SYN flooding attack defence method based on connection request authentication
A technology for connection request and connection establishment, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as unresolved, modified operating system kernel source code, and inconsistent TCP connection status between client and server.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
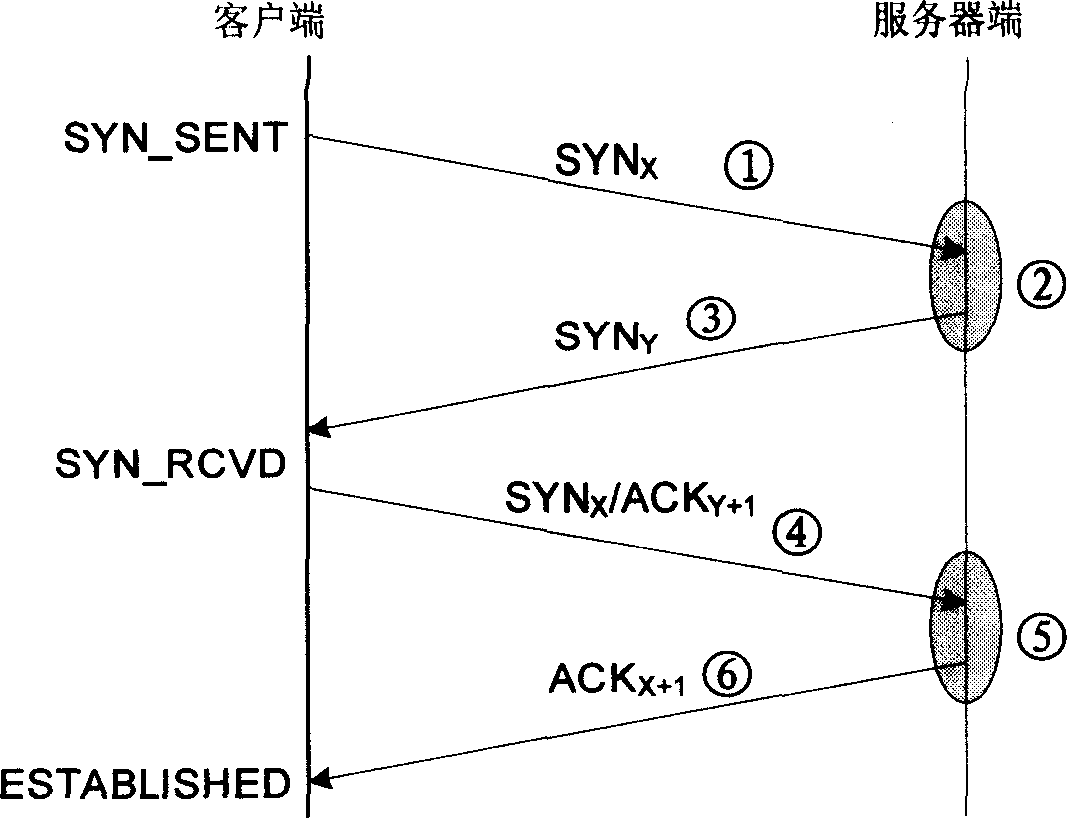
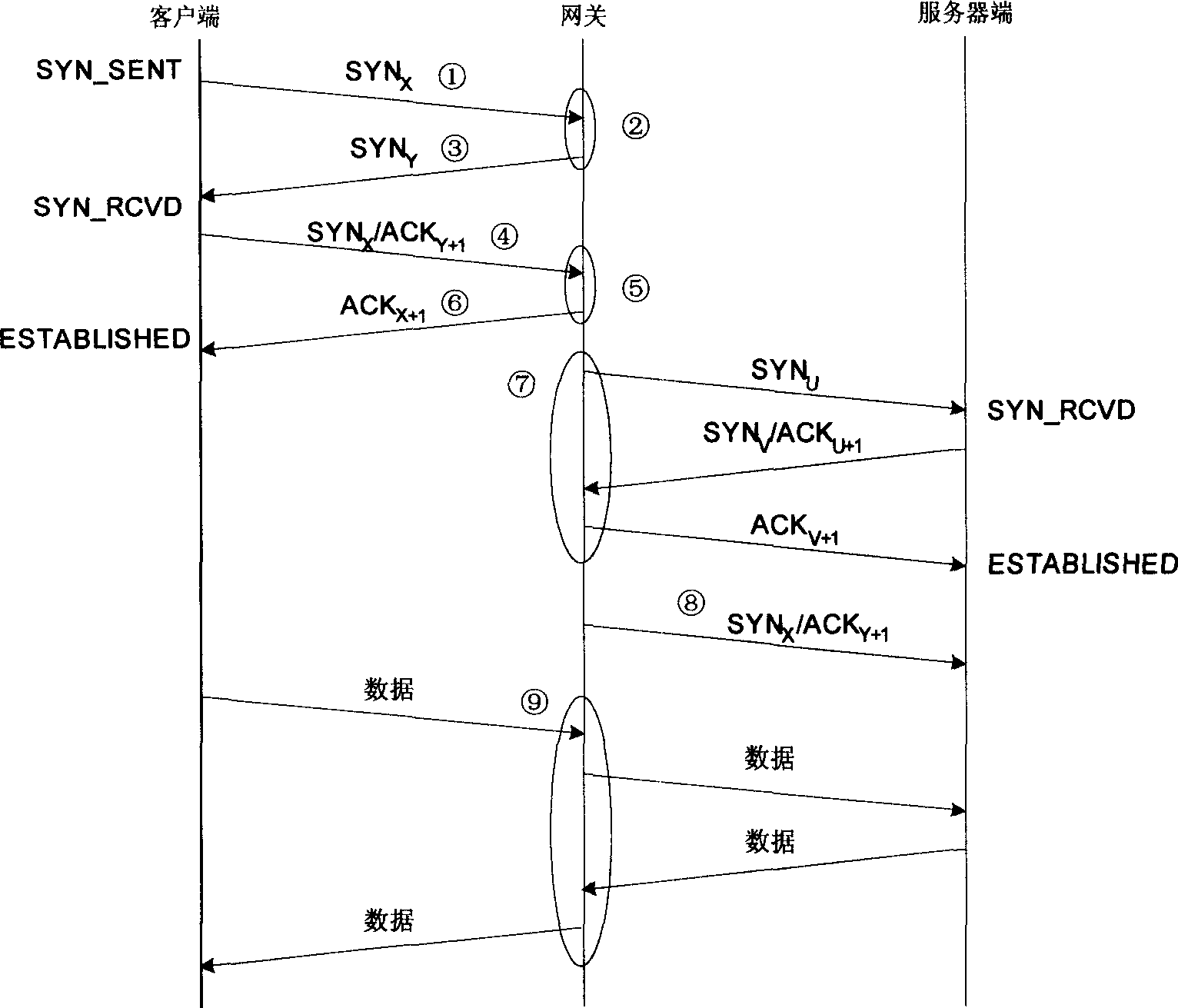
[0035] Such as figure 1 As shown, the present invention is realized by modifying the software technology of the code of the operating system TCP / IP protocol stack on the host. Mainly modify the implementation of the standard TCP / IP protocol stack on the host where the server is located, and modify the received SYN X Packet and SYN X / ACK Y+1 Package processing flow. When a connection request SYN is received X After the package, instead of allocating memory resources to save the connection state information and return SYN Y / ACK X+1 Package, but does not allocate any system memory resources, using the method described above, returns a SYN with authentication information Y packet; when a SYN is received X / ACK Y+1 After the package, execute the original process in the implementation of the TCP / IP standard to check the SYN X / ACK Y+1 Whether the packet belongs to an existing socket, if it is to execute the original process, otherwise, use the above method to SYN X / ACK...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com