Patents
Literature
726 results about "Pattern detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
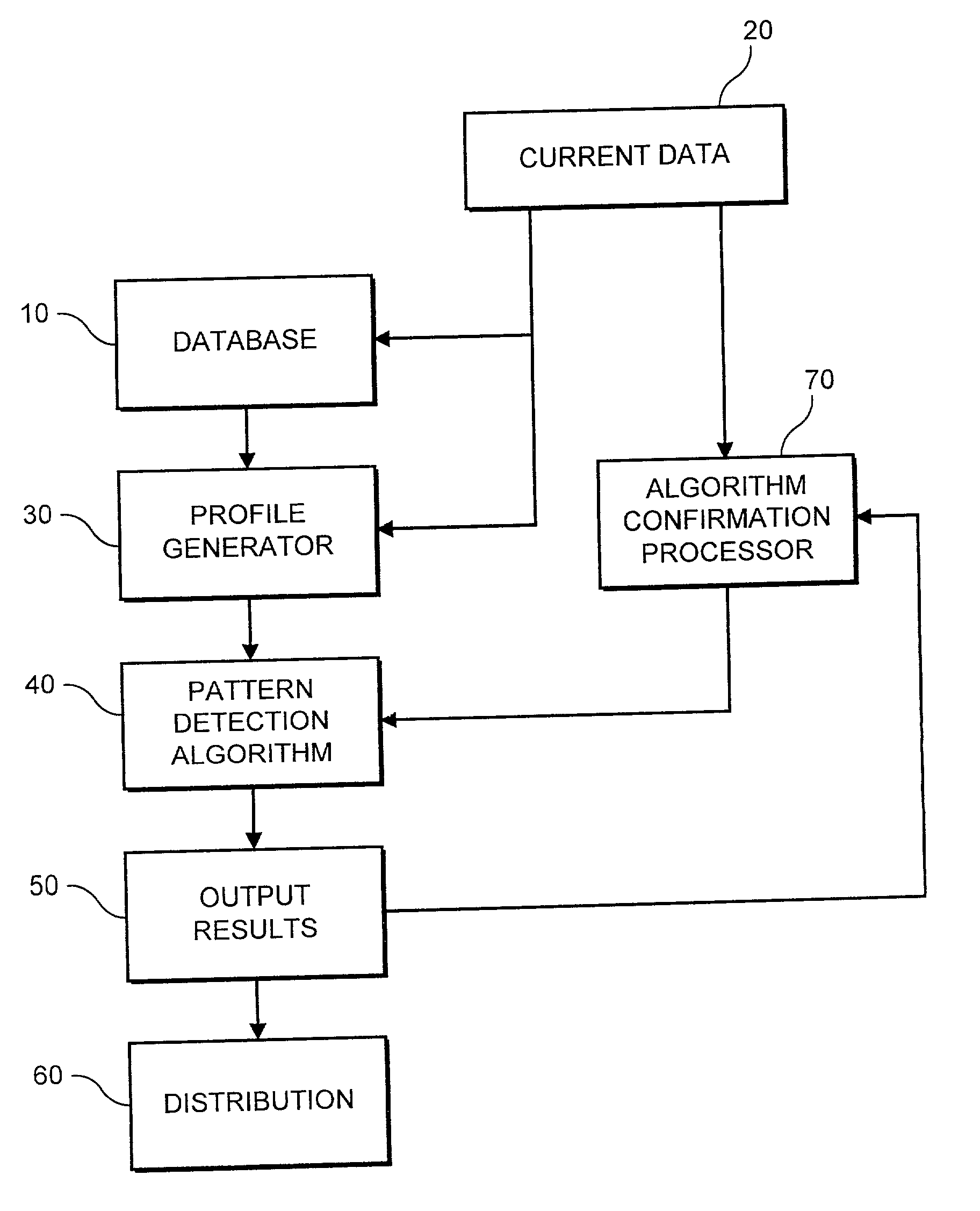
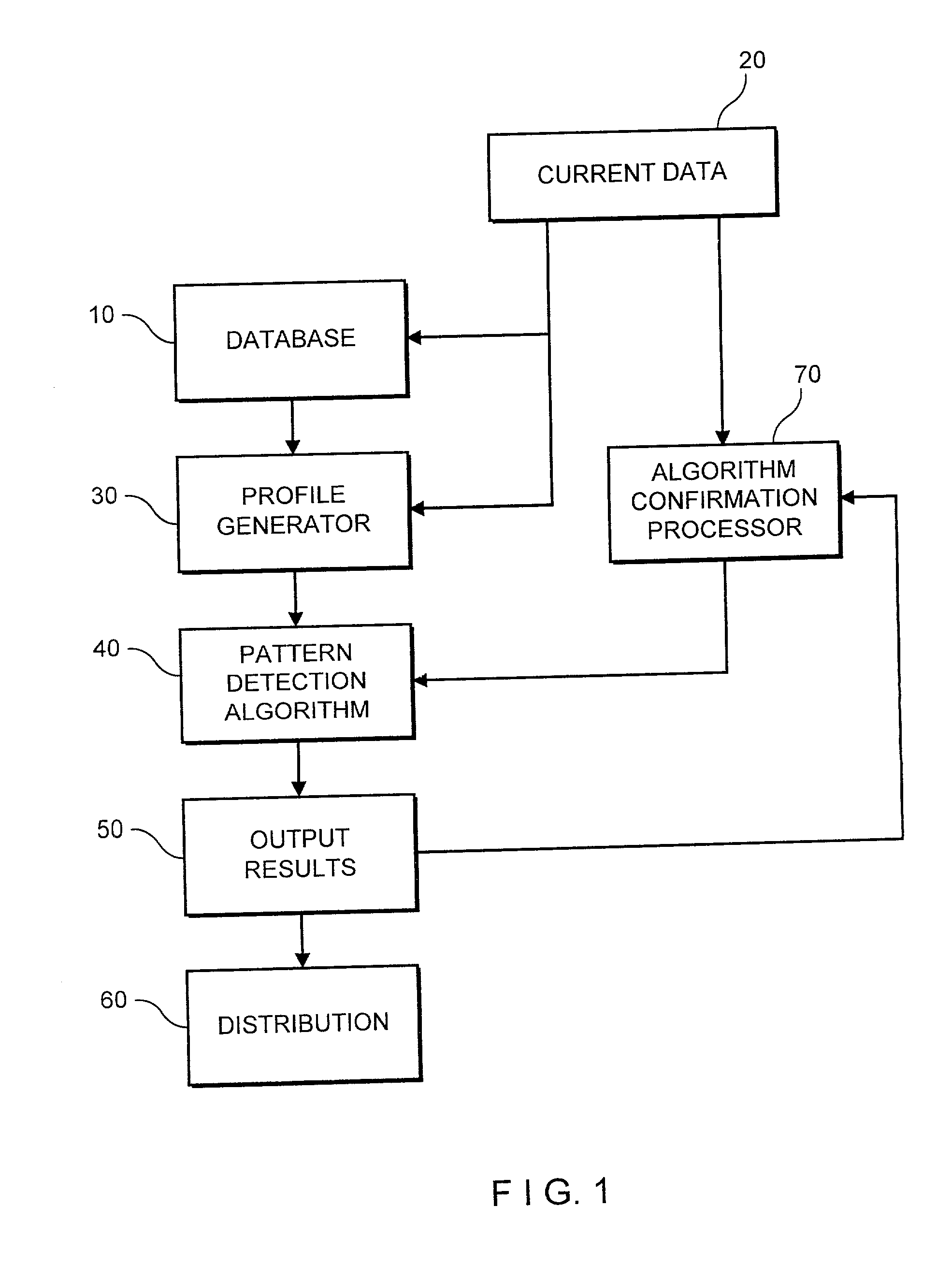
In Analytics and Operations Research, Pattern Detection includes a number of methods for extracting meaning from large and complex data sets through a combination of operations research methods, graph theory, data analysis, clustering, and advanced mathematics. Unlike machine learning, deep learning, or data mining, pattern detection is data agnostic, requiring only an ingestible data format to compute correlations in data. Graph algorithms detect patterns of co-occurrence to create a holistic representations of connections a given set of data. Analysis has been applied to industries including transportation, manufacturing, and others.
Apparatus and method for detecting or recognizing pattern by employing a plurality of feature detecting elements
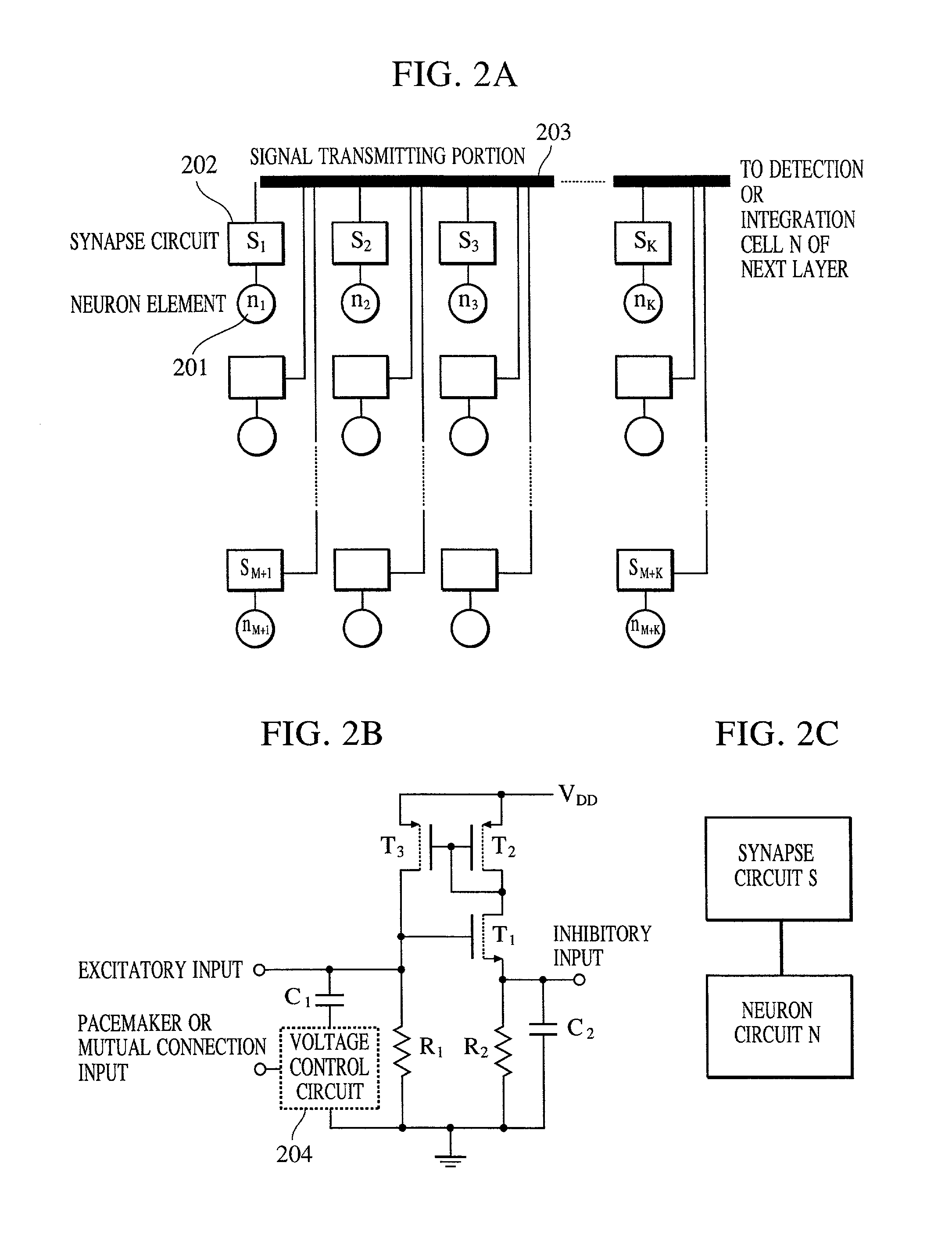
InactiveUS20020038294A1Easy constructionReduce in quantityDigital computer detailsCharacter and pattern recognitionSynapsePattern detection
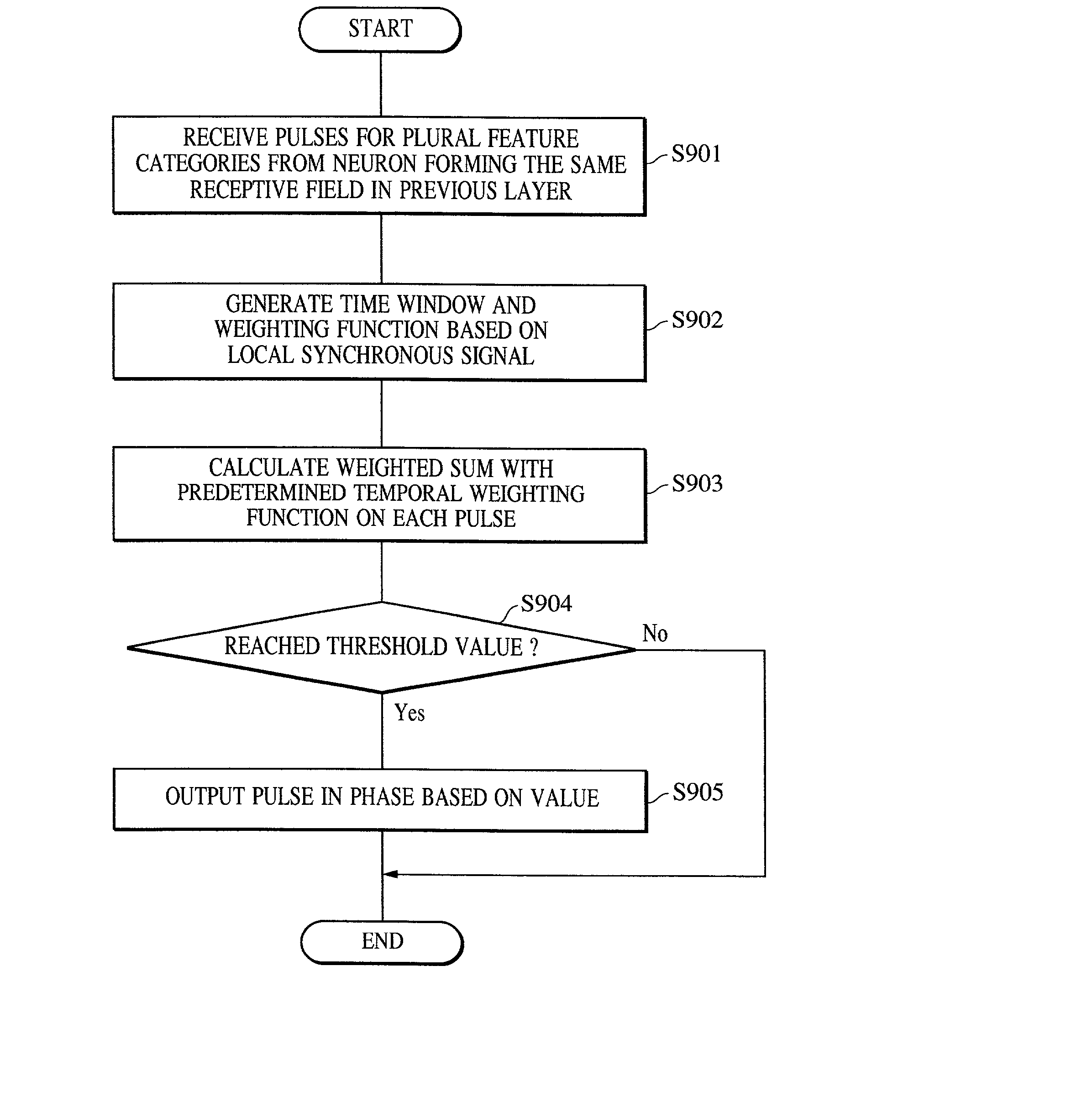
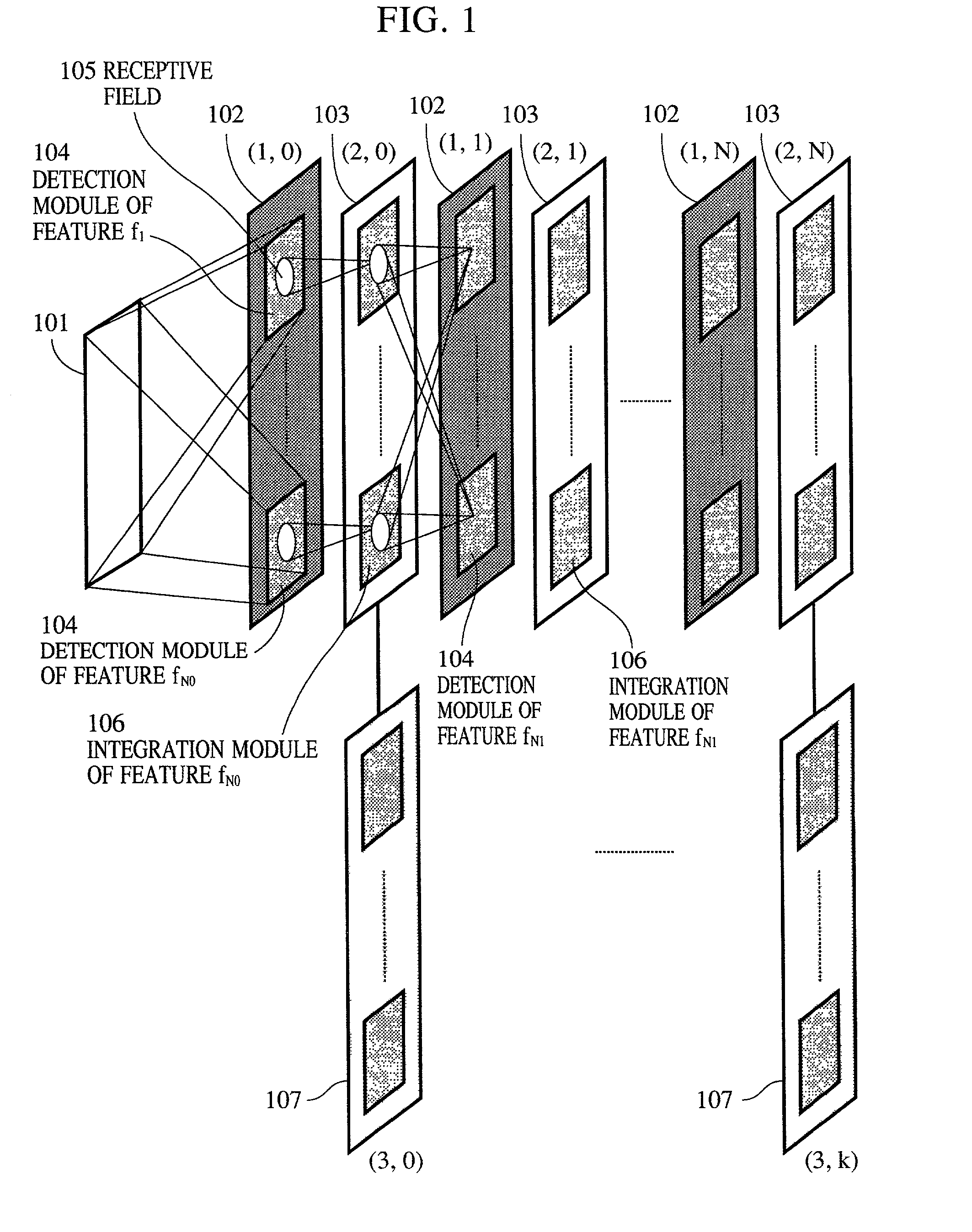
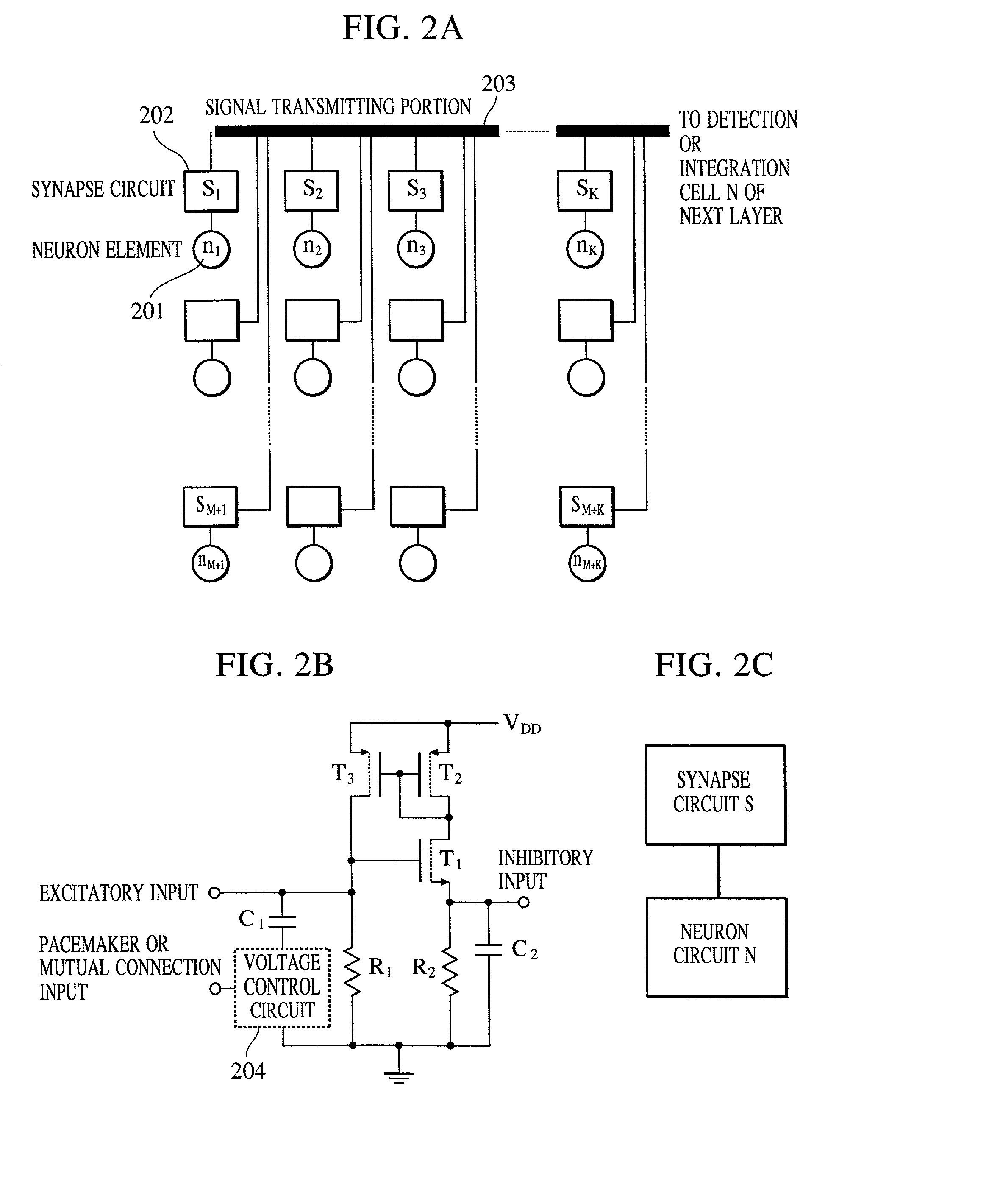
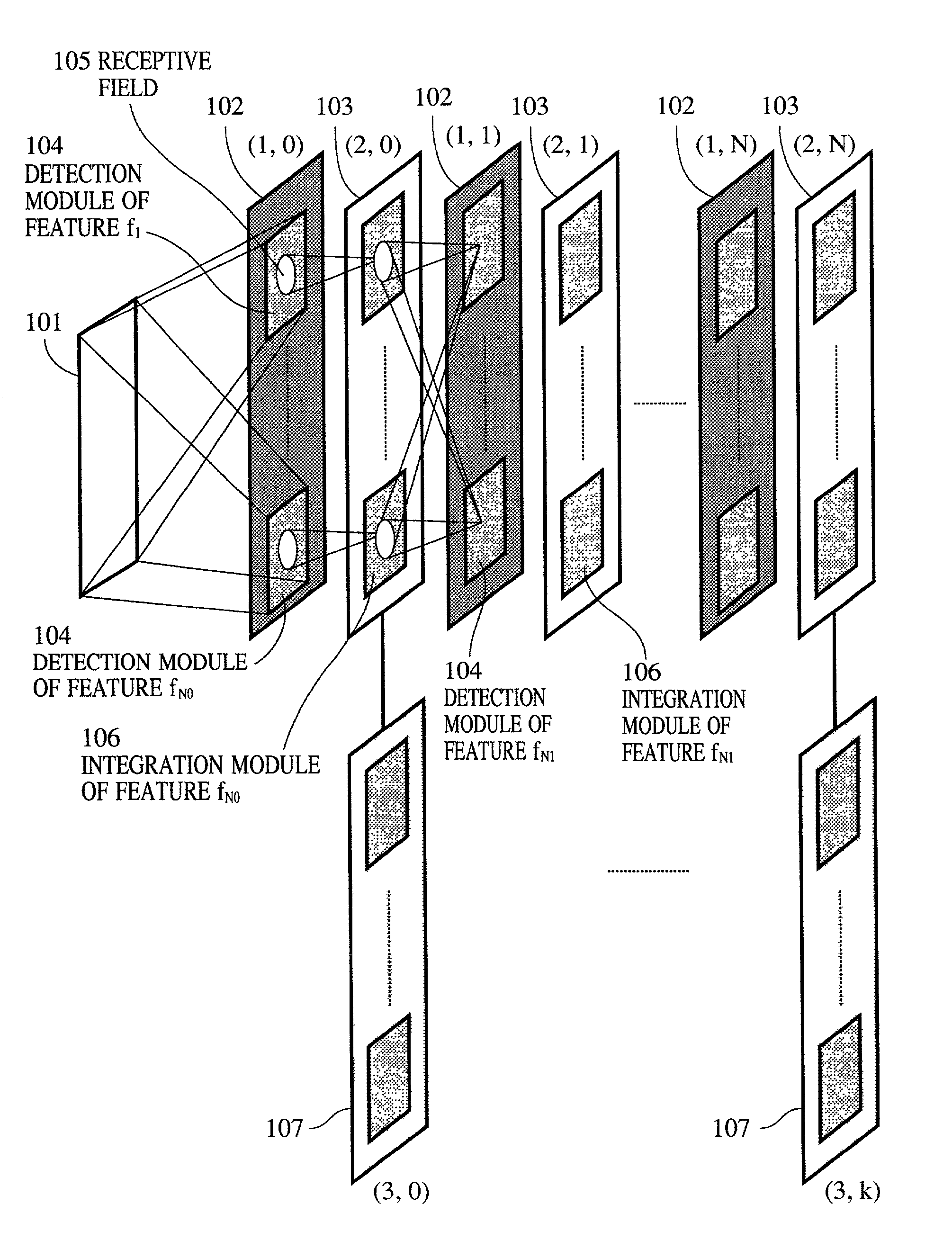
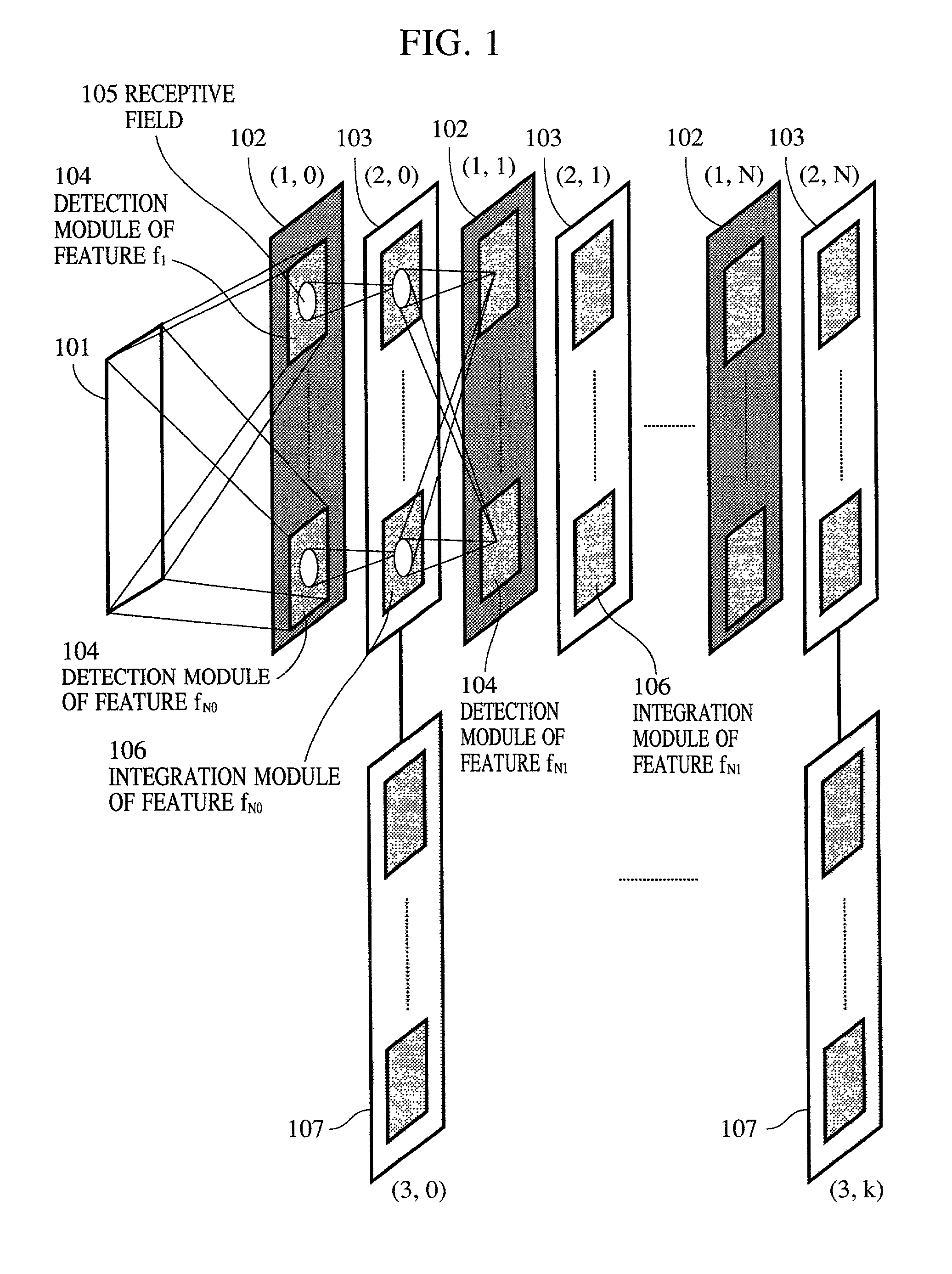
A pattern detecting apparatus has a plurality of hierarchized neuron elements to detect a predetermined pattern included in input patterns. Pulse signals output from the plurality of neuron elements are given specific delays by synapse circuits associated with the individual elements. This makes it possible to transmit the pulse signals to the neuron elements of the succeeding layer through a common bus line so that they can be identified on a time base. The neuron elements of the succeeding layer output the pulse signals at output levels based on a arrival time pattern of the plurality of pulse signals received from the plurality of neuron elements of the preceding layer within a predetermined time window. Thus, the reliability of pattern detection can be improved, and the number of wires interconnecting the elements can be reduced by the use of the common bus line, leading to a small scale of circuit and reduced power consumption.
Owner:CANON KK
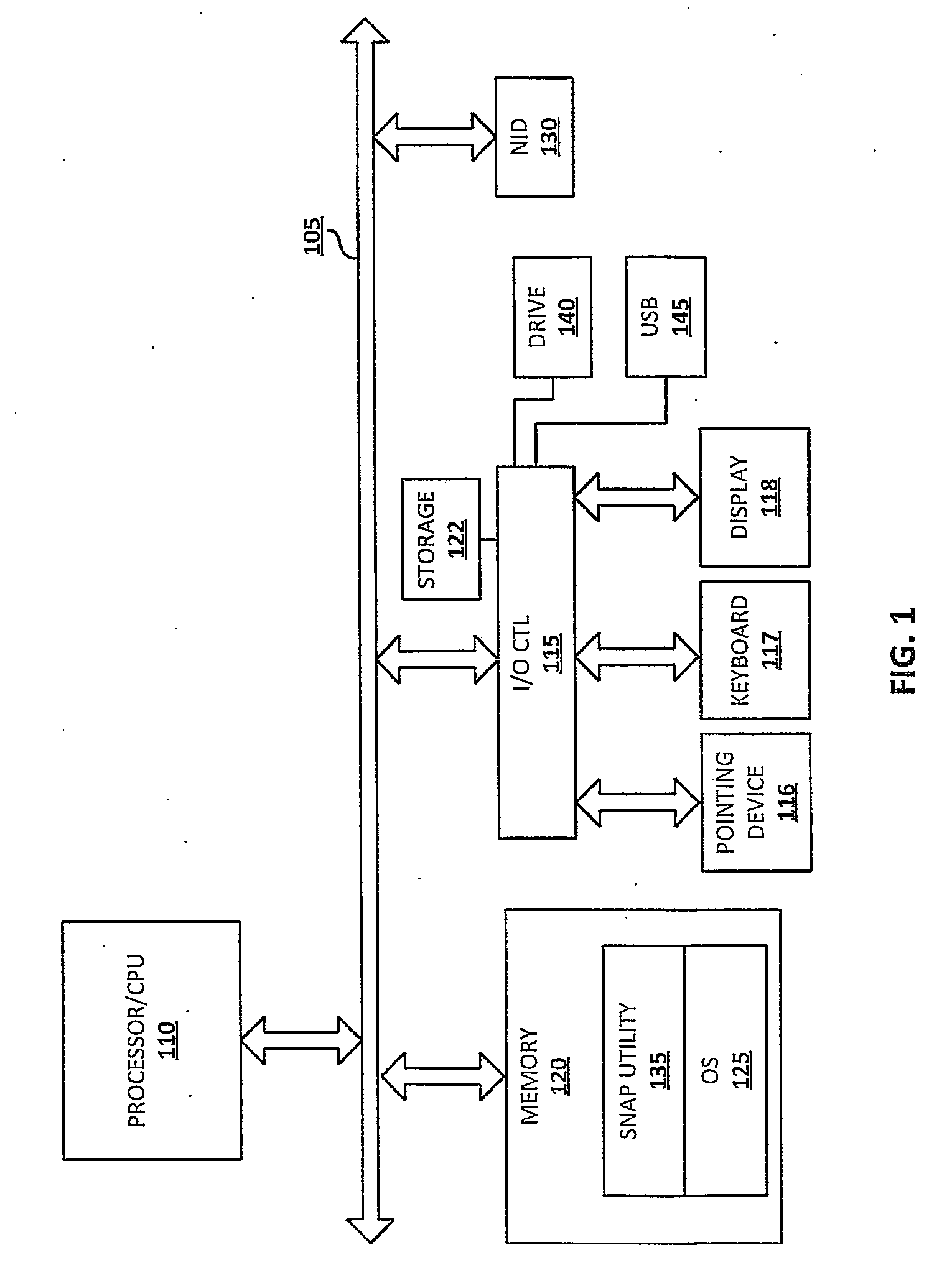
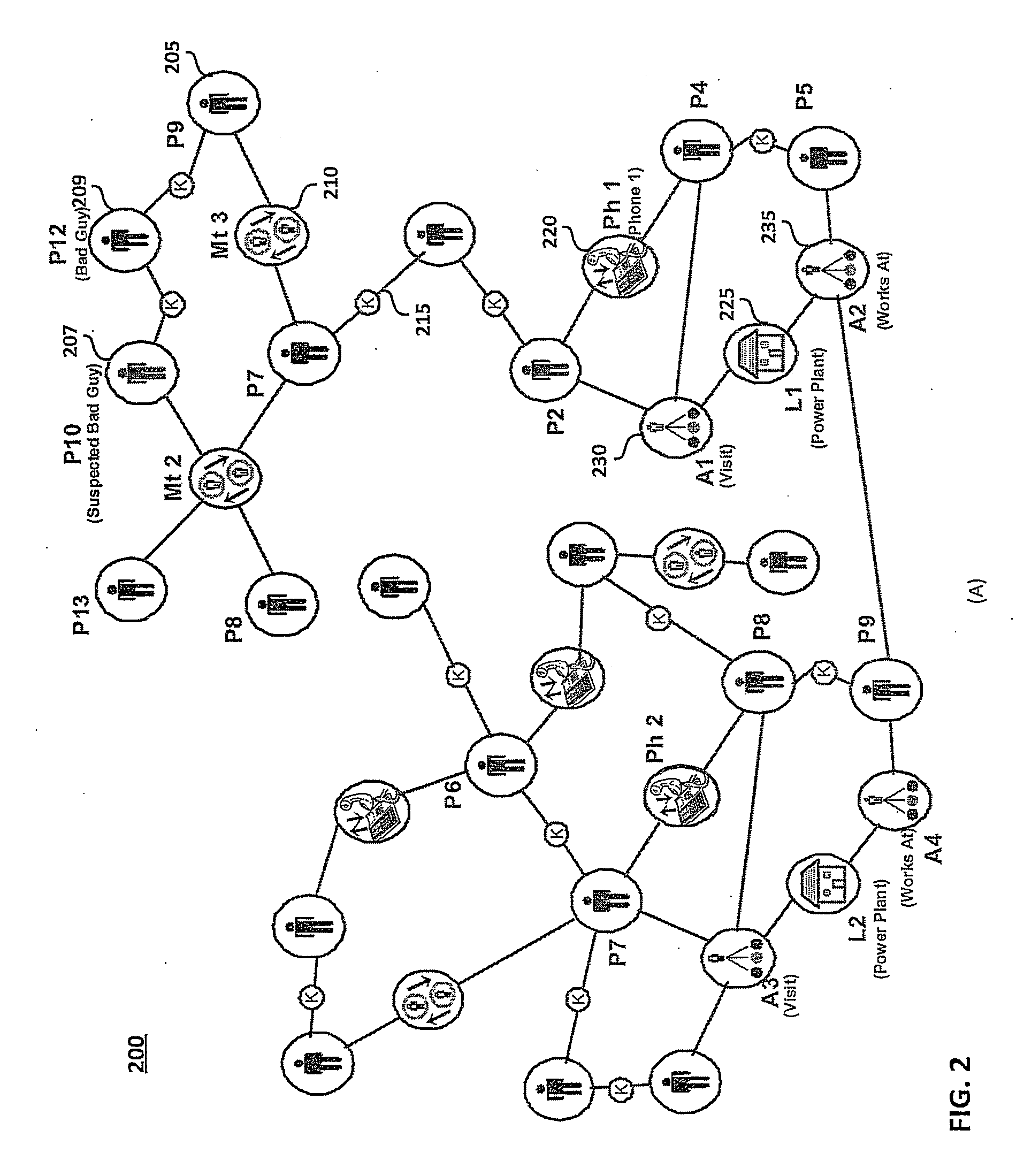
Social network aware pattern detection
ActiveUS20070226248A1Highly-scalable and computationally efficientDigital data processing detailsDigital computer detailsGraphicsPattern matching
Enabling dynamic, computer-driven, context-based detection of social network patterns within an input graph representing a social network. A Social Network Aware Pattern Detection (SNAP) system and method utilizes a highly-scalable, computationally efficient integration of social network analysis (SNA) and graph pattern matching. Social network interaction data is provided as an input graph having nodes and edges. The graph illustrates the connections and / or interactions between people, objects, events, and activities, and matches the interactions to a context. A sample graph pattern of interest is identified and / or defined by the user of the application. With this sample graph pattern and the input graph, a computational analysis is completed to (1) determine when a match of the sample graph pattern is found, and more importantly, (2) assign a weight (or score) to the particular match, according to a pre-defined criteria or context.
Owner:NORTHROP GRUMMAN SYST CORP
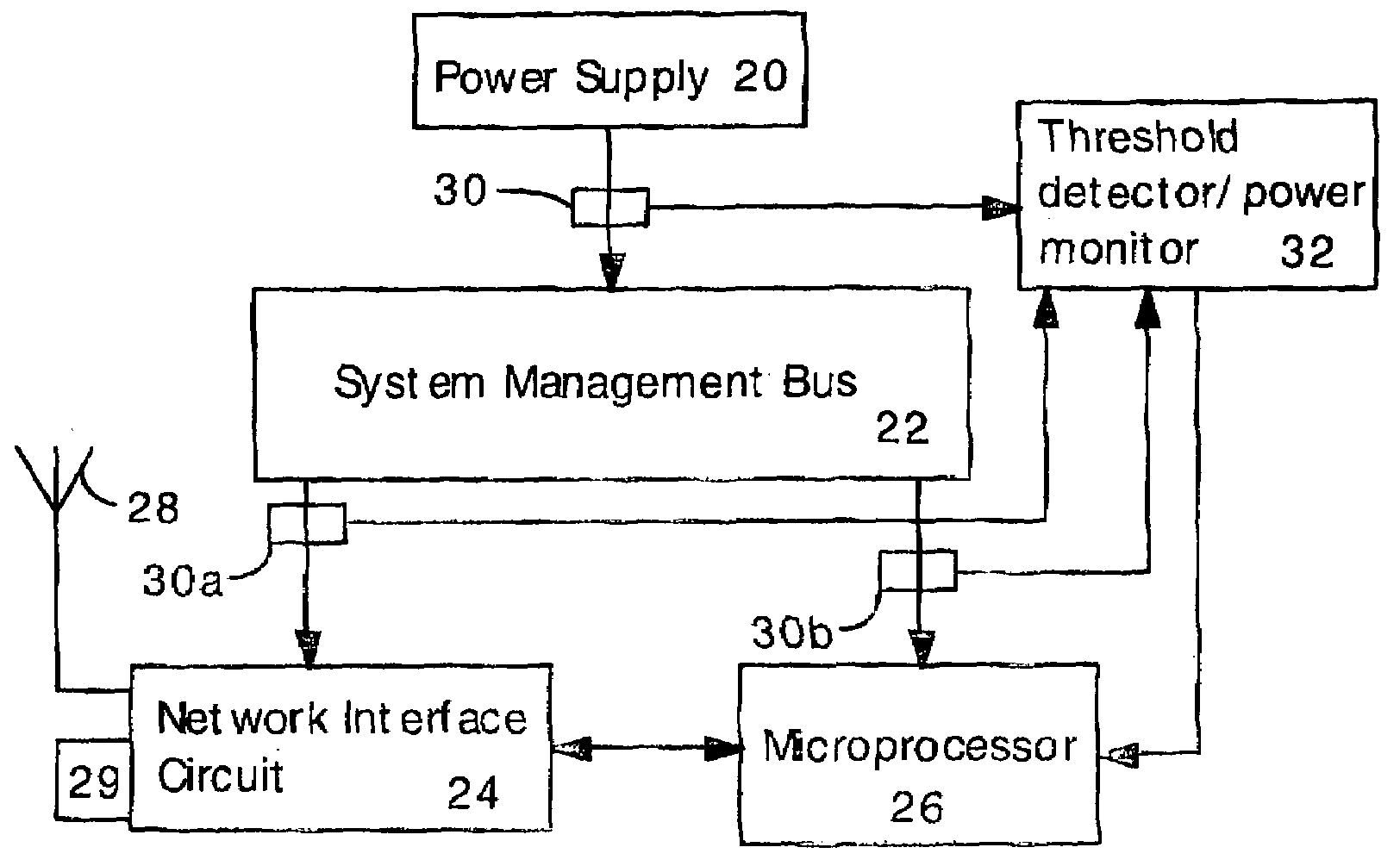
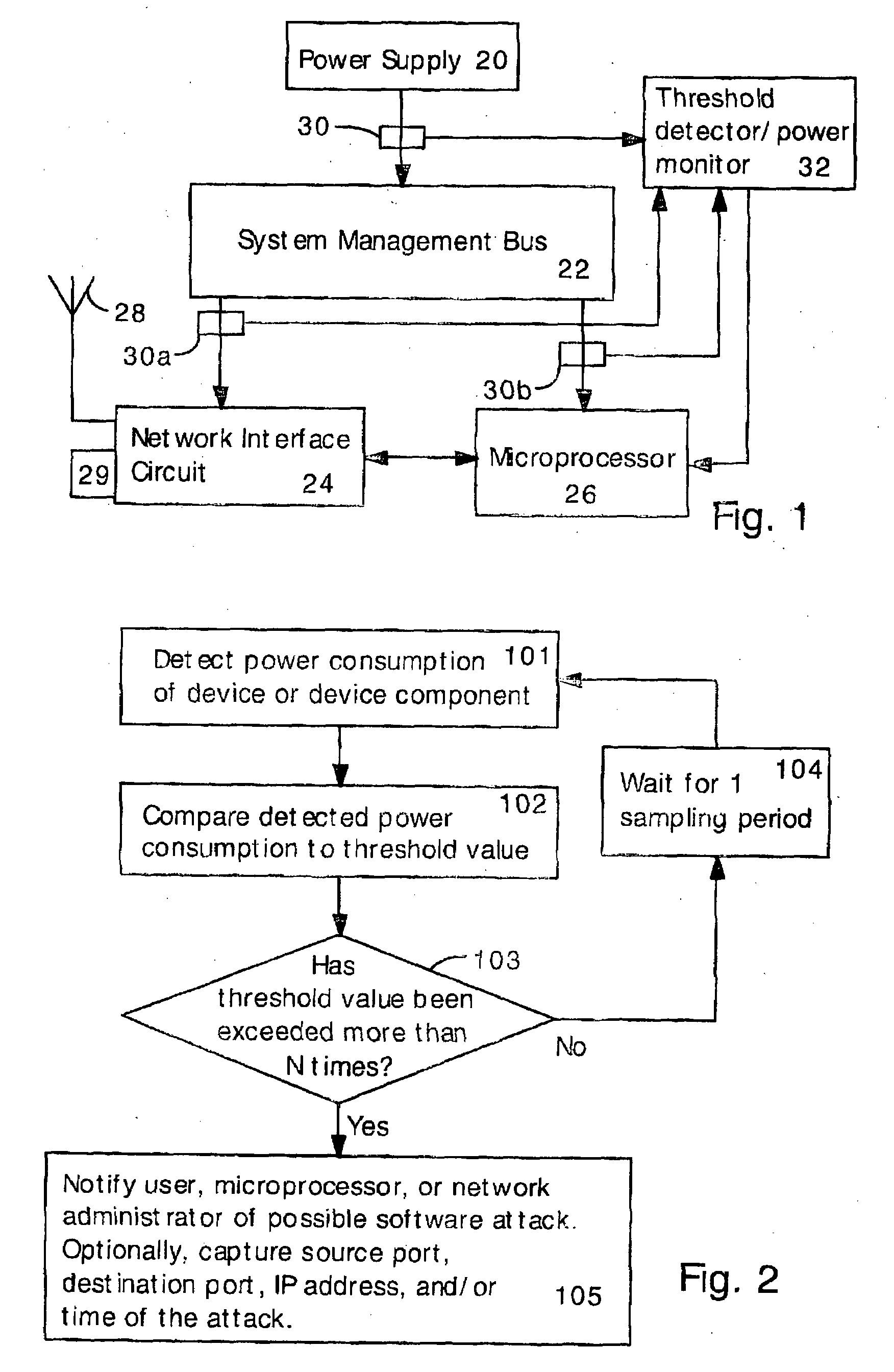
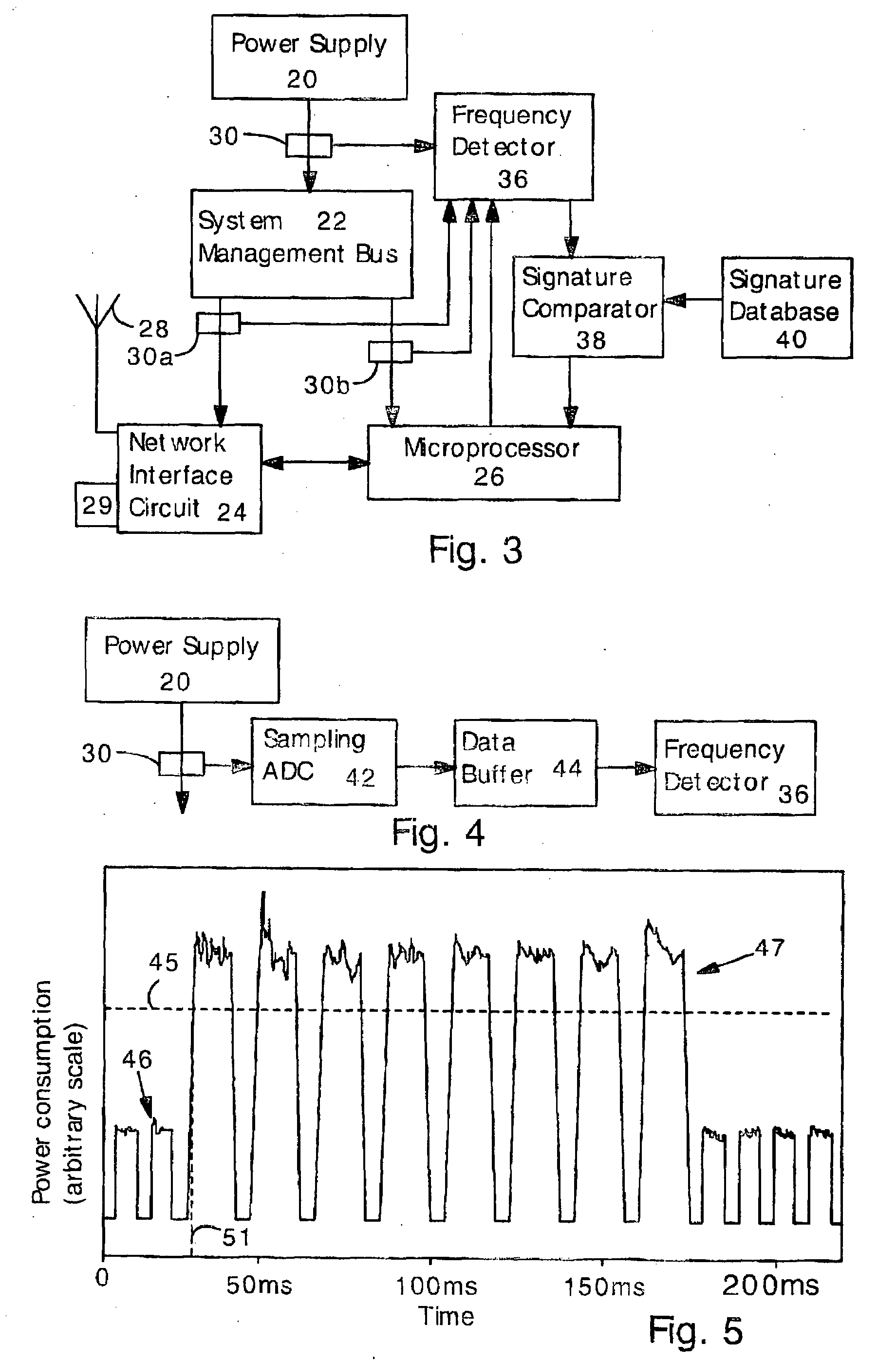
Detecting Software Attacks By Monitoring Electric Power Consumption Patterns
ActiveUS20080276111A1Reduce the valueMemory loss protectionUnauthorized memory use protectionFourier transform on finite groupsEngineering
Software attacks such as worms and viruses are detected in an electronic device by monitoring power consumption patterns. In a first embodiment, software attacks are detected by an increase in power consumption. The increased power consumption can be caused by increased network traffic, or by increased activity in the microprocessor. Monitoring power consumption is particularly effective for detecting DOS / flooding attacks when the electronic device is in an idle state. In a second embodiment, a power consumption signal is converted to the frequency domain (e.g., by fast Fourier transform). The highest amplitude frequencies are identified. Specific software attacks produce characteristic frequencies in the power consumption signal. Software attacks are therefore detected by matching the highest amplitude frequencies with frequencies associated with specific worms and viruses. Identification of a particular software attack typically requires matching of 3 or more of the highest amplitude frequencies, and, optionally, amplitude information.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY +1
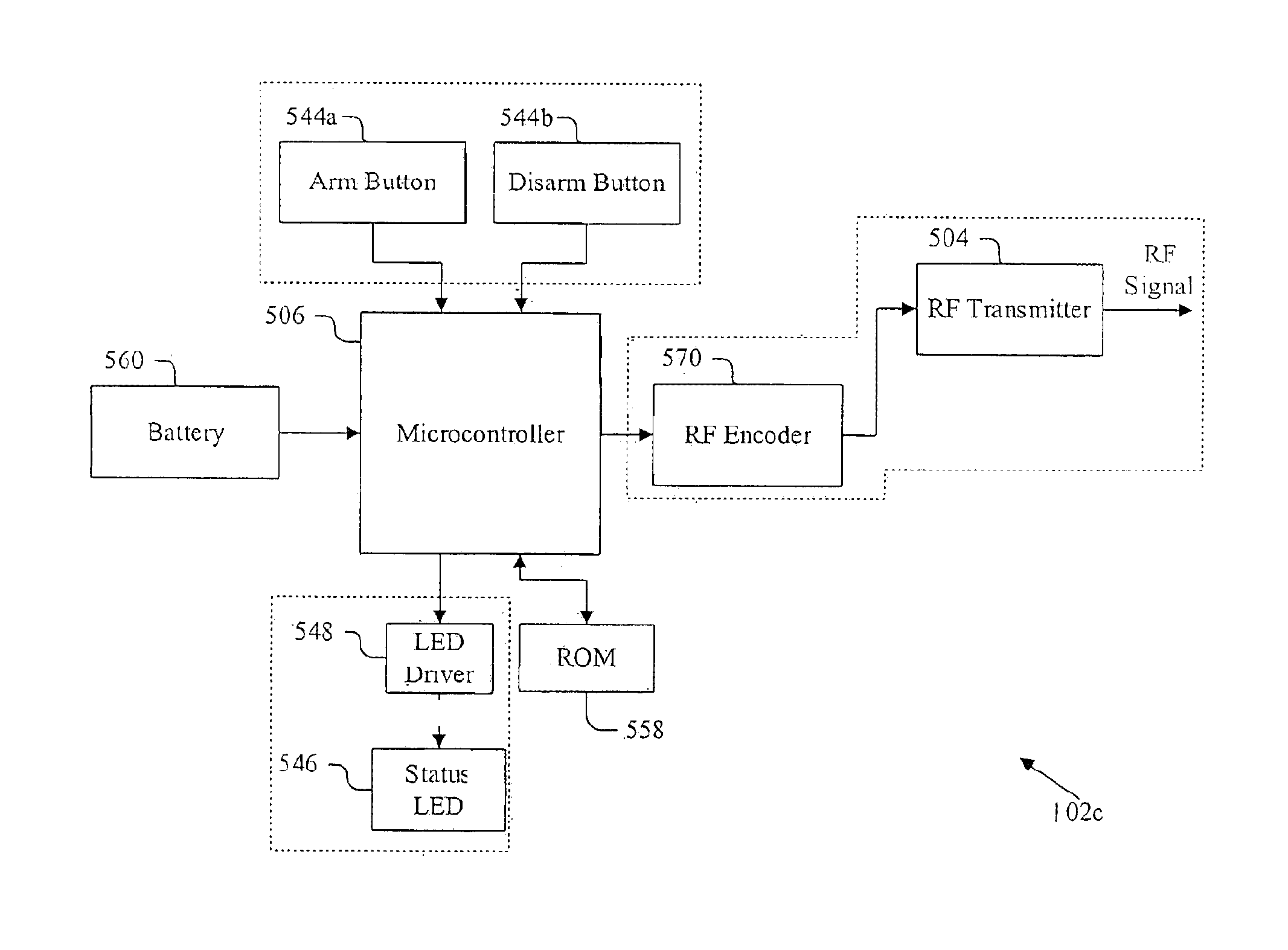
System and method for reliable communications in a one-way communication system
An alarm system, including ease of programming of a family or group of interoperating alarm devices via a learn mode that detects new devices and provides reliable accounting of the group via state dumps to an external system. Reliable communications with the external system are provided via a set of protocols. Disabling of the alarm system is prevented, by transmitting a pre-alarm signal prior to expiration of an entry delay, and by verifying communications with an external device, prior to an alarm-triggering event. Multi-priority message code assignment, including error tolerance, employs n-bit codes with maximized error tolerance. Message transmissions include multiple levels of error protection. The group of monitored alarm devices can be easily set up, purchased and activated by a consumer, and do not become permanent fixtures.
Owner:LASERSHIELD SYST
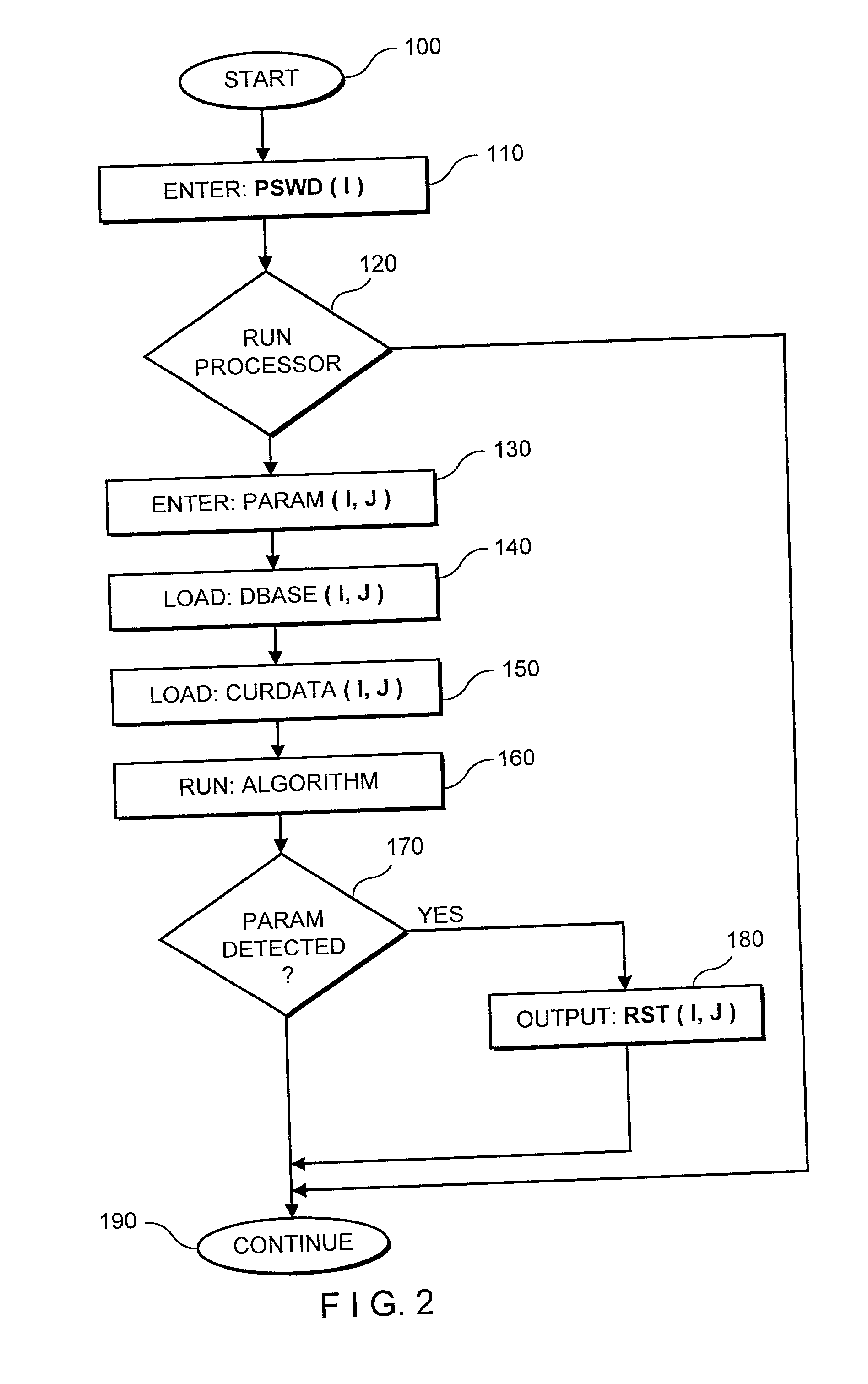
Data processor for implementing forecasting algorithms
InactiveUS20020007331A1Improve forecast accuracyFinanceForecastingData processing systemPrediction algorithms
A data processing system and method for developing predictions regarding future asset price movements, based on pattern detection in a time sequence of historical price data. The system includes computer implementation of a kernal regression to effect a smooth estimator of the non-linear price-time relationship. As tested against known patterns, the system provides an expectation regarding a future price movement.
Owner:MASSACHUSETTS INST OF TECH
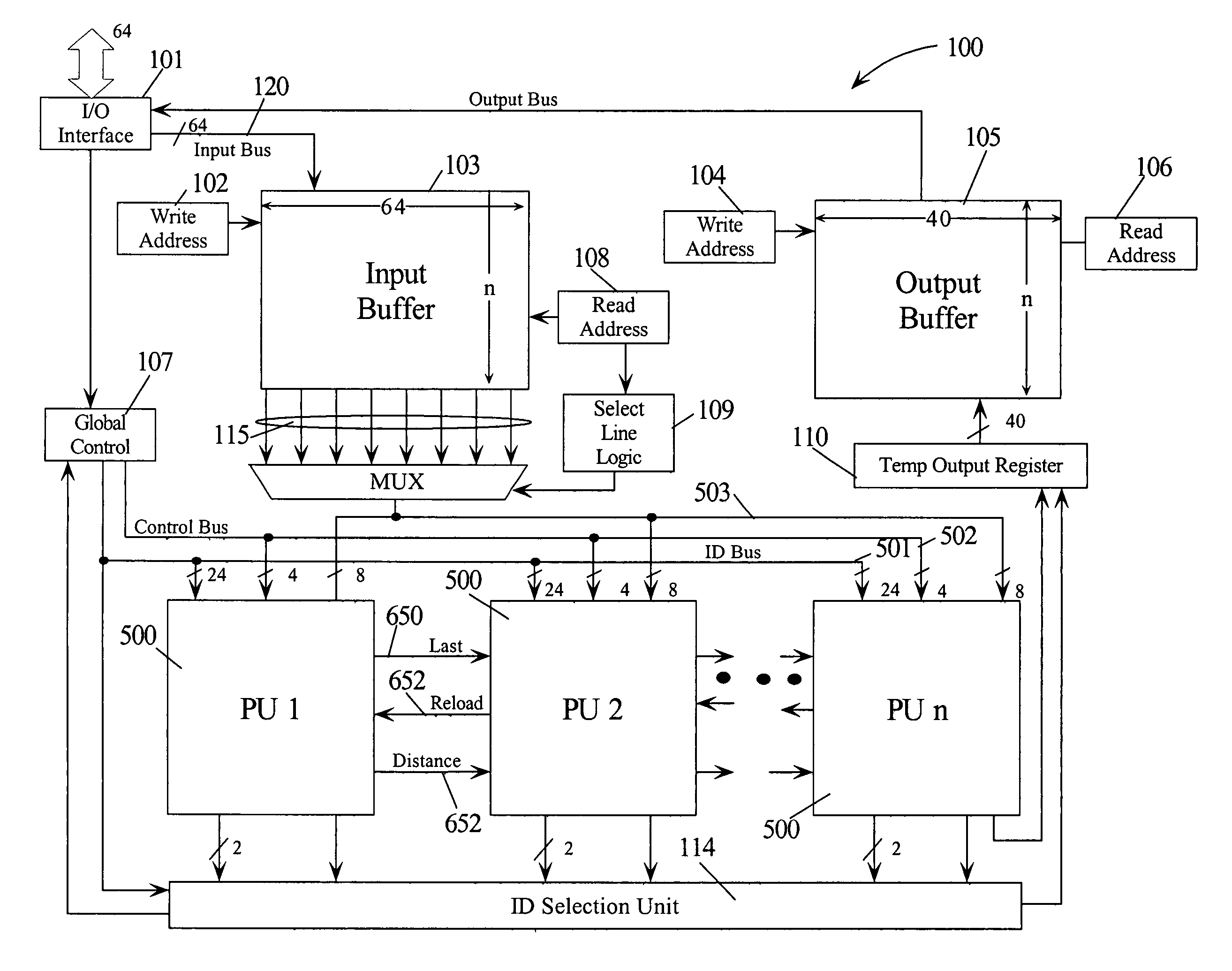
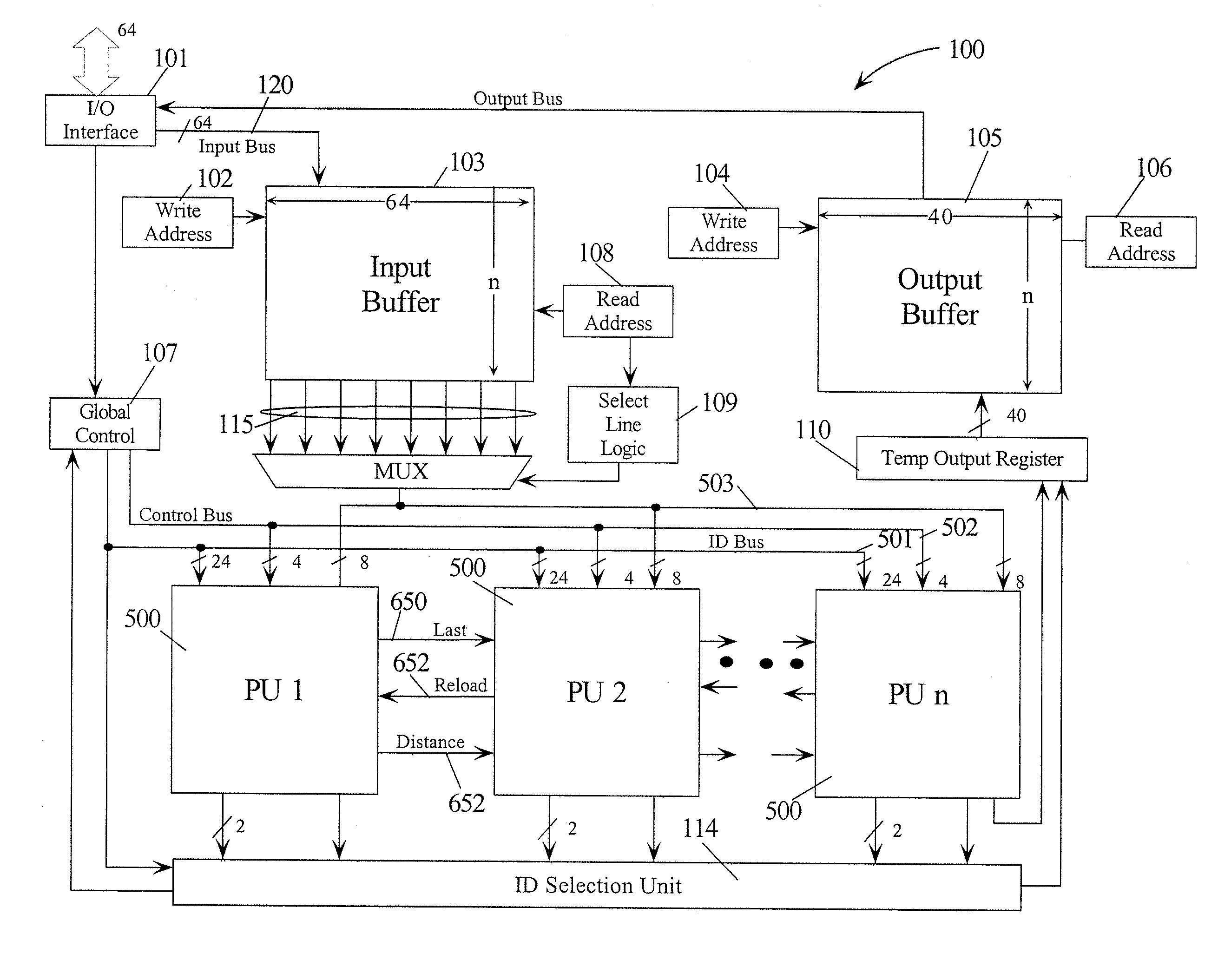
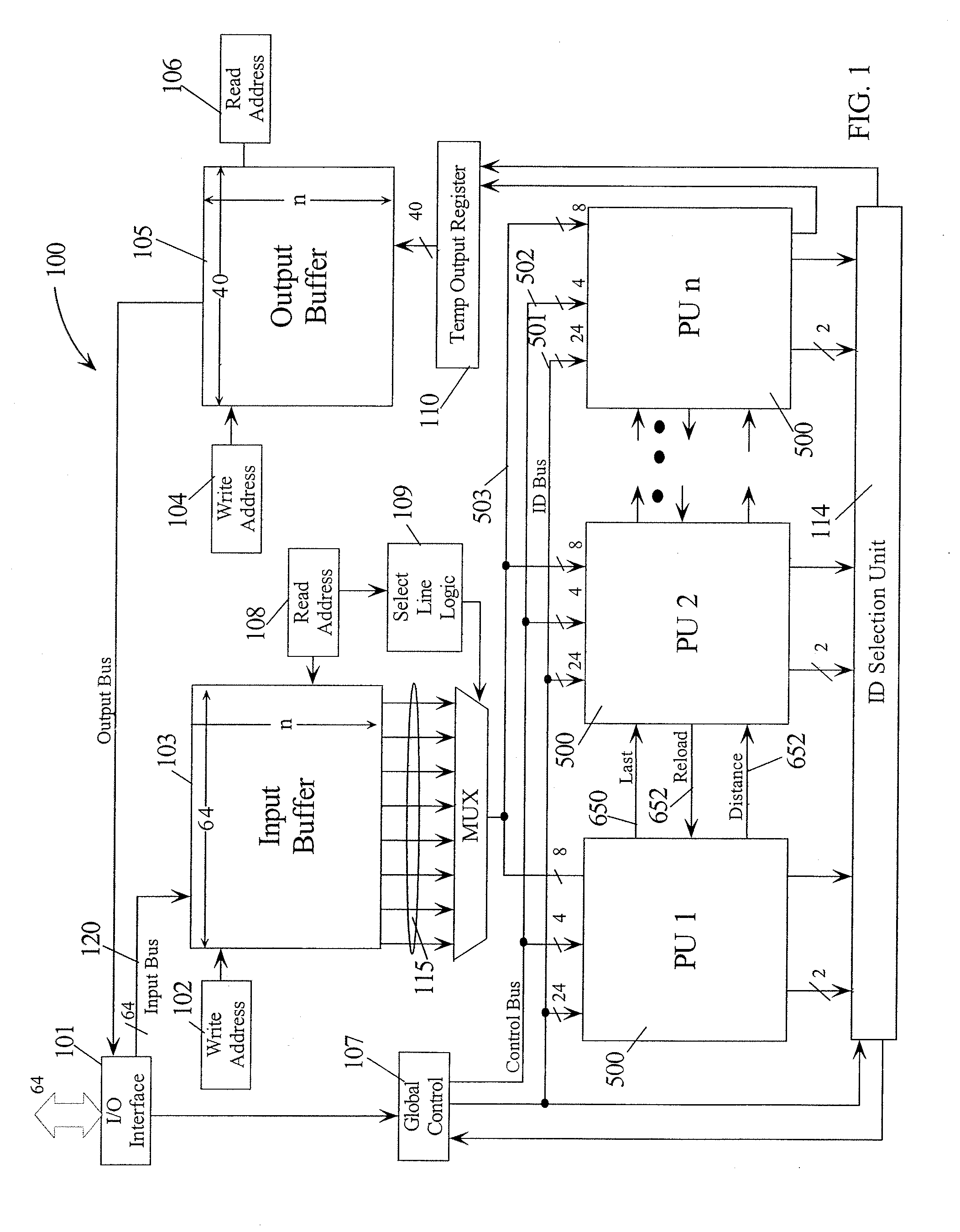
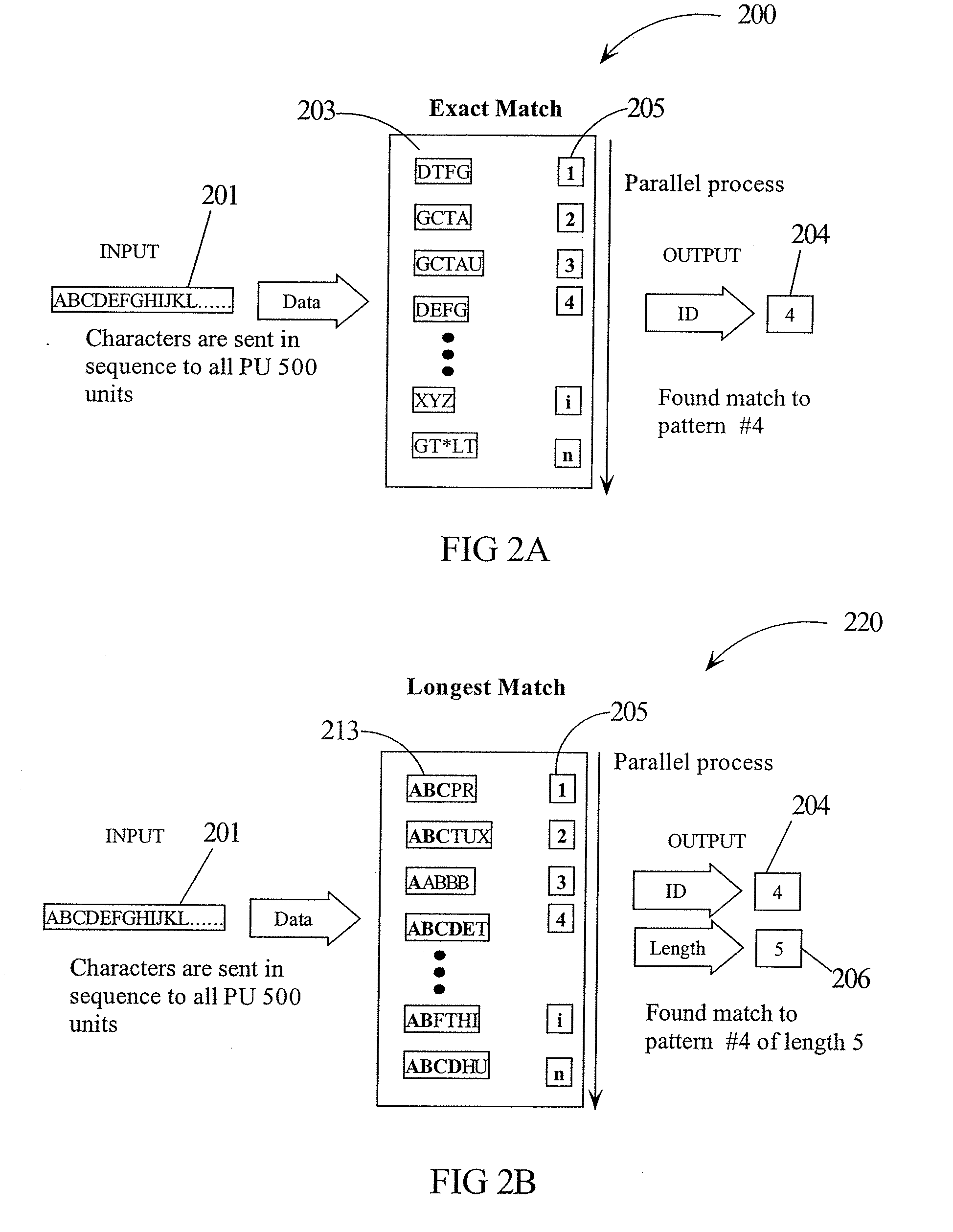
Intrusion detection using a network processor and a parallel pattern detection engine
InactiveUS7487542B2Improve scalabilityMemory loss protectionDigital data processing detailsData streamPattern matching
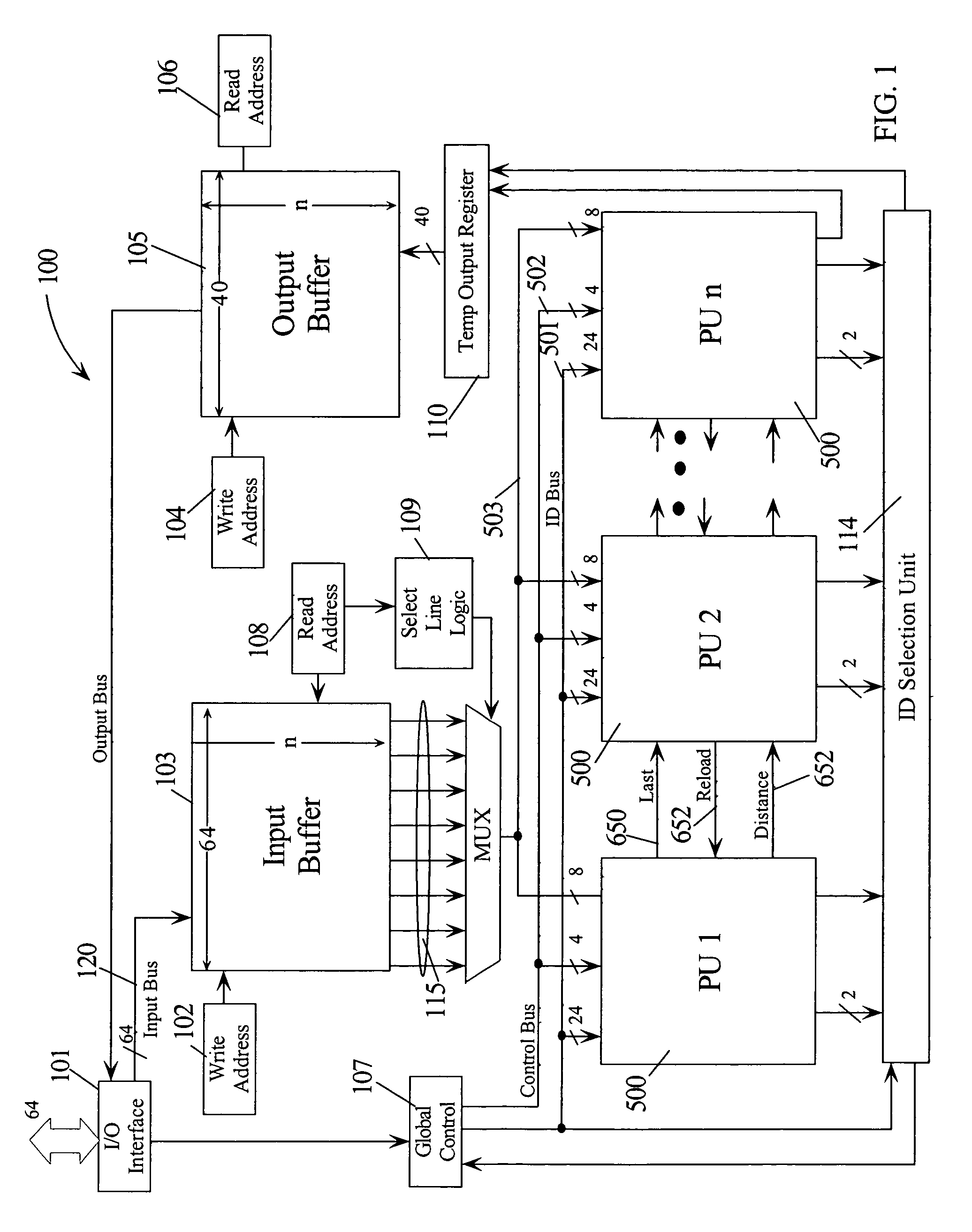
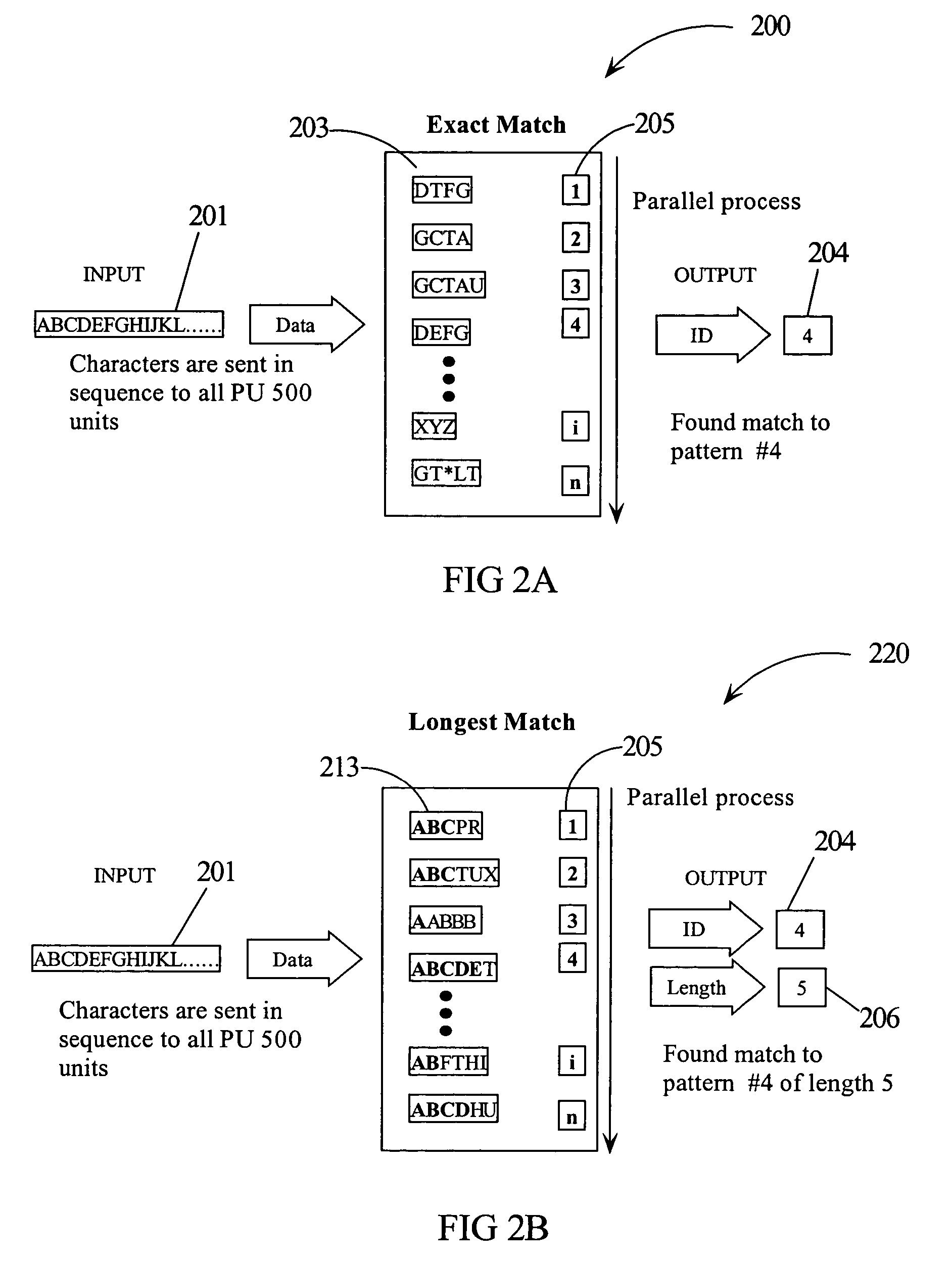
An intrusion detection system (IDS) comprises a network processor (NP) coupled to a memory unit for storing programs and data. The NP is also coupled to one or more parallel pattern detection engines (PPDE) which provide high speed parallel detection of patterns in an input data stream. Each PPDE comprises many processing units (PUs) each designed to store intrusion signatures as a sequence of data with selected operation codes. The PUs have configuration registers for selecting modes of pattern recognition. Each PU compares a byte at each clock cycle. If a sequence of bytes from the input pattern match a stored pattern, the identification of the PU detecting the pattern is outputted with any applicable comparison data. By storing intrusion signatures in many parallel PUs, the IDS can process network data at the NP processing speed. PUs may be cascaded to increase intrusion coverage or to detect long intrusion signatures.
Owner:TREND MICRO INC
Apparatus and method for detecting or recognizing pattern by employing a plurality of feature detecting elements
InactiveUS7054850B2High-precision detectionImprove process capabilityDigital computer detailsCharacter and pattern recognitionSynapsePattern detection
Owner:CANON KK
System and method for building a time series model
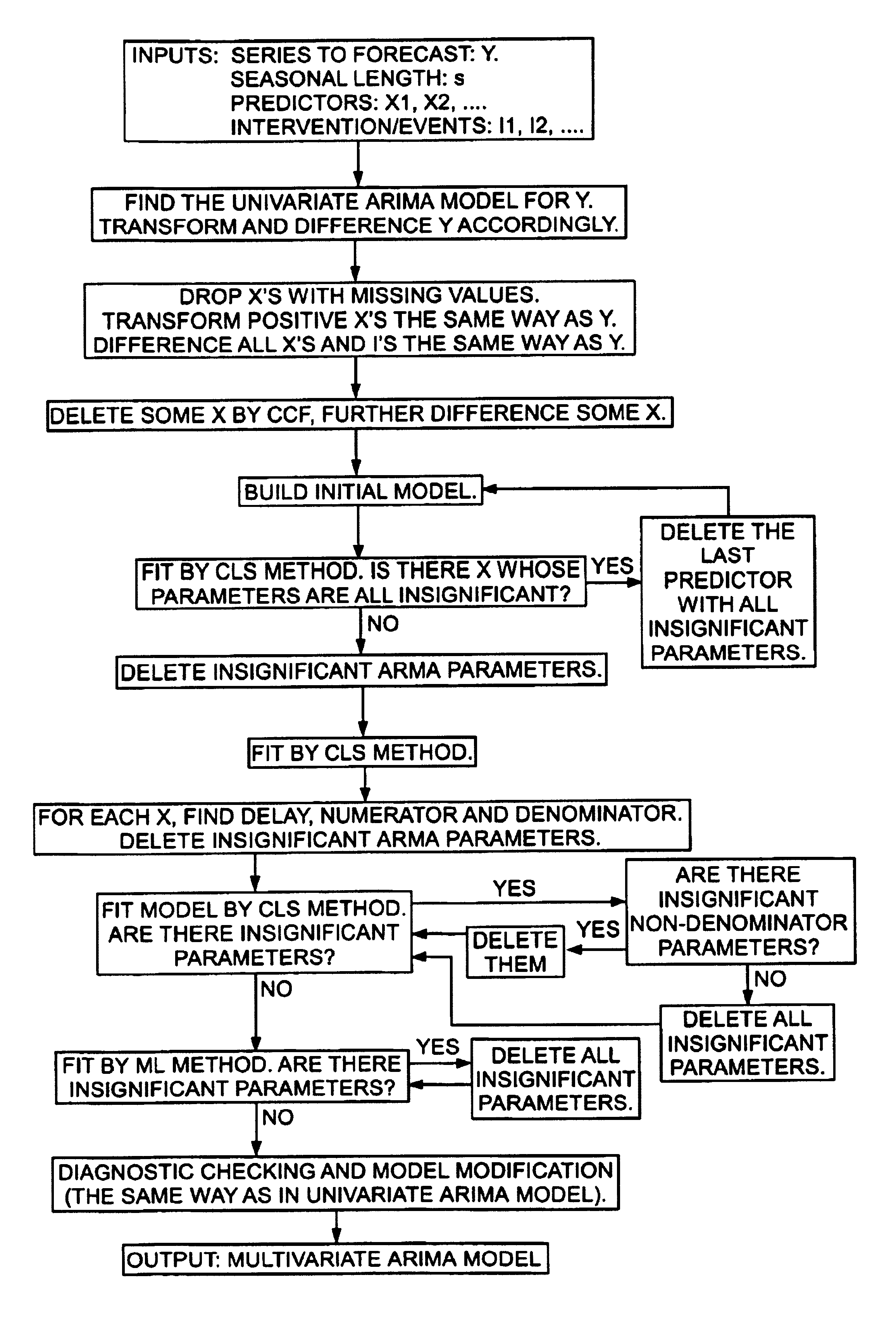
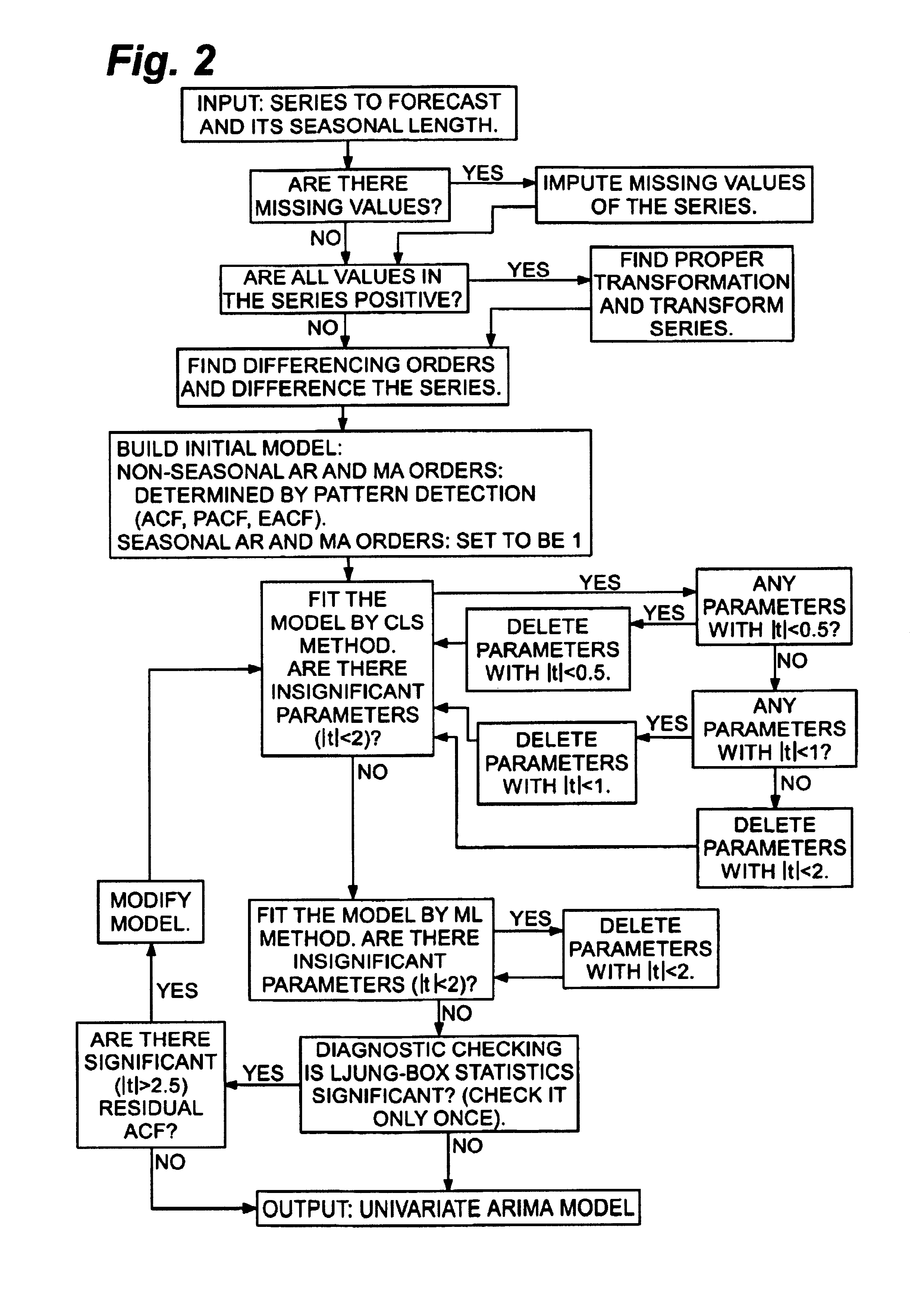
InactiveUS6928398B1Parameter estimates more accurateAvoid identificationComputation using non-denominational number representationResourcesAlgorithmPattern detection
A method and computer system is provided for automatically constructing a time series model for the time series to be forecasted. The constructed model can be either a univariate ARIMA model or a multivariate ARIMA model, depending upon whether predictors, interventions or events are inputted in the system along with the series to be forecasted. The method of constructing a univariate ARIMA model comprises the steps of imputing missing values of the time series inputted; finding the proper transformation for positive time series; determining differencing orders; determining non-seasonal AR and MA orders by pattern detection; building an initial model; estimating and modifying the model iteratively. The method of constructing a multivariate ARIMA model comprises the steps of finding a univariate ARIMA model for the time series to be forecasted by the method of constructing a univariate model; applying the transformation found in the univariate model to all positive time series including the series to be forecasted and predictors; applying differencing orders found in the univariate model to all time series including the series to be forecasted, predictors, interventions and events; deleting selected predictors and further differencing other predictors; building an initial model wherein its disturbance series follows an ARMA model with AR and MA orders found in the univariate model; estimating and modifying the model iteratively.
Owner:IBM CORP
Ac connected modules with line frequency or voltage variation pattern for energy control
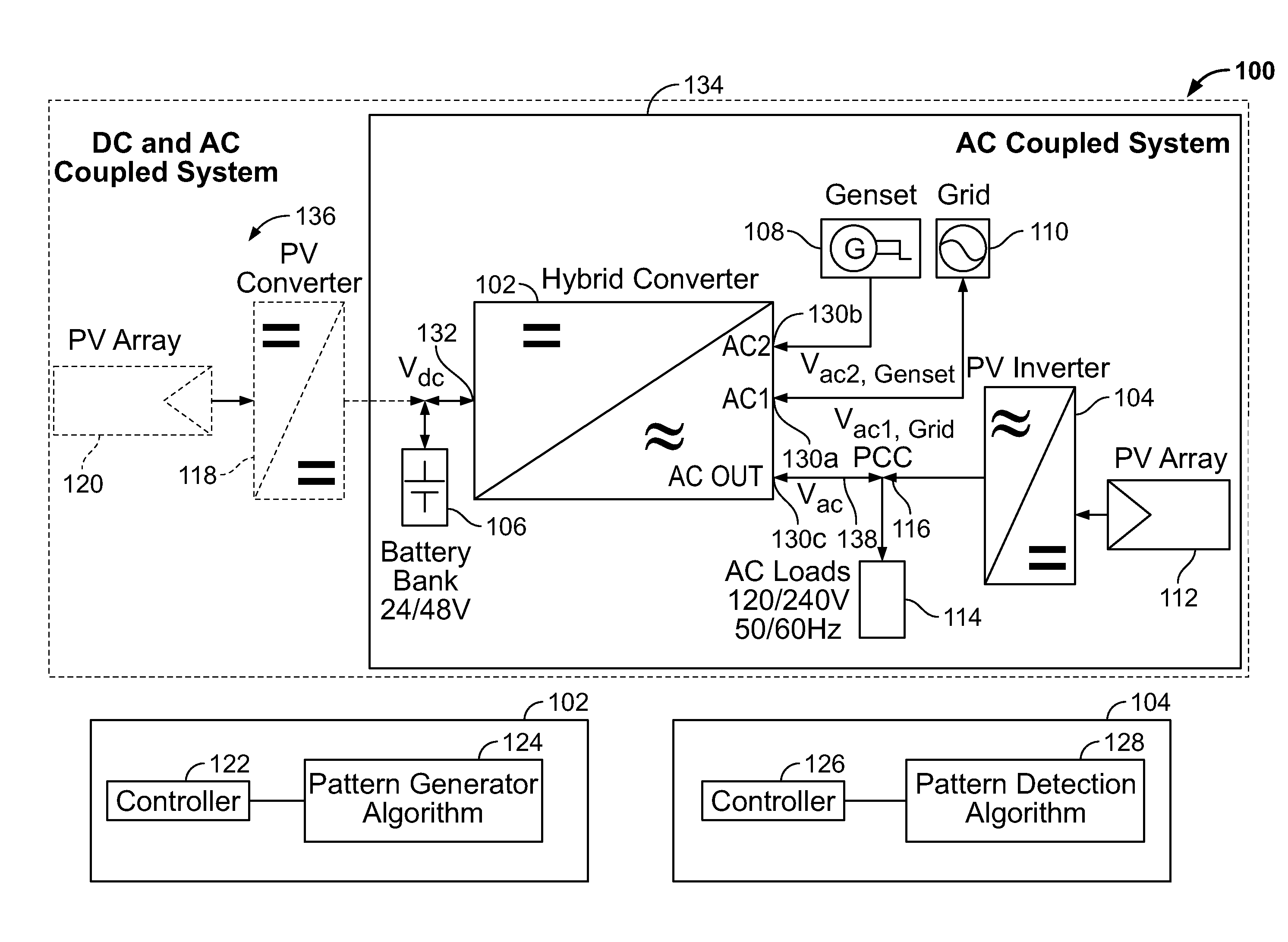
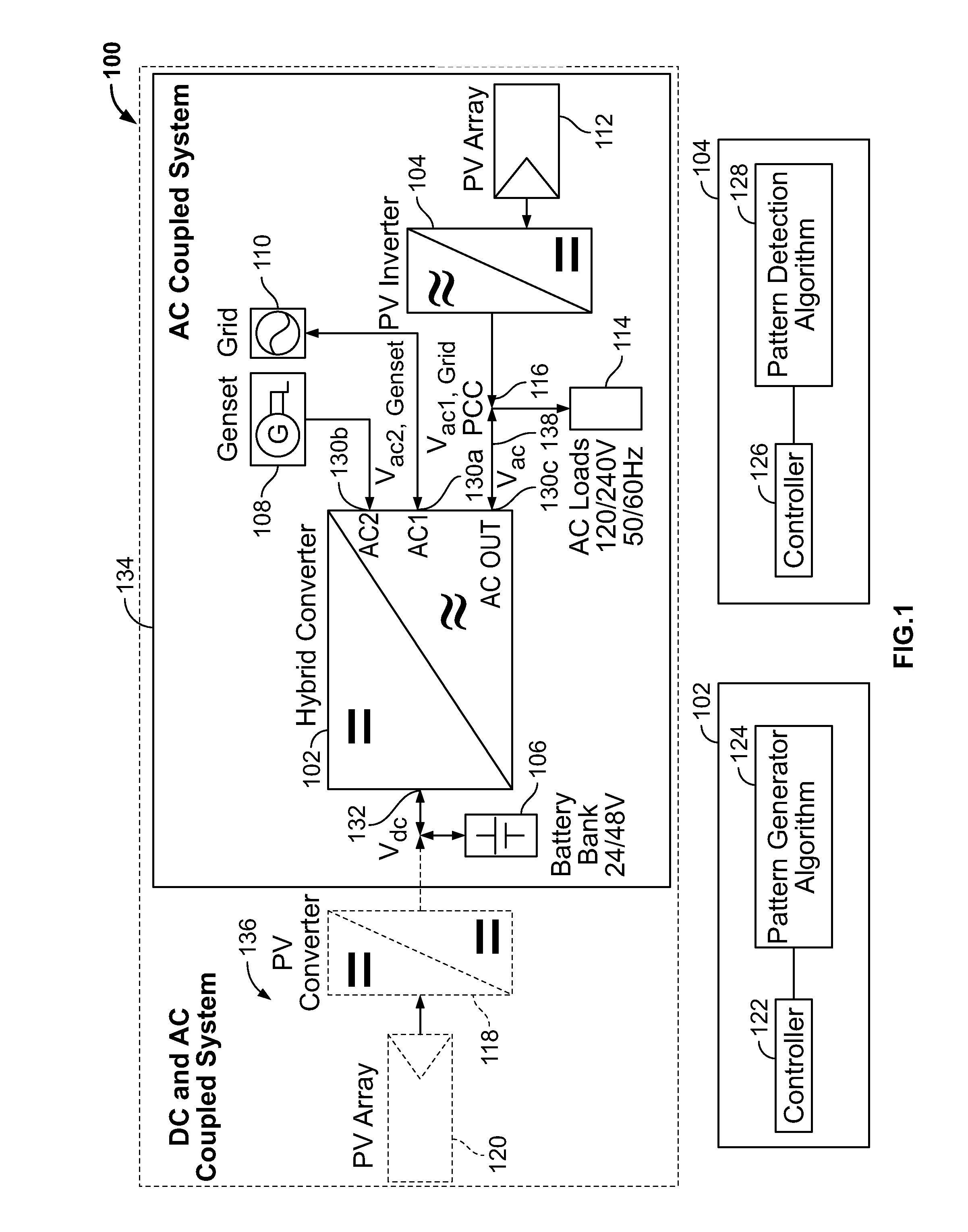
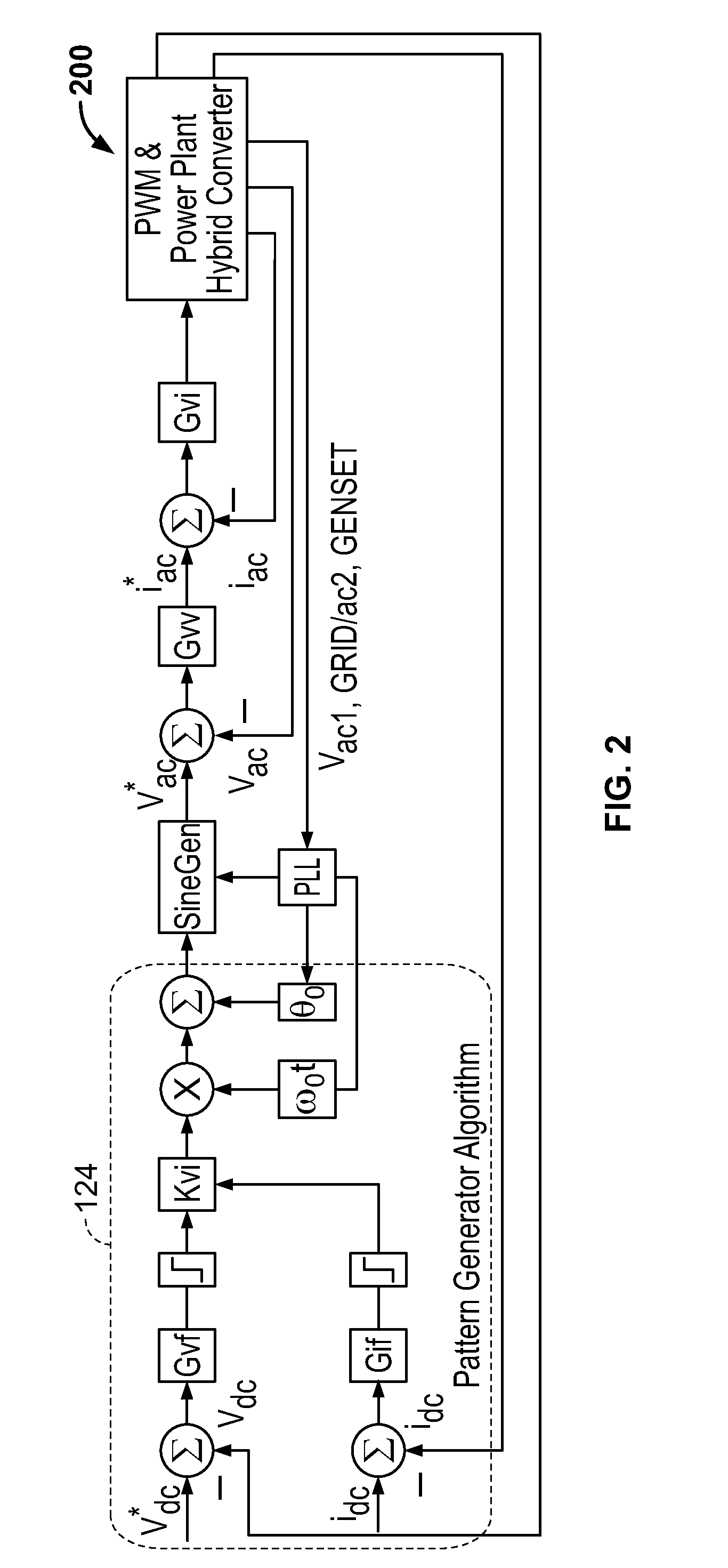
ActiveUS20110043160A1Maximize efficiencyEasy to controlBatteries circuit arrangementsPower supply linesIslandingEnergy control
A control strategy for distributed power generation modules in a power system that varies the line frequency or voltage according to a predetermined pattern to cause a PV inverter to modify its power output and thereby avoid overcharging a battery. When the power system operates in islanded mode, the AC load demand can be lower than the available energy from the PV array, causing the battery to become overcharged. To avoid this scenario, a hybrid inverter executes a pattern generator algorithm that varies the line frequency or voltage linearly, exponentially or any mathematical function or look-up tables. The PV inverter executes a pattern detection algorithm that detects the linear, exponential, or any mathematical function or look-up table change in the line frequency. In response, the PV inverter modifies its power output until an overcharging condition of the battery is removed. The line frequency / voltage can be varied within the anti-islanding limits to avoid premature disruption of the power system, and no additional settings are required at the device level in order to operate in any mode of operation: islanded, grid-connected or genset-connected.
Owner:SCHNEIDER ELECTRIC SOLAR INVERTERS USA
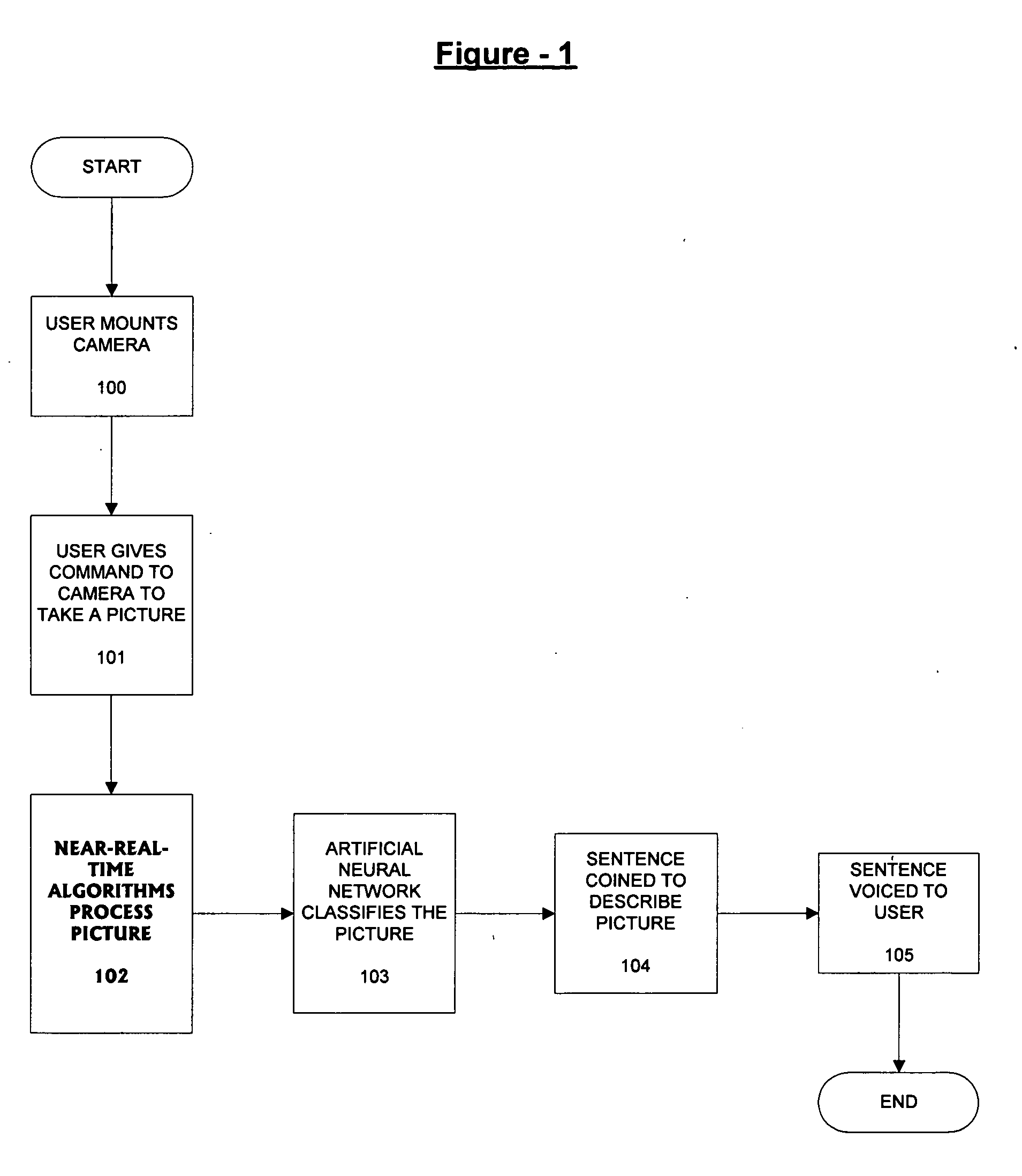
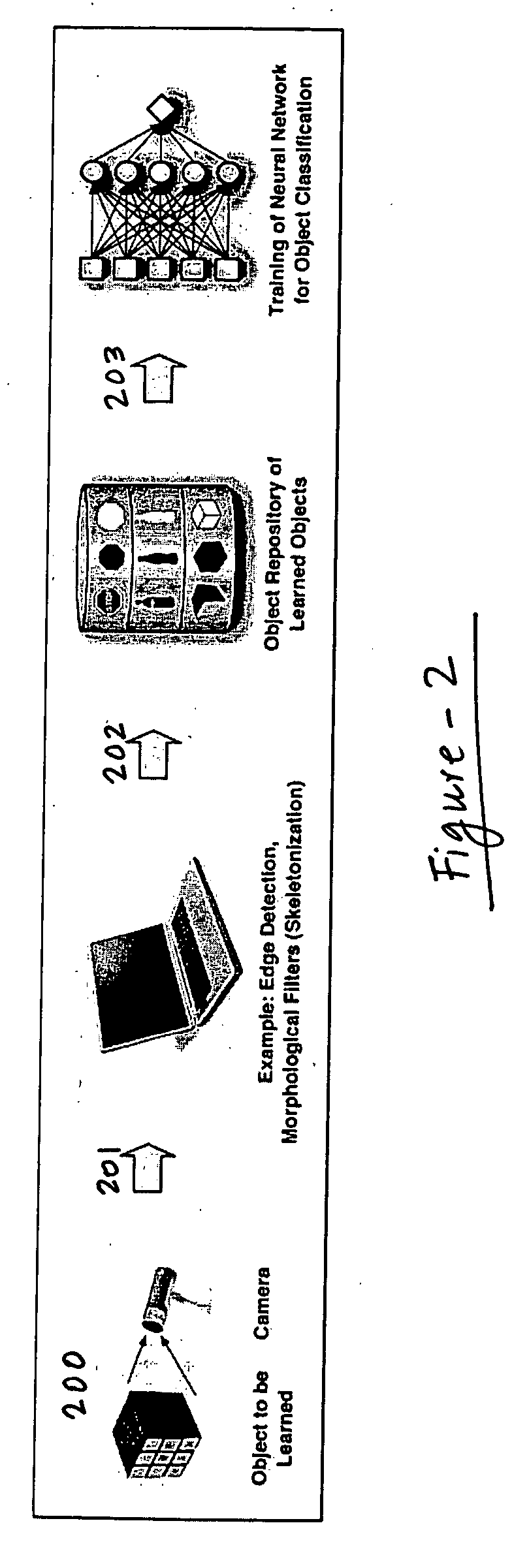
Digital object recognition audio-assistant for the visually impaired
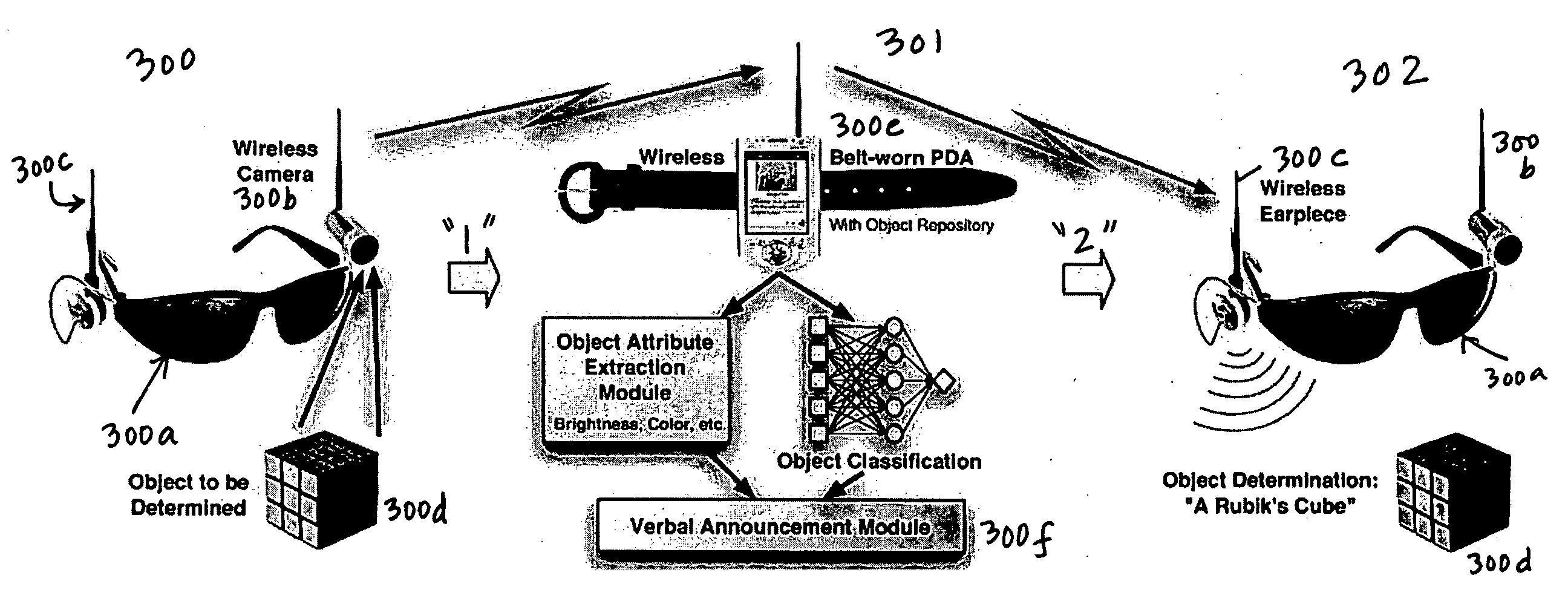
InactiveUS20050208457A1Character and pattern recognitionTeaching apparatusDECIPHERVisually Impaired Persons
A camera-based object detection system for a severely visually impaired or blind person consisting a digital camera mounted on the person's eyeglass or head that takes images on demand. Near-real time image processing algorithms decipher certain attributes of the captured image by processing it for edge pattern detection within a central region of the image. The results are classified by artificial neural networks trained on a list of known objects, in a look up table, or by a threshold. Once the pattern is classified a descriptive sentence is constructed of the object and its certain attributes and a computer-based voice synthesizer is used to verbally announce the descriptive sentence. The invention is used to determine the size of an object, or its distance from another object, and can be used in conjunction with an IR-sensitive camera to provide “sight” in poor visibility conditions, or at night.
Owner:CALIFORNIA INST OF TECH
Apparatus and method for cell search in mobile communication system using a multiple access scheme
InactiveUS20050002369A1Increase speedModulated-carrier systemsTransmission monitoringPattern detectionCell search
An apparatus and a method for cell search in an orthogonal frequency division multiplexing-based mobile communication system using a multiple access scheme. The method includes the steps of: detecting a symbol boundary of an input reception signal; detecting a frame cell boundary after synchronizing with the detected symbol boundary; detecting a reference signal for each symbol interval in a preset search interval; and detecting a pattern of the detected reference signals and detecting a base station to which the terminal belongs.
Owner:SAMSUNG ELECTRONICS CO LTD
Processing a video for vascular pattern detection and cardiac function analysis
InactiveUS20130322729A1Quick discoveryEffective toolImage enhancementImage analysisPattern detectionLength wave
What is disclosed is a non-contact system and method for determining cardiac function parameters from a vascular pattern identified from RGB and IR video signals captured simultaneously of a region of exposed skin of a subject of interest. In one embodiment, a video of a region of exposed skin is captured using a video camera that captures color values for pixels over visible channels and an IR camera that measures pixel intensity values in wavelength ranges of interest. Pixel intensity values are processed to generate a vascular binary mask that indicates pixel locations corresponding to the vascular pathways. The IR images are registered with corresponding data from the camera's visible channels such that pixels that correspond to the vascular pattern can be isolated in each frame of the video of visible color data. Once processed, pixels associated with the isolated vascular patterns are analyzed to determine desired cardiac function parameters.
Owner:XEROX CORP
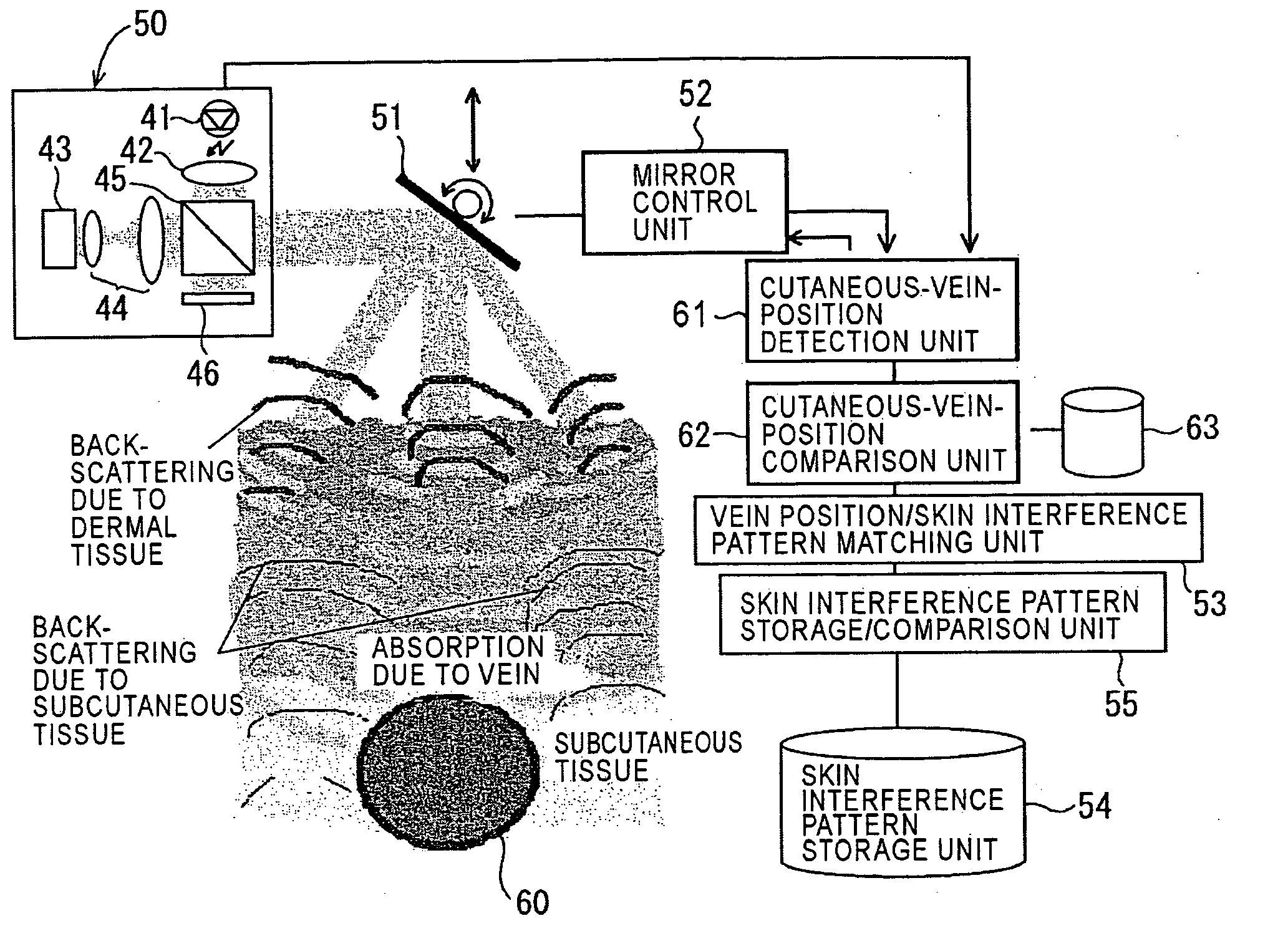
Method of detecting biological pattern, biological pattern detector, method of biological certificate and biological certificate apparatus
InactiveUS20050180620A1Reduce adverse effectsEfficient detectionImage enhancementImage analysisOptical propertyPattern detection
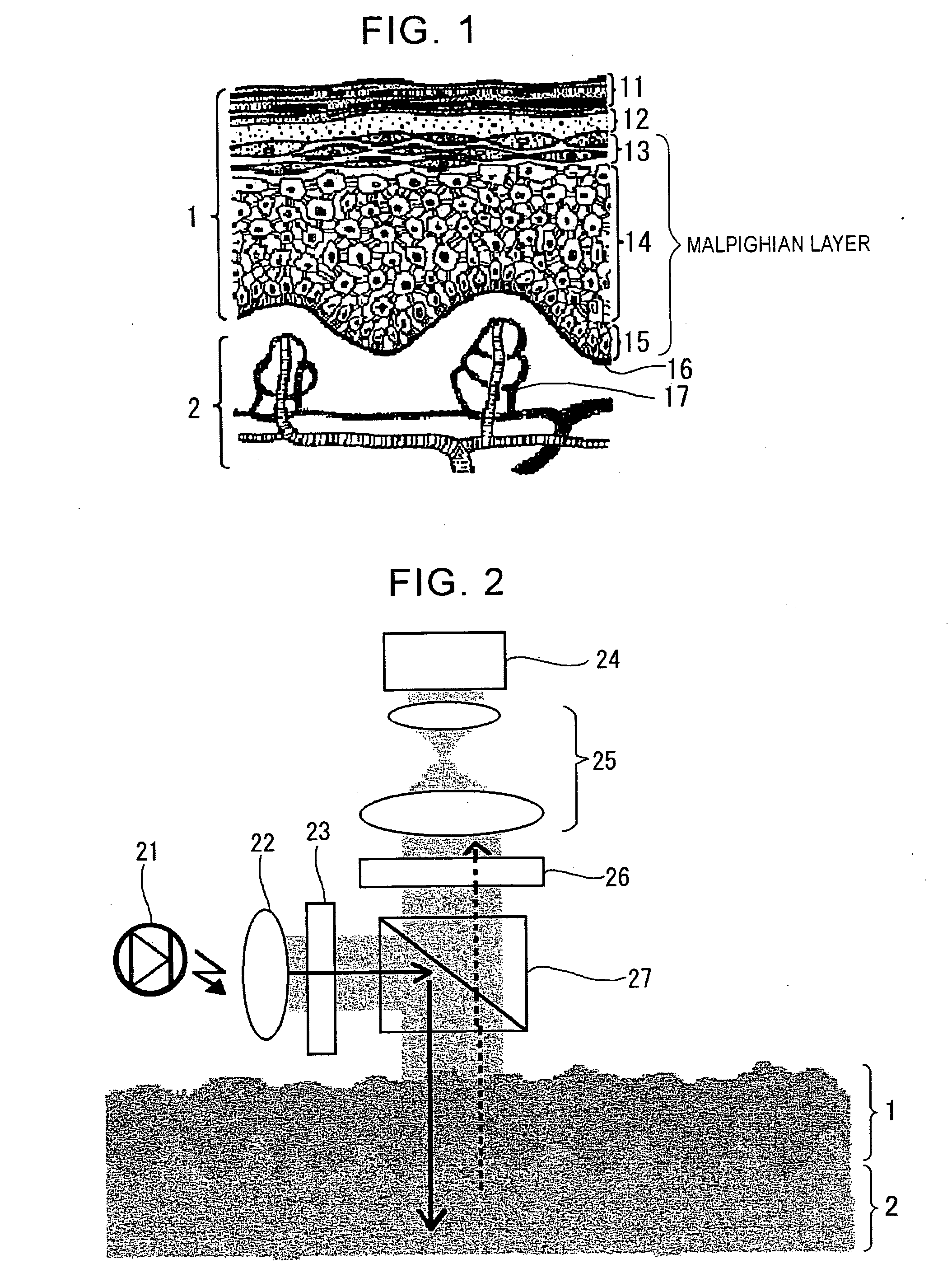
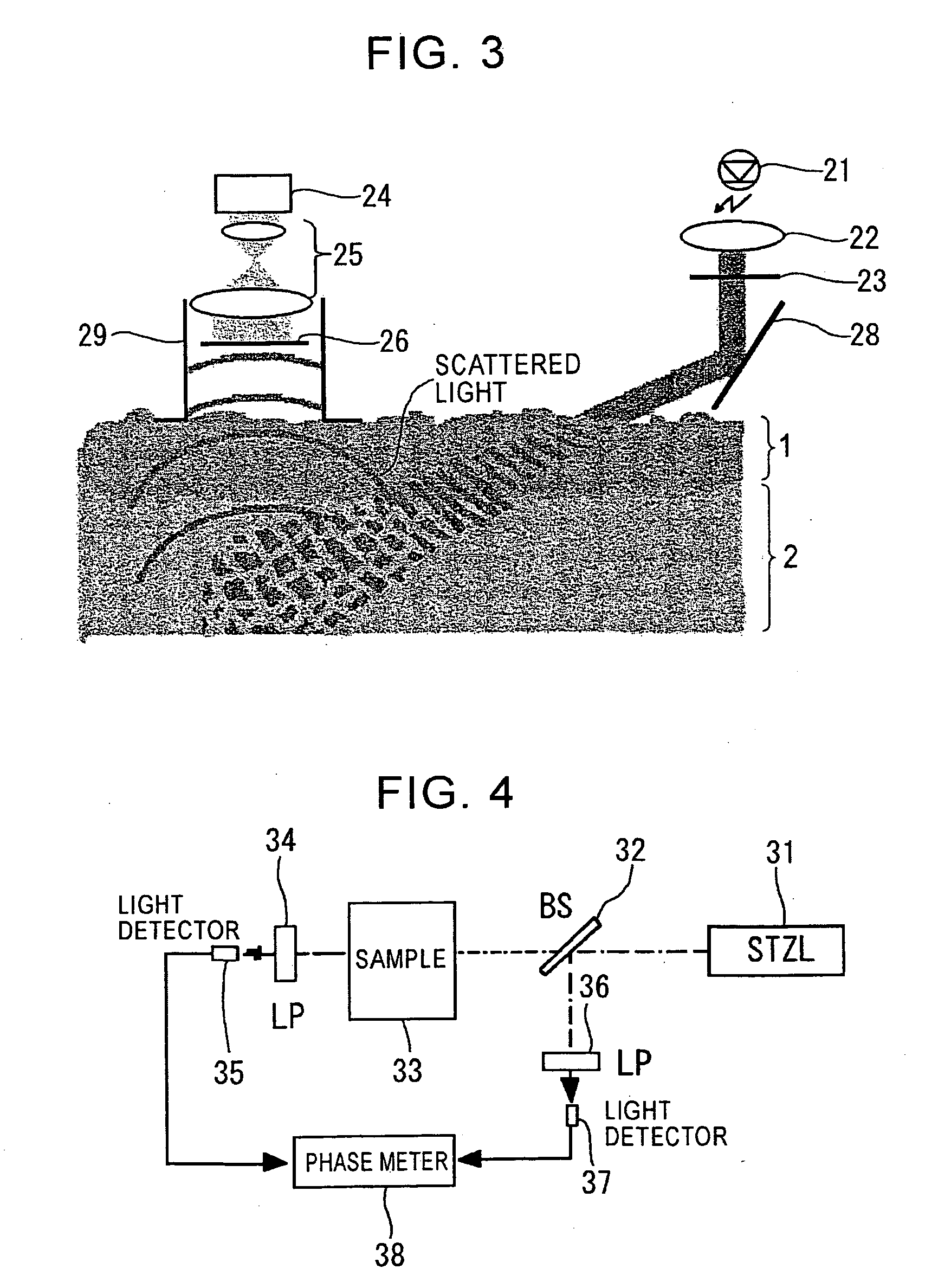
The present invention enables permanent biometric authentication without the risk of forgery or the like. The present invention enables living-tissue discrimination as well as biometric authentication. The roughness distribution pattern of deep-layer tissue of the skin covered with epidermal tissue is detected, thereby extracting a unique pattern of the living tissue. Then, biometric authentication is performed based upon the detected pattern. The roughness distribution pattern of the deep-layer tissue of the skin is optically detected using difference in optical properties between the epidermal tissue and the deep-layer tissue of the skin. In this case, long-wavelength light, e.g., near-infrared light is used as illumination light cast onto the skin tissue. A fork structure of a subcutaneous blood vessel is used as the portion which is to be detected, for example. The portion which is to be detected is determined based upon the structure of the fork structure. In this case, the living-tissue discrimination may be made using the subcutaneous blood vessel.
Owner:SONY CORP
Multimodal user interface
InactiveUS6779060B1Different length of timeLevel of tolerance to inherentExecution for user interfacesInput/output processes for data processingUser inputPattern detection
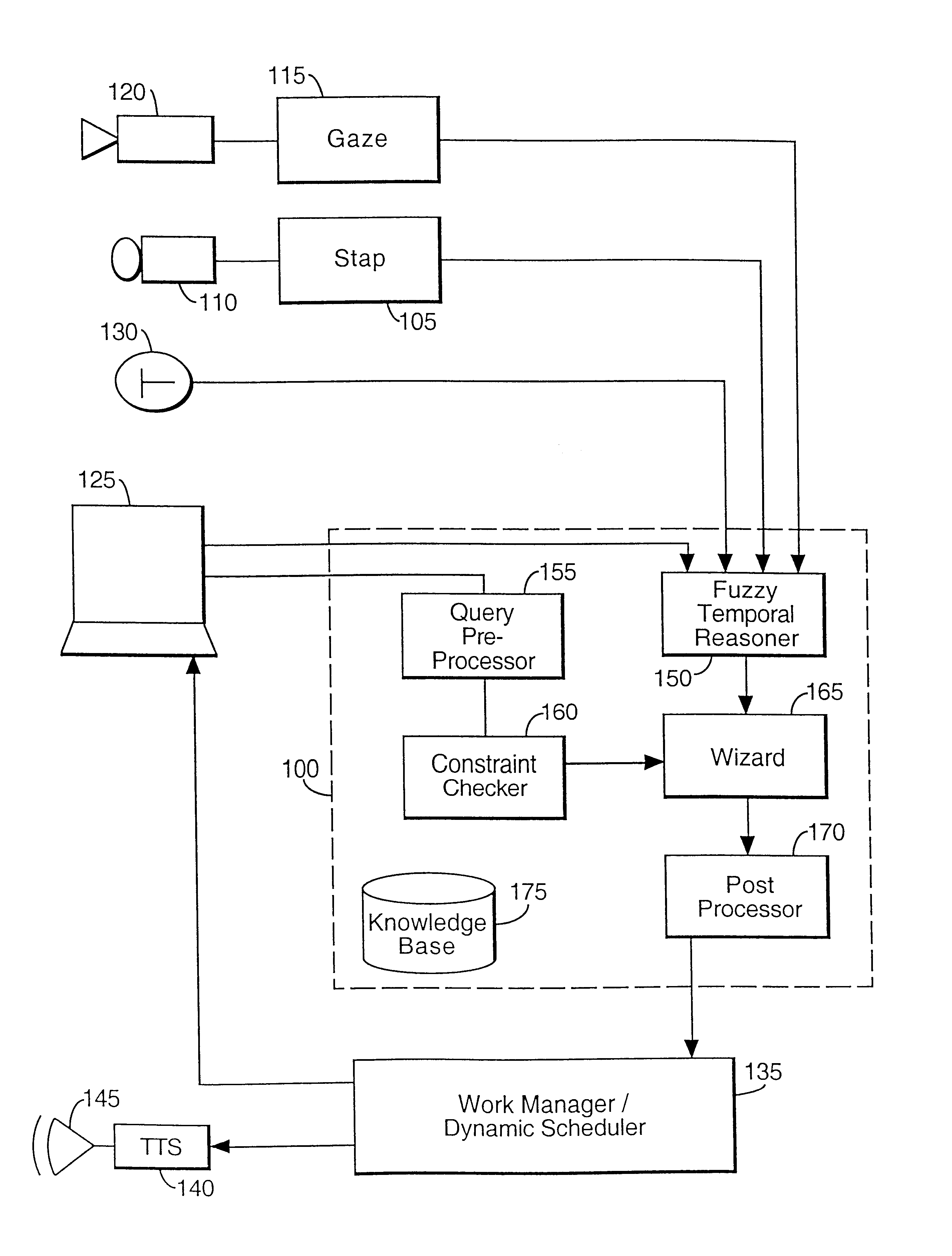
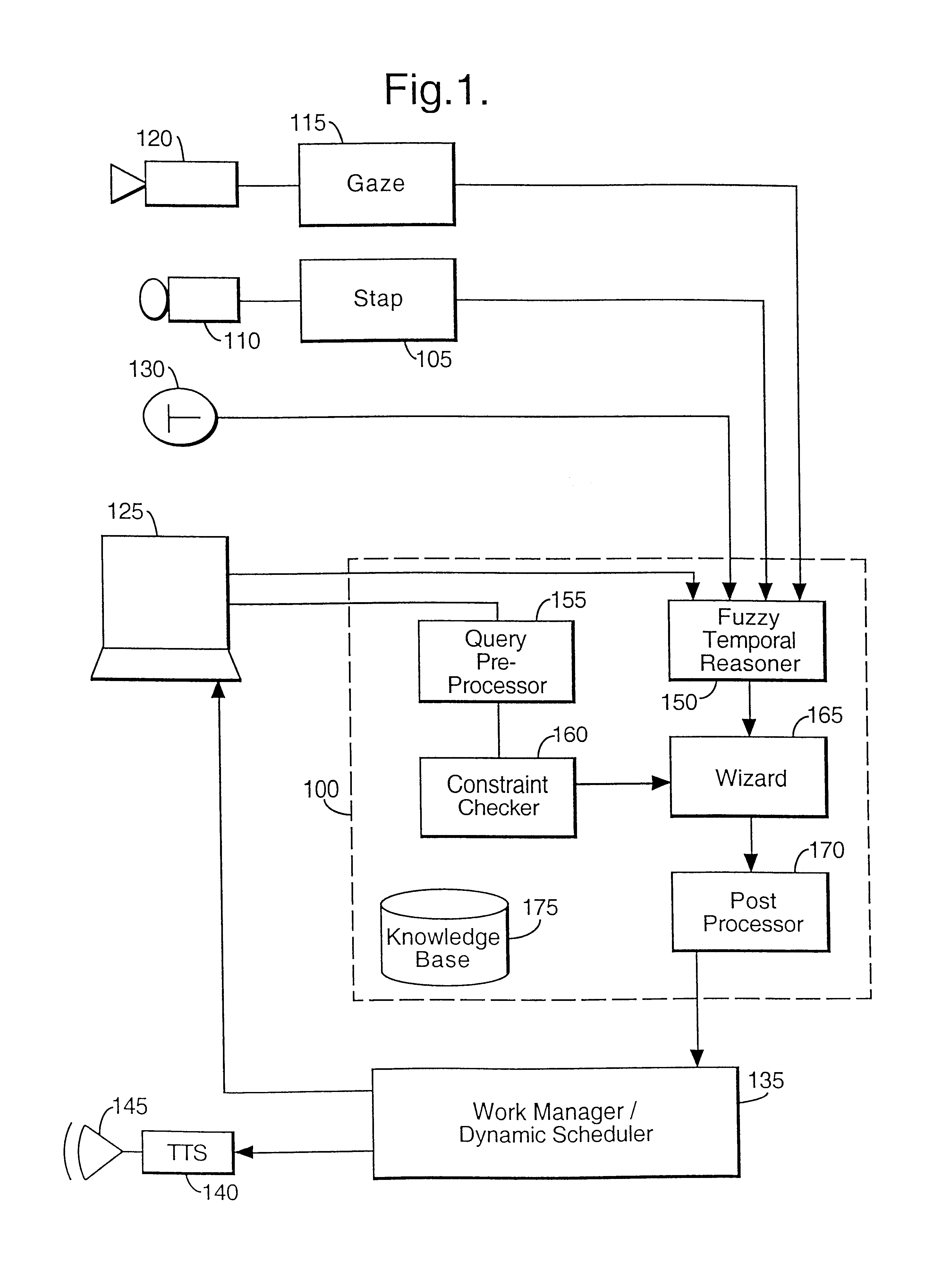
In a multi-modal user interface, user inputs may be made in various different ways. For instance, the user might use a keyboard, a speech system, a vision system, a mouse or pen. Different inputs made by the user may be related and may have different significance. A processing system detects and resolves ambiguities and / or conflicts in inputs made by the user using the different input modes available.
Owner:BRITISH TELECOMM PLC
Pattern detection in time-series data
ActiveUS20190379589A1Improve performanceHardware monitoringCharacter and pattern recognitionPattern detectionNetwork model
Systems and methods for detecting patterns in data from a time-series are provided. In one implementation, a method for pattern detection includes obtaining data in a time-series and creating one-dimensional or multi-dimensional windows from the time-series data. The one-dimensional or multi-dimensional windows are created either independently or jointly with the time-series. The method also includes training a deep neural network with the one-dimensional or multi-dimensional windows utilizing historical and / or simulated data to provide a neural network model. Also, the method includes processing ongoing data with the neural network model to detect one or more patterns of a particular category in the ongoing data, and localizing the one or more patterns in time.
Owner:CIENA
Method and Apparatus for Deep Packet Inspection
A system and method is provided for detecting malicious data such as, for example, viruses in a computer network. More specifically, system and method utilizes filters to detect pre-identified patterns or threat signatures in a data stream. In one embodiment, a deep packet inspection system for detecting a plurality of malicious programs in a data packet received from a network, wherein each malicious program has a unique pattern comprising a plurality of segments, includes a plurality of pattern detection modules configured to receive one or more data packets in parallel, wherein each of the plurality of pattern detection modules has an output, and one or more long pattern state machines coupled to the outputs of the plurality of pattern detection modules. The deep packet inspection system is configured to detect a pattern of any length at any location within a data packet.
Owner:RGT UNIV OF CALIFORNIA
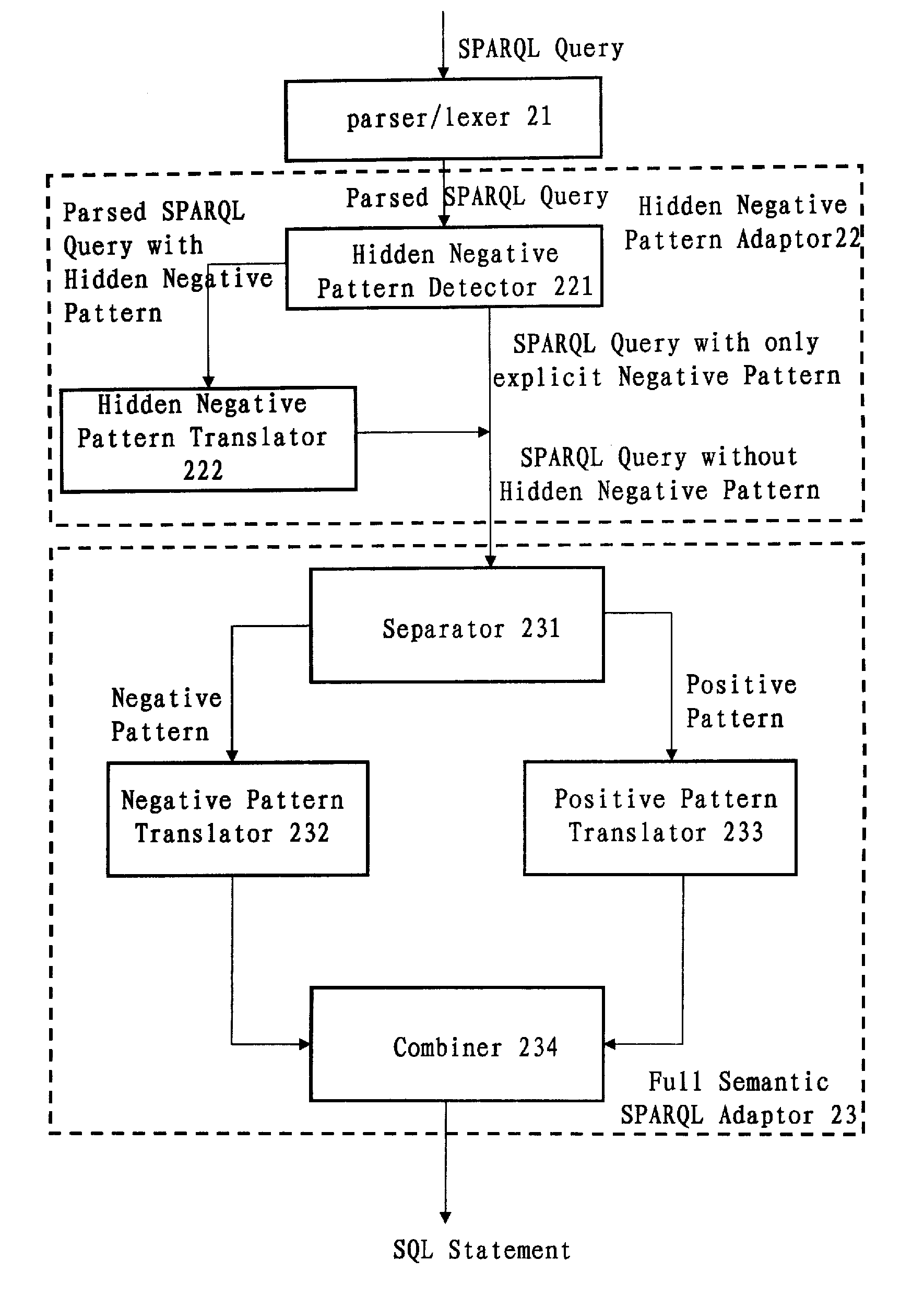
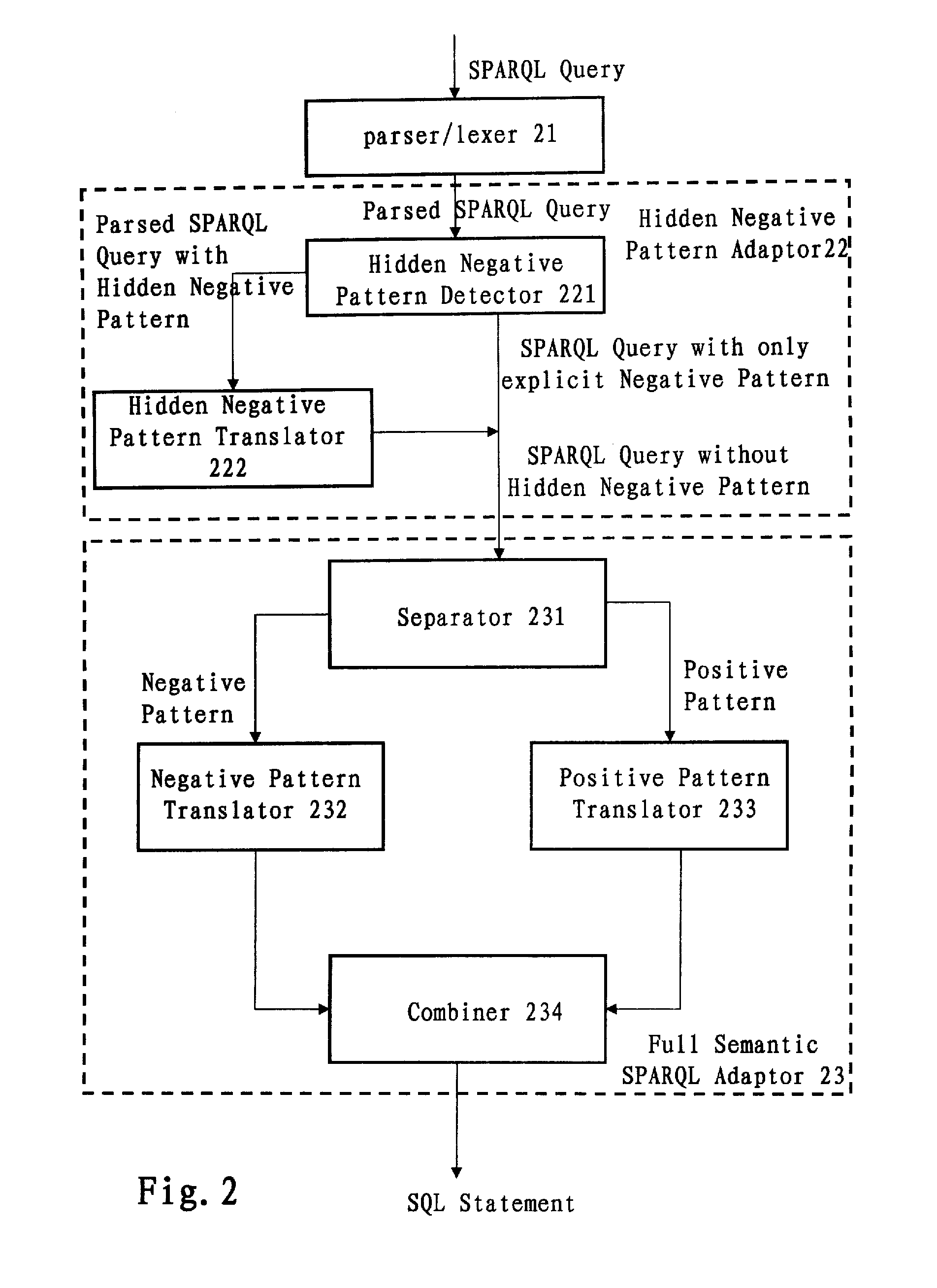
Translation system and method for sparql queries
InactiveUS20100250577A1Efficiently translatedDigital data information retrievalDigital data processing detailsLexical analysisPattern detection
A computer-implemented system and method for translating a SPARQL query. The system includes: a parser / lexer for parsing the SPARQL query; a hidden negative pattern detector for detecting a hidden negative pattern in the parsed SPARQL query; a hidden negative pattern translator for translating the detected hidden negative pattern into an explicit negative pattern; a separator for separating the explicit negative pattern from a positive pattern in the parsed SPARQL query; a negative pattern translator for translating the explicit negative pattern into a negative portion of an SQL statement; a positive pattern translator for translating the positive pattern into a positive portion of the SQL statement; and an SQL statement combiner for combining the negative portion of the SQL statement with the positive portion of the SQL statement.
Owner:IBM CORP
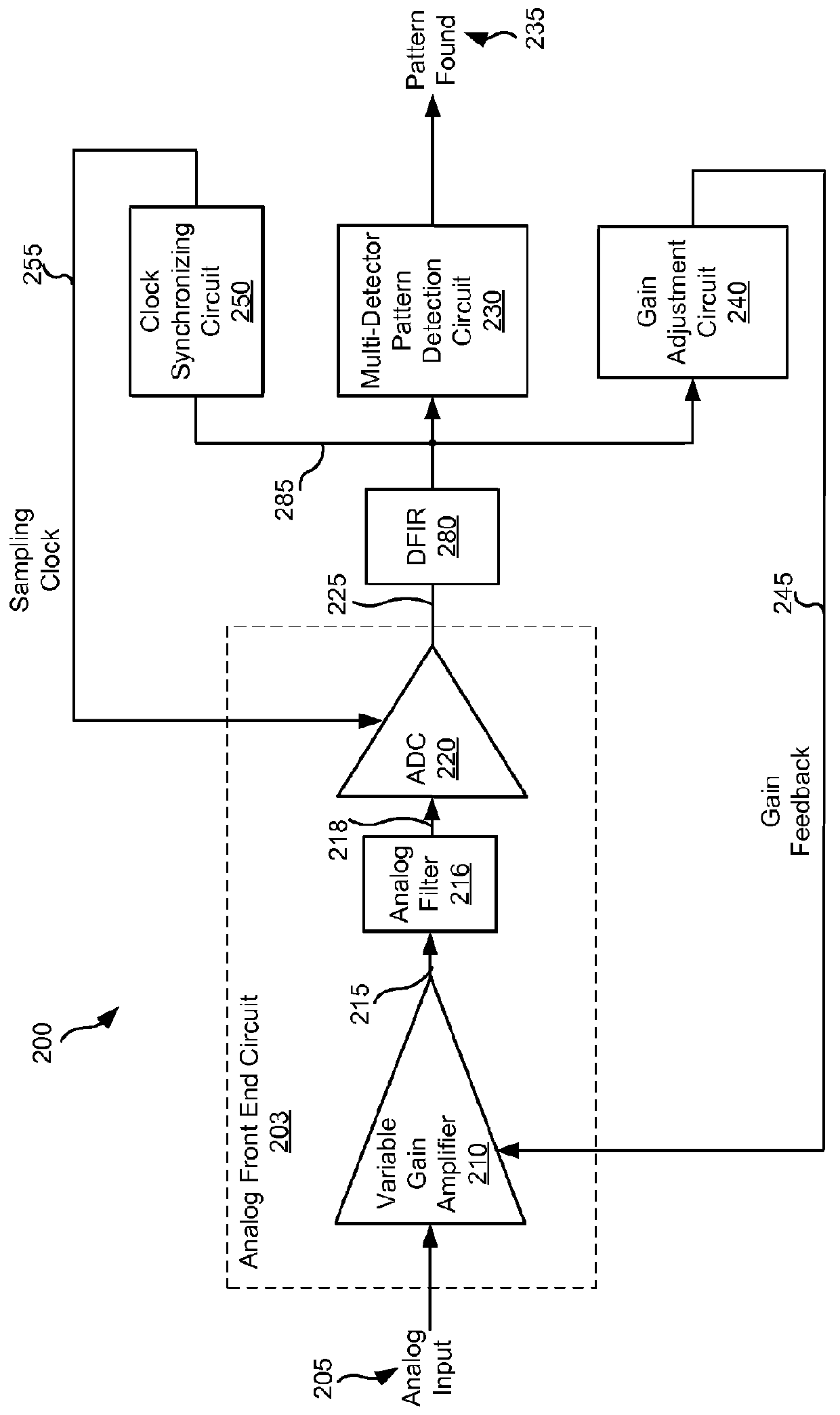
Systems and methods for diversity combined data detection
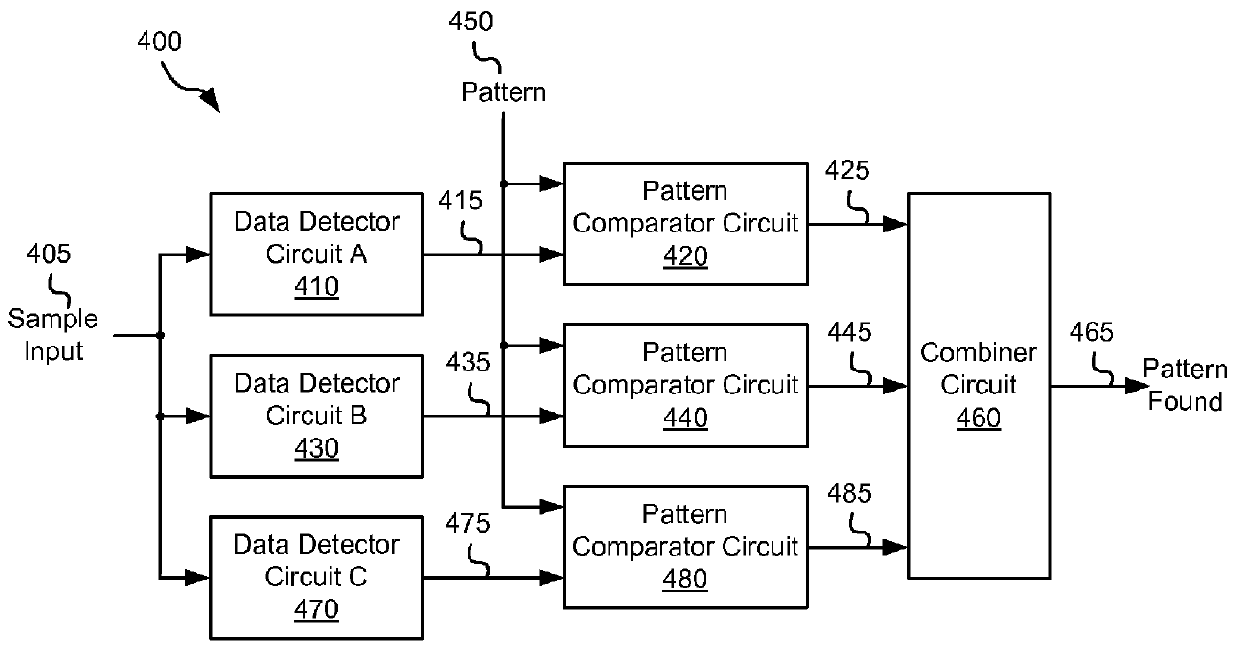
InactiveUS8261171B2Data representation error detection/correctionDigital data processing detailsDetector circuitsPattern detection
Various embodiments of the present invention provide systems and methods for data processing. For example, some embodiments of the present invention provide data processing circuits including a pattern detection circuit having at least two data detector circuits each operable to receive the same series of data samples and to provide a first detected data output and a second detected data output, respectively. In addition, the data pattern detection circuit includes a result combining circuit that is operable to assert a pattern found output based at least in part on the first detected data output and the second detected data output.
Owner:BROADCOM INT PTE LTD
Scattered pilot location detector
ActiveUS20080095255A1Polarisation/directional diversityTransmission path divisionBinary multiplierPhase difference
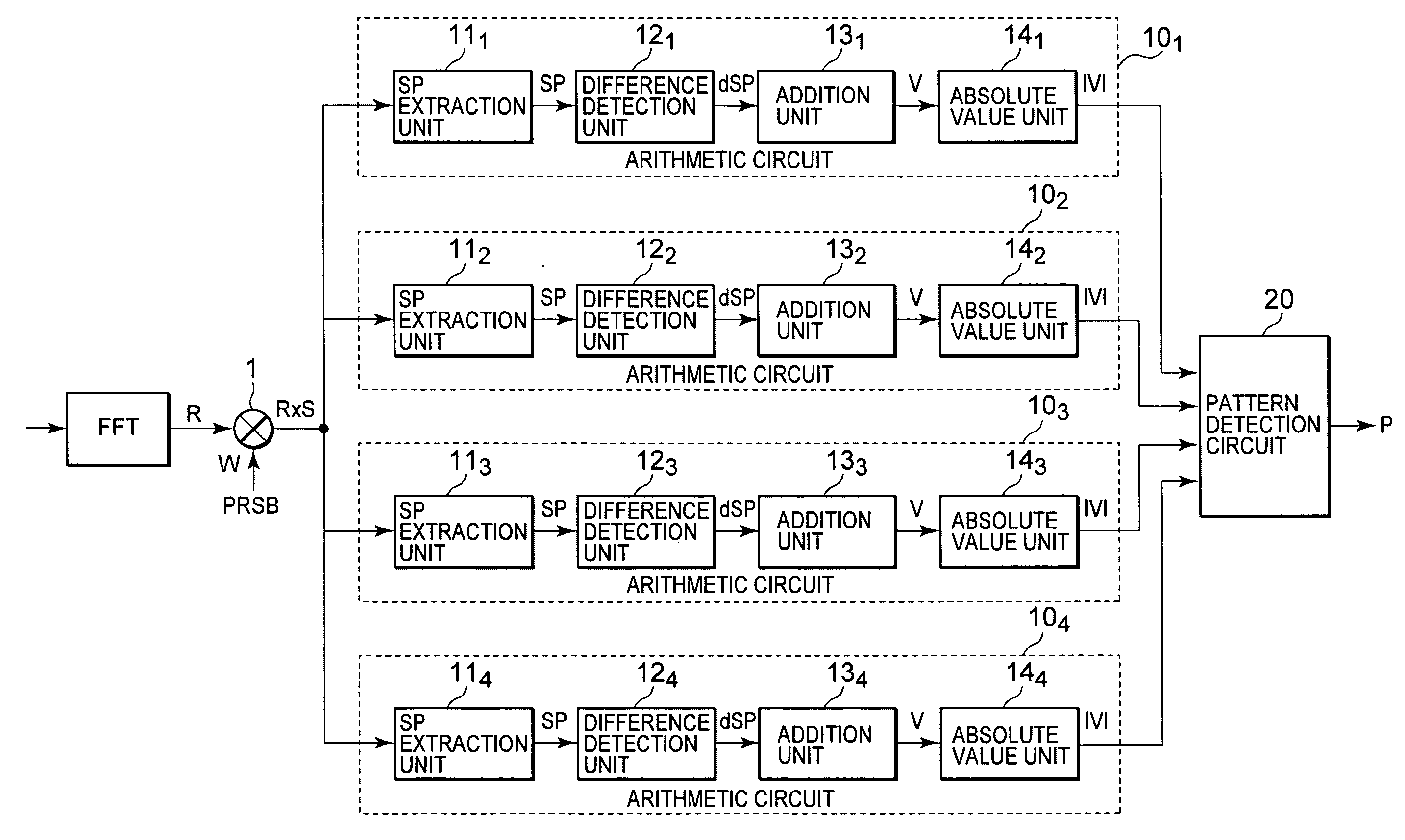
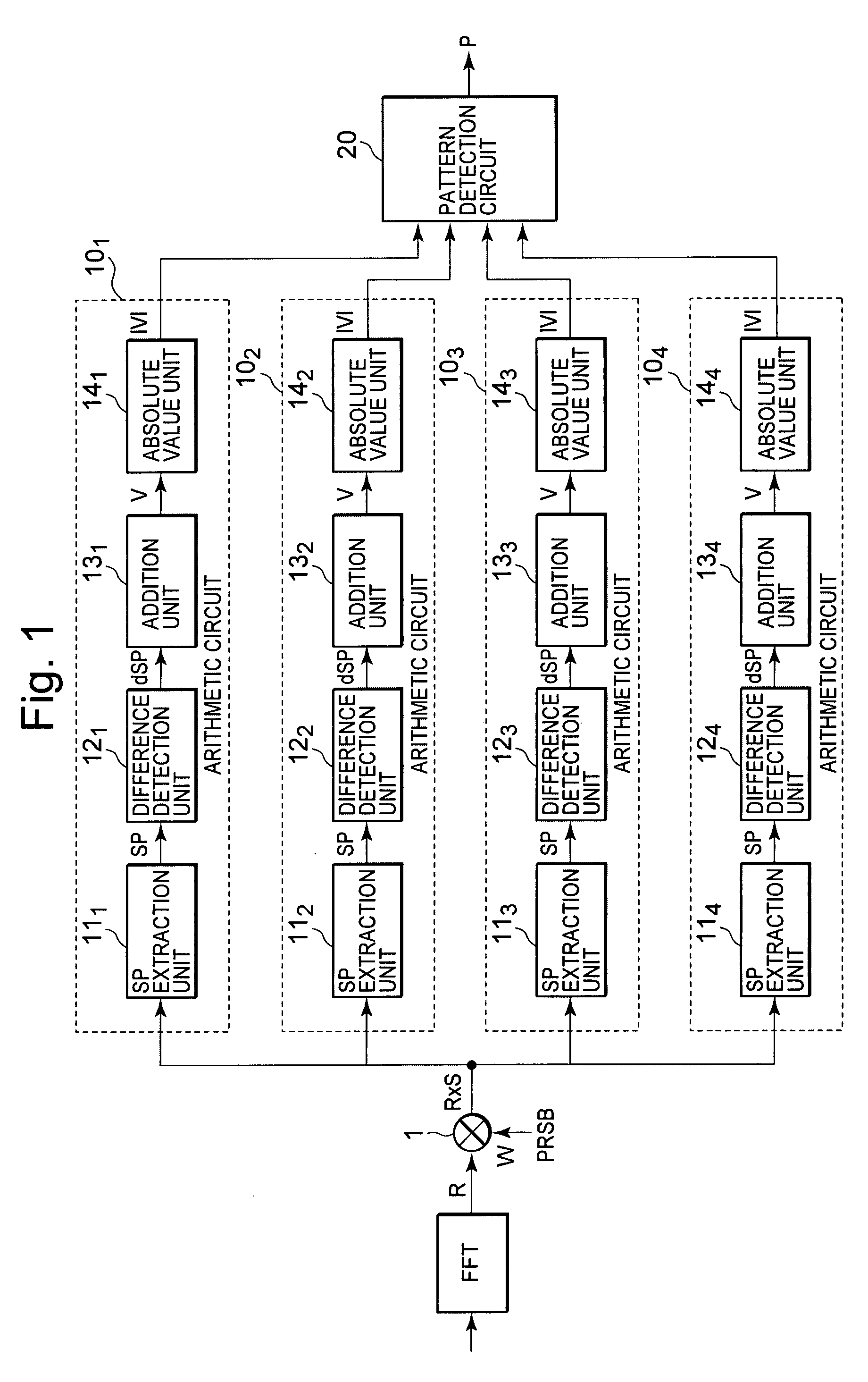
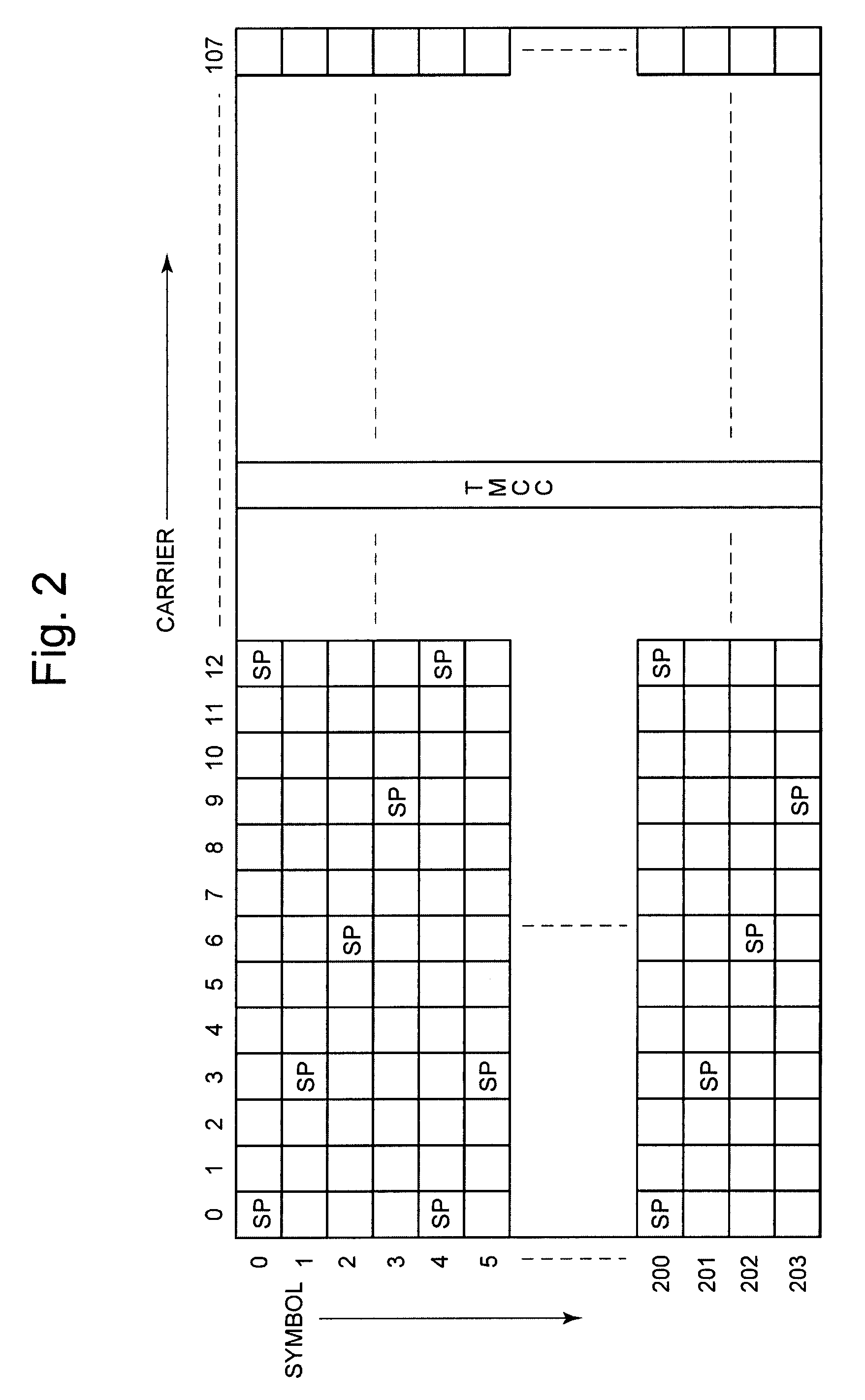
The present invention provides a scattered pilot (SP) location detector capable of detecting patterns of SP symbols promptly without using a TMCC signal. The SP location detector comprises a multiplier which multiplies received signals generated by demodulating OFDM modulation signals in which pilot symbols are dispersively disposed in accordance with four types of patterns and which are transmitted periodically, by a pseudo-random number bit sequence, four arithmetic circuits which are respectively provided corresponding to the four types of patterns and which respectively extract pilot symbols corresponding to respective patterns from results of multiplication by the multiplier and calculate sums of phase differences between the extracted pilot symbols, followed by outputting absolute values thereof, and a pattern detection circuit which detects the corresponding arithmetic circuit maximum in the calculated absolute value from within the four arithmetic circuits.
Owner:LAPIS SEMICON CO LTD
Method and apparatus for detecting a liquid spray pattern
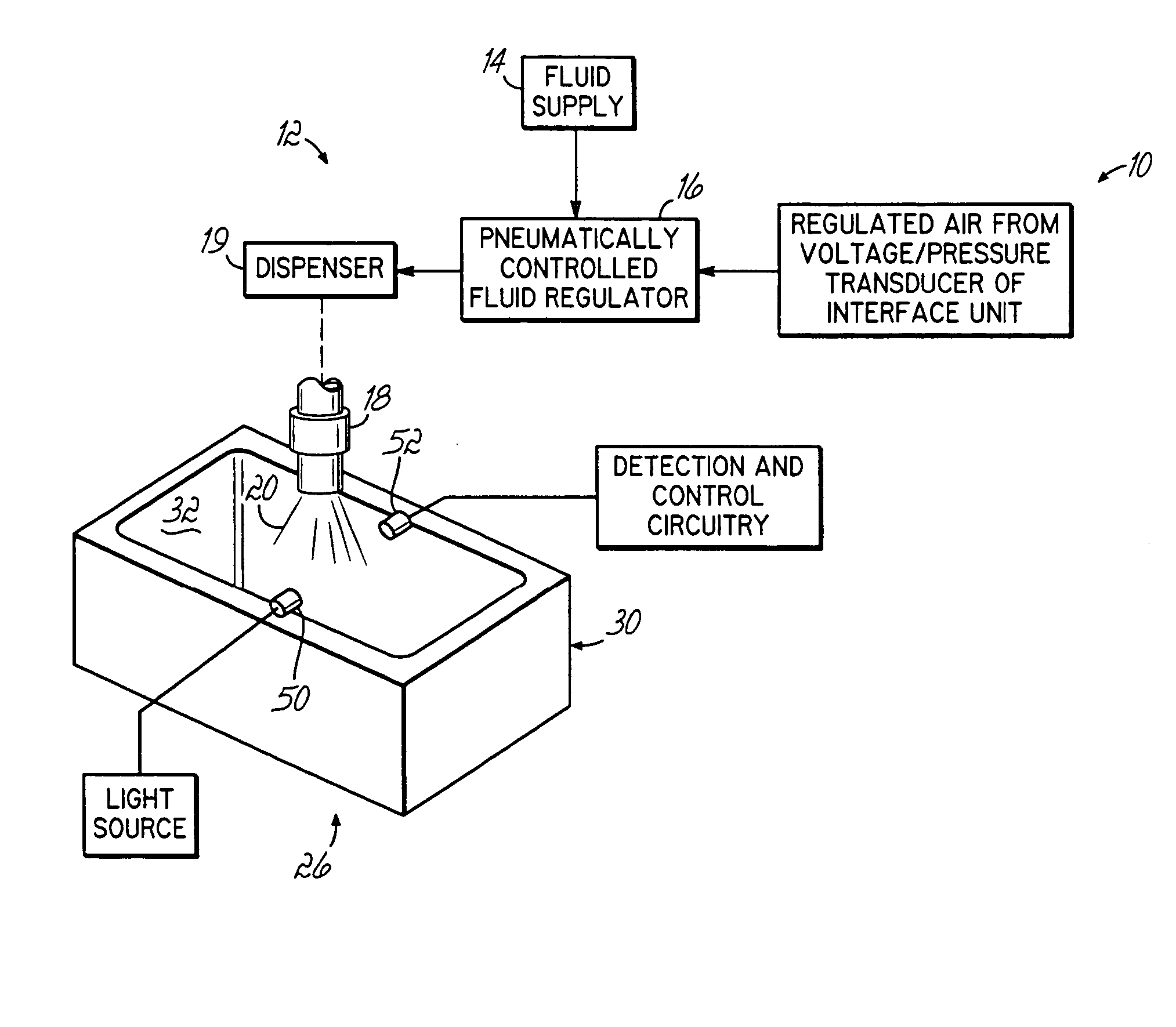
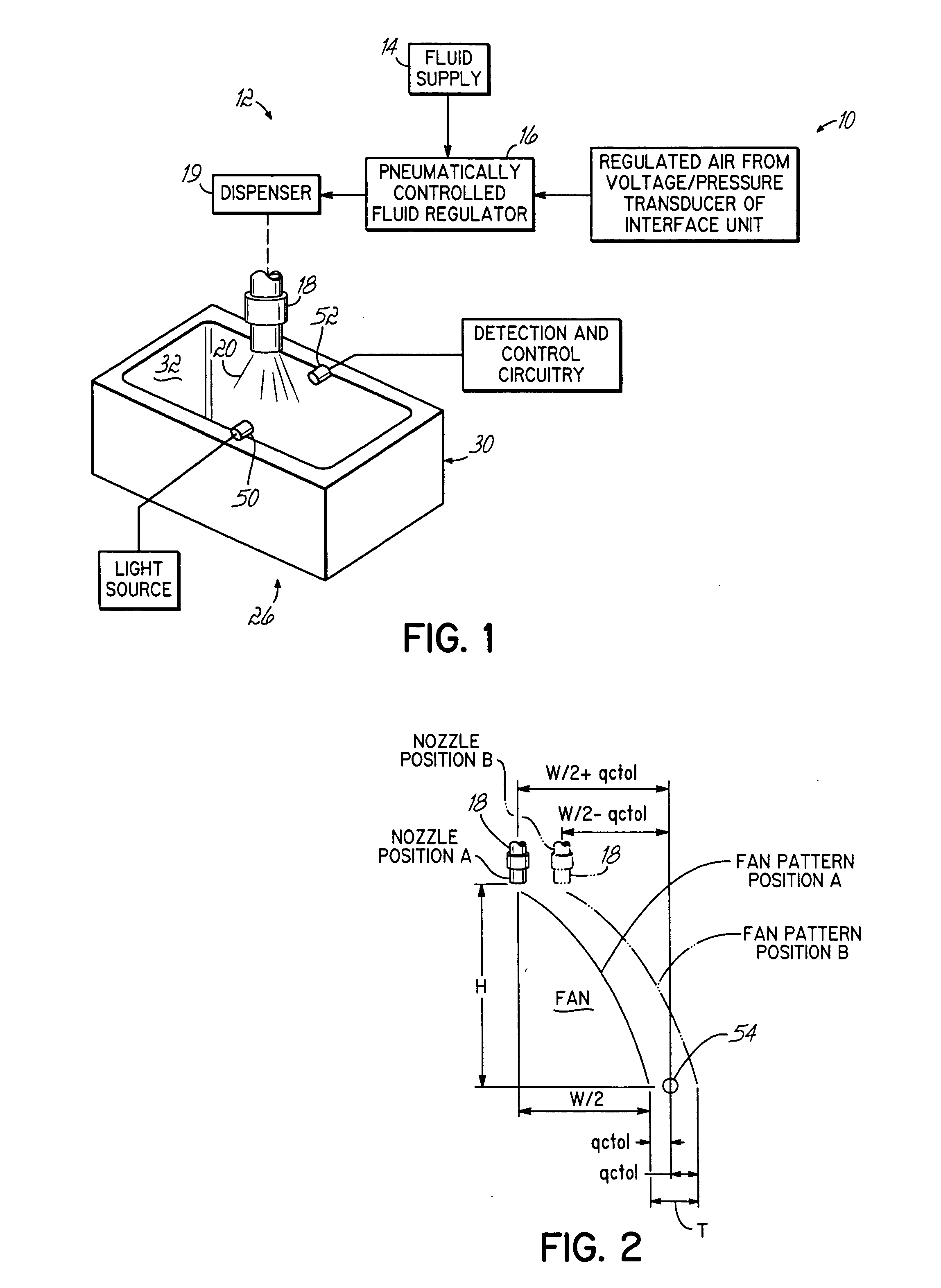
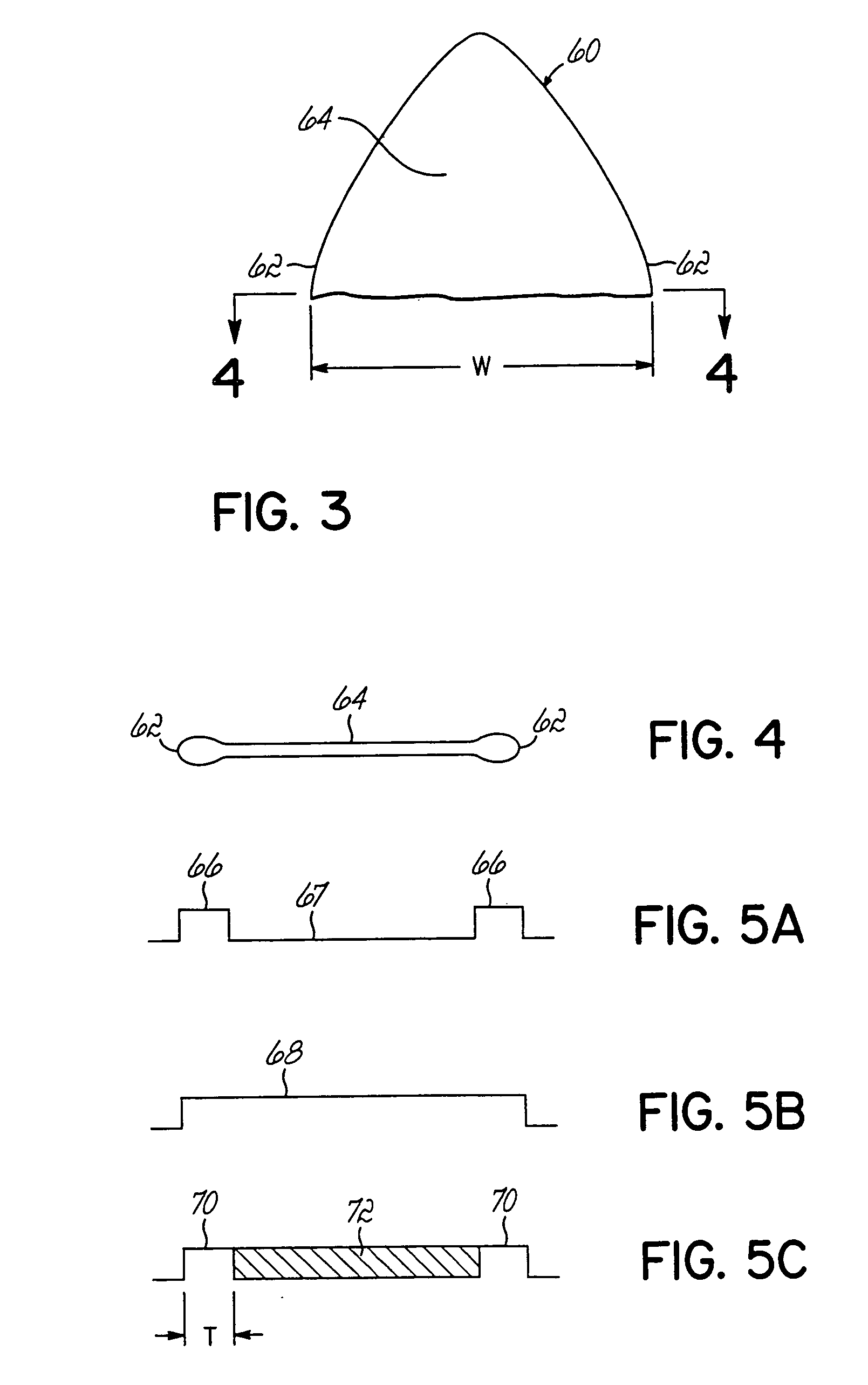
InactiveUS20050023367A1Liquid surface applicatorsSelf-acting watering devicesPattern detectionEngineering
During a liquid spray pattern detection procedure, the sensor (50, 52) is operable to detect the presence or absence of an edge of the dispensed liquid spray pattern. The nozzle (18) of the liquid dispensing system is moved to a predetermined position (A) relative to the sensor (50, 52) to determine the presence or absence of the spray pattern and is then moved to a second predetermined position (B) relative to the sensor (50, 52) to again determine the presence or absence of the spray pattern. Based on these determinations, the width of the spray pattern can be verified. This provides a quick means to verify that the width of the dispensed pattern is within certain tolerances.
Owner:NORDSON CORP
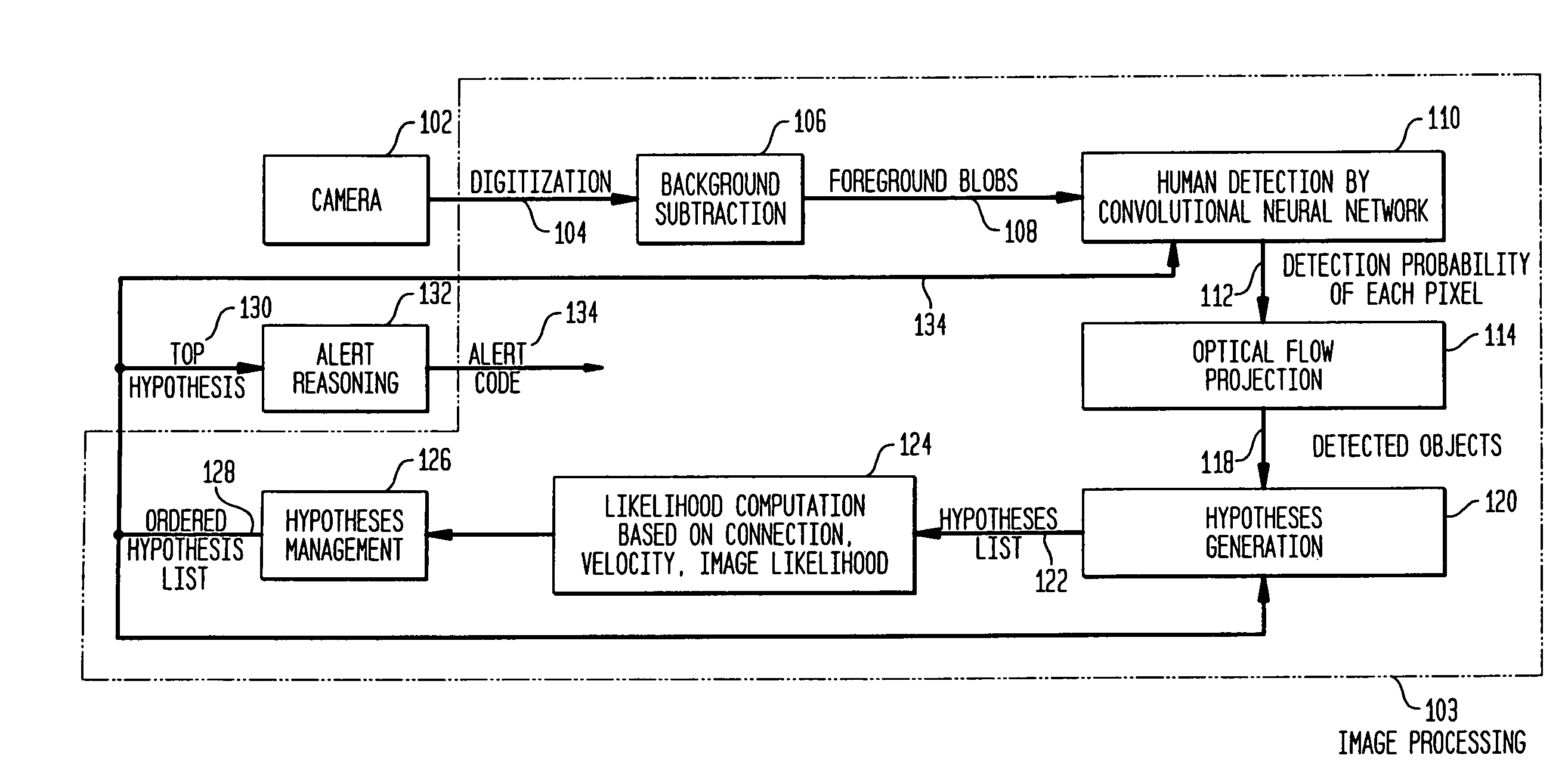
Video surveillance system that detects predefined behaviors based on predetermined patterns of movement through zones
ActiveUS7088846B2Character and pattern recognitionColor television detailsVideo monitoringObject based
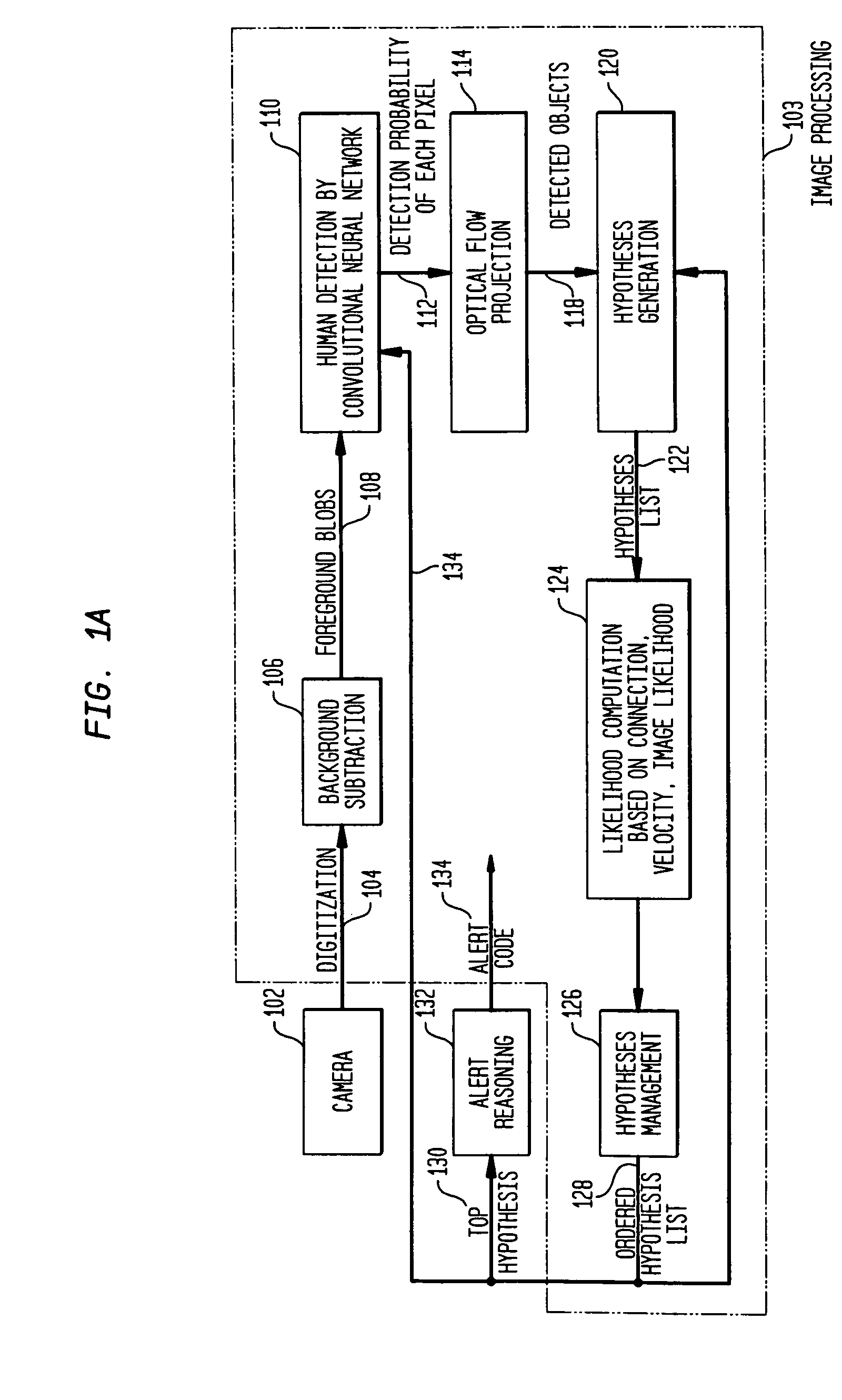
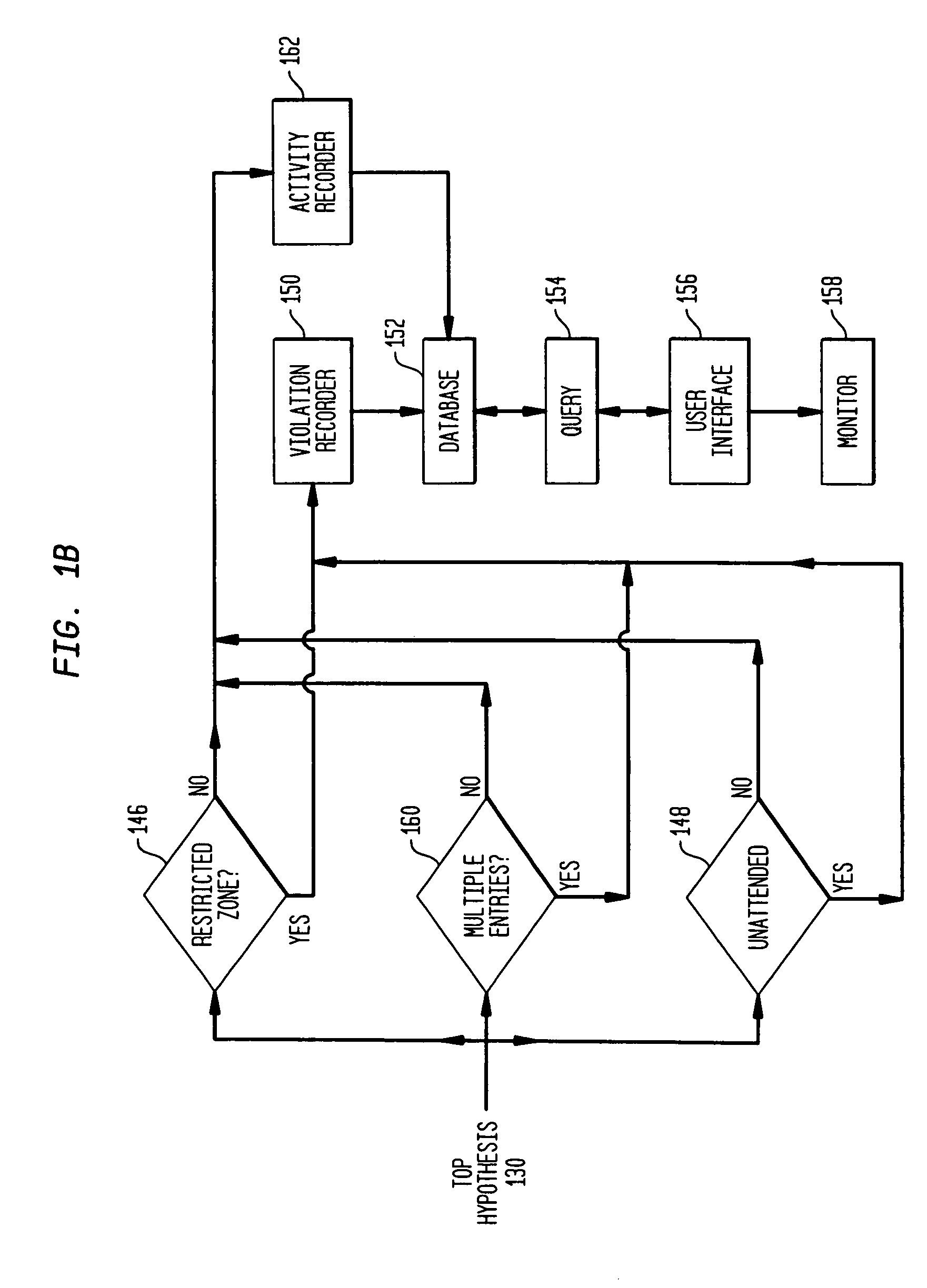
A video surveillance system uses rule-based reasoning and multiple-hypothesis scoring to detect predefined behaviors based on movement through zone patterns. Trajectory hypothesis spawning allows for trajectory splitting and / or merging and includes local pruning to managed hypothesis growth. Hypotheses are scored based on a number of criteria, illustratively including at least one non-spatial parameter. Connection probabilities computed during the hypothesis spawning process are based on a number of criteria, illustratively including object size. Object detection and probability scoring is illustratively based on object class.
Owner:AXIS
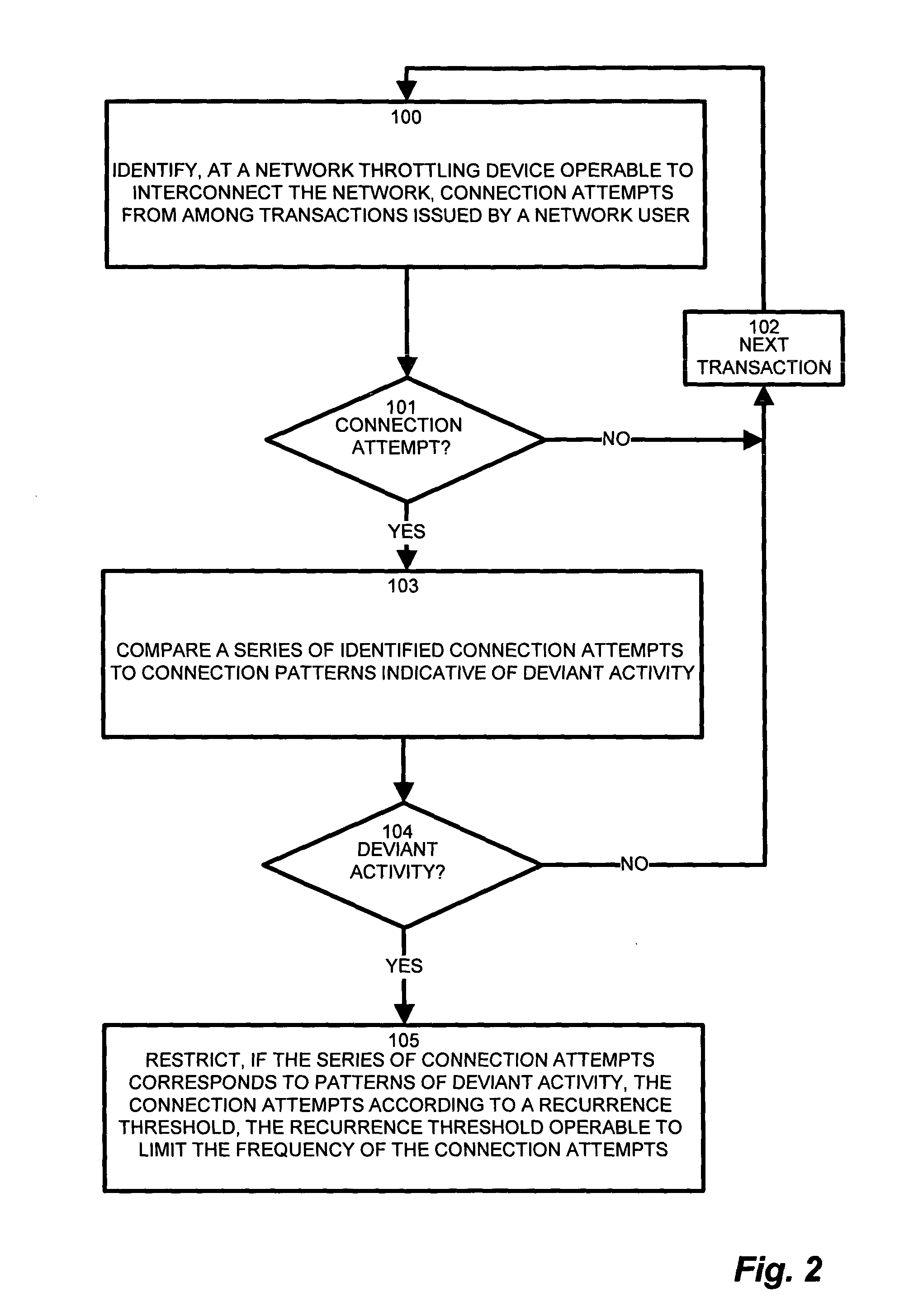
Network connection detection and throttling
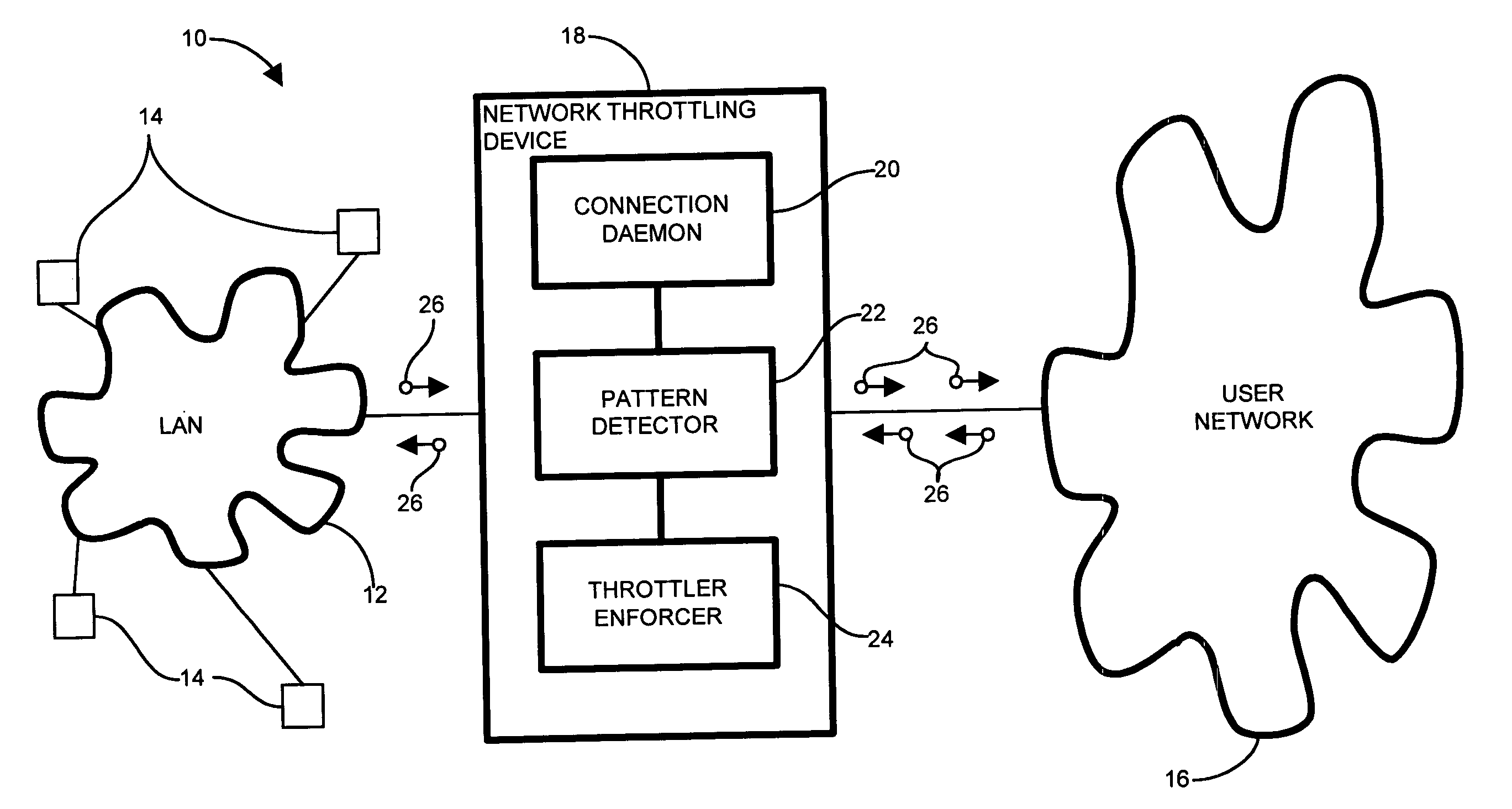
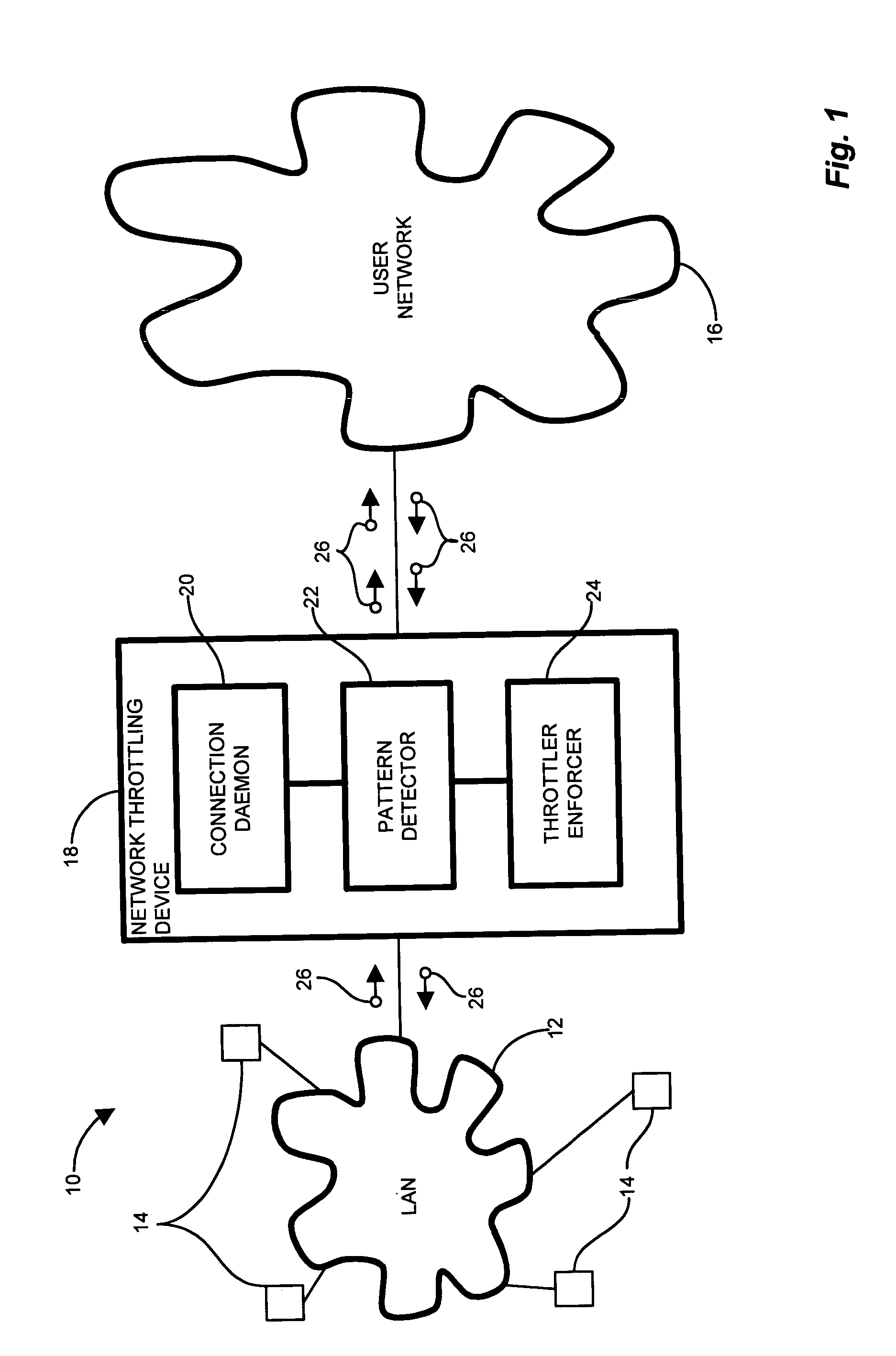
InactiveUS7814542B1Reduce harmful effectsMinimize activityMemory loss protectionUnauthorized memory use protectionPattern detectionNetwork connection
In an edge network, message traffic between the edge network and a core network passes through the edge router. A port scanning attack directed to the network as a whole (core network) potentially emanates from within the LAN. The edge router includes a network throttling device which identifies and mitigates harmful transmissions such that they do not propagate to the core network. The network throttling device has a connection daemon to scan transactions and determine deviant or atypical connection attempts. A session database stores a transaction history representing a window of previous connection attempts. A pattern detector examines the history and looks for malicious behavior. Identified deviant patterns cause a throttler enforcer to limit the triggering user by restricting future connection attempts, thus mitigating harmful effects. Usage, therefore, is not prevented, but resilience to deviant practices is provided. Accordingly, virus propagation via port scanning is mitigated to a safe level and false alarms targeting legitimate activity are minimized.
Owner:CISCO TECH INC
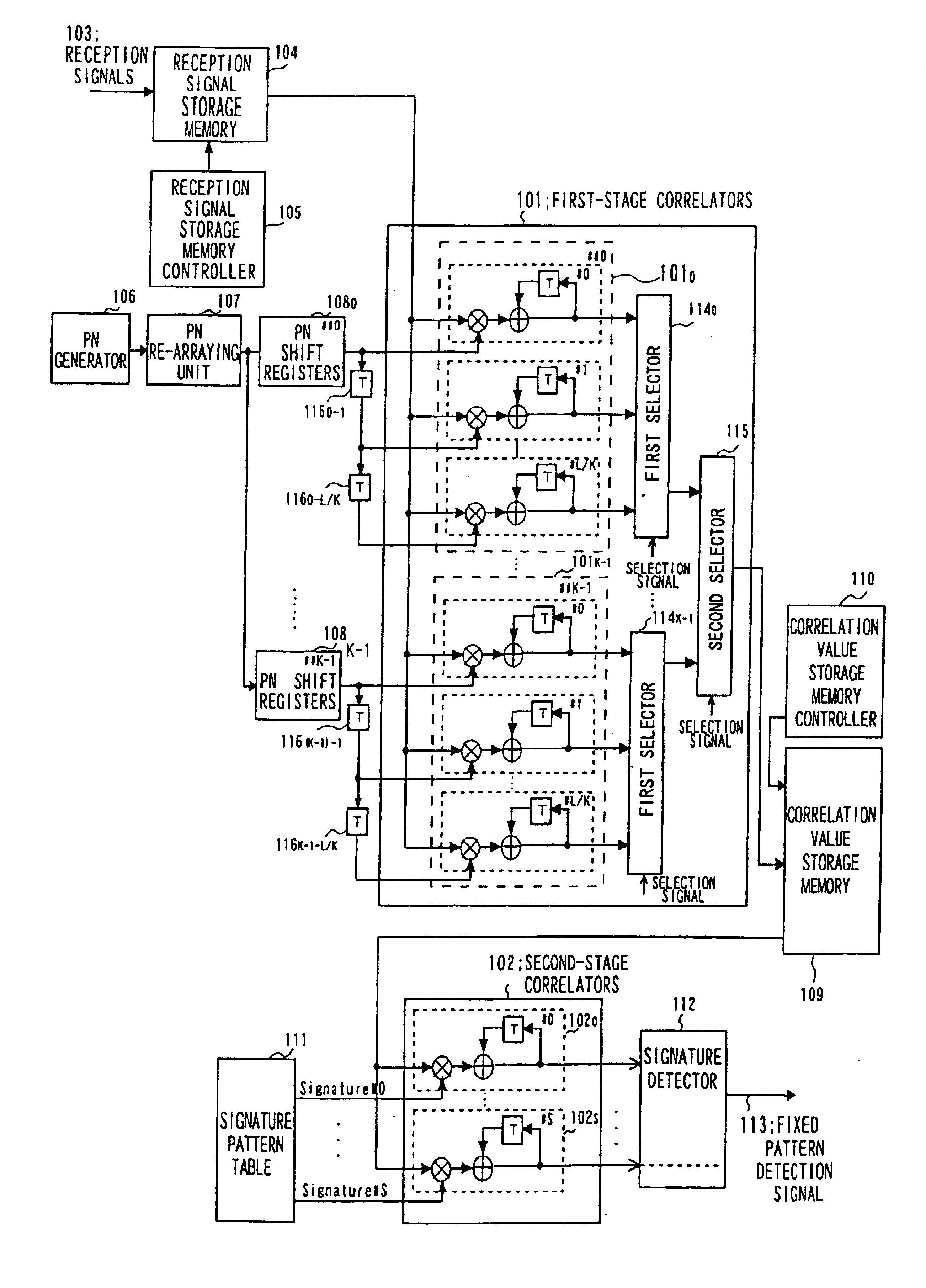
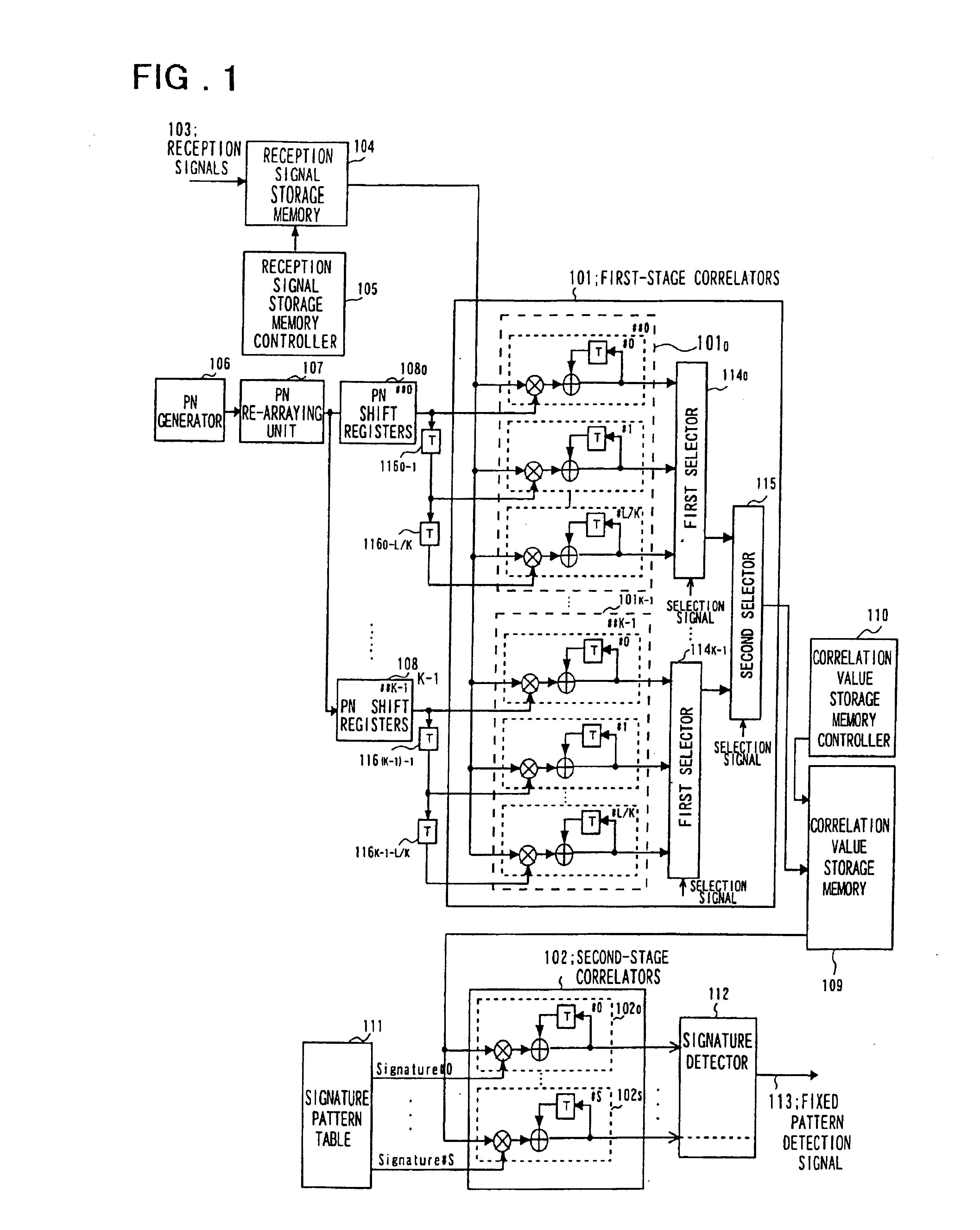
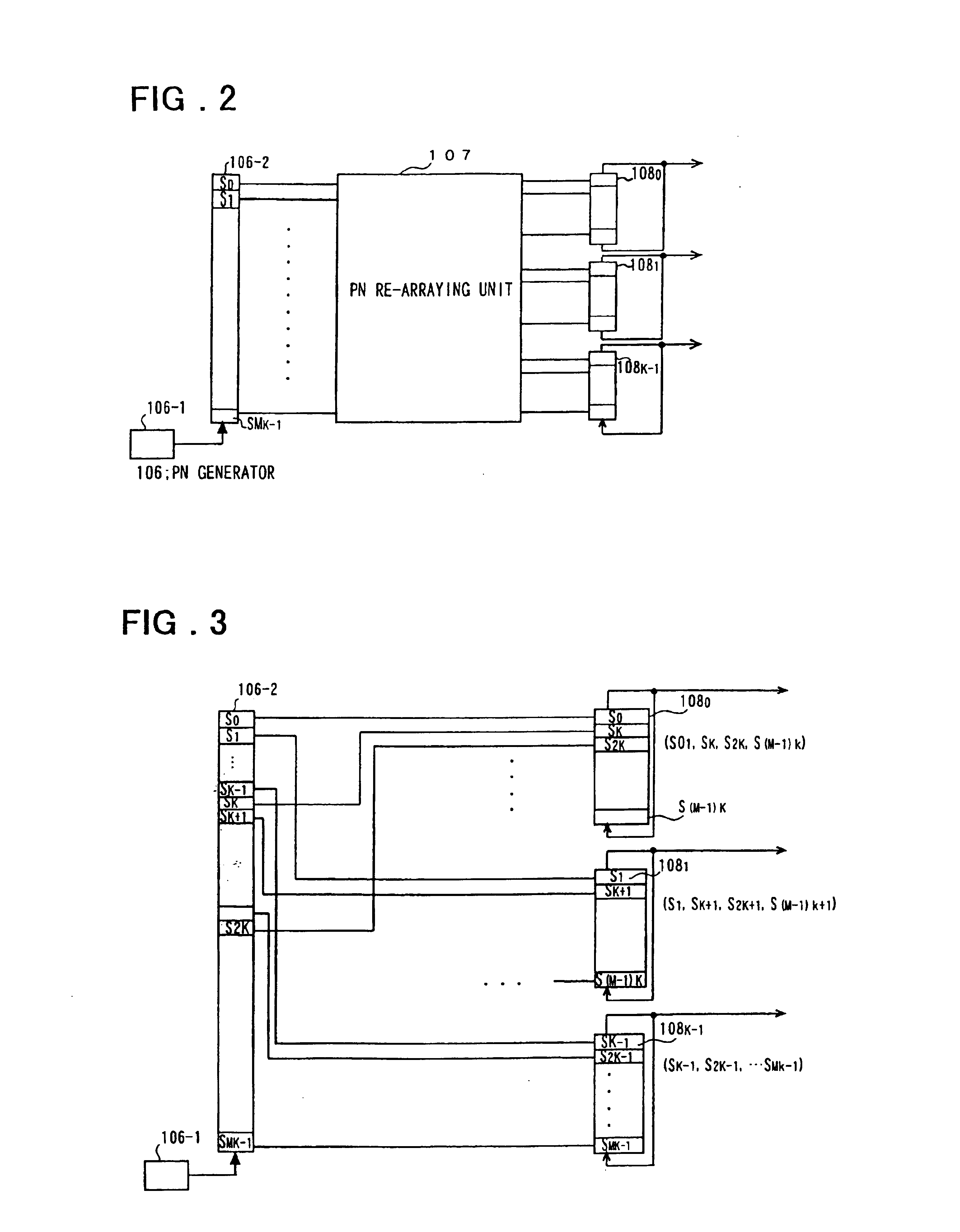
Fixed pattern detection apparatus
InactiveUS6882682B1Reduce detectionShorten the timeAmplitude-modulated carrier systemsAmplitude demodulationPattern detectionAnnular array
A fixed pattern detection device in which the device is fed as a received signal with a pattern of a length of N chips. The received signal is obtained by dividing and re-arraying each of K (integer) symbols in terms of a chip period as a unit, each symbol being spread with the spread code (PN) at a rate of M (integer) chips per symbol, and on repeatedly inserting into the re-arrayed symbols a signature pattern of a length K having one chip period as a unit, by M times, where N=K×M. The device includes first-stage correlators taking correlation between M received signals and M spread code sequences obtained on decimating a spread code sequence of a length N, and a second stage correlators taking correlation between the correlation values associated with K signatures output by the first-stage correlators and a pre-defined signature pattern.
Owner:NEC CORP
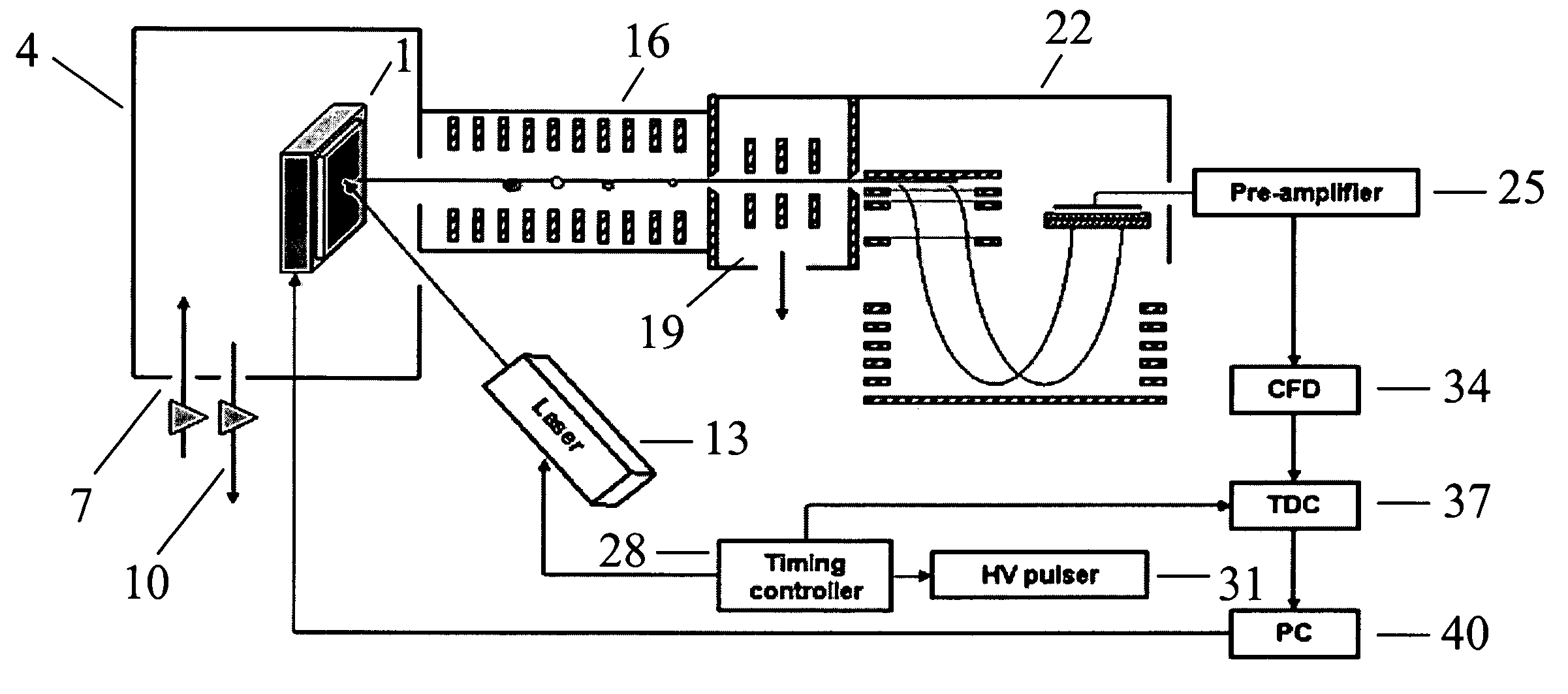
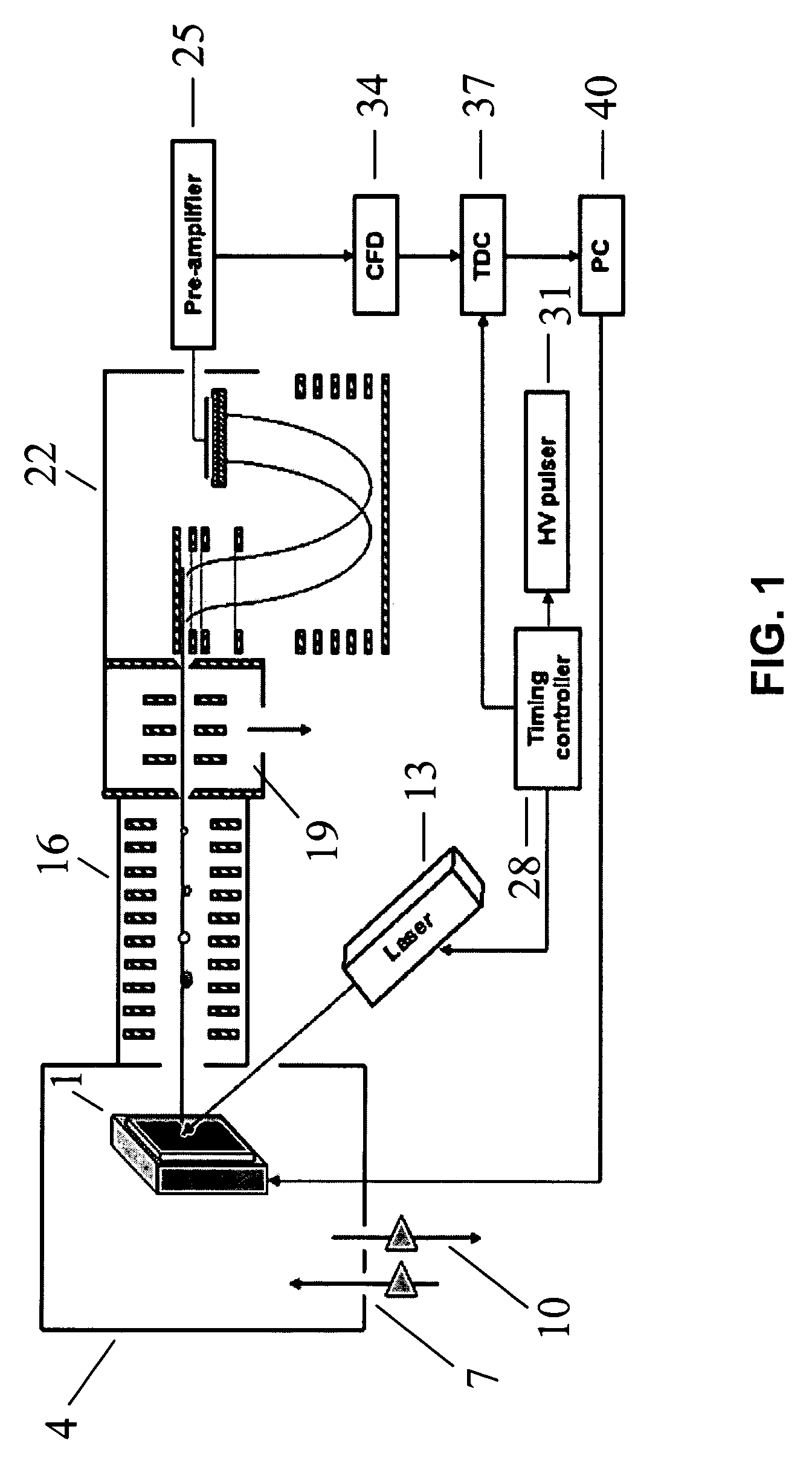
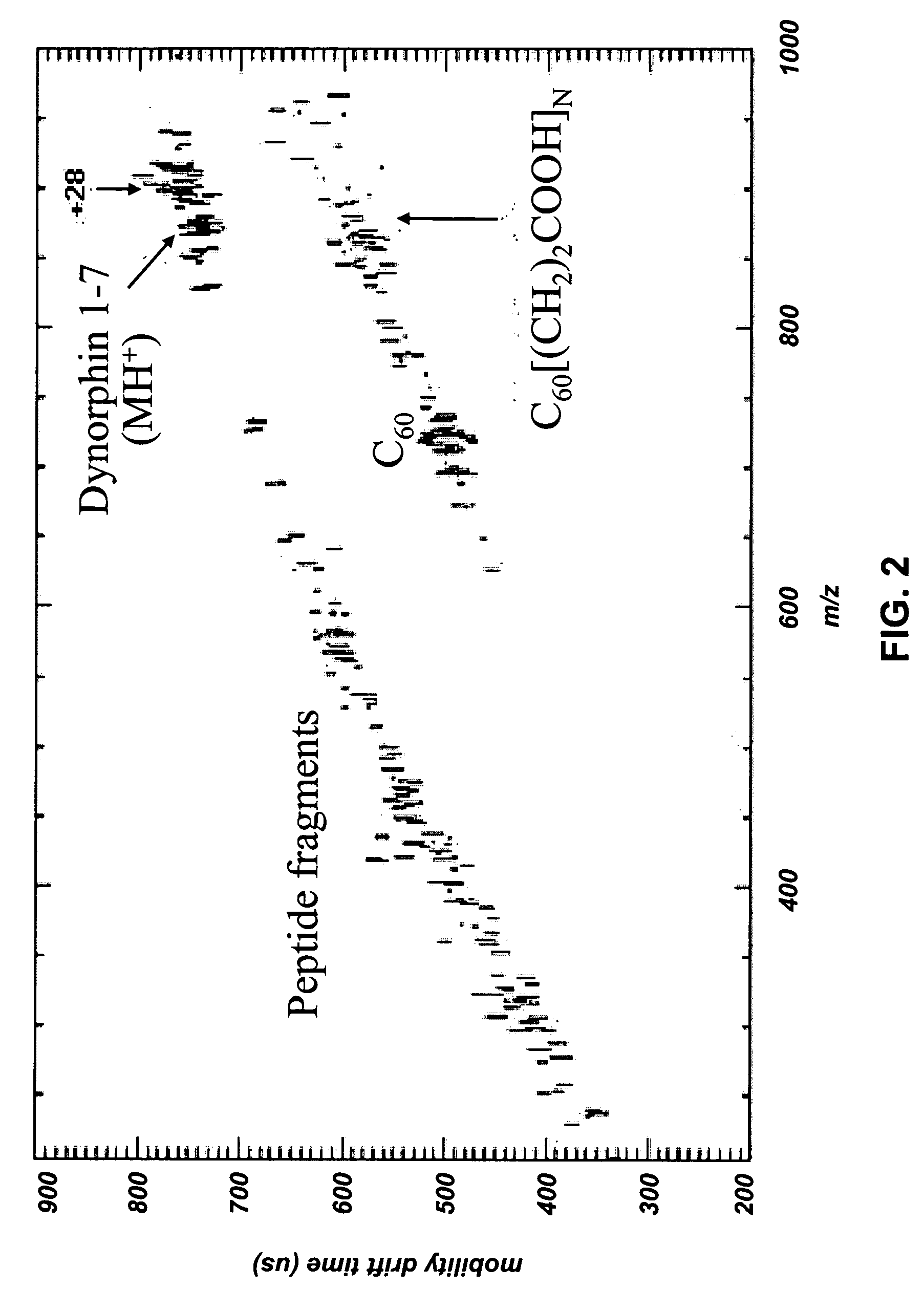
MALDI-IM-ortho-TOF mass spectrometry with simultaneous positive and negative mode detection
InactiveUS7170052B2Time-of-flight spectrometersPositive/negative analyte ion analysis/introduction/generationPattern detectionMass Spectrometry-Mass Spectrometry
An ion mobility / mass spectrometry method and instrument using aerosolized samples and dual positive and negative mode detection is described. Sample preparation methods are also described.
Owner:RGT UNIV OF CALIFORNIA +1
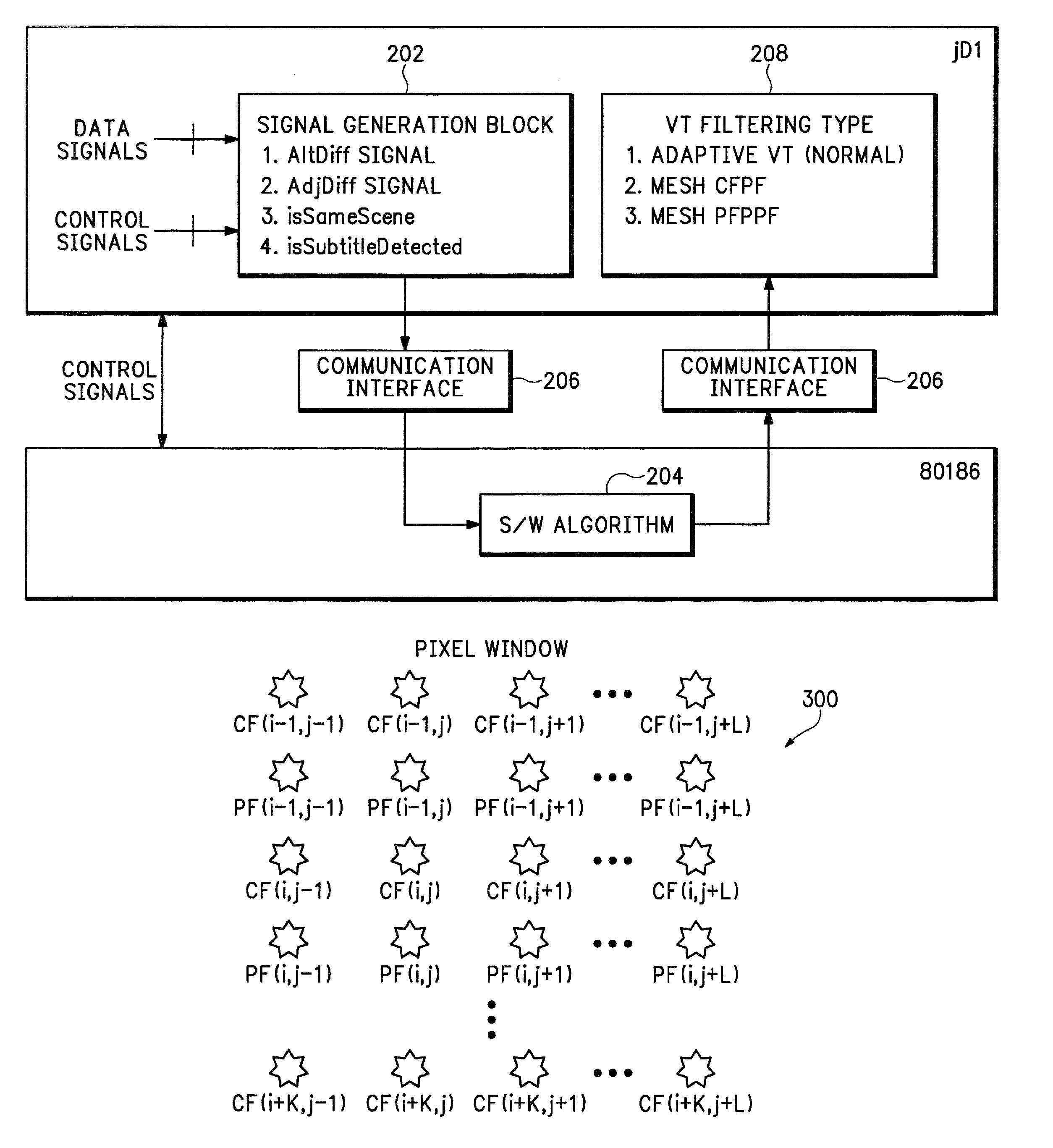
System and method for detecting a non-video source in video signals
InactiveUS7129990B2Television system detailsColor signal processing circuitsPattern recognitionPattern detection
A system detects a non-video source embedded in a video sequence and provides direction to a deinterlacing algorithm accordingly. The system comprises a signal generator for generating a plurality of signals. The signals are generated in accordance with pixels input from the video sequence. The system further comprises a plurality of pattern detection state machines, each for receiving the signals and for detecting a pattern in the video sequence. The pattern is detected in accordance with a preset threshold, wherein the pattern detection state machine varies the preset threshold in accordance with the received signals. The system further comprises an arbiter state machine coupled with the plurality of pattern detection state machines for governing the pattern detection state machines and for determining whether or not a non-video source is embedded in the video sequence.
Owner:PIXELWORKS SEMICON TECH SHANGHAI CO LTD
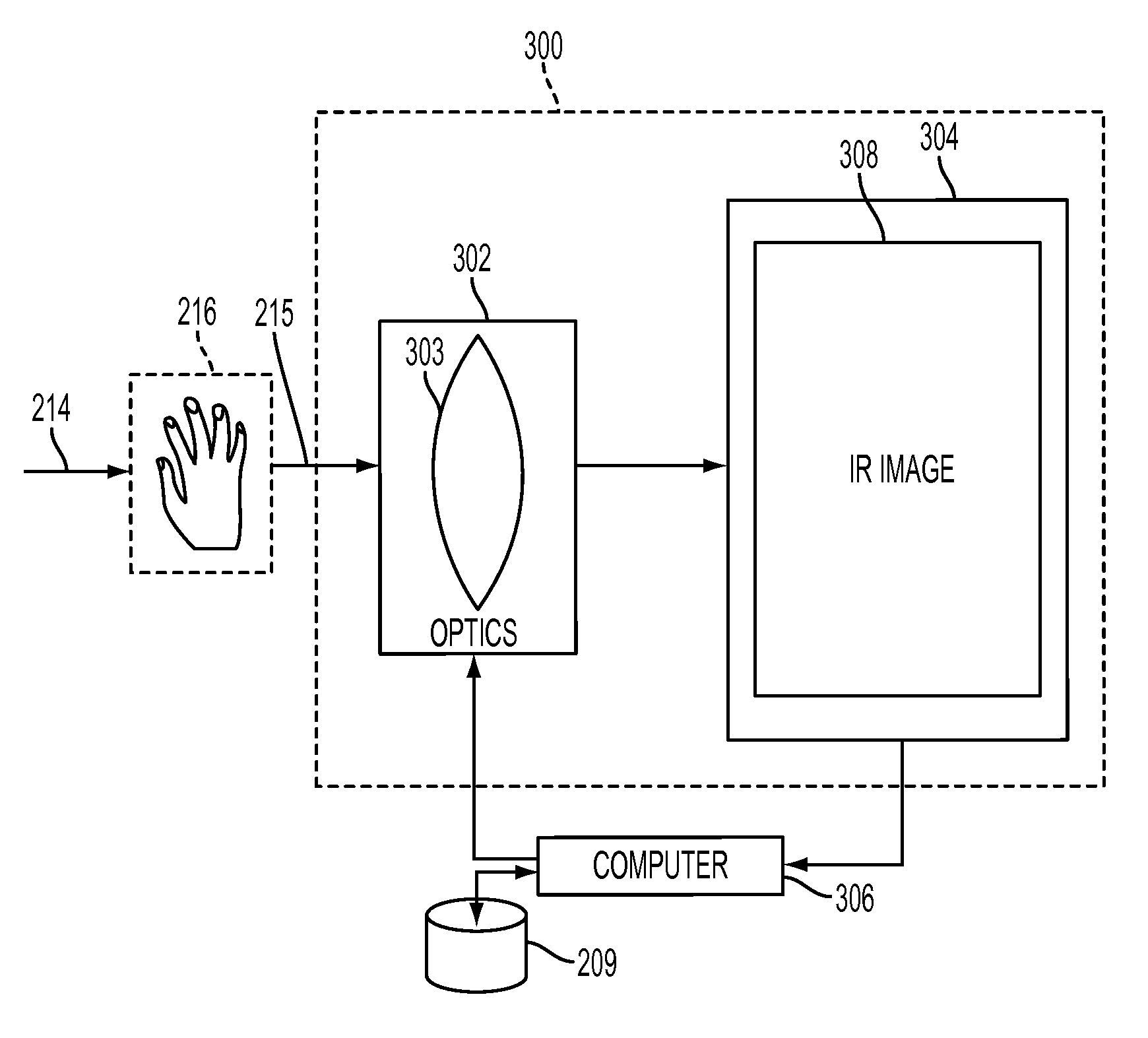
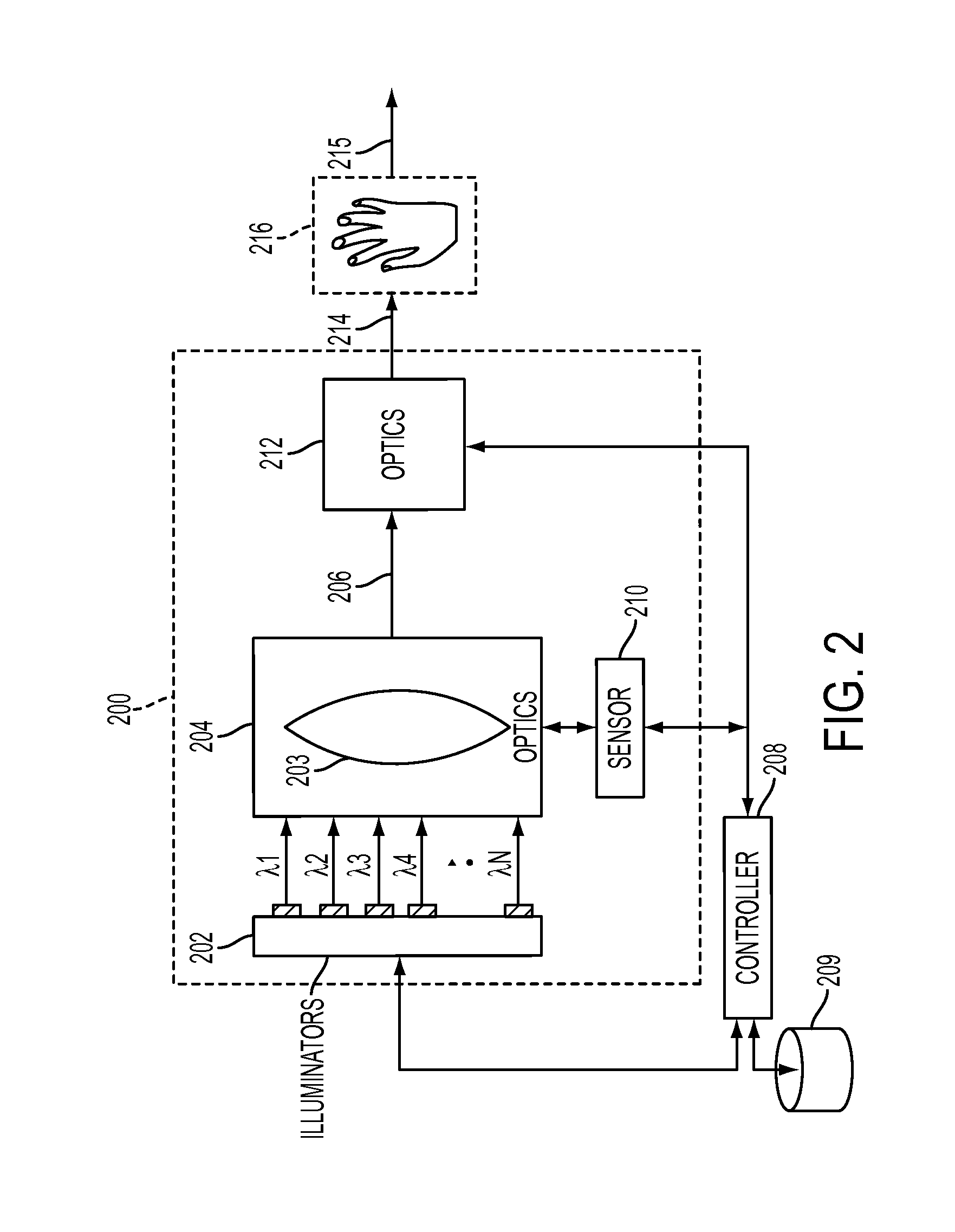
Subcutaneous vein pattern detection via multi-spectral IR imaging in an identity verification system
InactiveUS8509495B2Quick configurationImprove scalabilitySubcutaneous biometric featuresVerifying markings correctnessPattern recognitionVideo based
What is disclosed is a novel system and method for identifying an individual in an IR image involves the following. Intensity values are collected at N wavelengths for each pixel in an IR video-based image. The intensity values are collected using an IR imaging system having an IR detector and an IR Illuminator. The intensity values are then used to identify pixels of human skin in the IR image. If human skin is identified in the IR image then, the human hand is identified in the IR image from the human skin to distinguish the hand from the background. Vein patterns in the hand are then located and extracted. A reference vein pattern is retrieved from a database of known vein patterns for individuals, and a comparison is made to determine a match. If a match is determined, then the individual in the captured IR image can be identified.
Owner:XEROX CORP
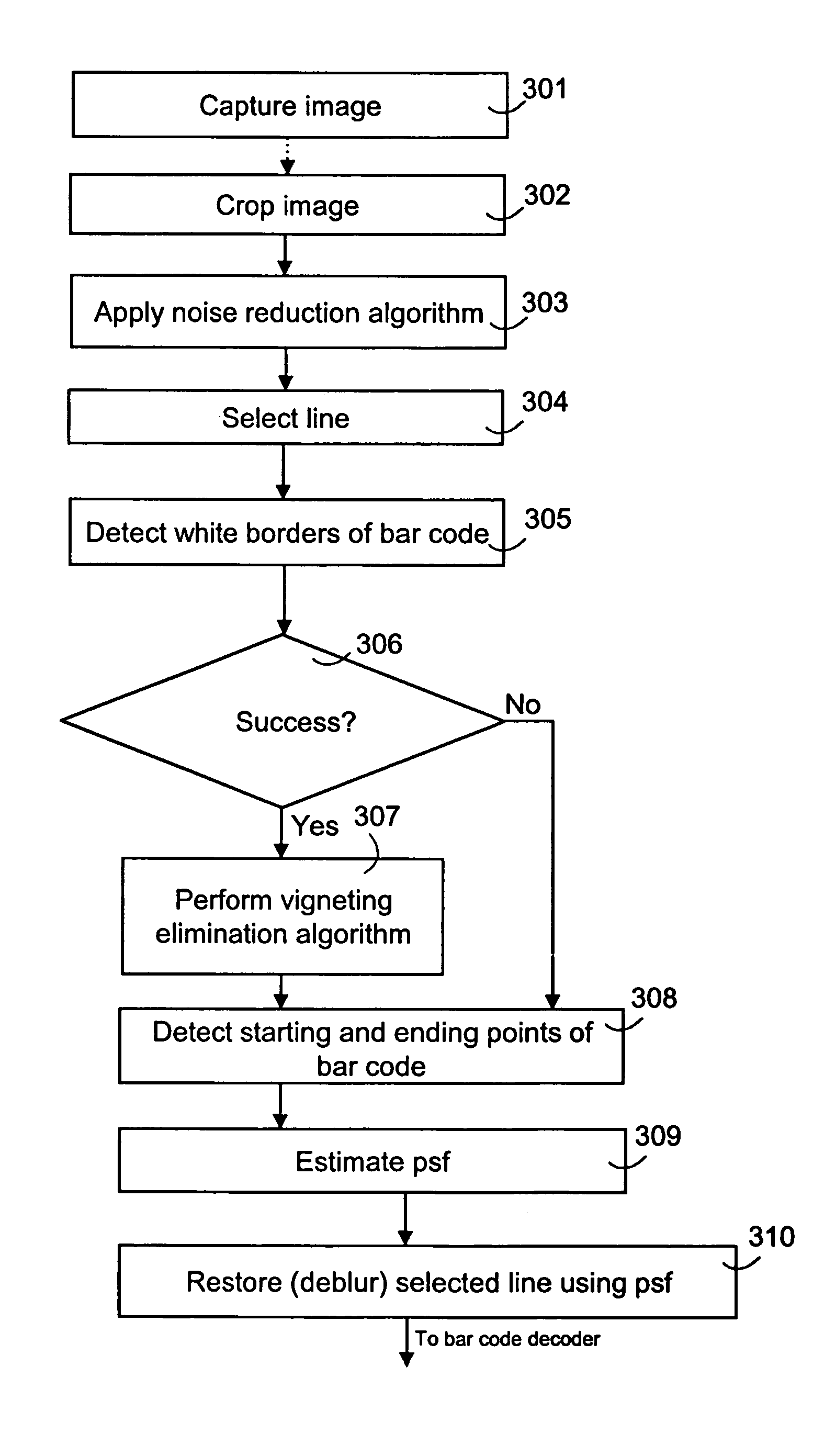
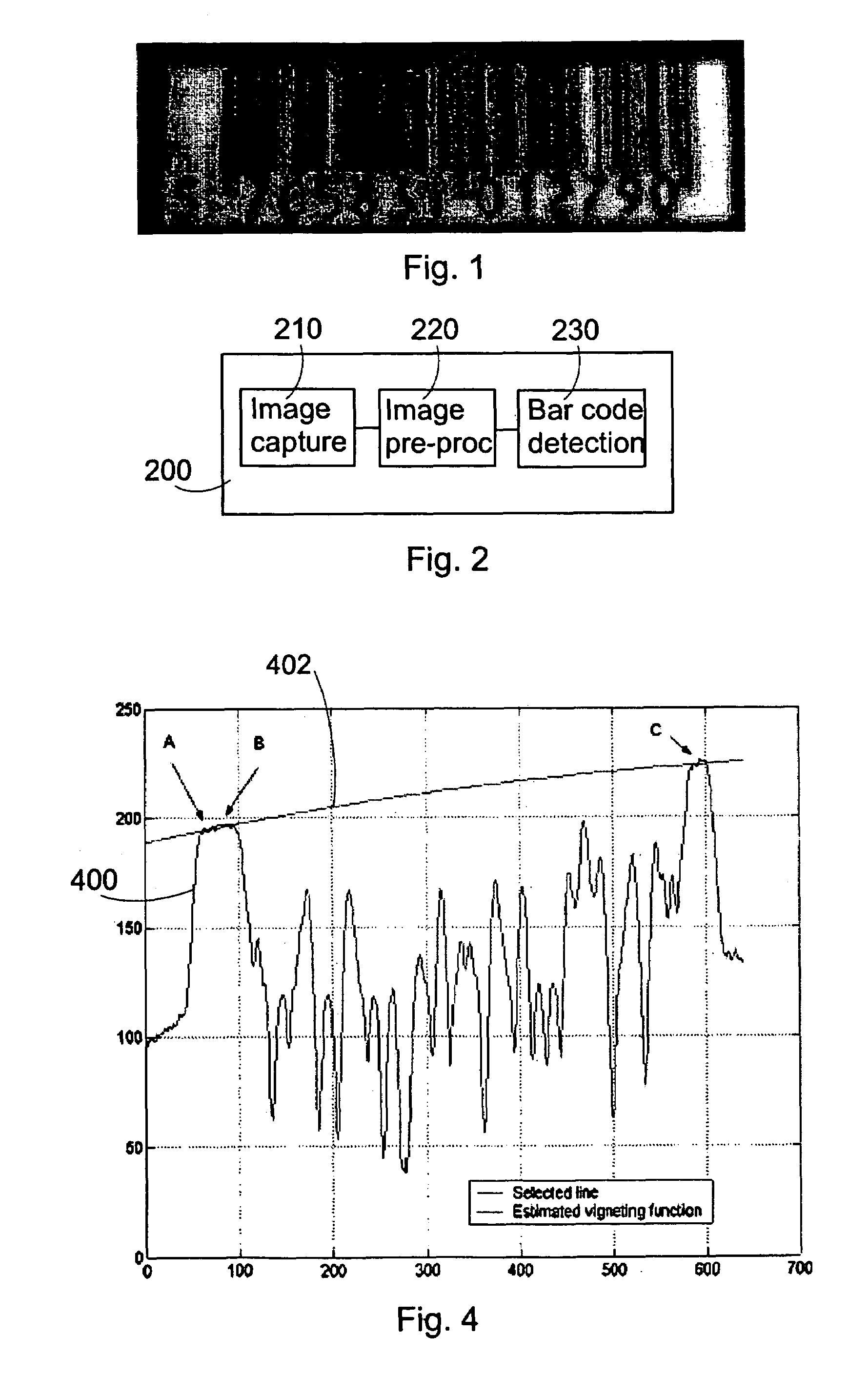
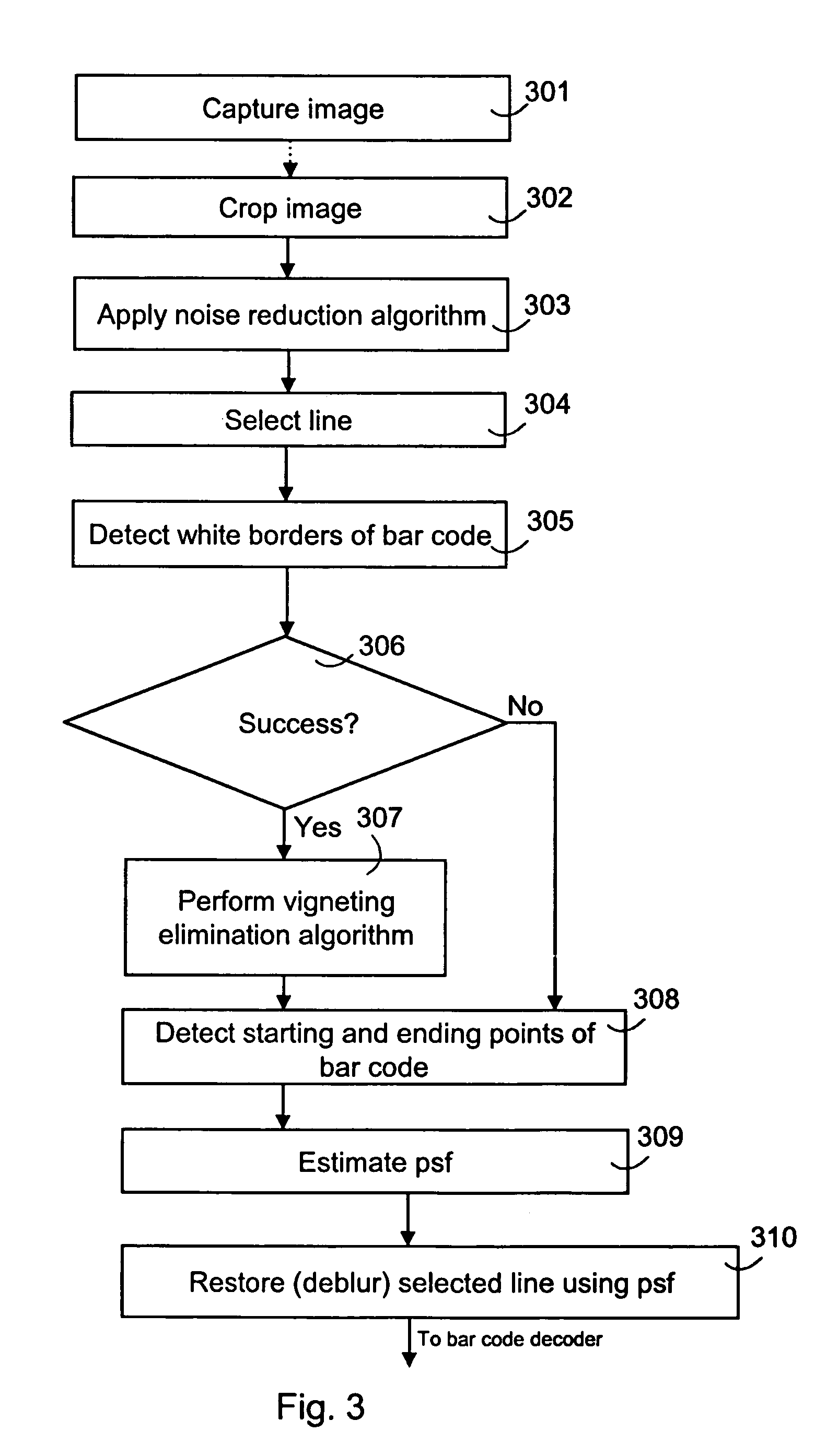
Image processing for pattern detection
InactiveUS7237721B2Improve captured image qualityReliable detectionImage enhancementImage analysisPattern recognitionImaging processing
The present invention relates to an image pre-processing method for a pattern detection system, such as a bar code detection system. The method comprises the steps of: detecting a start point and an end point of a pattern on the basis of image data of at least a portion of a captured image, estimating a point spread function from the image data or a modified image data on the basis of the detected start point and the end point, and restoring the image data or the modified image data using the estimated point spread function.
Owner:NOKIA CORP
Parallel Pattern Detection Engine
InactiveUS20070150623A1Character and pattern recognitionInput/output processes for data processingData matchingData stream
A parallel pattern detection engine (PPDE) comprise multiple processing units (PUs) customized to do various modes of pattern recognition. The PUs are loaded with different patterns and the input data to be matched is provided to the PUs in parallel. Each pattern has an Opcode that defines what action to take when a particular data in the input data stream either matches or does not match the corresponding data being compared during a clock cycle. Each of the PUs communicate selected information so that PUs may be cascaded to enable longer patterns to be matched or to allow more patterns to be processed in parallel for a particular input data stream.
Owner:KRAVEC KERRY A +3
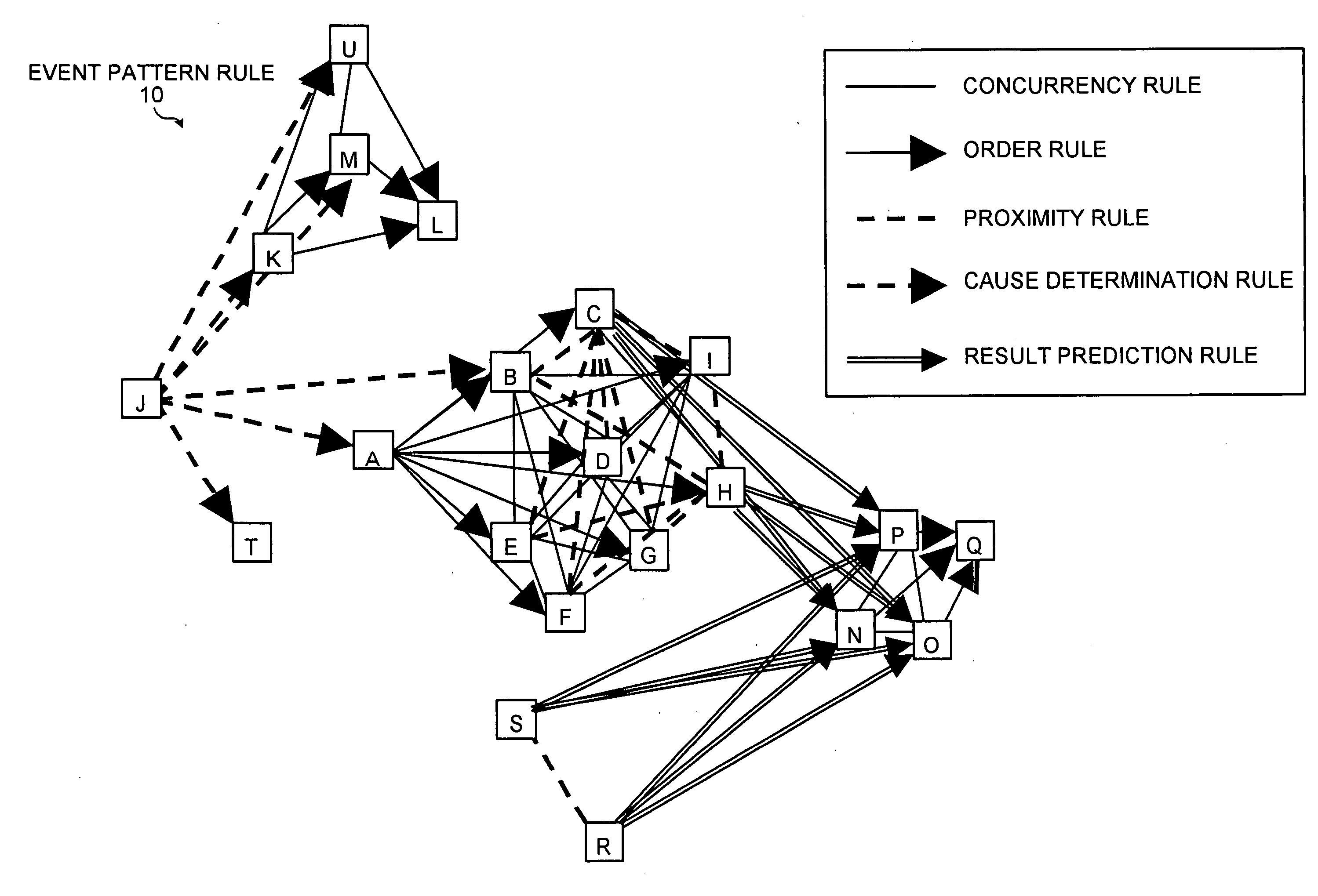
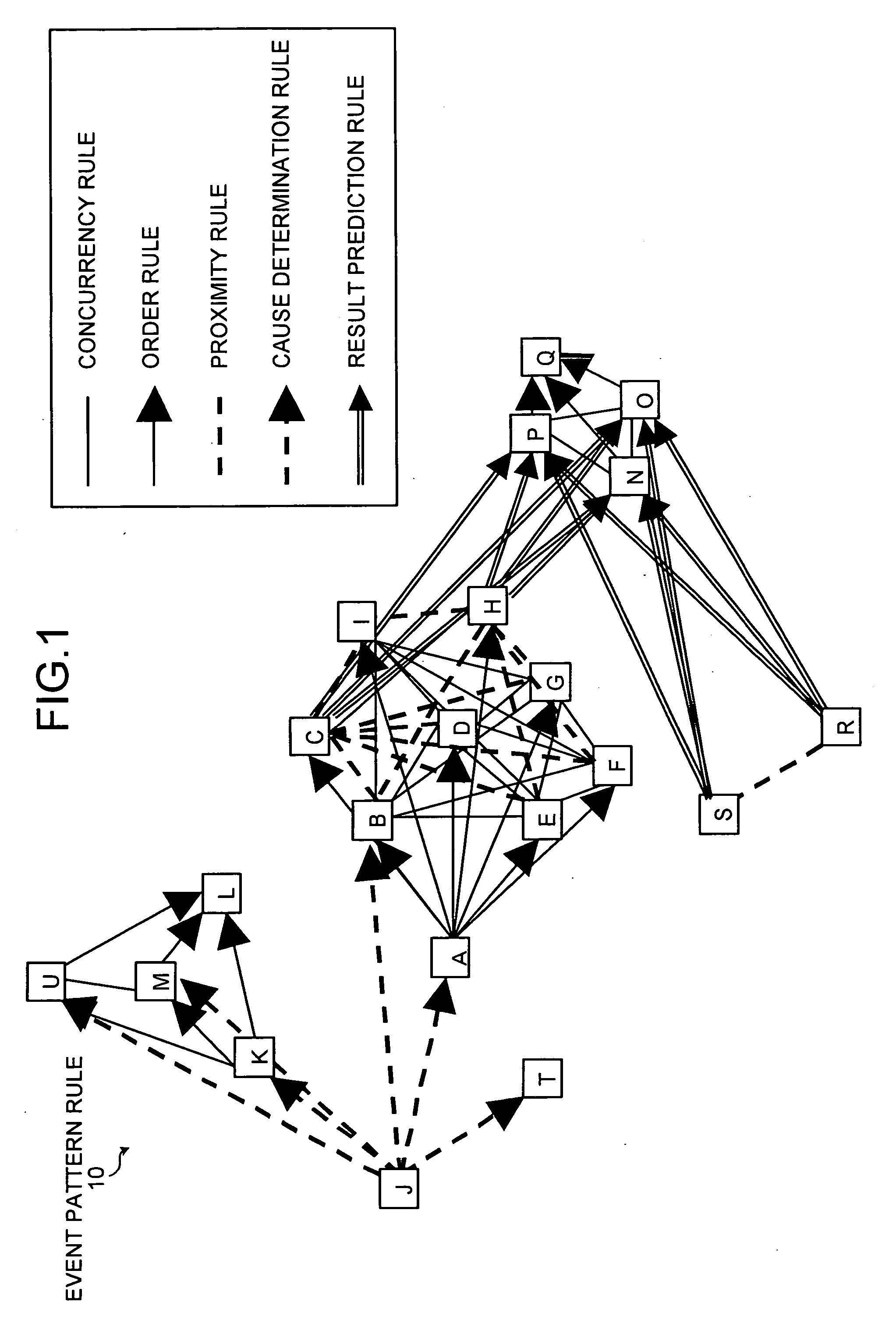
Apparatus, method, and computer product for pattern detection
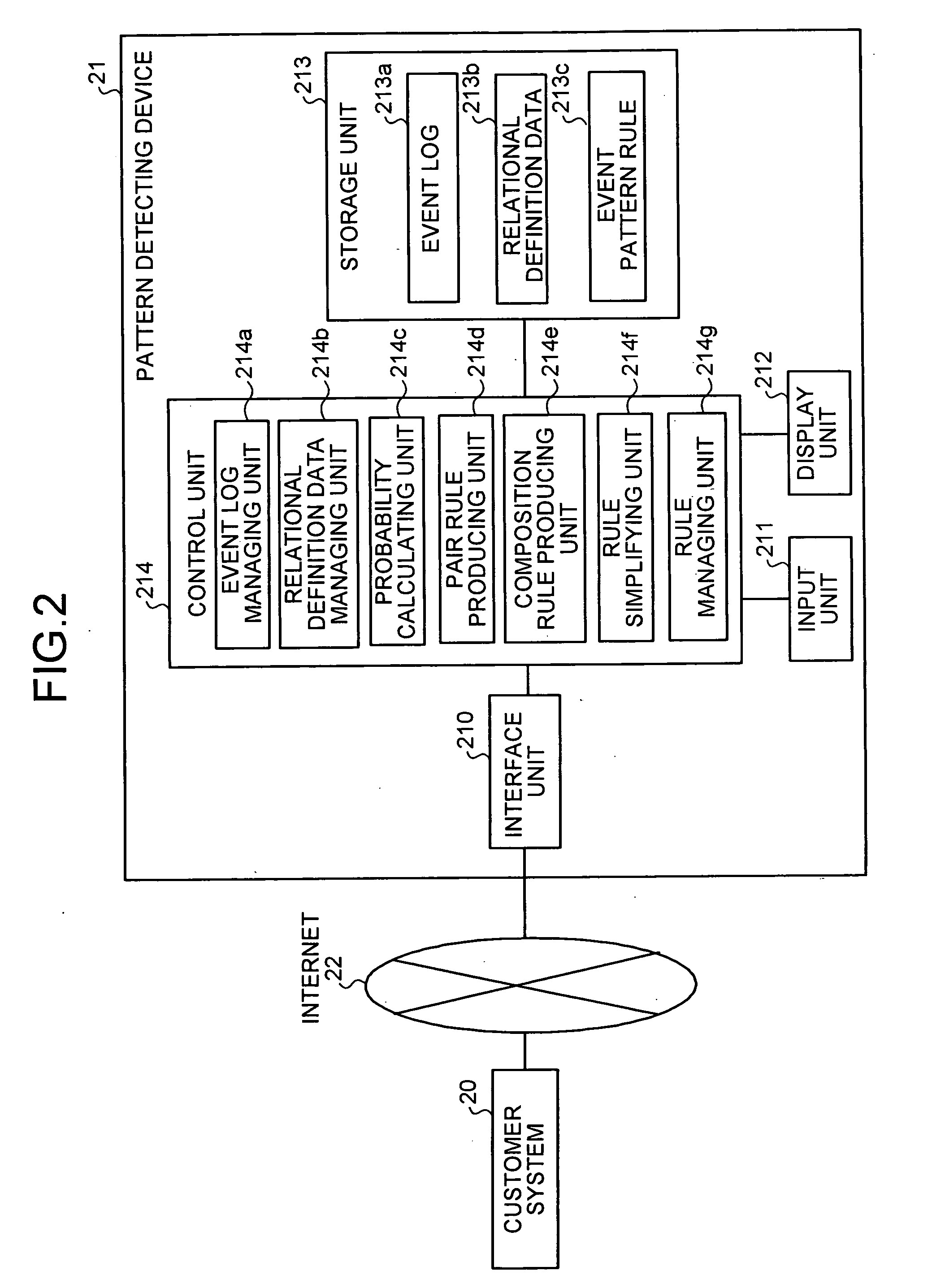
InactiveUS20050283680A1Digital data information retrievalError detection/correctionPattern detectionEvent data
An occurrence pattern of an event is detected from an event log based upon information concerning plural kinds of relationships defined among events, such as a simultaneity rule, an order rule, a proximity rule, a cause determination rule, and a result prediction rule and an occurrence pattern of the detected event is output. Accordingly, when an occurrence pattern of an event is detected from event data storing information concerning an occurred event, detailed information about an occurrence pattern of an event can be extracted from an event log.
Owner:FUJITSU LTD
Antipattern detection processing for a multithreaded application
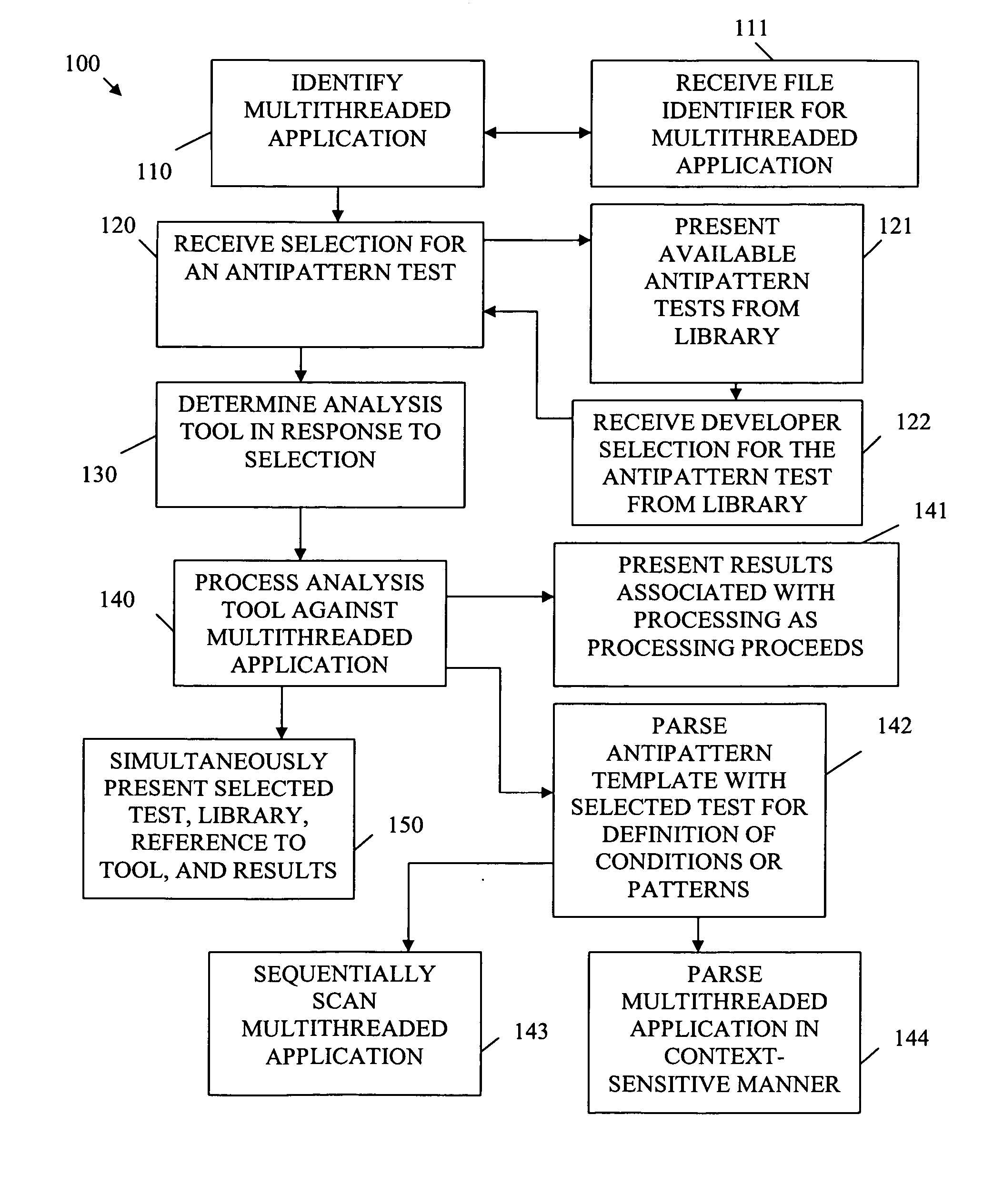
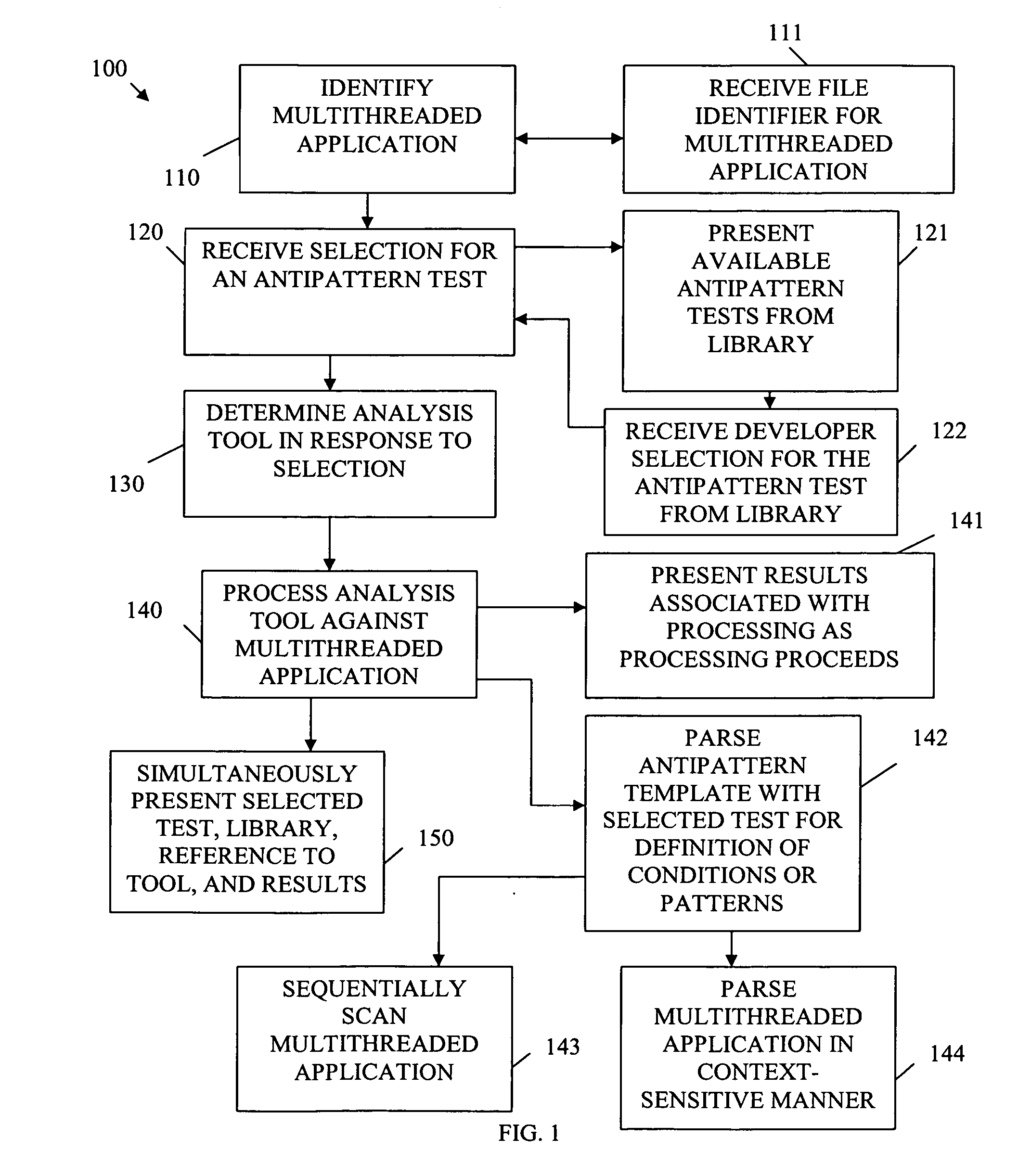
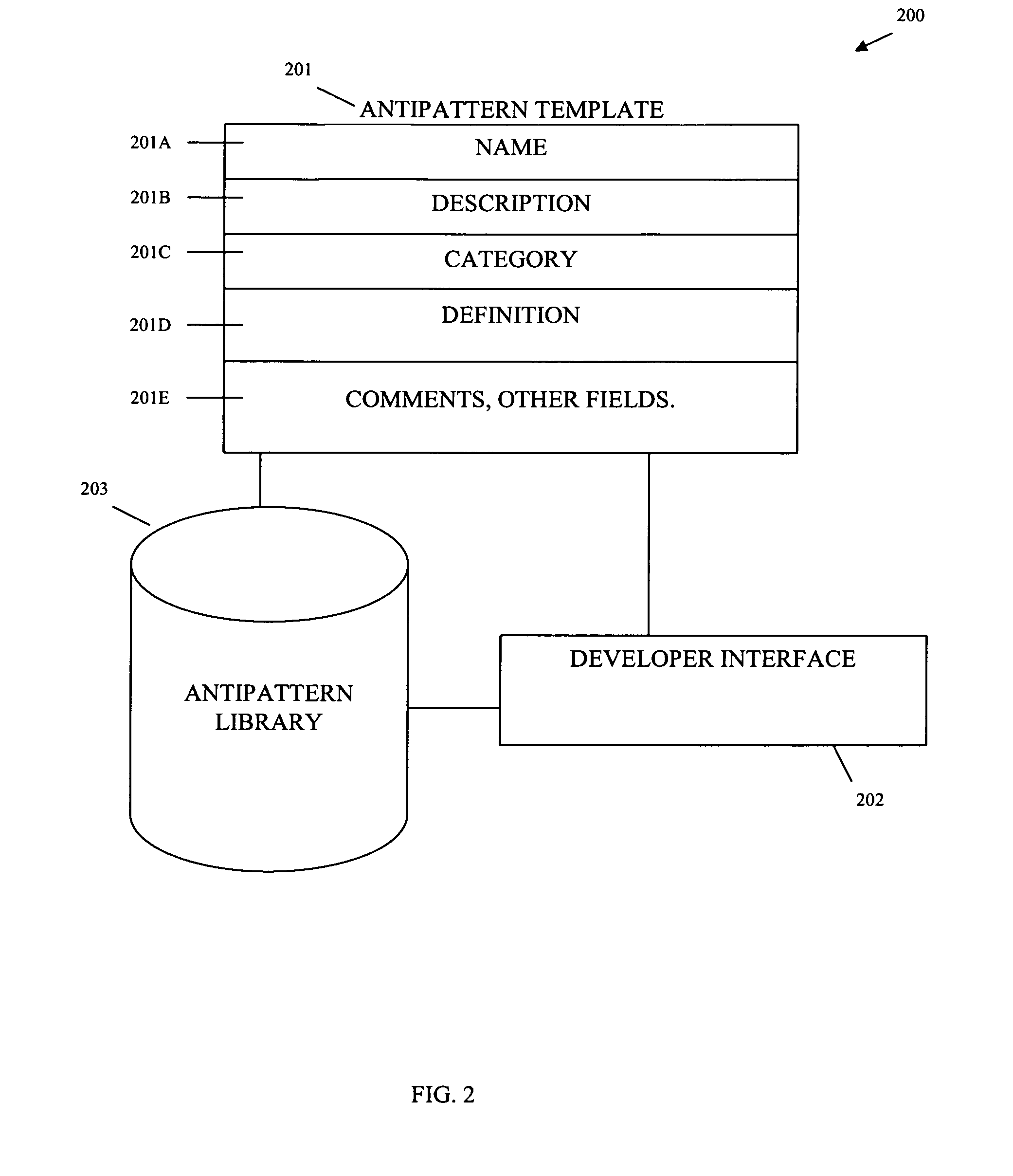
ActiveUS20060053422A1Error detection/correctionMultiprogramming arrangementsProgramming languagePattern detection
A method of analyzing a multithreaded application for an antipattern is presented. An antipattern test is selected from a library of available antipatterns. An analysis tool is determined in response to the selected antipattern. The analysis tool is processed against the multithreaded application for the selected antipattern for purposes of detecting coding deficiencies in the multithreaded application as defined by the antipattern.
Owner:SAP AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com