Patents
Literature
441 results about "Match rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A reconciliation matching rule is a set of criteria that are used to filter bank statement lines and Microsoft Dynamics 365 for Finance and Operations bank transaction lines during the reconciliation process.
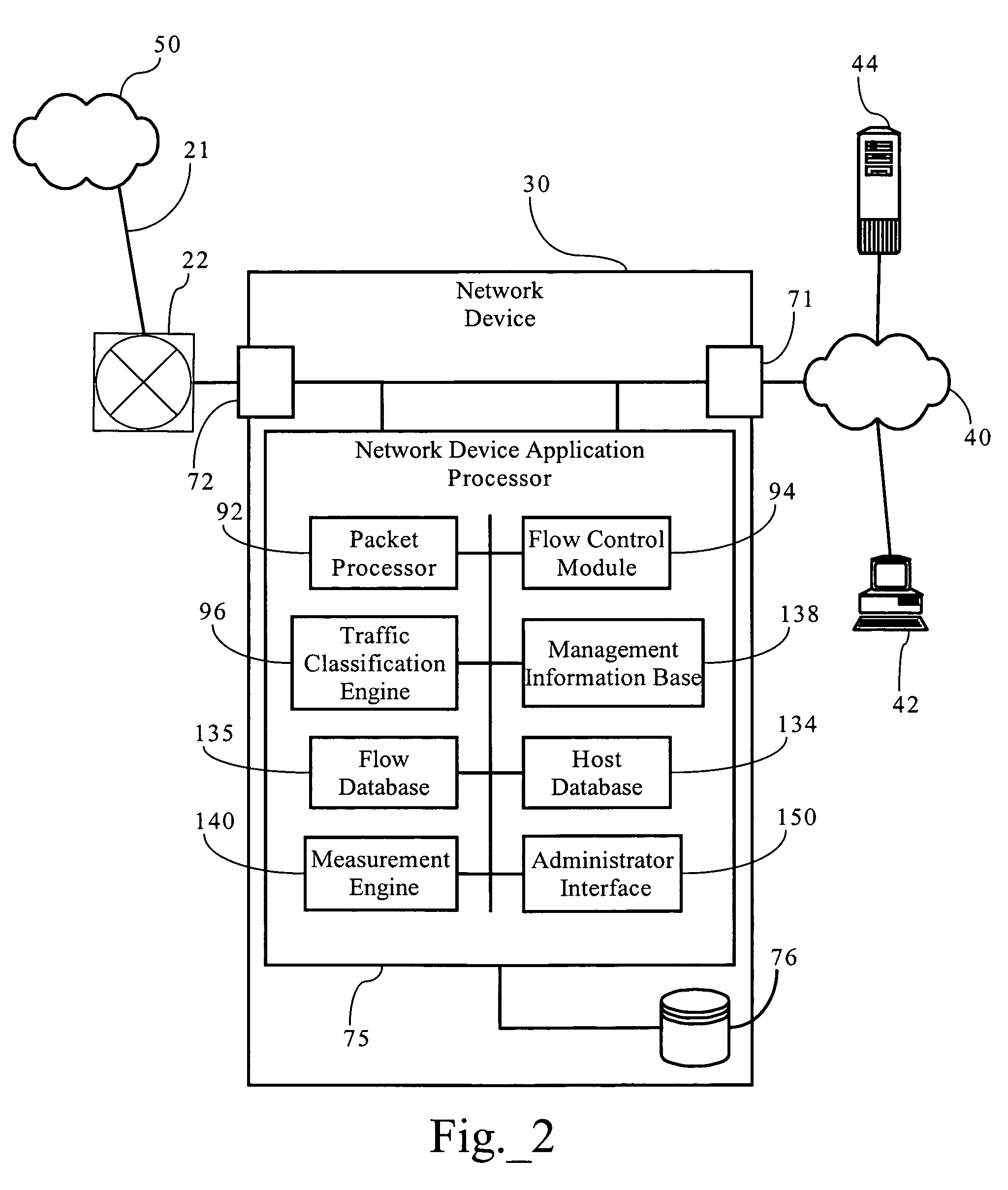
Systems and methods to facilitate selling of products and services
InactiveUS20050097000A1Easy to communicate in real timeIncrease expensesCustomer relationshipBuying/selling/leasing transactionsWeb siteVoice over IP
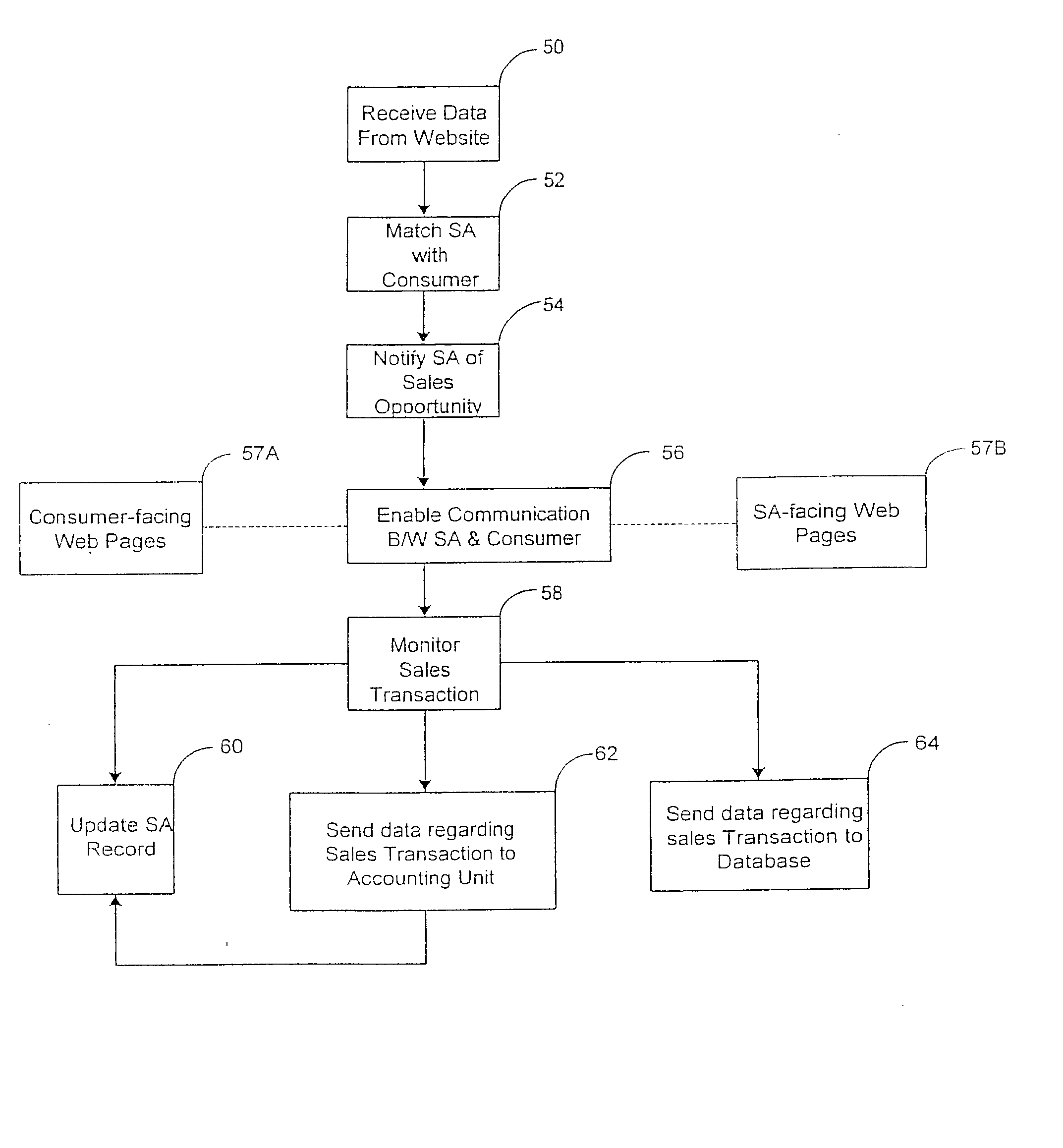
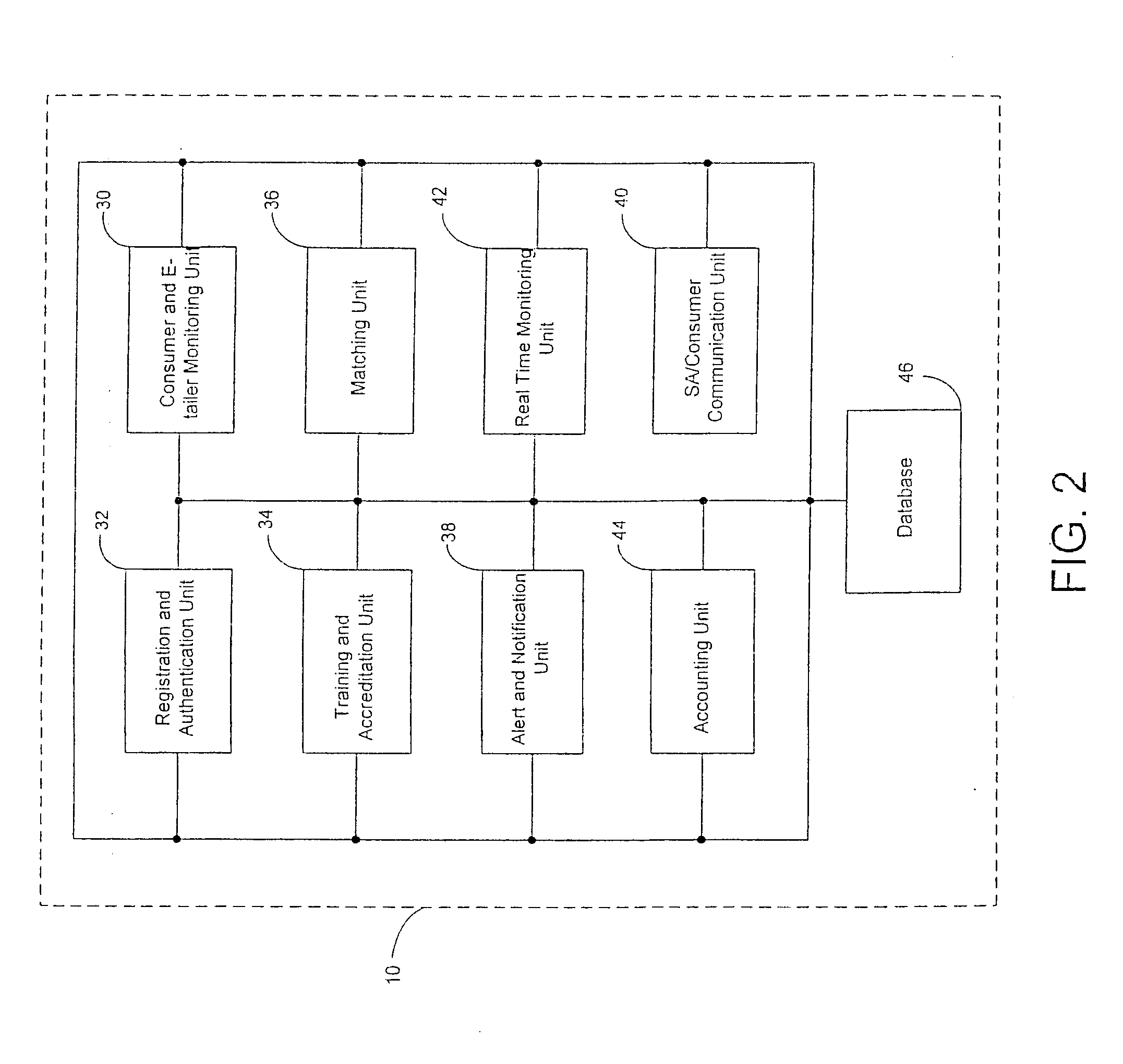
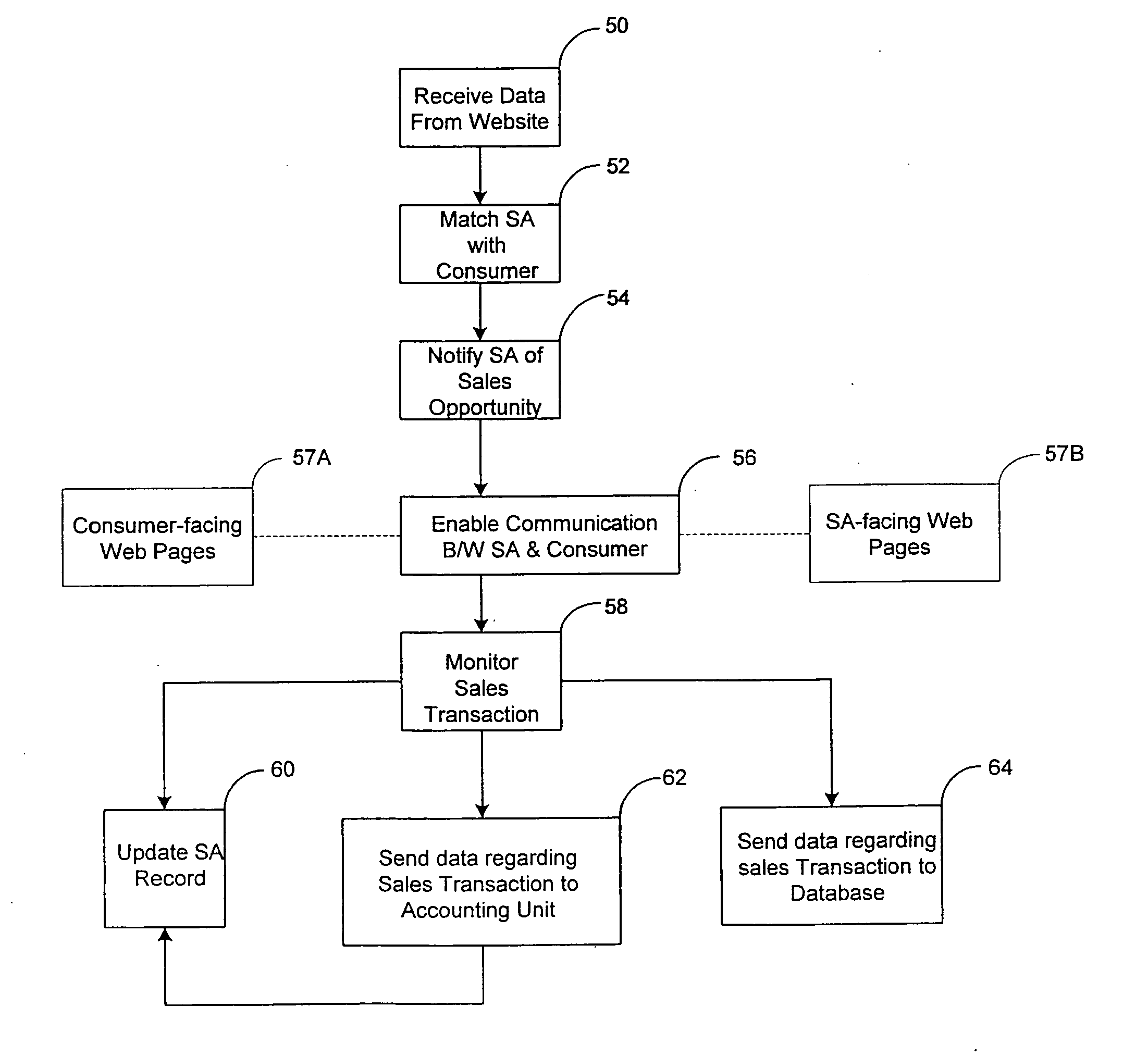
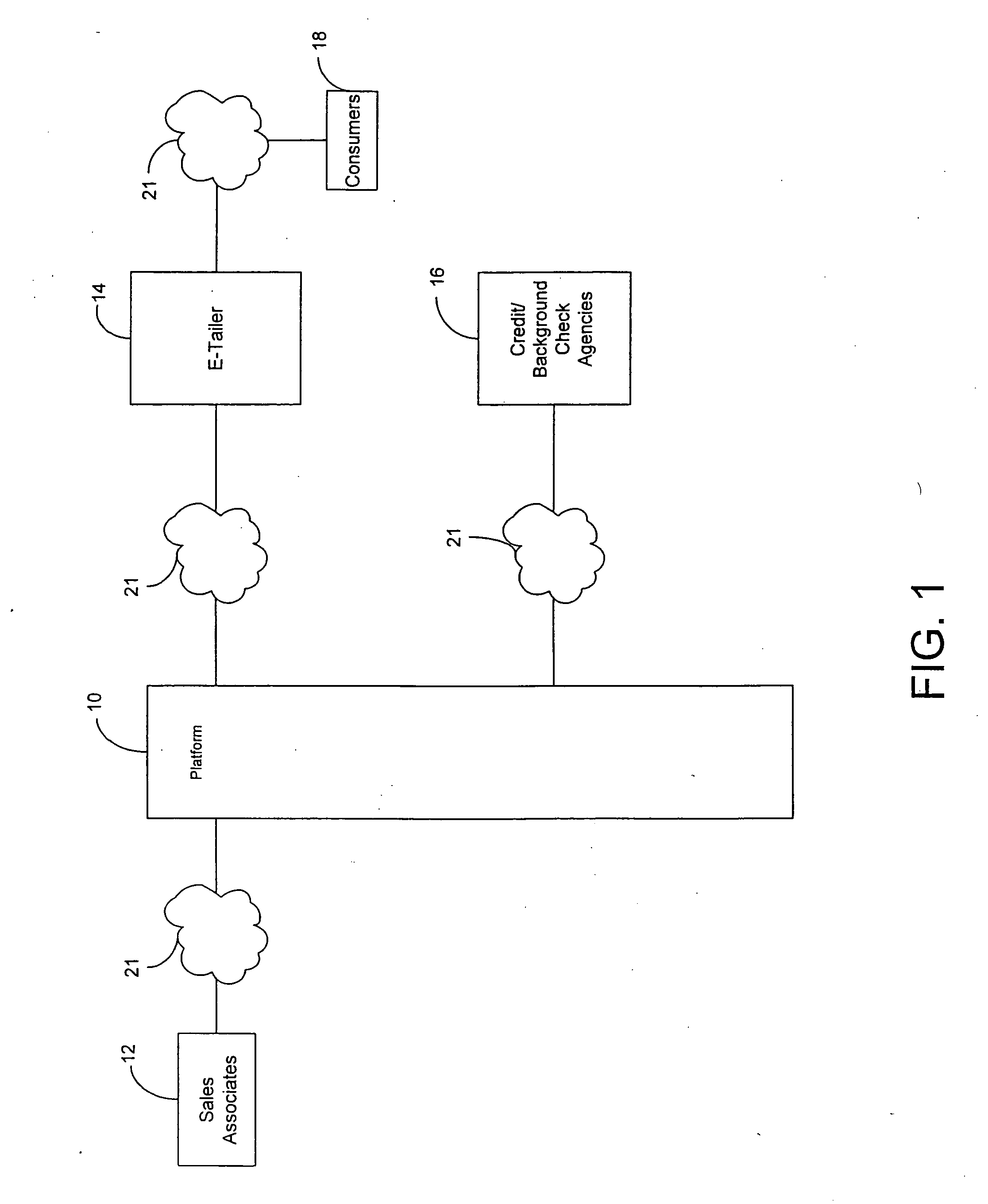
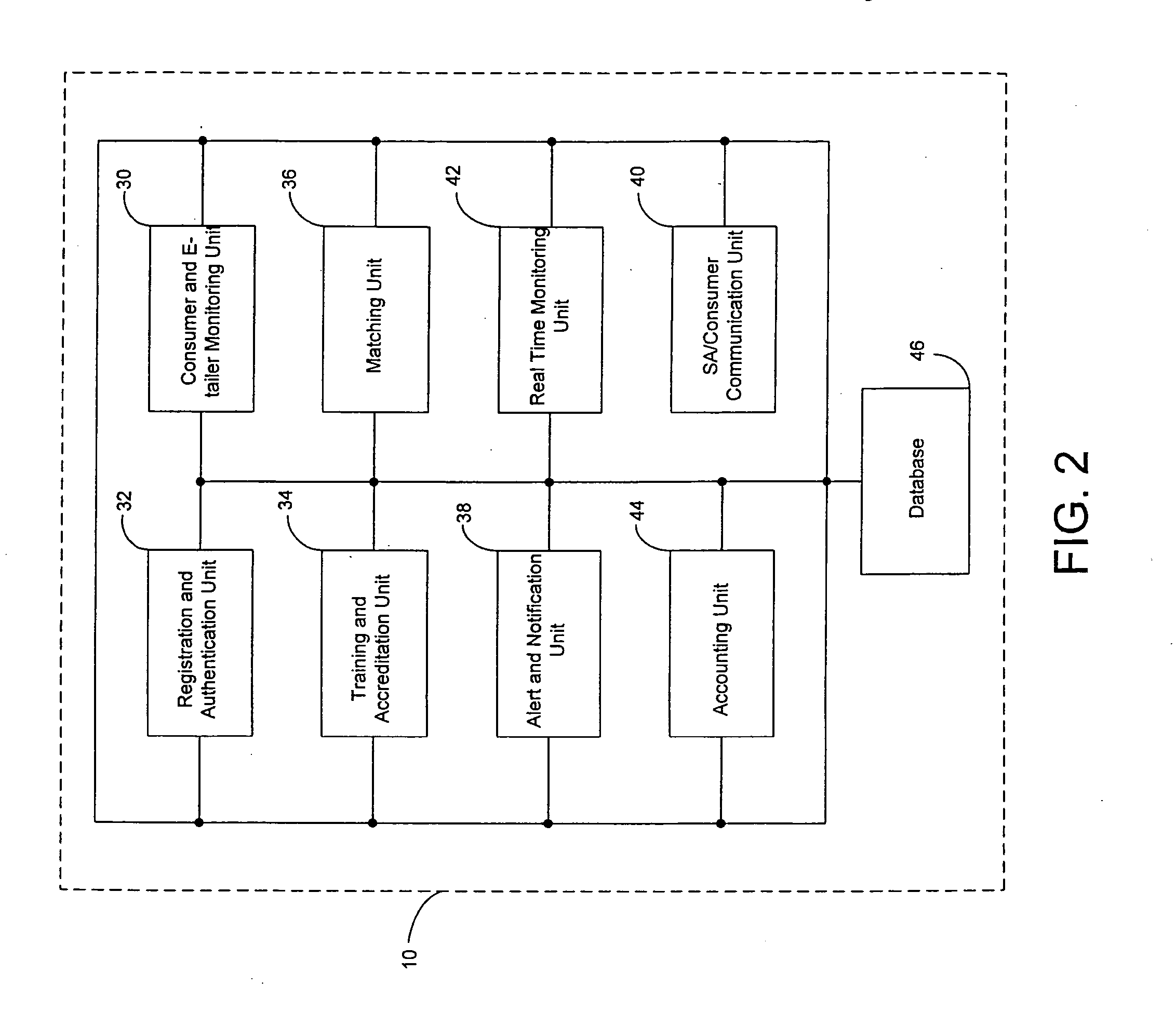
The system of the present invention provides systems and methods for selling goods and services on, over, through, and in conjunction with the Internet. The system receives session (clickstream) information on a customer's website session from the enterprise's website and may also receive customer information on the customer from the enterprise's CRM or eCRM system. The session information referred to comprises the goods or services the customer is searching and metadata about such search and the relevant products, such as the surfing pattern itself. The system determines from the received information, based on the interaction between matching rules created using the system by the enterprise and the system's matching engine, whether the customer is a candidate for assistance from a sales associate. The system creates and indexes information on available sales associates and their performance, selling capabilities and product expertise. The system further matches the customer with at least one sales associate, ideally the most appropriate sales associate, based on the customer, session, and sales profile associate information, and facilitates communication between the sales associate and the customer. Additionally, the system provides information on the customer, products or services the customer is interested in, and the collateral sales materials (both internal and external to the enterprise) and selling techniques to the sales associate based on the particular sales opportunity. The system facilitates communication between the sales associate and the customer on the basis of chat, voice over IP, email and the public switched telephone network, including the concept of bridging a chat session into a PSTN conference call during which call the sales associate and customer maintain a co-browsing session with regard to the opportunity over the Internet.
Owner:LIVEPERSON
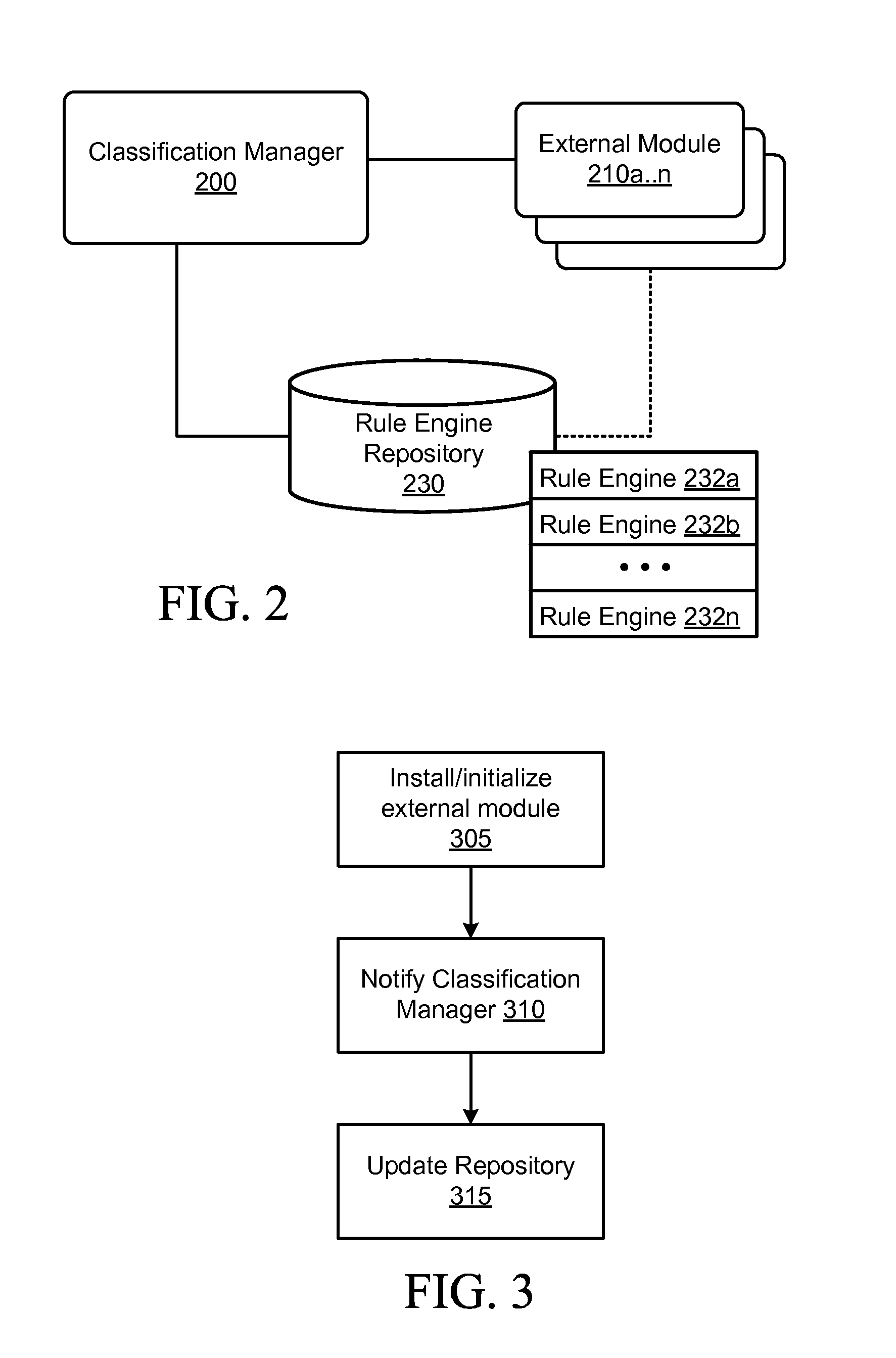
Electronic device and method for classification of communication data objects
InactiveUS20130297604A1Digital data processing detailsSpecial data processing applicationsPattern recognitionMatch rule
A method, system and electronic device are provided for classification of data objects such as messages. A number of rule engines, each of which may be associated with a different application or module, are provided on the electronic device. For each data object obtained by the electronic device, matching rule engines are identified, and the data object is processed by the matching rule engines to determine one or more classification values for the data object. The determined classification is stored in association with a data object identifier. Data objects can be subsequently collated according to their classification, or aggregations of data object listings can be collected and displayed in a plurality of views corresponding to the various classifications.
Owner:BLACKBERRY LTD
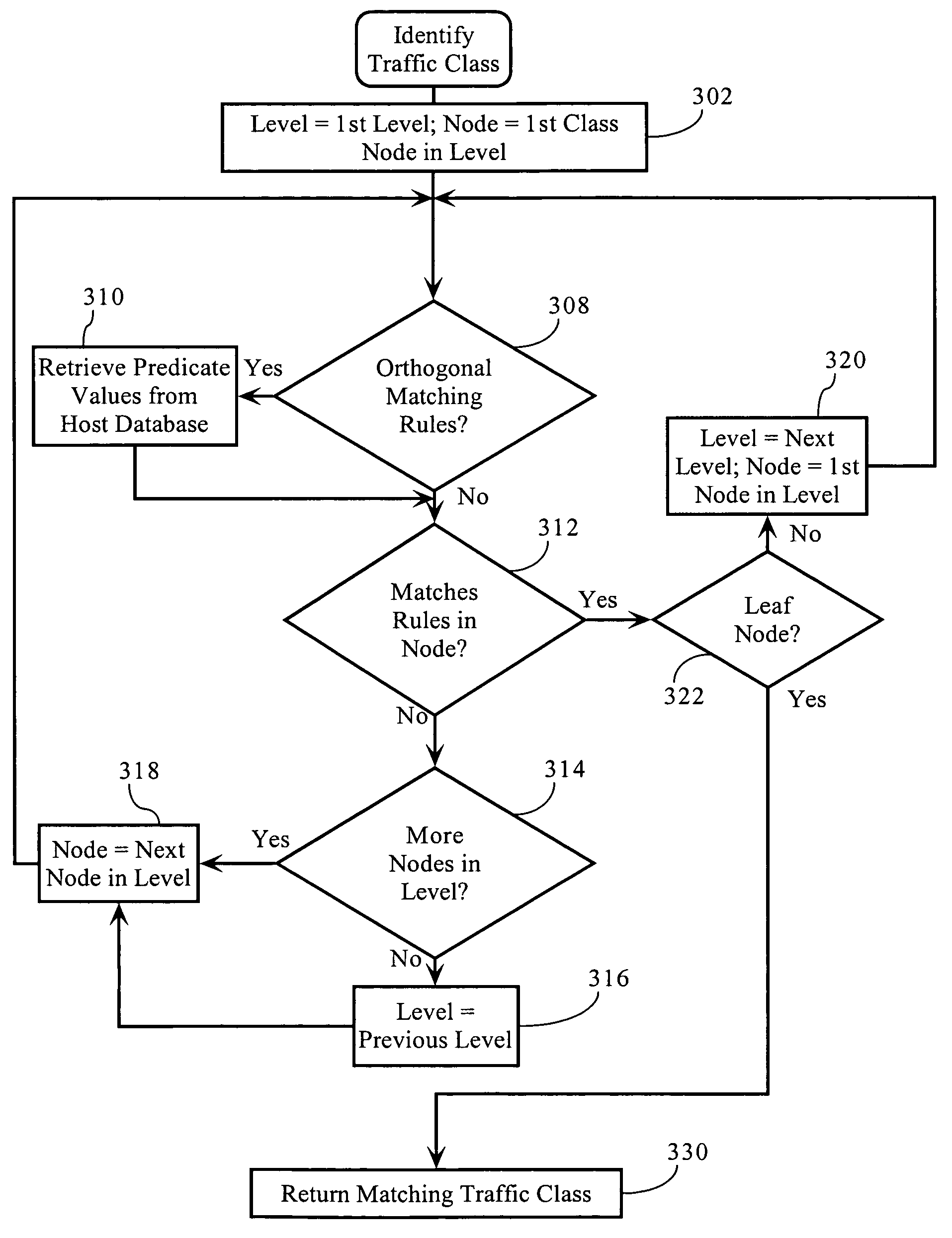
Classification and management of network traffic based on attributes orthogonal to explicit packet attributes
Classification of network traffic based on conditions orthogonal to explicit attributes of packets in network traffic. In one implementation, classification of network traffic based on the behavior of one or more nodes associated with the network traffic. In one implementation, a mechanism is provided that allows for the creation of matching rule predicates that match to certain node behaviors of interest and cause the application of appropriate policies to the network traffic. In one implementation, the node behavior matching functionality can be combined to seamlessly operate in connection with other Layer 7 traffic classification mechanisms that operate on explicitly-presented attributes of the packets.
Owner:CA TECH INC
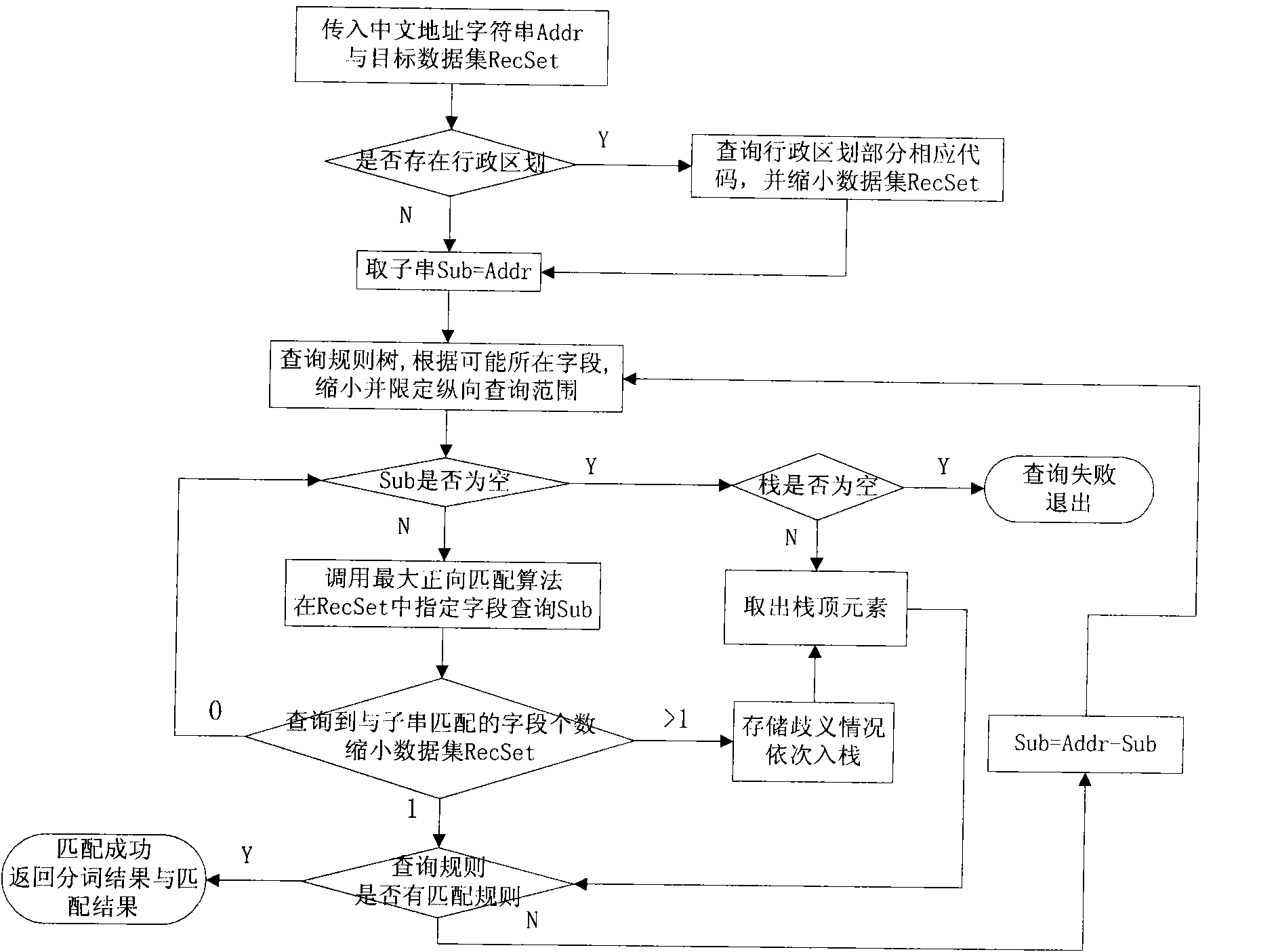
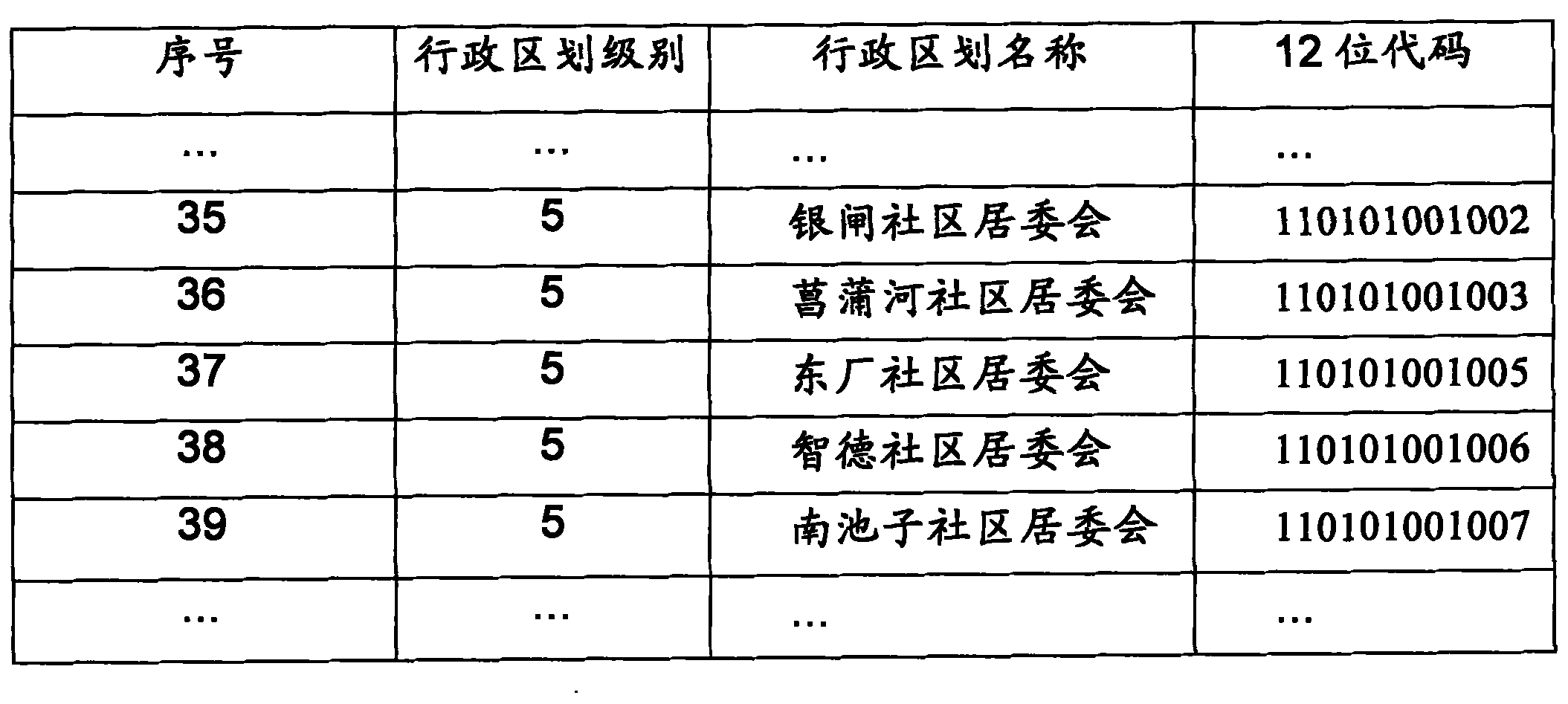
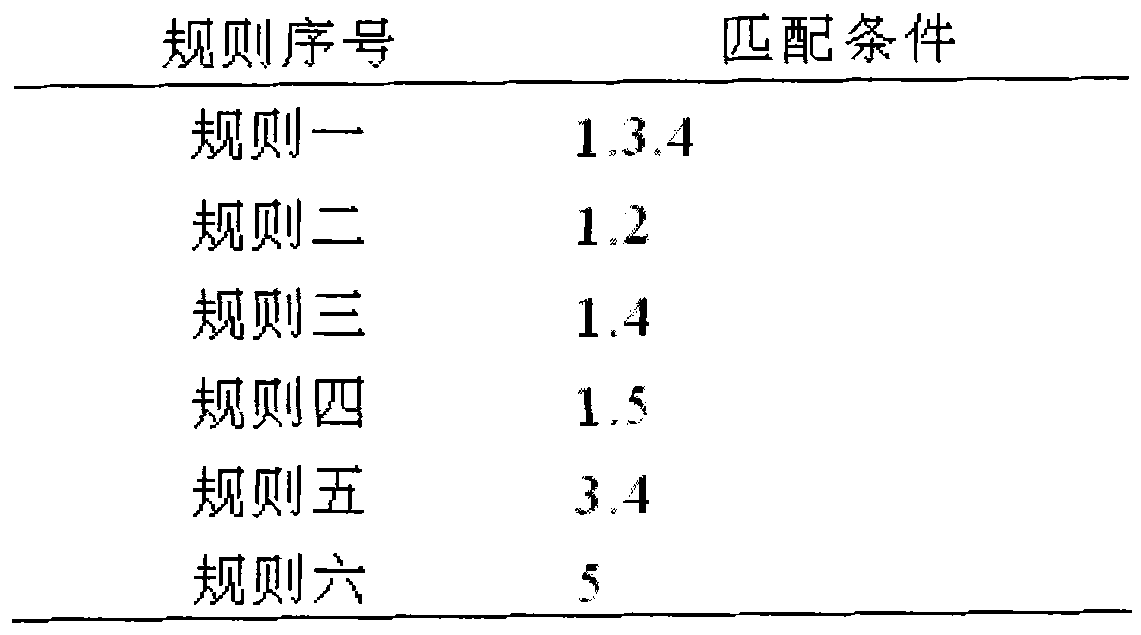
Fuzzy Chinese address geographic evaluation method based on matching rule
InactiveCN101882163AReduce the number of query visitsImprove matching speedSpecial data processing applicationsData setAmbiguity
The invention relates to a fuzzy Chinese address geographic evaluation method based on a matching rule, which belongs to the field of the address evaluation of a geographic information system. The method comprises the following steps: firstly, reading in an address character string and a standard address base; inquiring and dividing administrative division parts in the address character string and filtering reduced target data sets; then realizing the segmentation and the matching of an address by means of a matching rule tree and a rule base in allusion to the fuzzy problems of address element incompletion, address ambiguity and the like frequently appearing in the address character string, and returning a matching record meeting requirements. The invention integrates two important links of address segmentation and database matching in geographic evaluation, realizes that the database matching of the address is completed while in segmentation, effectively solves the address matching problem of the fuzzy Chinese address and improves the accuracy and correctness of address matching.
Owner:INST OF GEOGRAPHICAL SCI & NATURAL RESOURCE RES CAS
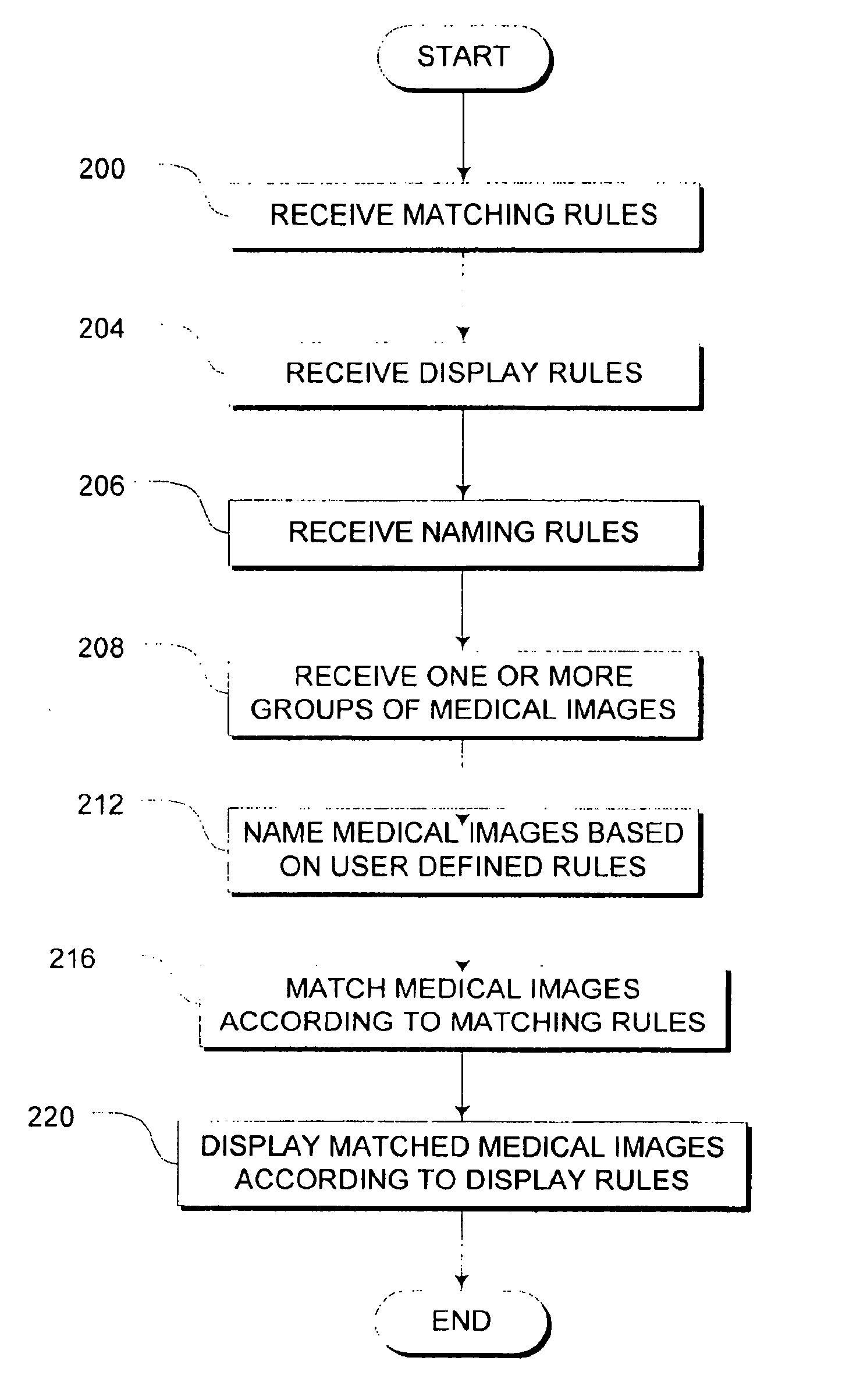
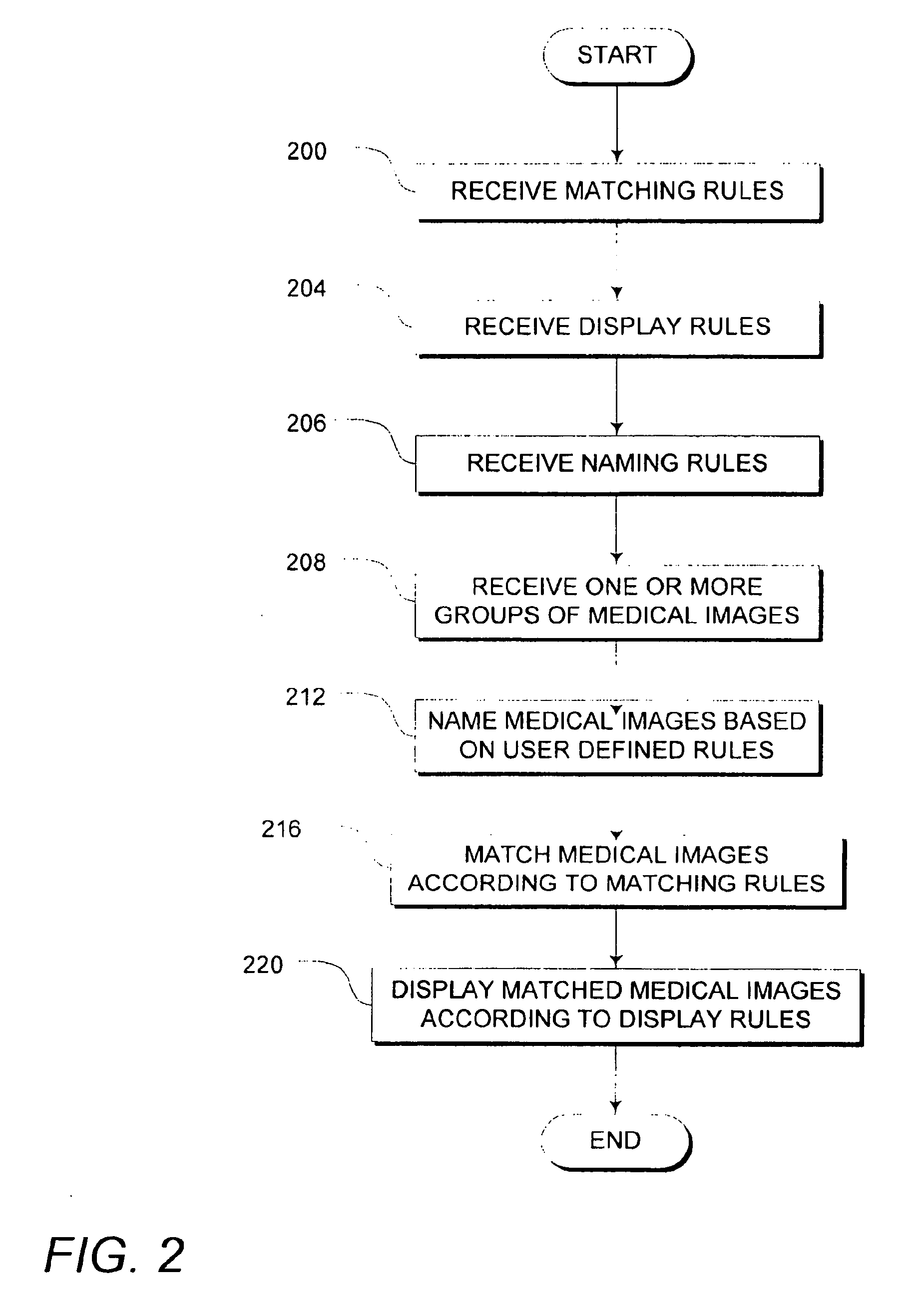
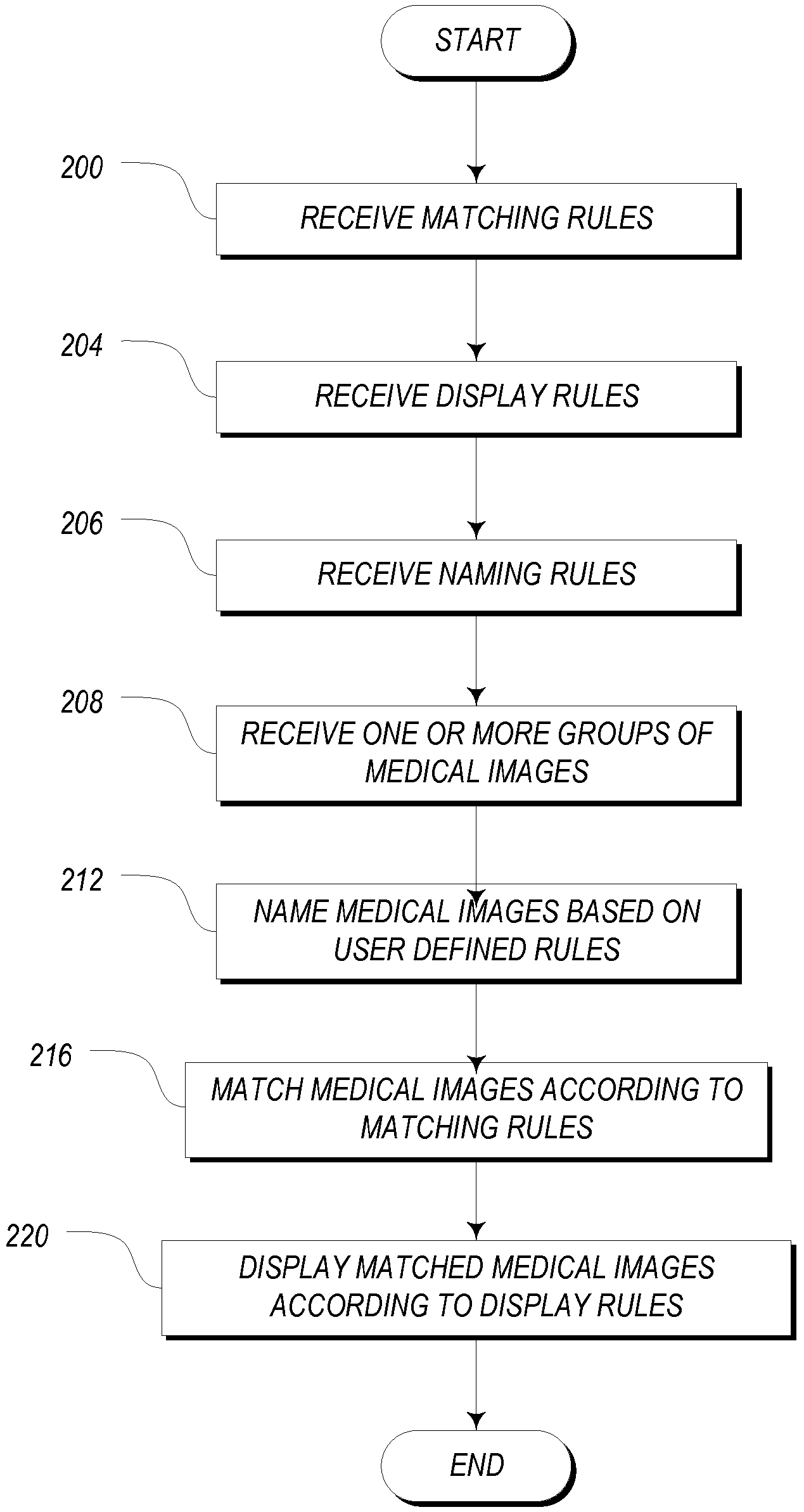
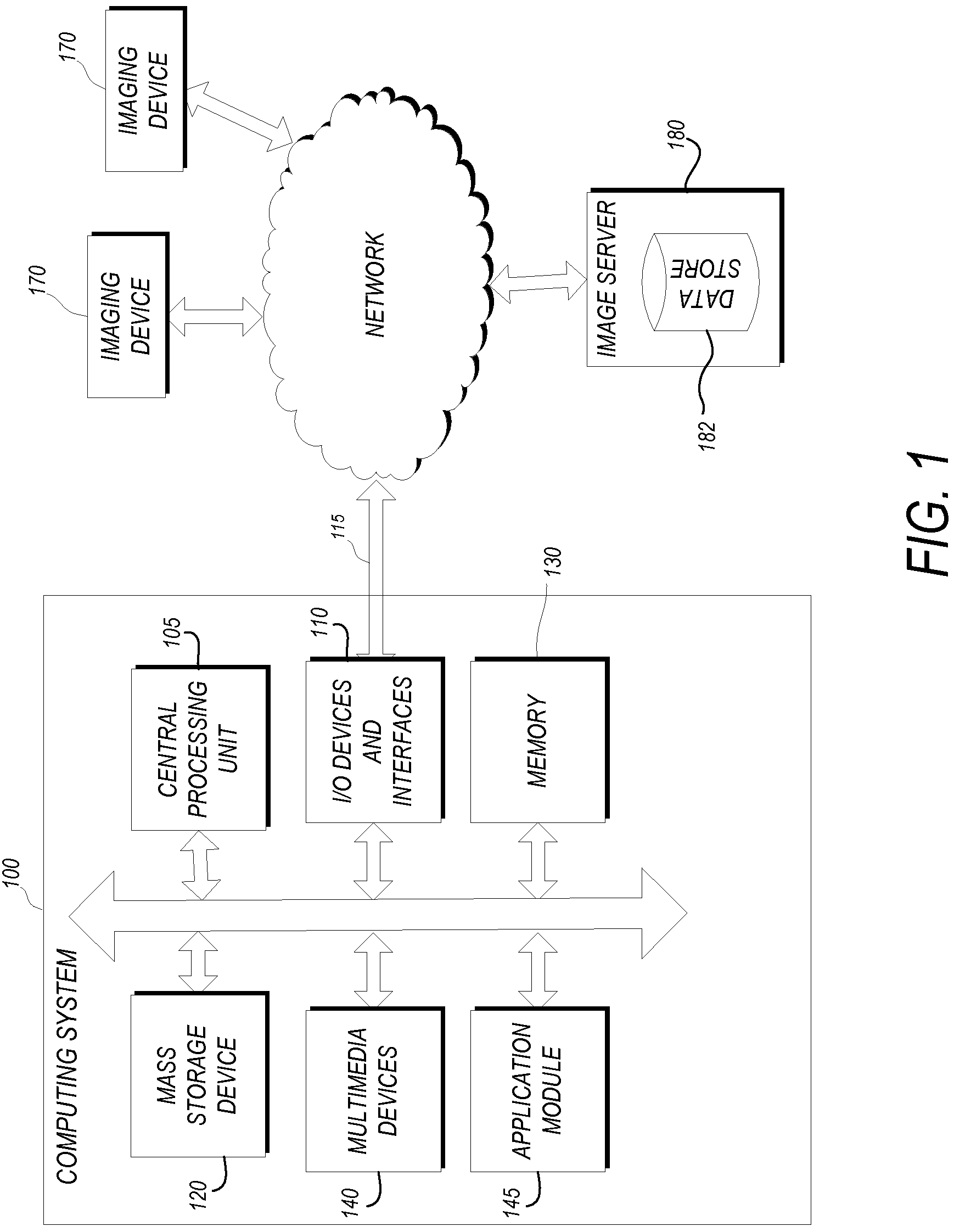
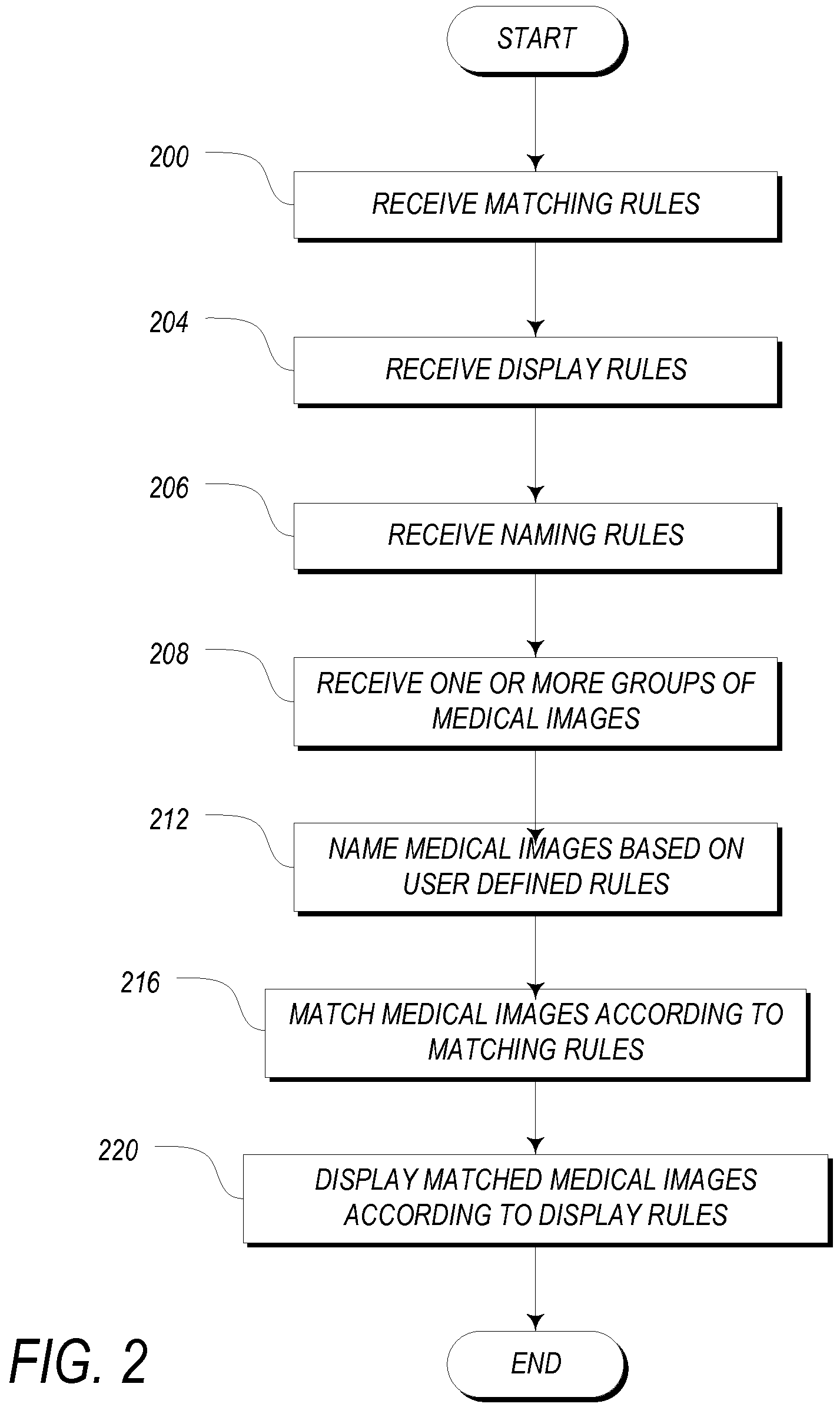
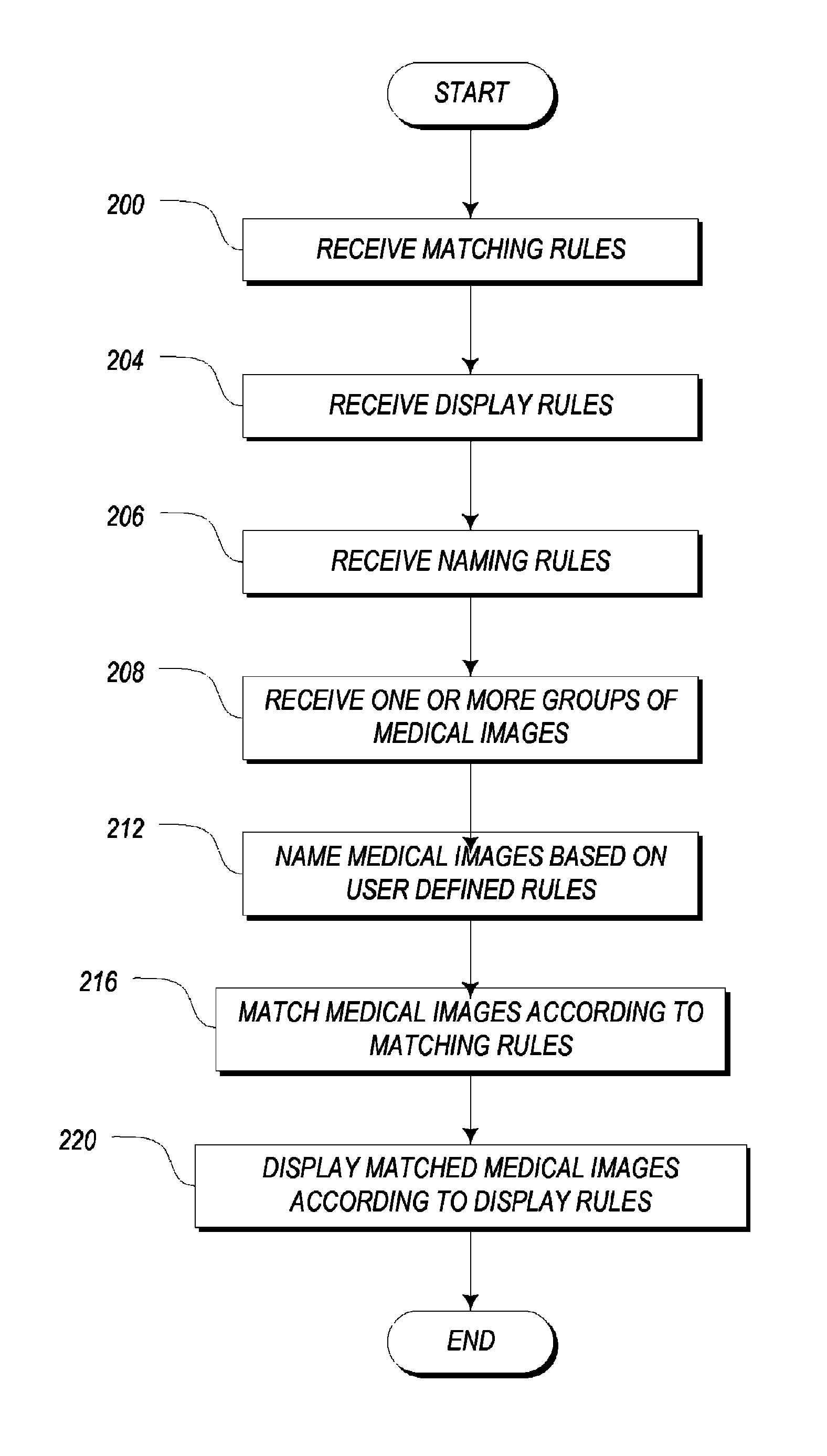
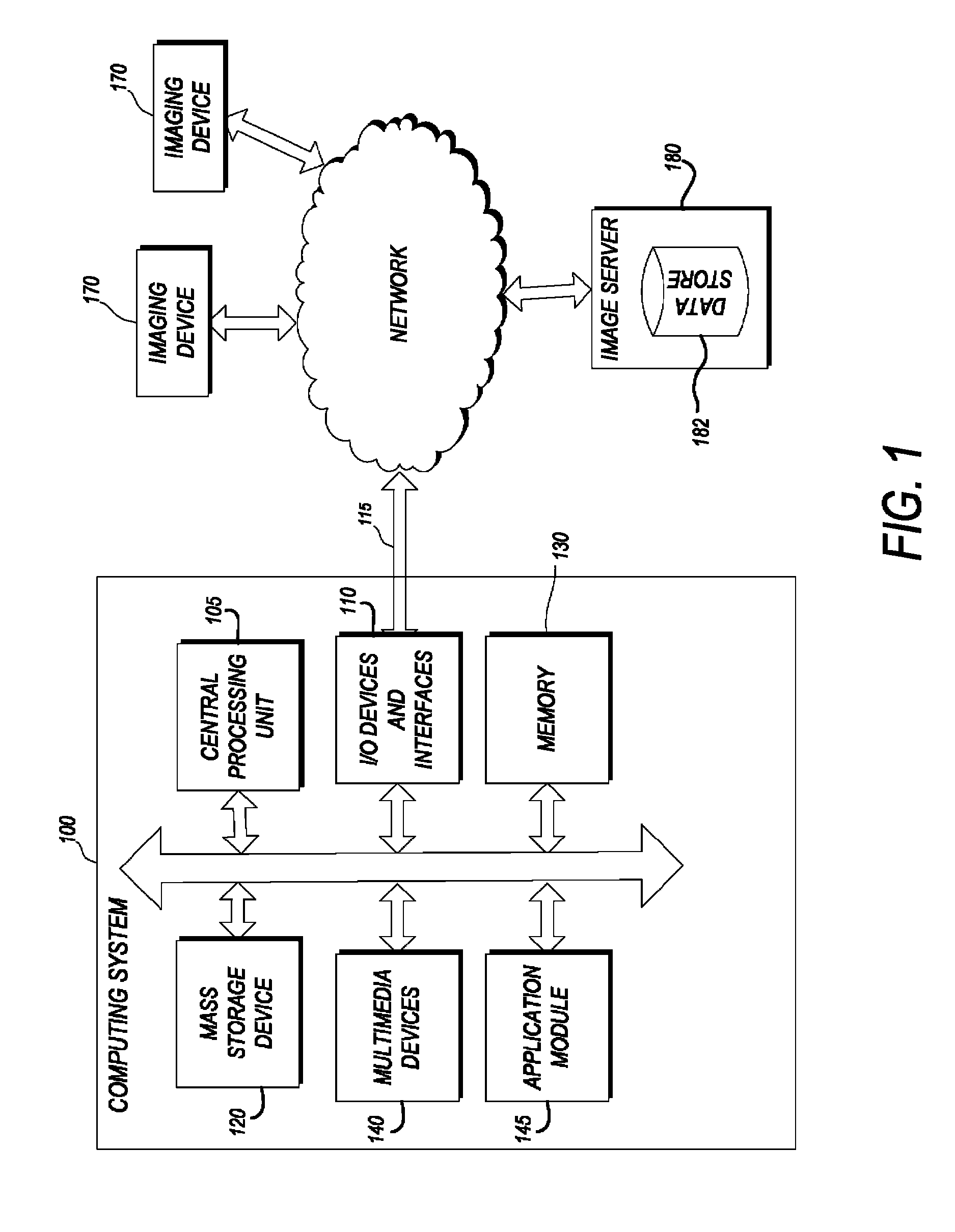
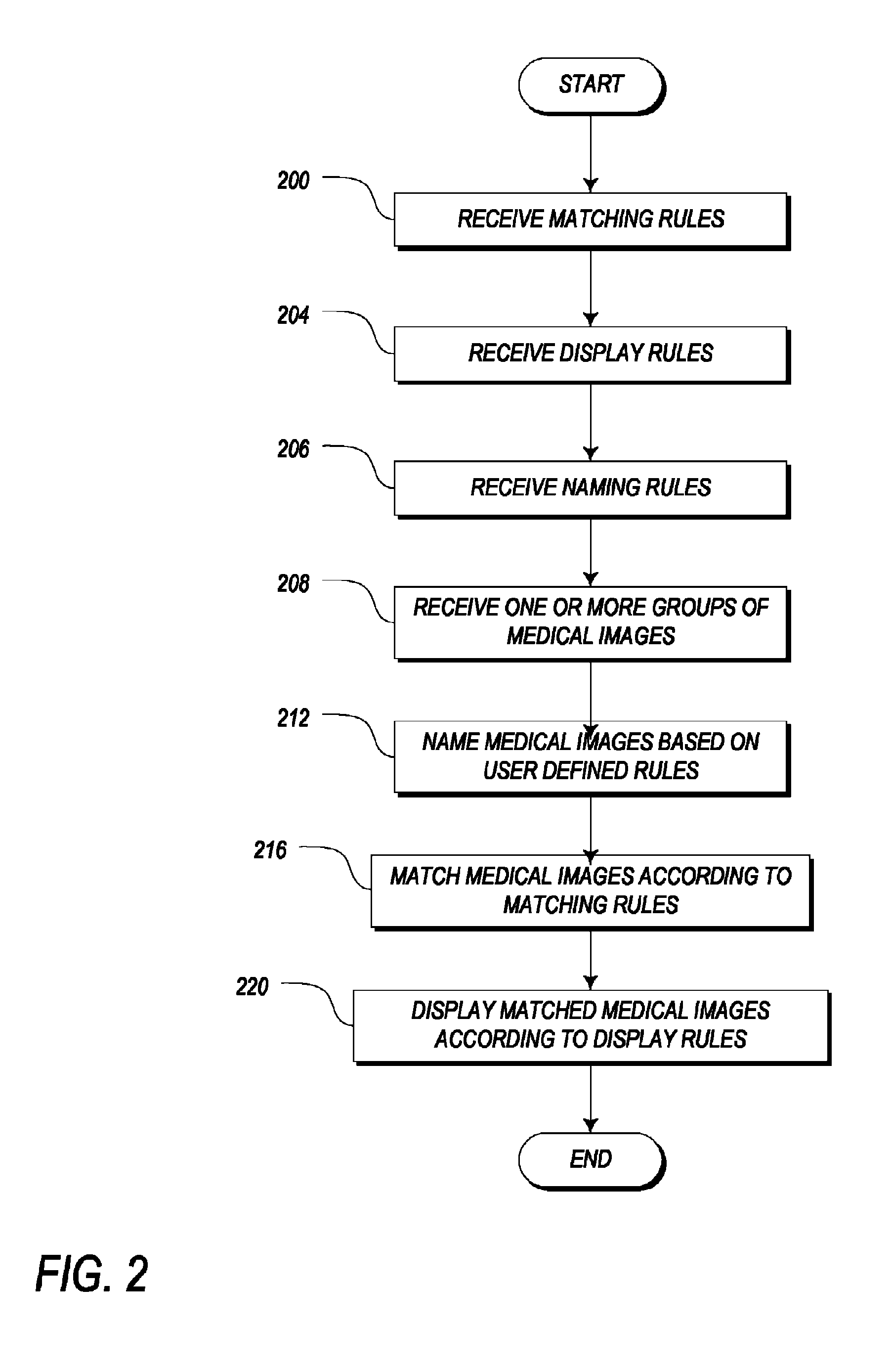
Systems and methods for matching, naming, and displaying medical images
Owner:MERATIVE US LP
Tracking Prefixes of Values Associated with Different Rules to Generate Flows
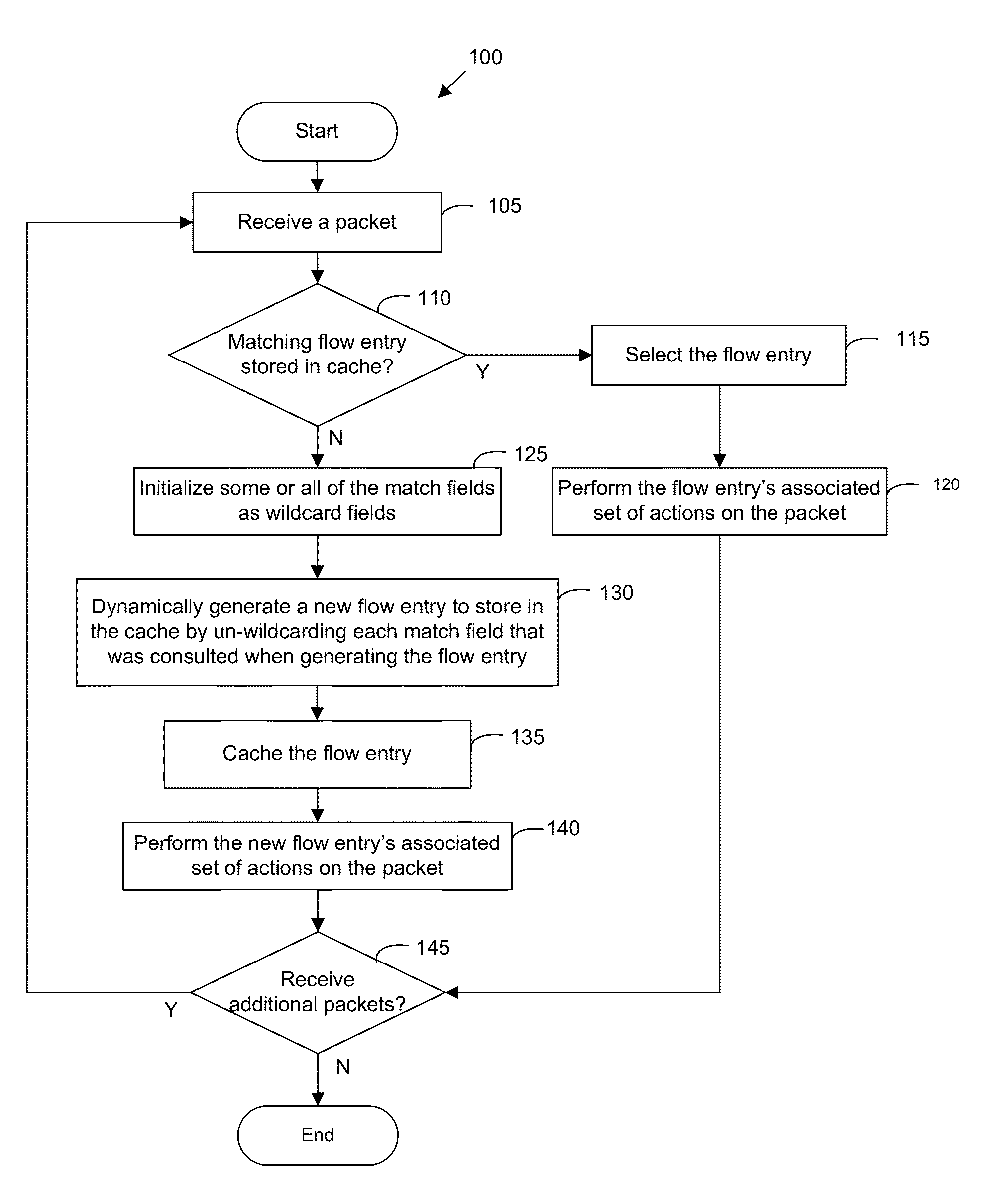
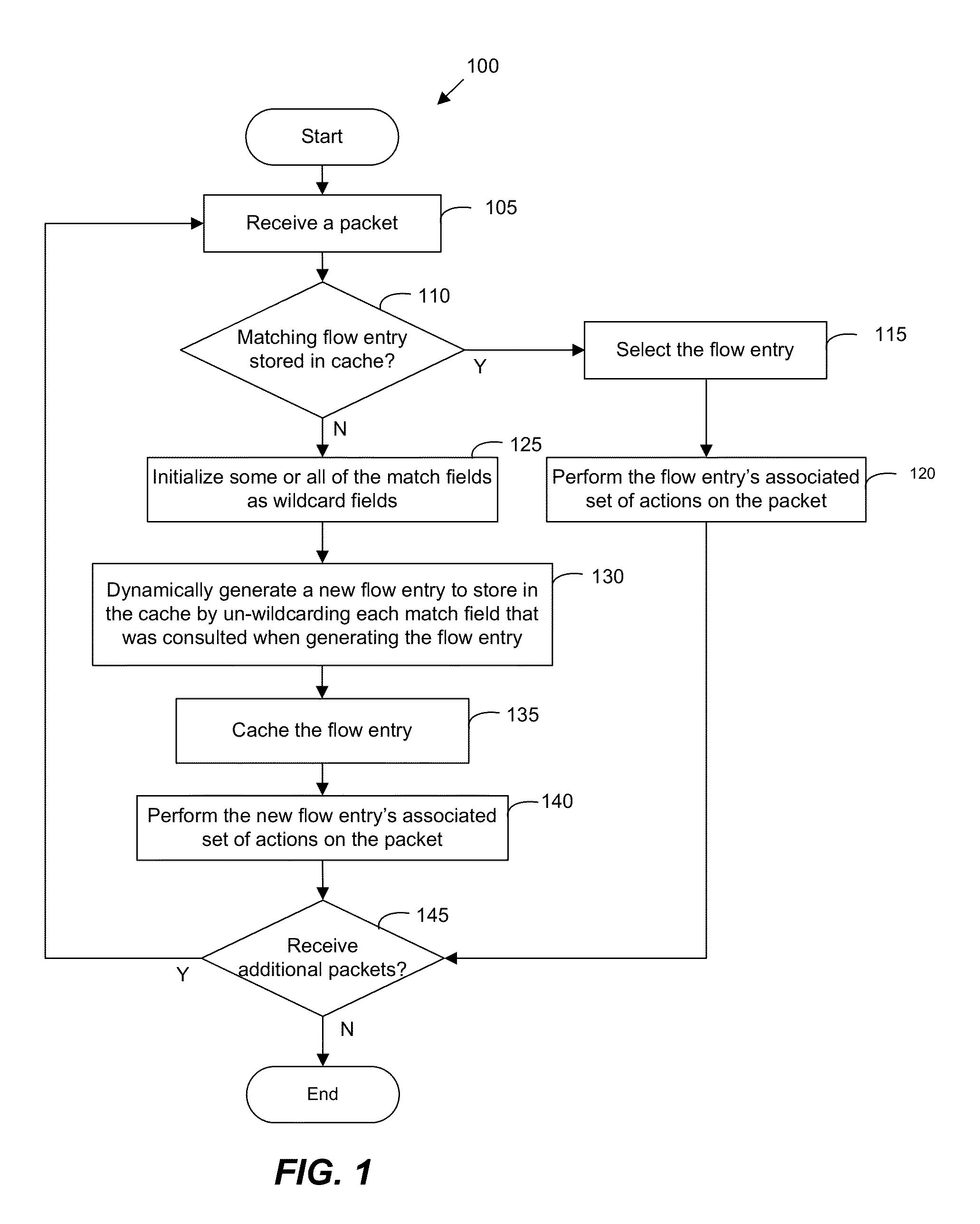
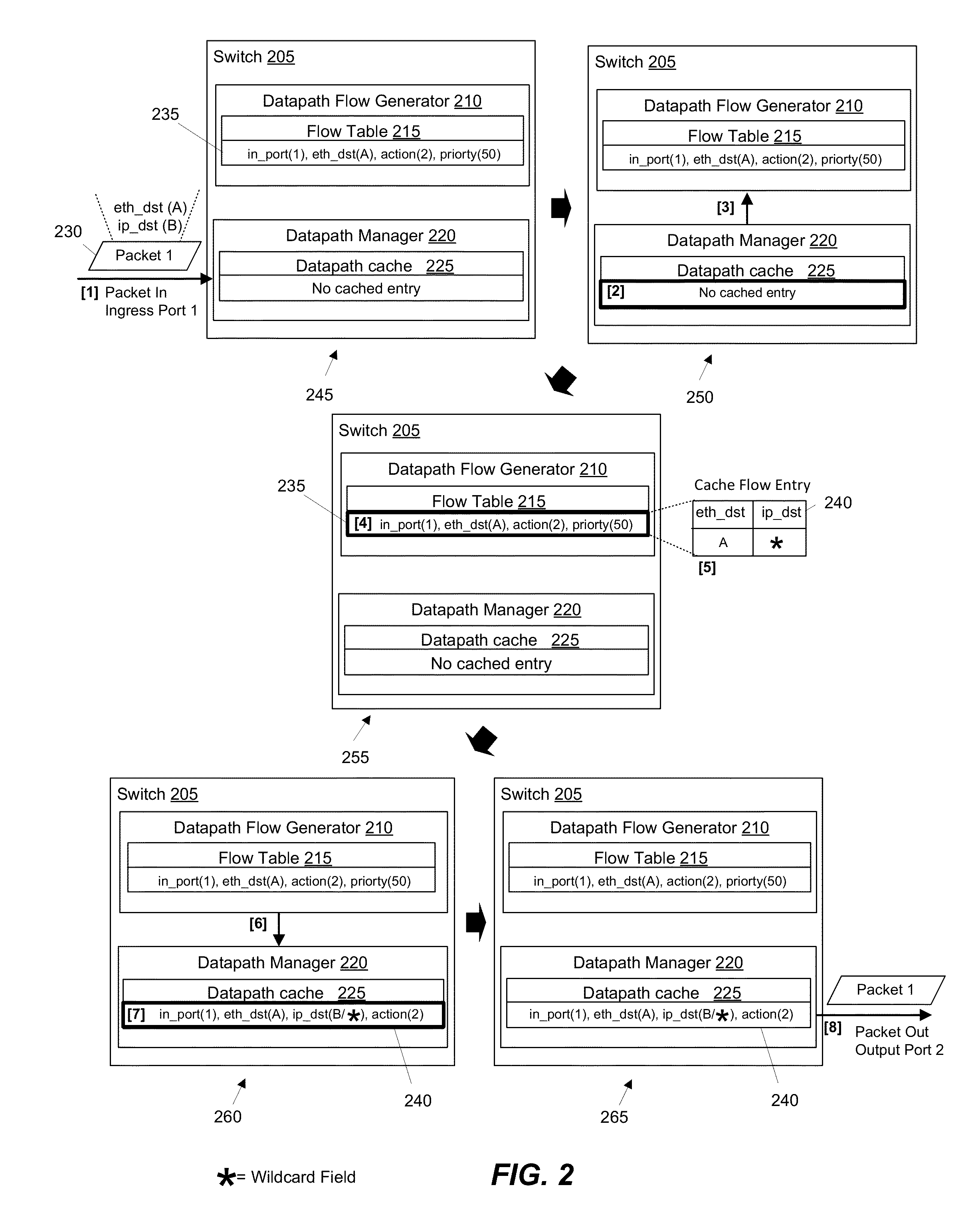
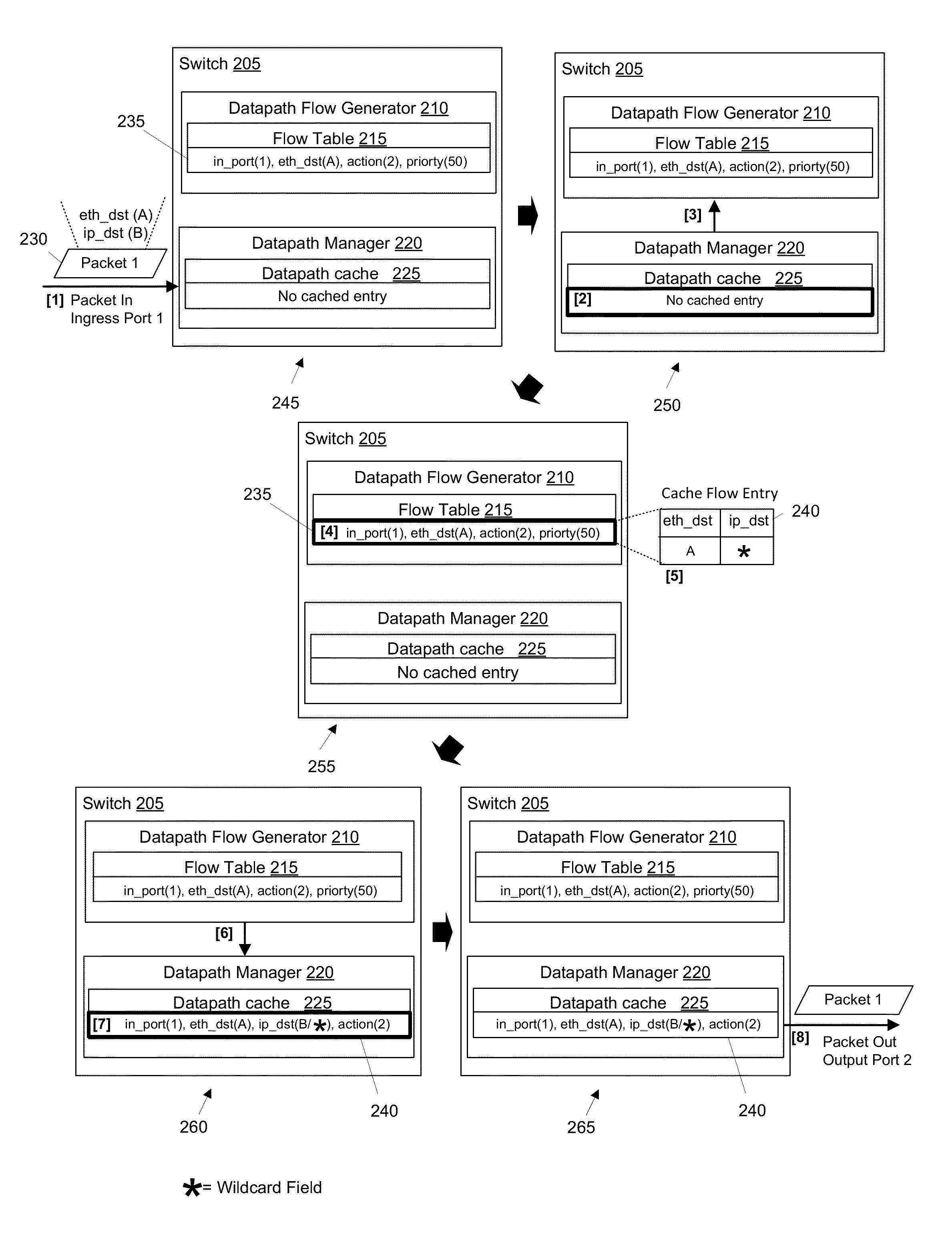
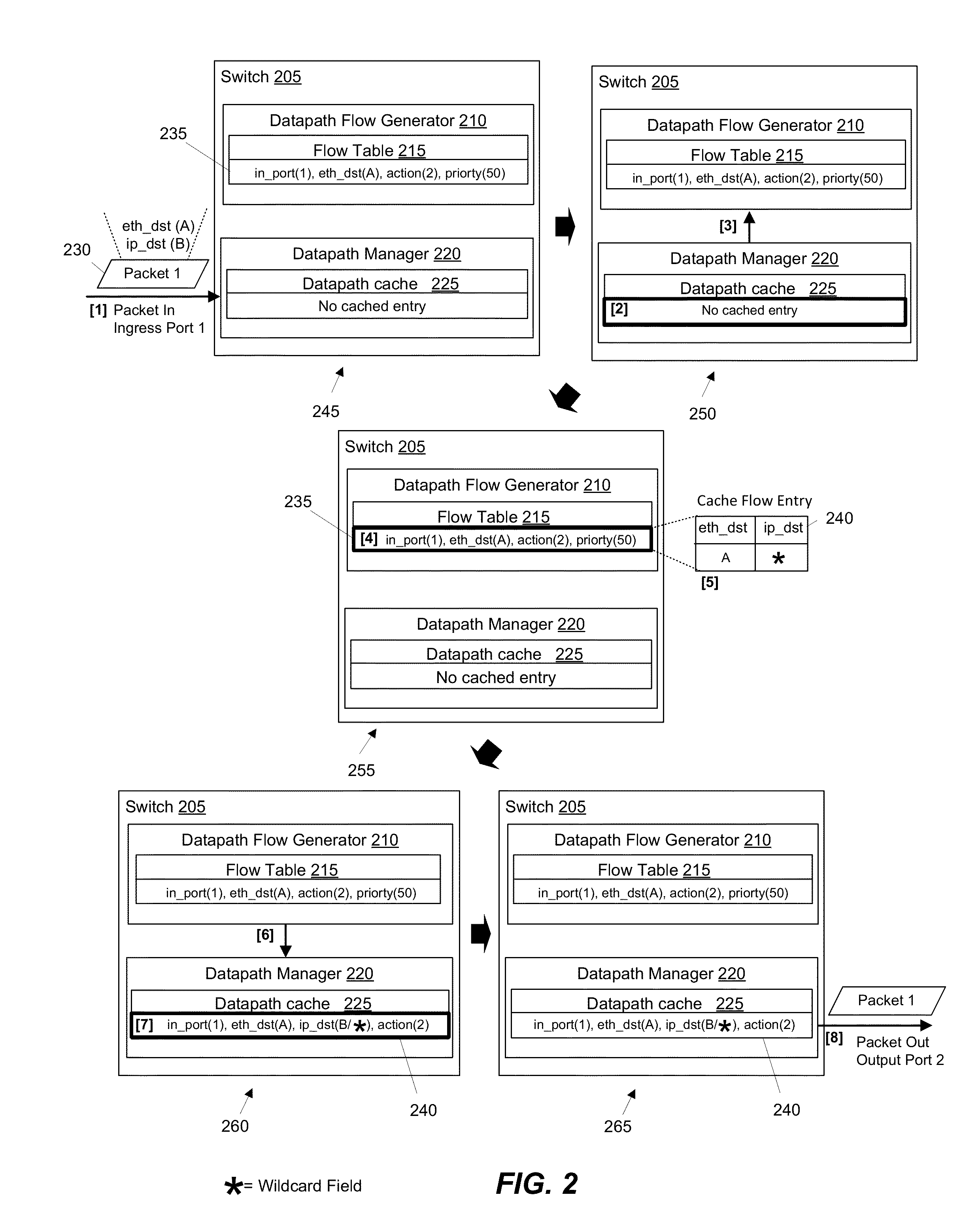
ActiveUS20150078384A1Avoid unnecessarily un-wildcardingData switching by path configurationIp addressNetwork packet
Some embodiments provide a method for a forwarding element that forwards packets. The method receives a packet and consults a tree structure to identity a prefix length associated with an IP address in the packet header. The method skips lookup of each subtable with a set of IP addresses that have a different prefix length than the identified prefix length. The method identifies a matching rule from a particular subtable. The method generates a flow based on the matching rule. The flow is used to process packets that have the same prefix.
Owner:NICIRA
Systems and methods for matching, naming, and displaying medical images
Owner:MERATIVE US LP
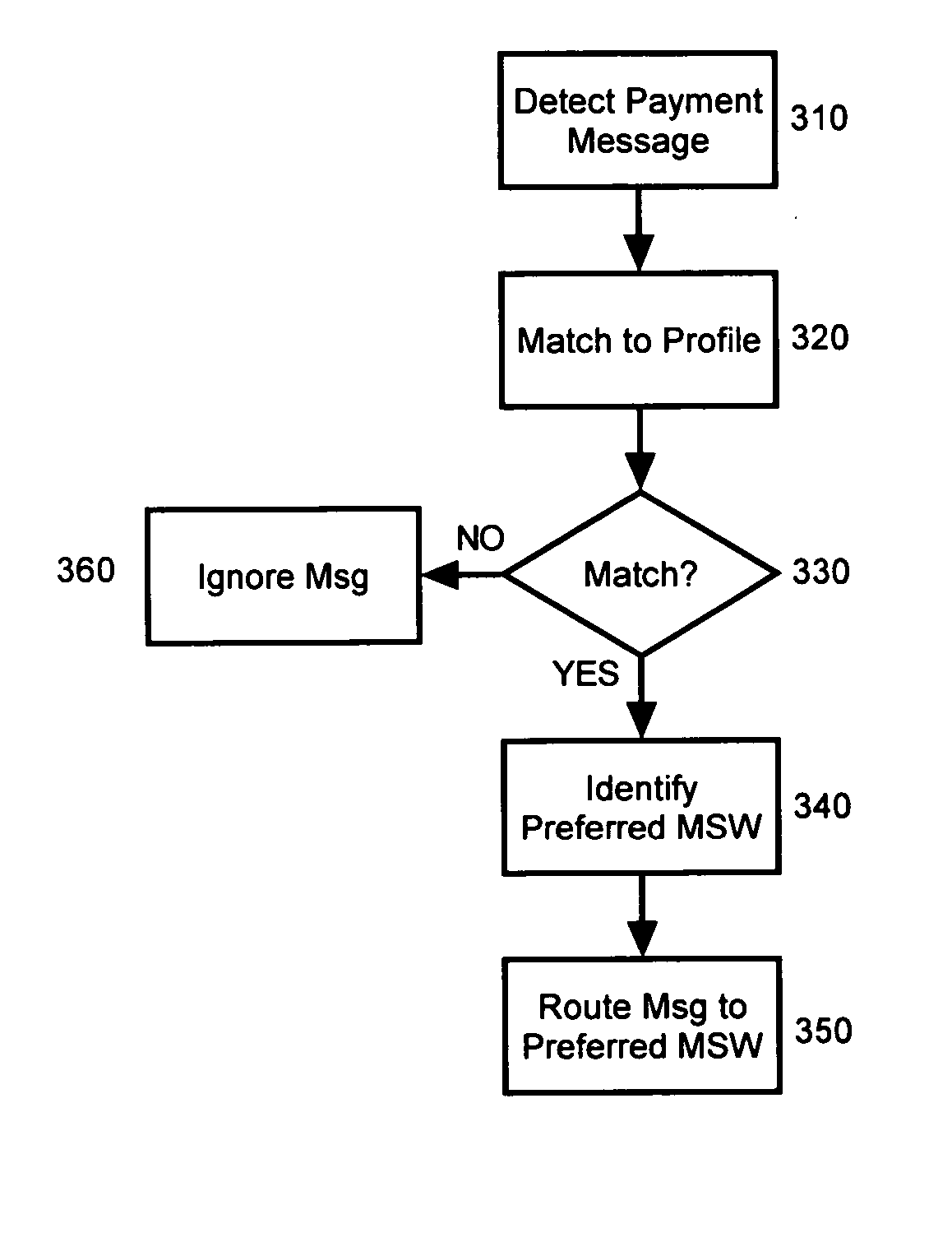
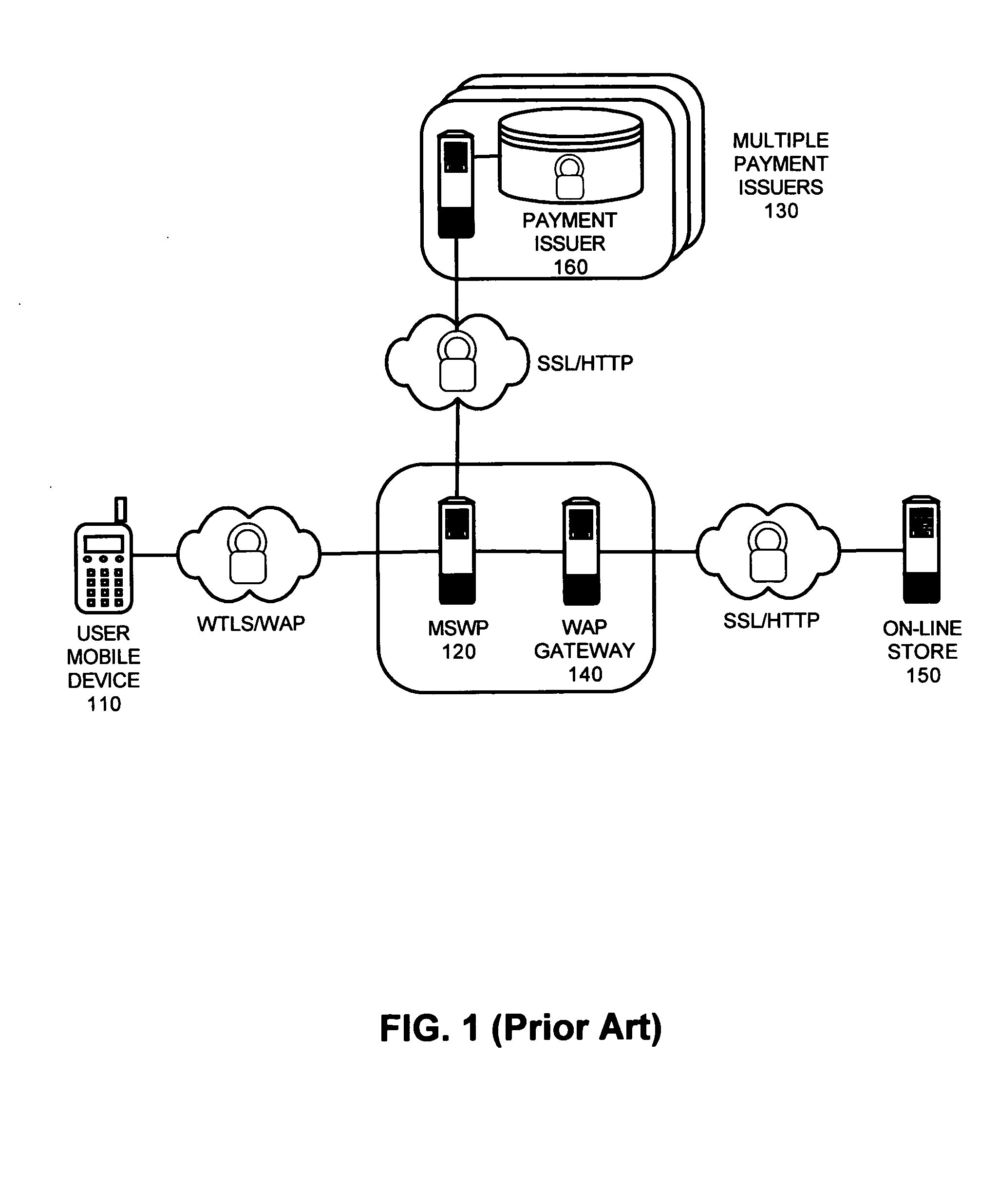
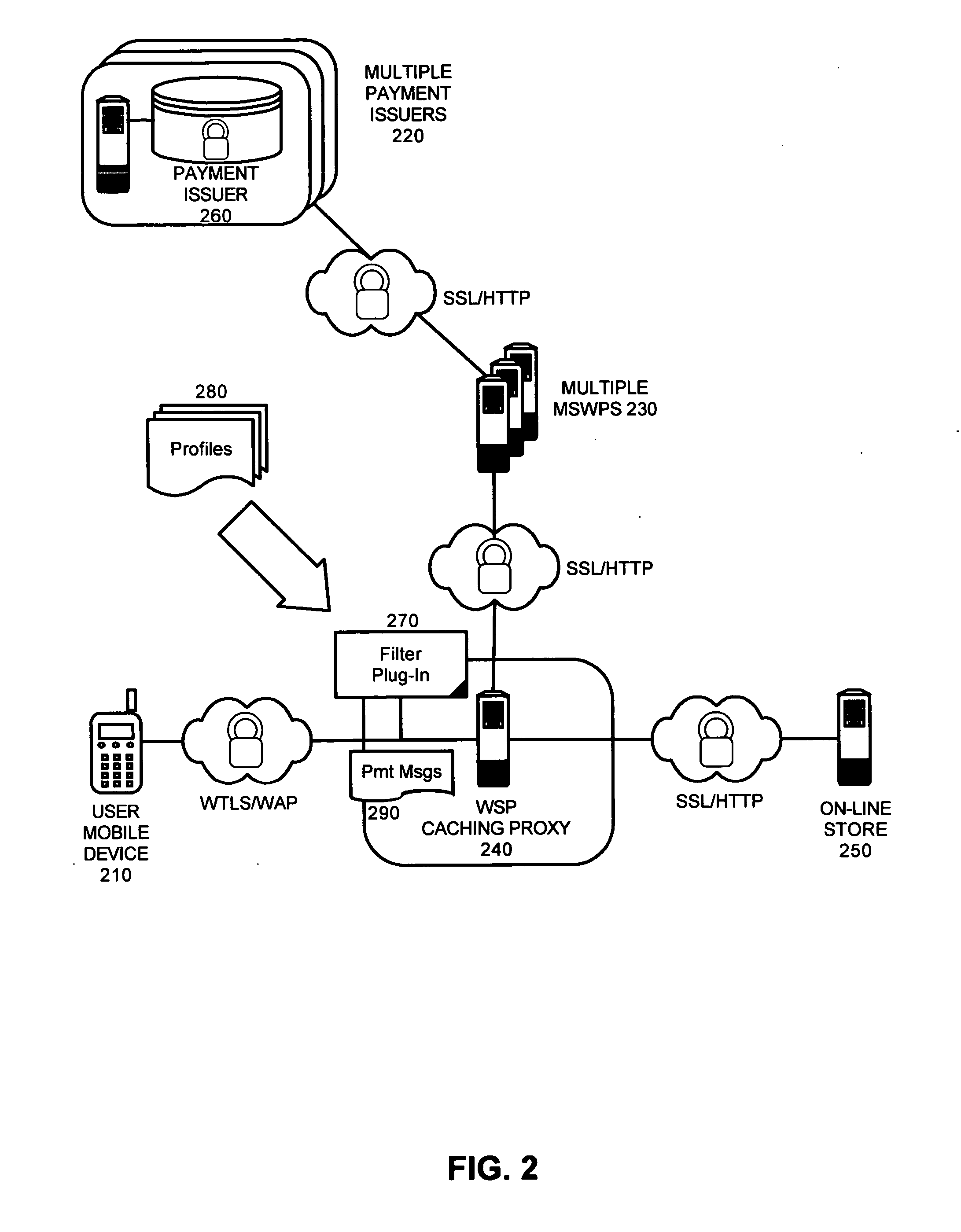
Server wallet provider portal
The present invention is a mobile server wallet provider portal, system, method and apparatus. A MSWP portal can include a configuration for communicative coupling both to a plurality of MSWPs and also to a content proxy. A composite profile generator further can be included which can be configured to combine a plurality of MSWP profiles into a single, composite profile for routing payment messages in the proxy to the MSWP portal. Finally, the MSWP portal can include selection logic configured to process a user selection of one of the MSWPs to process a payment transaction received through the proxy. In a preferred aspect of the invention, the content proxy can be a wireless service proxy (WSP). In this regard, the WSP further can include a filter plug-in configured to route the payment messages to the portal when the payment messages match rules specified within the composite profile.
Owner:IBM CORP
Switching circuit implementing variable string matching
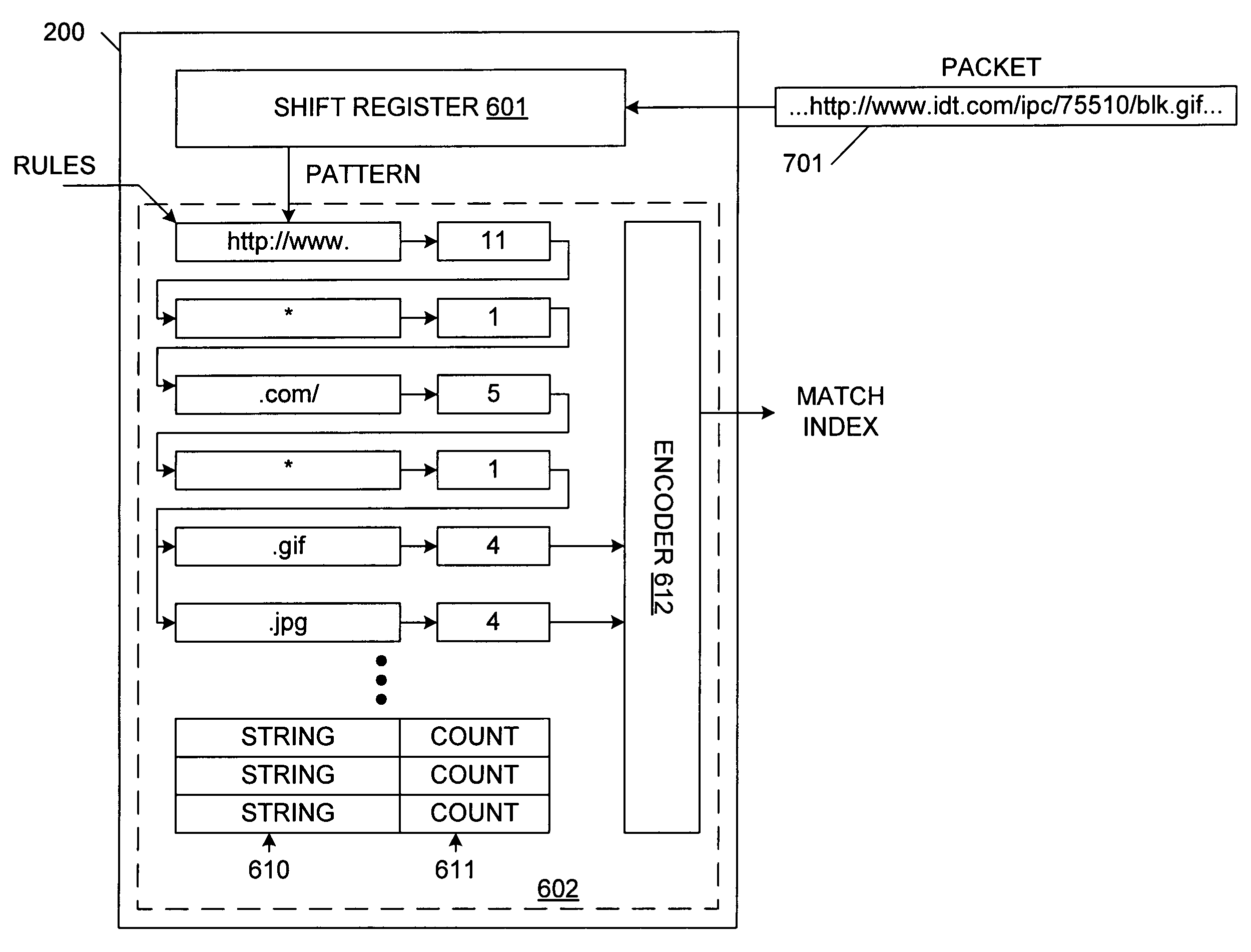
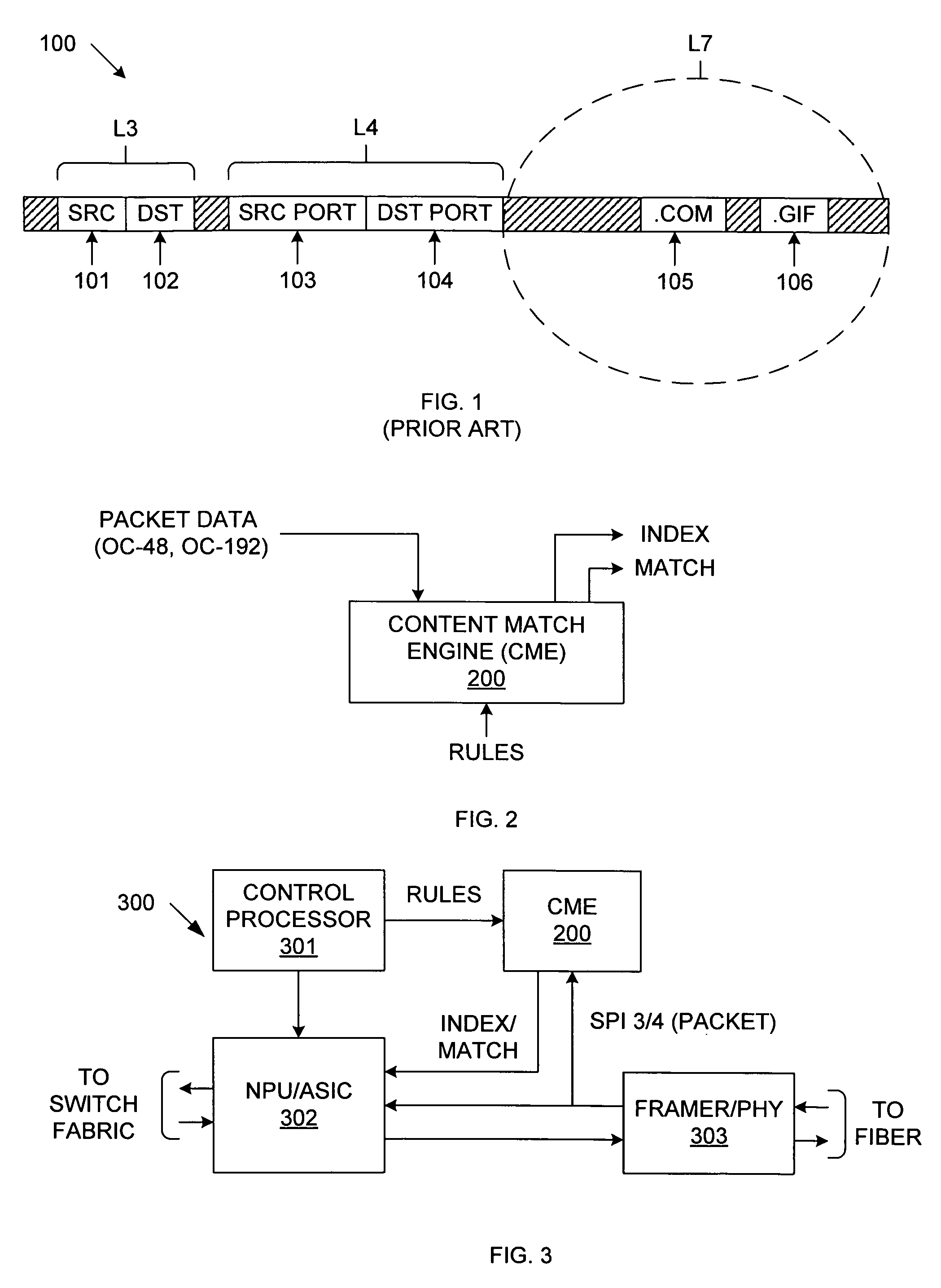
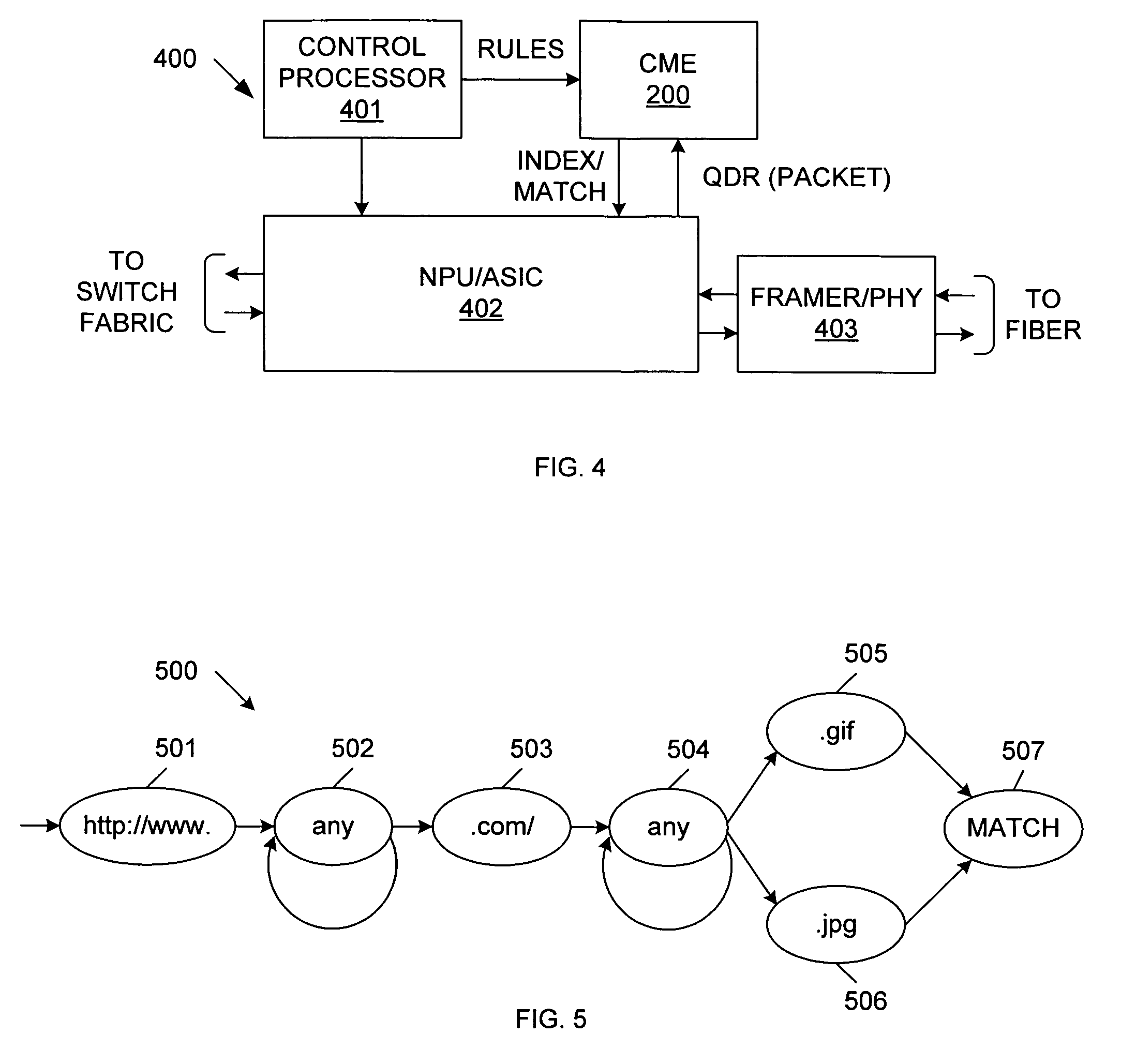
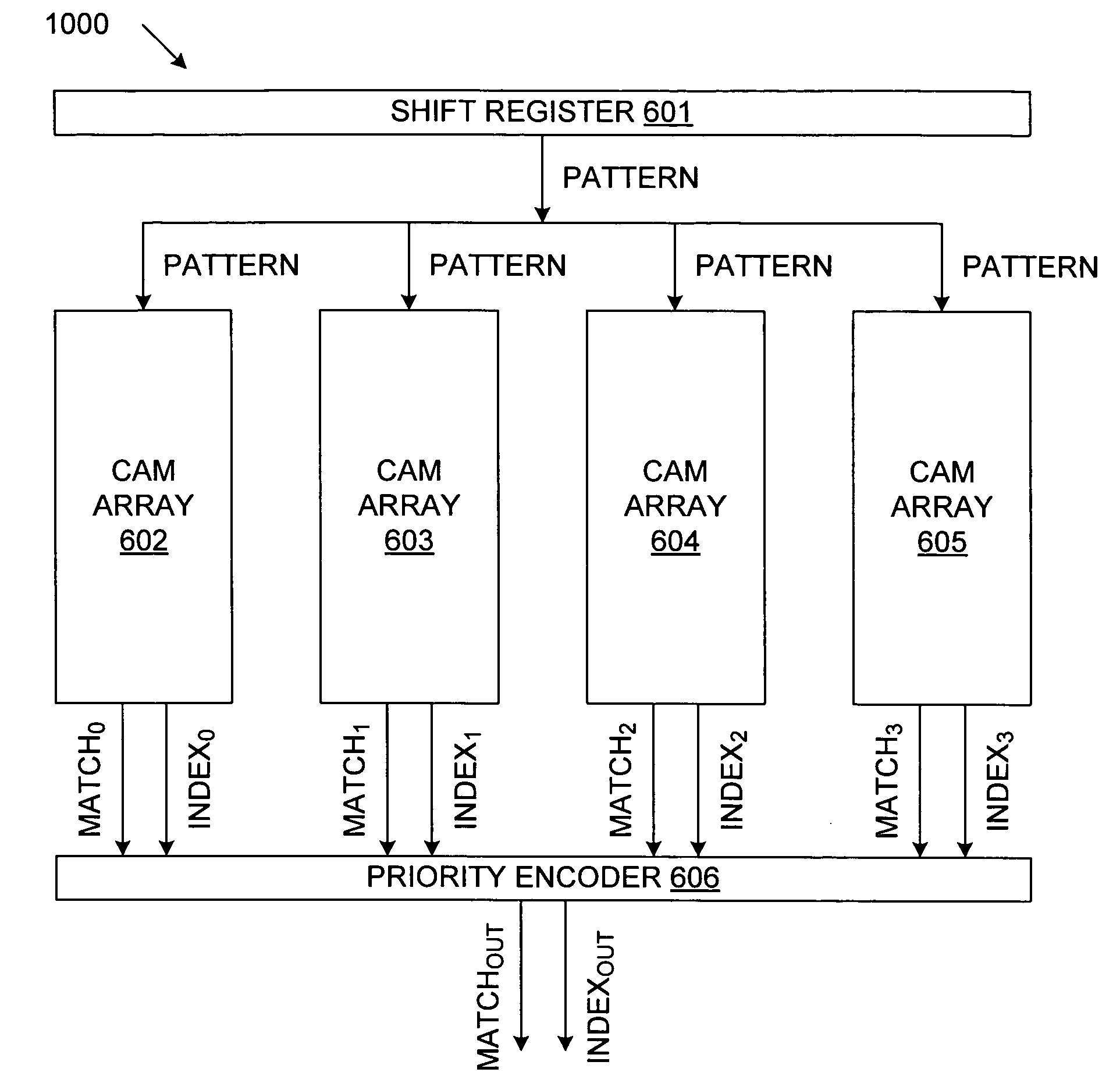
InactiveUS7353332B2Avoid matching problemsShorten the timeMultiple digital computer combinationsDigital storageArray data structureNetwork packet
A content matching engine (CME) uses a content addressable memory (CAM) array that stores a plurality of strings in separate entries. The strings define one or more rules to be matched. The strings of each rule are linked, thereby providing a required order. The strings of each rule can be linked by per-entry counters associated with each string, or by a state machine. The strings in the CAM array are compared with a packet, which is shifted one symbol at a time (because the strings can start on any boundary). When the CAM detects a match, the CAM skips over the string that resulted in the match, thereby preventing erroneous matches. The CAM allows parallel matching to be performed for multiple rules. If the contents of a packet match all of the strings of a rule, in order, then the CME asserts a match / index signal that identifies the matched rule.
Owner:AVAGO TECH INT SALES PTE LTD
Mapping processing system and method for solving problem of standard code control of medical data
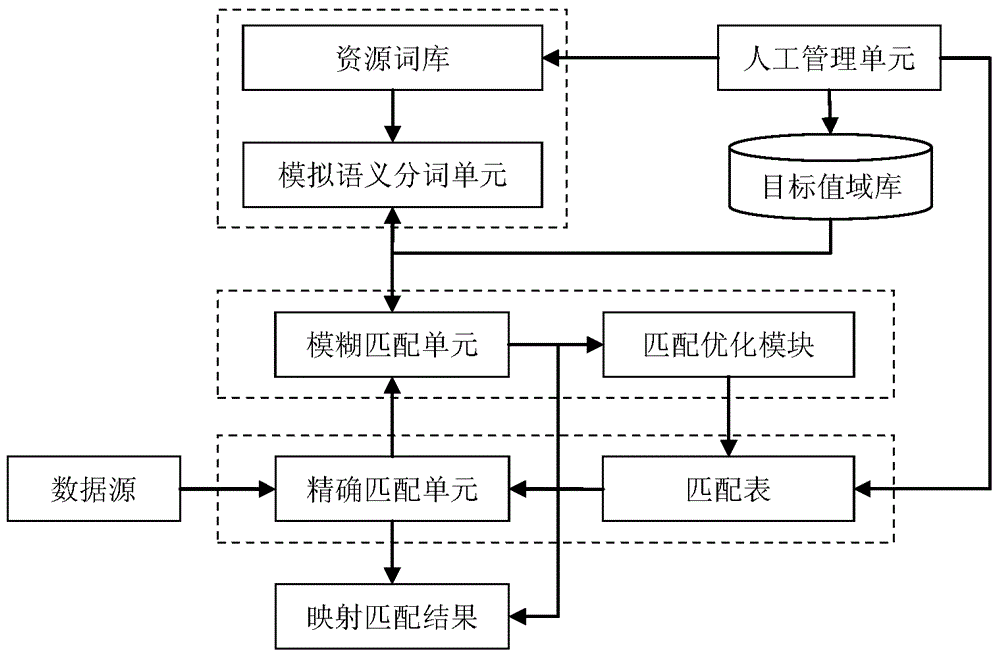
InactiveCN104156415ASolve coding standardization problemsImprove accuracySemantic analysisSpecial data processing applicationsManagement unitSemantics
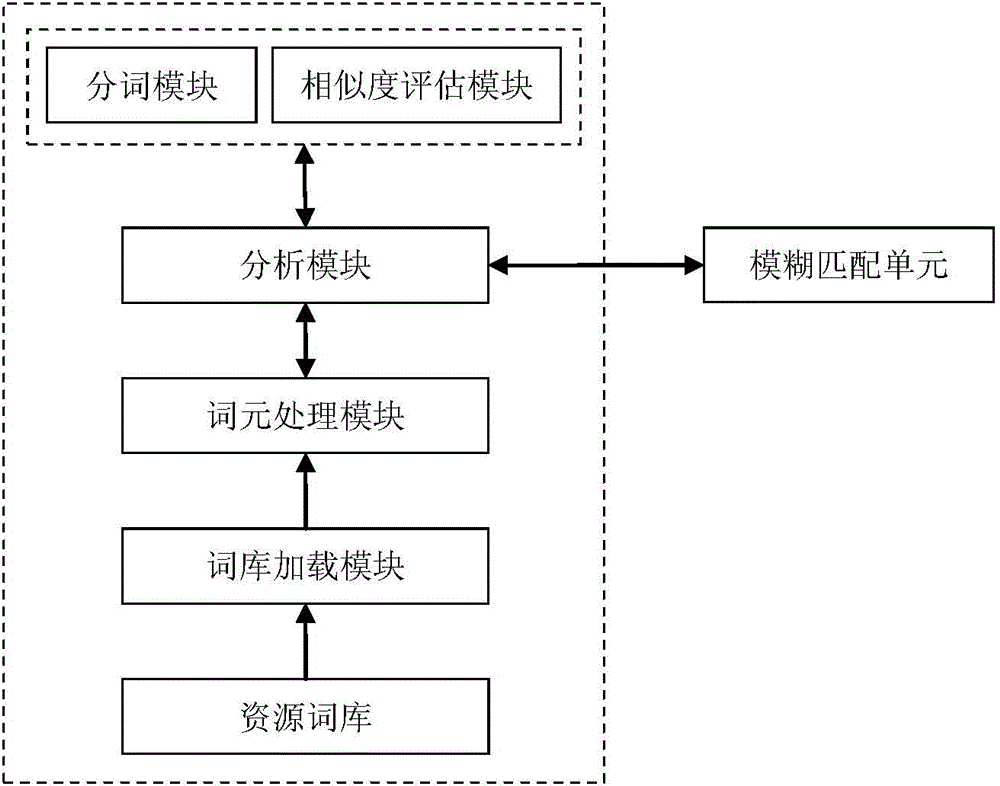
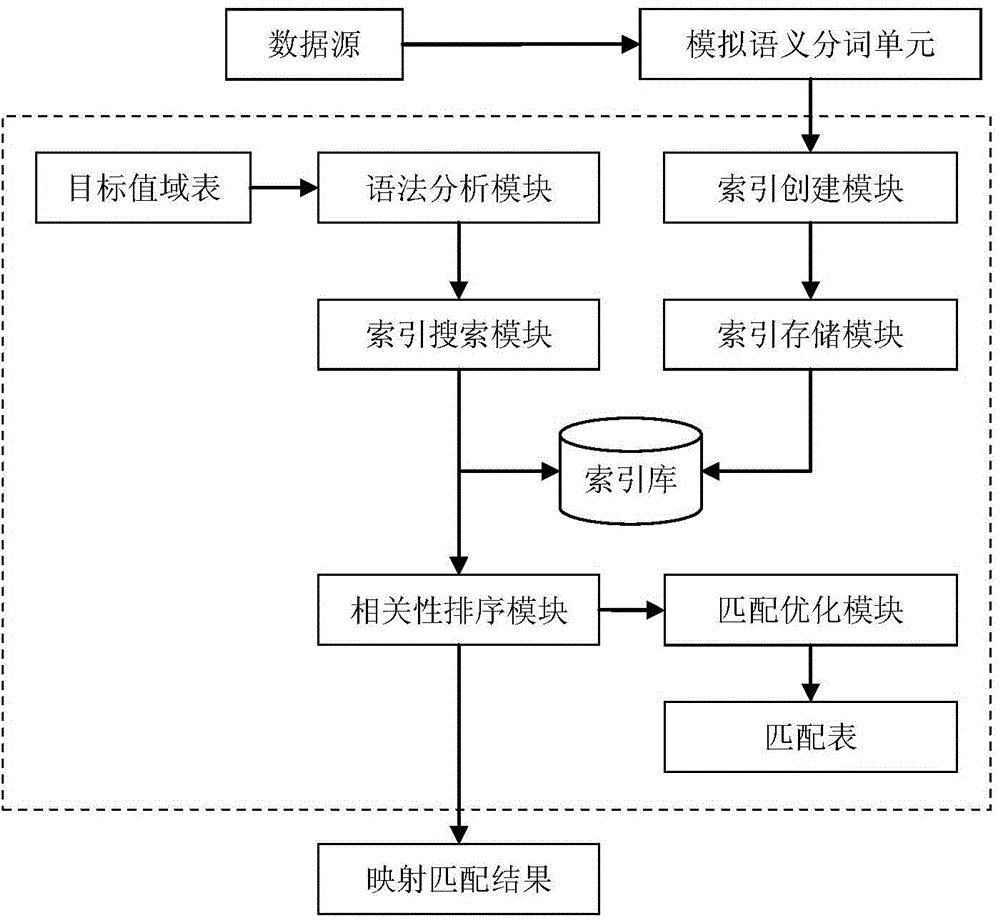
The invention provides a mapping processing system and method for solving a problem of standard code control of medical data. The mapping processing system comprises a resource word bank, a target value range bank, a simulation semantic word segmentation unit, a fuzzy matching unit, an accurate matching unit, a matching table and a labor management unit. The mapping processing method includes steps of acquiring data from the medical data, mapping the acquired data in an accurate match manner according to standard codes stored in the target value range bank or mapping matching rule information stored in the matching table; analyzing fuzzy semantics of the data acquired from a data source; subjecting simulation semantic word segmentation results to fuzzy matching to generate a mapping matching result; mapping the medical data into the standard codes according to the mapping matching rule information in the matching table and generating a medical data mapping processing result. The mapping processing system and method build an automatic mapping matching process, and high accuracy and matching accuracy of the mapping matching results are achieved by combination of fuzzy matching, labor check, mechanical training and the like.
Owner:SHENYANG REALESOFT TECH
Systems and methods for matching, naming, and displaying medical images
Owner:MERATIVE US LP
Switching circuit implementing variable string matching
InactiveUS20070083646A1Preventing subsequent erroneous matchReduce processing timeDigital storageMultiple digital computer combinationsData packTheoretical computer science
A content matching engine (CME) uses a content addressable memory (CAM) array that stores a plurality of strings in separate entries. The strings define one or more rules to be matched. The strings of each rule are linked, thereby providing a required order. The strings of each rule can be linked by per-entry counters associated with each string, or by a state machine. The strings in the CAM array are compared with a packet, which is shifted one symbol at a time (because the strings can start on any boundary). When the CAM detects a match, the CAM skips over the string that resulted in the match, thereby preventing erroneous matches. The CAM allows parallel matching to be performed for multiple rules. If the contents of a packet match all of the strings of a rule, in order, then the CME asserts a match / index signal that identifies the matched rule.
Owner:AVAGO TECH INT SALES PTE LTD
Tracking Prefixes of Values Associated with Different Rules to Generate Flows
ActiveUS20150092778A1Avoid unnecessarily un-wildcardingData switching by path configurationMatch ruleData mining
Some embodiments provide a method for a forwarding element that forwards packets. The method receives a packet. The method consults a tree structure to generate a wildcard mask. The consulting includes traversing the tree structure by tracing a set of bits from the packet header and un-wildcarding the corresponding set of bits from the wildcard mask. The method identifies a matching rule for the packet. The method generates a flow based on the matching rule and the wildcard mask. The flow is used to process each other packet that matches each un-wildcarded bit of the flow.
Owner:NICIRA
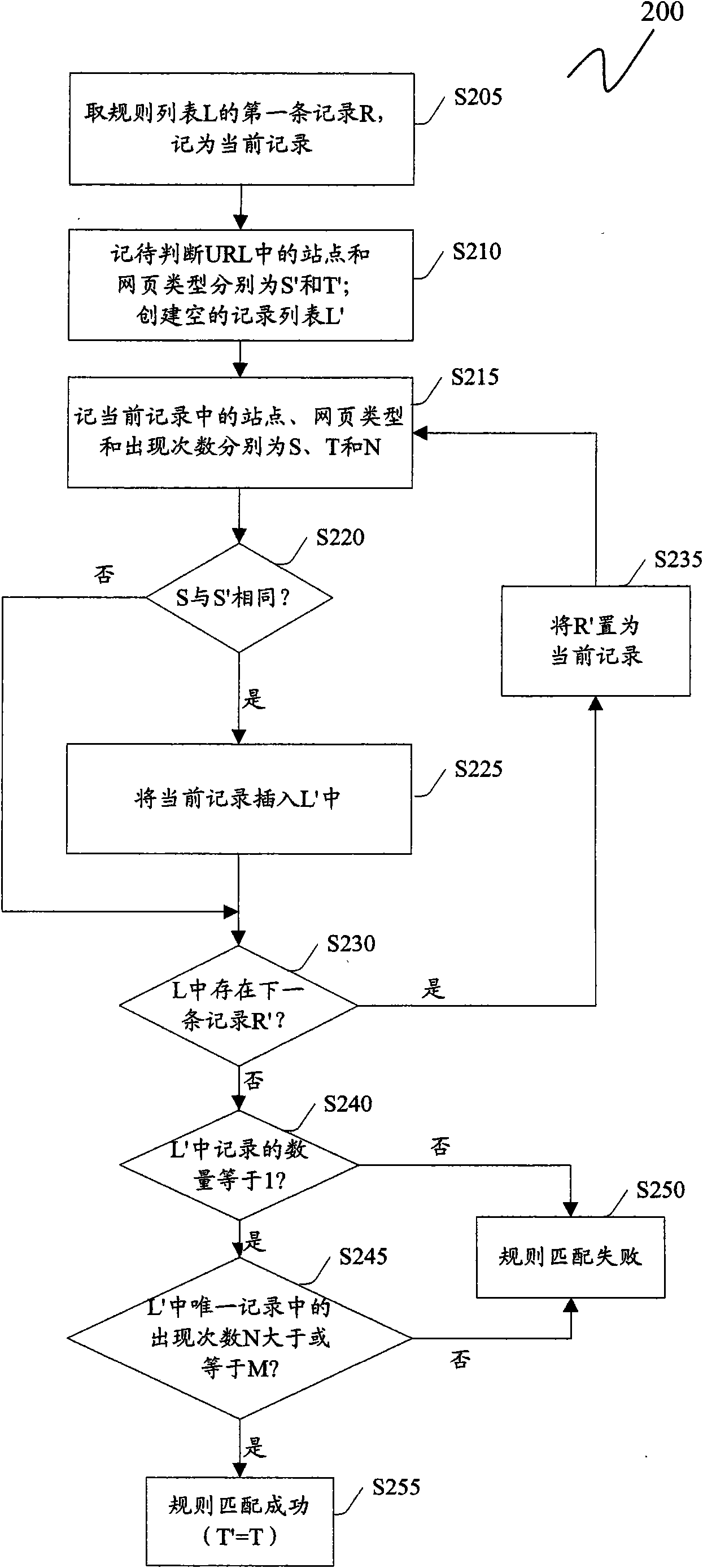
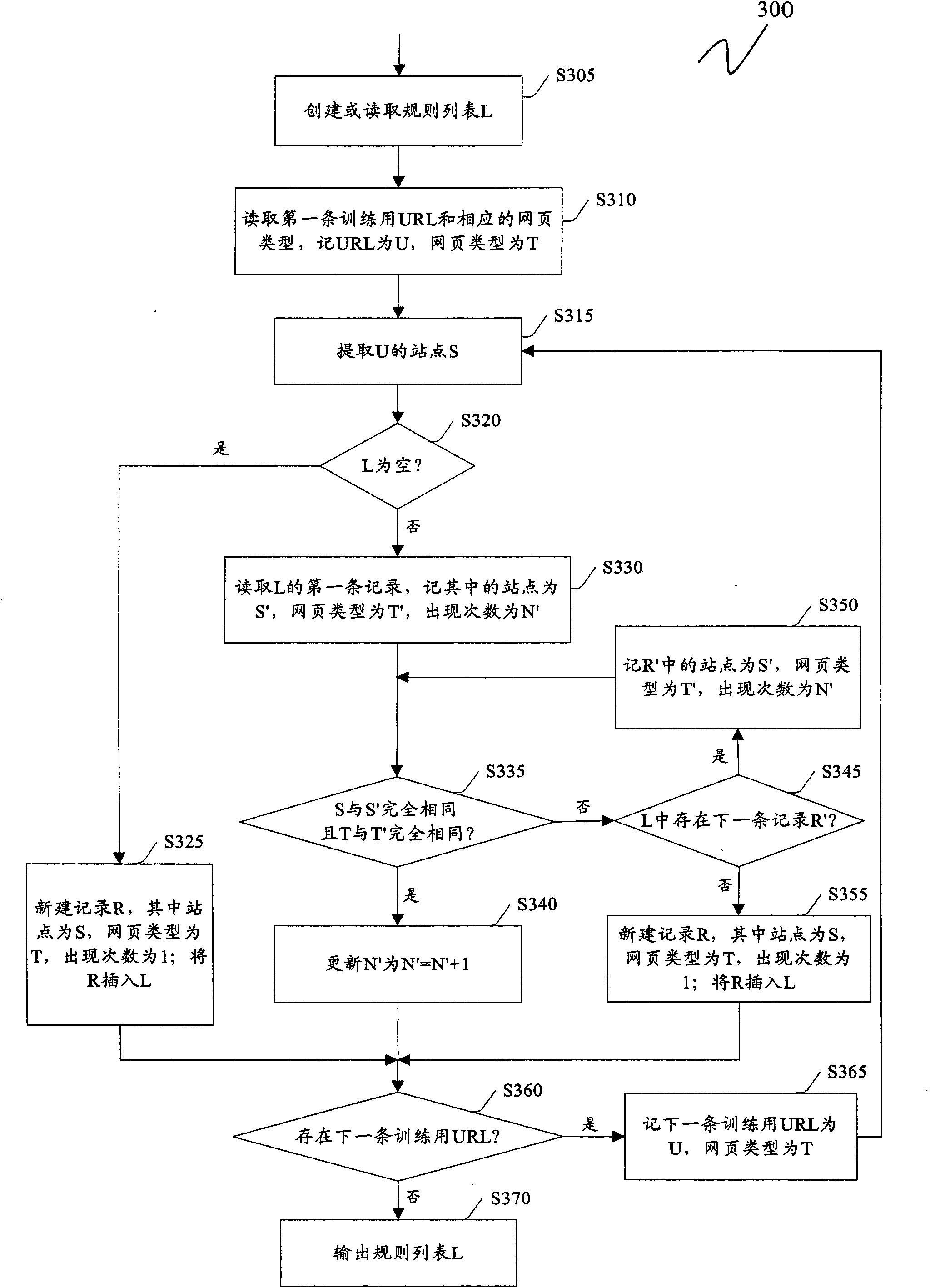
Method and device for judging type of webpage
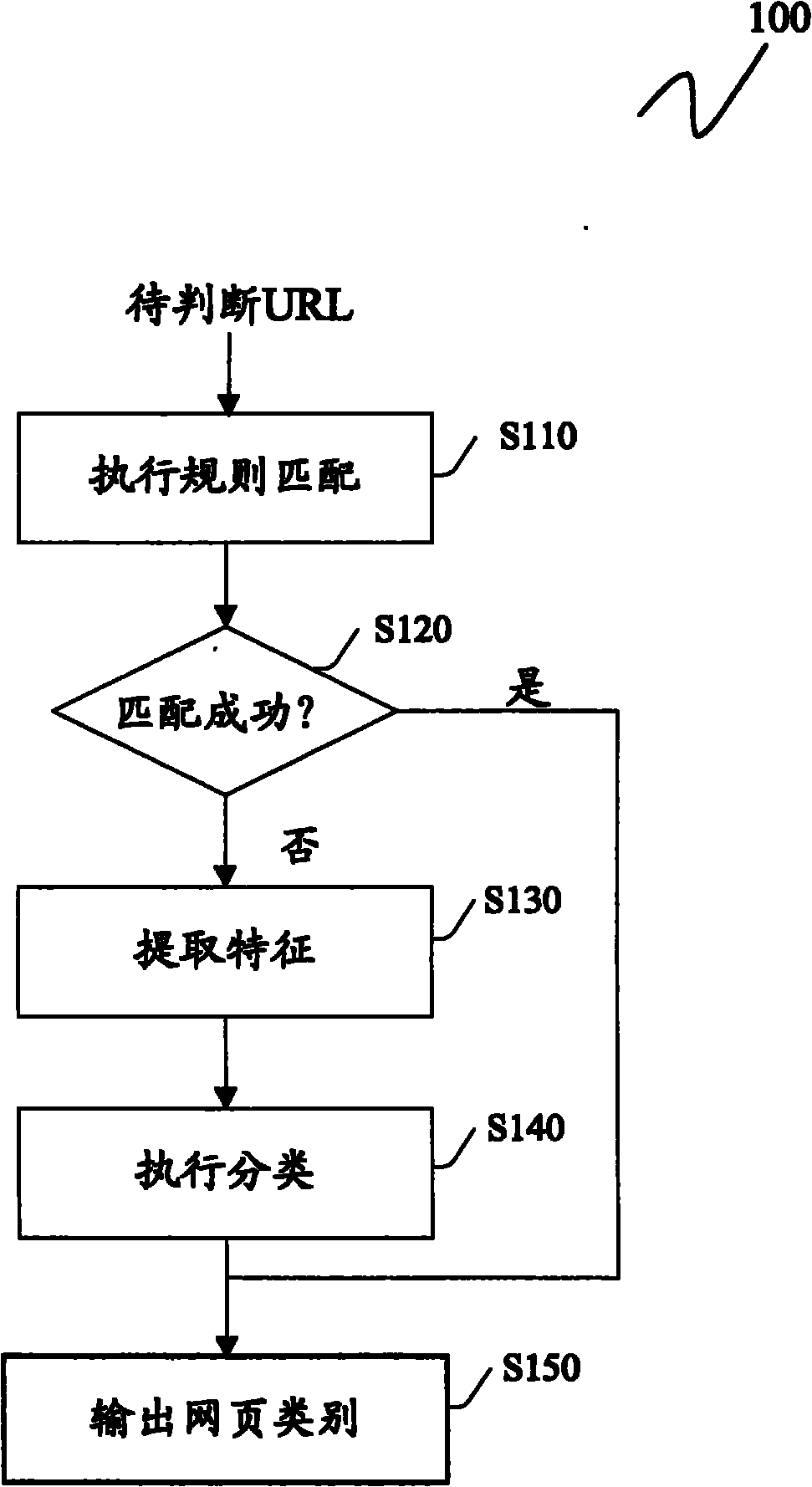
InactiveCN101872347ARealize judgmentCharacter and pattern recognitionSpecial data processing applicationsFeature vectorMatch rule
The invention discloses a method and a device for judging the type of a webpage. The method comprises the following steps: carrying out rule matching in a prestored rule table on the basis of the URL of a webpage to be judged, wherein the rule list comprises a plurality of rule records for judging the type of the webpage; if the rule matching is successful, obtaining the type of the webpage to be judged according to the successfully matched rules; if the rule matching is unsuccessful, extracting predetermined features from the URL and / or HTML source codes of the webpage to be judged, and utilizing a classifier to classify the type of the webpage to be judged so as to obtain the type of the webpage to be judged on the basis of a feature vector composed of features selected from the extracted predetermined features. In the scheme of the invention, the invention can combines the advantages of a rule recognition scheme and a recognition scheme based on statistical learning, and can realize to judge the types of various webpage such as blogs, forums, news and the like.
Owner:FUJITSU LTD
Automated discovery of a topology of a distributed computing environment
ActiveUS20100030893A1Digital computer detailsProgram controlLinkage conceptDistributed Computing Environment
Owner:IBM CORP
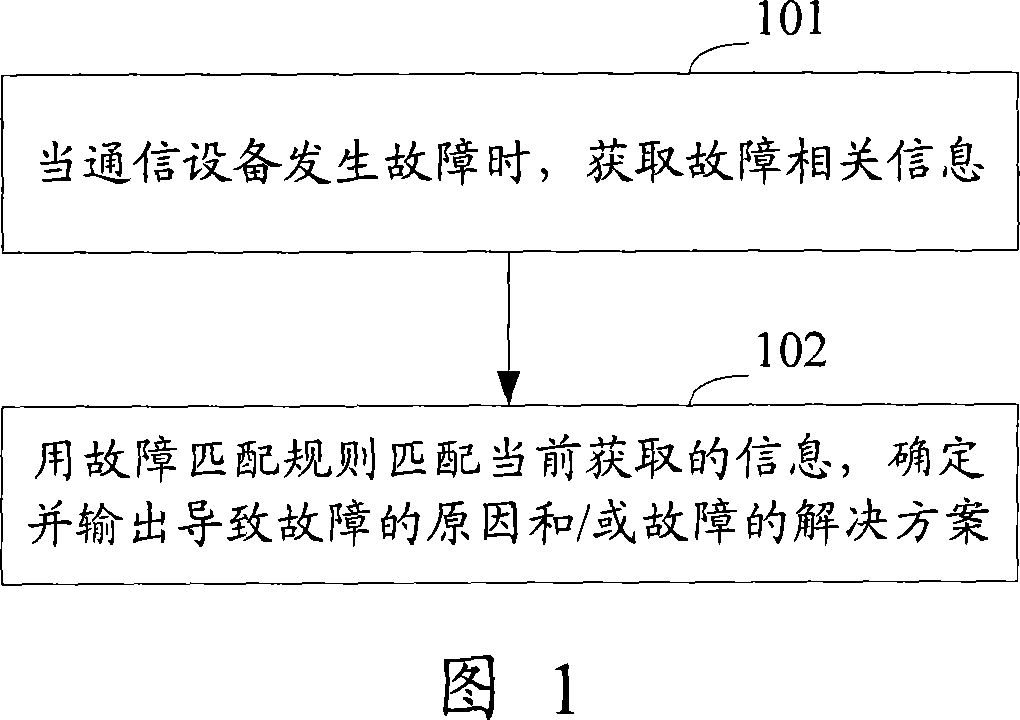
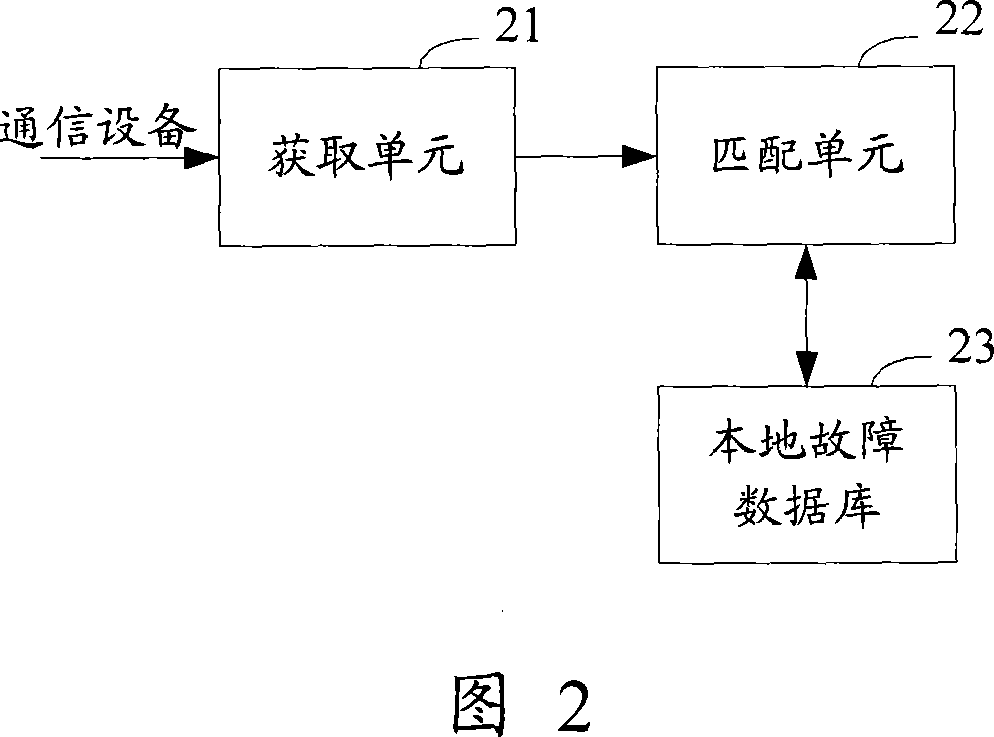
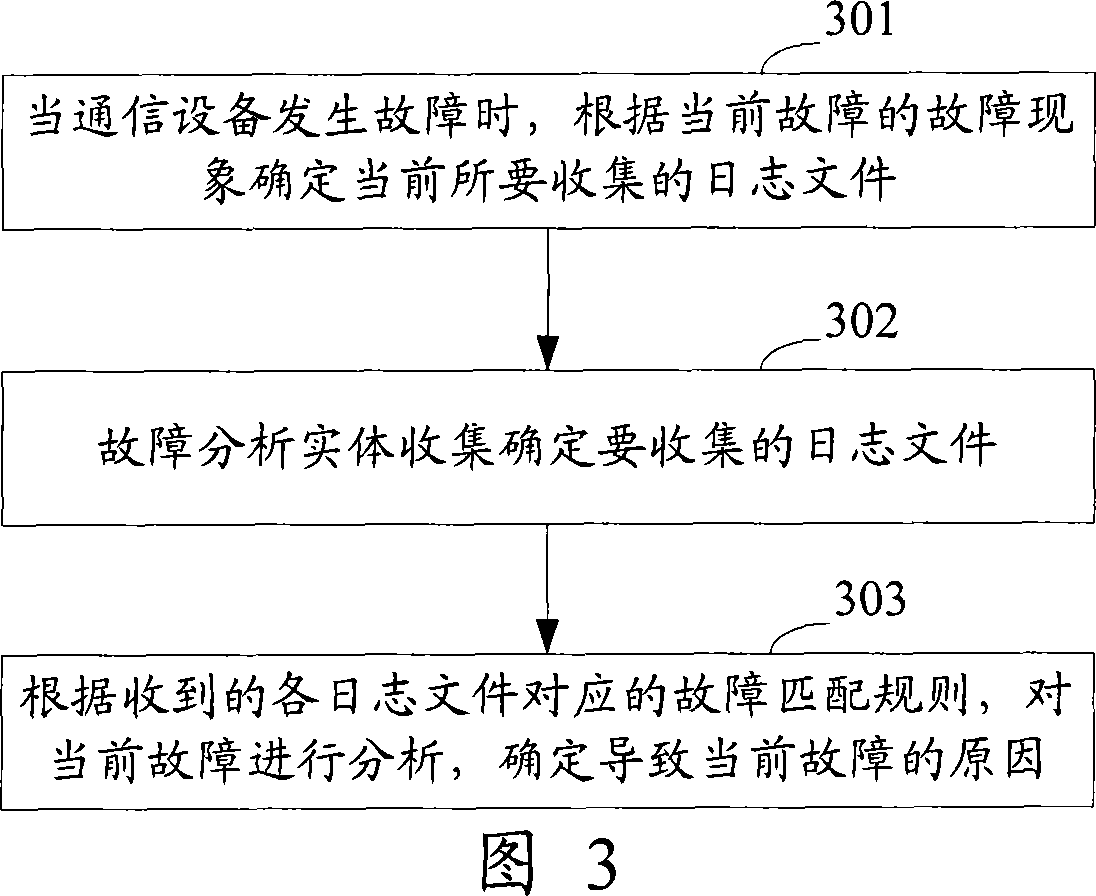
A fault analyzing method and device for communication equipment
InactiveCN101060436AImprove the efficiency of analyzing failuresAccelerates the determination of the cause of failuresData switching networksSpecial data processing applicationsRelevant informationFault analysis
The disclosed fault analysis method for communication device comprises: pre-setting and storing the fault match rule; when the device fails, obtaining fault message; using the match rule matching current message to determine the fault reason and / or solution scheme. This invention improves fault analysis efficiency, and quickens the process speed.
Owner:NEW H3C TECH CO LTD
Systems and methods to facilitate selling of products and services
InactiveUS20050044008A1Improve efficiencyAdd categoryCustomer relationshipBuying/selling/leasing transactionsWeb siteVoice over IP
The system of the present invention provides systems and methods for selling goods and services on, over, through, and in conjunction with the Internet. The system receives session (clickstream) information on a customer's website session from the enterprise's website and may also receive customer information on the customer from the enterprise's CRM or eCRM system. The session information referred to comprises the goods or services the customer is searching and metadata about such search and the relevant products, such as the surfing pattern itself. The system determines from the received information, based on the interaction between matching rules created using the system by the enterprise and the system's matching engine, whether the customer is a candidate for assistance from a sales associate. The system creates and indexes information on available sales associates and their performance, selling capabilities and product expertise. The system further matches the customer with at least one sales associate, ideally the most appropriate sales associate, based on the customer, session, and sales profile associate information, and facilitates communication between the sales associate and the customer. Additionally, the system provides information on the customer, products or services the customer is interested in, and the collateral sales materials (both internal and external to the enterprise) and selling techniques to the sales associate based on the particular sales opportunity. The system facilitates communication between the sales associate and the customer on the basis of chat, voice over IP, email and the public switched telephone network, including the concept of bridging a chat session into a PSTN conference call during which call the sales associate and customer maintain a co-browsing session with regard to the opportunity over the Internet.
Owner:LIVEPERSON
Open flow table security enhancement method and device
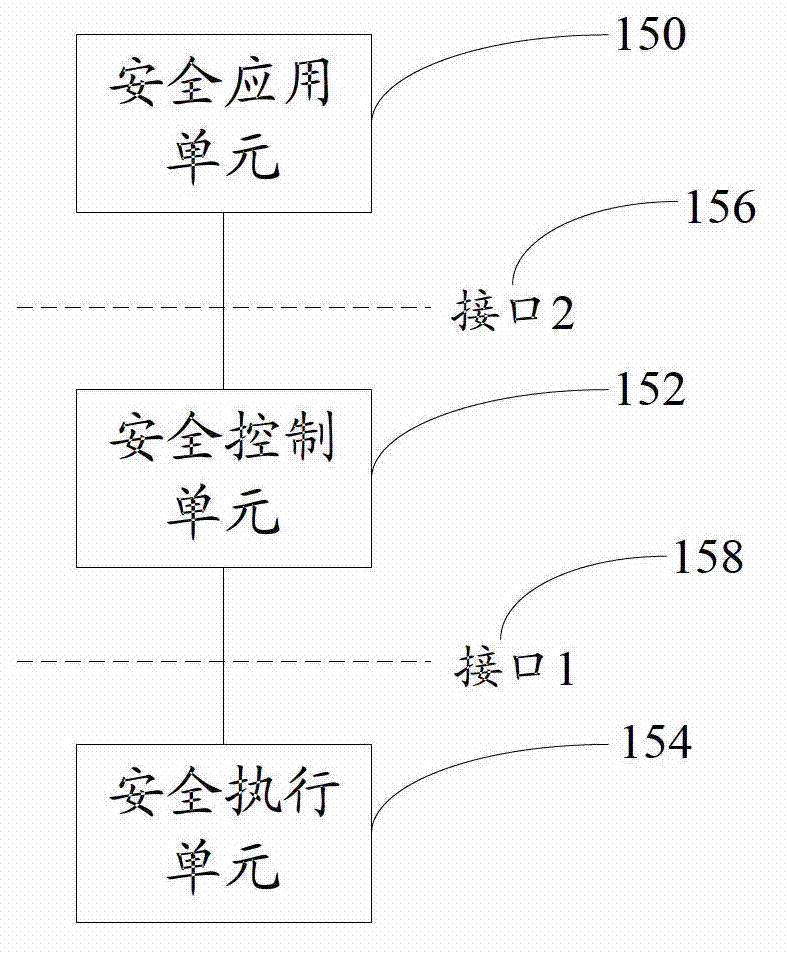
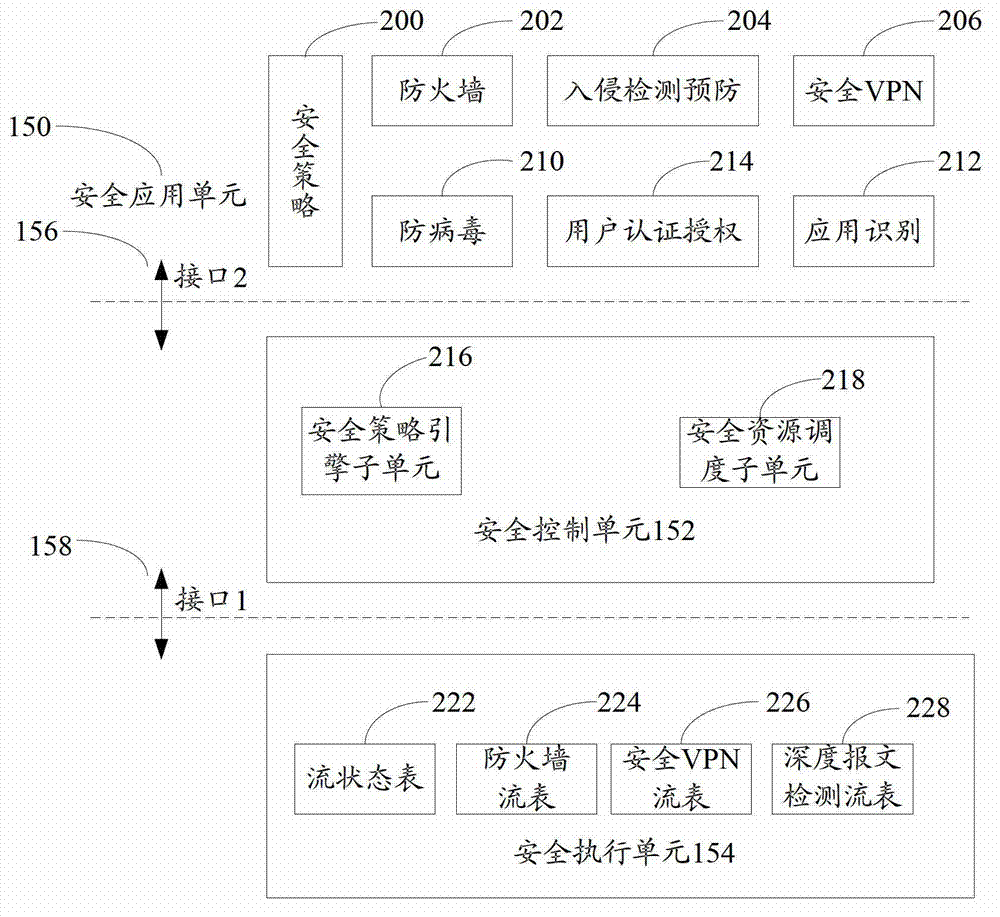
ActiveCN103095701AEasy to carry outProtect against zero-day attacksTransmissionVirtualizationPrivate network
The invention discloses an open flow table security enhancement method which can enable a security control function to be separated from a security executive function. The method includes the steps of obtaining security application corresponding to each security service, extracting security strategies, security protocols and feature libraries corresponding to the various security services from the security application, analyzing the security strategies of the security services to generate a security flow table, and creating a matching rule in the security flow table, and carrying out access control to messages and inspection for a state firewall, a security virtual private network (VPN) and deep messages according to the matching rule in the security flow table. The invention simultaneously discloses an open flow table security enhancement device. The open flow table security enhancement method and the open flow table security enhancement device can enable the security execution and the security application to be independently evolved and upgraded, and bring convenience to development of new security services, and can intensively carry out security management, resist zero-day attack, and relieve distributed denial of service attack according to the security strategies, and also support a virtualization multi-tenant security mode.
Owner:ZTE CORP
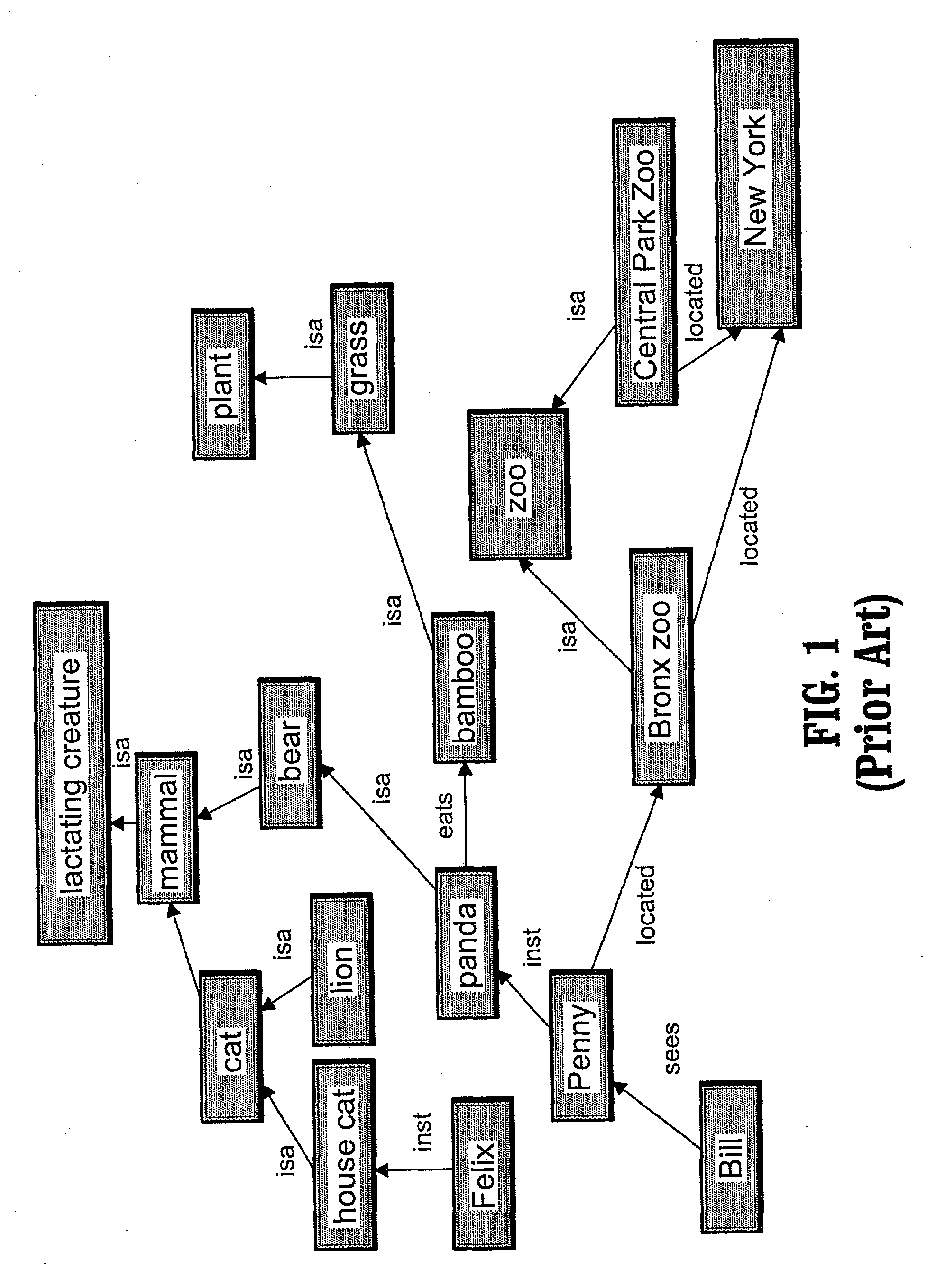
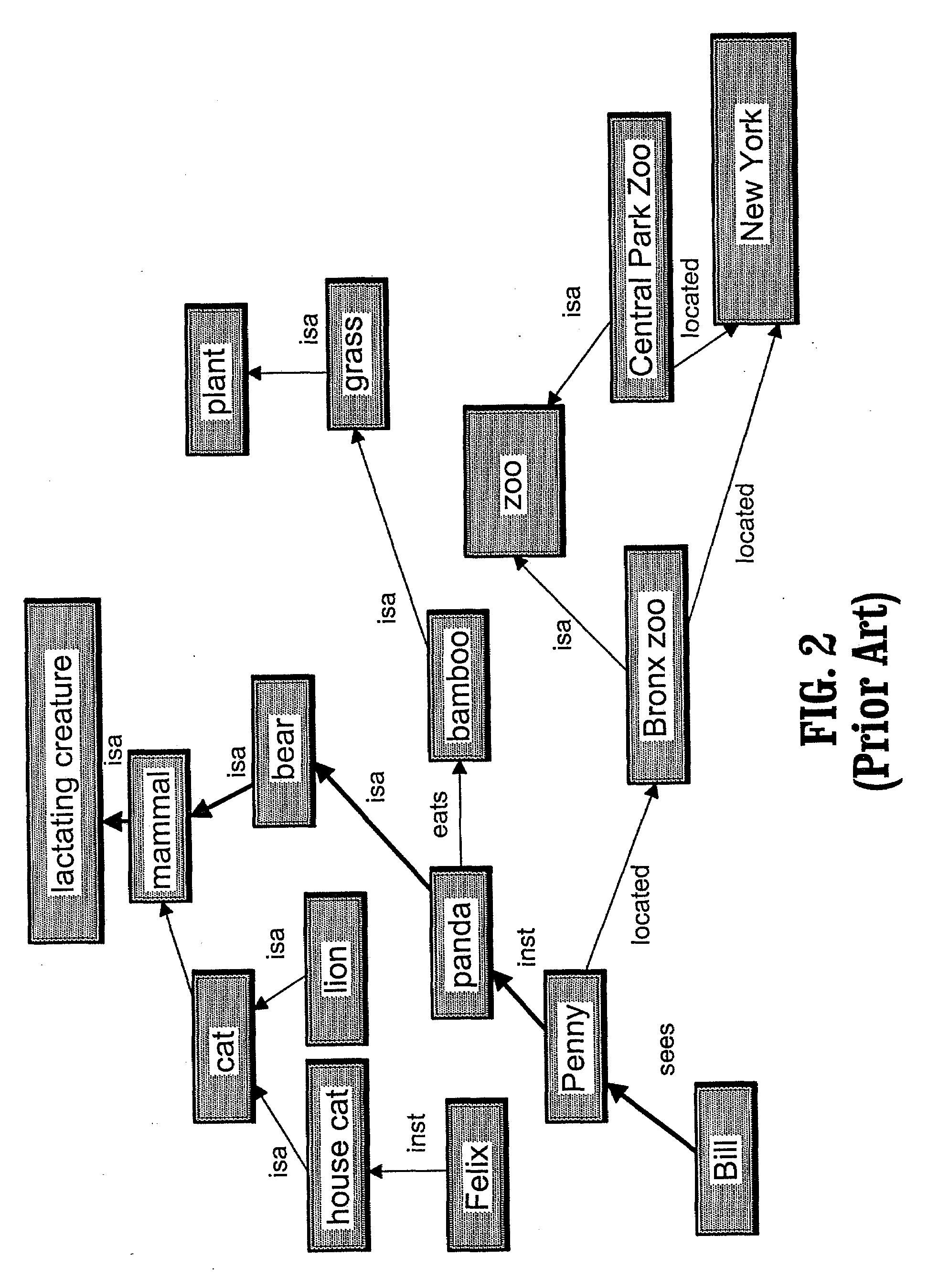
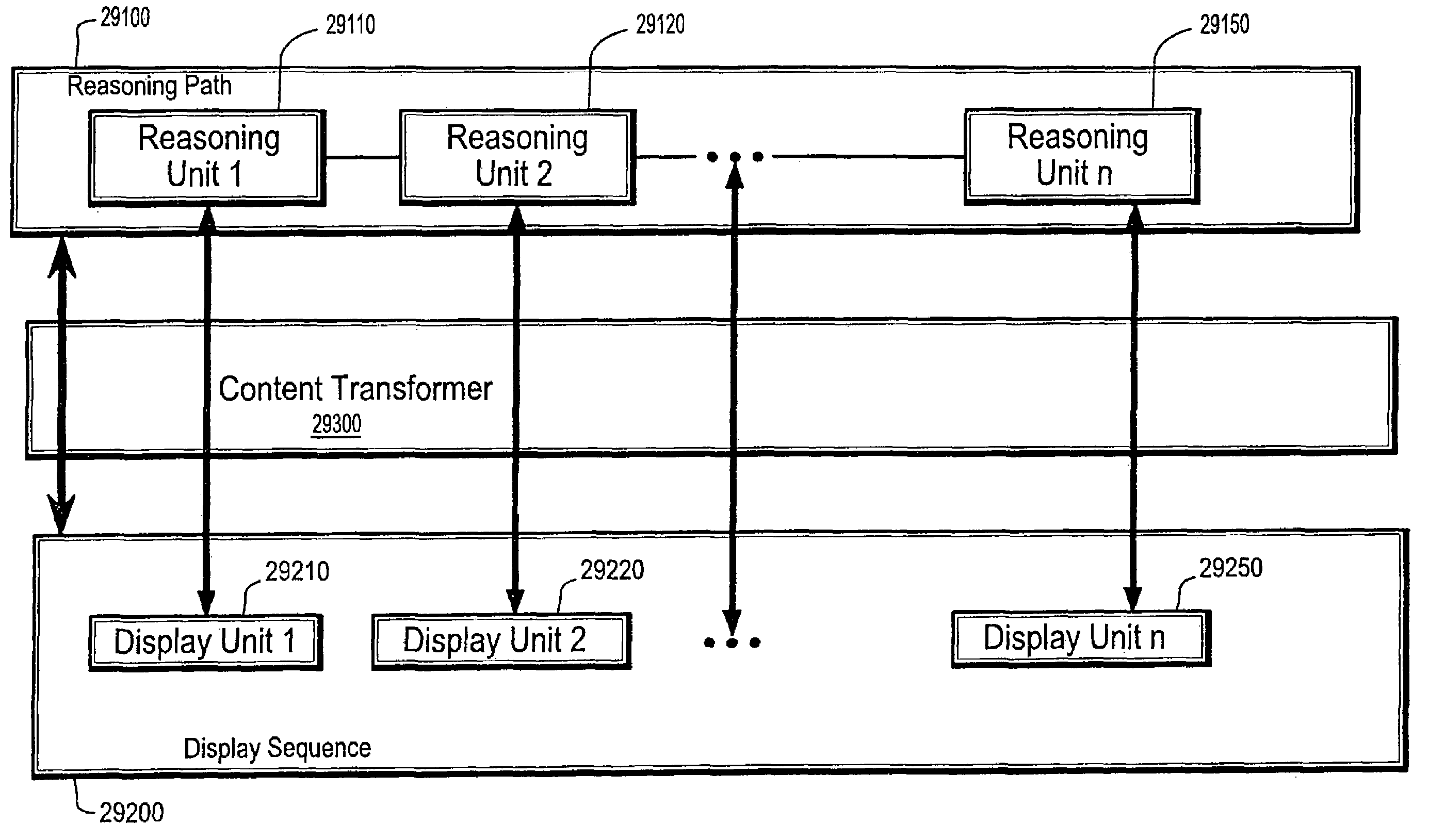
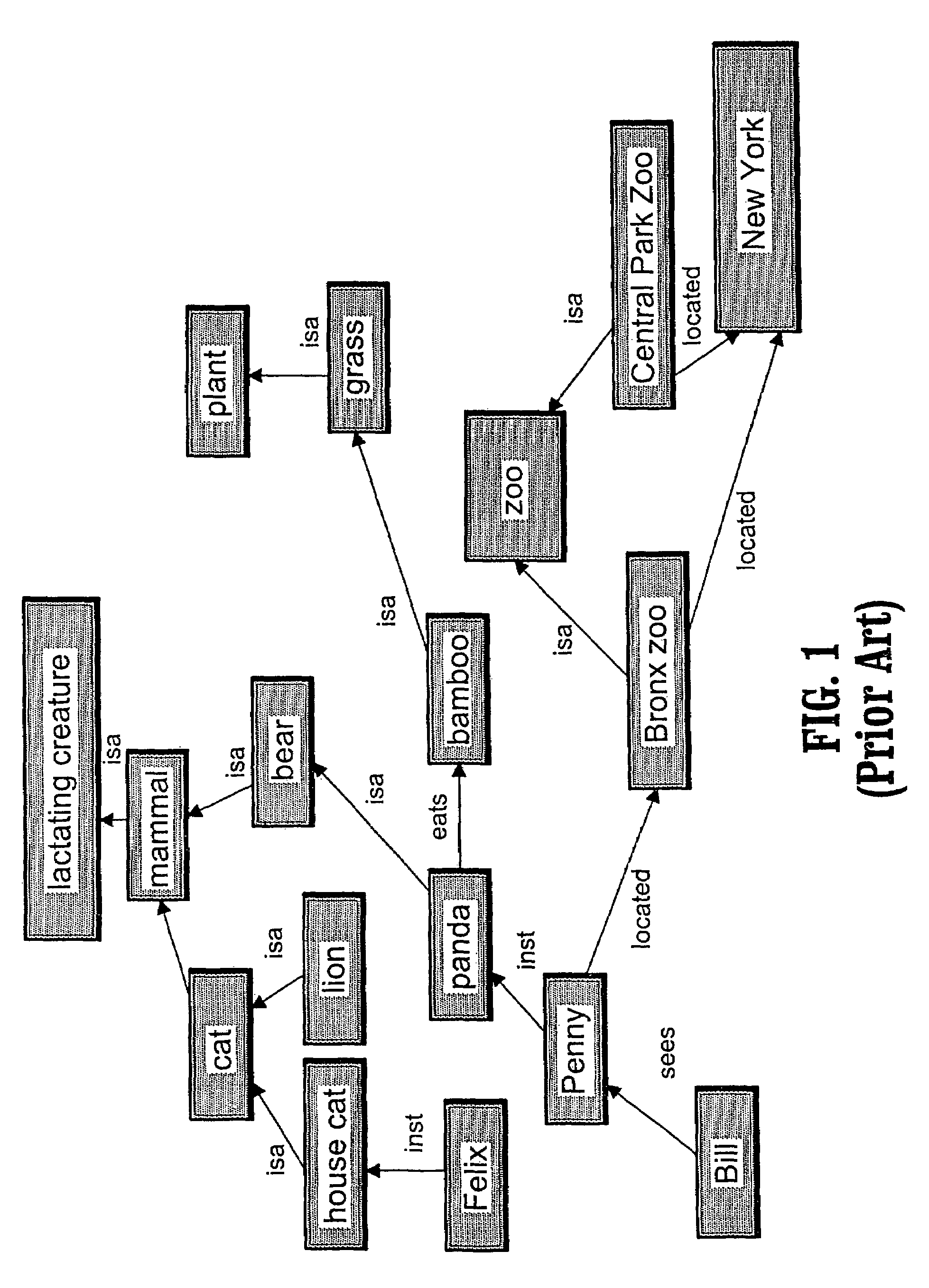
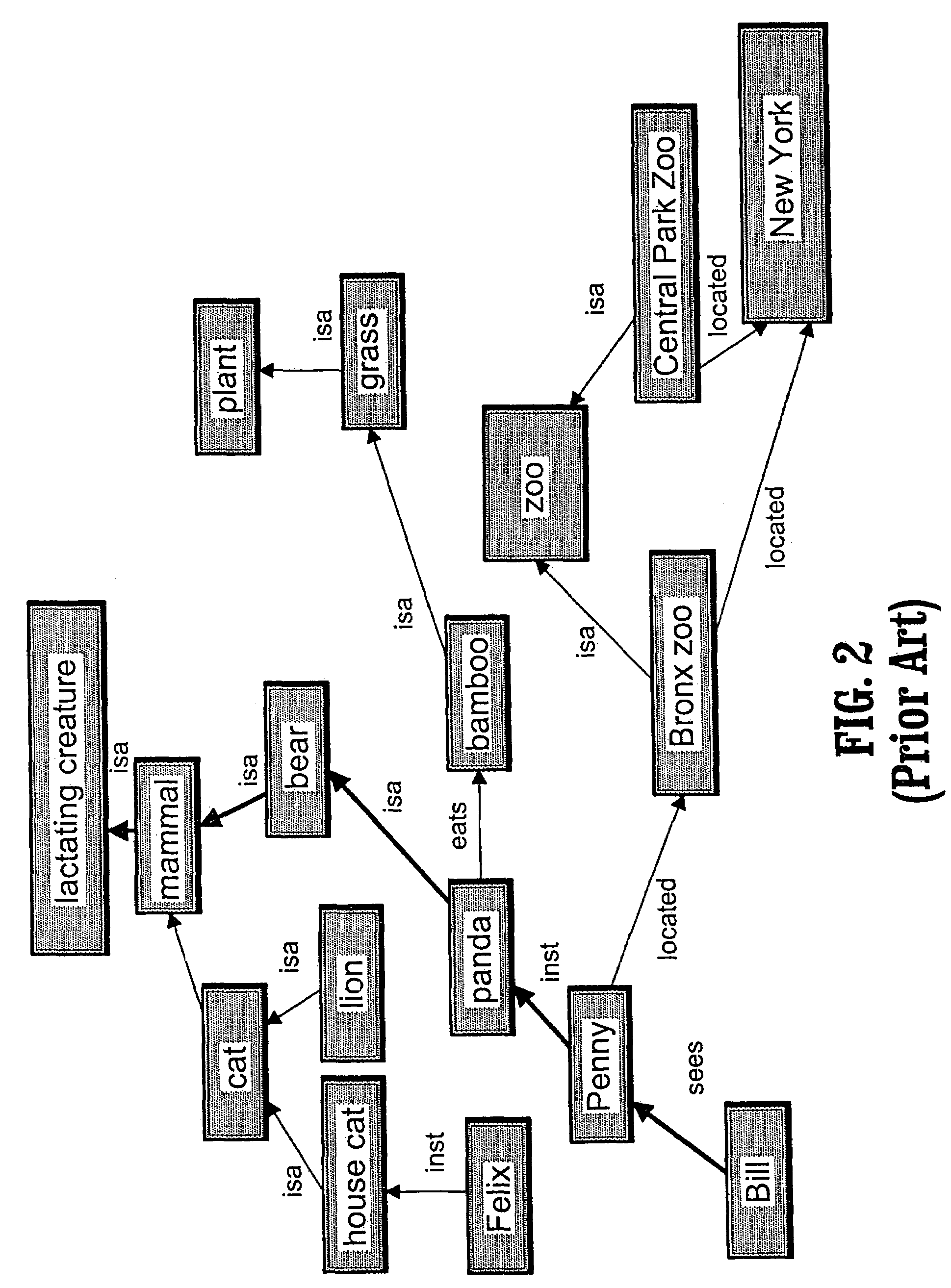
Method and knowledge structures for reasoning about concepts, relations, and rules
InactiveUS20090055342A1Data processing applicationsMultiple digital computer combinationsKnowledge structureMatch rule
A system and method for reasoning about concepts, relations and rules having a semantic network comprising at least one node from a predetermined set of node types, at least one link from a predetermined set of link types, and zero or more rules from a predetermined set of rule types, a subset of the rule types being matching rule types, each node and each link being associated with a set of zero or more rules; a network reasoning data structure having a reasoning type database having at least one regular expression, each of the regular expressions being a class of sequences having at least three node types and two link types, wherein the network reasoning data structure further has a context being a set of rules; and a reasoning engine having an activator for activating one or more activated paths in the semantic network, the set of activated paths having a common starting node in the semantic network, wherein the reasoning engine further has a validator for selecting a subset of the activated paths being valid paths, each rule from the set of rule matching types that is associated with one or more path elements on each valid path being matched by one or more rules in the context and wherein the reasoning engine further has a legal inferencer for selecting a subset of the set of valid paths being legal and valid paths, the legal and valid paths matching at least one of the regular expressions.
Owner:IBM CORP
Method and knowledge structures for reasoning about concepts, relations, and rules
A system and method for reasoning about concepts, relations and rules having a semantic network comprising at least one node from a predetermined set of node types, at least one link from a predetermined set of link types, and zero or more rules from a predetermined set of rule types, a subset of the rule types being matching rule types, each node and each link being associated with a set of zero or more rules; a network reasoning data structure having a reasoning type database having at least one regular expression, each of the regular expressions being a class of sequences having at least three node types and two link types, wherein the network reasoning data structure further has a context being a set of rules; and a reasoning engine having an activator for activating one or more activated paths in the semantic network, the set of activated paths having a common starting node in the semantic network, wherein the reasoning engine further has a validator for selecting a subset of the activated paths being valid paths, each rule from the set of rule matching types that is associated with one or more path elements on each valid path being matched by one or more rules in the context and wherein the reasoning engine further has a legal inferencer for selecting a subset of the set of valid paths being legal and valid paths, the legal and valid paths matching at least one of the regular expressions.
Owner:IBM CORP
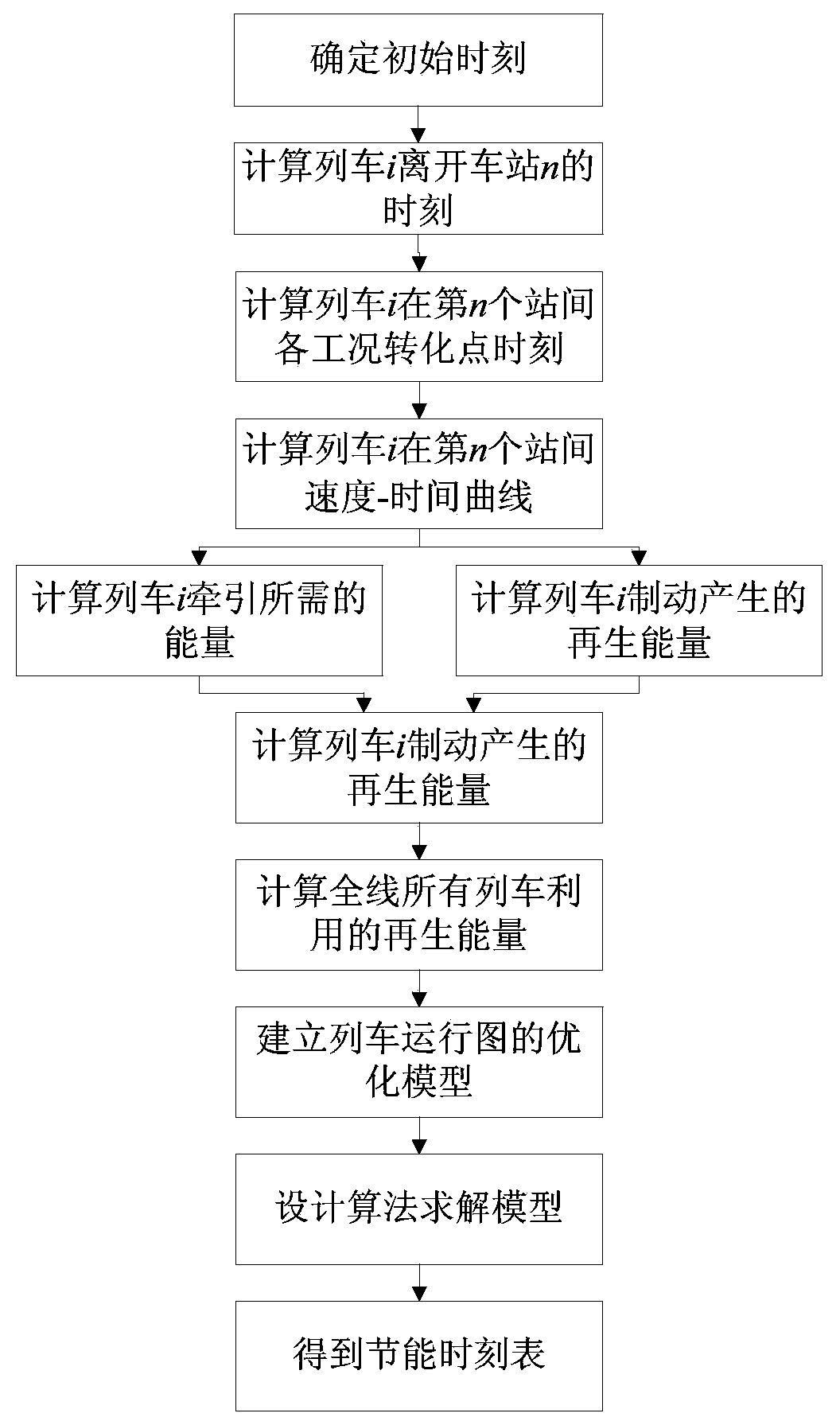
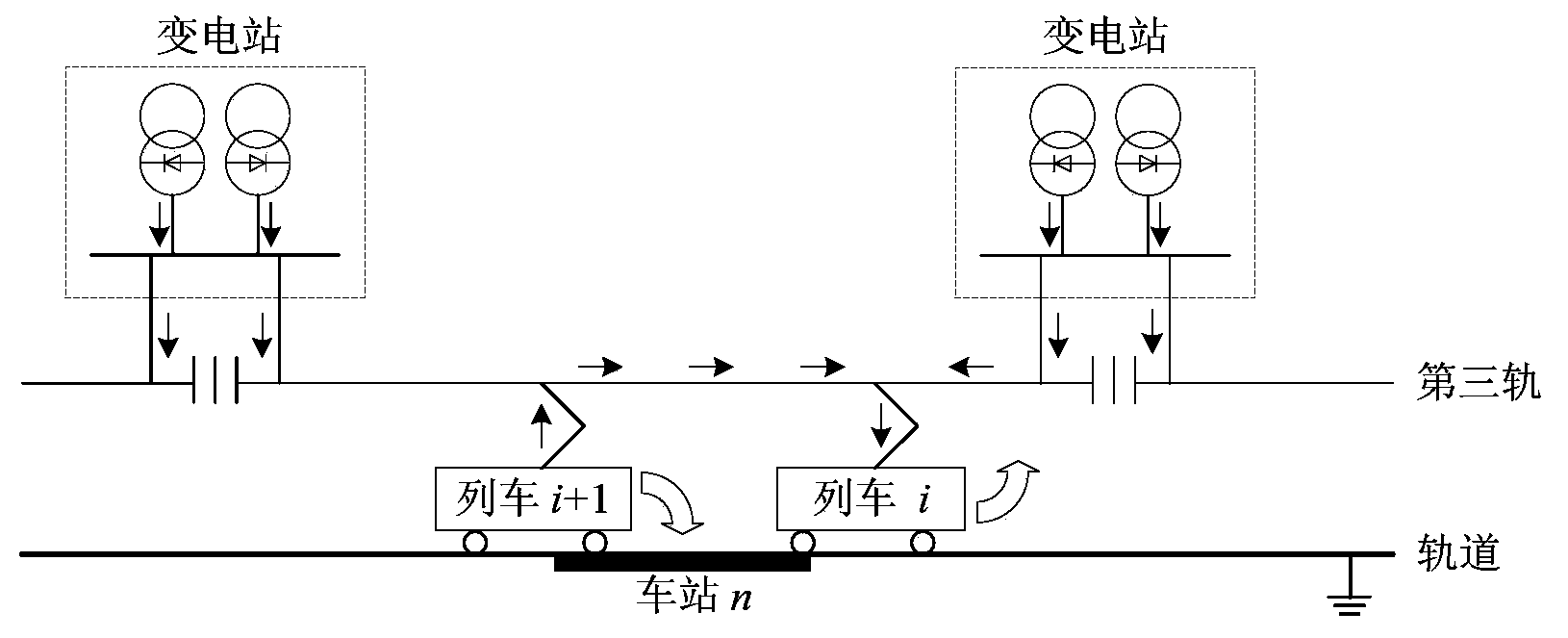
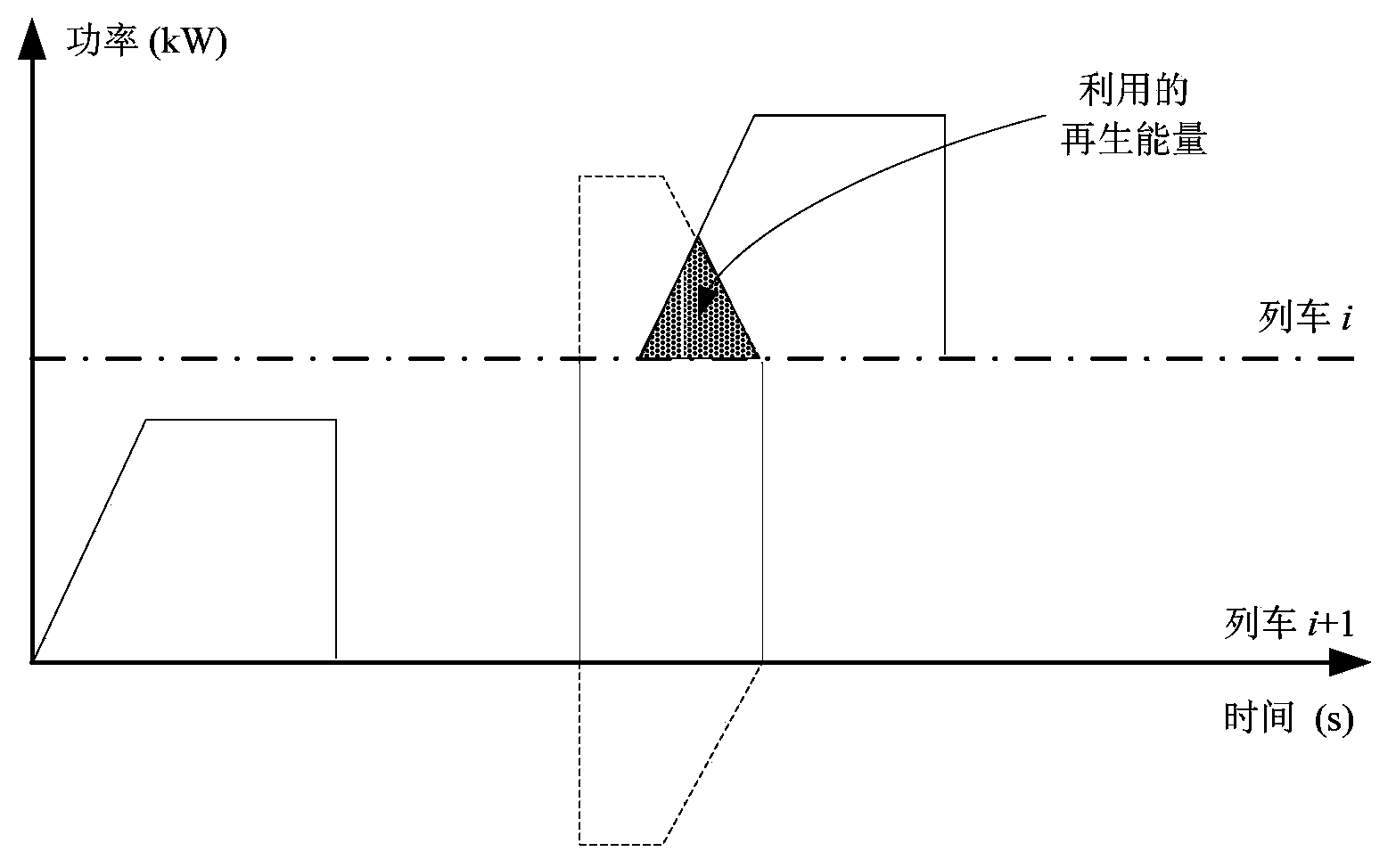
Energy-saving method of train operation of urban mass transit
InactiveCN103963805AReduce operating energy consumptionImprove securityAutomatic systemsSpecial data processing applicationsMatch ruleTime table
The invention belongs to the technical field of urban mass transit and particularly relates to an energy-saving method of train operation of the urban mass transit. The energy-saving method comprises the steps of 1, analyzing operation matching rules of adjacent trains and computing the size of utilized regeneration energy; 2, establishing an optimization model of the train operation by taking the utilized regeneration energy as the target; 3, solving the optimization model to obtain an energy-saving time table of the train operation of the urban mass transit. By means of the energy-saving method, energy consumption during train operation is reduced, and security of an overhead line system is improved. Furthermore, the energy-saving method has the advantages of (1) being high in operation speed and applicable to large-scale computer simulation by adopting an integer programming method; (2) considering comprehensive factors, being high in modeling accuracy and strong in applicability of the planned operation time table; (3) being capable of embedded into hardware of a train energy-saving driving auxiliary system in an online mode, easy to implement, low in cost and wide in application range.
Owner:BEIJING JIAOTONG UNIV
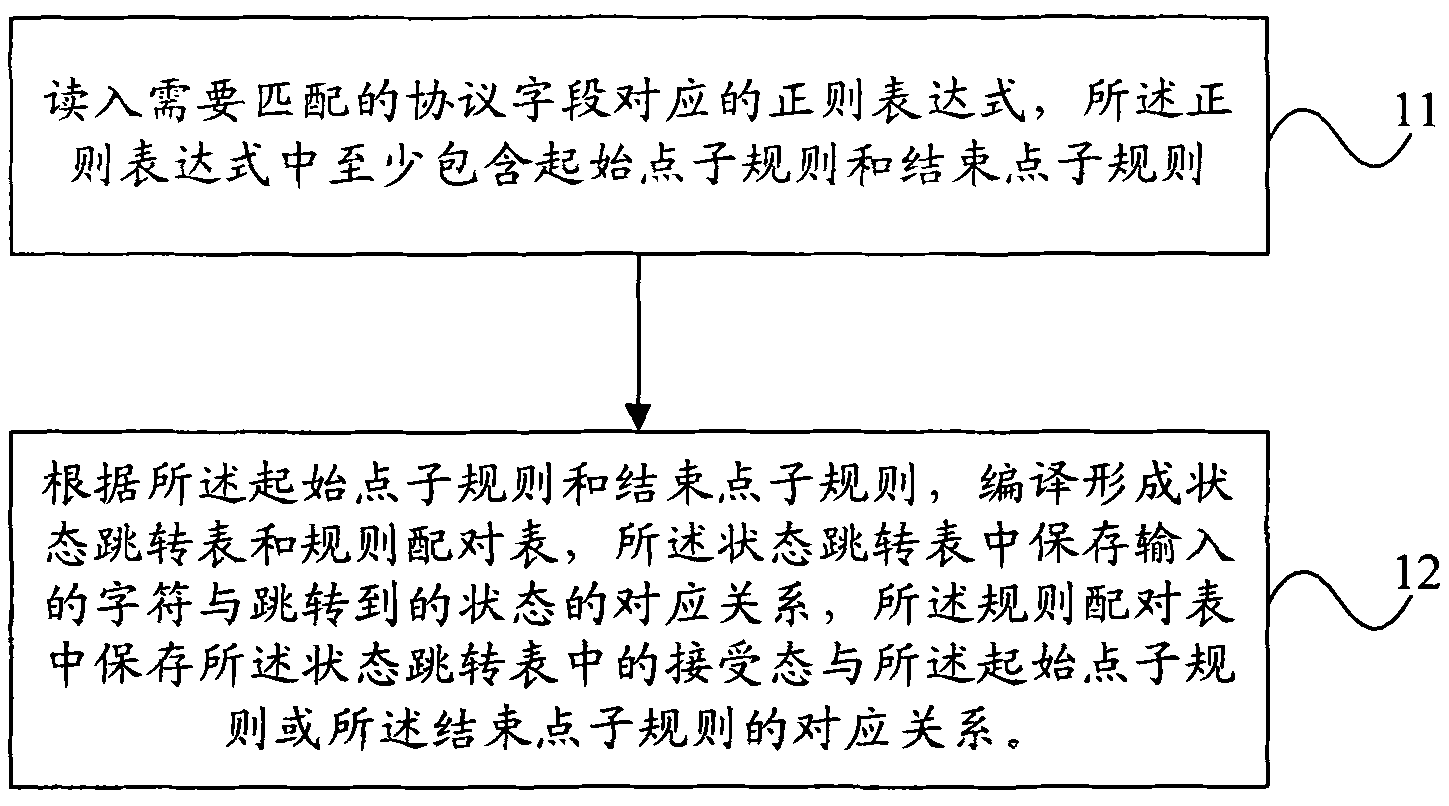
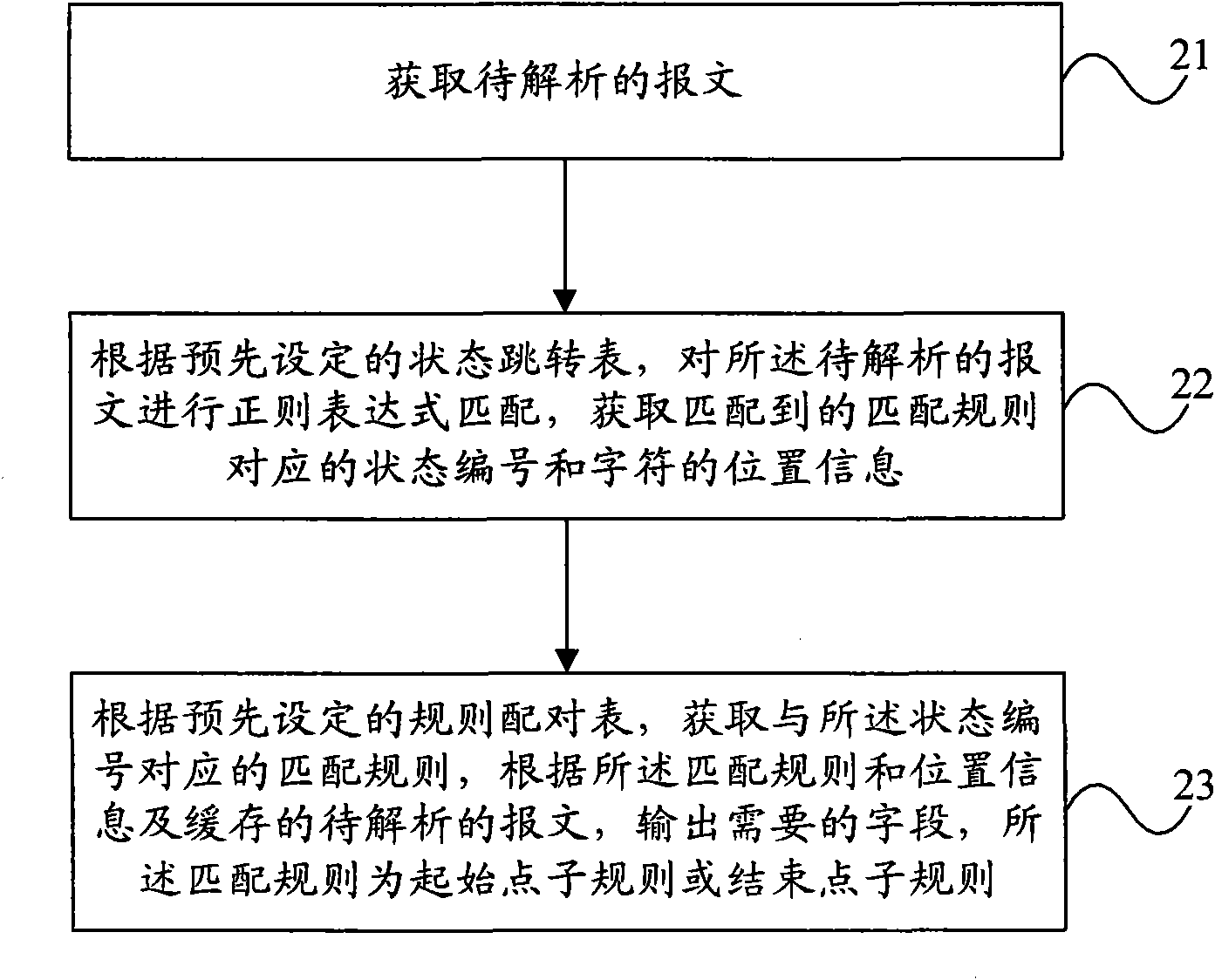
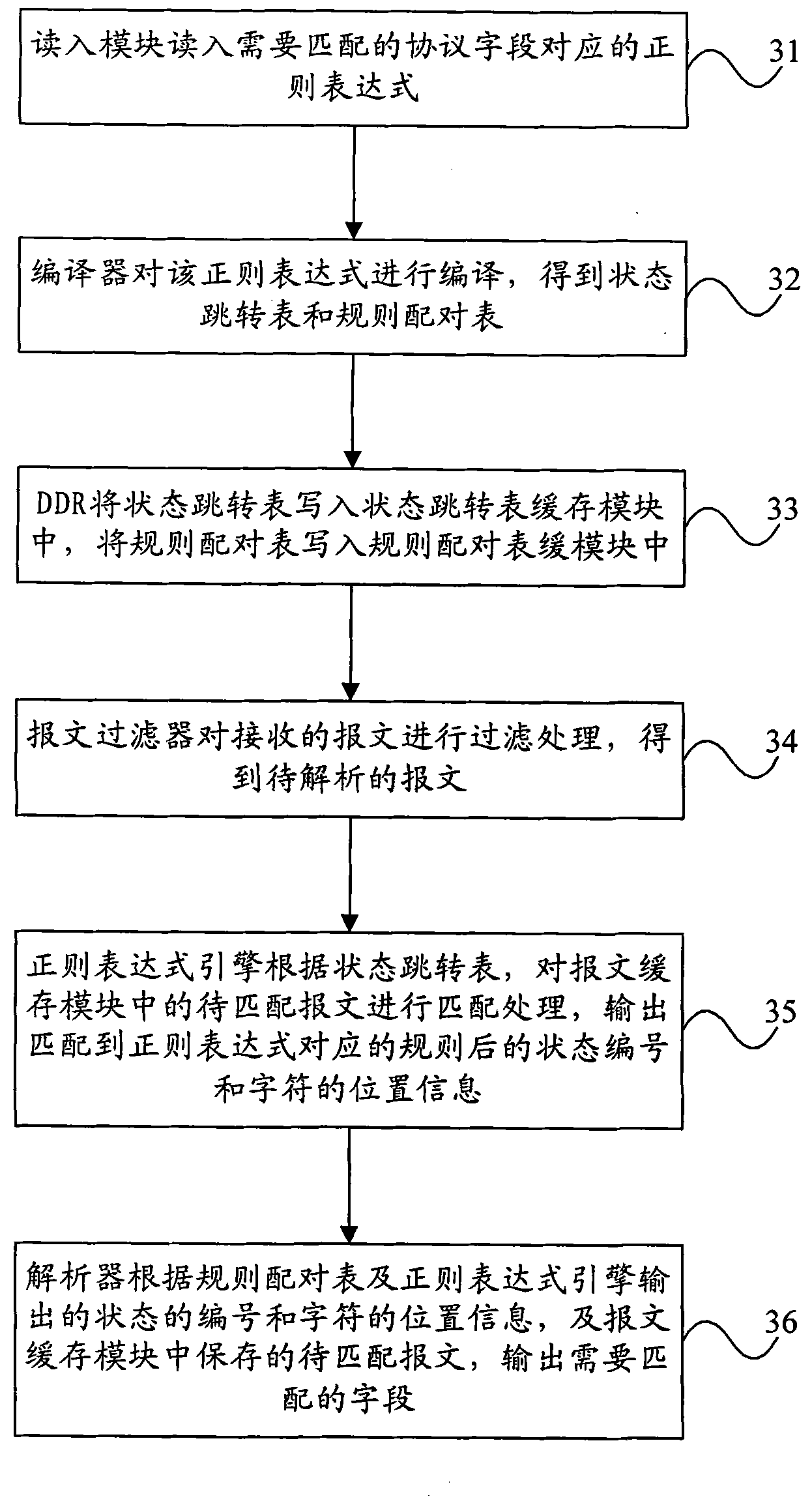
Parameter acquiring and general protocol analyzing method and device
The invention provides a parameter acquiring and general protocol analyzing method and device. The method comprises the steps of: obtaining a message to be analyzed; according to a preset state jump table, carrying out regular expression matching on the message to be analyzed to obtain a state number corresponding a matched matching rule and position information of characters; and obtaining a matching rule corresponding to the state number according to a preset rule pairing table, and outputting a required field according to the matching rule and the position information and the cached message to be analyzed, wherein the matching rule is a starting point subrule or ending point subrule. The embodiment of the invention can realize general analysis on protocols.
Owner:HUAWEI TECH CO LTD
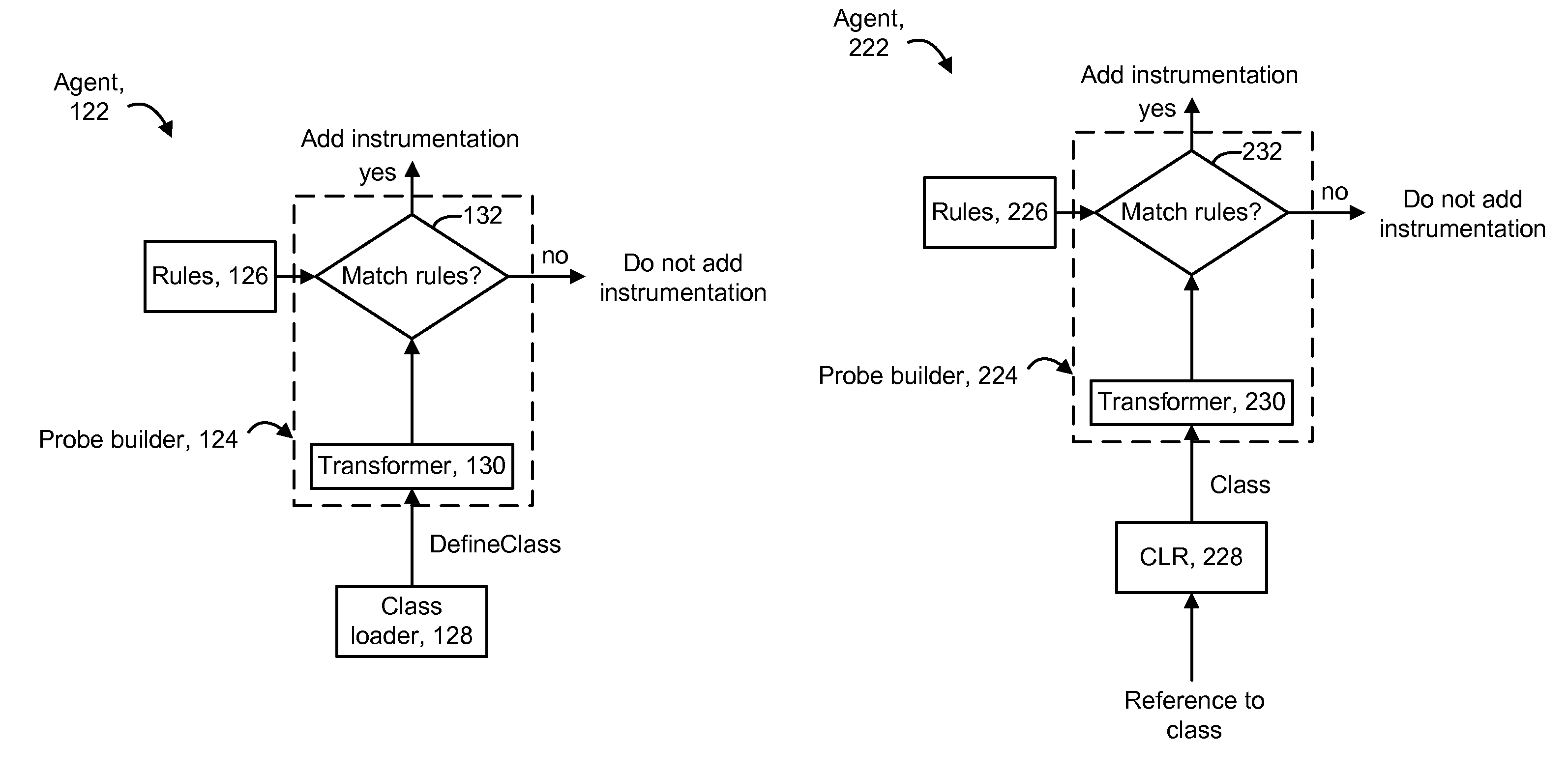
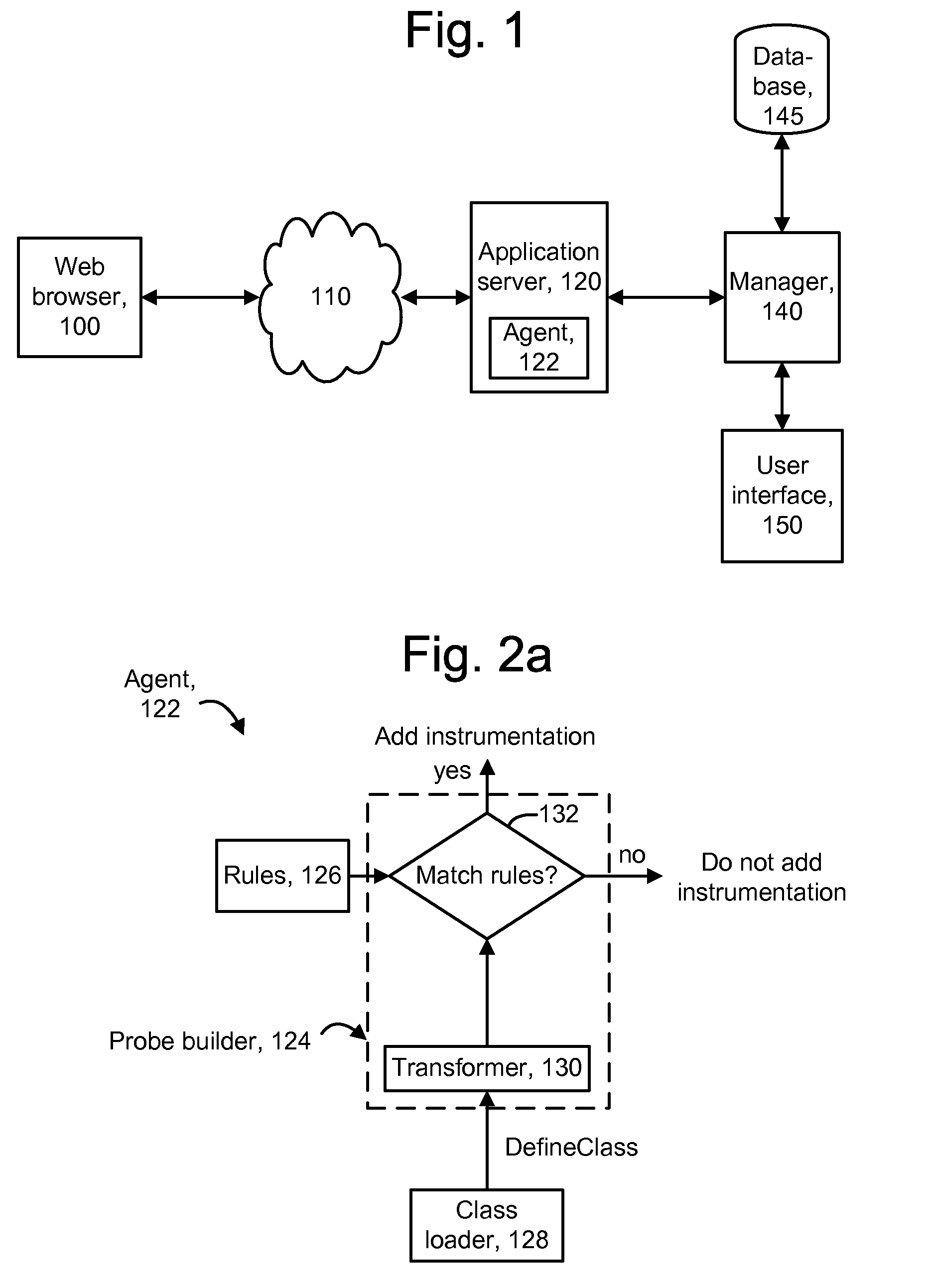
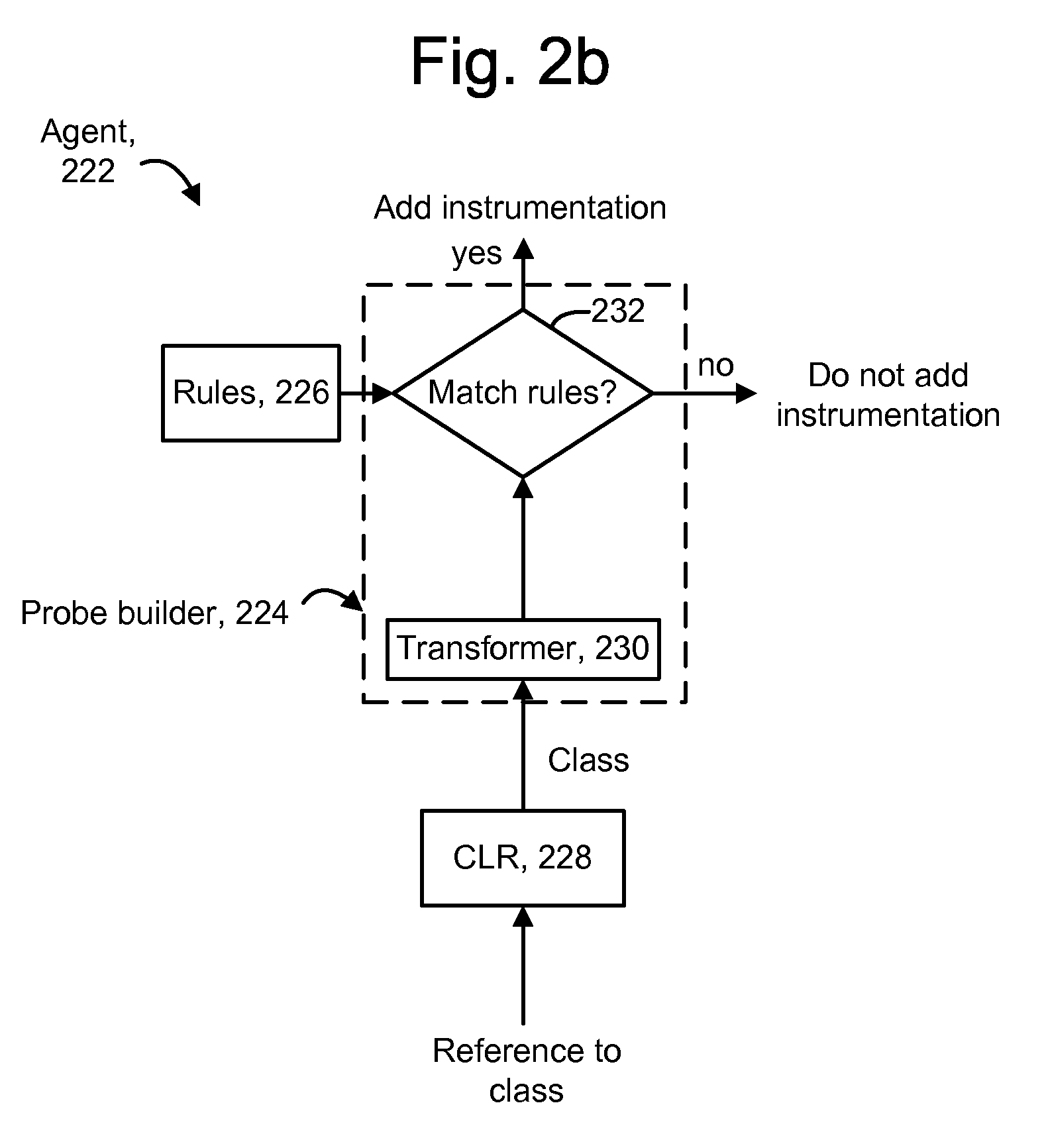
Intelligent engine for dynamic and rule based instrumentation of software
ActiveUS8307345B2Error detection/correctionSpecific program execution arrangementsIntelligent designHeuristic
Instrumentation is dynamically added to application components during runtime. An interestingness engine receives inputs from various sources which identify software components such as classes for which it is desired to provide instrumentation. The sources can include a heuristics engine which receives performance data from already-instrumented components, a user interface from which a user identifies component to be instrumented or de-instrumented, and a static list of components to be instrumented. During the runtime, instrumentation can be added to components which become interesting, or removed from components which become not interesting. When loading or redefining a component, if a component type matches rules, it is eligible for instrumentation, and the interestingness engine is consulted to determine whether the component is of interest, in which case instrumentation is added. If a component type does not match rules, but the component is interesting, the rules can be updated to include the component type.
Owner:CA TECH INC
Methods for matching metadata from disparate data sources
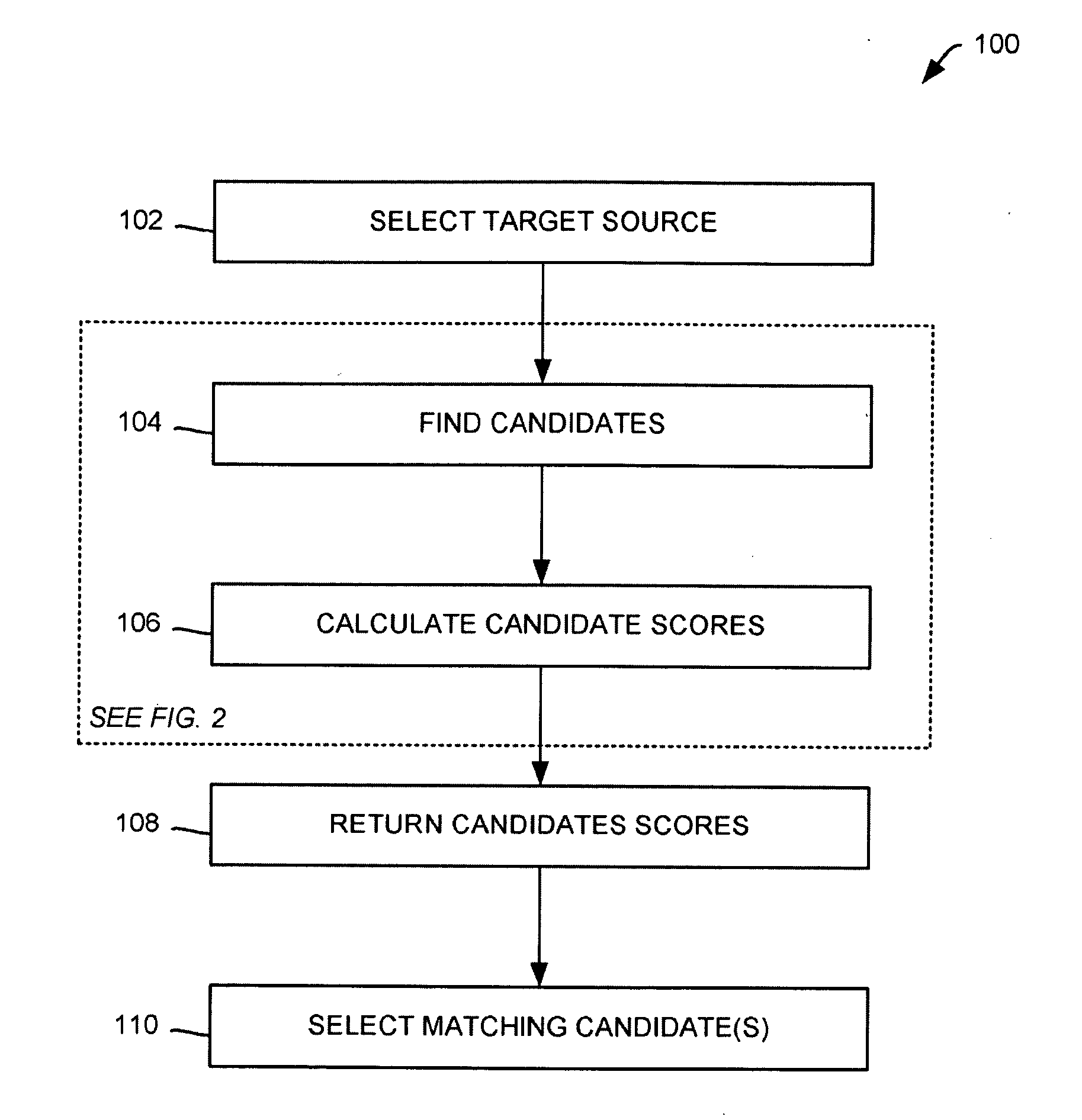
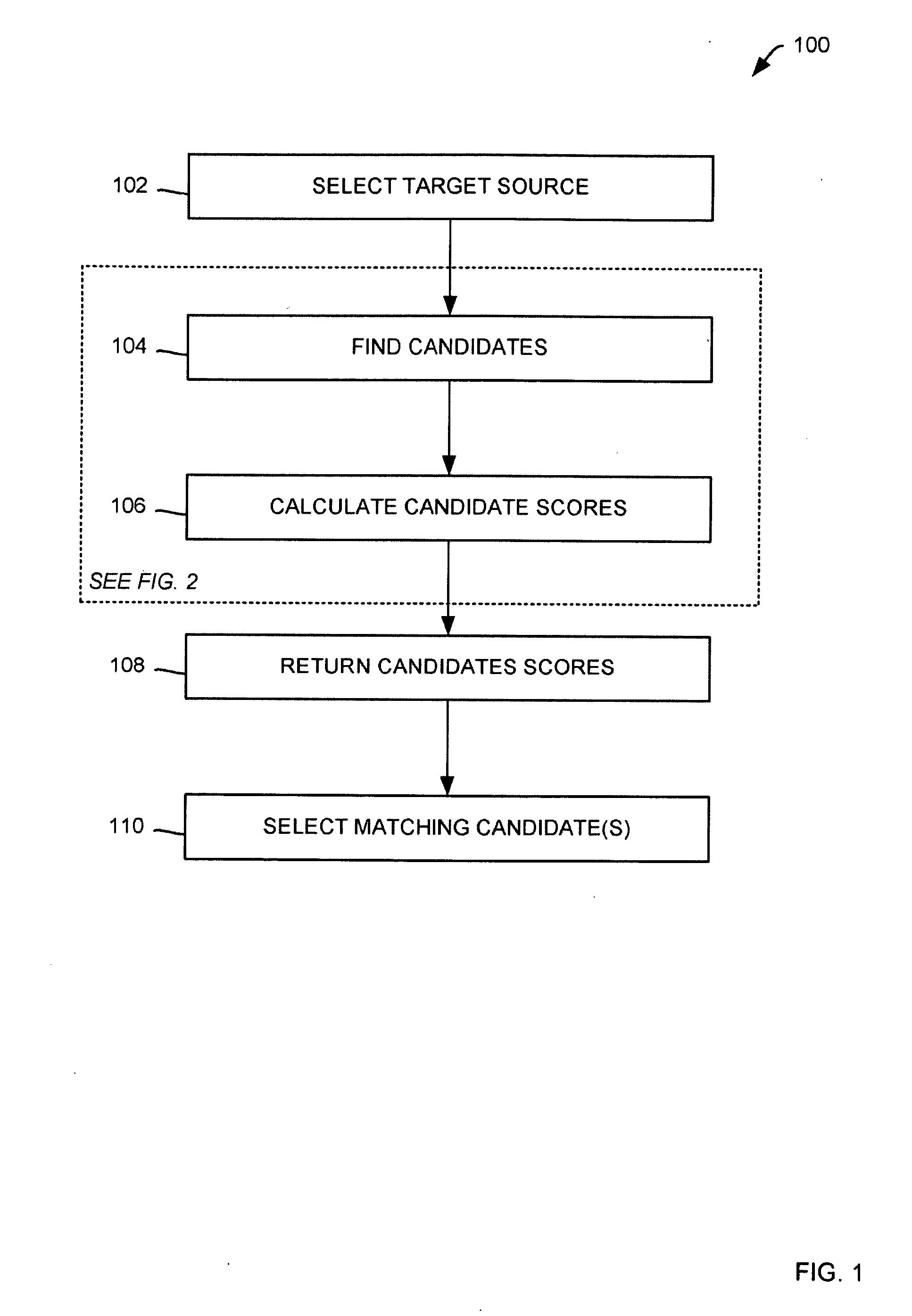
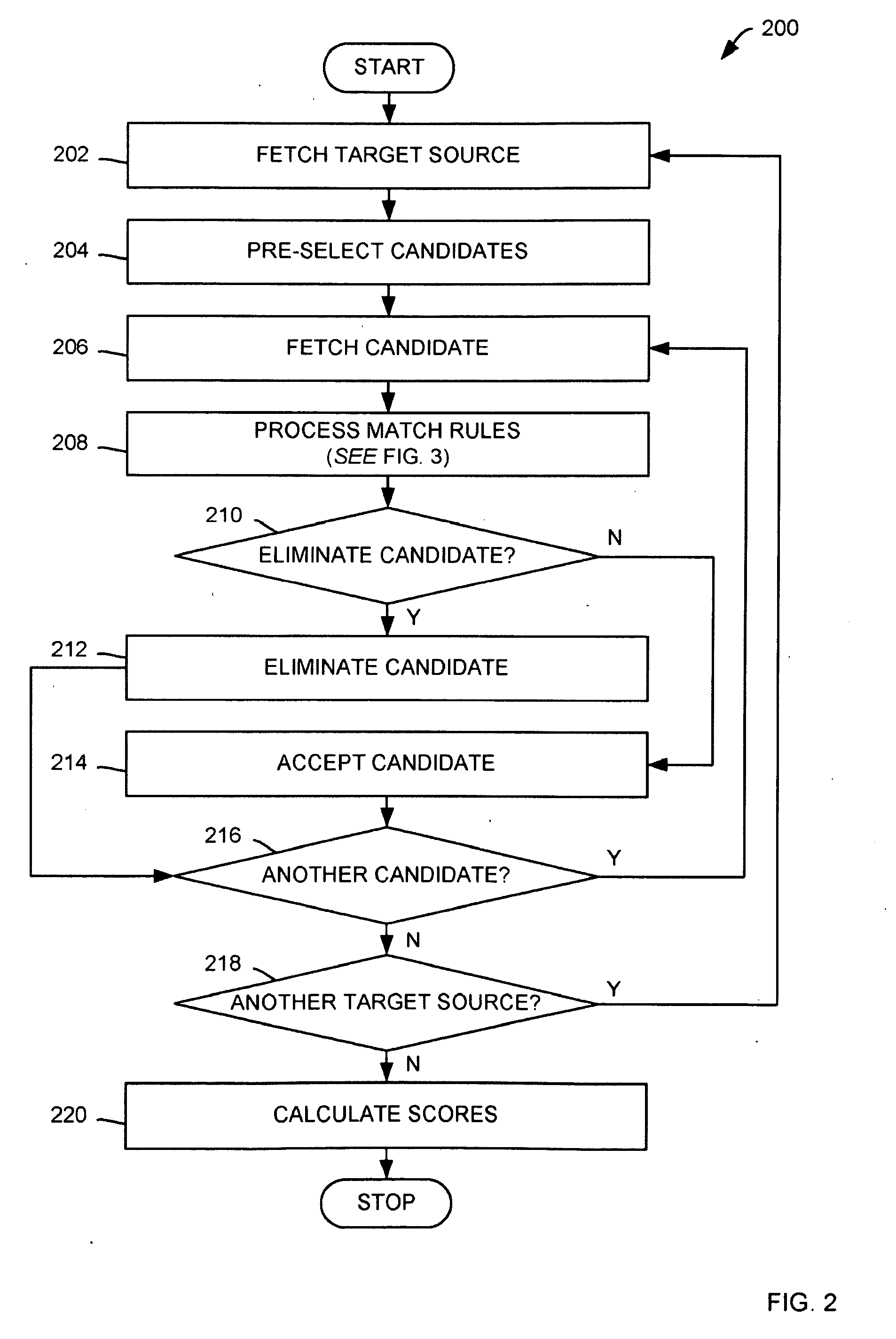
InactiveUS20100185637A1Well formedDigital data processing detailsSpecial data processing applicationsData sourceMatch rule
Methods for matching a candidates with a target utilizing extract, transform and load (ETL) metadata utilizing a computer, the candidates originating from a number of secondary data sources are presented including: causing the computer to receive the target from a target data source; causing the computer to fetch the candidates from the number of secondary data sources; causing the computer to process match rules, the match rules configured for determining whether the candidates match with the target, where the ETL metadata provides data for the processing; if the number of match rules determines a potential candidate match, causing the computer to score the potential candidate match utilizing a weighting method, the weighting method corresponding with a degree of importance of the match, where the potential candidate match corresponds with one of candidates; and causing the computer to display the potential candidate match.
Owner:IBM CORP
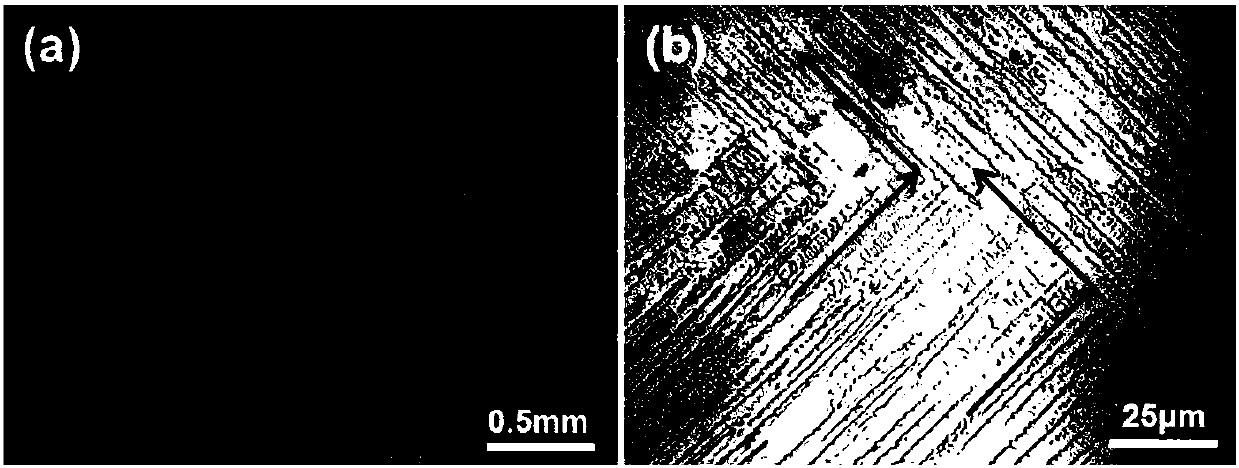
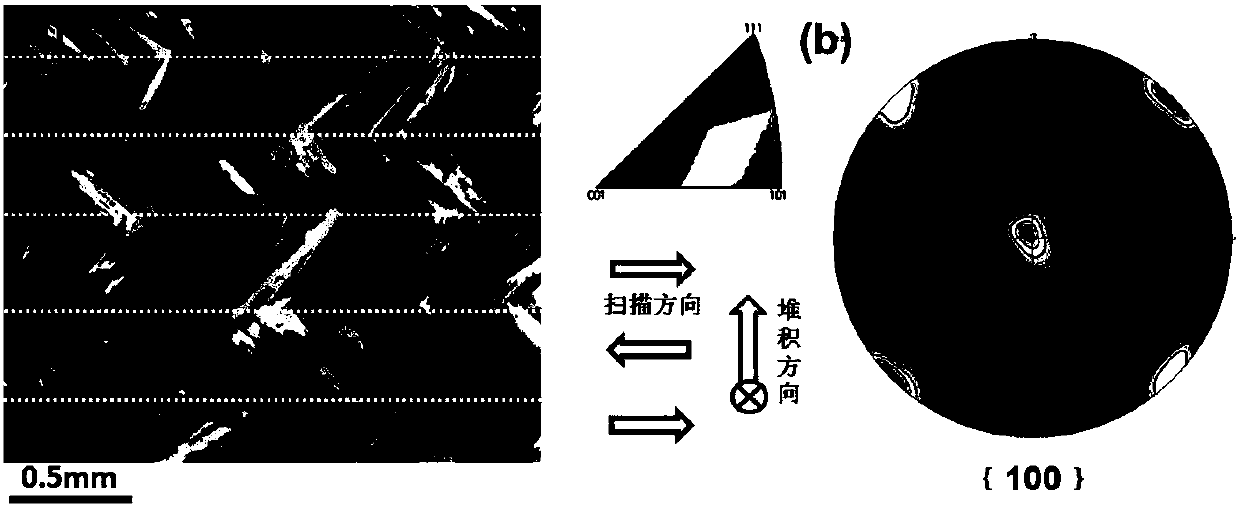
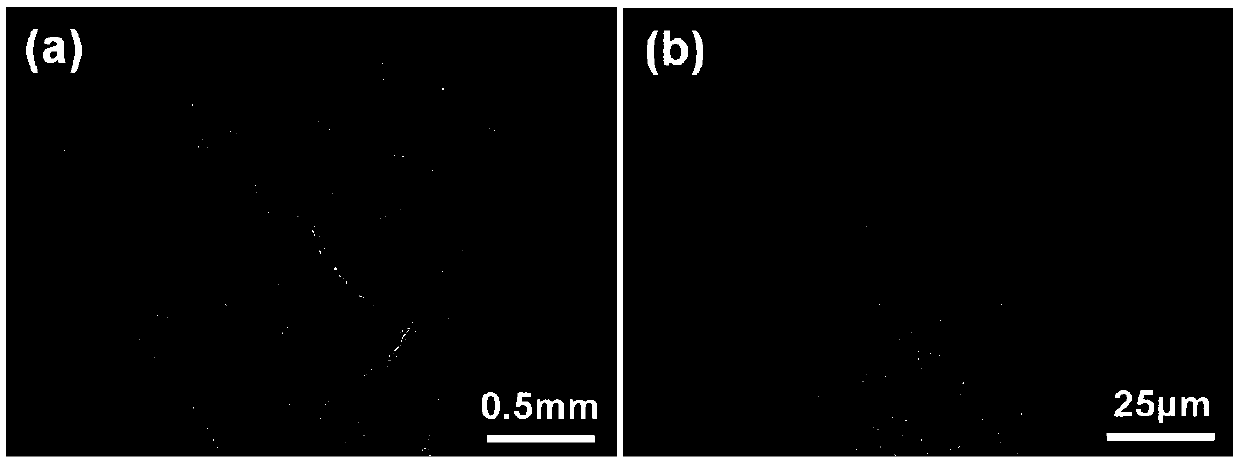
Quasi-continuous laser metal 3D printing method capable of realizing regulation of nickel base alloy crystallographic texture
ActiveCN107790717AImprove consistencyImprove microstructureAdditive manufacturing apparatusIncreasing energy efficiencyMolten bathMatch rule
The invention discloses a quasi-continuous laser metal 3D printing method capable of realizing regulation of nickel base alloy crystallographic texture. Laser output is set as a quasi-continuous lasermode, and then a laser metal 3D printing technical window is preliminarily optimized. The temperature field of a molten bath under the preliminarily optimized parameter is calculated by using a finite element heat transfer model; the temperature gradient G and the cooling rate xi of the moving boundary of the molten bath during closing of laser in a single pulse period are extracted, and the growth length L of a single pulse internal columnar dendrite is worked out according to a structure growth theoretical model; the laser parameter is optimized according to the matching rule that the ratioof the scanning speed V to pulse frequency f is 0.5-0.8L, and finally 3D printing forming is conducted according to the optimized parameter, so that a formed part with the consistent crystallographicorientation height is obtained. By regulating the heat source output mode, an effective remelting mechanism for mixed crystal or isometric crystal is introduced in the scanning direction, all columnar dendrite growth is obtained, and the consistency of grain orientation is remarkably improved.
Owner:HUNAN UNIV
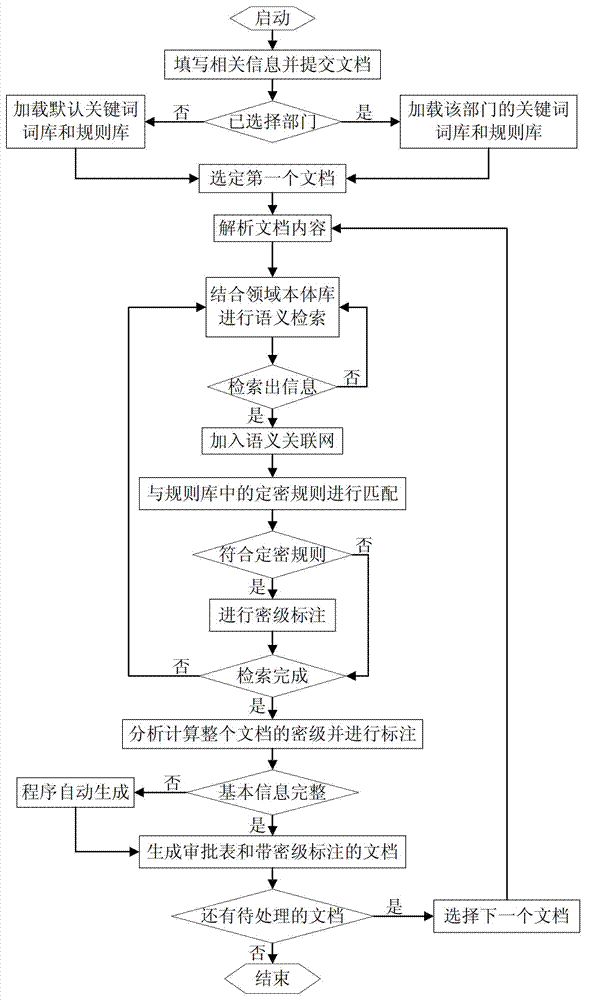
Method for retrieving confidential information of file and judging and marking security classification based on content correlation
InactiveCN102819604AAccurate and comprehensive searchEfficient searchSpecial data processing applicationsInternet privacyContent retrieval
A method for retrieving confidential information of a file and judging and marking the security classification based on content correlation is mainly characterized by comprising the following steps of: selecting corresponding confidential keywords and a matched rule base according to the range to which a document belongs; accurately and comprehensively searching confidential information in the document by carrying out word segmenting operation on the document contents and constructing a semantic correlation network; carrying out security classification judgment and encryption processing on each confidential information point according to a secret-level setting rule in a secret-level setting rule base; then giving out corresponding security classifications by integrating the security classifications of various confidential information points; and finally, marking related confidential information in the documents. According to the method, the confidential information in the document can be efficiently searched and the security classification of the document is accurately judged, so that the workload of manual secret-level setting is reduced, the efficiencies of secret-level setting work and the security classification appraisal work are increased, the random secret-level setting phenomenon in the secret-level setting process is effectively prevented and new confidential keywords and matching rules can be automatically learned, and further the precision of retrieval and security classification judgment is continuously improved.
Owner:徐亮 +1
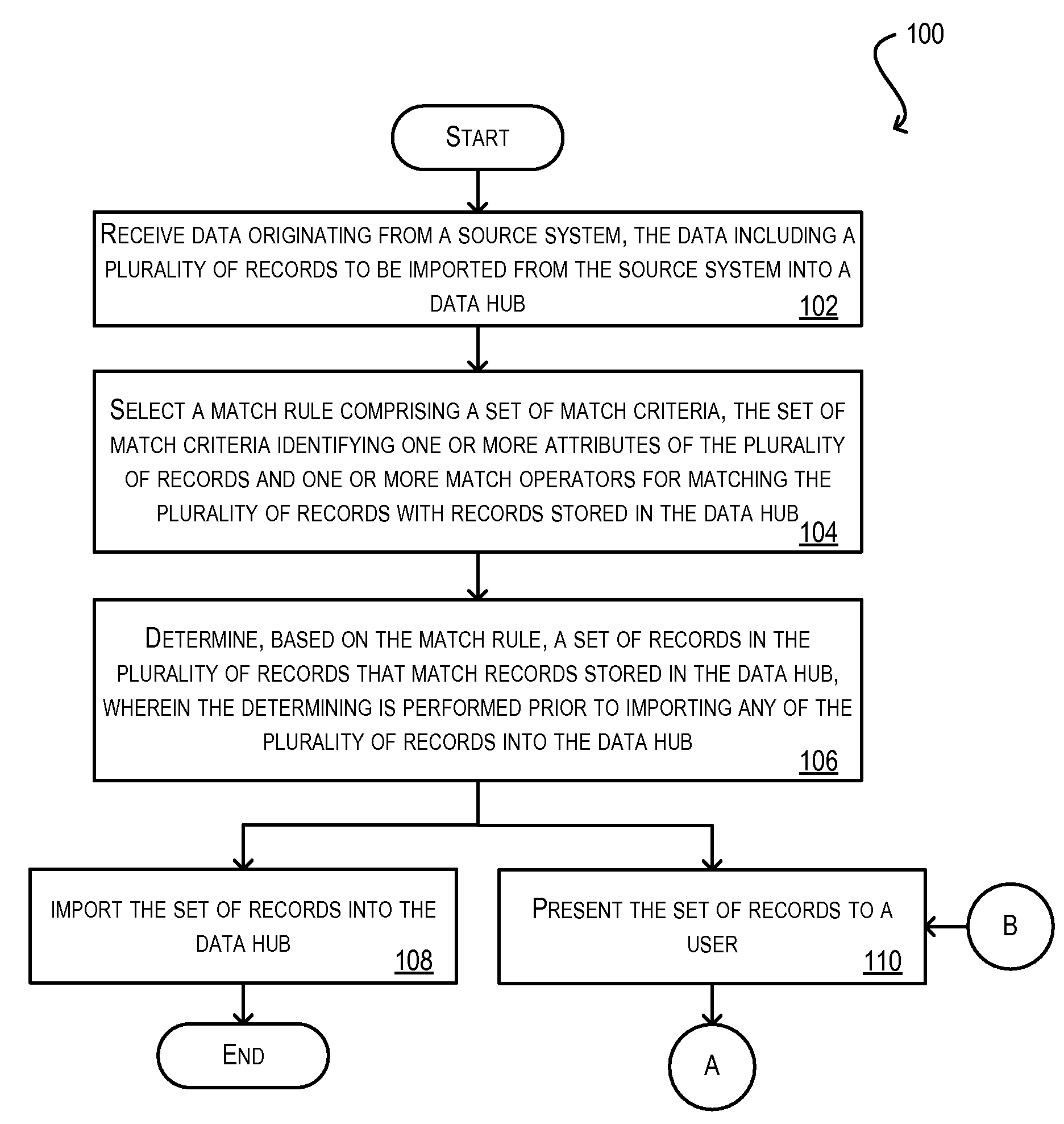
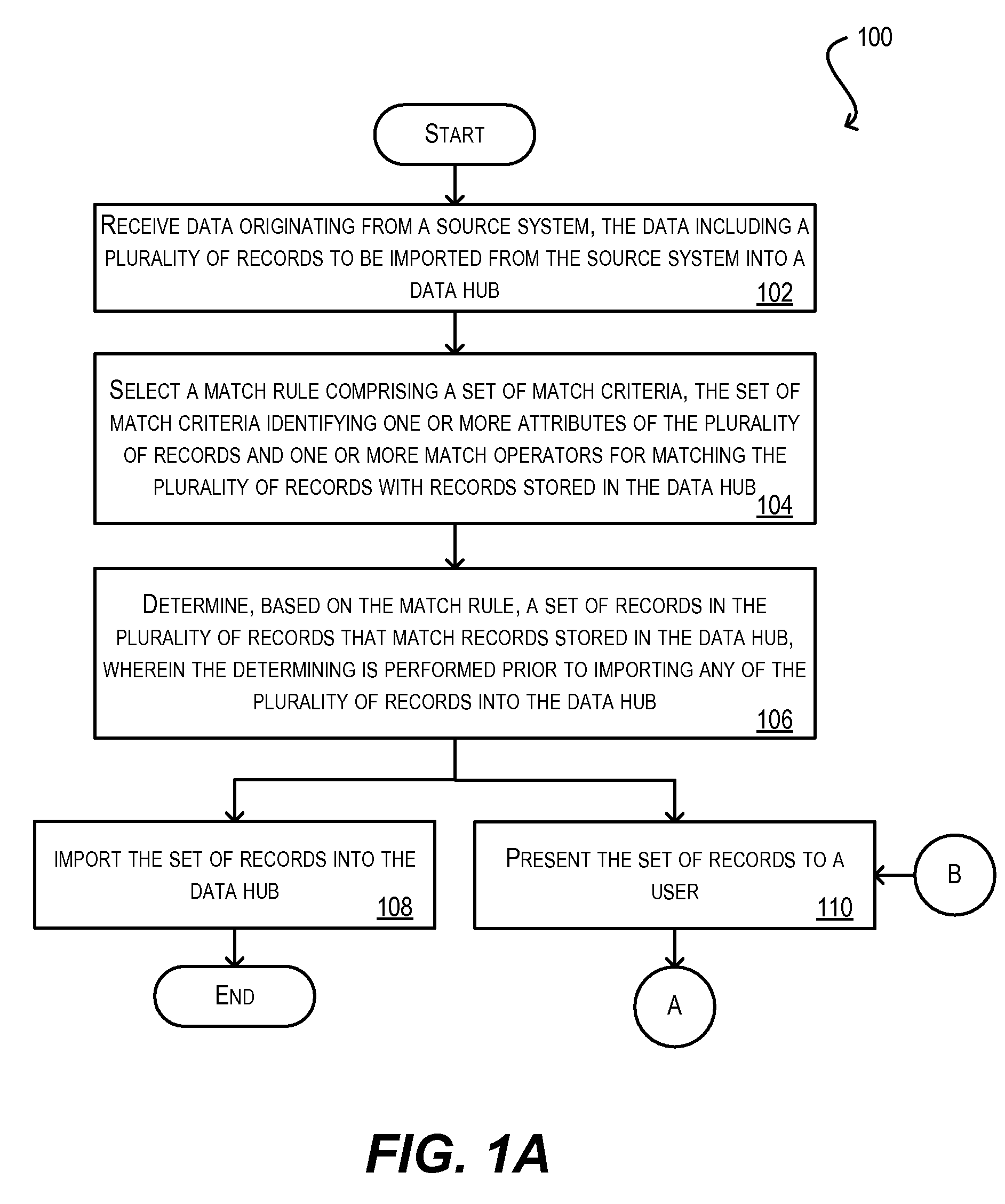
Match rules to identify duplicate records in inbound data
ActiveUS20090193046A1Digital data information retrievalDigital data processing detailsData centerMatch rule
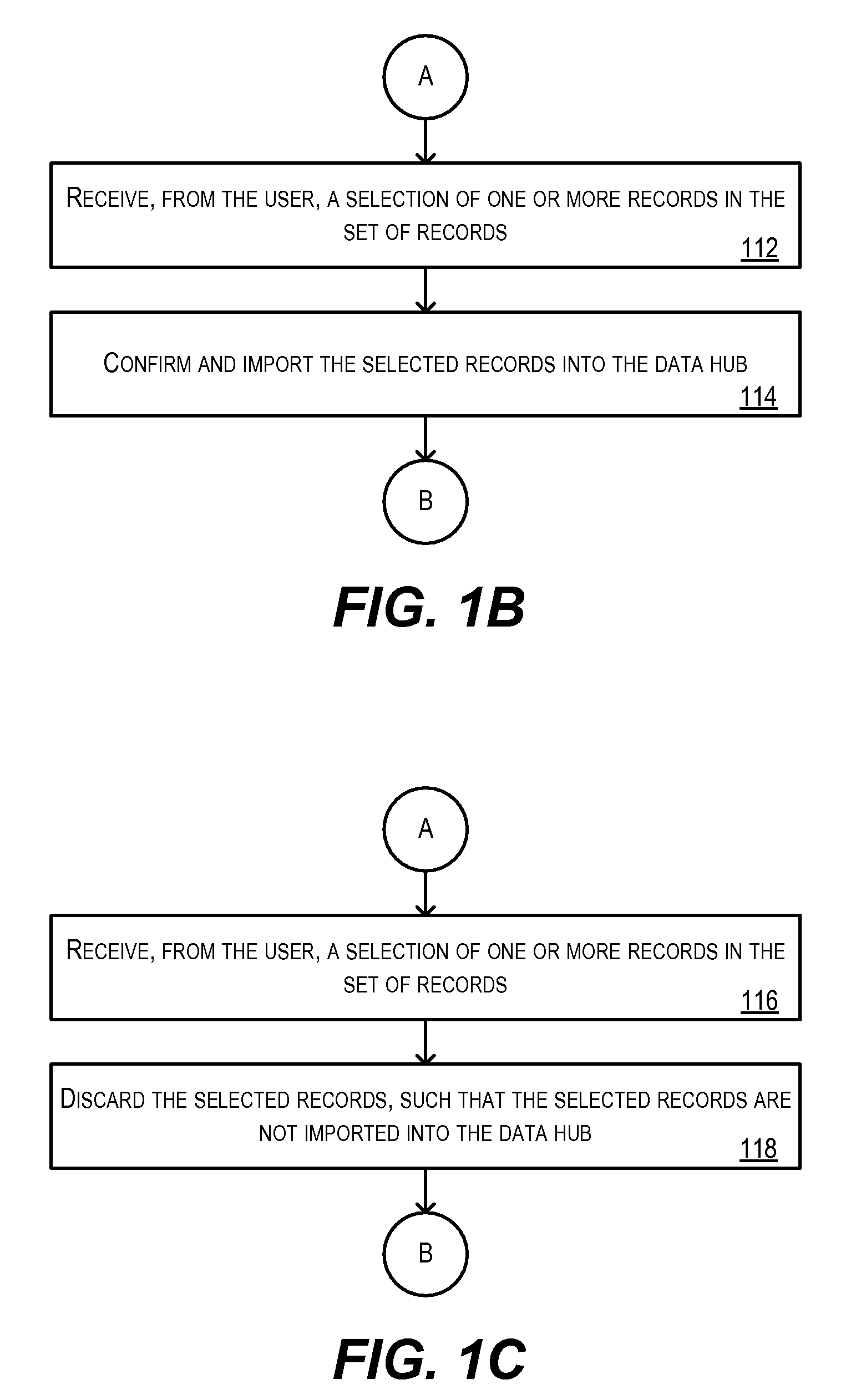
Techniques for identifying duplicate records in data to be imported into a data hub. In one set of embodiments, a batch of records to be imported into a data hub is received and a match rule for the batch of records is selected. The match rule includes a set of match criteria for matching records in the inbound batch to records stored in the data hub. A matching process is then carried out, prior to importing the batch of records, to determine whether any of the records in the batch are duplicates of records stored in the data hub. By identifying potential duplicate records before (rather than after) importation, the problems associated with prior art duplicate identification techniques are minimized or avoided. In a particular embodiment, an import workbench application comprising a plurality of user interface screens is provided for aiding a user in managing the matching process.
Owner:ORACLE INT CORP
Large-scale network monitoring oriented virtual deployment system and method
InactiveCN102437938AImprove work efficiencyImprove scalabilityData switching networksVirtualizationMatch rule
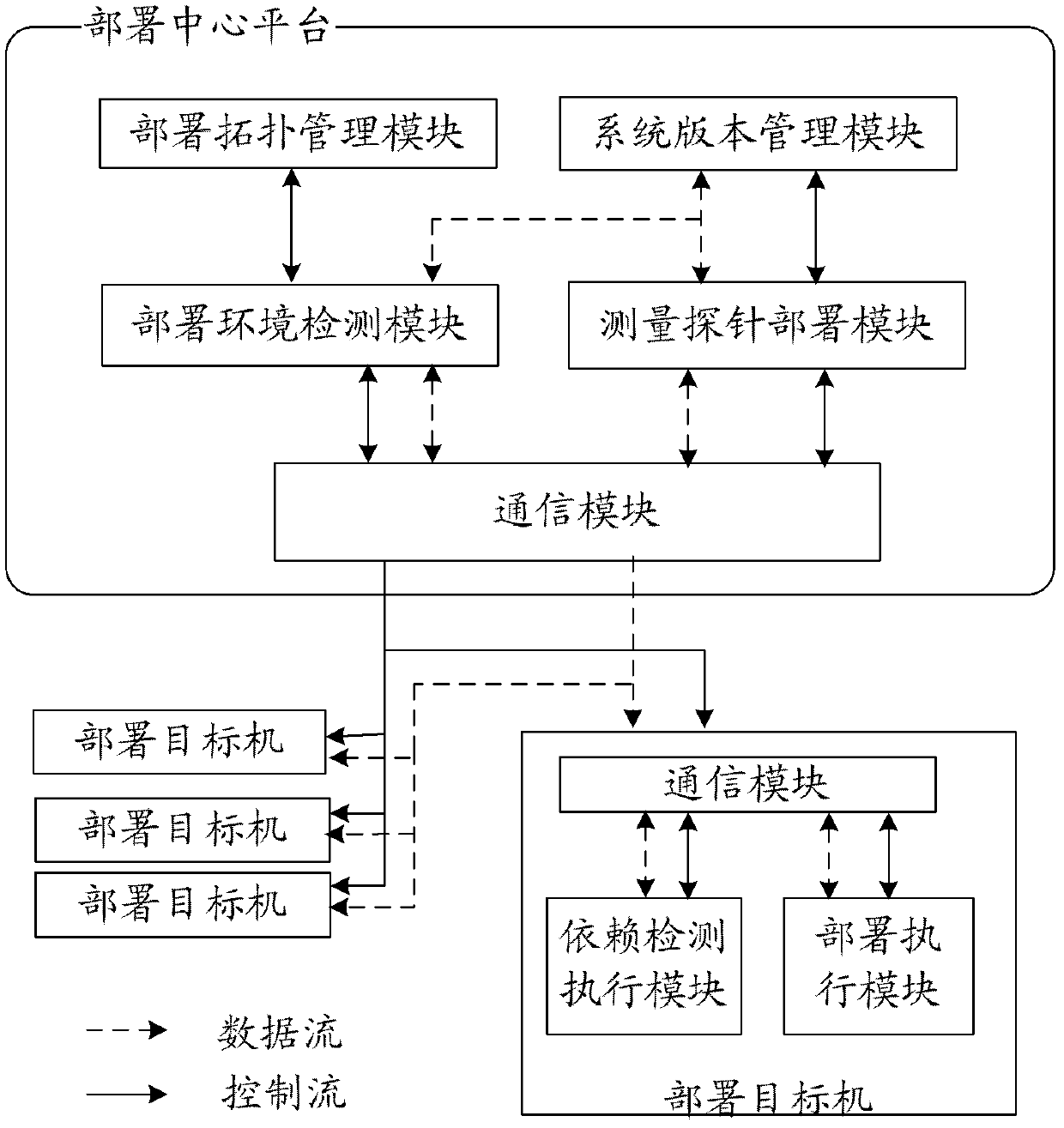
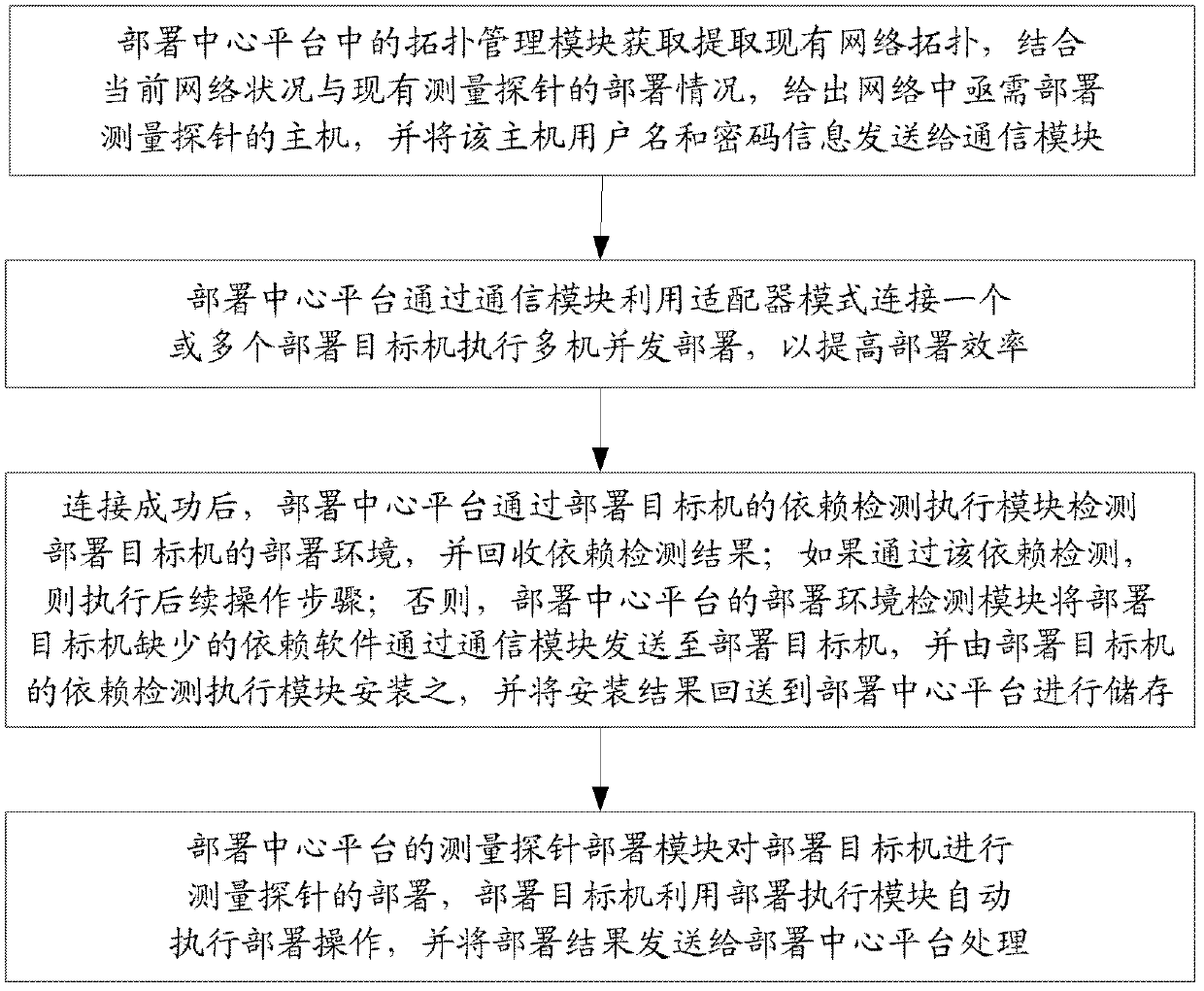
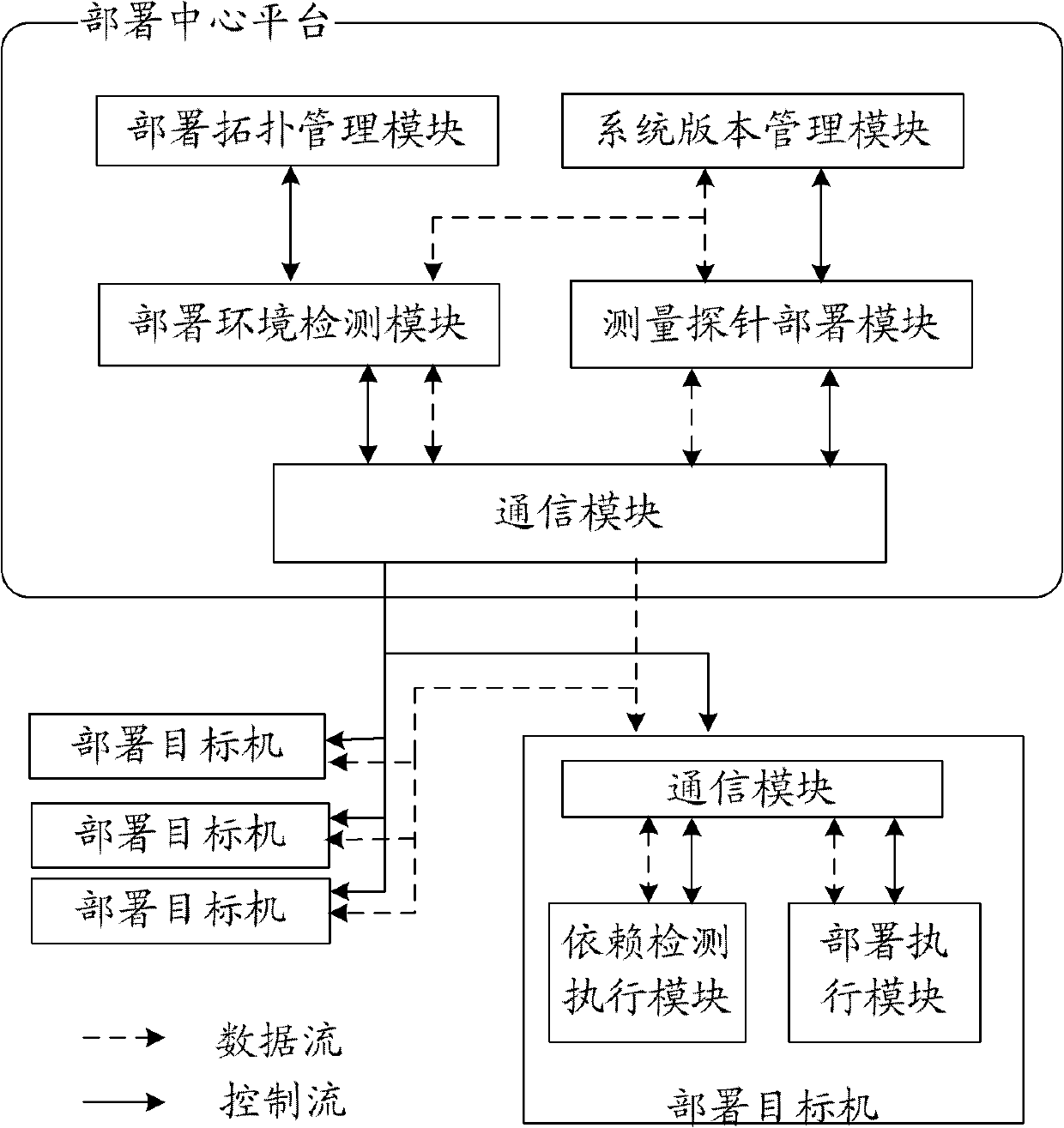
The invention discloses a large-scale network monitoring oriented virtual deployment system and method. The system is provided with a deployment center platform and a plurality of deployment target machines communicated with the deployment center platform via a network. The deployment center platform is responsible for uniformly planning and managing a topology structure of measurement probe deployment in an entire computer network, issuing a deployment task according to the existing measurement probe deployment condition and network congestion condition, and executing management and version control on the deployed measurement probes. The deployment target machines receive and execute commands from the deployment center platform, and automatically execute corresponding operations so as to enable the measurement probes to be usable in the network; and a software dependency detection mechanism and a process matching rule are respectively used for realizing the platform independency of deployment and verifying the achievement of deployment. The system and the method can be used for solving a plurality of problems, such as dependency detection for deployment environment of the target machines, upgrading and maintaining of a management system version, concurrent deployment, automatic installation and detection of the plurality of target machines, dynamic scheduling and the like, in the prior art, and have better promotion and application prospects.
Owner:BEIJING UNIV OF POSTS & TELECOMM
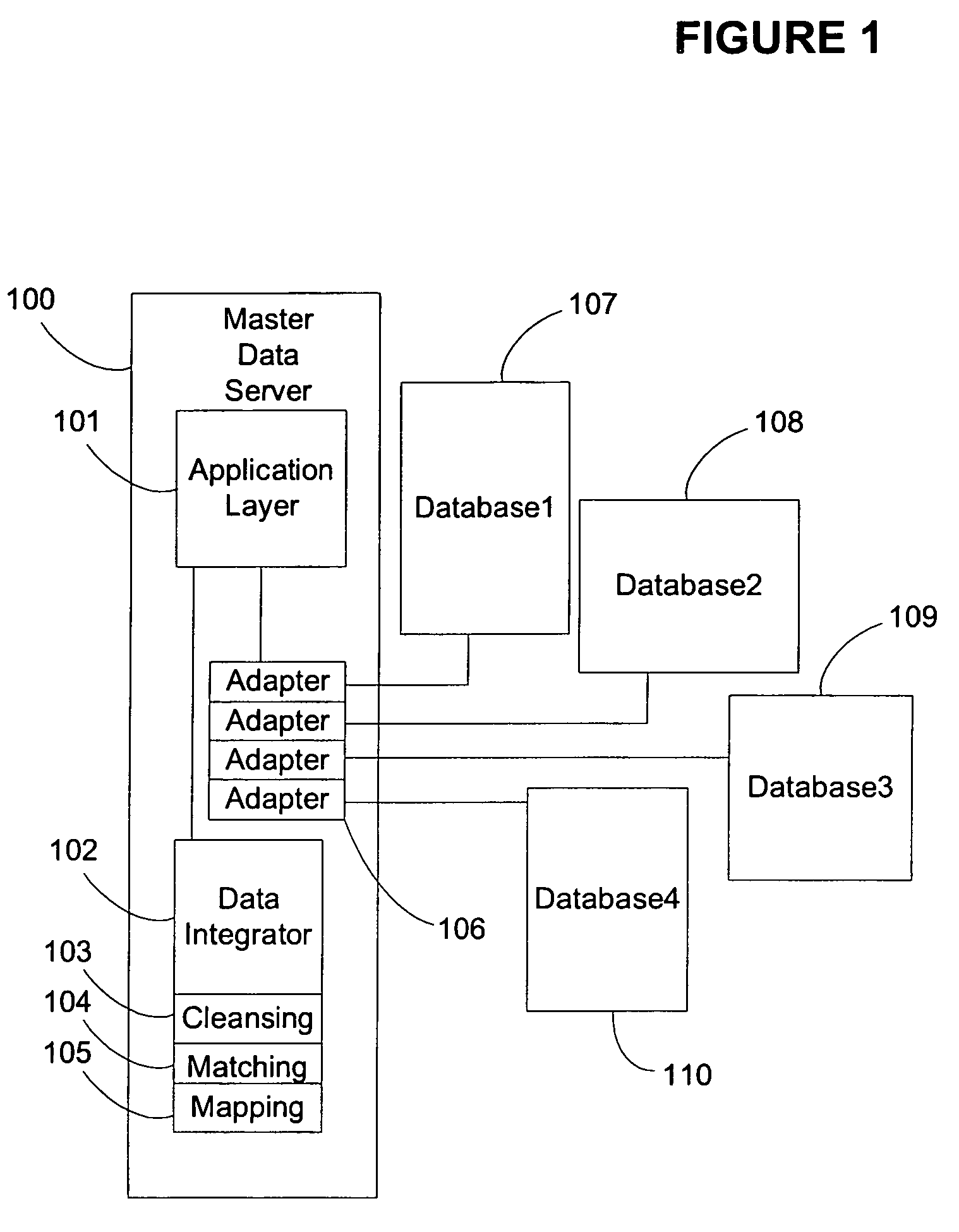
Rule-based database object matching with comparison certainty
Rule based data object matching to determine if two or more objects are similar to allow the objects to be merged into one master data object. The rules explicitly state what conditions are required to consider two or more objects equal. The certainty of the rule may be specified. Examples for the certainty are automatic, manual high, medium and low probability. For example, the certainty “automatic” specifies that the objects can be considered matches and no additional manual verification is needed. The certainty “manual low probability” specifies that there is a low probability that the objects are matches and that a manual verification is needed. Matching rules may be grouped by priority. If matches are not found, the next highest priority group of rules is processed. Hierarchical matching rules may be specified that are able to express similarity of objects considering structured objects containing sub-objects in a hierarchical manner.
Owner:REGIONAL RESOURCES LTD
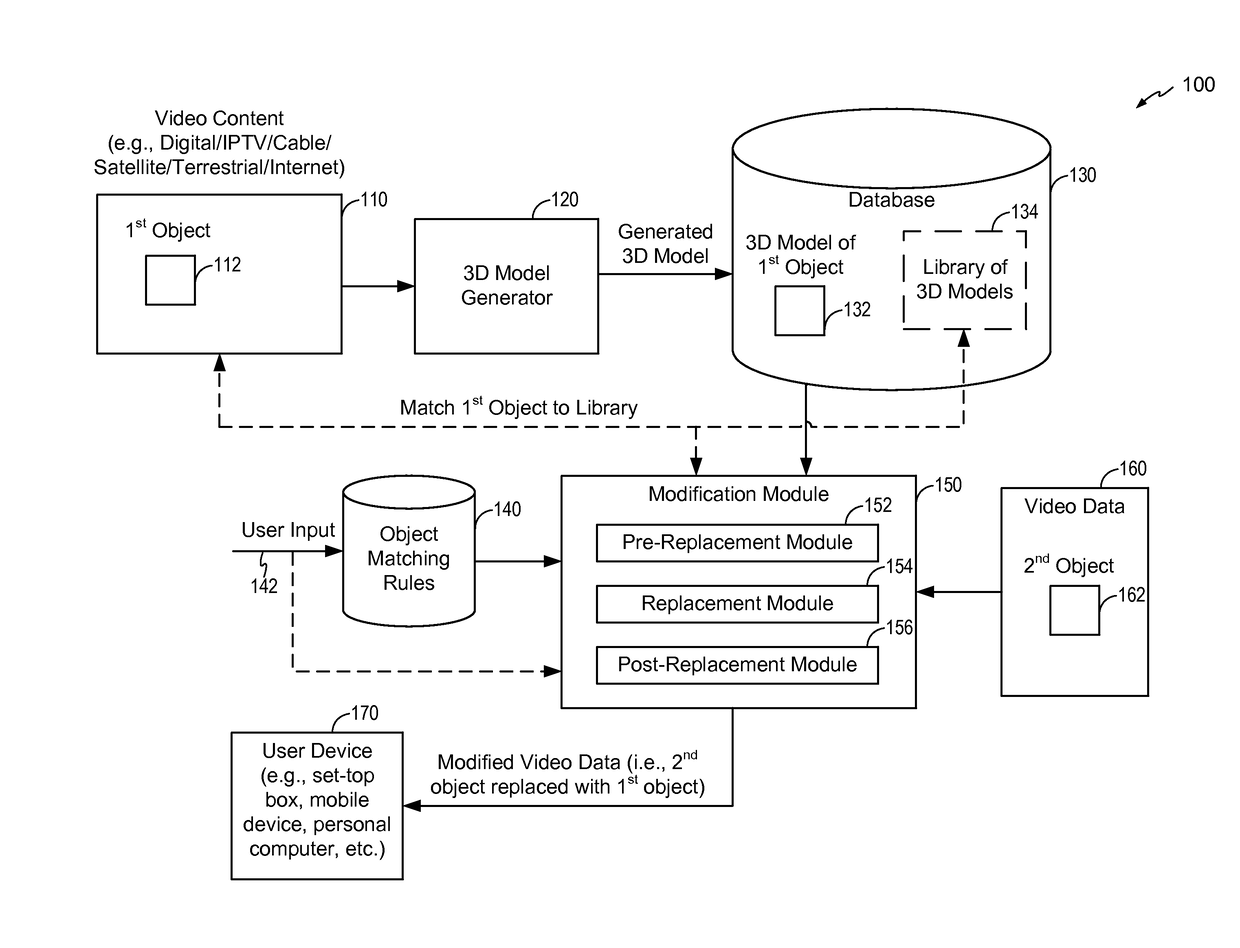
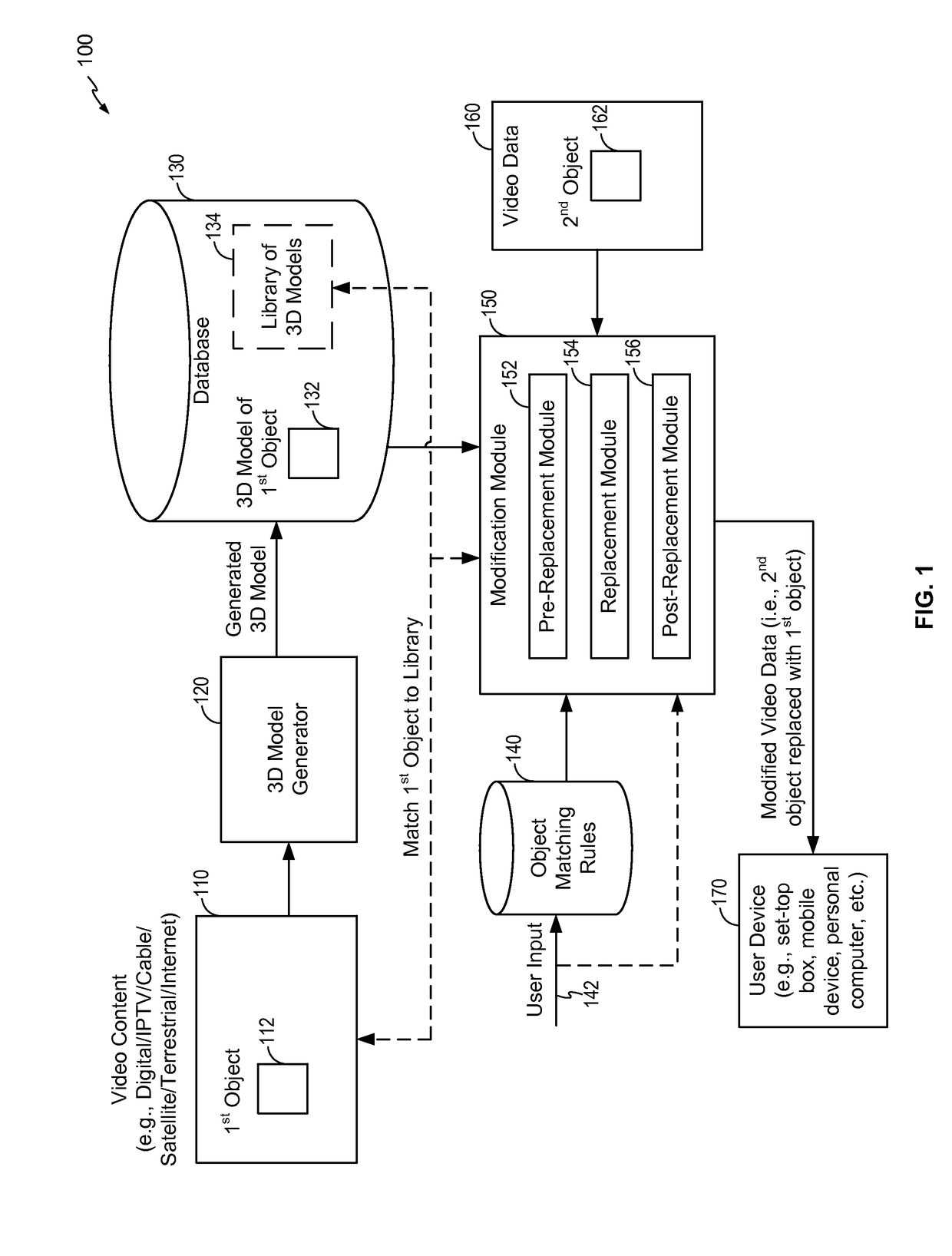
System and method to digitally replace objects in images or video
ActiveUS9626798B2Electronic editing digitised analogue information signalsSelective content distributionObject basedMatch rule
A method includes receiving video data and identifying a second object in at least one video frame of the video data. The method also includes determining whether to replace the second object in the at least one video frame with a first object based on at least one object matching rule. In response to determining that the second object is to be replaced with the first object, the method includes manipulating the three-dimensional model of the first object to generate a representation of the first object that matches at least one visual property of the second object and replacing the second object with the representation of the first object in the at least one video frame.
Owner:AT&T INTPROP I L P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com