Method for retrieving confidential information of file and judging and marking security classification based on content correlation
A technology of relevance and content, which is applied in the fields of file confidential content retrieval, classification judgment and labeling based on content correlation, can solve the problems of no way to involve confidential content, low accuracy, and hidden dangers of confidential work, so as to prevent The effect of random setting of secrets, reducing workload and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
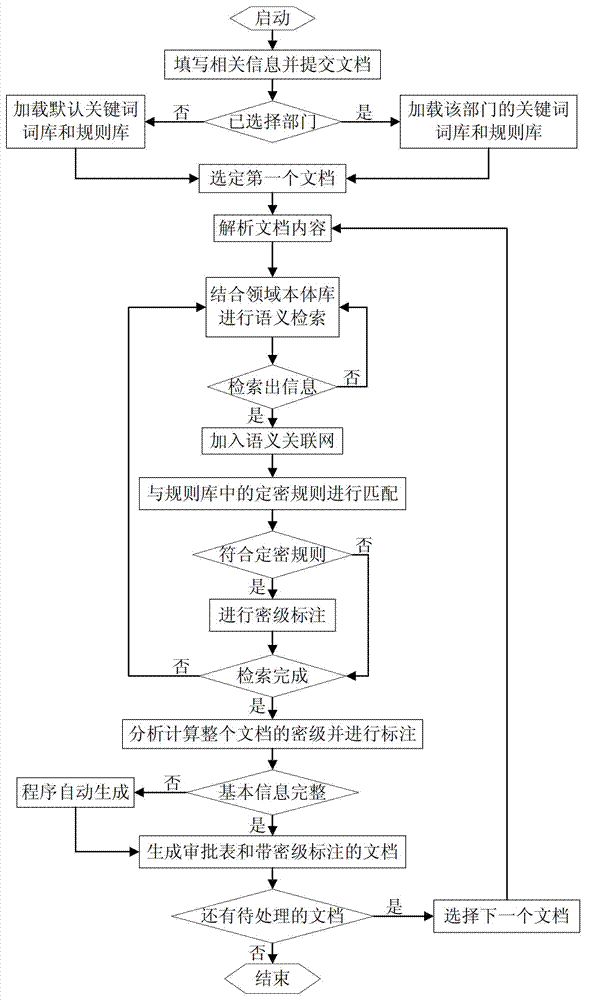
[0038] refer to figure 1 , the specific steps of the process of retrieval, classification determination and labeling of classified content of documents based on content correlation are described as follows:
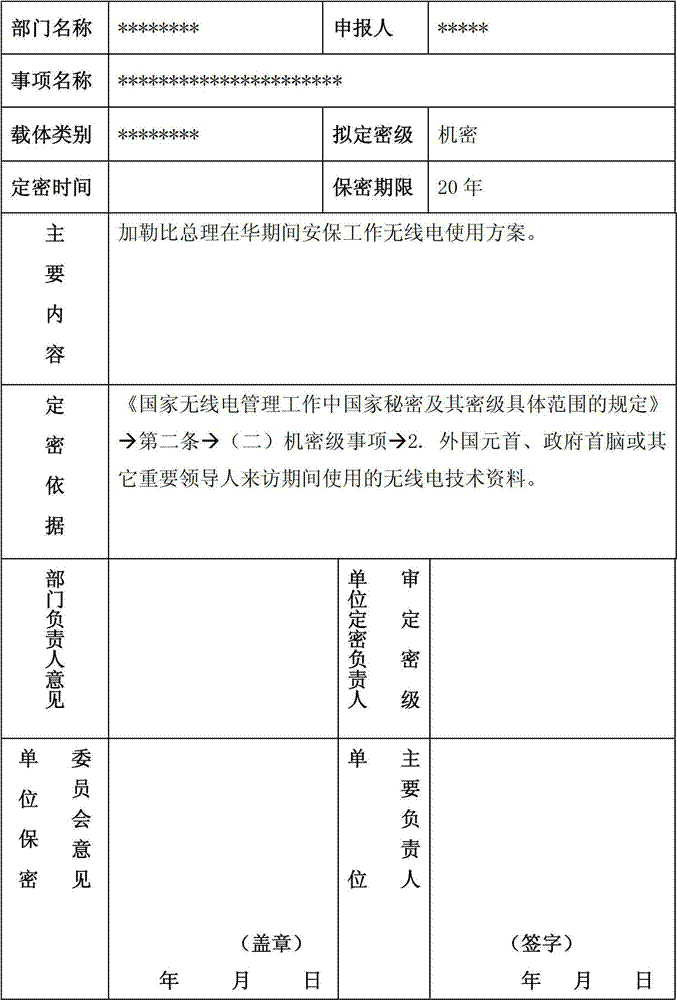
[0039] A. Loading steps: The user fills in relevant information, such as department name, confidentiality person, item name, etc., and submits the document. Among them, the confidentiality person is a required item, and other items can be automatically generated by the system, according to the department filled by the user The information loads the classified keywords and matching rule base, ontology base and confidentiality rule base within the scope. If the user does not fill in the department information, the default secret-related keywords and matching rule base, ontology base and confidentiality rule base will be loaded.
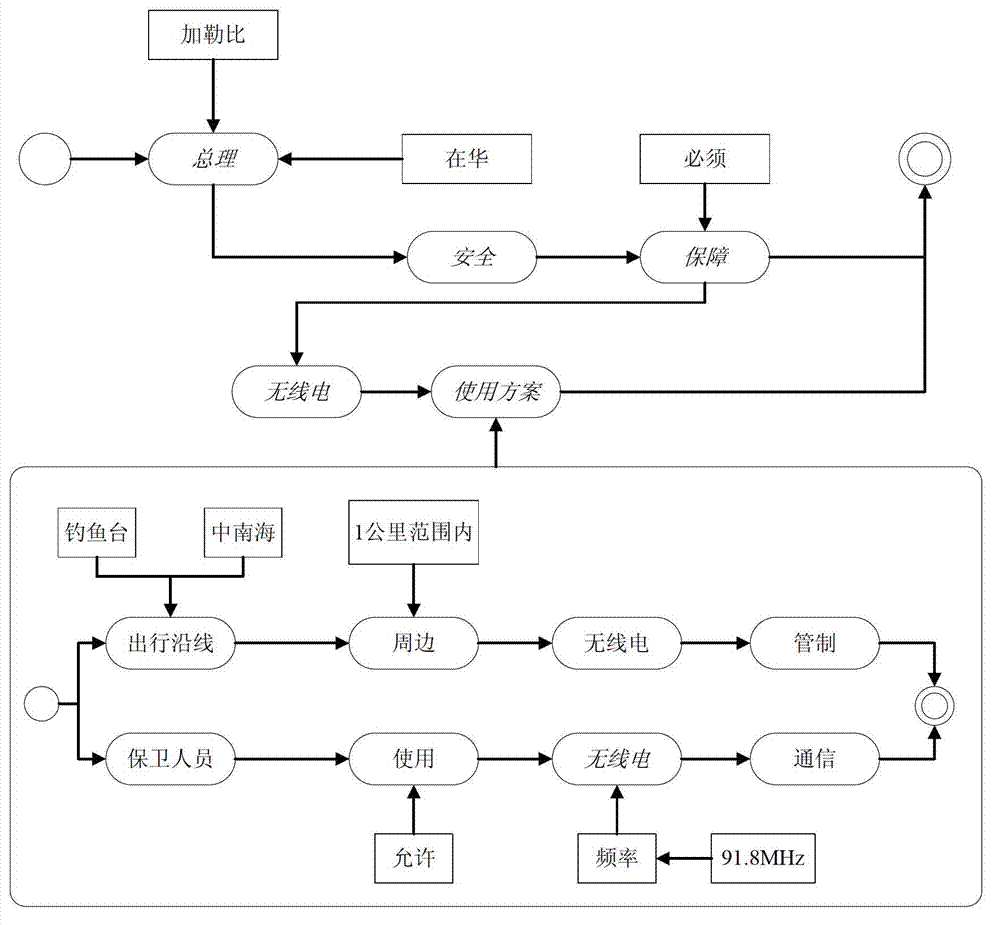
[0040] B. Parsing step: Segment the submitted document, and parse out the hidden information in the pictures, videos, and audio contained in the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com