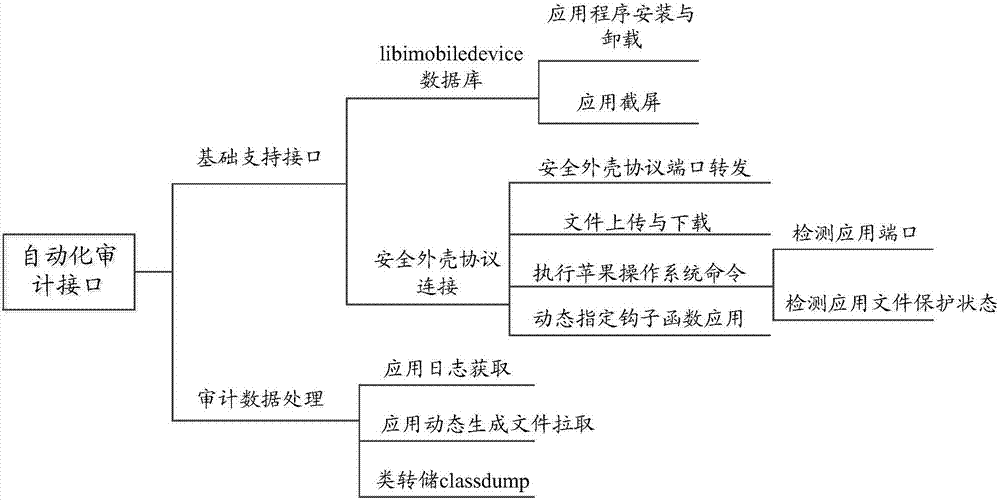
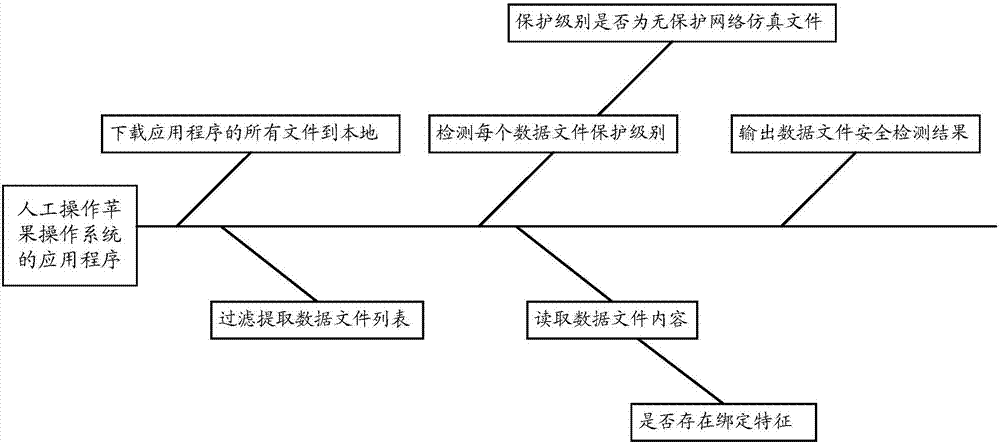
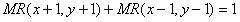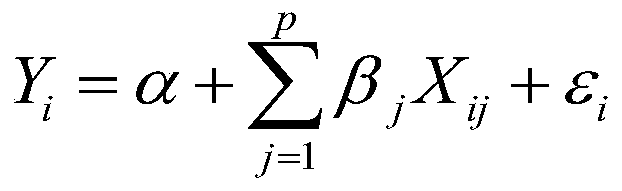Patents
Literature
609results about How to "Reduce threat" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
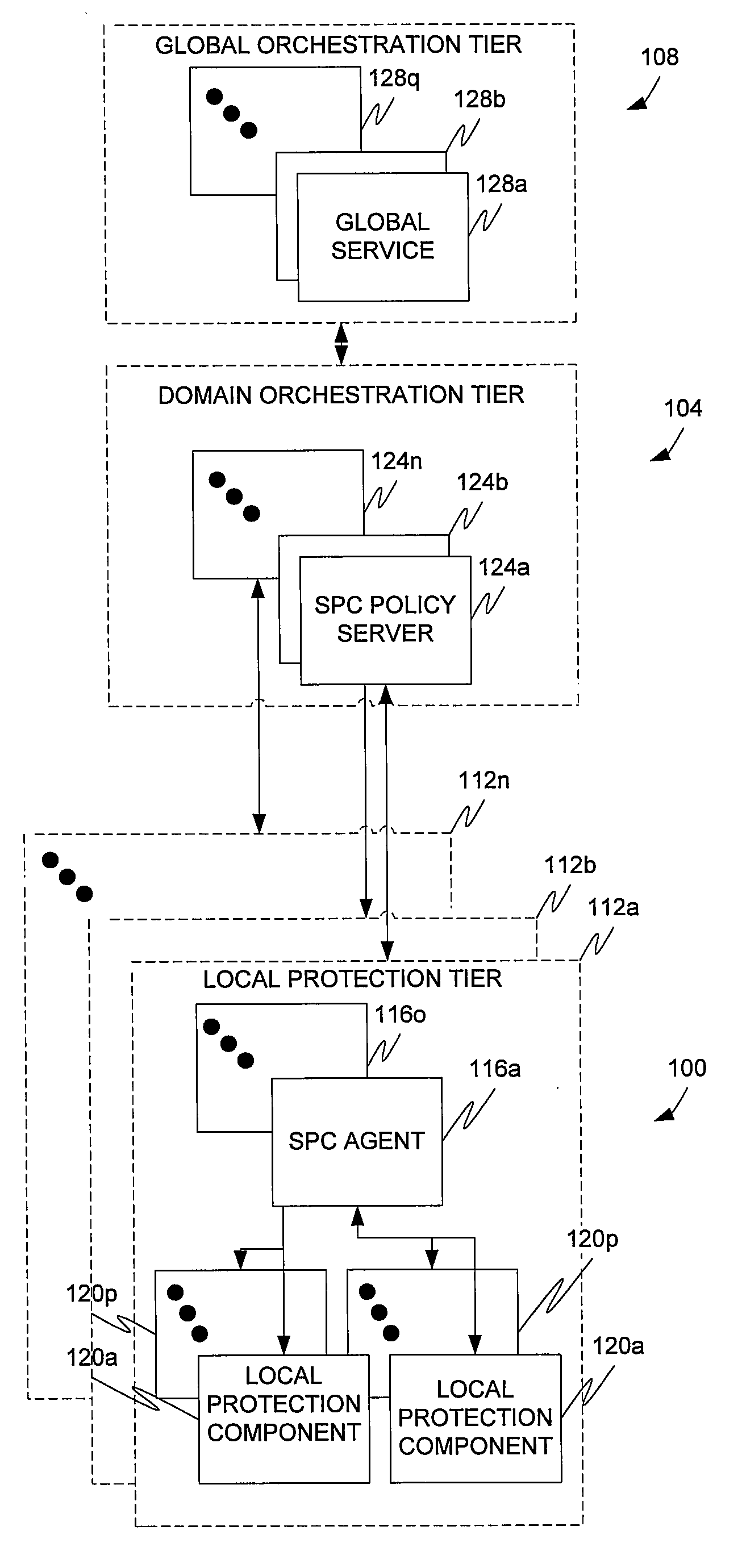
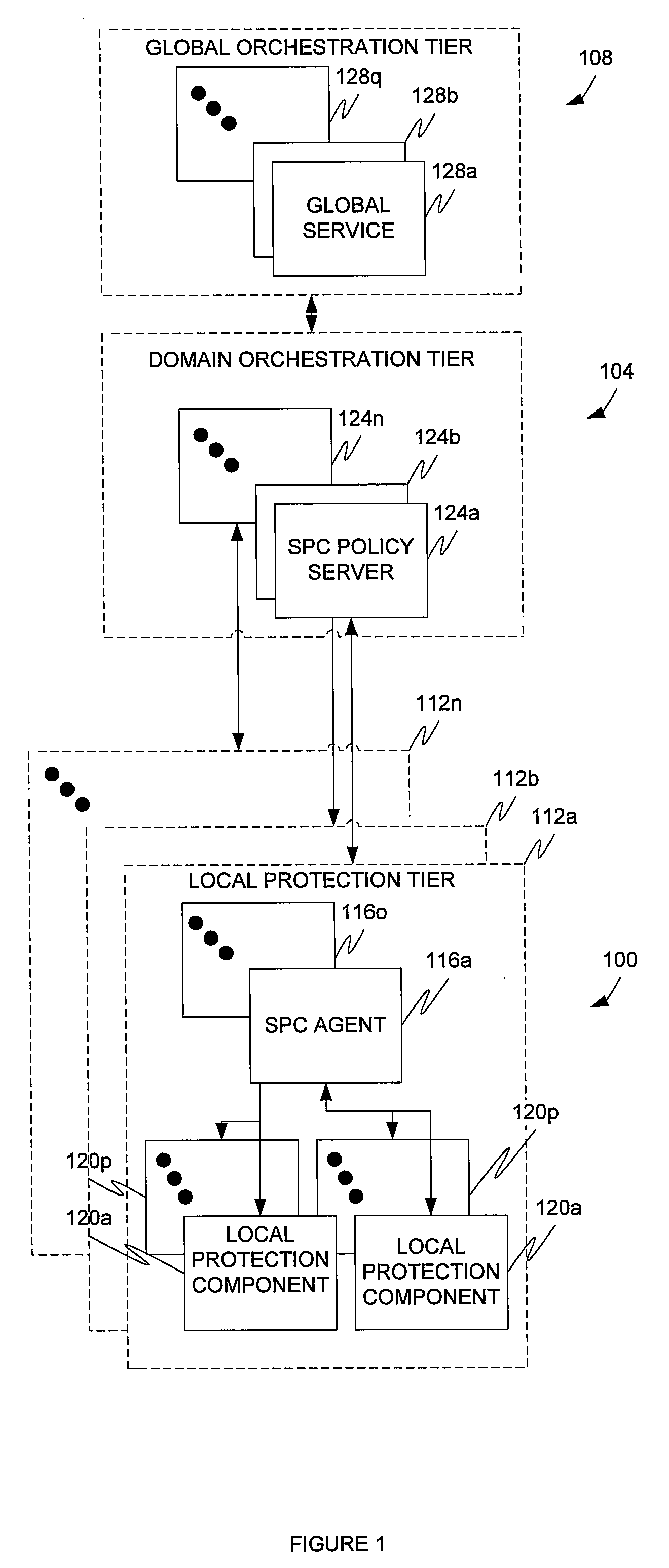
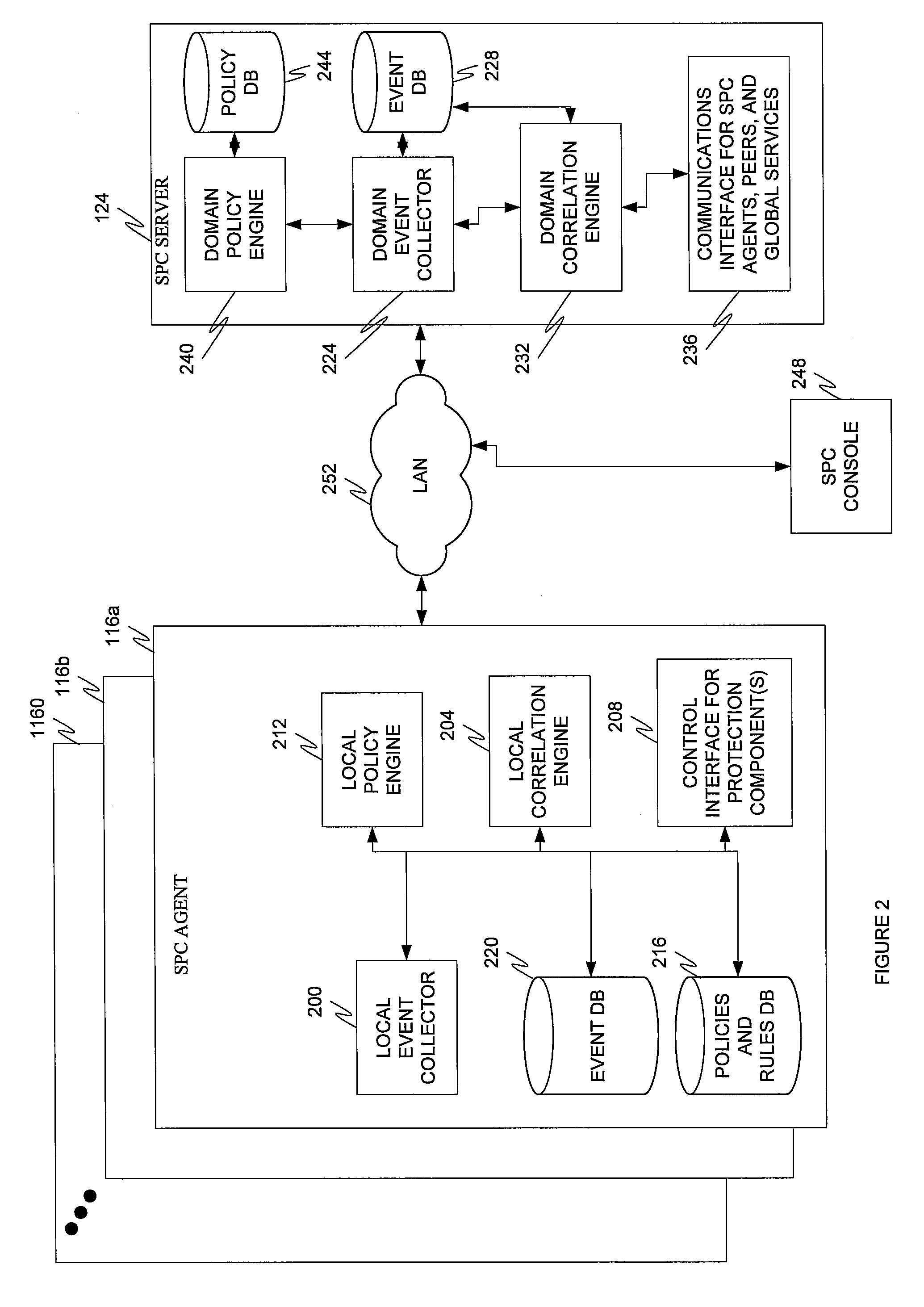
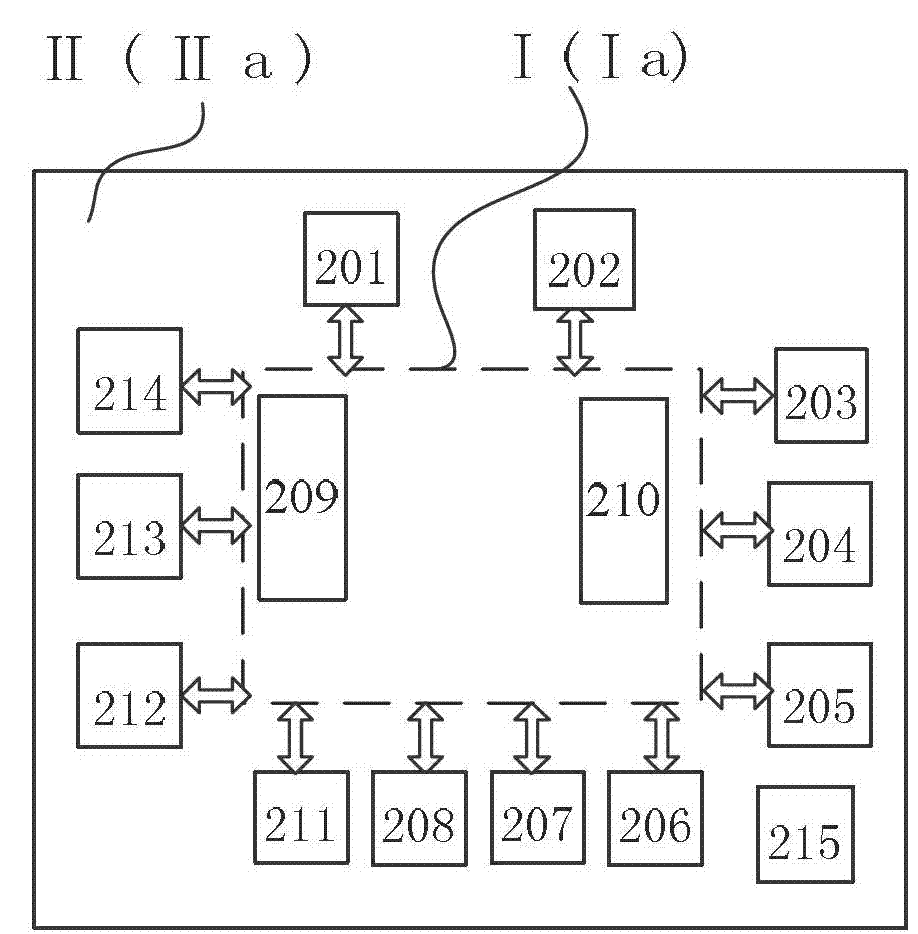
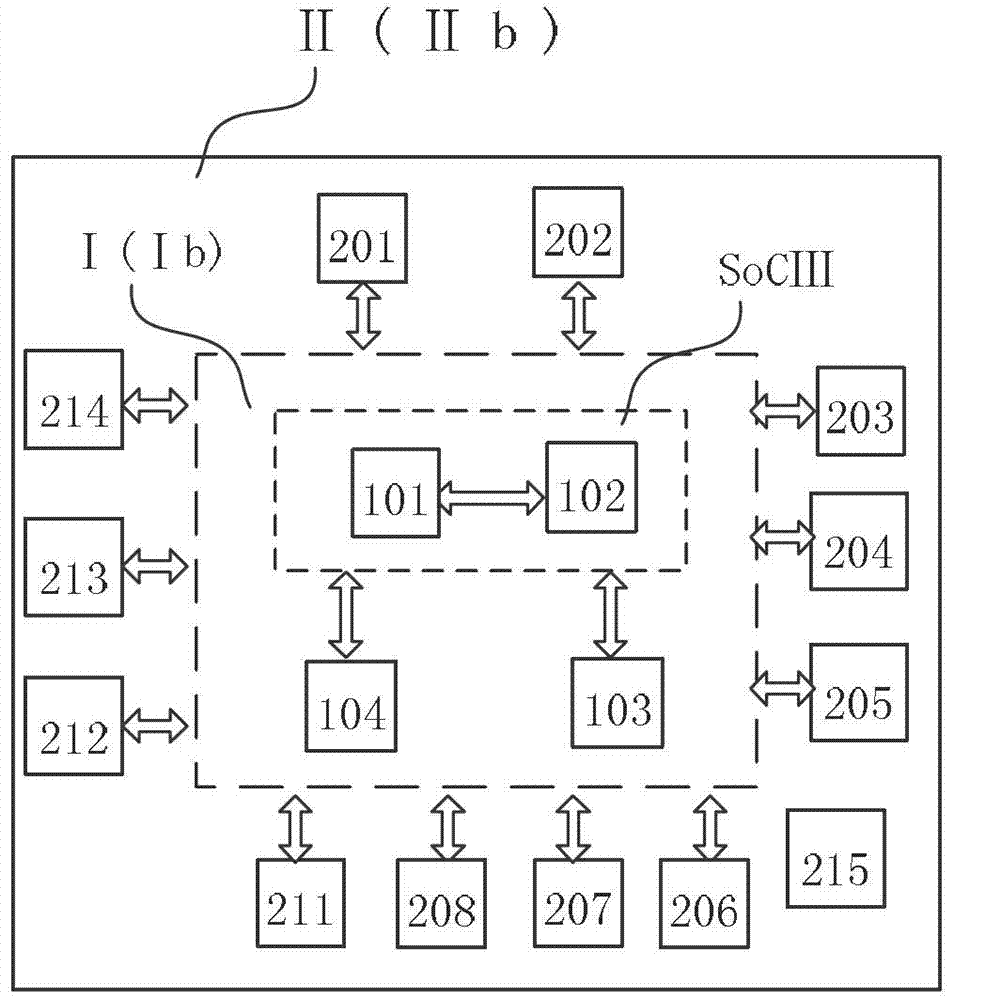
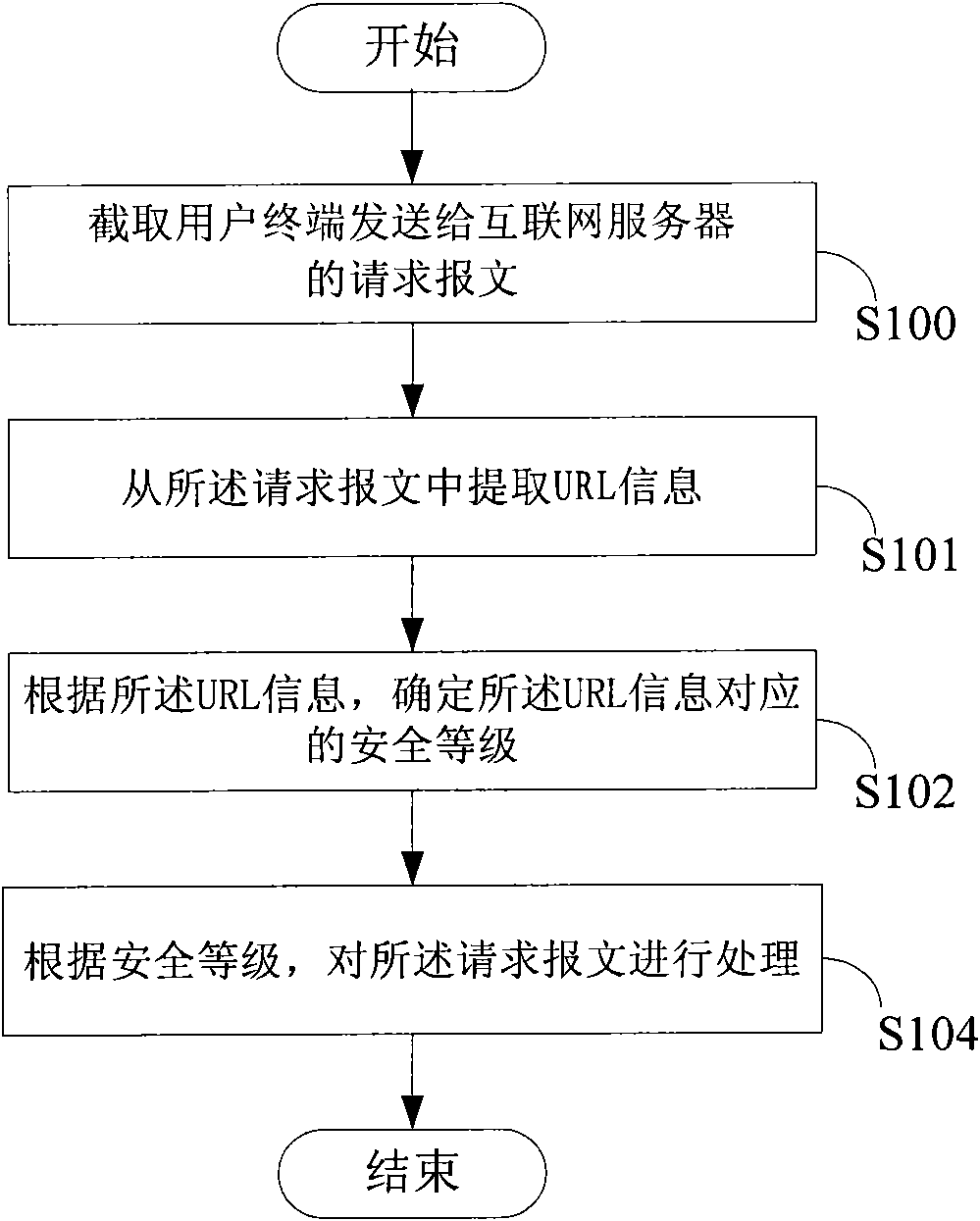
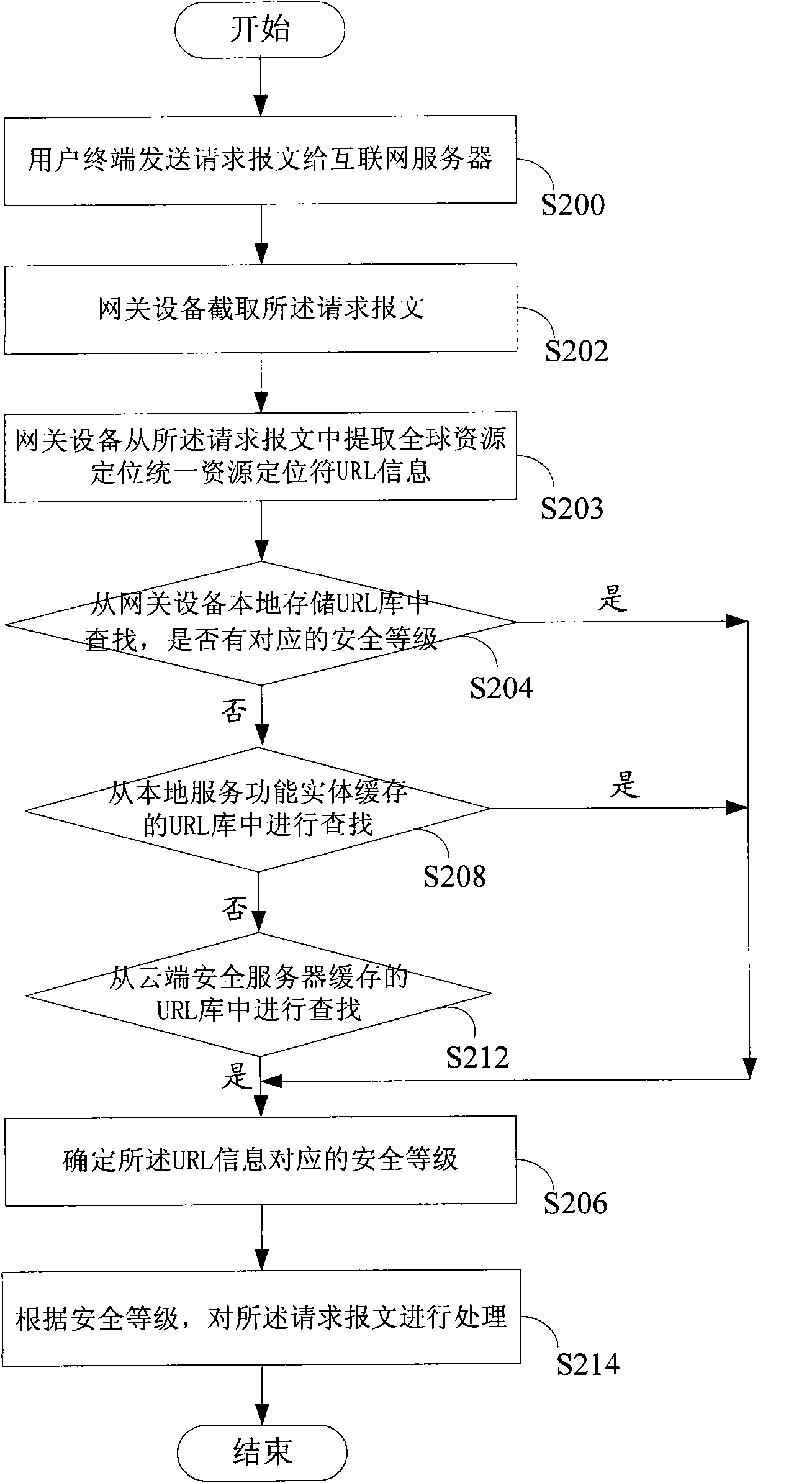
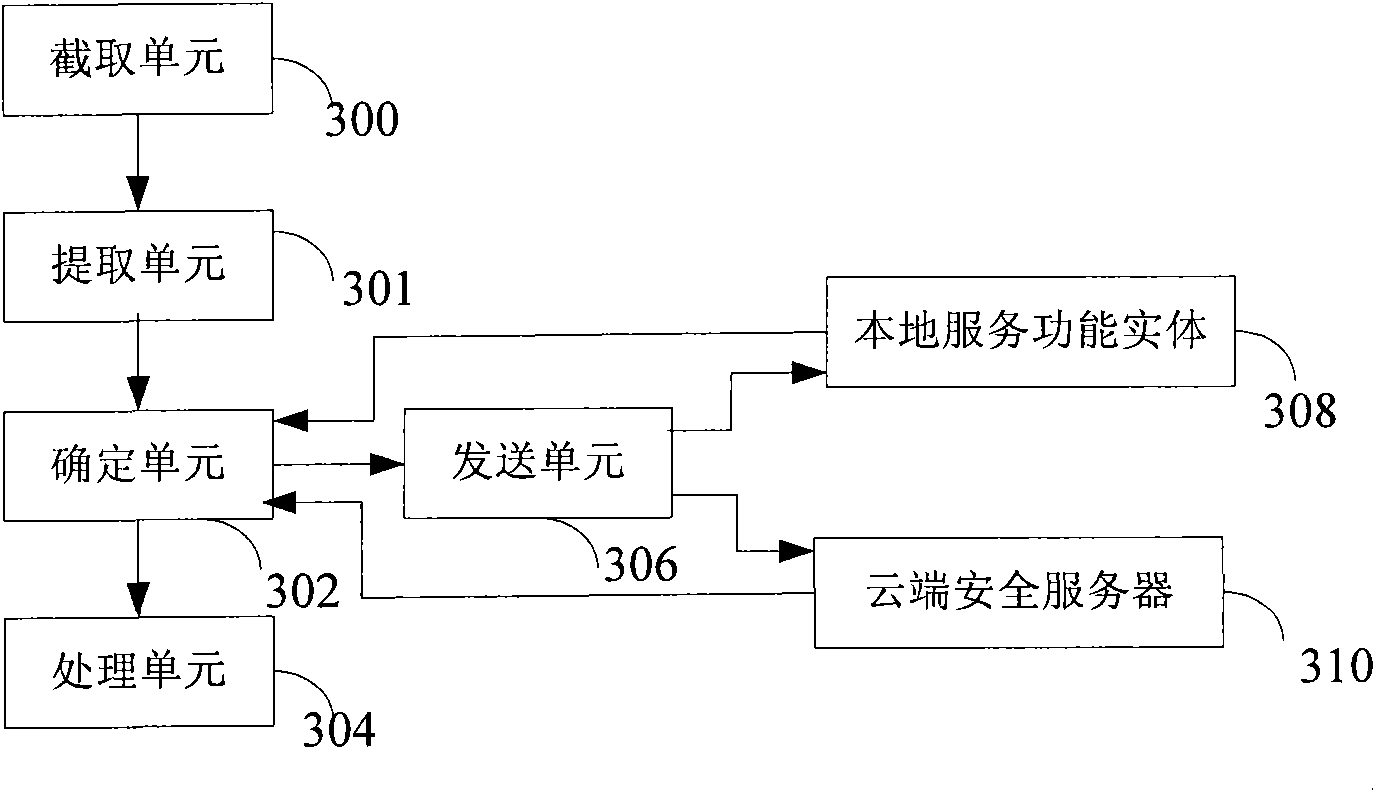
Multi-tier security event correlation and mitigation
InactiveUS20090254970A1Optimize event processingReduce threatComputer security arrangementsTransmissionComputer securityEvent correlation
Owner:AVAYA INC
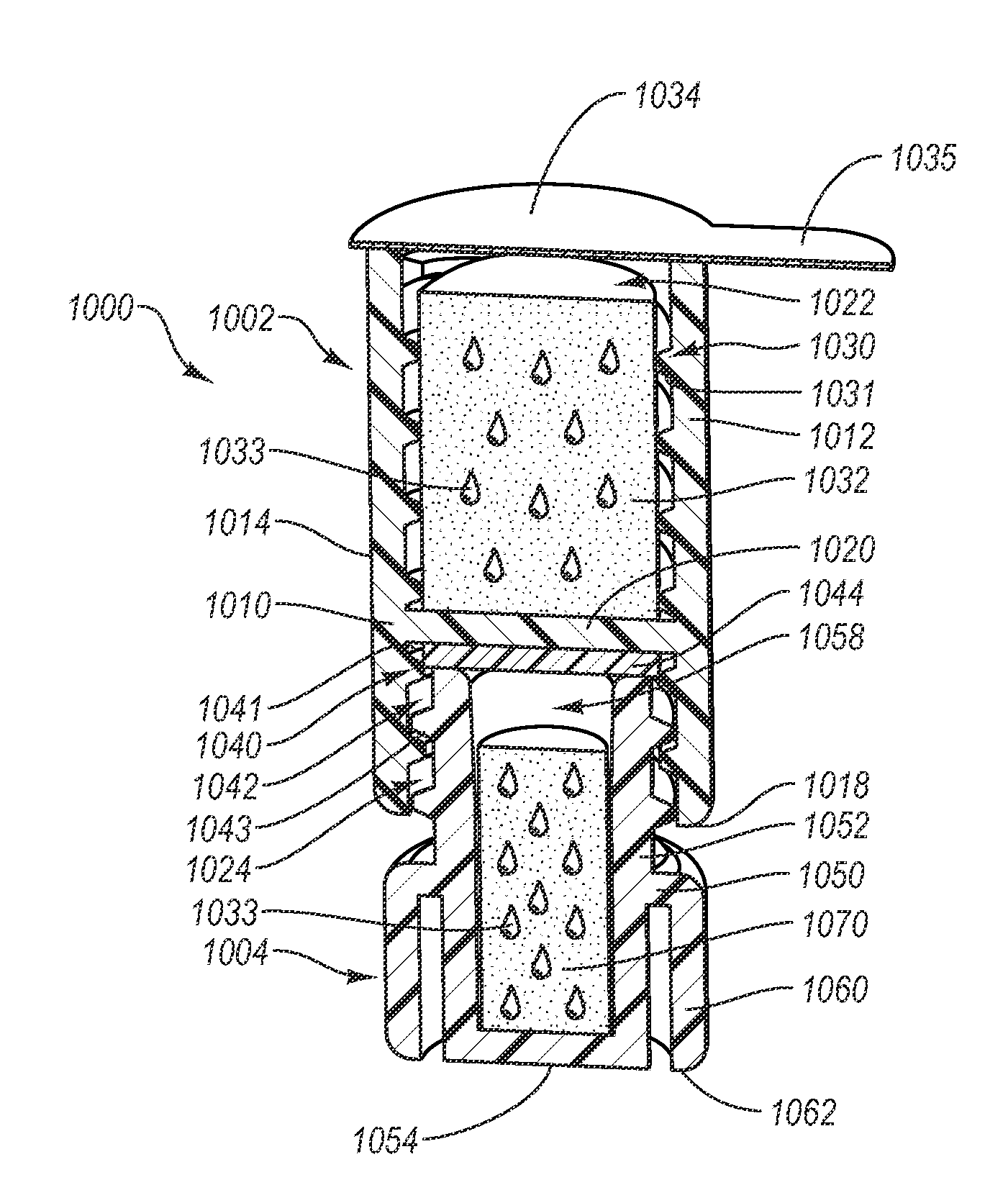
Sterilization caps and systems and associated methods
Caps can be used to cover and sterilize the male luer of a medical connector. Some caps can create a seal with the male luer to prevent antiseptic from entering a lumen of the male luer. A biasing element can aid in creating or maintaining the seal.
Owner:MERIT MEDICAL SYST INC
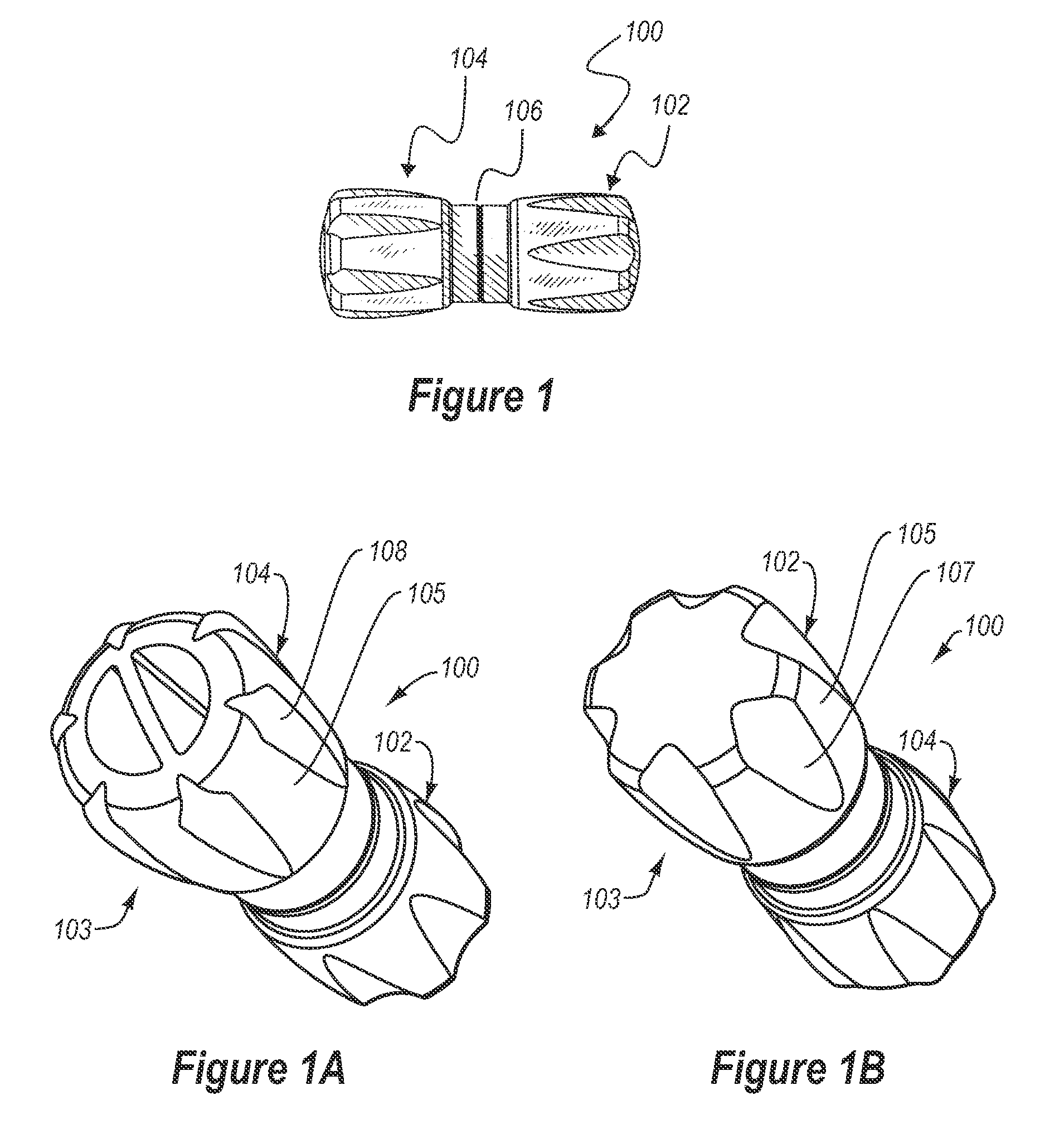
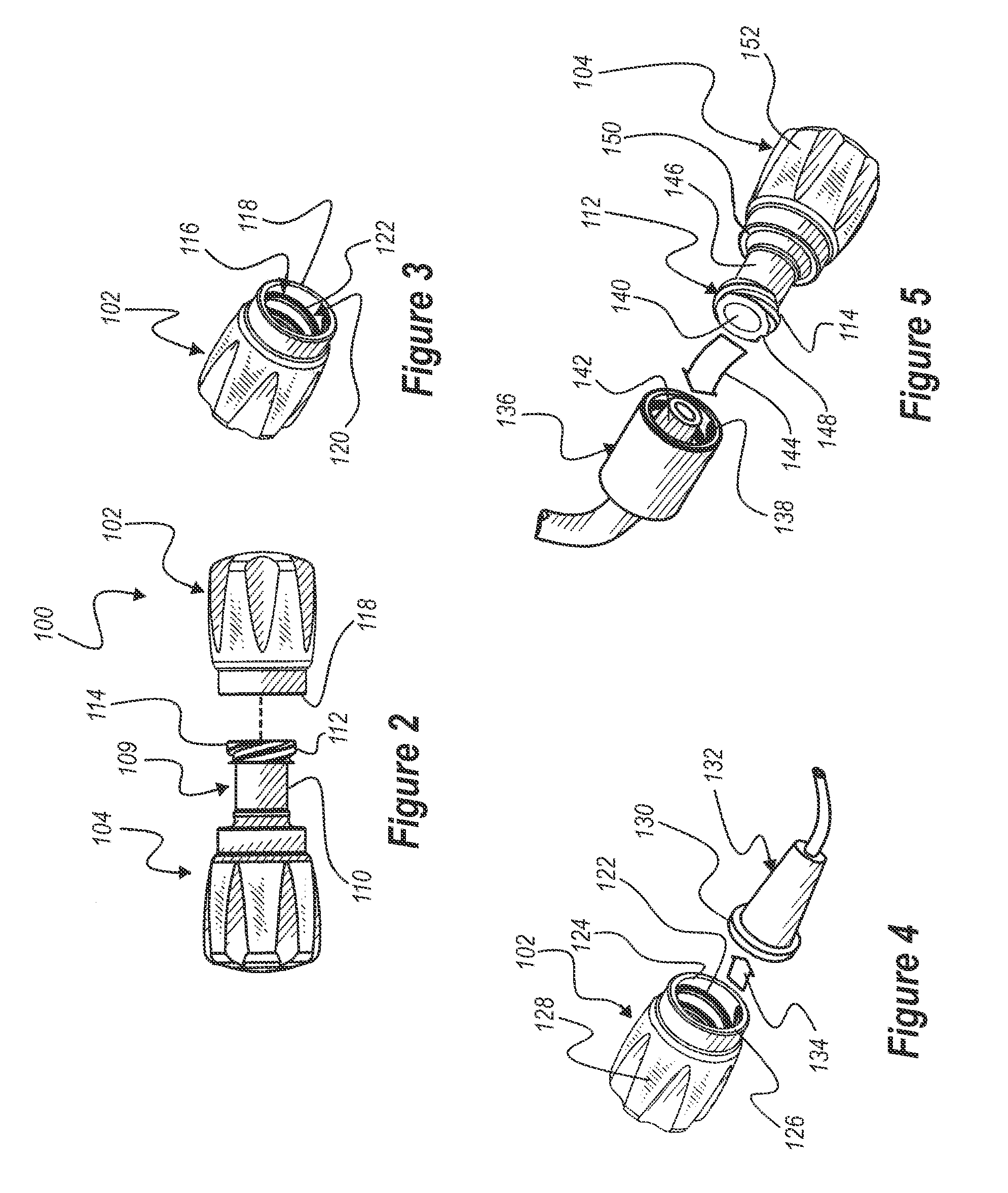
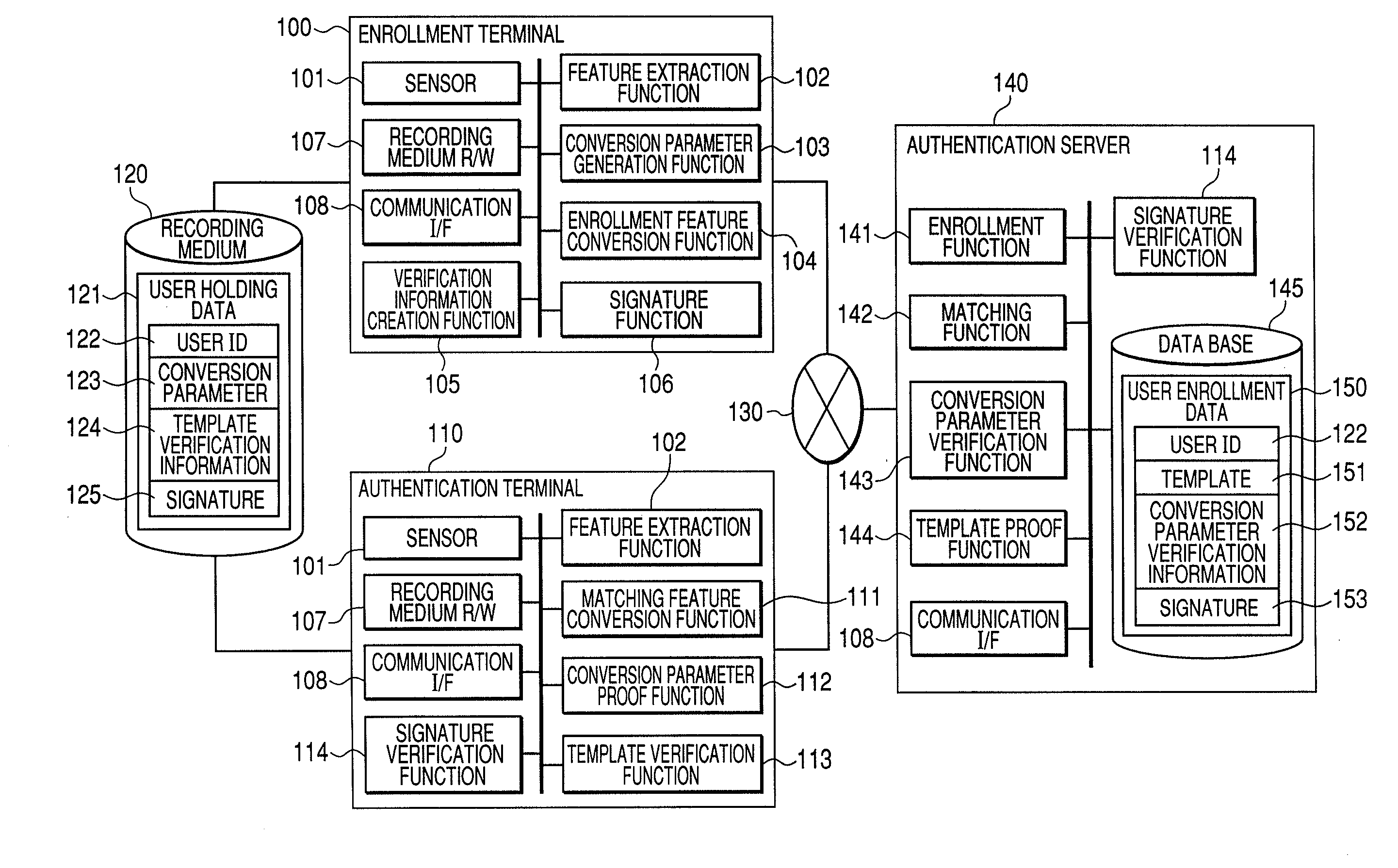
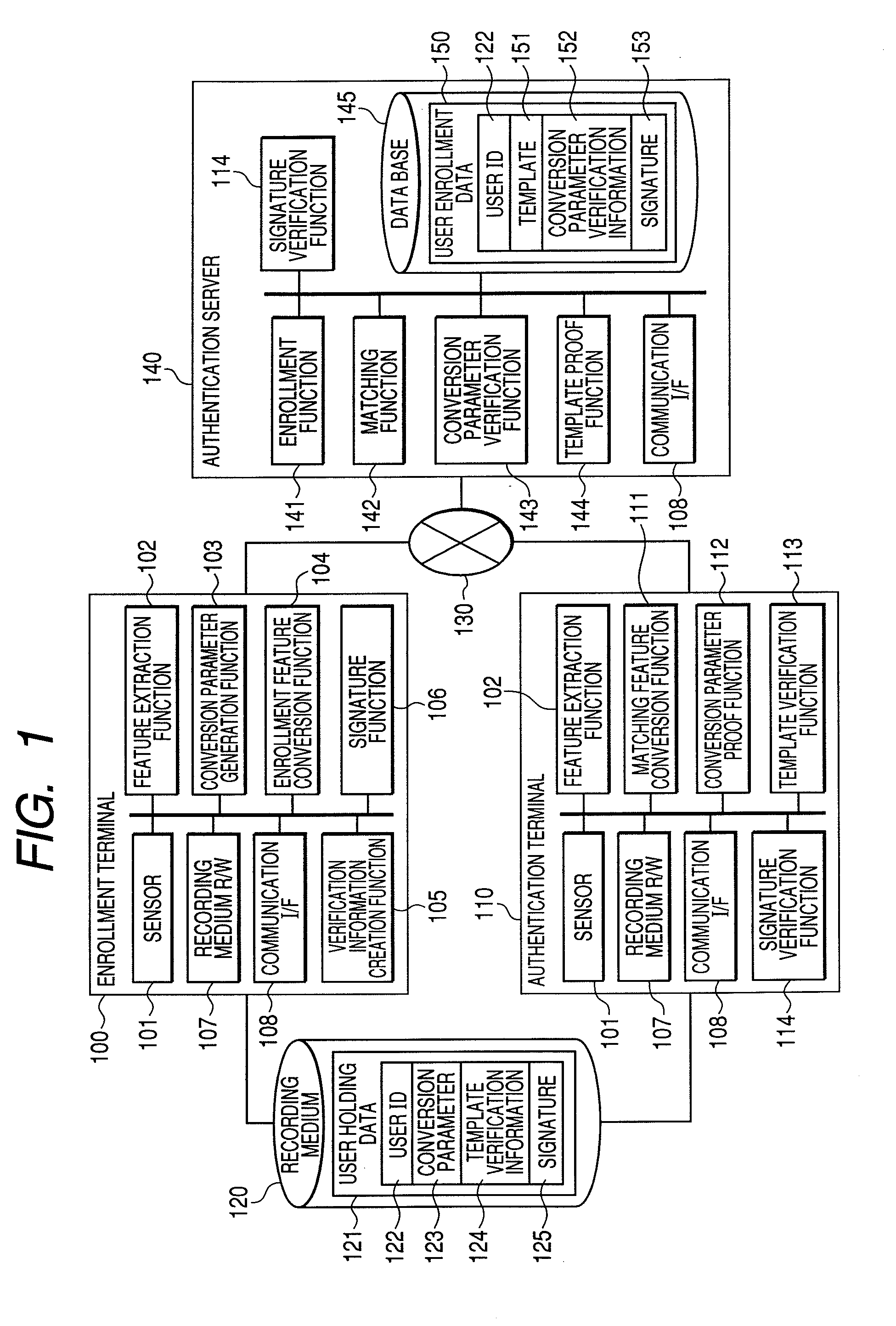
Biometric authentication system, enrollment terminal, authentication terminal and authentication server
ActiveUS20080178008A1Reduce threatDigital data processing detailsUser identity/authority verificationTemplate matchingAuthentication system
The present invention captures user's biometric data during enrollment and converts it by a given conversion parameter to create a template. It creates verification information for the conversion parameter, and enrolls it in an authentication server together with the template. The conversion parameter is stored in an IC card or the like for issuance to the user. During authentication, the authentication server verifies that the authentication terminal knows the conversion parameter, using conversion parameter verification information. Next, the authentication terminal converts user's biometric data newly captured by a conversion parameter to create matching information, and transmits it to the authentication server. The authentication server matches the matching information with the template to determine whether the user is a principal.
Owner:HITACHI LTD
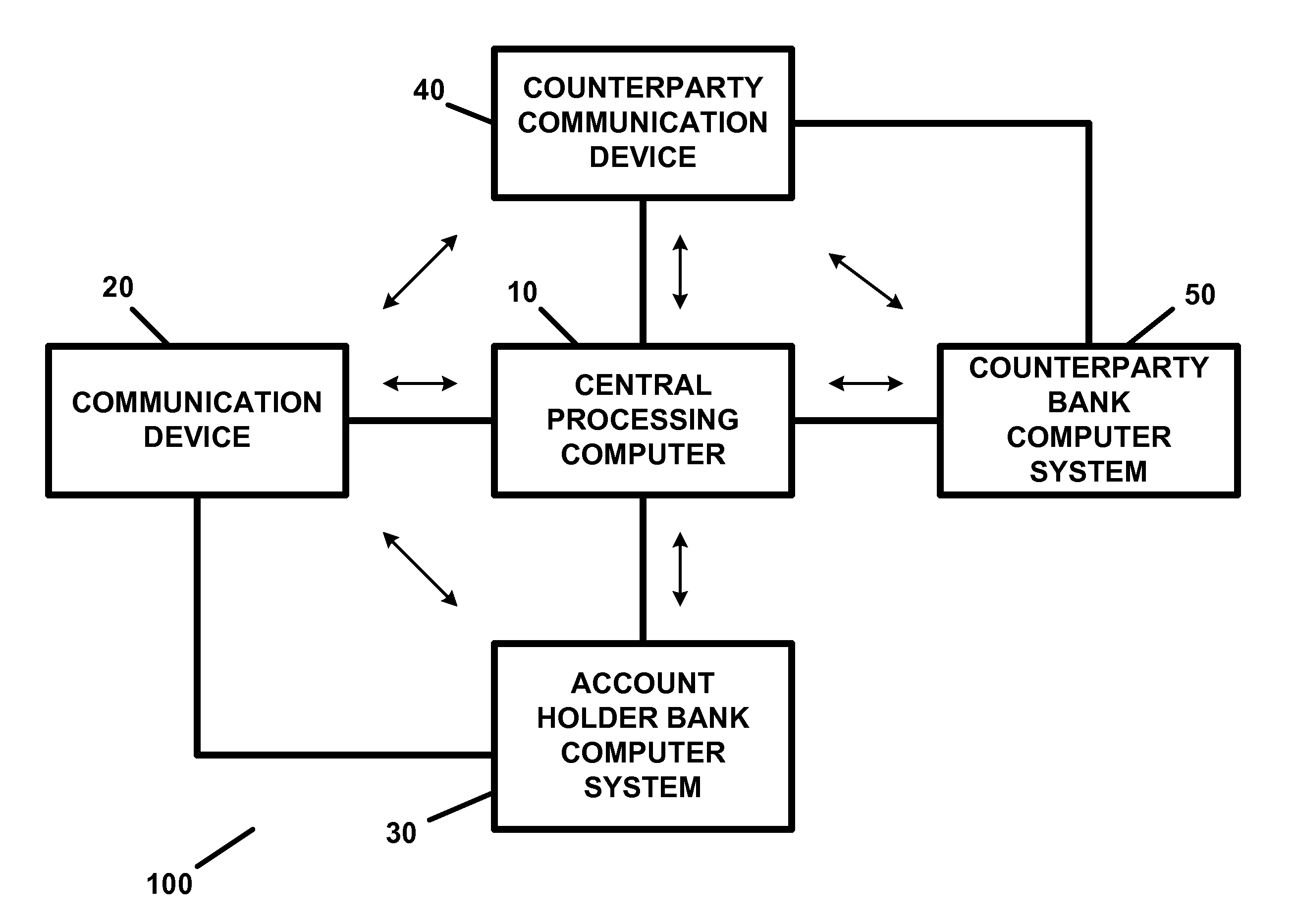
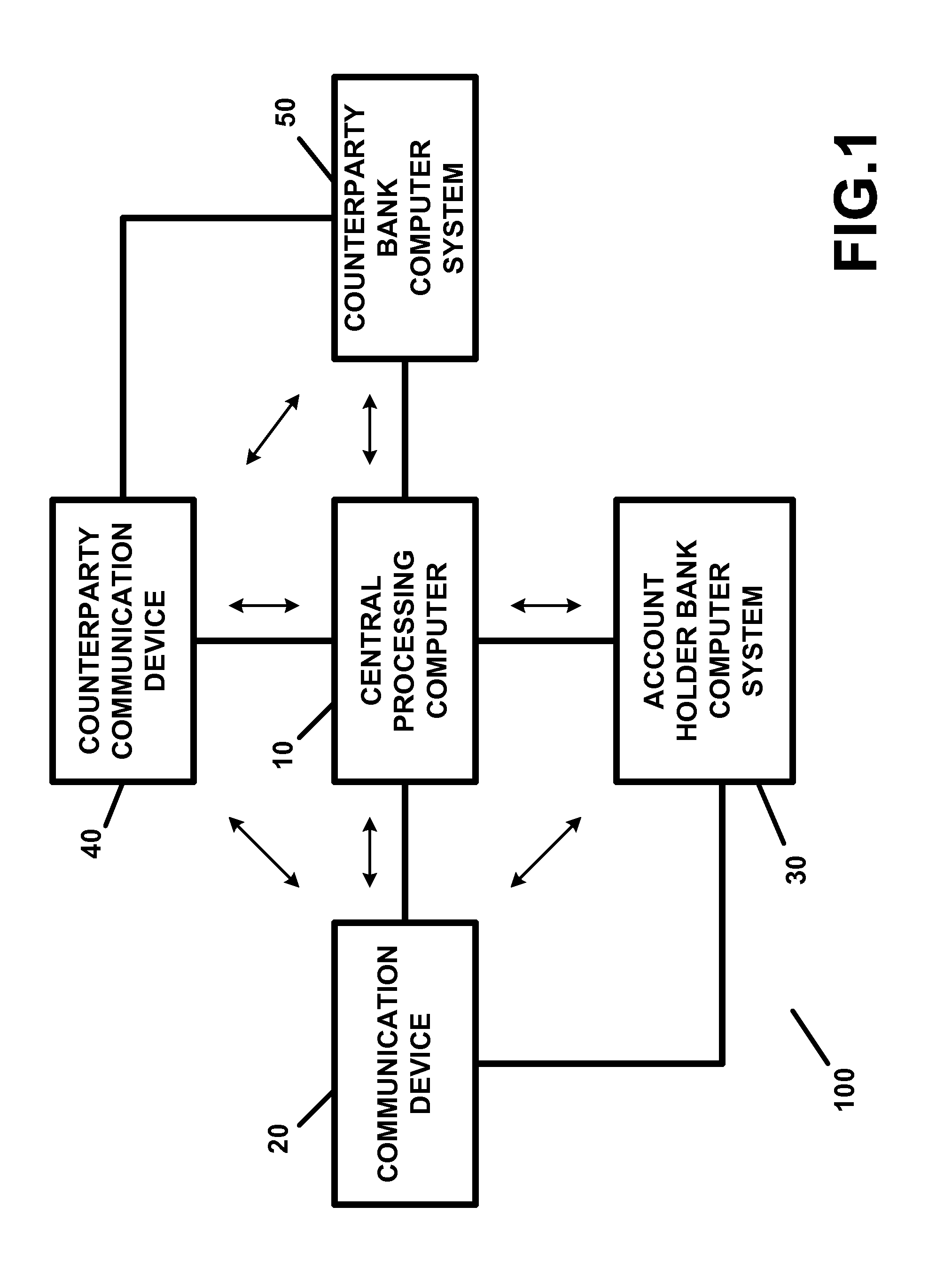
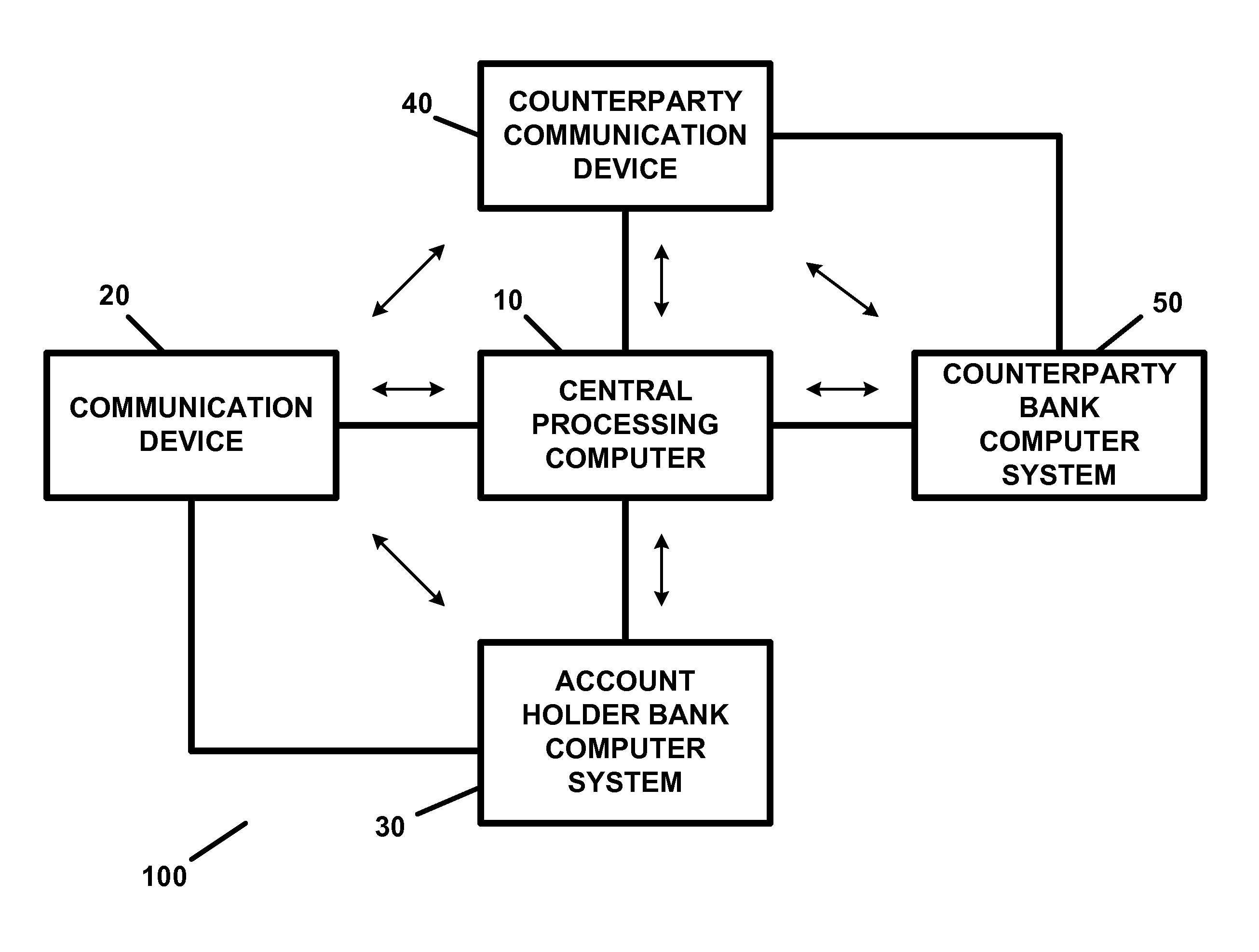
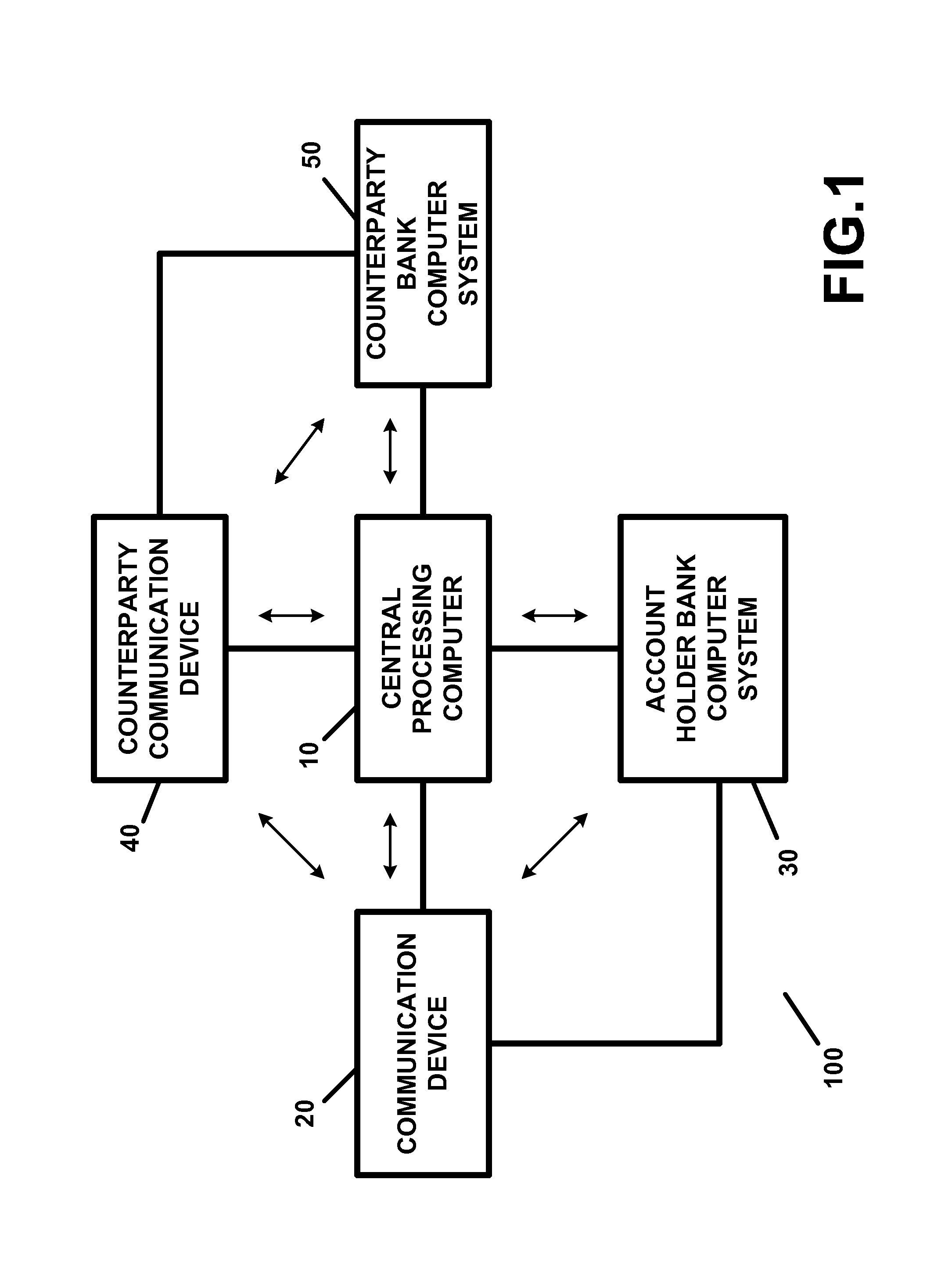
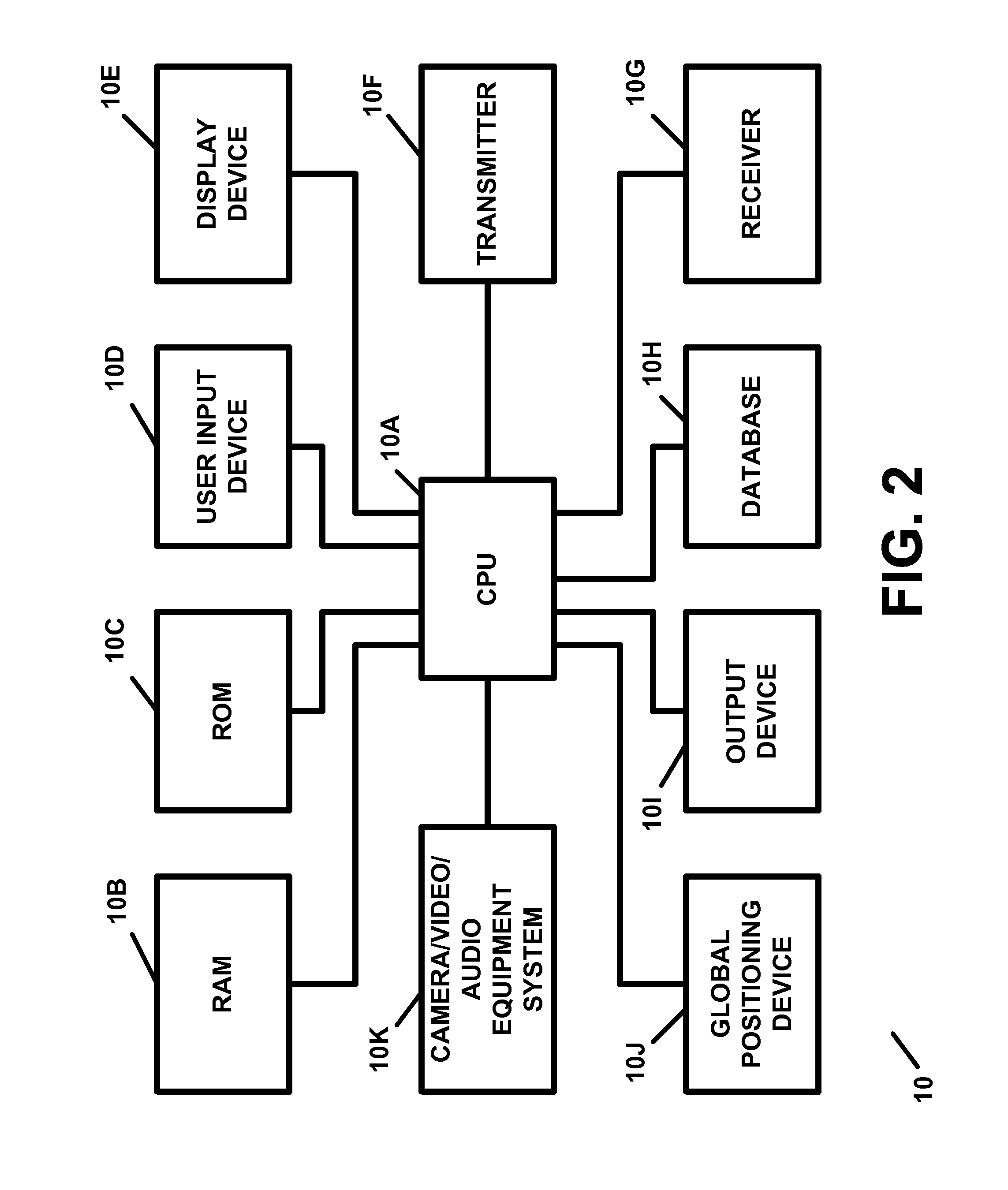
Apparatus and method for providing transaction security and/or account security
InactiveUS20150012417A1Reduce threatEasy accessFinancePayment protocolsTelecommunications linkInternet privacy
A transaction security apparatus, including a memory device for storing information regarding an account of or associated with an account holder, an input device or a receiver for inputting or for receiving transaction information regarding a transaction between the account holder and a counterparty, wherein the transaction is an in-person transaction or a face-to-face transaction, and wherein the transaction information includes information regarding the counterparty, information regarding an amount of the transaction, and information for accessing a communication device associated with the counterparty, a processing device, wherein the processing device processes the transaction information and generates a message containing information regarding the account, and further wherein the apparatus establishes a communication link with the communication device, and a transmitter, wherein the transmitter transmits the message to the communication device on, over, or via the communication link.
Owner:JOAO RAYMOND ANTHONY +1
Disinfecting caps and systems and associated methods
ActiveUS20120039764A1Reduce threatPrevent protrudingDiagnosticsClosure capsBiomedical engineeringMedical treatment
Caps can be used to cover and disinfect a male protrusion portion of a medical connector. Some caps can create a seal with the male protrusion to prevent antiseptic from entering a lumen the protrusion. A biasing element can aid in creating or maintaining the seal.
Owner:MERIT MEDICAL SYST INC
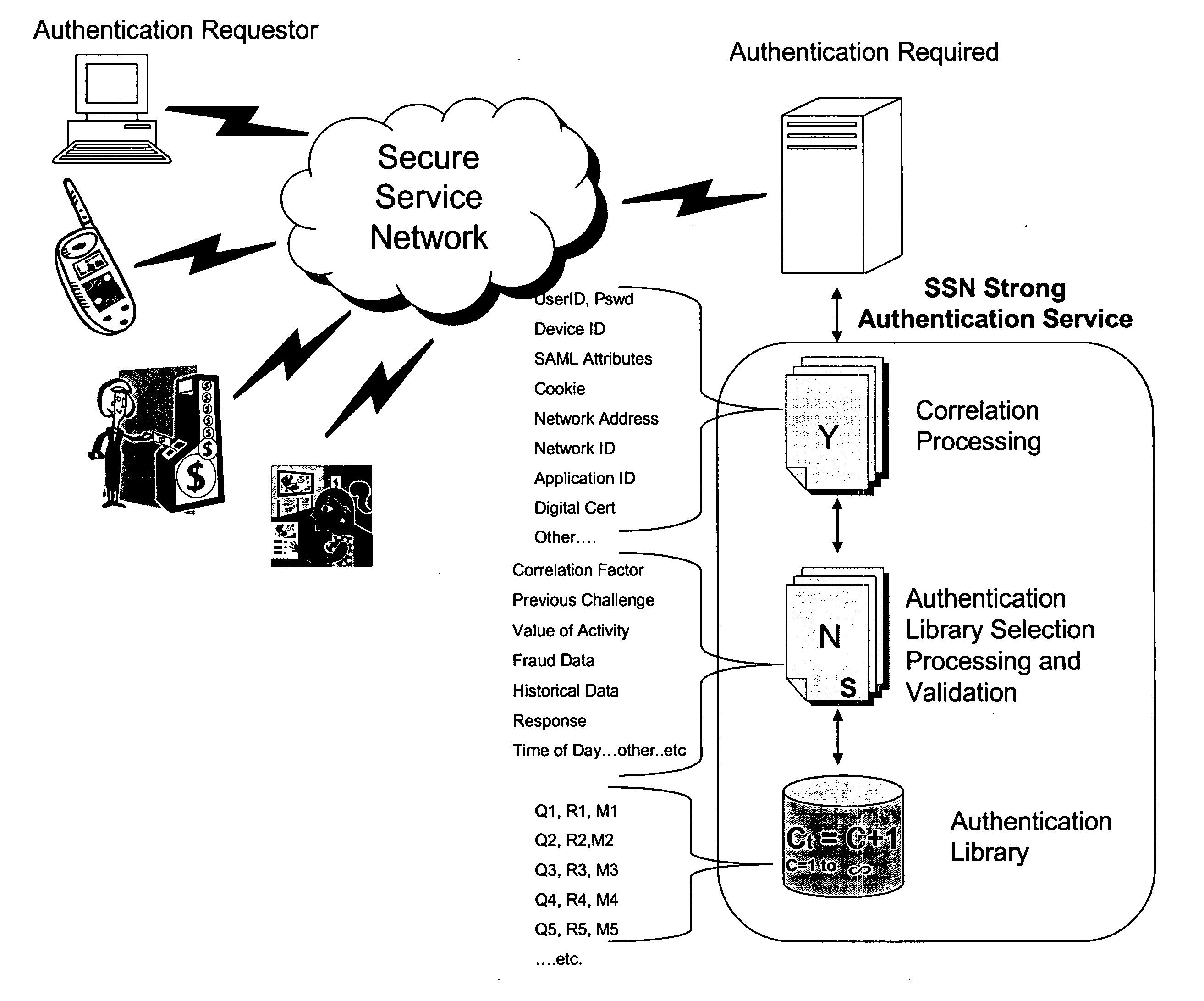
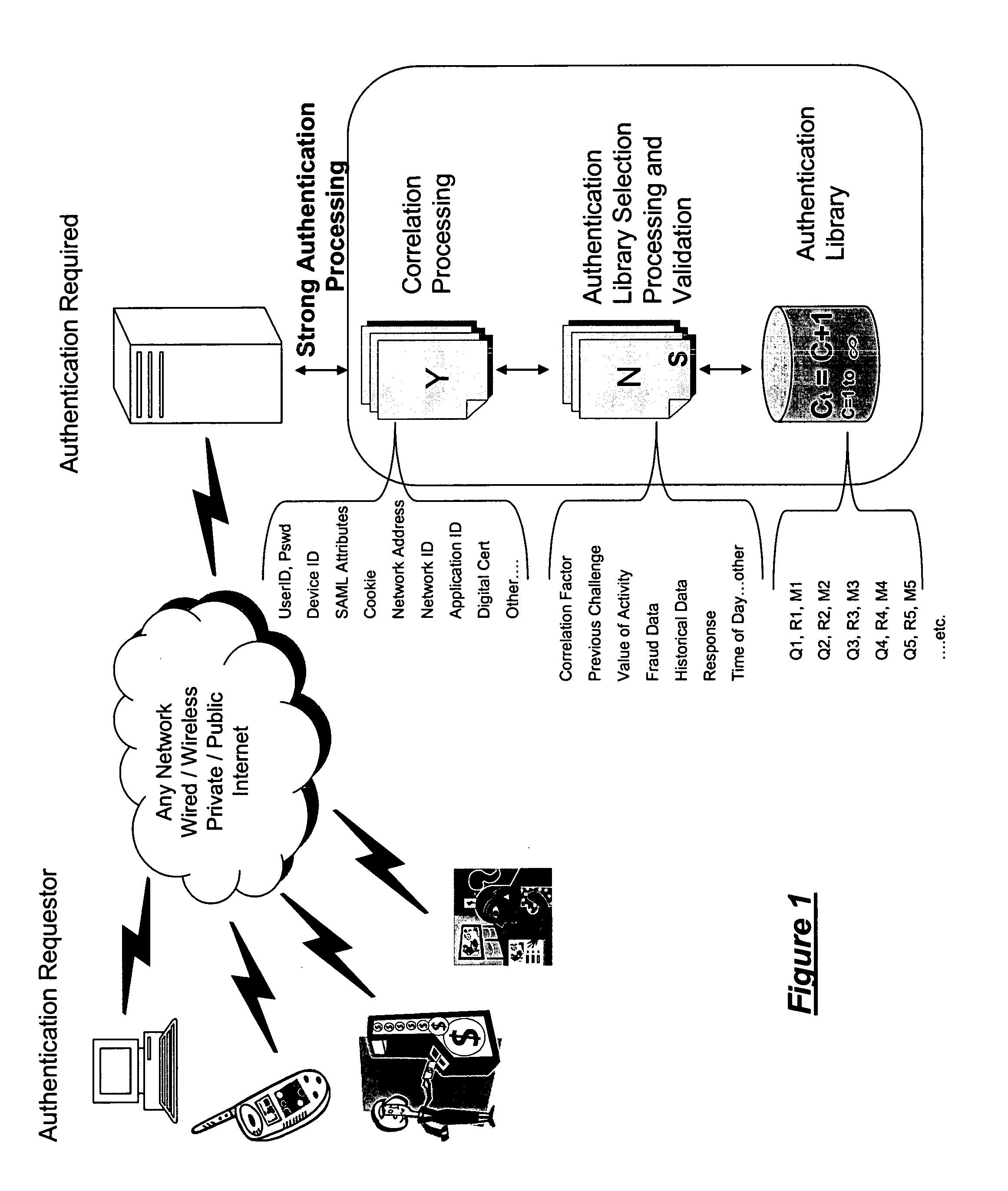
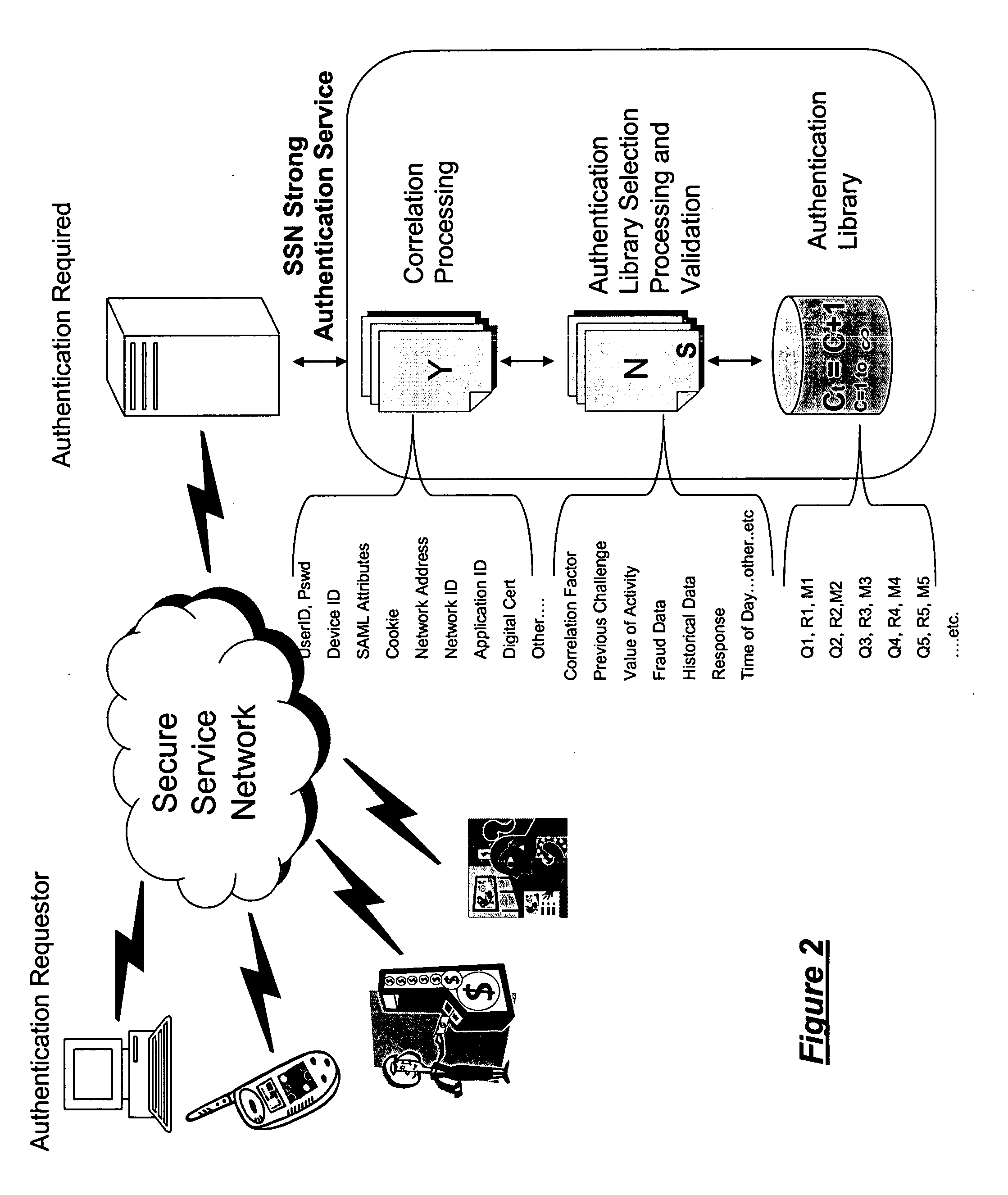
Common authentication service for network connected applications, devices, users, and web services
ActiveUS20070186103A1Reduce threatLimited abilityUser identity/authority verificationPayment architectureStrong authenticationWeb service
System architecture for network connected applications, devices, users, and web services providing security effected by means for managing interaction with an authentication library that effects a correlation between the use and creation of library entries having predetermined correlation indicia for effecting strong authentication of users and participants within the network. A common authentication service (CAS) based upon an XML or web services protocol is described.
Owner:RANDLE WILLIAM M +1
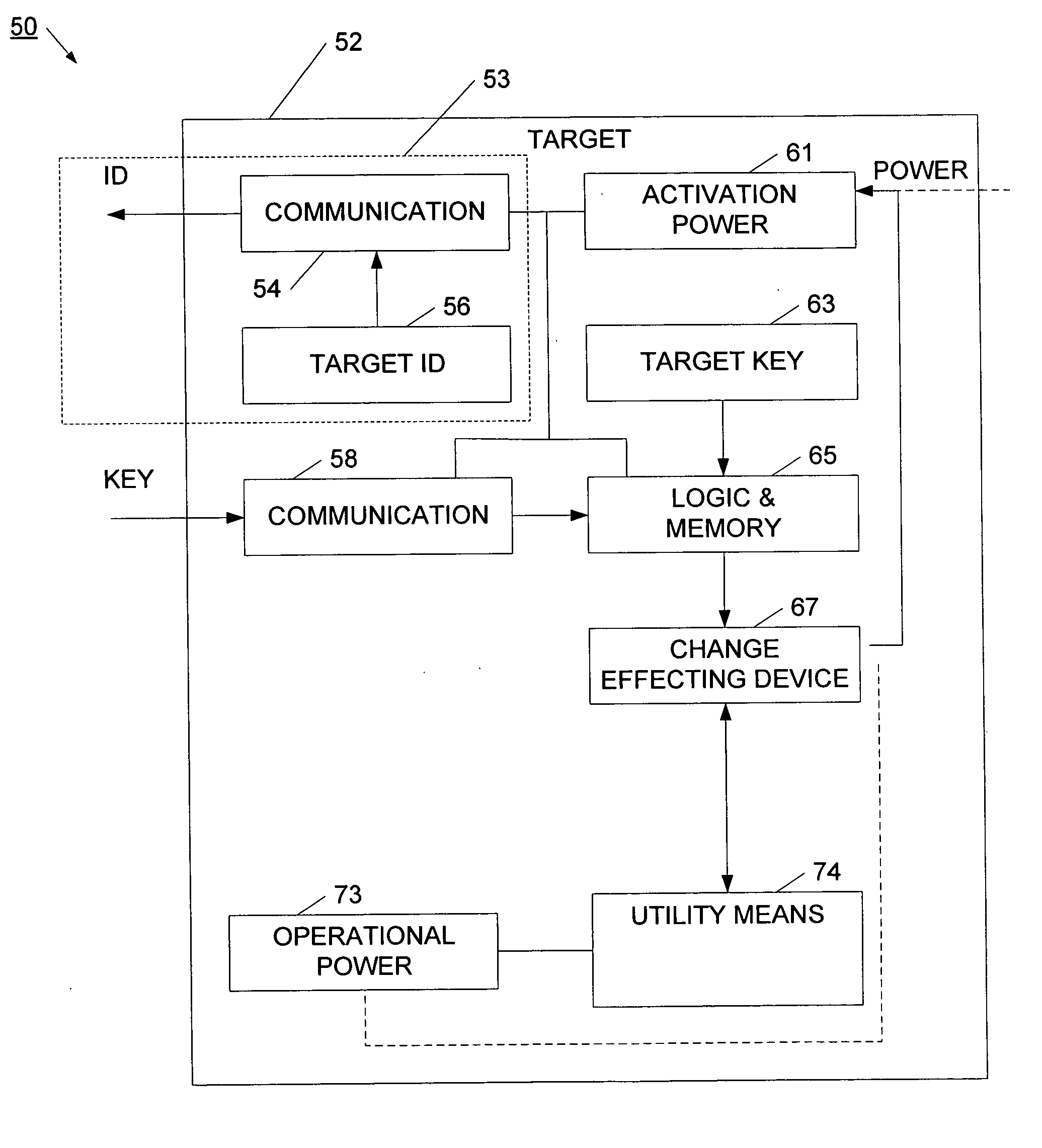
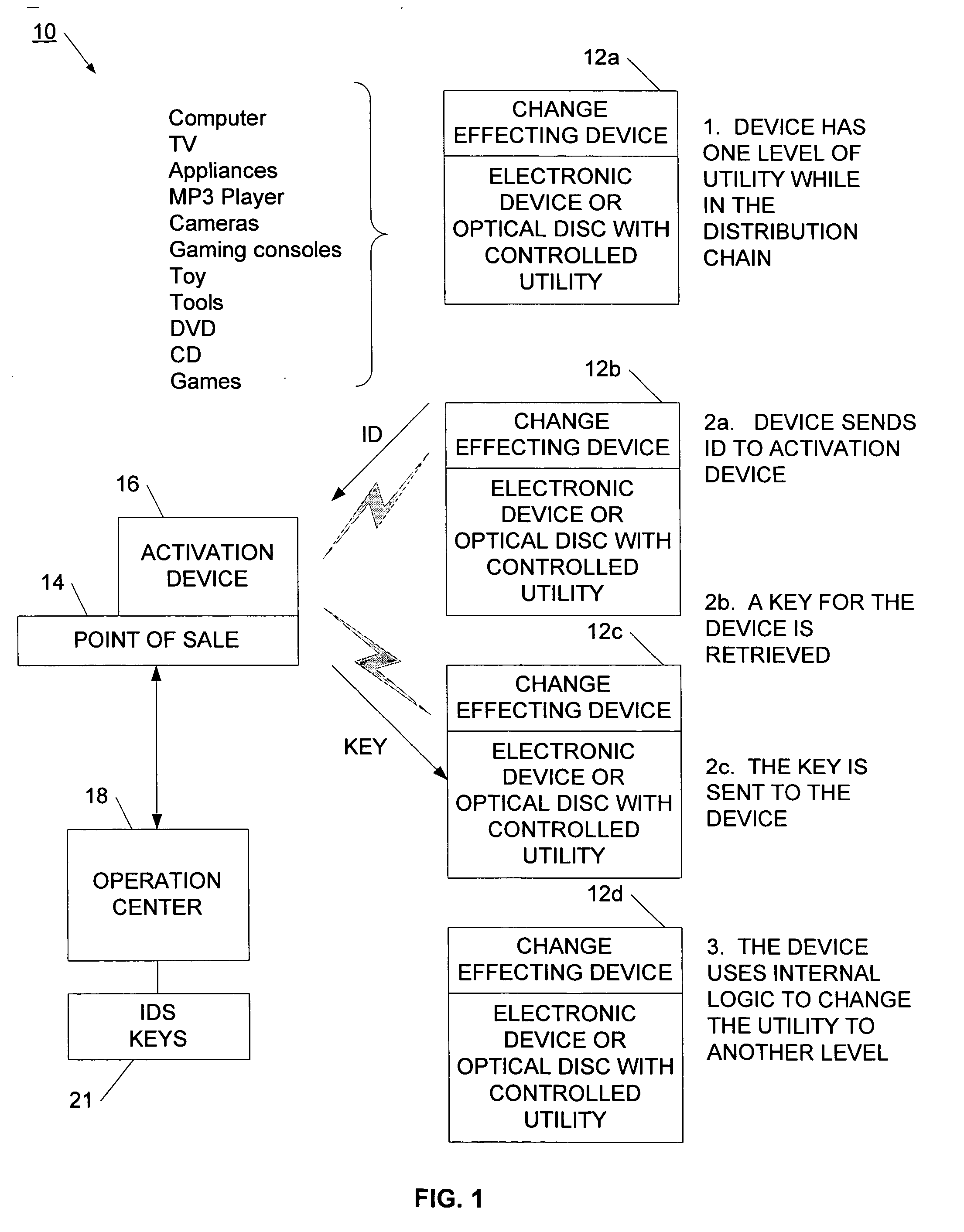
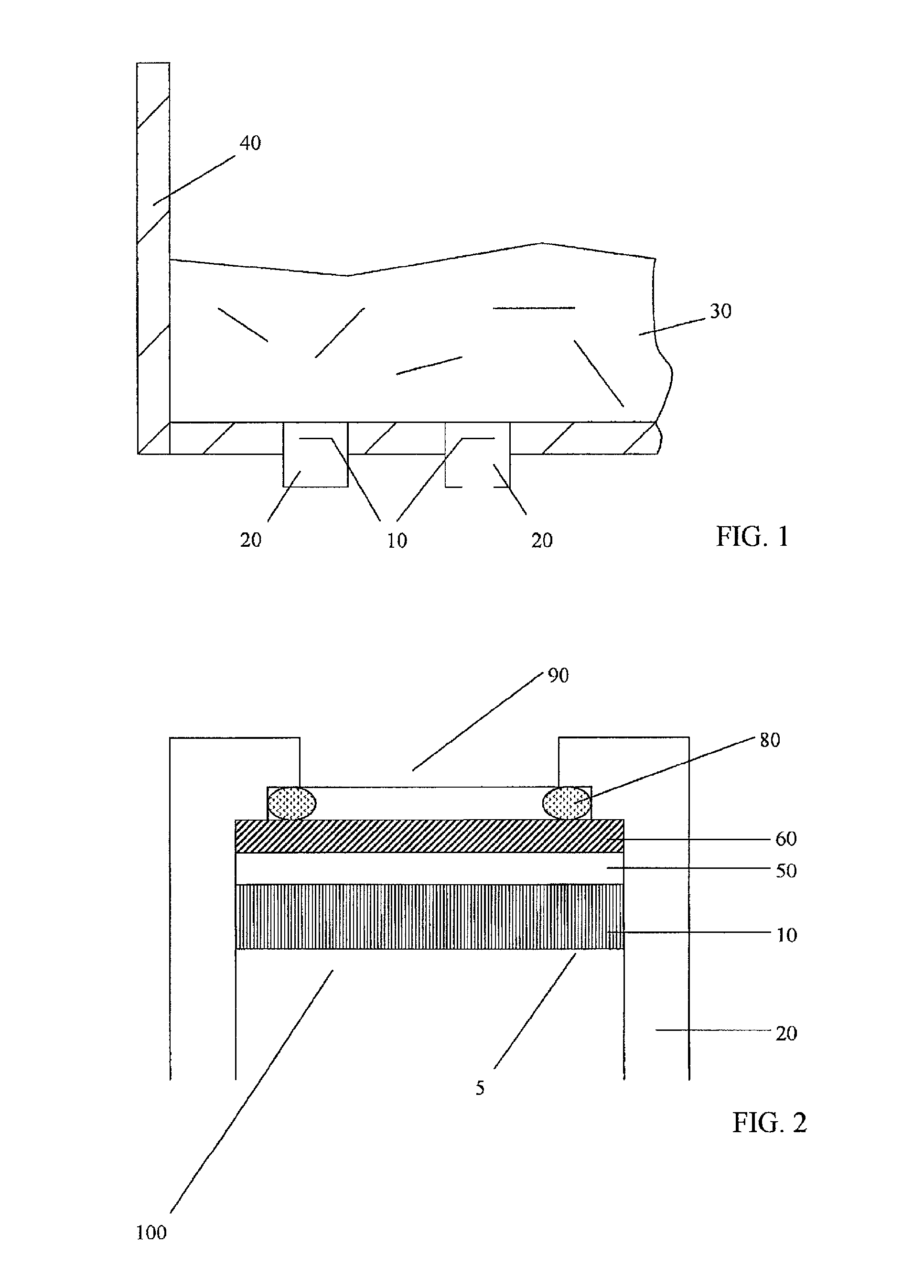
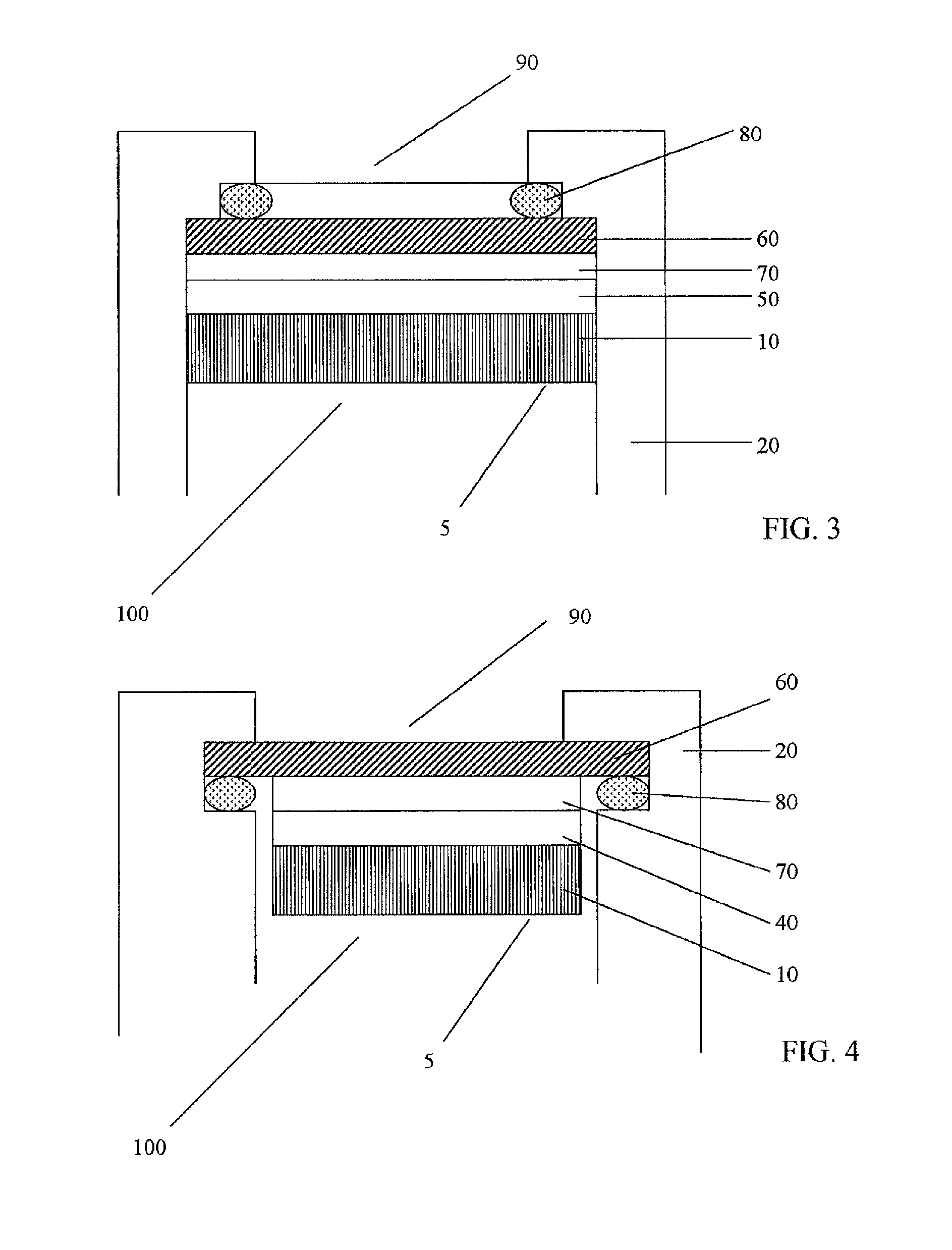
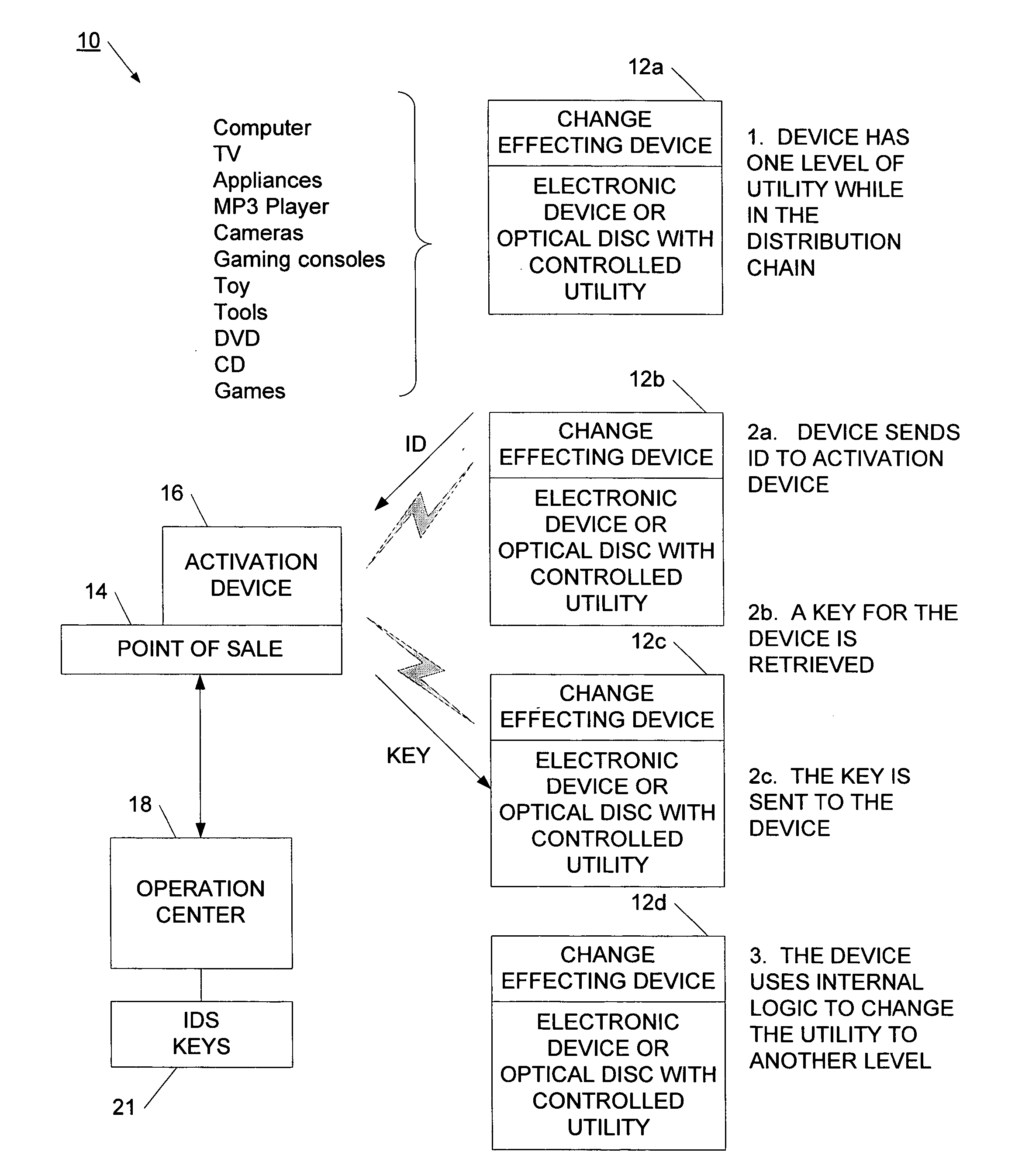
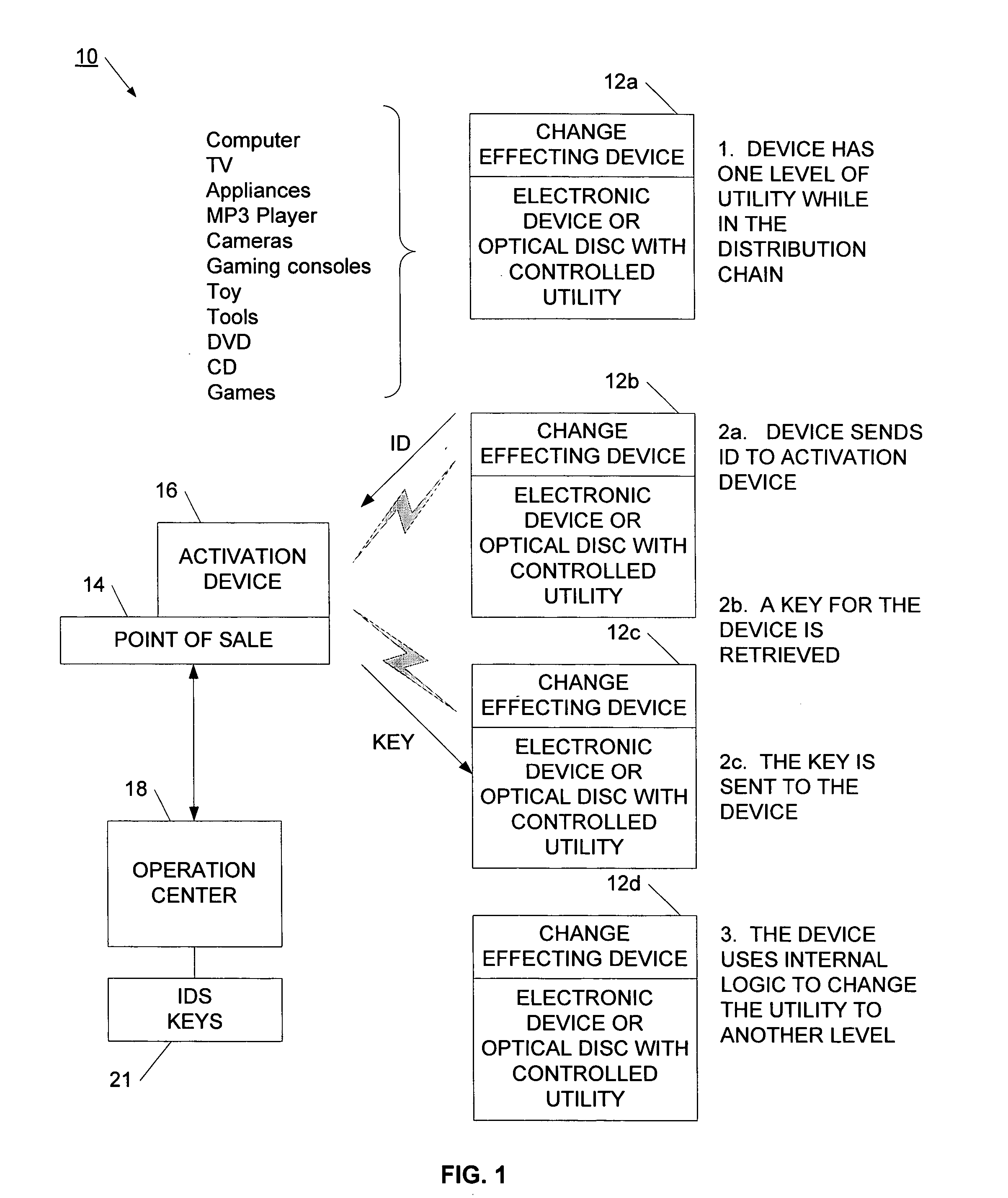
Method and network for selectively controlling the utility a target
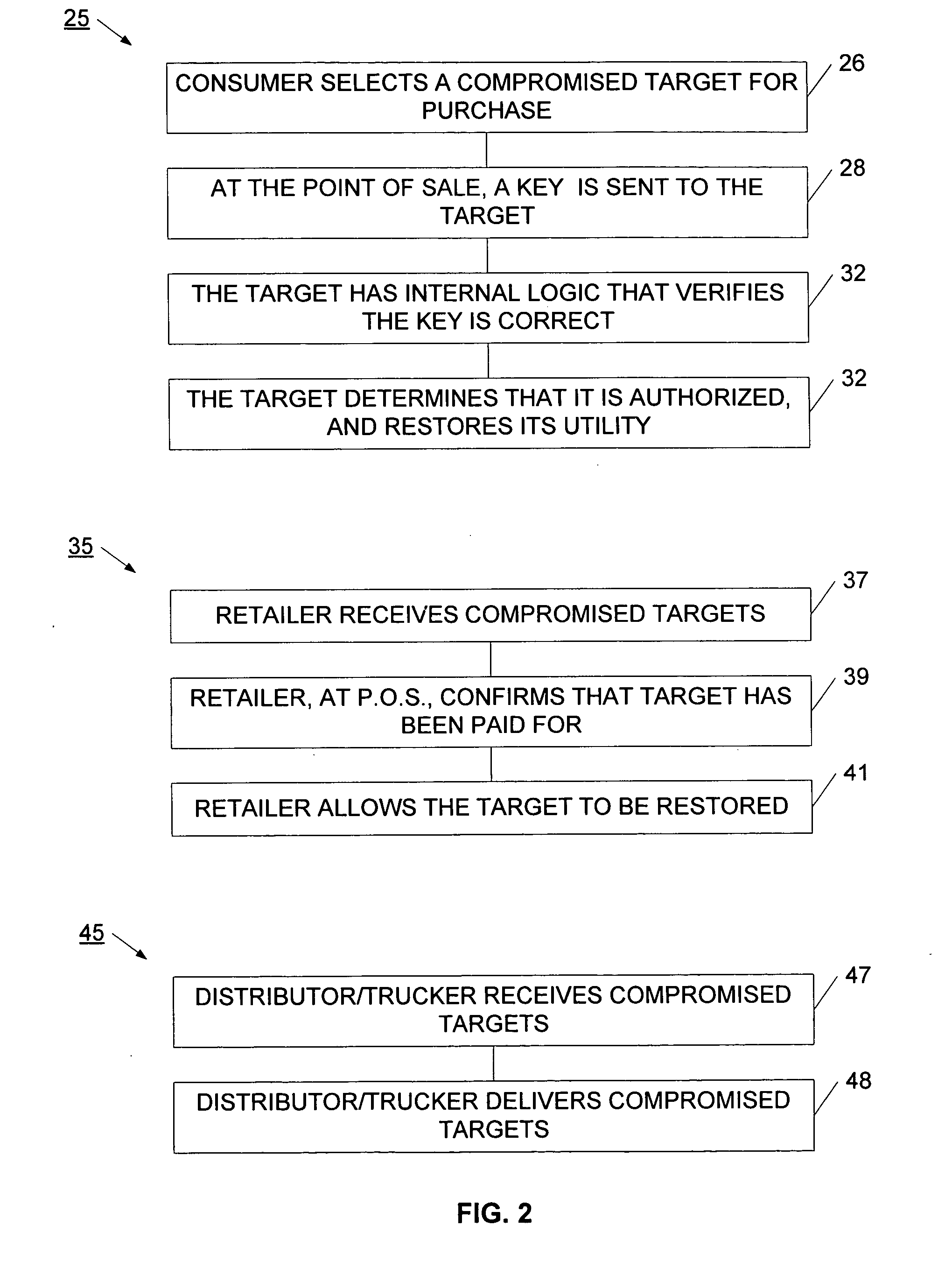
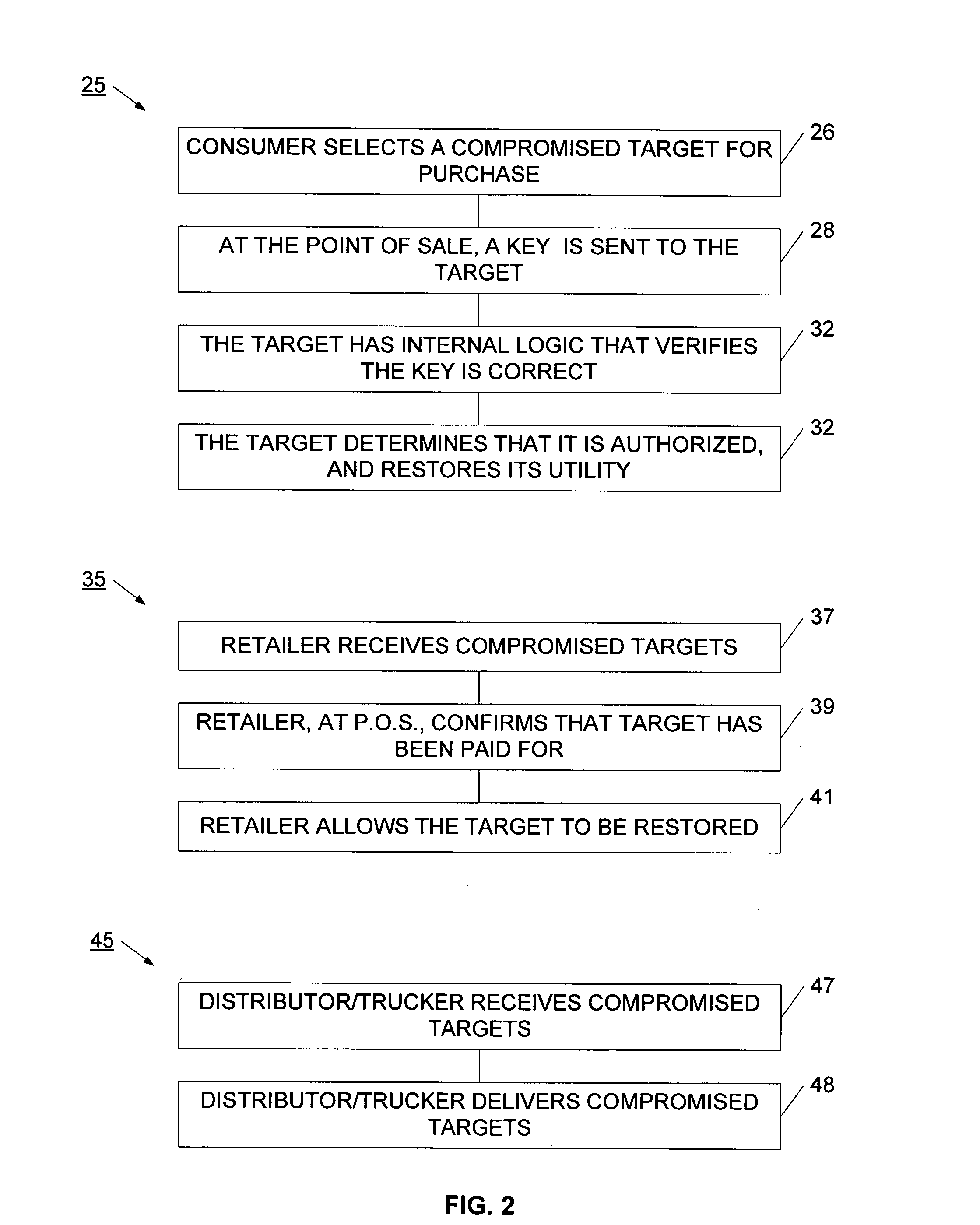
InactiveUS20060095385A1Reduce threatCompromise their utilityIndoor gamesUser identity/authority verificationDistribution controlBiological activation
A distribution control system is provided to support the controlled and selective changing of utility for a target. The target with controlled utility may be an electronic device, or alternatively, may be a tangible media, such as an optical disc. The distribution control system has a target with a change effecting device and a restricted access key. An activation device retrieves or generates an authorization key, and sends the authorization key to the target. The authorization key may be sent to the target wirelessly, for example, using a radio frequency signal. The target has logic that uses the restricted access key and the authorization key to change the utility of the target. In one example, the activation device retrieves the authorization key from a network operation center (NOC) by sending a target identifier to the NOC, and the NOC retrieves the authorization key for the identified target. The activation device may also connect to other systems for obtaining approval to change the utility of the target. For example, the authorization key may be sent to the target upon receiving payment, password, or other confirmation.
Owner:RPC IP HLDG
Network connection detection and throttling
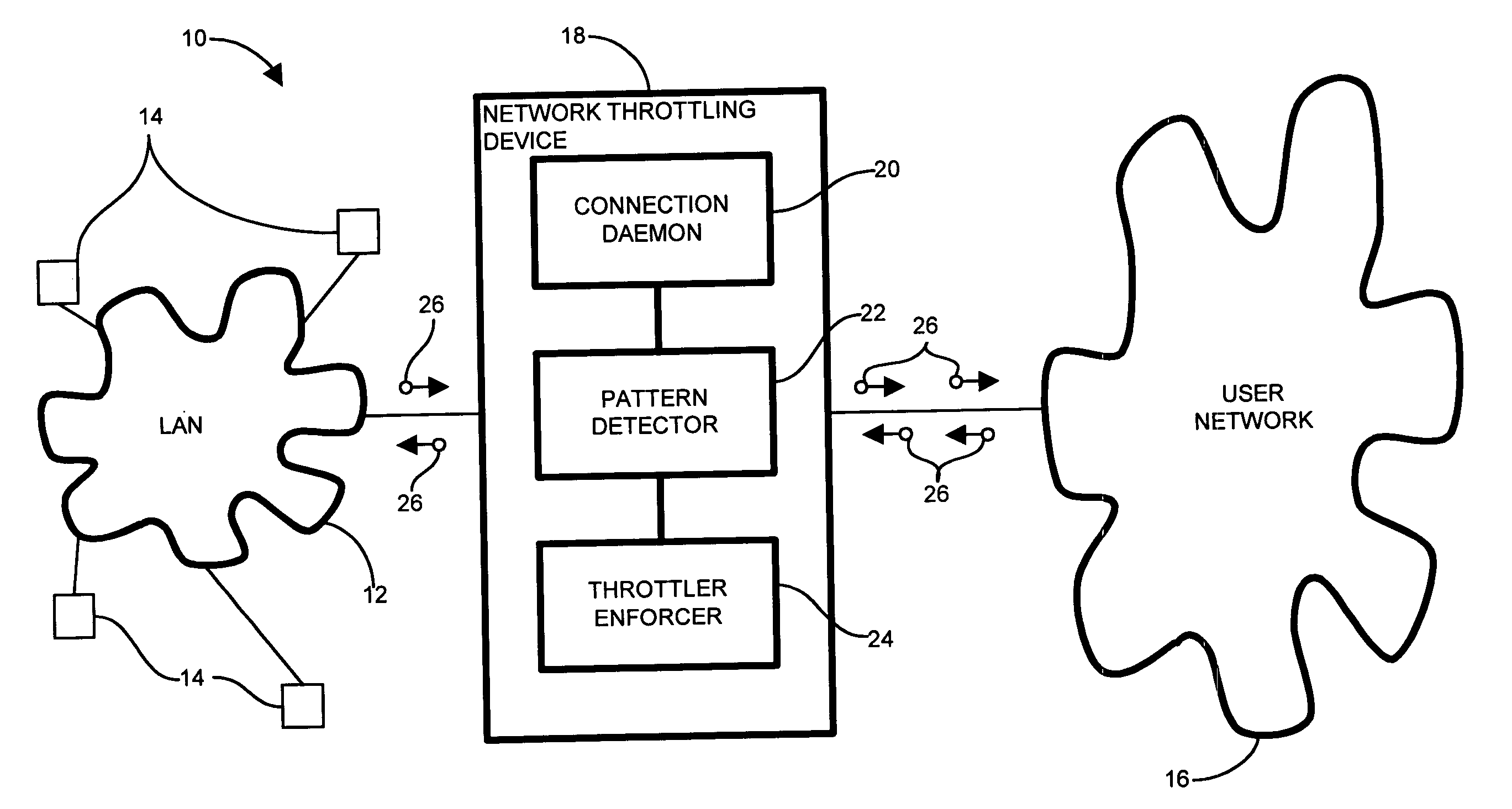
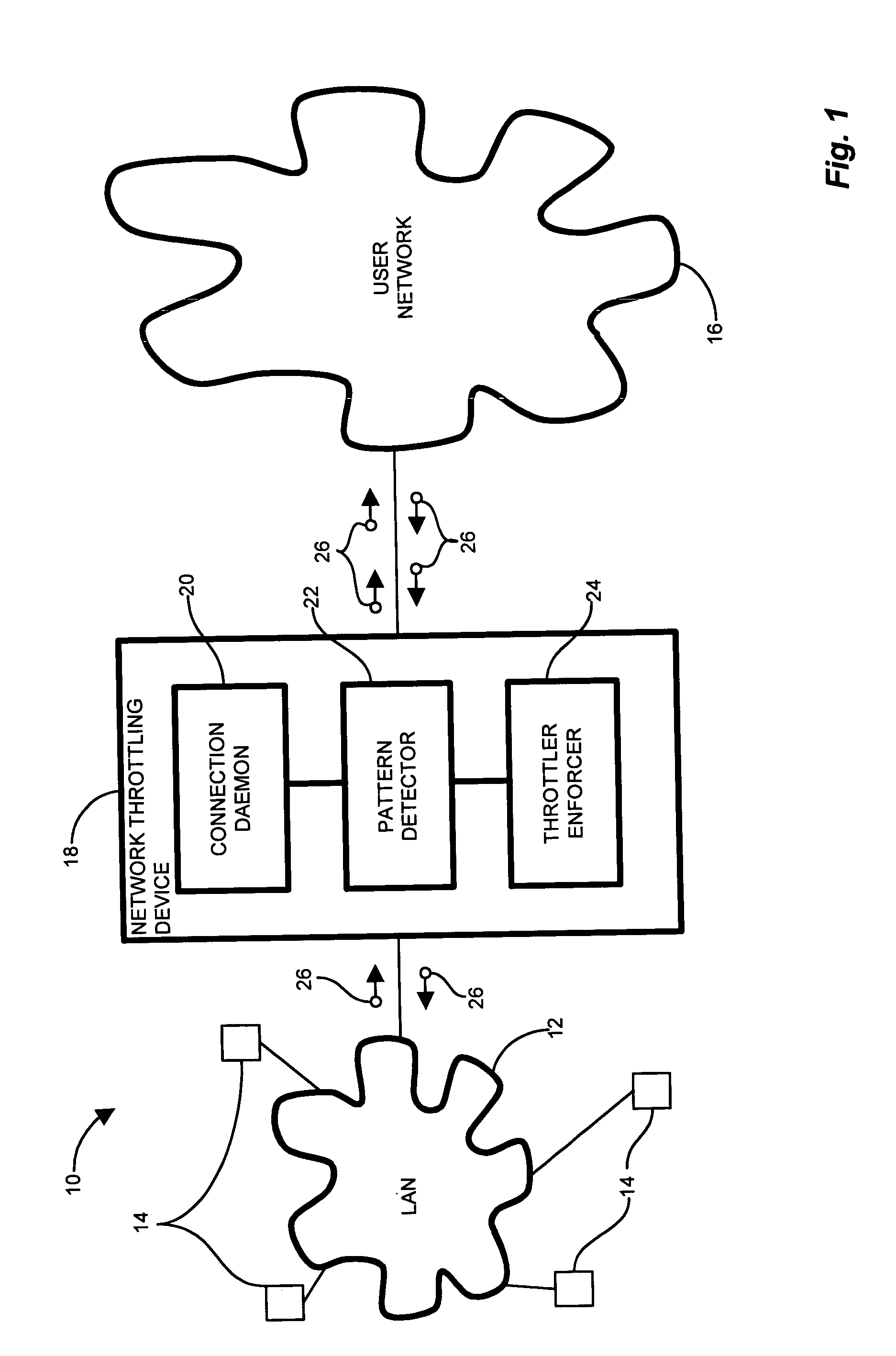
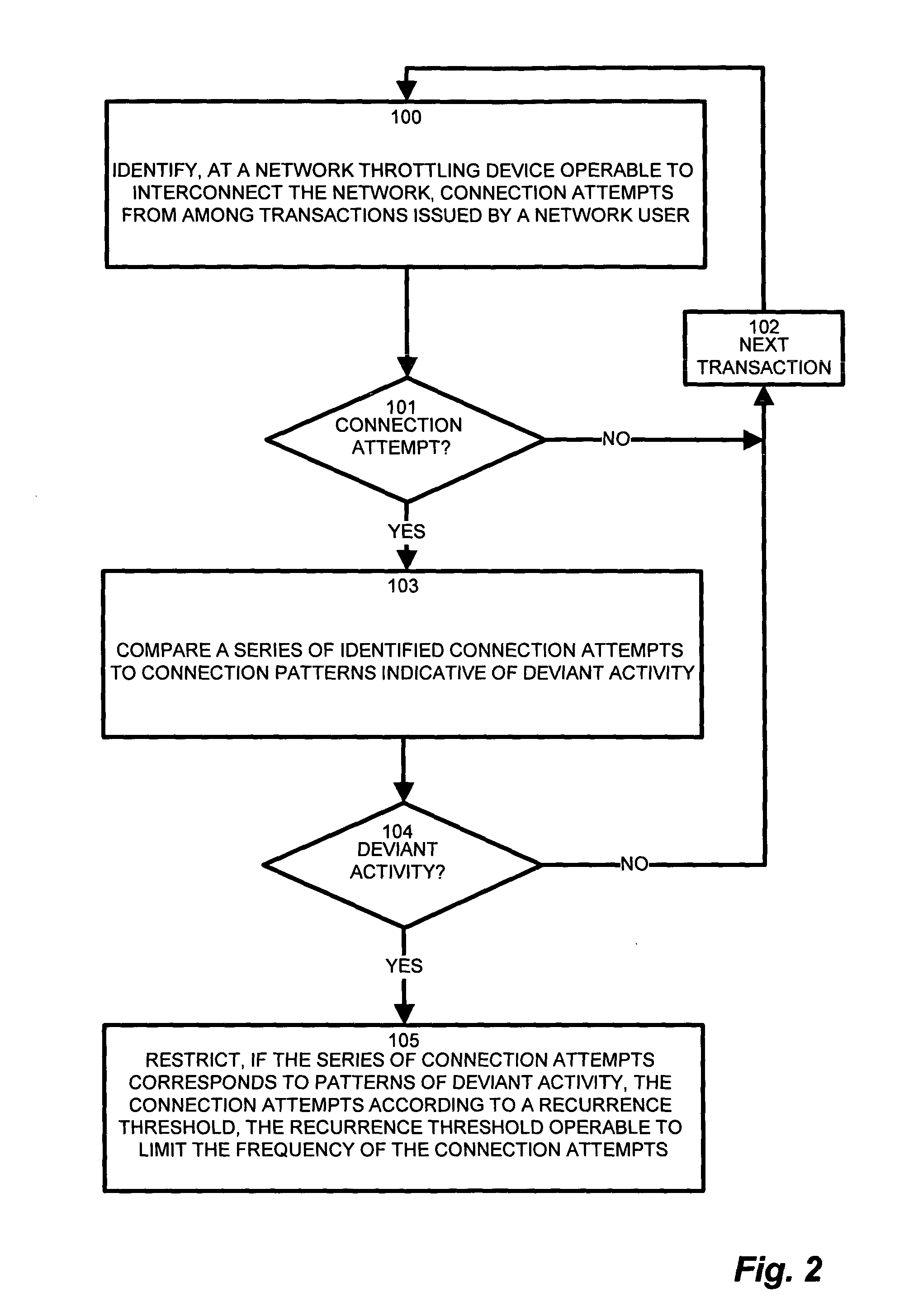
InactiveUS7814542B1Reduce harmful effectsMinimize activityMemory loss protectionUnauthorized memory use protectionPattern detectionNetwork connection
In an edge network, message traffic between the edge network and a core network passes through the edge router. A port scanning attack directed to the network as a whole (core network) potentially emanates from within the LAN. The edge router includes a network throttling device which identifies and mitigates harmful transmissions such that they do not propagate to the core network. The network throttling device has a connection daemon to scan transactions and determine deviant or atypical connection attempts. A session database stores a transaction history representing a window of previous connection attempts. A pattern detector examines the history and looks for malicious behavior. Identified deviant patterns cause a throttler enforcer to limit the triggering user by restricting future connection attempts, thus mitigating harmful effects. Usage, therefore, is not prevented, but resilience to deviant practices is provided. Accordingly, virus propagation via port scanning is mitigated to a safe level and false alarms targeting legitimate activity are minimized.
Owner:CISCO TECH INC
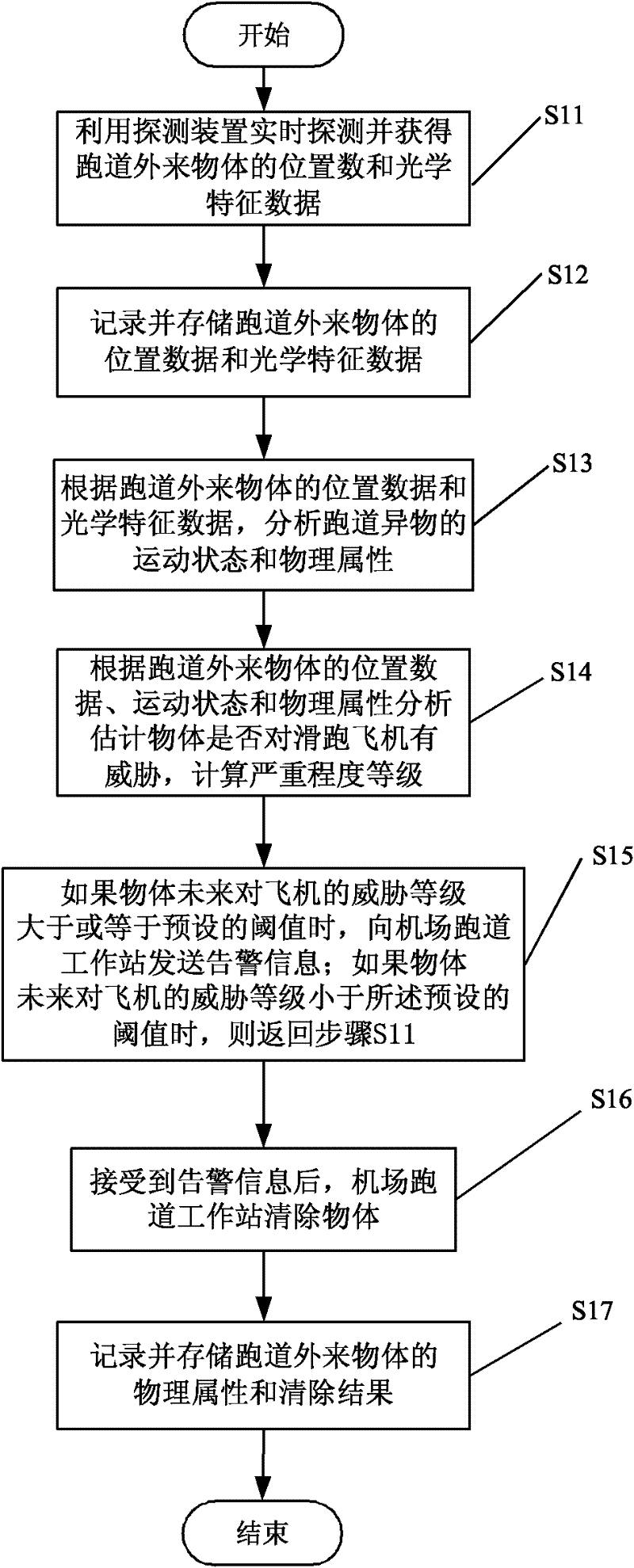
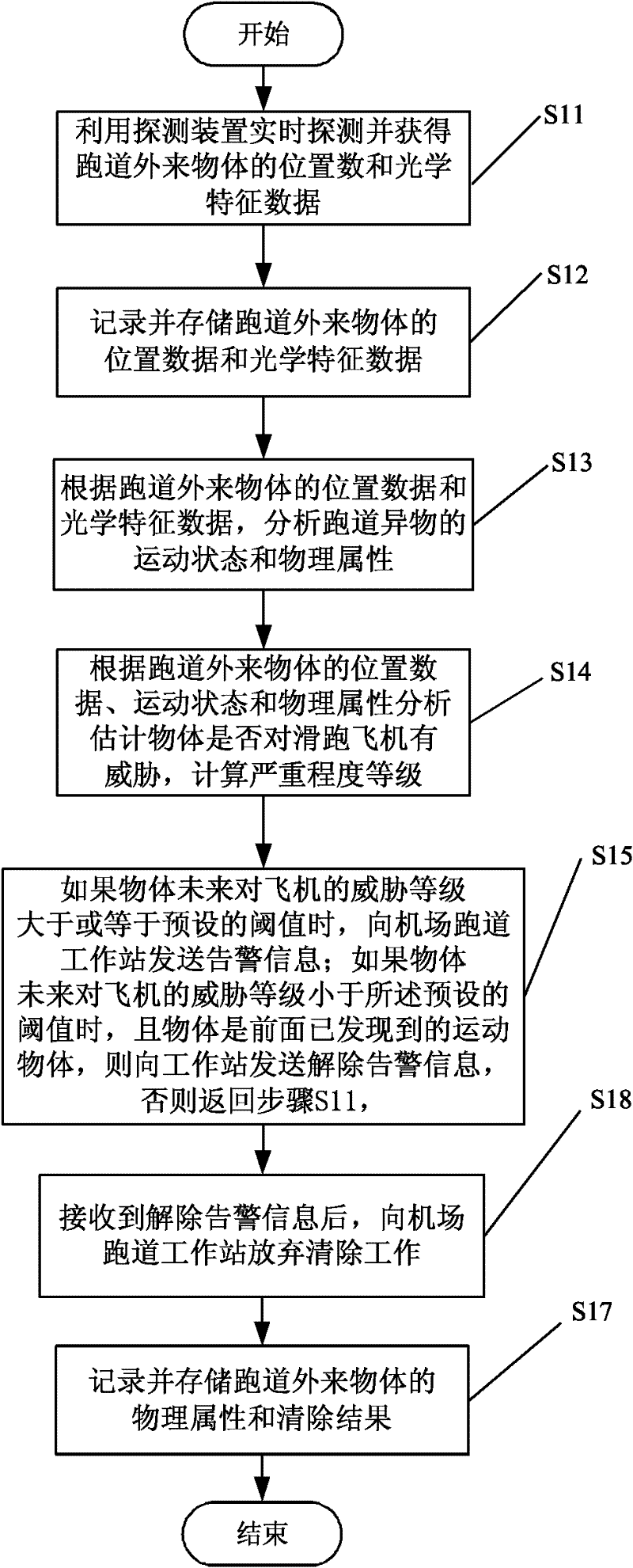
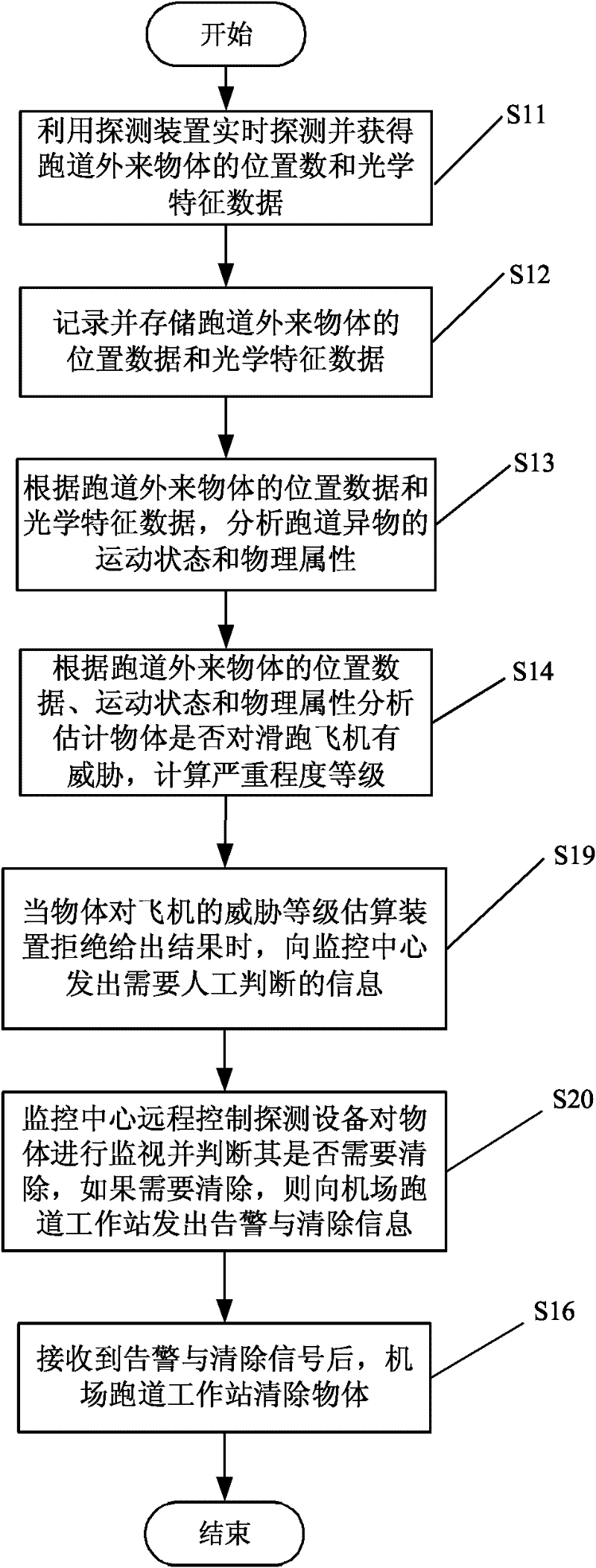
System and method for automatically detecting foreign object debris (FOD) on airfield runways
ActiveCN102253381AReduce threatRadiation pyrometryRadio wave reradiation/reflectionAutomatic controlAirplane
The invention provides a system and method for automatically detecting foreign object debris (FOD) on airfield runways, belonging to the technical field of automatic control of aviation. The system comprises a detector, an optical characteristic database, an FOD database, an object motion state analysis device, an object physical attribute analysis device, an estimation device of threat severity grade of the object towards the airplanes, an alarm device, a remote monitoring device and a workstation removing device. By the system and the method, all-day, all-weather and full-automatic detection, identification and alarm can be carried out on the FOD targets and the accuracy of automatic detection and alarm can be substantially improved.
Owner:SHANGHAI CAMA OPTOELECTRONICS EQUIP
Apparatus and method for providing transaction security and/or account security
InactiveUS20160086187A1Reduce threatEasy accessFinanceWireless commuication servicesTelecommunications linkBarcode
An communication apparatus, including a memory which stores information regarding a first account of an individual account holder, a barcode, or QR code, reader which reads or obtains information regarding a merchant involved in a transaction involving the first account, wherein the merchant information is input into the apparatus; a camera which obtains a picture or photograph of a party involved in the transaction; a processor which generates an authorization request containing information read or obtained by the barcode, or QR code, reader and information regarding the first account, wherein the processor or the apparatus initiates and establishes a communication link with a transaction authorization computer associated with an issuer or servicer of the first; and a transmitter which transmits the authorization request message and the picture or photograph to the transaction authorization computer after the communication link is established. The apparatus is associated with the individual account holder.
Owner:JOAO RAYMOND ANTHONY
Suspicious act detecting method based on video analysis
ActiveCN102663452AReduce threatEasy to installCharacter and pattern recognitionHuman bodySocial benefits
The invention relates to a suspicious act detecting method based on video analysis. The method provided by the invention comprises the following three steps: detecting a human body objective, modeling according to track of the human body objective, and extracting and classifying features of the human body objective. The method provided by the invention adopts a computer-assisted means and a video analysis technology to intelligently detect suspicious acts in a monitoring video for timely detection and early warning, so that the threat of suspicious actions to a monitored place can be effectively reduced; and at the same time, the suspicious act detecting method provided by the invention is easy for installation and convenient to use and has obvious economic and social benefits.
Owner:NAT UNIV OF DEFENSE TECH
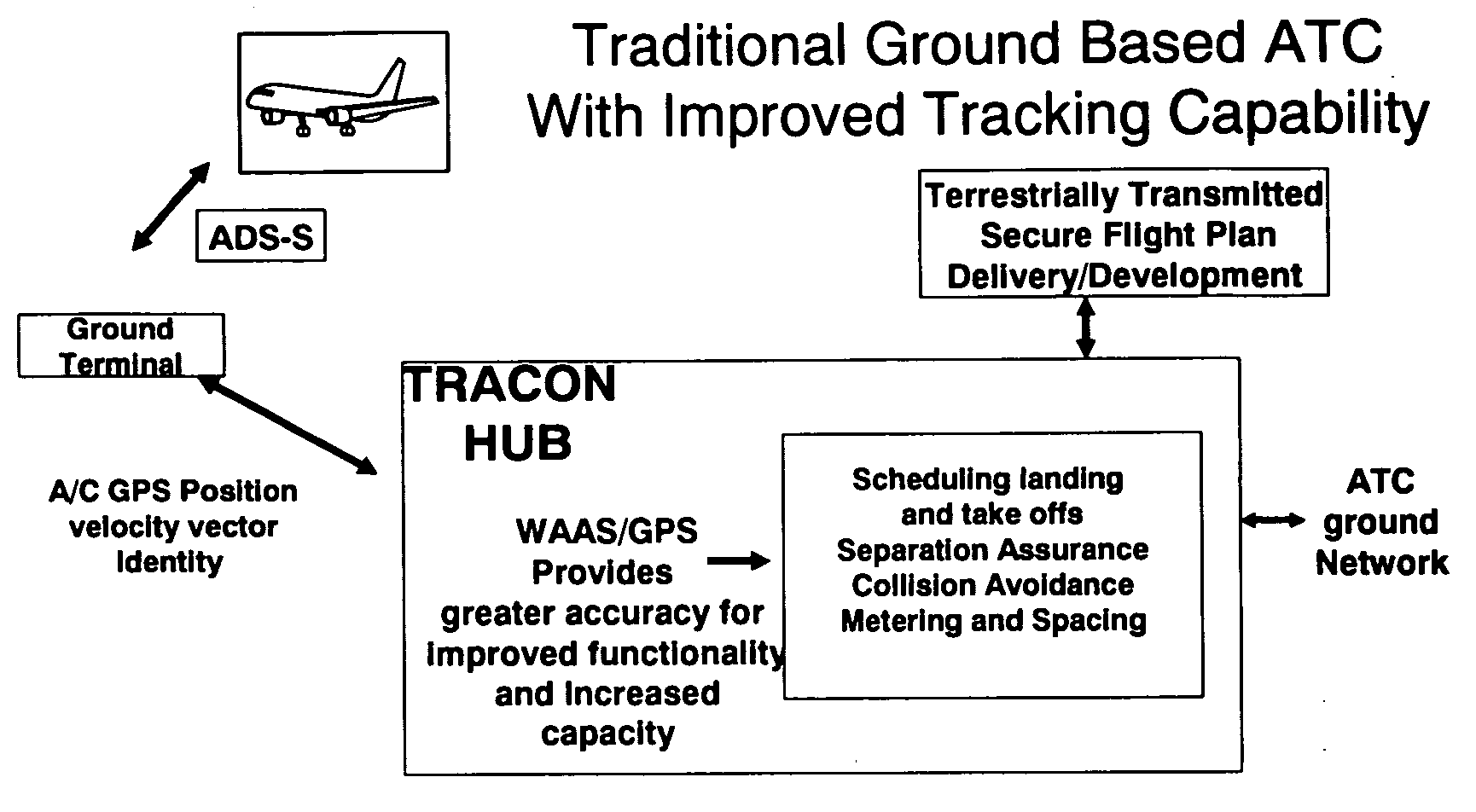
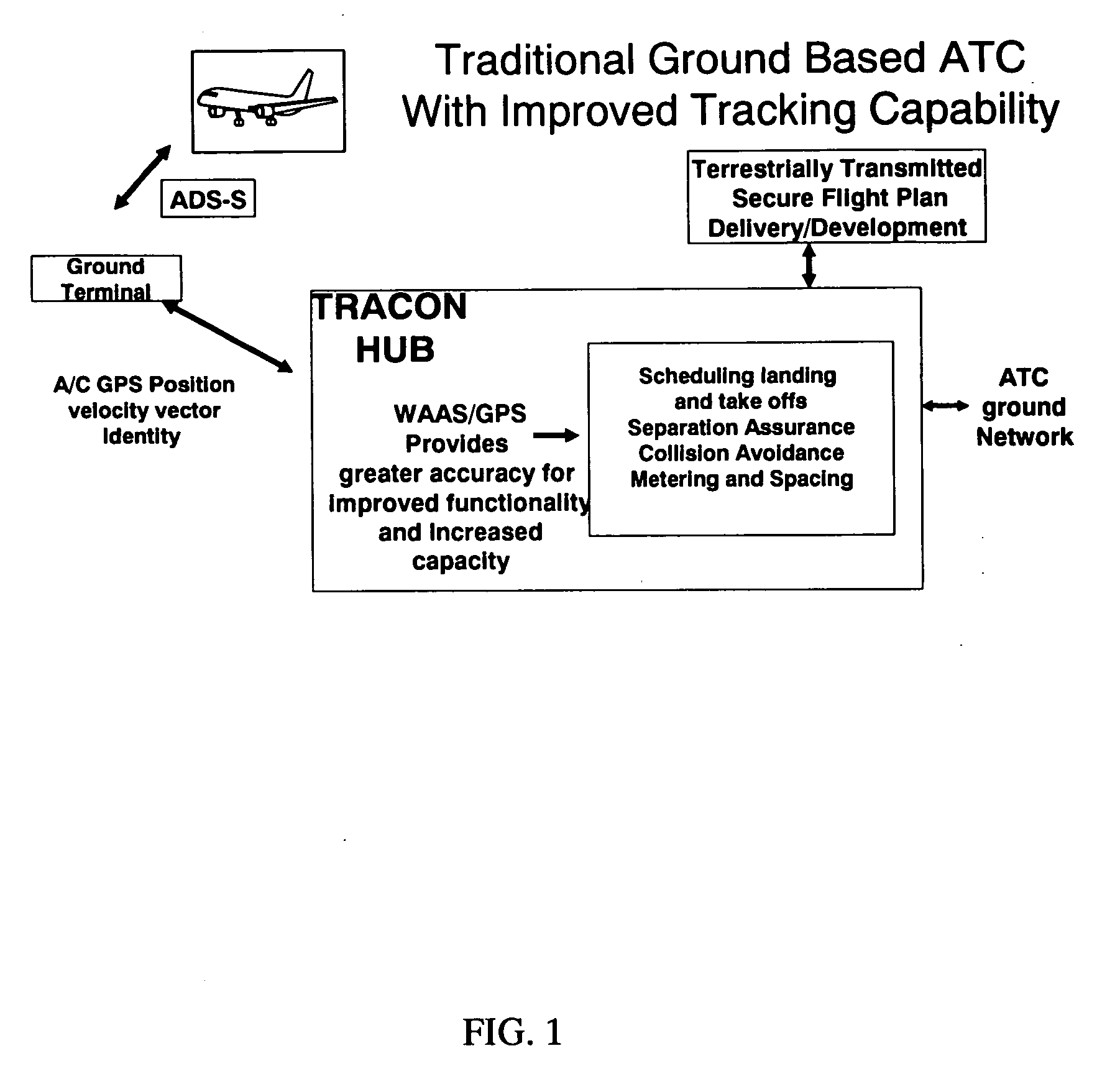
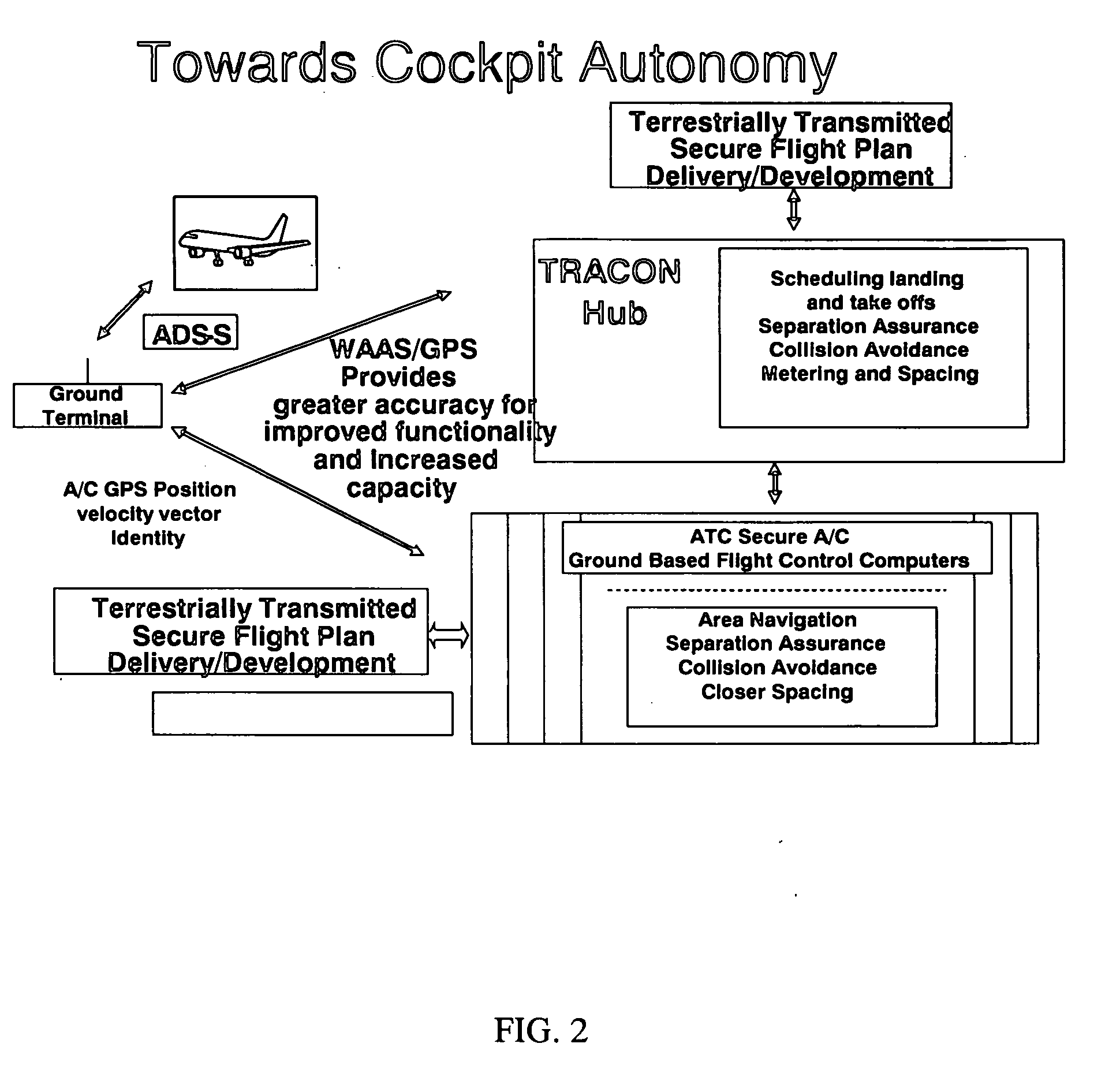
Automatic dependent surveillance system secure ADS-S
InactiveUS20080266166A1Provide securitySufficient securityAnalogue computers for vehiclesAnalogue computers for trafficMultilaterationEncryption
An air traffic control automatic dependent, WAAS / GPS based, surveillance system (ADS), for operation in the TRACON airspace. The system provides encryption protection against unauthorized reading of ADS messages and unauthorized position tracking of aircraft using multilateration techniques. Each aircraft has its own encryption and long PN codes per TRACON and transmit power is controlled to protect against unauthorized ranging on the ADS-S aircraft transmission. The encryption and PN codes can be changed dynamically. Several options which account for available bandwidth, burst data rates, frequency spectrum allocations, relative cost to implement, complexity of operation, degree of protection against unauthorized users, system capacity, bits per aircraft reply message and mutual interference avoidance techniques between ADS-S, ADS-B Enroute and Mode S / ATCRBS TRACON are disclosed. ADS messages are only transmitted as replies to ATC ground terminal interrogations (no squittering). Derivative surveillance backup systems provide an anti-spoofing capability.
Owner:SCHUCHMAN LEONARD
Electric car with maximized solar assist
InactiveUS20100193260A1Eliminate emissionsReduce threatAuxillary drivesVehicular energy storageElectricityContinuous flow
The present invention is an electric car with a maximized solar panel assist. Since batteries are normally charged at night while solar energy is created during the day, this system creates an almost continuous flow of electricity to the batteries. Since the weight and cost of the batteries are the main handicap for electric cars and a continuous flow of electricity minimizes the need for a large and expensive battery system, this is the most logical way to build a viable electric car.
Owner:FREEMAN BENJAMIN
Car driver driving skill practice guiding and examination scoring device and realization method
ActiveCN102768811ATimely voice promptRealize voice monitoring recordTeaching apparatusDigital videoSkill sets
A car driver driving skill practice guiding an examination scoring device comprises a core plate and an interface baseplate connected with the core plate, wherein the core plate comprises a DSP digital processing unit, an embedded MCU micro-controller, a program storage, a data storage and interface connector plugins; the DSP digital processing unit and the embedded MCU micro-controller are taken as the center namely a hardware platform of the device; the DSP digital processing unit is responsible for processing digital audios and digital video so as to obtain state data required by movement locus of an examination vehicle and other information; the embedded MCU micro-controller provides an operation platform for an operating system; and in addition to the interface connector plugins, interfaces containing corresponding interface circuit devices are also arranged on the interface baseplate. A realization method for car driver driving skill practice guiding an examination scoring, by means of the device, can improve the reliability of measurement data of the actual position of the examination car. Therefore, the integration level of functions of the vehicle-mounted equipment is improved, and the purchase and the maintenance cost for the customer are lowered.
Owner:LIUZHOU GUITONG TECH
Method, system and network device for filtration
Owner:HUAWEI TECH CO LTD
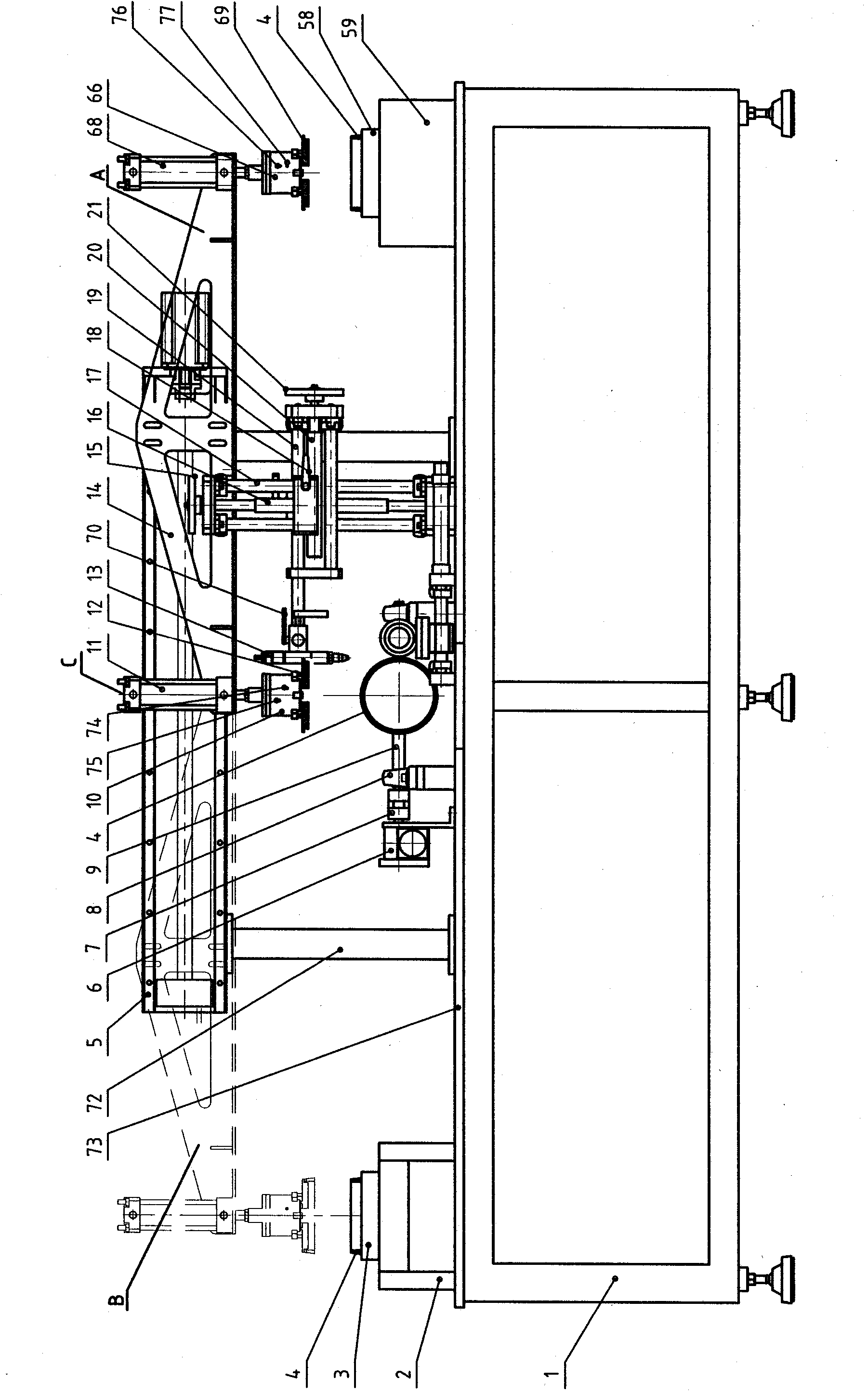
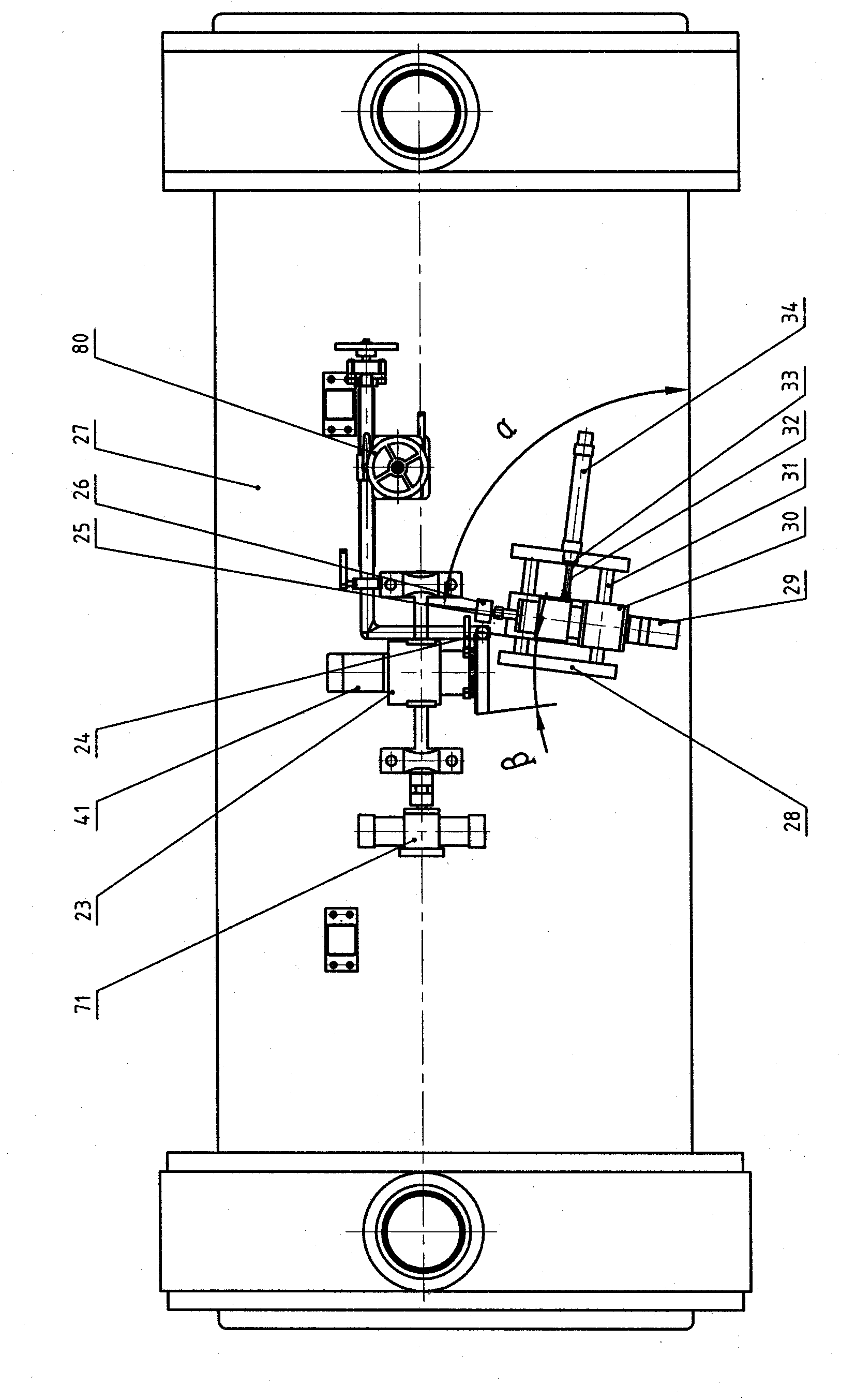
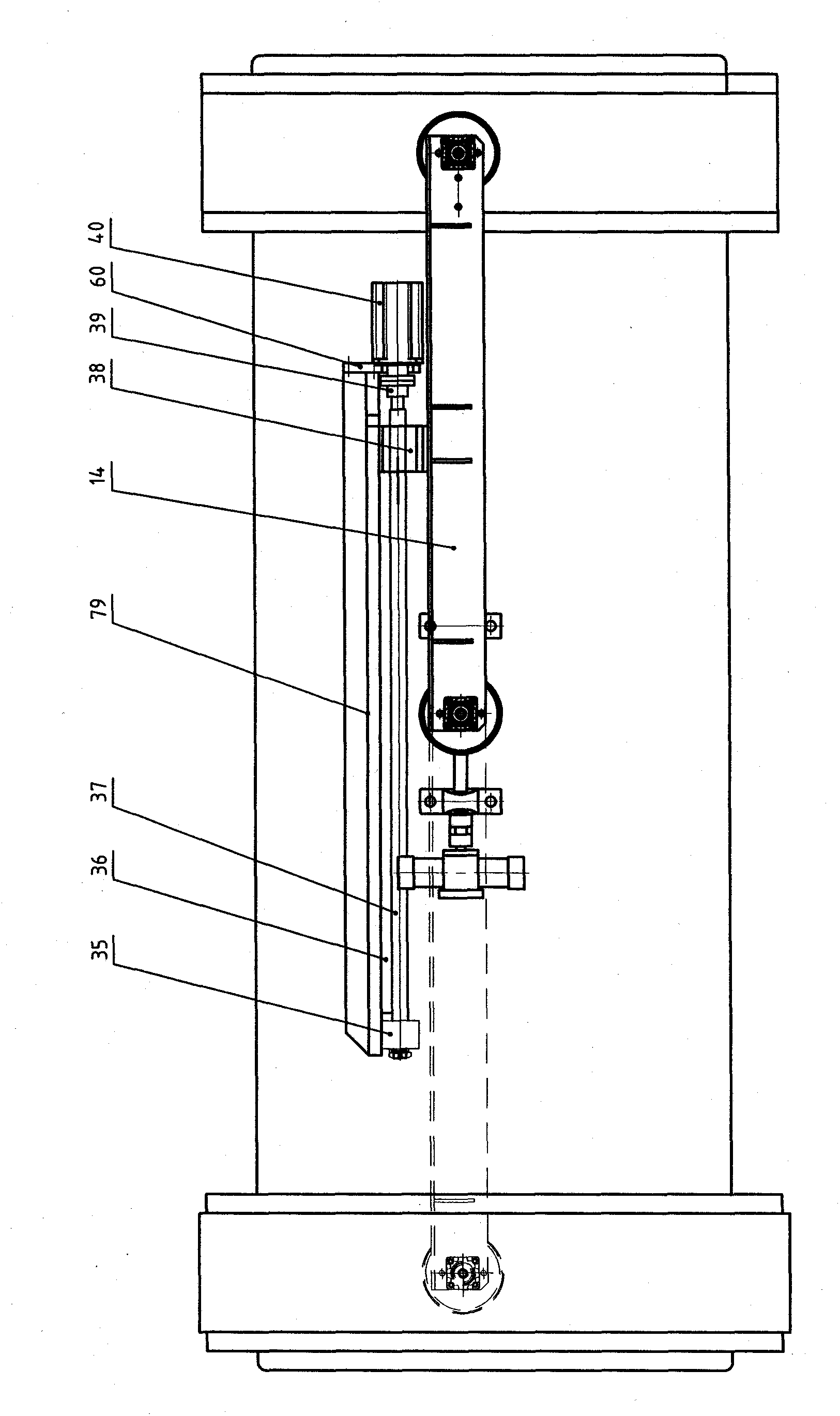
Fully-automatic gluing equipment suitable for various parts
ActiveCN102553774AApply glue evenlyMitigate threats to your healthLiquid surface applicatorsCoatingsEngineeringFully automatic
The invention provides fully-automatic gluing equipment suitable for various parts and relates to the fully-automatic gluing equipment. The fully-automatic gluing equipment solves the problem that the conventional cylindrical, ring-shaped, conical, circular truncated cone-shaped and circular truncated cone ring-shaped parts cannot be fully automatically glued on the same equipment. The fully-automatic gluing equipment comprises a machine frame, and a feeding workbench, a transmission platform, a part transverse transmission device, a tensioning collet A, a tensioning collet C, a rotary collet device, a swinging device, a glue head adjusting device and a glue scraping device which are fixed on the machine frame, wherein the feeding workbench comprises a feeding positioning die; the feeding positioning die is fixed on a feeding workbench panel; and the feeding positioning die is used for accurately positioning the parts and placing the parts in to the positioning die. The fully-automatic gluing equipment has high generality, can glue on the outer surfaces of the cylindrical, ring-shaped, conical, circular truncated cone-shaped and circular truncated cone ring-shaped parts and can glue on the inner surfaces of the cylindrical, ring-shaped, conical, circular truncated cone-shaped and circular truncated cone ring-shaped parts.
Owner:DALIAN HUAGONG INNOVATION TECH
Gaming terminal data monitoring network
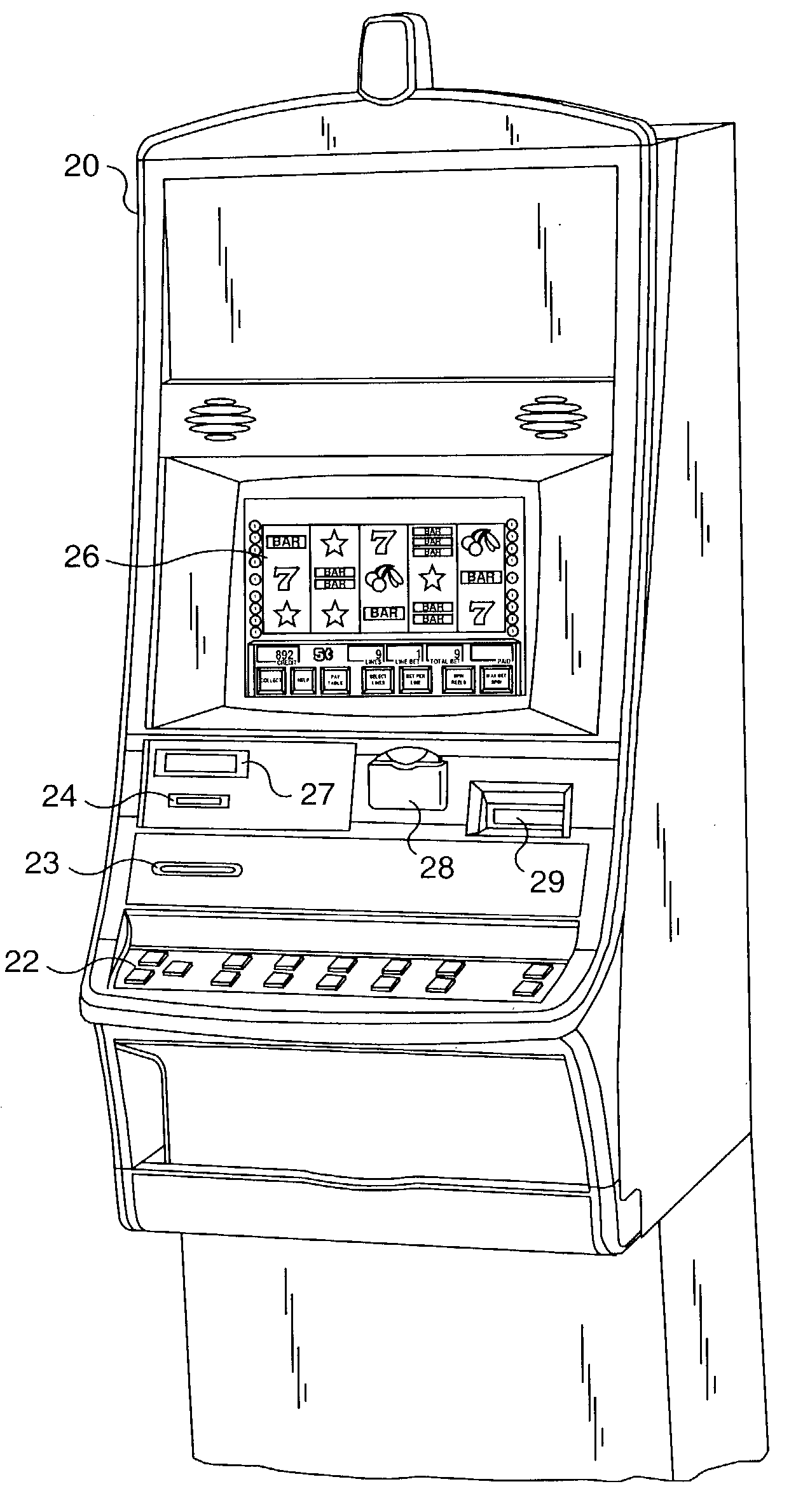
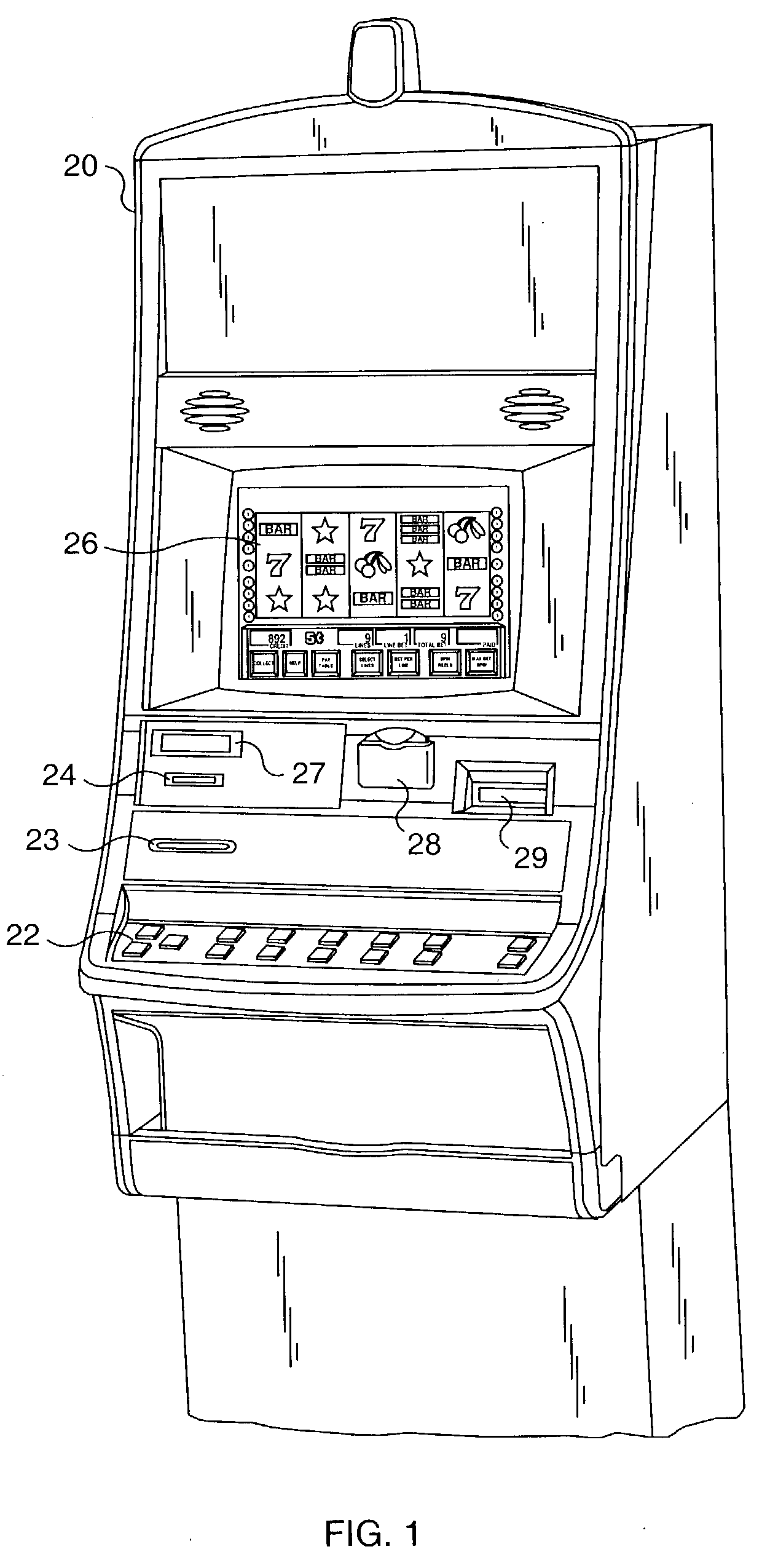
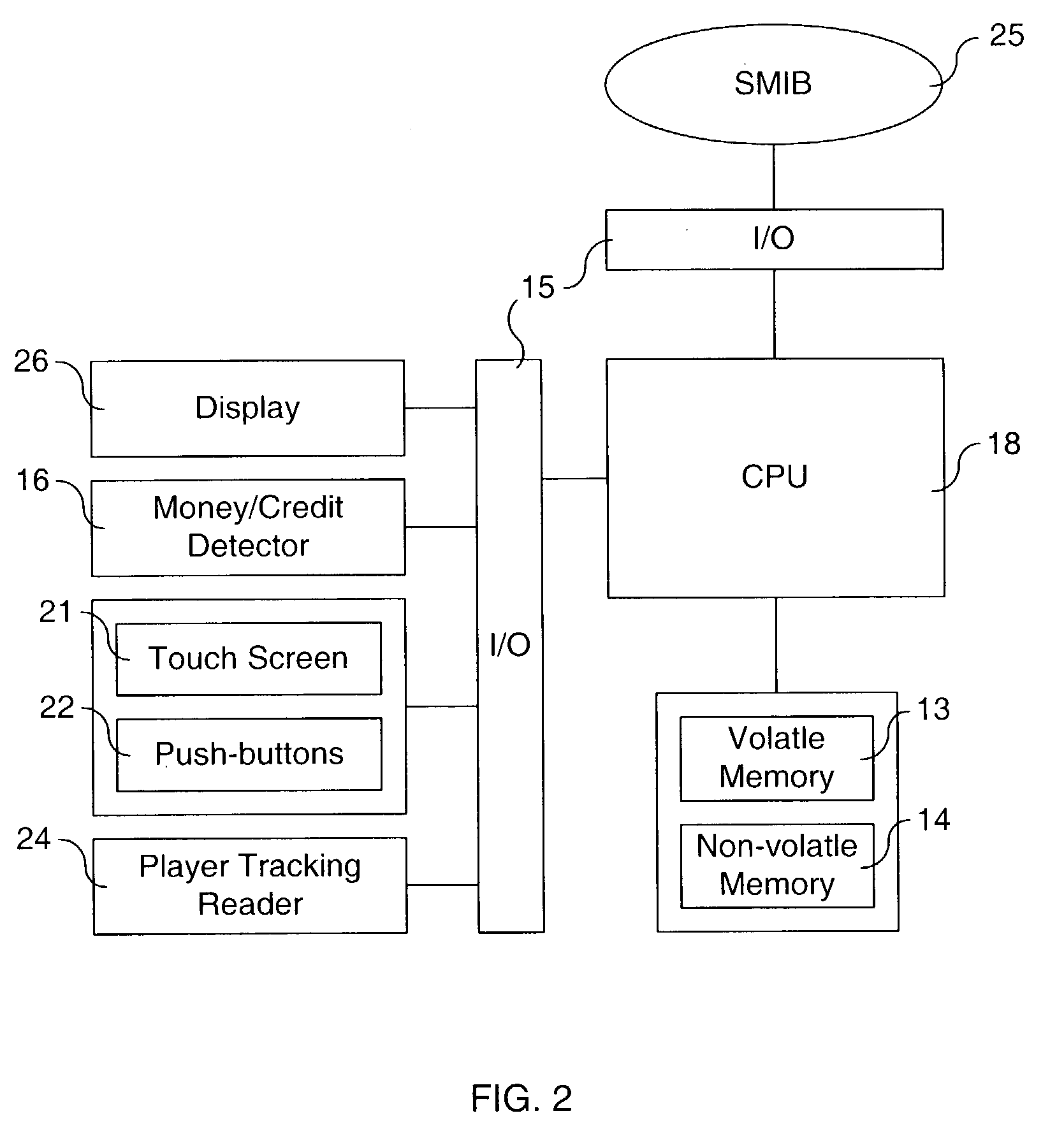
InactiveUS8197344B2Reliable and secure audit trailSimplify their oversightCard gamesApparatus for meter-controlled dispensingCommunication interfaceNetwork Communication Protocols
A method of storing data serially transmitted between a gaming terminal and a computer on one or more servers in a network. The gaming terminal and computer are typically linked in gaming establishments by a serial communication link utilizing serial communication protocols. Although this data is stored on the gaming establishment's computers, it is also highly desirable to make this data accessible on a secure server. Data is monitored and captured directly at the gaming terminal with a communication interface. The communication interface converts the captured data from a serial communication protocol into a network communication protocol for storage on a server in a network.
Owner:BALLY GAMING INC
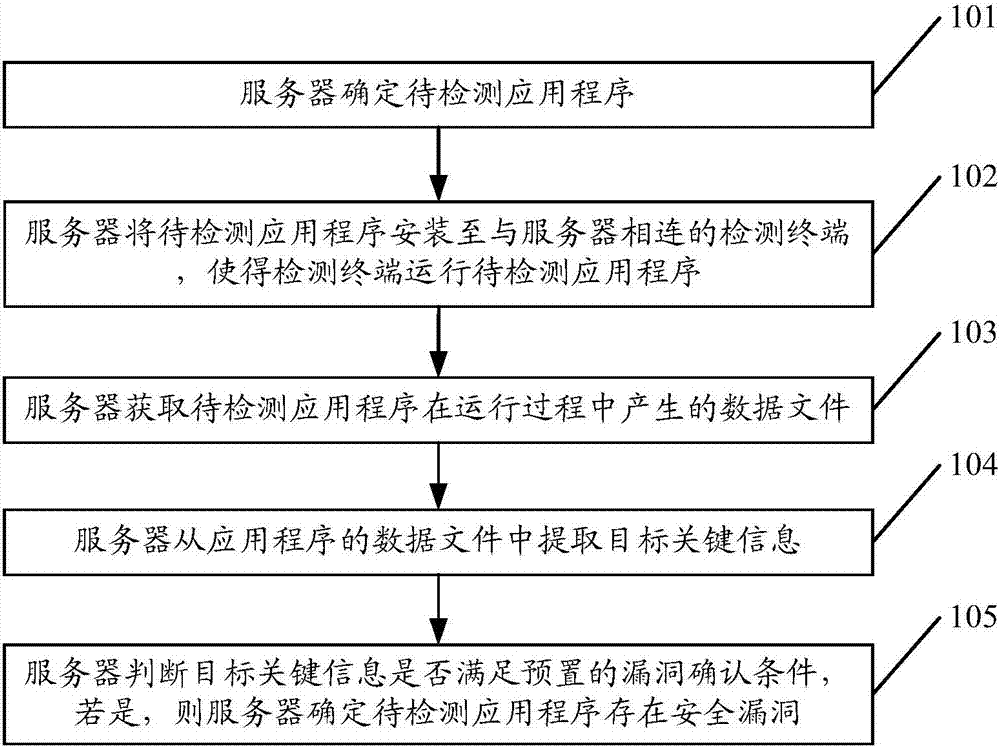
Security vulnerability detection method and device
InactiveCN107239702AReduce threatImprove securityPlatform integrity maintainanceData fileComputer terminal
The embodiment of the invention discloses a security vulnerability detection method. The method comprises the steps that a to-be-detected application program is determined; the to-be-detected application program is installed to a detection terminal connected with a server so that the detection terminal can run the to-be-detected application program; a data file generated in the running process of the to-be-detected application program is acquired; target key information is extracted from the data file of the application program; whether the target key information meets a preset vulnerability confirmation condition is judged; and if yes, the server determines that the to-be-detected application program has a security vulnerability. The embodiment of the invention furthermore provides the server. According to the embodiment, vulnerability detection can be performed on the generated data file in the running process of the application program, therefore, threat of unsecure data files on user information security is greatly lowered, and the security and practicability of the scheme are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for resisting simulated main customer attack in cognitive radio
InactiveCN101420758AAvoid interferenceHigh precisionConnection managementSecurity arrangementFrequency spectrumComputer science
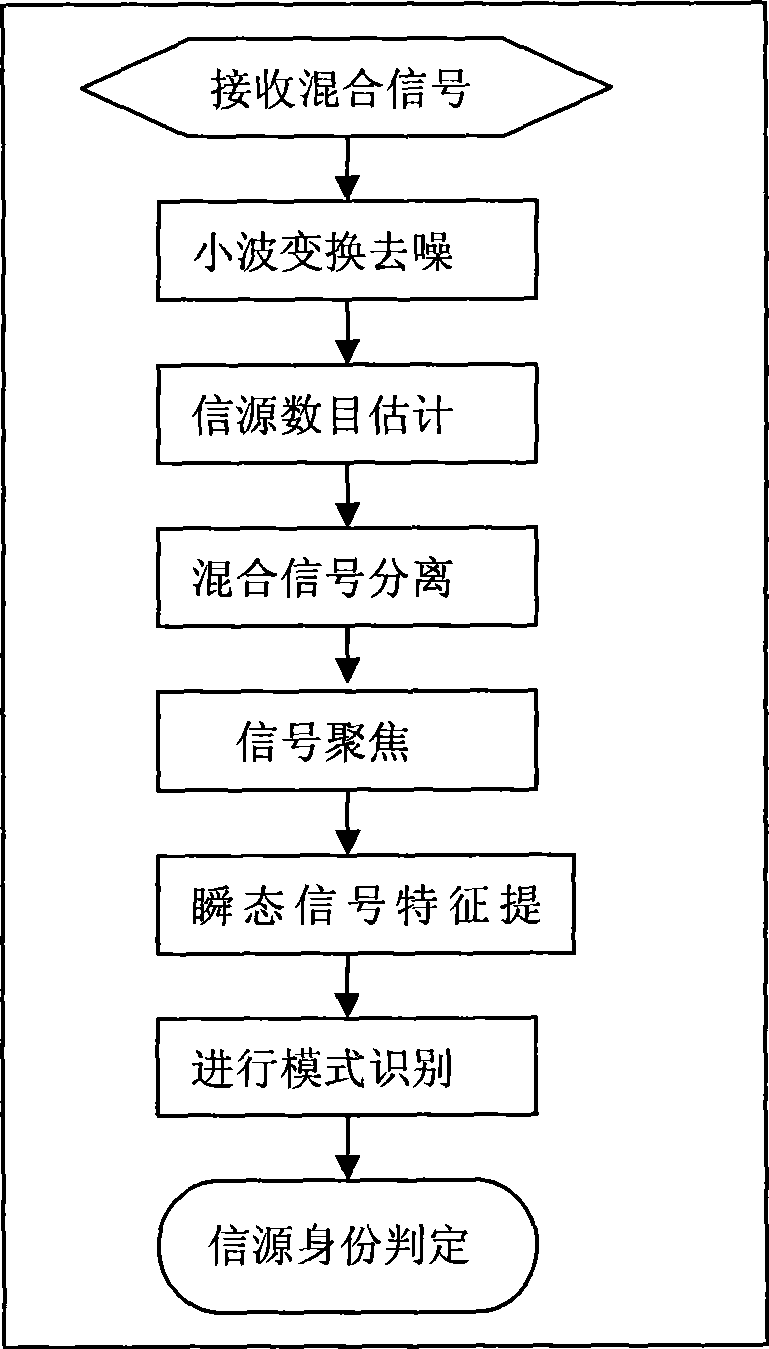
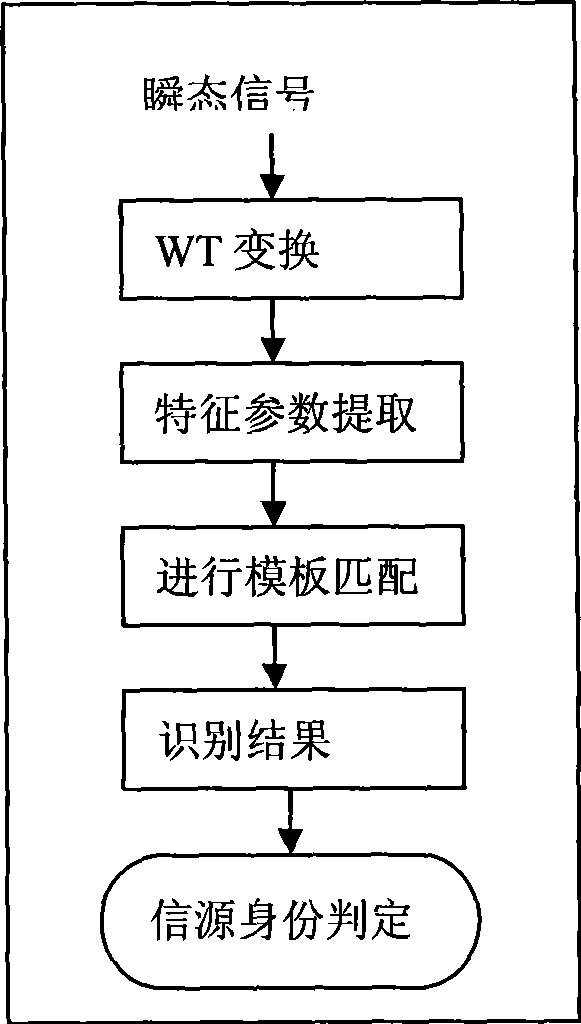
A method for resisting primary user impersonation attacks in cognitive radio belongs to the technical field of radio communication, particularly relates to sensing and processing of the signals in the cognitive radio system and identification of a signal source. The method comprises the following steps: reducing noise of a composite signal which is received during a spectrum sensing process, estimating number of the signal sources in the composite signal, and reconstructing various signals by a Capon beamformer; separating the signals of different radios, focusing the signals of different radios to separate out a transient signal and a modulation signal, analyzing the transient signal by wavelet transformation; extracting characteristic parameters and realizing identification of the signal source. The method for resisting the primary user impersonation attacks helps realize effective identification of the signal source and effectively resist the primary user impersonation attacks; and the method has a wide application scope, does not change a working mode of the existing primary user network, and satisfies operation requirements of FCC for a cognitive network.
Owner:UNIV OF SCI & TECH BEIJING
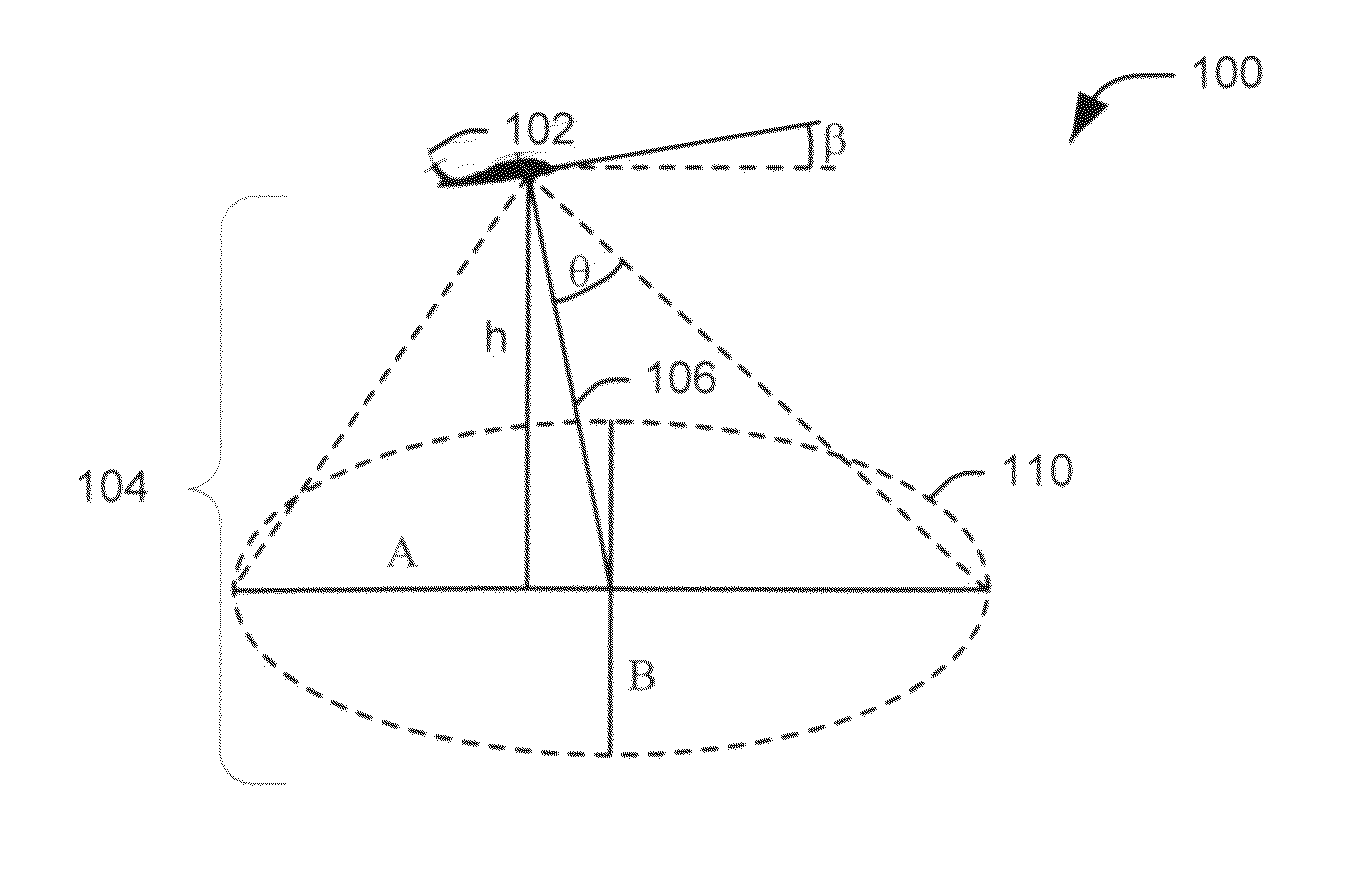
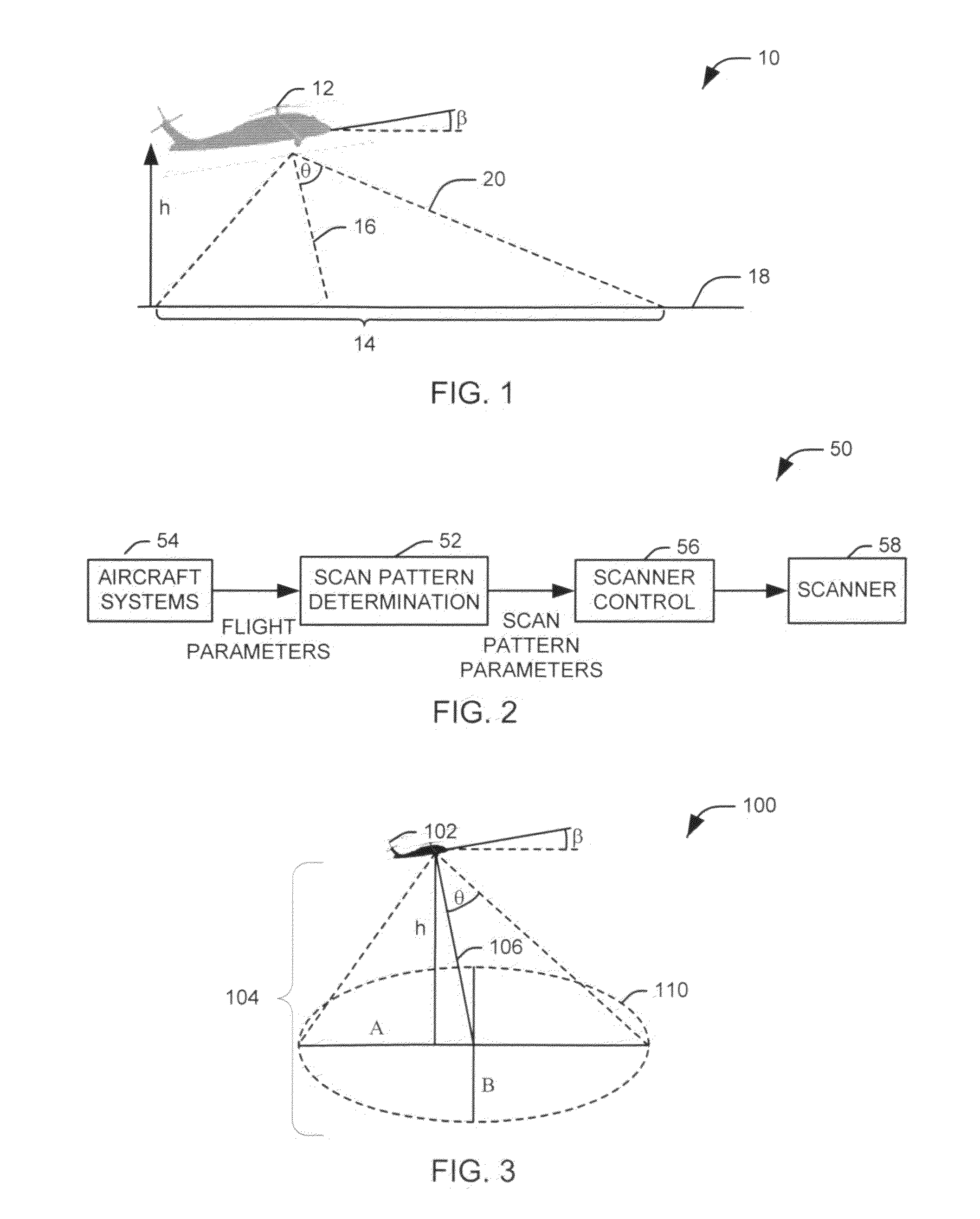
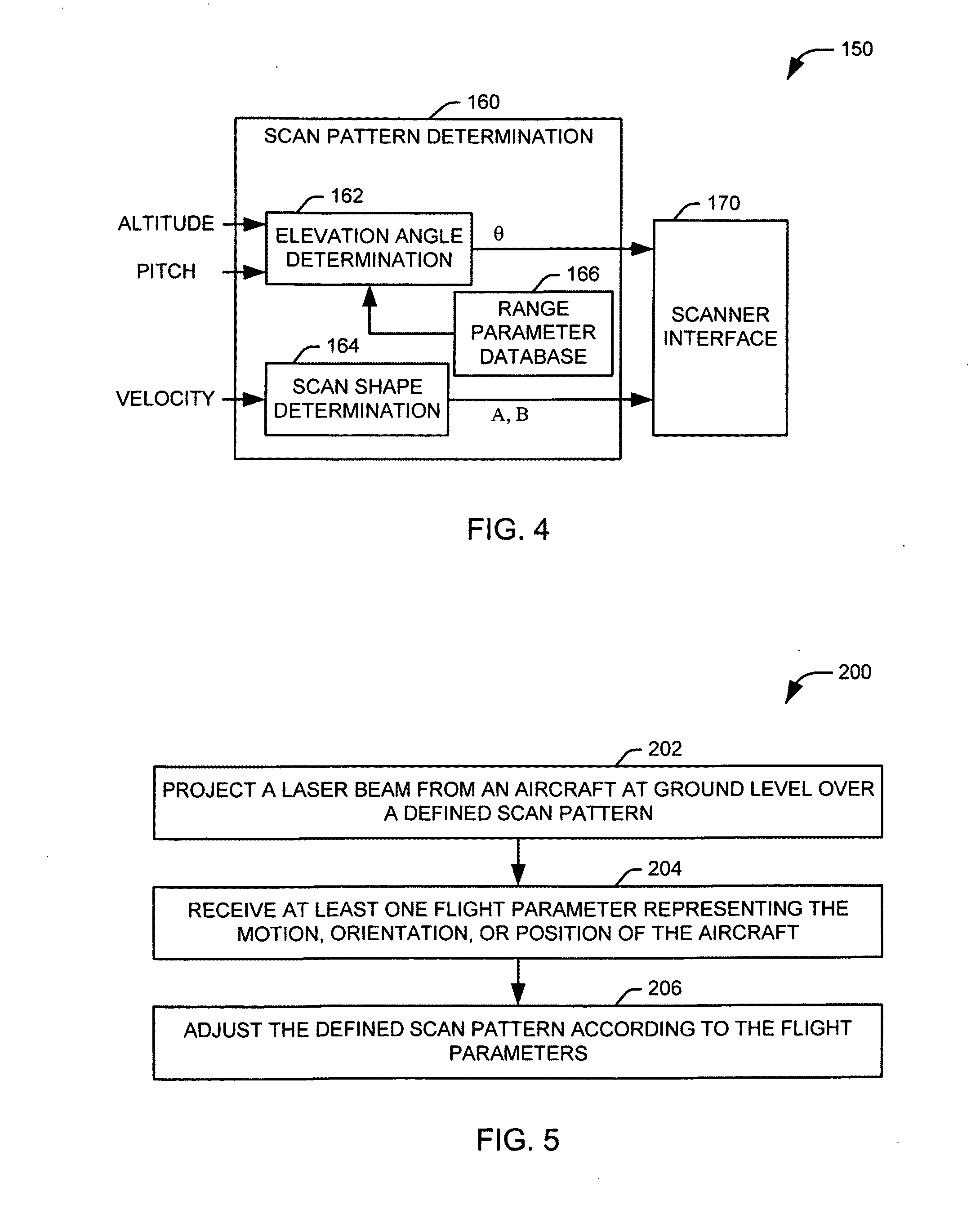
Dynamic optical countermeasures for ground level threats to an aircraft
InactiveUS20110001062A1Reduce threatStrong enoughDefence devicesWave based measurement systemsCountermeasureUltimate tensile strength
Systems and methods are provided for mitigating optically aimed threats to an aircraft from the ground. A laser beam, having sufficient intensity to interfere with the vision of a human being, is projected from the aircraft over a defined scan pattern at ground level. At least one flight parameter is received. Each flight parameter represents one of a current orientation, position, and motion of the aircraft. The defined scan pattern is adjusted according to at least one flight parameter.
Owner:LOCKHEED MARTIN CORP
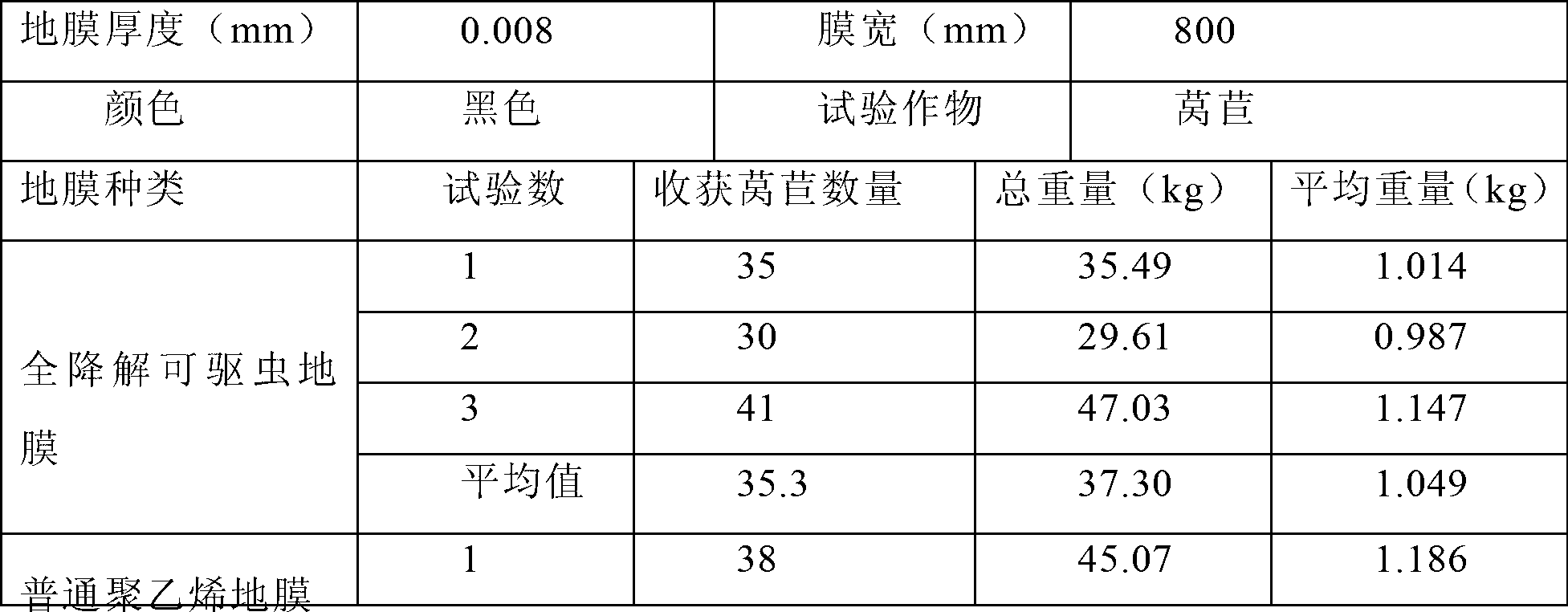
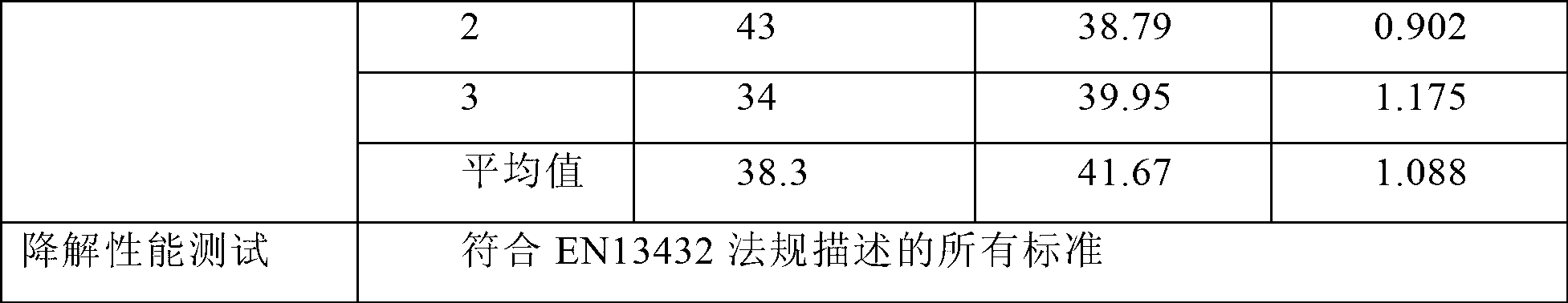
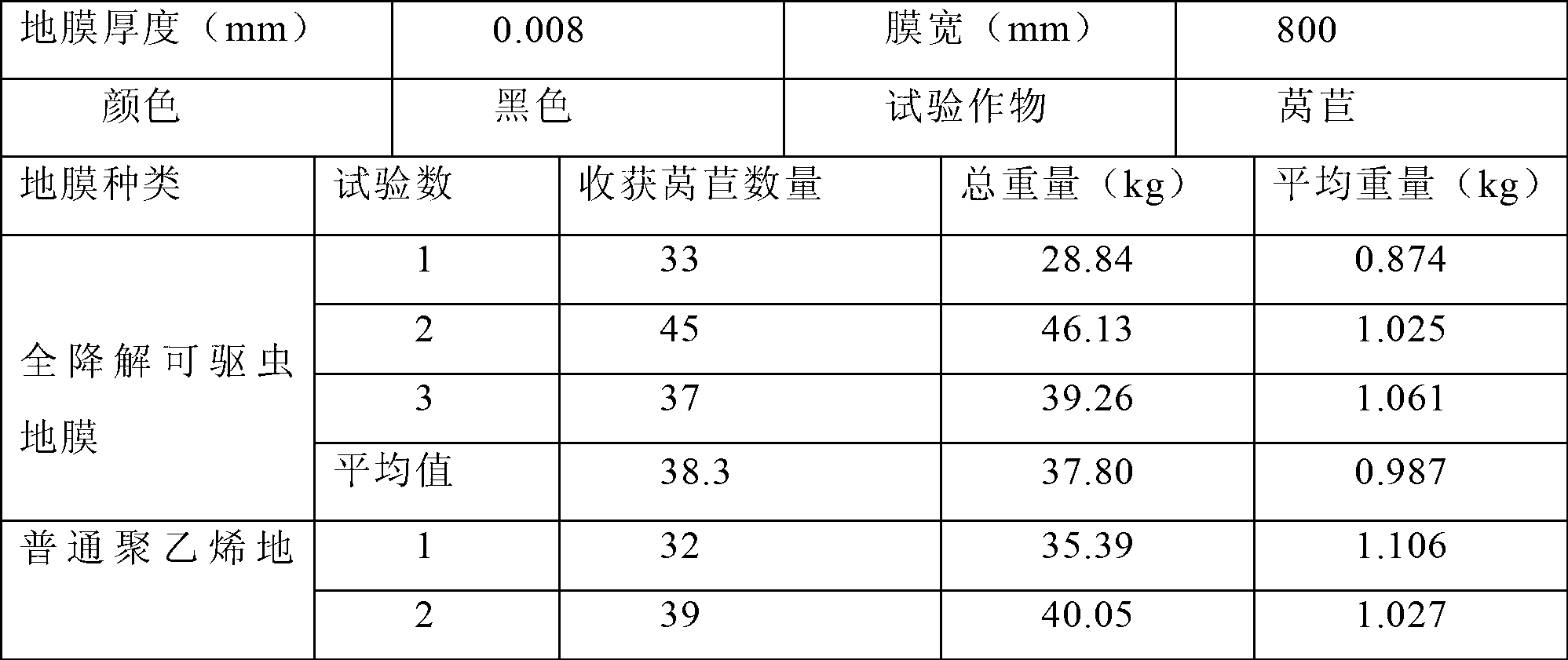
Full-degradation deworming mulching film and preparation method thereof
InactiveCN102936400AInhibition of growth and developmentReduce threatClimate change adaptationAnimal repellantsChemistryPesticide
The invention relates to a full-degradation deworming mulching film and a preparation method thereof. The full-degradation deworming mulching film comprises as follows in parts by mass: PBAT 30-60%, polylactic acid 10-30%, starch 10-30%, plasticizer 5-10%, chain extender 0-2%, filler 5-10%, plant source pesticide-sustained-release microcapsule 5-20% and full-degradation color master batch 0-5%. The preparation method comprises the steps of firstly absorbing plant source pesticide on diatomaceous earth, then processing with polyvinyl alcohol according to specific technology to obtain the plant source pesticide-sustained-release microcapsule, and then manufacturing materials for the full-degradation deworming mulching film with the PBAT, starch, polylactic acid, plasticizer, chain extender and the filler according to a specific production technology. The biological full-degradation mulching film has deworming effect, has important significance on crop pesticide residue reduction and environment protection, and meets the requirement of sustainable development.
Owner:WUHAN HUALI BIOLOGY CO LTD
Method and device for identifying server broiler chicken
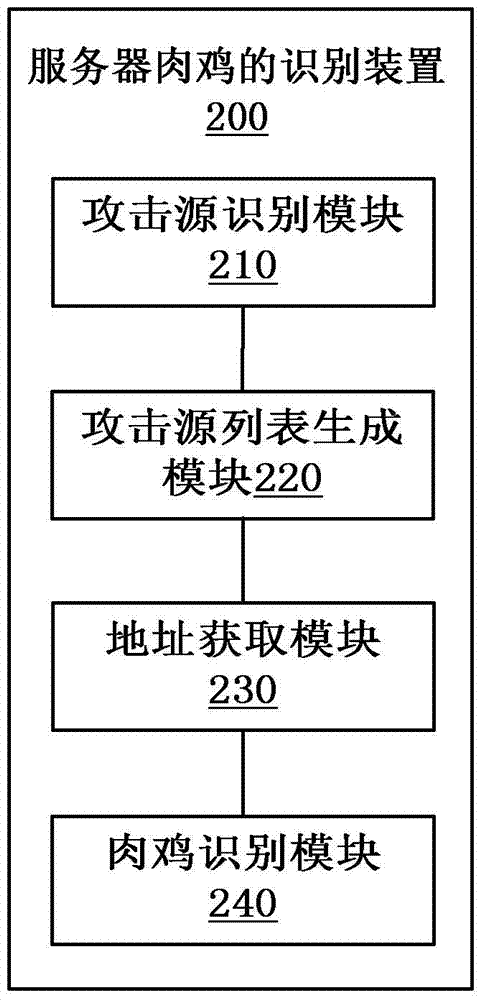
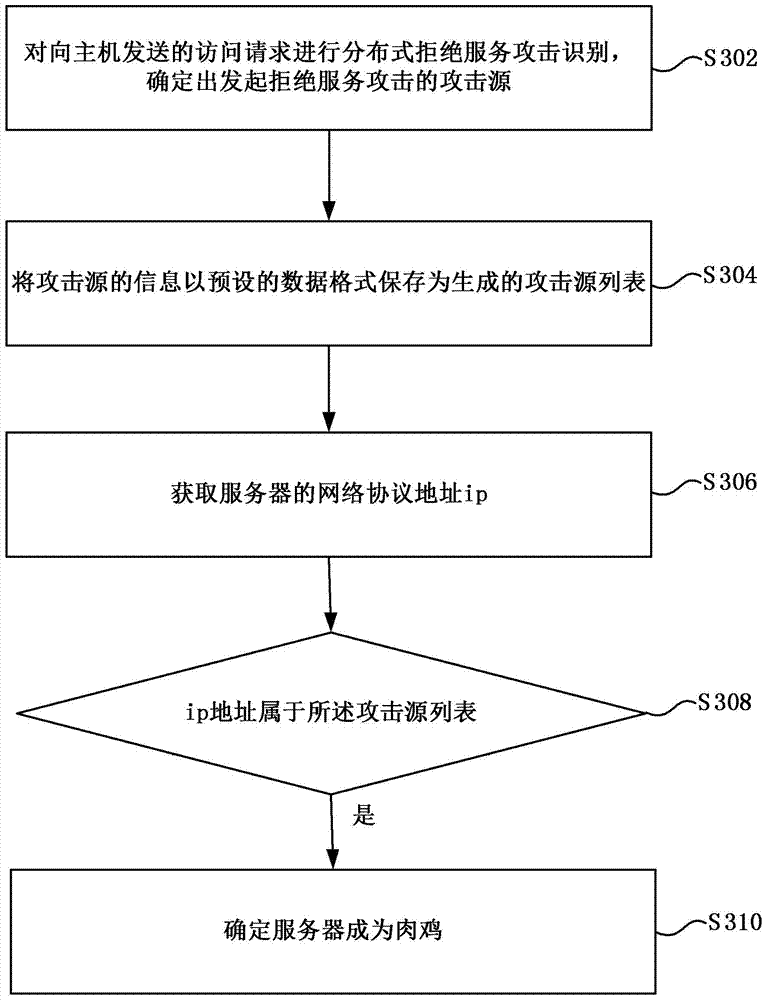
The invention provides a method and a device for identifying server broiler chicken. The method for identifying the server broiler chicken comprises the following steps: carrying out denial of service attack identification on an access request sent to a host machine so as to determine attack sources launching the denial of service attack; storing the information of the attack sources into a generated attack source list in a preset data format; obtaining the network protocol address ip of a server; judging whether the ip address belongs to the attack source list, if yes, determining the server to be broiler chicken. Through the application of the technical scheme, the attack sources for denial of service attack are identified, a data list of massive attack sources is formed, the server becoming the broiler chicken is identified according to the comparison result of the IP address of the existing server and the data in the attack source list, the advantages of big data are utilized, the identification is reliable and accurate, and the threat of broiler chicken server to network security can be reduced.
Owner:BEIJING QIANXIN TECH
Sewage treatment equipment fault diagnosis system and method based on Lasso regression
ActiveCN110320892AReduce threatReduce lagProgramme controlElectric testing/monitoringData acquisitionComputer module
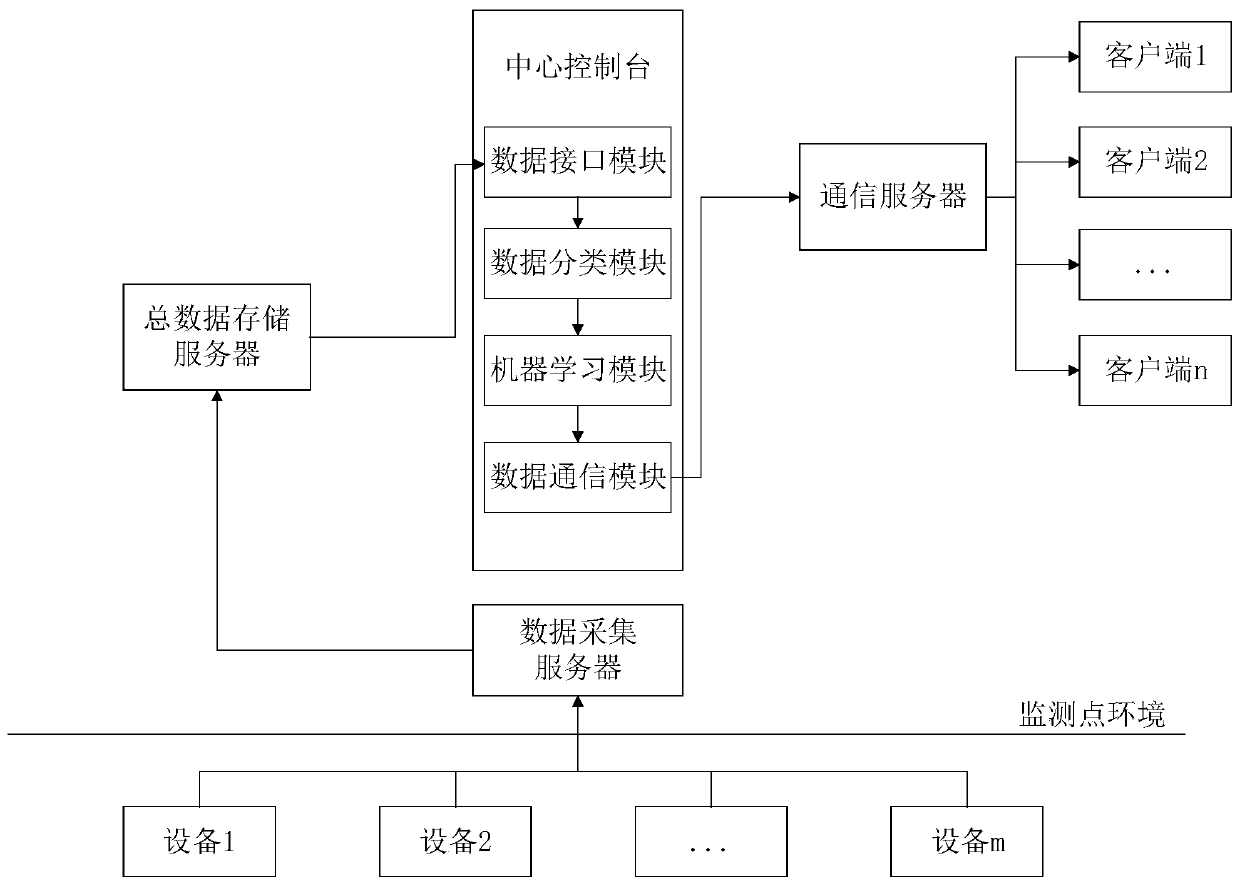
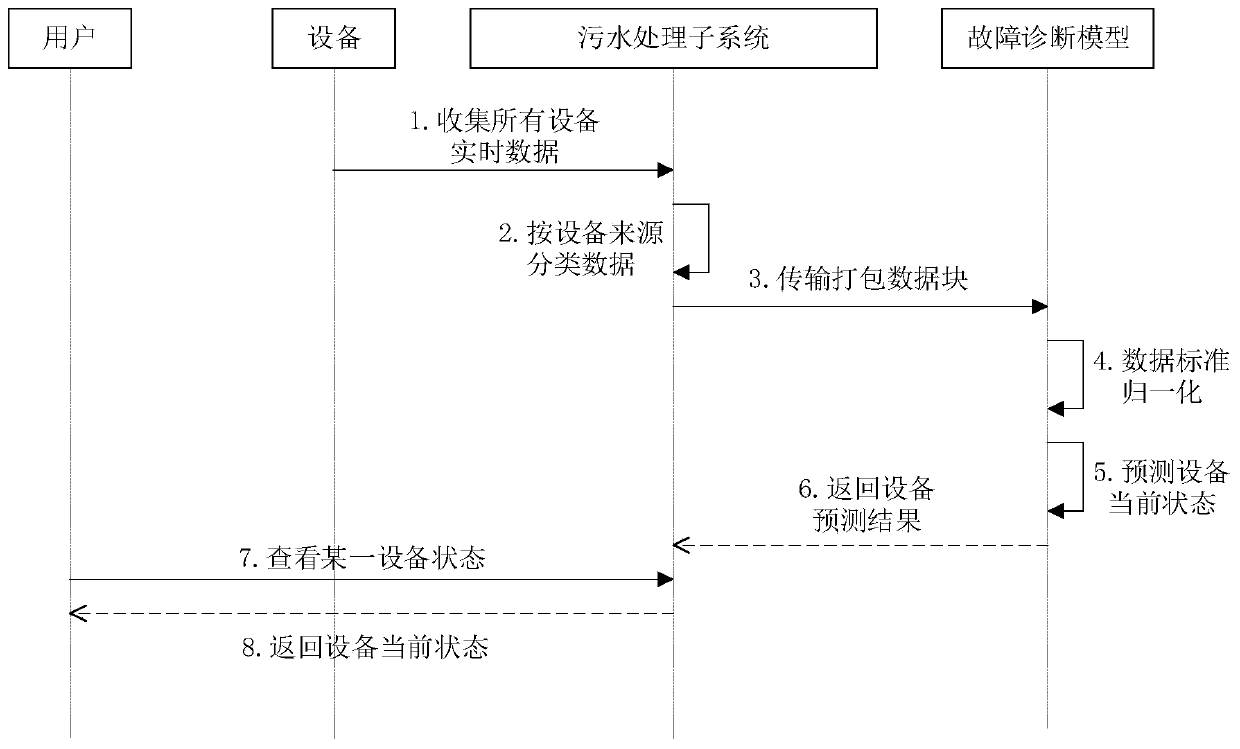
The invention belongs to the field of equipment fault diagnosis, and particularly relates to a sewage treatment equipment fault diagnosis system and method based on Lasso regression. The fault diagnosis system comprises a sewage treatment subsystem, a plurality of supervision clients and a plurality of data acquisition devices; the sewage treatment subsystem comprises a central console, a communication server, a total data storage server and a data acquisition server; the central console comprises a control module, a data interface module, a data classification module, a machine learning module and a data communication module; and by acquiring data on the data acquisition devices, the machine learning model carries out learning training on the data so as to construct a plurality of sub regression prediction models for predicting fault types of various types of sewage treatment equipment. The sewage treatment equipment fault diagnosis system and method disclosed by the invention providea certain basic diagnosis help for engineering supervision and treatment decisions of sewage treatment, and effectively meet requirements for real-time monitoring and diagnosis on the sewage treatment environment fault problem in the sewage treatment process.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
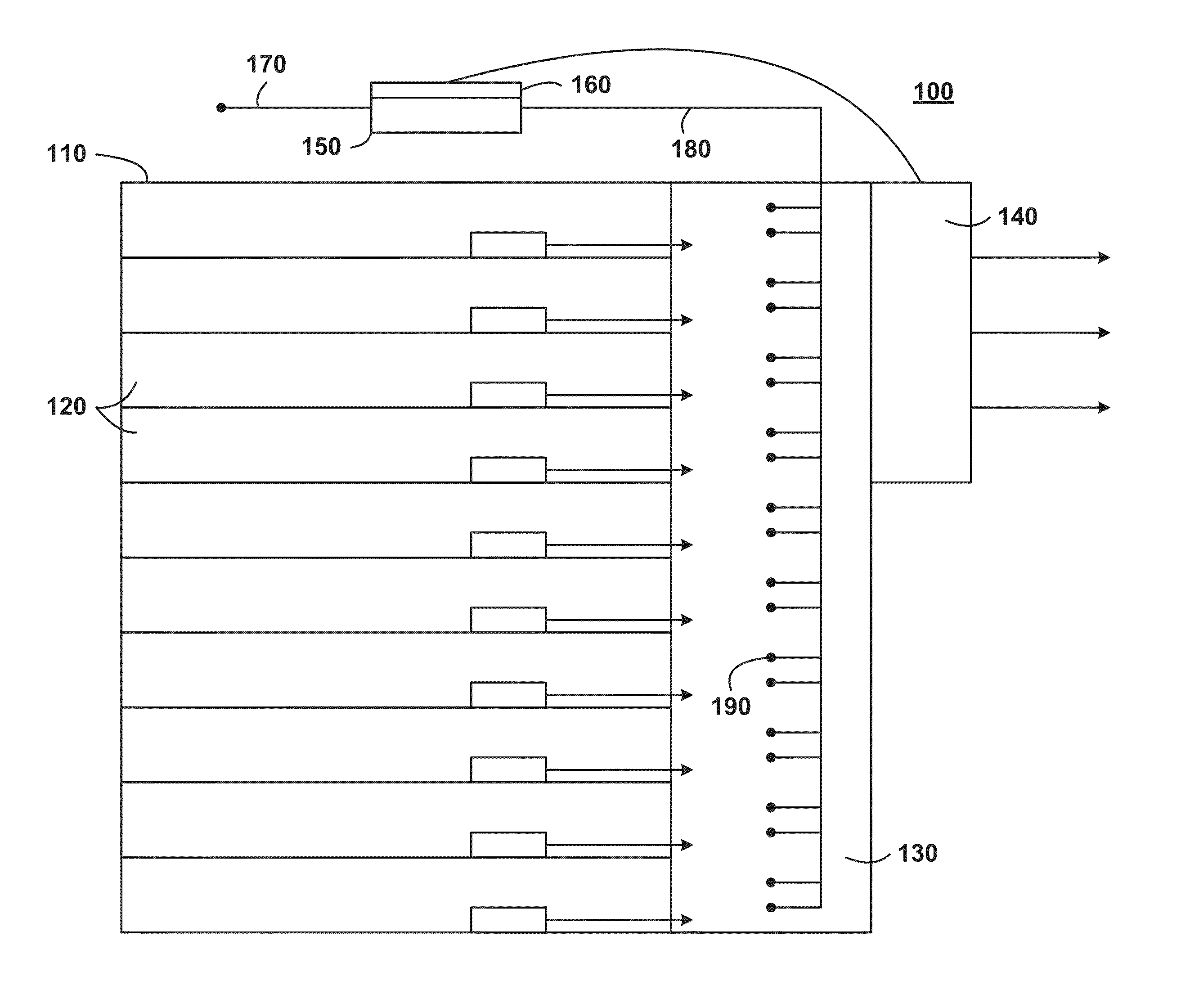
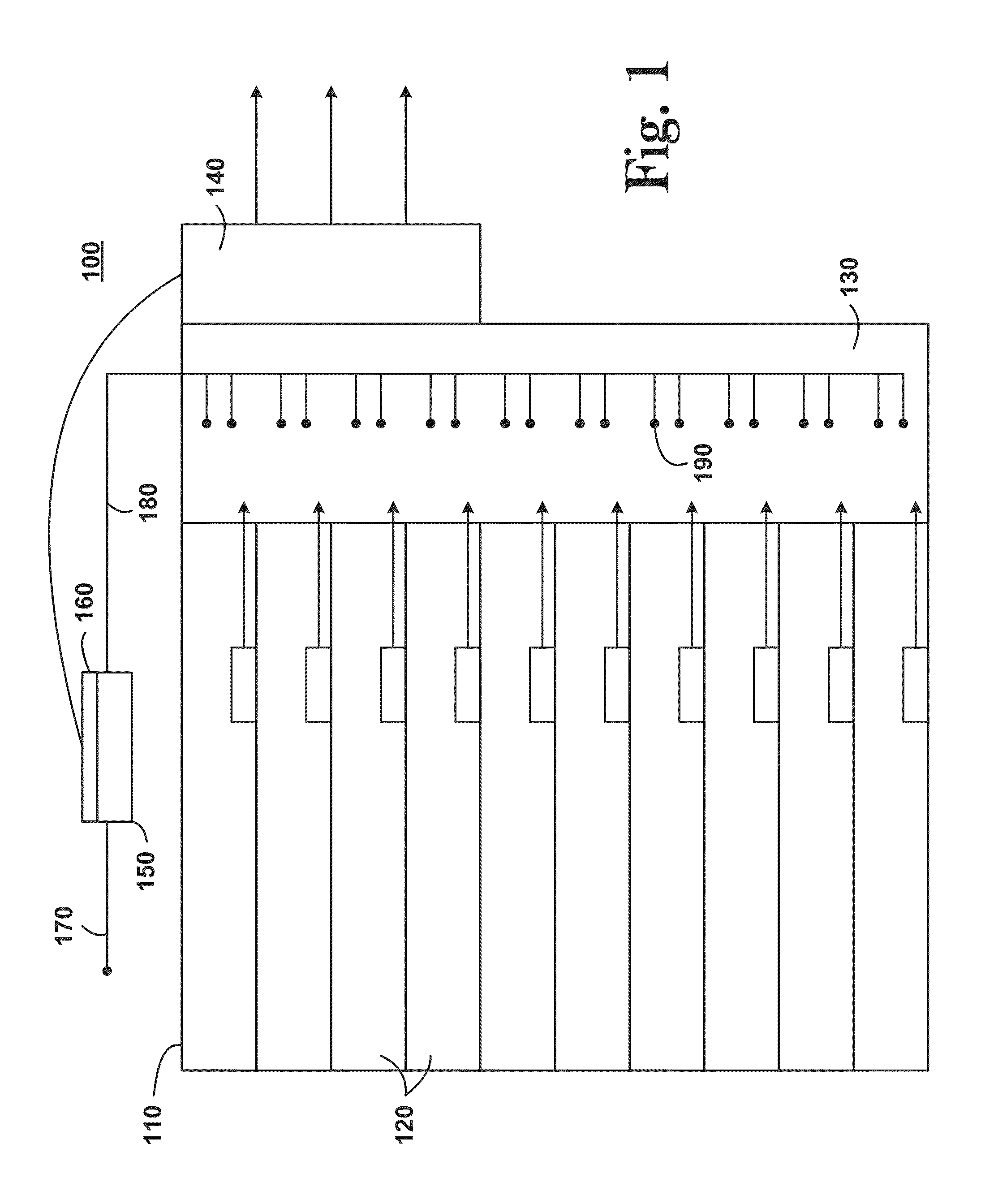
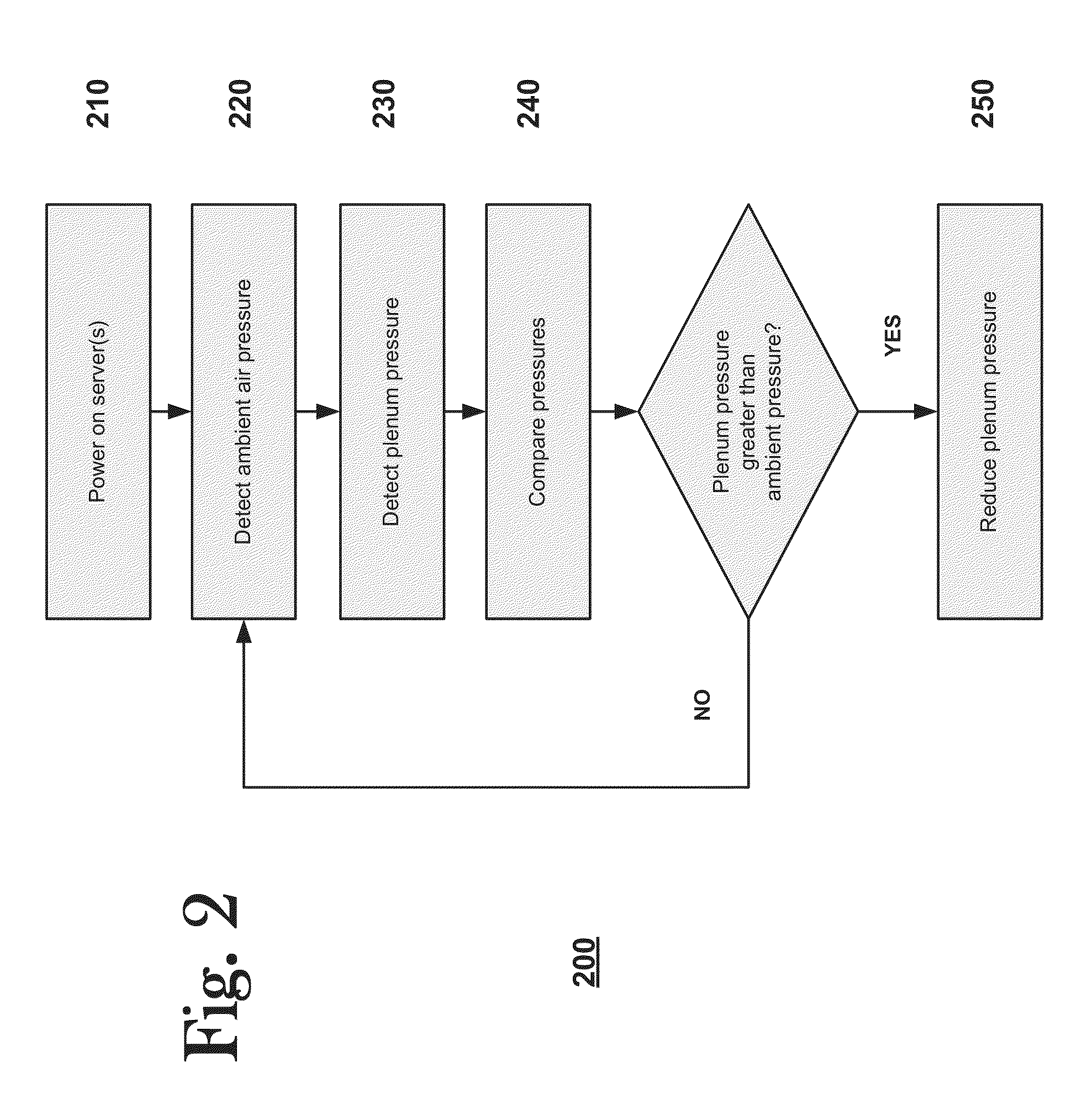
Pressure-activated server cooling system
InactiveUS20150003010A1Reduce threatDetrimental flow impedanceDigital data processing detailsCooling/ventilation/heating modificationsInternal pressureDifferential pressure
A pressure-activated server cooling system includes a server rack that houses one or more servers. The server rack has an interior plenum. A fan is coupled to the server rack that exhausts air from inside the plenum to outside the server rack. A differential pressure sensor collects pressure sensor data and a fan controller, which is operatively connected to the fan and the differential pressure sensor, activates the fan in response to the pressure sensor data. In some embodiments, the fan controller increases the speed of the fan when the pressure sensor data indicates greater than atmospheric pressure in the plenum.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Marine magnetic survey method and device for polar floating ice areas
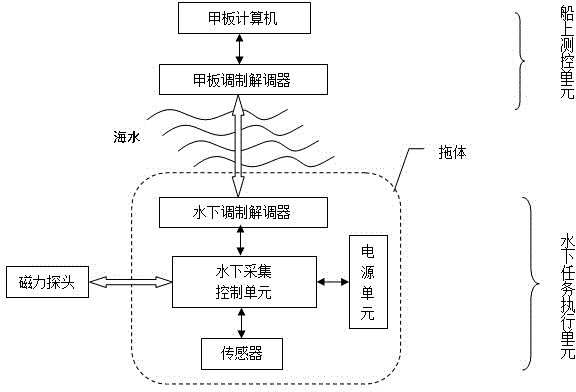
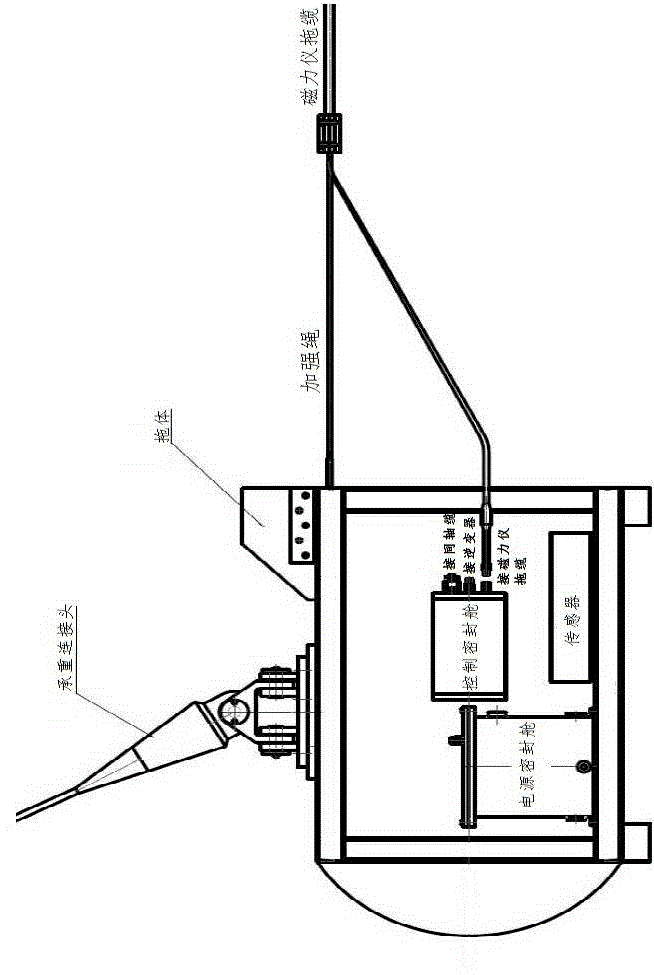
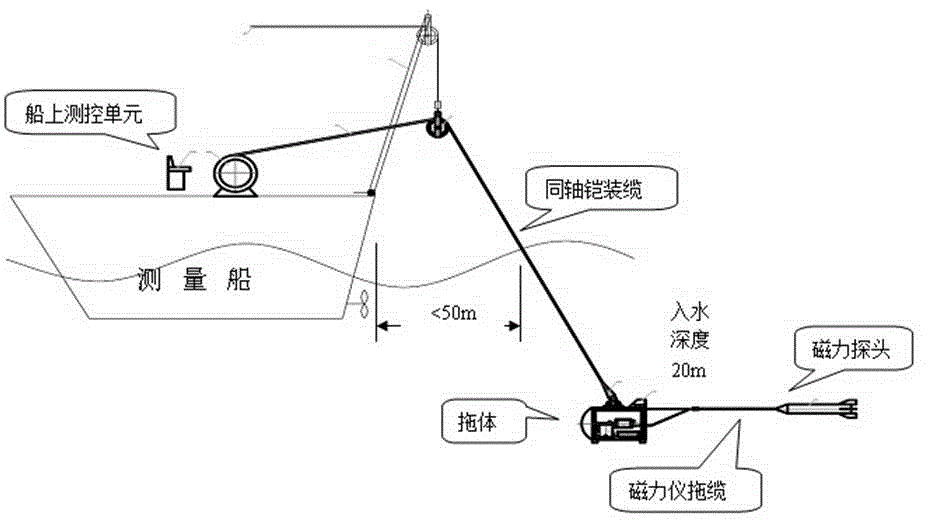
ActiveCN104793255AReduce threatReduce lossElectric/magnetic detectionAcoustic wave reradiationModem deviceMarine engineering
The invention relates to a marine magnetic survey device for polar floating ice areas. The device comprises an underwater task execution unit, an onboard measurement and control unit and a coaxial armor cable. The underwater task execution unit is connected with the onboard measurement and control unit through the coaxial armor cable; the underwater task execution unit comprises a towed body, an underwater acquisition control unit, an underwater modem, a sensor, a magnetic tow, a magnetic probe and a power supply unit; the onboard measurement and control unit comprises a deck acquisition and control unit and a deck modem; a sealed control cabin, a sealed power supply cabin and the sensor are mounted inside the towed body; the underwater acquisition control unit and the underwater modem are mounted in the sealed control cabin, and the power supply unit is mounted in the sealed power supply cabin; the underwater acquisition control unit supplies power to the magnetic probe and acquires signals of the magnetic probe and the sensor. The device has the advantages that threat of floating ice to equipment safety is lowered greatly, risk of equipment loss and damage is lowered, and polar-region magnetic survey efficiency is improved.
Owner:THE FIRST INST OF OCEANOGRAPHY SOA +1
Portable automated vent cover
ActiveUS8359984B1Reduce continued prevalenceReduce threatValve arrangementsVehicle fittings for liftingEngineeringDrive motor
A portable automated vent cover includes a drive system, a telescoping tube, a vent cover plate and a collapsible mobile tripod. The drive system preferably includes a drive motor, a gear box, an up-relay and a down-relay. The telescoping tube includes an outer support tube, an inner cover tube and a rack gear. The rack gear is attached to the inner cover tube. The vent cover plate is secured to a top of the inner cover tube. The drive motor drives a pinion gear through the gear box. The gear box is retained on the outer support tube. An up-down switch is used to raise and lower the vent cover plate. Electrical power is controlled by either the up-down switch or a controller and sent to the drive motor through either the up-relay or the down-relay. The collapsible mobile tripod is attached to a bottom of the outer support tube.
Owner:ALTAPURE
Method and system for selectively controlling the utility a target
InactiveUS20060100983A1Reduce threatCompromise their utilityIndoor gamesUser identity/authority verificationControl objectiveBiological activation
Owner:NXP BV
Method for preparing biological oil through catalytic liquefaction of microalgae
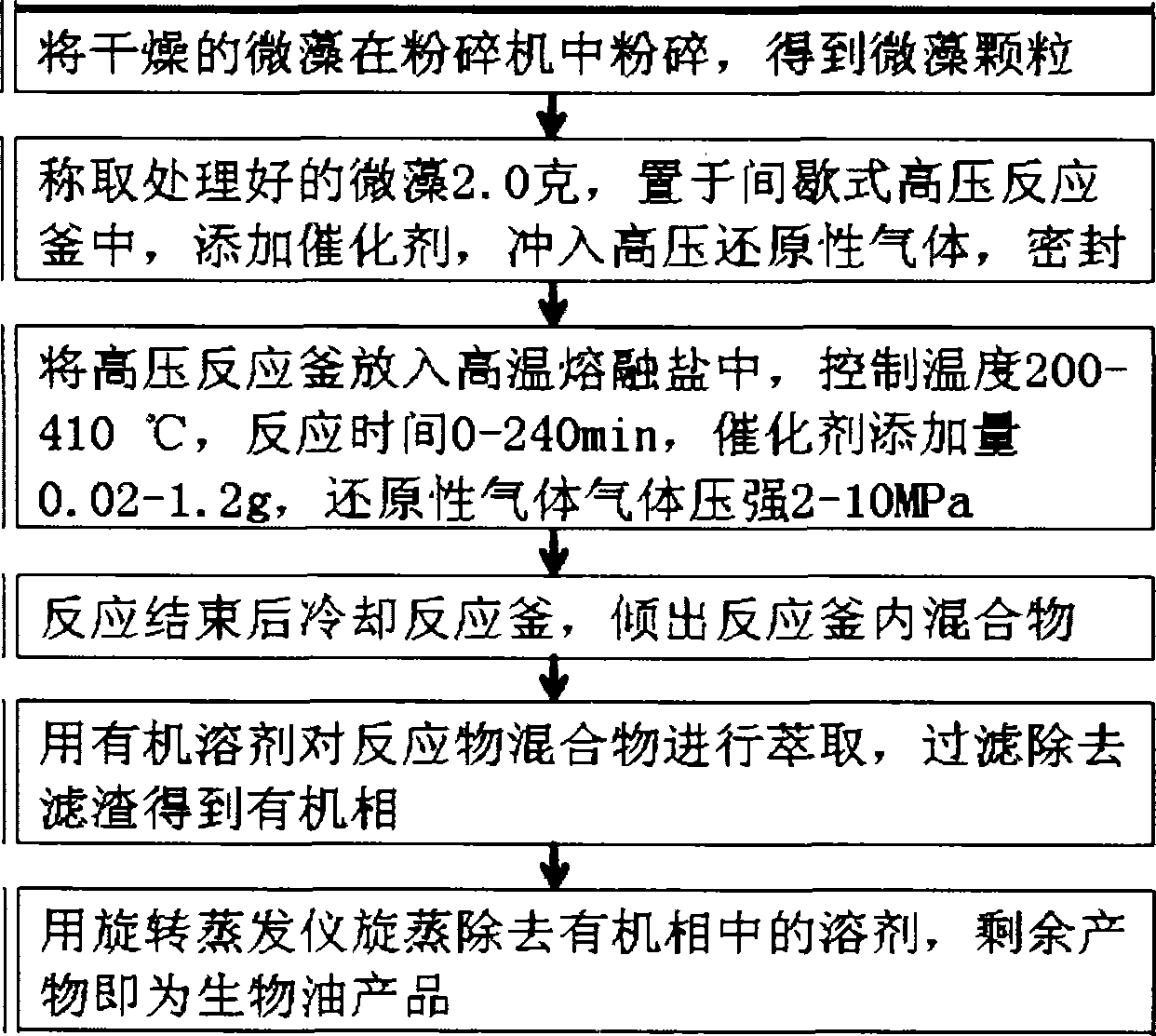
InactiveCN103060075ALow costReduce threatLiquid carbonaceous fuelsFatty-oils/fats productionChemistryActivated carbon
The invention discloses a method for preparing biological oil through catalytic pyrolysis of a microalgae biomass. The method is as follows: pyrolysis liquefaction is carried out on microalgae in the presence of a catalyst in an intermittent high-pressure reaction kettle so as to prepare the biological oil. Reduced high-pressure gas is filled into the reaction kettle. A catalyst is added to the pyrolysis reaction, and the catalyst is a loaded noble metal catalyst, molybdenum-based catalyst, active carbon and the like. The microalgae comprise chlorella, spirulina, micro-green-algae, dunaliella salina and the like. The microalgae have the advantages of various types, high photosynthetic efficiency, high oil content, short production period, high oil production rate per unit area, easiness for culturing, no farmland occupation and the like and is a good raw material for preparing biological oil fuel. In addition, diesel type hydrocarbon can be prepared through modifying and upgrading the microalgae biological oil, and dependence of people on fossil fuel can be expected to be relieved.
Owner:HENAN POLYTECHNIC UNIV
Bicycle Warning Device
InactiveUS20090033475A1Reduce in quantitySafe timeAcoustic signalOptical signalEngineeringRear-view mirror
A device for warning a bicycle rider of an object approaching the bicycle rider from behind a bicycle with a rear view mirror mounted to the bicycle by a mounting assembly, a detector mounted to the bicycle and capable of detecting the object and determining if the object is approaching the bicycle rider from behind the bicycle, and an alarm in electrical communication with the detector, the alarm mounted on one of the mirror or the mounting assembly.
Owner:ZUZIAK ZBIGNIEW +1
Private information retrieval method in environment of a plurality of servers
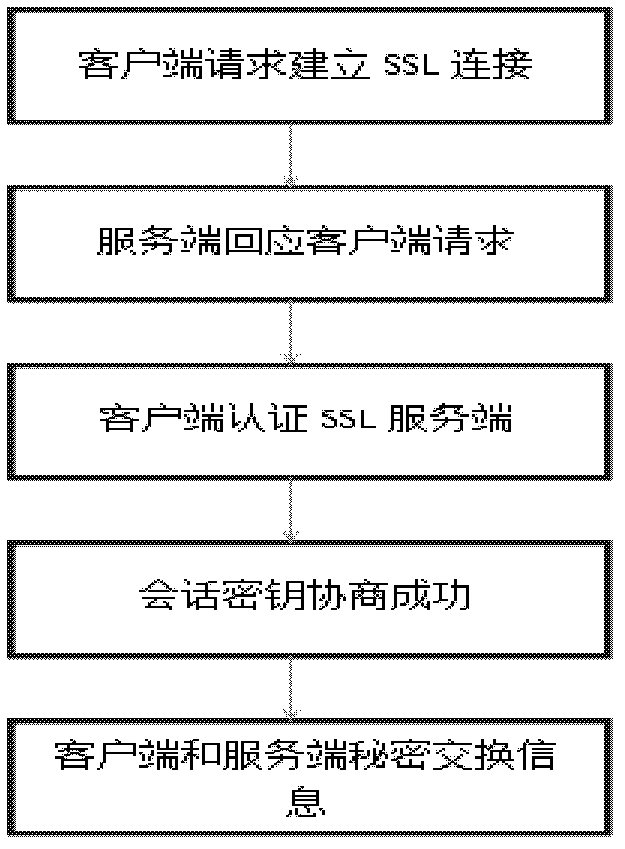
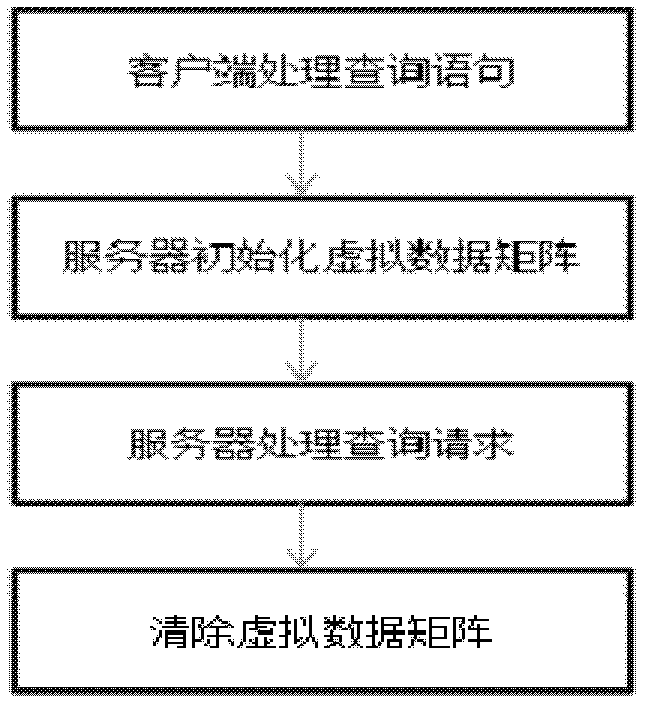
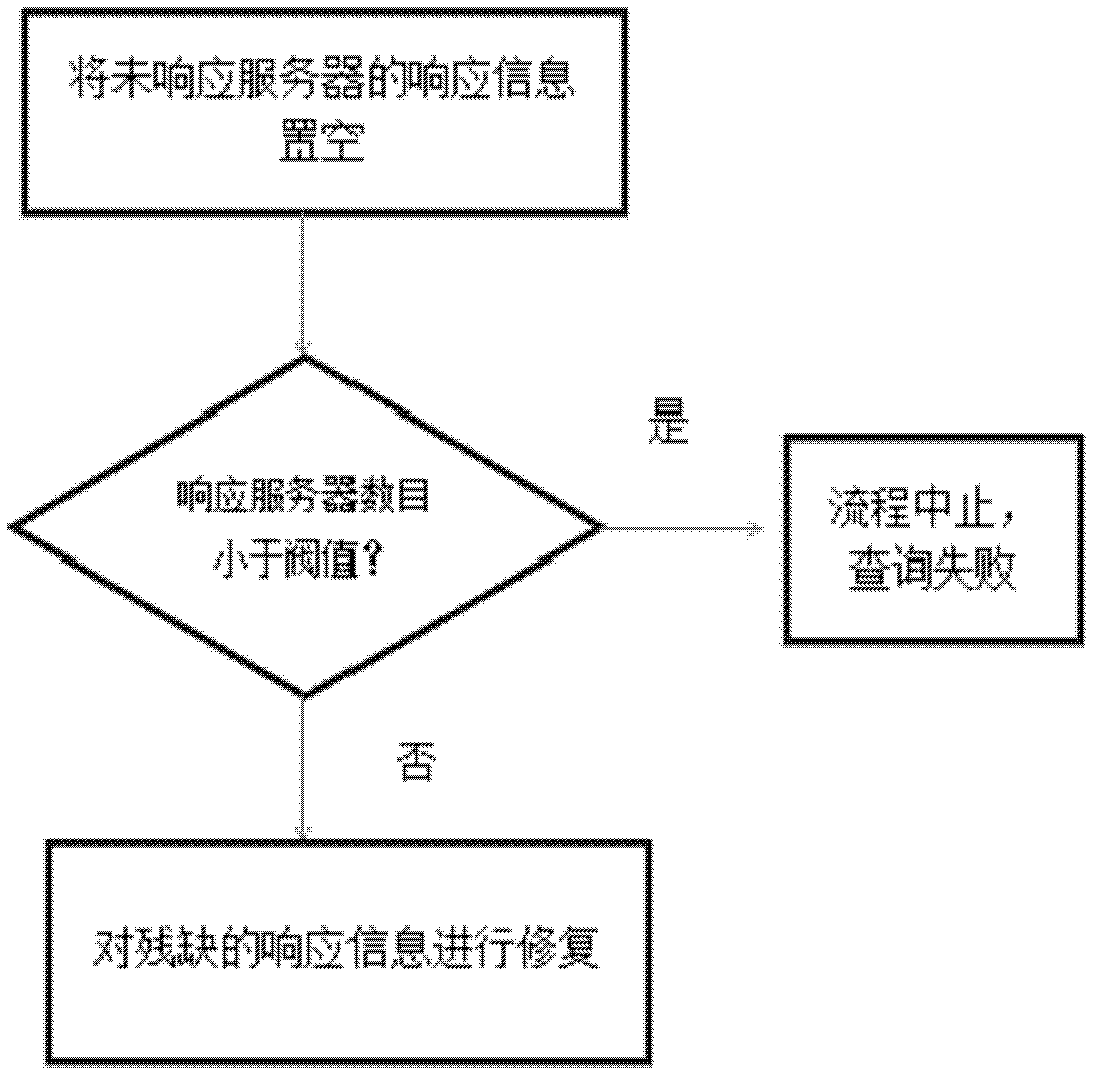
InactiveCN102629924AReduce threatTransmissionSpecial data processing applicationsDatabase serverClient-side
The invention discloses a private information retrieval method in the environment of a plurality of serves, which includes achieving confidential correspondence between a client and a server through a security socket layer (SSL) protocol; supporting mutual information retrieval between the client and the server through a secret sharing protocol and EIGamaI homomorphic encryption algorithm; and processing feedback information of the server with the Lagrange interpolation theory support through the client. According to the private information retrieval method, a virtual data matrix is presented for solving malicious saving and snooping of database servers to inquiring information of users, the retrieval of the client to the server can actually be performed on the virtual data matrix, thus, information on the virtual data matrix can be automatically cleared after the inquiring ends every time; the homomorphic encryption technology is applied in the search scheme of privacy information protection, and second encryption is performed to the secrete sharing vector of the inquiring information, accordingly, the threaten of a single server to the inquiring information is greatly reduced.
Owner:SHANGHAI JIAO TONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com