Private information retrieval method in environment of a plurality of servers
A server and server-side technology, applied in the field of private information retrieval, can solve the problem of not considering the potential threat to private information of a single server, and achieve the effect of reducing the threat
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
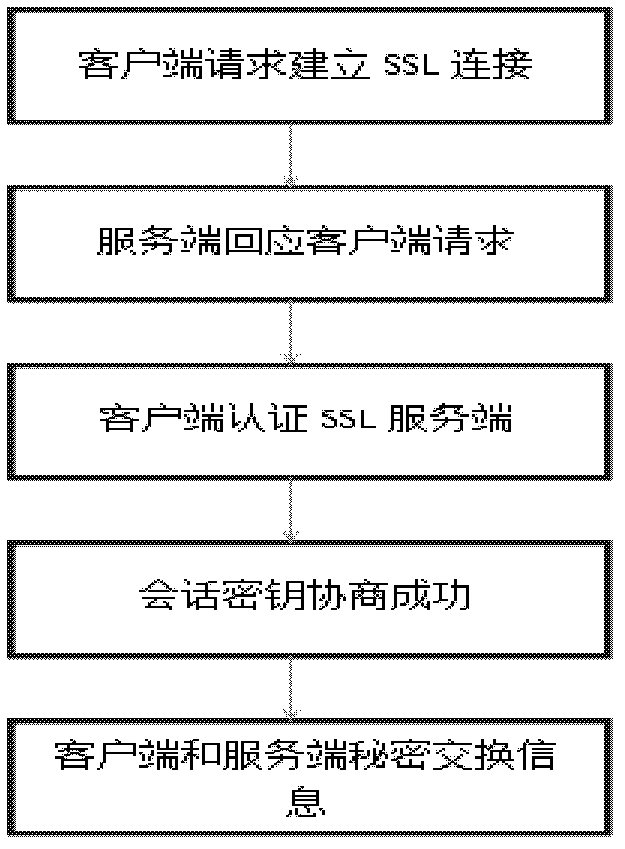
[0056] This embodiment provides a method for establishing a secret communication between a client and a server, and the user can use this method to establish a secret channel with the server. Such as figure 1 As shown, this embodiment includes the following steps:
[0057] Step 1, the user applies to establish a connection to the server. The user sends a Client-Hello message to the server, and transmits information such as the encryption type that the machine can handle to the server;
[0058] Step 2: The server responds to the user with a Server-Hello message and sends its own X.509 certificate so that the user can authenticate itself;
[0059] Step 3: After the user authenticates the server, the master key will be generated, and then encrypted with the public key of the server using the RSA encryption algorithm and then transmitted;
[0060] Step 4: The server uses its own private key to decrypt the information sent by the user. The user sends the session ID to the serve...
Embodiment 2
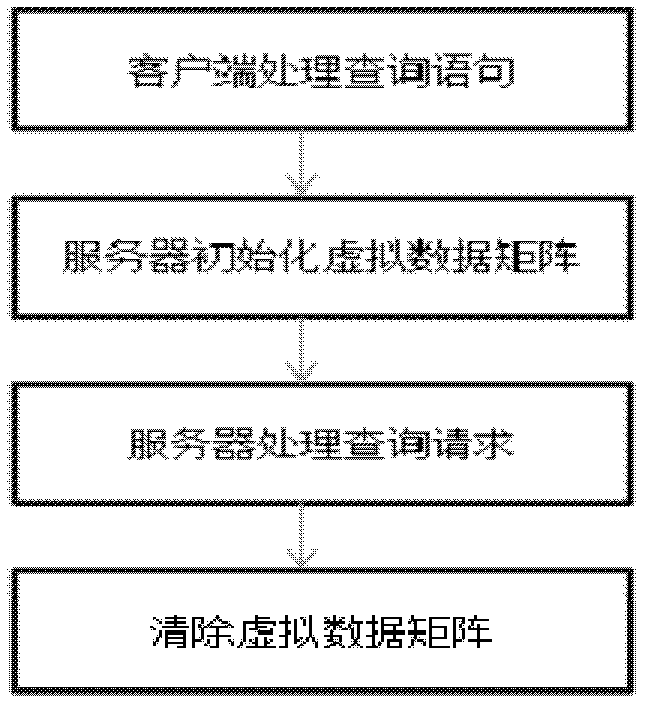
[0063] This embodiment provides a method for an interaction process between a client and a server, and the user can use this method to interact with the server. Such as figure 2 As shown, this embodiment includes the following steps:
[0064] Step 1: On the client side, the query statement sent to the server side needs to be processed. Here, it is assumed that the user's query sentence is "high blood pressure". Then, a certain encoding method is used to encode it, and it will be sent in the form of a digital stream, and then it needs to be processed using the secret sharing protocol and the ElGamal encryption algorithm. ,Specifically:
[0065] ①. Given a finite field Z and a secret σ∈Z, a (3+1)-private 6-way secret sharing scheme needs to be established. Here, l is taken as 6, and t is taken as 3, that is, there are 6 servers in total, and 3 of them conspire with each other, which are malicious servers. Select 6 pairwise different non-zero elements a from Z 1 , a 2 ,......
Embodiment 3
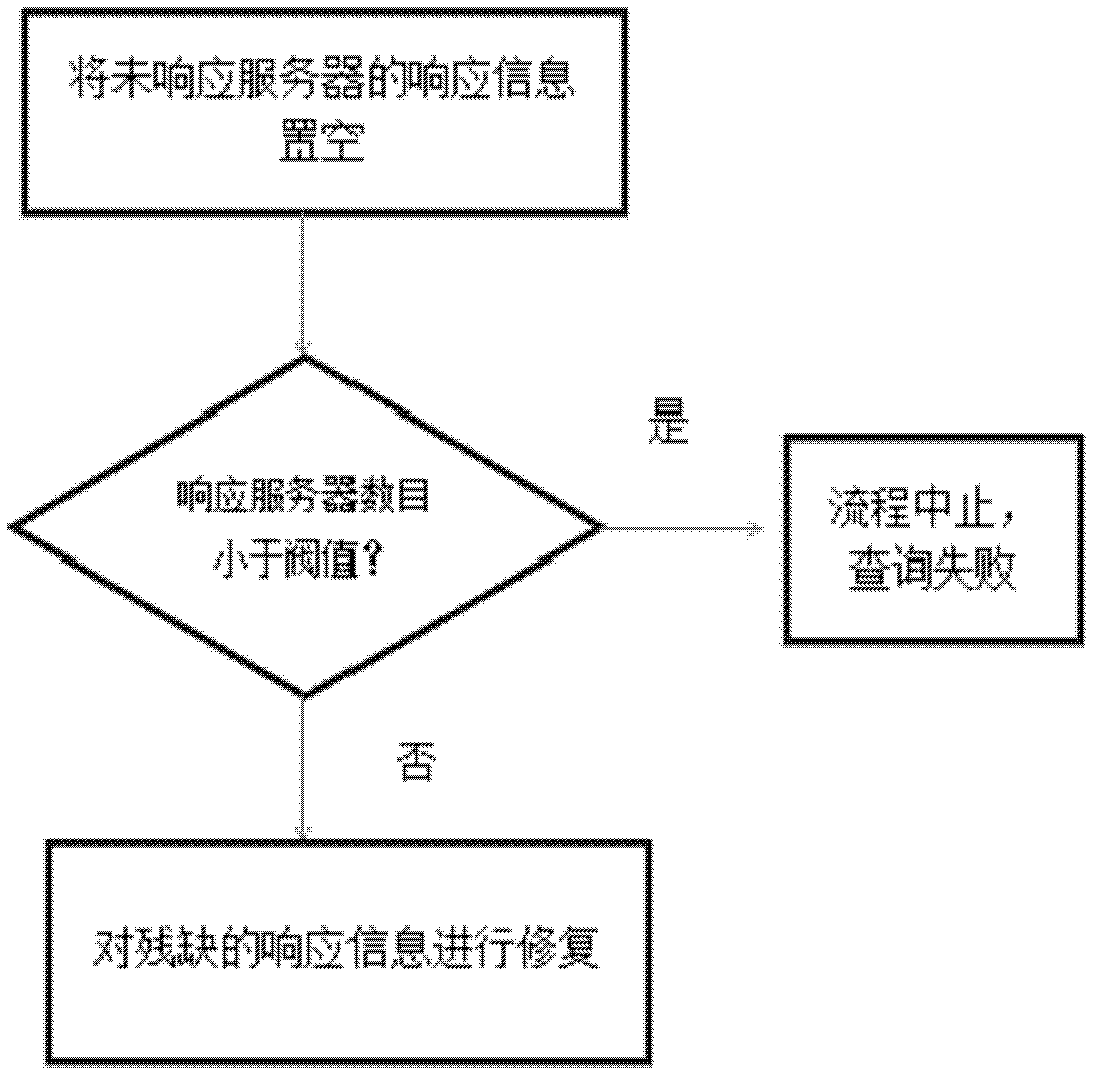
[0074] This embodiment provides a solution for the client to process the information fed back by the server. The user can use this solution to process the received information and obtain required data. Such as image 3 As shown, this embodiment includes the following steps:
[0075] Step 1: Because l (here are 6) servers may not all be able to respond to the client's request, assuming that there are k=4 servers that have responded, then let γ 1 , gamma 2 ,…, γ 4 For these 4 servers, the response vector [R j1 , R j2 ,...,R js ] is set to ⊥. Then G={γ 1 , gamma 2 ,…, γ 4}, and H={(G,ε)}.
[0076] Step 2: For the case of k≤t, that is, the number of responding servers has not reached the number of colluding servers, then the program is terminated and an error "not enough servers respond" is thrown. Therefore, let k be the number of the minimum number of trusted servers, then the range of the number of trusted servers h is In this example, k=4>t=3, so this problem does...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com