Privacy protection identity authentication method supporting thin client under blockchain PKI (Public Key Infrastructure)
A thin client and privacy protection technology, applied in the field of information security, can solve problems such as difficulty in completing identity authentication services based on blockchain PKI, limited storage capacity and computing power, and inability to download blockchains, so as to prevent man-in-the-middle attacks, The effect of protecting data privacy and protecting query privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment
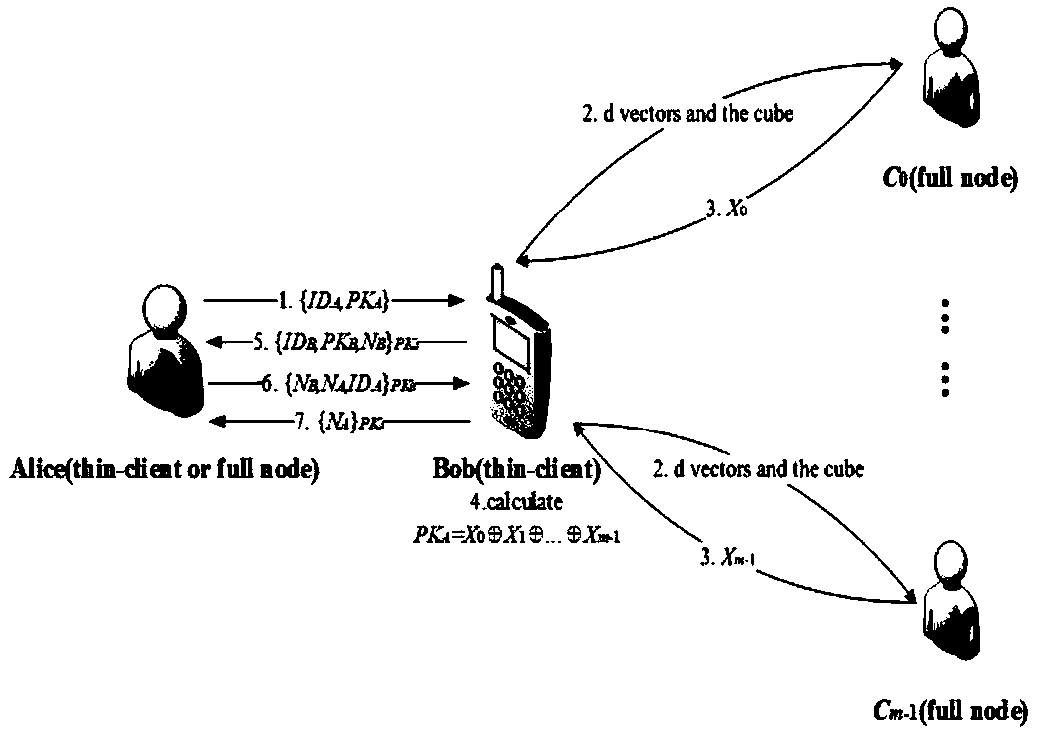
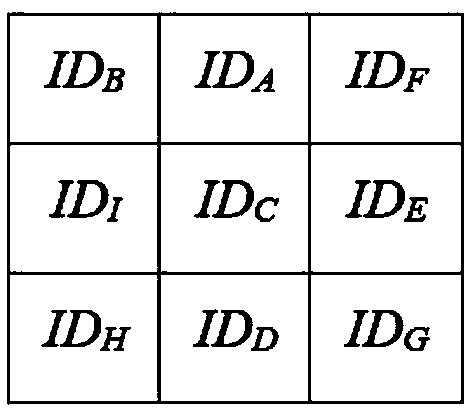
[0051] The thin client Bob needs to verify that the identity information is ID A , let d=2, l=3, have k=9, m=4. Bob chooses 8 identity IDs arbitrarily, which are ID B , ID C ,...,ID I . Such as figure 2 As shown, the 9 identity information ID A , ID B ,...,ID I Put it into a 3×3 grid after obfuscation, and use the position vector (1, 2) to represent the ID A position in the grid. Next, Bob generates two random vectors By calculating the ID A The position vector (1, 2) and XOR to get two new vectors Subsequently, Bob sends the same 3×3 grid and two different vectors to all four full-node users, specifically, to C 00 send vector to C 01 send vector to C 10 send vector to C 11 send vector
[0052] Full node user C 00 Find Get the position vector (3, 1). The position vector (3, 1) corresponds to the identity information ID H , so C 00 Traverse the blockchain to obtain the public key PK H , and the result X 1 = PK H Return to Bob; C 01 Find ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com