile of TCP / IP compression is written according to the ROHC profile specification; the sliding window width is dynamically adjusted to adapt to the change characteristics of the wireless link, and performance simulation and analysis are performed on the provided method; a test information source of ROHC is designed to facilitate the writing and test of the TCP / IP compression profile of ROHC; and according to the TCP / IP header compression technology and performance in a wireless IPv6 (internet protocol version 6) network, the imperfection of the ROHC and TCP compression scheme is improved, and the result is verified through a simulation test in a prototype system.
Owner:BEIJING INTERNET INST
Transmission method for multiplexed data flow
InactiveCN101325505AEasy to debugEasy maintenanceSpecial service provision for substationData streamMultiplexer
The present invention provides a transmission method of multiplexing data stream, including: a business apparatus firstly packaging business data into a multiplexing transmission message; and then, according to User Datagram Protocol(UDP) or Transfer Control Protocol(TCP), packaging the multiplexing transmission message into a UDP message or a TCP message and transmitting to a multiplexer. The method unionizes the data transmission method between the business apparatus and the multiplexer, thereby resolving the interconnection and intercommunication problem between network devices.
Owner:ZTE CORP
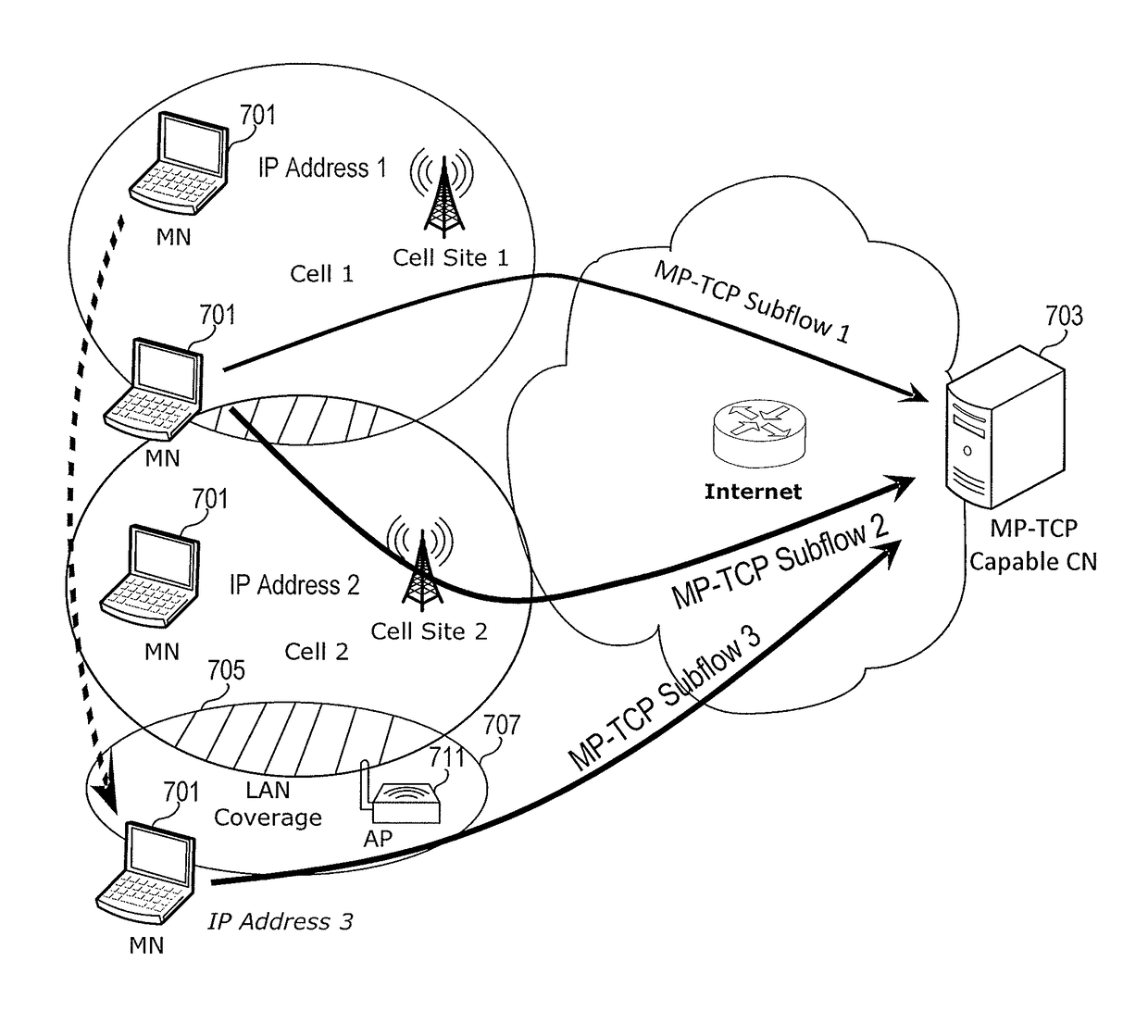
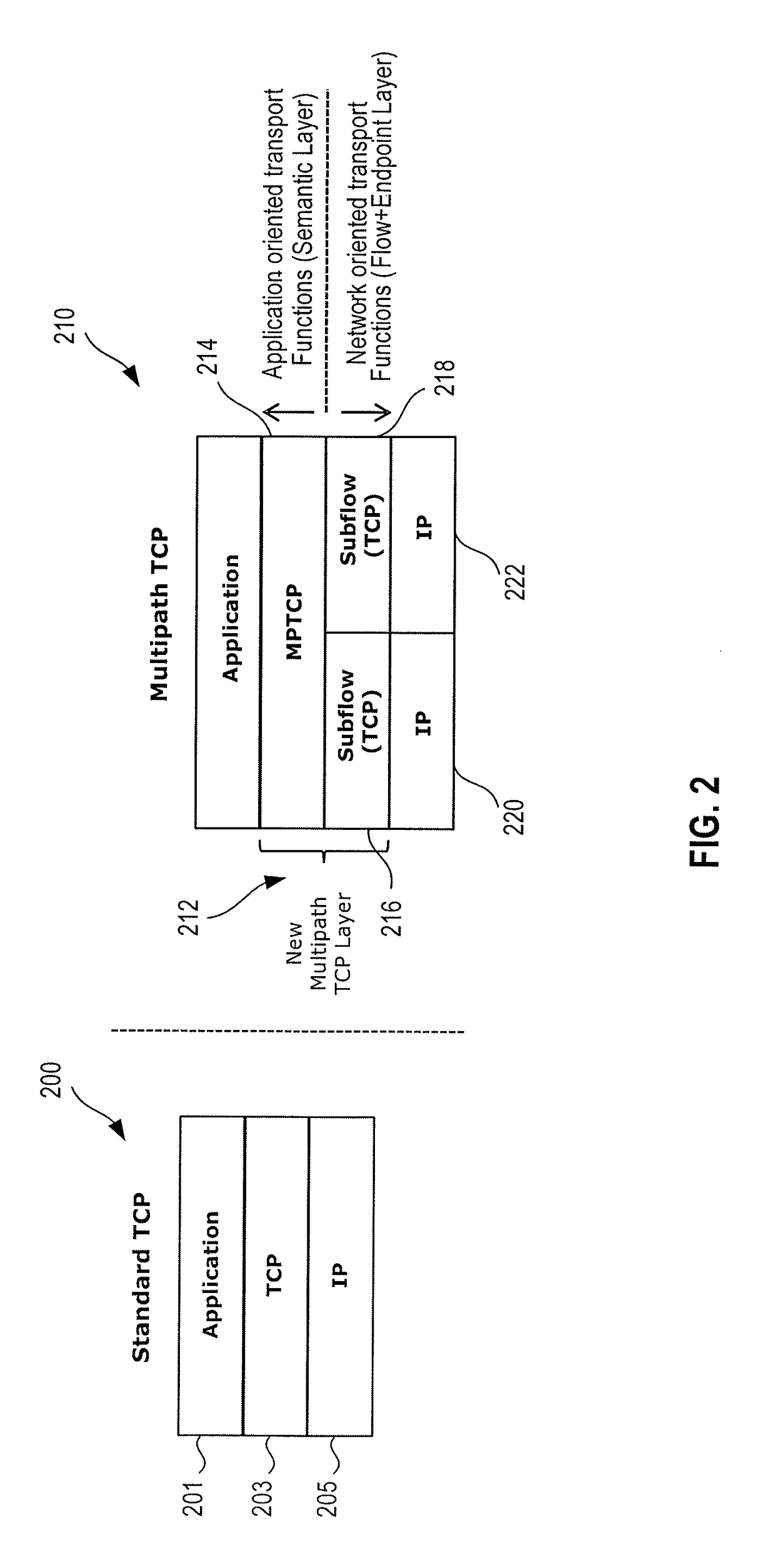
Mobility management of wireless networks based on multipath transfer control protocol
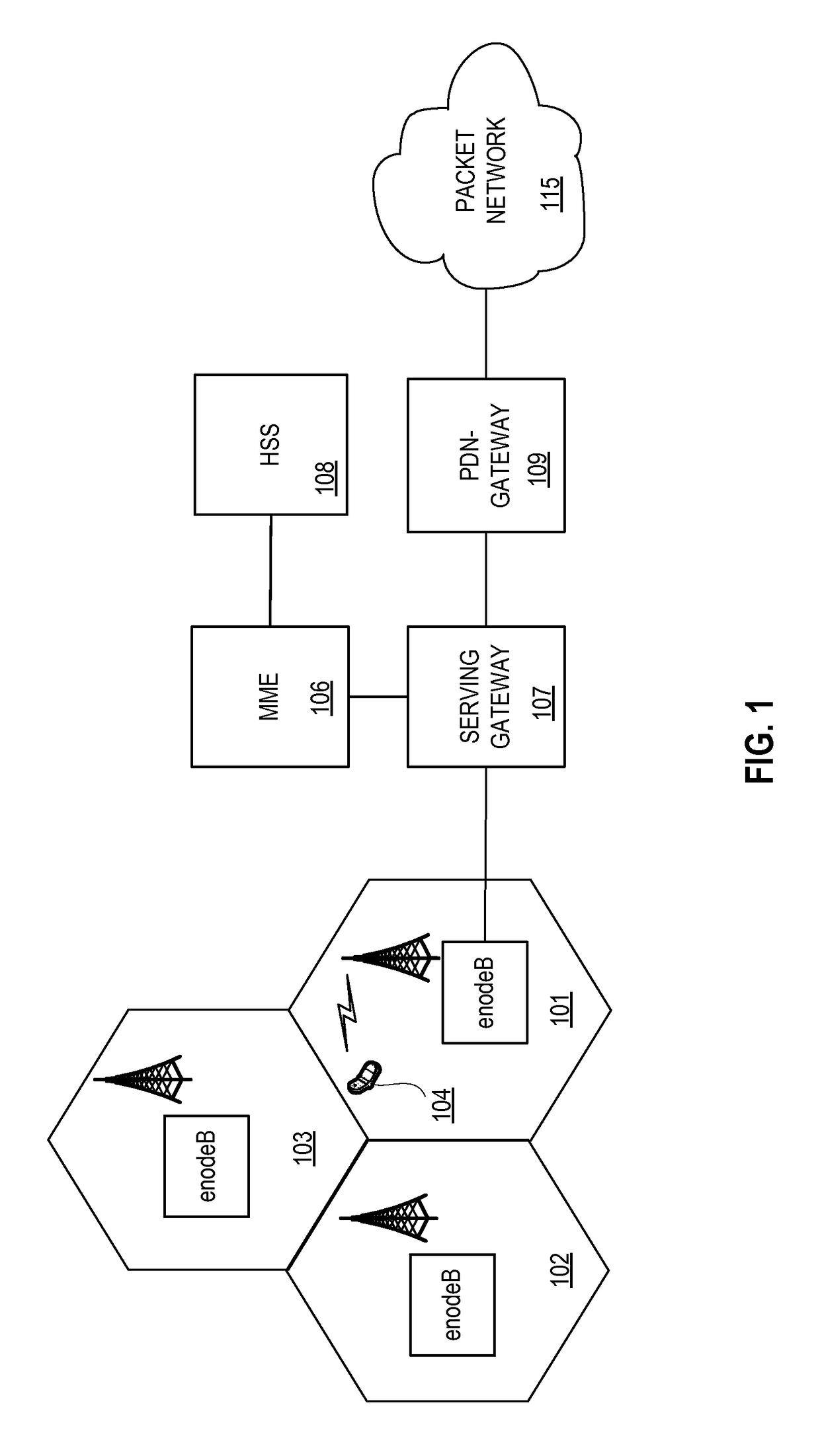
Mobile management in a cellular network utilizes the multipath-transfer control protocol (MP-TCP). A mobile device establishes a first multipath-transfer control protocol (MP-TCP) subflow to a corresponding node using a first internet protocol (IP) address corresponding to the mobile device. At least a portion of the first IP address is uniquely associated with the first coverage area. The mobile device establishes a second MP-TCP subflow using a second IP address corresponding to the mobile device while the mobile device is in an overlapped coverage area including a first portion of the first coverage area and a second portion of a second coverage area. At least a portion of the second IP address is uniquely associated with the second coverage area. The mobile node turns off the first subflow when the mobile node determines it has left the first coverage area.
Owner:AT&T INTPROP I LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com