Patents
Literature
40results about How to "Minimize activity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
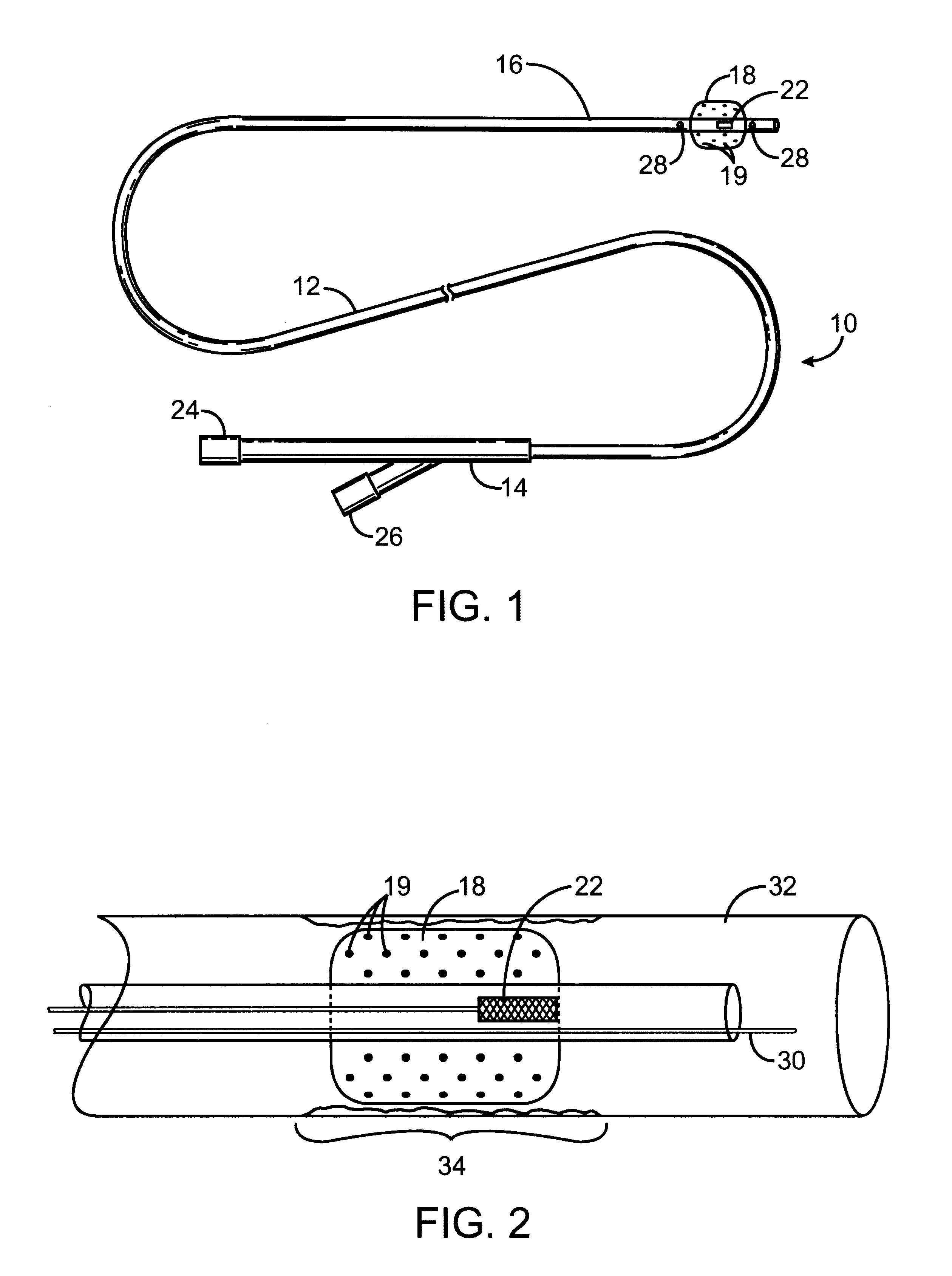
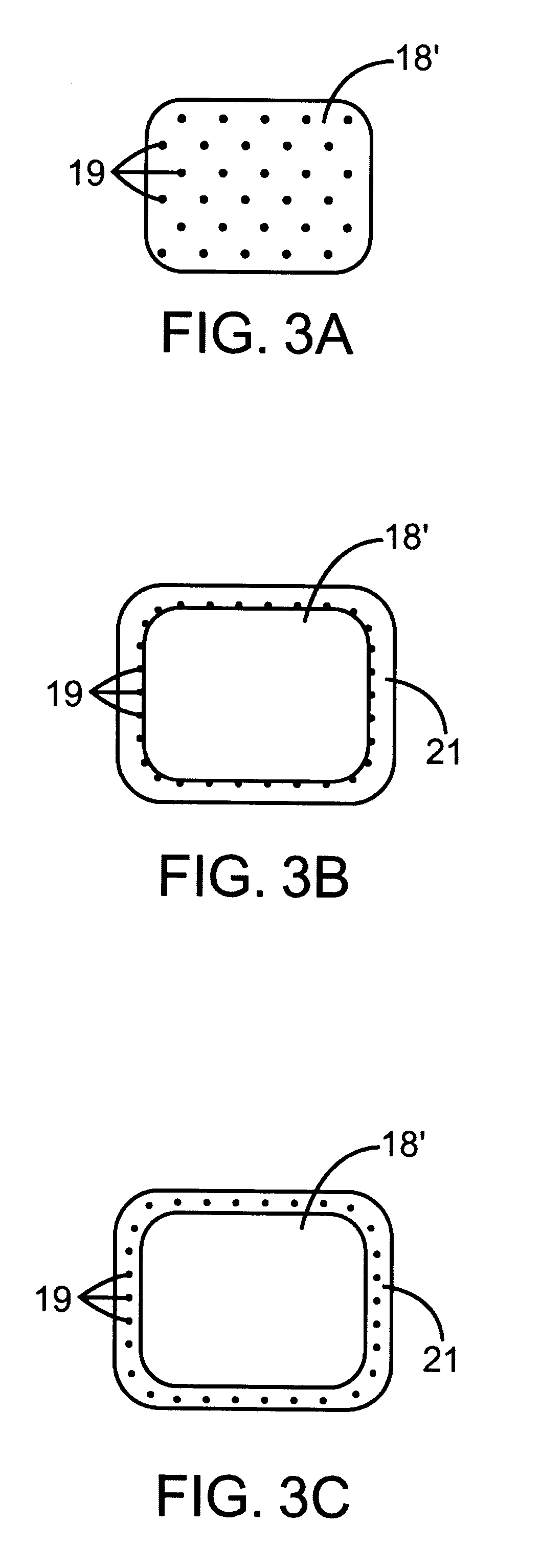
Biodegradable implantable medical devices, methods and systems
InactiveUS20060018948A1Risk minimizationMinimize activitySurgeryProsthesisMedical deviceBiomedical engineering
Owner:SURMODICS INC
Combination x-ray radiation and drug delivery devices and methods for inhibiting hyperplasia
InactiveUS6537195B2Promote endothelializationReduced dosages/concentrationsStentsElectrotherapyInsertion stentPercent Diameter Stenosis
The present invention provides improved devices, methods, and kits for inhibiting restenosis and hyperplasia after intravascular intervention. In particular, the present invention provides controlled drug delivery in combination with x-ray radiation delivery to selected locations within a patient's vasculature to reduce and / or inhibit restenosis and hyperplasia rates with increased efficacy. In one embodiment, the combination radiation and agent delivery catheter for inhibiting hyperplasia comprises a catheter body having a proximal end and distal end, an x-ray tube coupleable to the catheter body for applying a radiation dose to a body lumen, and a porous material, matrix, membrane, barrier, coating, infusion lumen, stent, graft, or reservoir for releasing an agent to the body lumen.
Owner:XOFT INC +1
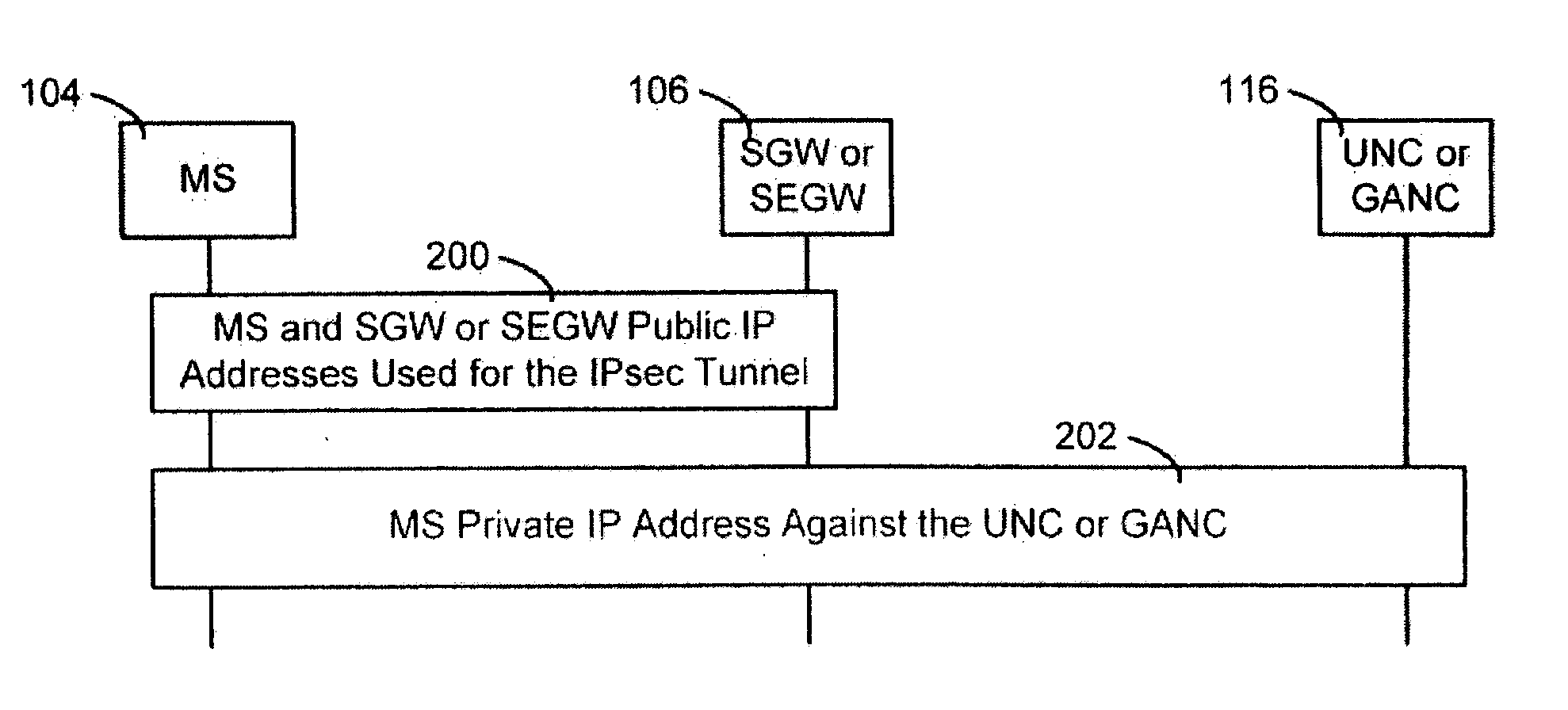
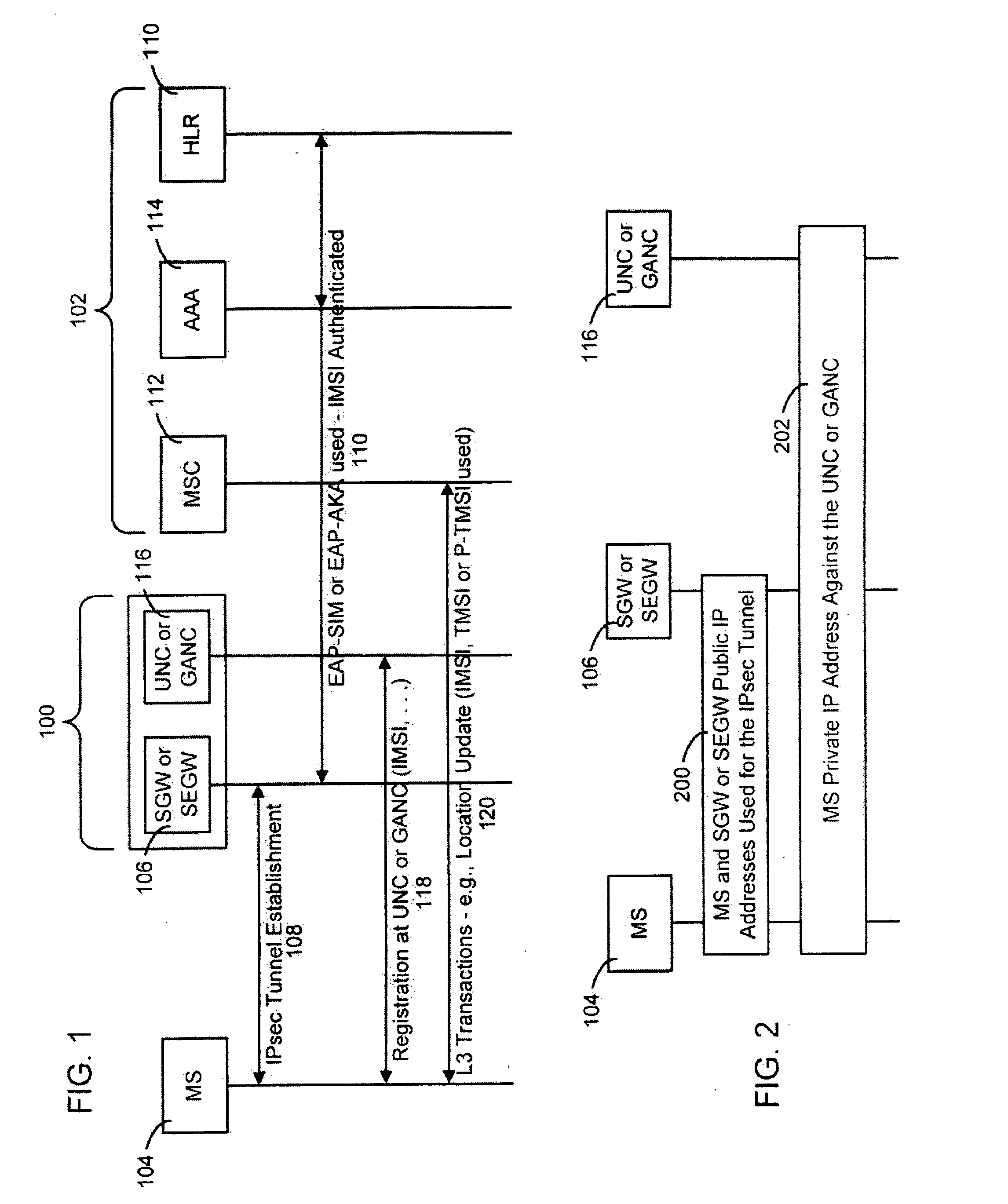
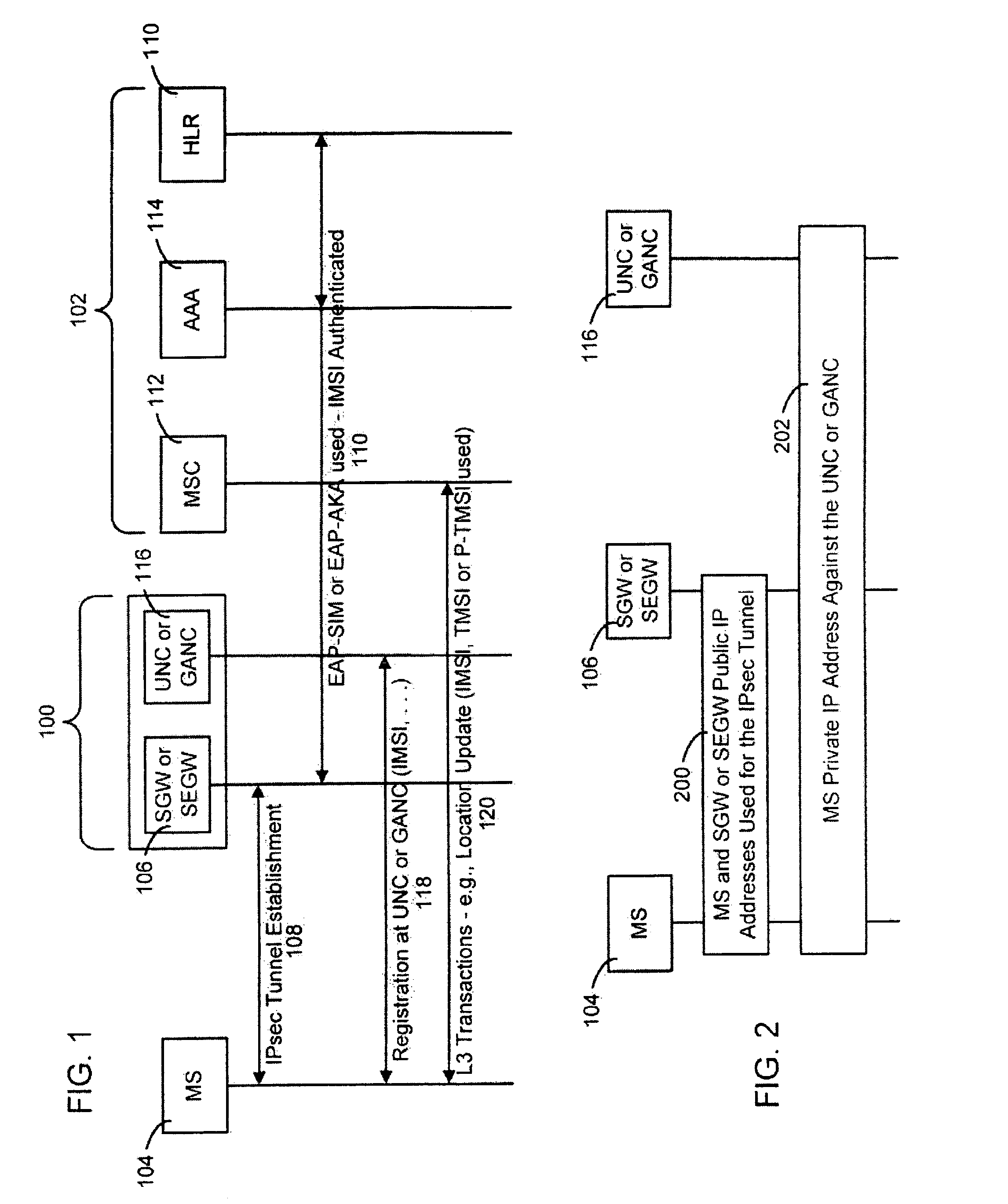
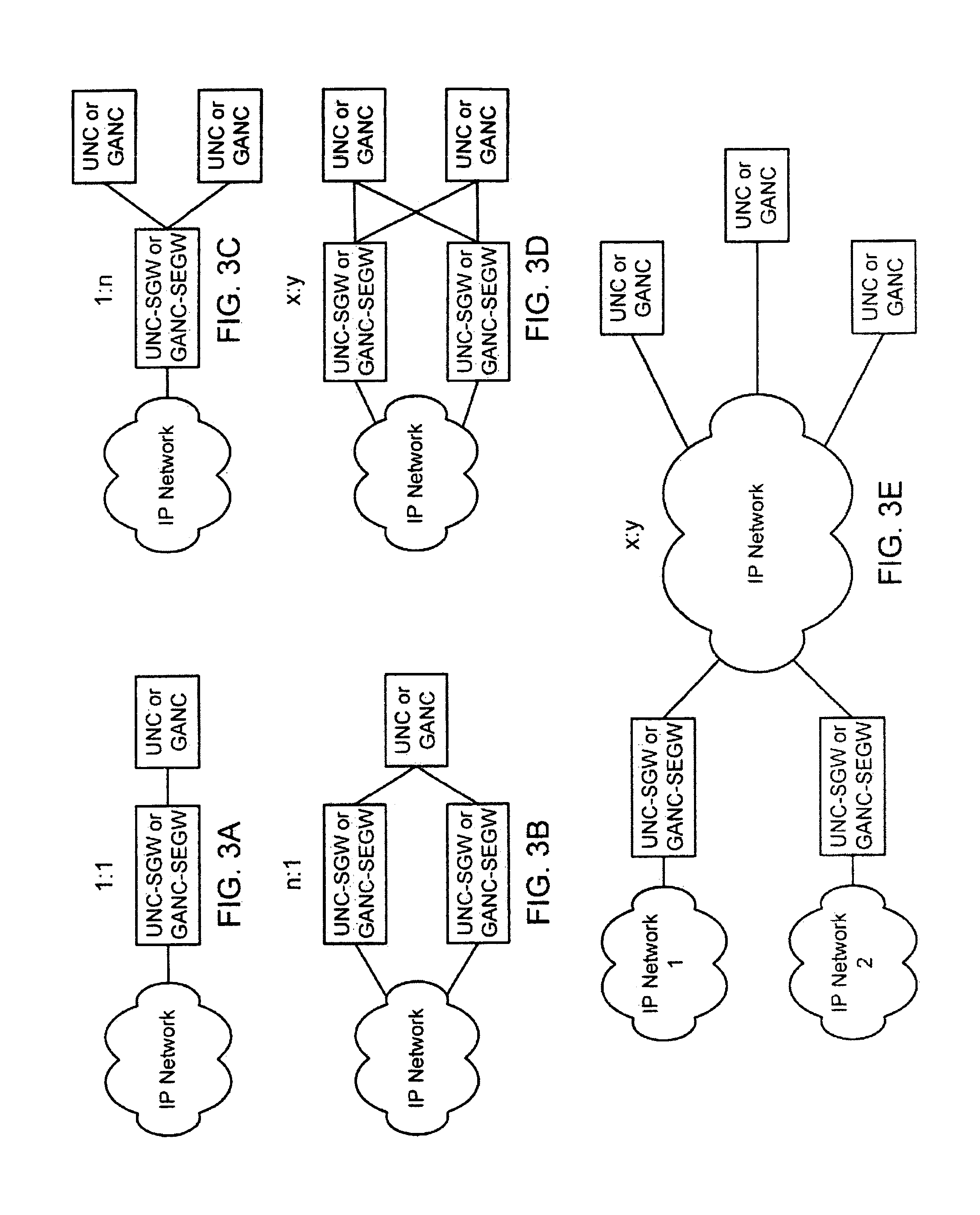
Method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network
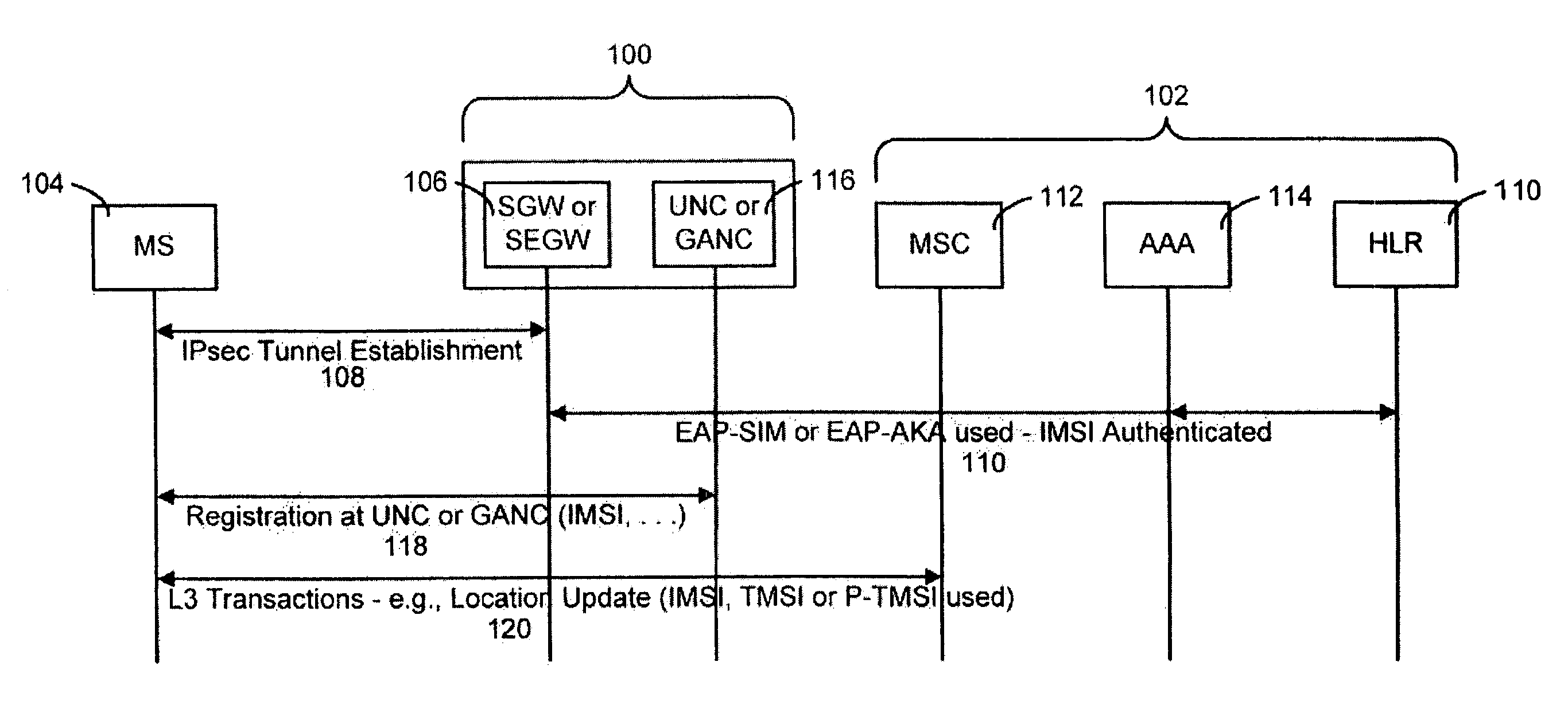
ActiveUS20060172732A1Minimizes O & M activityImprove standardizationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkGeneral Packet Radio Service
The present invention provides a method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network by receiving a message containing a mobile identity of a mobile station (MS) and dropping or rejecting the message whenever the received mobile identity does not match a stored mobile identity associated with the MS. The message is processed whenever the received mobile identity matches the stored mobile identity associated with the MS. The stored mobile identity is provided by a secure gateway. The mobile identity can be an International Mobile Subscriber Identity, Temporary Mobile Subscriber Identity, Packet Temporary Mobile Subscriber Identity, private Internet Protocol (IP) address or public IP address. The message can be a registration request, uplink message or a downlink message, such as a Mobility Management message, a General Packet Radio Service Mobility Management message, or a UMA or Unlicensed Radio Resources message.
Owner:TELEFON AB LM ERICSSON (PUBL)
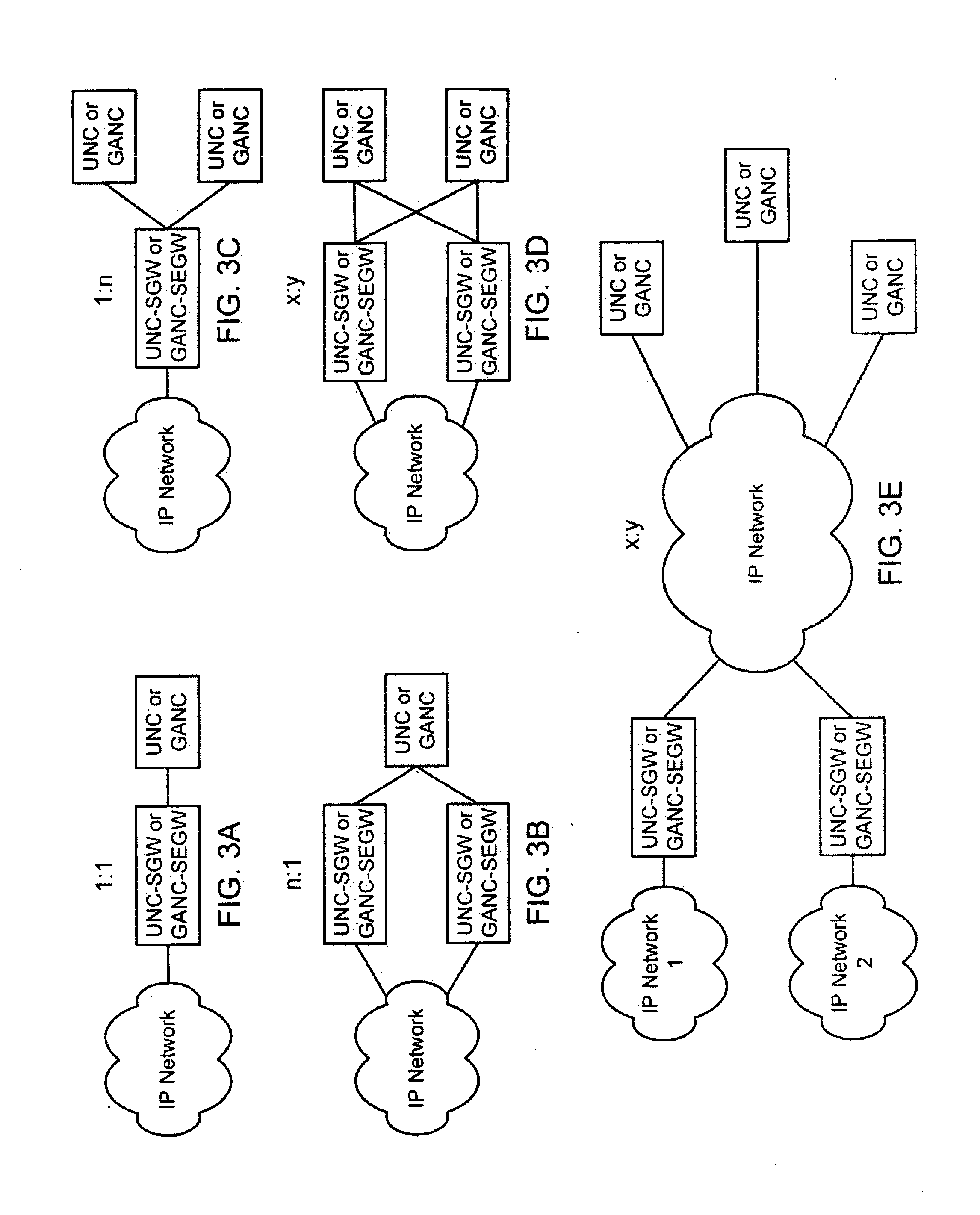
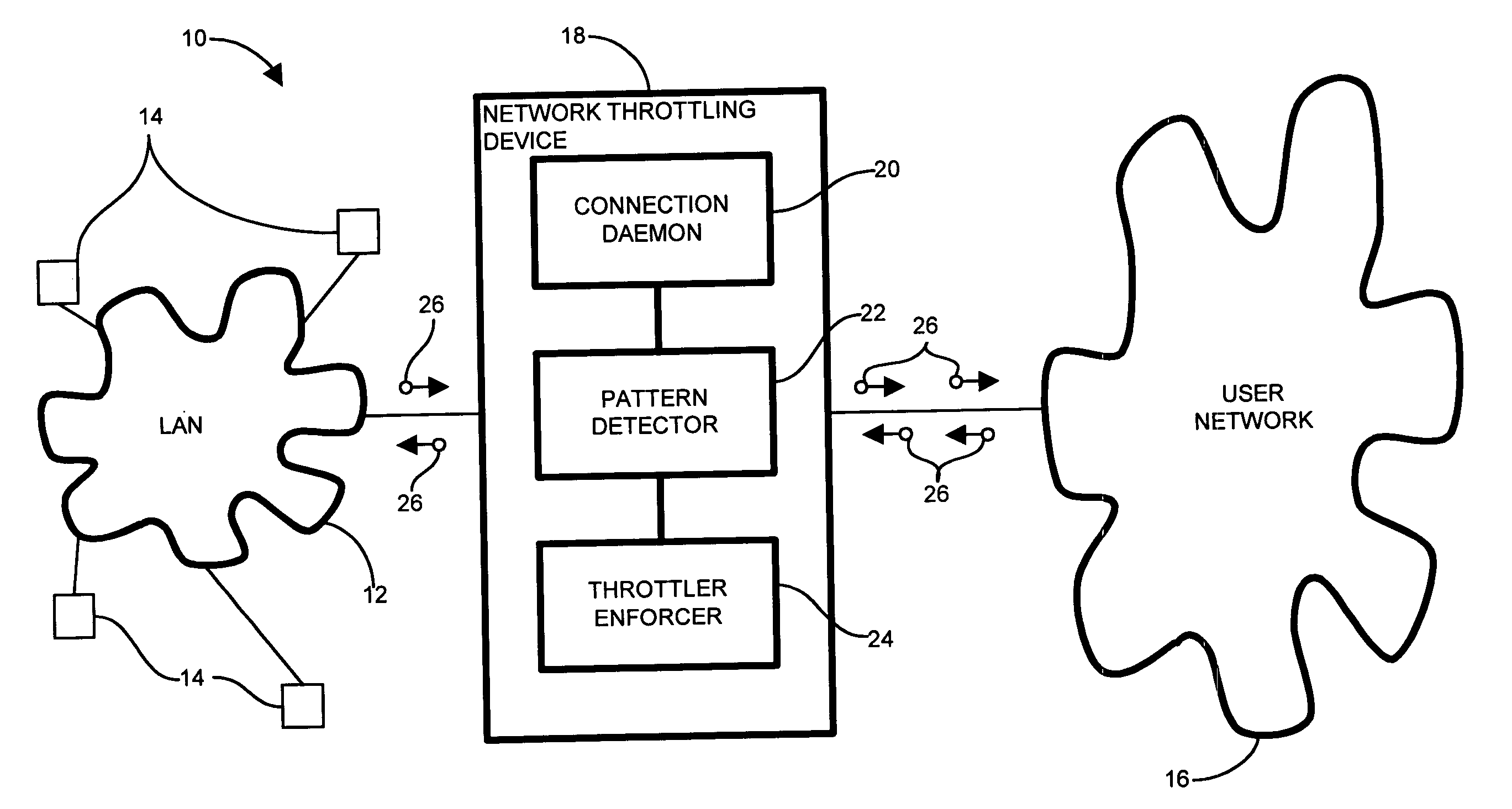
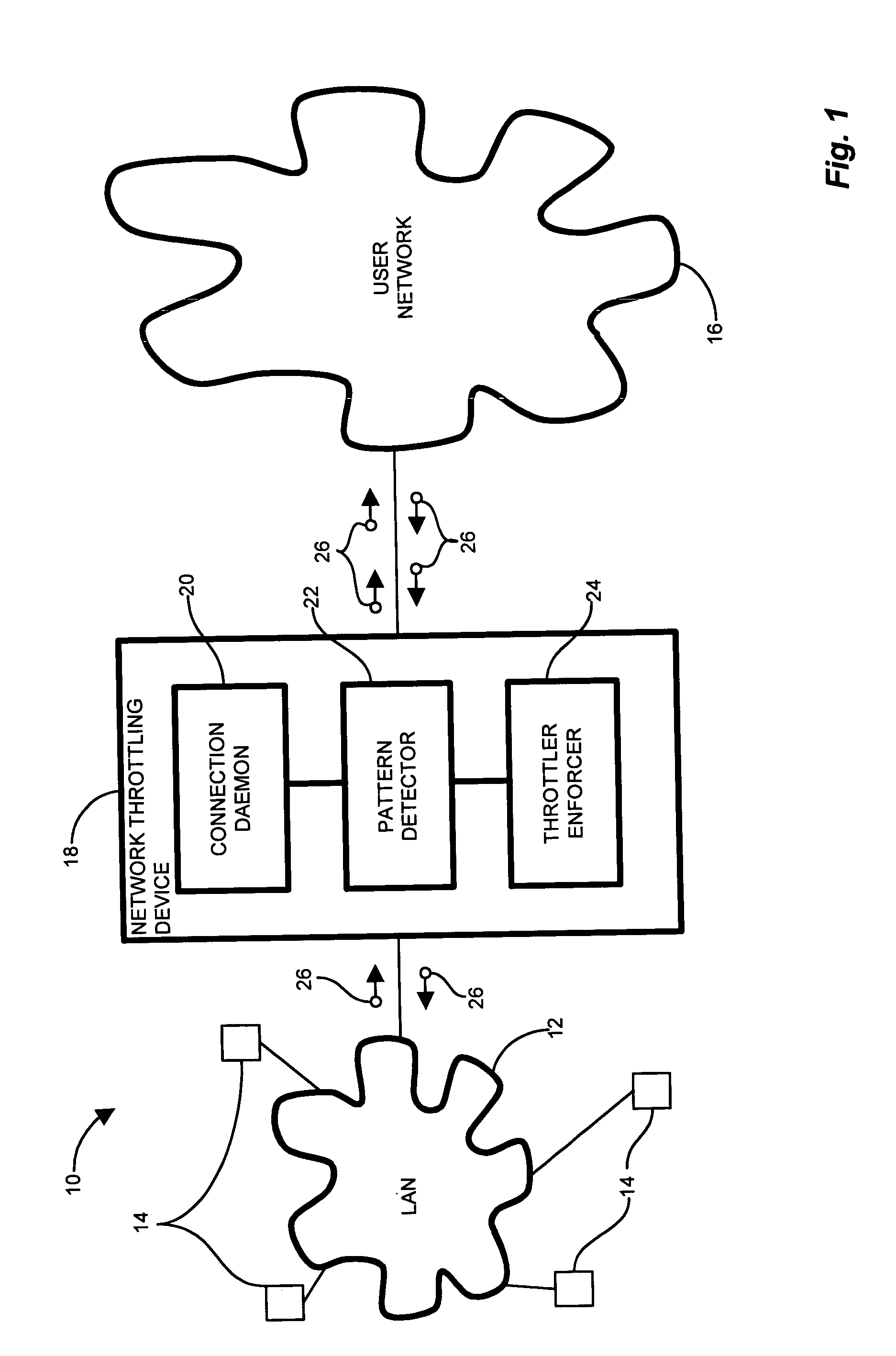
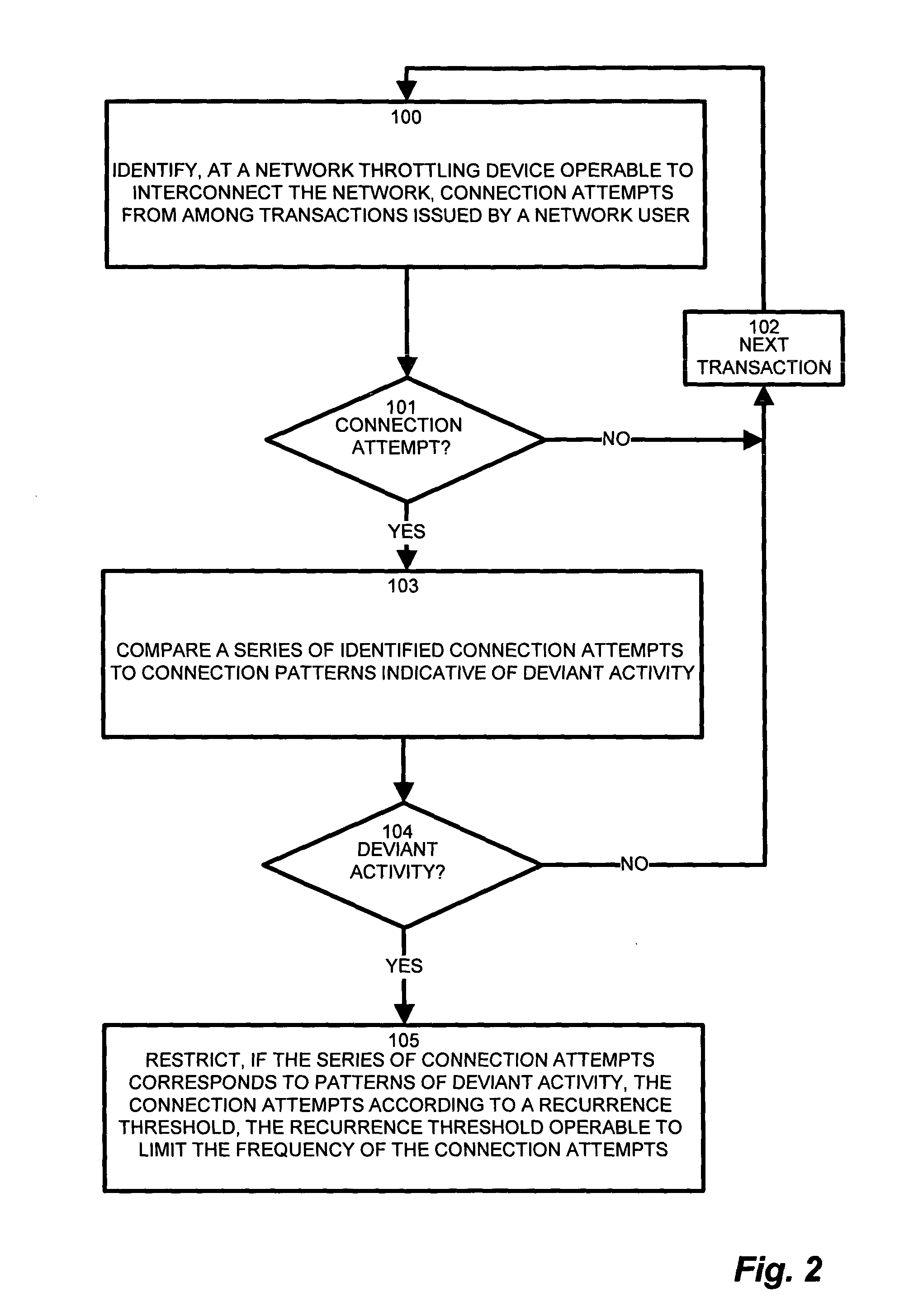
Network connection detection and throttling
InactiveUS7814542B1Reduce harmful effectsMinimize activityMemory loss protectionUnauthorized memory use protectionPattern detectionNetwork connection
In an edge network, message traffic between the edge network and a core network passes through the edge router. A port scanning attack directed to the network as a whole (core network) potentially emanates from within the LAN. The edge router includes a network throttling device which identifies and mitigates harmful transmissions such that they do not propagate to the core network. The network throttling device has a connection daemon to scan transactions and determine deviant or atypical connection attempts. A session database stores a transaction history representing a window of previous connection attempts. A pattern detector examines the history and looks for malicious behavior. Identified deviant patterns cause a throttler enforcer to limit the triggering user by restricting future connection attempts, thus mitigating harmful effects. Usage, therefore, is not prevented, but resilience to deviant practices is provided. Accordingly, virus propagation via port scanning is mitigated to a safe level and false alarms targeting legitimate activity are minimized.
Owner:CISCO TECH INC
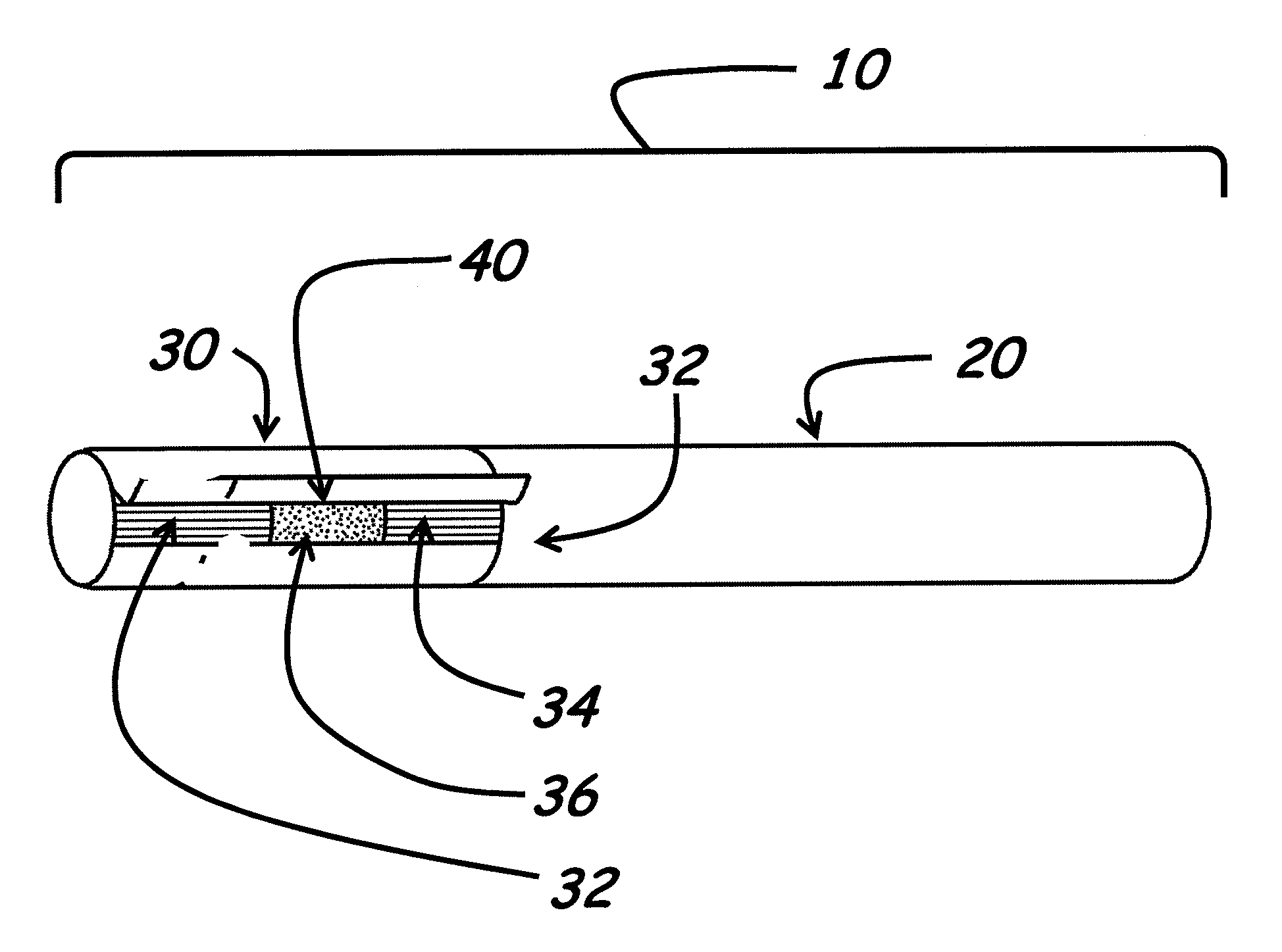
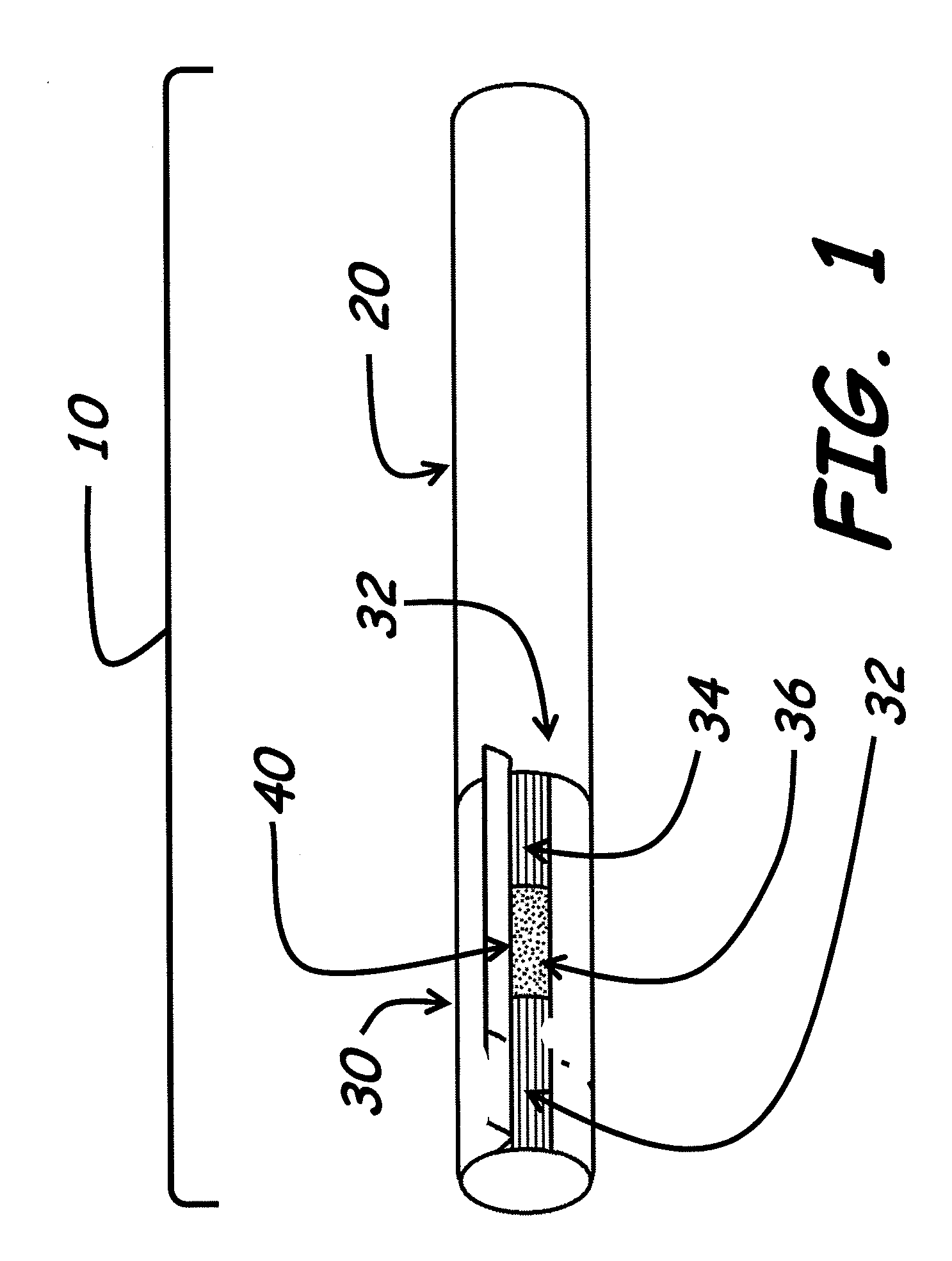
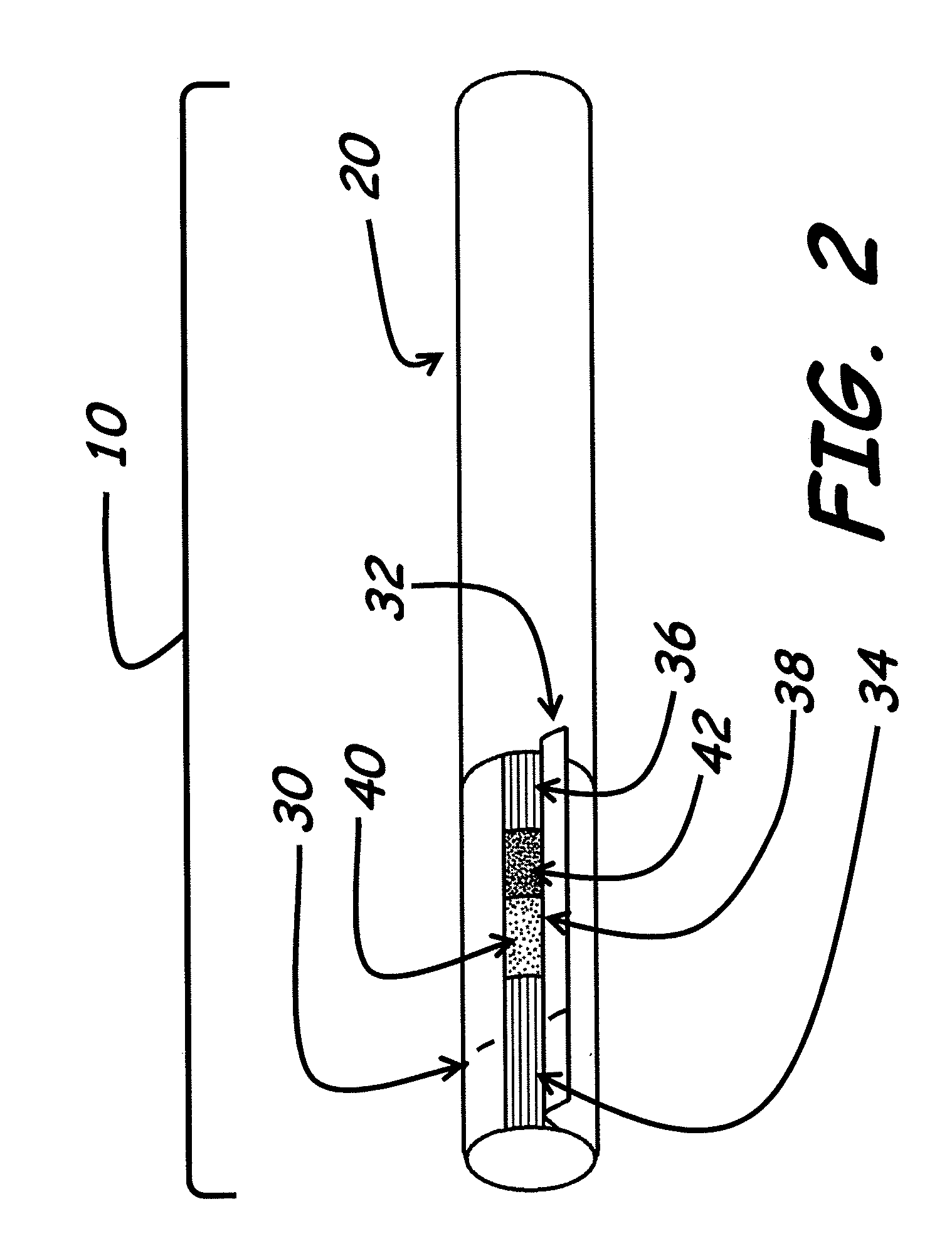
Smoking article and smoking article filter
InactiveUS20090056729A1Undesirable componentReduced characteristicsTobacco treatmentTobacco smoke filtersActivated carbonGas phase
Improved filters useful for tobacco products, such as cigarettes, and novel cigarettes having such filters are disclosed. The filters include adsorbents such as activated carbon which reduce amounts of one or more gas phase constituents of mainstream tobacco smoke. The adsorbents are treated with off-taste suppressants which reduce the off-taste associated with adsorbent containing filters and substantially restore the taste normally associated with tobacco smoke.
Owner:ZAWADZKI MICHAEL A +4
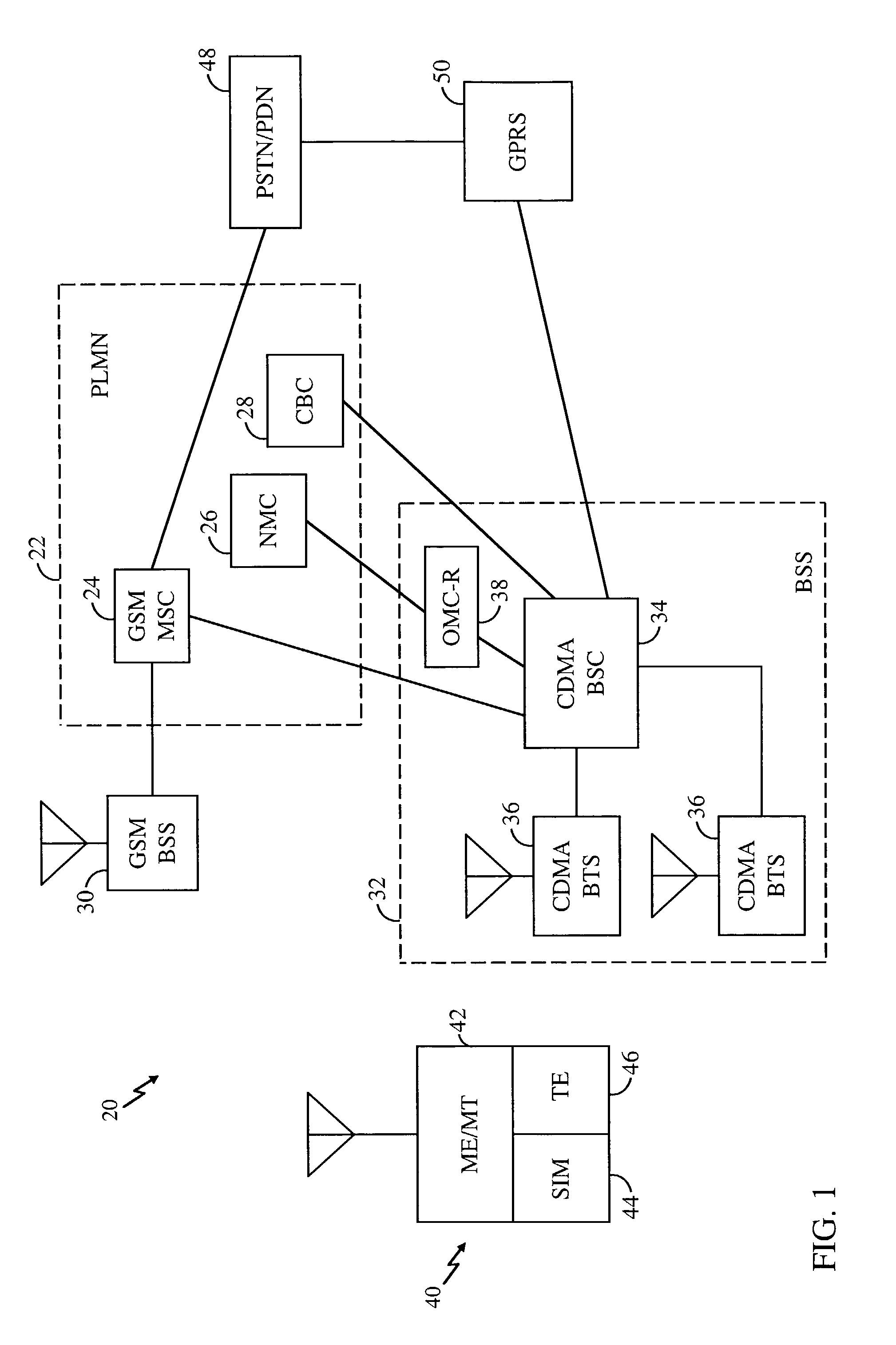
Idle mode handling in a hybrid GSM/CDMA network
InactiveUS7092716B2Minimize activityConserve battery lifeTime-division multiplexFrequency-division multiplexAir interfaceMobile station
In a mobile wireless telecommunications system, which includes base stations (30) of a first type operating over a first air interface, and base stations (32) of a second type operating over a second air interface, a method for reselection by a mobile station (40) camped on a cell associated with a first base station (30), which is of the first type, of a second base station (32), which is of the second type. The method includes receiving signals over the second air interface from the second base station (32) and evaluating a characteristic of the signals. Responsive to the characteristic, the second base station (32) is selected in place of the first base station (30), and the mobile station (40) camps on a cell associated with the second base station (32).
Owner:QUALCOMM INC
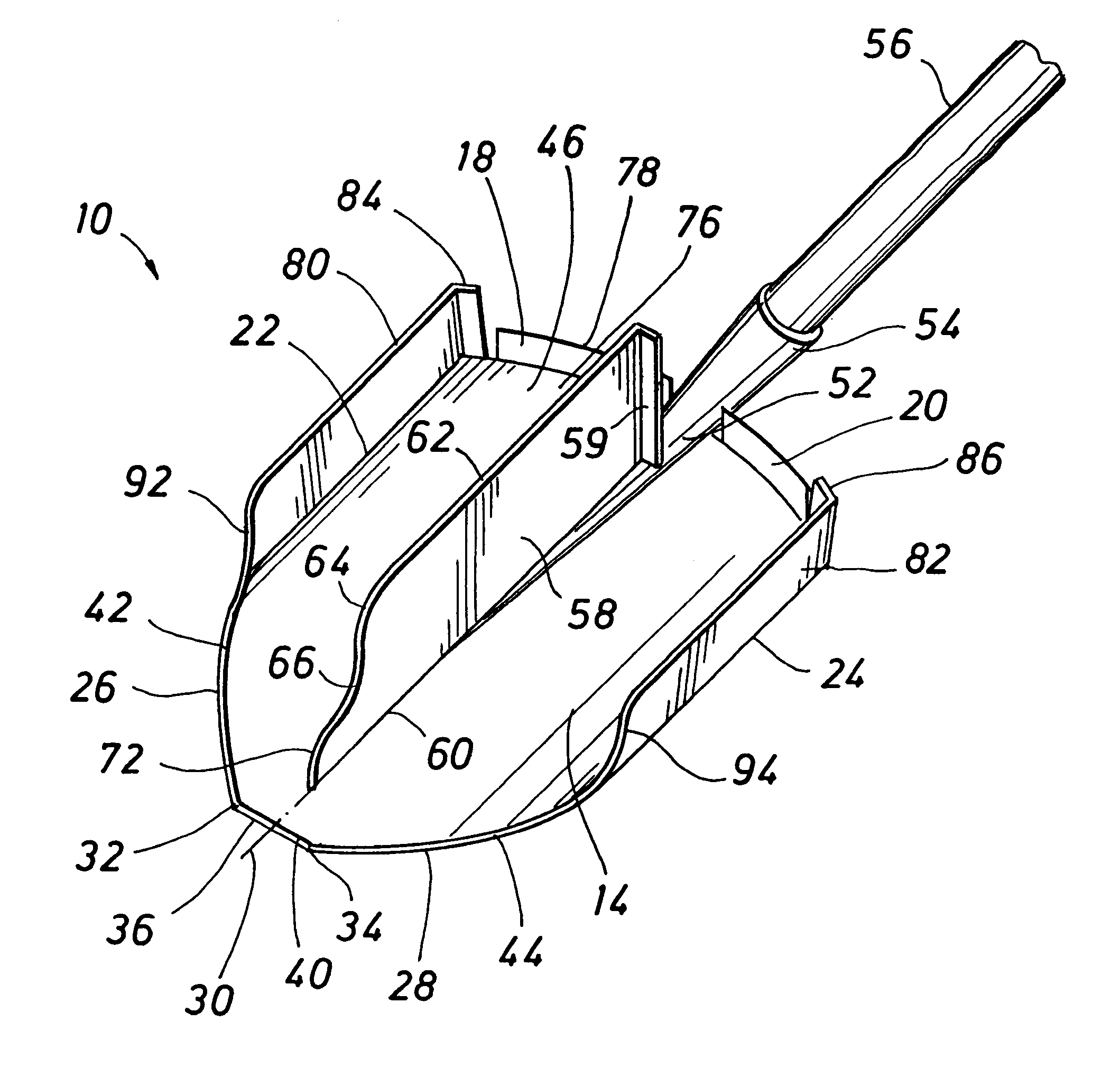
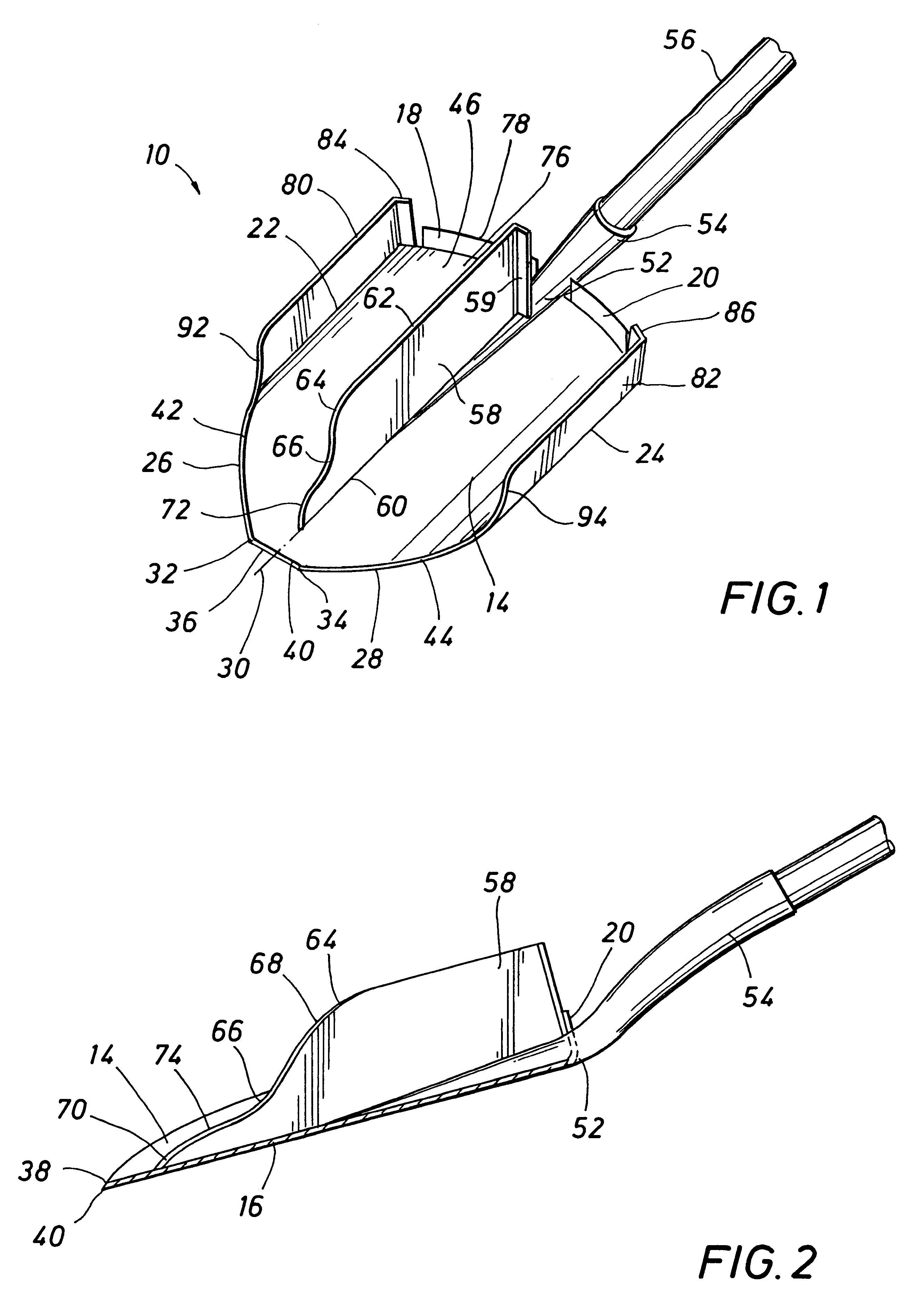
Root cutting shovel
A shovel for manual use, comprising a shovel blade having concave and convex faces and defining a longitudinal center-line and having side edges, an upper edge and a forward cutting edge. The shovel blade defines a handle connector receptable having a shovel handle fixed therein. A root cutting blade is fixed to the shovel blade substantially along the longitudinal center-line and projects from the concave face of the shovel blade. A sharpened root cutting edge is defined on the root cutting blade and is oriented toward the forward cutting edge of the shovel blade. The root cutting edge of the central blade preferably defines an intermediate edge recess and forms a slightly inclined sharp edge section for enhancing root cutting action. A pair of side blades are fixed to side edge portions of the shovel blade and are oriented in diverging relation projecting from the convex face of the shovel blade. The side blades also preferably define forwardly inclined sharpened cutting edges and are located for cutting surface roots at respective sides of the shovel blade to facilitate efficient fracturing of the soil when the shovel blade has penetrated into the soil and is pivoted to pry a soil load loose from the surrounding soil.
Owner:DOUGLAS ORMOND S +1
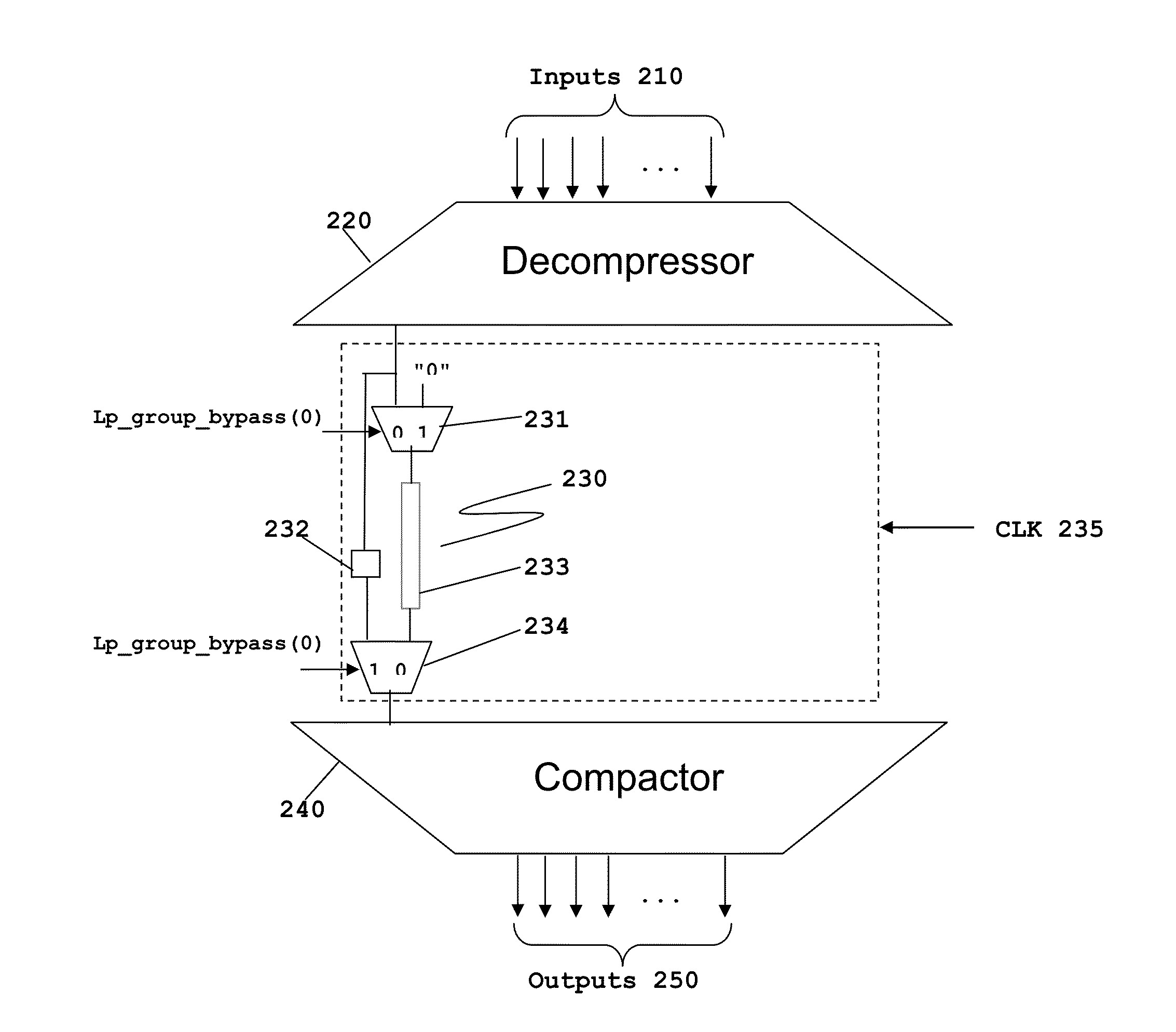
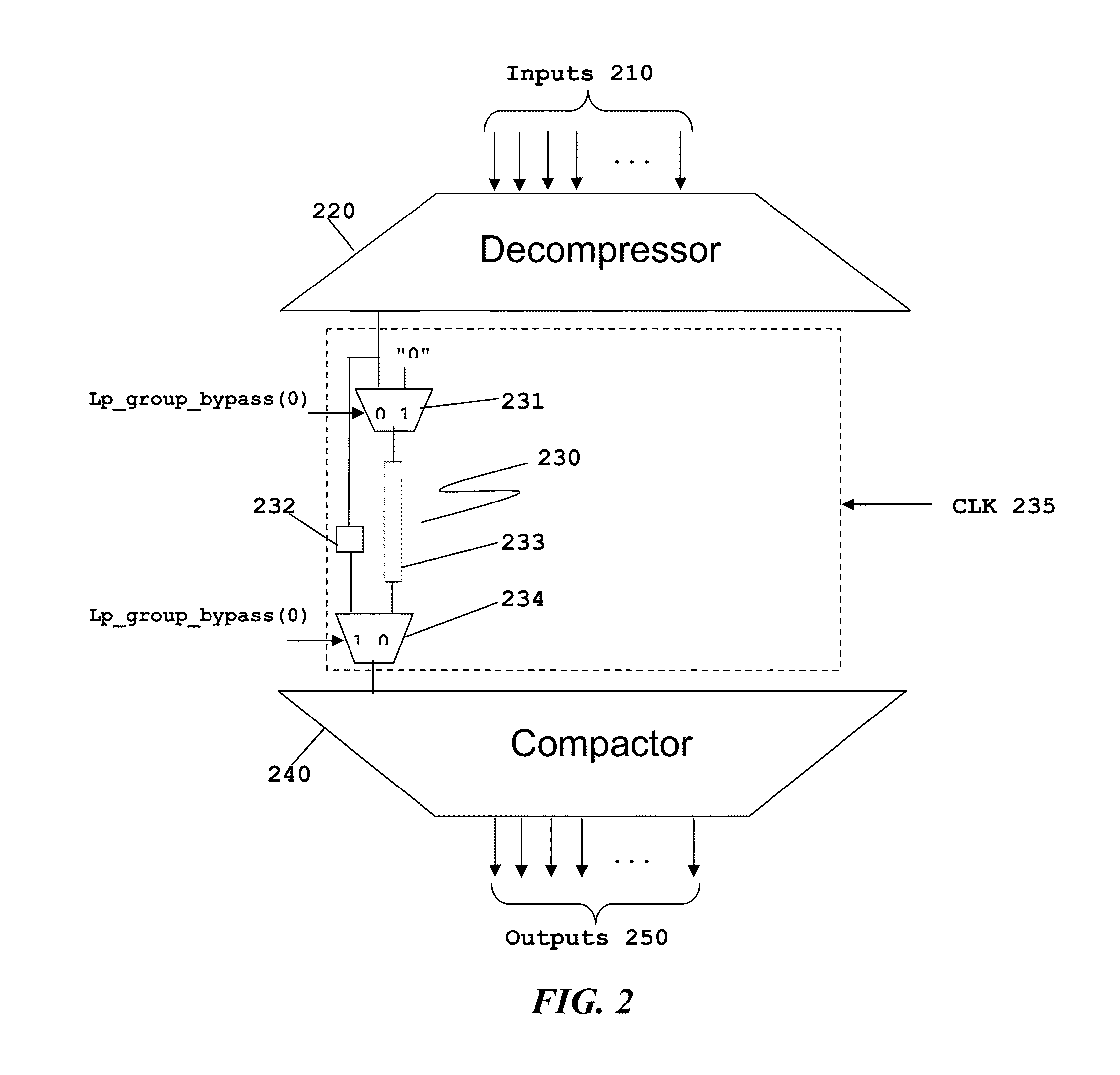
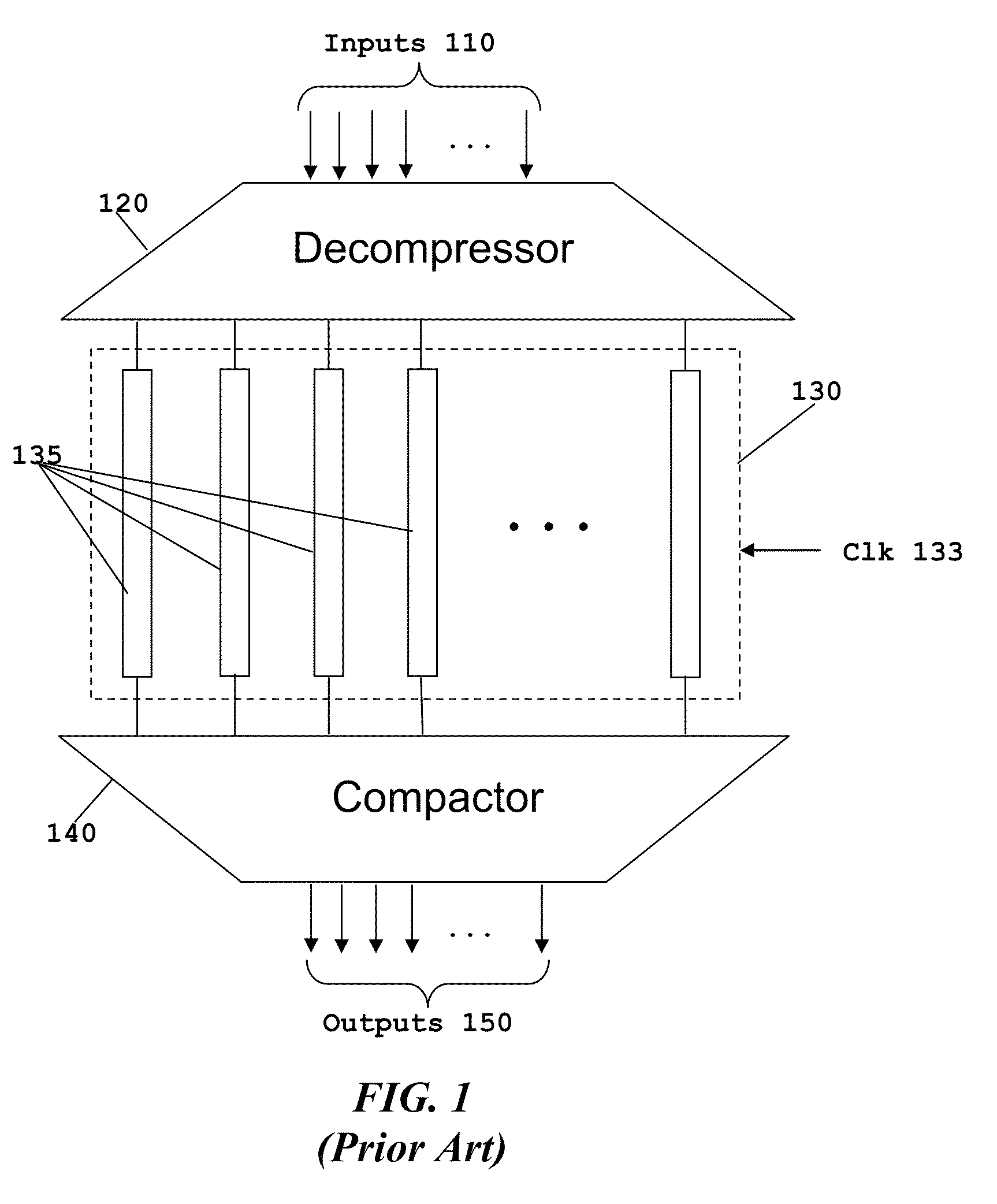
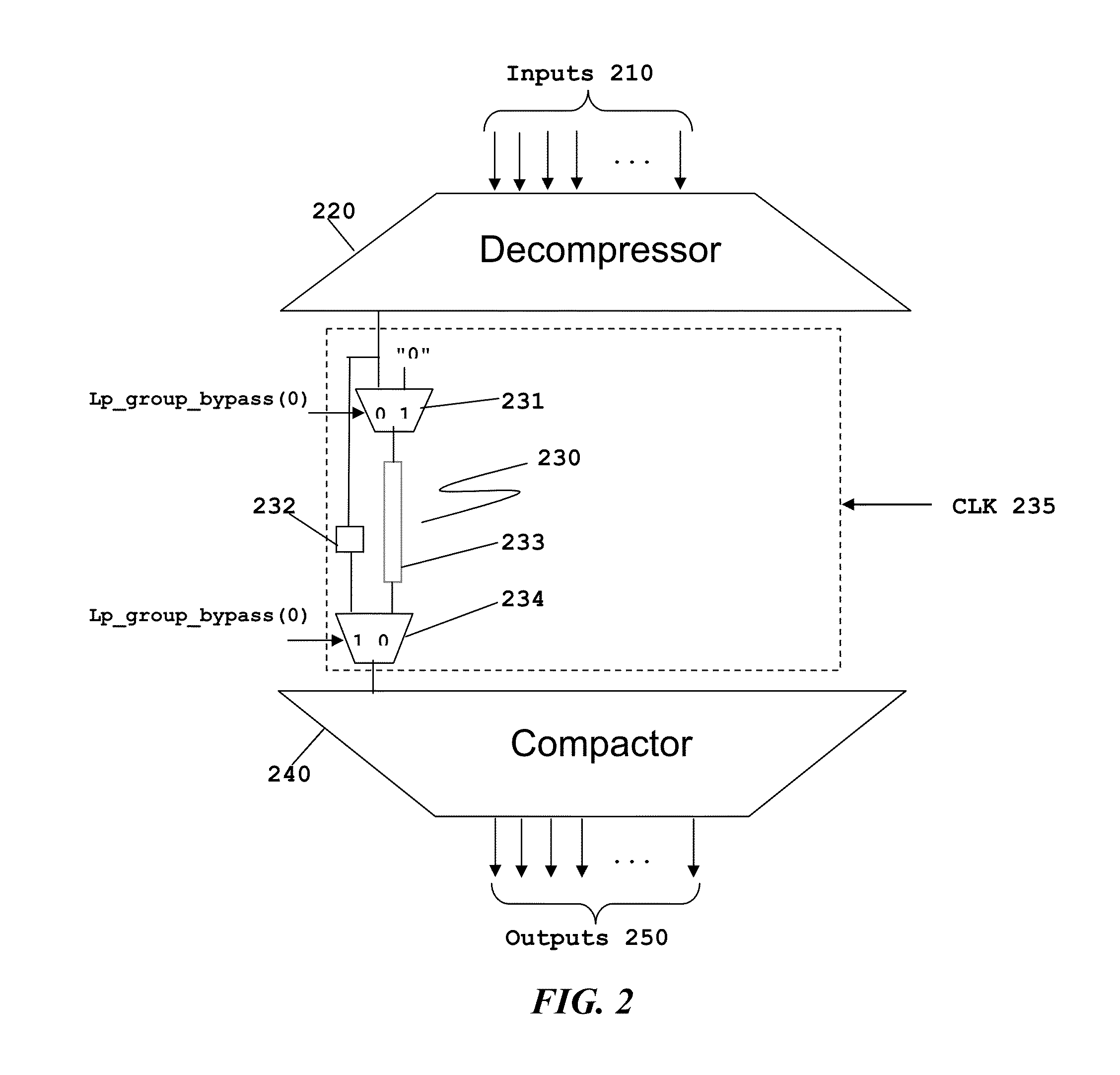
Scan Compression Architecture with Bypassable Scan Chains for Low Test Mode Power
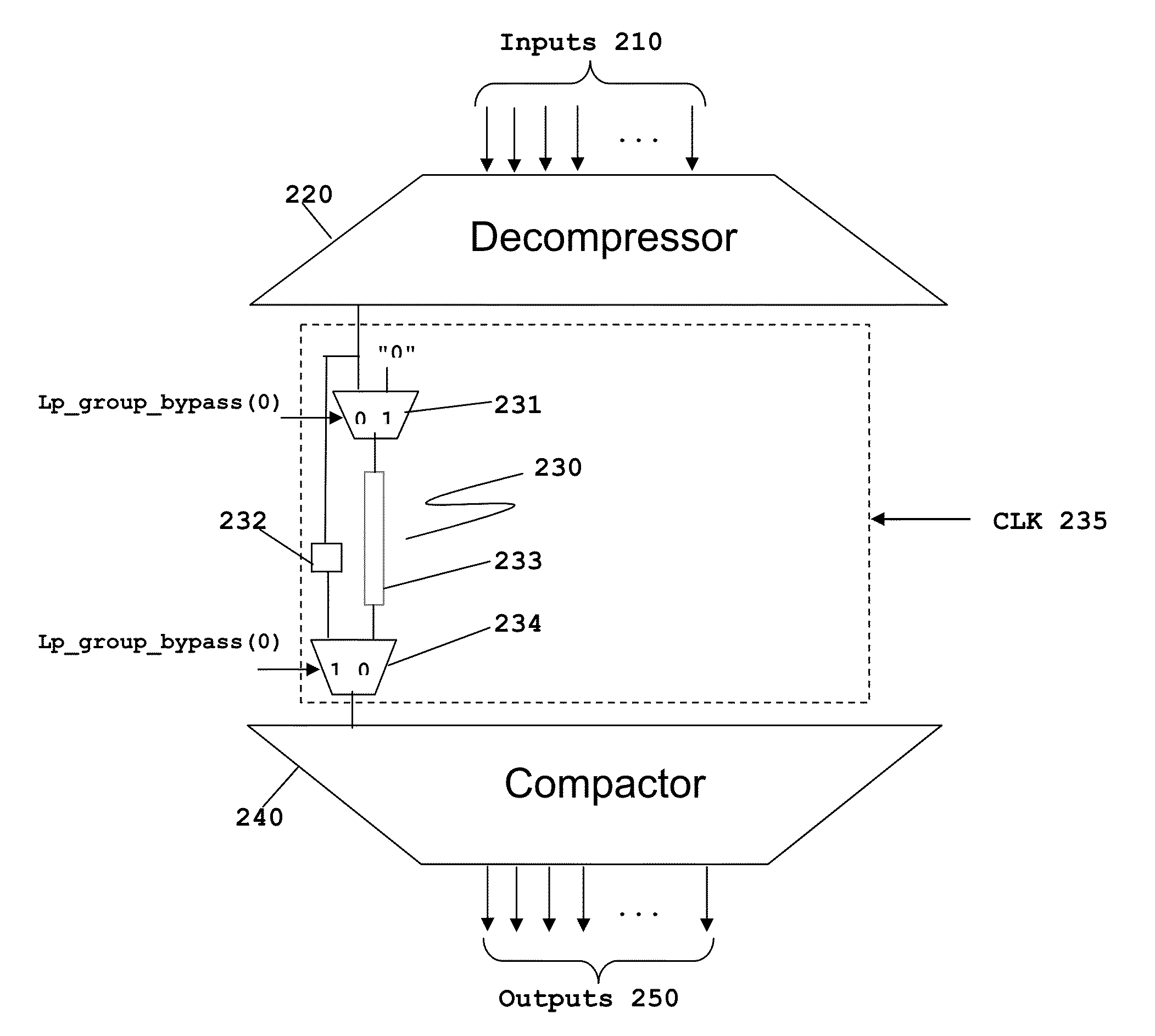
ActiveUS20130159800A1Minimize activitySave considerable powerElectronic circuit testingOptimal testEngineering
This invention permits selectively bypasses serial scan chains. Constant or low toggle data is directed to the bypassed serial scan chain, thus reducing power consumption. The number and identity of serial scan chains bypassed during a particular test can be changed dynamically dependent upon the semiconductor process variations of a particular integrated circuit. This enables an optimal test to be preformed for integrated circuits having differing semiconductor process variations.
Owner:TEXAS INSTR INC
Cleavable reagents for specific delivery to disease sites
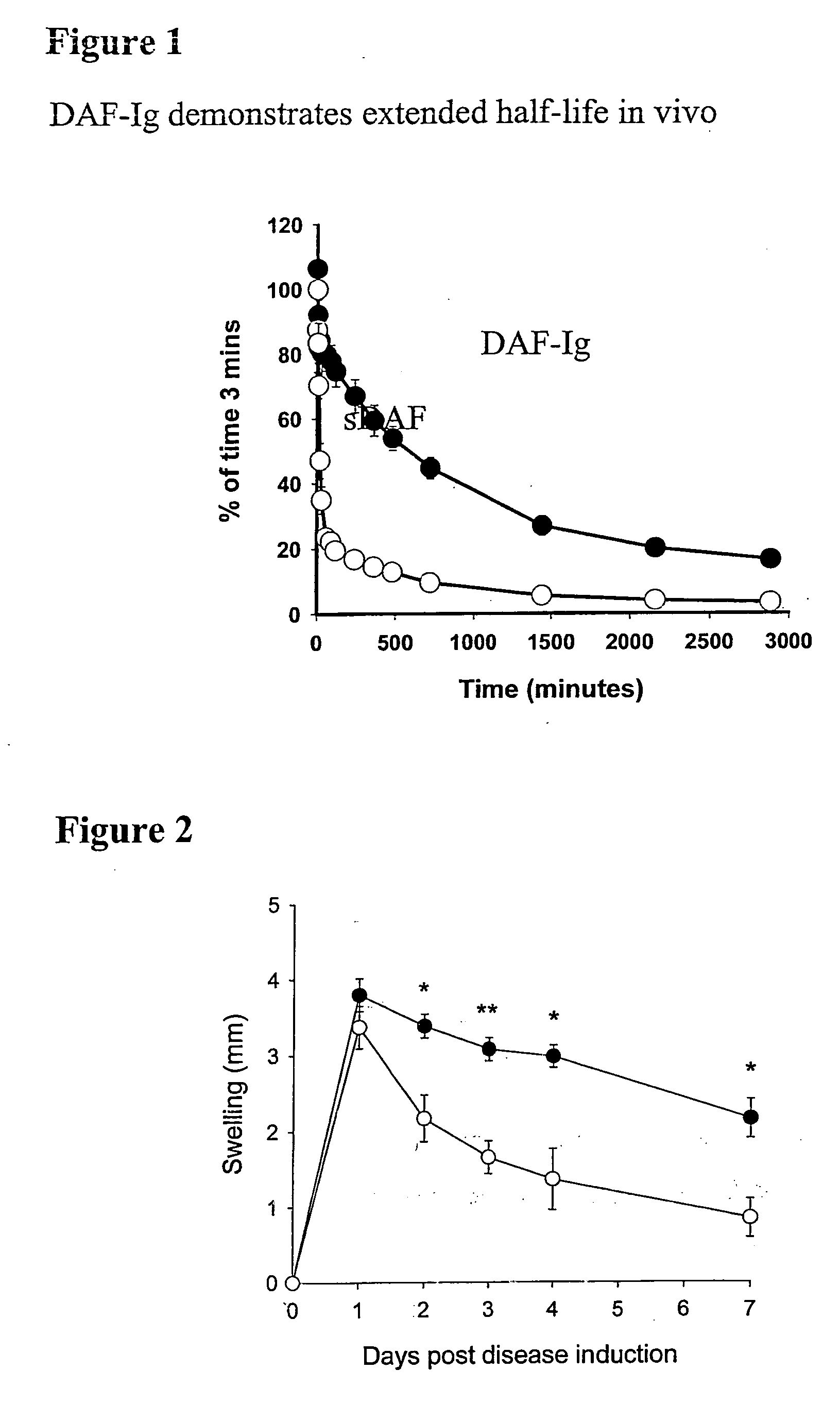
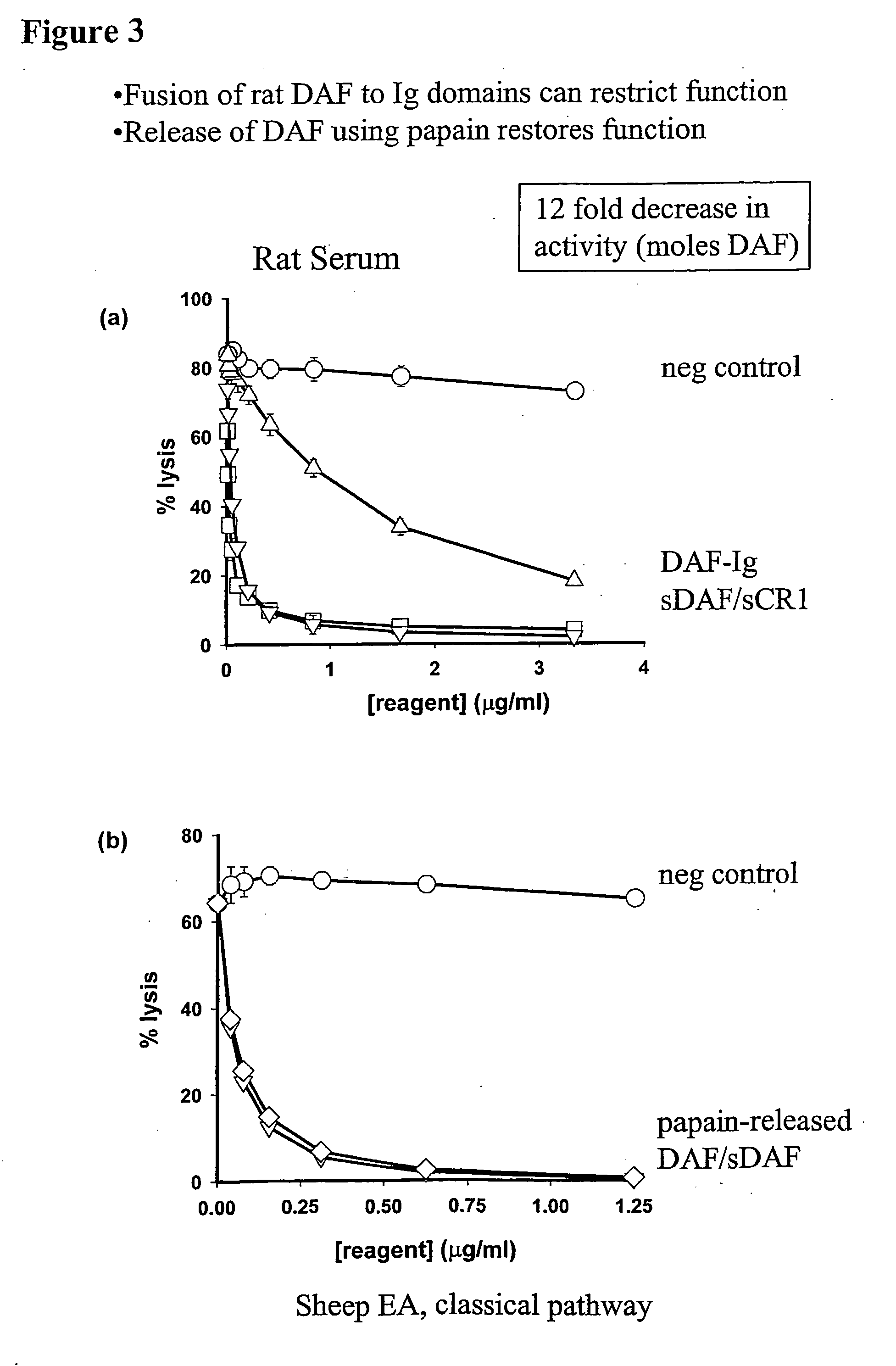
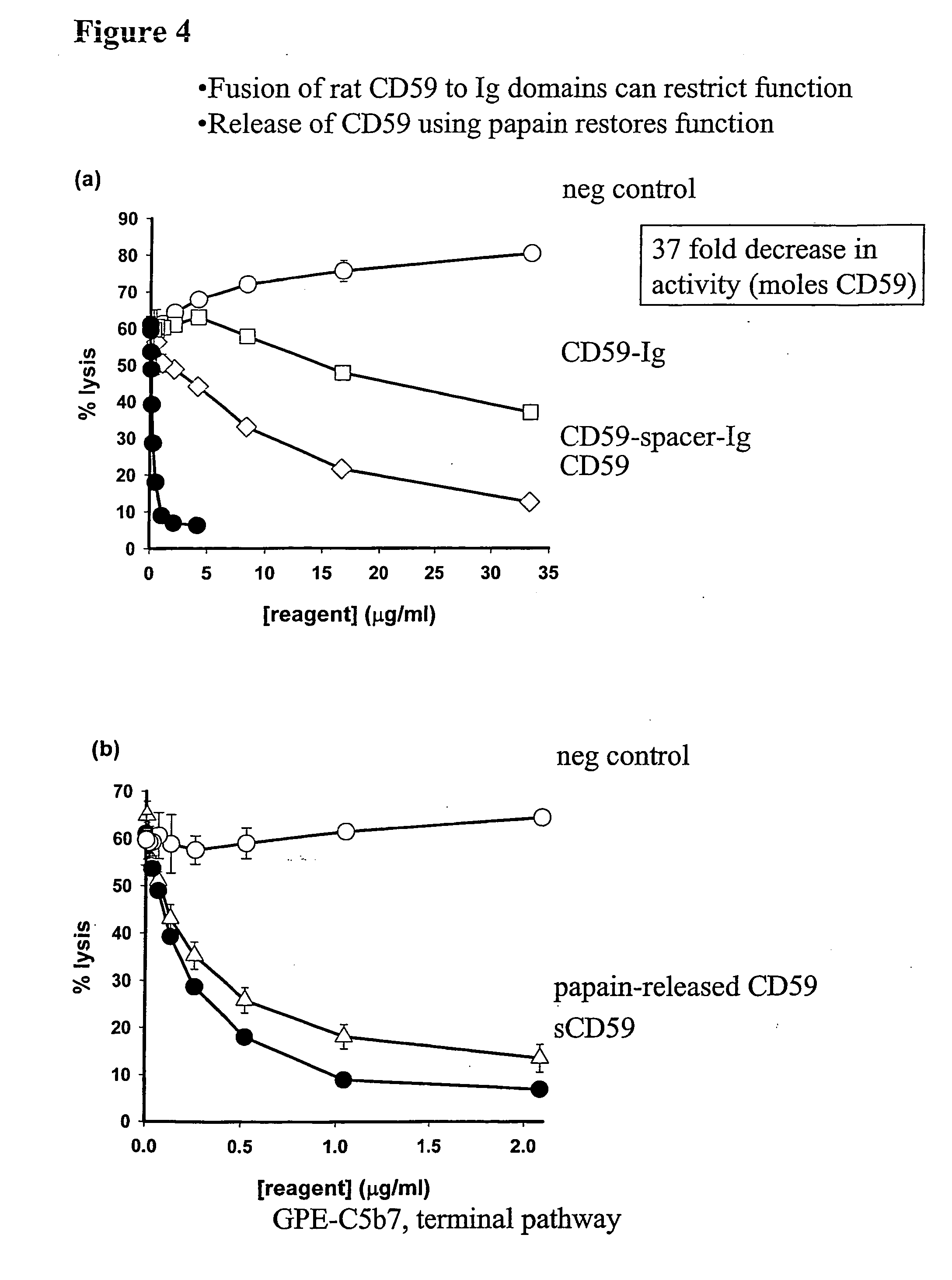
InactiveUS20060246066A1Long plasma half lifeMinimal systemic effectNervous disorderPeptide/protein ingredientsDiseaseCarrier protein
A therapeutic reagent to control one or more reactions of the immune system in a host, or to deliver anti-tumour agents, or disease treatment agents to the host. The therapeutic reagent comprises a regulatory moiety and a carrier protein that inactivates or substantially reduces the activity of the regulatory moiety. Also, the therapeutic reagent includes a cleavage site at which cleavage of the therapeutic reagent can occur to free the regulatory moiety from the carrier protein so that the therapeutic reagent can act at a diseased site in the host.
Owner:UNIV COLLEGE CARDIFF CONSULTANTS LTD
Method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network
ActiveUS7280826B2Minimize activityImprove standardizationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsGeneral Packet Radio ServiceAccess network
The present invention provides a method, system and apparatus for providing security in an unlicensed mobile access network or a generic access network by receiving a message containing a mobile identity of a mobile station (MS) and dropping or rejecting the message whenever the received mobile identity does not match a stored mobile identity associated with the MS. The message is processed whenever the received mobile identity matches the stored mobile identity associated with the MS. The stored mobile identity is provided by a secure gateway. The mobile identity can be an International Mobile Subscriber Identity, Temporary Mobile Subscriber Identity, Packet Temporary Mobile Subscriber Identity, private Internet Protocol (IP) address or public IP address. The message can be a registration request, uplink message or a downlink message, such as a Mobility Management message, a General Packet Radio Service Mobility Management message, or a UMA or Unlicensed Radio Resources message.
Owner:TELEFON AB LM ERICSSON (PUBL)
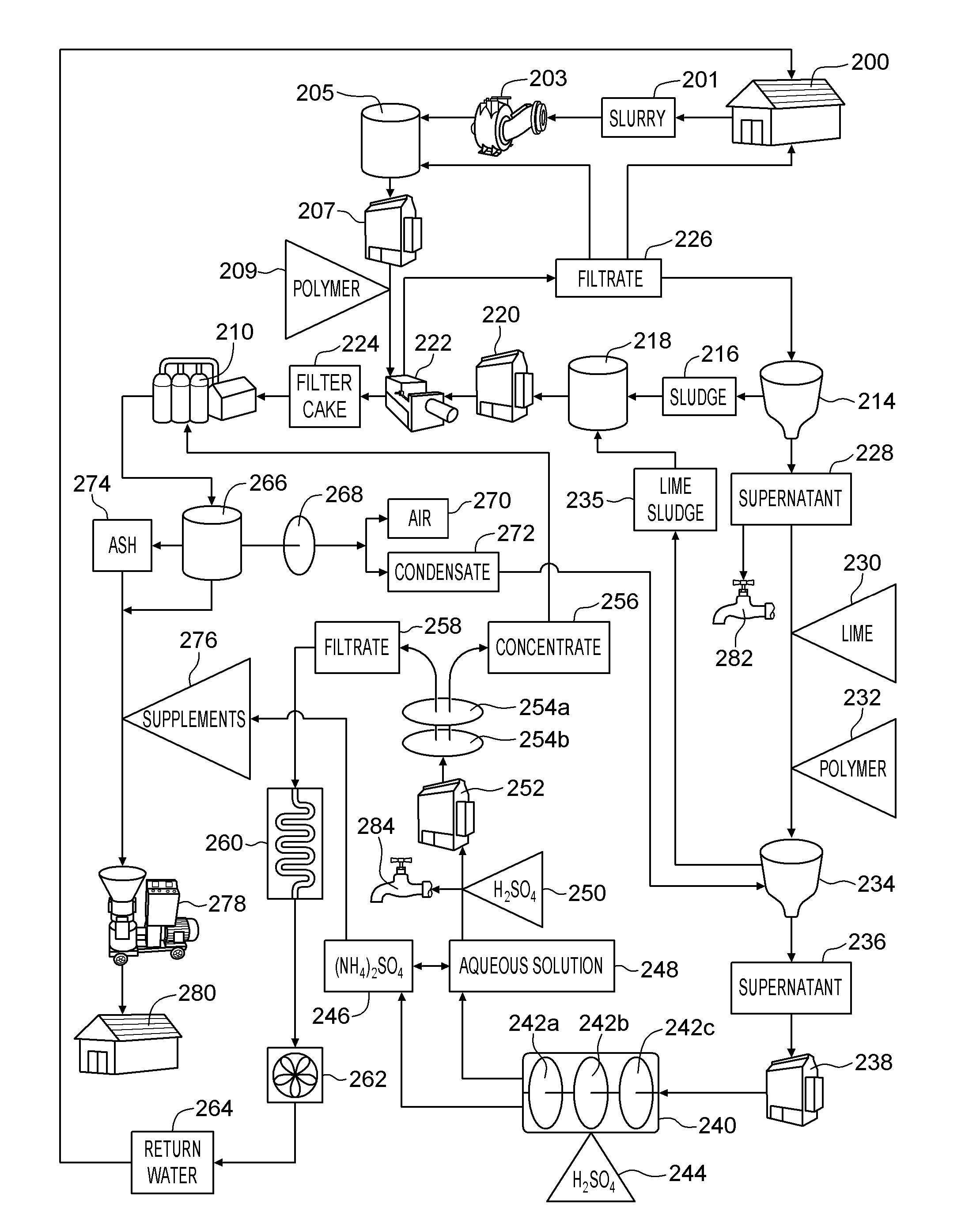
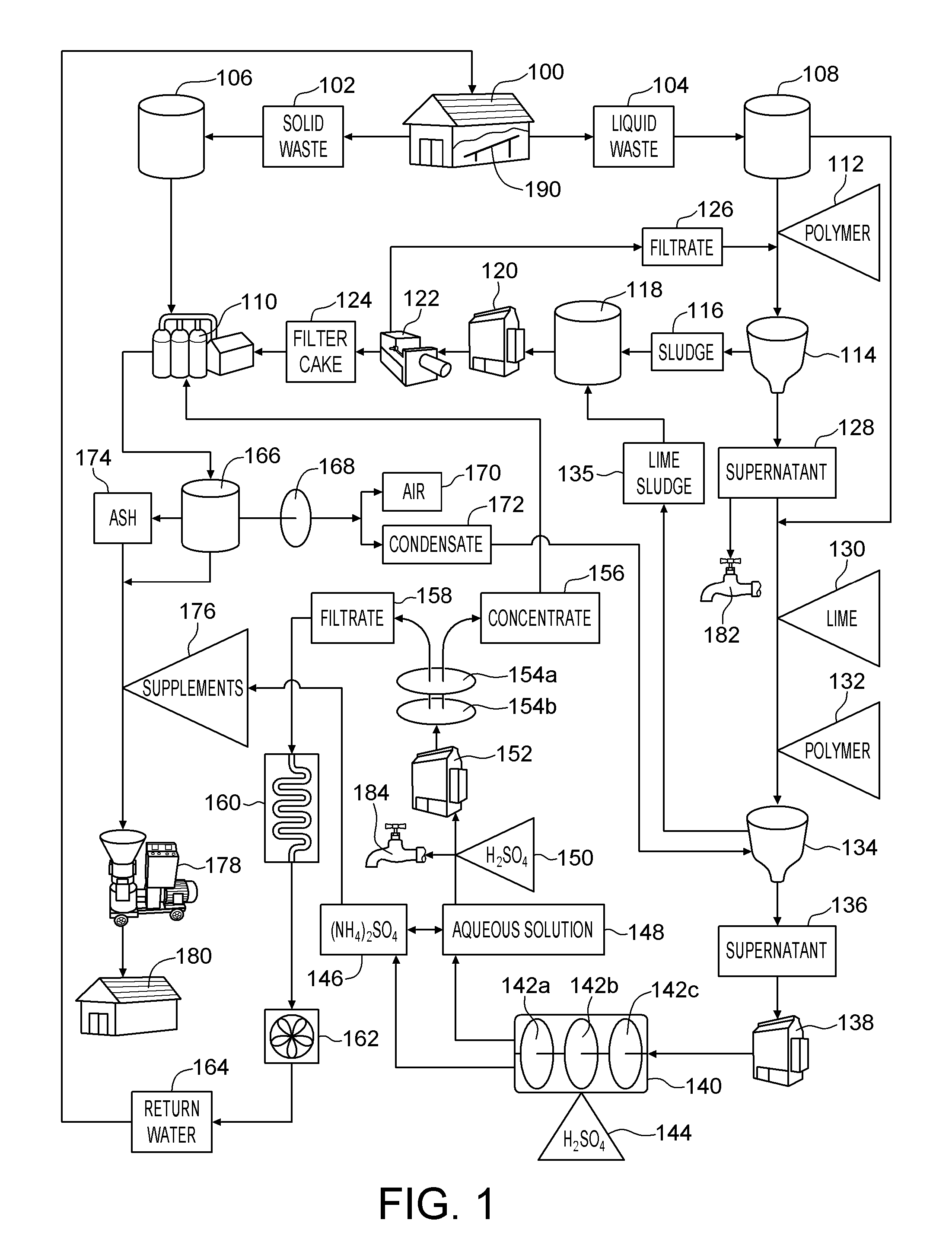
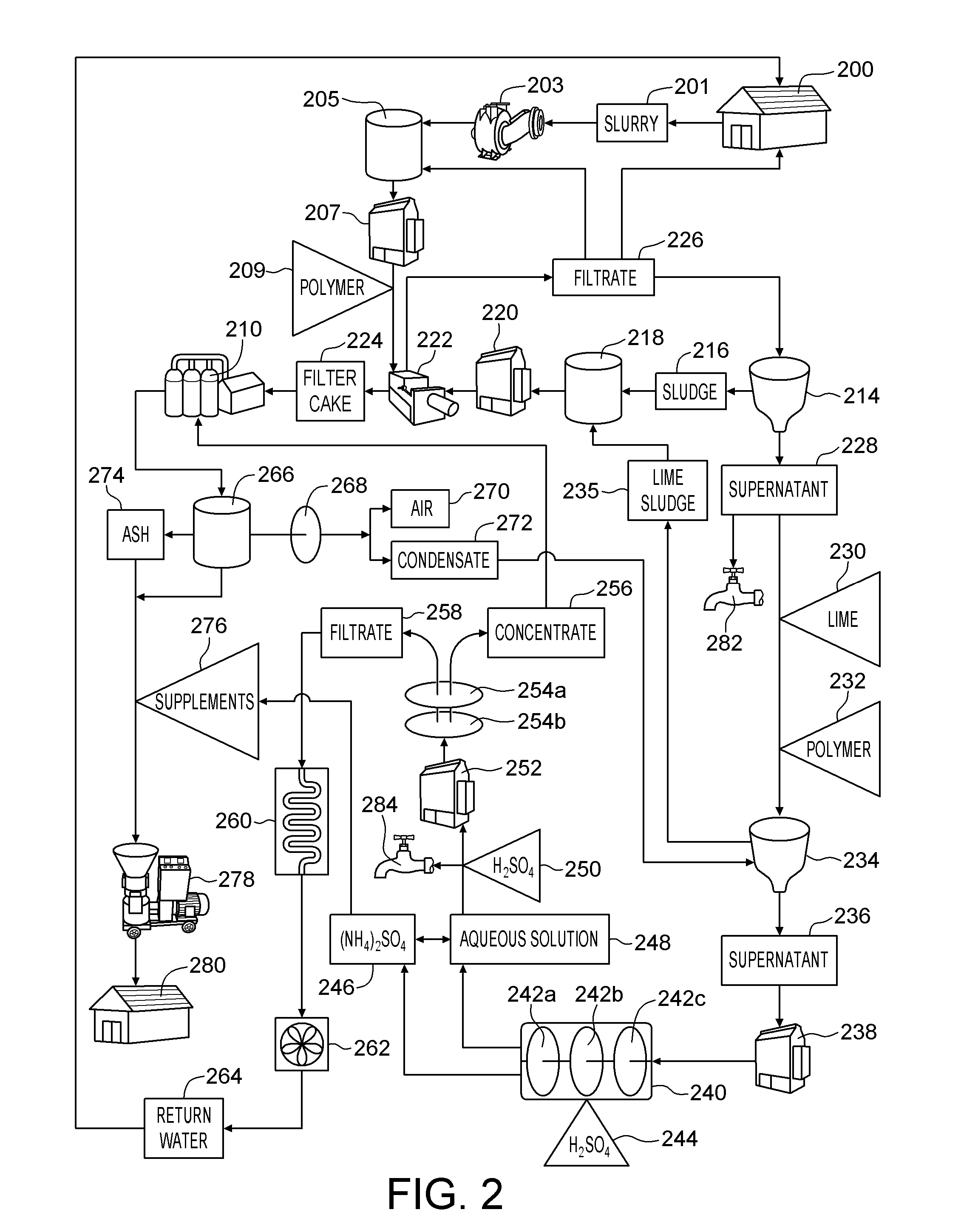
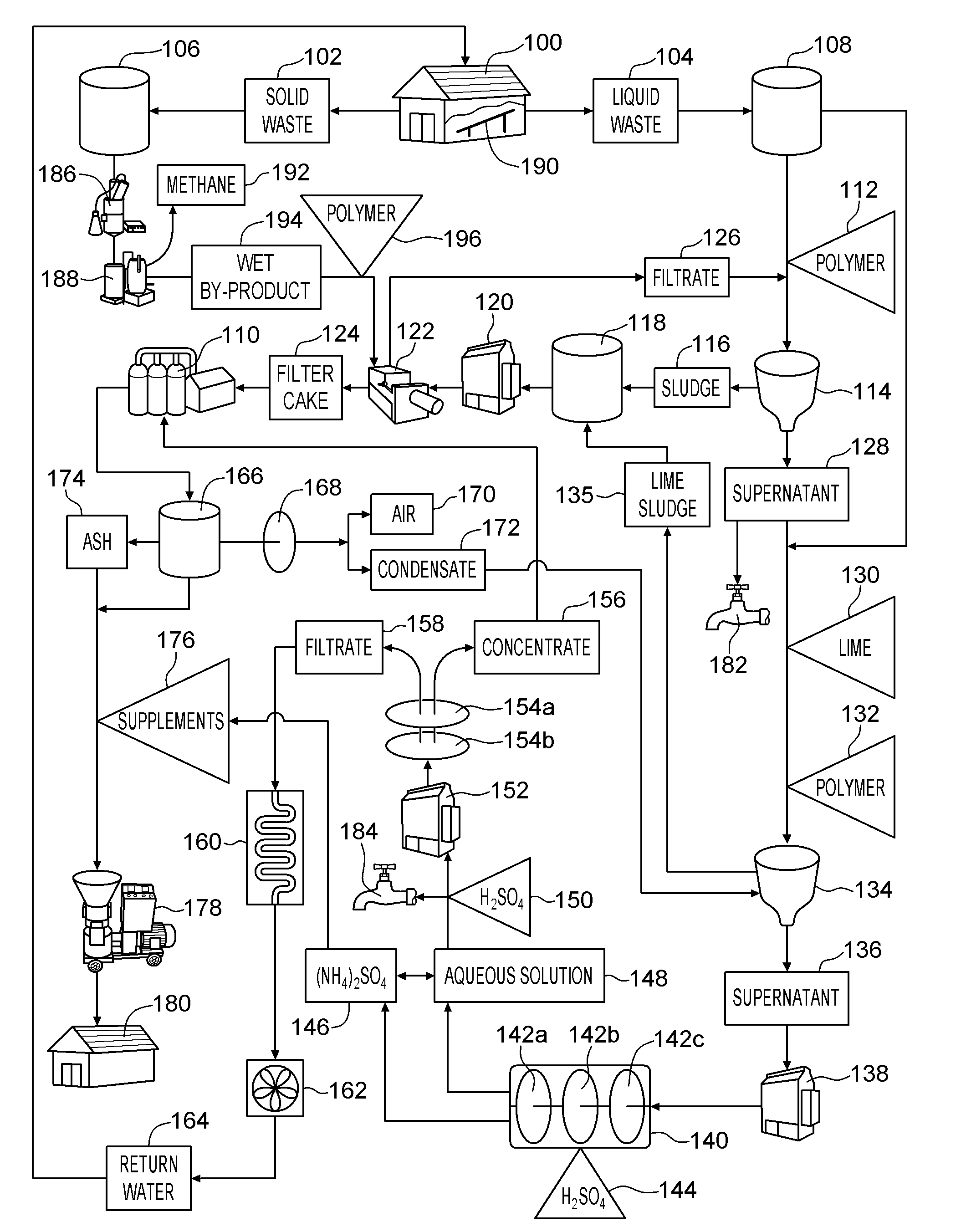
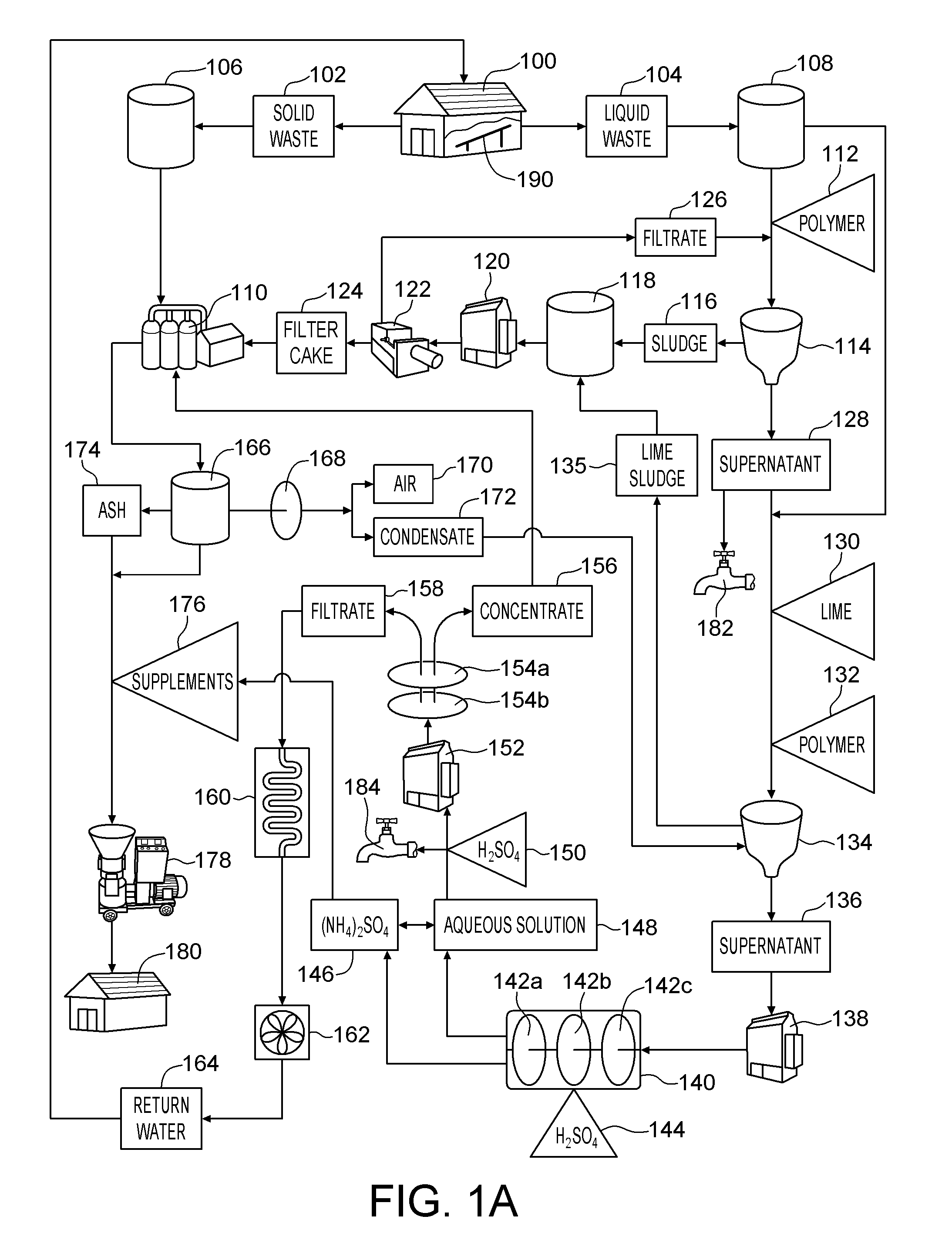
System and method for producing an organic based fertilizer and usable water from animal waste
InactiveUS20100218573A1Reduce water consumptionMinimize releaseCalcareous fertilisersBio-organic fraction processingLiquid wasteSludge
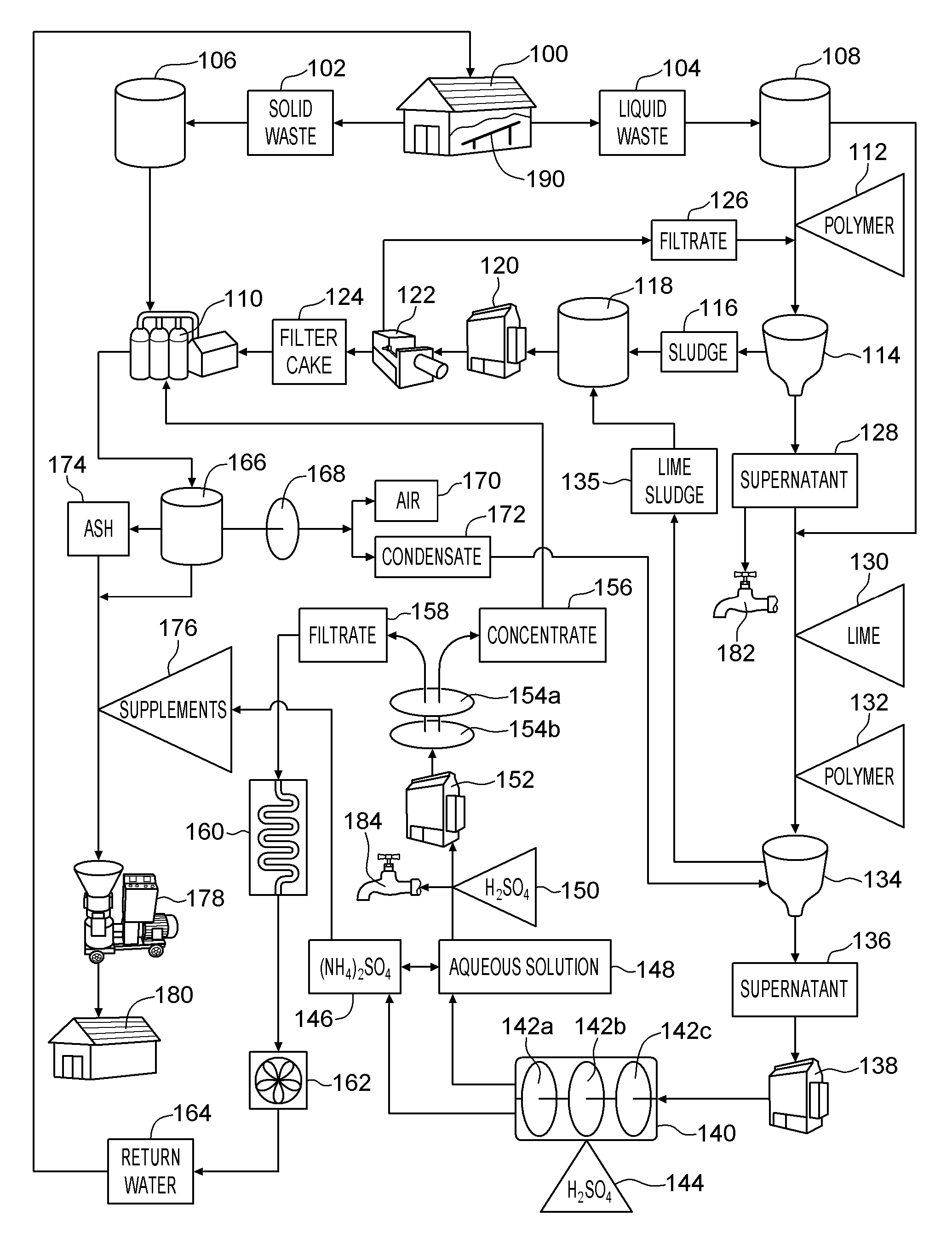
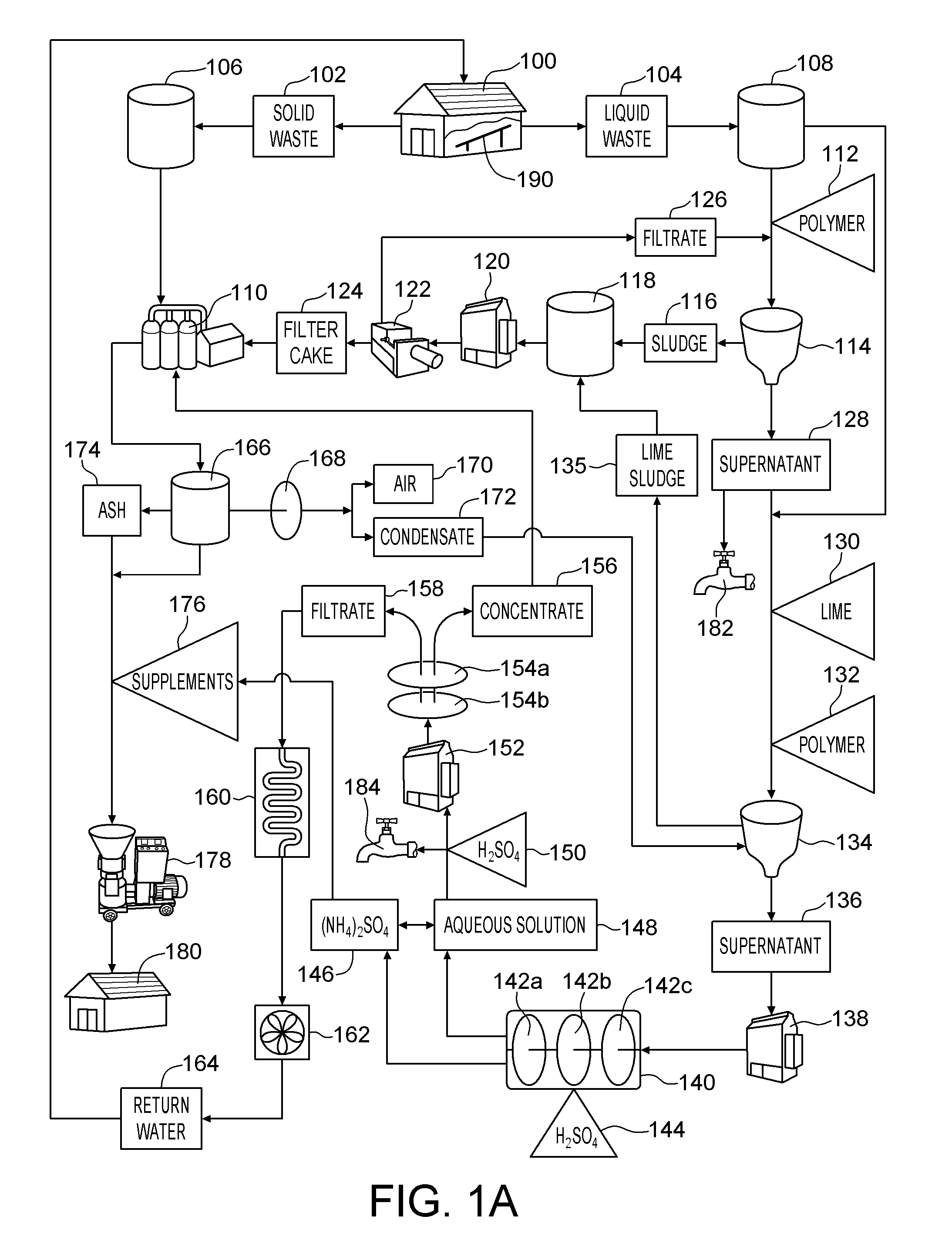
A method of producing an organic based fertilizer and usable water from animal waste includes the step of separating the animal waste into liquid waste and solid waste. The liquid waste is clarified to produce a supernatant and a sludge which is pressed into a filter cake. Ammonia is extracted from the supernatant to produce ammonium sulfate and an aqueous solution. The aqueous solution is filtered to produce a concentrate and water filtrate. The water filtrate may be used as drinking and washing water. The filter cake, ammonium sulfate, and concentrate may be used to supplement to the solid waste which is pelletized into the organic based fertilizer. In alternative embodiments a portion of the supernatant and aqueous solution may be used as a liquid fertilizer.
Owner:ATD WASTE SYST
Combination x-ray radiation and drug delivery devices and methods for inhibiting hyperplasia
InactiveUS20020165423A1Promote endothelializationReduced dosages/concentrationsStentsElectrotherapyPercent Diameter StenosisBlood vessel
The present invention provides improved devices, methods, and kits for inhibiting restenosis and hyperplasia after intravascular intervention. In particular, the present invention provides controlled drug delivery in combination with x-ray radiation delivery to selected locations within a patient's vasculature to reduce and / or inhibit restenosis and hyperplasia rates with increased efficacy. In one embodiment, the combination radiation and agent delivery catheter for inhibiting hyperplasia comprises a catheter body having a proximal end and distal end, an x-ray tube coupleable to the catheter body for applying a radiation dose to a body lumen, and means coupleable to the catheter body for releasing an agent to the body lumen.
Owner:XOFT INC
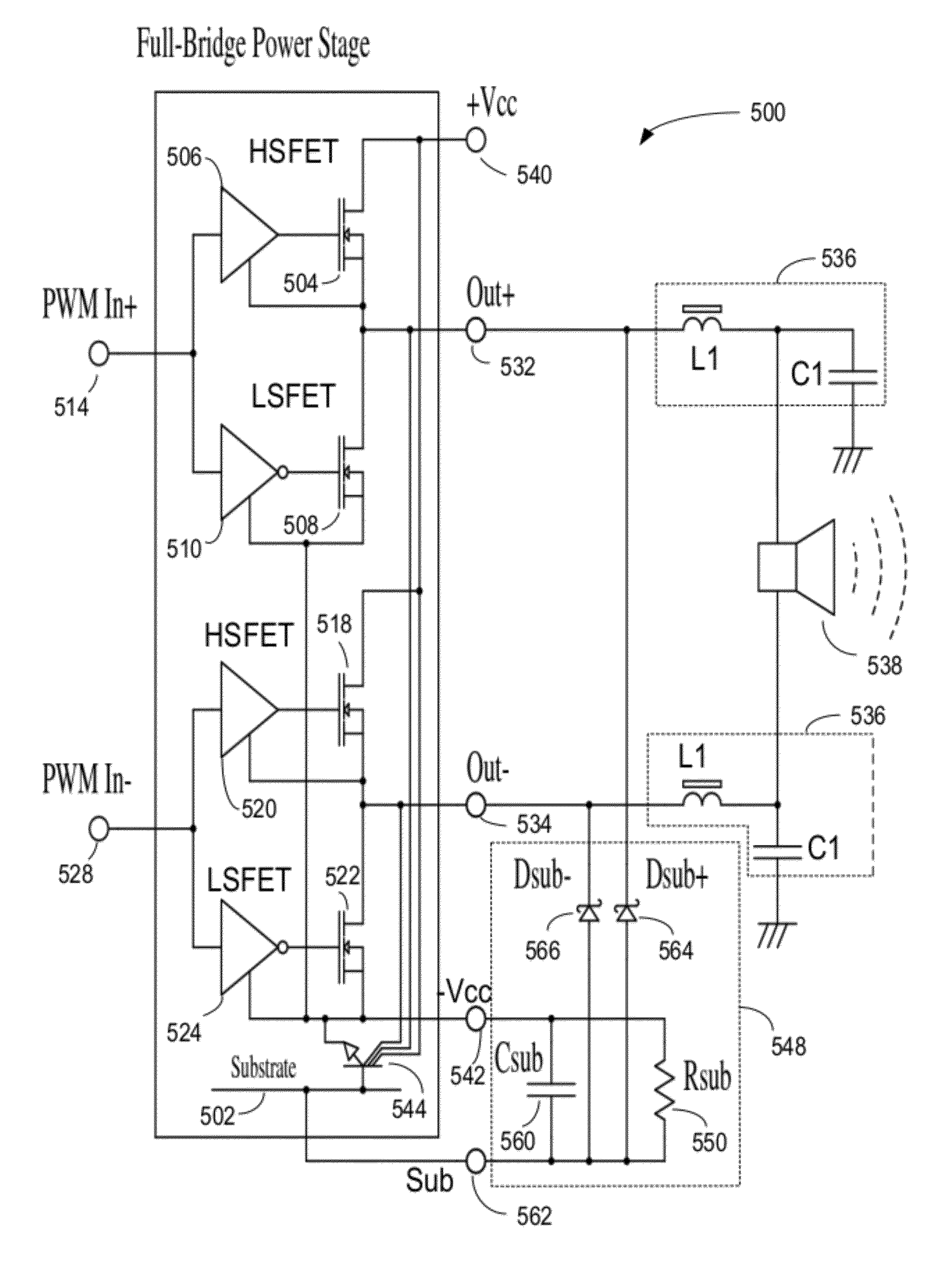
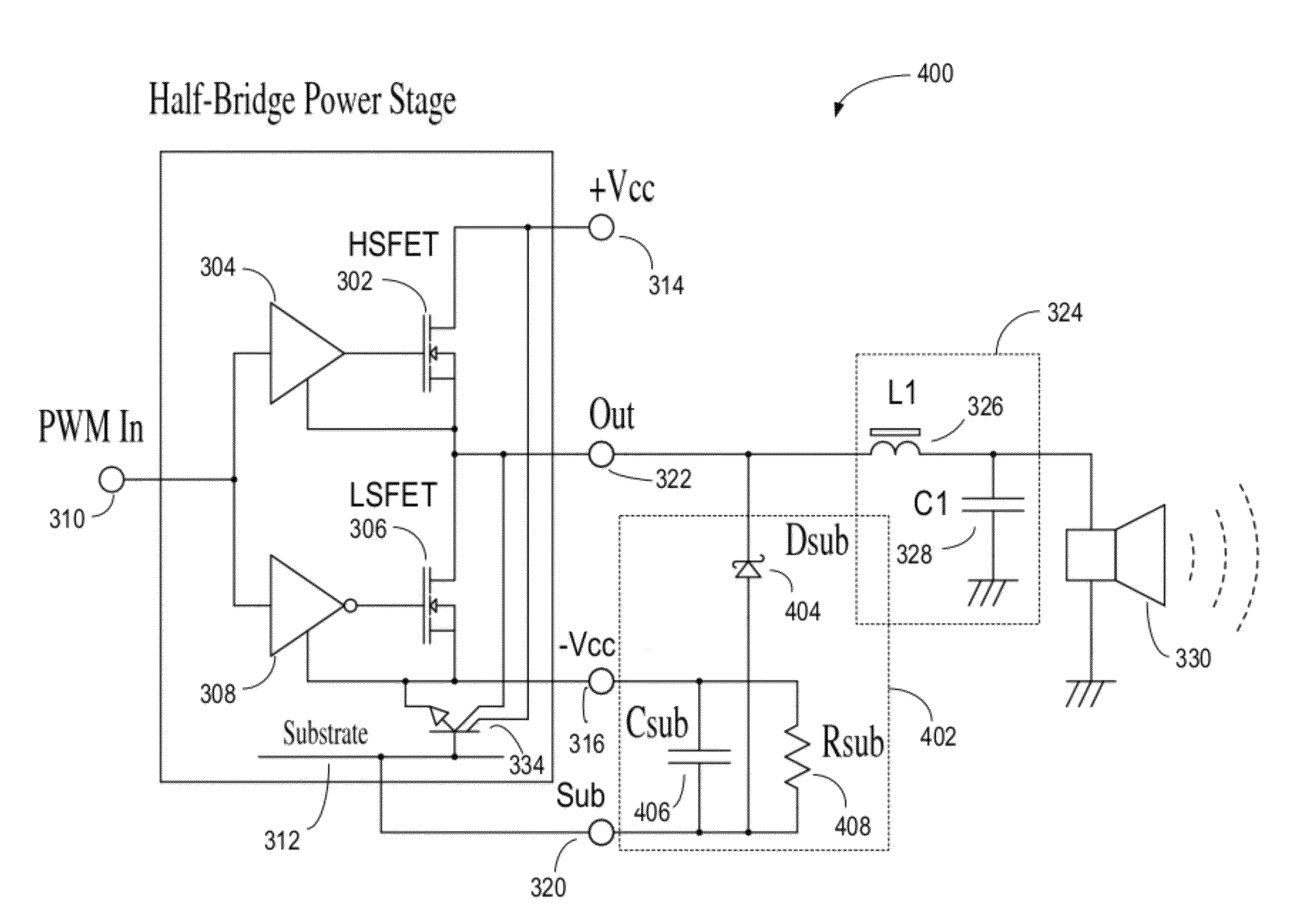
Amplifier system for a power converter
ActiveUS20120182069A1Minimize activityHigh power outputTransistorDc-dc conversionAudio power amplifierDevice form
An amplifier system for a power converter includes at least a first switching device and a second switching device formed in an integrated circuit in a substrate of a semiconductor. The first and second switching devices may be formed in a half bridge configuration and may be cooperatively switchable to generate an amplified output signal on an output node of the semiconductor. A resistor and a capacitor may be coupled in parallel between a power supply input node and a substrate node included in the semiconductor. The capacitor may be selectively charged to a de-biasing voltage during a switching cycle of the first and second switching devices to reverse bias a parasitic switching device appearing in the integrated circuit.
Owner:HARMAN INT IND INC
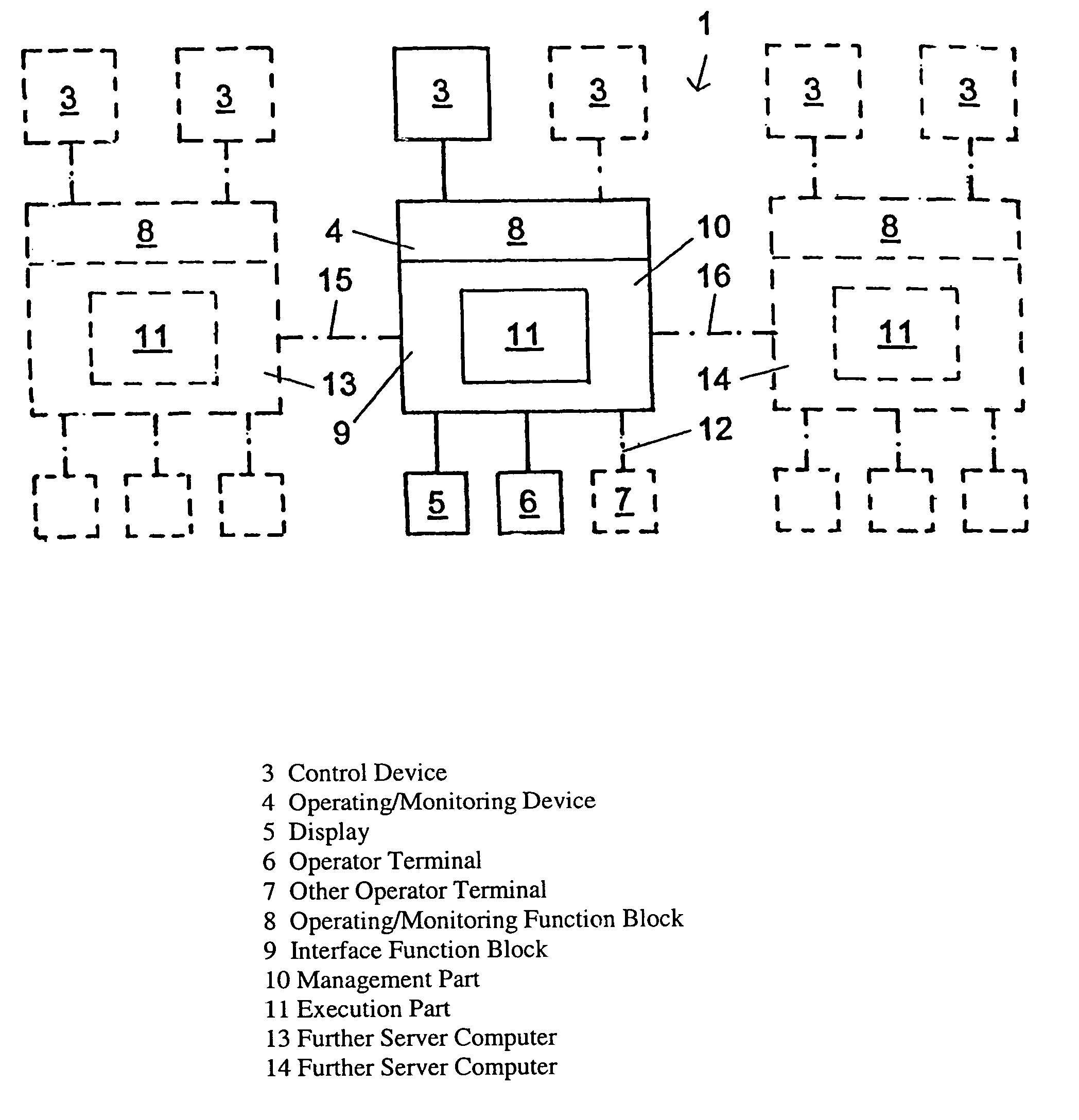
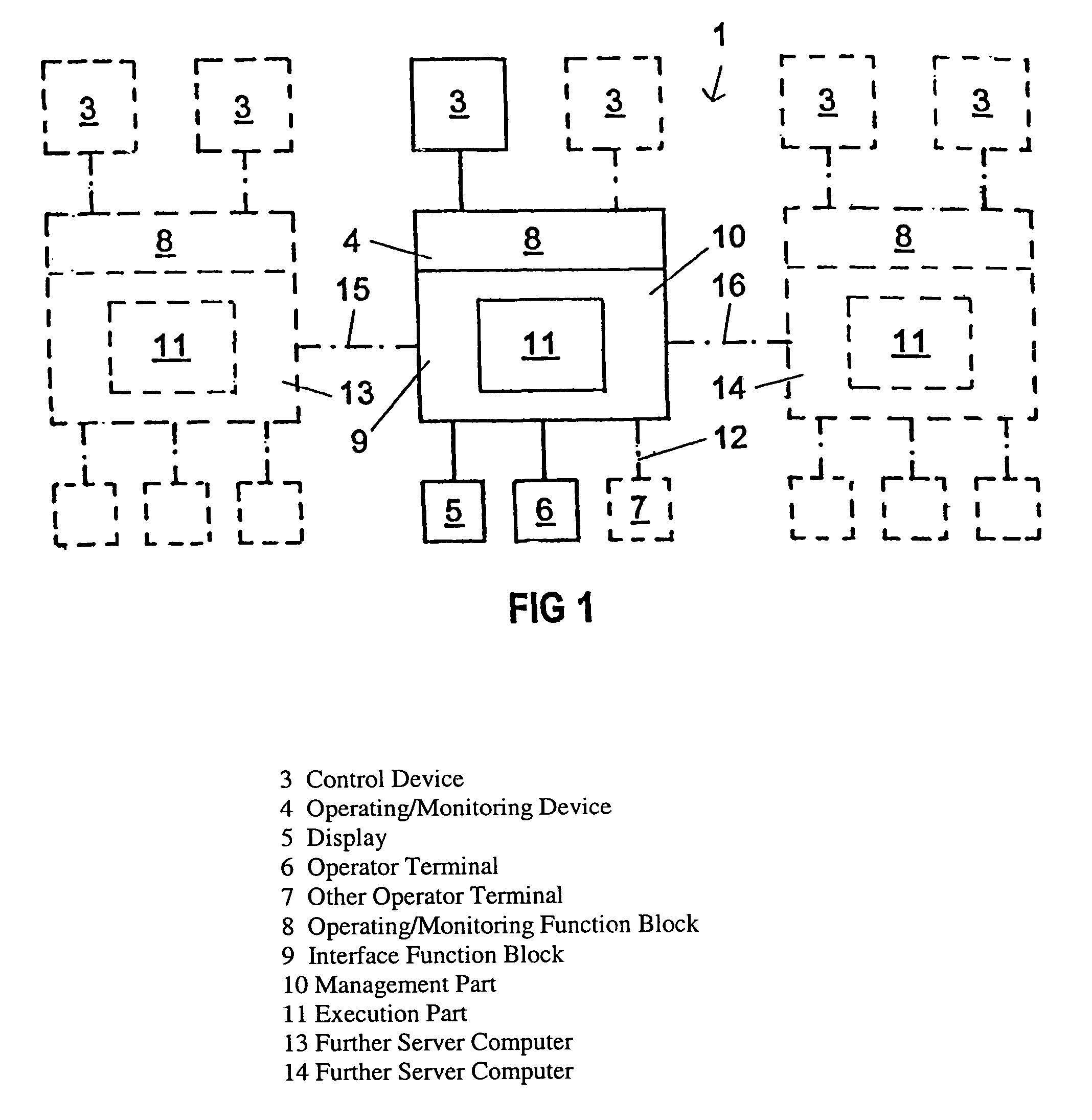
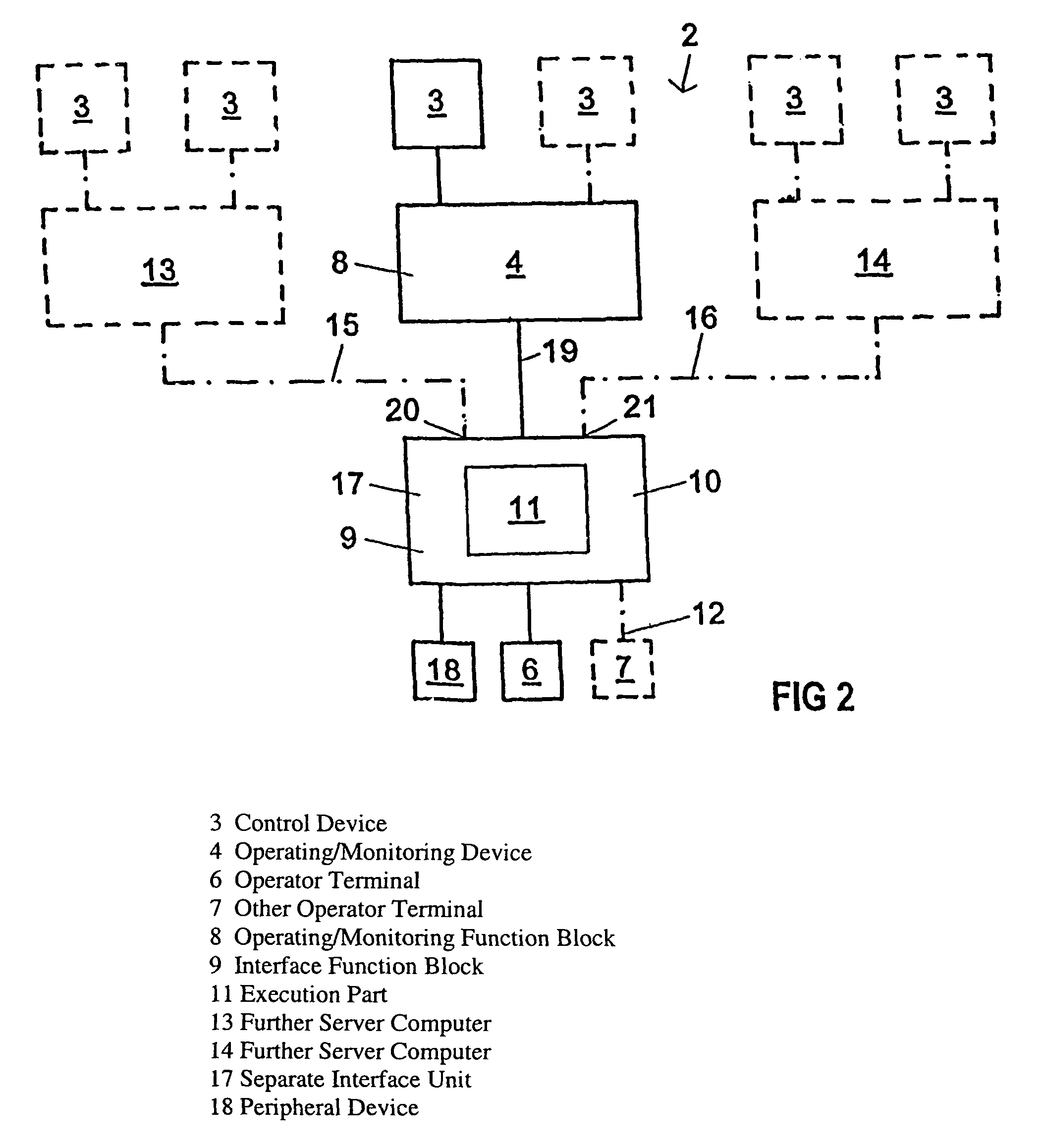
Method and assembly for operating and/or observing a device that monitors an industrial controller
InactiveUS6973356B2Easy to useAvoid confictFrequency-division multiplex detailsElectric testing/monitoringMonitor equipmentConnected operator
A system for operating / observing a monitoring device of a process controller device of / in a remote operator unit. An additional function block is provided in / on the monitoring device, which intervenes in the communication between the monitoring device and the connected operator units, at least partially takes over the functions that are to be executed by one or more of the operator units and processes the information to be displayed on the operator unit in such a way that the information can be directly displayed.
Owner:SIEMENS AG
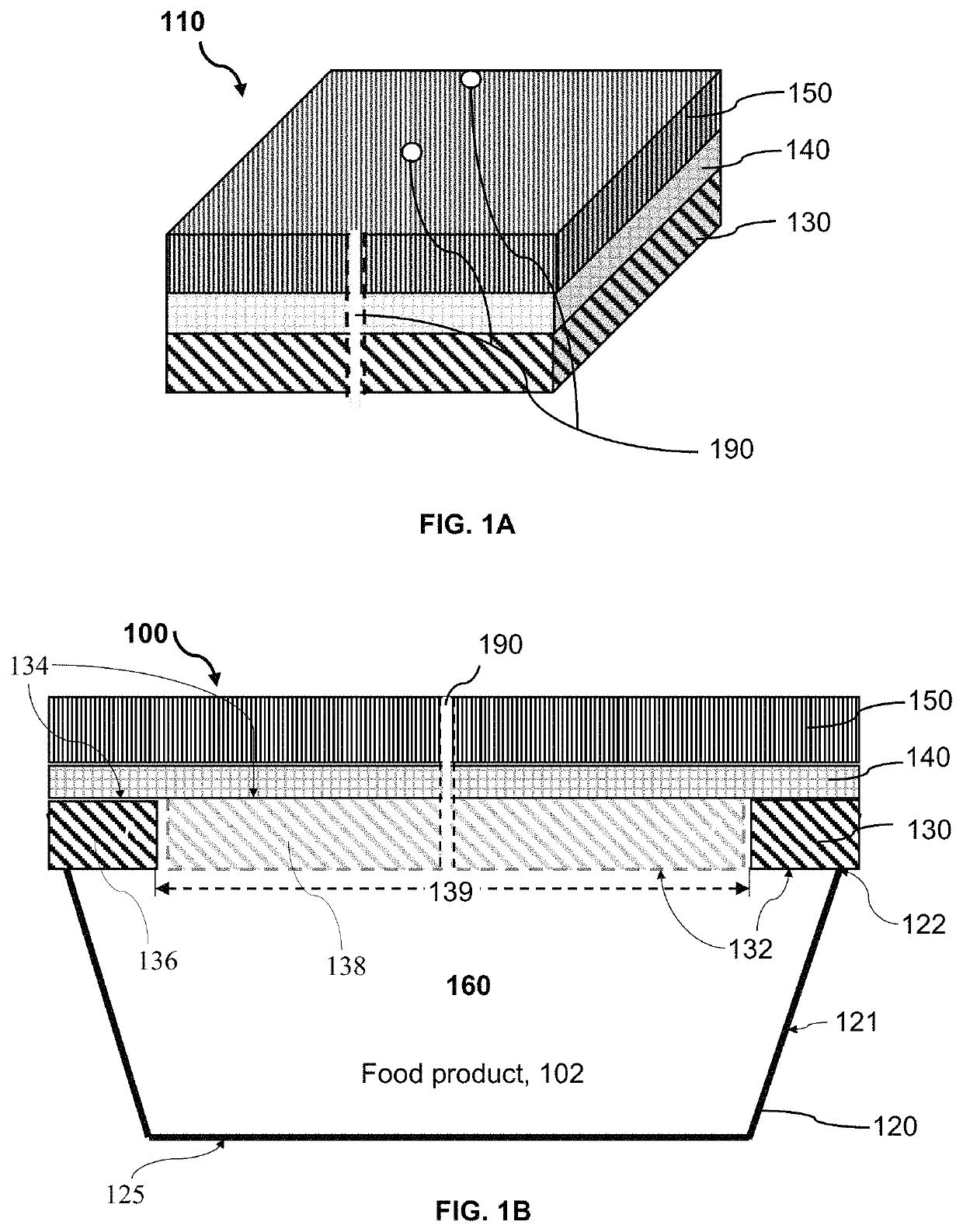
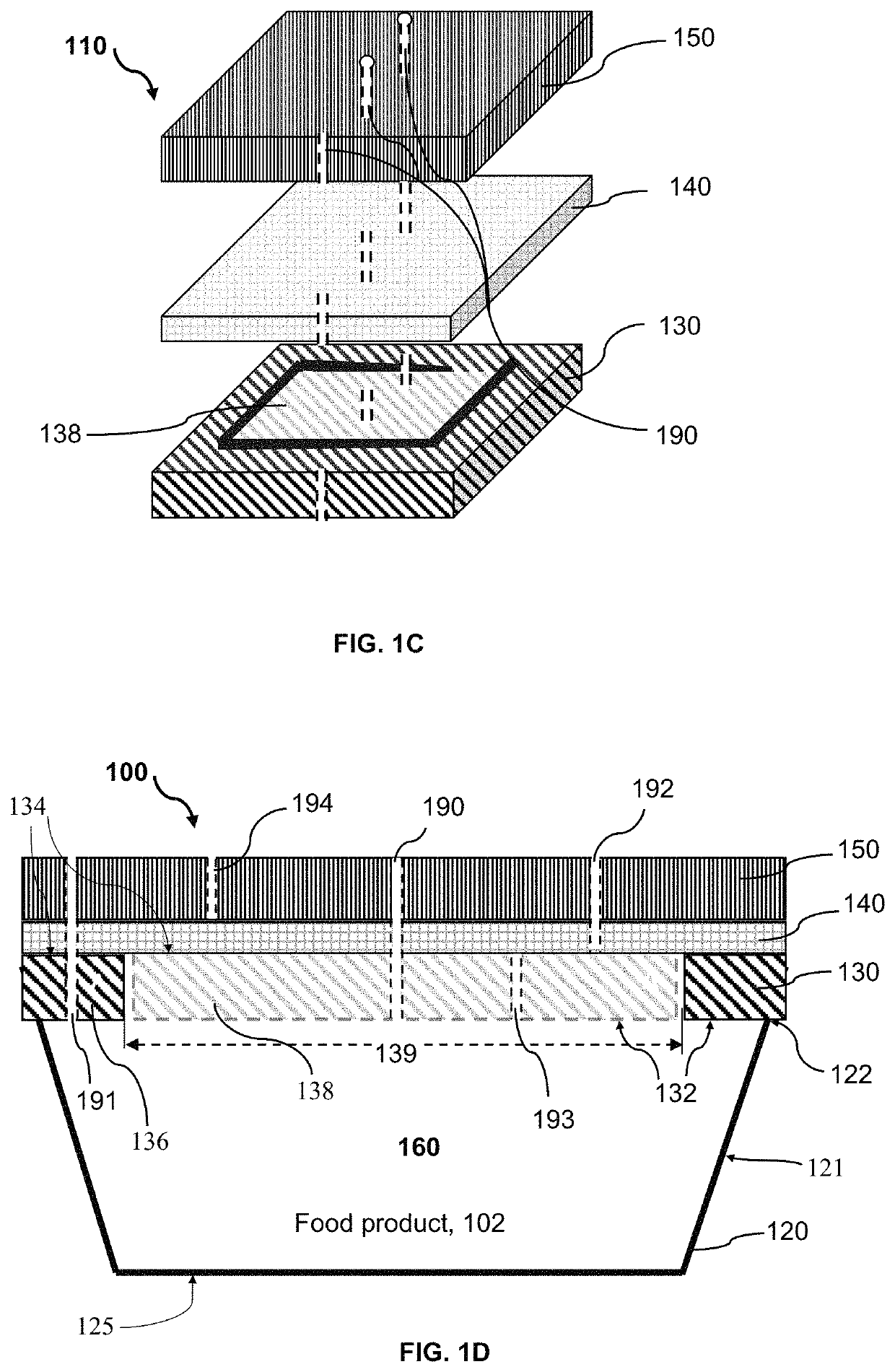
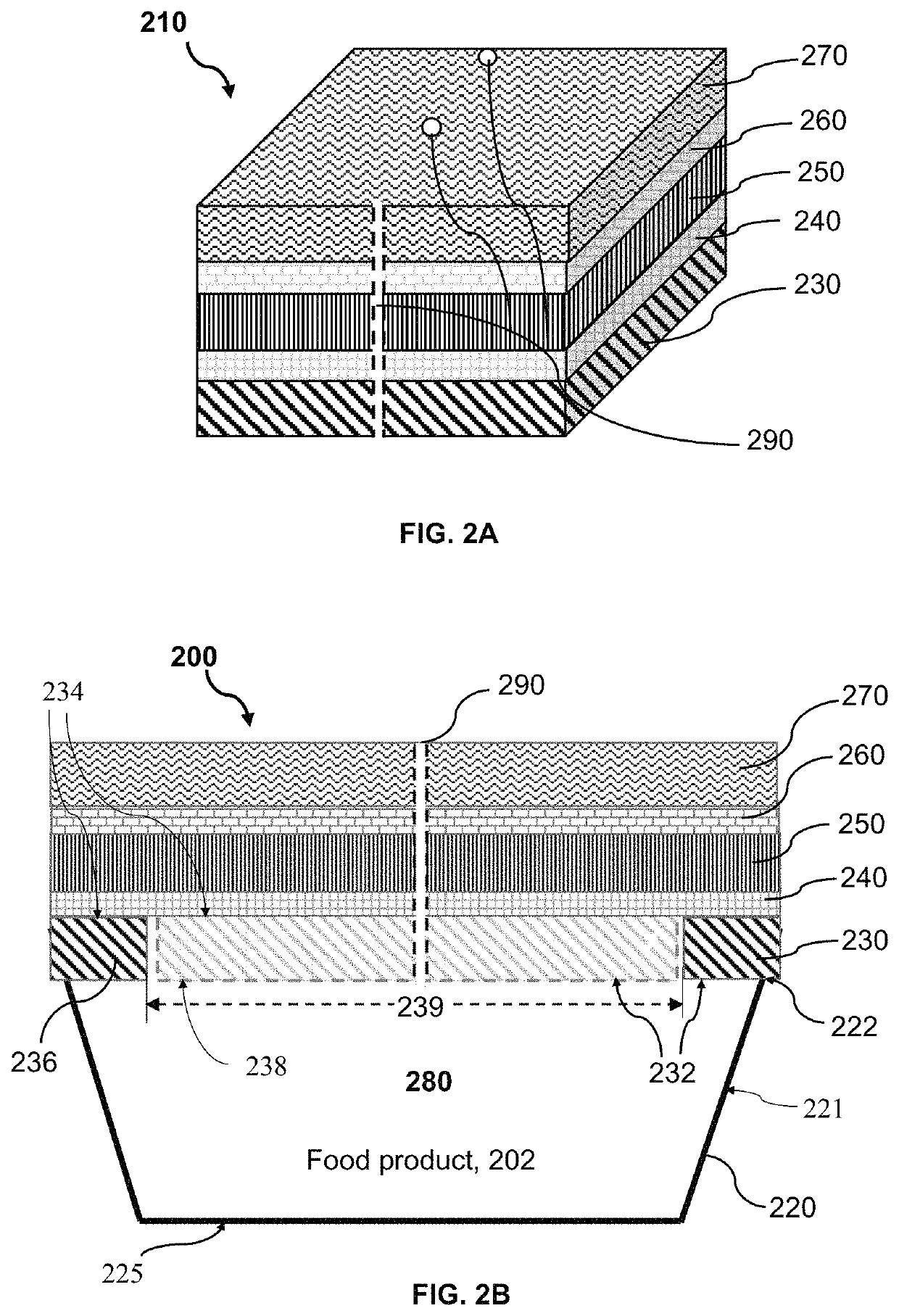
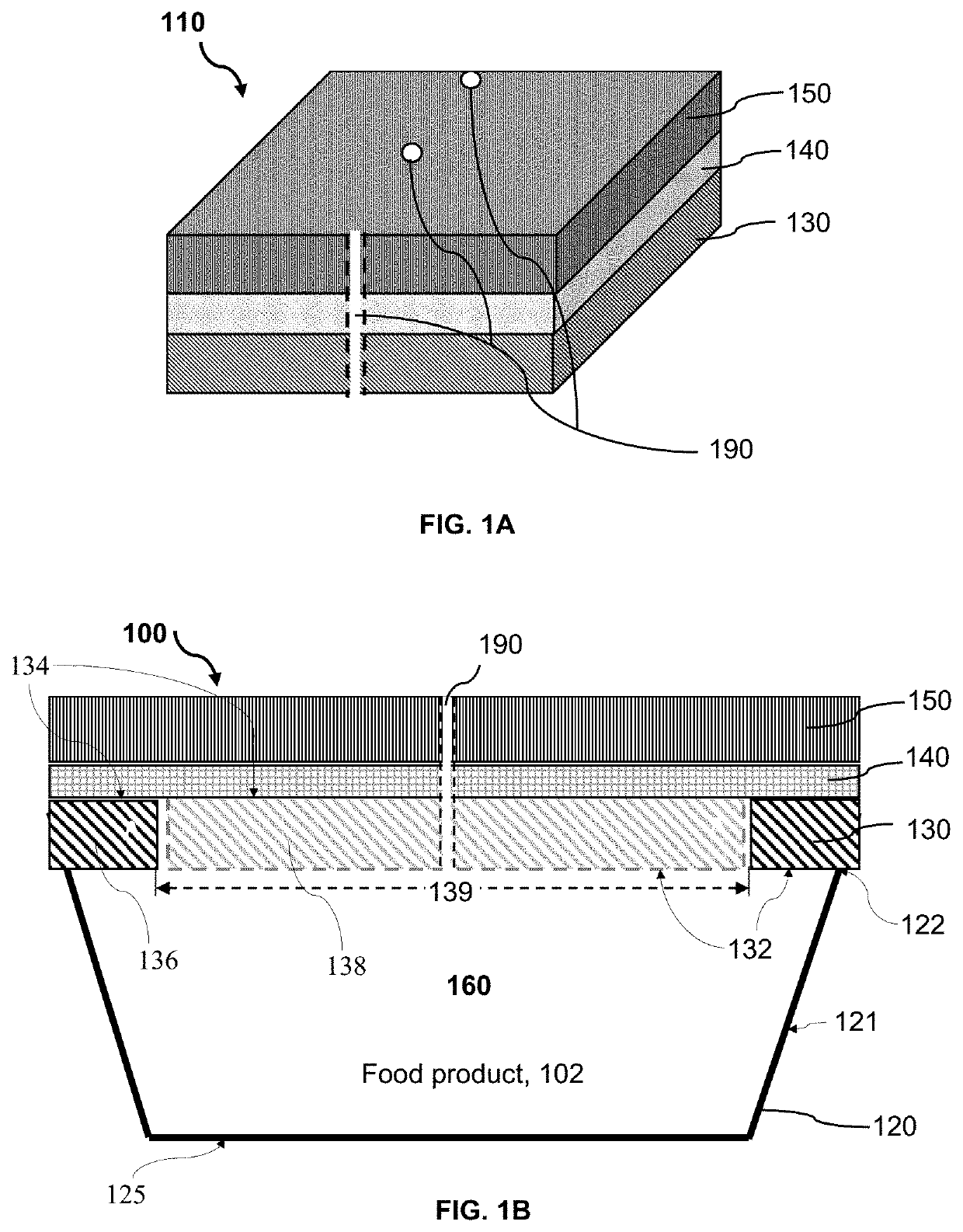
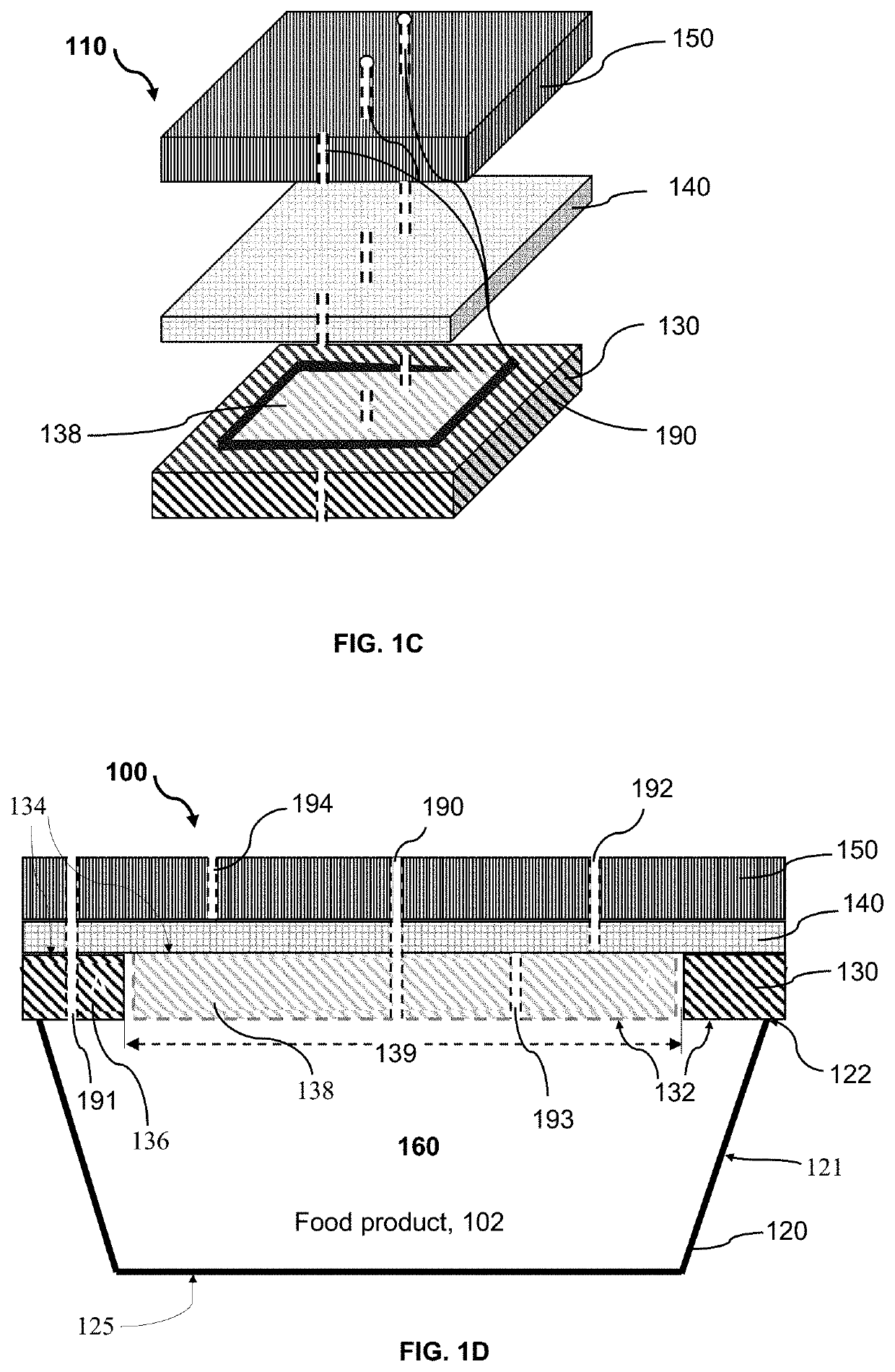
Resealable packaging device and method for packaging food product
ActiveUS10589917B1Extended shelf lifeEasy to useWrappersFruit and vegetables preservationPerishable foodProcess engineering
A packaging device incorporating a breathable peel / reseal film and enabling a preservation process for allowing for the distribution, storage and multiple servings of a food product, particularly perishable food product(s), and initiating and controlling the transmission rates, respiration rates or deterioration of the perishable food product(s) and thereby, maintaining good internal and external food quality and normal development of flavor and aroma characteristics. The packaging device includes a plurality of atmospheric control attributes that modulates or controls the atmosphere within the packaging device as the food product(s) respire in order to promote the extended shelf-life of the food product and the maintenance of the quality and desirable marketable characteristics of the food product. The atmospheric control attributes can include perforations that may be positioned in breathable peel / reseal film portion of the package to allow the product respiration for multiple servings without substantially altering the shelf life extension properties of the packaging device.
Owner:MIR NAZIR
Amplifier system for a power converter
ActiveUS8283979B2Minimize activityHigh power outputTransistorSolid-state devicesAudio power amplifierDevice form
Owner:HARMAN INT IND INC
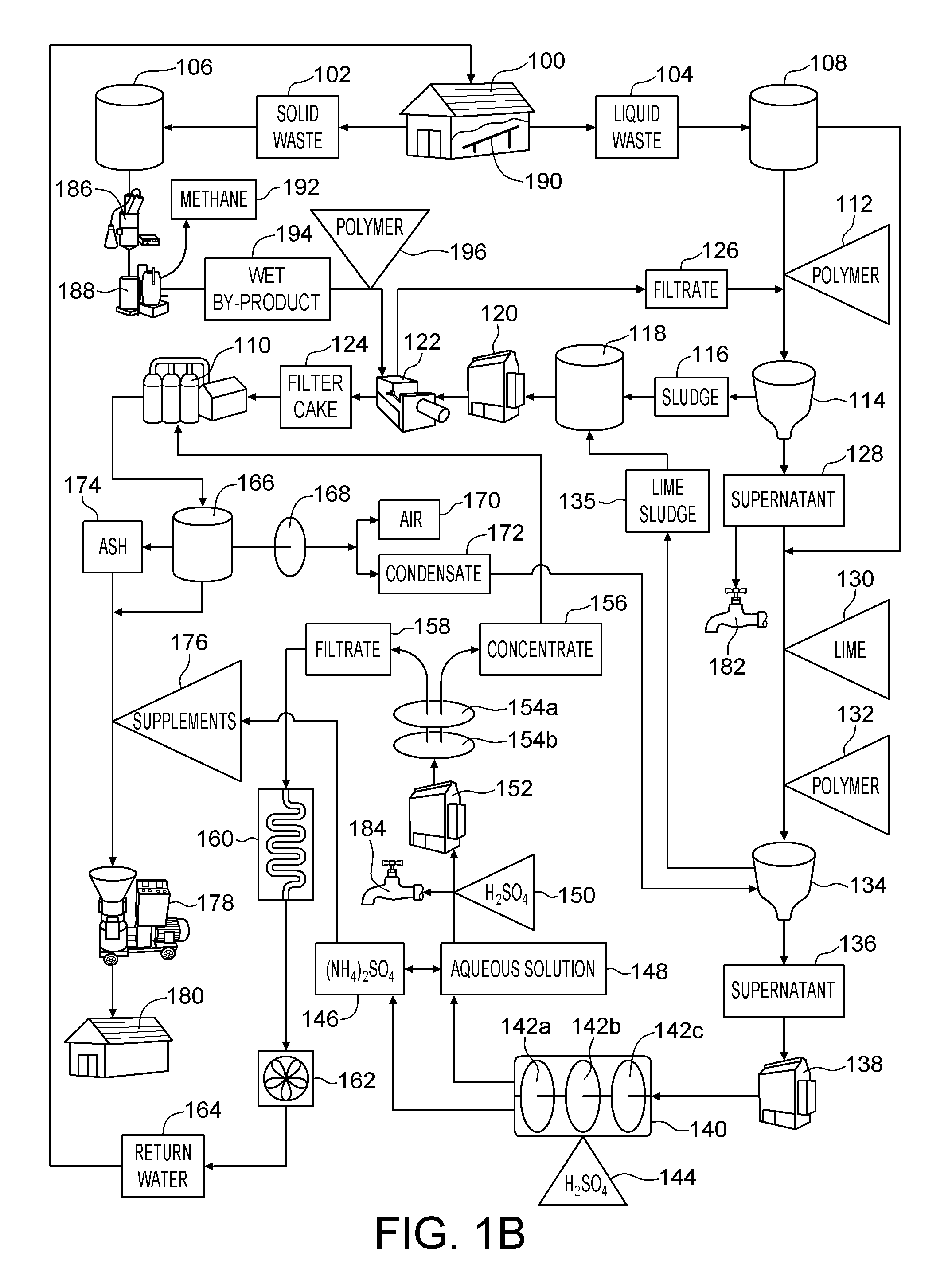
System and method for producing methane, an organic based fertilizer and usable water from animal waste
InactiveUS8282827B2Reduce water consumptionMinimize releaseCalcareous fertilisersBio-organic fraction processingLiquid wasteOrganic base
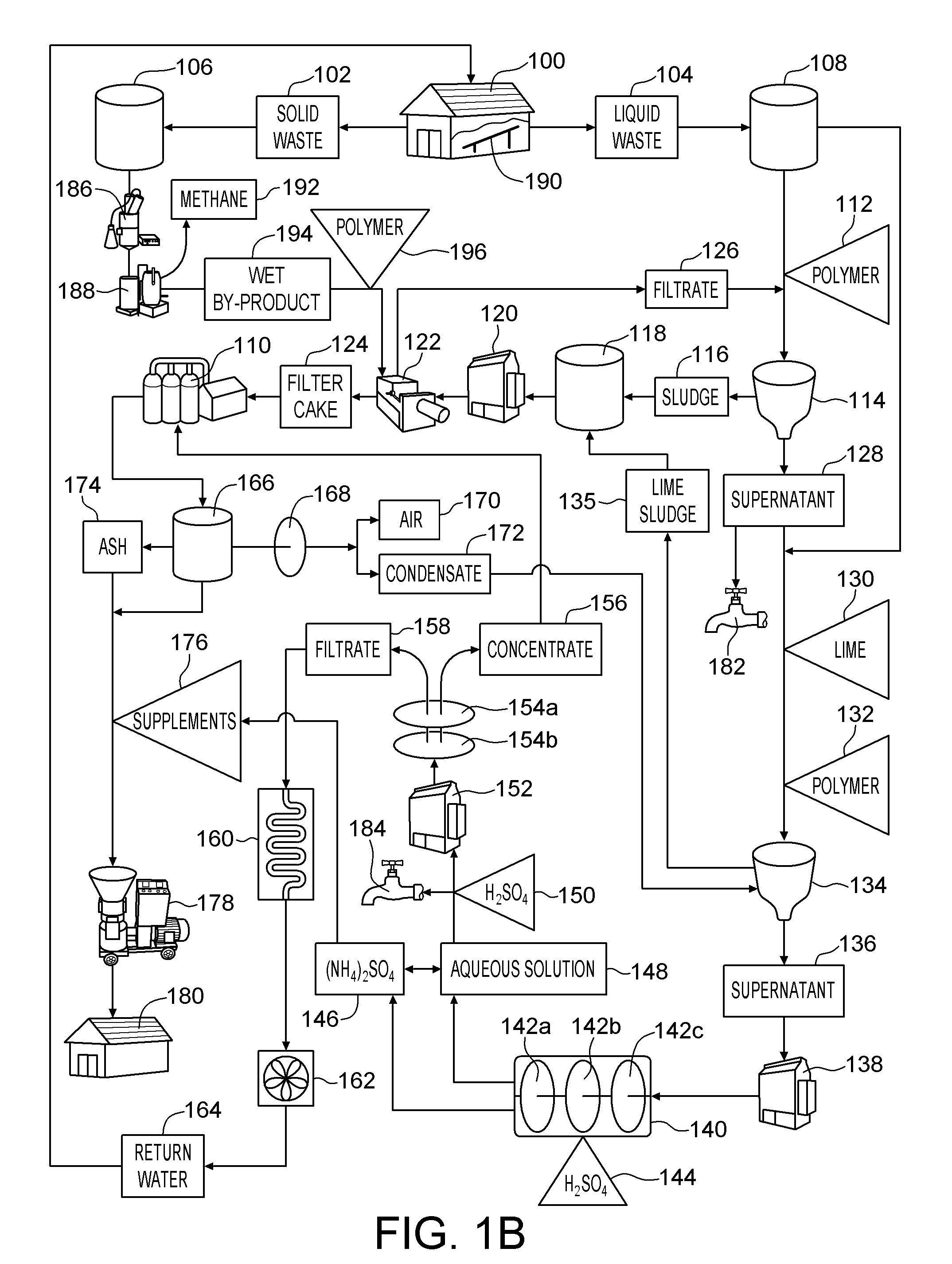
A method of producing methane, an organic based fertilizer and usable water from animal waste includes the step of separating the animal waste into liquid waste and solid waste. The solid waste is subjected to anaerobic digestion to produce methane and a wet by-product. The wet by-product is pressed to into a filter cake which is pelletized into the organic based fertilizer. The liquid waste is clarified to produce a supernatant and a sludge which is pressed into a filter cake together with the wet by-product. Ammonia is extracted from the supernatant to produce ammonium sulfate and an aqueous solution. The aqueous solution is filtered to produce a concentrate and water filtrate. The water filtrate may be used as drinking or washing water. The ammonium sulfate and concentrate may be used to supplement to the solid waste which is pelletized into the organic based fertilizer. In alternative embodiments a portion of the supernatant and aqueous solution may be used as a liquid fertilizer.
Owner:ATD WASTE SYST
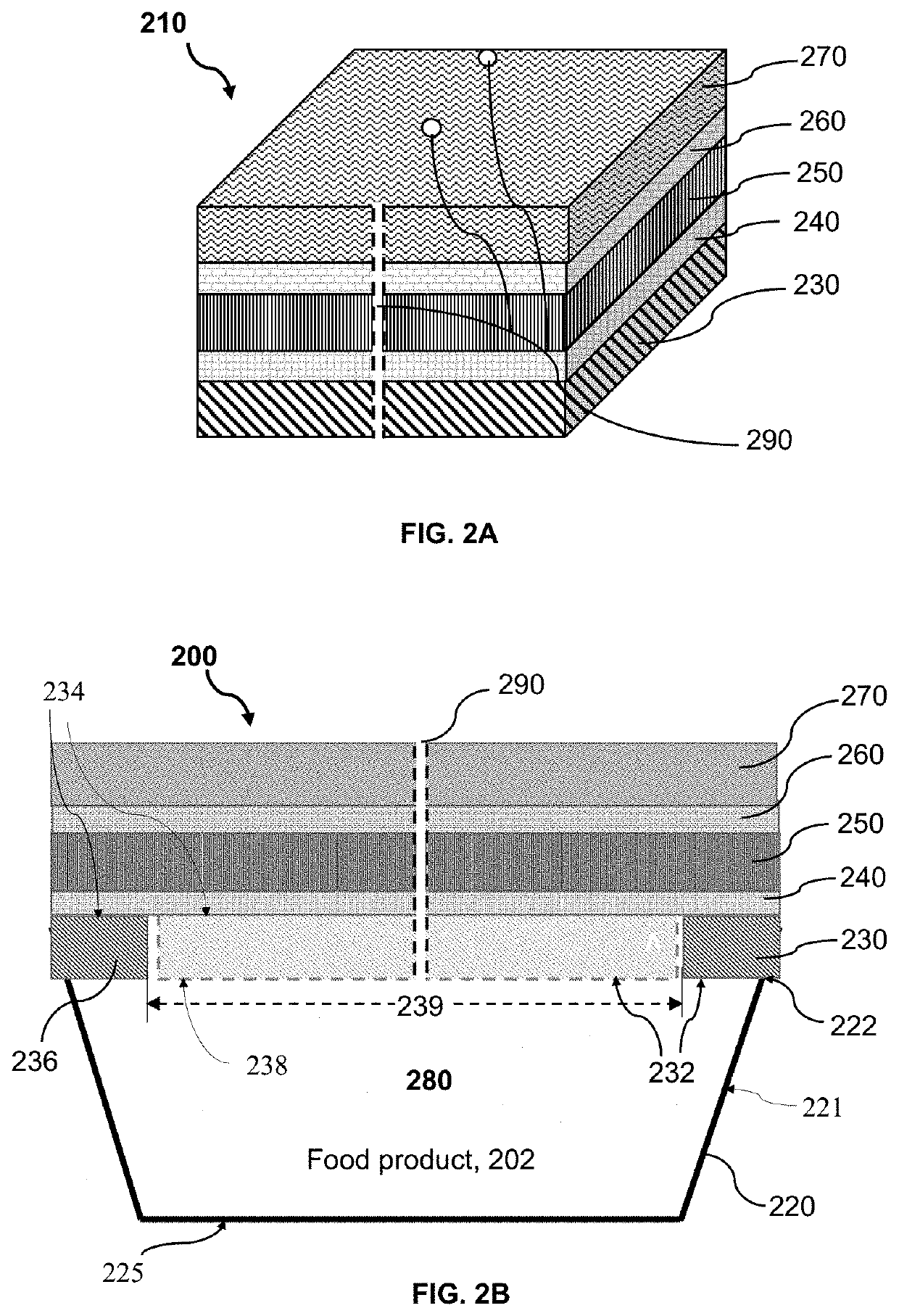
Resealable packaging device and method for packaging food product
ActiveUS10836551B1Extended shelf lifeIncrease usageFruit and vegetables preservationWrappersFood qualityPerishable food
A packaging device incorporating a breathable peel / reseal film and enabling a preservation process for allowing for the distribution, storage and multiple servings of a food product, particularly perishable food product(s), and initiating and controlling the transmission rates, respiration rates or deterioration of the perishable food product(s) and thereby, maintaining good internal and external food quality and normal development of flavor and aroma characteristics. The packaging device includes a plurality of atmospheric control attributes that modulates or controls the atmosphere within the packaging device as the food product(s) respire in order to promote the extended shelf-life of the food product and the maintenance of the quality and desirable marketable characteristics of the food product. The atmospheric control attributes can include perforations that may be positioned in breathable peel / reseal film portion of the package to allow the product respiration for multiple servings without substantially altering the shelf life extension properties of the packaging device.
Owner:MIR NAZIR
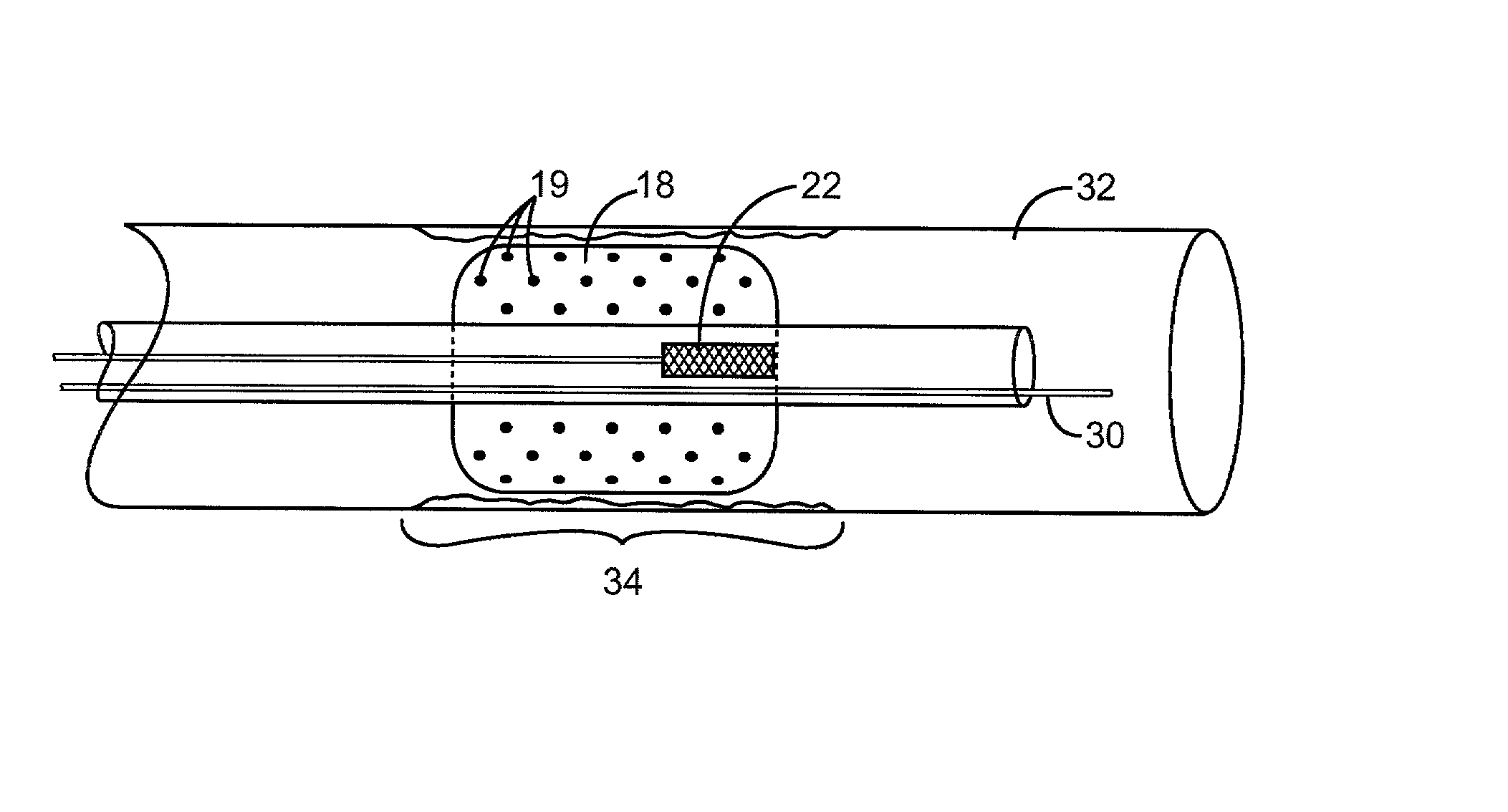
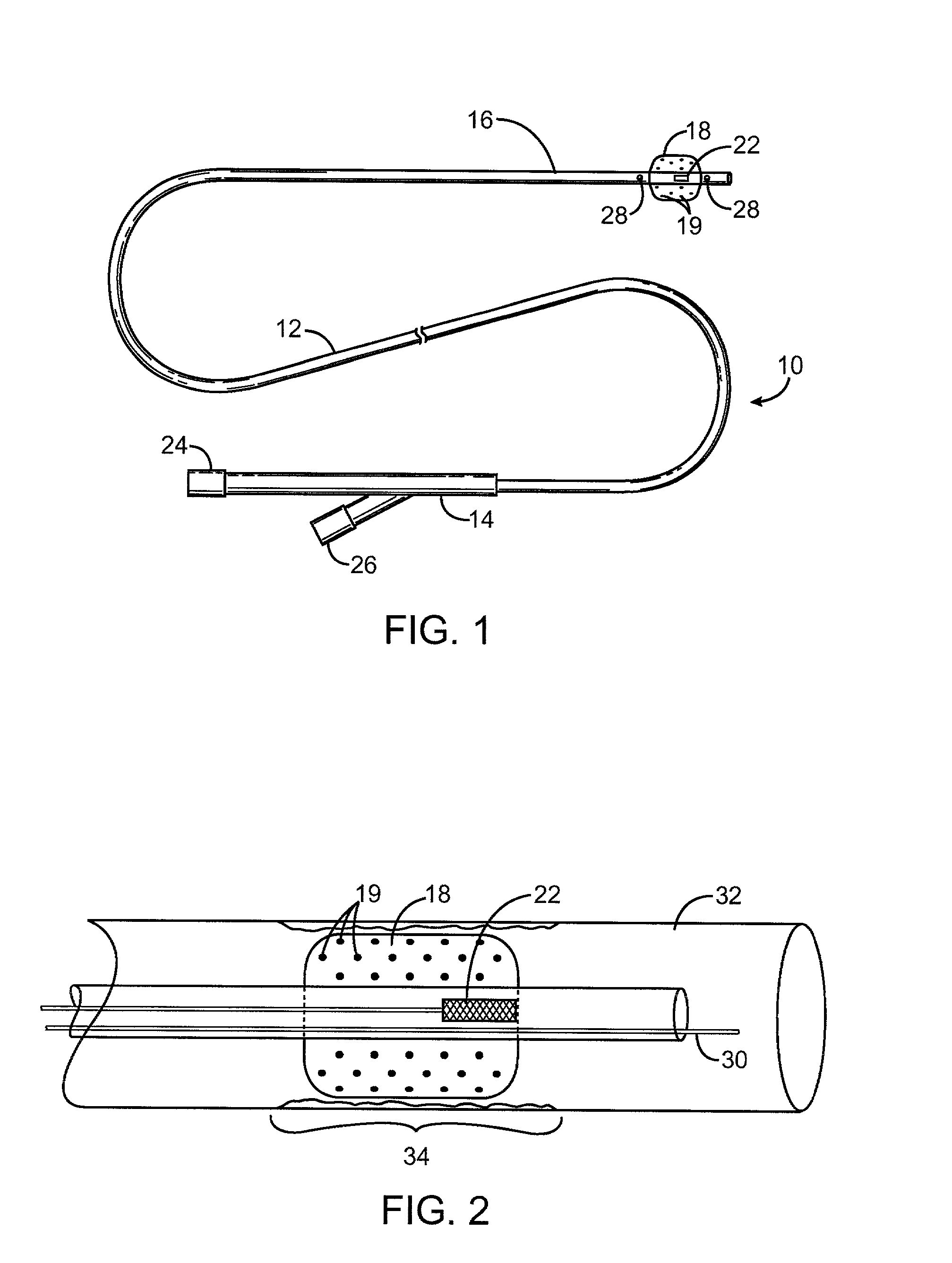
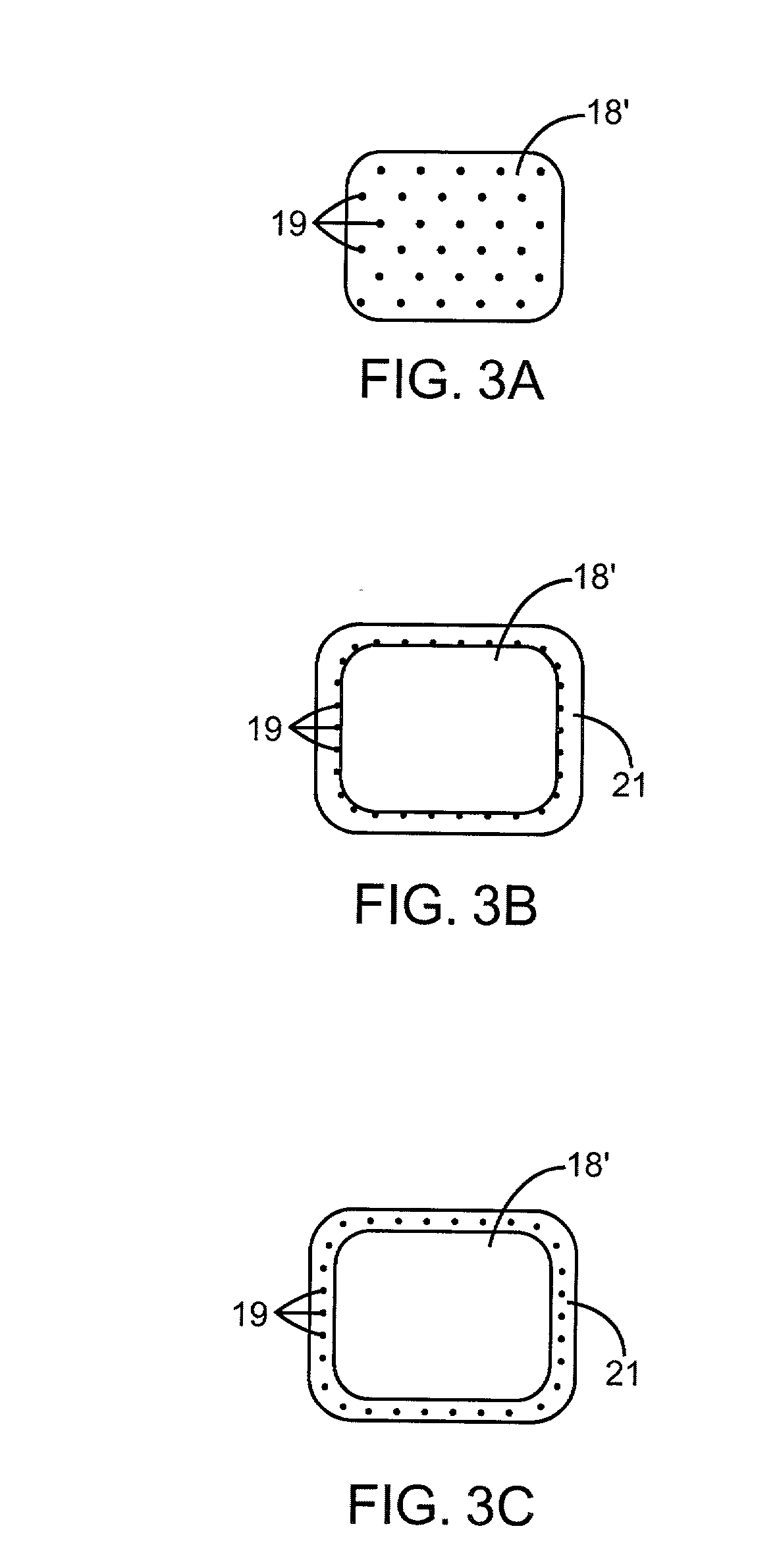
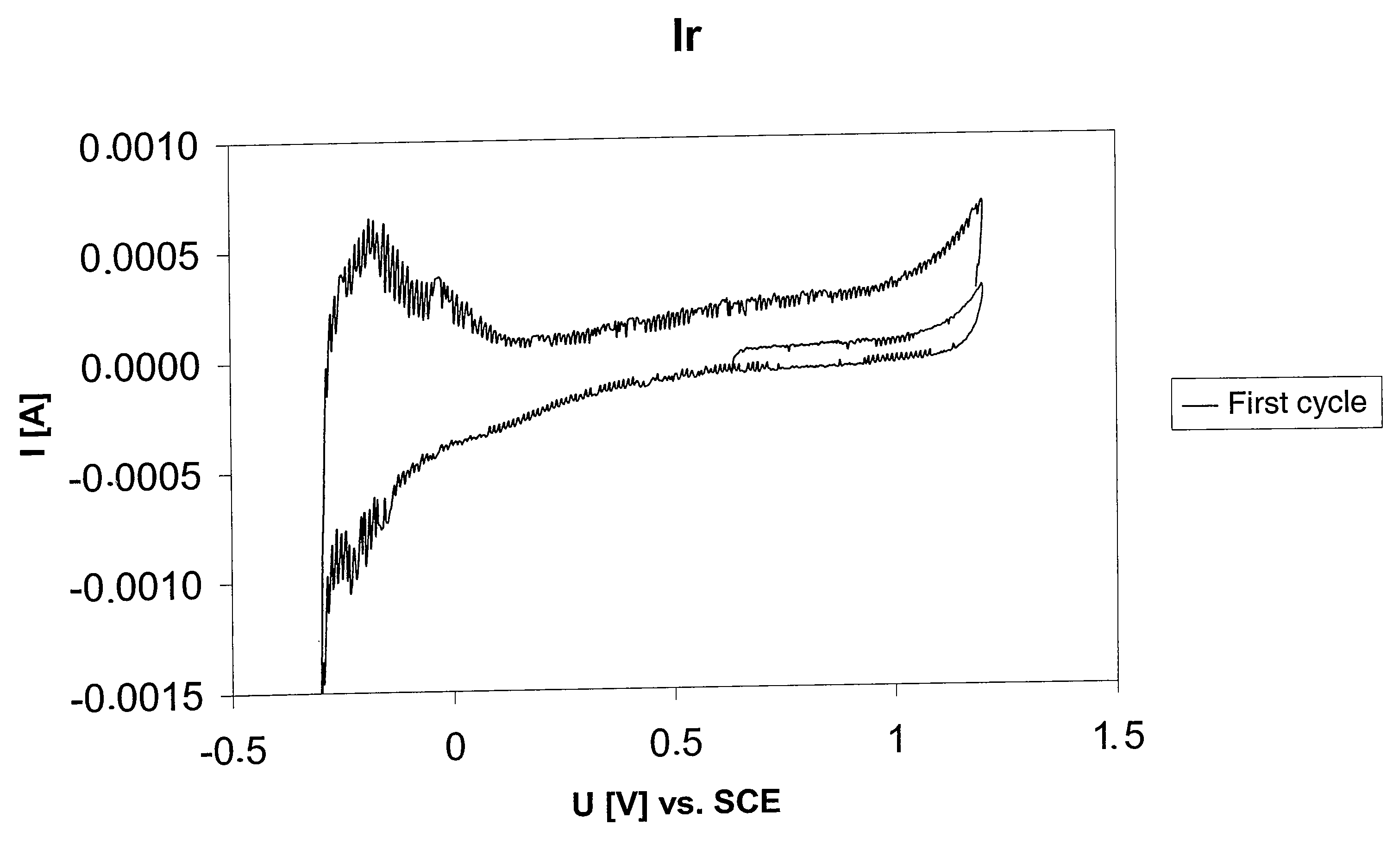
Stimulation electrode with porous coating
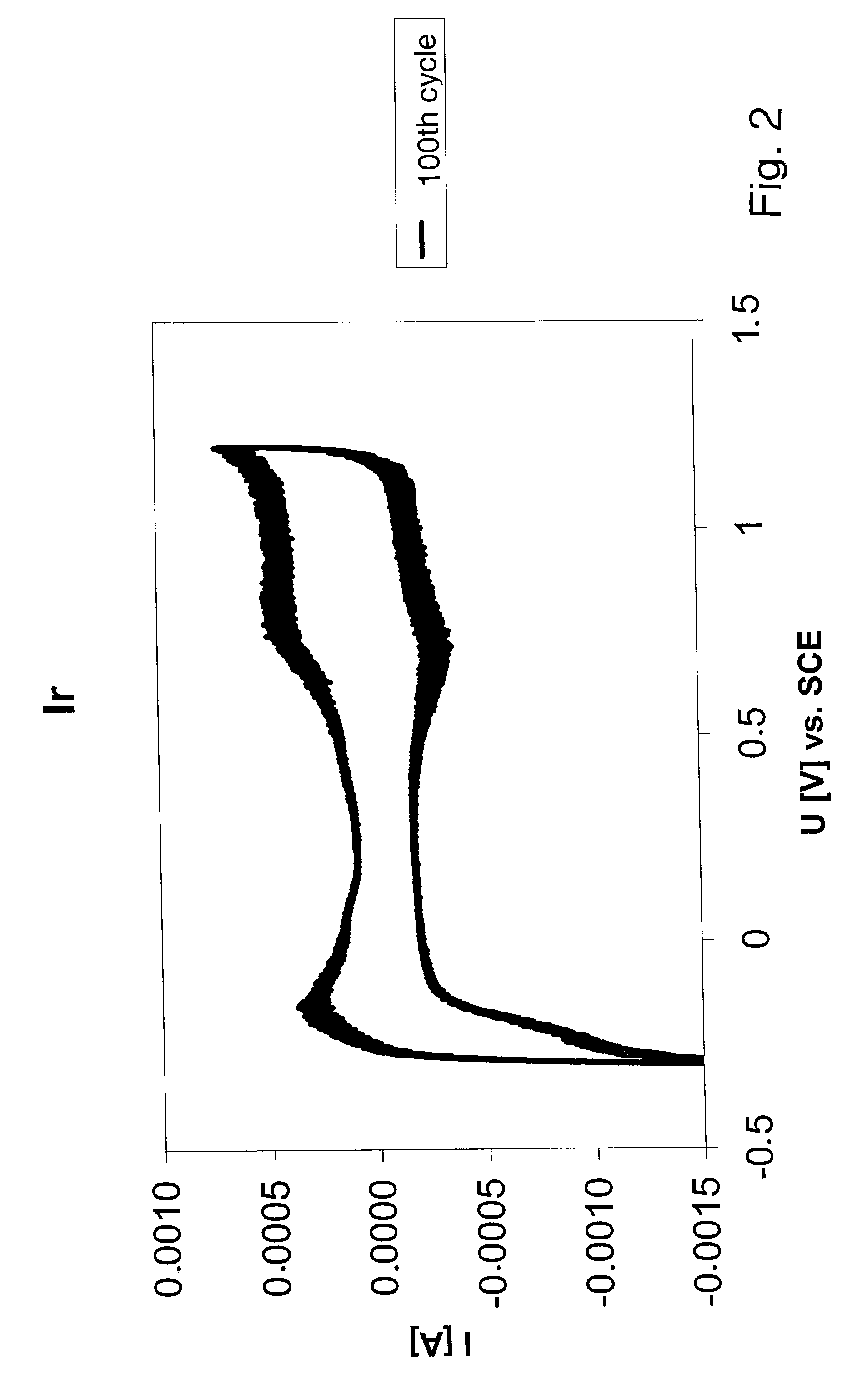
ActiveUS7603169B2Increase capacitanceMinimizing their catalytic activityTransvascular endocardial electrodesCatheterPorous coatingPlatinum
An electrode for medical applications is provided with a PtIr coating which is at least partly porous. The coating contains more than 20% iridium by weight and at least 100 ppm Pt. The coated areas of the electrode exhibit an electrochemical capacitance of more than 5 mF / cm2 in physiological saline solution at 37° C. and a measurement frequency of 100 mHz. A sputter process is suitable for this purpose, in which a porous platinum-iridium layer is deposited on the electrode by simultaneously sputtering at least one iridium target and at least one platinum target.
Owner:HERAEUS PRECIOUS METALS GMBH & CO KG
Enhanced security fence and method of construction and installation
An enhanced security fence for use in high security situations is provided. The fence is made of high strength materials that are preferably welded together in a convenient location and sent as prefabricated sections to the installation location to form an all welded bracket-less perimeter barrier fence system. Posts with section hangers are provided and installed at a perimeter, and the prefabricated panels are quickly and securely attached to the posts. The panels can be friction fit to the posts and, if desired welded thereto. The invention includes a method of creating an enhanced security fence, that includes prefabrication of panels and rapid fitting and securing the panels to posts to more quickly create a secure perimeter in places having difficult environments.
Owner:IND FENCE INC
System and method for producing methane, an organic based fertilizer and usable water from animal waste
InactiveUS20100219124A1Reduce water consumptionMinimize releaseCalcareous fertilisersBio-organic fraction processingLiquid wasteOrganic base
A method of producing methane, an organic based fertilizer and usable water from animal waste includes the step of separating the animal waste into liquid waste and solid waste. The solid waste is subjected to anaerobic digestion to produce methane and a wet by-product. The wet by-product is pressed to into a filter cake which is pelletized into the organic based fertilizer. The liquid waste is clarified to produce a supernatant and a sludge which is pressed into a filter cake together with the wet by-product. Ammonia is extracted from the supernatant to produce ammonium sulfate and an aqueous solution. The aqueous solution is filtered to produce a concentrate and water filtrate. The water filtrate may be used as drinking or washing water. The ammonium sulfate and concentrate may be used to supplement to the solid waste which is pelletized into the organic based fertilizer. In alternative embodiments a portion of the supernatant and aqueous solution may be used as a liquid fertilizer.
Owner:ATD WASTE SYST
Scan compression architecture with bypassable scan chains for low test mode power
ActiveUS8856601B2Minimize activityMinimize power consumptionElectronic circuit testingOptimal testIntegrated circuit layout
This invention permits selectively bypasses serial scan chains. Constant or low toggle data is directed to the bypassed serial scan chain, thus reducing power consumption. The number and identity of serial scan chains bypassed during a particular test can be changed dynamically dependent upon the semiconductor process variations of a particular integrated circuit. This enables an optimal test to be preformed for integrated circuits having differing semiconductor process variations.
Owner:TEXAS INSTR INC
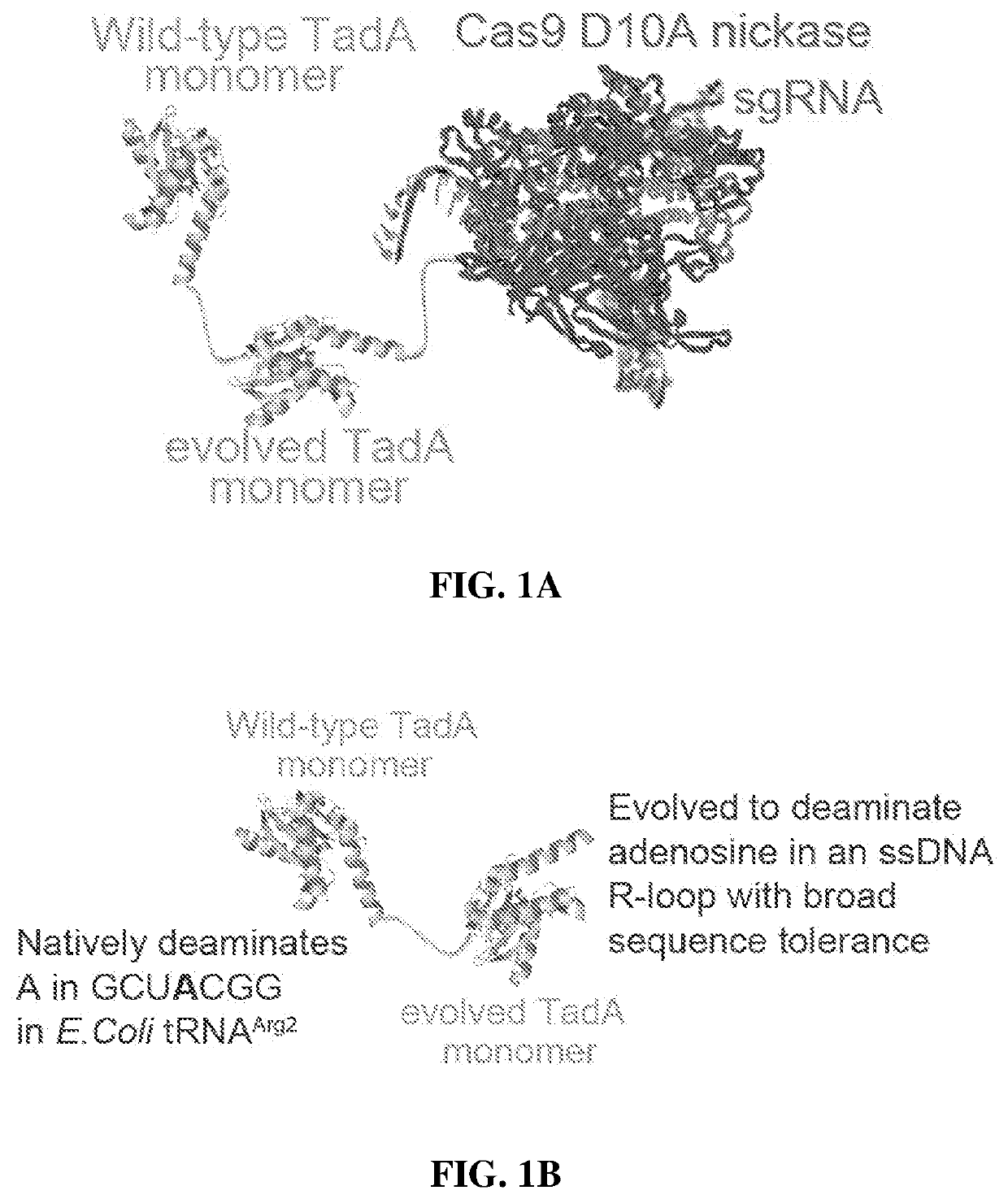
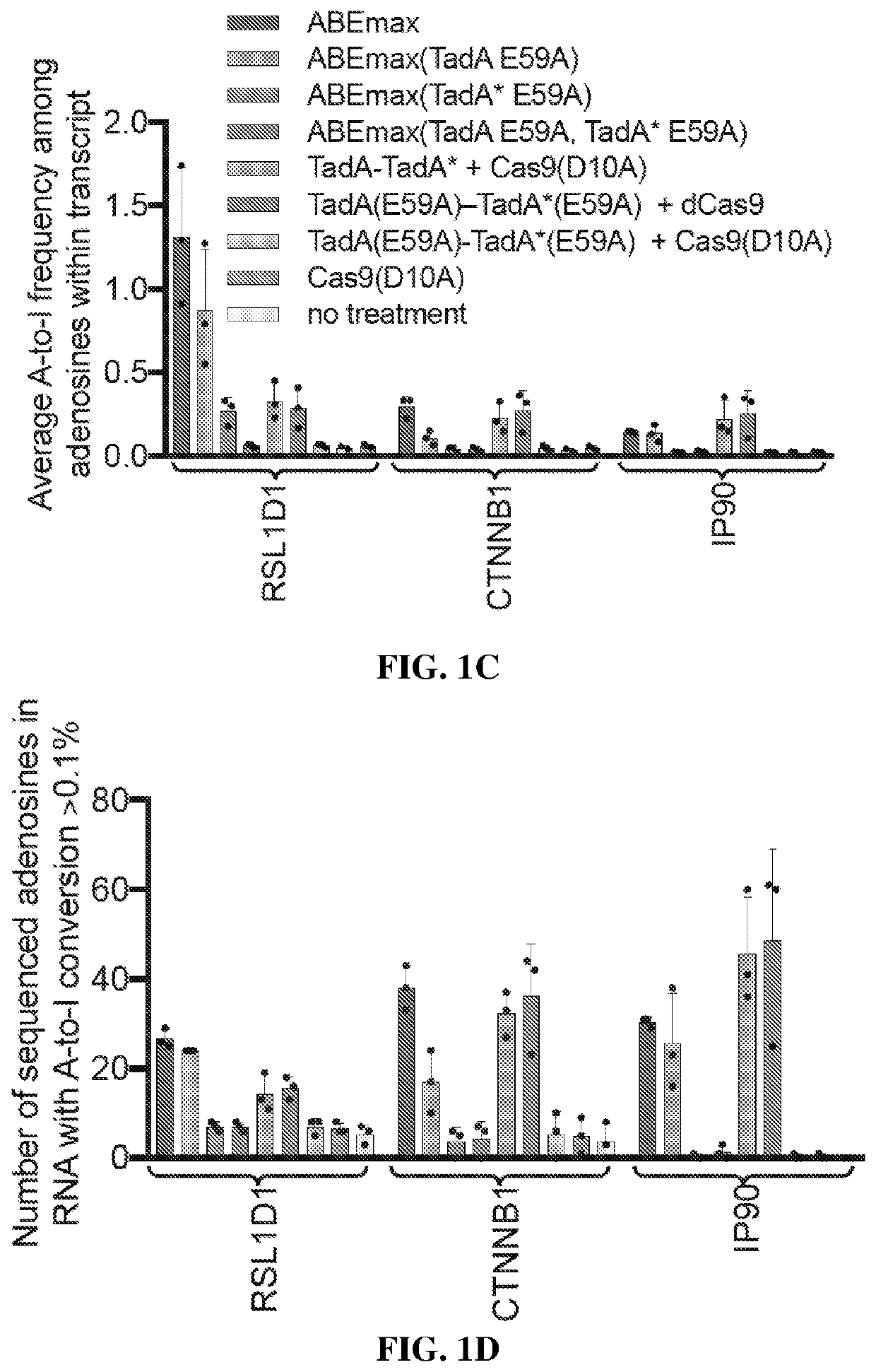
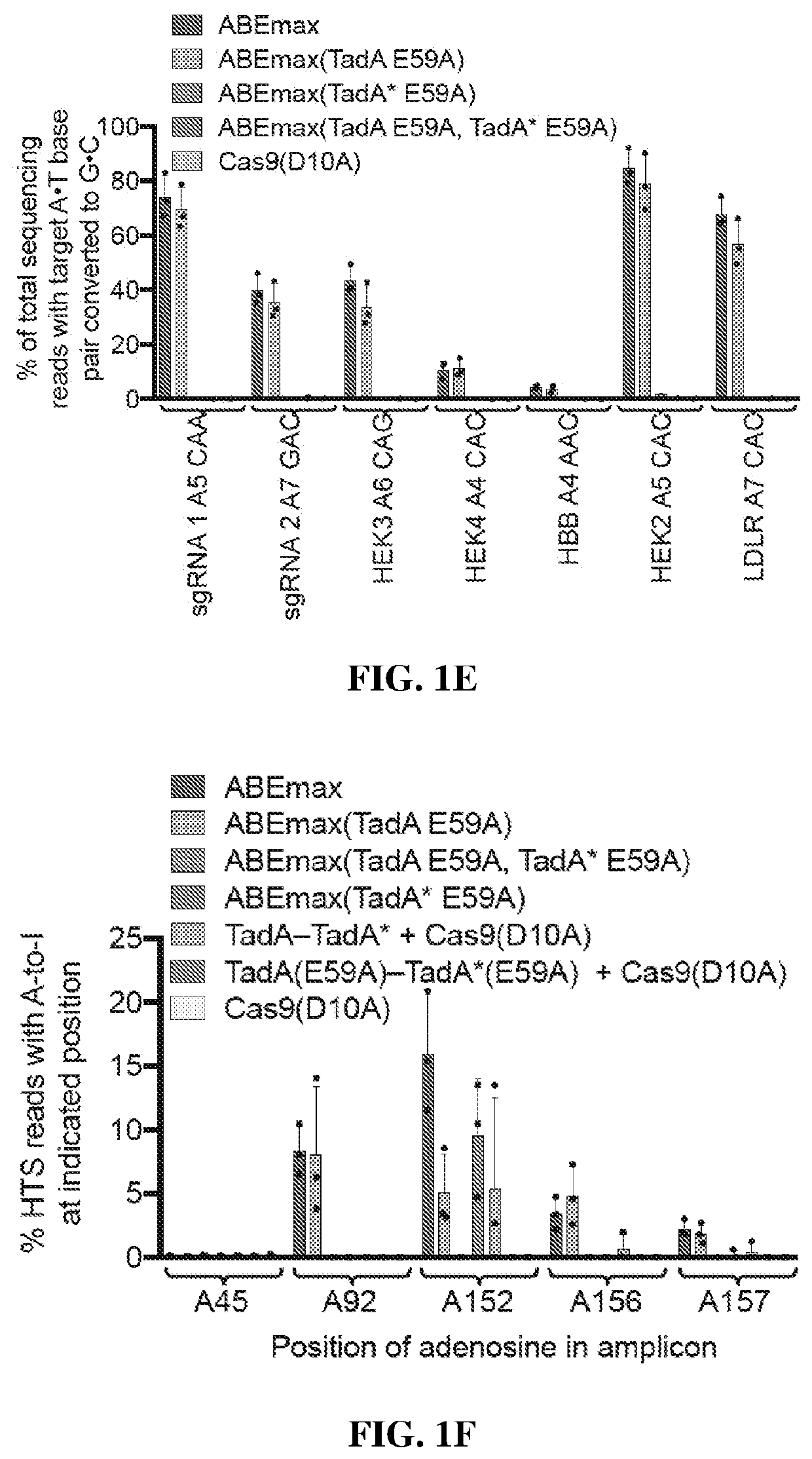
Adenine base editors with reduced off-target effects
PendingUS20220307003A1Expanded toolboxImprove efficiencyPolypeptide with localisation/targeting motifFusion with DNA-binding domainBiologyOrganic chemistry
The present disclosure provides novel adenine base editors that retain ability to edit DNA efficiently but show greatly reduced off-target effects, such as reduced RNA editing activity, as well as lower off-target DNA editing activity and reduced indel by product formation. Also provided are base editing methods comprising contacting a nucleic acid molecule with an adenine base editor and a guide RNA that has complementarity to a target sequence. Further provided are complexes comprising a guide RNA bound to a base editor provided herein; and kits and pharmaceutical compositions for the administration of adenine base editor variants to a host cell.
Owner:THE BROAD INST INC
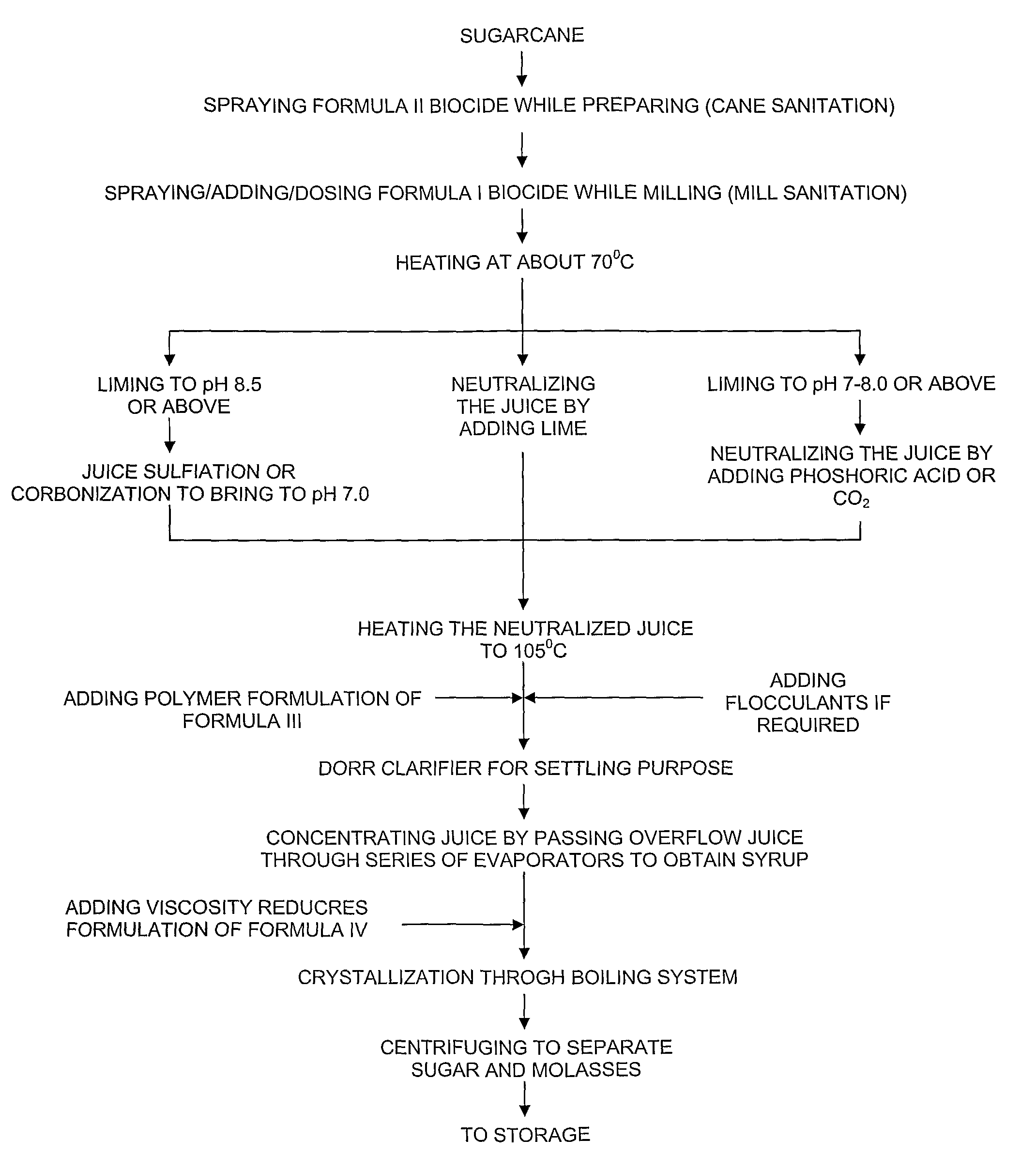
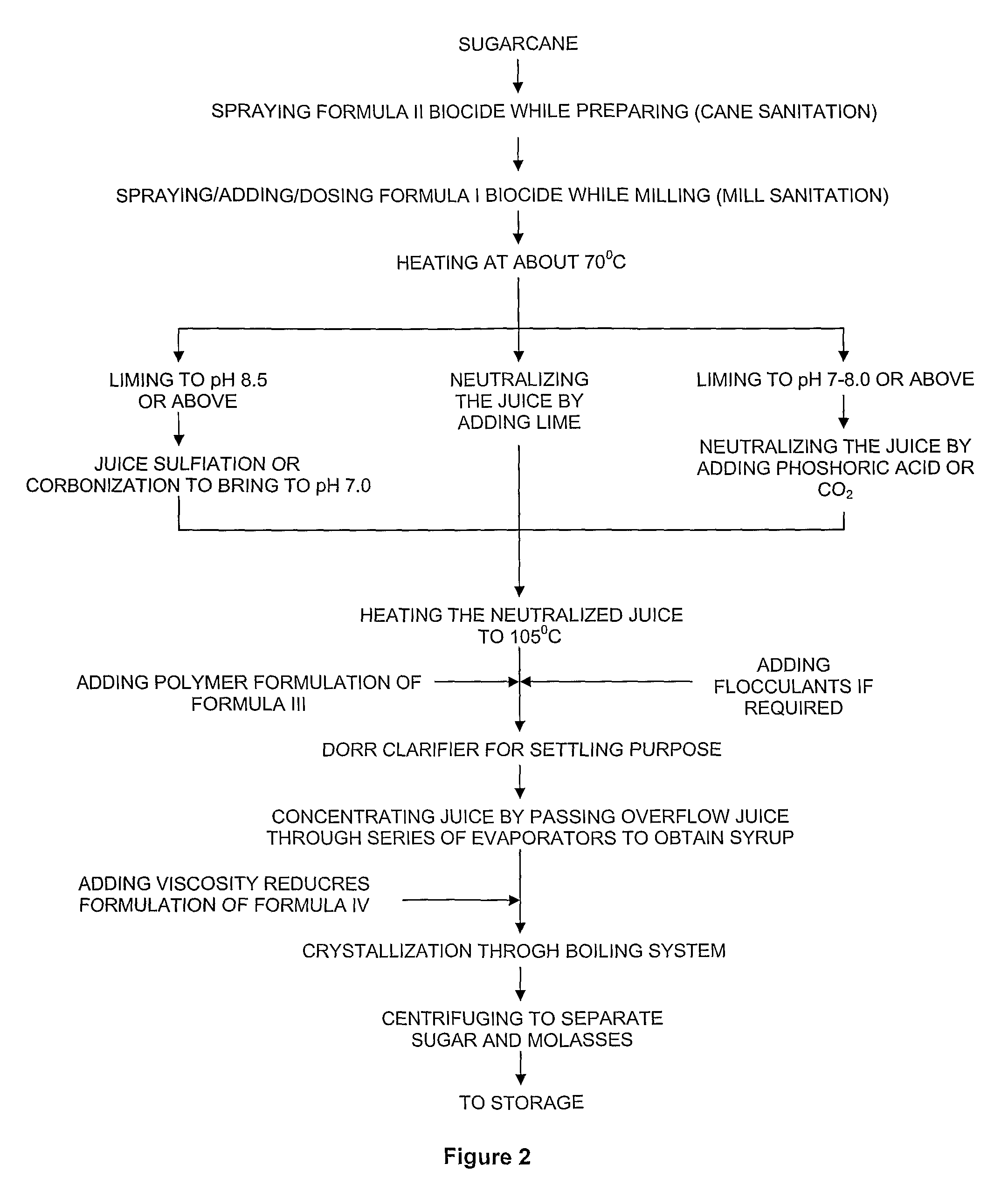
Method for manufacturing sugar from sugarcane
InactiveUS8394202B2Minimize and discontinue useReduce lossesPurification using alkaline earth metal compoundsSucrose extraction by chemical meansFruit juiceSulfur
Disclosed is a method for manufacturing sugar from sugarcane. The method consists of steps of dosing biocides on sugarcane during cane preparation and milling to kill about 90% of microbes; heating juice, obtained from a mill to 70° C.; subsequently, neutralizing the juice; subsequent to the neutralizing step, heating the neutralized juice to about 105° C.; subsequent to the neutralizing step, passing the heated neutralized juice through clarifiers or settling tanks; concentrating the neutralized juice by evaporating to boil-off water from the neutralized juice to obtain syrup of the neutralized juice having about 60% solids; crystallizing the syrup, obtained in the concentrating step, to obtain a liquor; separating the sugar from the liquor obtained in the crystallizing step; and washing and drying the sugar obtained in the separating step. The sugar thus produced is about neutral and contains substantially zero amount of sulfur.
Owner:KULKARNI VISHNUKUMAR MAHADEO
Enhanced security fence and method of construction and installation
ActiveUS11261617B2High strengthProvide quicklyFencingArchitectural engineeringStructural engineering
An enhanced security fence for use in high security situations is provided. The fence is made of high strength materials that are preferably welded together in a convenient location and sent as prefabricated sections to the installation location to form an all welded bracket-less perimeter barrier fence system. Posts with section hangers are provided and installed at a perimeter, and the prefabricated panels are quickly and securely attached to the posts. The panels can be friction fit to the posts and, if desired welded thereto. The invention includes a method of creating an enhanced security fence, that includes prefabrication of panels and rapid fitting and securing the panels to posts to more quickly create a secure perimeter in places having difficult environments.
Owner:IND FENCE INC
Combination ionizing radiation and immunomodulator delivery devices and methods for inhibiting hyperplasia
ActiveUS20020165424A1Dosing is convenientTurn easilyStentsBalloon catheterPercent Diameter StenosisBlood vessel
The present invention provides improved devices, methods, and kits for inhibiting restenosis and hyperplasia after intravascular intervention. In particular, the present invention provides controlled immunomodulator delivery in combination with ionizing radiation to selected locations within a patient's vasculature to reduce and / or inhibit restenosis and hyperplasia rates with increased efficacy. In one embodiment, the combination radiation and immunomodulator delivery catheter for inhibiting hyperplasia comprises a catheter body having a proximal end and distal end, an ionizing radiation source coupleable to the catheter body for applying a radiation dose to a body lumen, and means coupleable to the catheter body or the radiation source for releasing an immunomodulator to the body lumen.
Owner:XOFT INC
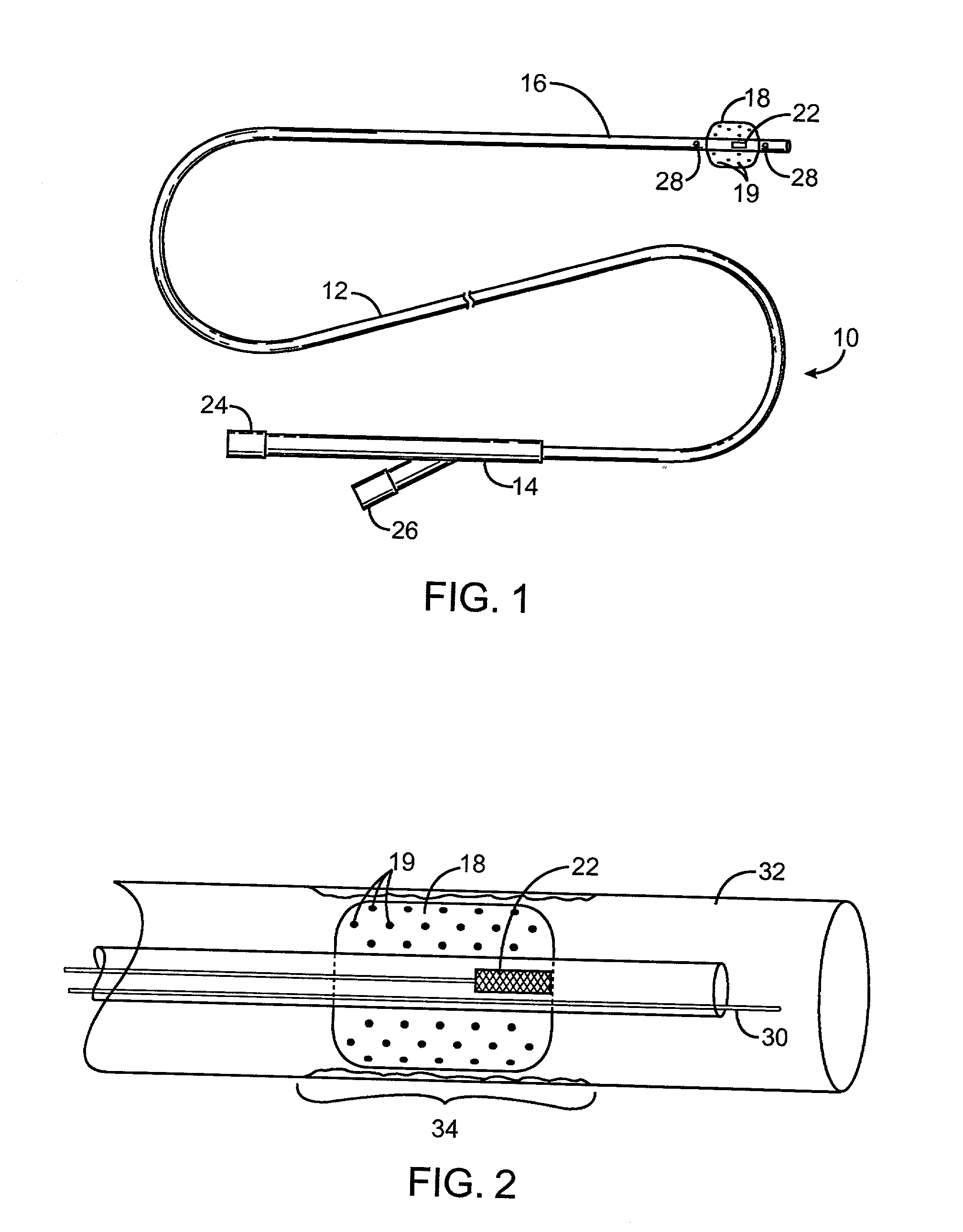
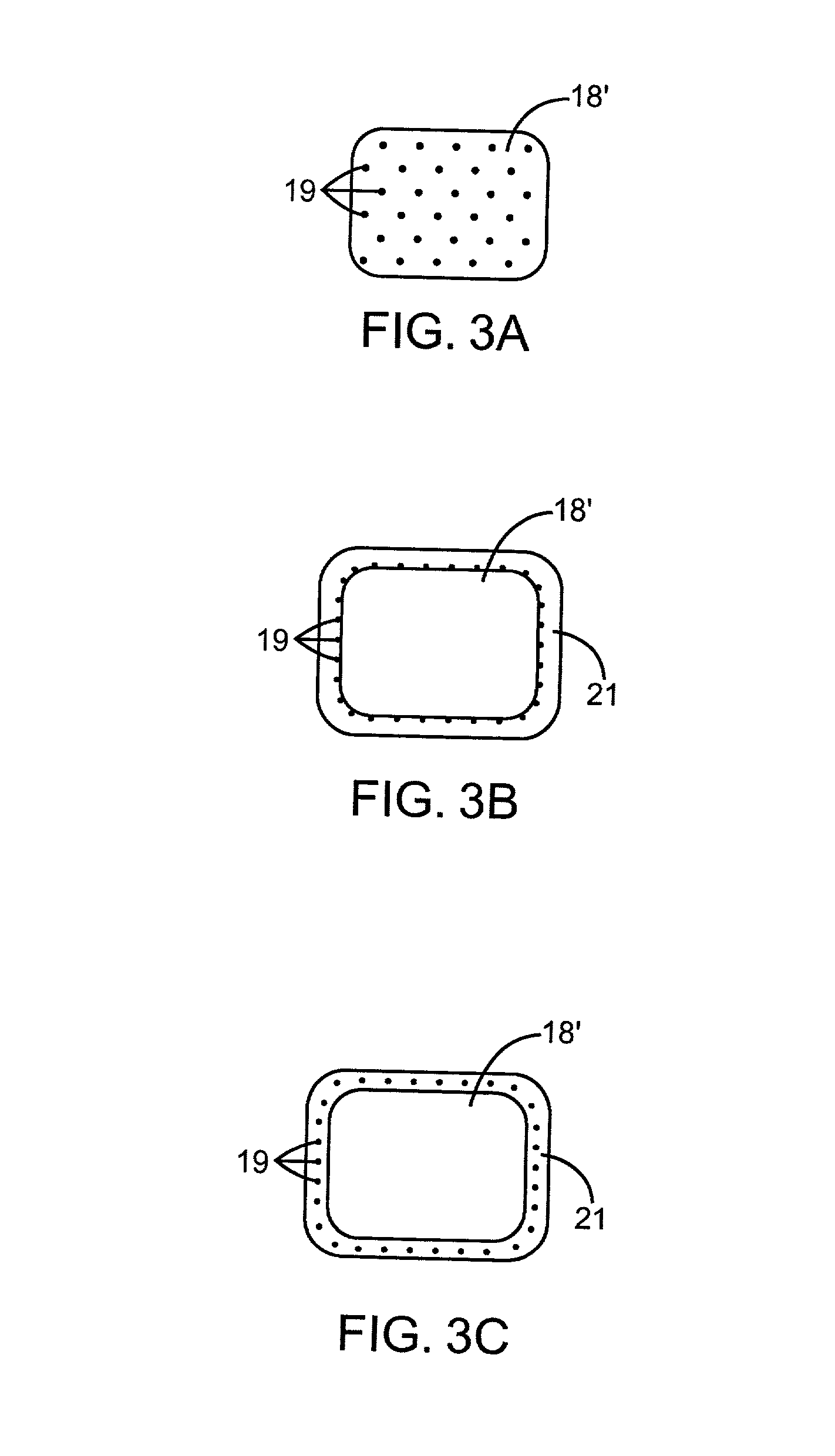
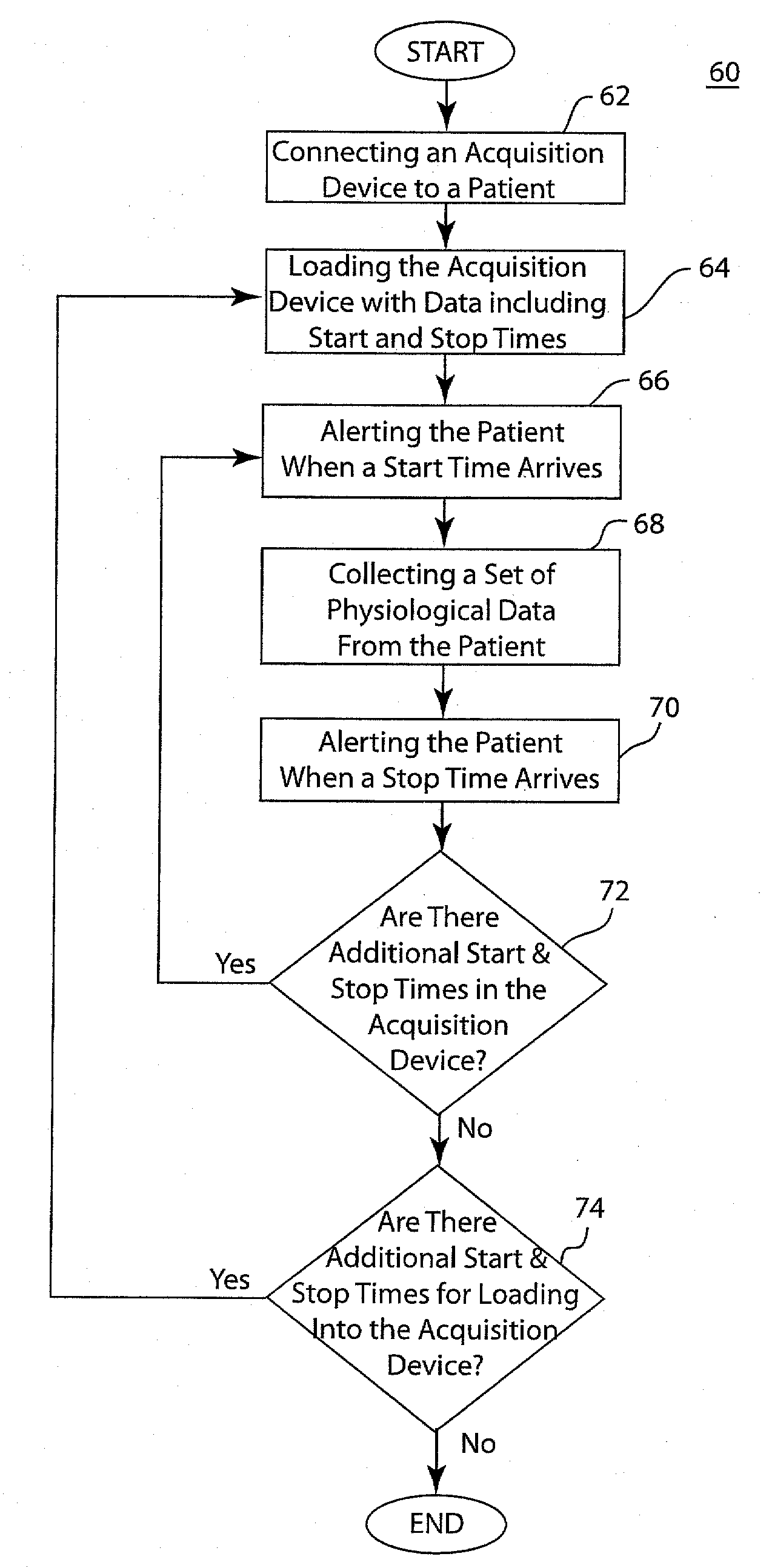
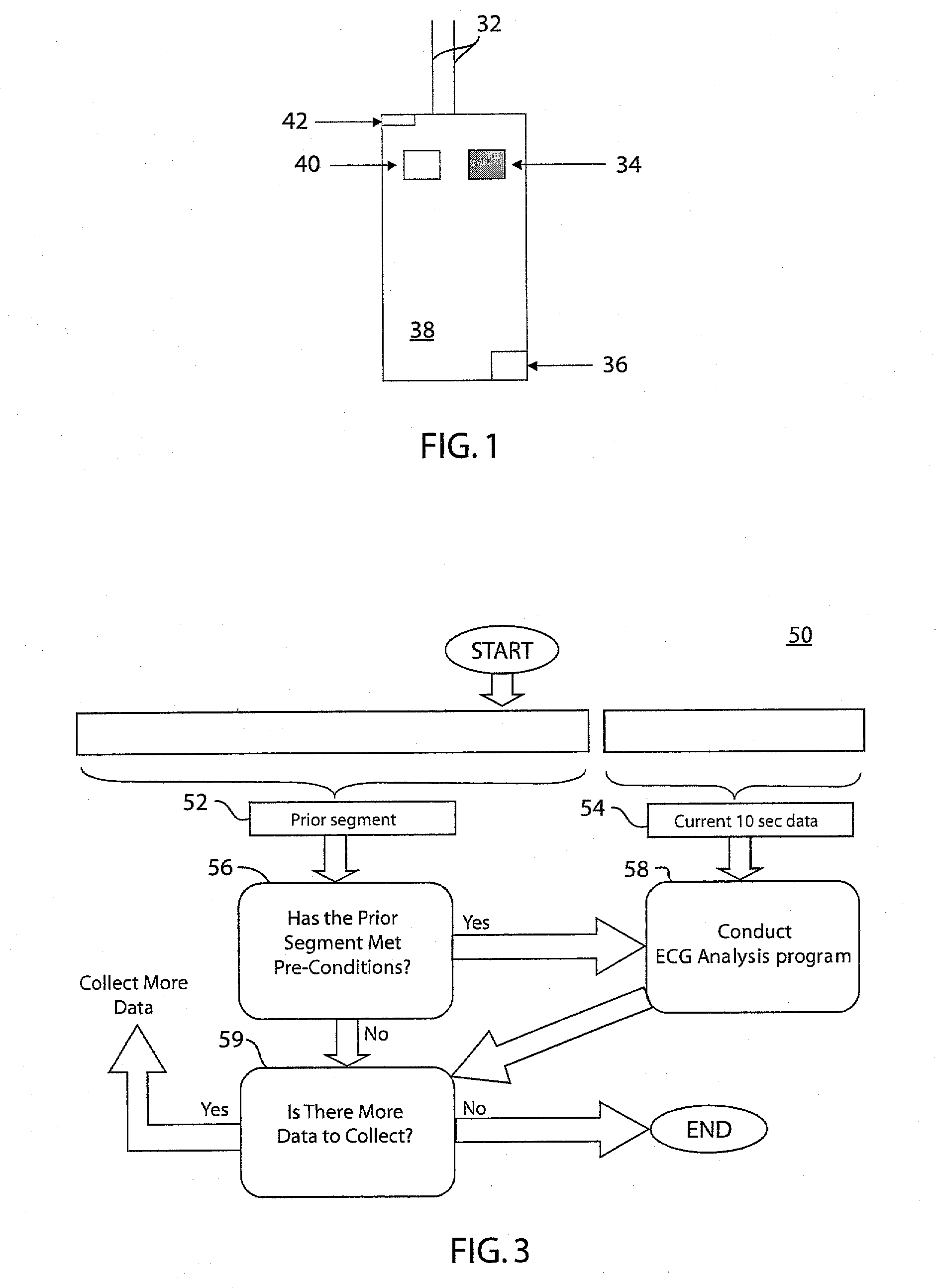
Pre-conditioned ECG system and method
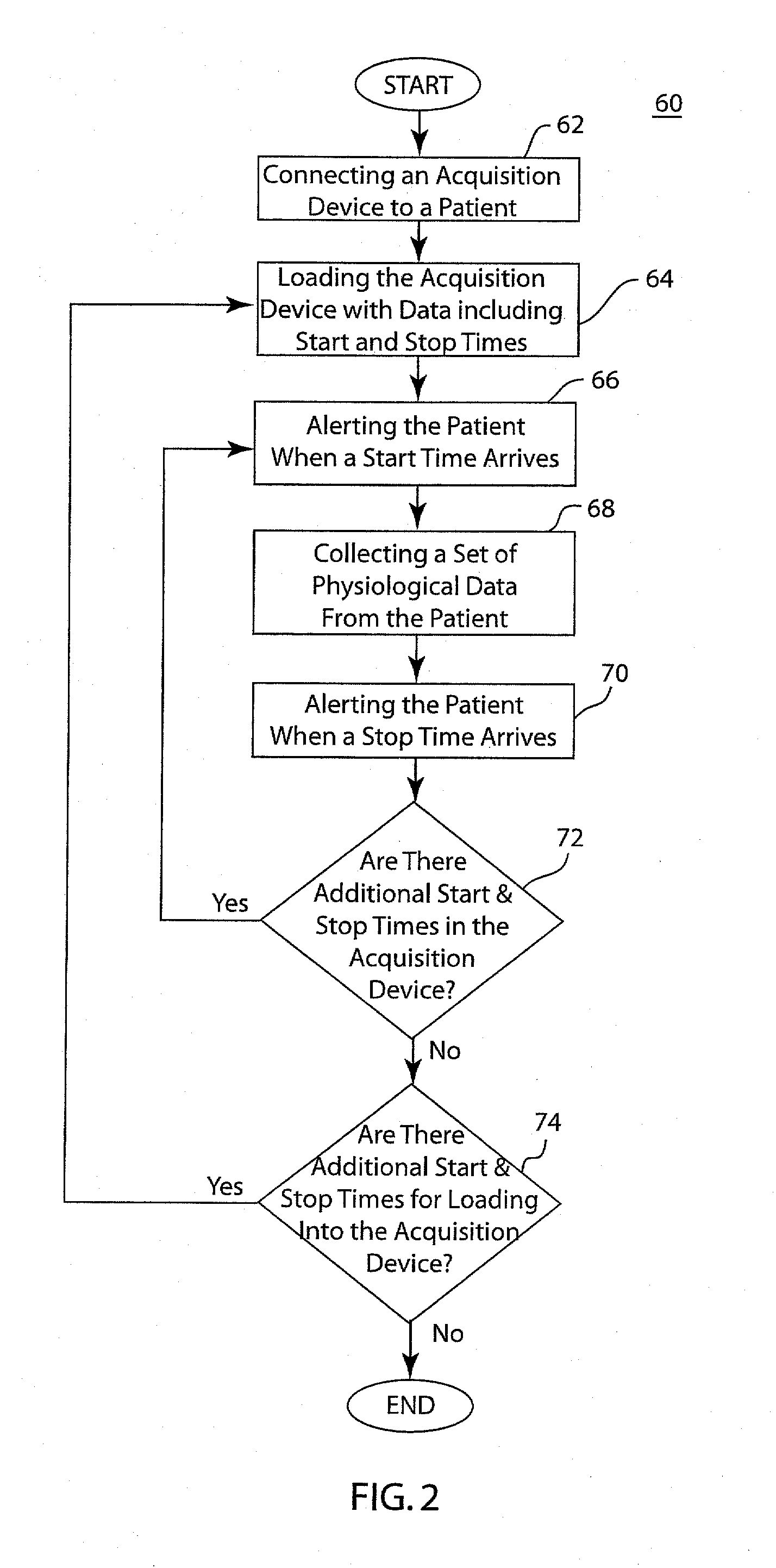
InactiveUS20080082015A1Minimize activityMinimize timeElectrocardiographySensorsPre-conditionPre conditioning
A pre-conditioned ECG system and method includes a patient signaling device configured to alert the patient to minimize the patient's activity so that an ECG measurement may be taken, and further alerts the patient when the measurement is completed. The pre-conditioned ECG system and method also includes a pre-set buffer configured to hold a preset length of ECG data, and further configured to hold pre-set ECG parameters such as mean R-R interval, standard deviation of R-R interval, or simple rhythm analysis. The system and method may analyze the current 10 seconds of ECG data when the preset parameters are met or when selected parameters are met.
Owner:GENERAL ELECTRIC CO
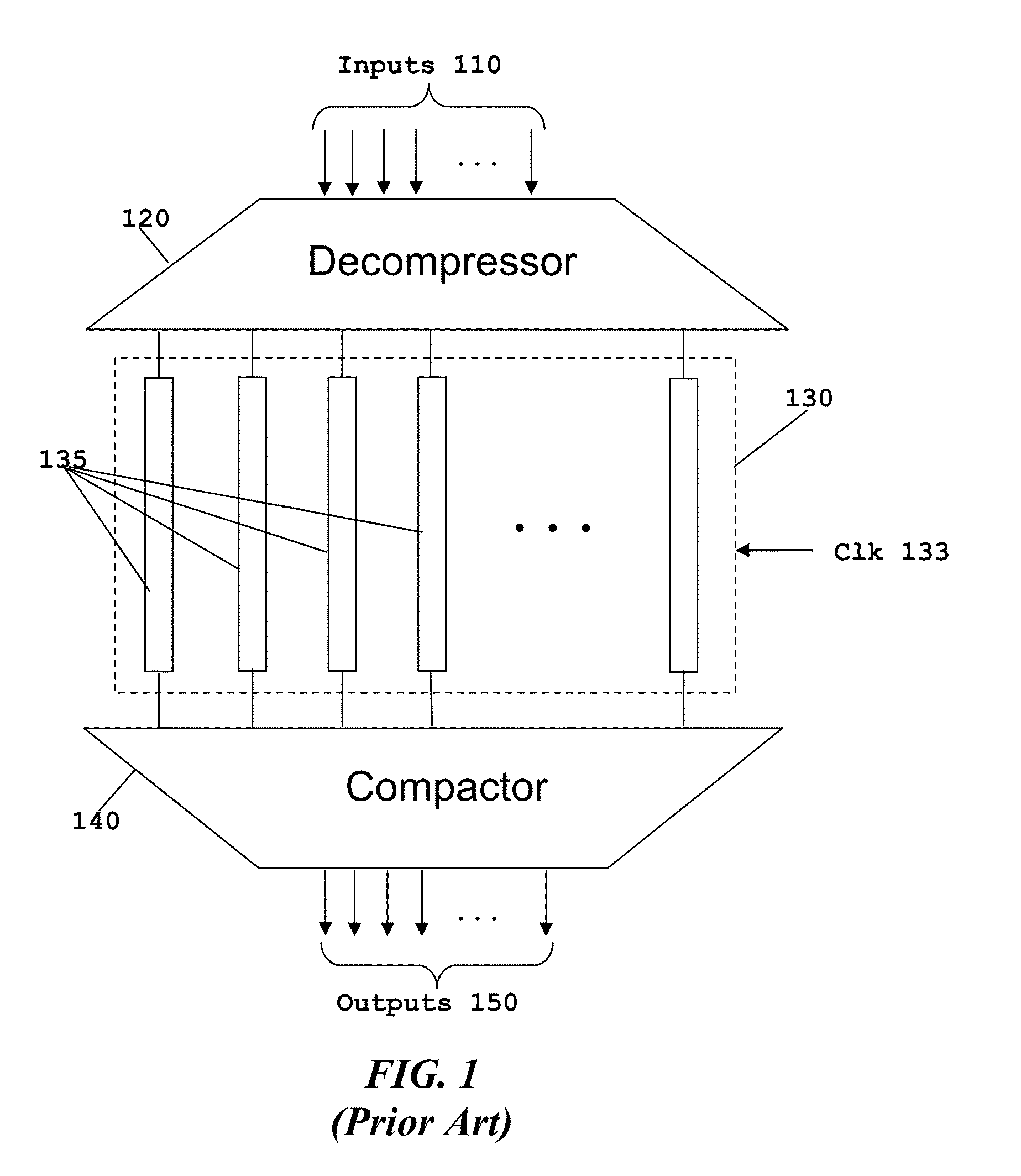
Cost reduction schema for advanced raid algorithms
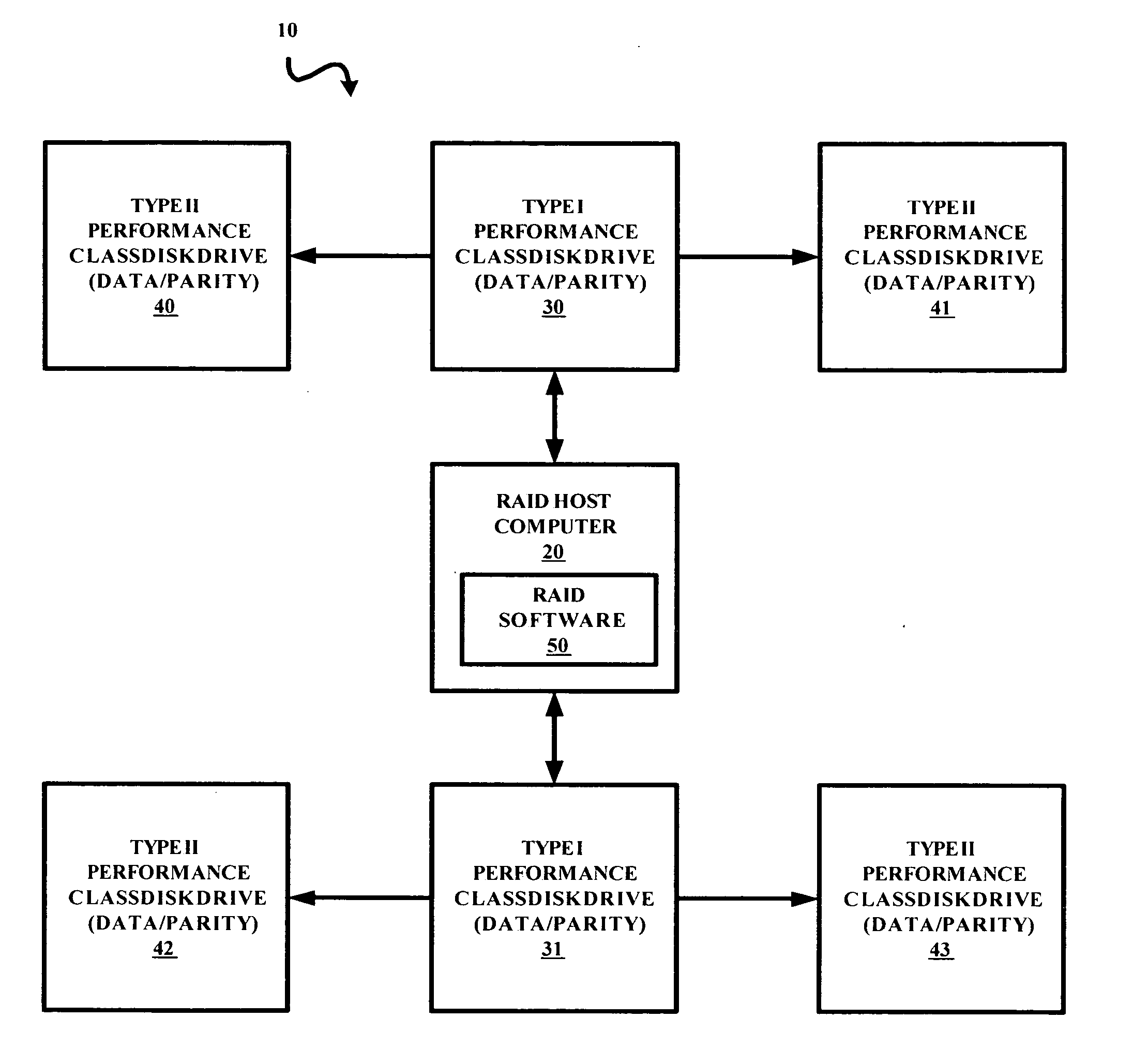
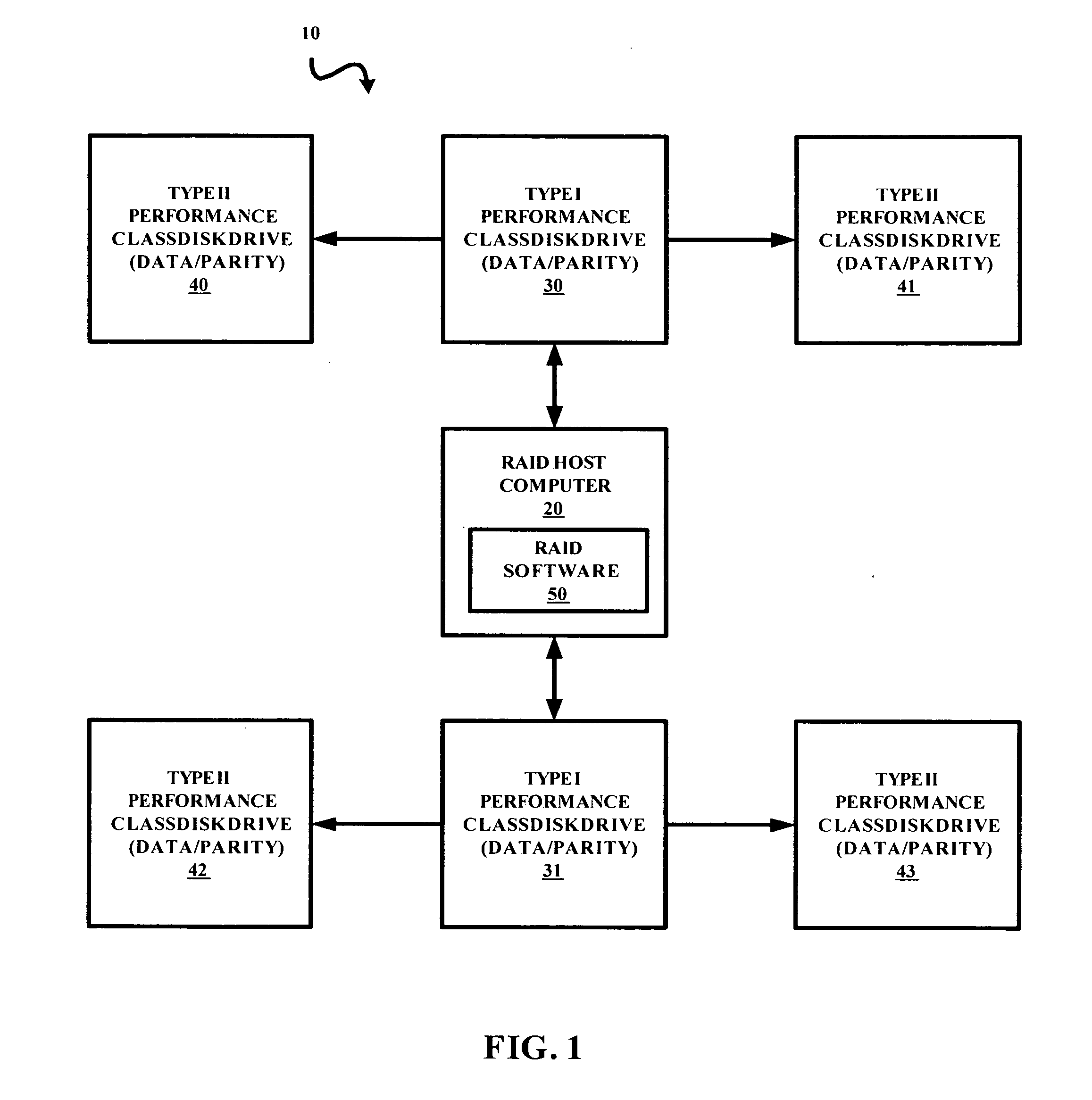
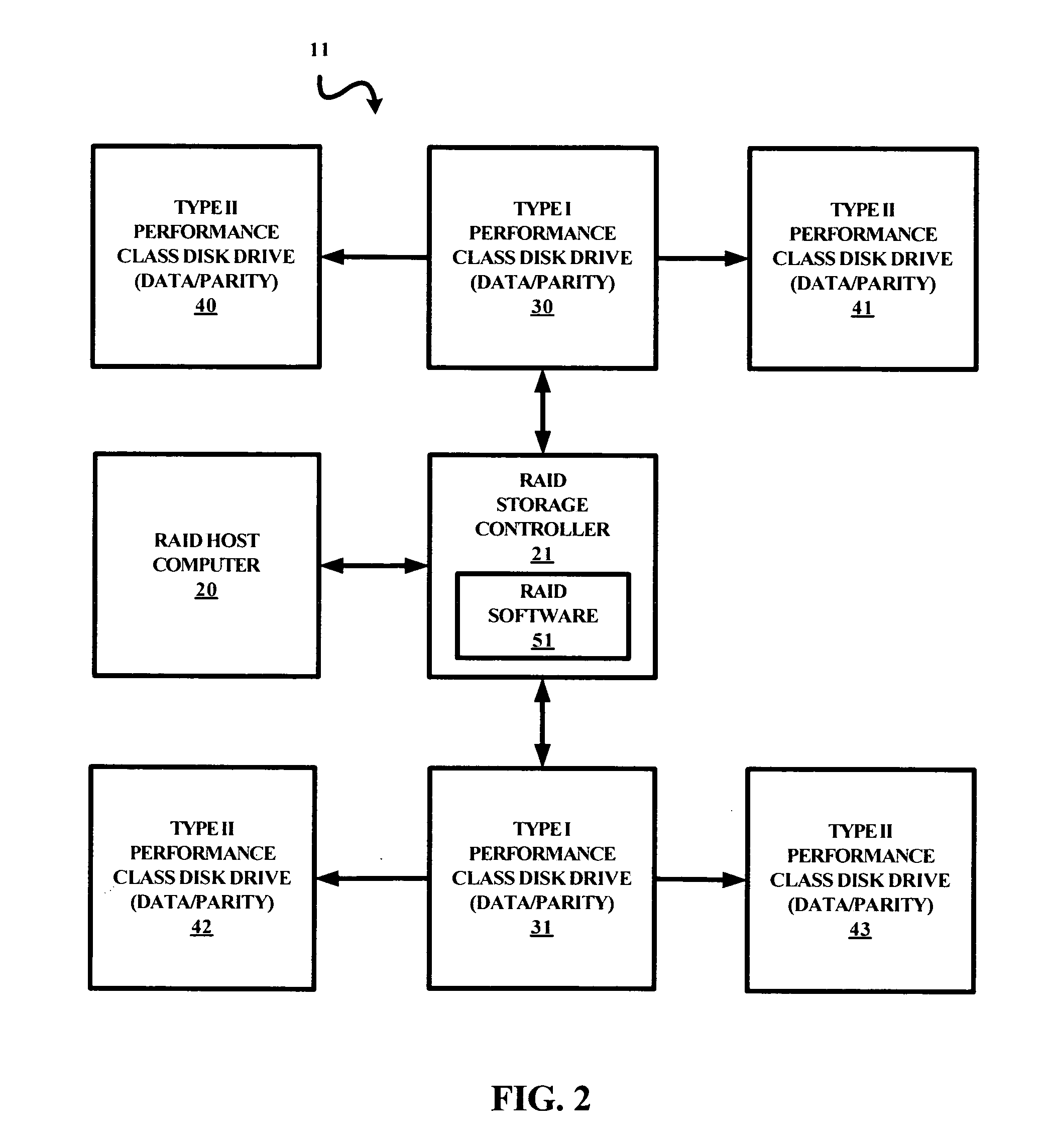
InactiveUS20060048003A1Minimize activityMaximize reliabilityMemory systemsRedundant hardware error correctionRAIDBackup
A signal bearing medium tangibly embodying a program of machine-readable instructions executable by a processor to perform operations to read information stored in a storage system. The storage system includes a controller coupled to a plurality of type I performance class disk drives and at least one type II performance class backup disk drive. The operations include executing a first read request for a first set of information from a first type I performance class disk drive and executing a second read request for the first set of information from a first type II performance class backup disk drive in response to an occurrence of a first read error associated with the execution of the first read request.
Owner:GOOGLE LLC
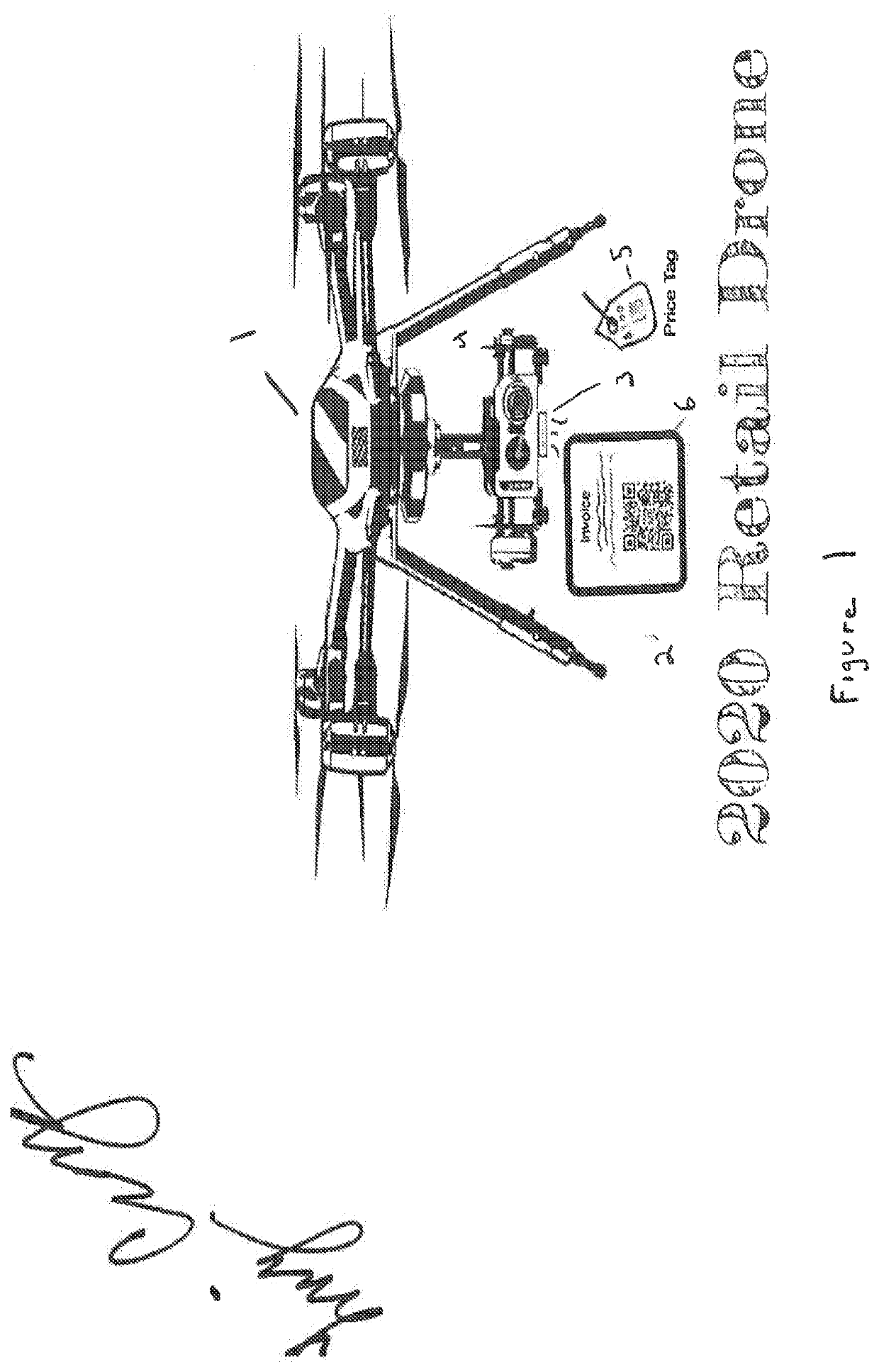
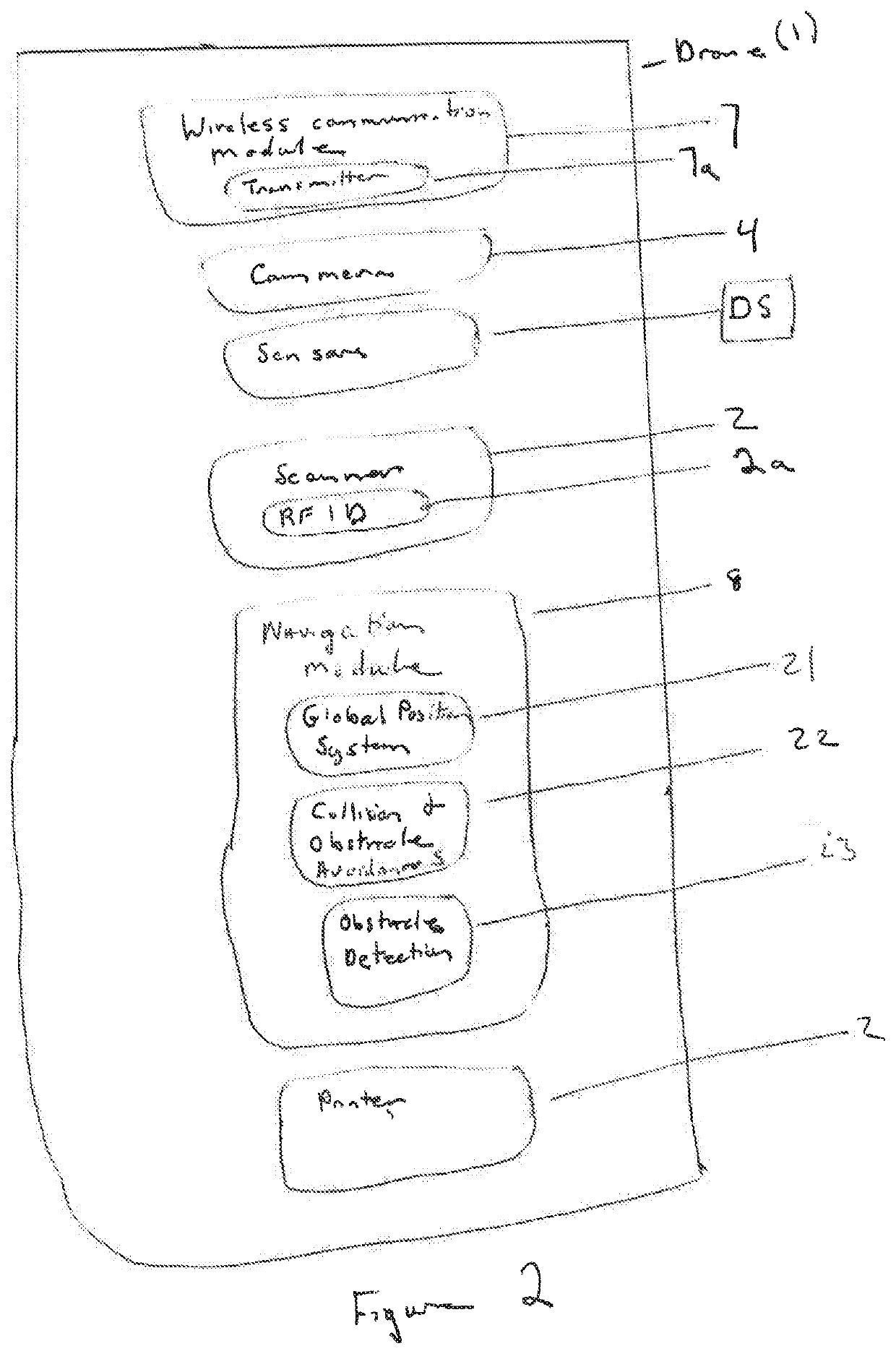
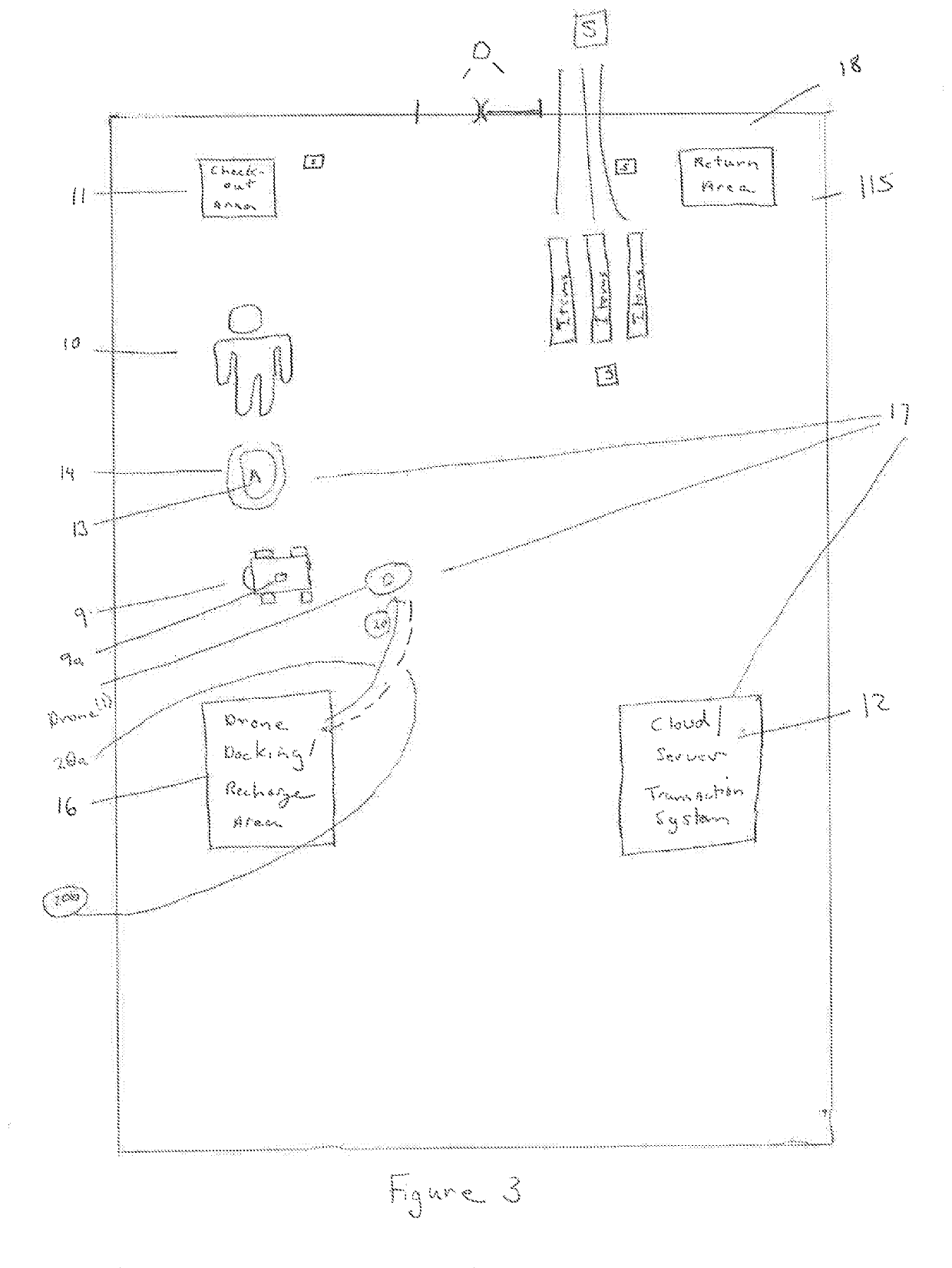
Retail drone
PendingUS20210103966A1Improve shopping experienceIncrease productivityAircraft componentsUnmanned aerial vehiclesComputer printingBarcode
A system for a point of sale transaction within a retail facility includes an aerial drone having a barcode scanner and printer capabilities, an onsite transaction application that can run on a handheld smart device, and a server / cloud transaction system that can act as a transaction system and an anti-theft system. A shopper can summon the aerial drone for a sales transaction or return, and using the drone scanner, list the items that are present in their shopping cart, which generates a physical or electronic listing of the items to be purchased or returned. The list can be presented to a clerk for payment, or the customer can present a debit / credit card at a kiosk portal to pay for their items electronically. The list is also transmitted to the cloud / sever as a record and used to manage inventory. The shopper has an assigned or preassigned identifier for use by the transaction system, e.g. the anti-theft system.
Owner:CUMMINGS LUJEAN J
Nutraceutical composition and method for promoting the rejuvenation of cells in warm-blooded animals including humans
InactiveUS20070202091A1Promote rejuvenationIncrease mitochondrial energy productionBiocideHydroxy compound active ingredientsBiotechnologyChemical composition
A nutraceutical composition and method for promoting the rejuvenation of cells in warm-blooded animals including humans employing mitochondrial energy production-inducing agent for inducing the mitochondrial energy production to proceed from a lower energy production state to a higher energy production state and a nutraceutical composition for supporting the metabolic requirements of the increased mitochondrial energy production induced by the mitochondrial energy production-inducing agent.
Owner:DEFELICE STEPHEN L
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com