Patents
Literature
37 results about "Private information retrieval" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a private information retrieval (PIR) protocol is a protocol that allows a user to retrieve an item from a server in possession of a database without revealing which item is retrieved. PIR is a weaker version of 1-out-of-n oblivious transfer, where it is also required that the user should not get information about other database items. One trivial, but very inefficient way to achieve PIR is for the server to send an entire copy of the database to the user.
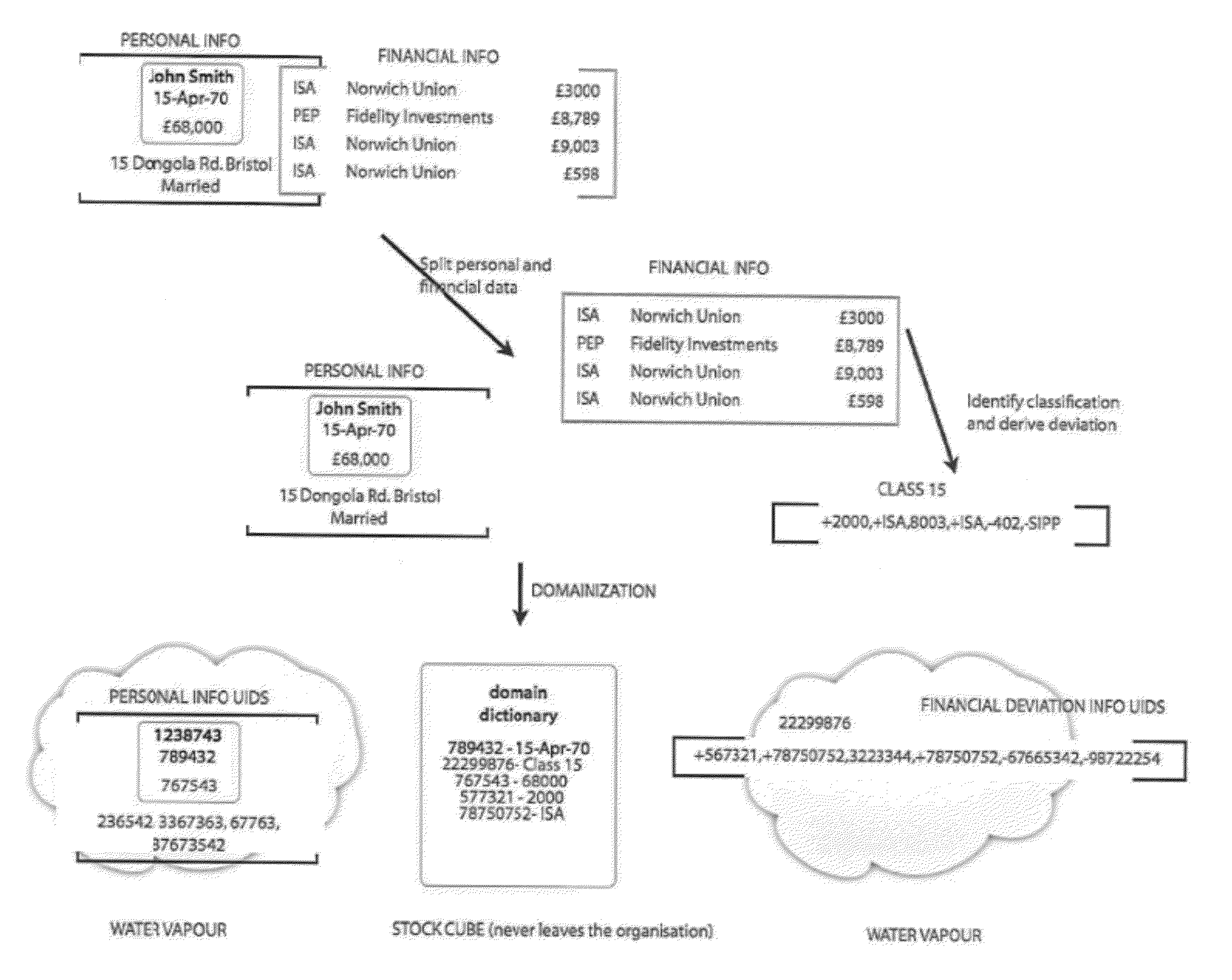
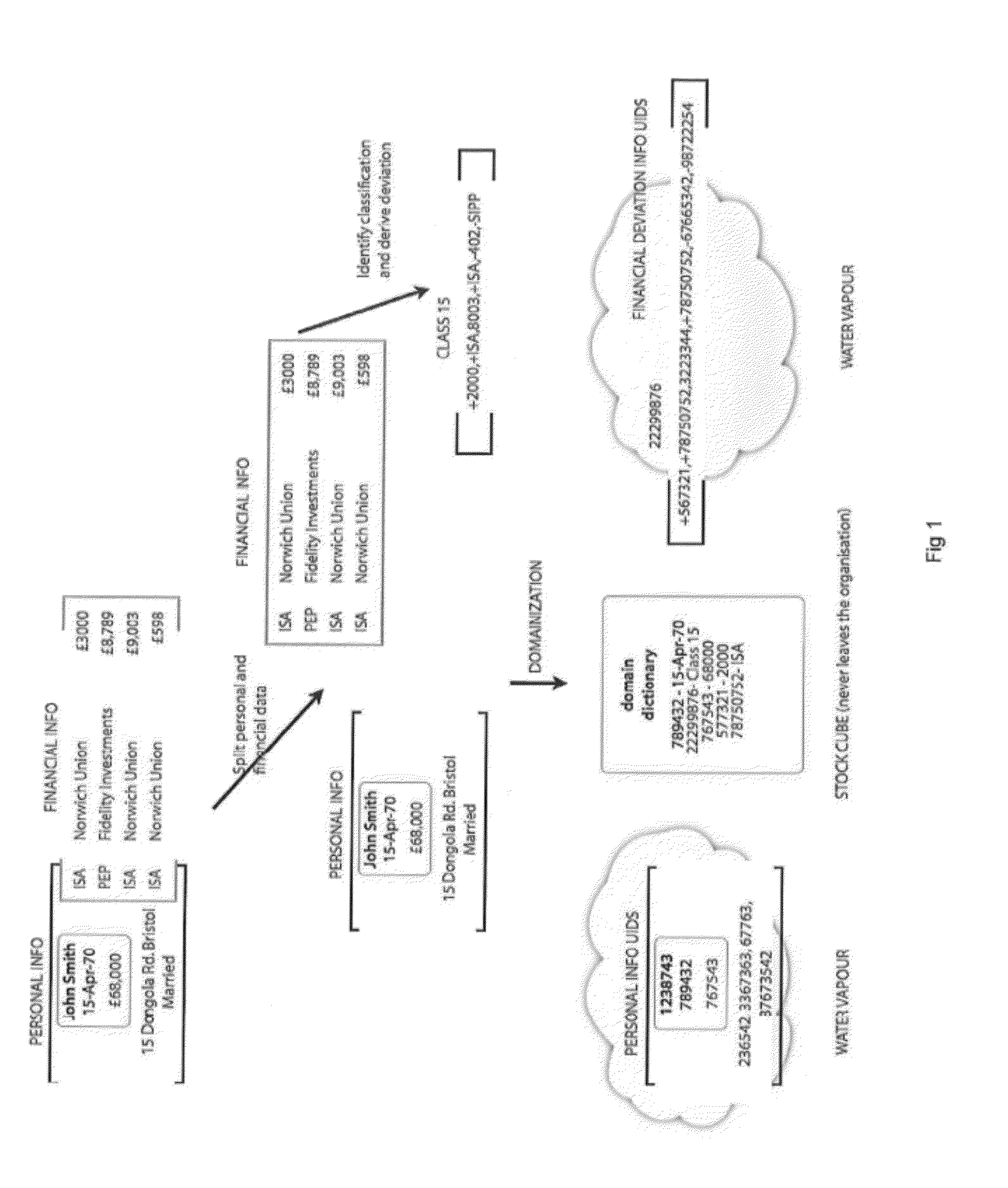
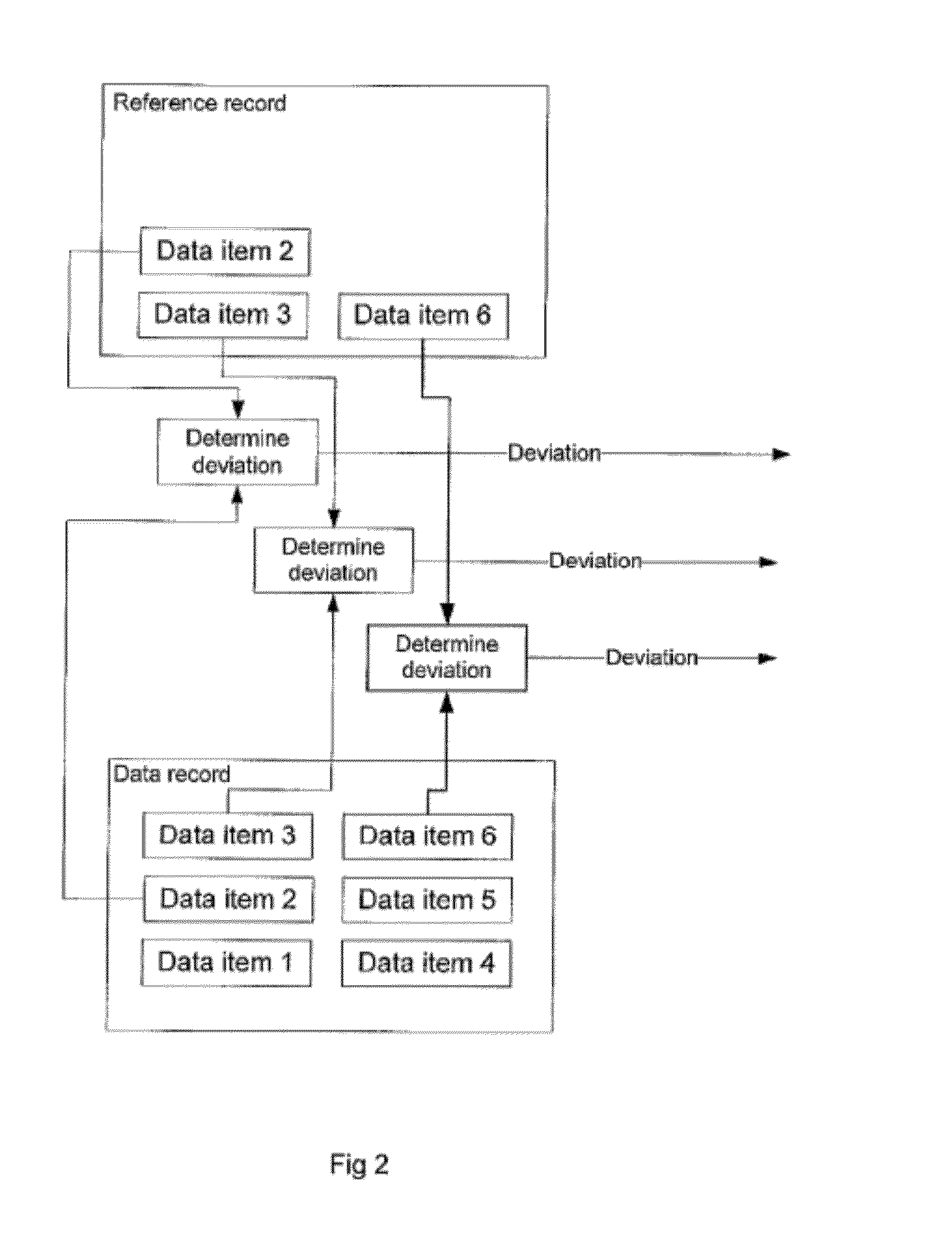
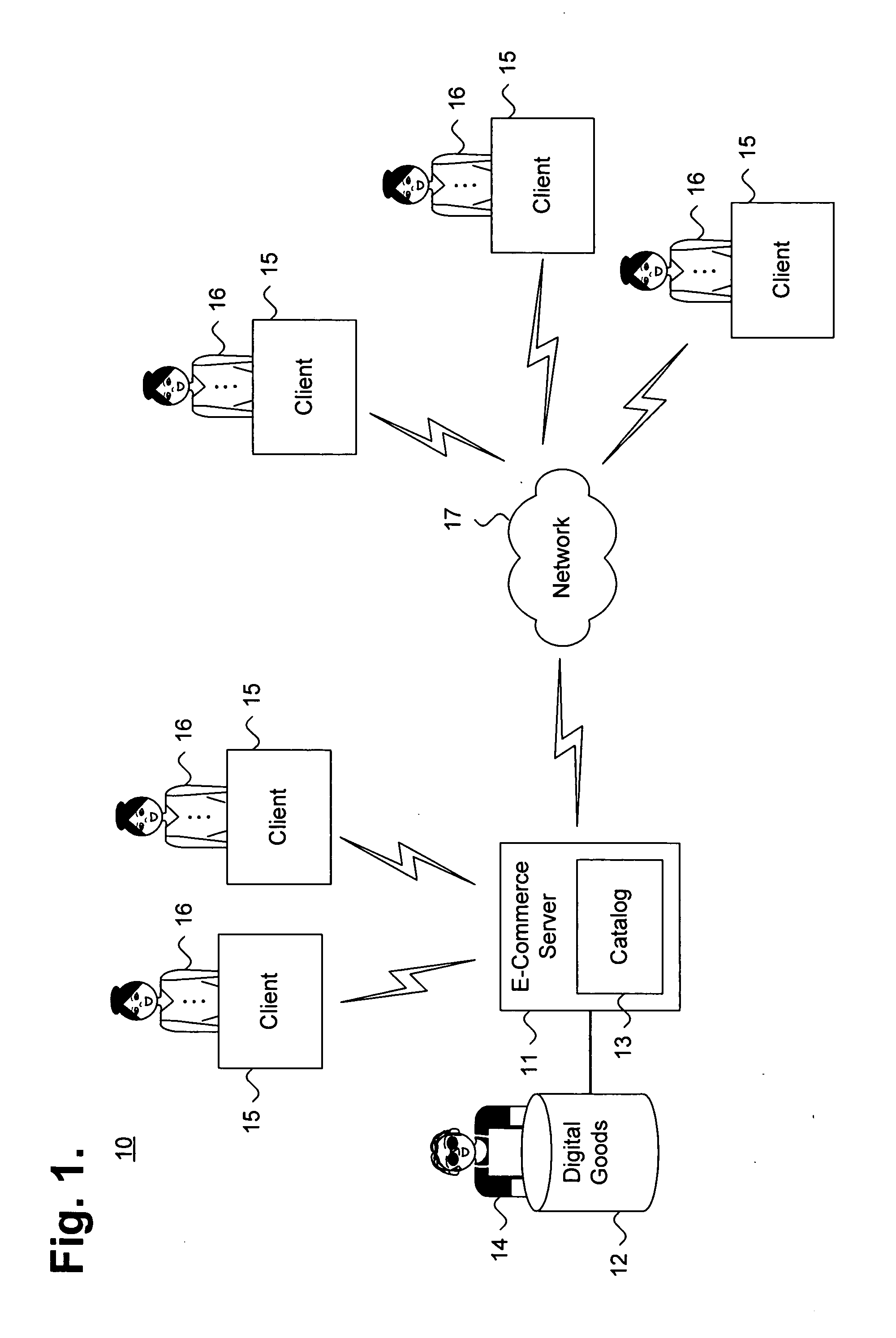
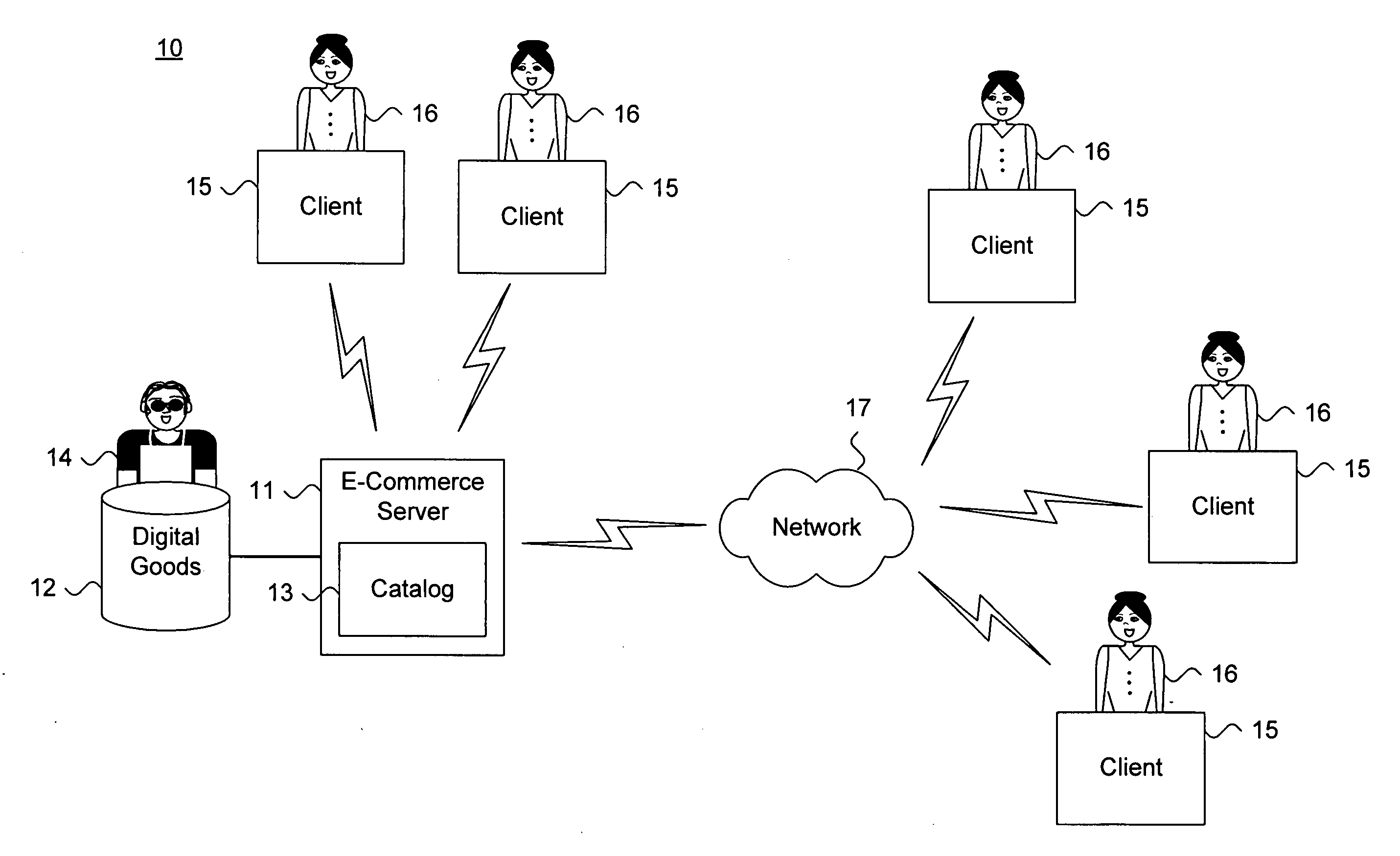
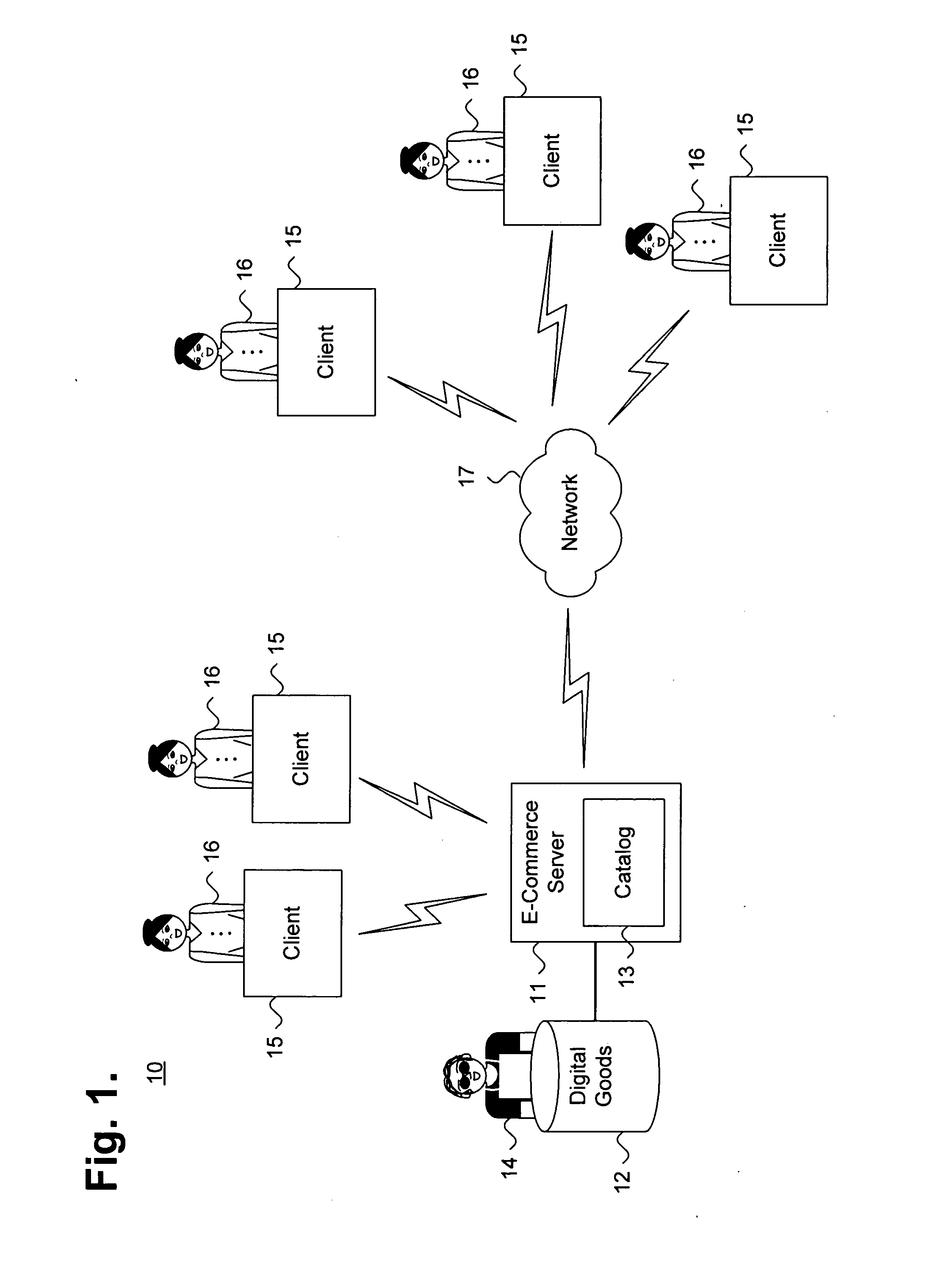
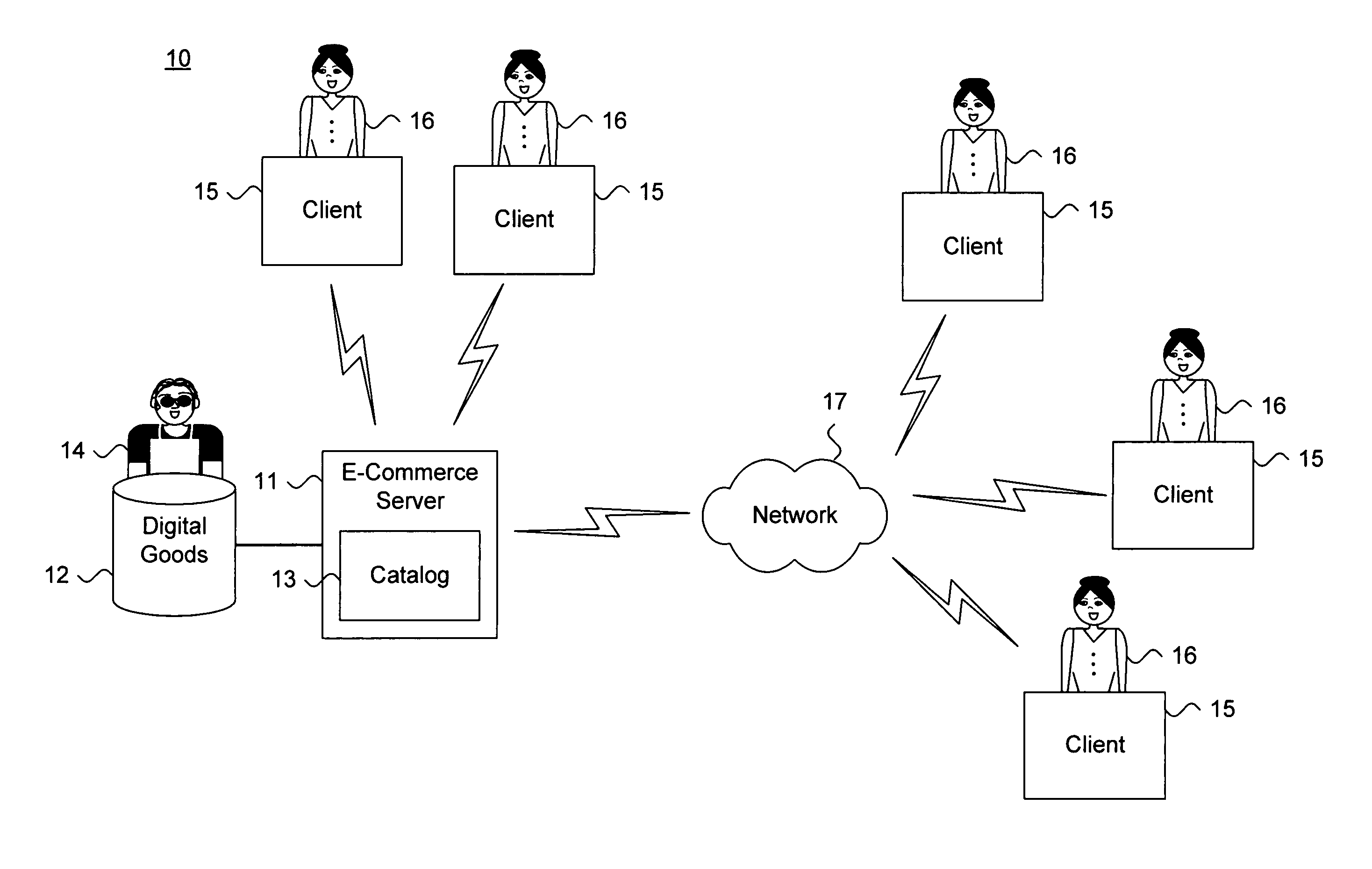
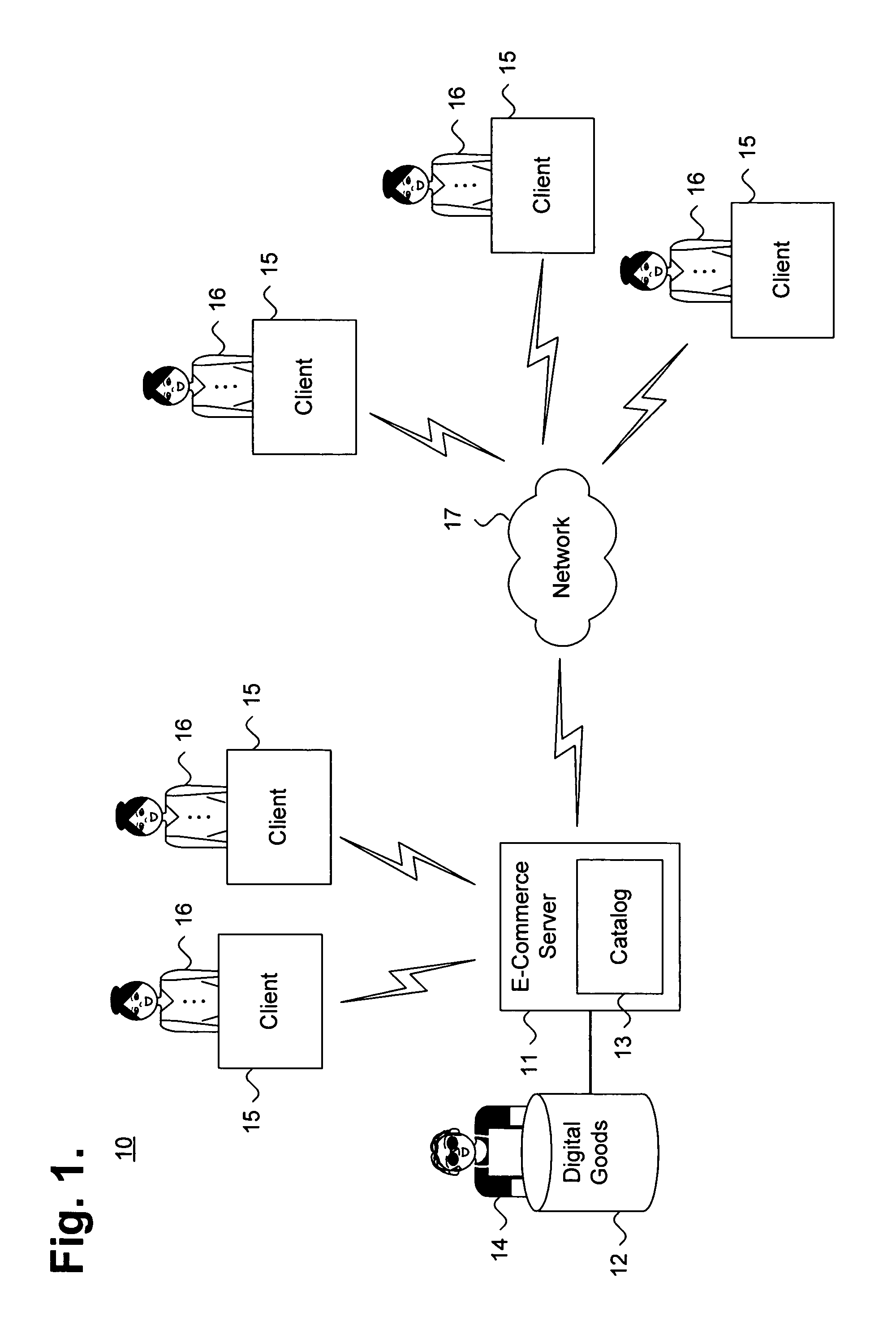
Private information storage system
This invention relates to a scheme for storage of private information on a cloud computing platform without contravention of territorial privacy laws. A method of anonymising a database of personal data is described whereby data identifiers are assigned to data items and deviation identifiers are assigned to deviations for selected data items derived from reference records. Such information can then be uploaded to a cloud based storage platform. A translation table maps the data items, data identifiers and deviation identifiers to the original data entries. This translation table is stored locally and separate to the anonymised information uploaded to the cloud. The invention further describes a method of decoding the database anonymised according to the above method.
Owner:ANZEN TECH SYST LTD
Method and apparatus for communication efficient private information retrieval and oblivious transfer
ActiveUS20050259817A1Data processing applicationsPublic key for secure communicationOblivious transferData mining
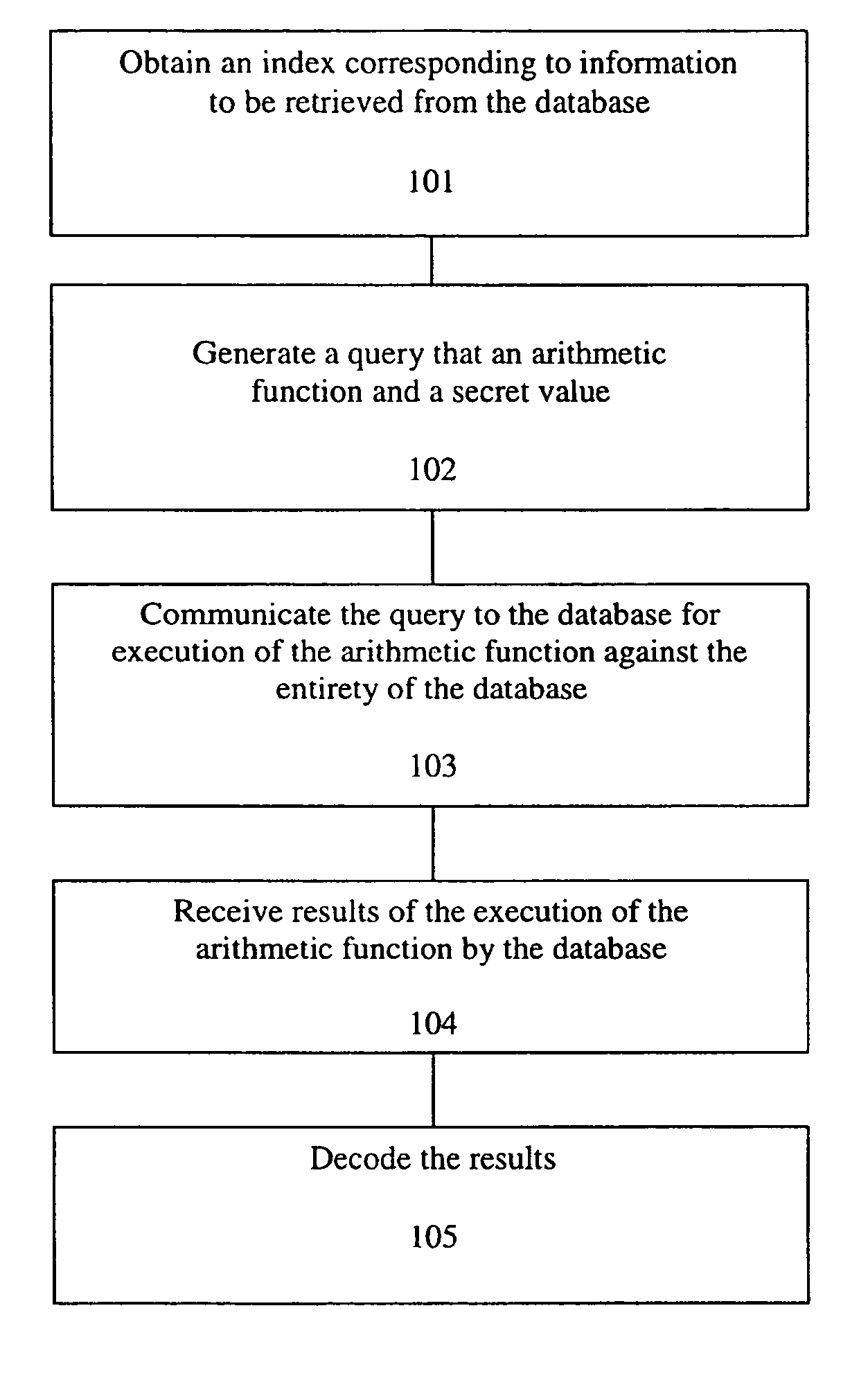
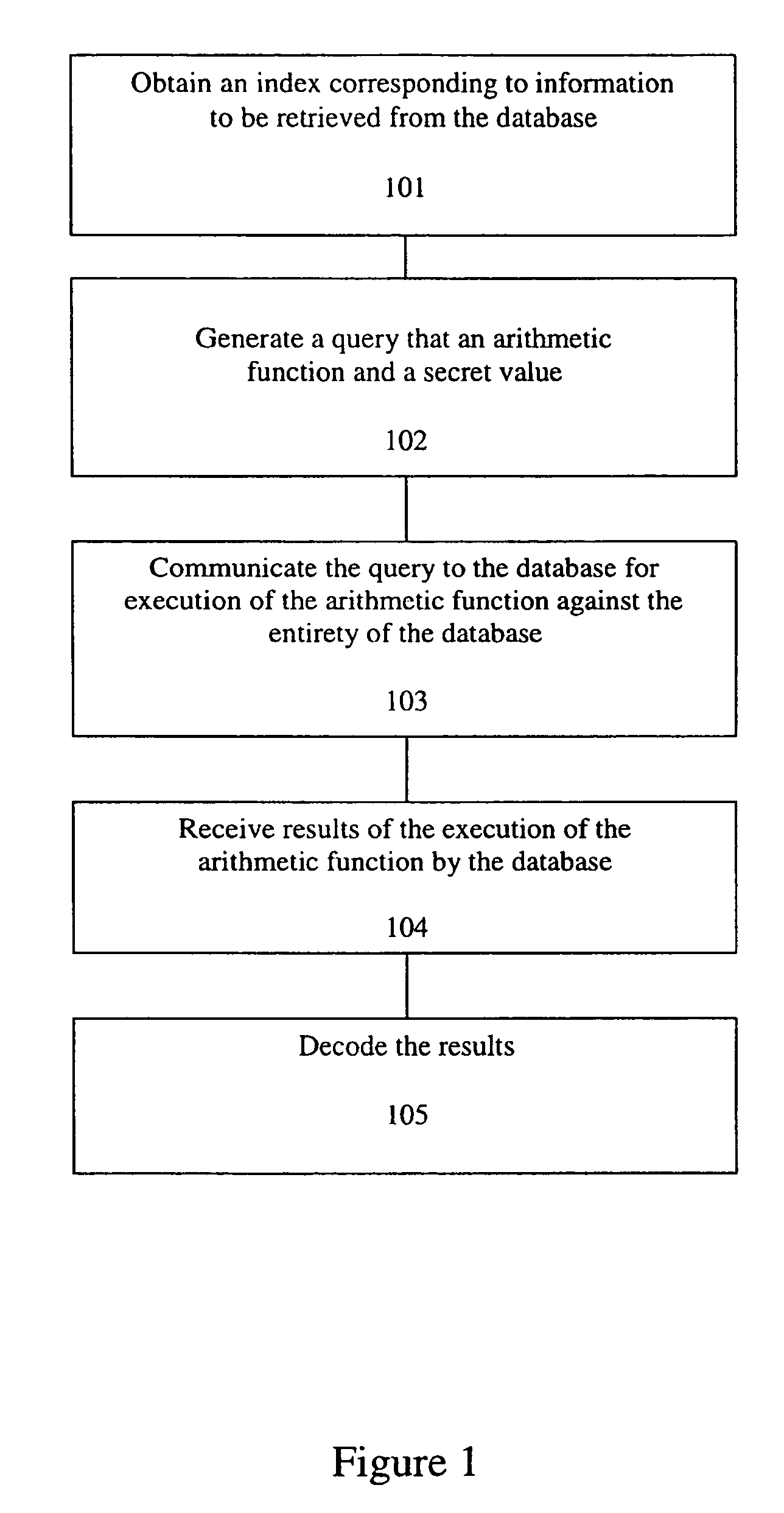
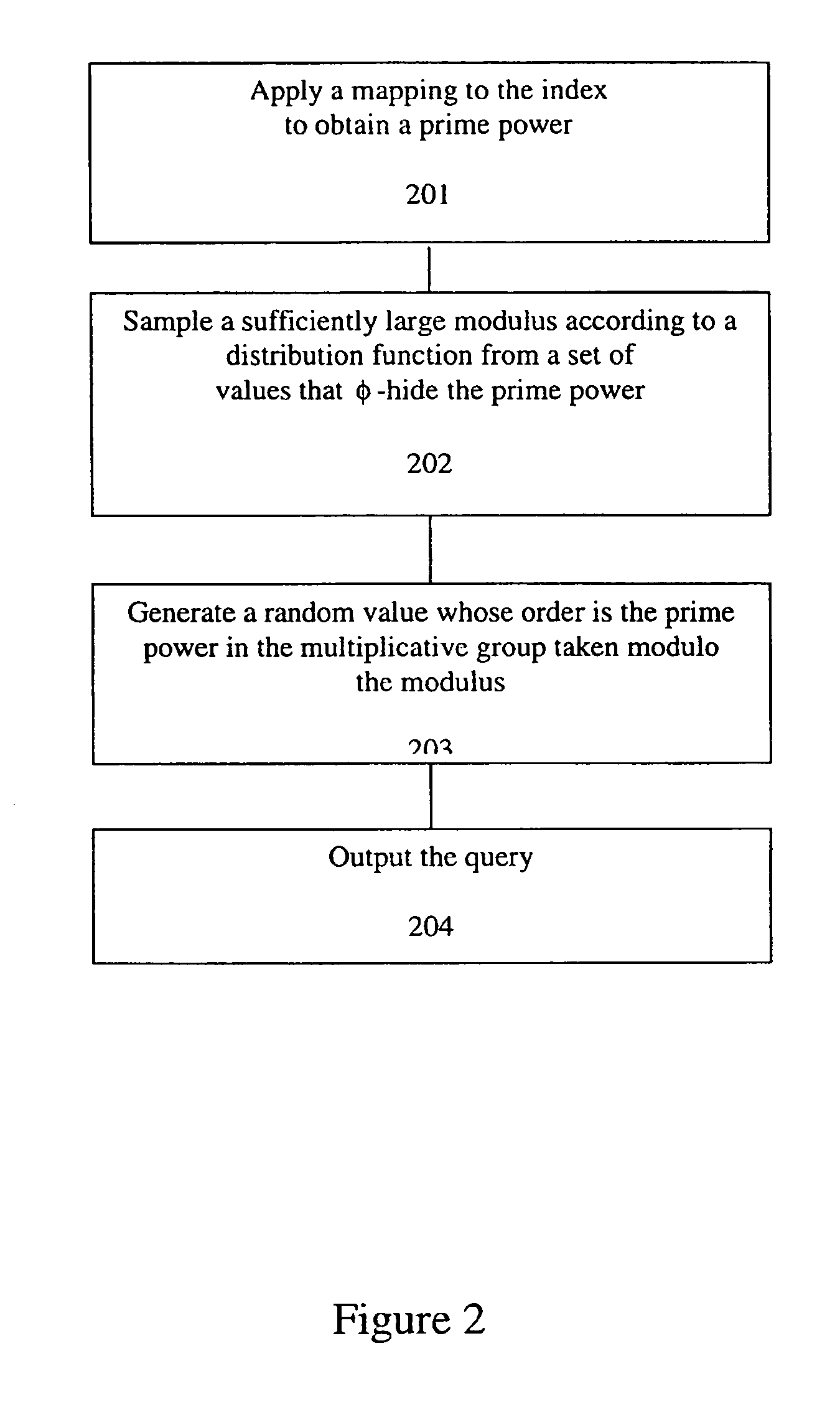
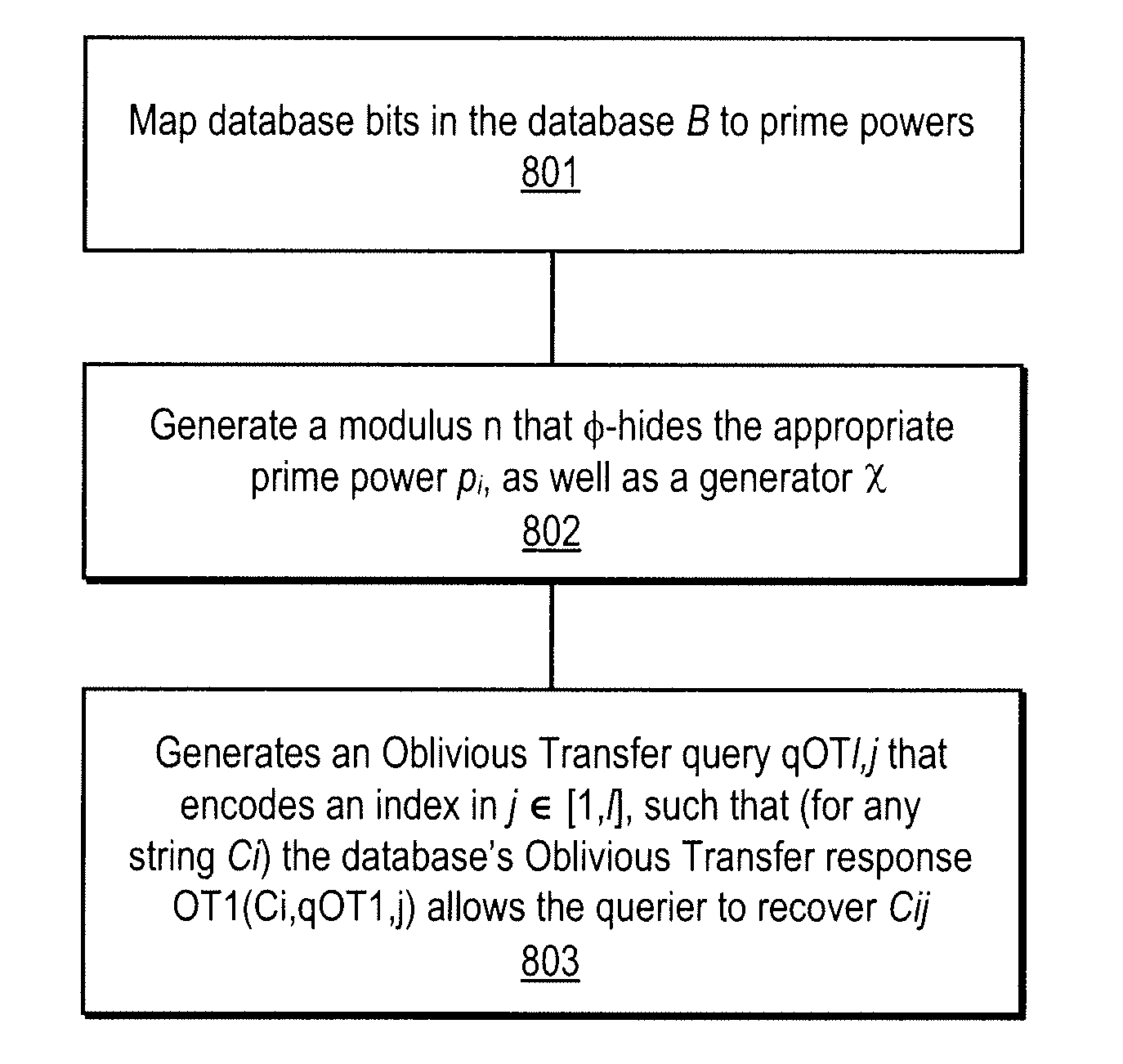
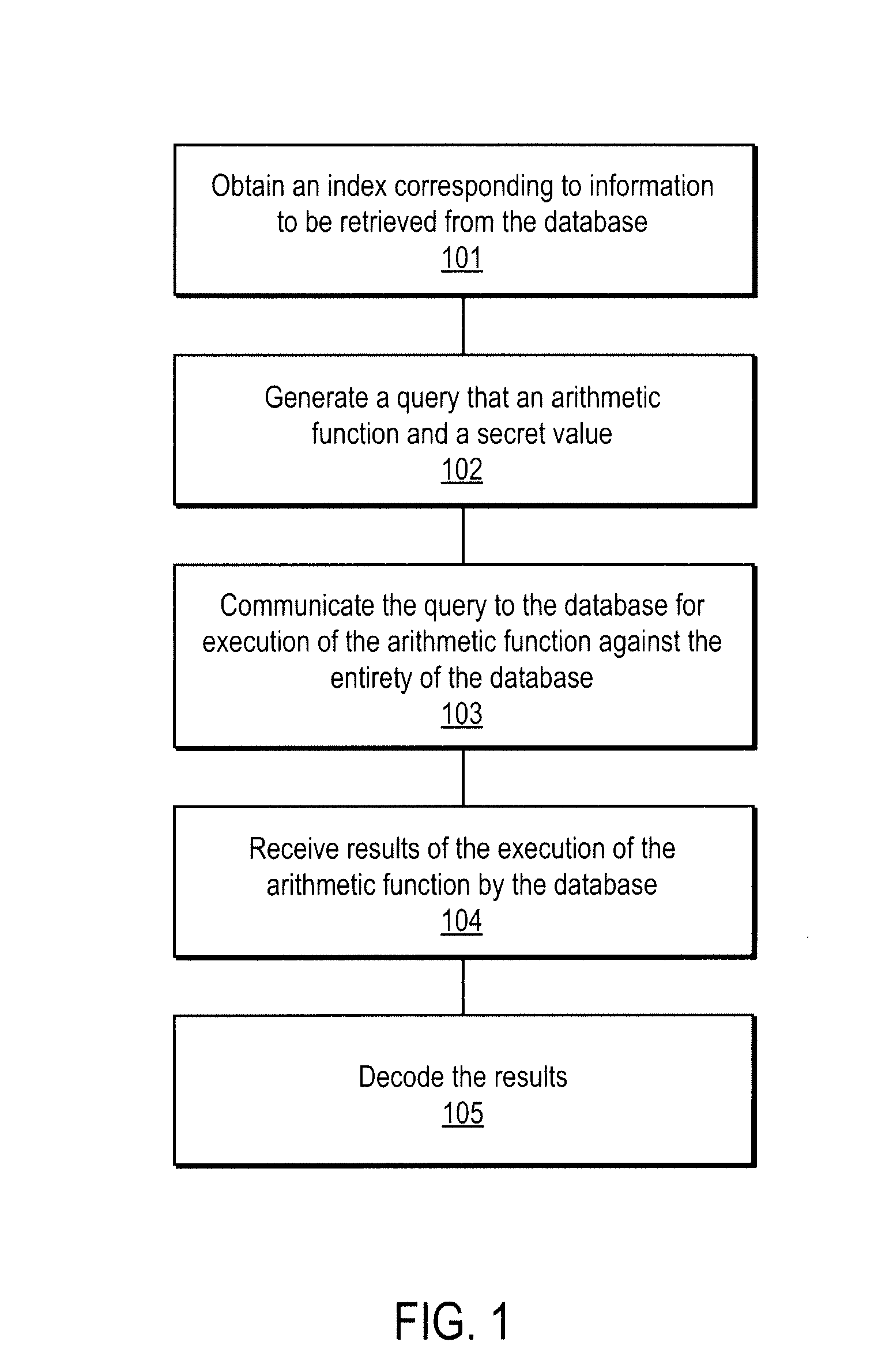
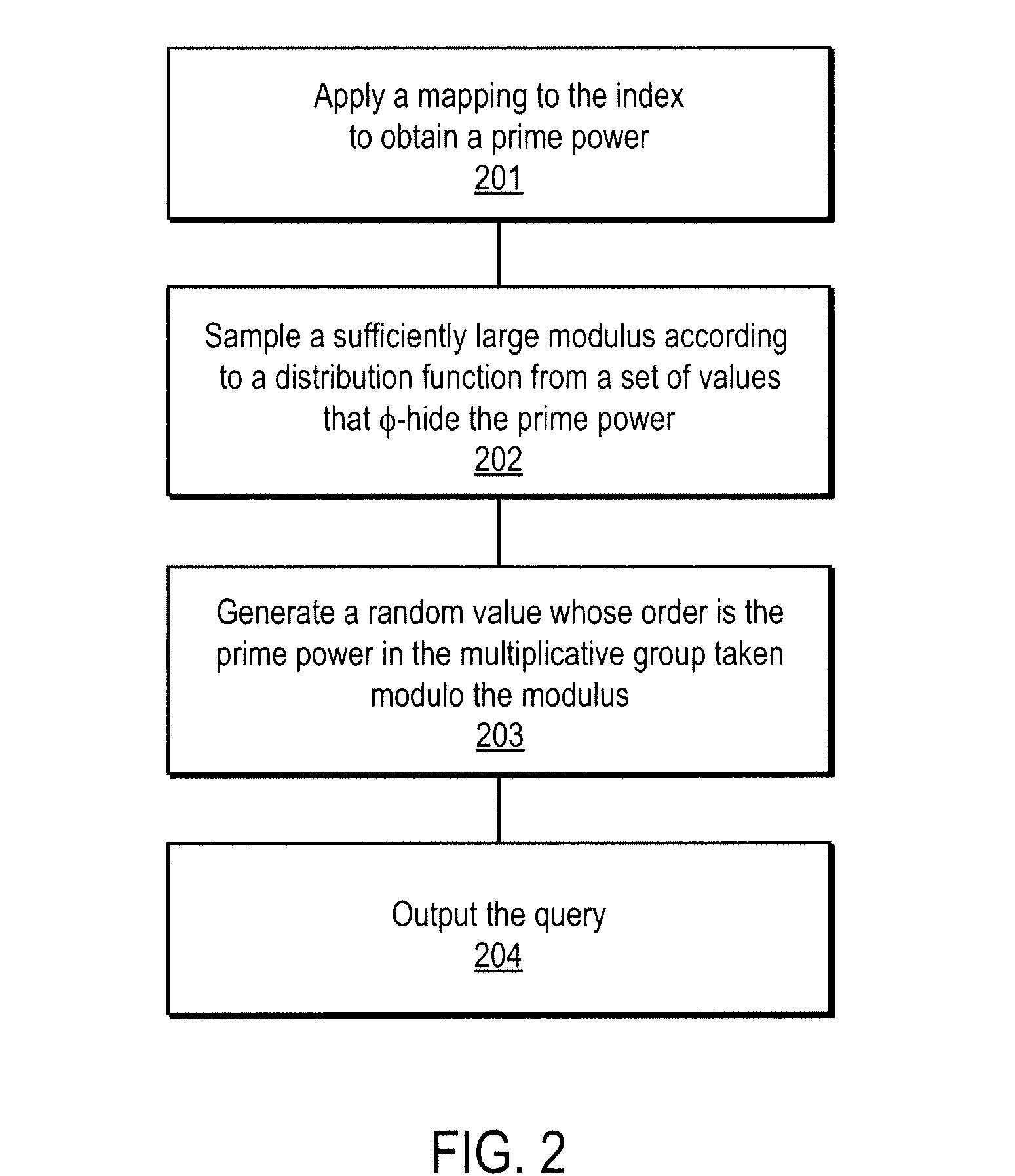
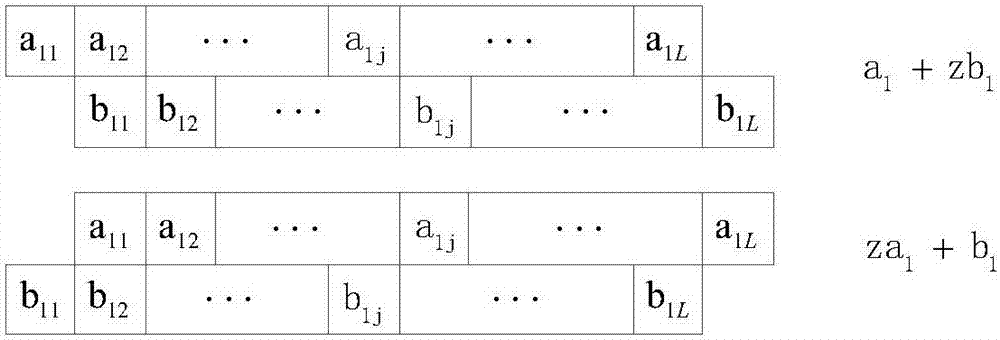
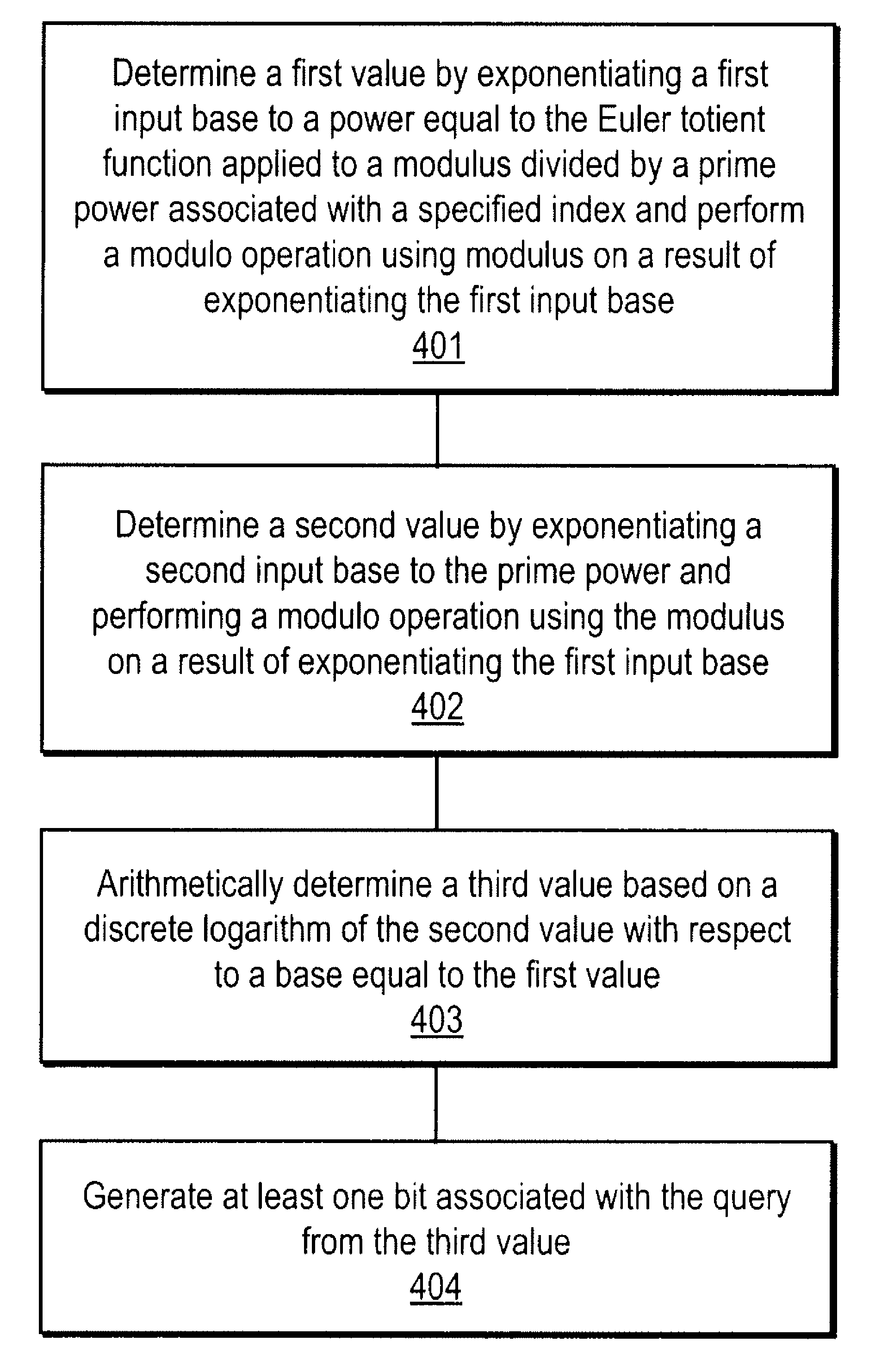
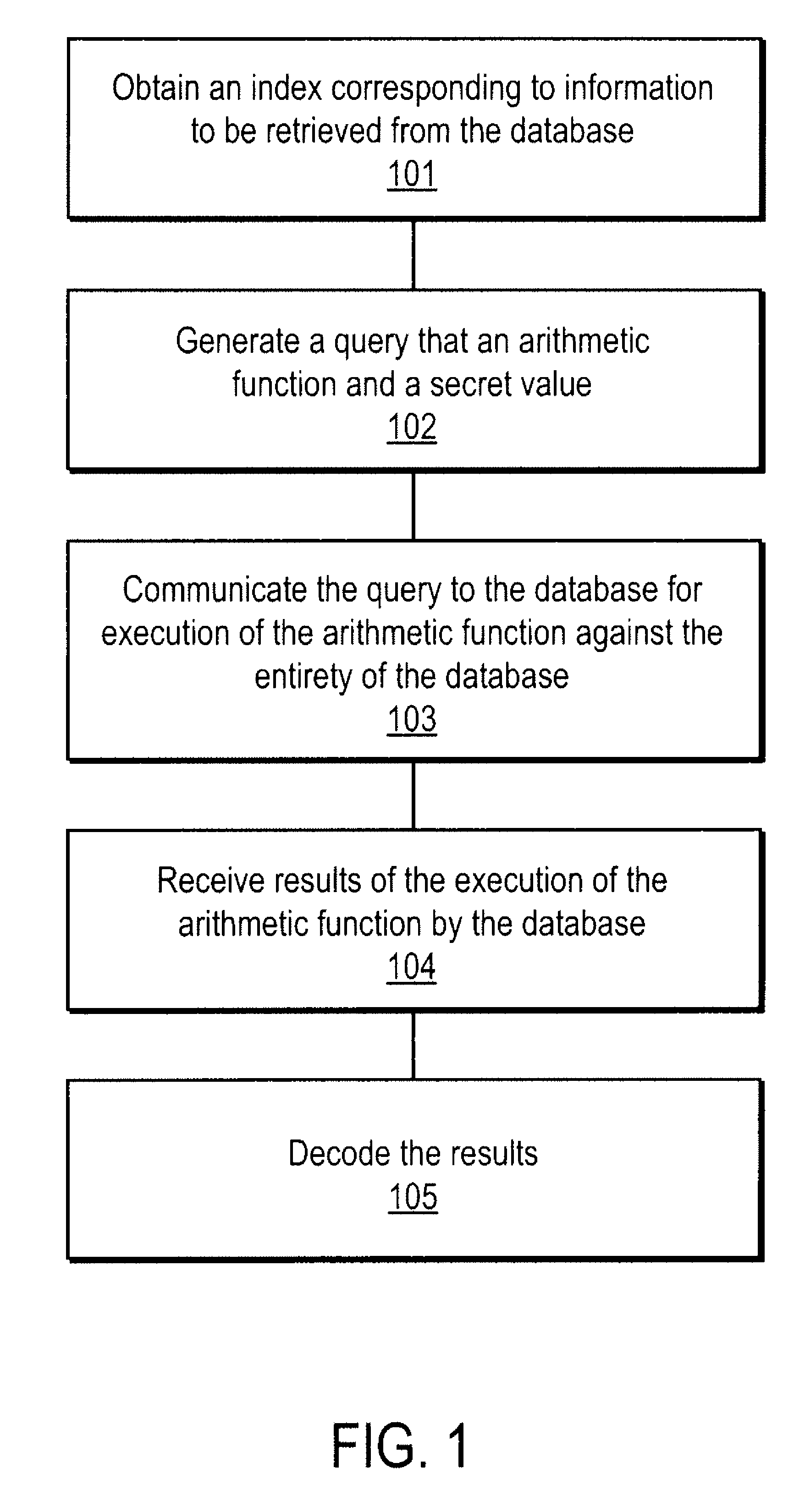
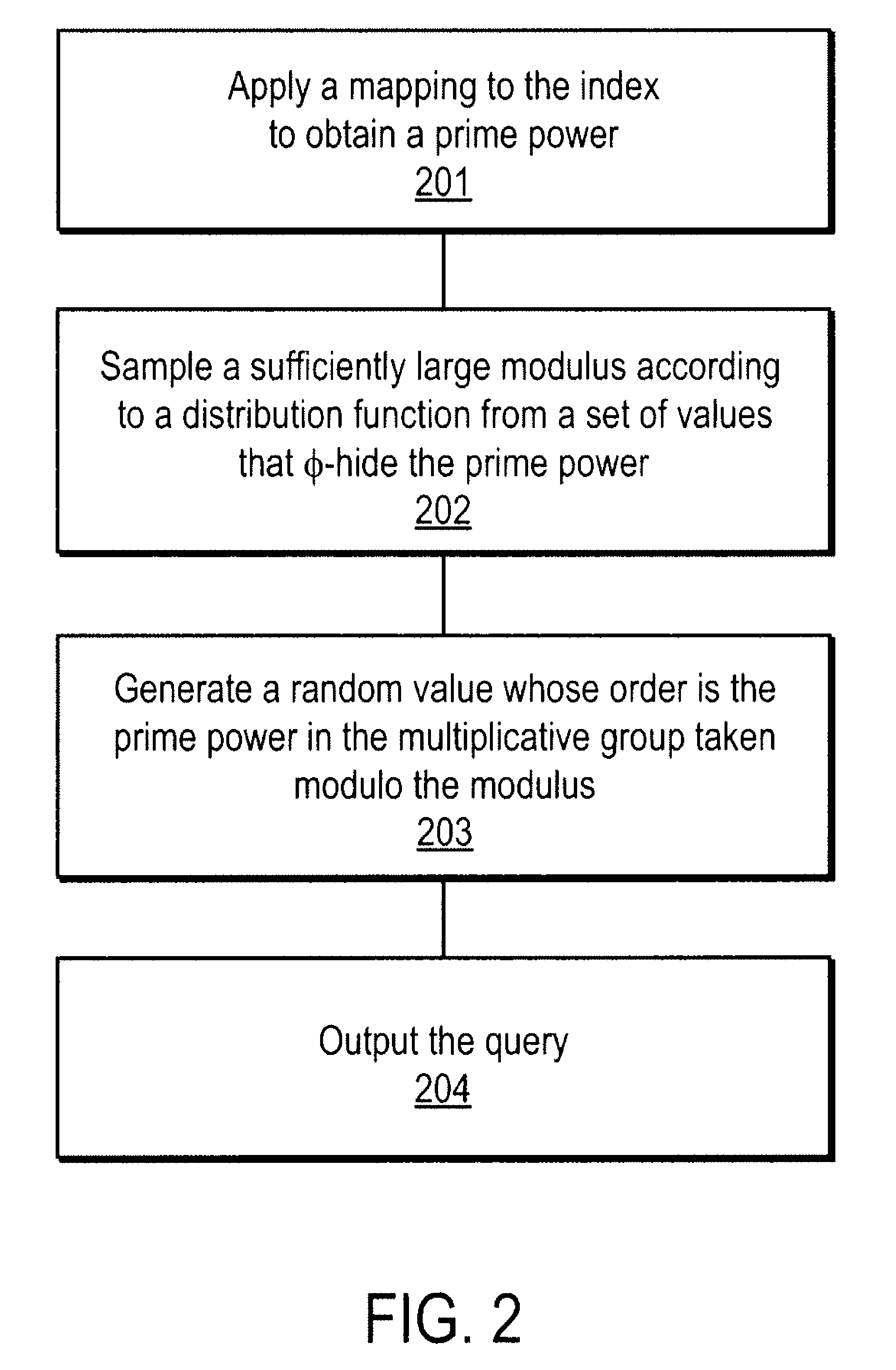
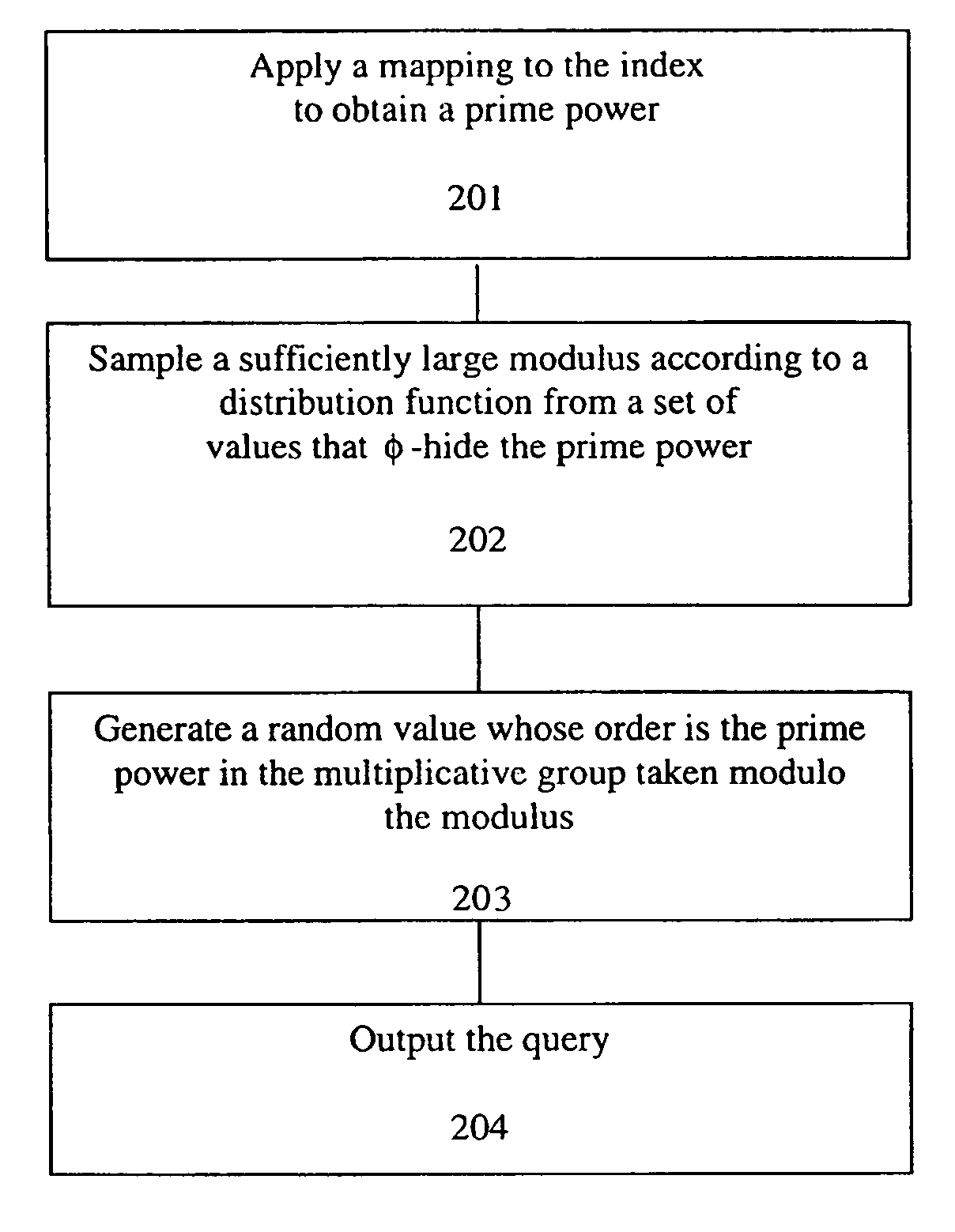
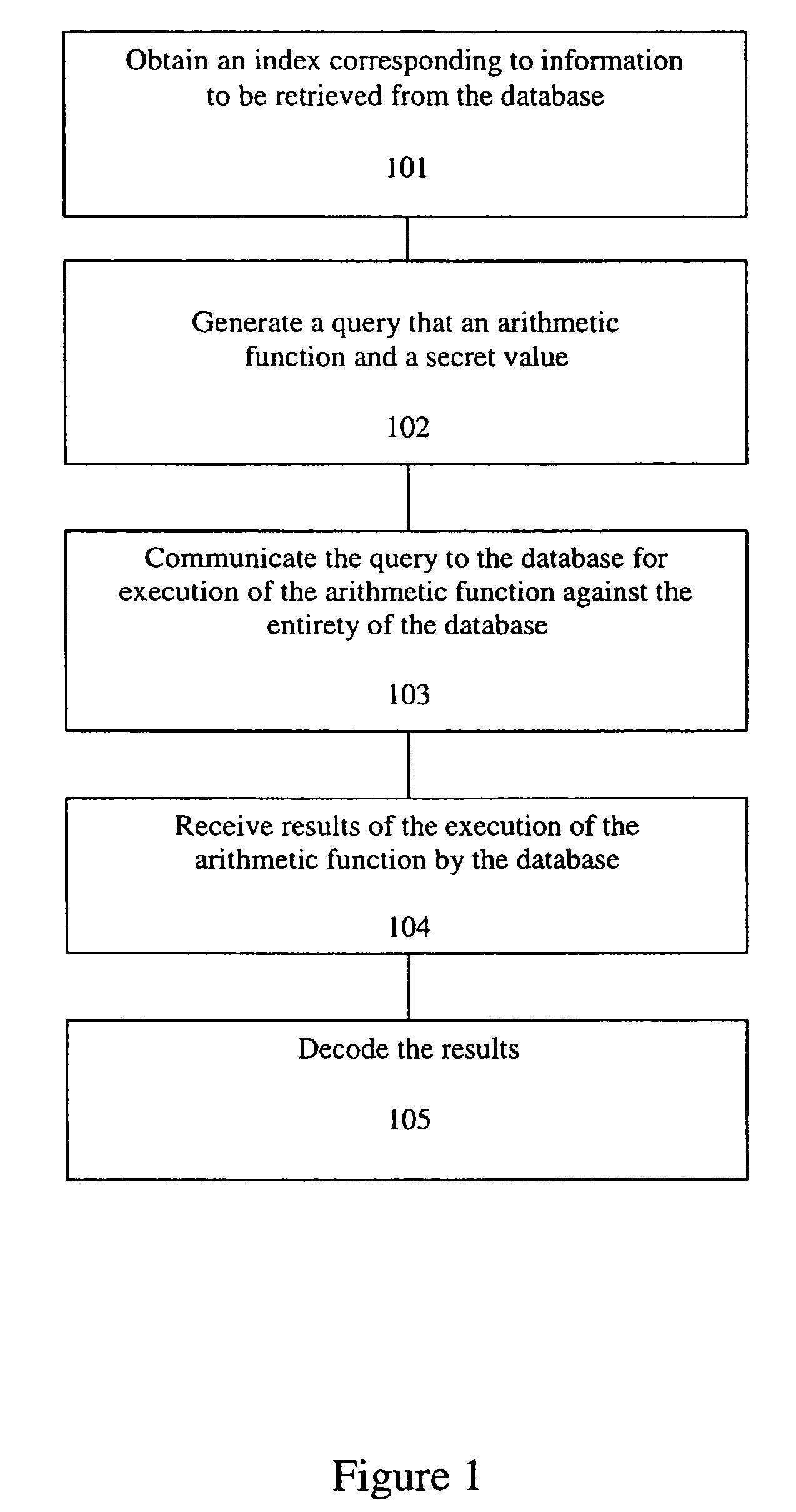
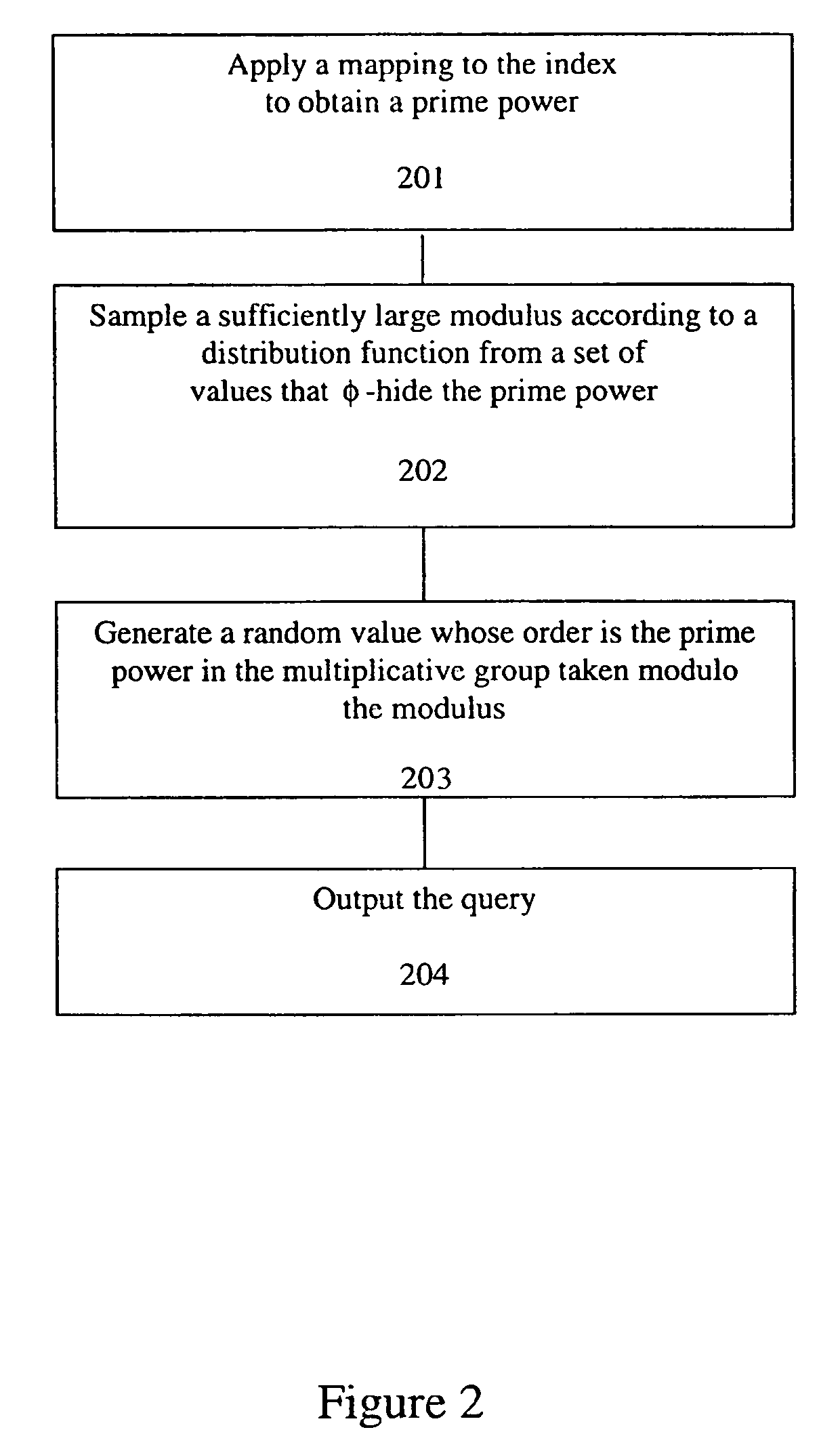
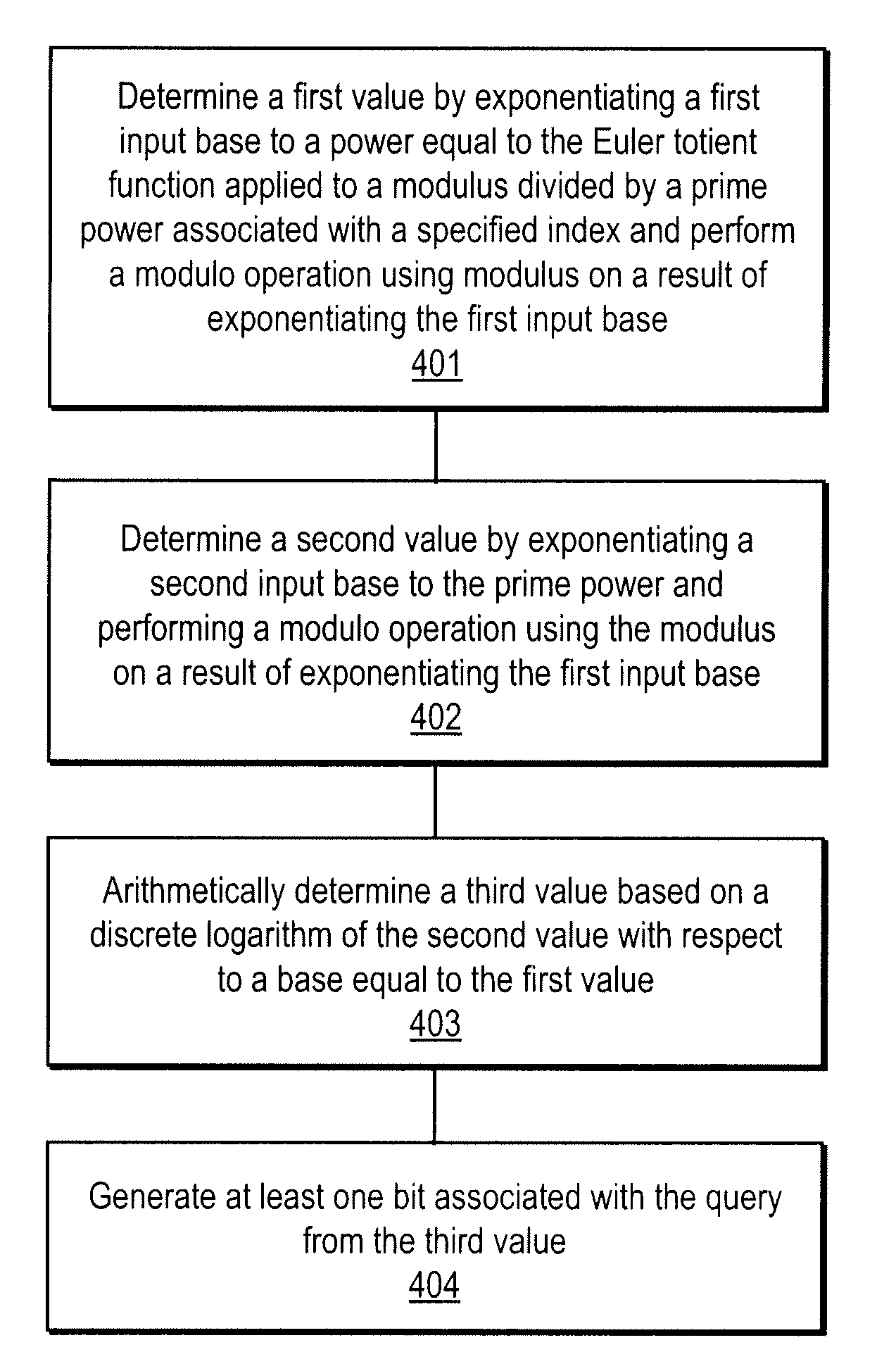
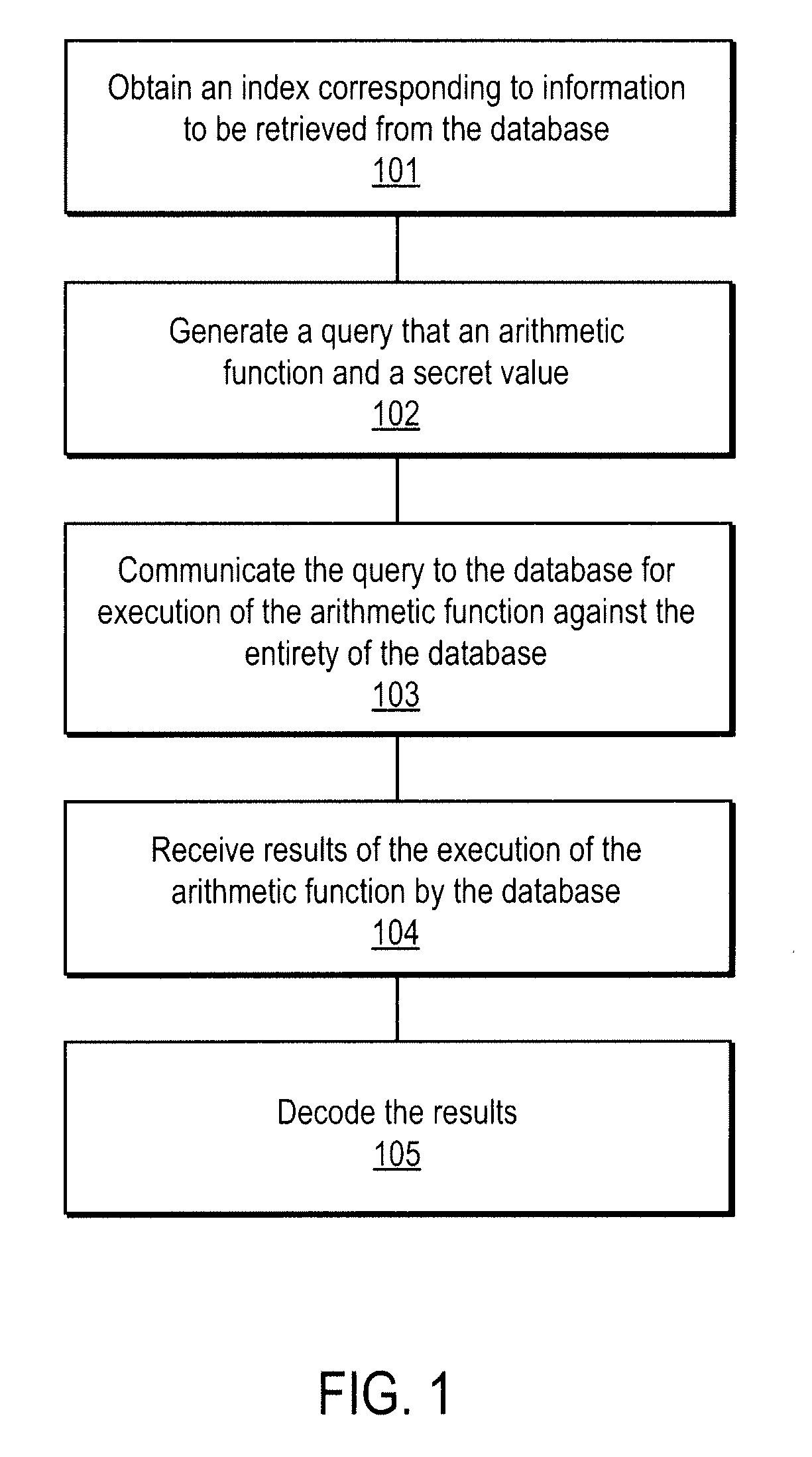
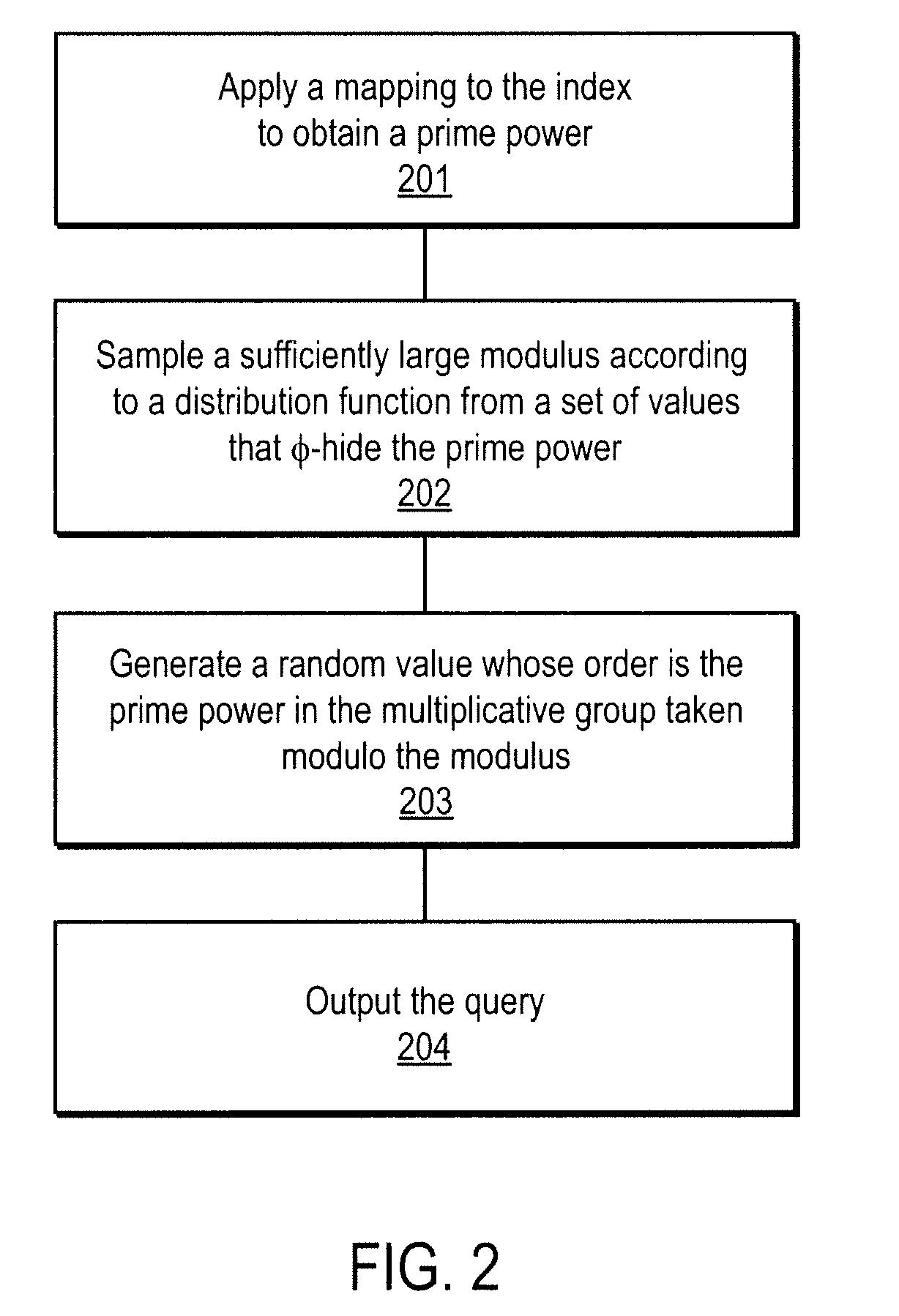
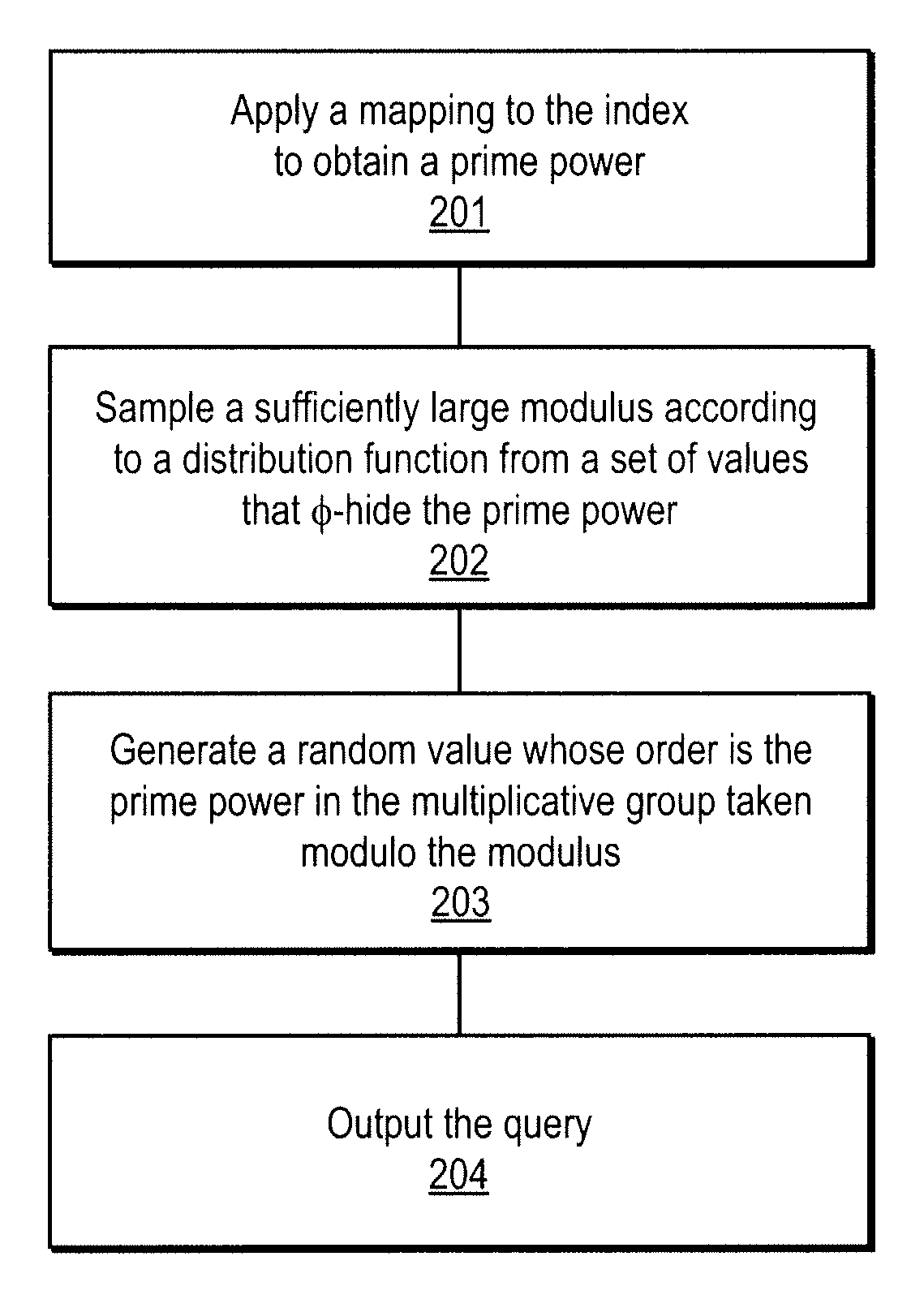
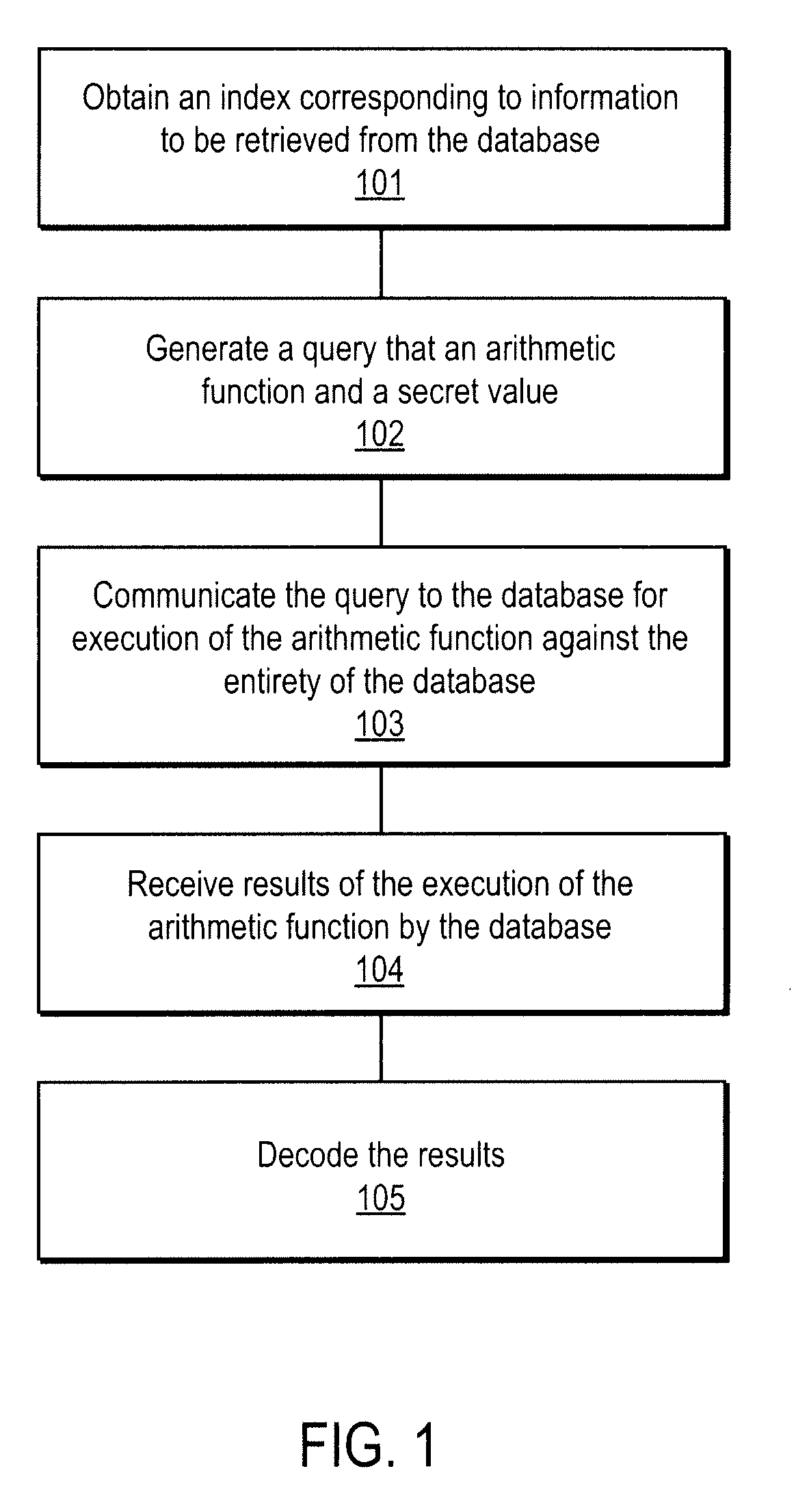
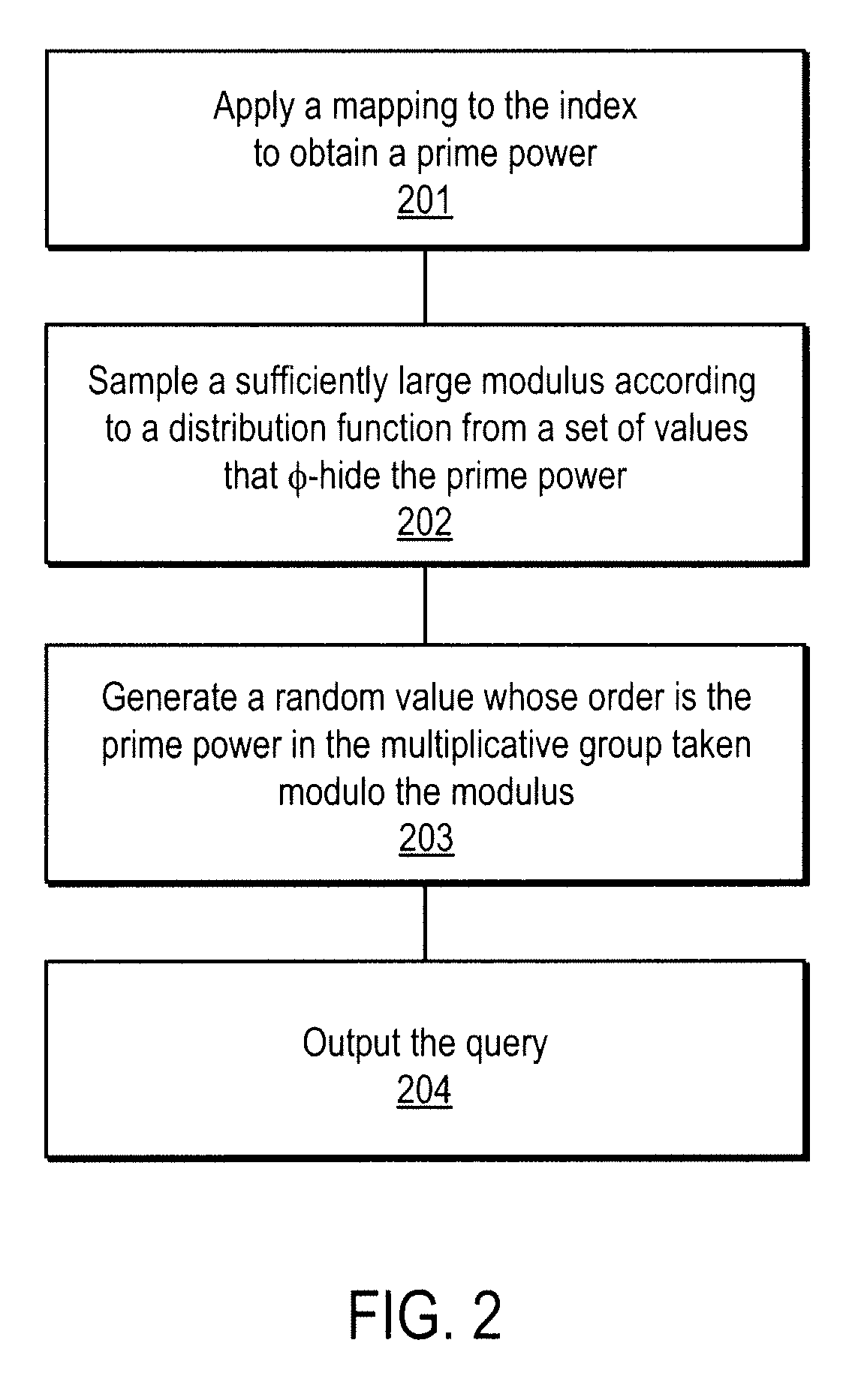
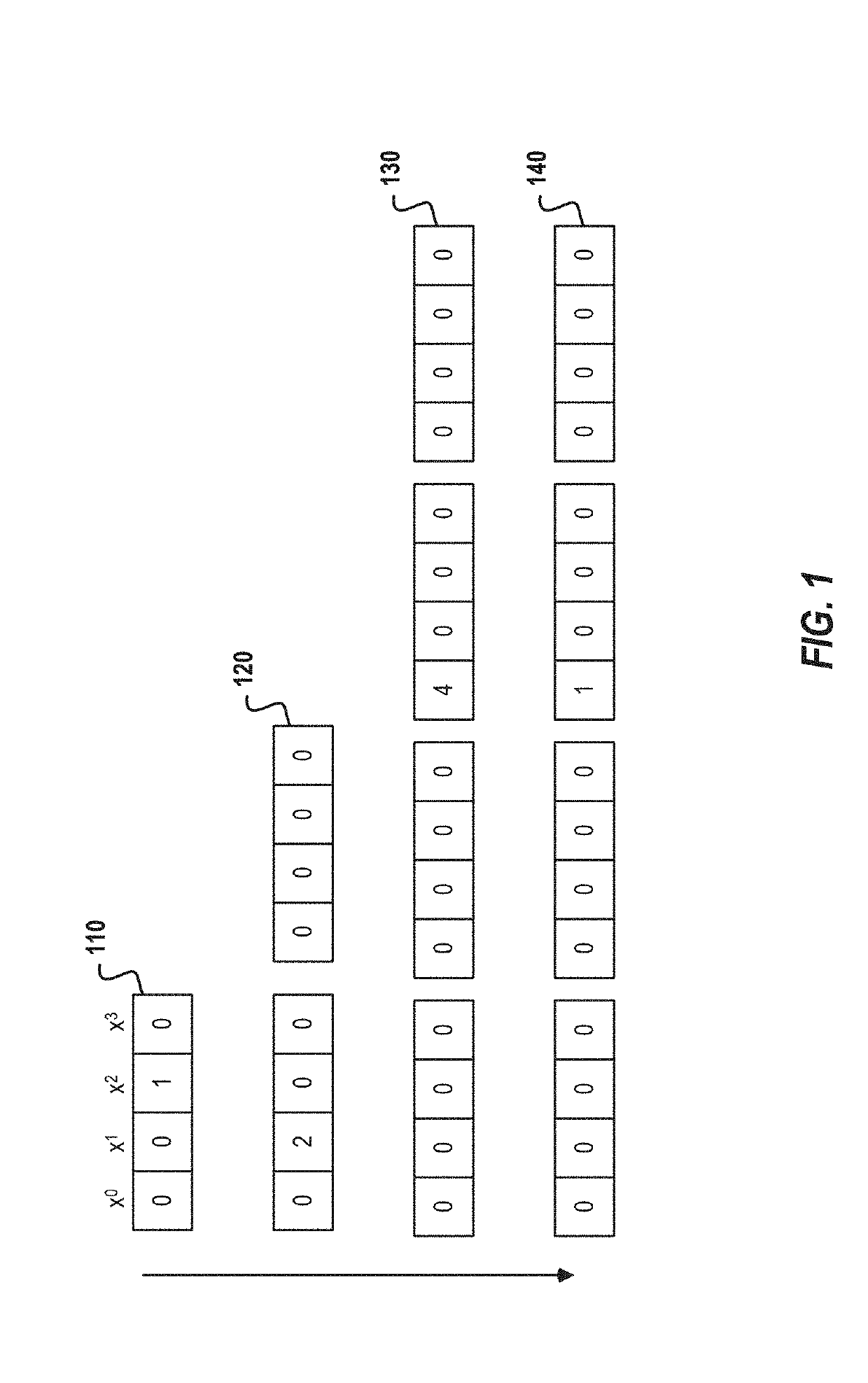
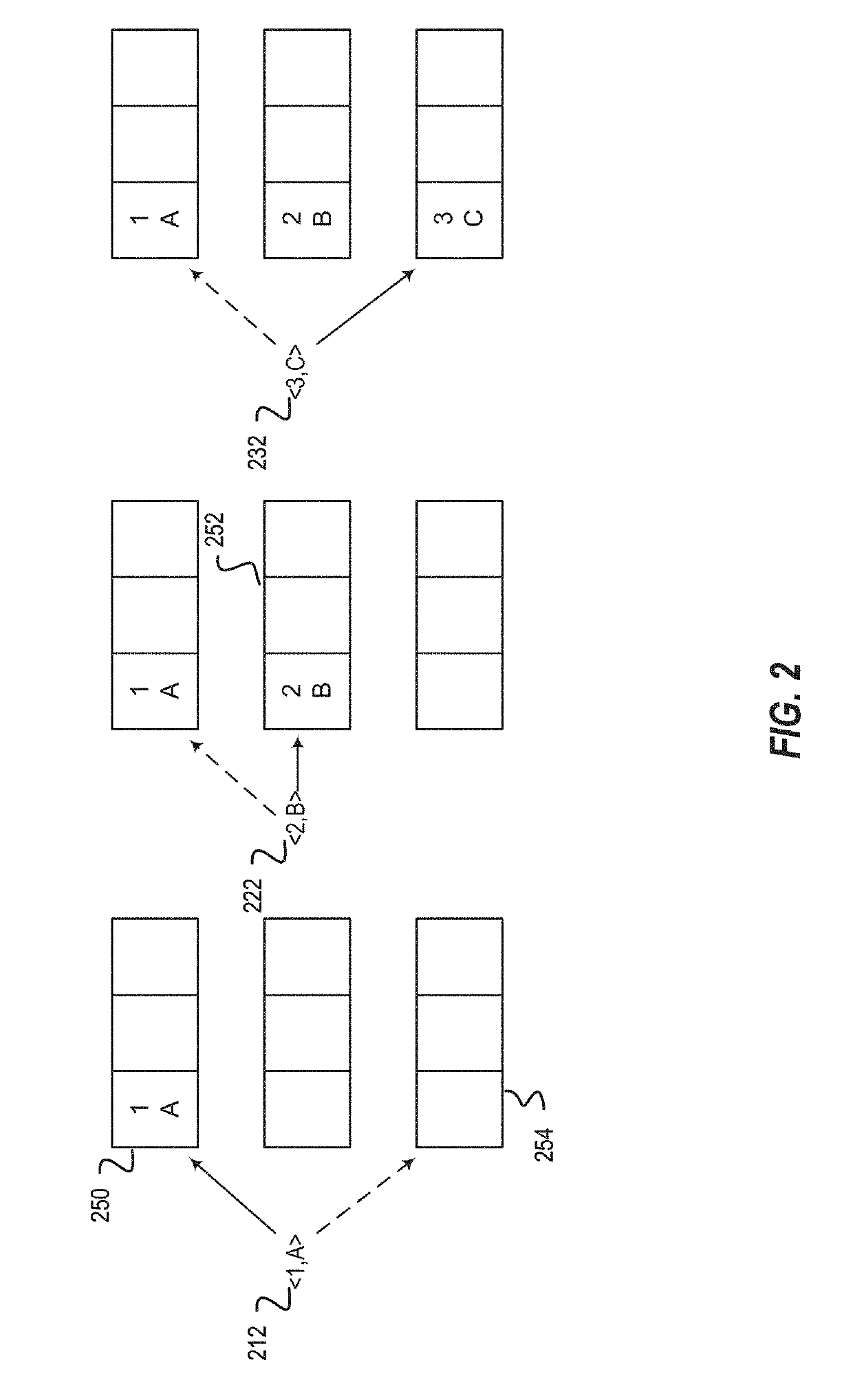
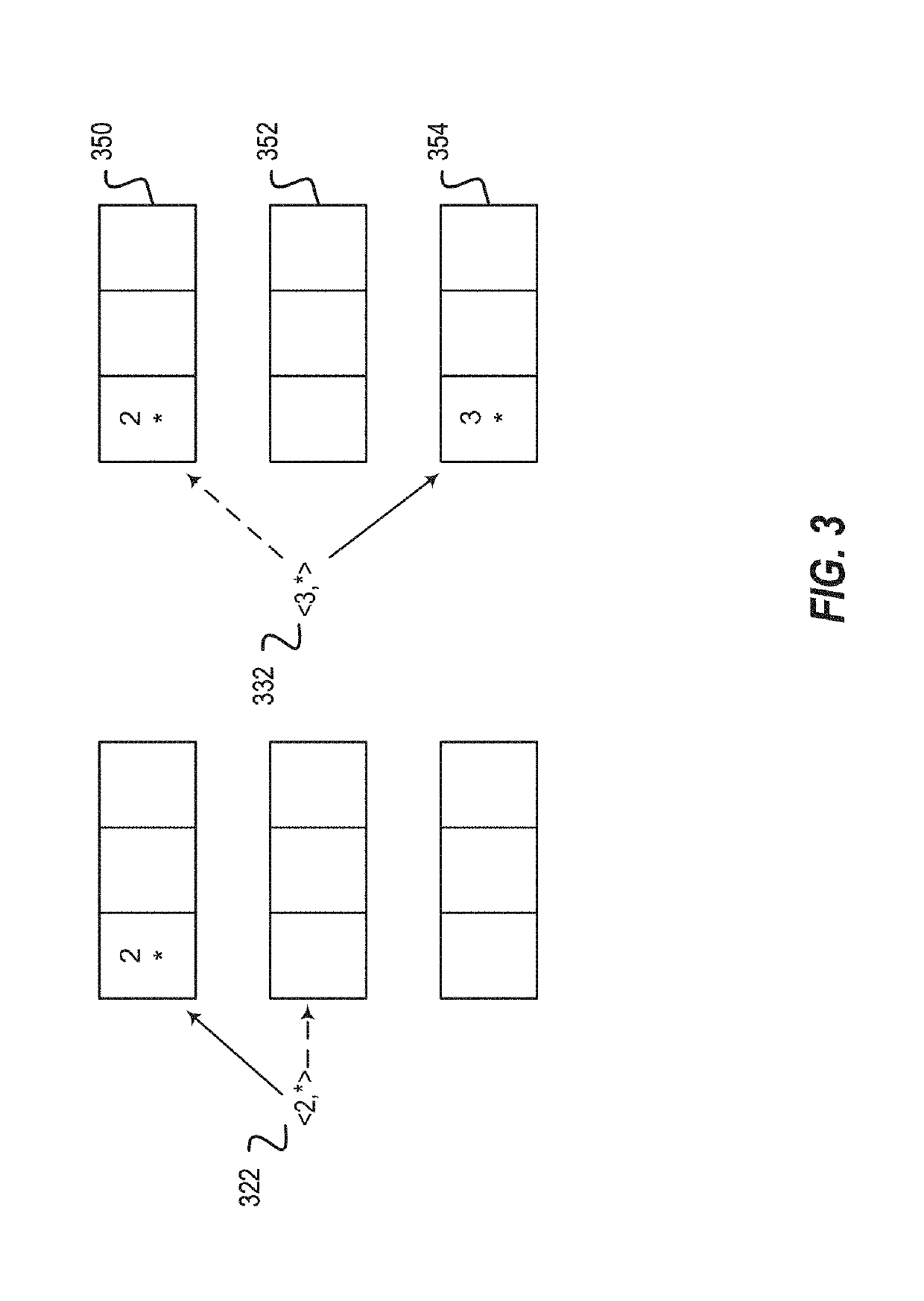
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
Method and apparatus for communication efficient private information retrieval and oblivious transfer
InactiveUS20090193033A1Digital data processing detailsSpecial data processing applicationsOblivious transferData mining
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
Secure and granular index for information retrieval
InactiveUS7874013B2Digital data information retrievalDigital data processing detailsInternet privacyDocumentation
A method and apparatus for a secure and granular index for information is described herein. According to one embodiment of the invention a computer-implemented method is described including evaluating a user query against a set of documents having sub-document level security control, determining a security access for said user, and providing a result for the user query based on the security access for the user and the sub-document level security control.
Owner:SAWTEETH
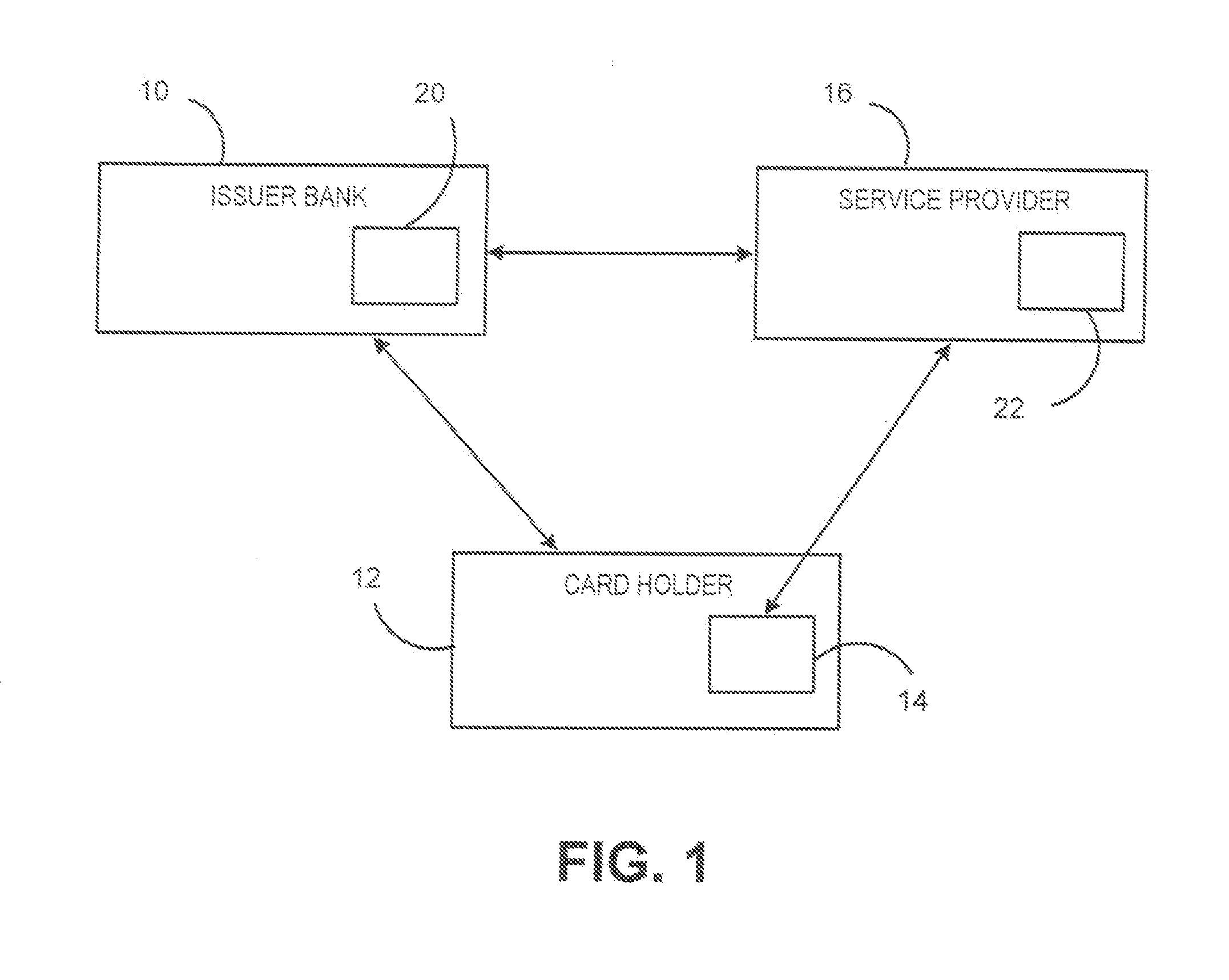
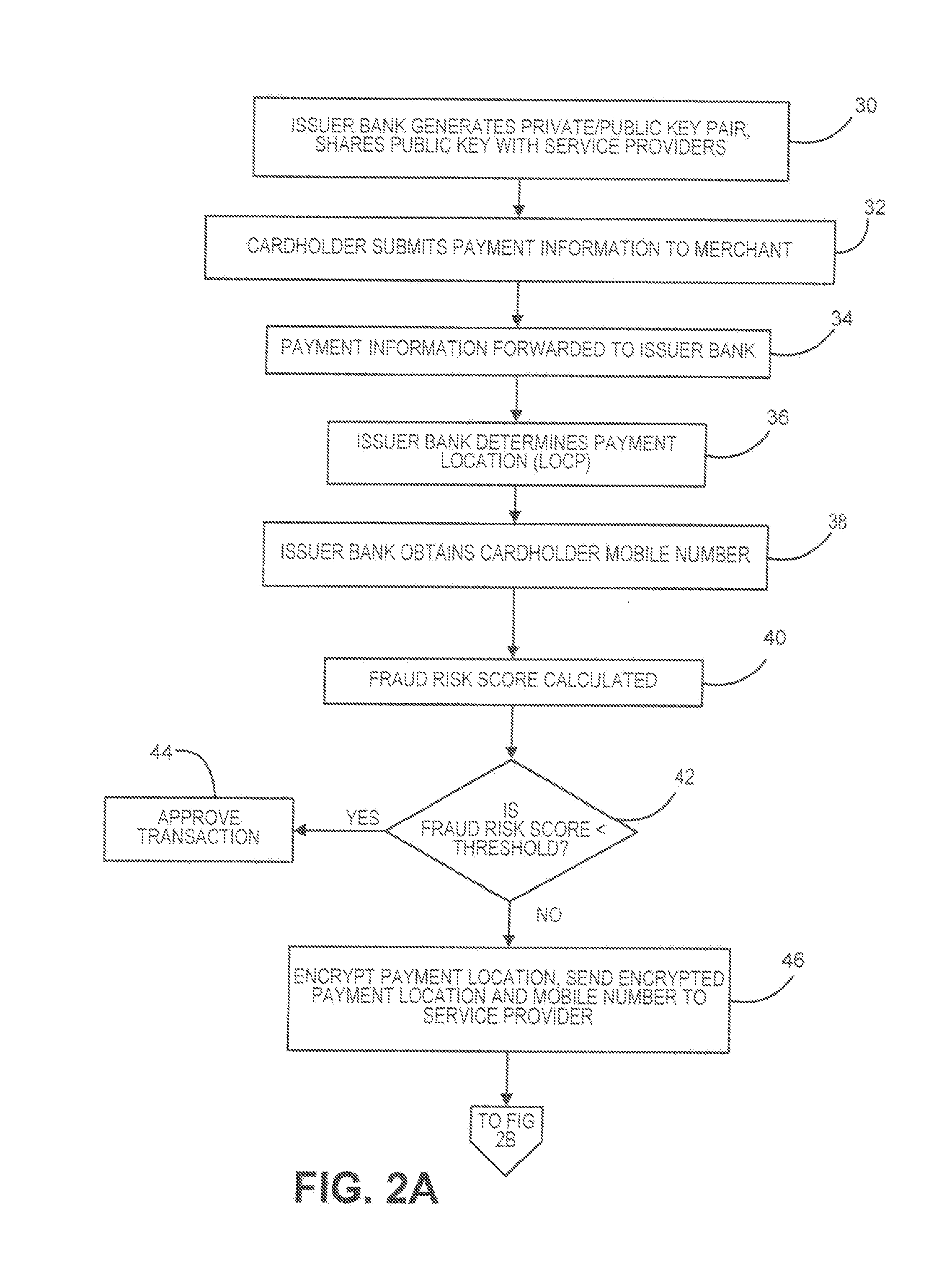
Fraud risk score using location information while preserving privacy of the location information
InactiveUS20170053282A1Enhance fraud risk scoreIncreased riskProtocol authorisationService provisionNon specific
Solutions that protect consumer location information yet still enable the use of such location information in the determination of fraud risk scores are provided. Cryptographic techniques of private information retrieval (PIR) and homomorphic encryption are used to protect consumer location information even as ii is used to enhance fraud risk scares. PIR is used to enable m issuer to retrieve non-specific location information using a consumer mobile number as the query criterion without needing to snare or disclose the mobile number with the service provider. Homomorphic encryption is used to protect location information of mobile consumers, while ensuring card issuers are only able to learn non-specific information about the location of the consumer.
Owner:PITNEY BOWES INC
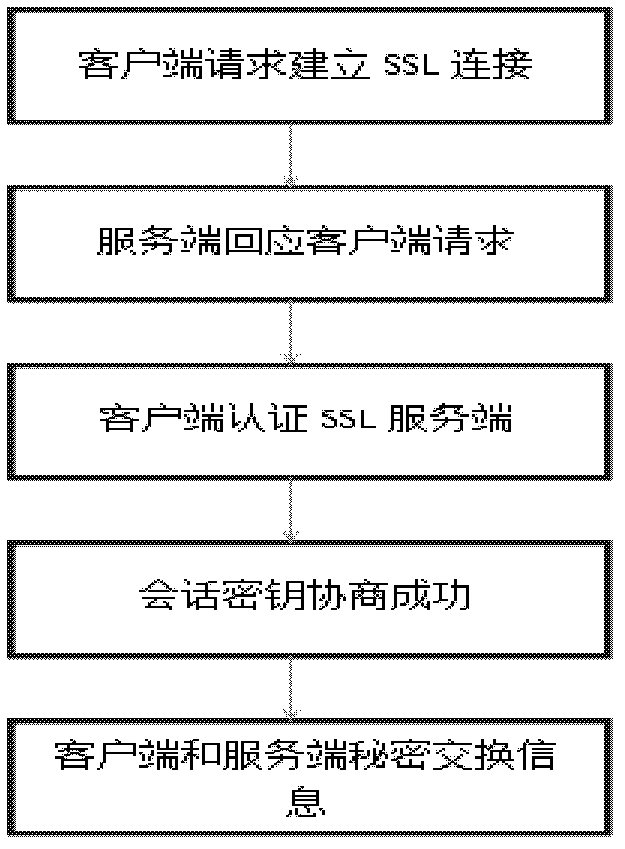
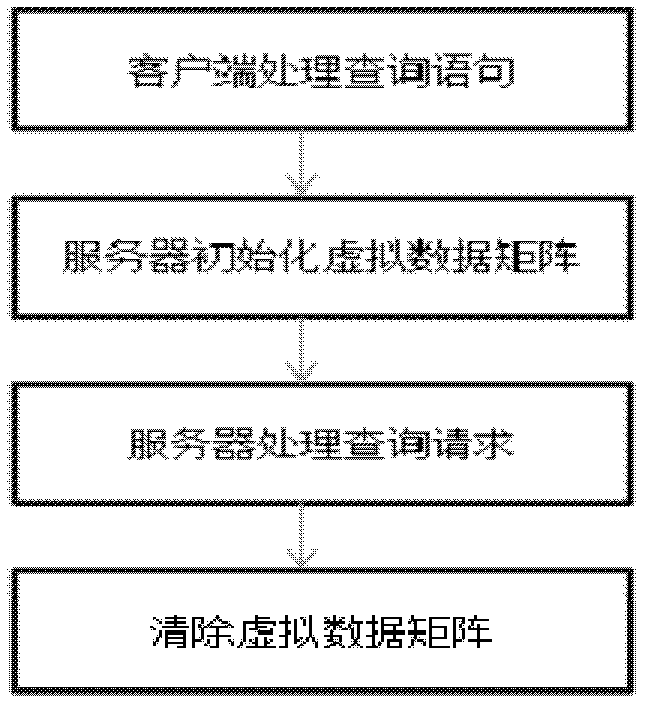
Private information retrieval method in environment of a plurality of servers
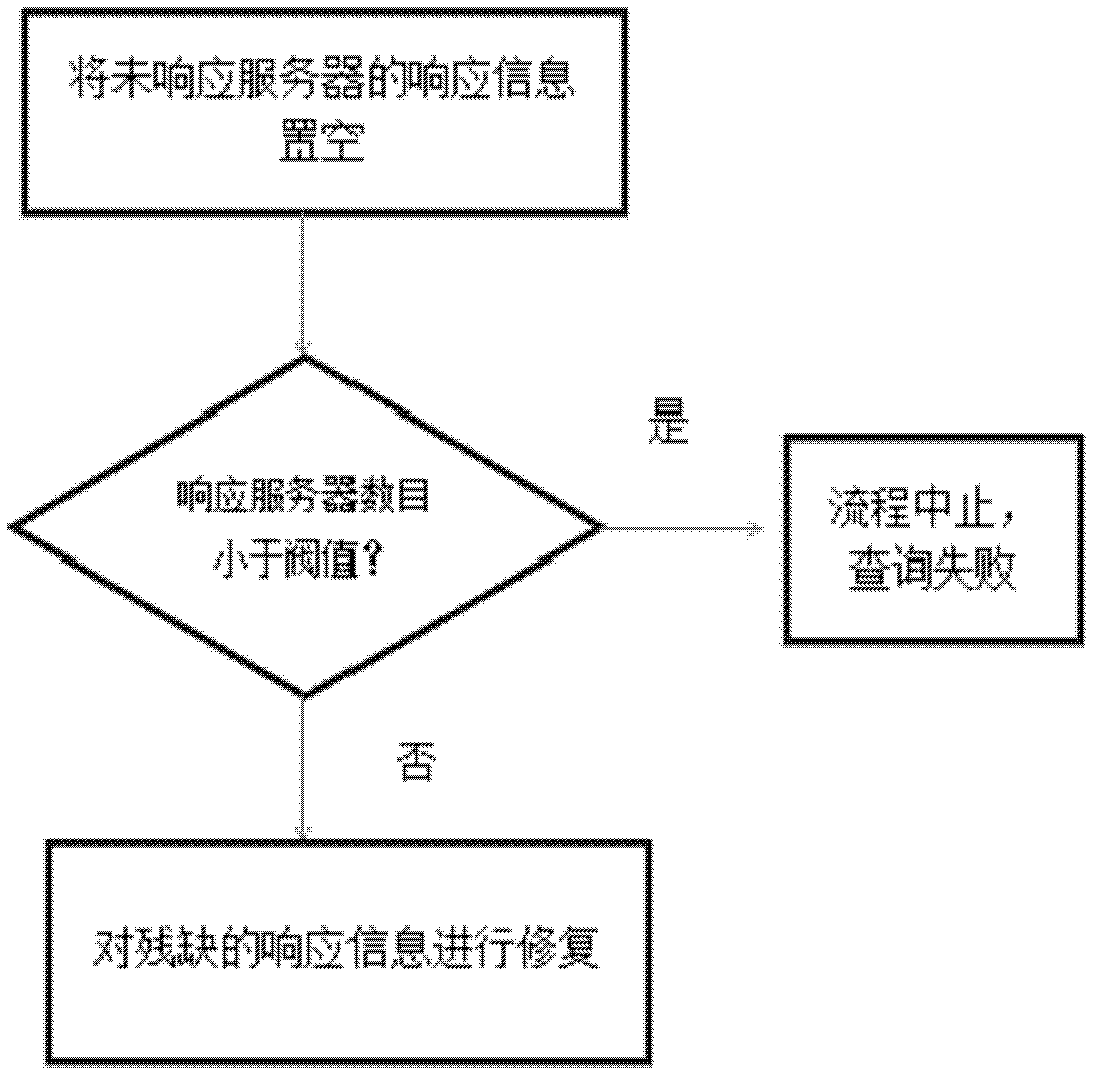
InactiveCN102629924AReduce threatTransmissionSpecial data processing applicationsDatabase serverClient-side
The invention discloses a private information retrieval method in the environment of a plurality of serves, which includes achieving confidential correspondence between a client and a server through a security socket layer (SSL) protocol; supporting mutual information retrieval between the client and the server through a secret sharing protocol and EIGamaI homomorphic encryption algorithm; and processing feedback information of the server with the Lagrange interpolation theory support through the client. According to the private information retrieval method, a virtual data matrix is presented for solving malicious saving and snooping of database servers to inquiring information of users, the retrieval of the client to the server can actually be performed on the virtual data matrix, thus, information on the virtual data matrix can be automatically cleared after the inquiring ends every time; the homomorphic encryption technology is applied in the search scheme of privacy information protection, and second encryption is performed to the secrete sharing vector of the inquiring information, accordingly, the threaten of a single server to the inquiring information is greatly reduced.
Owner:SHANGHAI JIAO TONG UNIV
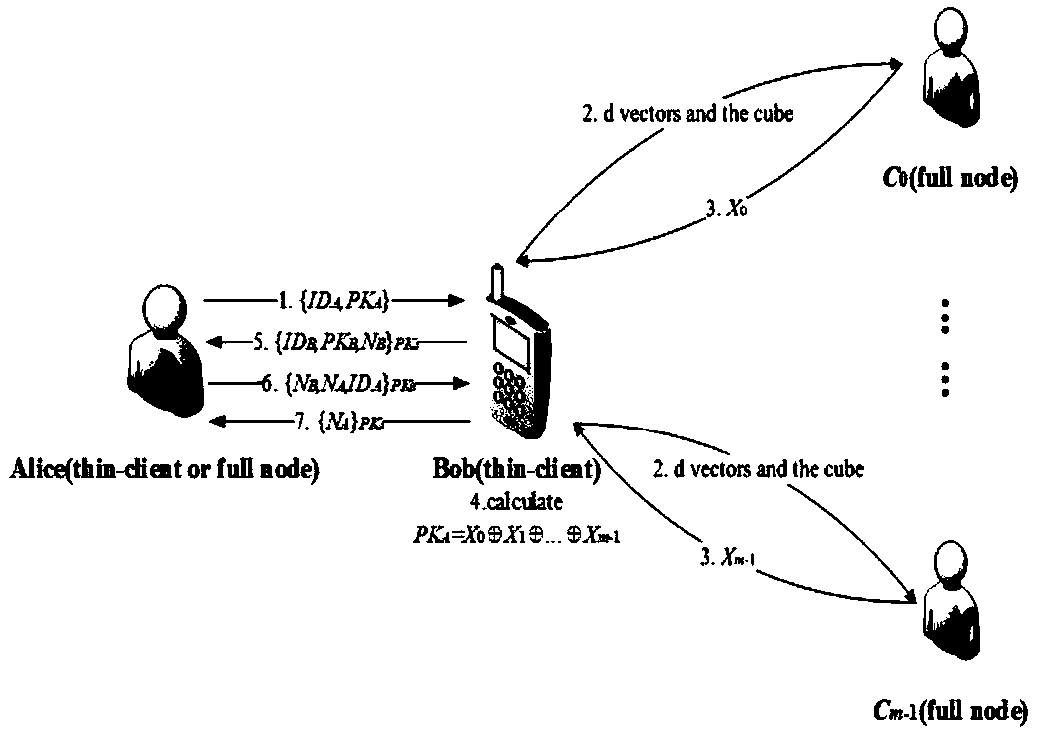
Privacy protection identity authentication method supporting thin client under blockchain PKI (Public Key Infrastructure)
ActiveCN108768608AProtect query privacyRealize the identity authentication functionUser identity/authority verificationPublic key infrastructure trust modelsMan-in-the-middle attackPrivacy protection
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
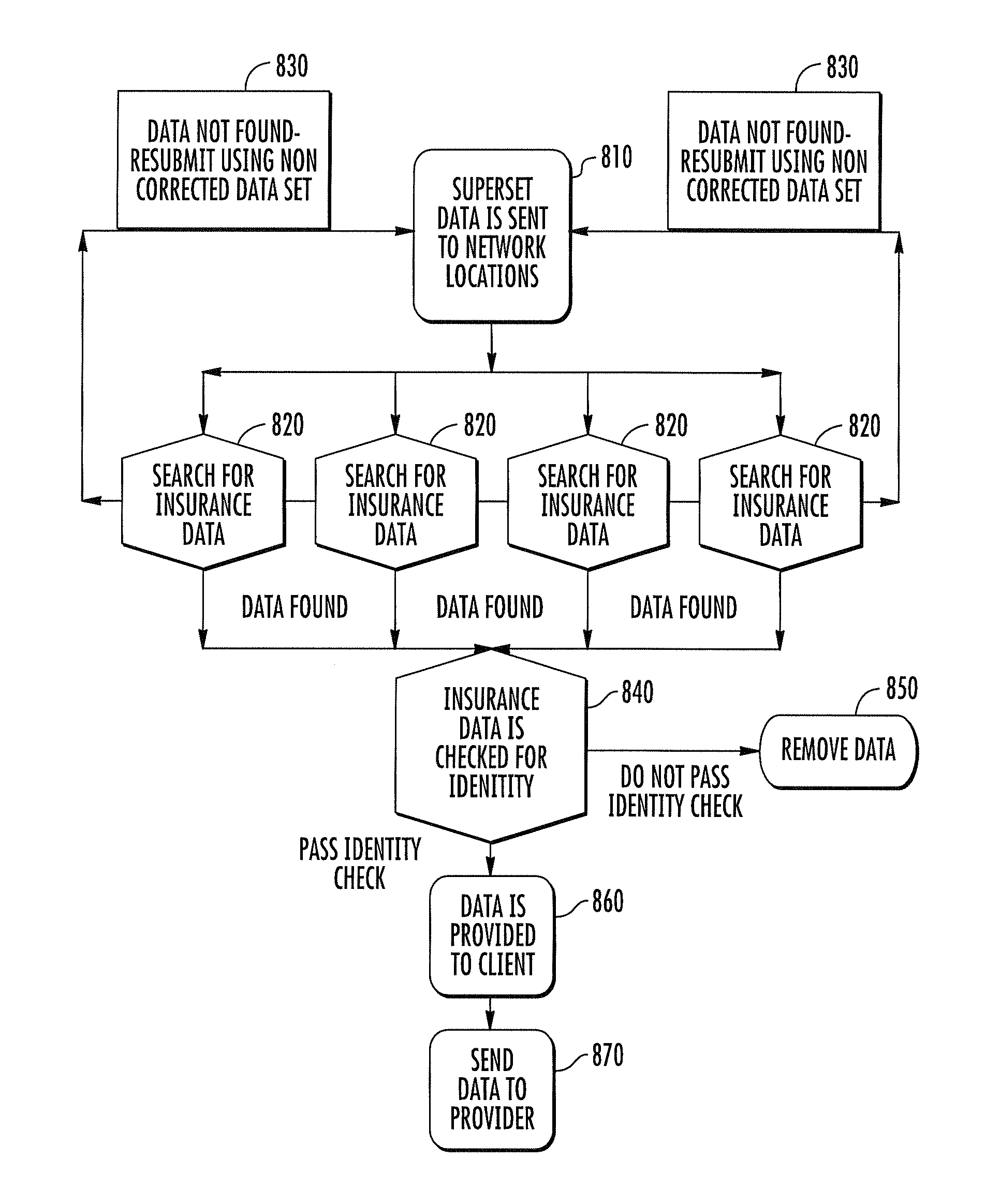
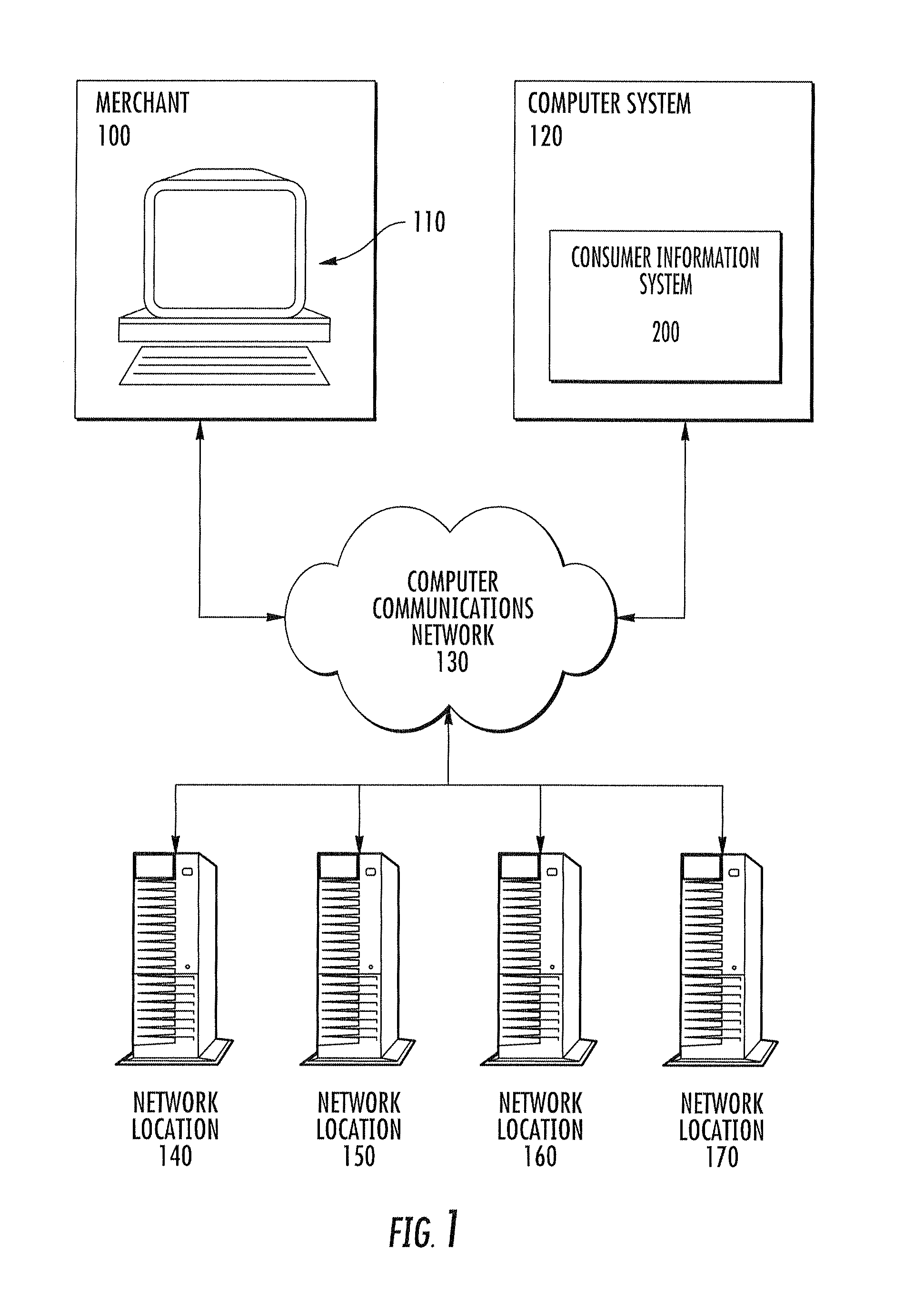
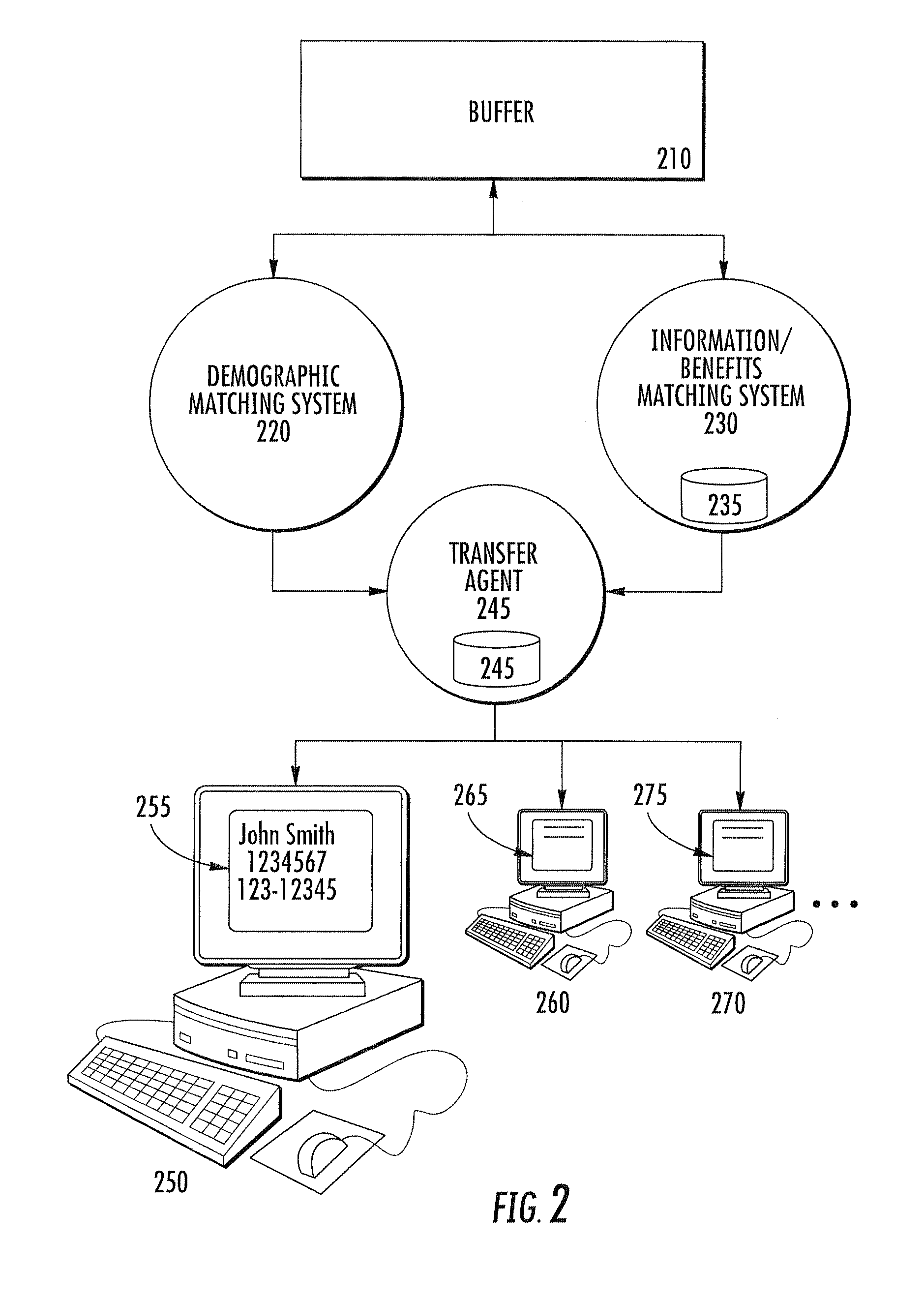
Method and system for information retrieval and transfer
A method for providing medical insurance information corresponding to a consumer of medical services can include receiving consumer medical insurance information from a consumer. This information includes one or more identity fields. A request is sent to network sources of identity information for the consumer, the requests including one or more of the identity fields. The identity information that is received is compared to the consumer medical insurance information using matching rules to store data which satisfies the rules. The identity data which satisfies the matching rules is used to generate requests for insurer medical insurance information. The insurer information is compared to the consumer medical insurance information using matching rules to store only data which satisfies the matching rules. A processor can be used to generate different permutations and combinations of the data for the identity requests and for the insurer requests until a satisfactory response has been received.
Owner:TEVIXMD
Zigzag decoding based private information retrieval method and system
ActiveCN107241414AImprove securityReduce communication costsDigital data protectionTransmissionNODALOperating system
The invention provides a Zigzag decoding based private information retrieval method and system, and belongs to the computer technical application field; the method comprises the following steps: employing (n, k)MDS codes to store files; forming a random vector U so as to retrieve a file f; decoding and obtaining the file f. The invention also provides a zigzag decoding based private information retrieval method and system; the advantages are that the method and system allow users to download files without displaying the specific downloading files, and the communication cost and complexity are relatively low; in a distributed storage system, the method and system can restore the original files when random n-k nodes simultaneously fail, thus increasing the data storage safety.
Owner:杭州研趣信息技术有限公司
Method and apparatus for communication efficient private information retrieval and oblivious transfer
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
Method and apparatus for communication efficient private information retrieval and oblivious transfer
ActiveUS7620625B2Data processing applicationsPublic key for secure communicationOblivious transferData mining
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
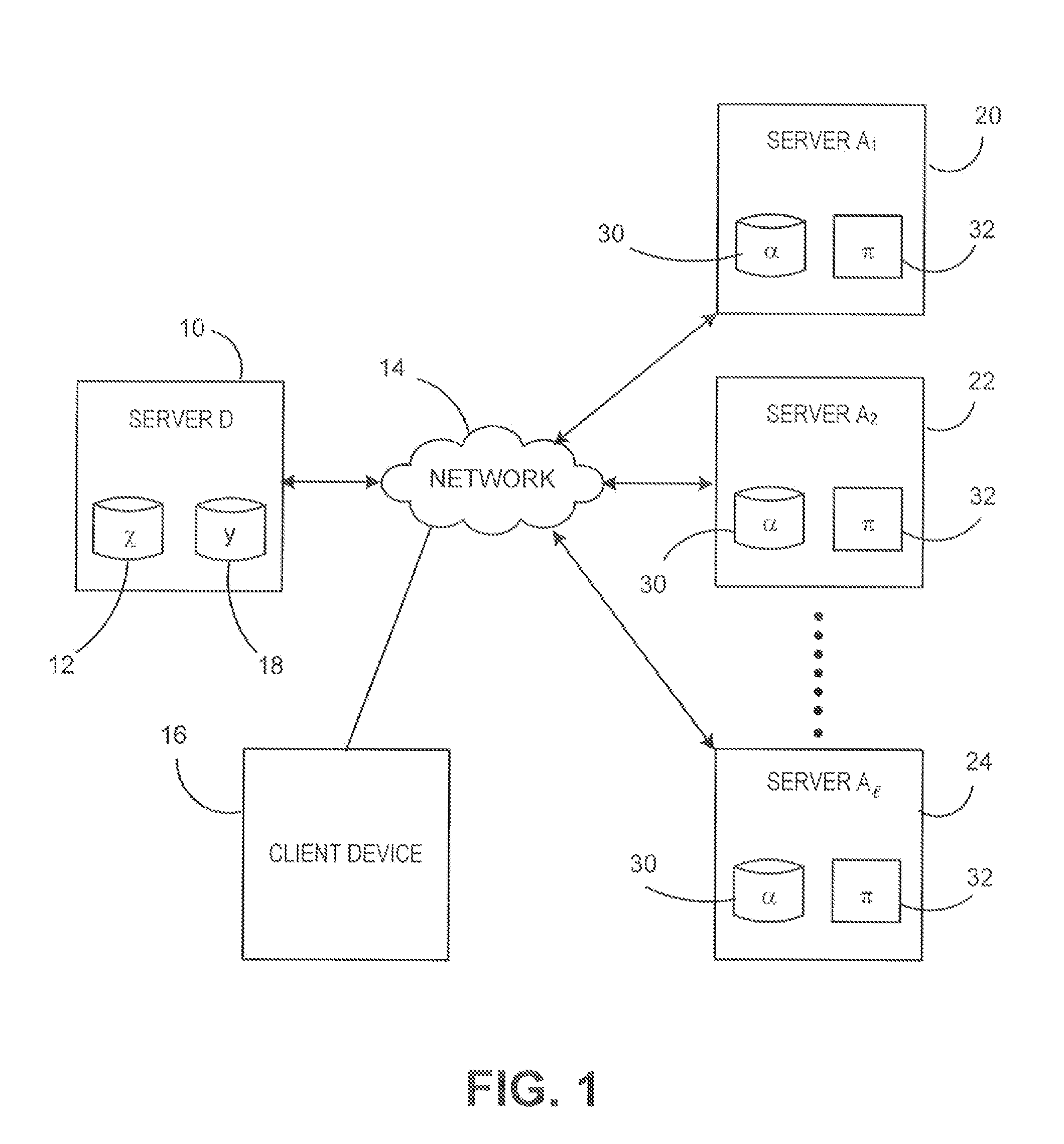
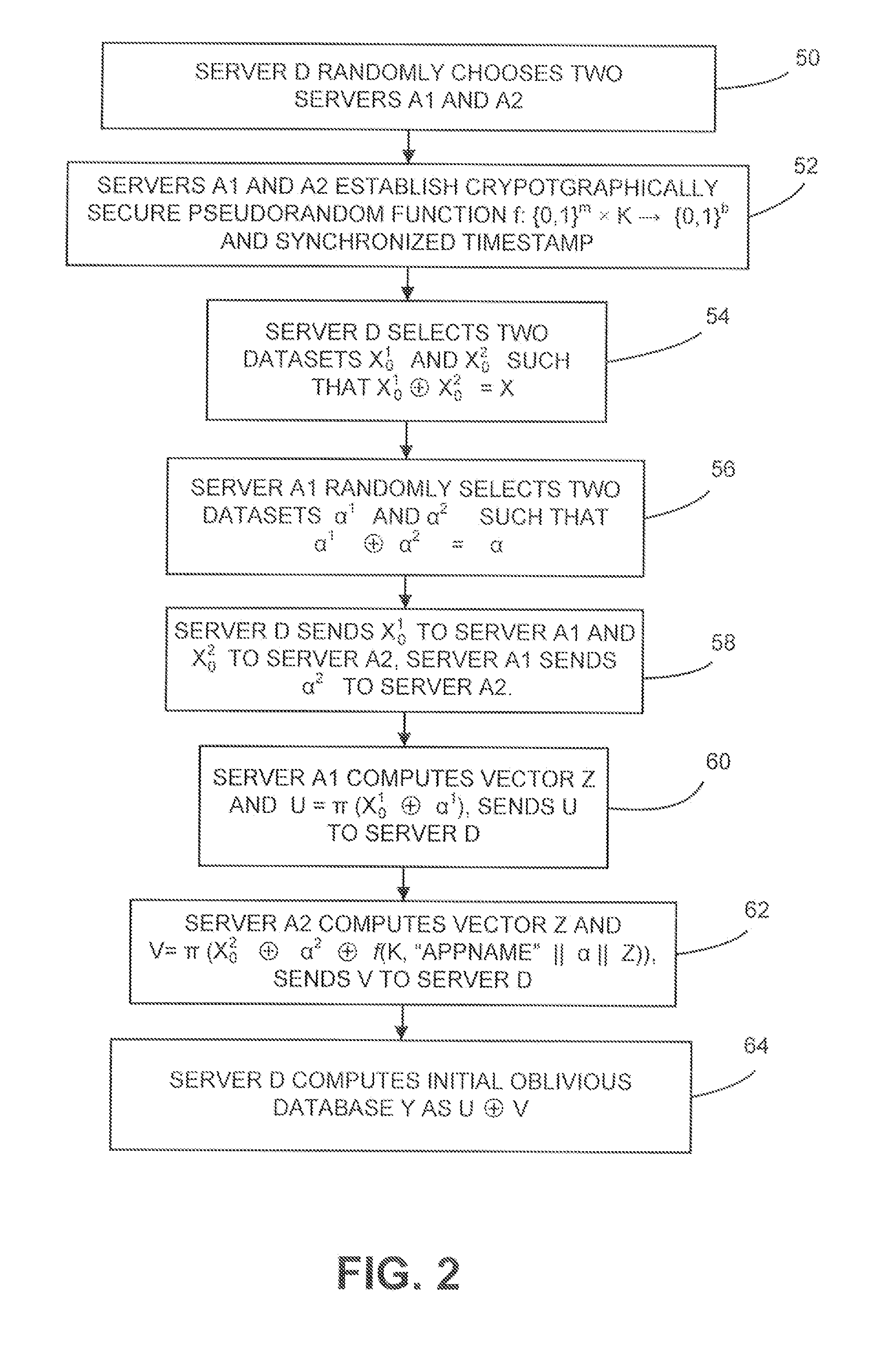
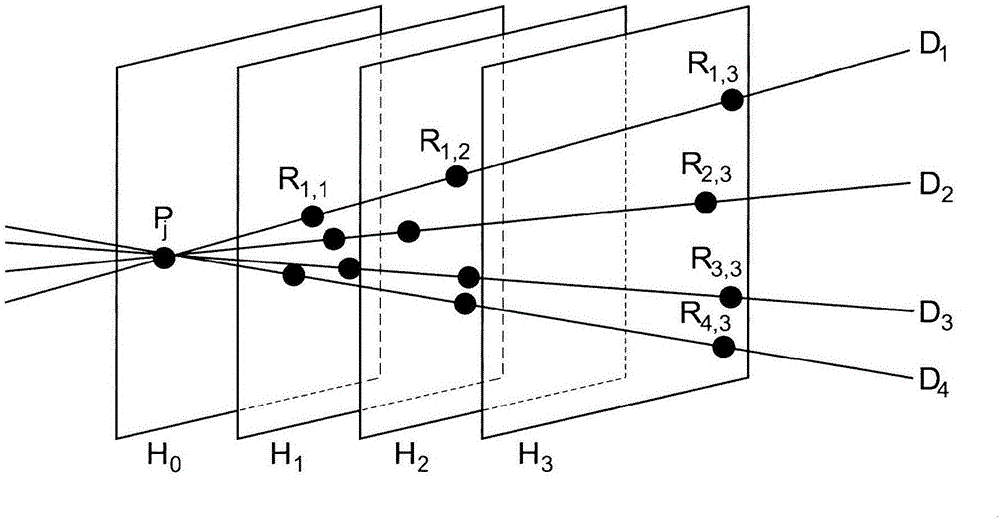
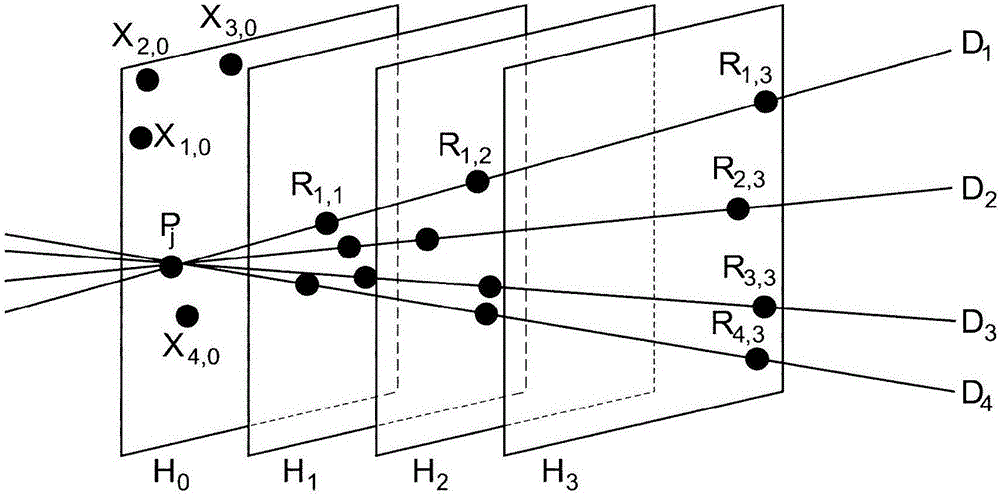
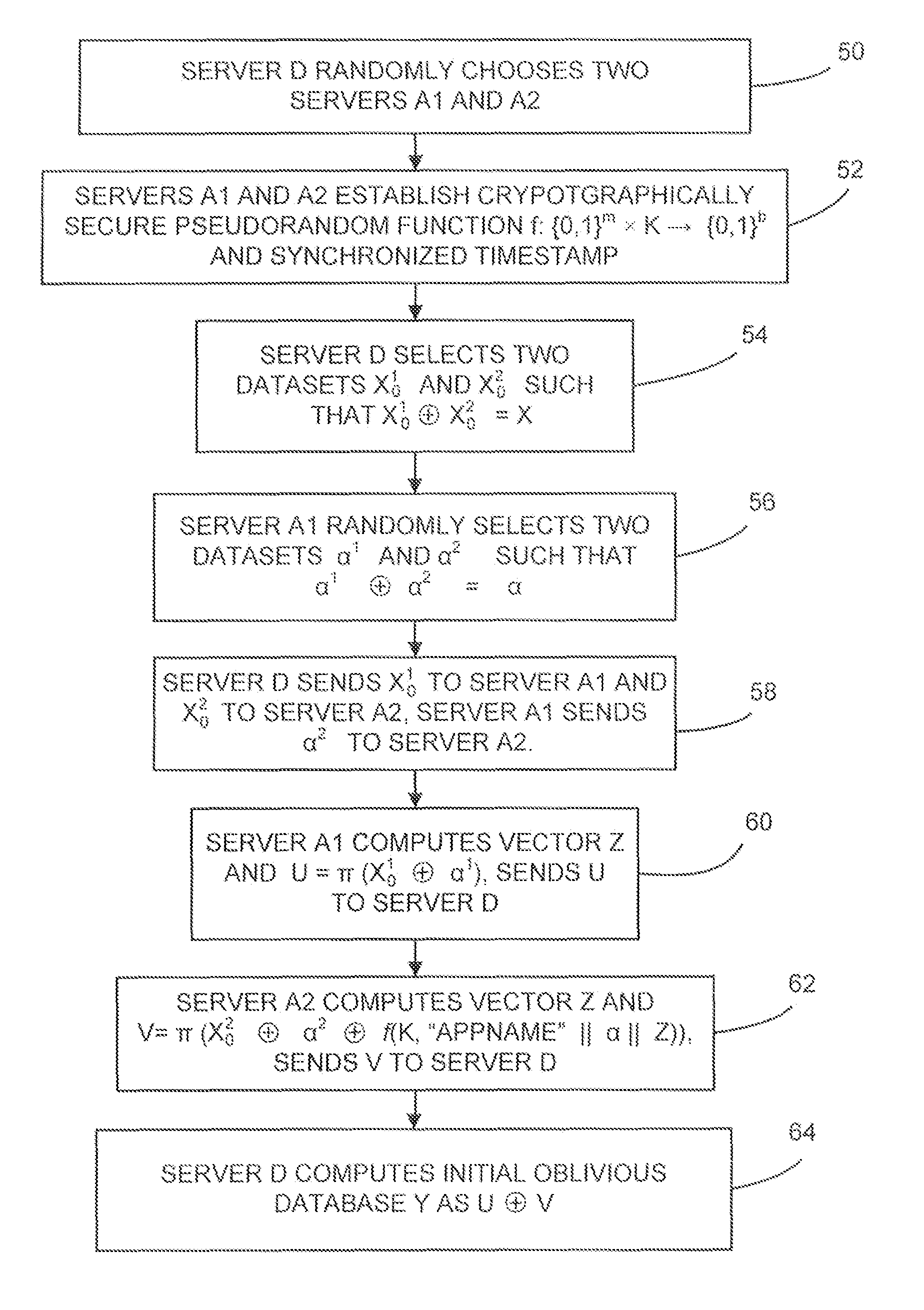
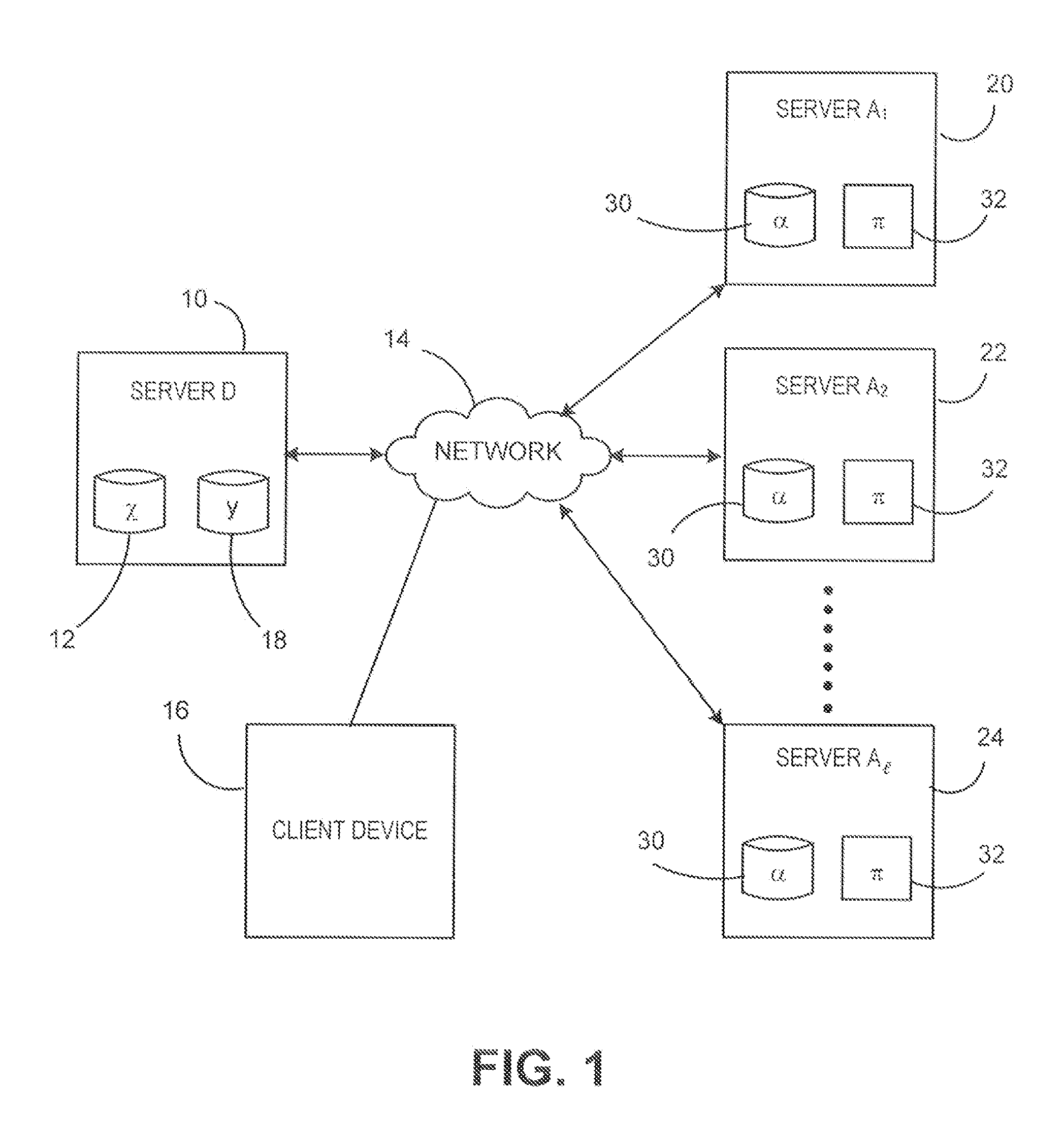
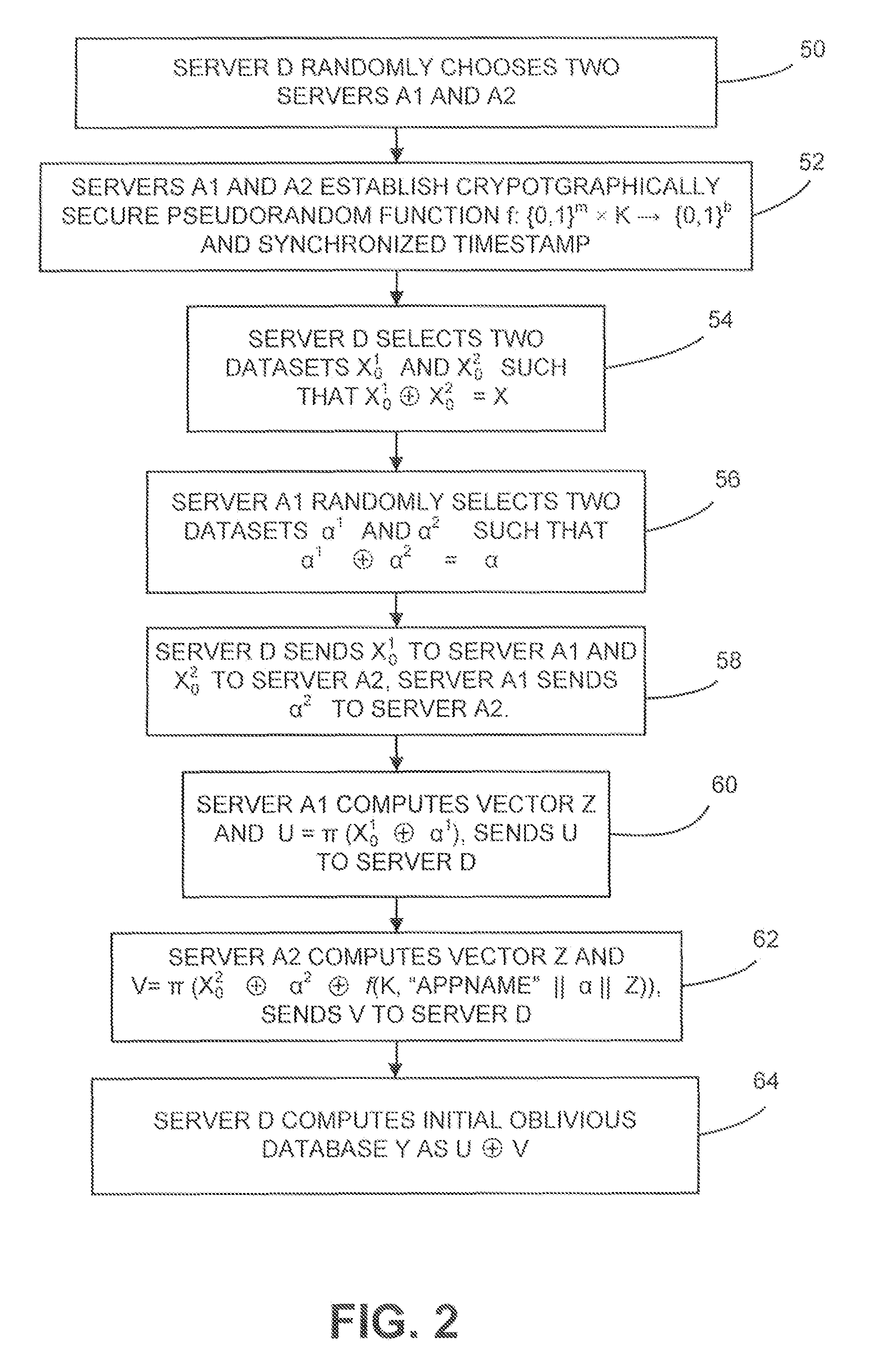
Dynamic database update in multi-server private information retrieval scheme
InactiveUS20140344944A1Digital data processing detailsUser identity/authority verificationOriginal dataDowntime
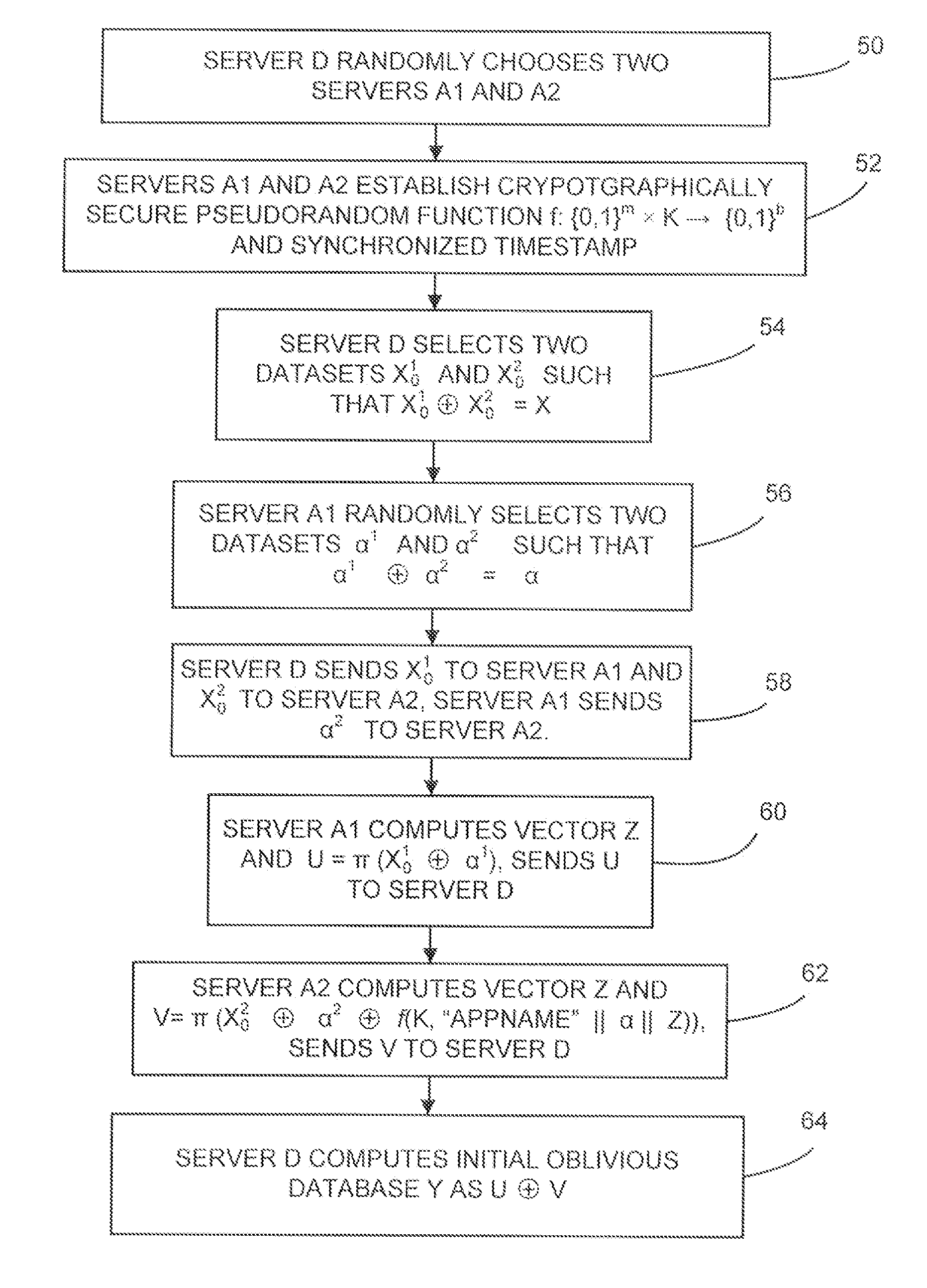
A system and methods to provide updates of an oblivious database that is based on an original database without compromising privacy guarantees, and without requiring a periodic downtime to re-initialize the database. According to embodiments of the present invention, update caches are provided at the random servers that are not emptied or sent to the oblivious database after every update in a predictable fashion. Instead, updates are made incrementally to the oblivious database in an order that is independent of how the original database is updated. Hence there is no way for the server to learn which record of the oblivious database corresponds to an updated block from the original database.
Owner:PITNEY BOWES INC
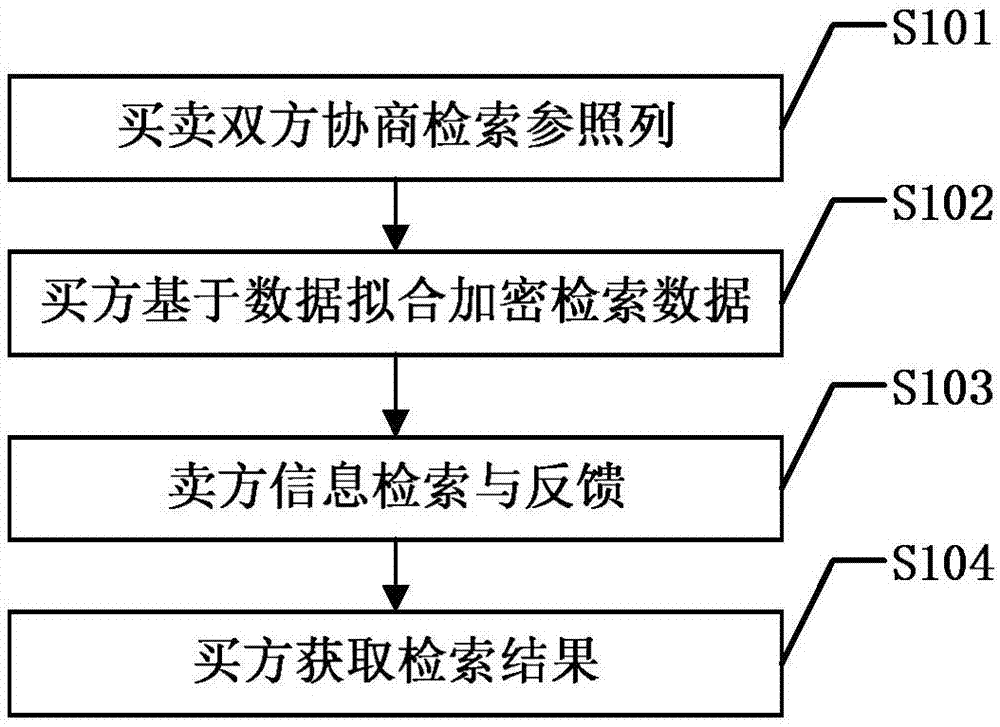
Personalized private information retrieval method based on data fitting
ActiveCN106909617AProtectDigital data protectionSpecial data processing applicationsPersonalizationCiphertext
The invention discloses a personalized private information retrieval method based on data fitting. A buyer of a data exchange platform and a seller of the data exchange platform negotiate and obtain a retrieval reference column, the buyer determines a distribution function of retrieval reference column data through fitting, according to the distribution function of the retrieval reference column data and private requirement parameters, k anonymous sets are obtained, an irreversible encryption algorithm is adopted to encrypt the anonymous sets, anonymous ciphertext sets are sent to the seller, the seller adopts the same irreversible encryption algorithm as the buyer adopts to encrypt data in a reference column R in a database of the seller, then, retrieval is conducted according to the anonymous ciphertext sets, retrieval record sets are sent to the buyer, the buyer screens out needed retrieval records in the retrieval record sets according to actual retrieval reference column data, and retrieval results are obtained. By the adoption of the method, the privacy of retrieval contents and intentions of the buyer can be well protected.
Owner:EAST CHINA NORMAL UNIVERSITY
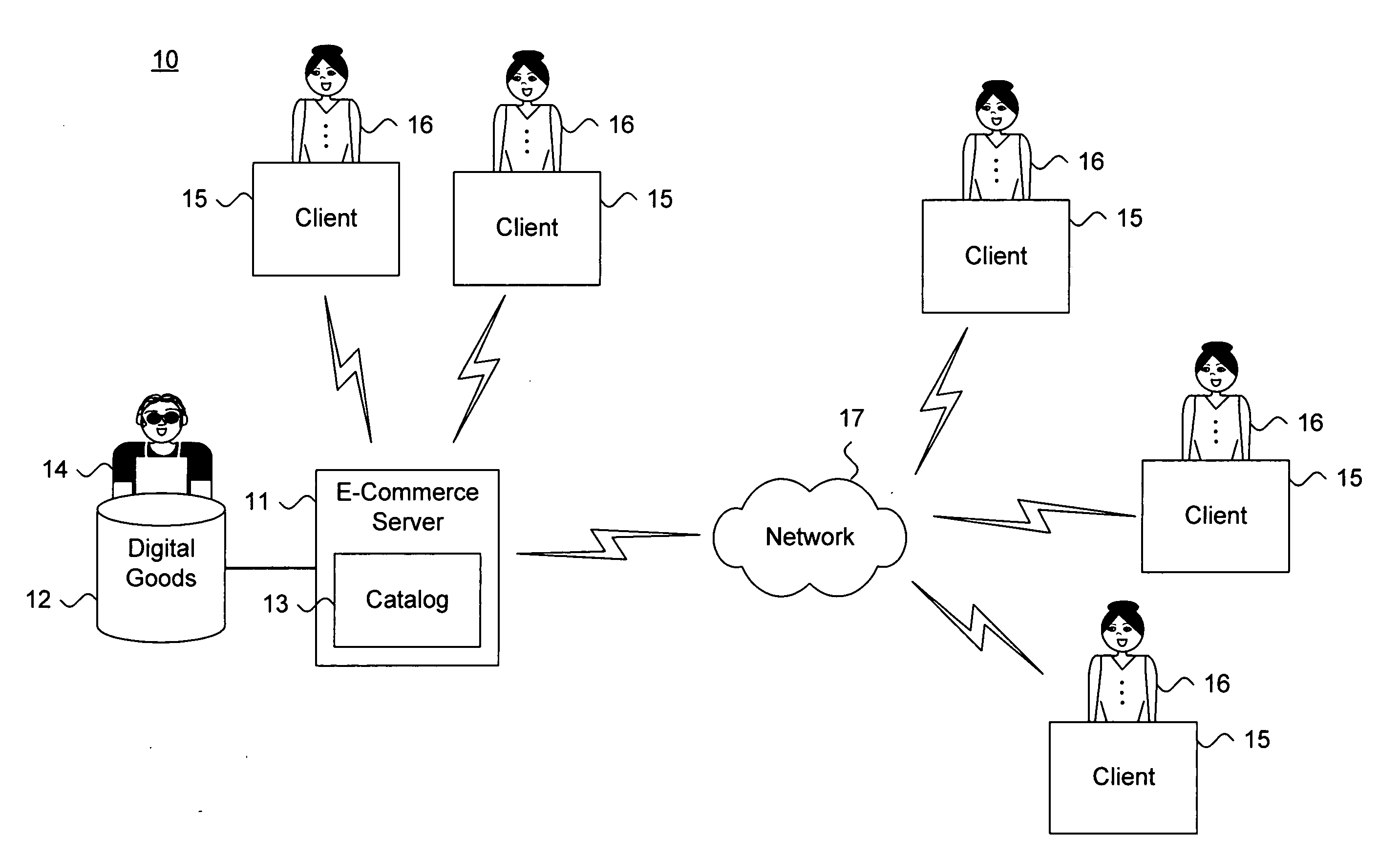
System and method for providing private demand-driven pricing
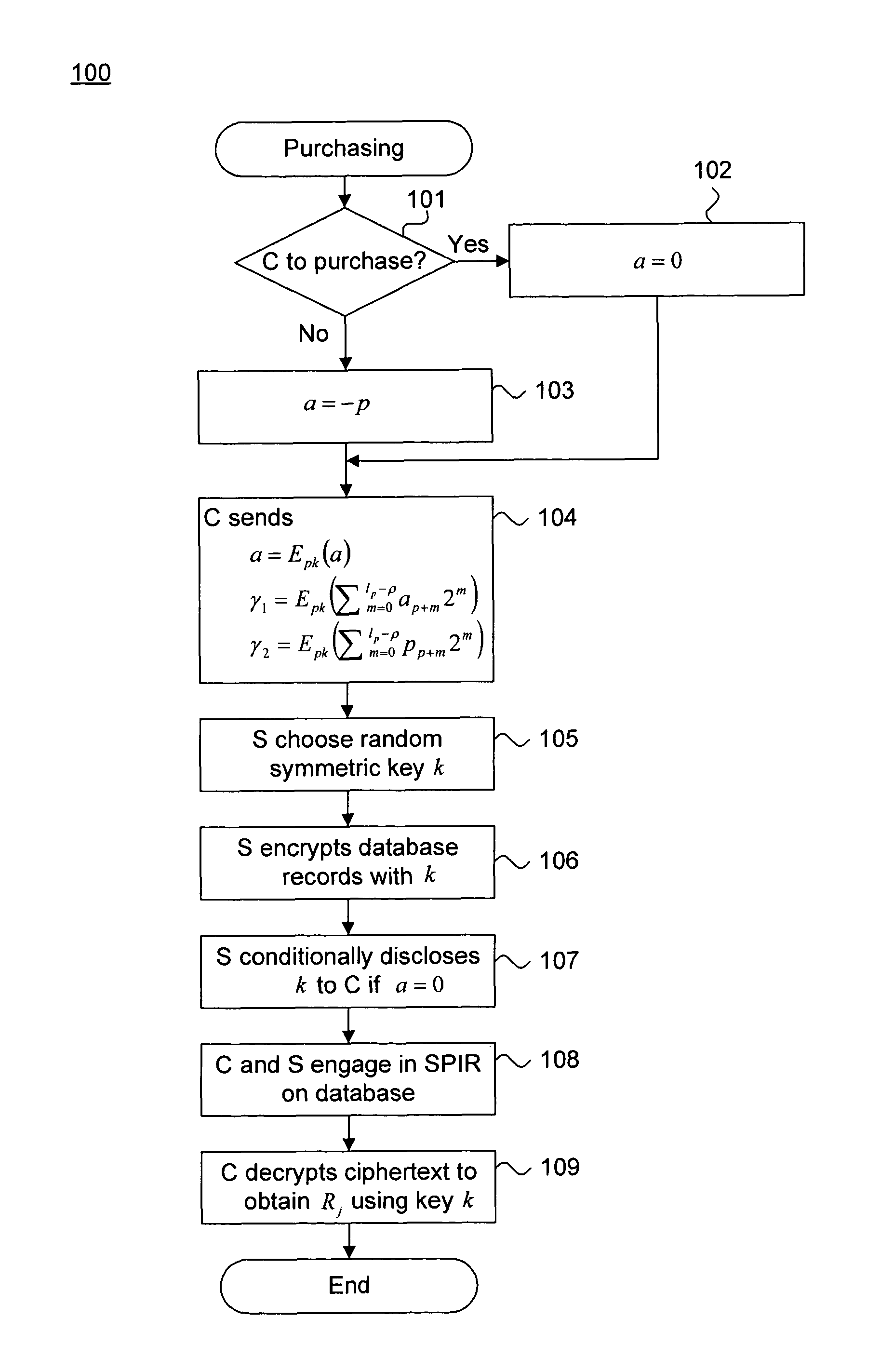
InactiveUS20080114682A1Computer security arrangementsBuying/selling/leasing transactionsDigital goodsComputer science
A system and method for providing private demand-driven pricing for fixed cost digital goods are described. An encrypted price of identically-priced digital goods is additively perturbed. The digital goods are stored in a database by a seller system and an approximate revenue maximizing price for the digital goods has not been realized. A purchasing decision about one of the digital goods based upon the additively-perturbed price is sent to the seller system without revealing the particular digital good. A conditionally disclosed symmetric key is received in return under which the digital goods in the database have been encrypted. The purchaser system and seller system engage in symmetric private information retrieval on the database. The purchaser system decrypts the digital good purchased with the symmetric key. The seller system privately updates the encrypted price of the digital goods to close on the approximate revenue maximizing price whenever a purchase is made.
Owner:PALO ALTO RES CENT INC
System and method for providing private demand-driven pricing
InactiveUS20080114681A1Computer security arrangementsBuying/selling/leasing transactionsDigital goodsEncryption
A system and method for providing private demand-driven pricing for fixed cost digital goods are described. Symmetric private information retrieval is engaged on a table that includes public key encryptions of prices for digital goods stored in a database by a seller system, wherein a desired marginal pricing level has not been realized. The price of one digital good is decrypted with a private key for pricing by a purchaser system. A purchasing decision based upon the decrypted price is sent to the seller system without revealing the particular digital good being purchased. A conditionally disclosed symmetric key for goods is received under which the digital goods in the database have been encrypted. Symmetric private information retrieval is engaged on the database and the digital good purchased with the symmetric key is decrypted. The encrypted prices of the digital goods are privately updated based upon the desired marginal pricing level.
Owner:PALO ALTO RES CENT INC
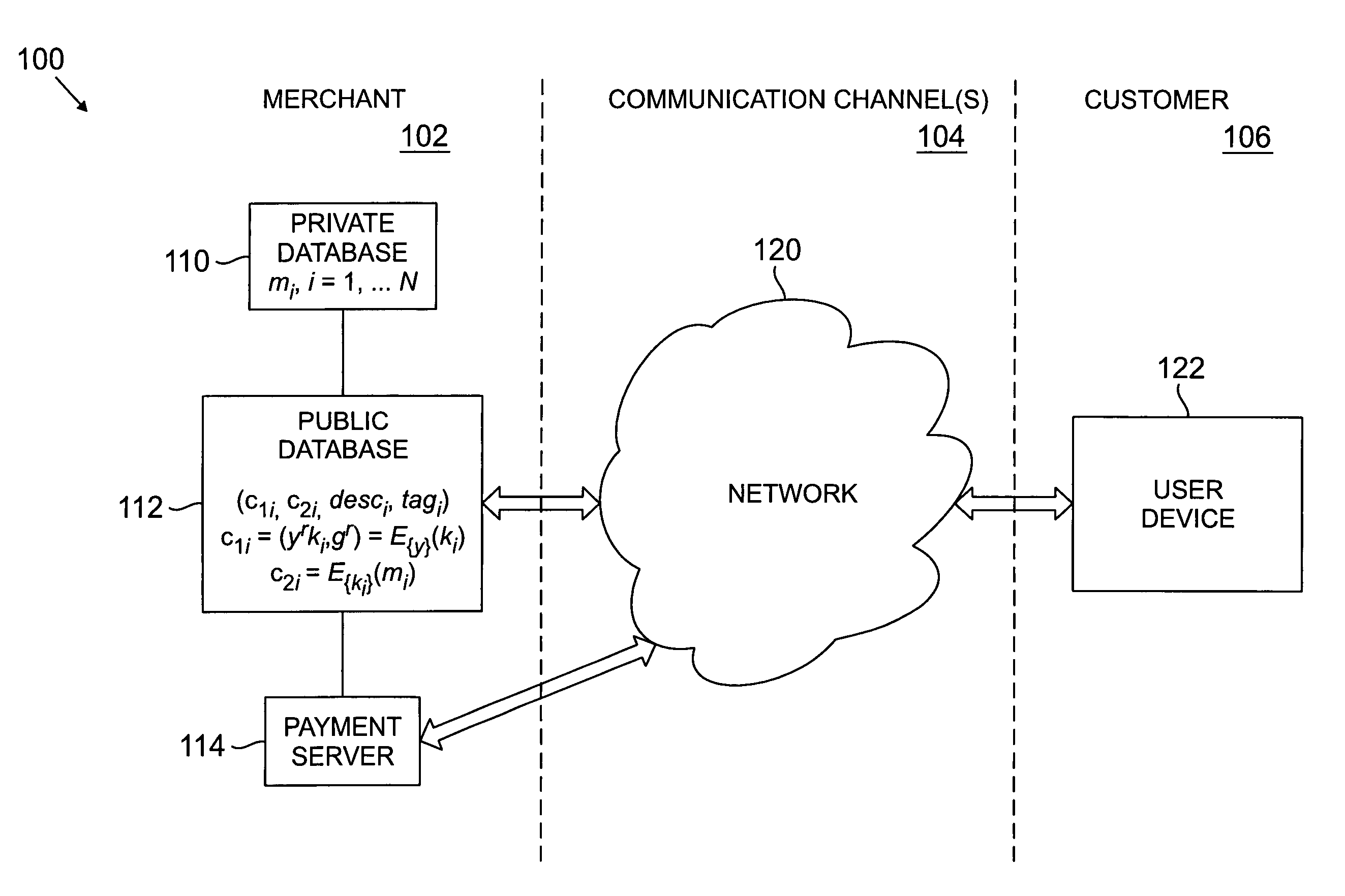
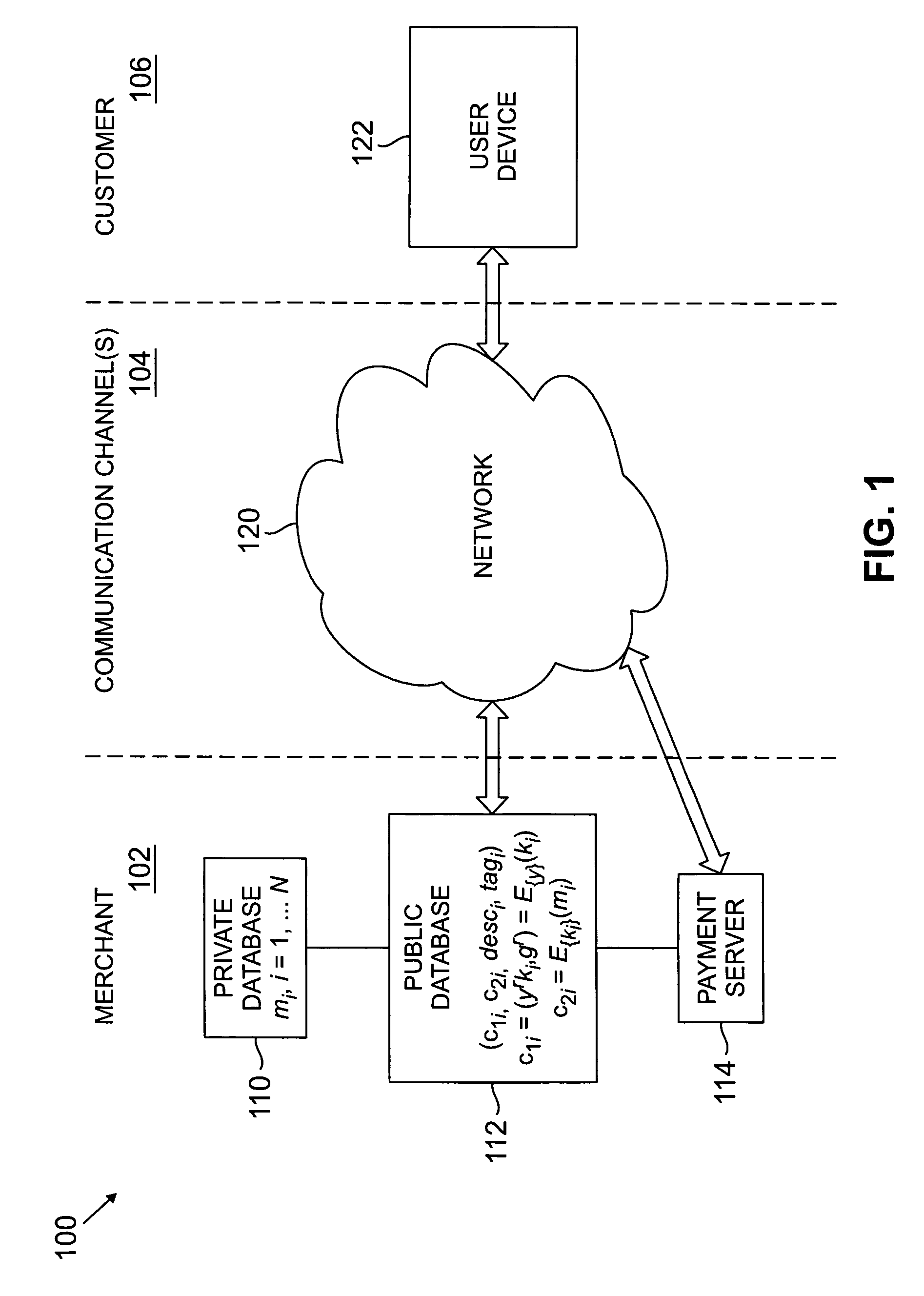
Tagged private information retrieval
Purchase of information items from a merchant over the Internet or other network is implemented so as to ensure that the merchant is unable to identify the particular information item(s) purchased by a user. The user when considering purchase of a given information item is permitted to access a corresponding signed ciphertext of that item. The signed ciphertext in an illustrative embodiment includes a first ciphertext portion in the form of a symmetric key encrypted using a public key associated with the merchant, a second ciphertext portion corresponding to the information item encrypted using the symmetric key, an unencrypted description of the information item, and a tag corresponding to a signature. The user requests purchase of the information item by sending a blinded version of the first ciphertext portion to a payment server along with an appropriate payment. The payment server decrypts the blinded version of the first ciphertext portion and returns the resulting symmetric key to the user. The user then utilizes the symmetric key to decrypt the second ciphertext portion so as to obtain the desired information item. The decrypting operation performed by the payment server may be implemented using at least part of a set of multiple rounds, with the user providing a blinded ciphertext and receiving a corresponding decryption result for each of the rounds.
Owner:SOUND VIEW INNOVATIONS
System and method for providing private demand-driven pricing
InactiveUS8712915B2Computer security arrangementsMultiple digital computer combinationsDigital goodsEncryption
A system and method for providing private demand-driven pricing for fixed cost digital goods are described. Symmetric private information retrieval is engaged on a table that includes public key encryptions of prices for digital goods stored in a database by a seller system, wherein a desired marginal pricing level has not been realized. The price of one digital good is decrypted with a private key for pricing by a purchaser system. A purchasing decision based upon the decrypted price is sent to the seller system without revealing the particular digital good being purchased. A conditionally disclosed symmetric key for goods is received under which the digital goods in the database have been encrypted. Symmetric private information retrieval is engaged on the database and the digital good purchased with the symmetric key is decrypted. The encrypted prices of the digital goods are privately updated based upon the desired marginal pricing level.
Owner:PALO ALTO RES CENT INC
File protection method and system
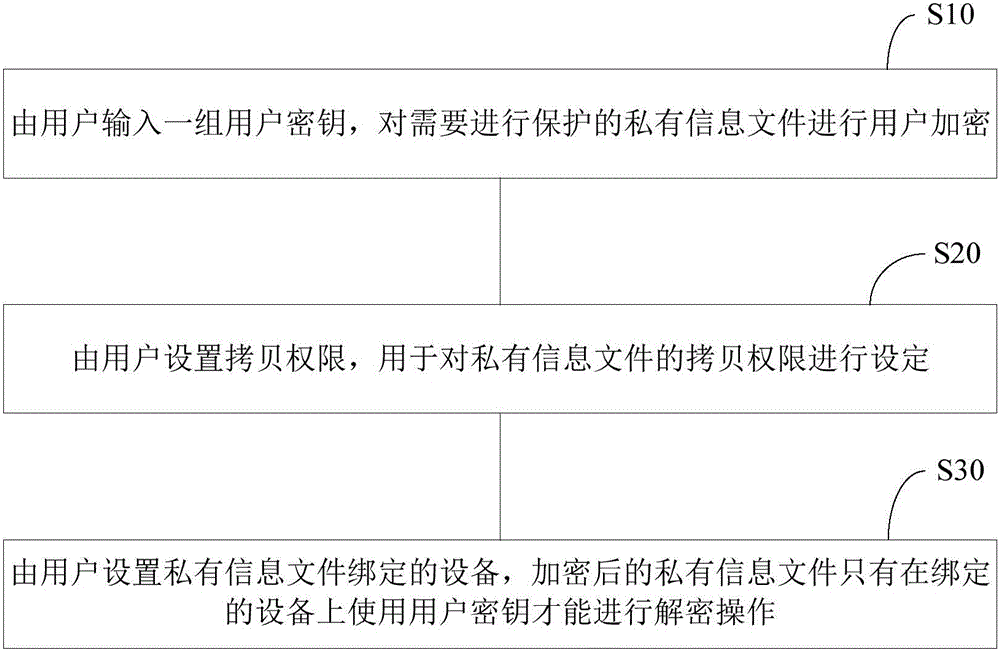
InactiveCN104966010AEnsure safetyAvoid infringementDigital data protectionDigital data authenticationUser inputInternet privacy
The present invention relates to a file protection system and method. In a manner of inputting a user key by a user, setting a copy authority and binding a specific device, a private information file is protected, so that the private information file is effectively prevented from being easily attacked and copied; under the condition that the key of the private information file is destroyed, the private information file is further protected by means of the bound device, so that the security of private information of the user is effectively ensured to the greatest extent and extreme guarantee for the security of the private information of the user is brought.
Owner:SHENZHEN JIUZHOU ELECTRIC
Method and apparatus for communication efficient private information retrieval and oblivious transfer
InactiveUS20090190752A1Digital data processing detailsSecret communicationOblivious transferData mining
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
Storage efficient and unconditionally secure private information retrieval
InactiveCN106464486AReduce storage overheadKey distribution for secure communicationComputer security arrangementsOriginal dataEngineering
Owner:ALCATEL LUCENT SAS +1
Dynamic database update in multi-server private information retrieval scheme
A system and methods to provide updates of an oblivious database that is based on an original database without compromising privacy guarantees, and without requiring a periodic downtime to re-initialize the database. According to embodiments of the present invention, update caches are provided at the random servers that are not emptied or sent to the oblivious database after every update in a predictable fashion. Instead, updates are made incrementally to the oblivious database in an order that is independent of how the original database is updated. Hence there is no way for the server to learn which record of the oblivious database corresponds to an updated block from the original database.
Owner:PITNEY BOWES INC
Method and apparatus for communication efficient private information retrieval and oblivious transfer
InactiveUS20090190751A1Data processing applicationsDigital data processing detailsOblivious transferData mining
A method, article of manufacture and apparatus for performing private retrieval of information from a database is disclosed. In one embodiment, the method comprising obtaining an index corresponding to information to be retrieved from the database and generating a query that does not reveal the index to the database. The query is an arithmetic function of the index and a secret value, wherein the arithmetic function includes a multiplication group specified by a modulus of a random value whose order is divisible by a prime power, such that the prime power is an order of the random value. The secret value is an arithmetic function of the index that comprises a factorization into prime numbers of the modulus. The method further comprises communicating the query to the database for execution of the arithmetic function against the entirety of the database.
Owner:GOOGLE LLC
System and method for providing private demand-driven pricing
A system and method for providing private demand-driven pricing for fixed cost digital goods are described. An encrypted price of identically-priced digital goods is additively perturbed. The digital goods are stored in a database by a seller system and an approximate revenue maximizing price for the digital goods has not been realized. A purchasing decision about one of the digital goods based upon the additively-perturbed price is sent to the seller system without revealing the particular digital good. A conditionally disclosed symmetric key is received in return under which the digital goods in the database have been encrypted. The purchaser system and seller system engage in symmetric private information retrieval on the database. The purchaser system decrypts the digital good purchased with the symmetric key. The seller system privately updates the encrypted price of the digital goods to close on the approximate revenue maximizing price whenever a purchase is made.
Owner:PALO ALTO RES CENT INC
Secure and efficient multi-server oblivious random access machine in a malicious execution environment
PendingCN112783851ADigital data information retrievalDigital data protectionRandom-access machineDistributed File System
The invention relates to a secure and efficient multi-server oblivious random access machine in a malicious execution environment. An oblivious distributed file system is provided using an oblivious random access machine (ORAM), including an ORAM balanced tree structure, where each node in the tree is configured to store data blocks, the structure including at least two shares. The system also includes at least two ORAM servers, each of the servers configured to communicate with a client ORAM device, and programmed to facilitate storage of a different subset of the shares of the tree structure using a distributed file system and to implement an access procedure of a tree-based ORAM using the tree structure, including a retrieval phase and an eviction phase. In the retrieval phase, the servers utilize an authenticated Private Information Retrieval (PIR) protocol to retrieve data blocks as requested from the client ORAM device. In the eviction phase, the servers utilize a linear secret sharing scheme.
Owner:ROBERT BOSCH GMBH
Privacy information retrieval method and system suitable for large-scale database
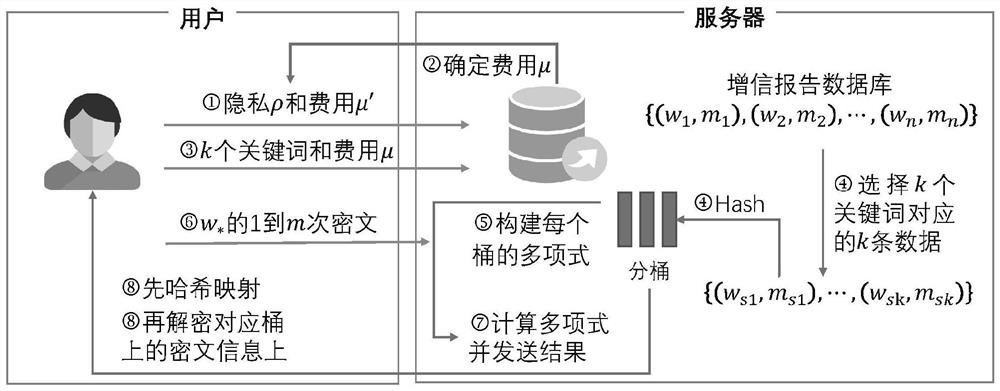
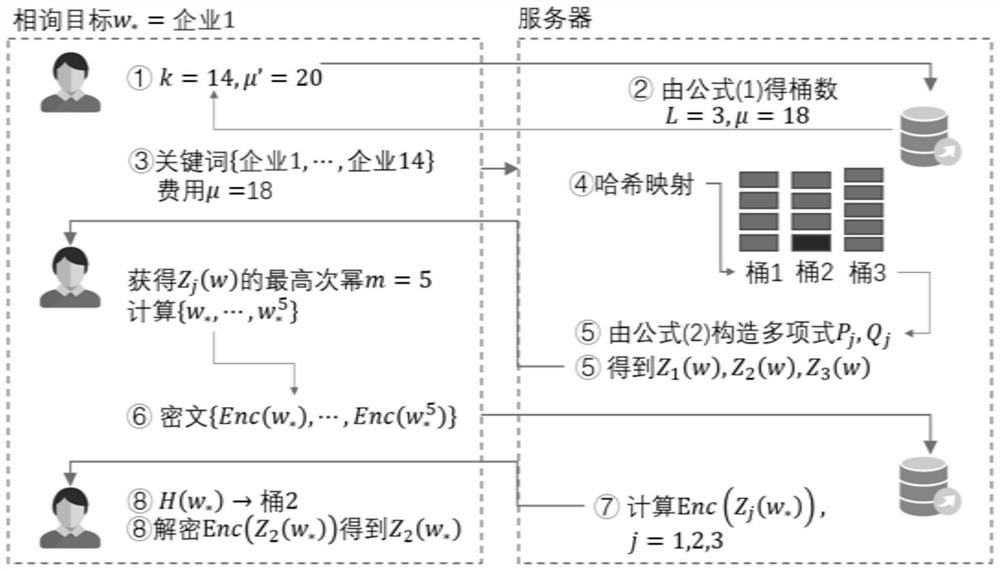
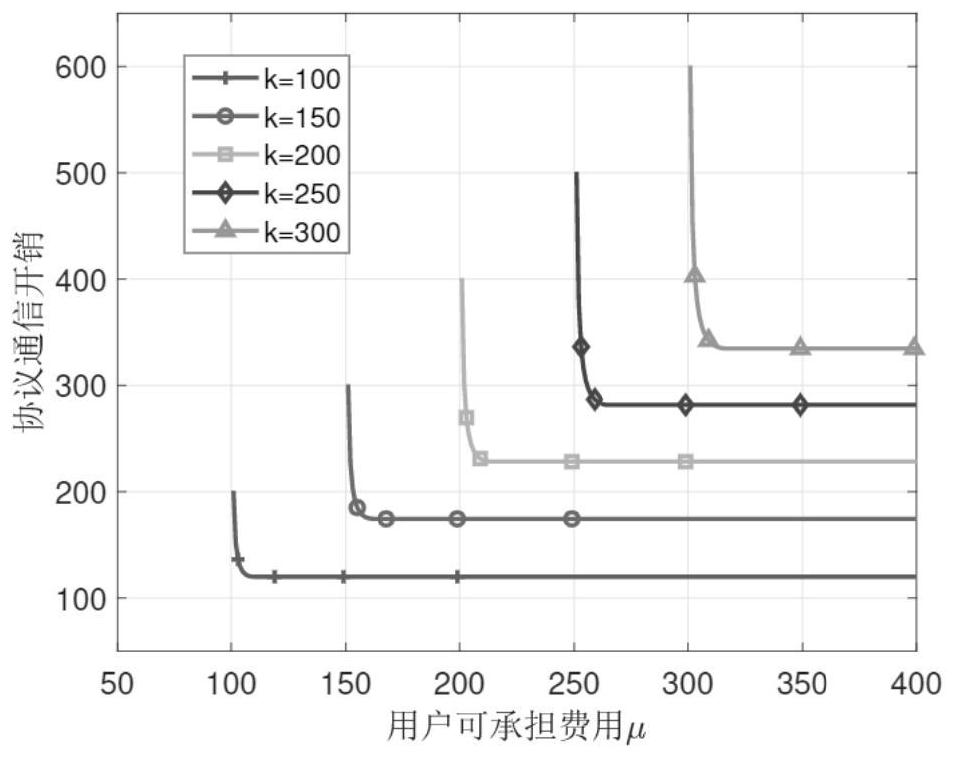
ActiveCN114662147ARealize requirementsReduce the computational complexity of decryptionDigital data protectionEnergy efficient computingPersonalizationHash function
The invention discloses a privacy information retrieval method and system suitable for a large-scale database, and the privacy security of a user query target and a server database is protected by using casual polynomial transmission and Paillier homomorphic encryption. And the influence of the personalized privacy demand of the user and the bucket number on the communication overhead and the calculation cost in an actual scene is fully considered. The bucking operation and the oblivious polynomial calculation are executed on the subsets corresponding to the k keywords specified by the user, so that the overall calculation complexity can be effectively reduced, and the personalized privacy demand preference of the user in an actual scene can be met. Through the disclosed hash function, the number of times of ciphertext communication between the user and the server and the decryption operation complexity of the user can be reduced, and the response speed of private information retrieval is improved.
Owner:云南电网有限责任公司信息中心
Private information retrieval with probabilistic batch codes
Systems, methods, and computer-executable instructions for reducing amortized computational costs for a query that includes receiving at least two indexes for elements stored in an n-element database. The n-element database is encoded into at least three buckets. Each element is stored within at least two buckets. Each bucket stores a proper subset of the n-elements. For each of the two indexes, a bucket is determined to retrieve the element at the index. The determined buckets are queried to retrieve the elements. The elements at the indexes are retrieved based on the querying the determined buckets.
Owner:MICROSOFT TECH LICENSING LLC
Private information retrieval method and device, equipment and storage medium
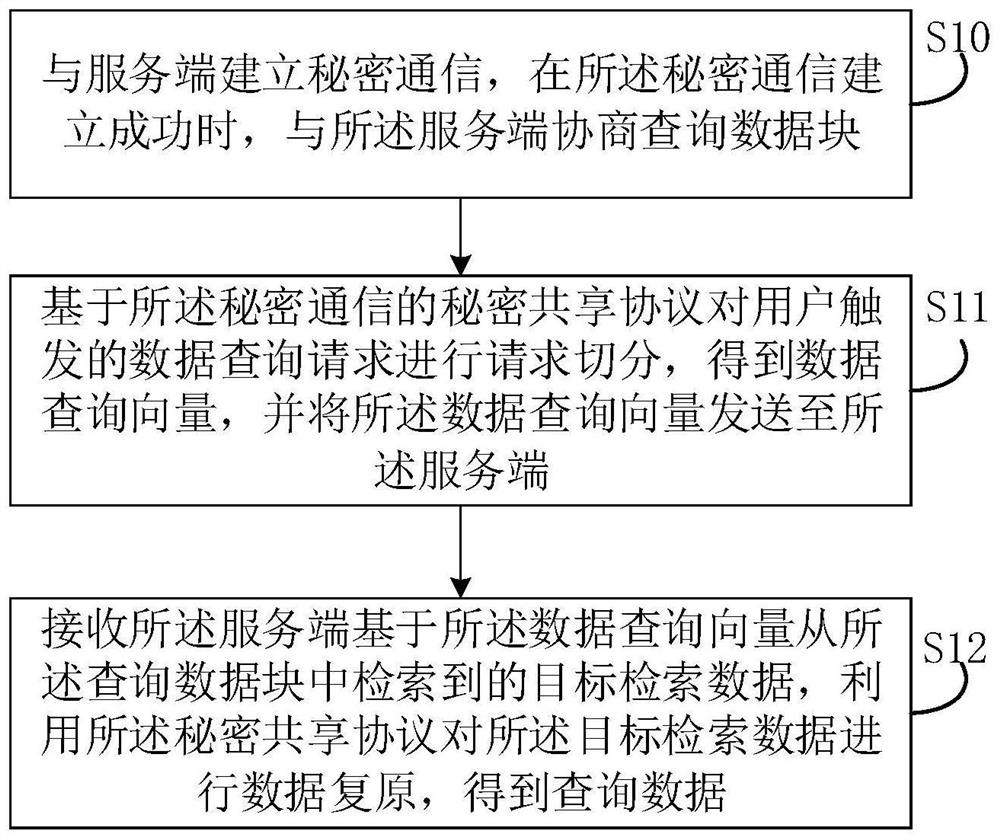
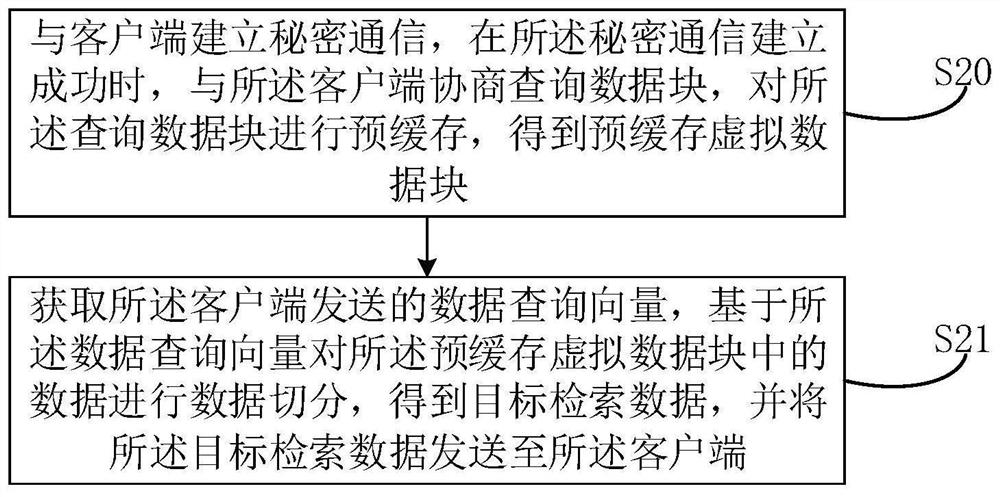
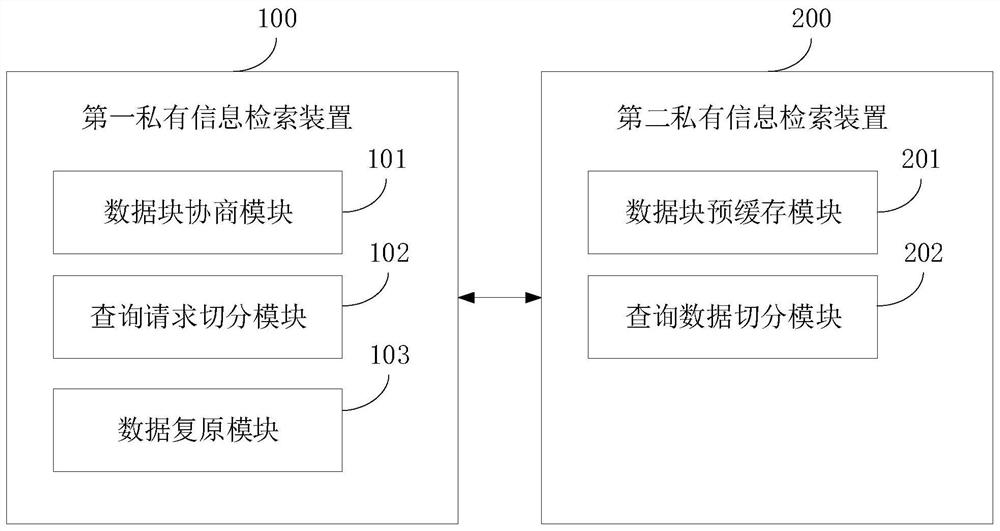
PendingCN113378228AImprove query speedImprove retrieval efficiencyDatabase management systemsDigital data protectionEngineeringData query
The invention relates to the technical field of security, and discloses a private information retrieval method, which comprises the steps of establishing secret communication with a server side, negotiating a query data block with the server side when the secret communication is successfully established, performing request segmentation on a data query request triggered by a user based on a secret sharing protocol of the secret communication, and obtaining a data query vector, sending the data query vector to the server side, receiving target retrieval data retrieved from the query data block by the server side based on the data query vector, and performing data recovery on the target retrieval data by using the secret sharing protocol to obtain query data. The invention further provides a private information retrieval device, electronic equipment and a computer readable storage medium. The problem that the private information retrieval efficiency is low can be solved.
Owner:招商局金融科技有限公司
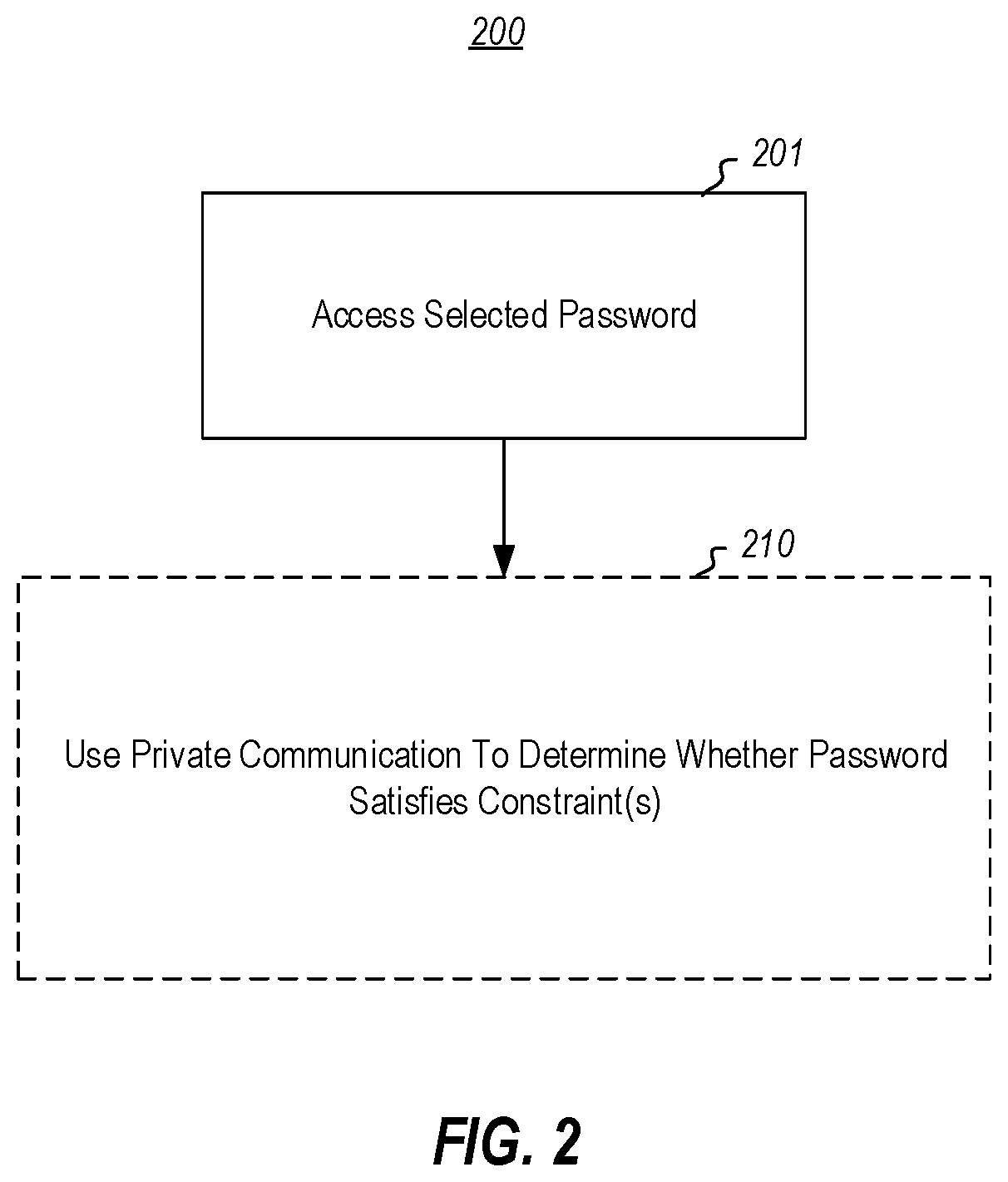
Private password constraint validation
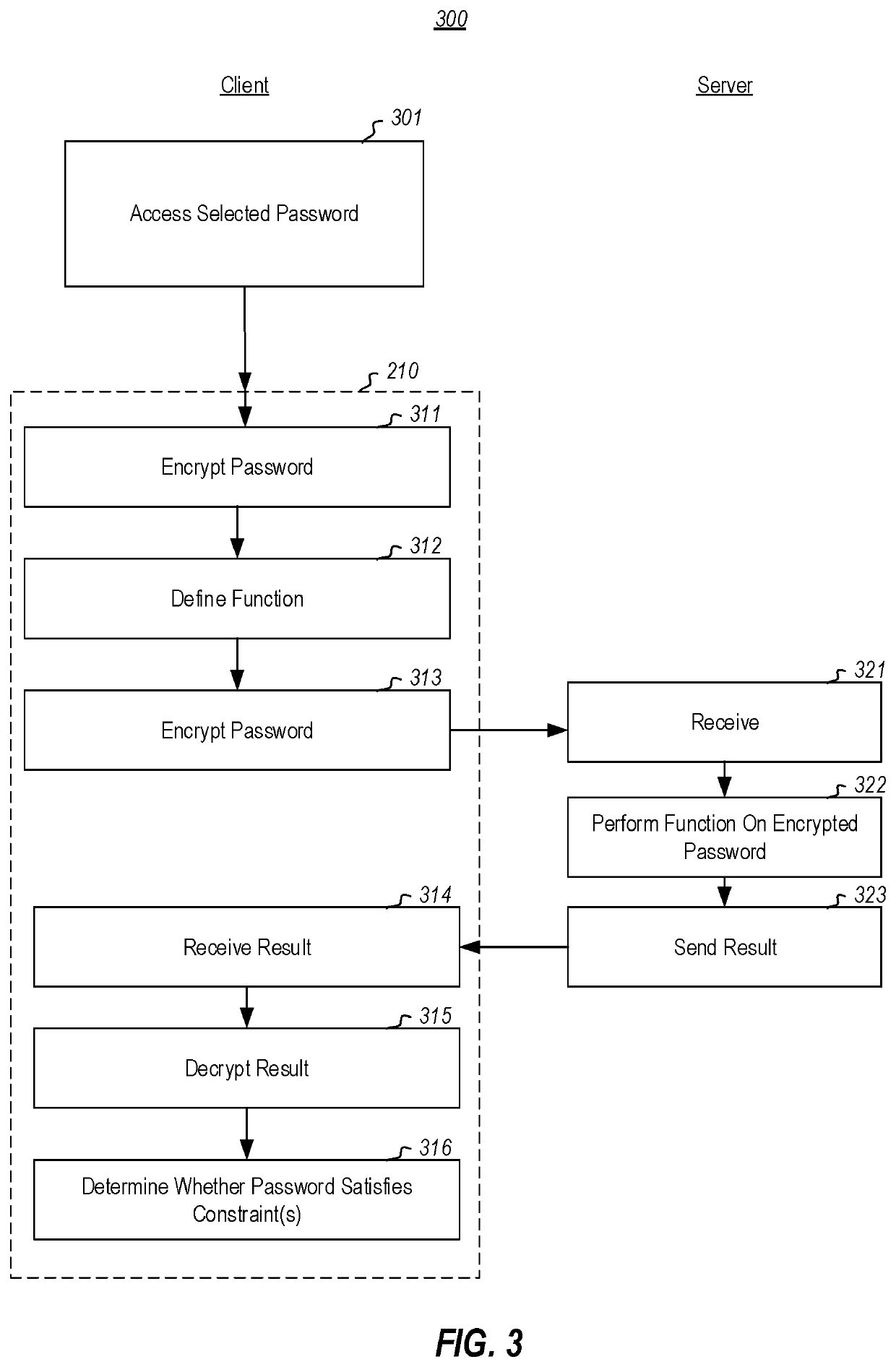
ActiveUS20210117533A1Easy to useDigital data protectionDigital data authenticationPrivate communicationThird party
Privately determining whether a password satisfies a constraint without having to divulge the password itself to a third party that evaluates the constraint, and without the third party even being aware of the result of the evaluation. After the user selects a password, private communication (e.g., private information retrieval) is used to determine whether the selected password satisfies password constraints. For instance, the password might be encrypted (e.g., homomorphically), and then the encrypted password and a function definition (e.g., a homomorphic function definition) is then provided to the third party. The third party then performs the function and returns an already encrypted result. The third party generated the encrypted result directly, without having access to the result in the clear. Upon receiving the encrypted result, the user's computing system may then decrypt the result, to find out whether the password satisfies the constraints, and thus is sufficiently safe.
Owner:MICROSOFT TECH LICENSING LLC
All-parameter private information retrieval method based on sawtooth decoding
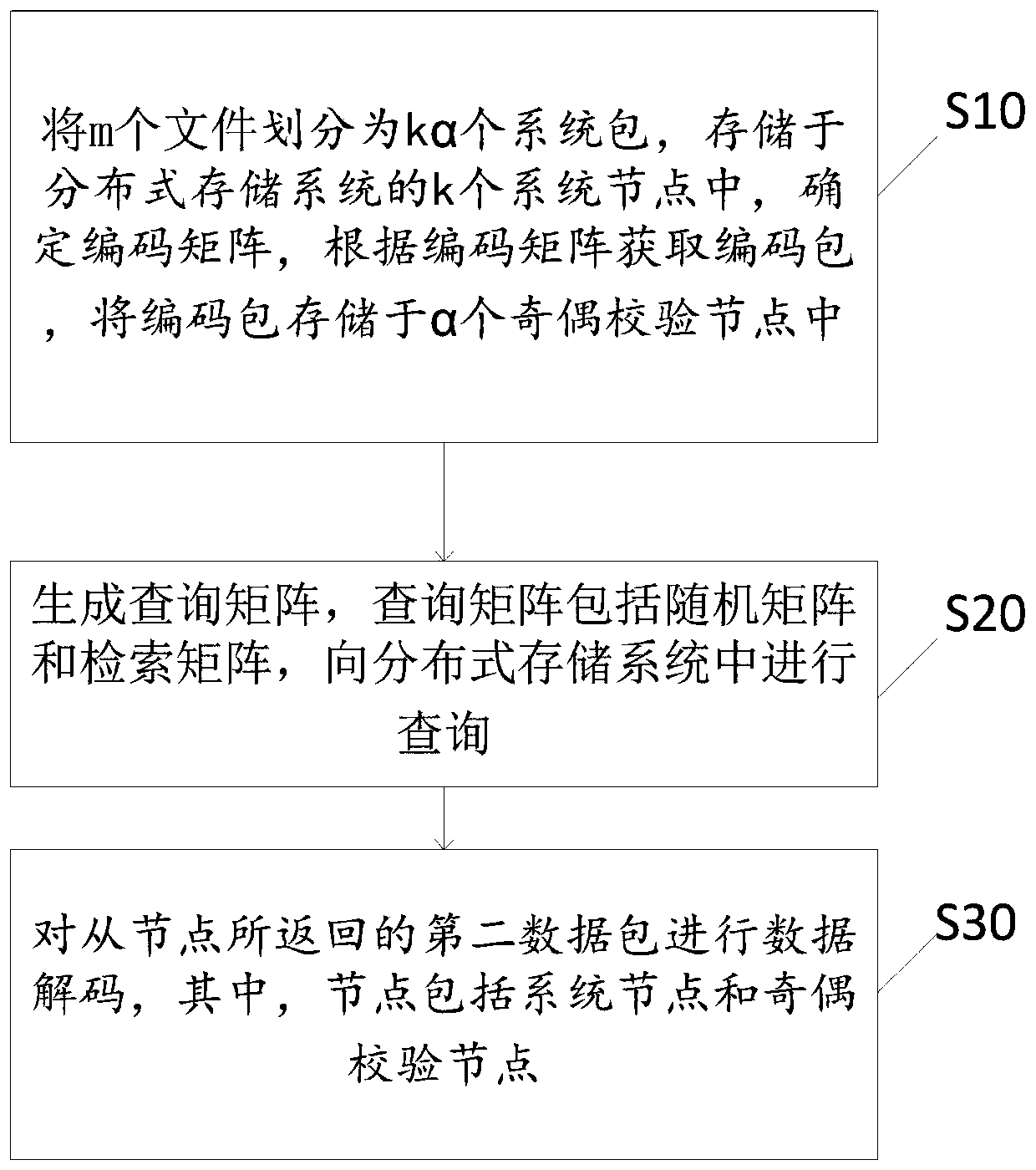
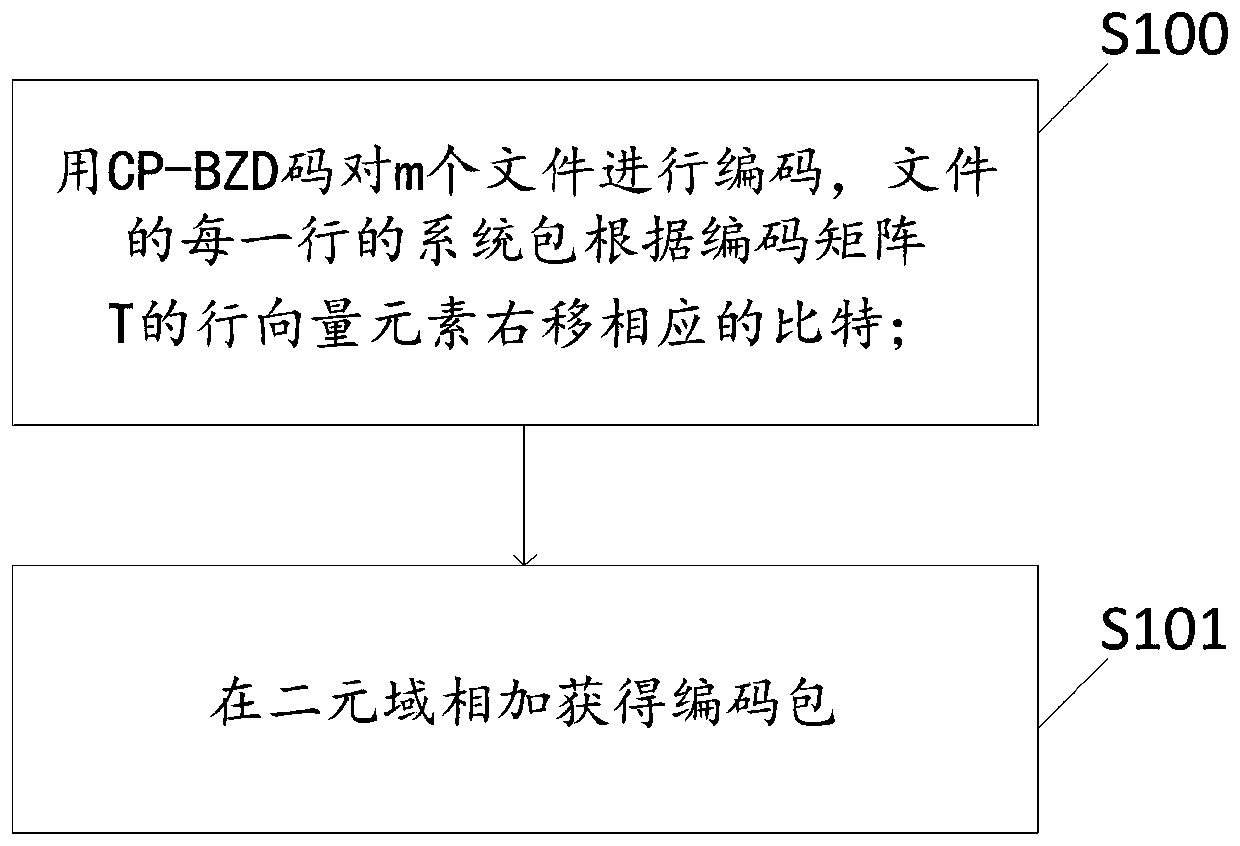
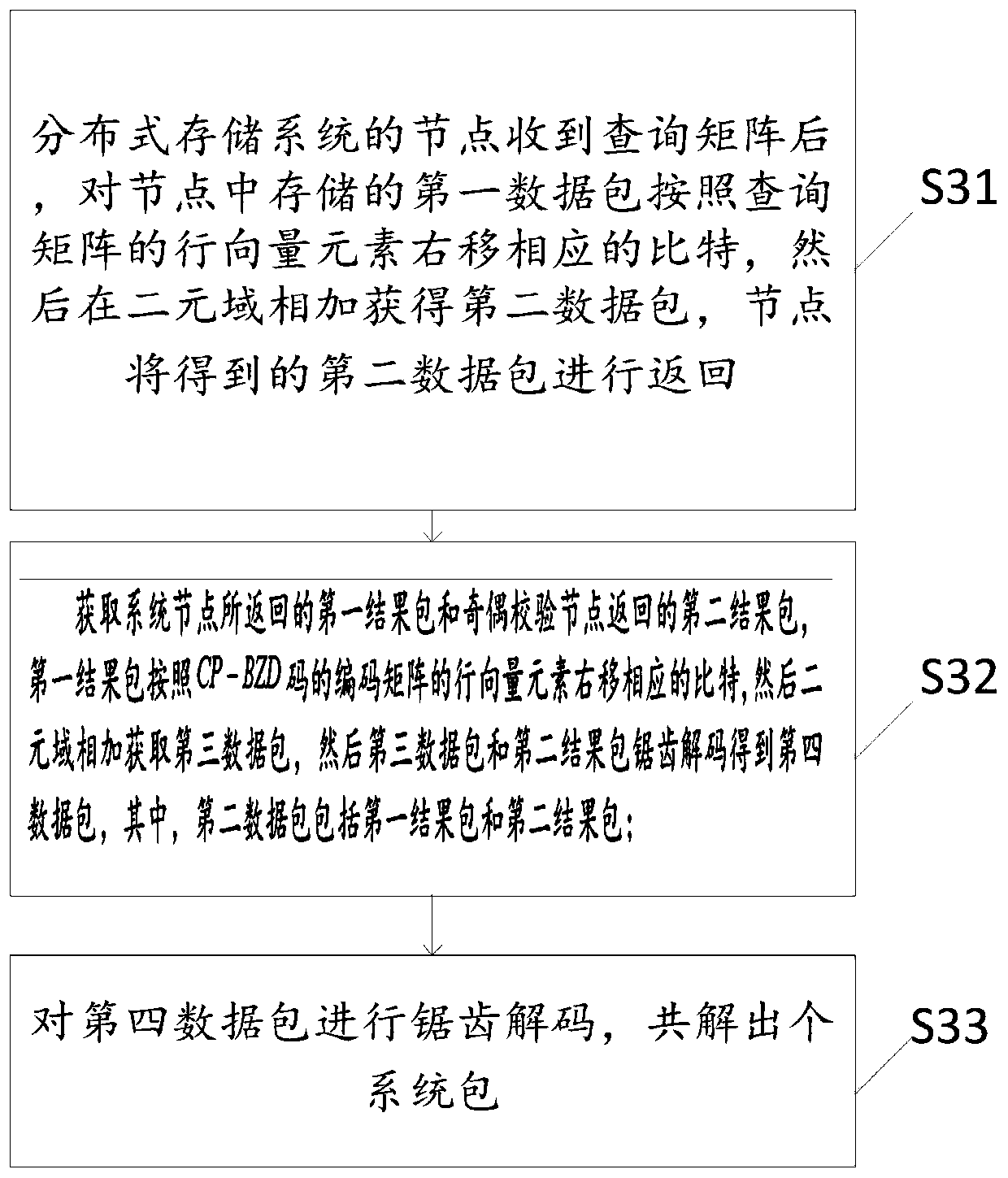
ActiveCN110362537AReduce computational complexityReduce communication costsError preventionFile metadata searchingComputation complexityNetwork packet
The invention discloses an all-parameter private information retrieval method based on sawtooth decoding. The method comprises the following steps: step S10, dividing m files into k alpha system packets, storing the k alpha system packets in k system nodes of a distributed storage system, determining a coding matrix, obtaining a coding packet according to the coding matrix, and storing the codingpacket in alpha parity check nodes; s20, generating a query matrix, wherein the query matrix comprises a random matrix and a retrieval matrix, and query is conducted in the distributed storage system;and step S30, carrying out data decoding the second data packet returned by the slave node, wherein the node comprises a system node and a parity check node. The method can be suitable for all parameters, the application range is widened, the calculation complexity is low, and the communication cost is low.
Owner:SHENZHEN UNIV
User Privacy Protection Method in Personalized Information Retrieval
ActiveCN103279499BGuaranteed privacy and securityDoes not affect calculation resultsDigital data protectionSpecial data processing applicationsStatistical databasePersonalized search
The invention discloses a user privacy protection method in personalized information retrieval. The user privacy protection method in personalized information retrieval is a user interest model anonymization method based on difference privacy and aims to remove contradiction between user privacy protection and improvement of personalized information retrieval performance. The user privacy protection method in personalized information retrieval aims to conduct anonymization after identifiers of a user interest model are concealed, and namely after the identifiers (including the ID, the name, the ID number, the SSN and the like of a user) are eliminated, related technologies of the difference privacy are mainly used for anonymizing standard identifiers of the user interest model. Namely, generalization is conducted on the standard identifiers of the user, Laplace noise is added so as to enable difference privacy protection requirements to be met, the inquiry precision of a statistical database is maximized, and the probability of identification of an entity and attributes is minimized. The user privacy protection method in personalized information retrieval can be widely applied to service systems, such as a personalized retrieval service system and a personalized recommendation service system. The invention belongs to the technical field of information and computers.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com