Method and device for releasing transfer control protocol resources
A technology of transmission control protocol and release device, which is applied in the field of communication, and can solve problems such as unproposed solutions, failure to send the user's HTTP message, and full server resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
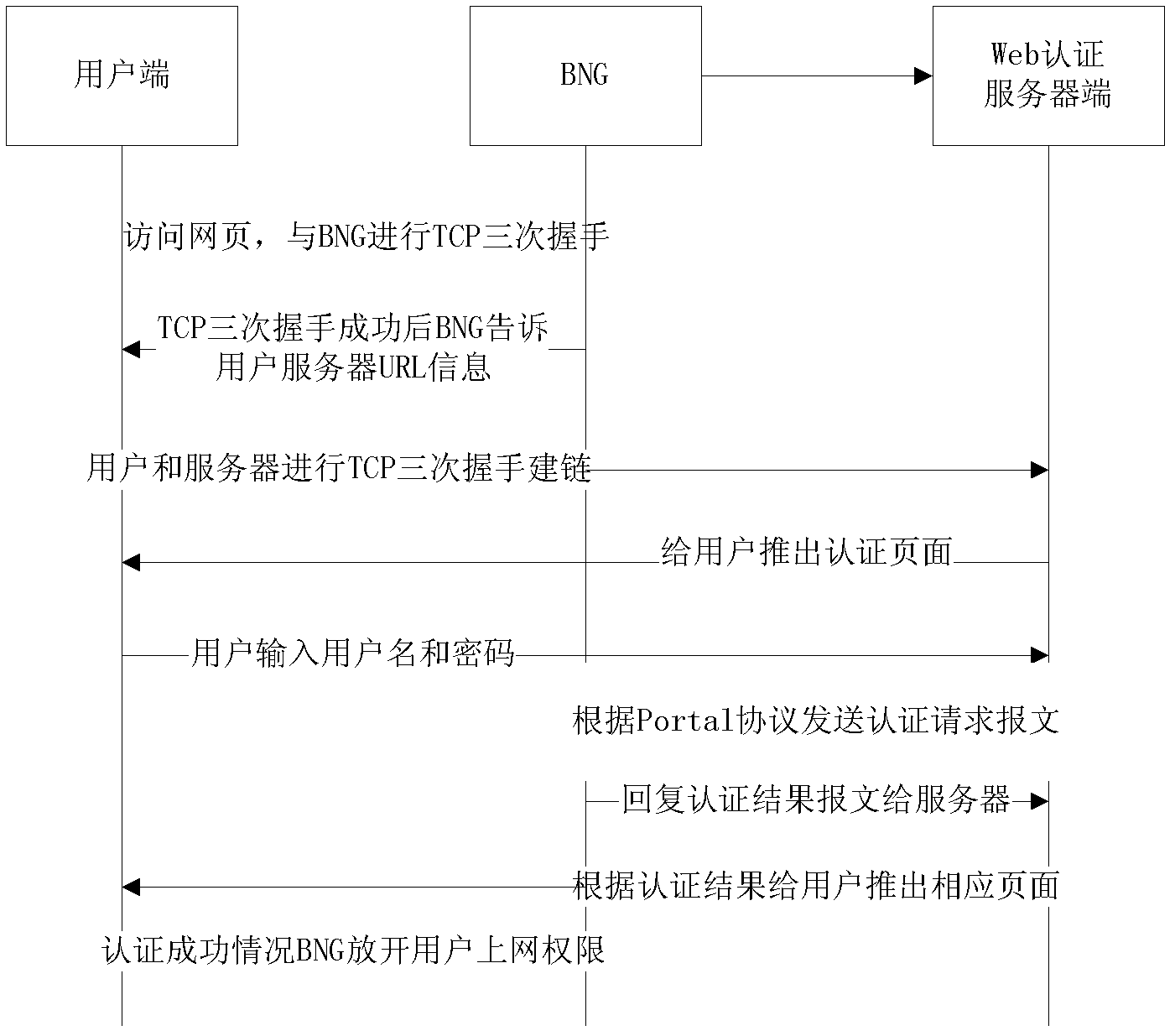
[0059] Based on the above method and device for releasing TCP resources, this embodiment provides a method for protecting TCP resources when HTTP is abnormal in a WEB authentication scenario.
[0060] Before describing the specific steps of this embodiment, the principle of this embodiment will be described first. In this embodiment, after the WEB authentication user and the BNG three-way handshake to establish a TCP connection, after the HTTP keep-alive time set by the BNG expires, the BNG detects whether the WEB authentication user's TCP connection is active through the TCP keep-alive. If the BNG judges that the TCP connection of the user is not active, BNG releases the TCP resources occupied by the user. For details, please refer to Figure 5 .
[0061] Figure 5 Among them, IPSTACK is the module on the BNG that handles sending and receiving packets. Here, its small TCP module interacts with the UE to perform a three-way TCP handshake. After the three-way handshake succe...
Embodiment 2
[0091] In this embodiment, the WEB authenticated user is a malicious attacking user. After the three-way handshake establishes the TCP connection, the user maliciously releases the TCP connection without notifying the BNG.
[0092] Figure 7 It is a schematic flowchart of a method for releasing TCP resources according to Embodiment 2 of the present invention. Such as Figure 7 As shown, the method includes:
[0093] Step S702, the user successfully obtains the address and goes online, that is, the WEB authenticated user accesses the BNG and obtains the address from the BNG;
[0094] Step S704, the user and the BNG TCP three-way handshake are successful, and the keep-alive mechanism is started, that is, the WEB authenticated user visits any webpage, and BNG and the user normally establish a TCP connection through the three-way handshake and start the keep-alive mechanism;
[0095] Step S706, when the keep-alive time is up, the user's HTTP+GET message is not received, that is...
Embodiment 3
[0099] In this embodiment, after the WEB authentication user shakes hands three times to establish a TCP connection, the HTTP GET message transmission process is abnormally discarded, the user's TCP connection is still maintained, and the BNG sets the HTTP keep-alive time.
[0100] Figure 8 It is a schematic flowchart of a method for releasing TCP resources according to Embodiment 3 of the present invention. Such as Figure 8 As shown, the method includes:
[0101] Step S802, the user successfully obtains the address and goes online, that is, the WEB authenticated user accesses the BNG and obtains the address from the BNG;
[0102] Step S804, the user and the BNG TCP three-way handshake are successful, and the keep-alive mechanism is activated, that is, the WEB authenticated user visits any web page, and the BNG and the user normally establish a TCP connection through the three-way handshake and start the keep-alive mechanism;
[0103] Step S806, when the keep-alive time e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com