CC (Challenge Collapsar) attack protection method and device
A protective device and client technology, applied in the field of network security, can solve problems such as poor protection effect and denial of service requests, and achieve the effect of improving protection effect and reducing usage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
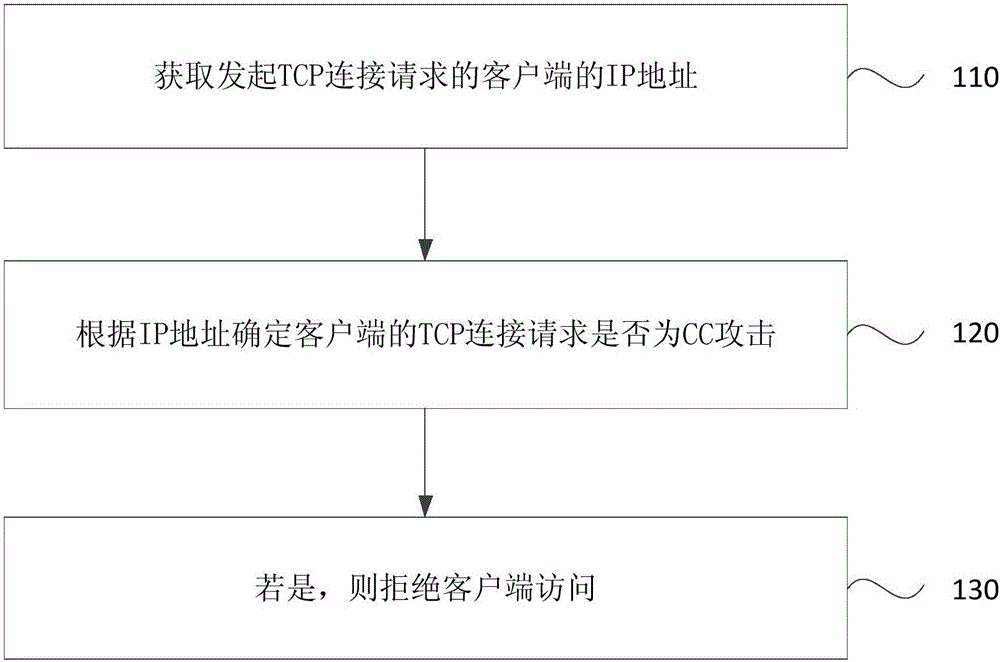
[0023] figure 1 It is a schematic flowchart of a CC attack protection method provided by Embodiment 1 of the present invention. This embodiment can be applied to any situation that needs to defend against CC attacks. This method can be executed by a CC attack protection device. The CC attack protection The device can be configured in the server, and the method specifically includes the following steps:
[0024] Step 110, obtaining the IP address of the client that initiates the TCP connection request;
[0025] Among them, TCP (Transmission Control Protocol, transmission control protocol) is a connection-oriented reliable transport layer communication protocol. The TCP connection process includes a three-way handshake process. In the first handshake, the client sends a SYN message to the server, waiting for the server to confirm; in the second handshake, the server receives the SYN message sent by the client, sends a confirmation message to the client, that is, an ACK message...
Embodiment 2
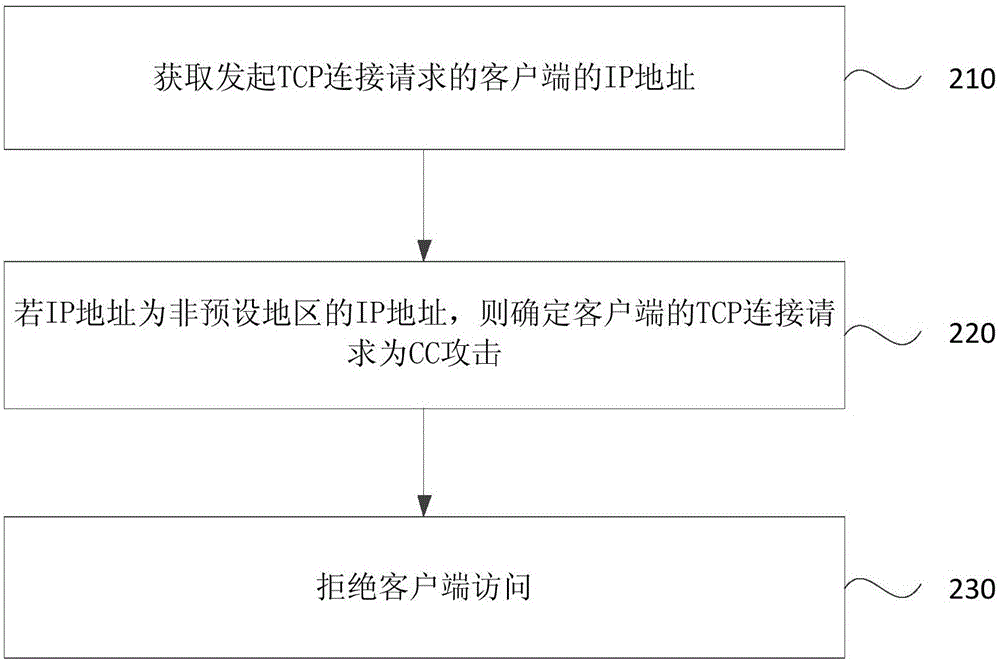
[0035] figure 2 It is a schematic flowchart of a CC attack protection method provided by Embodiment 2 of the present invention. This embodiment is a further optimization of the above-mentioned embodiment. In this embodiment, it is determined whether the TCP connection request of the client is a CC attack based on the IP address. The TCP connection request at the end is a CC attack, and the method specifically includes:
[0036] Step 210, obtaining the IP address of the client that initiates the TCP connection request;
[0037] Step 220, if the IP address is an IP address in a non-preset area, determine that the TCP connection request of the client is a CC attack.
[0038] Exemplarily, according to the obtained IP address, the region to which the obtained IP address belongs can be obtained by querying the IP geographic location.
[0039] Exemplarily, the preset region is China, and if it is found that the obtained IP address is a non-Chinese IP address, it is determined tha...
Embodiment 3
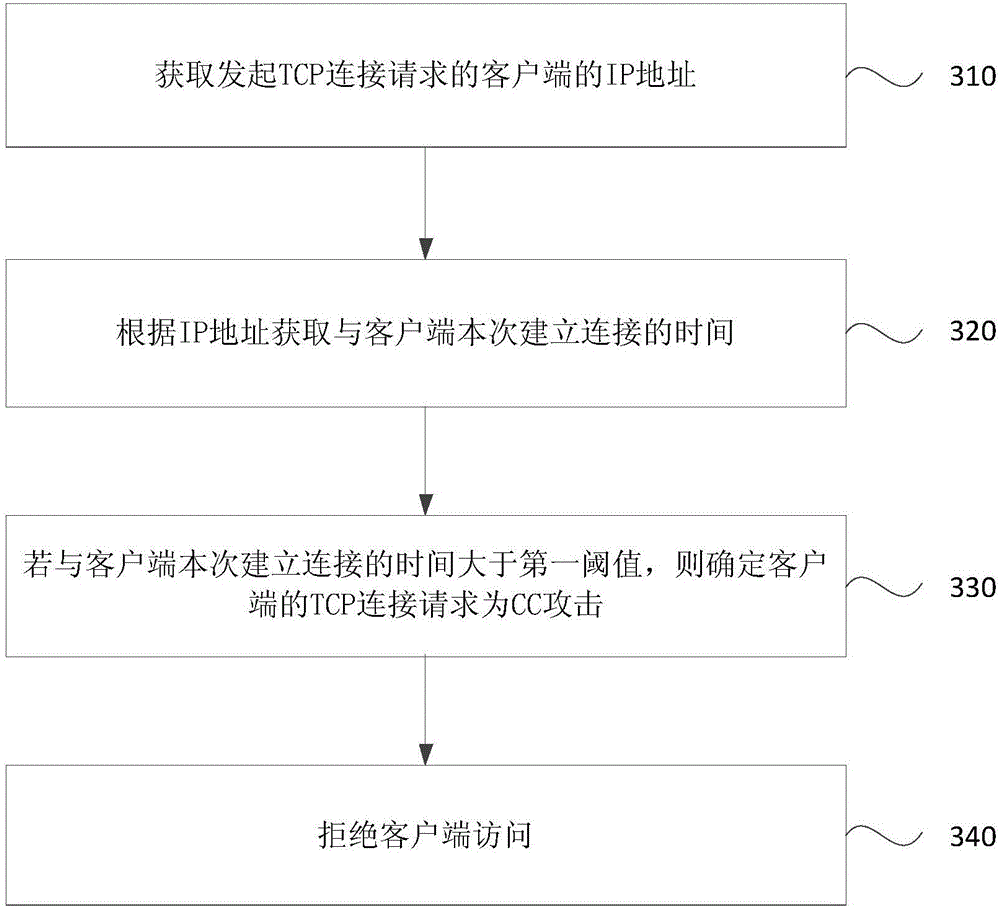
[0044] image 3 It is a schematic flowchart of a CC attack protection method provided by Embodiment 3 of the present invention. This embodiment is a further optimization of the foregoing embodiment. In this embodiment, determining whether the TCP connection request of the client according to the IP address is a CC attack is optimized as follows: obtain the time to establish a connection with the client according to the IP address; If the current connection establishment time of the client is greater than the first threshold, it is determined that the client's TCP connection request is a CC attack. The method specifically includes:
[0045]Step 310, obtaining the IP address of the client that initiates the TCP connection request;
[0046] Step 320, obtain the time of establishing the connection with the client according to the IP address;
[0047] Step 330, if the current time for establishing a connection with the client is greater than the first threshold, determine that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com