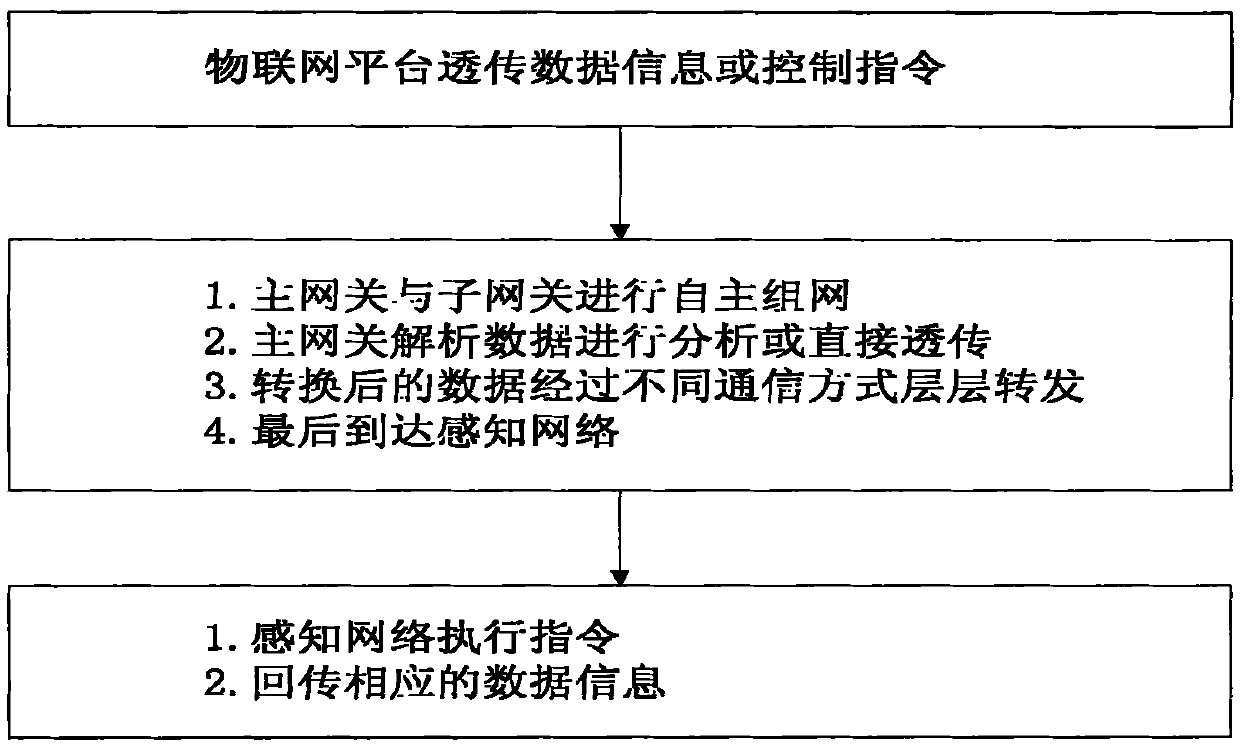
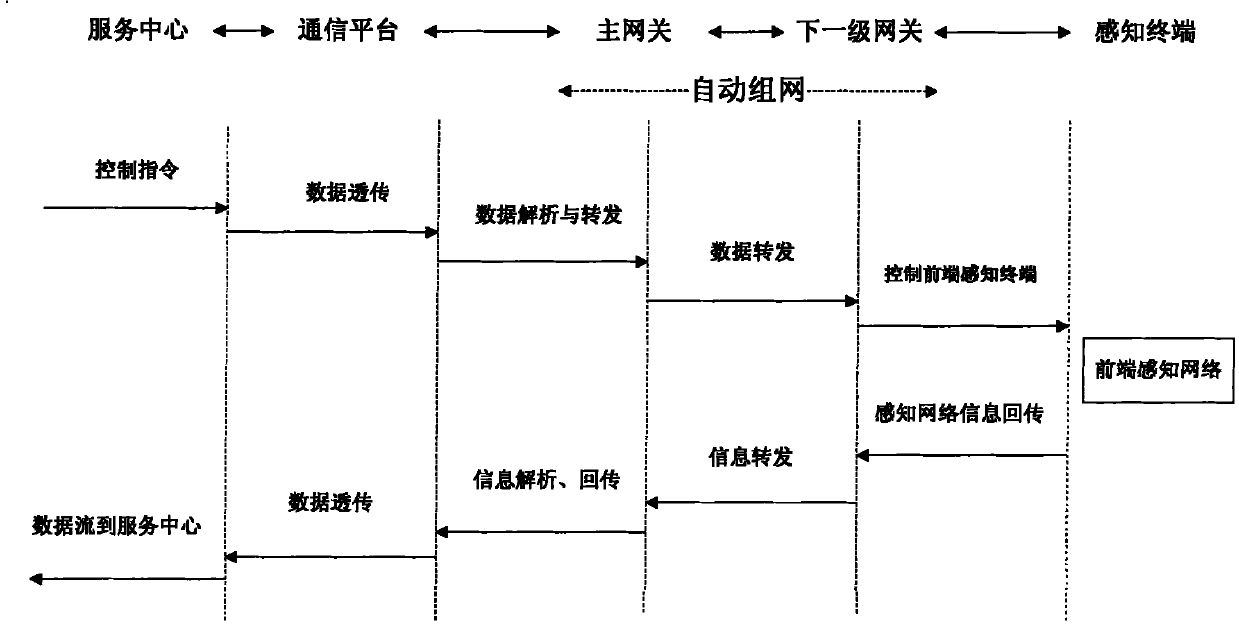
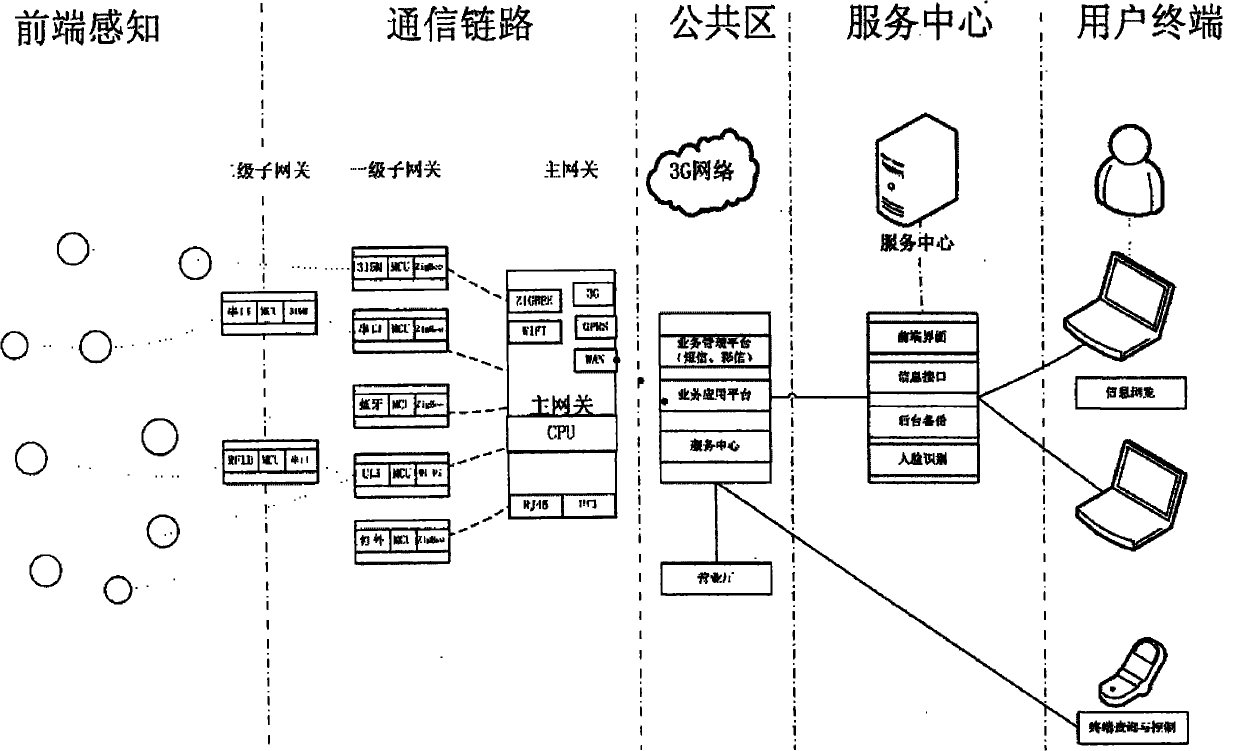
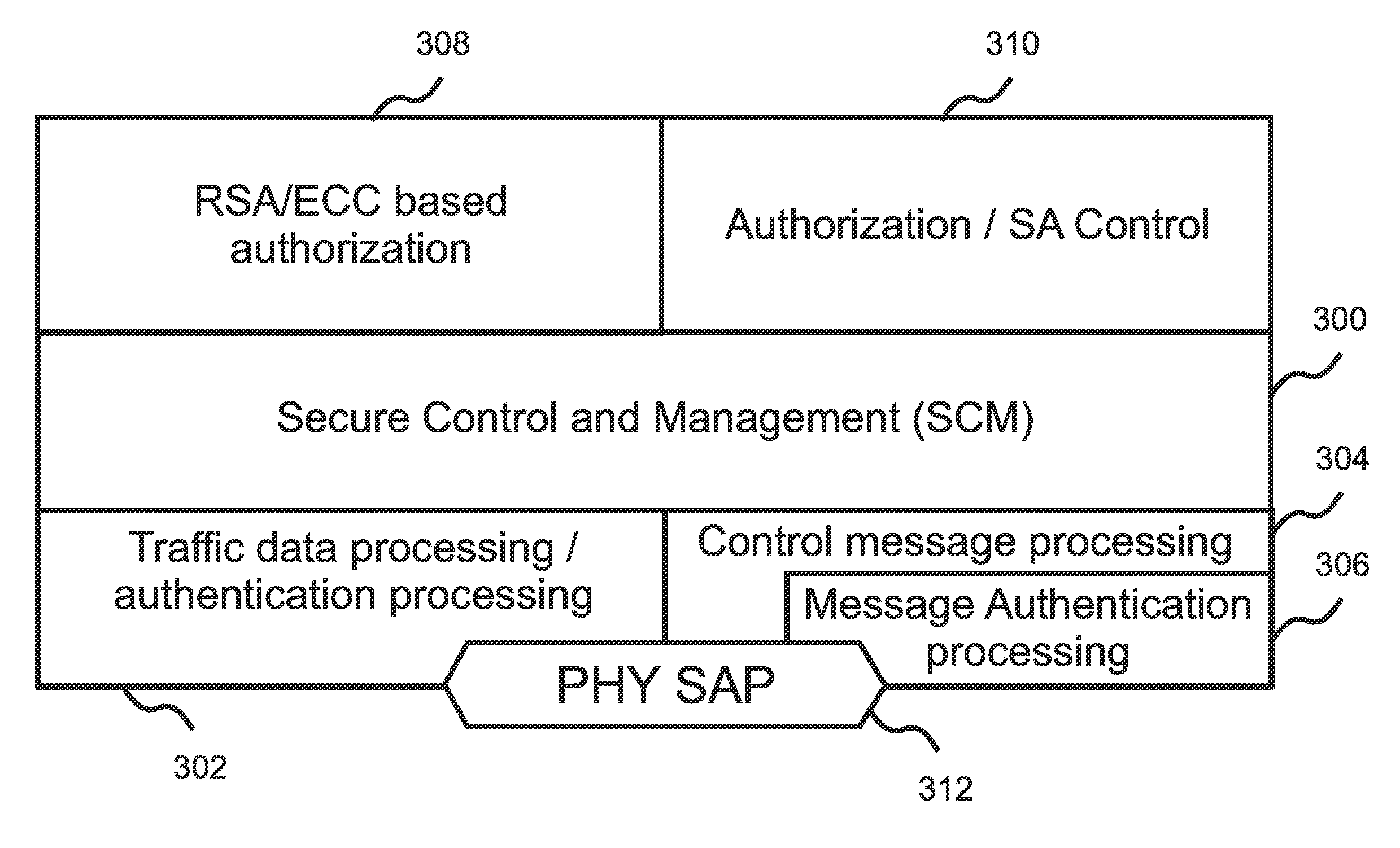
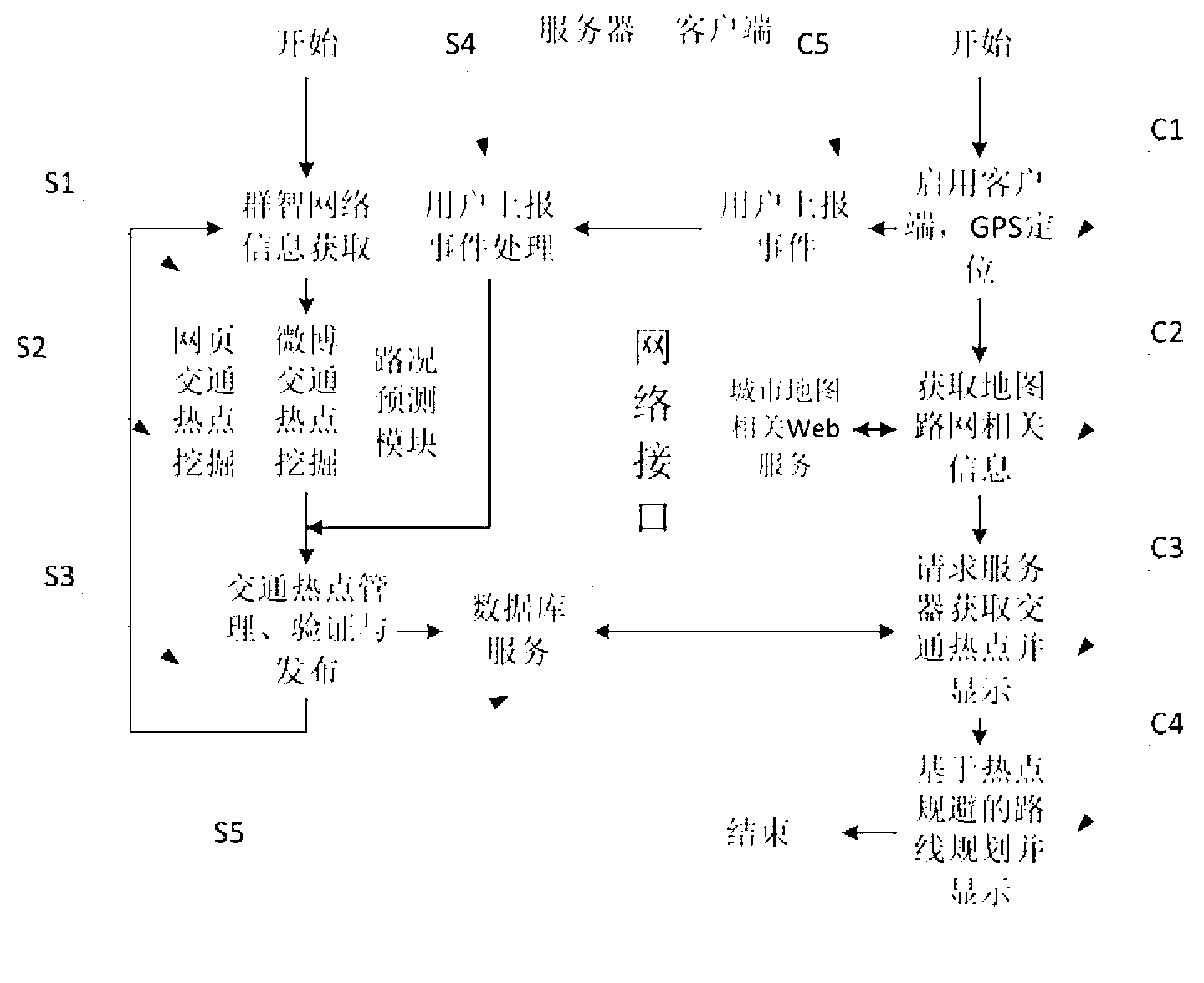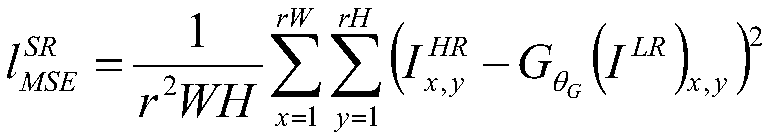Patents
Literature
1011 results about "Cognitive network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
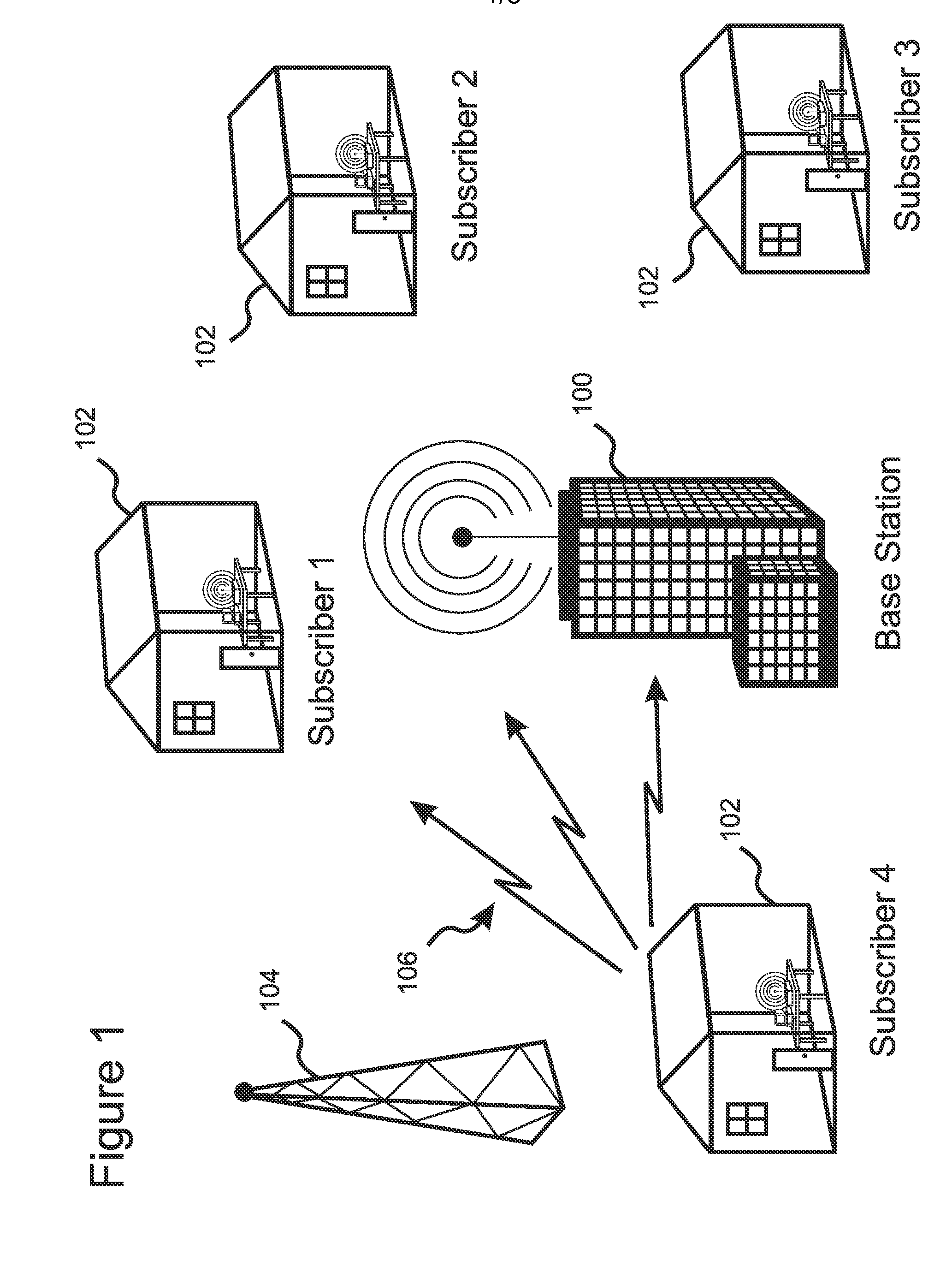
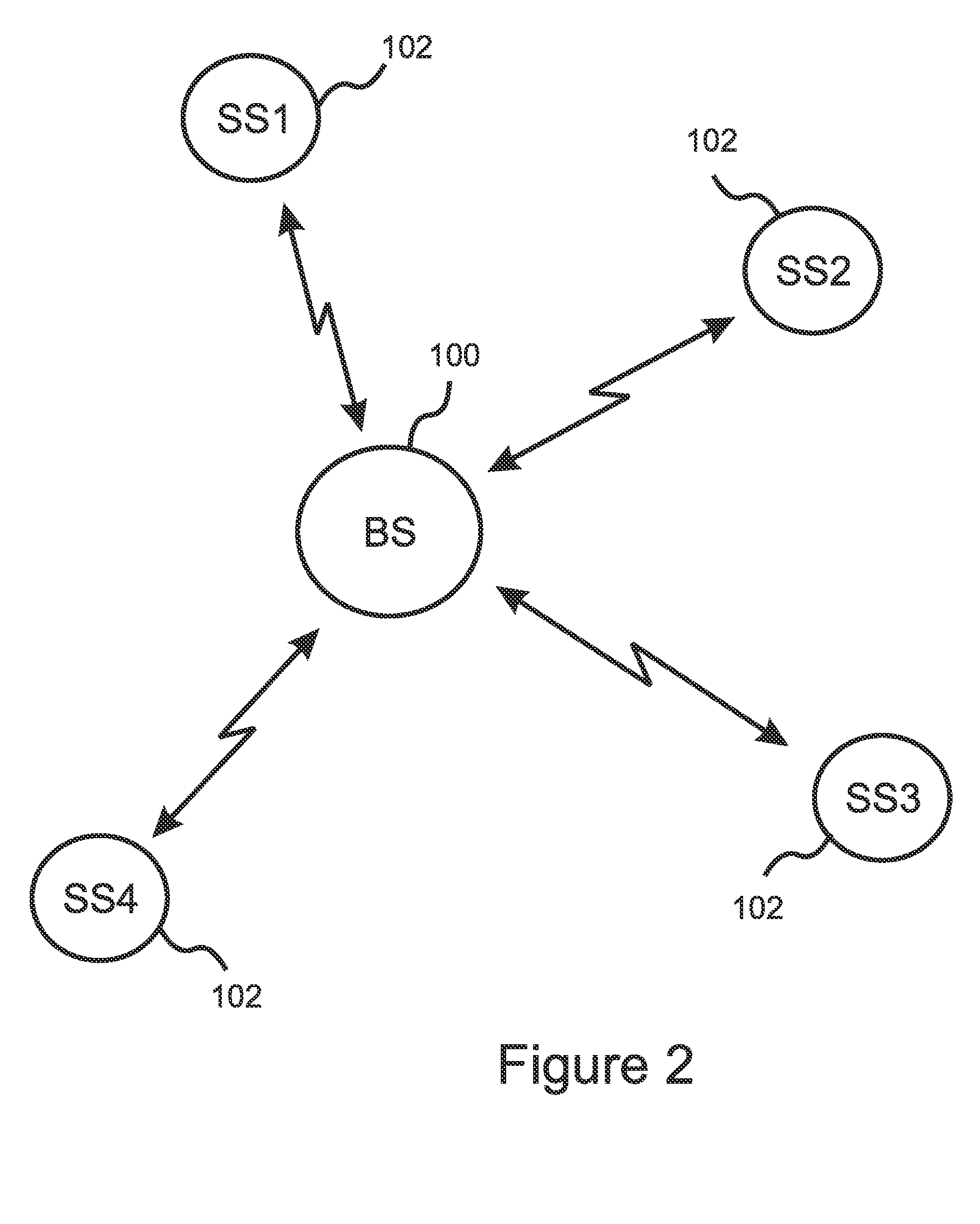
In communication networks, cognitive network (CN) is a new type of data network that makes use of cutting edge technology from several research areas (i.e. machine learning, knowledge representation, computer network, network management) to solve some problems current networks are faced with. Cognitive network is different from cognitive radio (CR) as it covers all the layers of the OSI model (not only layers 1 and 2 as with CR ).
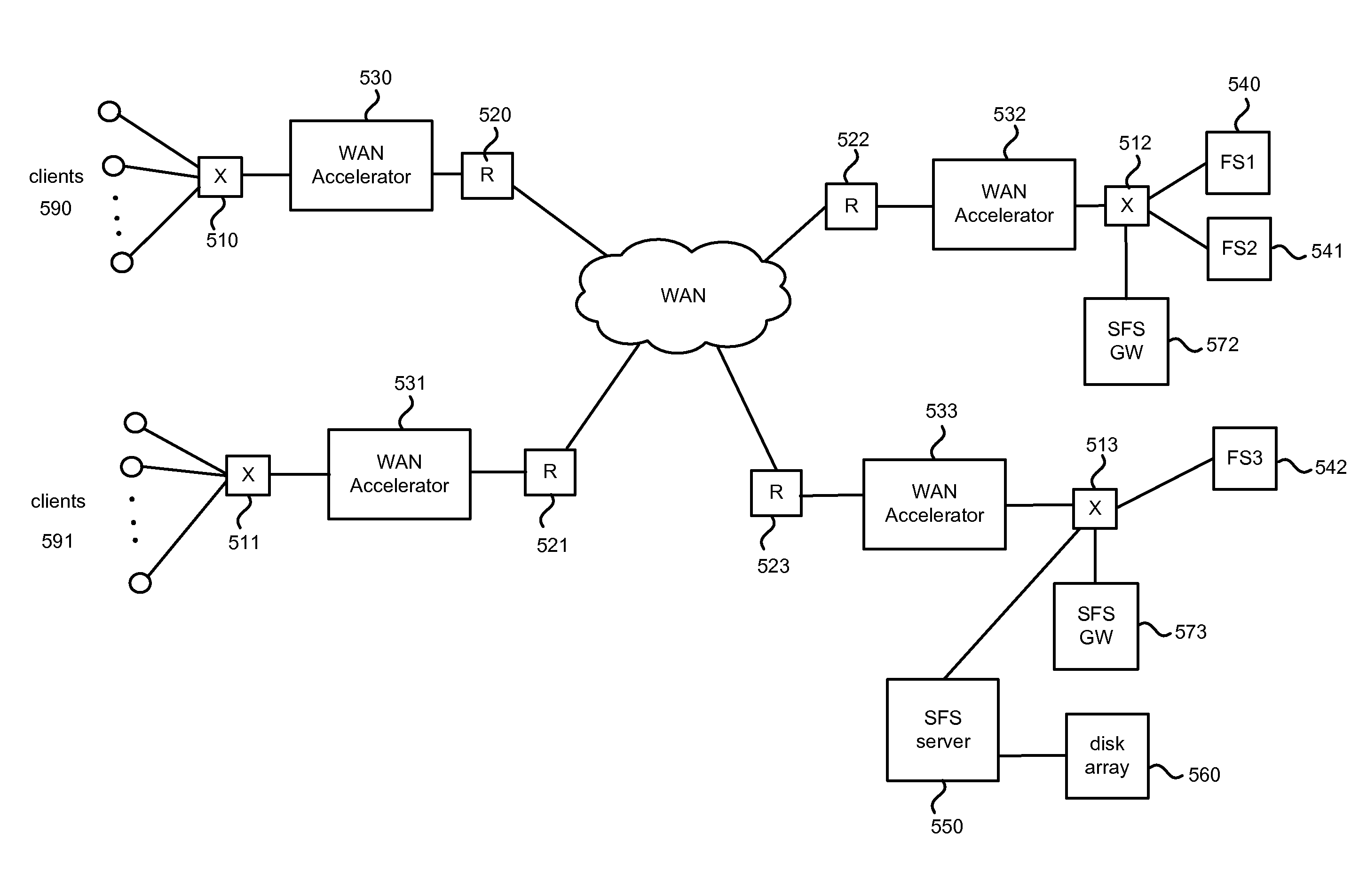
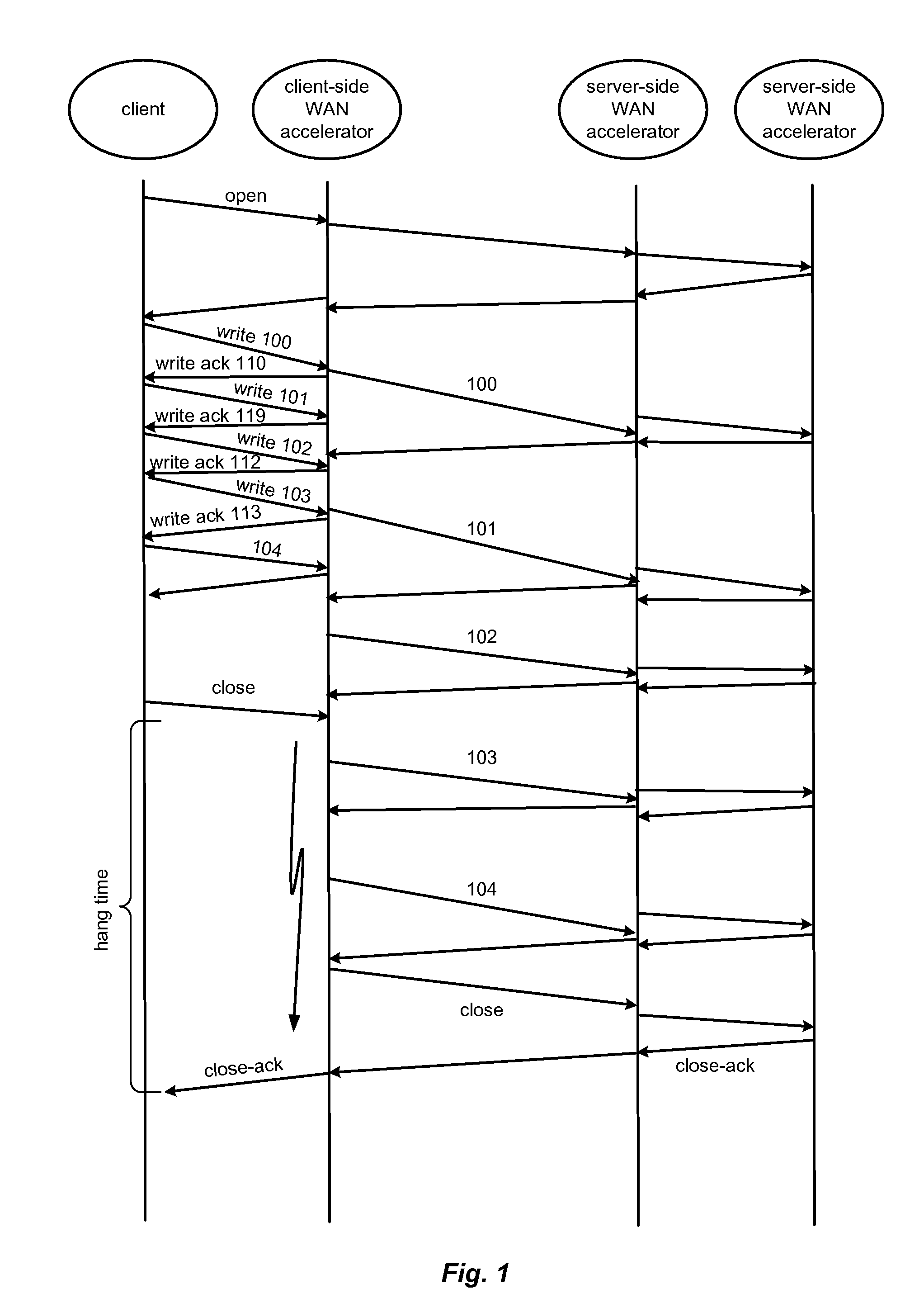
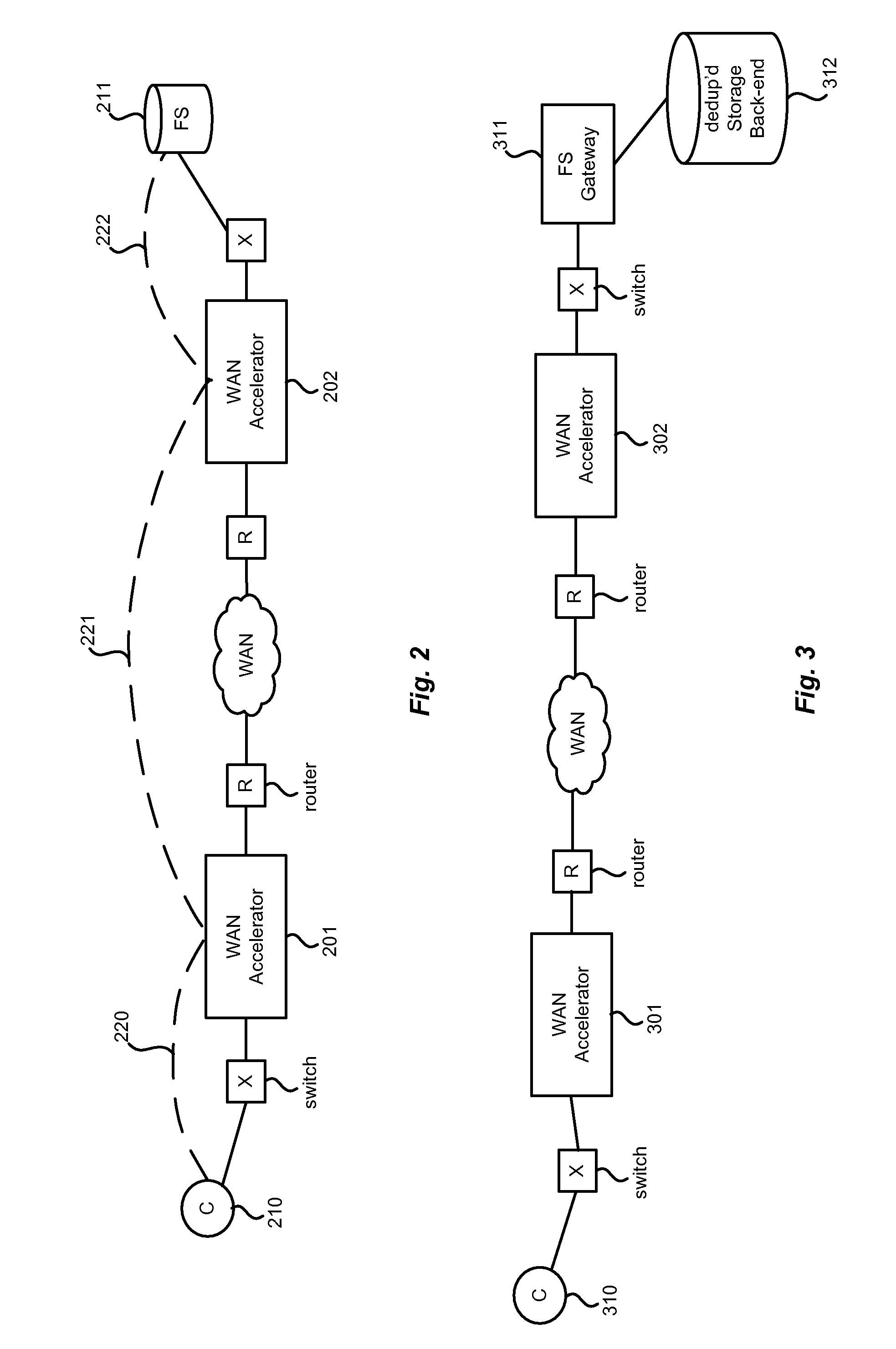
Hybrid segment-oriented file server and wan accelerator
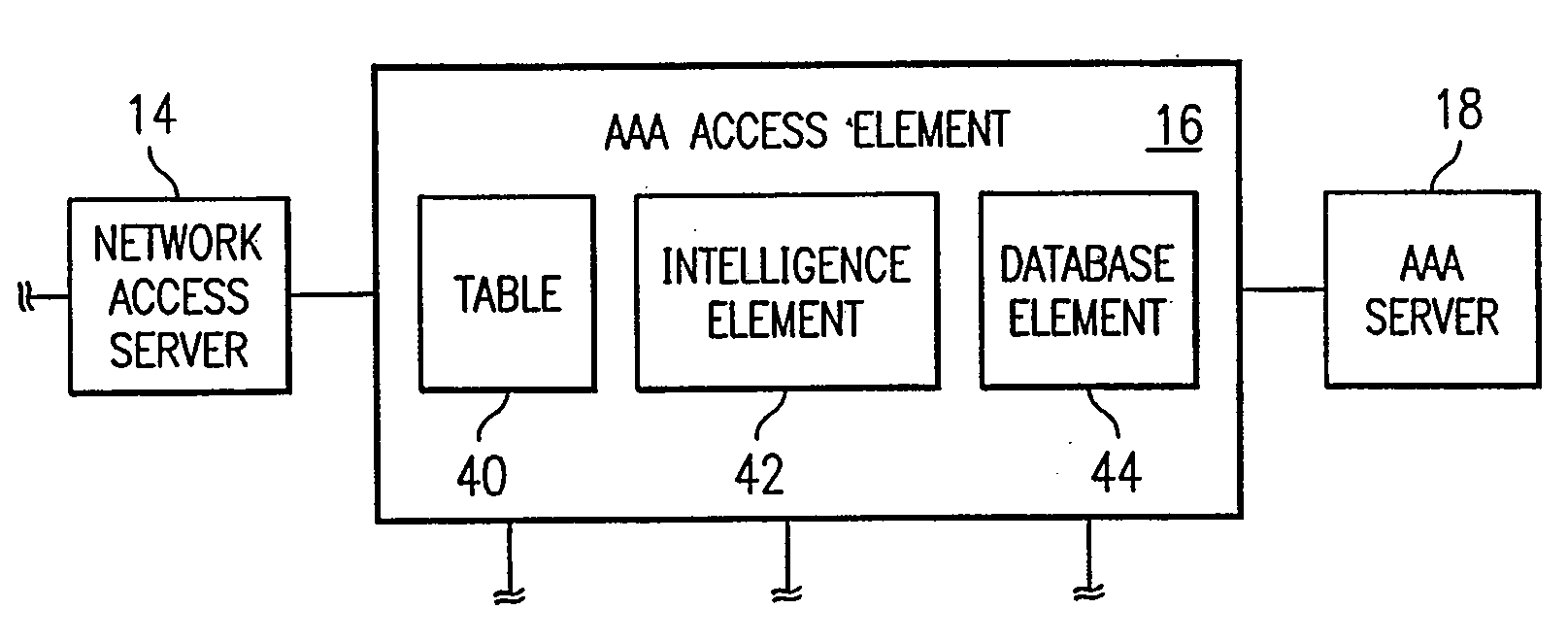
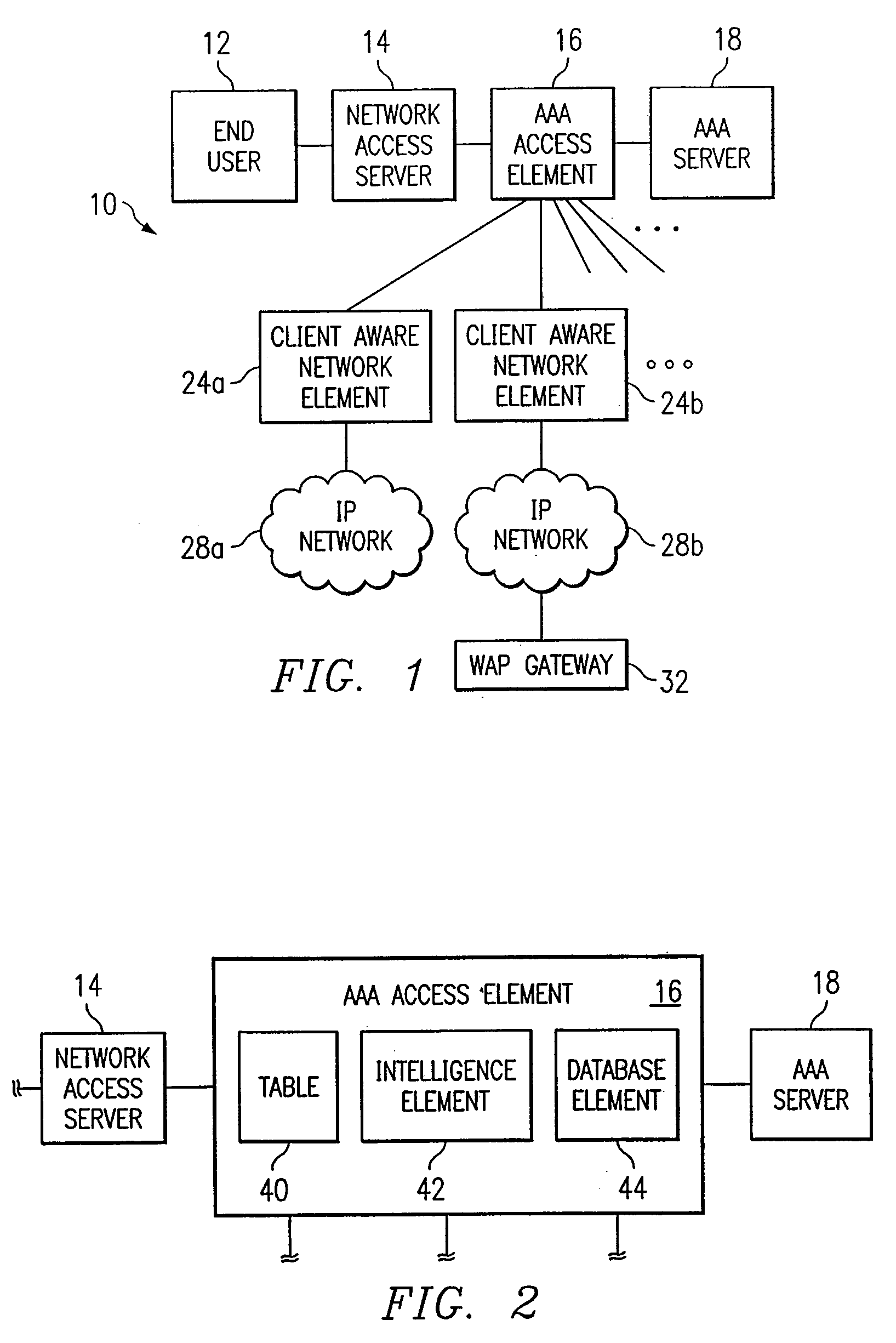
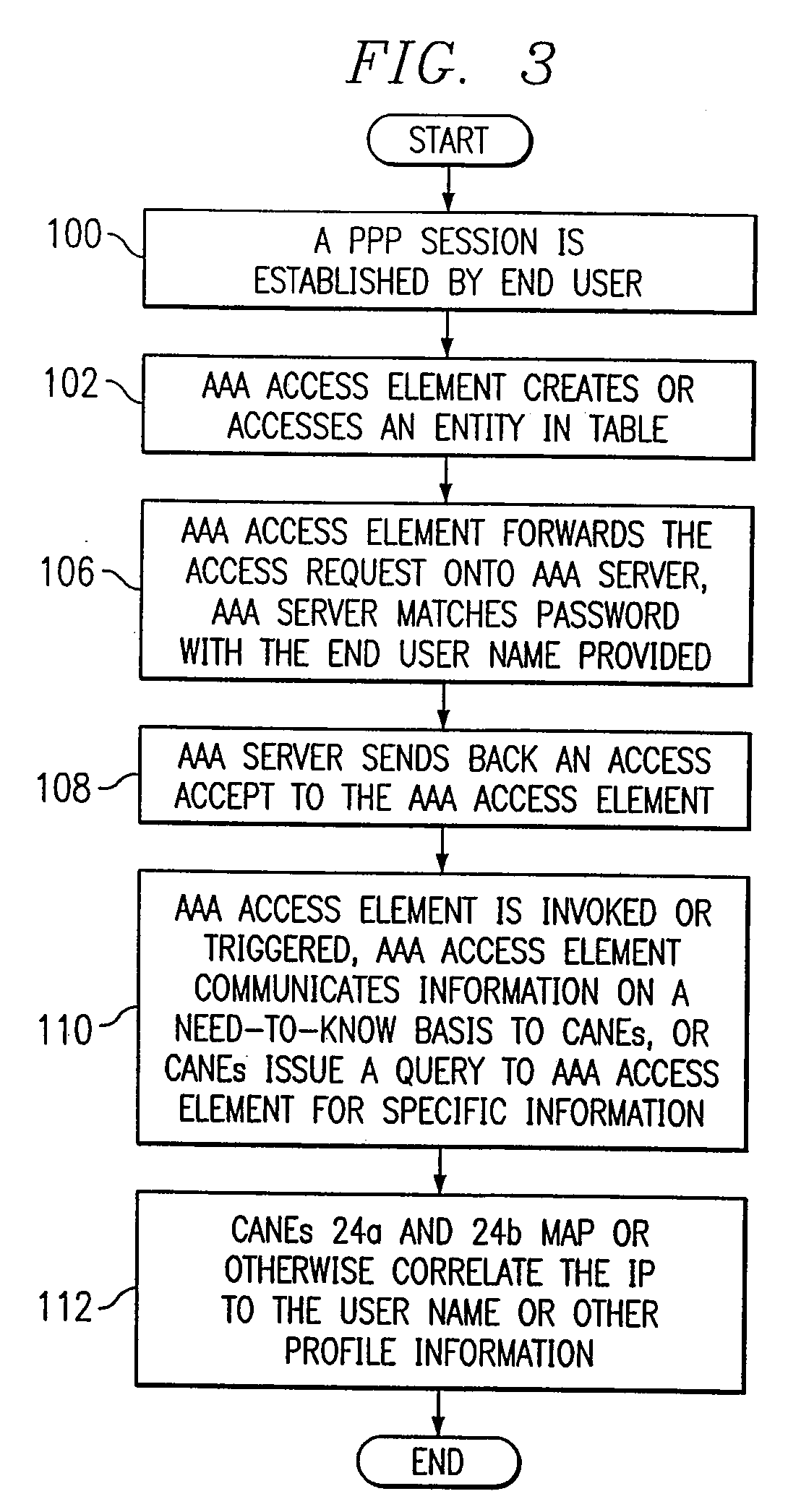
ActiveUS20080281908A1Error detection/correctionComputer security arrangementsFile serverProtocol for Carrying Authentication for Network Access
In a network including WAN accelerators and segment-oriented file servers, a method comprises responding to a client request to manipulate a file via a network file protocol by receiving a first request at a first WAN accelerator, wherein the request is a request to open a file located at a file server that is a segment-oriented file server, sending a local request for the file, corresponding to the first request, from the WAN accelerator to the file server, using a segment-aware network request protocol, returning at least a portion of the requested file in the form of a representation of a data map corresponding to the at least a portion of the requested file stored on the file server and using a data map for reconstruction of the requested file.
Owner:RIVERBED TECH LLC
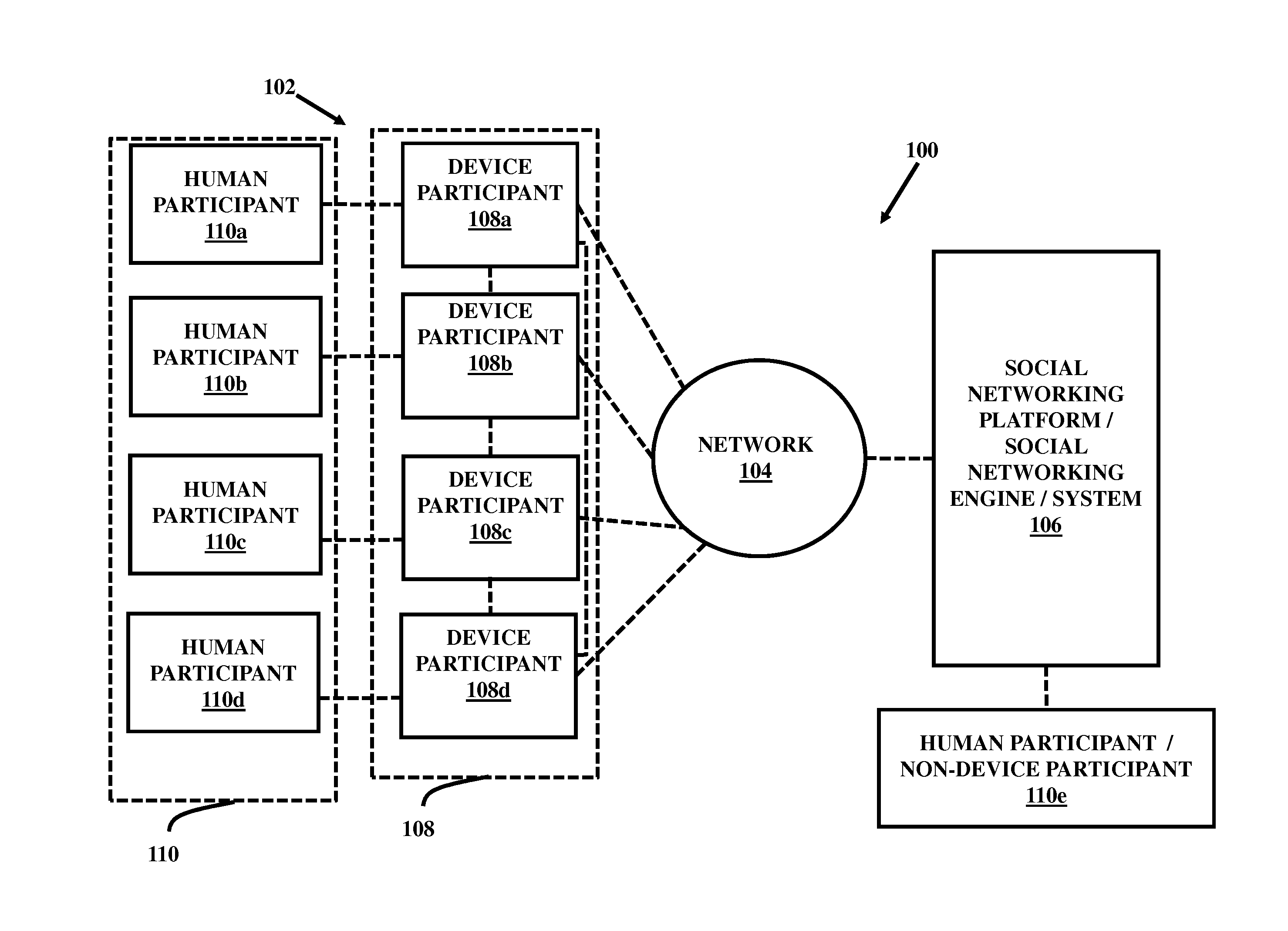
Integration of devices through a social networking platform
ActiveUS20140164519A1Near-field transmissionMedical equipmentSocial network serviceIntegration appliance
A system and method for providing a social networking service to a plurality of devices. A social networking server for facilitating social information exchange among the plurality of devices through a socially aware network. A social profiles manager is coupled to the social networking server that creates and manages individual centric profiles of the plurality of devices. The individual centric profiles of the plurality of devices are social representation of individual devices within the socially aware network. The plurality of devices are identifiable by other participants and the social networking server through their social profiles.
Owner:INTELLECTUAL FRONTIERS LLC
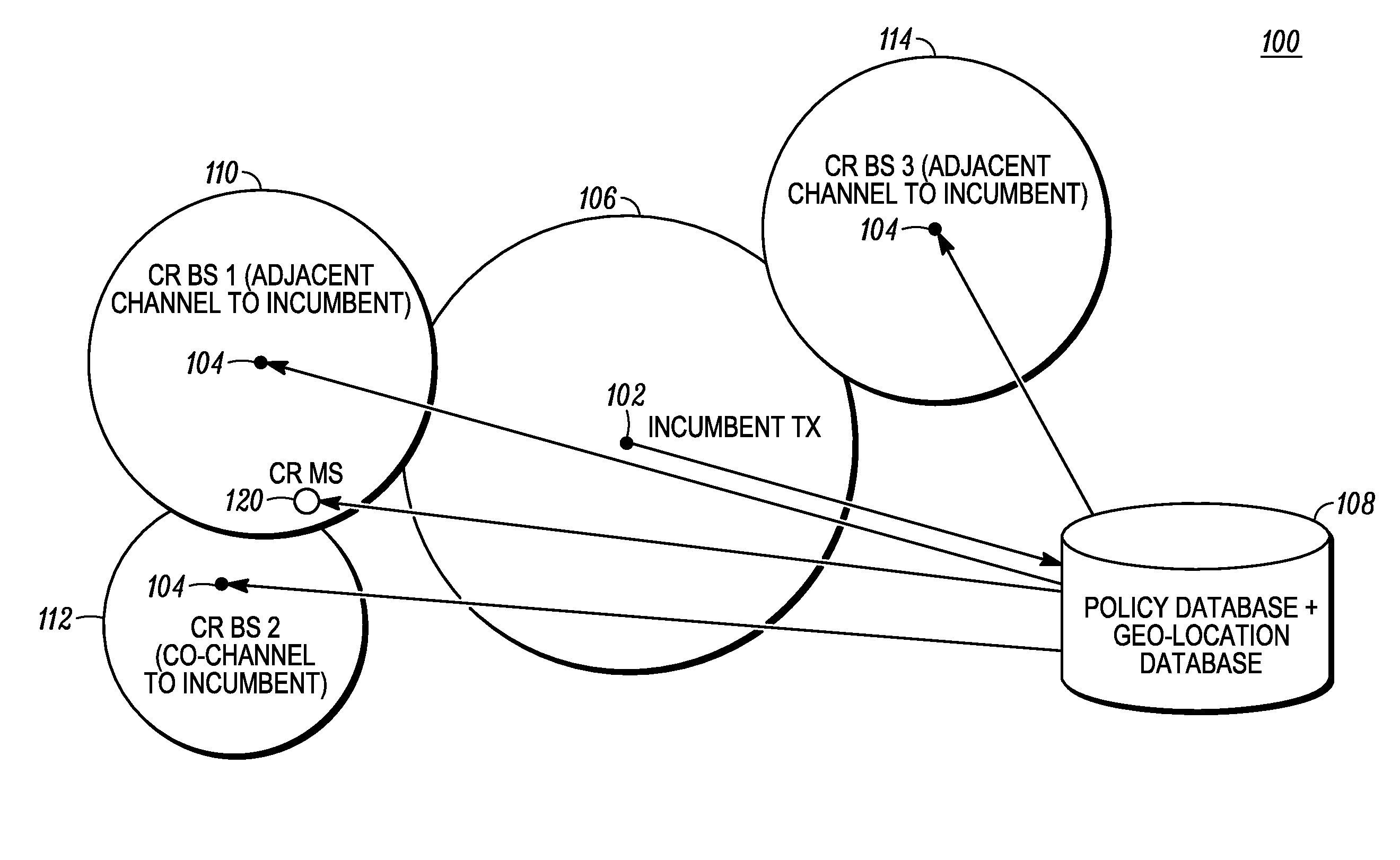
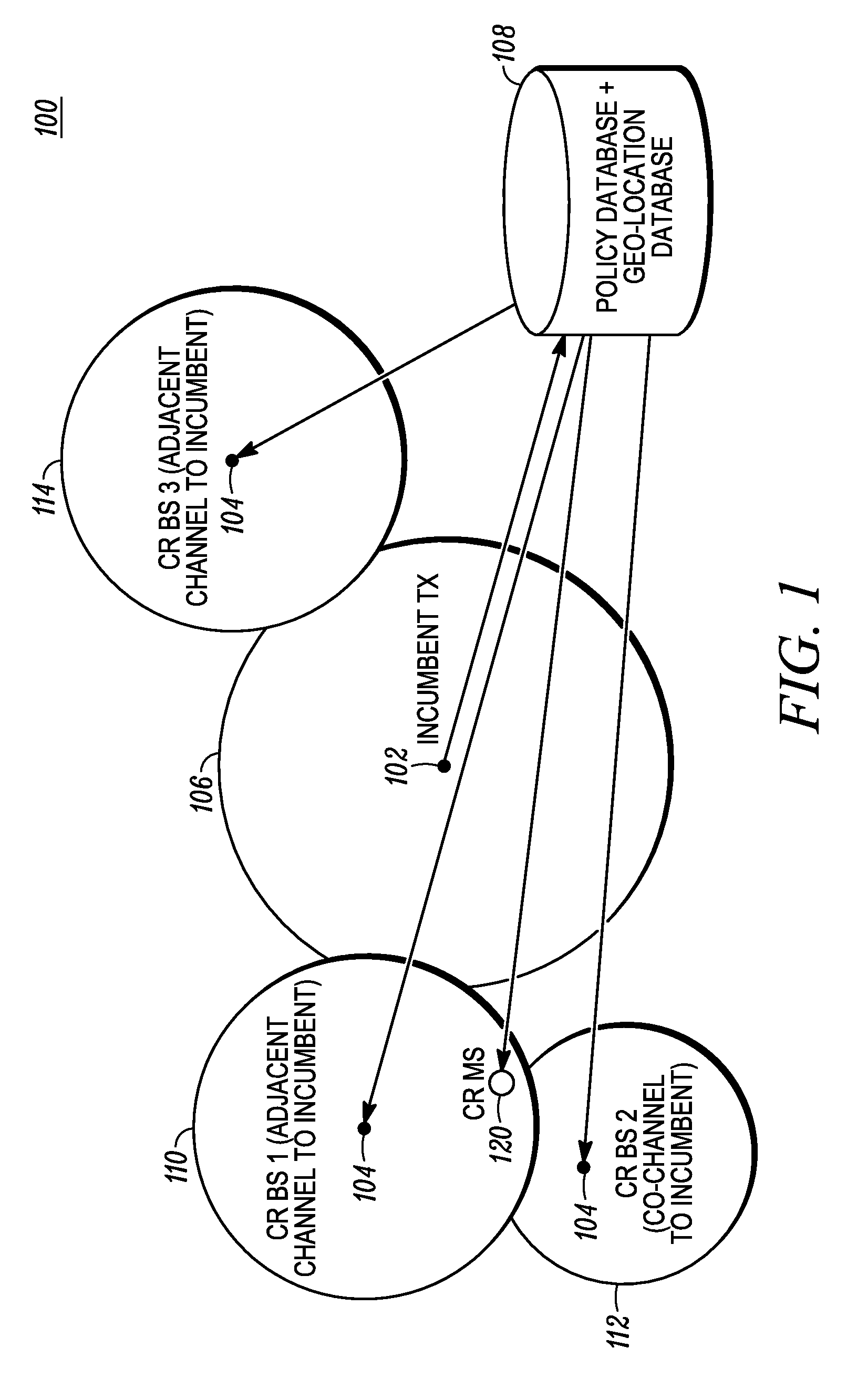
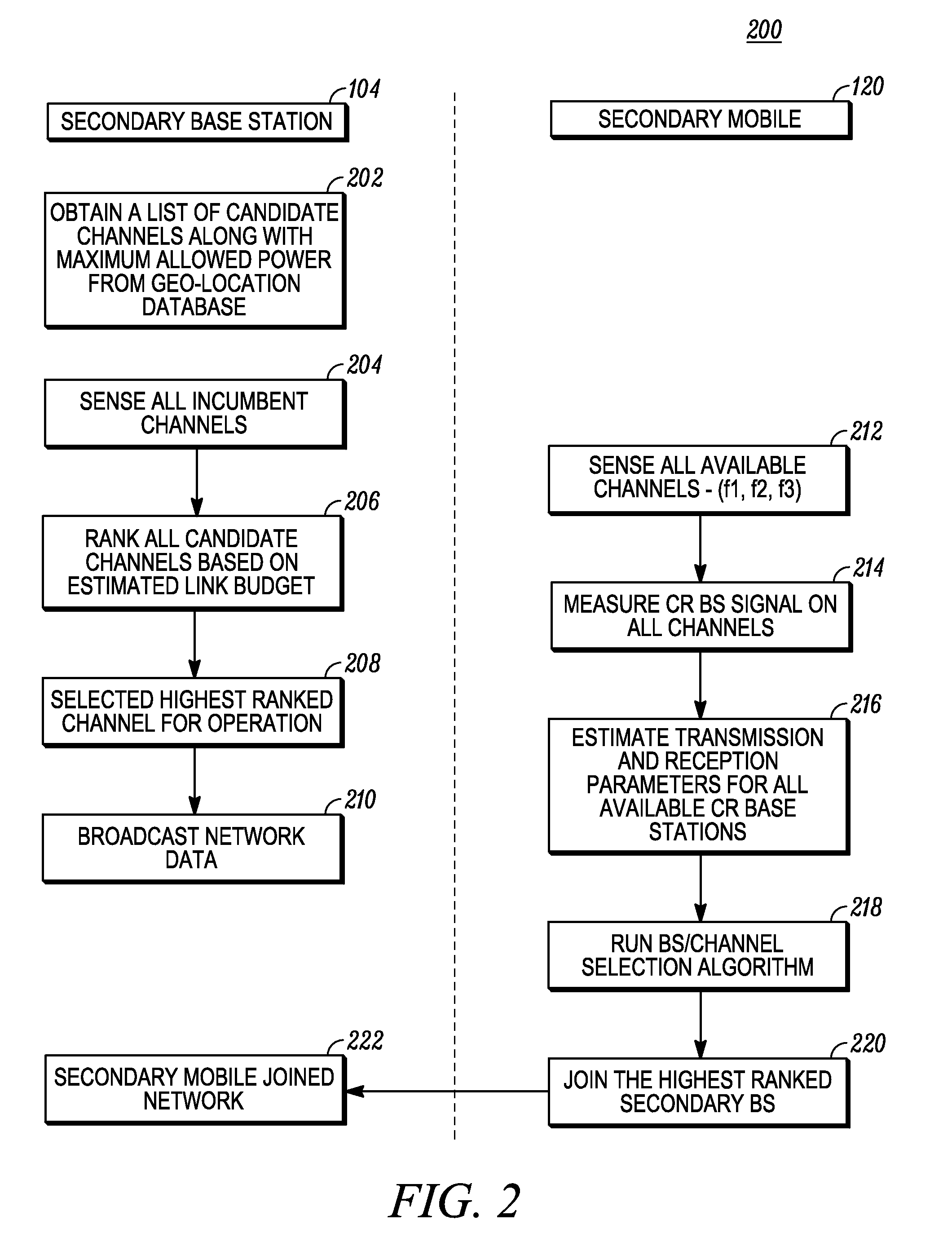
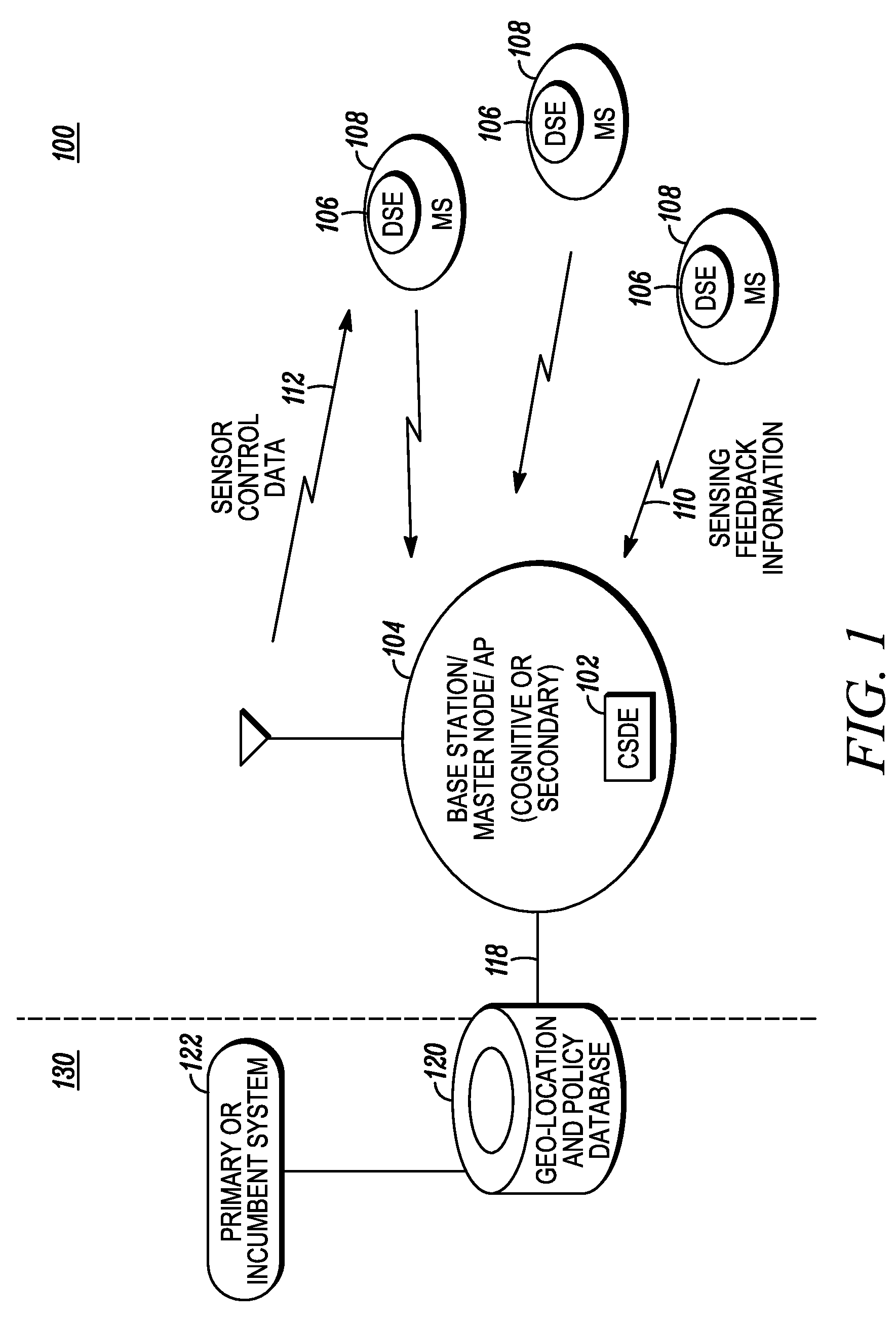
Method and apparatus for optimizing spectrum utilization by a cognitive radio network
ActiveUS20100081449A1Spectral gaps assessmentAssess restrictionCommunications systemFrequency spectrum
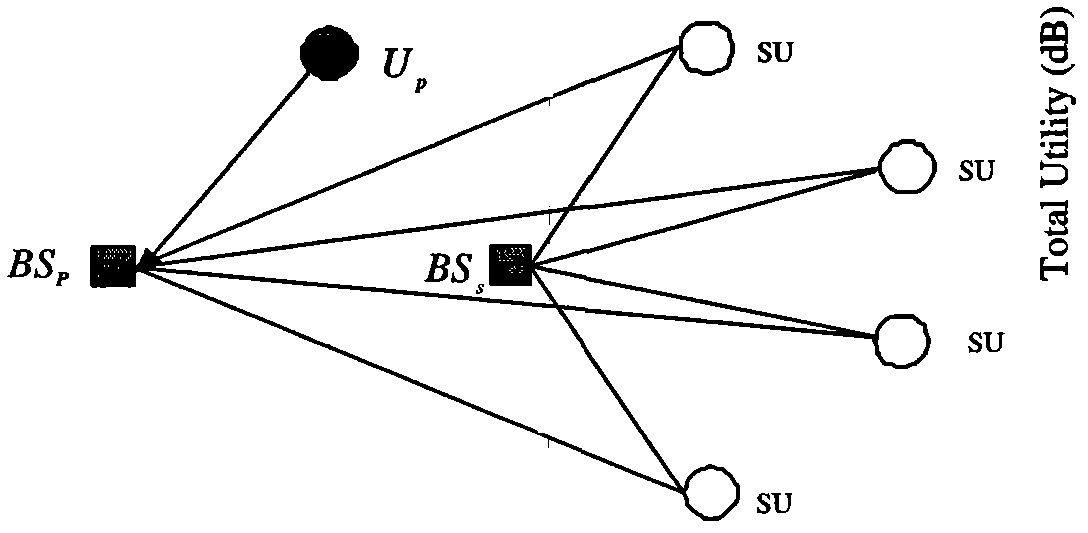
A technique for a secondary communication system to utilize spectrum designated to another (or primary) communication system is provided. By ranking a plurality of secondary base stations based on base station transmit power, calculated required transmit power and path loss, a set of criteria is developed for selecting a highest ranked secondary base station for operation within a primary's spectrum. The ranking may be adapted based on mobility of the secondary's subscriber; and as such the secondary system communicates within the primary's spectrum using the adaptively ranked base stations. Channel selection may also be ranked. The technique and apparatus allows a cognitive radio (CR) network to operate within an incumbent network's spectrum.
Owner:MOTOROLA SOLUTIONS INC
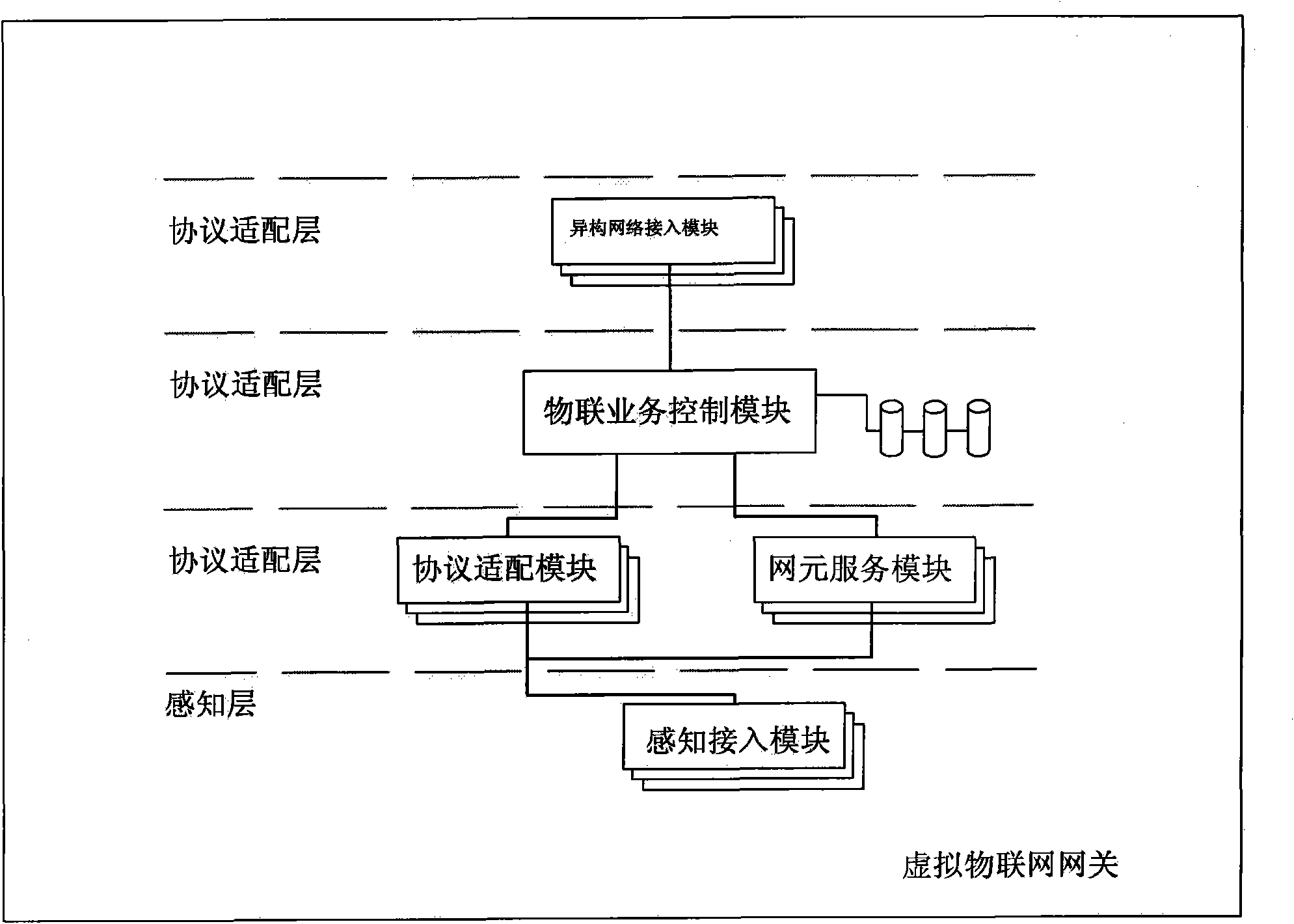
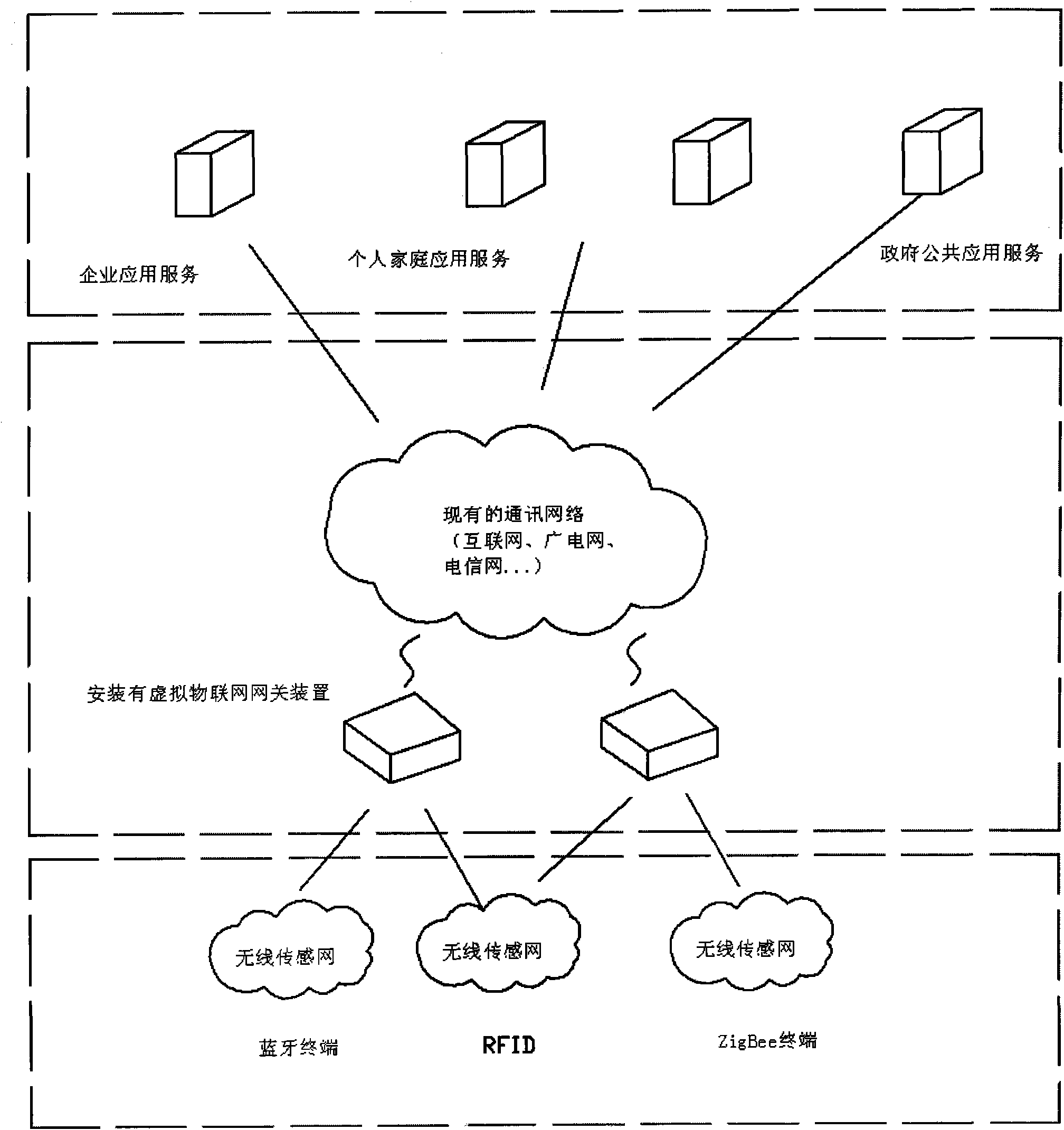
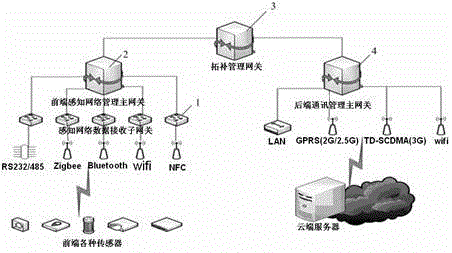
Virtual Internet-of-things gateway system capable of realizing multiprotocol and network self-adapting
InactiveCN102045896ABroad network applicabilityMeet development needsWireless communicationWide areaControl layer
The invention discloses a virtual Internet-of-things gateway system capable of realizing multiprotocol and network self-adapting; and the gateway system uses a virtual Internet-of-things gateway to connect a sensor network with a traditional communication network and realize the protocol conversions of different types of sensor networks, equipment local interconnect and remote control. The invention is characterized in that the virtual Internet-of-things gateway contains a sensing access module in a sensing access layer, a protocol adaptation module and a network element service module which are in a protocol adaptation layer, a thing-connecting service control module in a control layer, and a heterogeneous network access module in a wide area access layer; the entire system adopts the virtual gateway method; the gateway equipment of the virtual Internet-of-things gateway system are arranged and only a plurality of physical interfaces are required to be added without greatly changing the internal circuit structure, thus the various demands of the future network can be satisfied and the development demand of the future Internet of things can be satisfied; and the incompatibility problem of the existing common gateway to the future Internet of things is effective solved, thus the gateway in the virtual gateway system has wide network applicability.
Owner:ZHONGSHAN IKER DIGITAL TECH
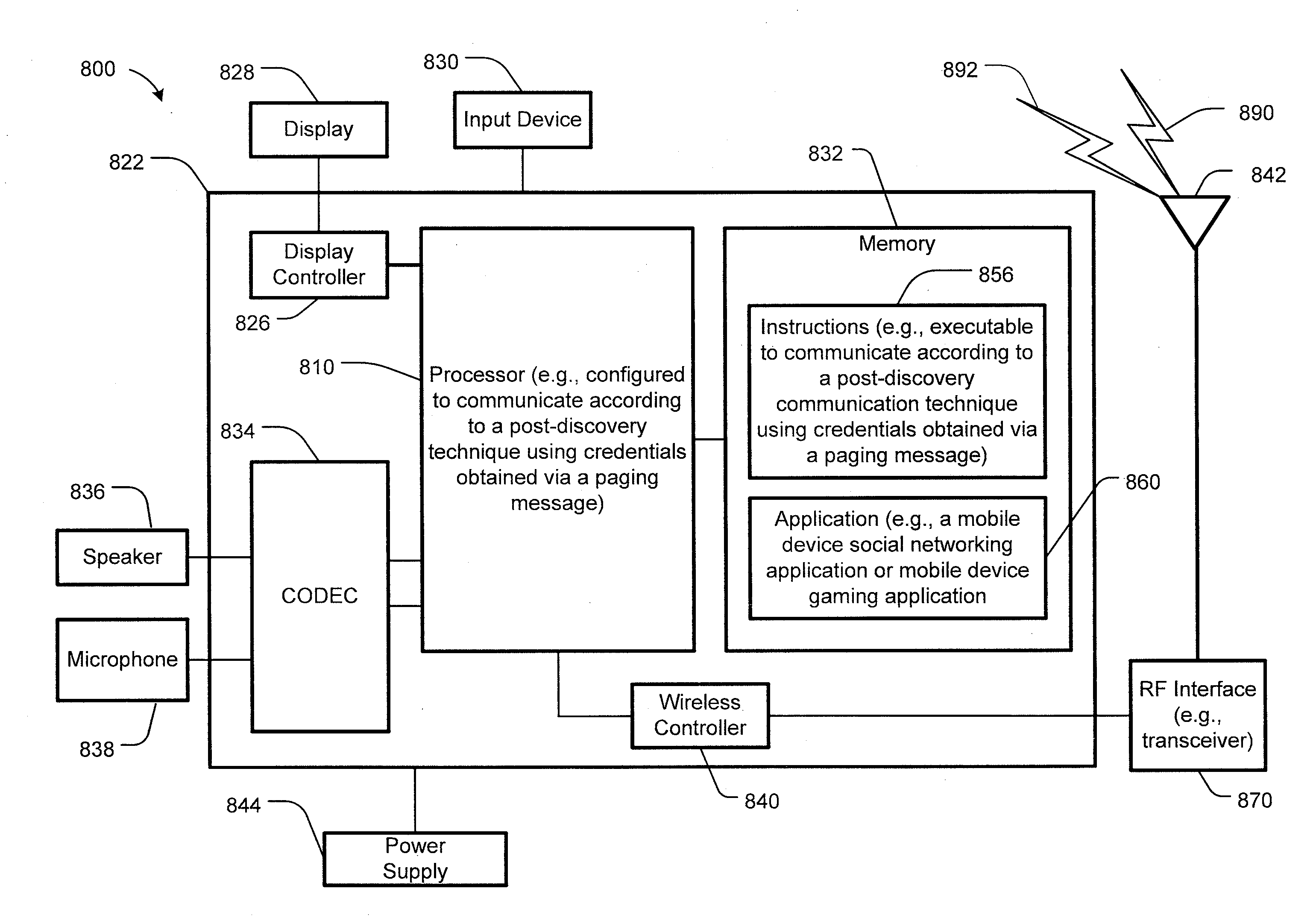
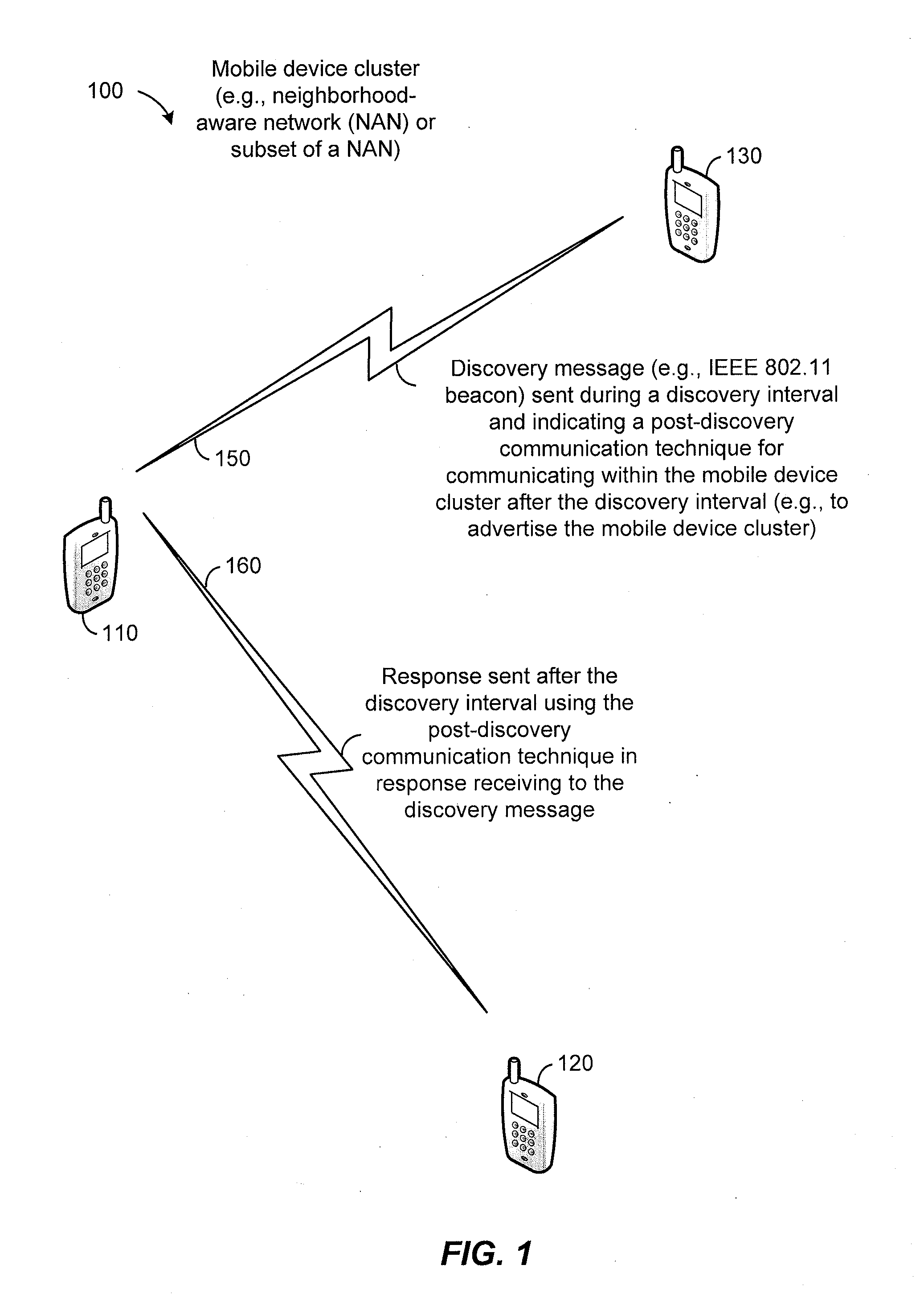
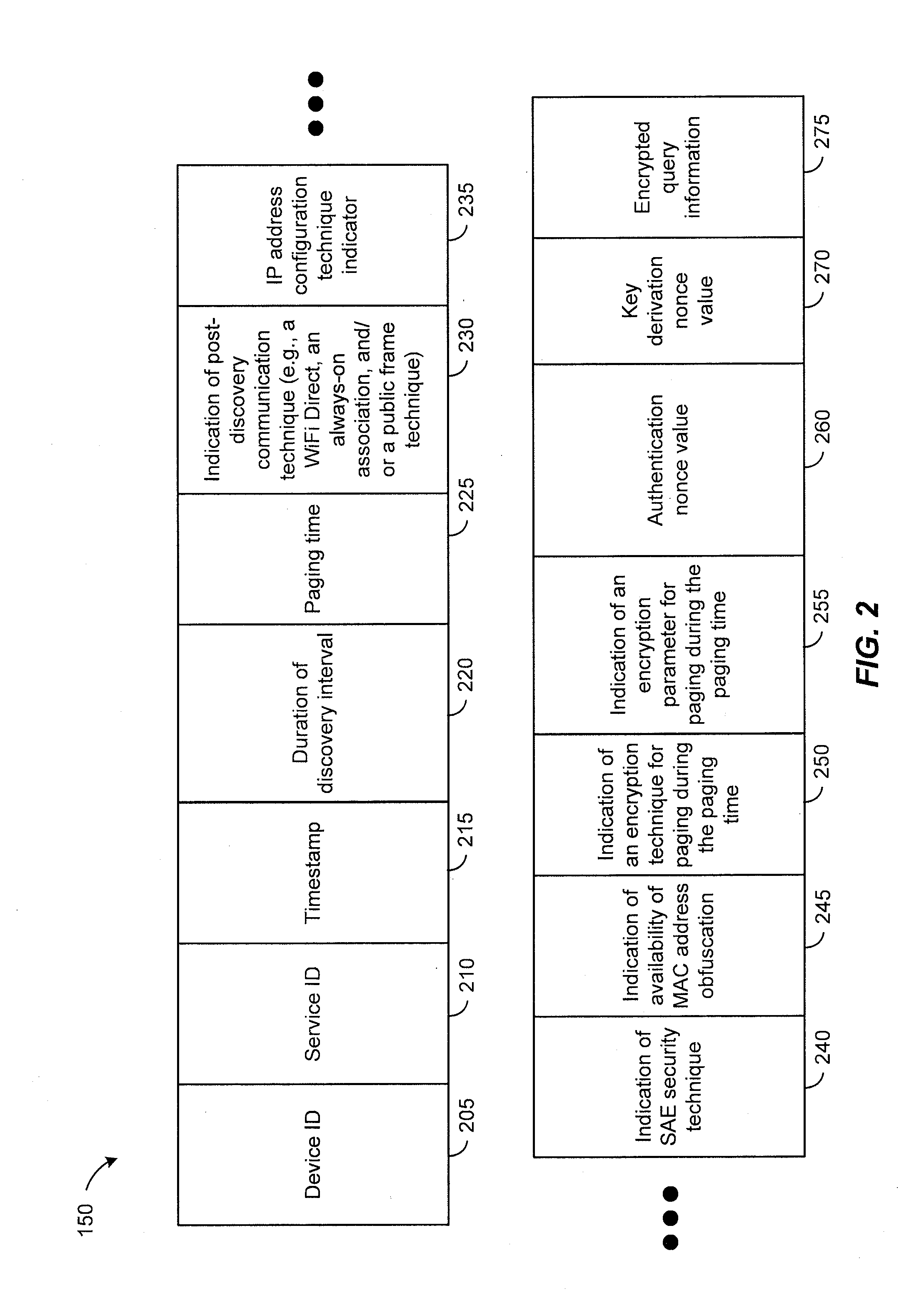
System and method for post-discovery communication within a neighborhood-aware network
ActiveUS20140082205A1Reduce the burden onMultiple digital computer combinationsTransmissionMobile deviceSecurity information
In a particular embodiment, a method includes determining, at a first mobile device, a post-discovery communication technique for communicating within a mobile device cluster after a discovery interval. During the discovery interval, a discovery message may be sent. The discovery message indicates the post-discovery communication protocol for communicating within the mobile device cluster after the discovery interval. The discovery message may further indicate a time interval for sending and receiving a paging request. In response to the receipt of the discovery message a second mobile devices may send a paging request, the paging request including a security information request. The method further includes sending from the first mobile device a paging response including security information and exchanging one or more post-discovery communications with the second mobile device using the security information.
Owner:QUALCOMM INC
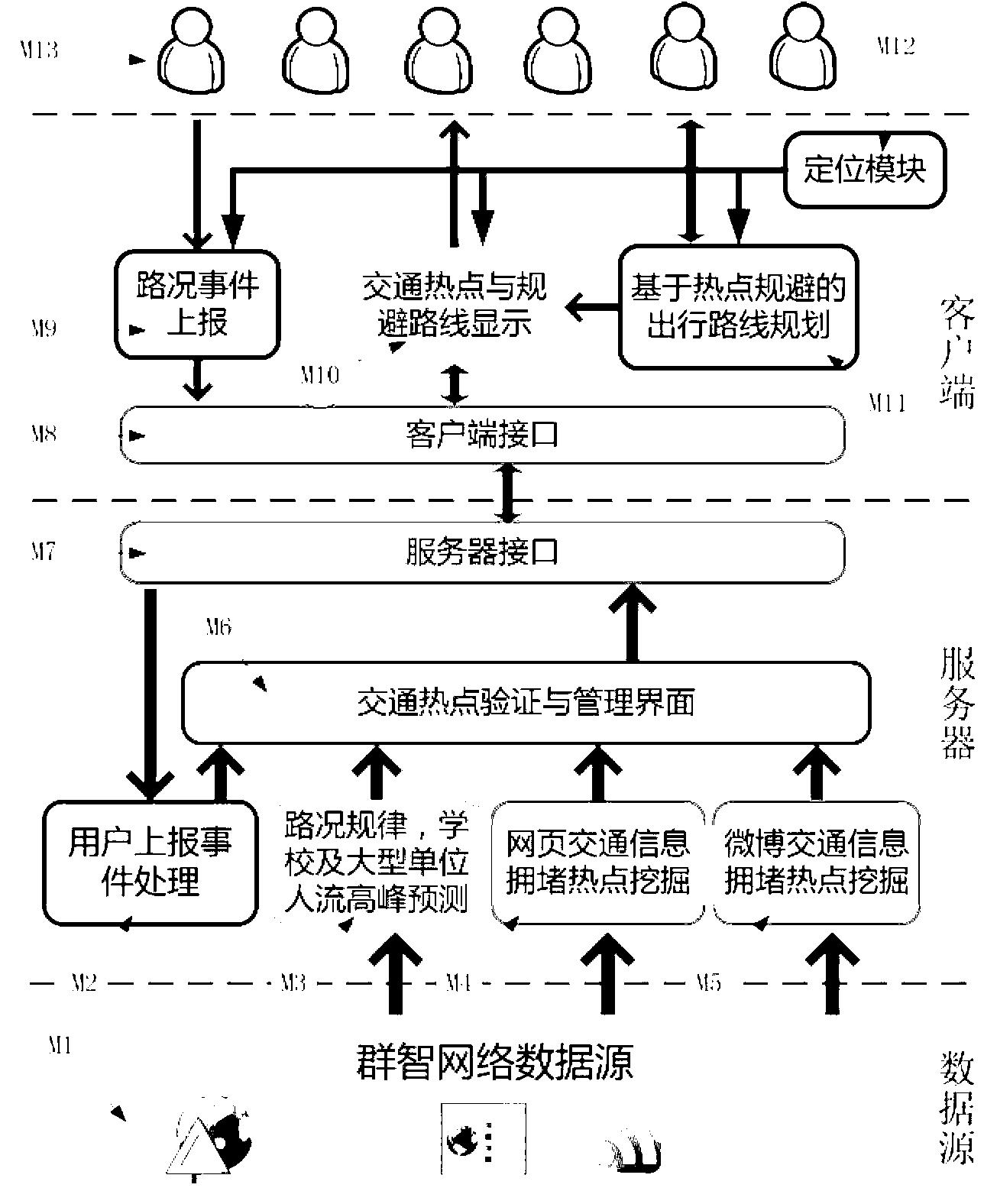
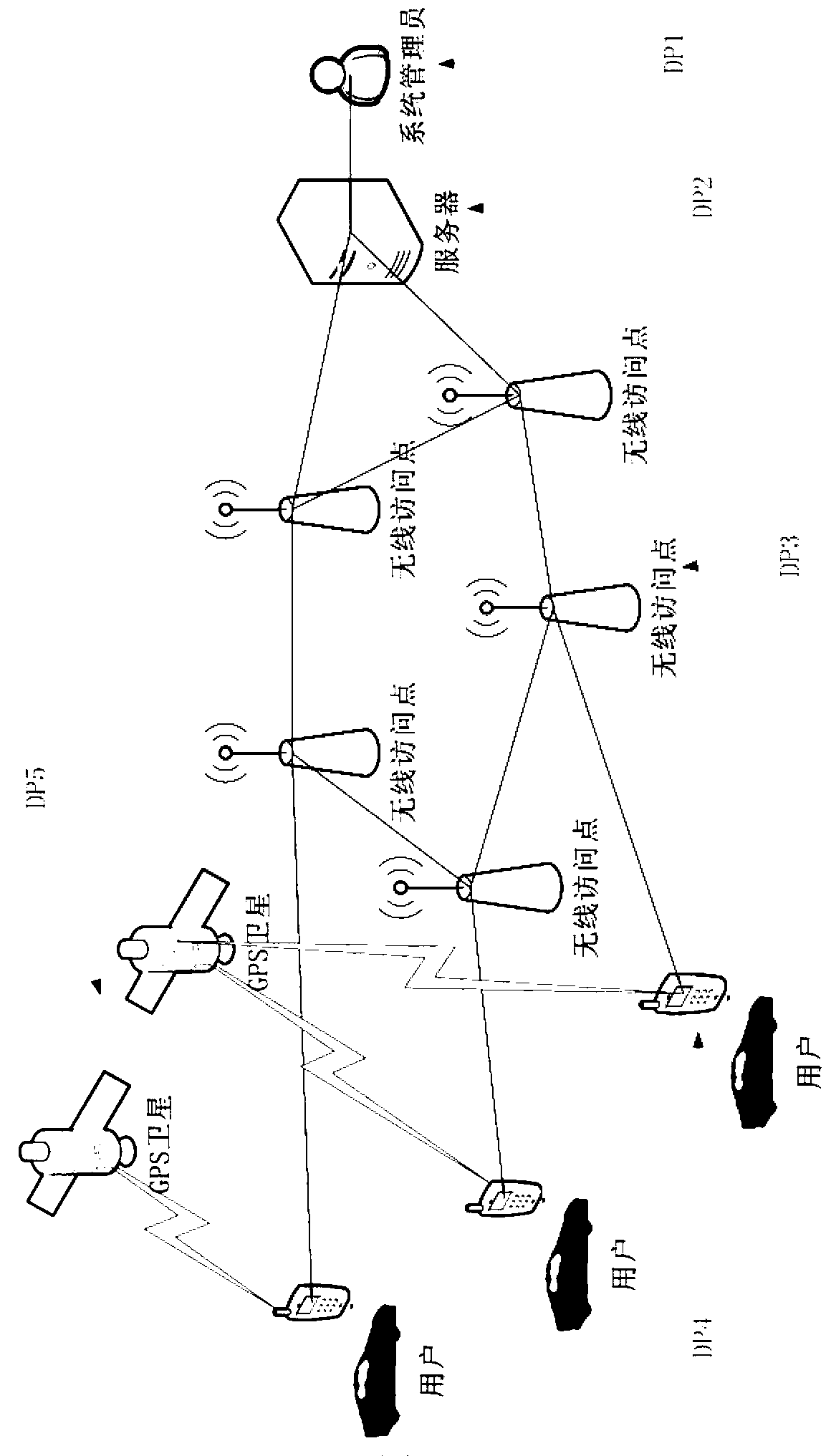
Traffic jam avoiding prompting system based on collective intelligence network
ActiveCN103236163AImprove accuracyImprove reliabilityDetection of traffic movementMicrobloggingCollective intelligence
The invention provides a traffic jam avoiding prompting system based on a collective intelligence network. The traffic jam avoiding prompting system consists of a webpage traffic hot spot digging module, a microblog traffic hot spot digging module, a road condition rule predicting module, a jam hot spot verification and management module, a real-time traffic hot spot server, a traveling route planning module based on hot spot avoiding, a traffic hot spot and avoiding route display module and intelligent mobile phone end application software. The traffic jam avoiding prompting system faces the collective intelligence sensing network, is combined with the traditional traffic information sources, carries out digging and prediction on the urban traffic hot spots on the basis of the data activation technology, and further provides the traffic jam hot spot display and avoiding prompt service for intelligent terminal users. The traffic jam avoiding prompting system has the advantages that the data is from the multi-source collective intelligence network, the accuracy is good, the checking comprehensive rate is high, the hot spots are captured and fed back in real time, high efficiency and practicability are realized, the design is good, the operation is stable, the installation is convenient, the traffic jam avoiding prompting system can become a tool capable of providing wide and practical intelligent traffic information for urban residents, and the efficient information prompt is provided for the users to realize the smooth traveling.
Owner:BEIHANG UNIV
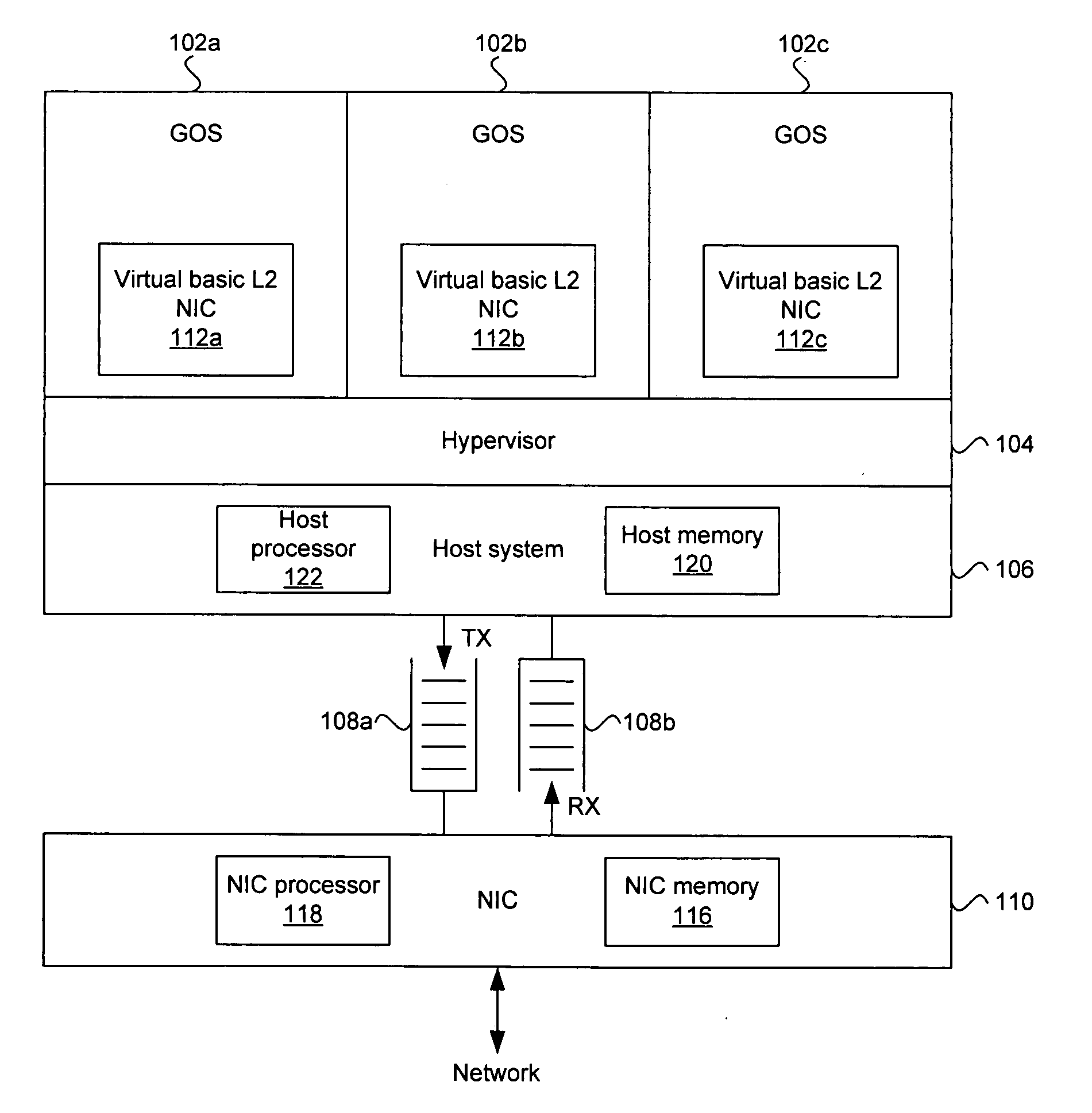
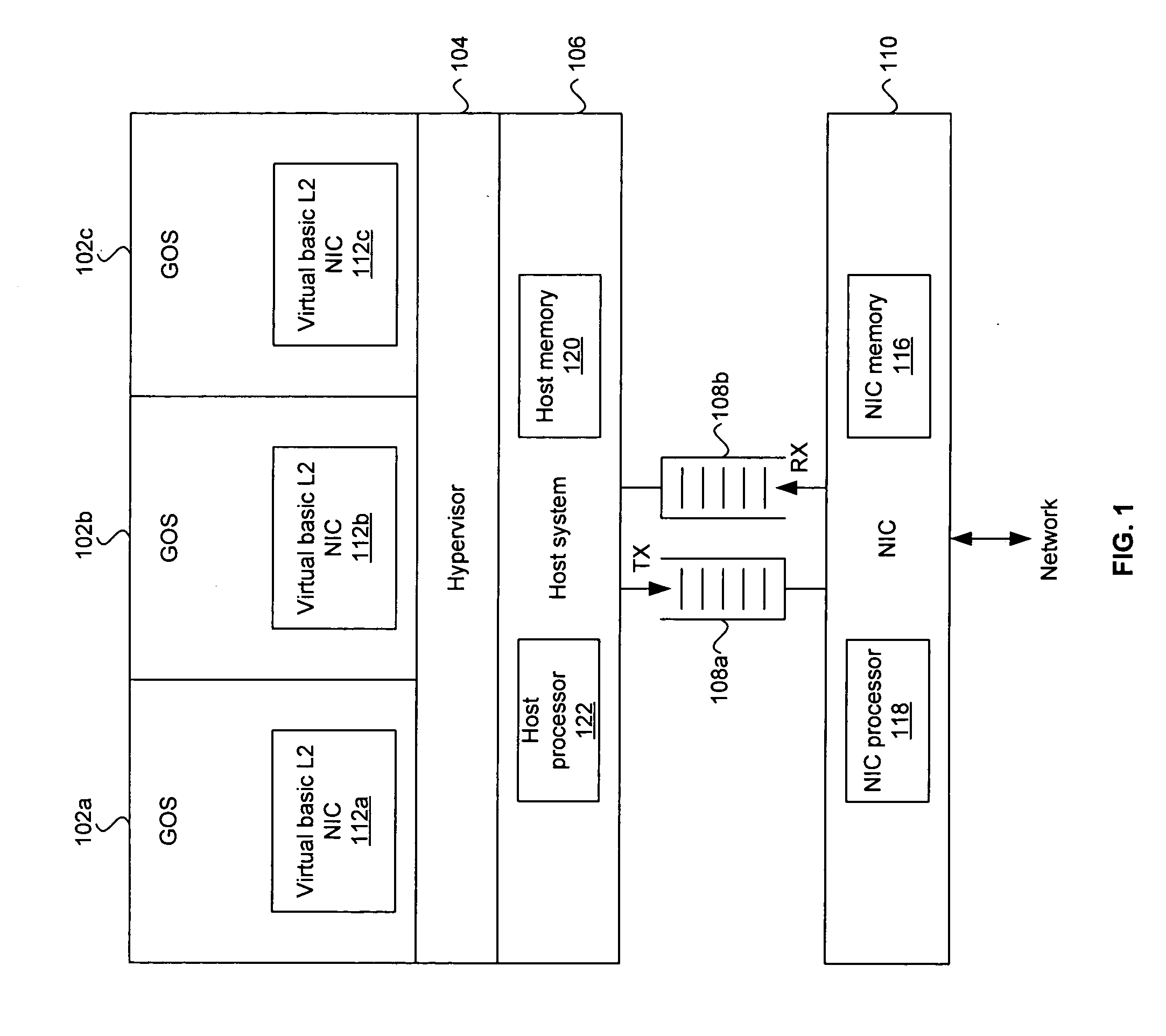
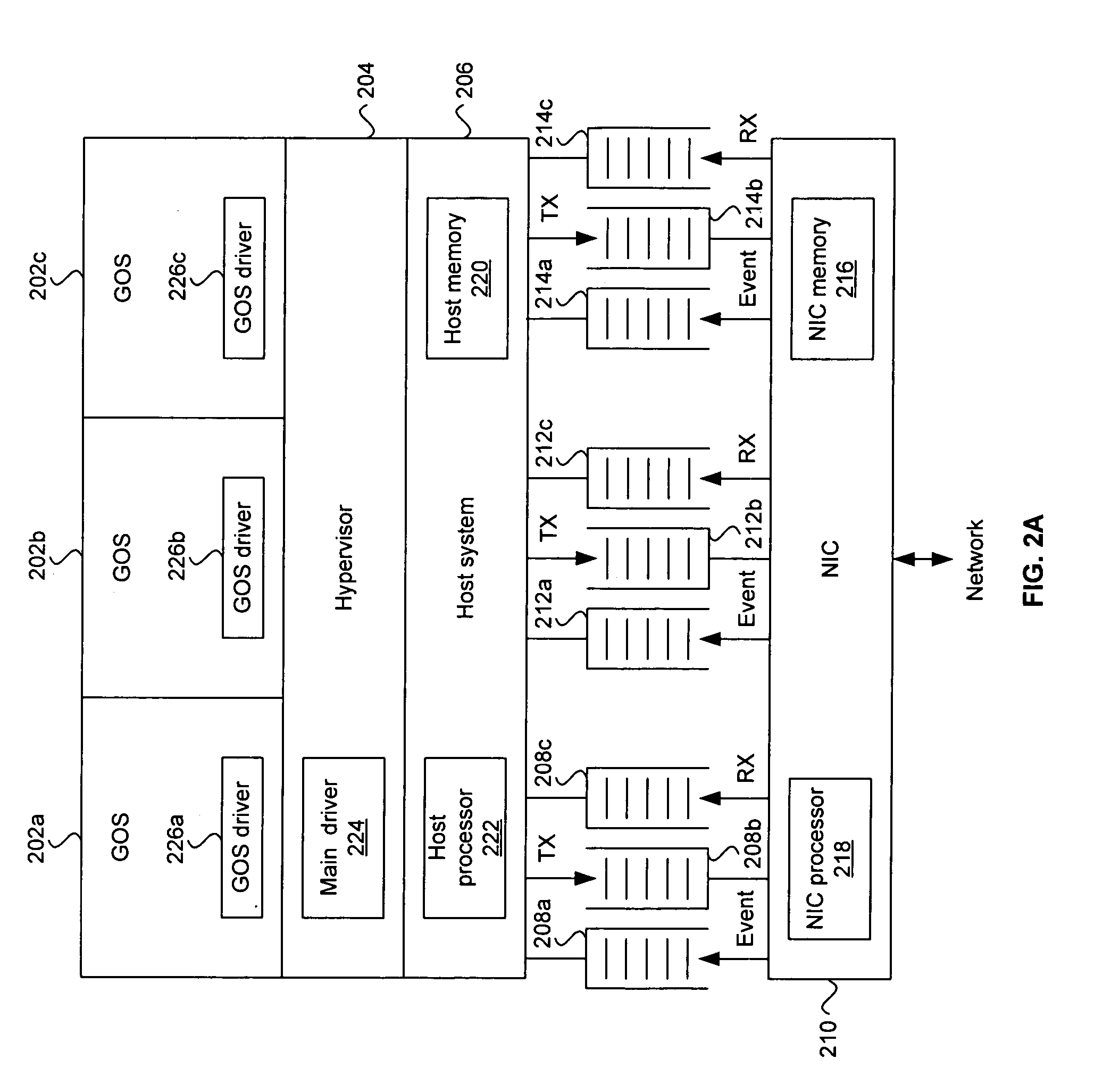
Method and system for an OS virtualization-aware network interface card
Aspects of a method and system for an operating system (OS) virtualization-aware network interface card (NIC) are provided. A NIC may provide direct I / O capabilities for each of a plurality of concurrent guest operating systems (GOSs) in a host system. The NIC may comprise a GOS queue for each of the GOSs, where each GOS queue may comprise a transmit (TX) queue, a receive (RX) queue, and an event queue. The NIC may communicate data with a GOS via a corresponding TX queue and RX queue. The NIC may notify a GOS of events such as down link, up link, packet transmission, and packet reception via the corresponding event queue. The NIC may also support unicast, broadcast, and / or multicast communication between GOSs. The NIC may also validate a buffered address when the address corresponds to one of the GOSs operating in the host system.
Owner:AVAGO TECH INT SALES PTE LTD
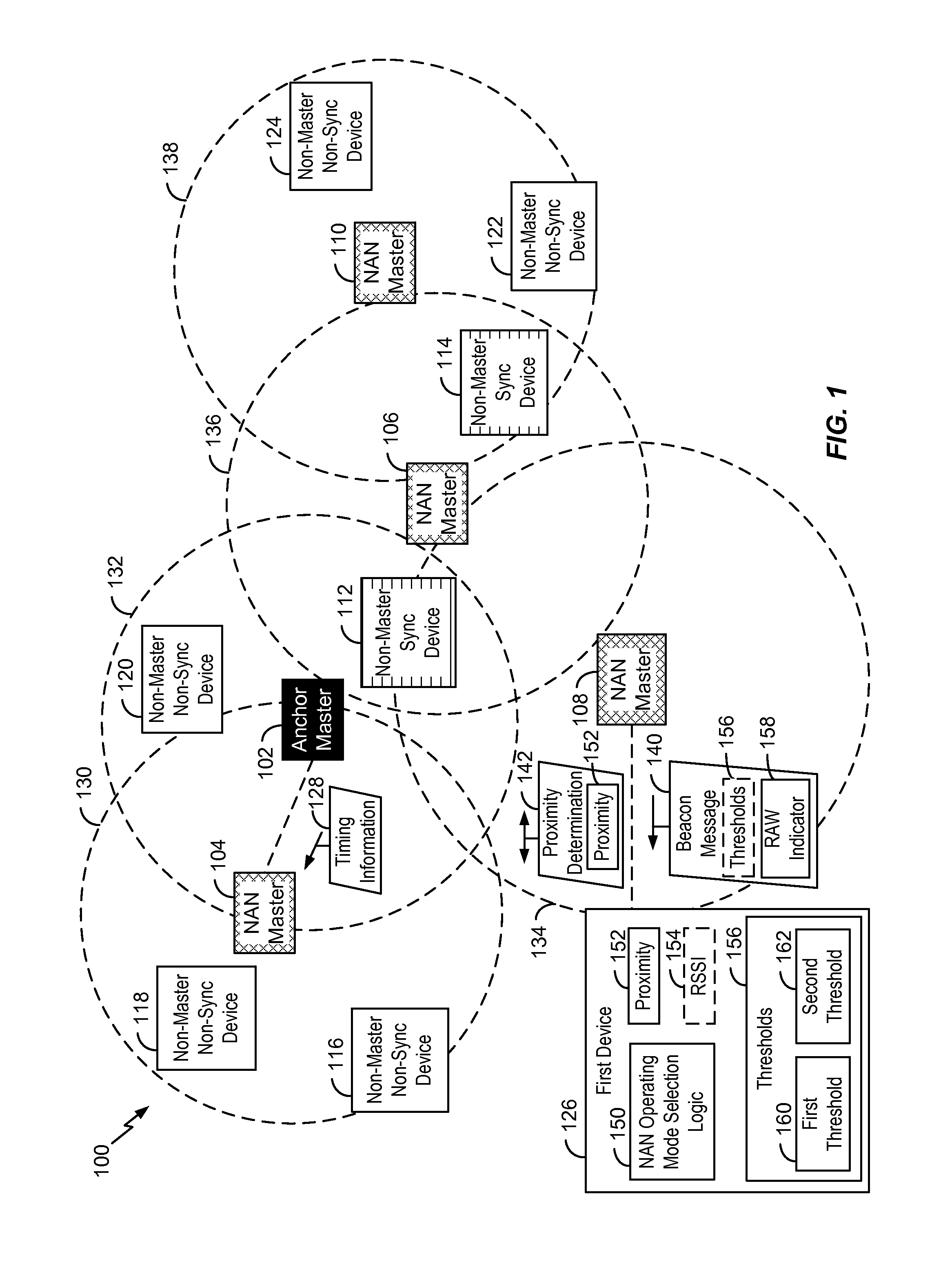
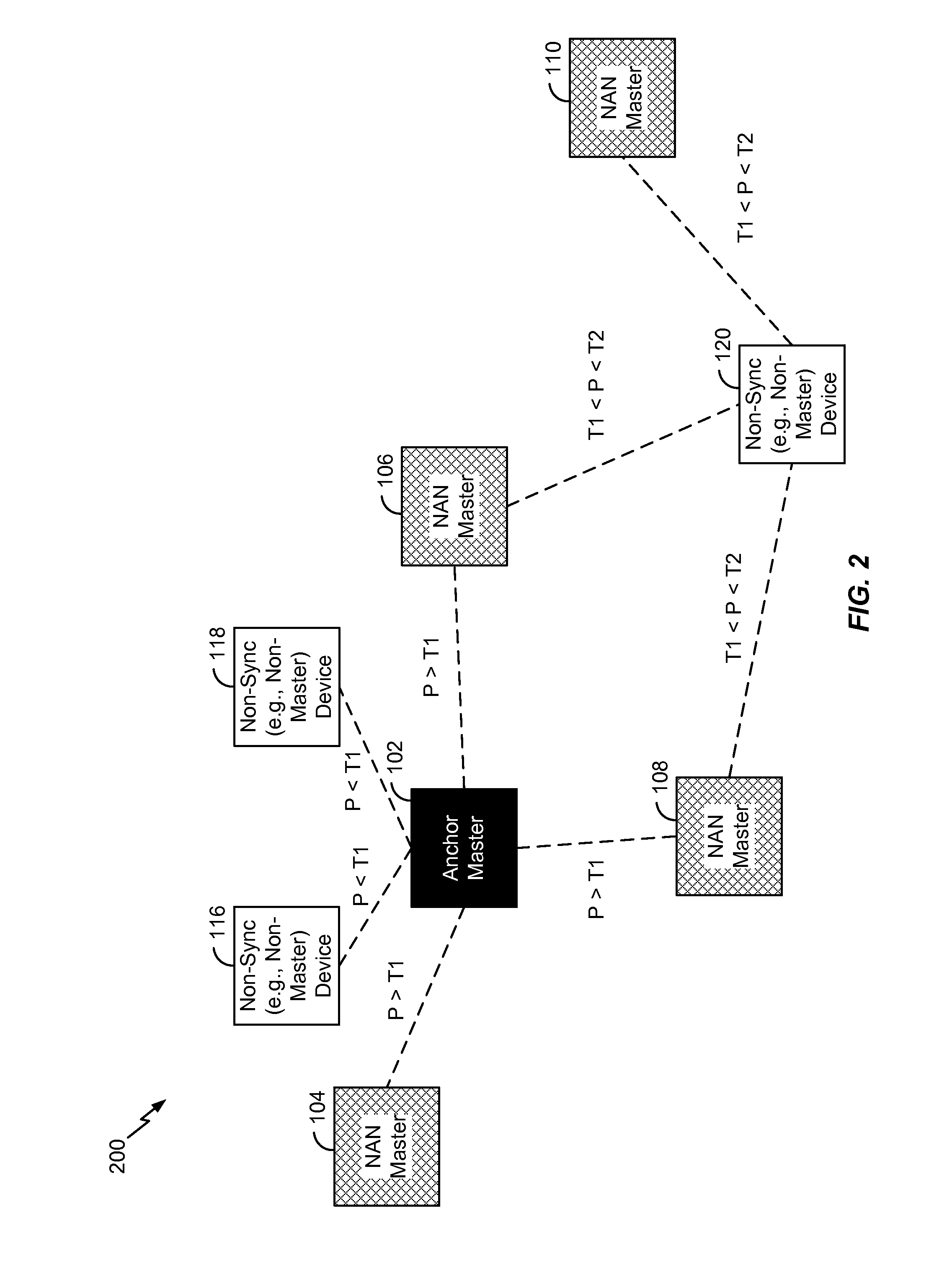
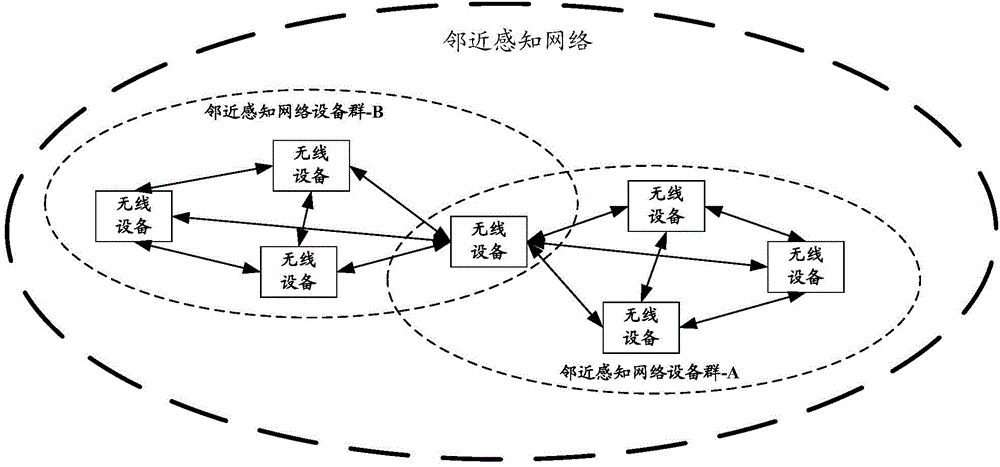
Neighbor aware network cluster topology establishment based on proximity measurements
InactiveUS20150350027A1Reduce power consumptionLess powerPower managementSynchronisation arrangementNetwork clusteringReal-time computing
Owner:QUALCOMM INC
Thing Internet gateway of heterogeneous wireless network and control method thereof
InactiveCN101951693ARealize ad hoc networkOvercoming Accessibility LimitationsNetwork topologiesWireless network protocolsStructure of Management InformationThe Internet
The invention discloses a thing Internet gateway of a heterogeneous wireless network and a control method thereof. Function, such as protocol conversion, route selection, data exchange and the like, is provided in the network interworking process of different structures or protocols of the thing Internet. The gateway is a multi-layer cascading gateway and comprises a main gateway used for communication, sensor network management and topology management, and sub-gateways responsible for converting and penetrating a short-range wireless protocol and receiving front-end sensing network data, wherein each of the sub-gateways is connected with the main gateway. The limitation to the access ability of a sensor network is overcome, so that various front-end sensing nodes access a thing Internet platform without barriers; free networking of the sensor network front end is realized by taking full advantage of the conventional communication capacity and cascading gateway technology at the same time; the problems of the failure management and performance management of the sensor network front end are effectively solved; and the safety, the reliability and the stability of the sensor network and neurones are enhanced.
Owner:天津中启创科技有限公司
Method for ensuring security and privacy in a wireless cognitive network
ActiveUS20110138183A1Improve protectionFacilitate sharing of available WRAN channelsUser identity/authority verificationSecret communicationConfidentialityNetwork management
In some embodiments, authentication, confidentiality, and privacy are enhanced for a wireless network of cognitive radios by encryption of network management and control messages as well as data traffic, thereby protecting information pertaining to node identification, node location, node-sensed incumbent transmissions, CRN frequency channel selections, and such like. During initial network registration, a temporary ID can be issued to a node, and then replaced once encrypted communication has been established. This prevents association of initial, clear-text messages with later encrypted transmissions. Elliptic curve cryptography can be used for mutual authentication between subscribers and the base station. ECC-based implicit digital certificates can be embedded in co-existence beacons used by CRN nodes to coordinate use of frequency channels, thereby preventing denial of service attacks due to transmitting of falsified beacons. Similar certificates can be embedded within identity beacons used to protect certain incumbents from interference by the CRN.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
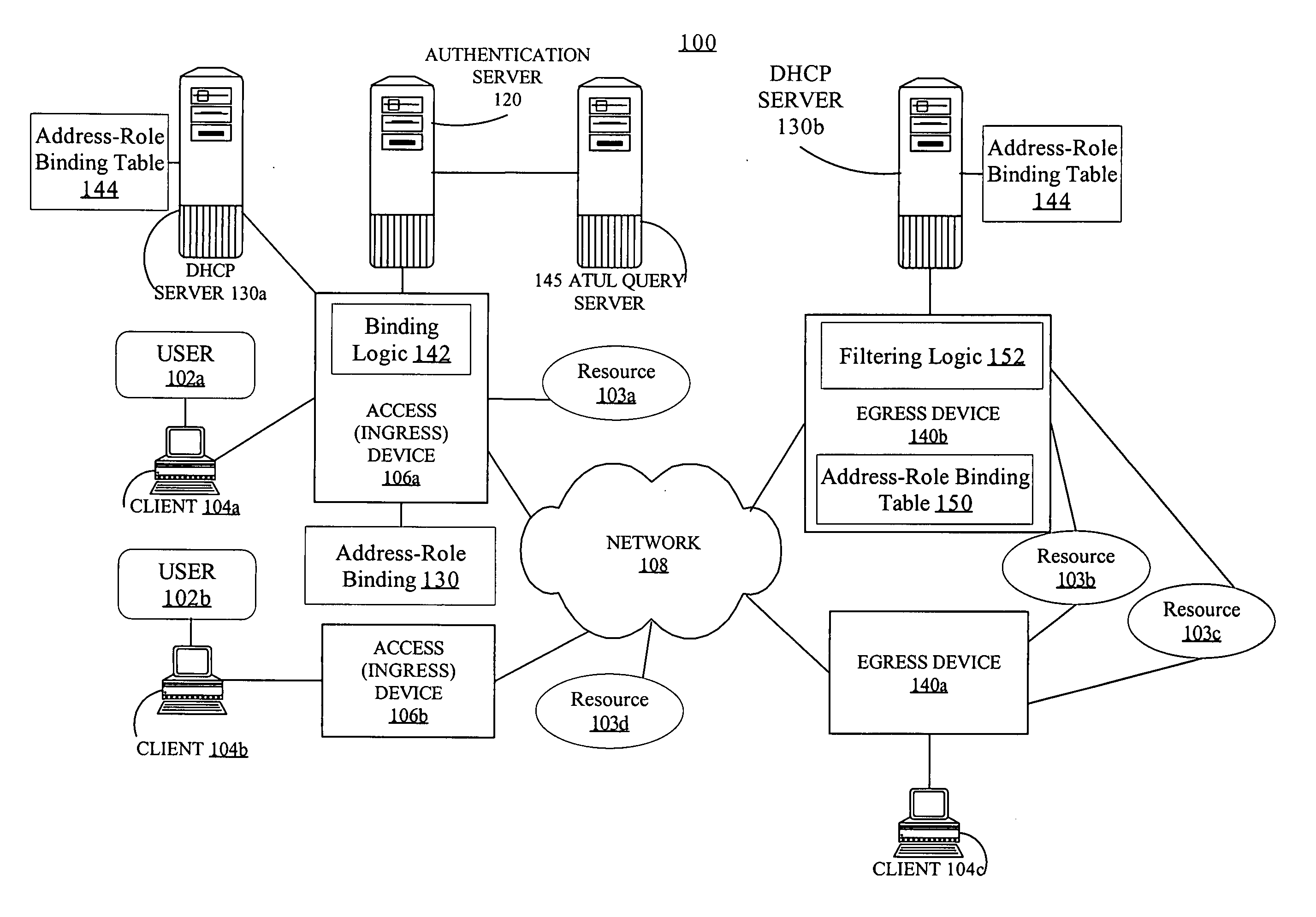
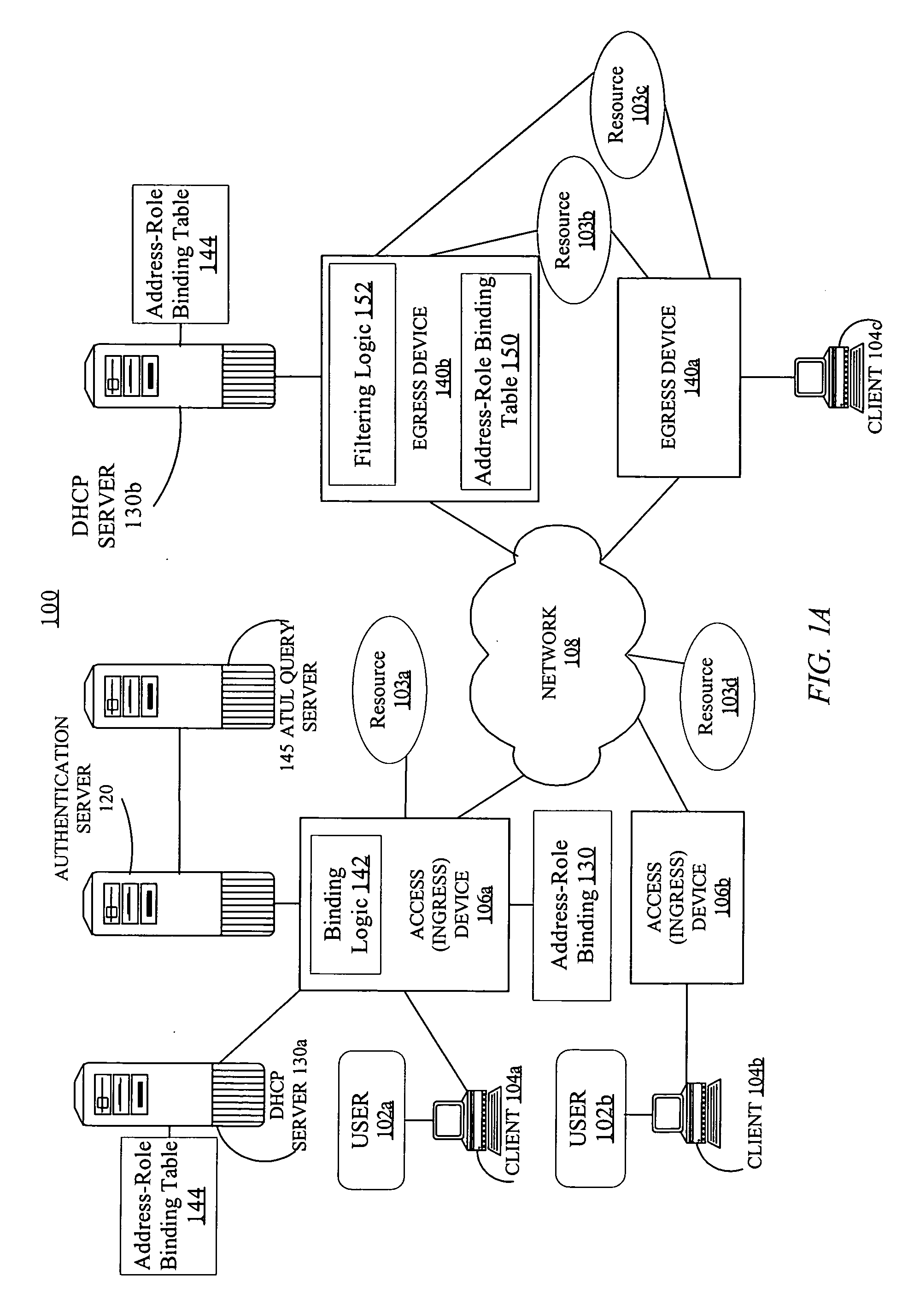
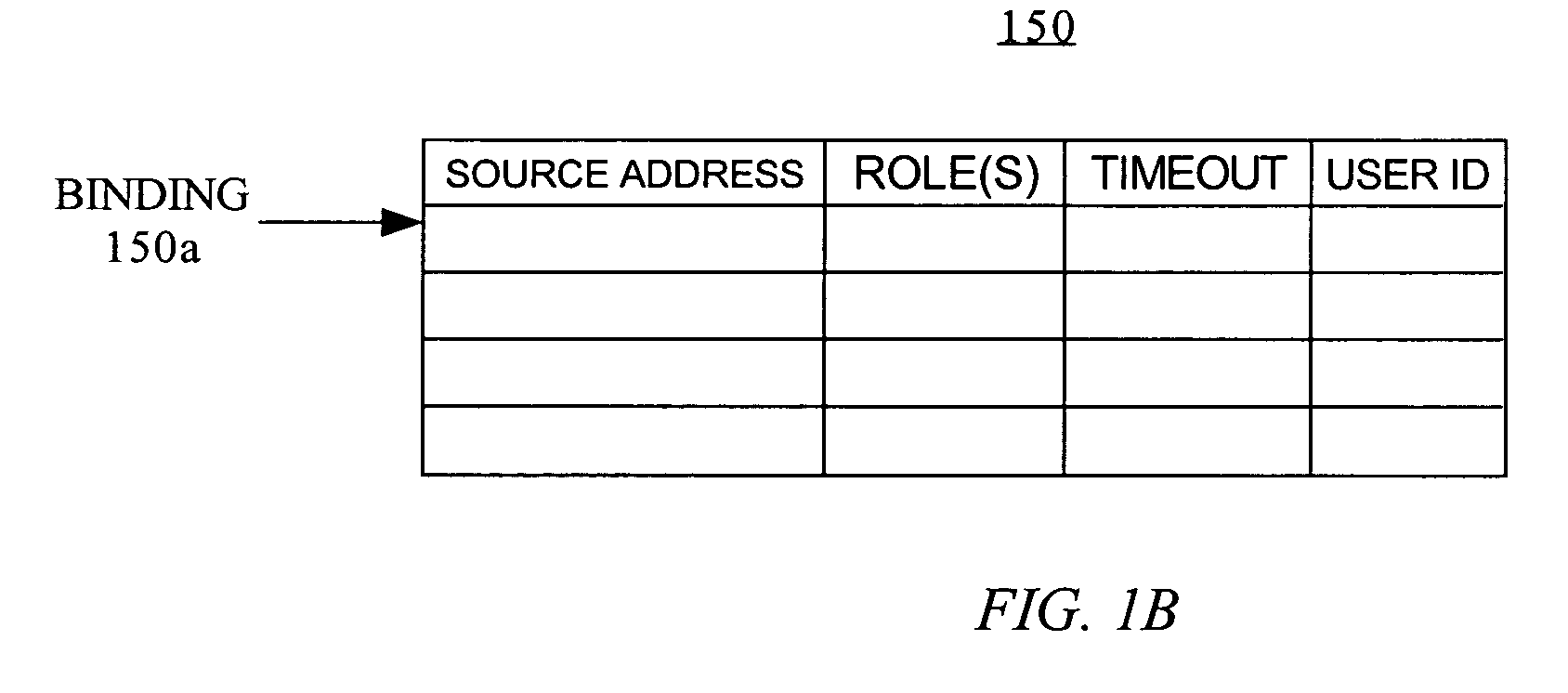
Role aware network security enforcement
InactiveUS20070214352A1Multiple digital computer combinationsProgram controlUser authenticationSecurity policy
Generating a binding between a source address and one or more roles of a user accessing the network and distributing the binding to a filter node. The source address is currently assigned to the device. The binding may be generated by one or more nodes on an ingress path used during authentication of the user. The binding may be distributed to the filter node on demand or without any request from the filter node. Responsive to a determination that the user is associated with a new source address, a new binding is generated to associate a new source address with the one or more roles for the user. The new binding is distributed to the filter node. Another aspect is a method of enforcing a role based security policy at a filter node, using bindings of source addresses to roles.
Owner:CISCO TECH INC
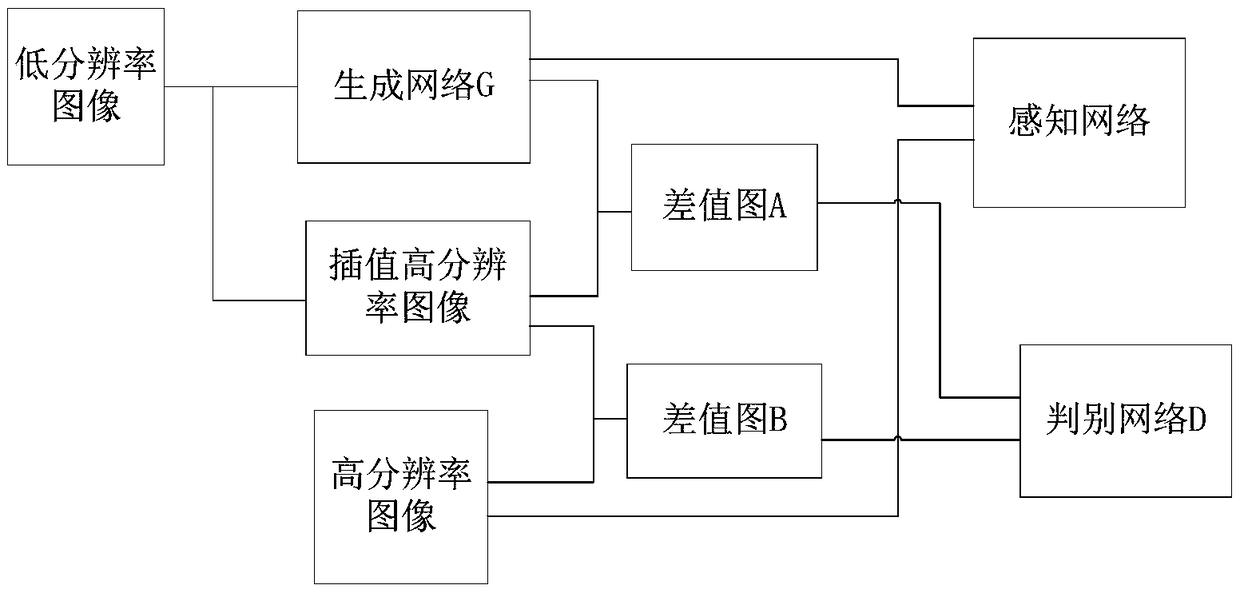
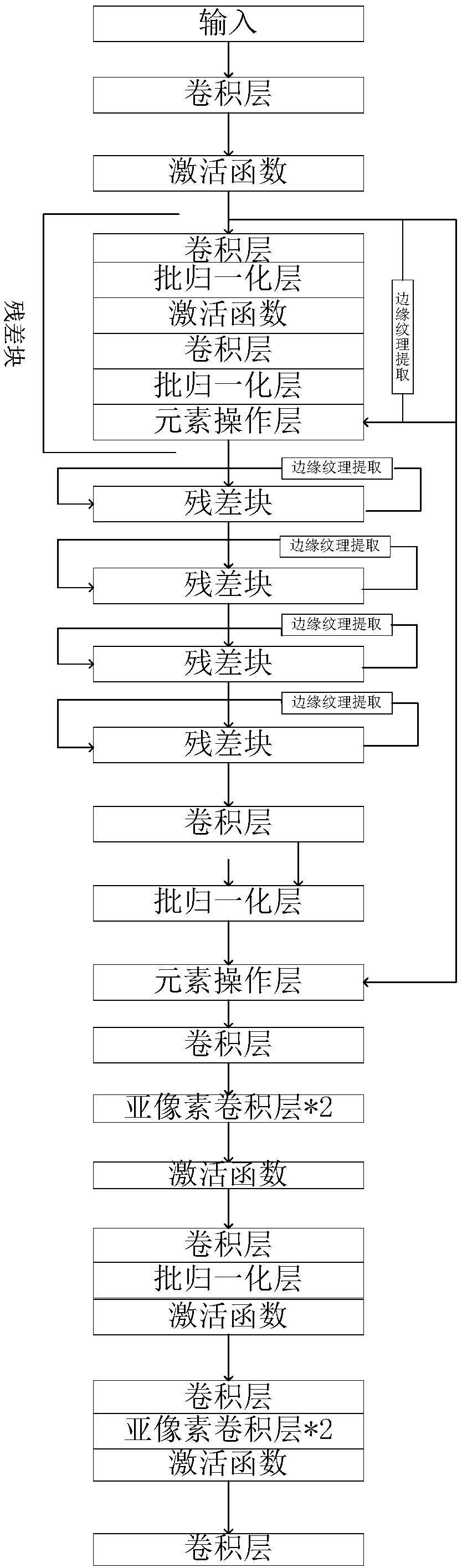
Image super-resolution reconstruction method for generating antagonistic network based on feature fusion
ActiveCN109509152AReduce computational complexityImprove generation effectGeometric image transformationNeural architecturesPattern recognitionData set
The invention discloses an image super-resolution reconstruction method for generating antagonistic network based on feature fusion, which comprises the following steps: pre-processing ImageNet data set to obtain a reconstruction data set corresponding to high-resolution image and low-resolution image; The model of generating antagonistic network for training is constructed, and the interpolationreconstruction module is introduced into the model to construct the generating network and perceptual network for multi-feature fusion. The reconstructed data sets are sequentially input into the generated antagonistic network for model training. The images to be processed are normalized to obtain low-resolution images, which are input to the trained generation network to obtain the reconstructedhigh-resolution images. As that recursive residual network is utilize to extract multiple features such as edge and texture, highlight the edge and texture information of the generated image, so thatthat reconstruct image is clearer, The interpolation reconstruction module is used as a mediator to realize the residual discrimination, highlight the difference between the reconstructed and real high-resolution images and reduce the computational complexity of the discrimination network, and use VGG network to fuse multiple features to calculate the loss function, which makes the reconstructed image more effective and more consistent with the observation mode of human eyes.
Owner:DALIAN MARITIME UNIVERSITY
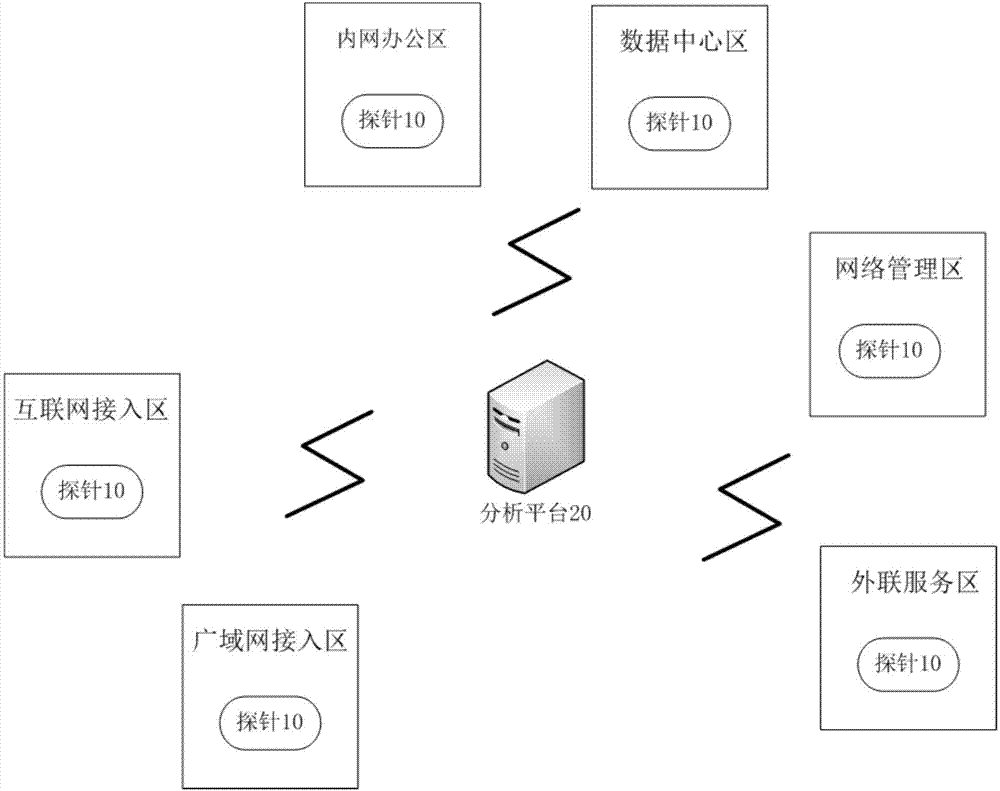
Network security perception system and method, and readable storage medium
The invention discloses a network security perception system comprising multiple probes respectively deployed on switches or routers of monitoring network areas and used for dynamically obtaining mirror image traffic of the respective monitoring network areas, collecting specific traffic information from the mirror image traffic, and uploading the collected mirror image traffic to an analysis platform through an encrypted communication channel; the analysis platform used for dynamically receiving the traffic information uploaded by the probes, performing multi-dimensional correlation analysisto identify the security threats in the entire network, and displaying an analysis result in a visible manner. The invention further discloses an implementation method of the network security perception system and a computer storage medium. The network security perception system provided by the invention can monitor the entire network in mesh network form in all directions, perceive the potentialsecurity threats in the network and protect the information security in the entire network.
Owner:SANGFOR TECH INC
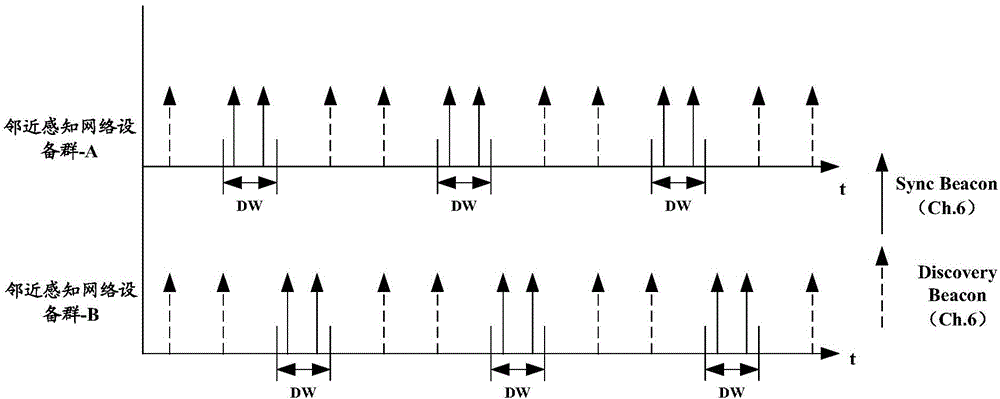
Method, device and system for joining in neighbor awareness network cluster
ActiveCN104378800AShort working hoursReduce power consumptionAssess restrictionNetwork topologiesTelecommunicationsNetwork clustering
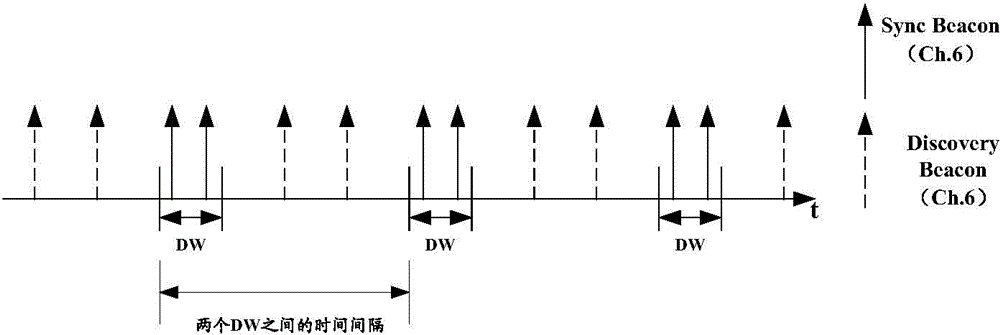
Disclosed are a method, device and system for joining a Neighbor Awareness Network (NAN) cluster. When a wireless device in a first NAN cluster scans and finds a second NAN cluster, if joining the second NAN cluster is necessary, then the wireless device leaves the first NAN cluster and joins the second NAN cluster; as the wireless device does not join a plurality of NAN clusters at the same time, the wireless device has low power consumption; in addition, as times goes on, when all the wireless devices in the first NAN cluster leave the first NAN cluster and join the second NAN cluster, the discovery window (DW) of the first NAN cluster on the working channel will not be occupied, thus increasing available resources on the working channel.
Owner:HUAWEI DEVICE CO LTD
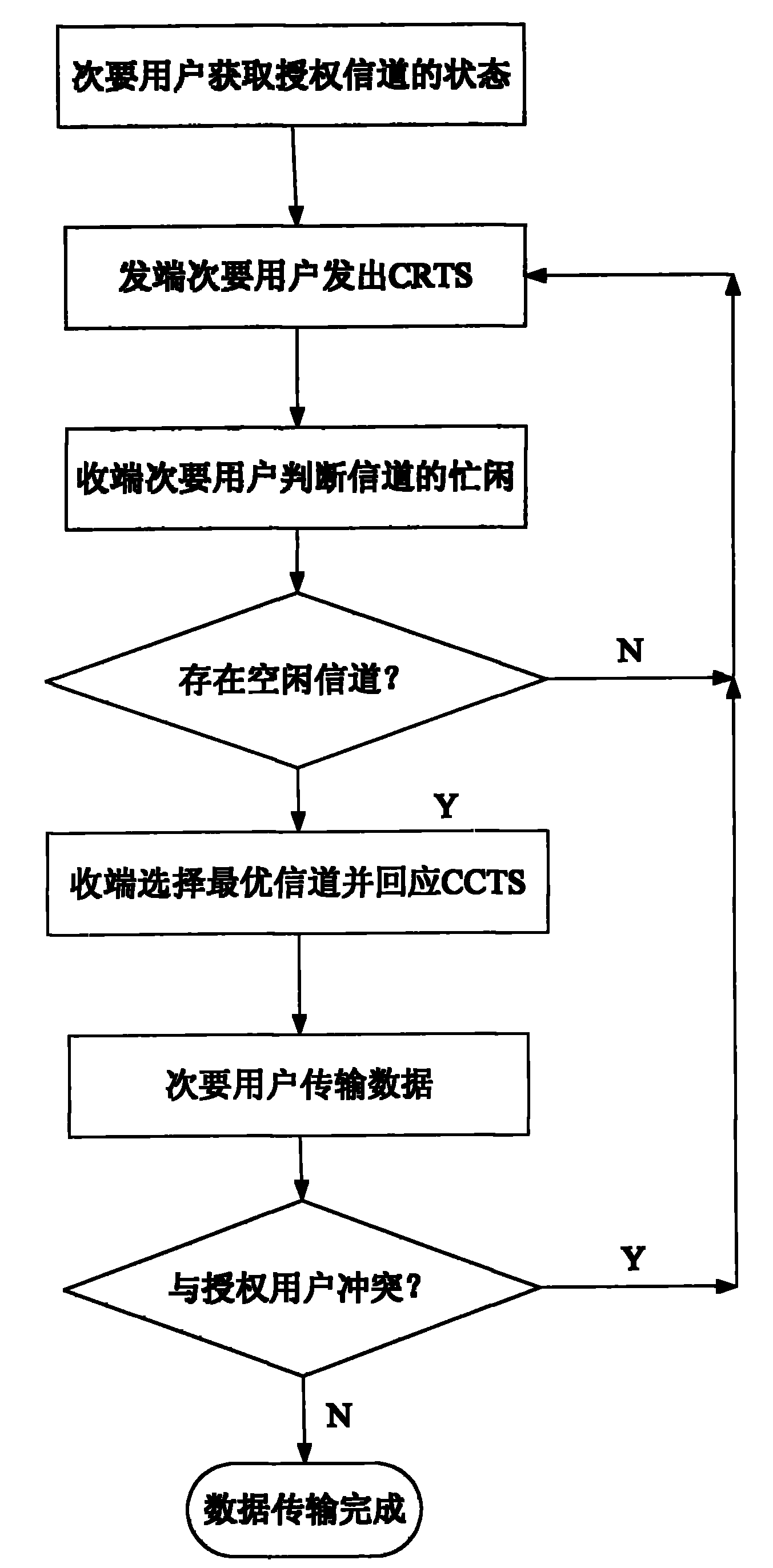
Frequency spectrum access method using idle channel in cognitive radio network
The invention provides a frequency spectrum access method using communication of a selected idle authorized channel in a cognitive radio network. The method comprises the following steps: periodically perceiving a plurality of authorized channels and recording channel states which comprise a busy / idle state, utilization rate and waiting time by using each secondary (non-authorized) user in the cognitive radio network; and interacting control frames by the secondary users at transceiving two ends, calculating the maximum time that the secondary users can be accessed to the idle channels according to the utilization rate of the idle channels in the current network, selecting the idle authorized channel capable of transmitting maximum traffic, and performing communication between the secondary users on the selected channel. The method can solve the problems of a 'hidden' terminal and an 'exposed' terminal at the same time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Heterogeneous network adaptive data communication method and sensor network multi-protocol gateway
InactiveCN102624621AAccess capacity restrictionTroubleshoot managementNetwork connectionsWireless communicationStructure of Management InformationNetwork management
The invention relates to a sensor network multi-protocol gateway, which comprises receiving subnet gateways corresponding to front-end sense networks, a front-end sense network management main gateway, and a topology management gateway, wherein the receiving subnet gateways are used for networking through searching different front end structures or protocol network node signals in a multi-protocol network manner so as to establish the front-end sense networks, and realizing communication between the same network nodes through route selection; the front-end sense network management main gateway is respectively connected with the receiving subnet gateways, and is used for distributing routing information for the receiving subnet gateways, and forming a multi-path network for maintaining a routing relation between the receiving subnet gateways so as to establish communication between the front-end sense networks; and the topology management gateway is used for establishing communication between the front-end sense networks and rear-end equipment or network. The gateway realizes the efficacy of data receiving of a multiple network protocol and network routing of a multi-type heterogeneous network, and overcomes the limitation of access capability of the front-end sense networks in the prior art, so that the front-end sense networks are mutually connected and communicated.
Owner:上海宜云物联科技有限公司
Method for collaborative discrimation between authentic and spurious signals in a wireless cognitive network
InactiveUS20100317391A1ConfidenceImprove discriminationRadio transmissionSecurity arrangementPattern recognitionFall time
A WRAN discriminates between authentic incumbent and spurious / malicious signals by collaboratively sensing the frequency environment, classifying and fusing the sensed results, and categorizing each signal as valid or invalid. Embodiments categorize signals according to reports from at least two nodes, thereby increasing detection confidence and resisting denial-of-service attacks. A “voting-rule” can be applied whereby a signal is authentic only if it is detected by a specified percentage of the nodes. Some embodiments categorized signals by comparing sensed analog signal properties, such as amplitude, bandwidth, pulse width, mean, variance, modulation, standard deviation, moments, cumulants, and rise and fall times, with properties of known incumbents and / or known incumbent types. Sensed results can be weighted according to known node locations and / or local topology, sensed signal strengths, and comparisons of sensed analog features with corresponding features of known incumbents and / or known incumbent types in the same class.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
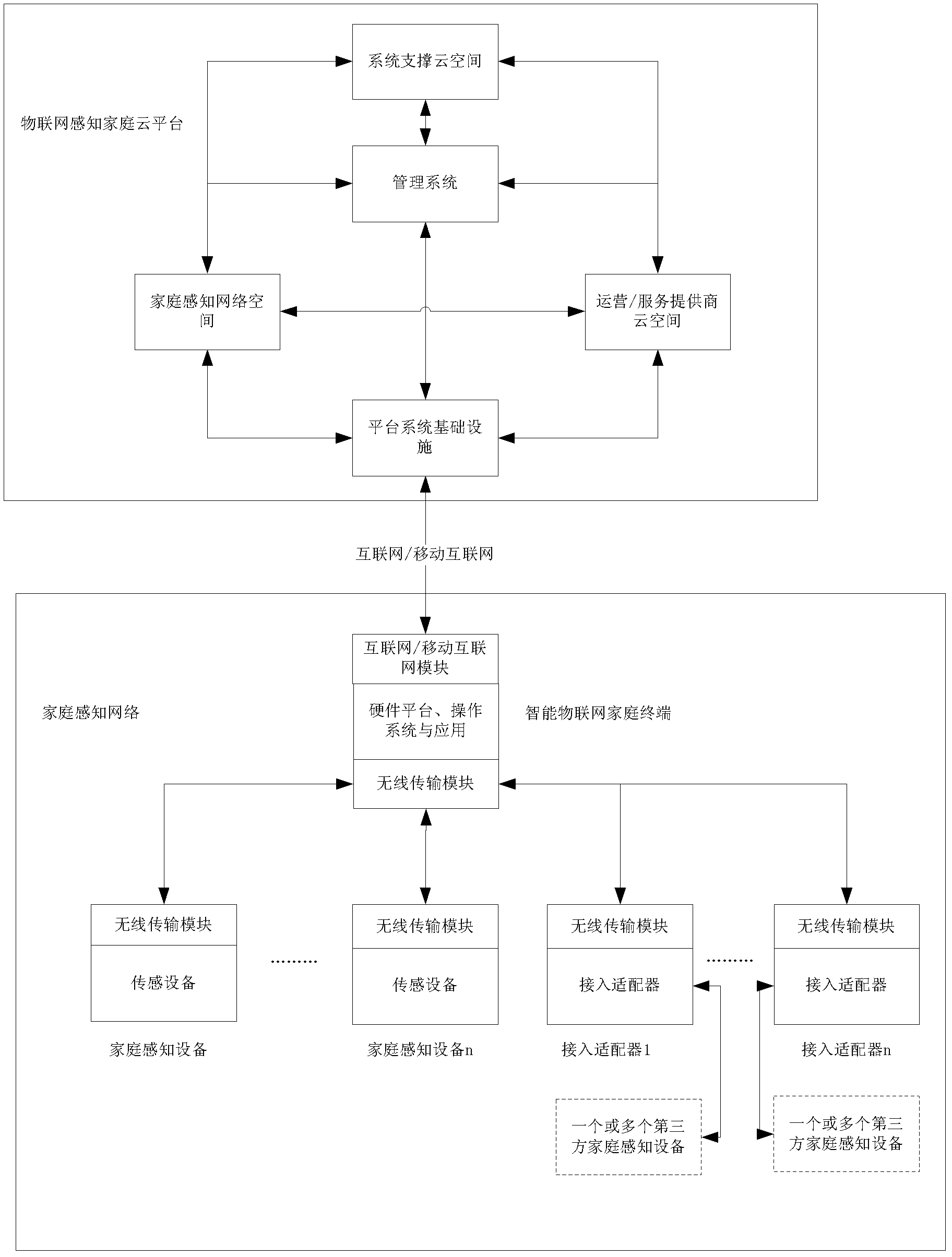
IOT sensing family cloud platform system
InactiveCN102624925AEasy to installEasy to install and deployData switching by path configurationWireless transmissionDistributed services
The invention discloses an IOT (Internet of things) sensing family cloud platform system which comprises an IOT sensing family cloud platform and a family sensing network which are connected by a network. The family sensing network comprises various family sensing equipment, a plurality of access adapters and a family IOT intelligent terminal which are networked by a wireless transmission module with an intelligent self-networking function; the family IOT intelligent terminal is used for connecting the IOT sensing family cloud platform with the family sensing network as a gateway; and the IOT sensing family cloud platform comprises a platform system infrastructure, an operation management system, a family sensing network cloud space, an operator / service provider cloud space and a system supporting cloud space. The system integrates the family sensing network with the IOT sensing family cloud platform by utilizing a software / hardware integrated assembly technology to form an integrated distributed service system structure and a sensing family system which can be interconnected, is easy to expand, has diversified services and can provide the high-quality services is constructed.
Owner:江苏运赢物联网产业发展有限公司
Improved particle swarm-based power control optimization algorithm in cognitive radio network
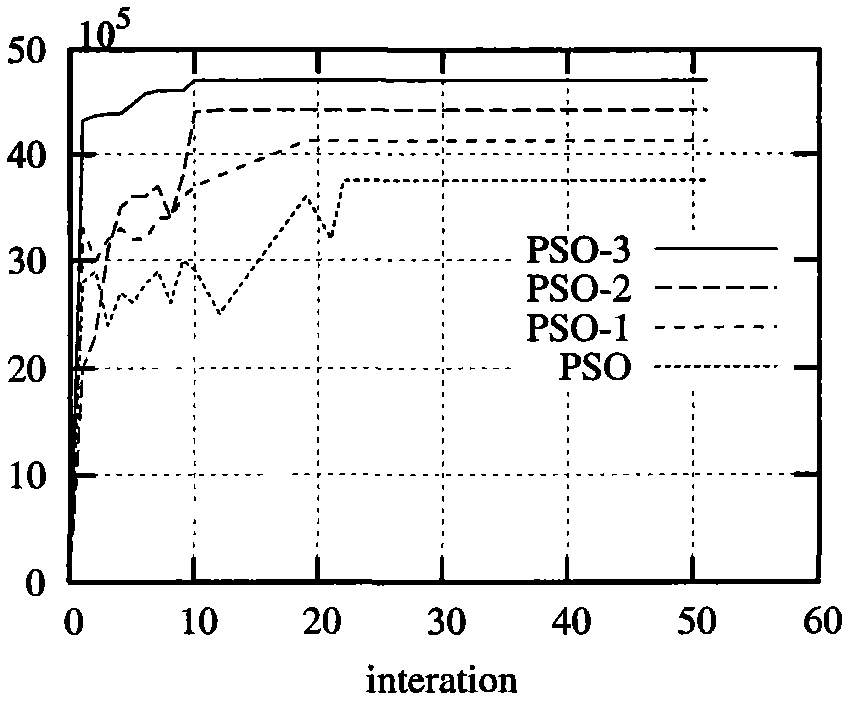
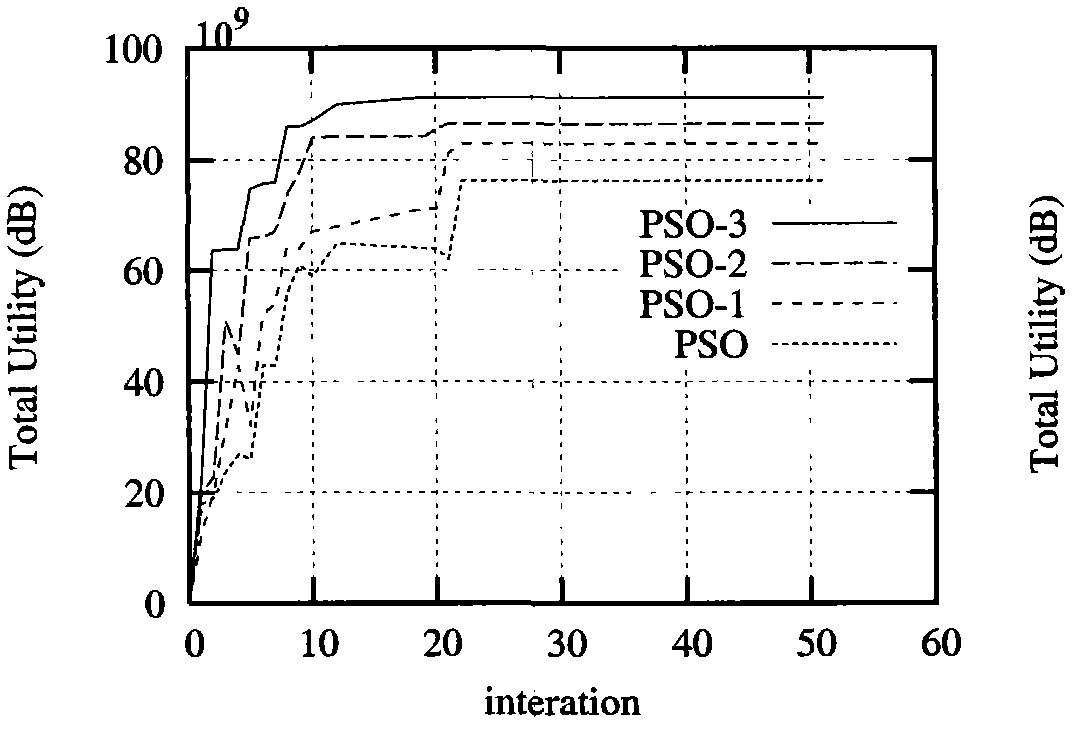
The invention relates to a power control optimization algorithm in a cognitive radio network, which belongs to the field of system resource allocation. The algorithm comprises the following steps: 1, initializing the iteration number of the algorithm, the positions and speed of particles and the basic parameters of the particle swarm; 2, calculating a fitness function value, setting the position Xa of an individual particle as the initial best position, and setting the particle with the best function value in the swarm as the initial best swarm position Gbestk; 3, searching based on a PSO algorithm, updating the best positions of the particles and the swarm and updating the speed and positions of the particles by using a fundamental formula of the particle swarm; and 4, setting a termination standard. The invention conducts study on the non-convex optimization problem controlled by the cognitive radio power and puts forward an improved particle swarm-based power control algorithm which allows utility functions such as an S-type function a convex function and the like to be non-concave, thereby conforming to the actual network better. Parameter adjustment is performed by the particle swarm algorithm to guarantee the global astringency of the algorithm. The algorithm of the invention has better validity and rapidity.
Owner:LUDONG UNIVERSITY
Across layer self-adapting paralleling channel allocating method of cognized radio system
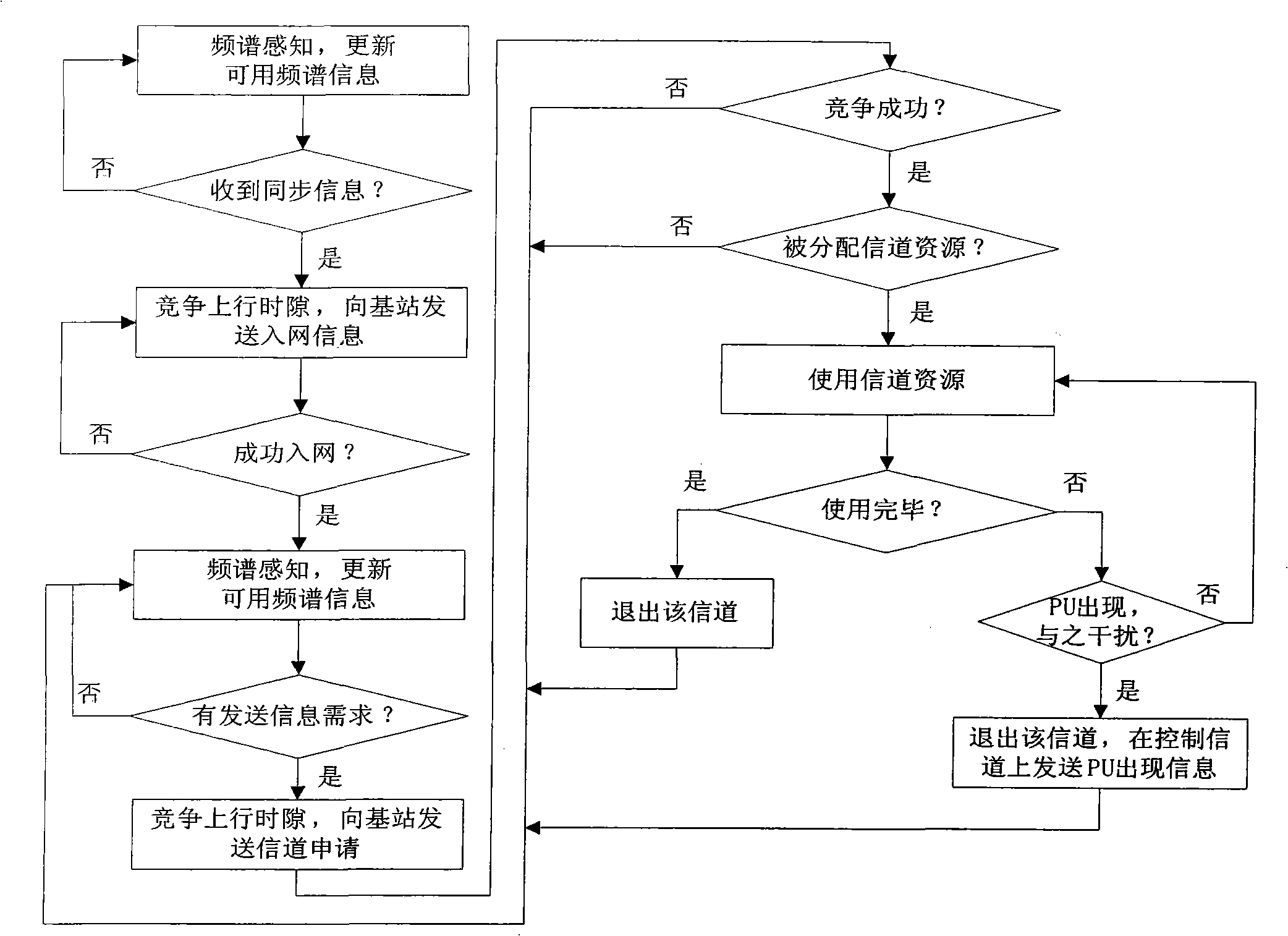
InactiveCN101257714AReduce distractionsIncrease capacityRadio/inductive link selection arrangementsCross layerParallel channel
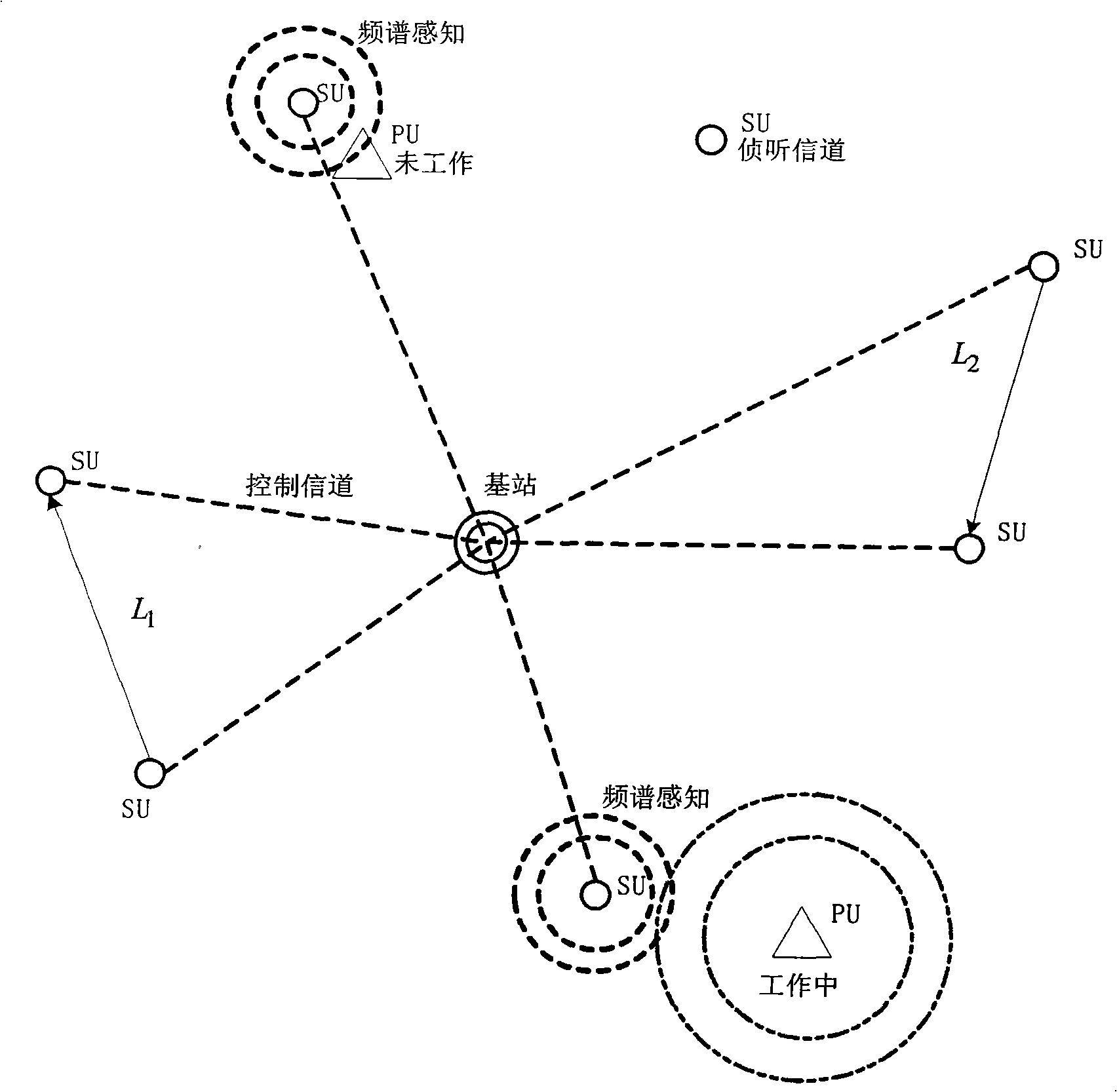
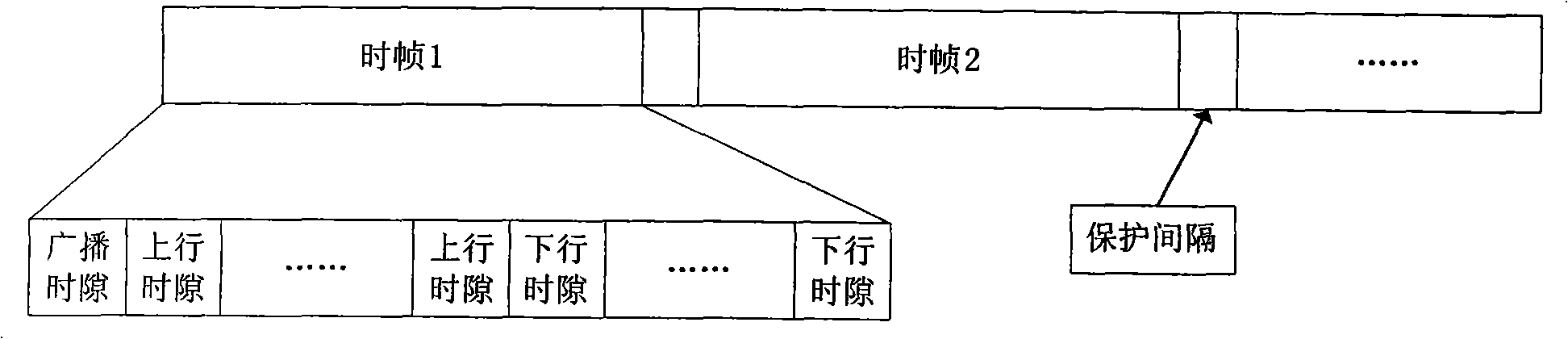
The invention provides a method for allocating cross-layer adaptive parallel channels of a cognitive radio system. The method includes steps that a base station receives channel requests of each unauthorized subscriber SU in an uplink time slot analyzes the channel request information, and allocates available channel resources adaptively on the premise that SU do not disturb each other and do not disturb patchusers PU. The invention adopts the method of dividing uplink and downlink time slots of time division duplexing TDD, analyzing the signal noise ratio information of available channel resources by the base station, adopts transmission set portion, channel parallel allocation, adaptive adjustment of the optimized channel, maximizing transmission efficiency and determining optimum transmission modes for each SU, provides optimum channel resources, and utilizes SU to monitor presence of PU in real time, reduces interference at the lowest to the PU, improves capacity of radio cognitive networks and channel utilization.
Owner:ZHEJIANG UNIV
Router for sensing bearing state and service flow bandwidth distribution method thereof
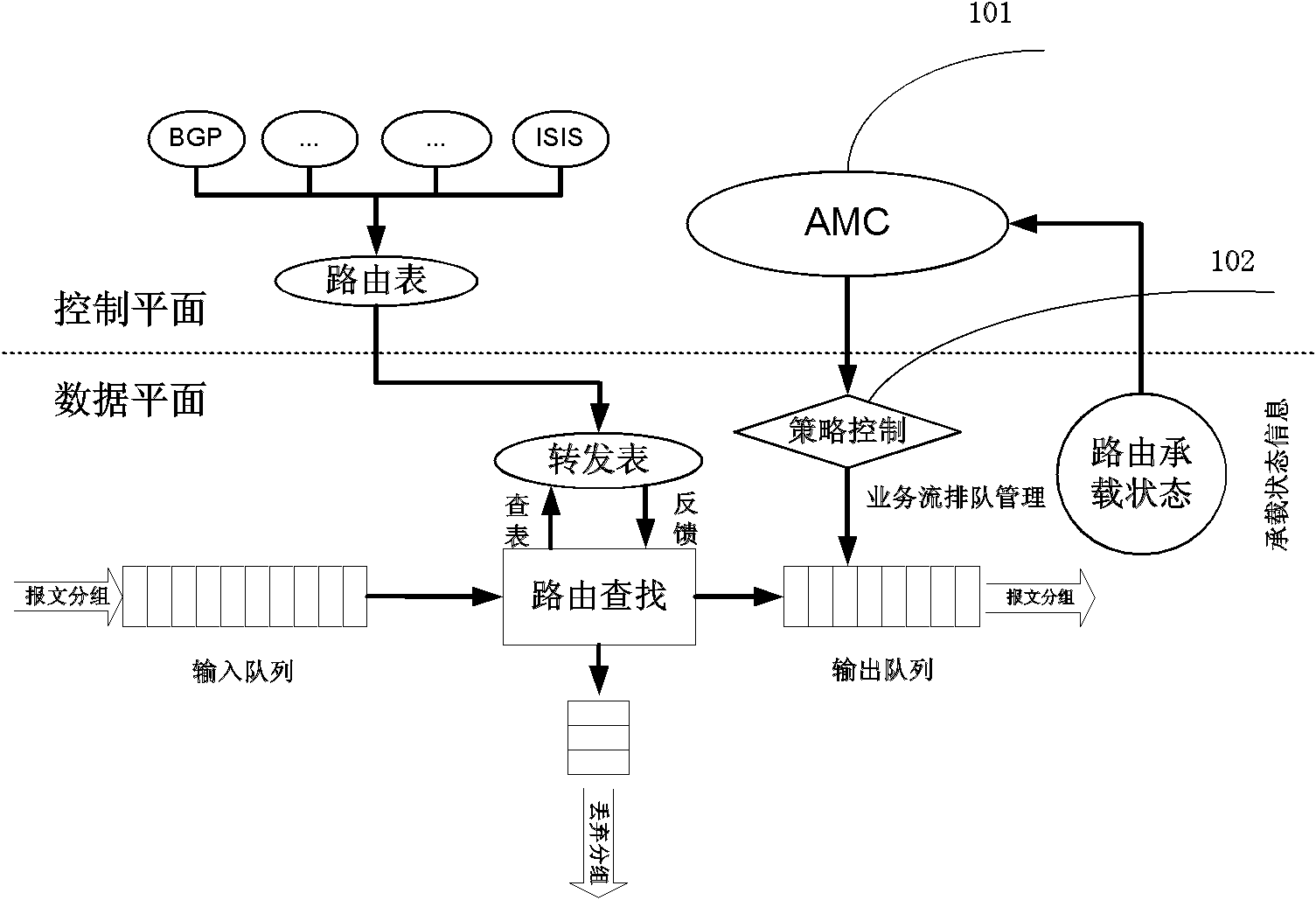
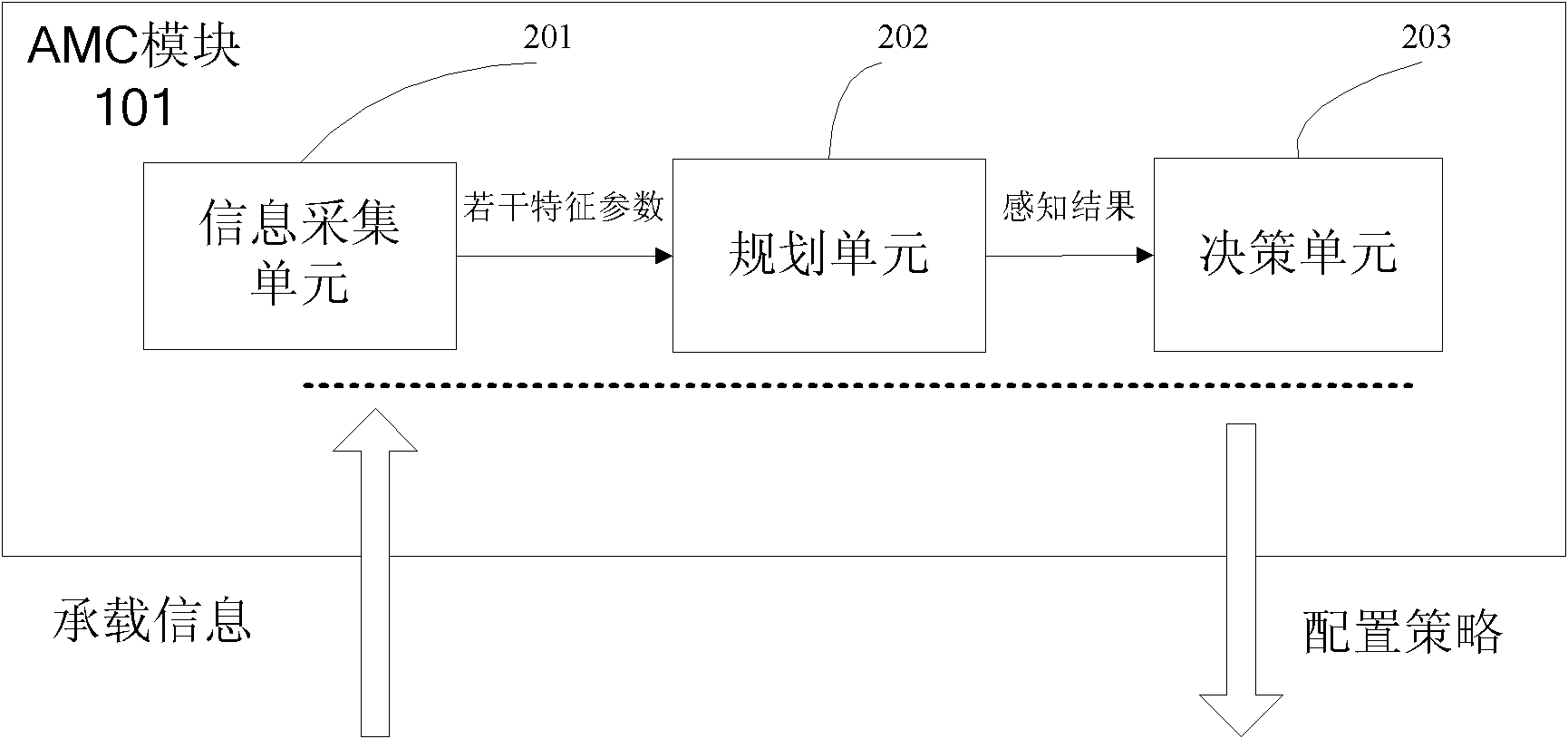
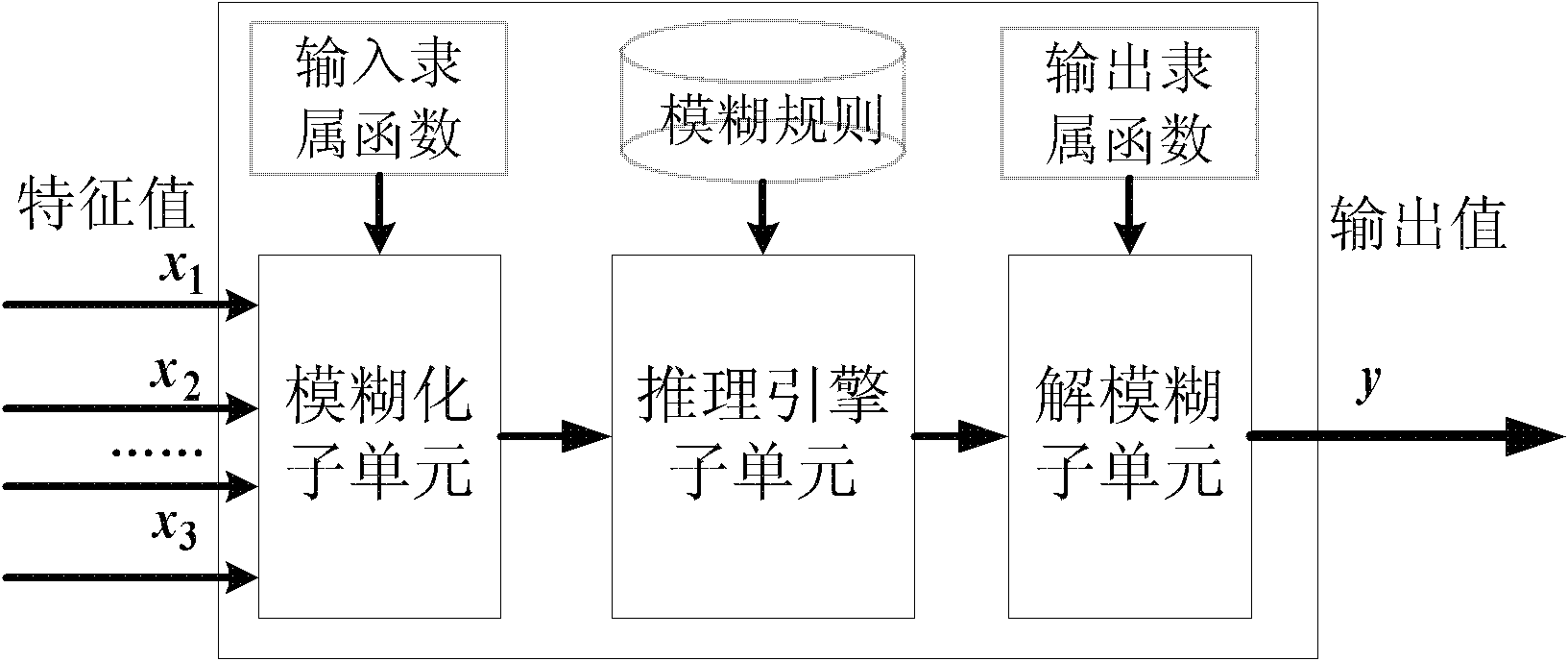
InactiveCN102739507AFully consider the characteristics of dynamic changesIncrease flexibilityData switching networksService flowCognition Network Technology
The invention provides a router for sensing a bearing state and a service flow bandwidth distribution method thereof. The method comprises: a bandwidth distribution strategy generation step for all services; to be specific, collecting bearing state information of a router and quality of service (QoS) demand information of a service flow, employing bandwidth distribution algorithm that is provided based on a cognitive network technology to carry out analyzing and processing on the collected data, and integrating a plurality of set rules and using difference of QoS demands of various service flows for reference to generate a bandwidth distribution strategy for all the services; and a step for distributing bandwidths for all the service flows; to be specific, mapping the strategy into an operation instruction that can be identified by the router according to a requirement of configuration strategy and executing the operation to change router queue management so as to carry out bandwidth distribution on the service flows. According to the invention, the cognitive network technology is utilized to realize sensing of a network bearing state and a service flow state, so that network bandwidth distribution can fully consider a dynamic changing characteristic of the network to enable the distribution mode to become reasonable.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Multi-path load balancing method based on price mechanism for industrial real-time network
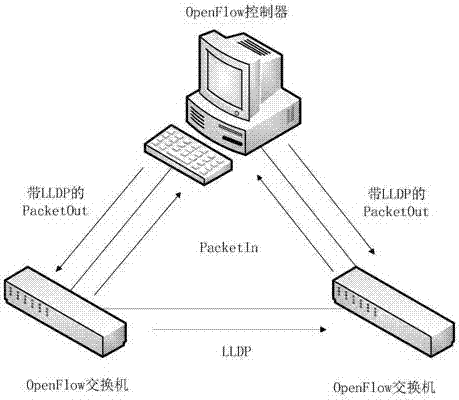
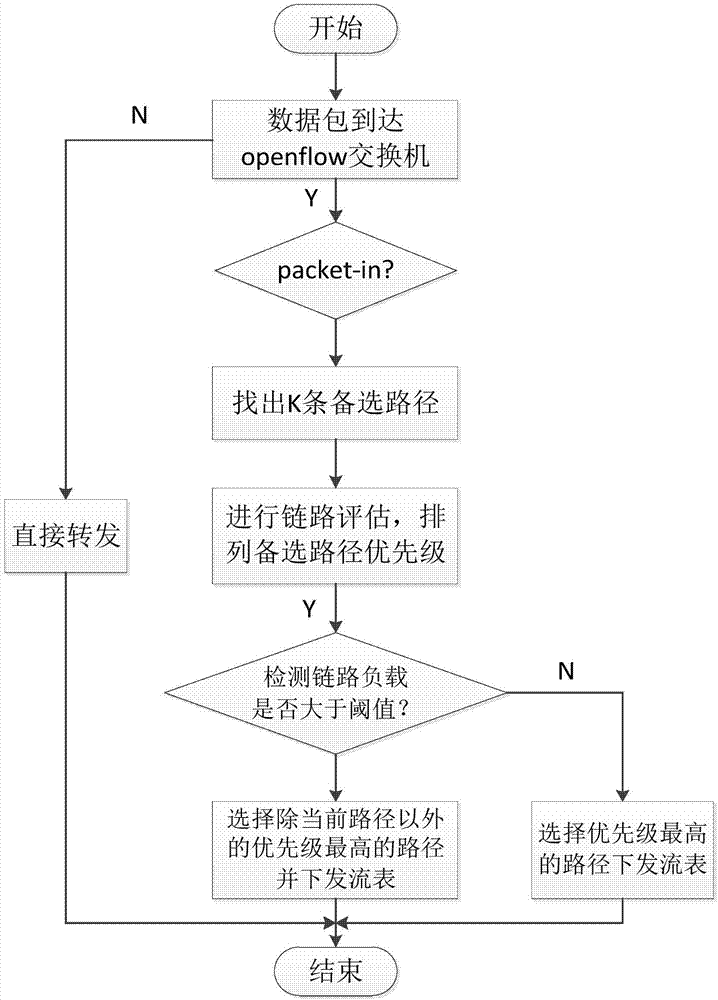
ActiveCN107959633AImprove resource utilizationReduce congestionData switching networksResource utilizationData center
The invention discloses a multi-path load balancing method based on the price mechanism for an industrial real-time network. The method specifically comprises the following steps: an RYU control sendsa data packet to sense an overall network topology; real-time bandwidth and delay monitoring is carried out through the OpenFlow protocol; k shortest paths from feasible paths are calculated throughthe KSP algorithm and used as candidate path; link evaluation is carried out on the k candidate paths, the candidate path with the optimum current link status serves as a forwarding path, and the candidate path with the second optimum current link status serves as a reserved path; the RYU controller sends a forwarding strategy for a current network flow to flow tables of corresponding switches; and the RYU controller carries out real-time link status monitoring, and when a link utilization rate is larger than a threshold, reselects the optimum path other than the current path for rerouting andsends the flow tables to the switches. The method provided by the invention has the advantages that the network resource utilization rate can be improved, and network congestion can be reduced; and an SDN controller is used for whole network monitoring on a data center, and the forwarding path is selected according to current real-time network conditions, so that dynamic multi-path load balancingcan be achieved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
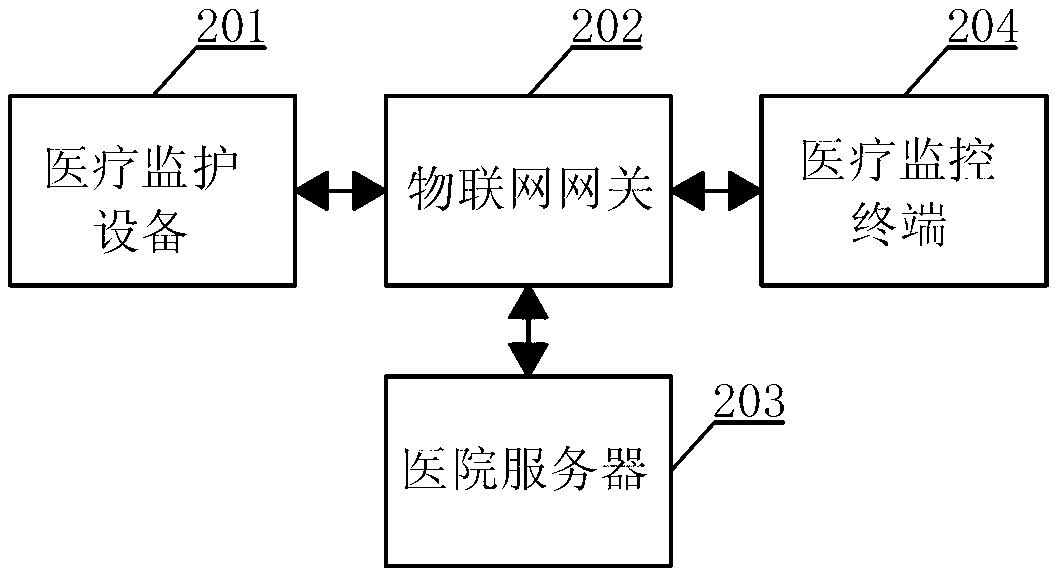
Internet-of-things gateway and medical monitoring system comprising same
InactiveCN103237085ARealize monitoringBroad access capabilityNetwork traffic/resource managementDiagnostic recording/measuringSensing dataIot gateway
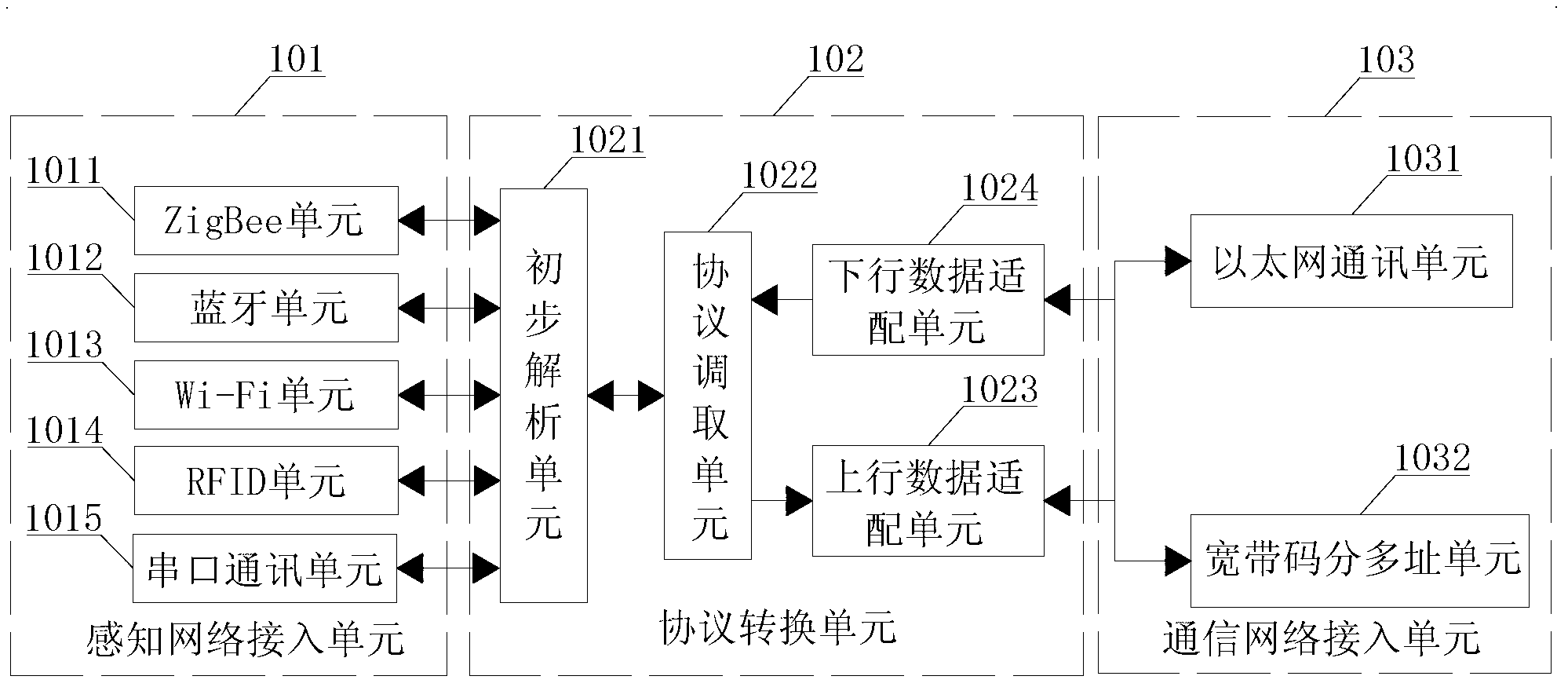
The invention discloses an internet-of-things gateway and a medical monitoring system comprising the same. The gateway comprises a sensing network access unit, a protocol conversion unit and a communication network access unit, wherein the sensing network access unit is used for receiving sensing data input by sensing equipment; the protocol conversion unit is used for analyzing the sensing data, calling a data adapting protocol according to an analysis result, coding the data subjected to secondary analysis by using a ubliquitous machine to machine protocol (UMMP) after performing secondary coding on the sensing data according to the data adapting protocol and outputting the coded sensing data to the communication network access unit; and the communication network access unit is used for selecting an access mode of the data and outputting the coded sensing data to the internet-of-things management platform in the access mode. The system has wide access capability and strong protocol conversion capability, so that the medical monitoring system comprising the internet-of-things gateway can be connected with the medical monitoring equipment supporting an international medical standard protocol to realize comprehensive monitoring on a patient.
Owner:晁彦公 +1
System and Method for Monitoring Information in a Network Environment
InactiveUS20060252410A1Eliminate and greatly reduce disadvantageEliminate and greatly reduce and problemUnauthorised/fraudulent call preventionEavesdropping prevention circuitsEnd userReal-time computing
A method for monitoring information in a network environment is provided that includes receiving one or more packets from a communication flow initiated by an end user. The information associated with the communication flow is then selectively communicated to a plurality of client-aware network elements.
Owner:CISCO TECH INC
Cooperative cognitive radio spectrum sensing using a hybrid data-decision method
ActiveUS20150181436A1Radio transmissionTransmission monitoringSpectrum availabilityFrequency spectrum
A spectrum sensing method for cognitive radio to detect spectrum holes in an environment of bandwidth scarcity. The method comprises first receiving a wireless signal at a cognitive radio user, and then discovering the frequency edges of allocated frequency bands by using wavelet transform coefficients to detect discontinuities in the power spectral density of the received signal. After determining the allocated frequency bands, the method determines frequency band availability by detecting the in band energy using a bi-threshold energy detector, where the energy detector makes hard decisions and soft decisions. Finally, a fusion center combines hard and soft decisions collected from a cooperative spectrum sensing network of cognitive radio users and makes a final decision using a hybrid of data fusion and decision fusion to determine the final decision regarding spectrum availability.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Cognitive IP radio with repeaters
InactiveUS20090190508A1Frequency-division multiplex detailsTime-division multiplexTransceiverEngineering
An operational mechanism enables extending the range of cognitive networks through the use of repeater transceivers and selective routing.
Owner:BONE VALLEY PATENTS
Method for spectrum sensing in cognitive radio networks with open wireless architecture
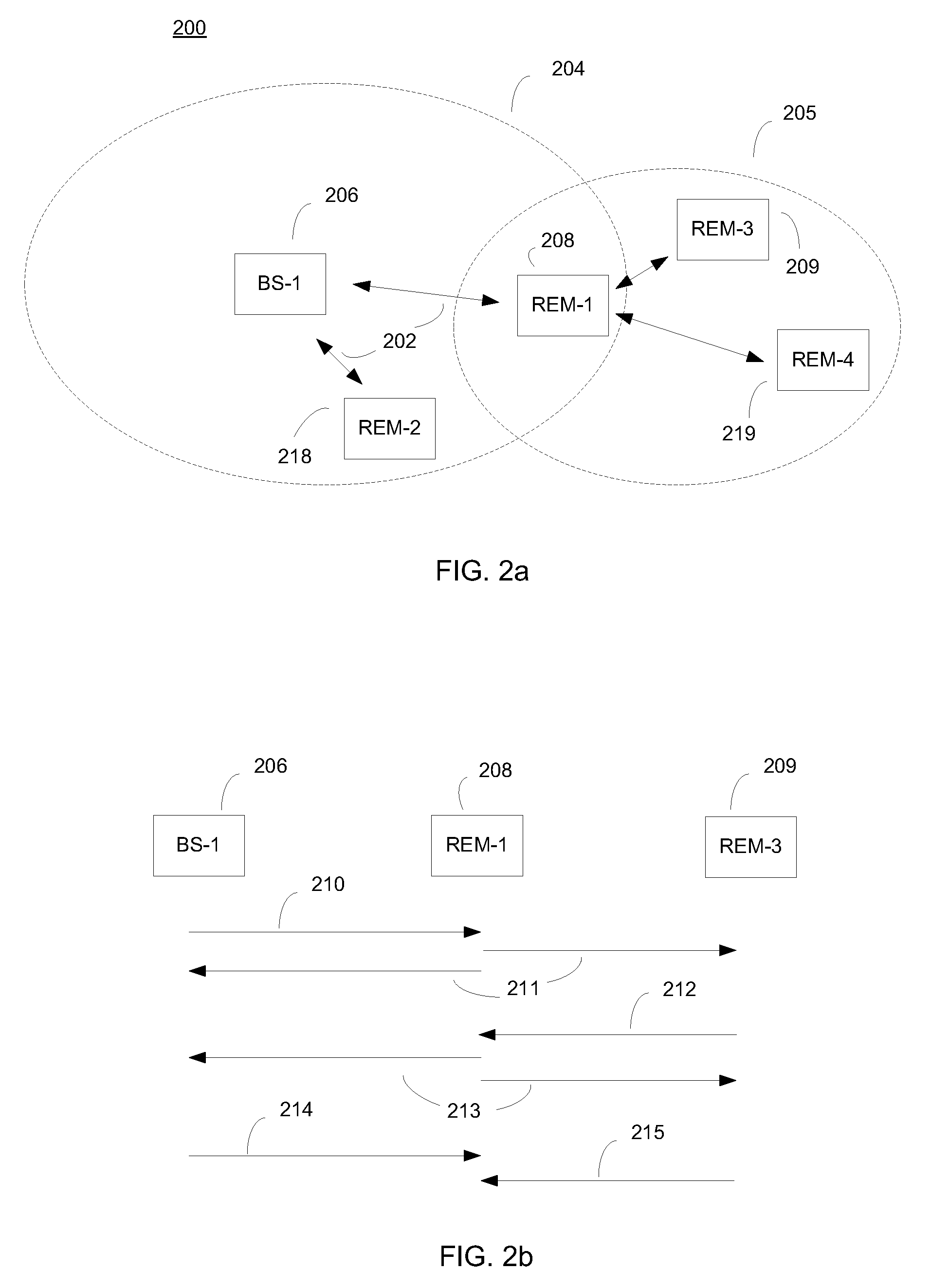
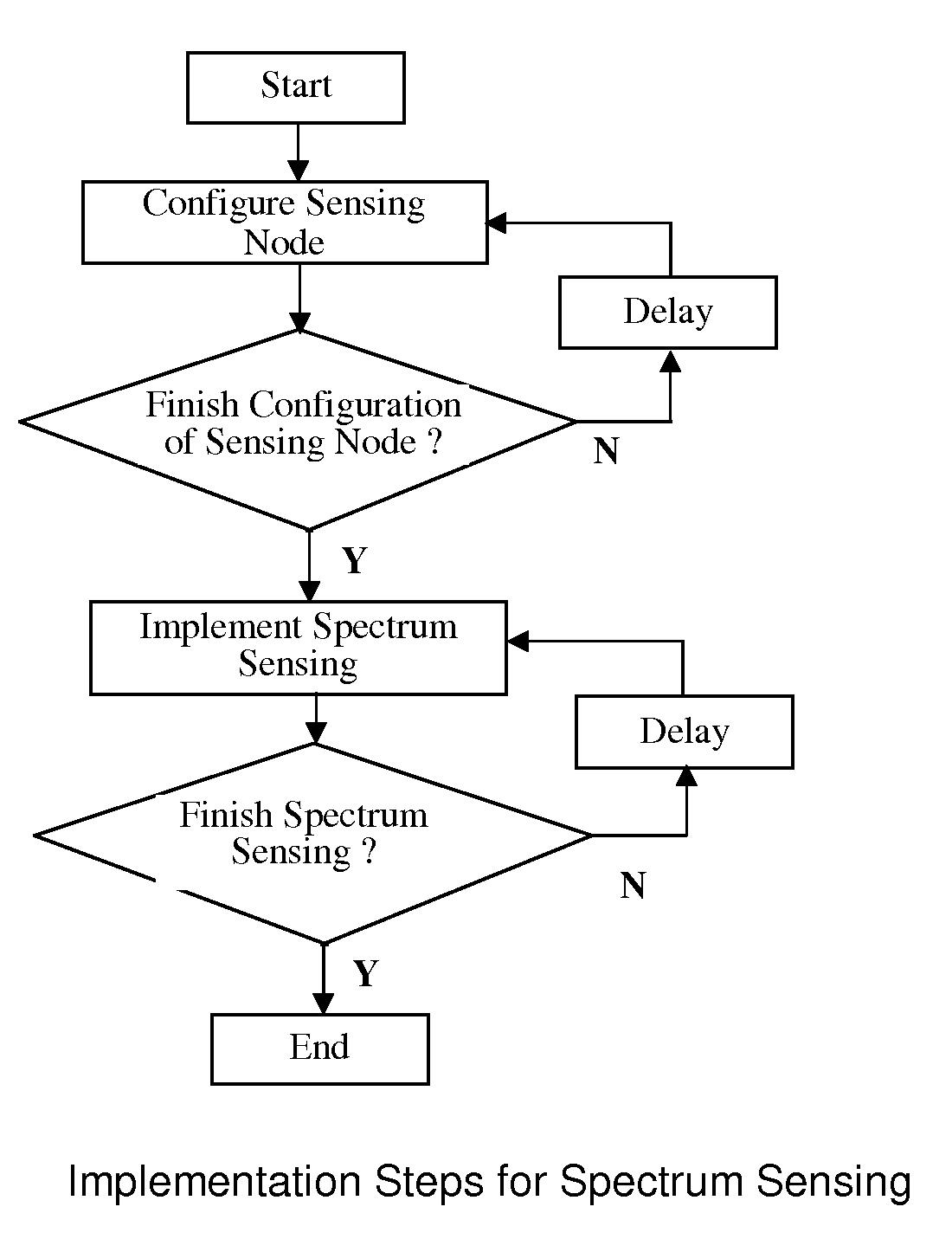
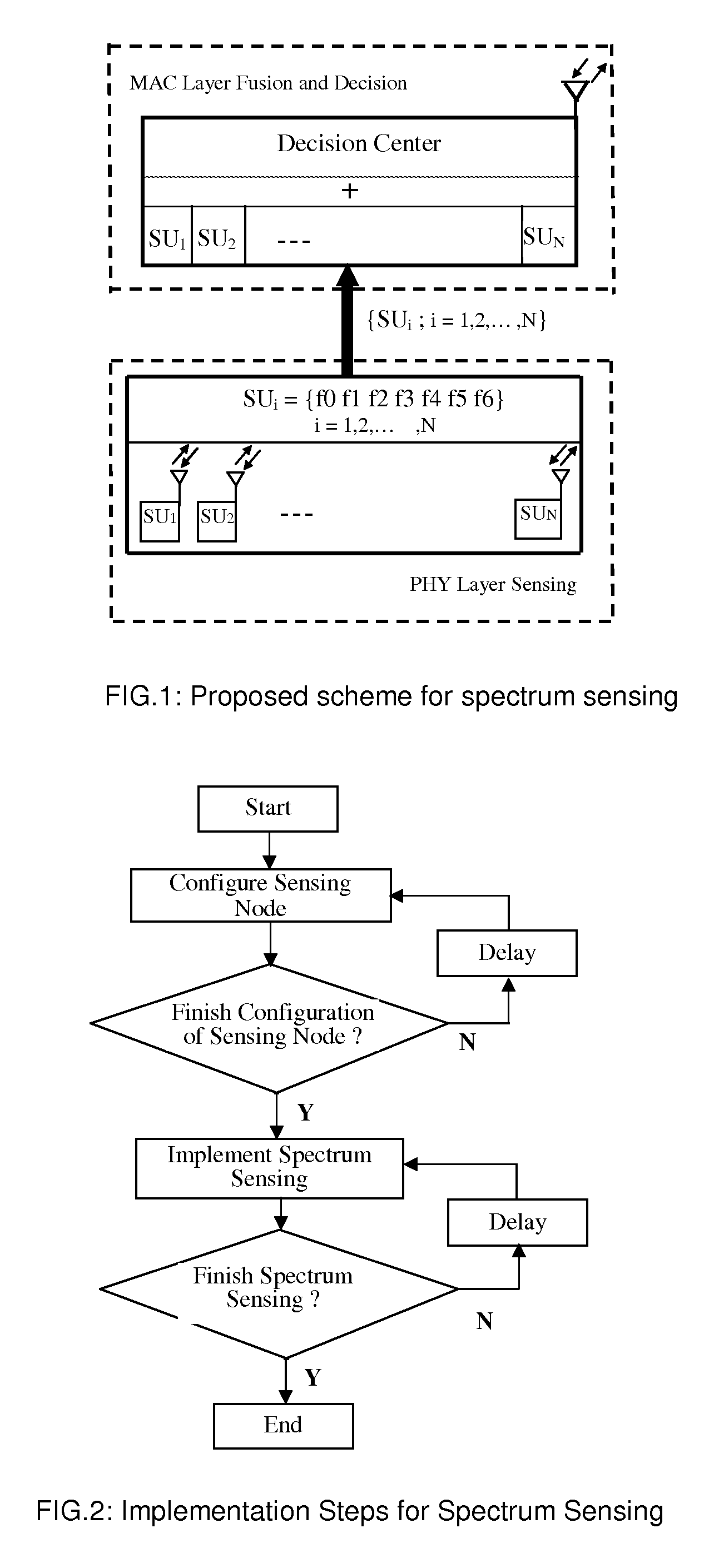
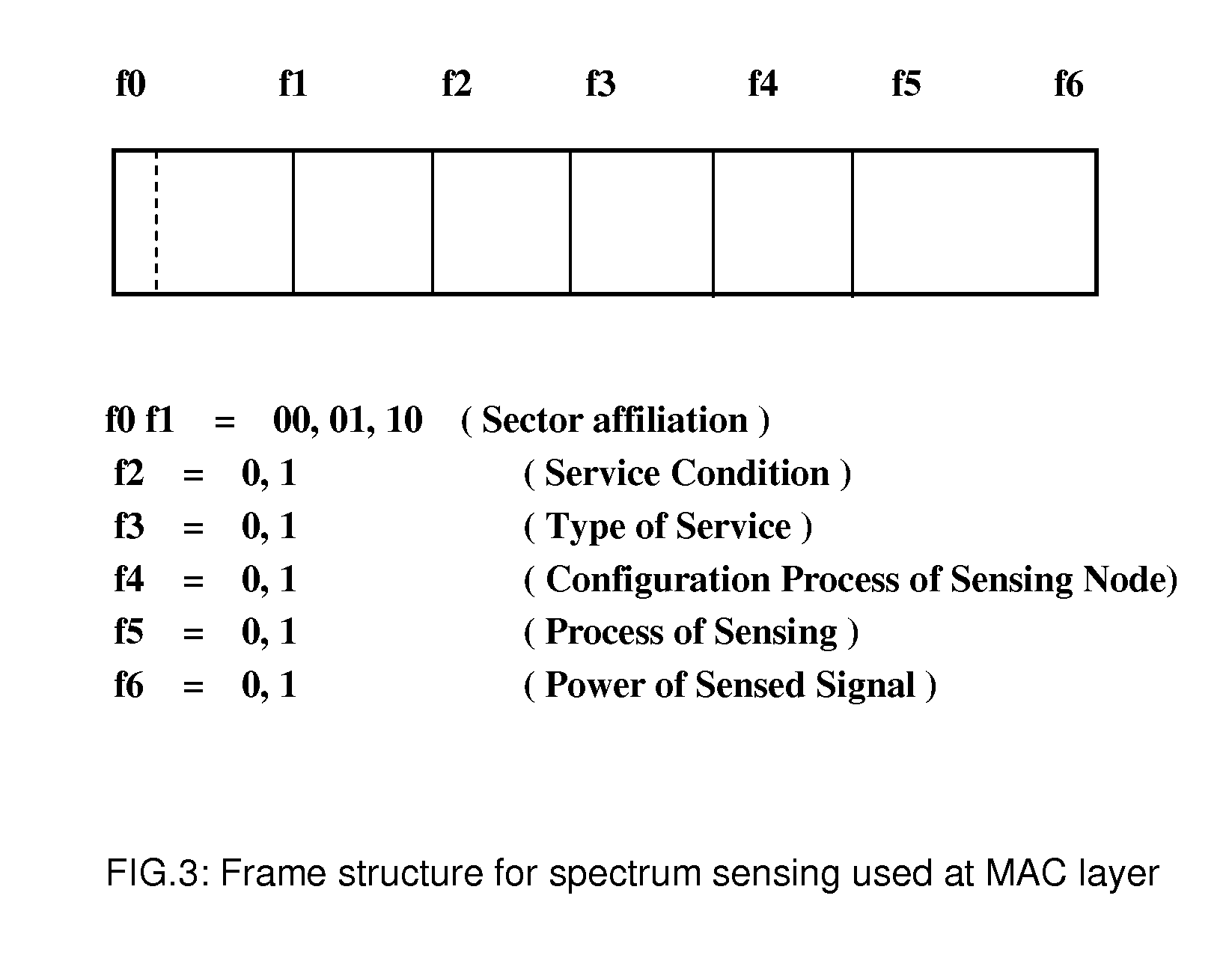
This invention relates to a method for controlling location distribution of sensing nodes, selection of sensing nodes, control of sensing implementation and process of performing spectrum sensing in cognitive radio networks of open wireless architecture (OWA) systems. Specifically, the invention relates to an efficient and reliable method minimizing time overhead consumed during spectrum sensing with open wireless architecture (OWA).
Owner:PALO ALTO RES
Wireless communications method and apparatus
ActiveUS20100296404A1Easy maintenanceReduce battery consumptionPower managementError preventionTelecommunicationsWireless network
The invention relates to a method of accessing a channel in a wireless network having a plurality of communication nodes, the method comprising identifying a first channel available for use, forming a cognitive network to manage utilisation of said first channel, said cognitive network comprising a leader node and at least one of said plurality of said communication nodes, managing said cognitive network by means of said leader node including identifying a second channel available for use in an event that said first channel being no longer available for use, and switching to said second channel upon said second channel being identified.
Owner:KK TOSHIBA
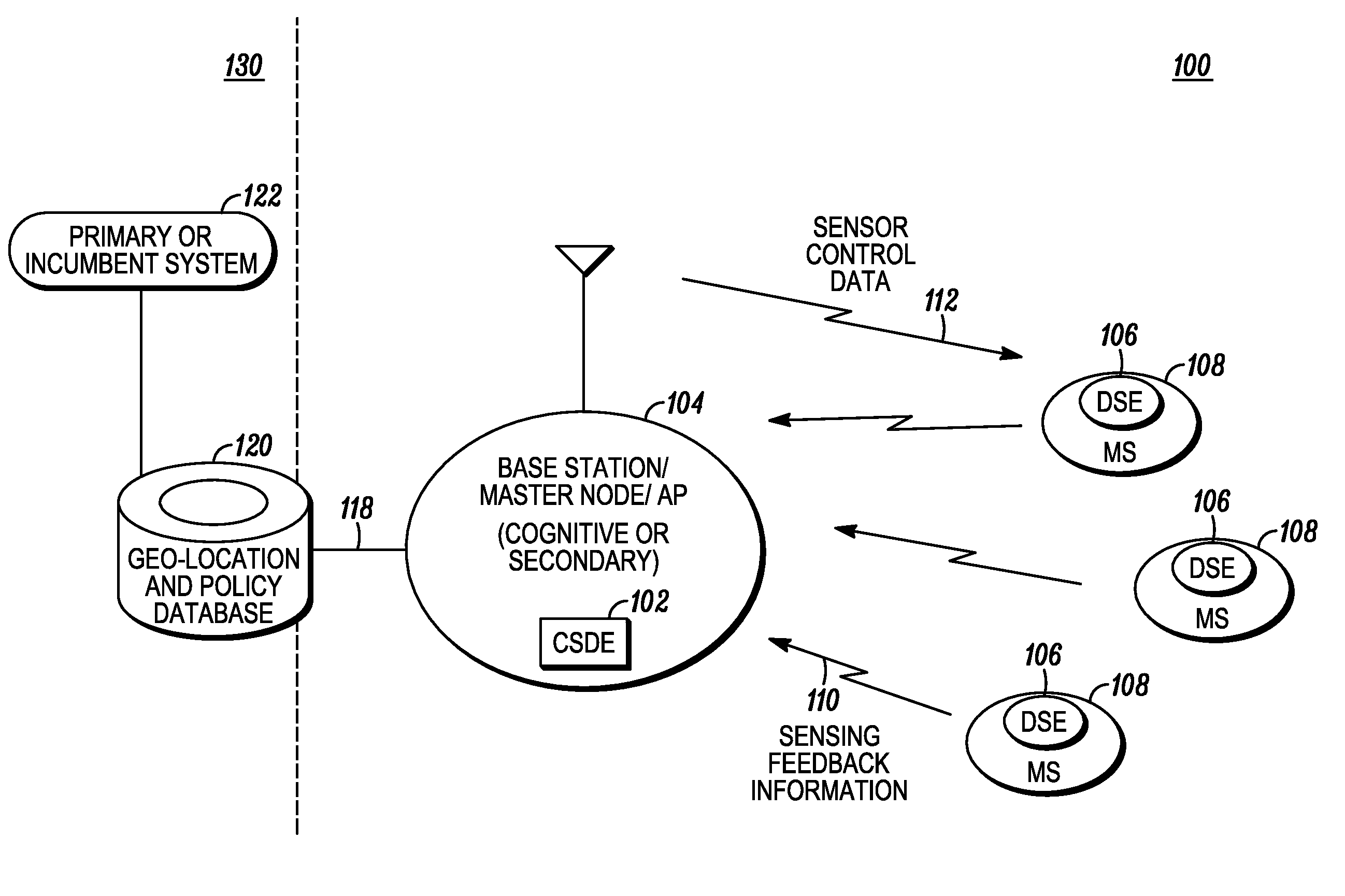
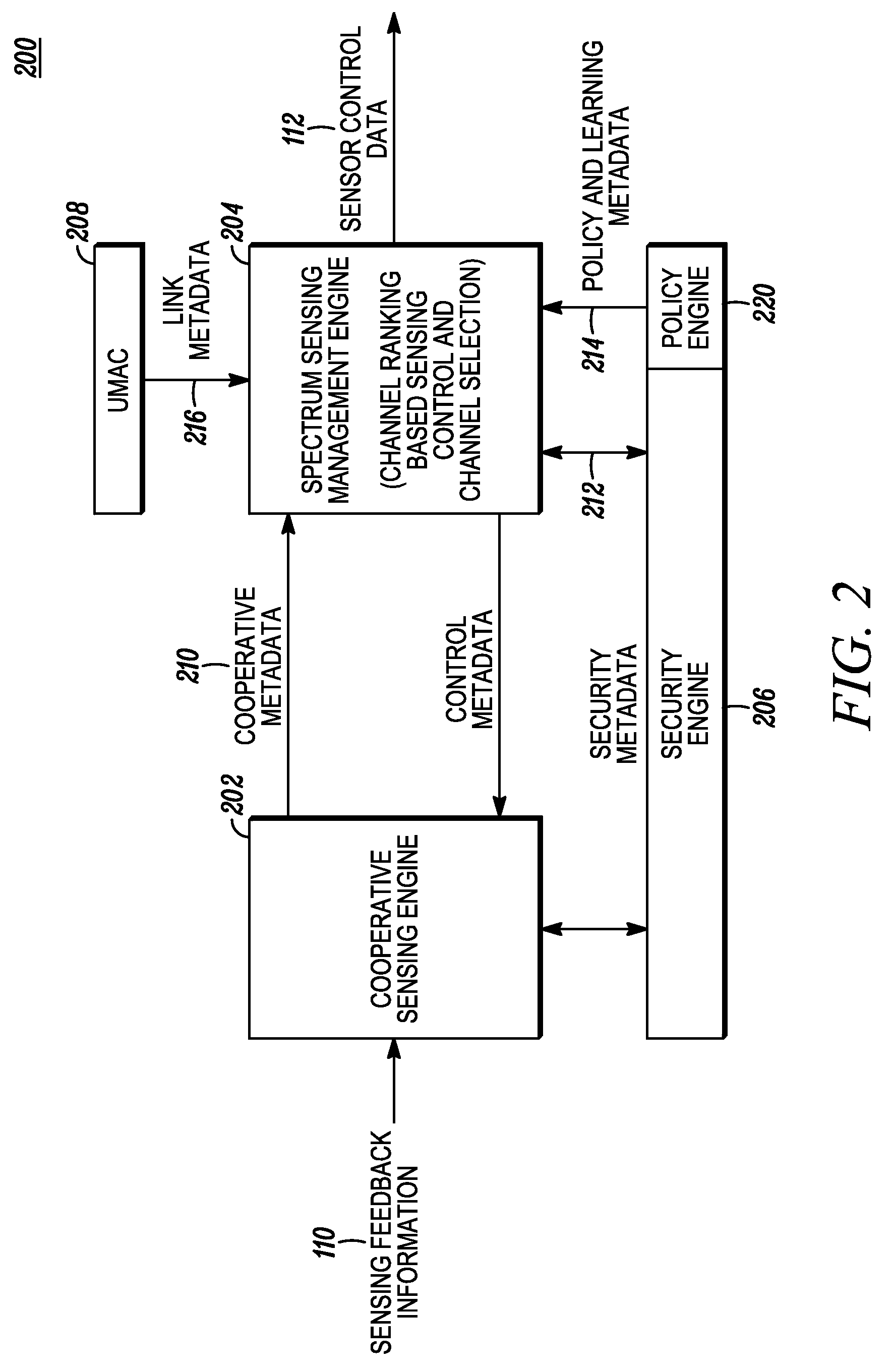
Method and apparatus for distributed sensing management and control within a cognitive radio network
ActiveUS8150328B2Transmission control/equalisingTransmission monitoringCommunications systemFrequency spectrum
A technique for spectrum sensing management and control for a secondary communication system seeking to utilize another communication system's spectrum is provided (600). Sensor control data is sent from a base station to subscriber units (604). Sensing measurements are taken and sent back to the base station for ranking (608) as sensed feedback information. Comparisons of the sensed feedback information are made to each other and to thresholds aligned with the types of measurements taken (610). An initial ranked channel list is generated (612). Weighting of the initial ranking list and secondary ranking list is followed by re-ranking the channels according to the weighting into a final ranking list (612). The final ranking list is transmitted to the mobile units to enable operation within the other communication system's spectrum within interfering with that system (614). The weighting is based on the type of sensing measurement taken as opposed to the channel.
Owner:MOTOROLA SOLUTIONS INC
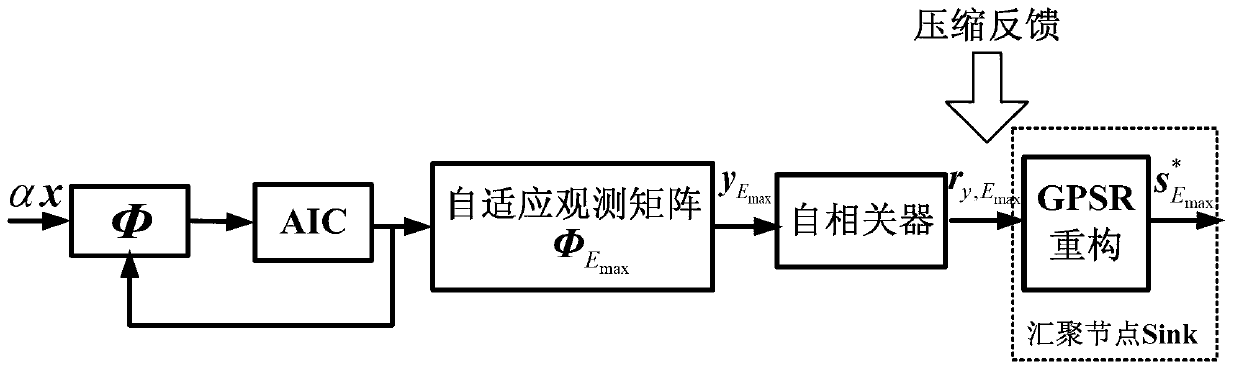
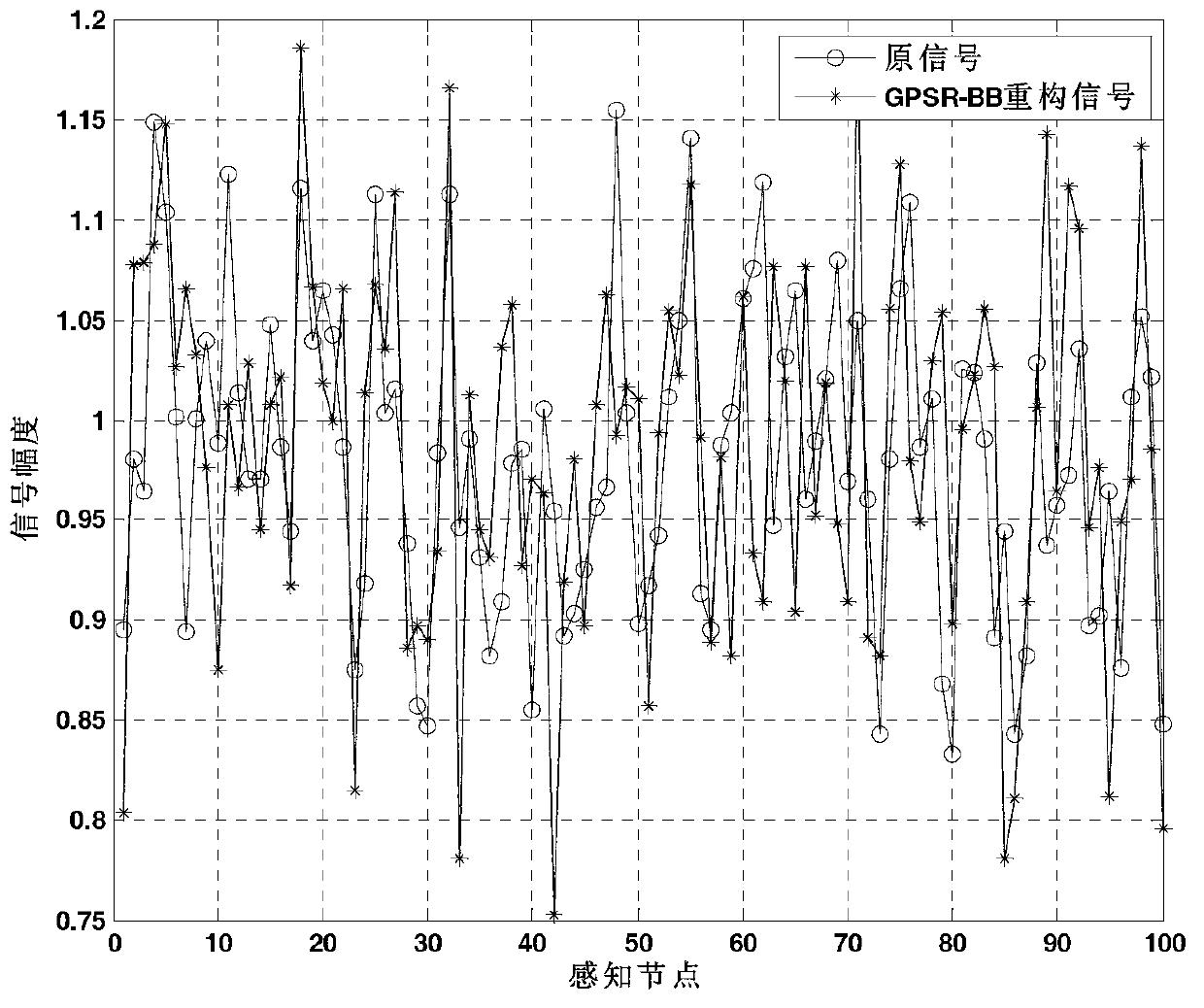
Self-adaptation compression reconstruction method based on energy effectiveness observation in cognitive sensor network
InactiveCN103347268AConsider energy efficiencyTaking into account effectivenessNetwork topologiesHigh level techniquesAdaptive compressionNODAL
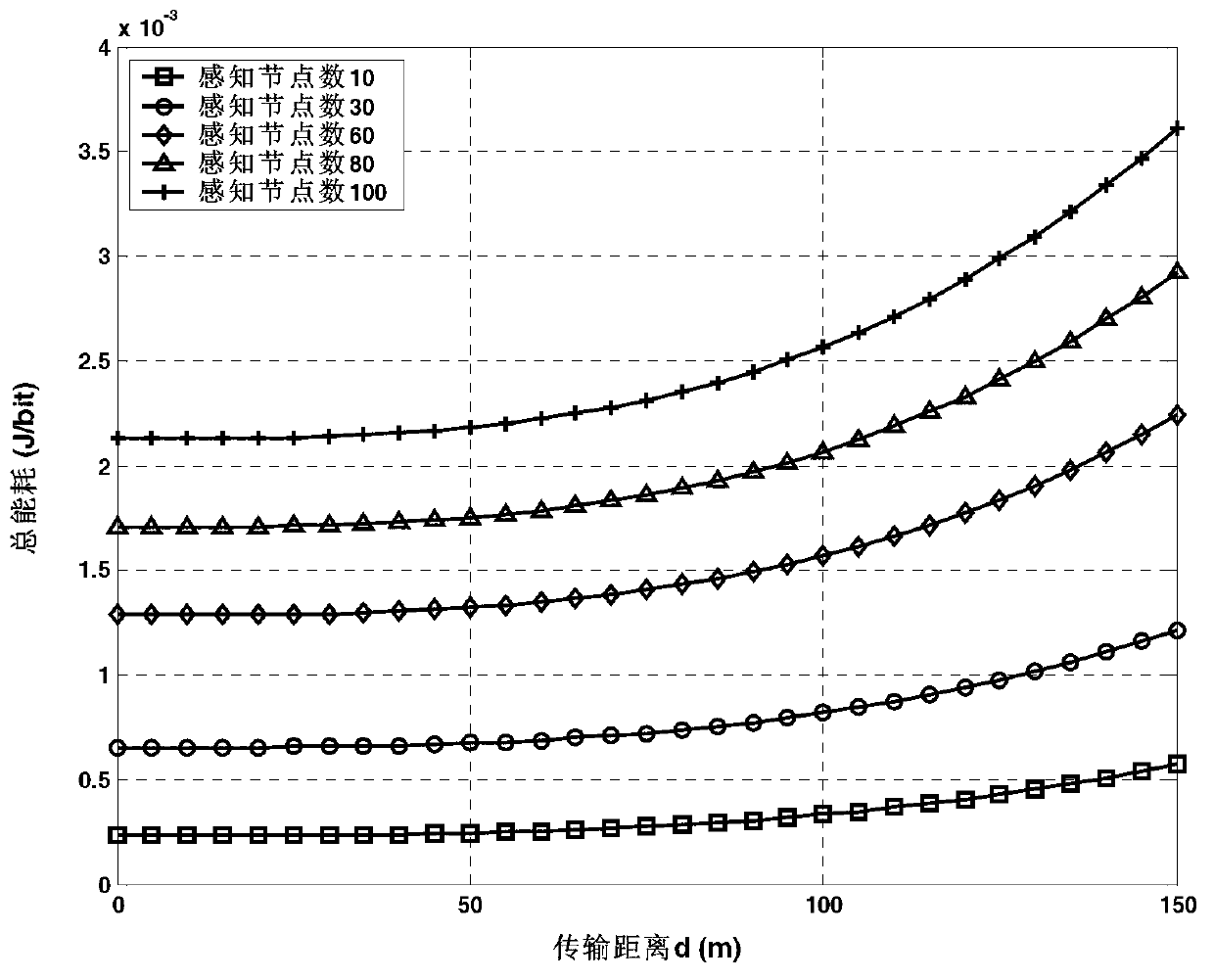
The invention discloses a self-adaptation compression reconstruction method based on energy effectiveness observation in a cognitive sensor network. The self-adaptation compression reconstruction method based on the energy effectiveness observation in the cognitive sensor network comprises the steps that (1) a node carries out local detection and compression measurement on data which are actually sensed through an analog transcriber according to the characteristic that power consumption of the node of a cognitive sensor is limited, (2) a space-time relevance structure of sensing signals is used, sensing data are mapped to a wavelet orthogonal basis cascading dictionary to carry out sparse conversion and to carry out self-adaptation observation through a weighting energy subset function, appropriate observation values are obtained in an energy effectiveness mode, orthogonalization is carried out on selected observation vectors to construct a measurement matrix, (3) the sensing data after compression measurement are fed back to an aggregation node through a report channel, the aggregation node carries out self-adaptation reconstruction on the sensing data by using a gradient projection sparse reconstruction Barzilai-Borwein method based on a convex relaxation method, and effective compromise between reconstruction performance and energy consumption of the node is achieved. The self-adaptation compression reconstruction method based on the energy effectiveness observation in the cognitive sensor network can carry out accurate reconstruction on the sensing signals, ensures energy effectiveness of the sensing node, and has actual application significance.
Owner:HANGZHOU DIANZI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com