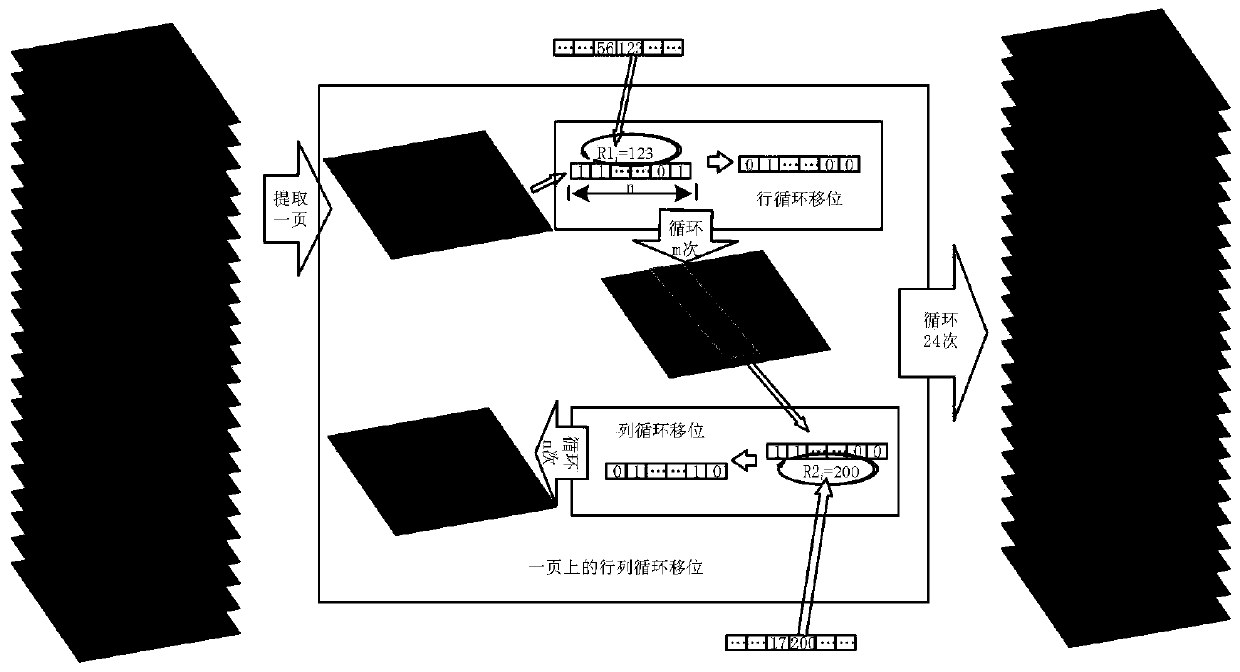
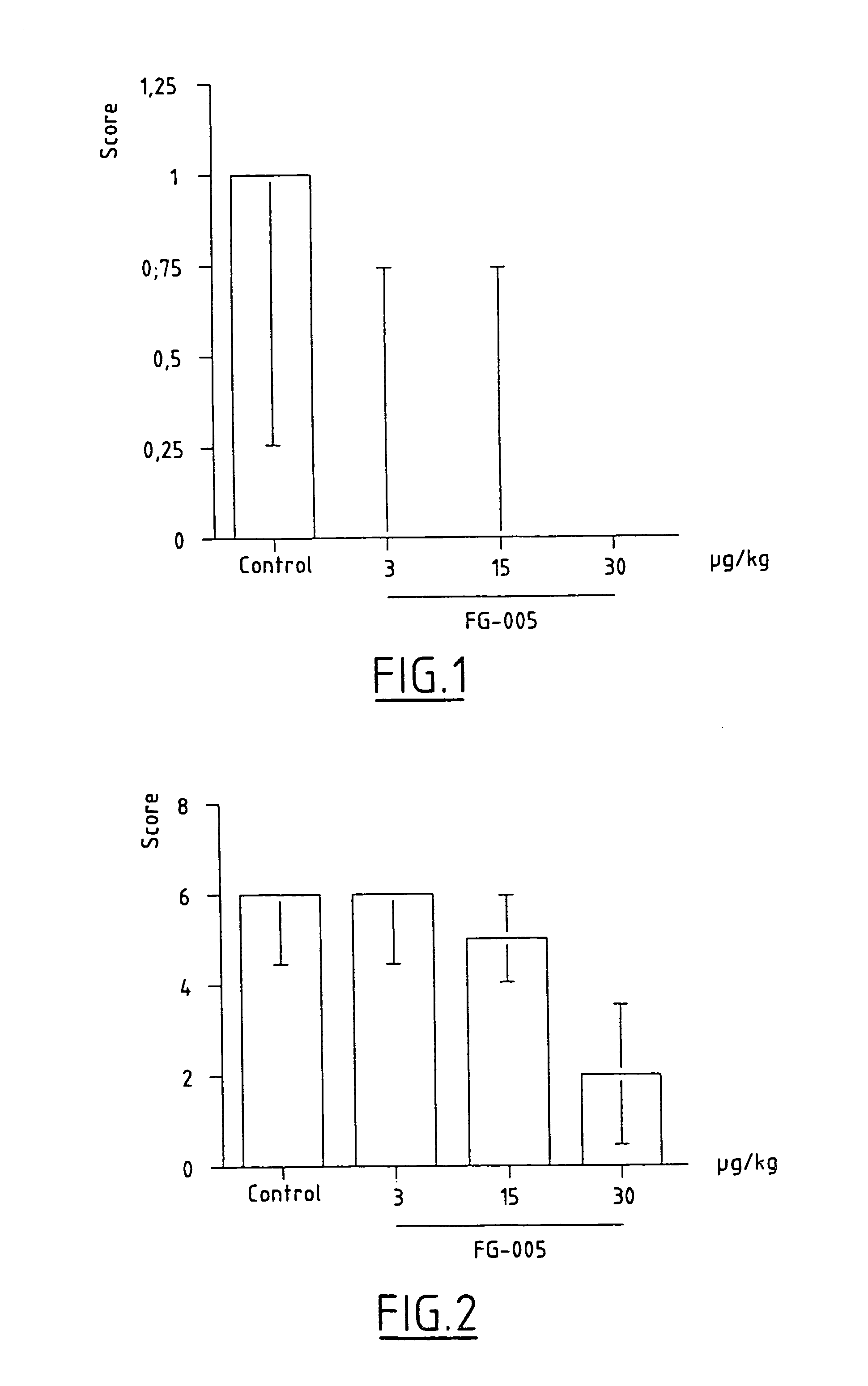
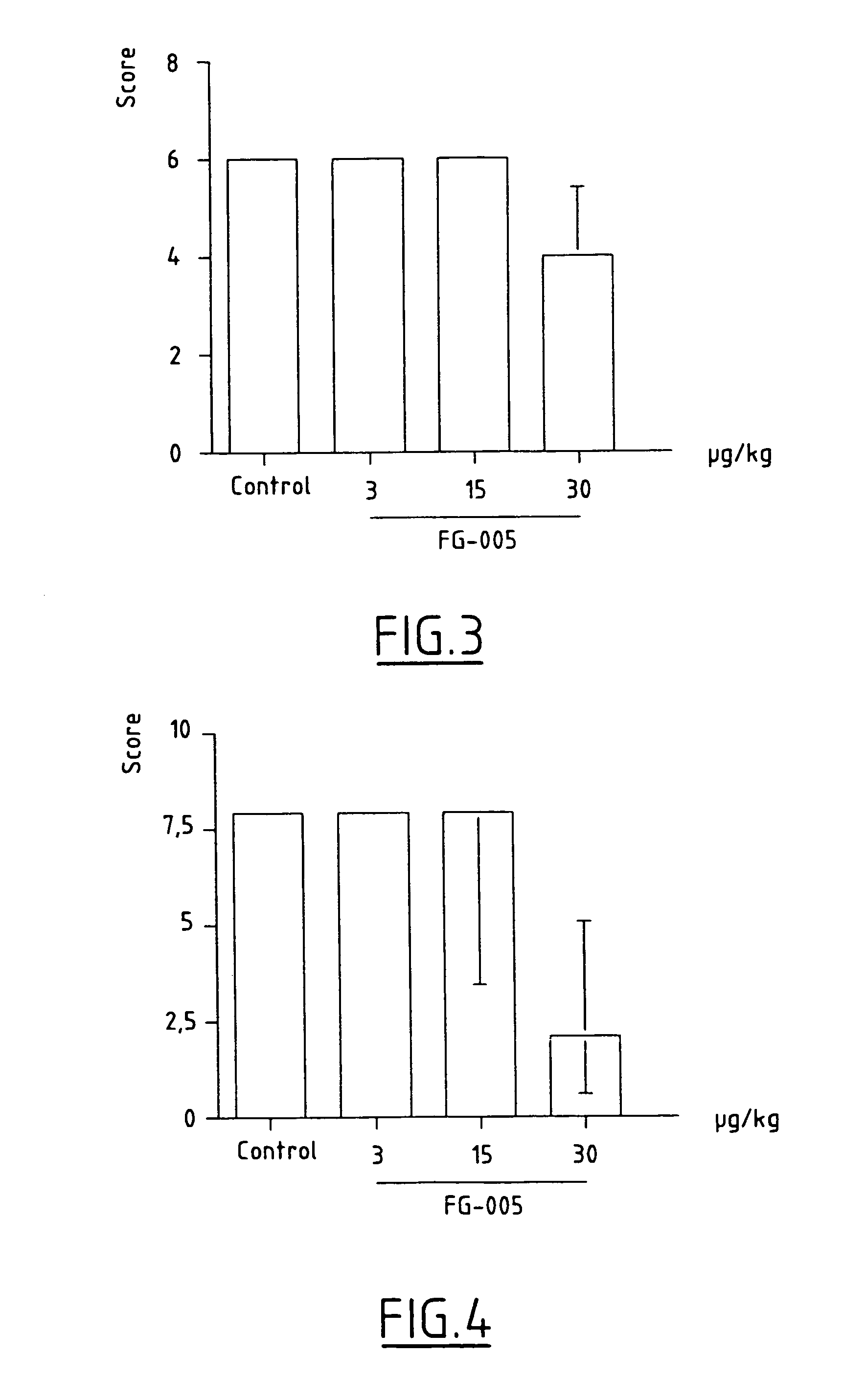
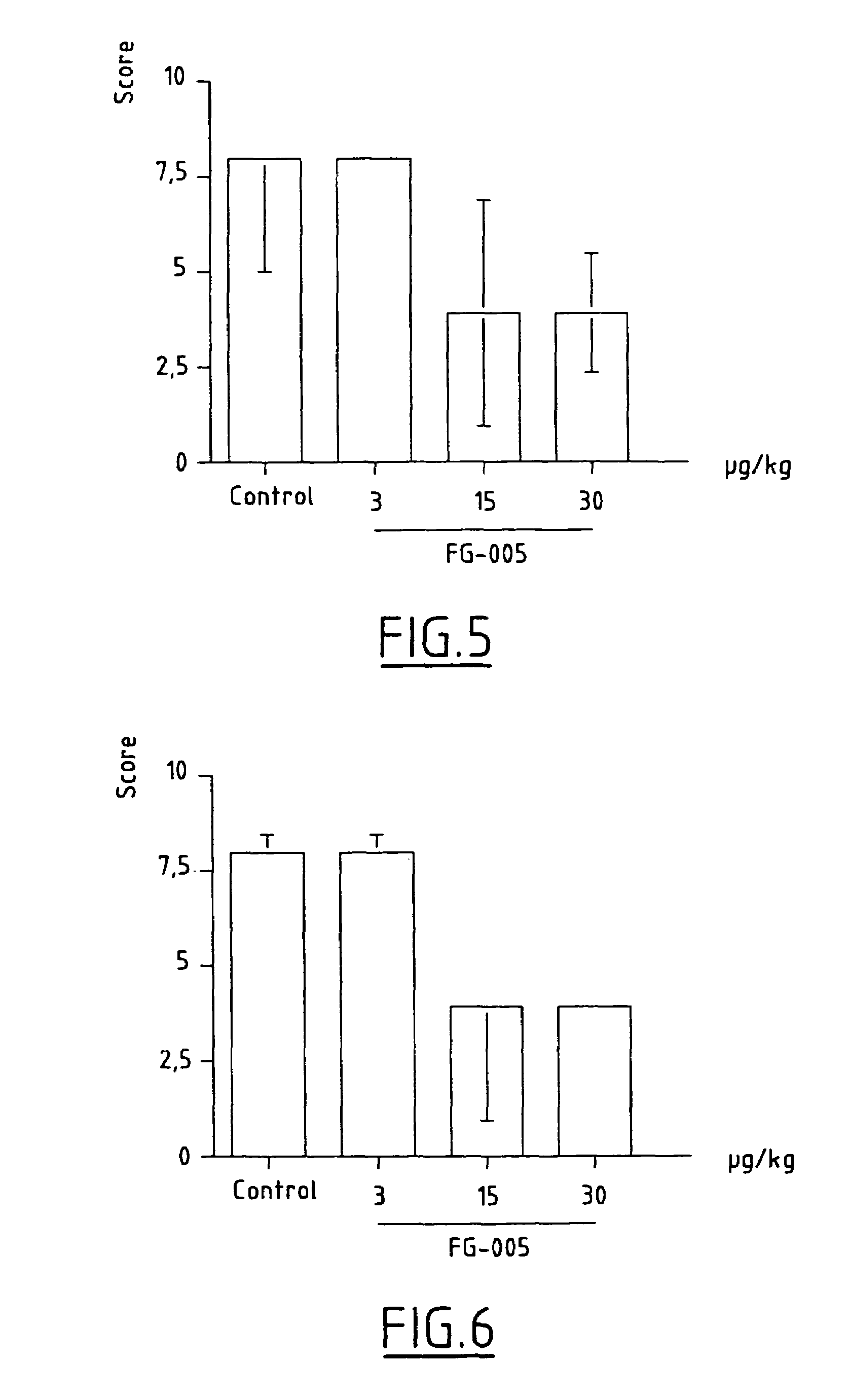
Patents
Literature
202results about How to "Increase aggressiveness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and apparatus for monitoring drug effects on cardiac electrical signals using an implantable cardiac stimulation device
InactiveUS7142911B2Increase aggressivenessIncrease dosePhysical therapies and activitiesDrug and medicationsEcg signalCardiac pacemaker electrode
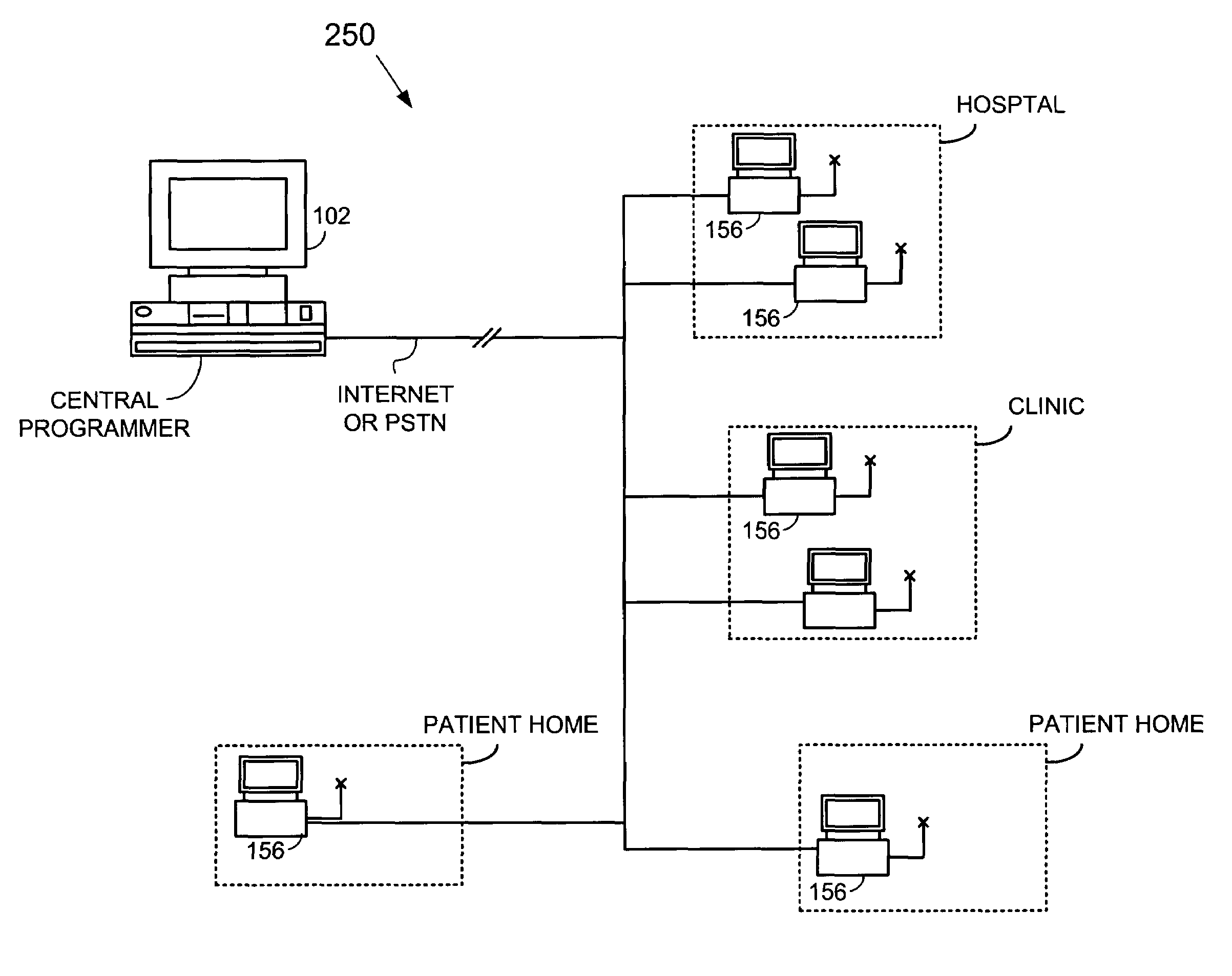
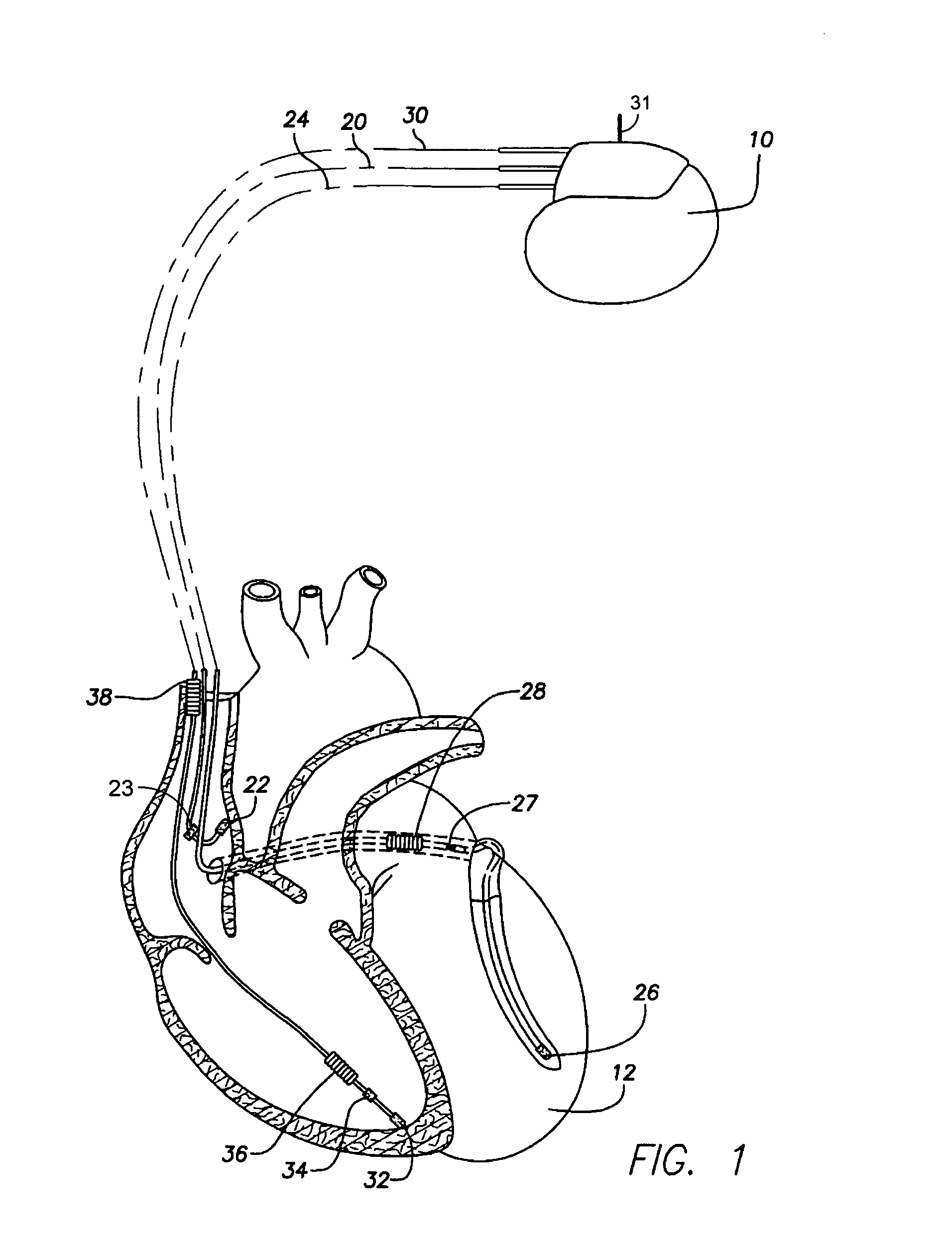
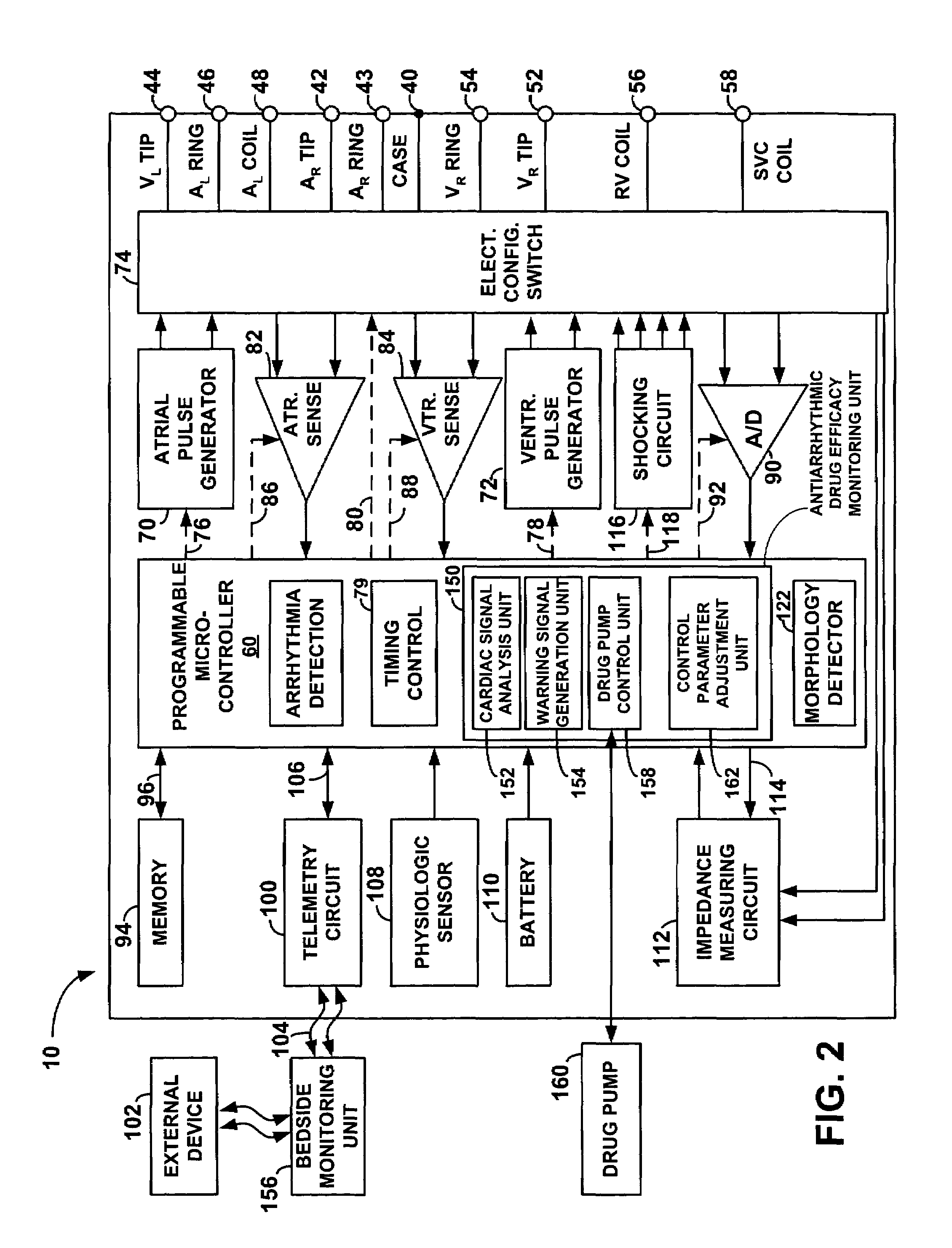
An implantable cardiac stimulation device, such as a pacemaker or Implantable Cardioverter Defibrillator, is configured to automatically monitor the effects of antiarrhythmic drugs on cardiac electrical signals within a patient to verify the efficacy of the drugs taken. In one example, an analysis of patient cardiac electrical signals is performed by comparing the cardiac electrical signals with values representative of the effects of different classes of antiarrhythmic drugs. If the implantable device determines that the prescribed antiarrhythmic drugs have not been effective, a warning signal is generated. The warning signal is conveyed directly to the patient via a bedside monitor and to the patient's physician via remote connection to an external programmer device so that both are notified of the drug efficacy problems. Additionally, the implantable device may be configured to automatically adjust pacing and defibrillation control parameters in an attempt to compensate for any lack of efficacy in the drugs. For example, the aggressiveness of overdrive pacing may be increased. Alternatively, a drug pump is controlled to adjust the dosage of antiarrhythmic drugs if an initial dosage is found to be ineffective.
Owner:PACESETTER INC
Authentication method and device based on blockchain
InactiveCN106790253AImprove the ability of hackingImprove accuracyUser identity/authority verificationProtocol authorisationDigital assetBlockchain
The invention discloses an authentication method and device based on a blockchain. The method comprises the following steps: generating a roll-out private key for transferring digital assets through the blockchain and a corresponding roll-out public key according to a random number; carrying out coding treatment on the roll-out public key, and generating a roll-in address; carrying out digital signature on the basis of the roll-out private key, a transferring numerical value of the digital assets to be transferred and the roll-in address; acquiring digital asset transferring data on the basis of the transferring numerical value, the roll-in address, the digital signature and the roll-out public key; and broadcasting the digital asset transferring data into the blockchain so that the digital asset transferring data are subjected to first-grade authentication by an authentication side, or are subjected to multi-grade authentication by a server side and the authentication side jointly after first-grade authentication is finished. Therefore, by the embodiment, hacker attack ability can be improved, and safety requirements of data and transaction in a blockchain open environment can be met.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
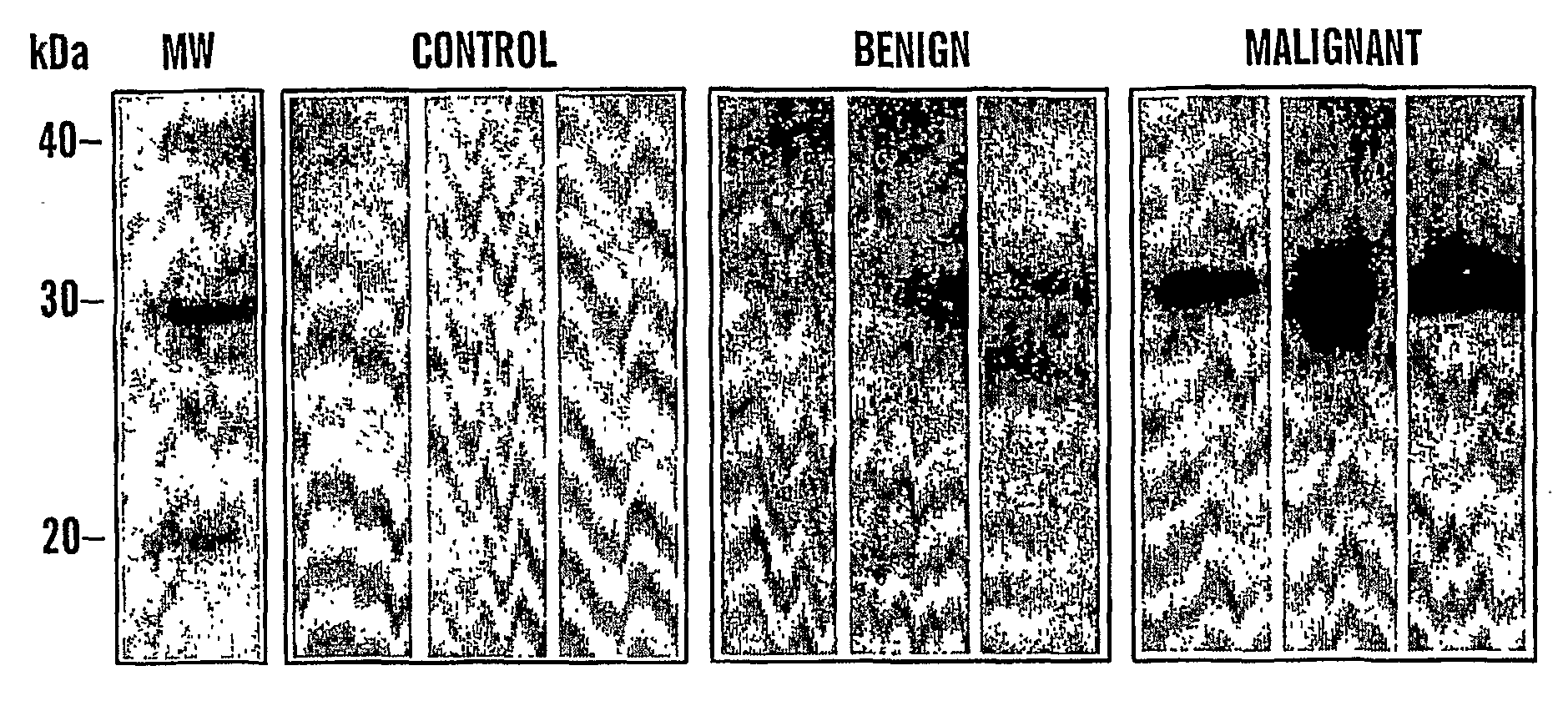
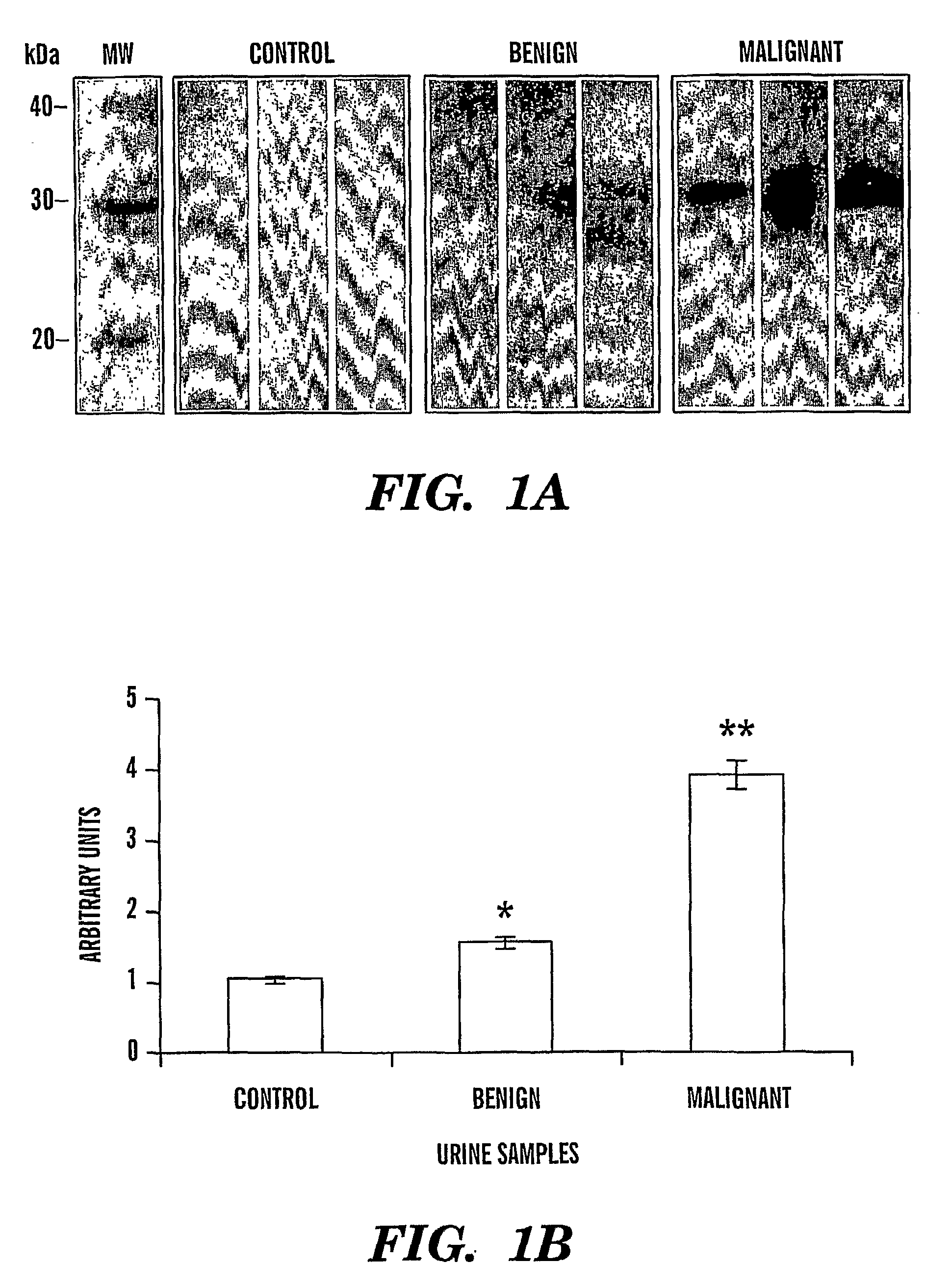
Cyr61 as a Biomarker for Diagnosis and Prognosis of Cancers of Epithelial Origin
ActiveUS20080286811A1Easy diagnosisRaise the possibilityMicrobiological testing/measurementBiological material analysisBacteriuriaOncology
Urinary Cyr61 protein levels are up regulated in patients that have cancers of epithelial origin, i.e. breast cancer and ovarian cancer. Accordingly, the present invention is directed to methods for prognostic evaluation, and diagnosis of cancers of epithelial origin. Further, the amount of Cyr61 protein detected in a urine sample correlates with disease status such that Cyr61 levels can be used to predict the presence of, as well as the metastatic potential of cancer. Thus, measuring the level of Cyr61 in urine provides a quick, easy, and safe screen that can be used to both diagnose and prognose cancer in a patient.
Owner:CHILDRENS MEDICAL CENT CORP
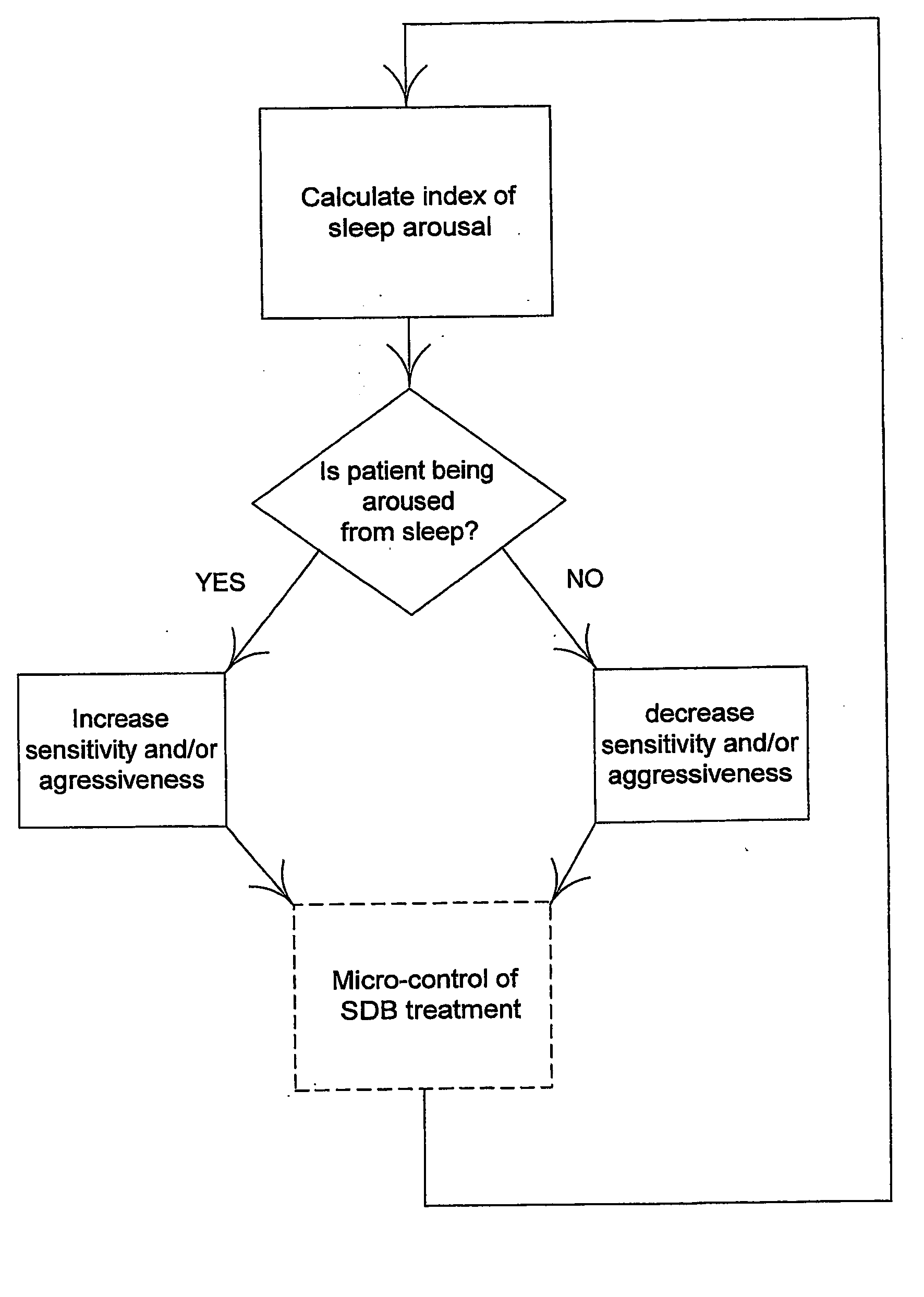
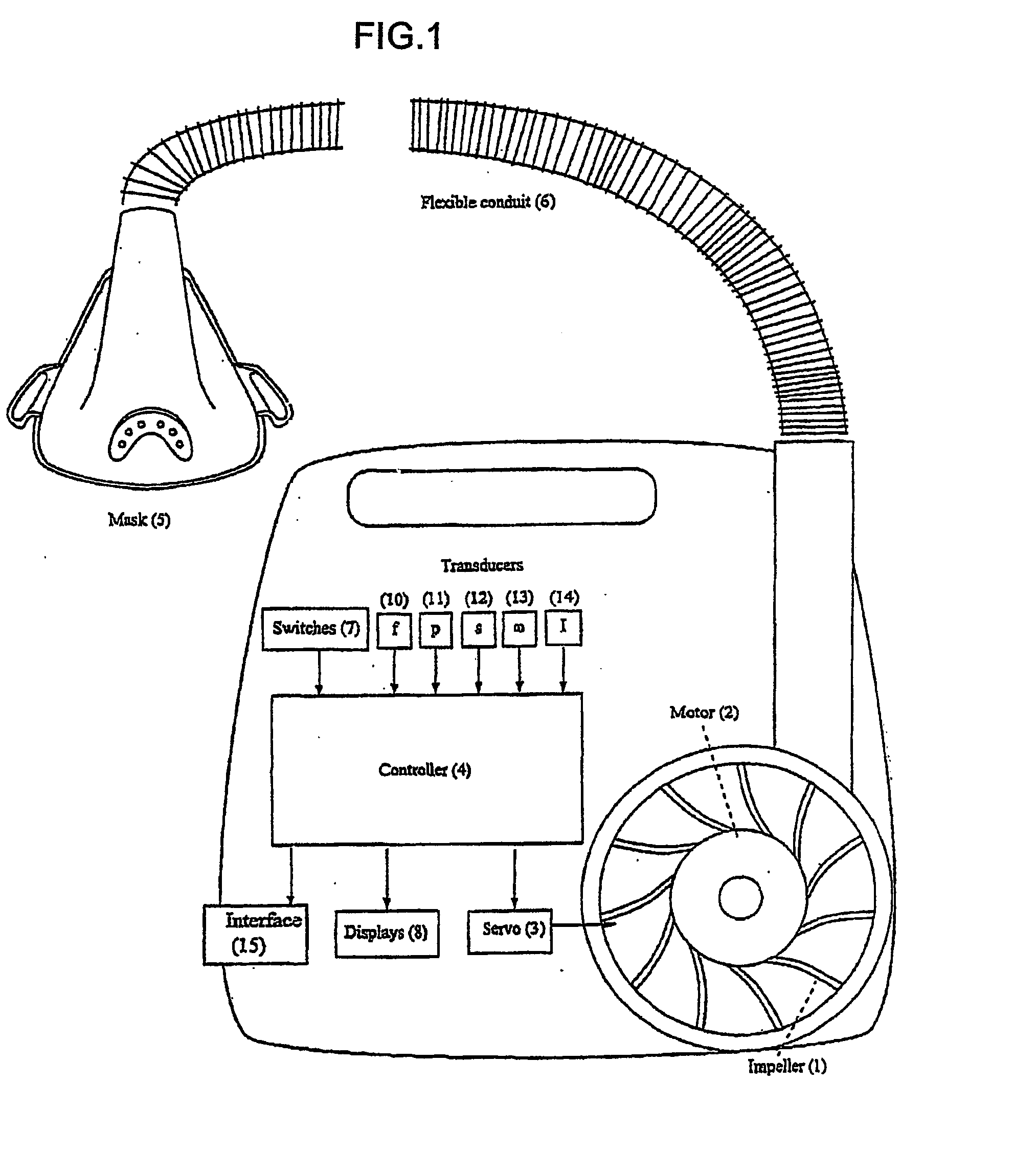
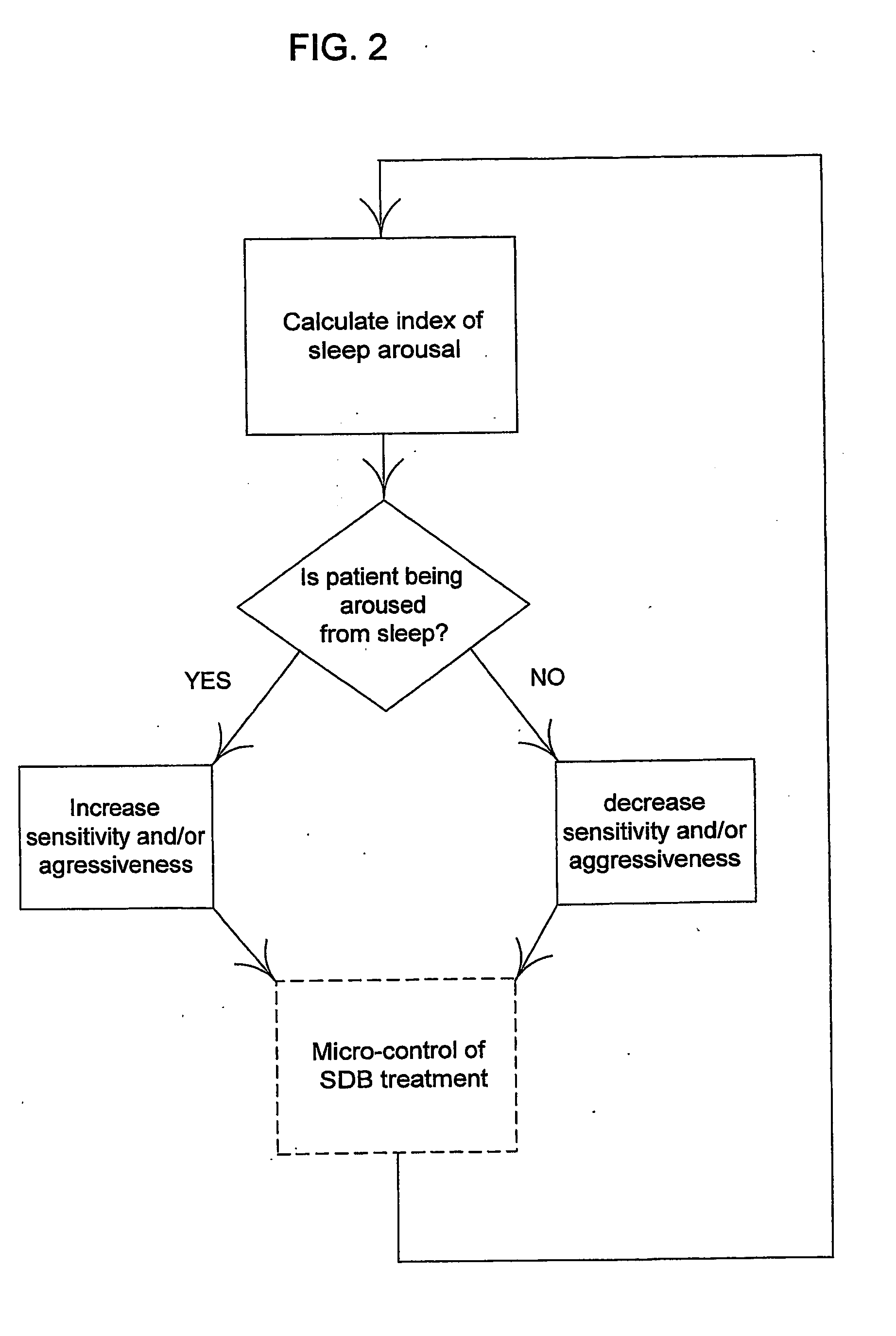
Macro-control of treatment for sleep disordered breathing
ActiveUS20070142741A1Improve performanceMonitor effectivenessPhysical therapies and activitiesRespiratory masksInner loopSleep arousal
A method and apparatus for treating sleep disordered breathing. An arousal index is determined for use in an outer loop of a control algorithm, the arousal index being a measure of the frequency of sleep arousals. The respiratory airflow signal in an inner loop of the control algorithm is monitored to detect an airway obstruction. If the arousal index is high, then the sensitivity of obstruction detection and / or the aggressiveness of the treatment is increased, and if the arousal index is low, then the sensitivity of the obstruction detection and / or the aggressiveness of the treatment is decreased
Owner:RESMED LTD
Long window scaling factor-based playback voice attack detection algorithm
ActiveCN105913855AIncrease aggressivenessImprove securitySpeech analysisSpeaker recognition systemSpeech sound
The invention discloses a long window scaling factor-based playback voice attack detection algorithm which is developed for solving a problem that rights and interests of a legitimate are damaged when conventional attackers use playback voice to enter a speaker identification system. The detection algorithm can be used for effectively identifying playback voice from different sources and is high in detection accuracy; after a module of the detection algorithm is loaded to a GMM-UBM system, playback voice attack resistant capability is improved, error probability of the identification system and the like is lowered by 32%, and a safety problem of the identification system is greatly alleviated.
Owner:NINGBO UNIV
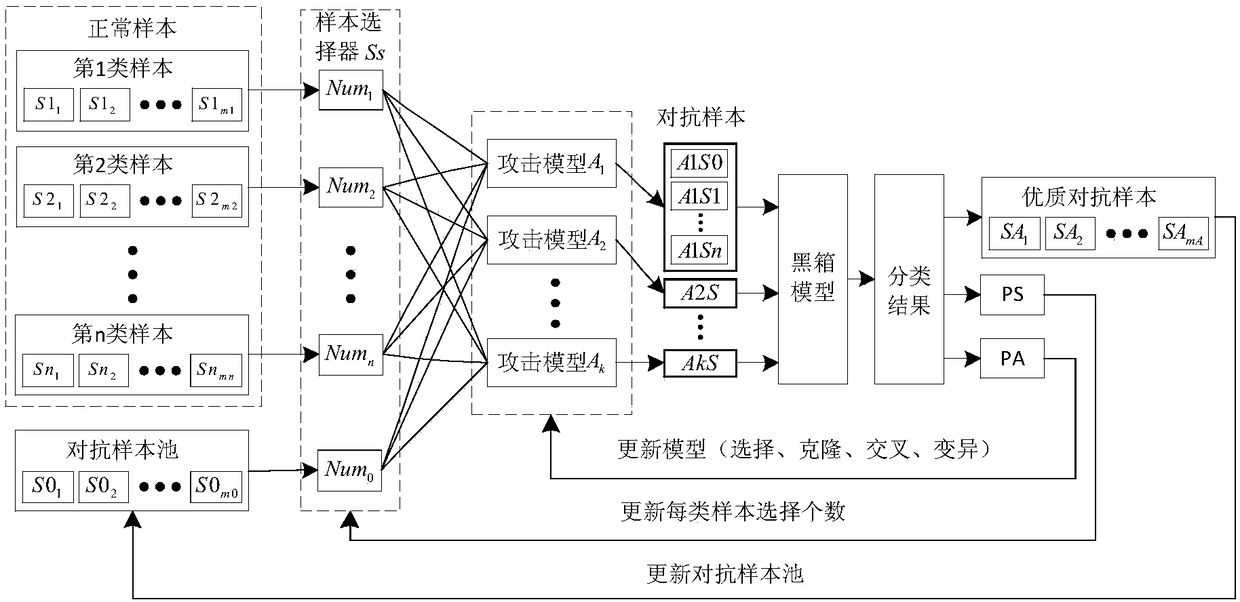
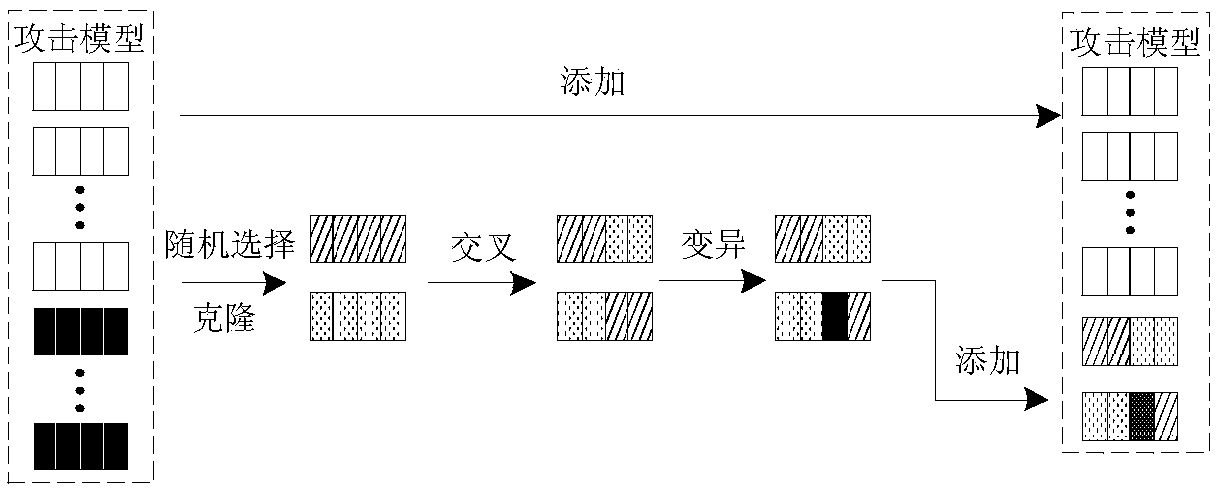
Black box antagonistic attack defense method based on sample selection and model evolution
ActiveCN108520268AIncrease the number ofIncrease diversityCharacter and pattern recognitionAttack modelAlgorithm
The invention provides a black box antagonistic attack defense method based on sample selection and model evolution. The method includes the following steps: 1) using a sample selector to randomly select partial samples from the multiple types of samples to be input into various attack models to generate a large number of counter samples; 2) calculating the attack effect of the counter samples, and analyzing the attack effect of different input samples and the attack model; (3) updating the number of different samples selected by different samples in the attack model and the sample selector according to the attack effect to make the newly generated counter sample have a better attack effect, meanwhile, updating the counter sample pool, storing the several counter samples with the best attack effect, and outputting the counter samples with the best attack effect in the pool to serve as the final result of the current evolution; and 4) training a large number of training output results and normal samples, so that the attack can be defended. According to the invention, the defense capability of the black box model can be improved.
Owner:ZHEJIANG UNIV OF TECH
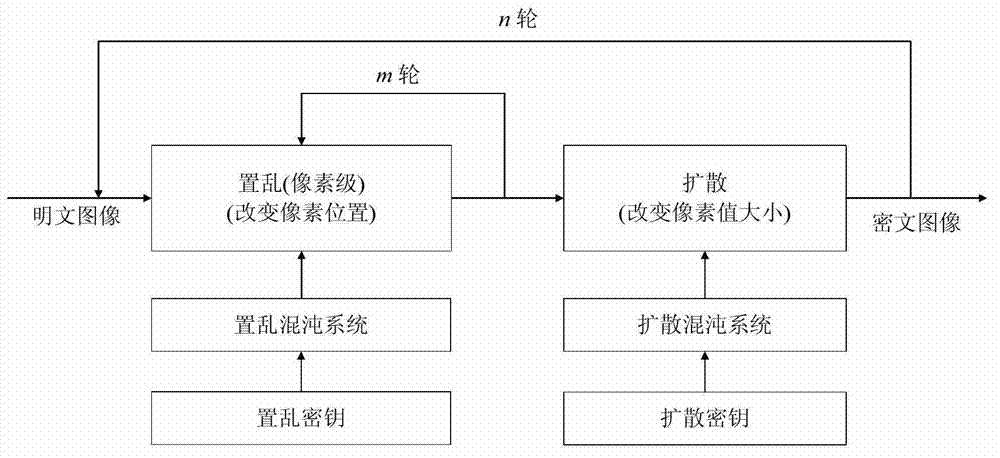
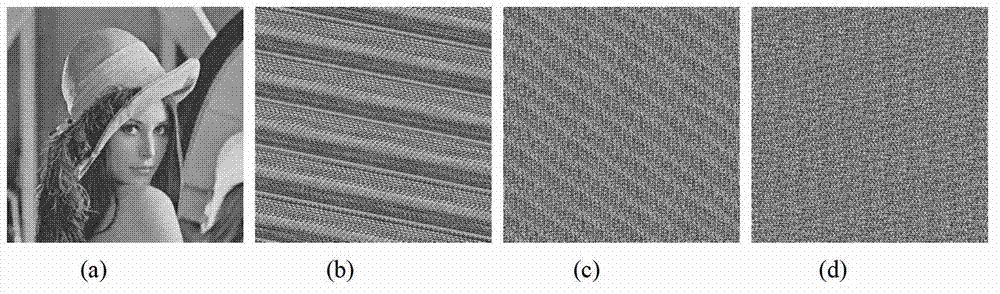
Image two-grade encrypting method based on double-chaos system
InactiveCN102693523ALarge key spaceEnhanced ability to resist known plaintext attacksImage data processing detailsKnown-plaintext attackComputer vision
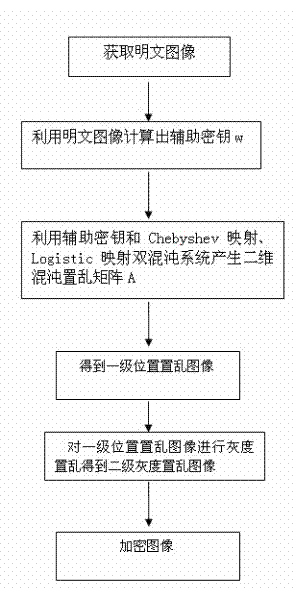
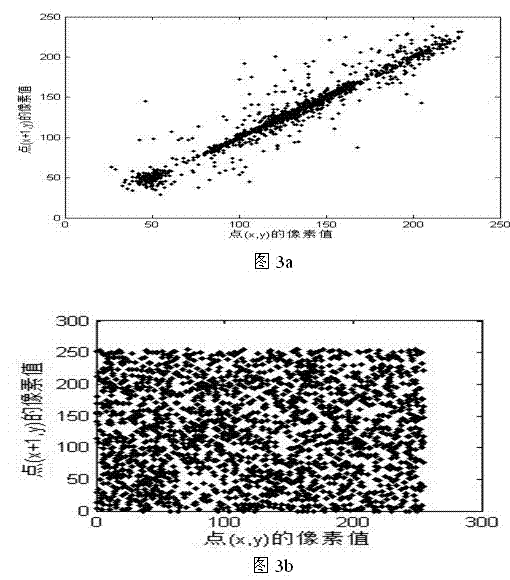
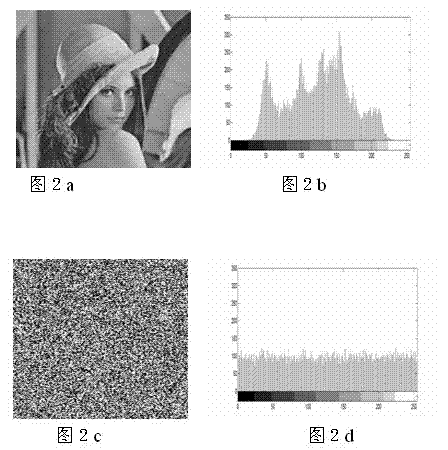
The invention discloses an image two-grade encrypting method based on a double-chaos system, relating to the field of image encrypting systems. The adopted method comprises the steps of creating an auxiliary key by a plaintext image firstly; creating a two-dimension chaos scrambling matrix by the auxiliary key combined with the double-chaos system of the Chebyshev mapping and Logistic mapping to dually scramble the position and grey level of the pixels of plaintext image so as to realize the encryption of images. According to the image two-grade encrypting method, the auxiliary key based on the plaintext image is introduced to expand key space and correlate the key with the plaintext, so that the ability of the image encryption system for resisting attack of the known plaintext is enhanced; and meanwhile, the complicated characteristics of dynamics of the double-chaos system is utilized to dually scramble the position and grey level of the plaintext image, with good encryption effect and high security.
Owner:SOUTH CHINA UNIV OF TECH
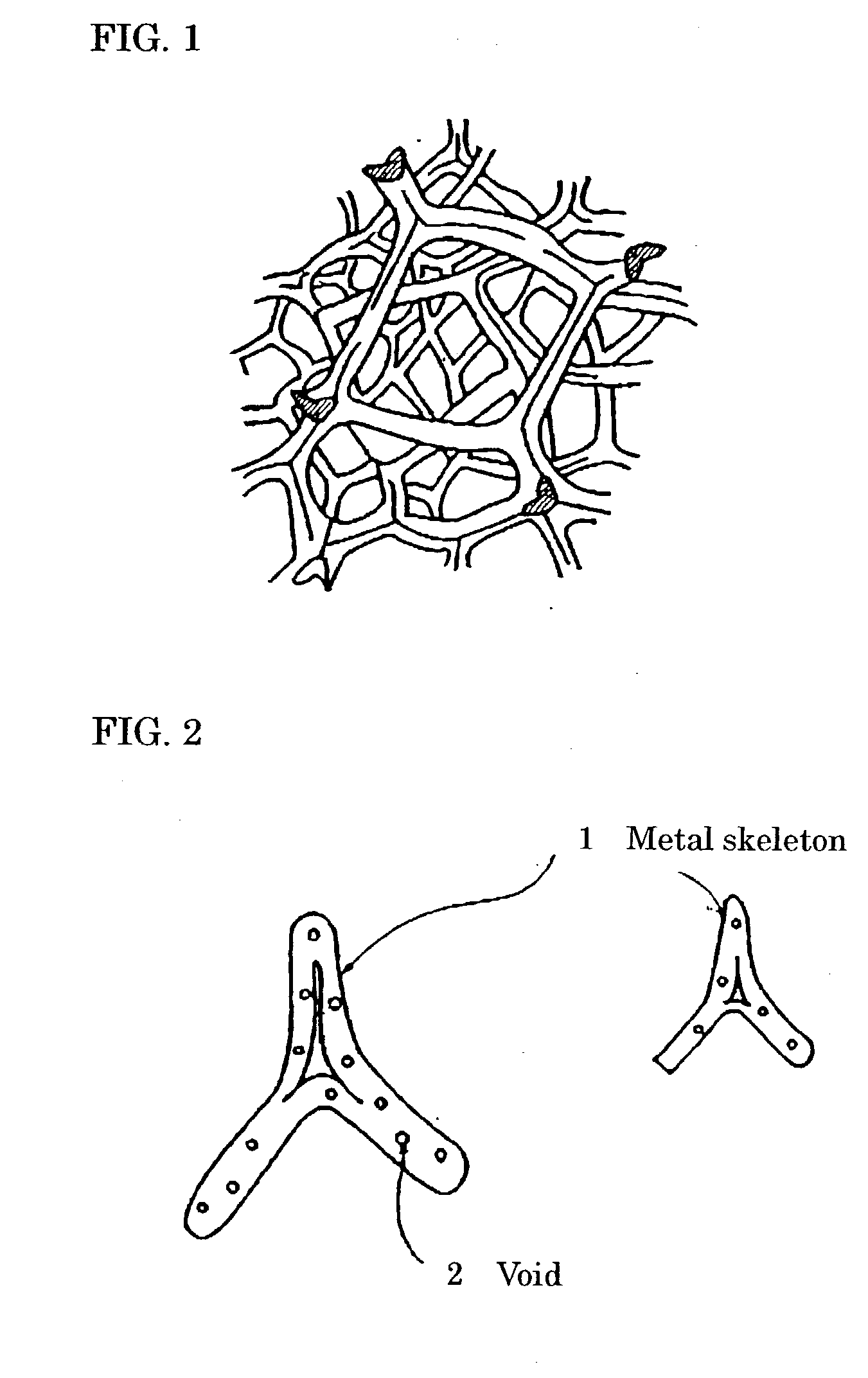
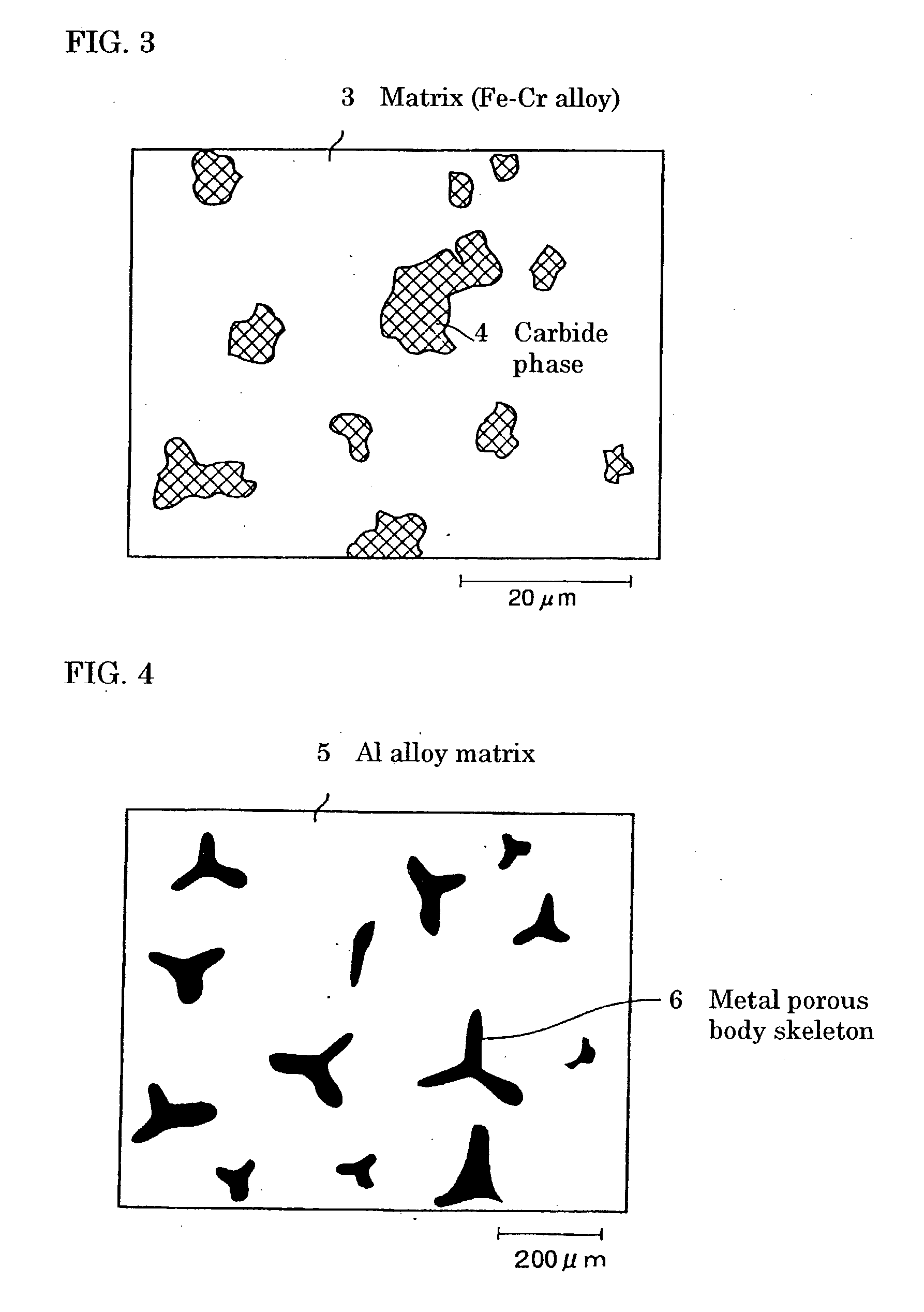
Porous metal article, metal composite material using the article and method for production thereof
InactiveUS20030200837A1Preferable characteristicHigh mechanical strengthSolid state diffusion coatingCarbideDiluent
Owner:SUMITOMO ELECTRIC IND LTD
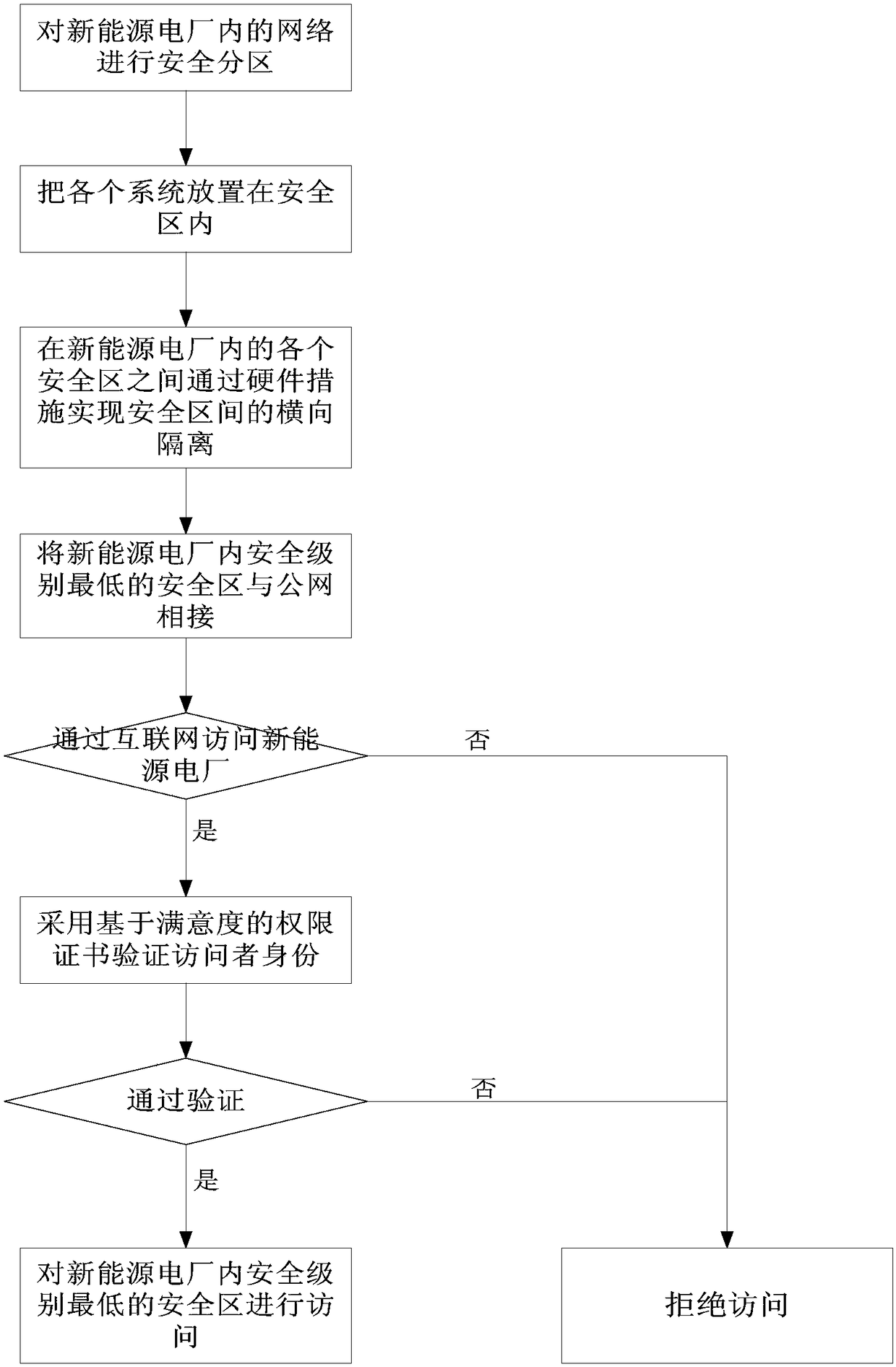
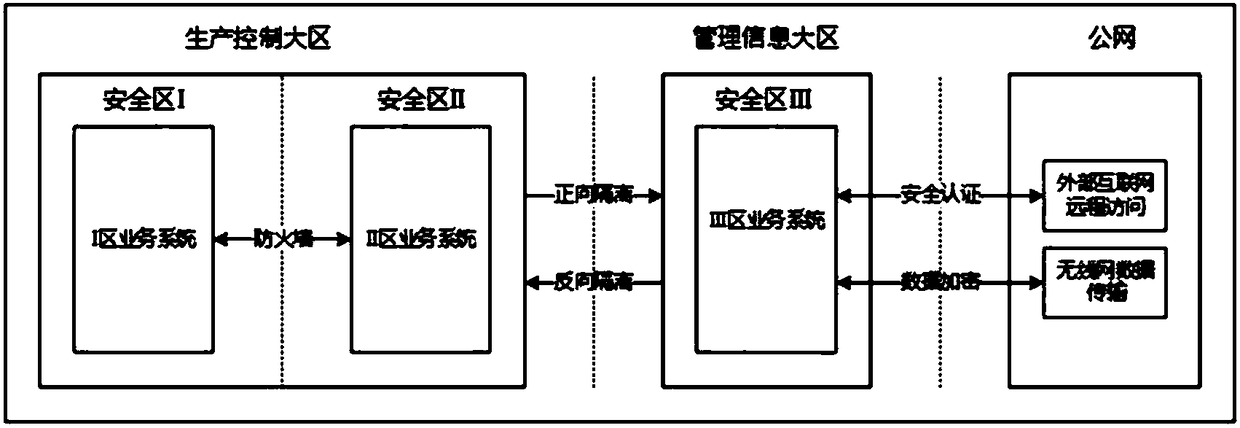
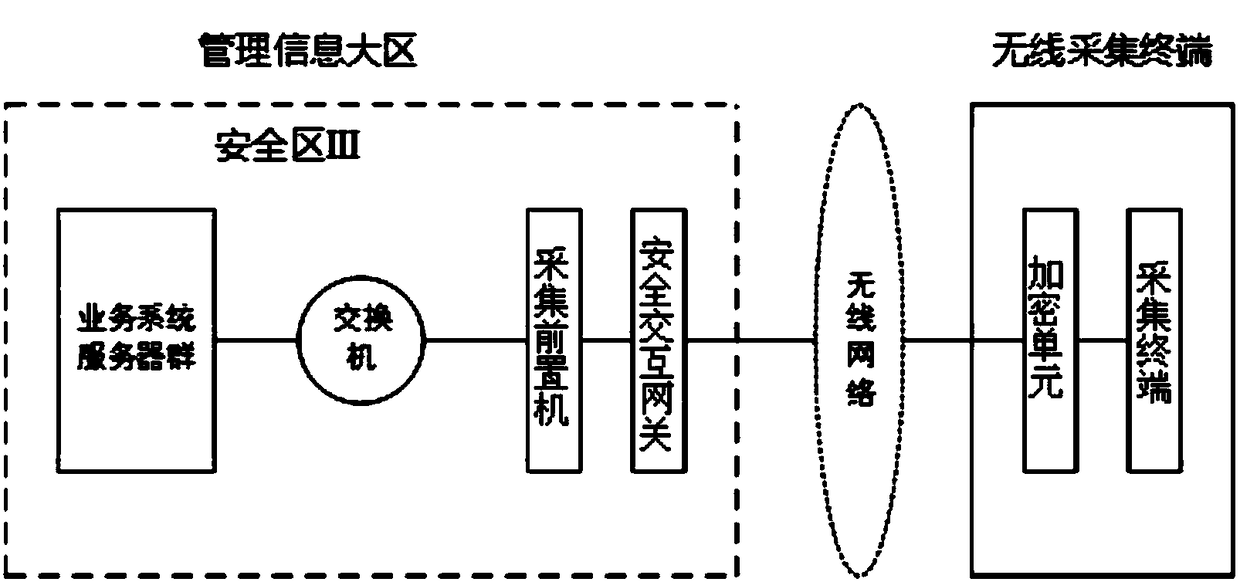
Public network safety access method for new energy power plant
InactiveCN108063751AAvoid security risksIncrease aggressivenessCircuit arrangementsUser identity/authority verificationAccess methodNew energy
The invention discloses a public network safety access method for a new energy power plant, which comprises the following steps of: carrying out safety partitioning on a network in the new energy power plant, and placing each service system in safety regions; carrying out transverse separation between each safety region by a hardware measure; connecting the safety region with the lowest safety level in the new energy power plant with a public network; and when accessing the new energy power plant by the internet, verifying a user identity by an authority certificate based on satisfaction, andpassing verification, carrying out access on the safety region with the lowest safety level in the new energy power plant. By the public network safety access method disclosed by the invention, not only is a safety risk from the public network, which an internal network system of the new energy power plant directly faces, avoided, but also the ability of preventing a public network attack is greatly improved.
Owner:STATE GRID NINGXIA ELECTRIC POWER +1
Digital image encryption method with rapid key stream generative mechanism
InactiveCN103258312AReduce the number of iterationsHigh speedImage data processing detailsComputer hardwareChosen-plaintext attack
The invention discloses a digital image encryption method with a rapid key stream generative mechanism, and belongs to the field of image encryption. According to a digital image encryption system with the rapid key stream generative mechanism, a plurality of key stream elements are generated every time chaotic system iteration and key stream element quantification are conducted in a diffusion stage, the number of chaotic system iteration is effectively reduced, so that speed of the encryption system is increased significantly. In addition, the number of the key stream elements which are generated in each time of iteration and quantification is relevant to plaintexts, and capacity of the encryption system for resisting attack from known plaintexts and chosen plaintexts is improved. Cryptology analyses and encryption speed tests indicates that the encryption speed of the digital image encryption system with the rapid key stream generative mechanism is one time higher than the encryption speed in a tradition method on the premise that the encryption system is high in safety.
Owner:NORTHEASTERN UNIV
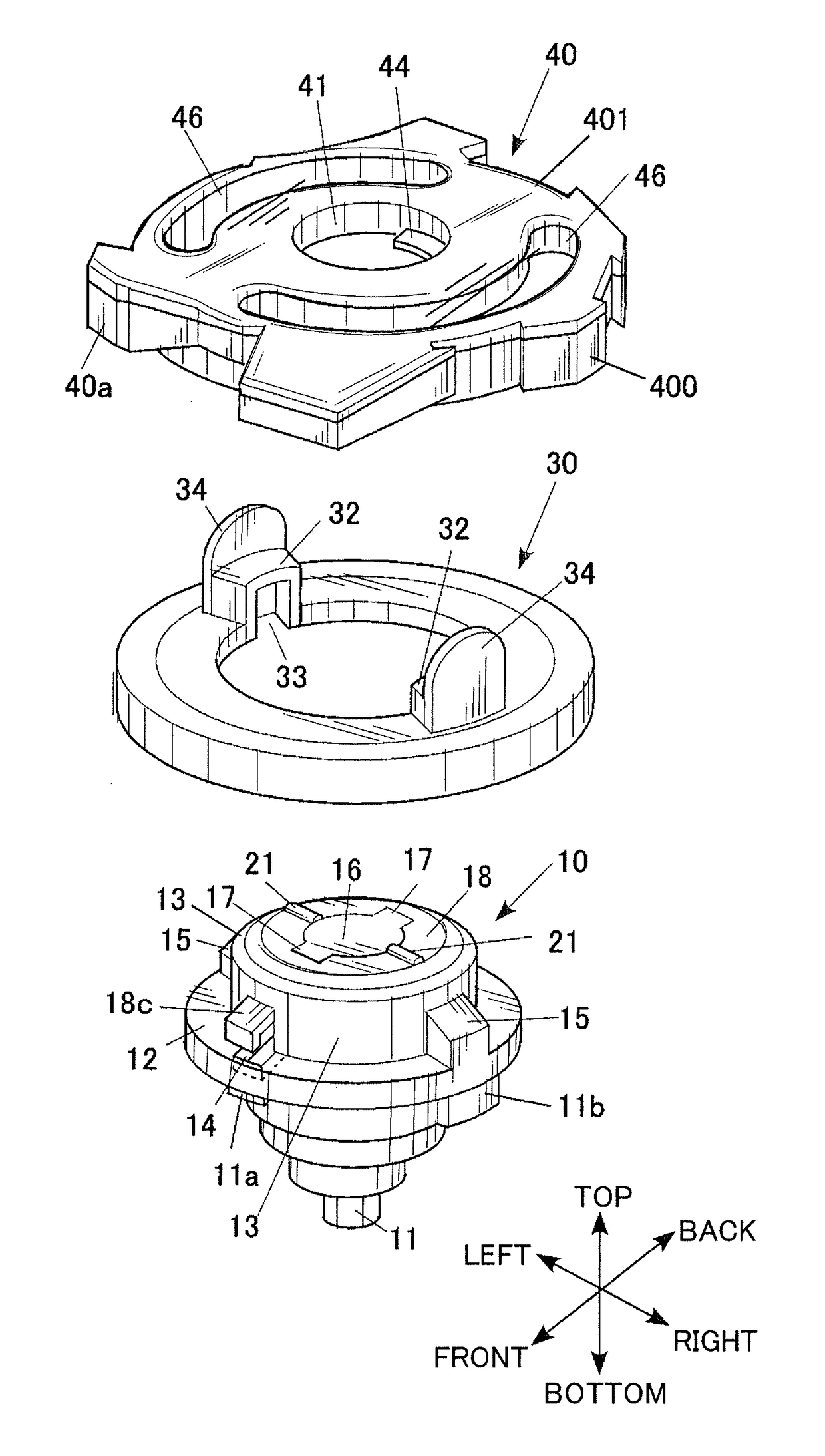
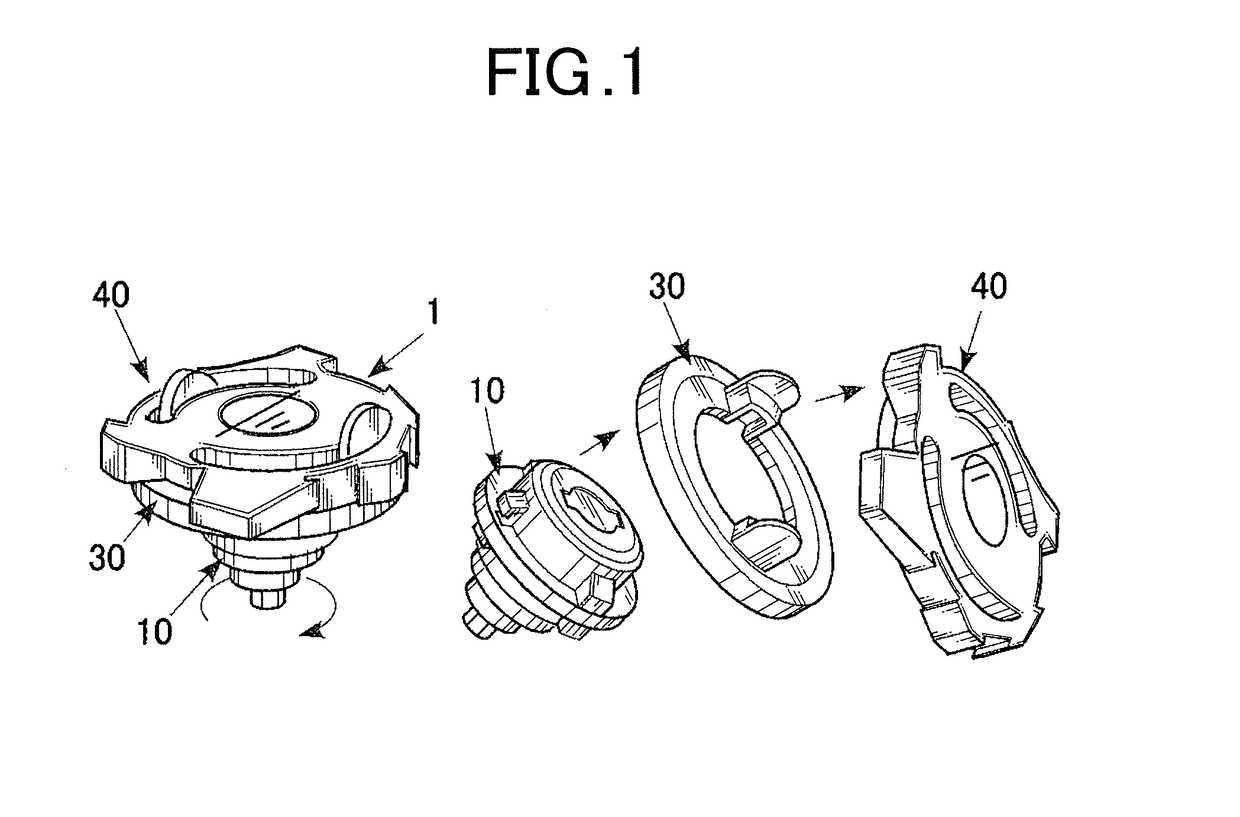
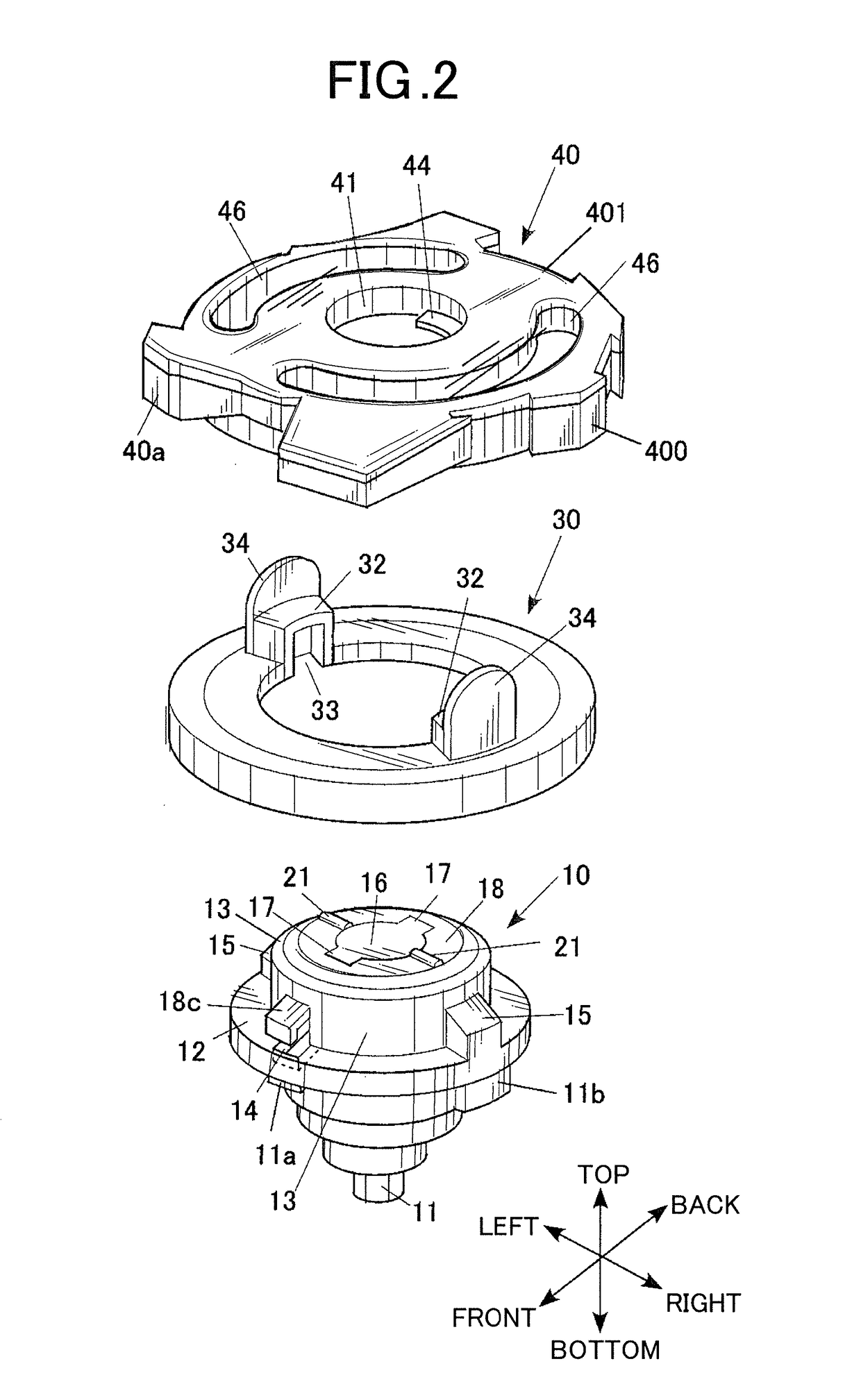
Toy top
A toy top includes a body and a shaft part. A rotating shaft of the shaft part includes plastic or metal shaft tip segments disposed at predetermined intervals in a circumferential direction of the rotating shaft. The shaft tip segment constitutes part of an outer periphery of the rotating shaft. The part of the outer periphery is configured to come into contact with the ground. Rubber is provided at the outer periphery of the rotating shaft so as to protrude outward beyond outer surfaces of the shaft tip segments. The rubber has higher frictional force than the shaft tip segments. The rubber is disposed between adjacent shaft tip segments in the circumferential direction.
Owner:TOMY CO LTD
Technique for making lithium battery pole ear
The invention discloses a method for manufacturing a lithium cell electrode tab, which comprises the following steps: a, cutting a metal strip of an electrode tab substrate into sections; b, performing ultrasonic cleaning; c, drying; d, performing surface treatment on the metal strip in a treating fluid; e, rinsing the metal strip by using deionized water; f, drying; g, fixing a sealant with the metal strip by PET and a double faced adhesive tape to ensure that the dimension reaches requirements; h, hot pressing, i, cooling at room temperature; and j, cutting a side-layer material into a single electrode tab. Due to the addition of the pretreatment and the surface treatment of the electrode tab base material metal strip or the surface treatment of the electrode tab base material metal strip, oxides on the surface of the metal strip can be removed effectively, and the surface activity of the metal strip is enhanced, so that the binding strength between the metal surface and the sealant is improved, the capability for resisting electrolyte attack is strengthened, the sealing property of battery cells is improved, and the service life of the lithium cell is prolonged from 3 to 6 months to 3 years.
Owner:厦门宝龙工业股份有限公司
AES (Advanced Encryption Standard)-based encryption method and device
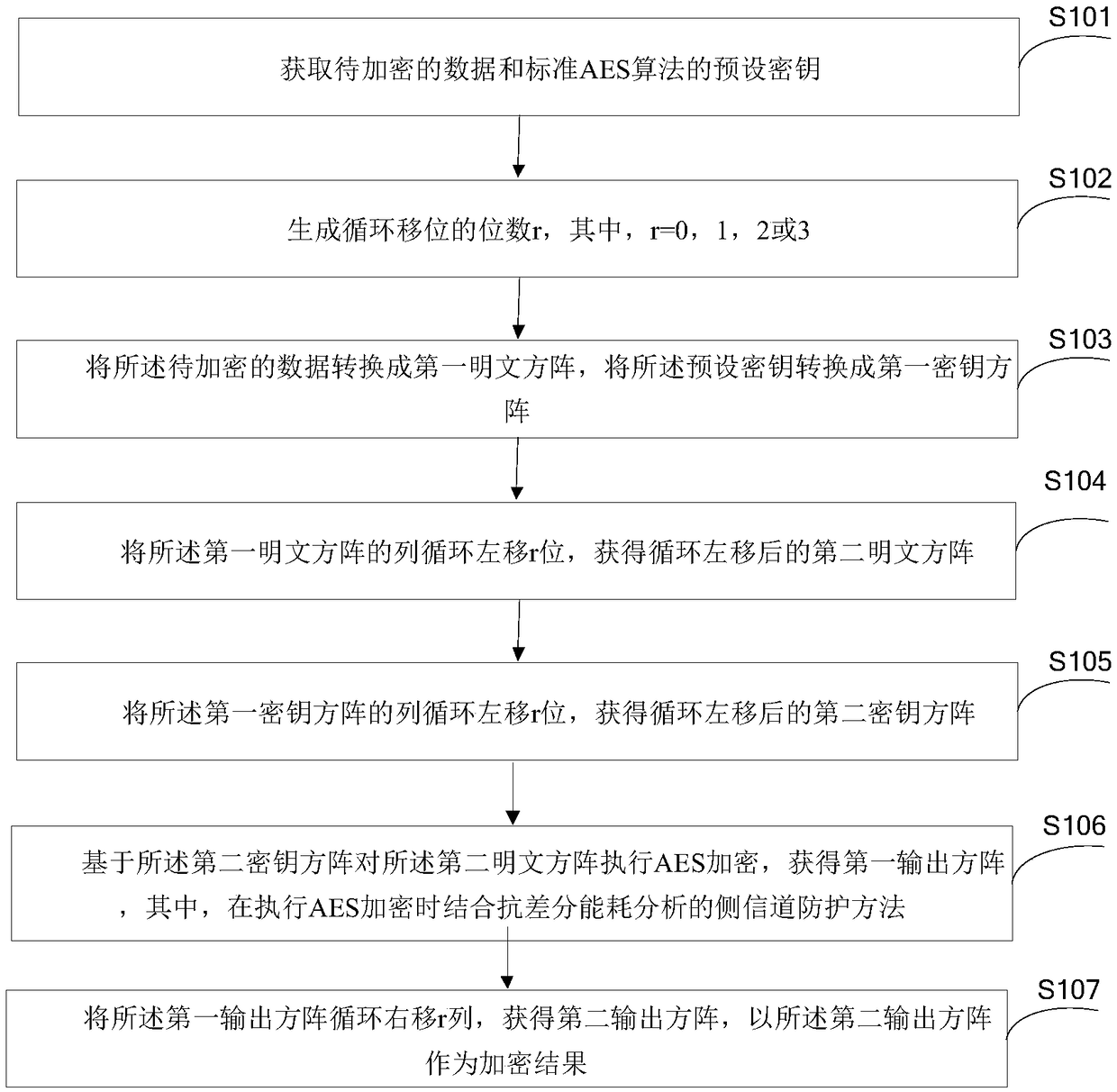
InactiveCN108964872AIncrease aggressivenessIncreased complexityEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPlaintextAdvanced Encryption Standard
The invention provides an AES (Advanced Encryption Standard)-based encryption method and device. The method comprises the following steps: firstly, acquiring to-be-encrypted data and a preset key of astandard AES algorithm; secondly, generating a digit number r of cyclic shift, converting the to-be-encrypted data into a first plaintext square matrix, and converting the preset key into a first keysquare matrix; thirdly, cyclically shifting the column of the first plaintext square matrix leftwards by r digits to acquire a second plaintext square matrix subjected to cyclic leftward shifting, and cyclically shifting the column of the first key square matrix leftwards by r digits to acquire a second key square matrix subjected to cyclic leftward shifting; fourthly, performing AES encryption on the second plaintext square matrix based on the second key square matrix to acquire a first output square matrix, wherein during the performing of the AES encryption, a differential energy consumption analysis-resistant side channel protection method is combined; and finally, cyclically shifting the first output square matrix rightwards by r columns to acquire a second output square matrix, wherein the second output square matrix is used as an encryption result. The AES-based encryption method achieves a technical effect of enhancing the side channel attack resistance.
Owner:WUHAN UNIV
Nickel-free phosphating process
InactiveUS6197126B1Firm lacquer adhesionImprove protectionPretreated surfacesSolid state diffusion coatingChemistryPhosphate ion
Owner:HENKEL KGAA
Image encryption method based on L-F cascade chaos and 3D bit scrambling
InactiveCN110889877AGuaranteed speedExpand the chaotic intervalImage codingDigital data protectionChosen-plaintext attackKey space
The invention discloses an image encryption method based on L-F cascade chaos and 3D bit scrambling. Image encryption is mainly divided into two steps: (1) 3D bit scrambling encryption and (2) diffusion operation. A novel L-F cascade chaos is constructed, the problem that a blank window exists due to uneven distribution of Logistic is solved while the rapidity of the Logistic is guaranteed, the chaos interval and number of parameters are increased, the secret key space is increased, and the exhaustion attack resistance of the system is improved. According to the method, the randomness of scrambled ciphertext is improved by adopting a 3D cyclic shift bit scrambling mode, and the problem that a bit scrambling sequence is insensitive is solved. According to the method, high-order informationcontaining a large amount of plaintext information and low-order information containing a small amount of plaintext information are separately scrambled, so that the noise attack resistance of the system is improved. According to the encryption system, the plaintext SHA-256 is used for carrying out strong association on the chaotic key, so that the plaintext sensitivity and the capability of resisting the attack of the selected plaintext are effectively improved.
Owner:QIQIHAR UNIVERSITY
PDC drill tool with alternating cutting trajectory
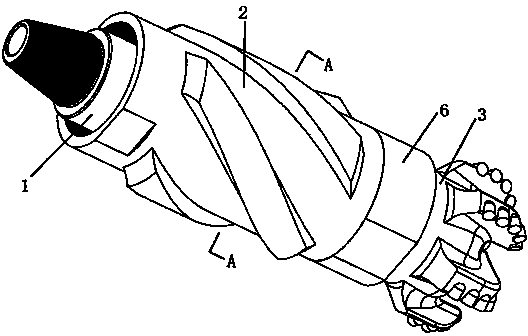
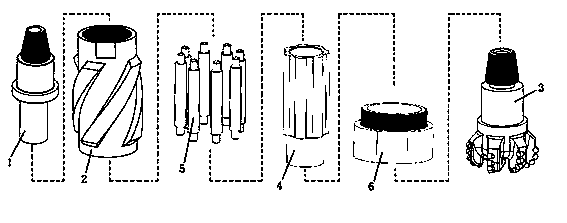
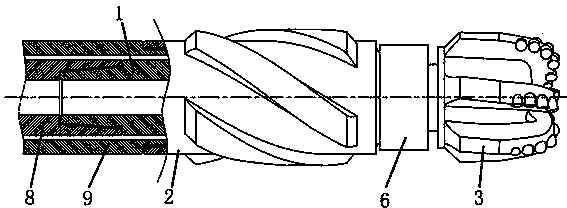
ActiveCN104196456AHighly consistentEccentric rotation is normalDrill bitsConstructionsEngineeringHardness
The invention discloses a PDC drill tool with an alternating cutting trajectory, and belongs to the field of rock breaking tools for drilling equipment. The PDC drill tool with the alternating cutting trajectory comprises an eccentric shaft, an outer shell, a PDC drill and a cycloid shaft. The PDC drill is fixedly connected to the cycloid shaft, the cycloid shaft is matched inside the outer shell and can eccentrically rotate relative to the alternating trajectory, and an eccentric shaft section arranged on the eccentric shaft is matched in an inner cavity of the cycloid shaft to form a revolute pair. An inner flow channel of the eccentric shaft, an inner flow channel of the cycloid shaft and an inner flow channel of the PDC drill are communicated. By the adoption of the PDC drill tool, the alternating cutting trajectory movement can be made, the stratum eating-in capacity of the PDC drill can be improved remarkably, rock breaking efficiency is improved, the abrasion speed of cutting teeth can be better lowered, and in particular, the PDC drill tool has obvious technical advantages in a deep stratum which cannot be drilled easily and in a high hardness and high abrasiveness stratum.
Owner:四川宝石机械石油钻头有限责任公司
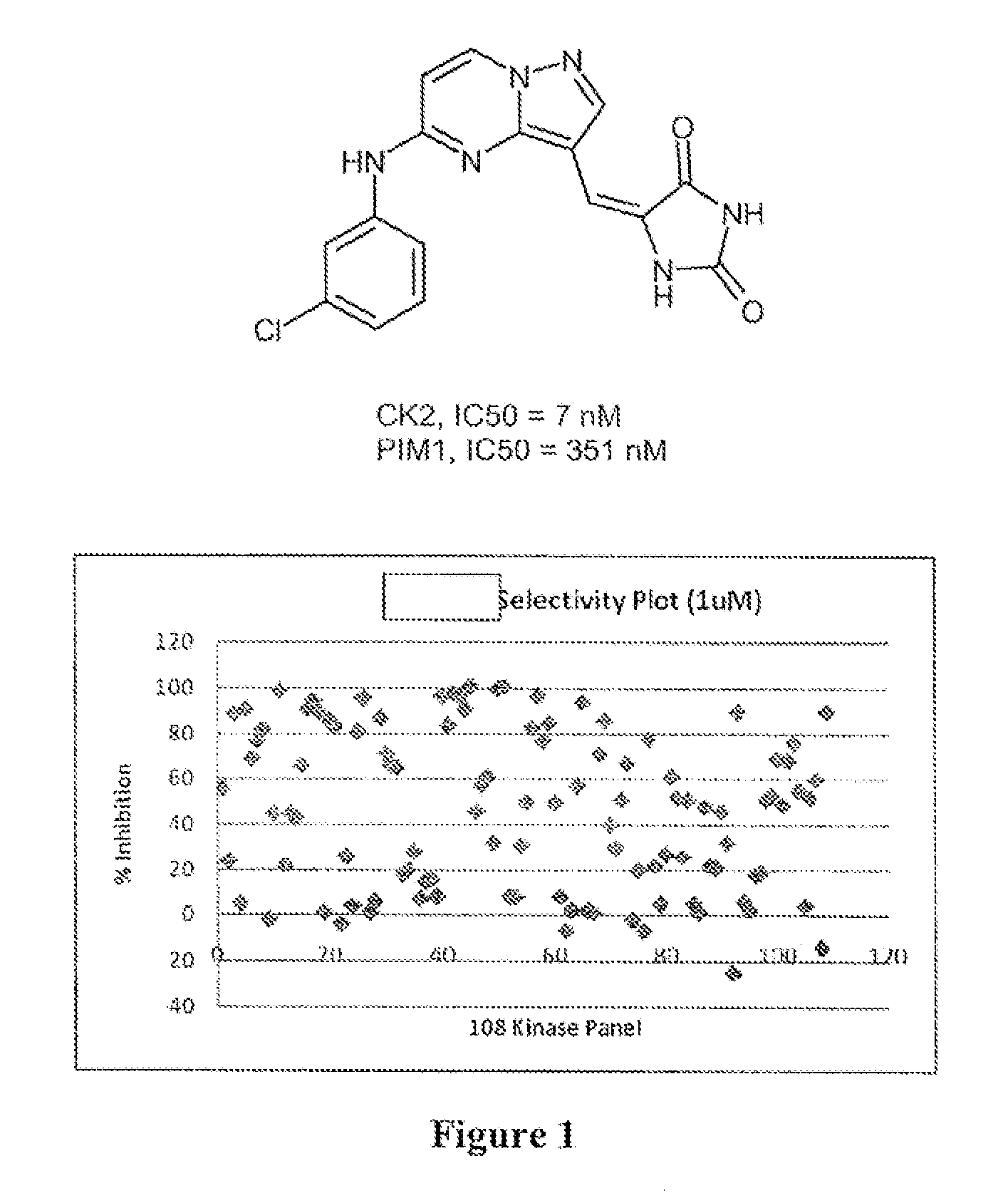
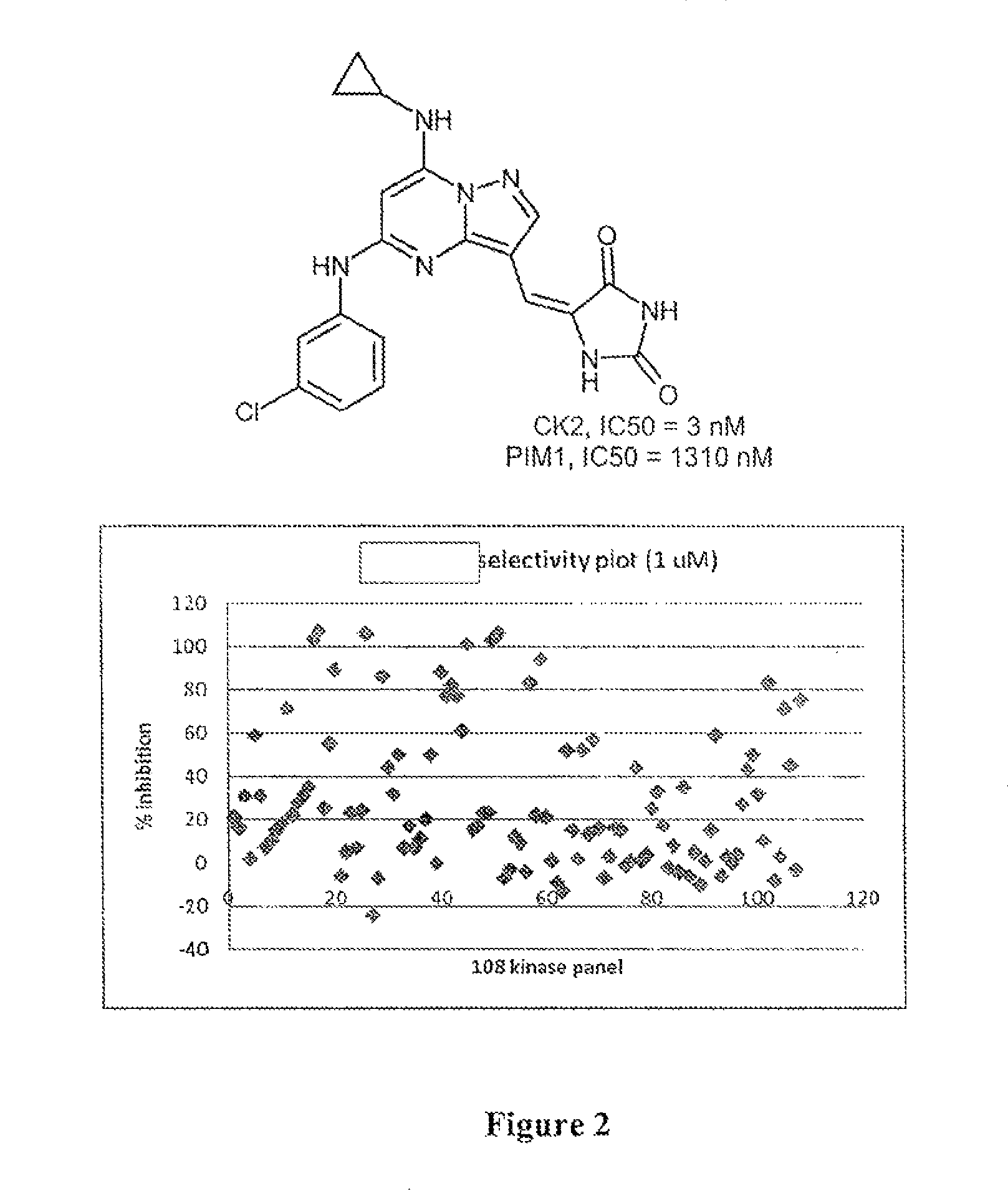
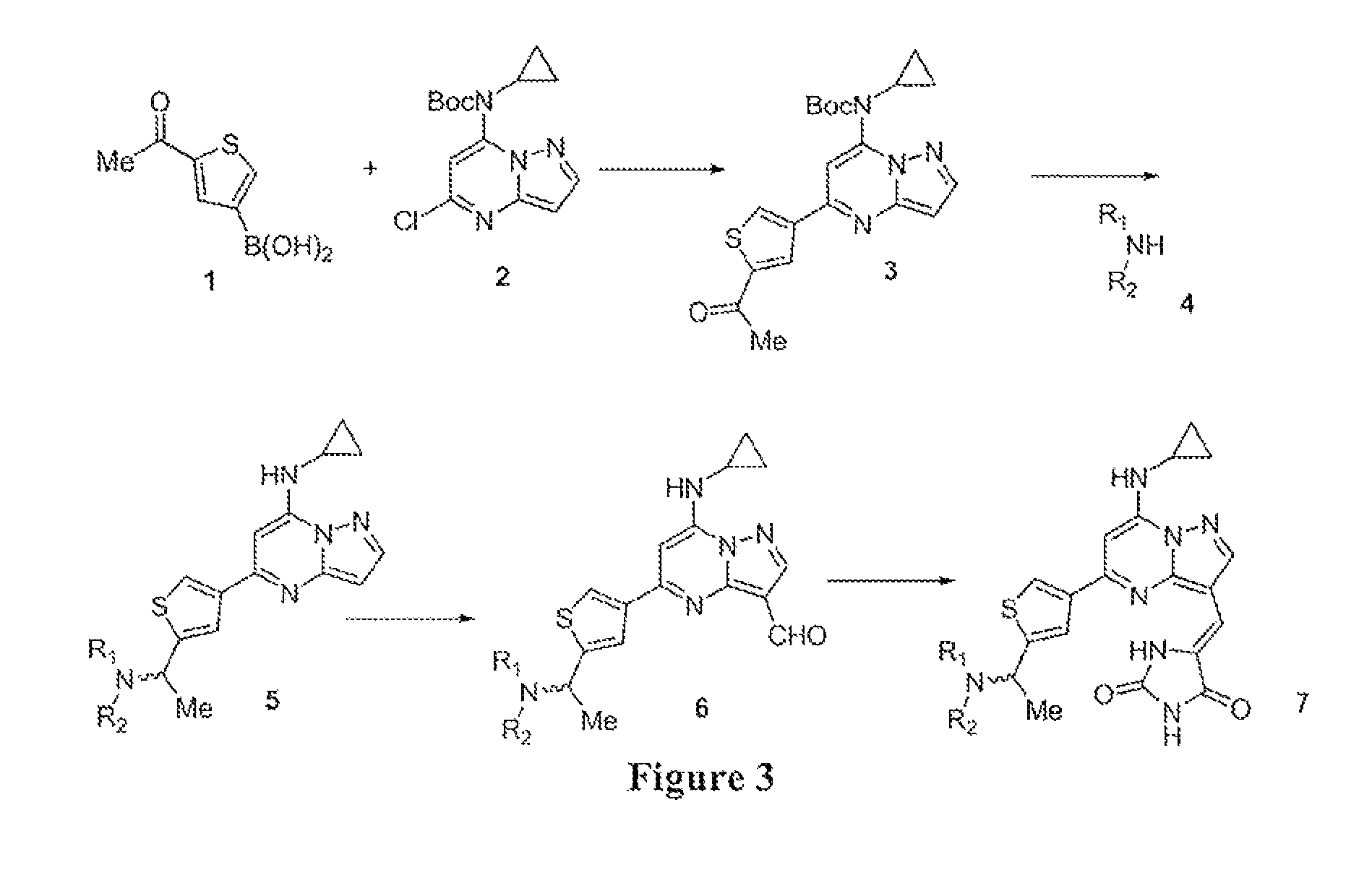
Pyrazolopyrimidines and related heterocycles as CK2 inhibitors
The invention provides compounds that inhibit protein kinase CK2 activity (CK2 activity), and compositions containing such compounds. These compounds and compositions are useful for treating proliferative disorders such as cancer, as well as other kinase-associated conditions including inflammation, pain, and certain immunological disorders, and have the following general formula:
Owner:SENHWA BIOSCIENCES INC
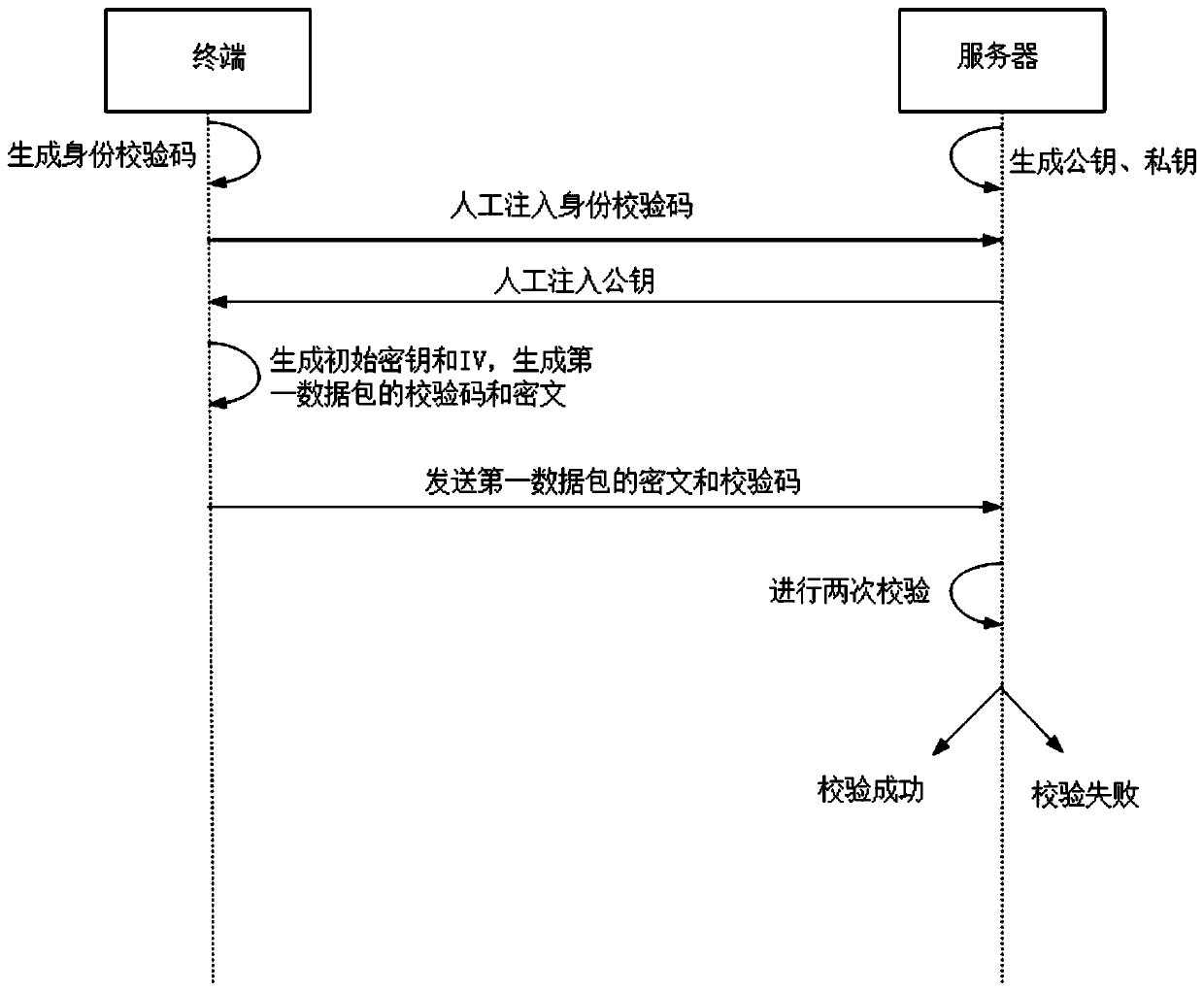
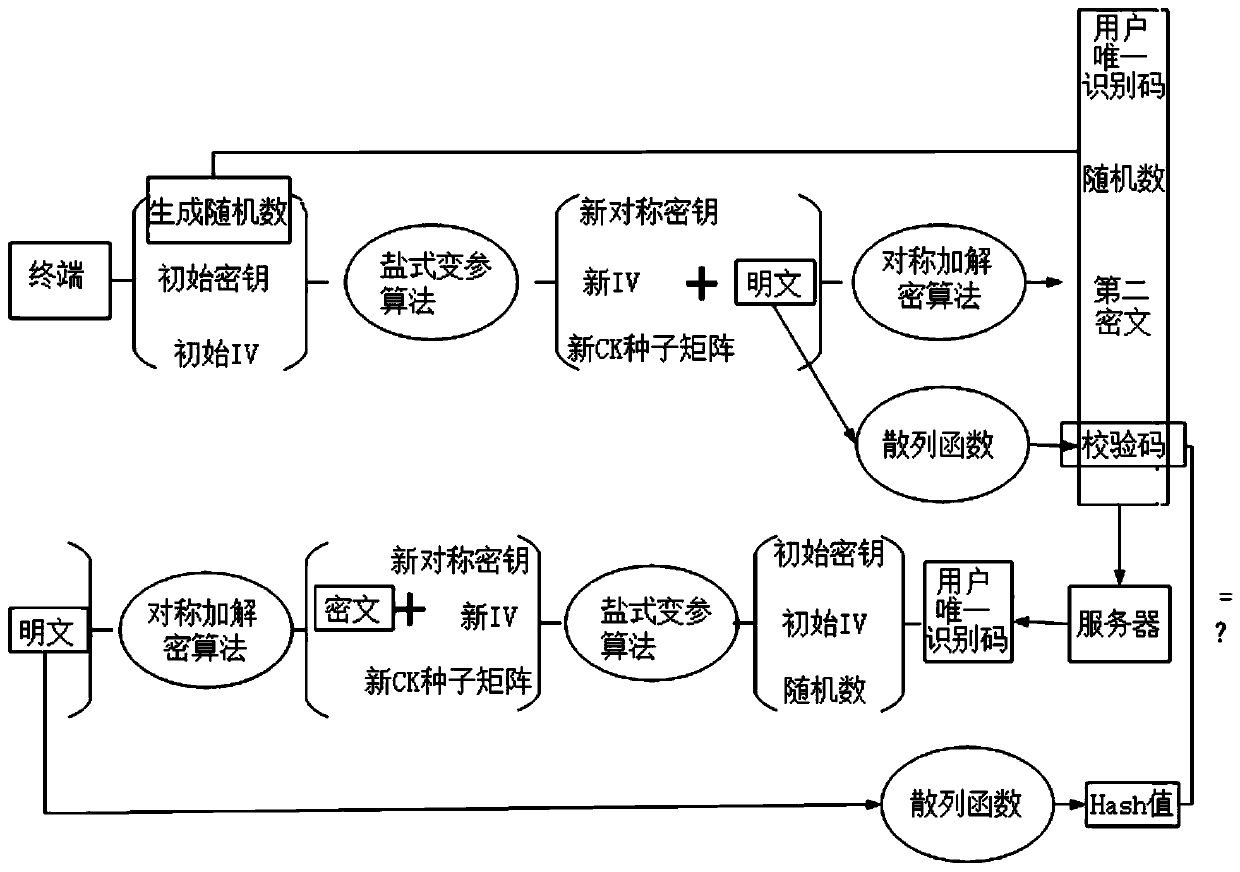
Security hybrid encryption method based on narrowband Internet of Things
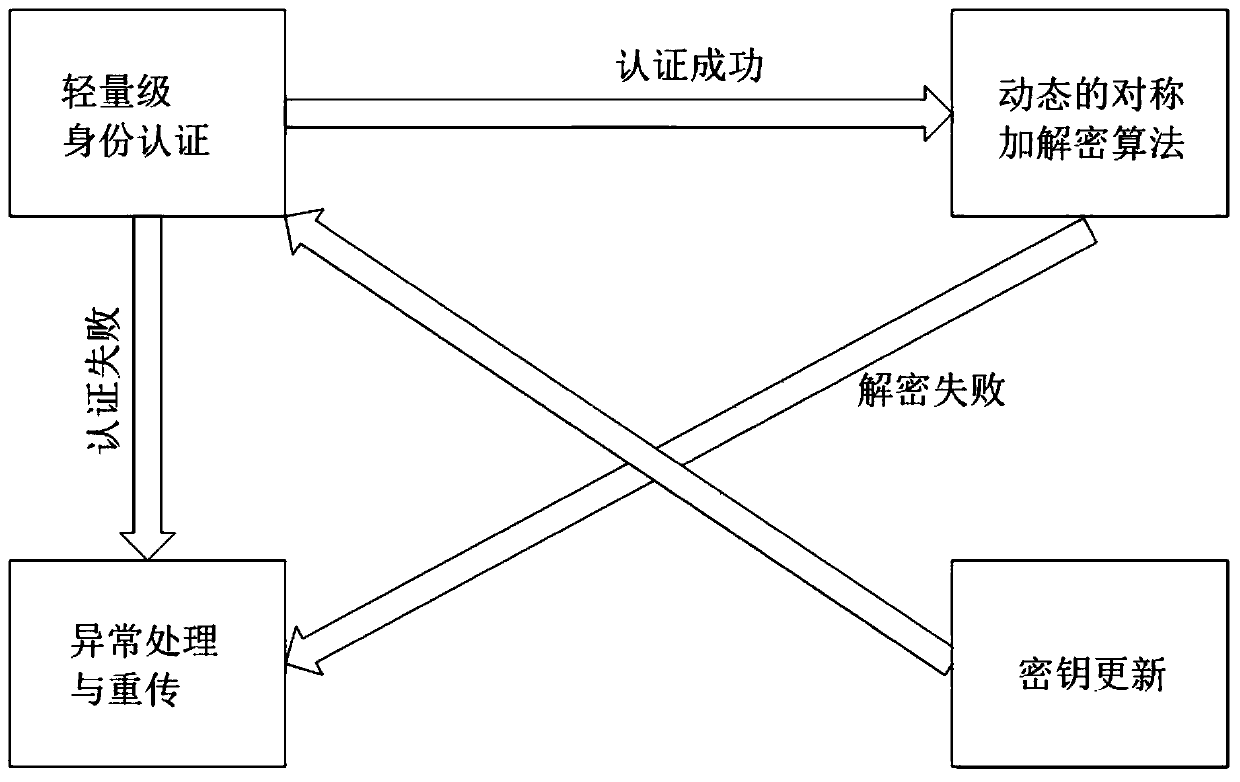
ActiveCN111541677AIncrease aggressivenessEasy to primeKey distribution for secure communicationMultiple keys/algorithms usageIdentity recognitionEngineering
The invention provides a security hybrid encryption method based on narrowband Internet of Things, which comprises the following steps of carrying out lightweight identity authentication on each terminal and a server, and realizing the identity authentication of the terminal and the transmission of an initial key and an initial IV vector by using unidirectional asymmetric encryption in the lightweight identity authentication, and after the identity authentication of the terminal succeeds, performing encryption communication between the terminal and the server by adopting a dynamic symmetric encryption and decryption algorithm, so that the symmetric encryption and decryption algorithm uses different symmetric keys and different structural parameters in each time of encryption communicationof each terminal. Lightweight identity recognition is adopted; on the basis of ensuring the security, the authentication time and the calculation consumption are greatly reduced, a dynamic symmetric encryption and decryption algorithm is adopted, a symmetric key and a set of structural parameters are ensured to be set at a time, the structural parameters of the algorithm are changed in a nonlinearmode under the condition that the large structure is not changed, and the capacity of the algorithm for resisting side channel attacks such as energy analysis is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
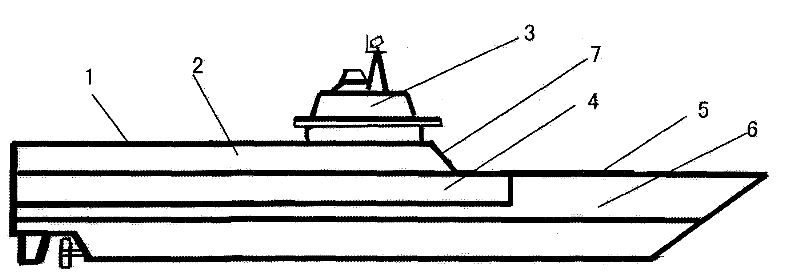
Invisible aircraft carrier with high combat power and survivability
InactiveCN102390507AImprove survivabilityInvisibility effect is goodAircraft carriersGround installationsSurvivabilityInvisibility
The invention discloses an invisible aircraft carrier with high combat power and survivability. The invisible aircraft carrier is characterized in that: firstly, width of a flight deck is greatly reduced, the flight deck and the aircraft carrier body below the deck are changed to be more regularly strip-shaped, the surrounding outer surface of the aircraft carrier body is made into a structure that large areas of outward bent and inward bent planes are crossed, and an invisible material is additionally adhered to the outer surface of the aircraft carrier body or an invisible coating is additionally coated on the outer surface of the aircraft carrier body; secondly, an aircraft hangar with width of 40m and length of 200-300m is made on the lower part of the flight deck; or a vertical two-layer aircraft hangar is made below the aircraft carrier surface of a middle rear part so as to greatly increase the number of aircrafts carried by the aircraft hangar; thirdly, 4-5 flight flying and receiving hatchways are formed on the tail part of the flight deck and on two side edges or in the center of the aircraft carrier surface of the middle front part, and the aircraft carrier surfaces on the front parts of the four aircraft flying and receiving hatchways on the side edge of the flight deck are provided with catapults, or the forefront part of the aircraft carrier body is provided with a flying deck; and fourthly, the upper part of the flight deck on the aircraft carrier surface for landing and receiving aircrafts is provided with four or more arrester wires, and the aircraft carrier surface on the ahead part is provided with a barrier net. Thus, the aircraft carrier with high combat power and high invisibility can be made.
Owner:郭宏斌
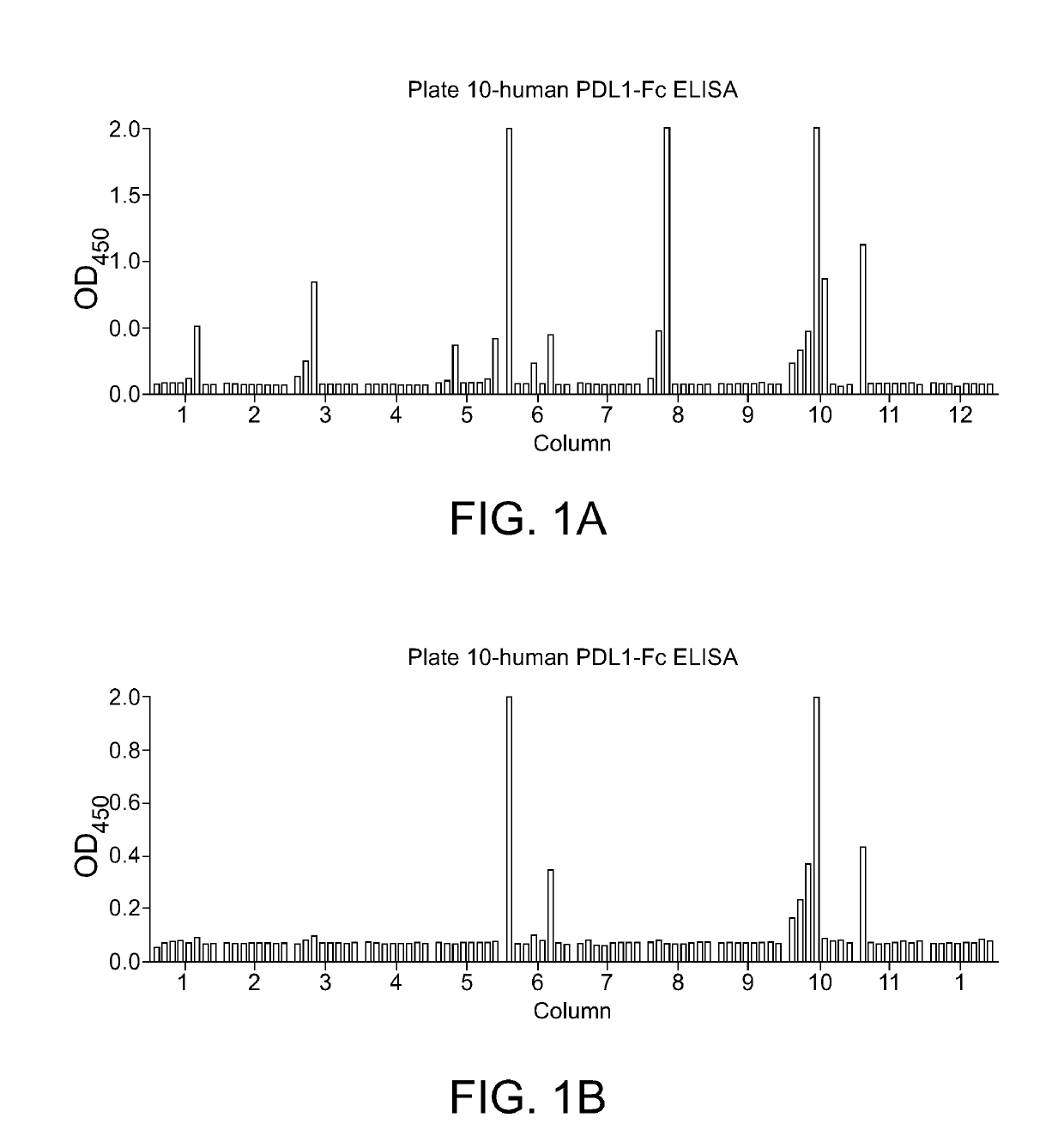
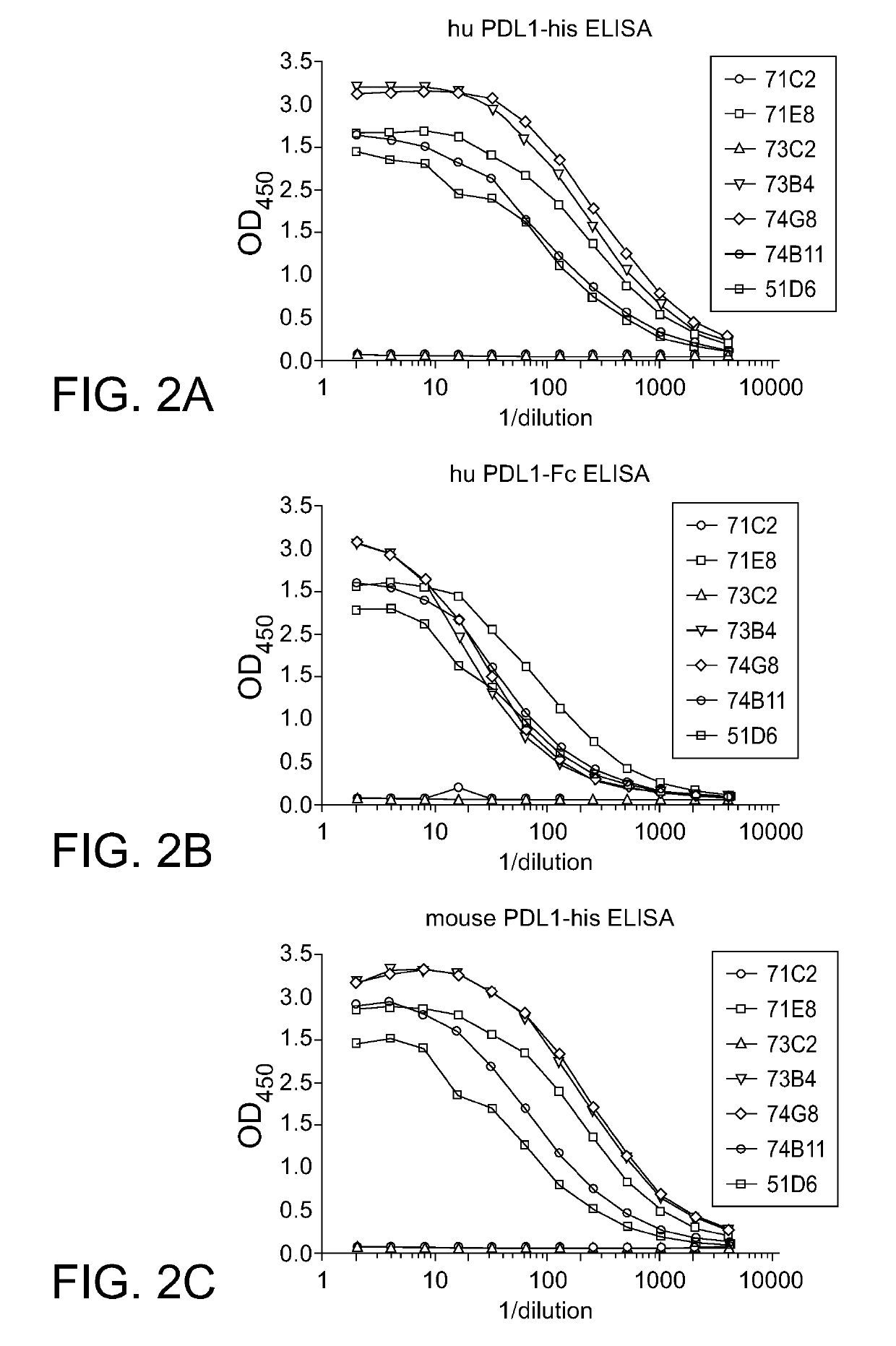
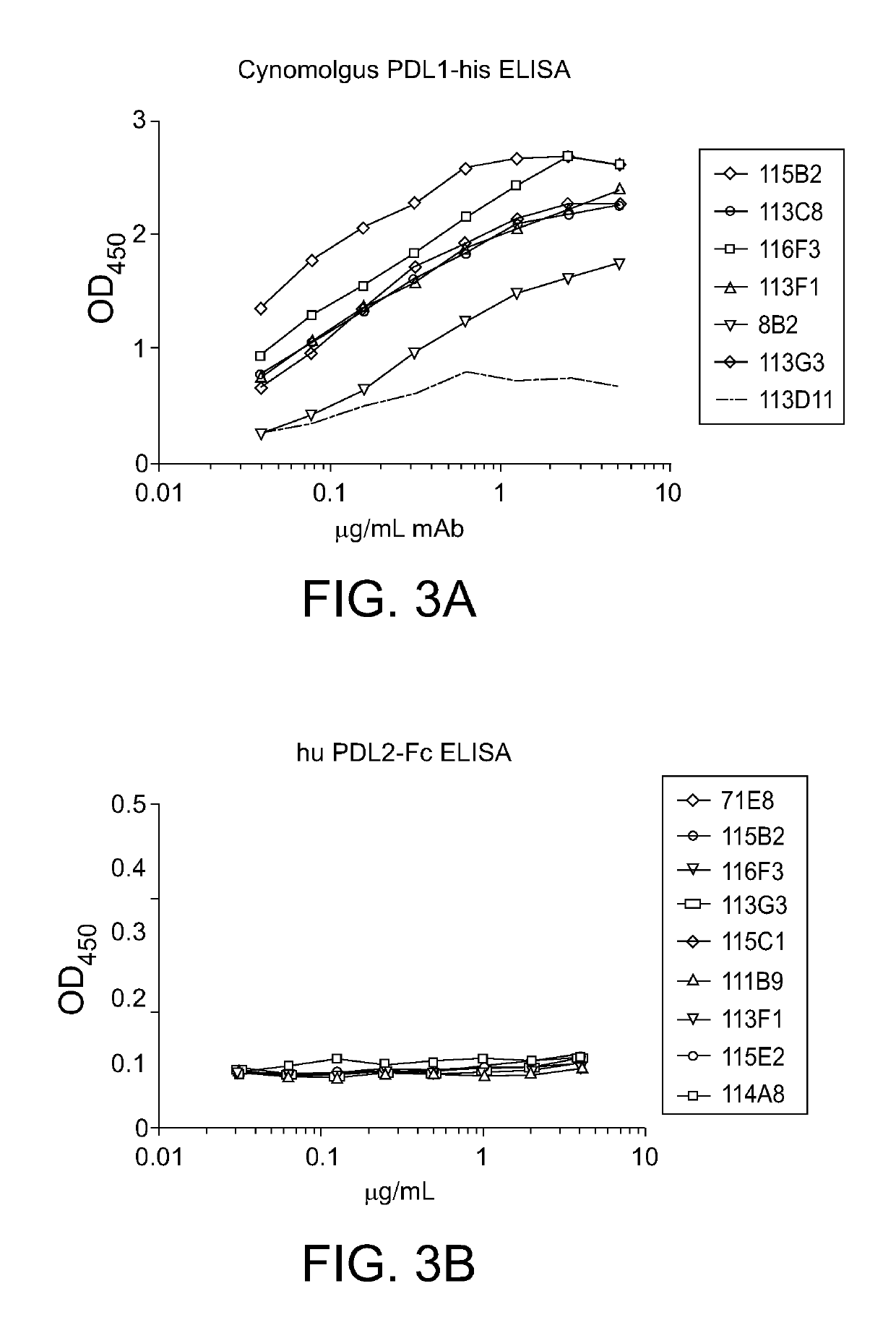
PD-L1 Specific Monoclonal Antibodies for Disease Treatment and Diagnosis
InactiveUS20190106494A1High expressionIncrease aggressivenessHybrid immunoglobulinsImmunoglobulins against cell receptors/antigens/surface-determinantsDiseaseMonoclonal antibody
The present invention relates to compositions and methods for immunotherapy of a subject afflicted with diseases such as cancer, an infectious disease, or a neurodegenerative disease, which methods comprise administering to the subject a composition comprising a therapeutically effective amount of an anti-PD-L1 antibody or portion thereof that potentiates an endogenous immune response, either stimulating the activation of the endogenous response or inhibiting the suppression of the endogenous response.
Owner:ASKGENE PHARM INC +1
Method and apparatus for capturing images with variable sizes
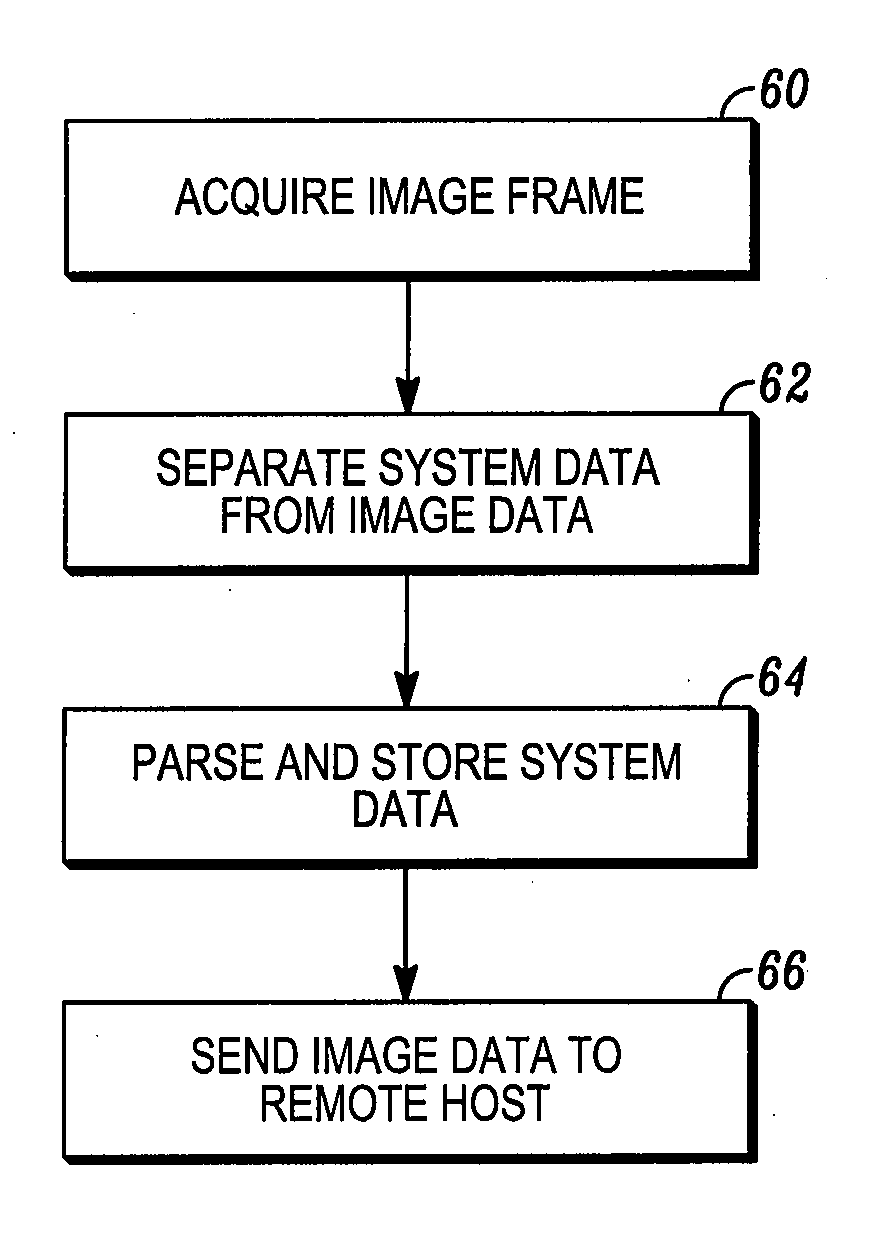
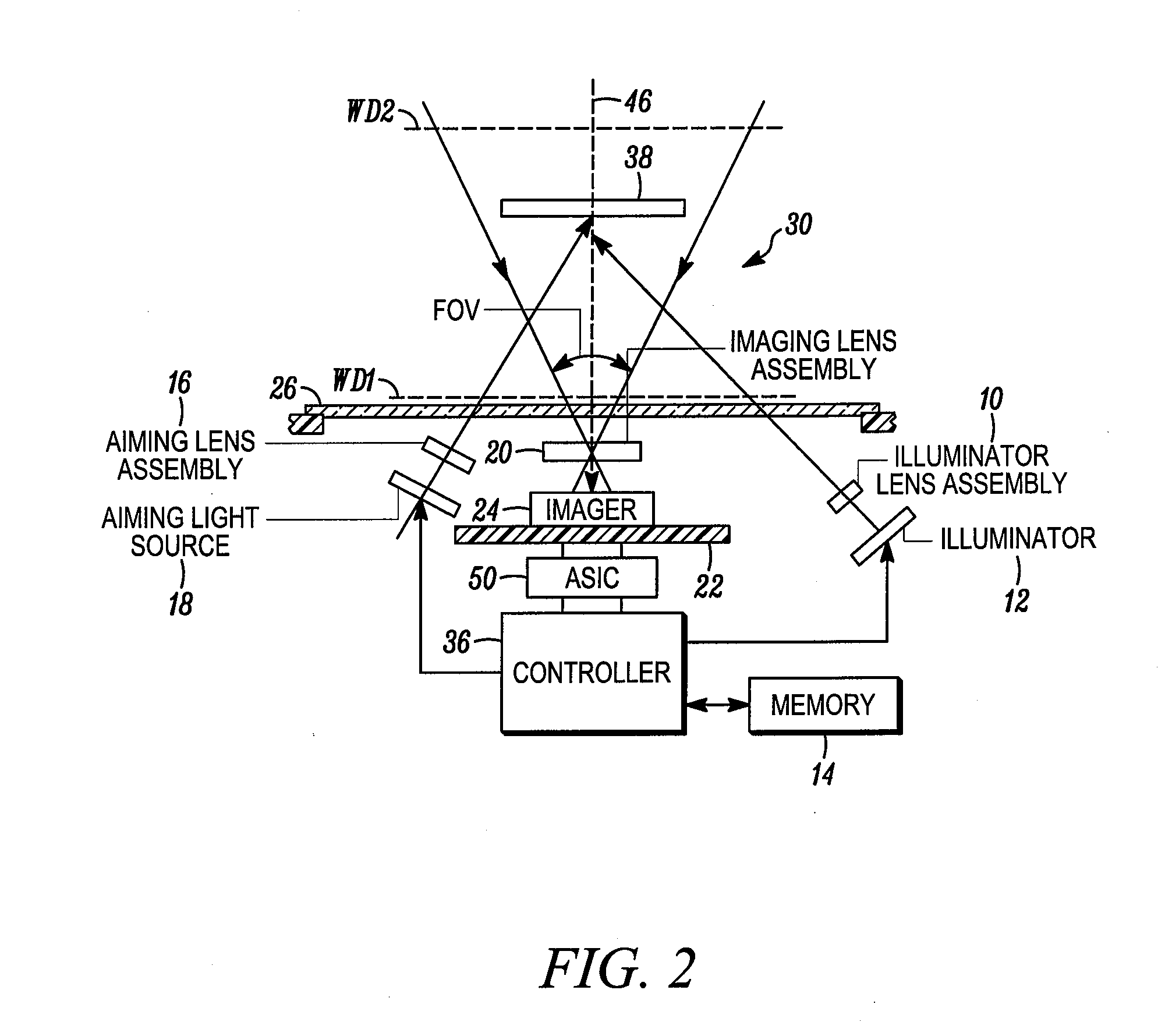
InactiveUS20120091206A1Easy to captureEasy to processSensing by electromagnetic radiationApplication-specific integrated circuitImaging data
A method and apparatus for imaging targets with an imaging reader. The method includes: operatively connecting an application specific integrated circuit (ASIC) to the solid-state imager to receive the image data from the solid-state imager and generating a stream of combined data frames by the ASIC. A combined data frame in the stream generated by the ASIC including an image frame from the image data and a header. The method also includes receiving and processing the stream of combined data frames from the ASIC at a controller operatively connected to the ASIC.
Owner:SYMBOL TECH LLC
Preparation method of polypeptide for inhibiting gelatin enzyme A activity and its application
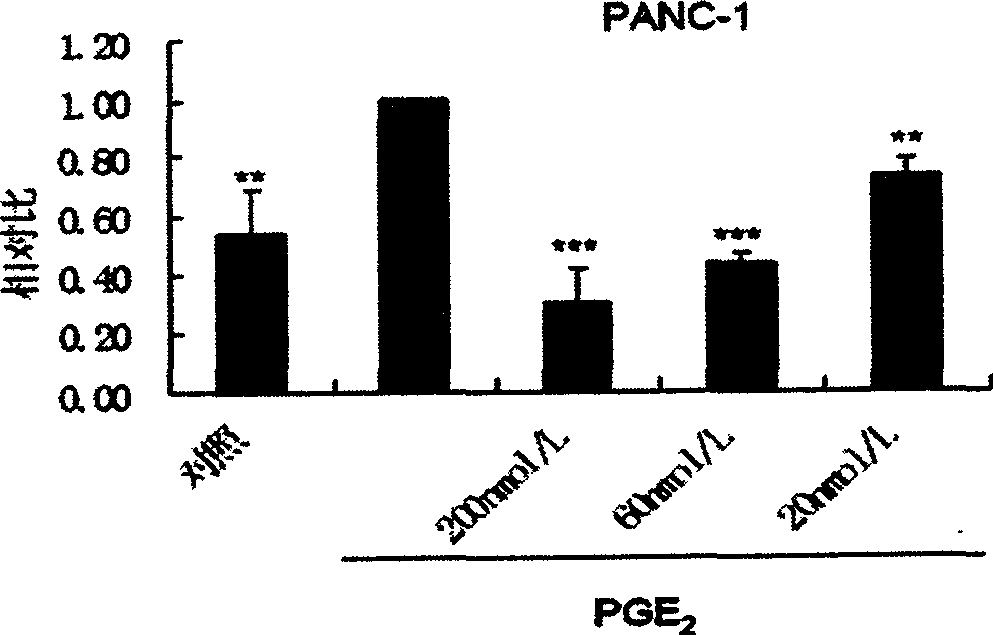
InactiveCN1869063AIncrease aggressivenessInhibition of invasion and metastasisPeptide/protein ingredientsMicrobiological testing/measurementPancreas CancersFluorescence
A polypeptide M204C4 for suppressing the activity of gelatinase A (MMP-2) is composed of the amino acid sequence shown by HNWTRWLLHPDRGGGS is disclosed. It can also suppress the invasion and transfer of external pancreas cancer cells PANC01 and CFPAC-1. Its preparing process includes such steps as affinity screening and reproduction of bacteriophage several times to obtain the bacteriophage with specific binding to MMP-2, coating, cloning and monoclonal screening with fluorescent screening reagent kit.
Owner:NANJING MEDICAL UNIV
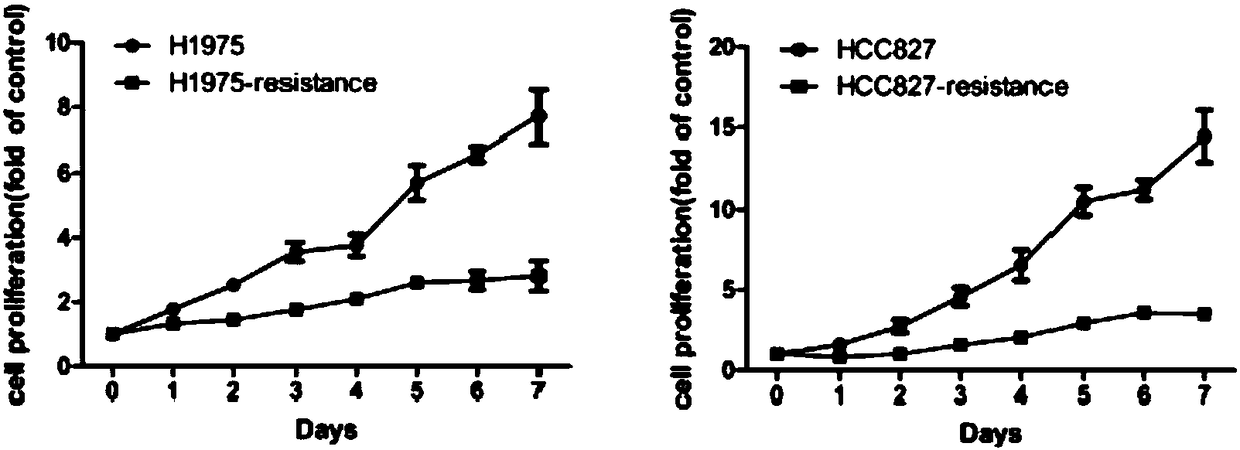
Drug-resistance cell system for lung cancer and preparation method thereof
InactiveCN108118031AEffectively induce the formation ofManufacturableCulture processTumor/cancer cellsCell systemDrug resistance
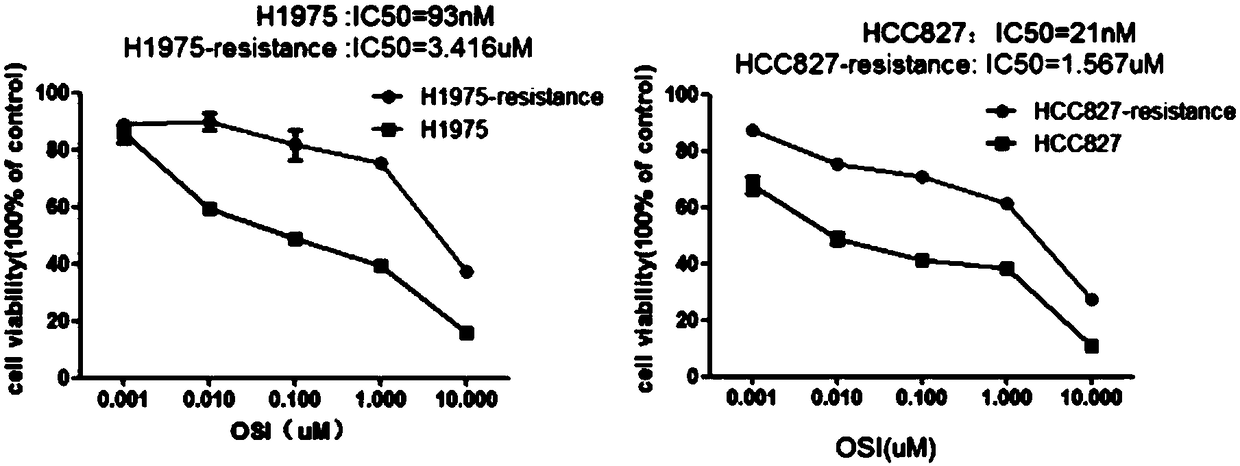
The invention relates to the field of drug-resistance cell systems, and particularly relates to a drug-resistance cell system and a preparation method thereof. The method comprises the following steps: inoculating the lung cancer cells to a culture medium containing a 21-93nM lung cancer targeted drug; culturing until cells can normally live and multiply under the same concentration; improving andculturing at 50nM concentration difference; improving and culturing at concentration difference of every 100nM when the cell multiplying inhibiting concentration is 4 times of IC50; improving and culturing at concentration difference of every 1 microns when the drug sieving concentration is 8 times of IC50; and obtaining the drug-resistance cell systems for the lung cancer when the lung cancer cells can live and multiply in a cell culture system of 10 microns osimertinib. According to the method, the drug-resistance cell system is prepared on the basis of gradually increasing the concentration of drugs in the culture medium; the foundation is provided for later simulation of clinical drug resistance, researching of drug resistance mechanism of lung cancer targeted drugs, and developing ofeffective drug resisting drugs.
Owner:SHANGHAI CHEST HOSPITAL
Imperceptible watermark attack method based on residual learning, storage medium and electronic device
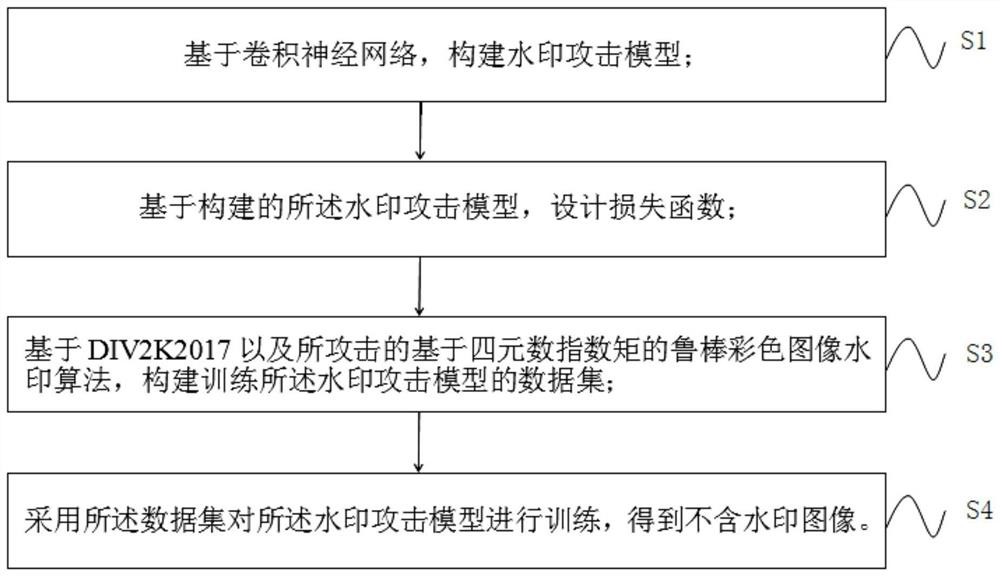
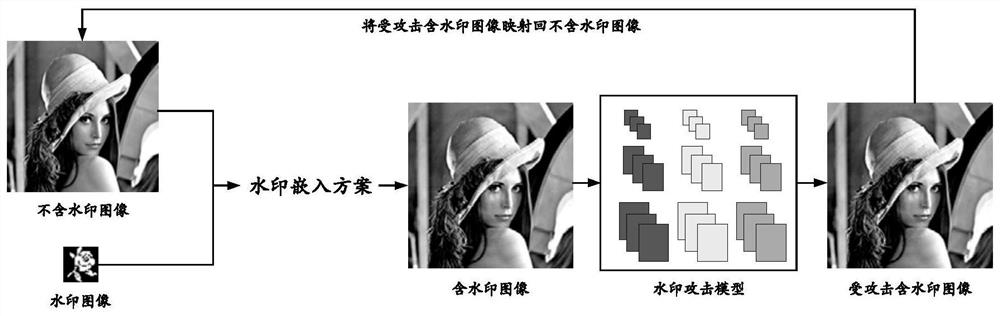
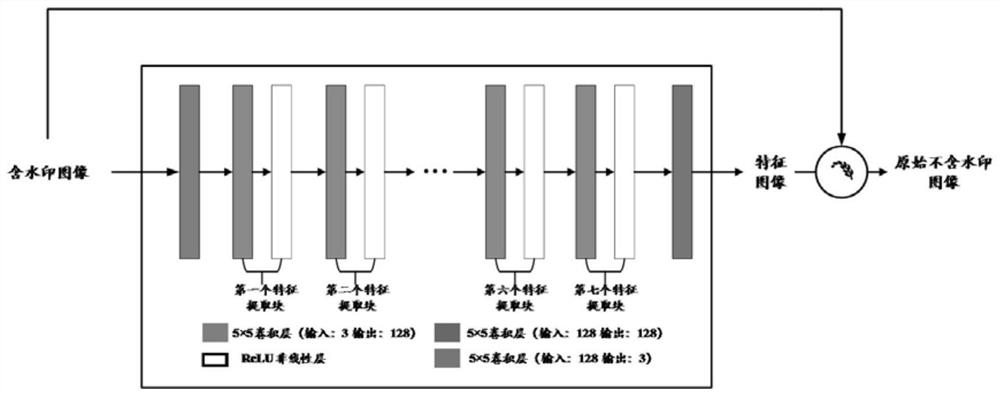
PendingCN113379584AReduce content changesGuaranteed high imperceptibilityImage watermarkingNeural architecturesLearning machineData set
The invention provides an imperceptible watermark attack method based on residual learning, a storage medium and an electronic device. The method comprises the steps: constructing a watermark attack model based on a convolutional neural network, carrying out the end-to-end nonlinear learning between a watermark-containing image and a watermark-free image, mapping the watermark-containing image to the watermark-free image, and carrying out watermark attack; selecting a proper number of feature extraction blocks according to the embedded area of the watermark information to extract a feature map containing the watermark information; introducing a residual learning mechanism to improve the convergence speed and learning ability of a watermark attack model, and improving the imperceptibility of an attacked image by reducing the difference between a residual image and the watermarking-free image; and constructing a data set for training a watermark attack model according to a DIV2K2017 super-resolution data set and a robust color image watermark algorithm based on a quaternion exponential moment. The watermark attack model provided by the invention can attack a robust watermark algorithm at a high bit error rate on the premise of not destroying the visual quality of a watermark-containing image.
Owner:DALIAN MARITIME UNIVERSITY
Therapeutic methods and compositions for the treatment of impaired interpersonal and behavioral disorders
InactiveUS7387778B2Increase capacityImprove the environmentNervous disorderAerosol deliverySustaining attentionBehavioural disorders
The invention relates to the field of psychopharmacology. More particularly, the invention relates to the treatment of mental disorders, such as impaired interpersonal and behavioral disorders, including sexual disorders such as M.E.D. and H.S.D.D. The invention provides new therapeutic compositions and methods for treating mental disorders, including M.E.D. and H.S.D.D. The compositions and methods according to the invention provide improved awareness and alertness to environment, improved adaptation to environment and ability to sustain attention, and increased interest in environment and capacity for arousal, without increased aggressiveness.
Owner:INST PASTEUR +1
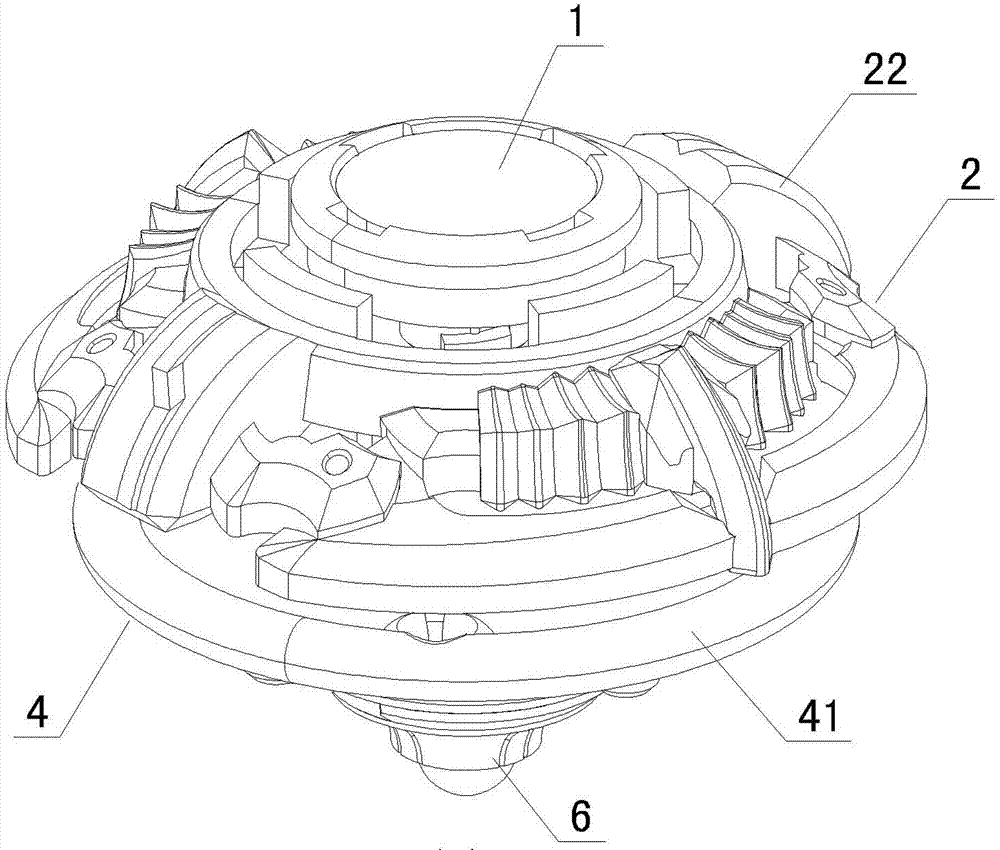
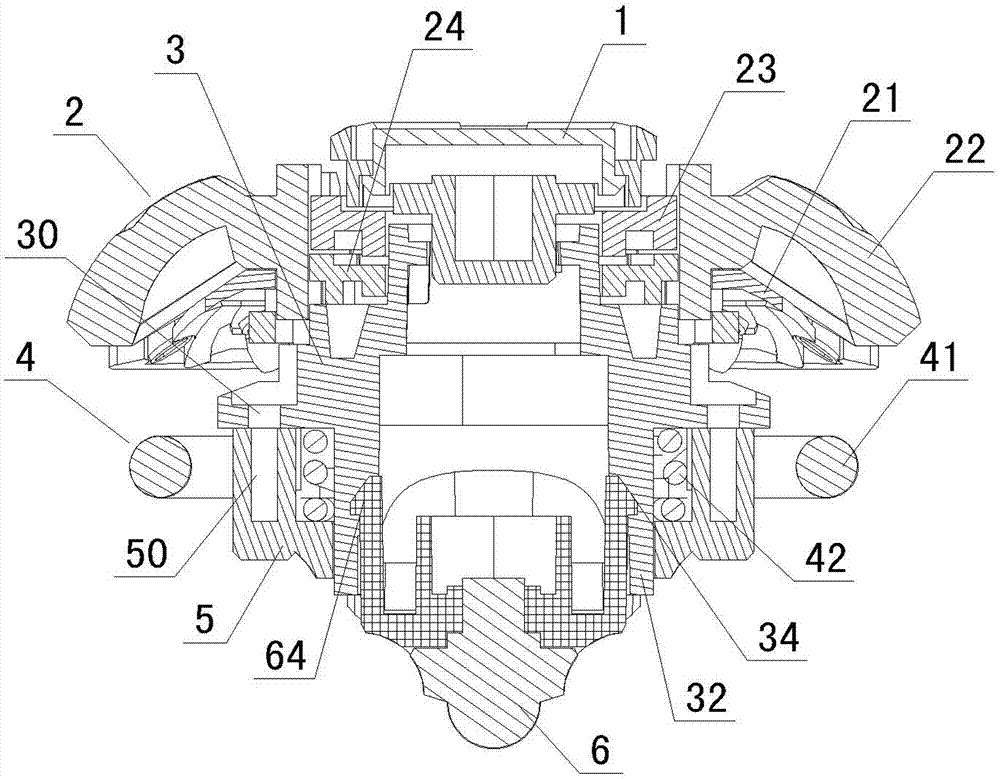
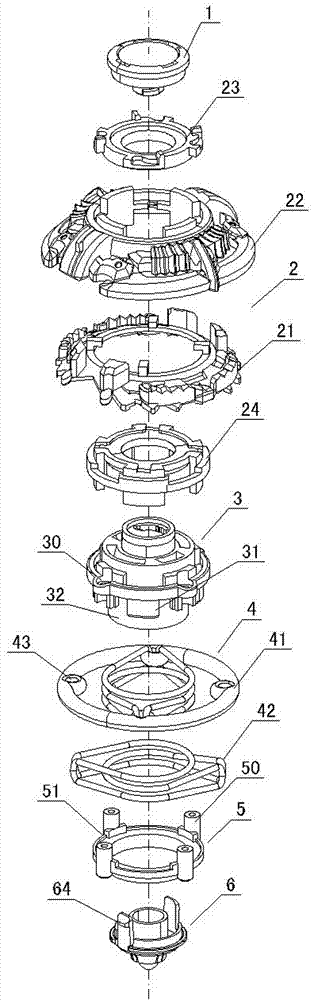
Toy gyro good in defensiveness
The invention provides a toy gyro good in defensiveness. The toy gyro comprises a spiral cover, a spiral sheet, a spiral base and a hillock point, and is characterized by further comprising an elastic shock absorption piece for buffering impact force when the gyro is impacted. The shock absorption piece is provided with an elastic part used for resisting impact and a connection part fixedly connected with the spiral base. The elastic part is located on the periphery of the spiral base through fixed connection of the connection part and the spiral base, and therefore when the gyro competes with other gyros and the other party impacts on the elastic part, impact force will be reduced due to elastic deformation of the elastic part; thus, the shock absorption effect is achieved to make the gyro rotate stably, anti-impact force is produced and returned to the other party at the same time to interfere the other party, and accordingly the win rate of the gyro is improved. The toy gyro is strong in interestingness, the elastic property of the elastic shock absorption piece can be changed by a player according to judgments so as to achieve a better anti-impact effect, the method to play the toy gyro is novel, the toy gyro can attract more players, and manipulative ability and competitive ability of children can be trained at the same time.
Owner:ALPHA GRP CO LTD +2
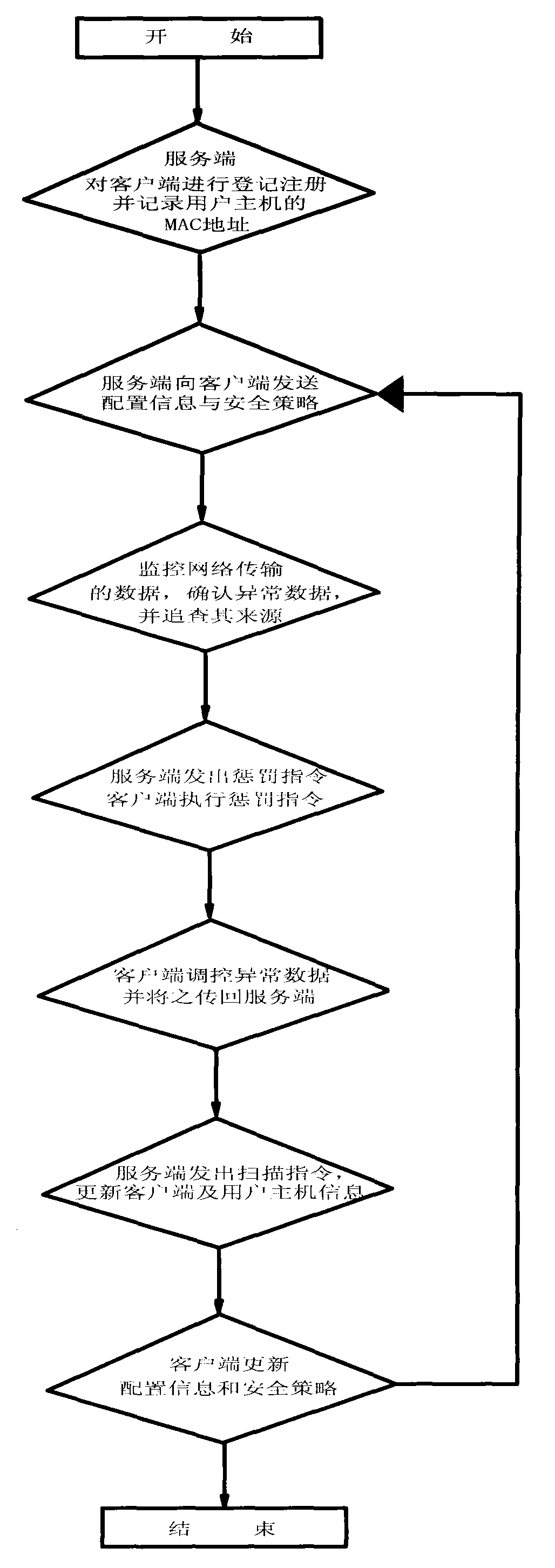
ASN (attack security interaction) and implementation method thereof
InactiveCN102088455ARealize direct unified managementSimplify administrative proceduresData switching networksProtocol processingSystems management
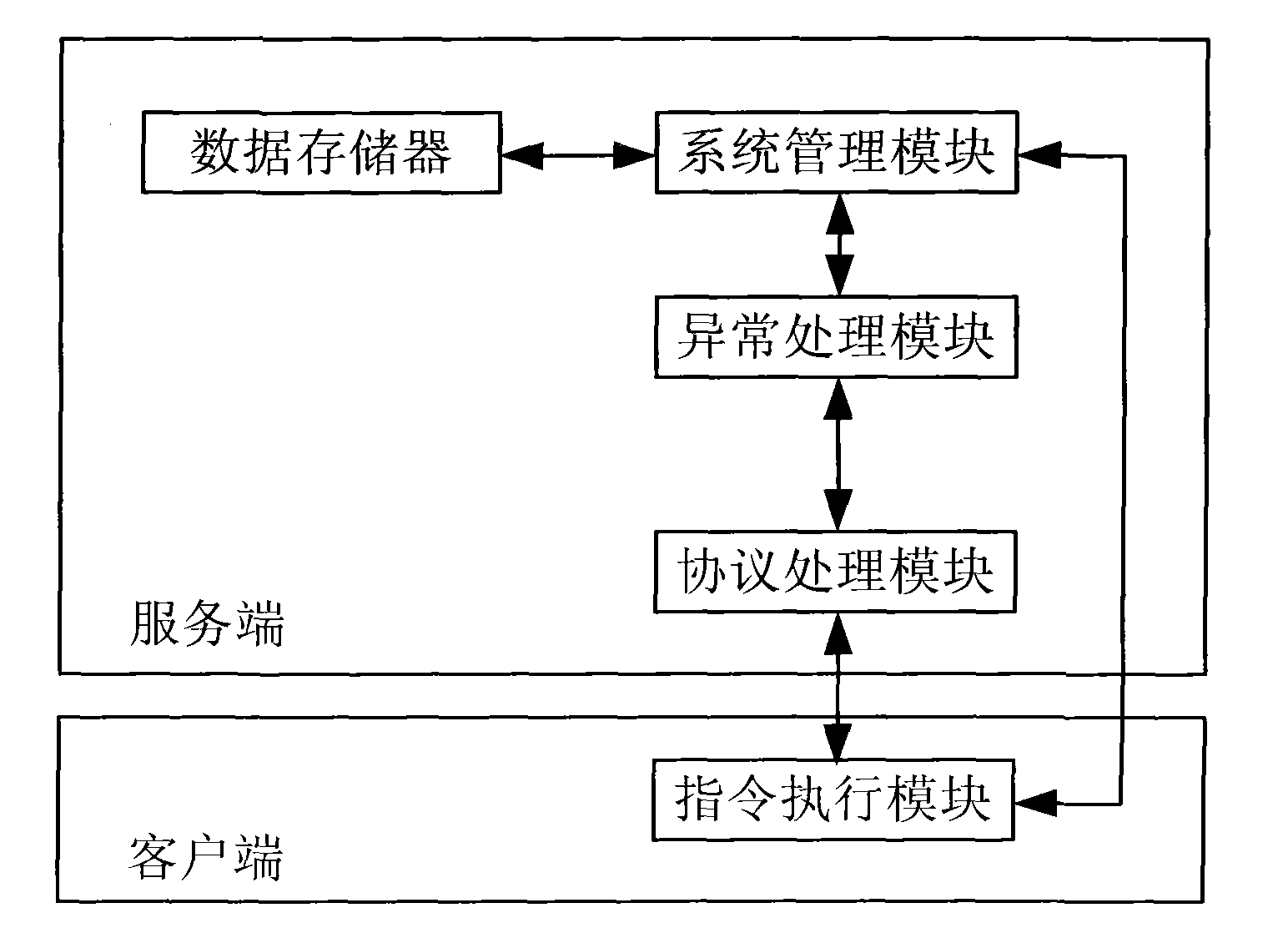
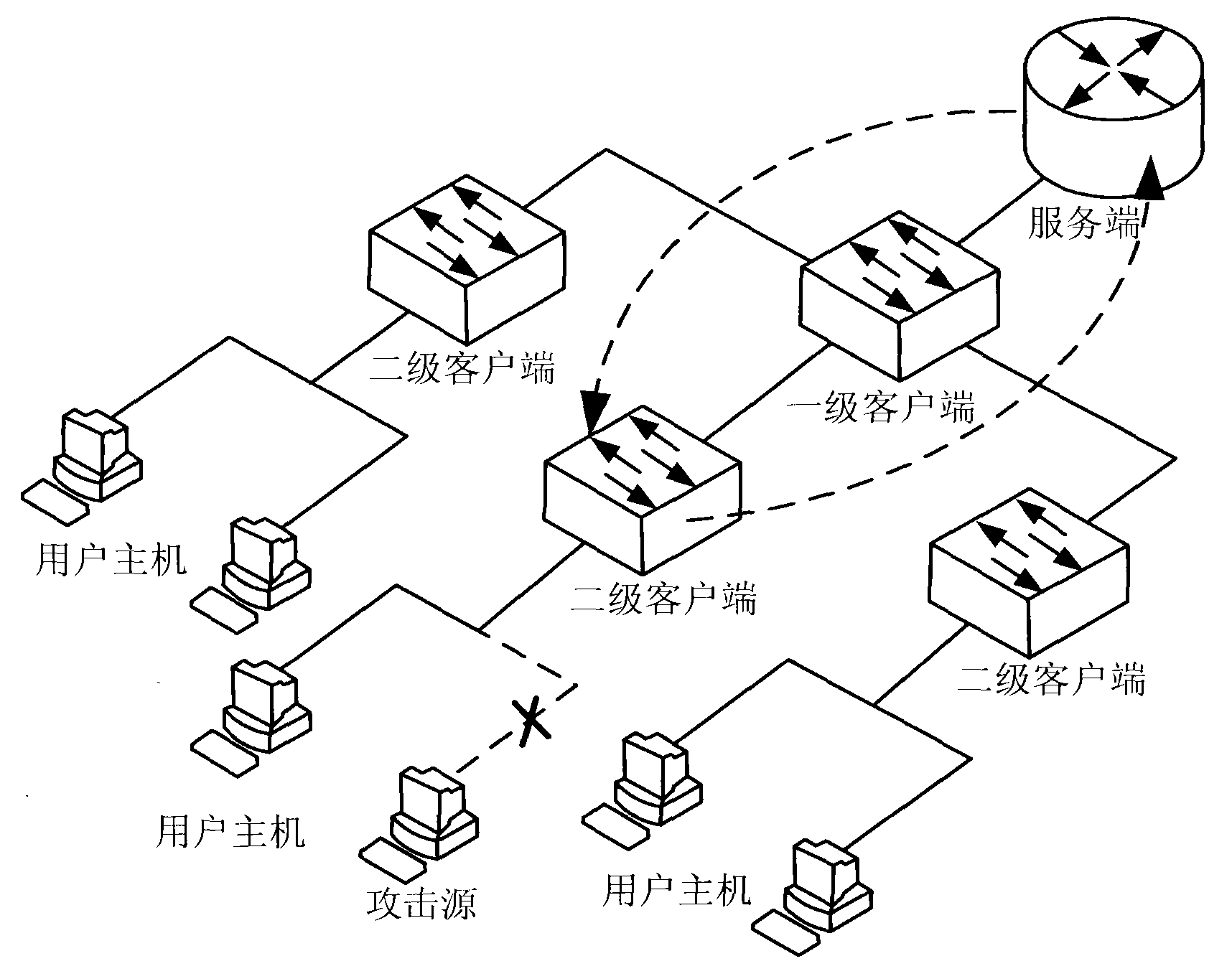
The invention discloses an ASN (attack security interaction), which belongs to the technical field of network communications and is used for solving the problem that the self-protection capacity of a network service end in the prior art is too weak. The ASN comprises a service end, a client-side and a user host machine, wherein the service end and the client-side are in a mapping relation; the client-side and the user host machine are in a mapping relation; a system management module, an exception handling module, a protocol processing module and a data storage are embedded in the service end; an instruction execution module is embedded in the client-side; the data storage, the exception handling module and the instruction execution module are directly connected with the system management module and controlled by the system management module; and the protocol management module is respectively connected with the exception handling module and the instruction execution module. The invention also provides an implementation method of the ASN. By using the implementation method of the ASN, the active defense and attack of the service end and the client-side is implemented, the network safety is improved, and the practical value is very high.
Owner:成都飞鱼星科技股份有限公司
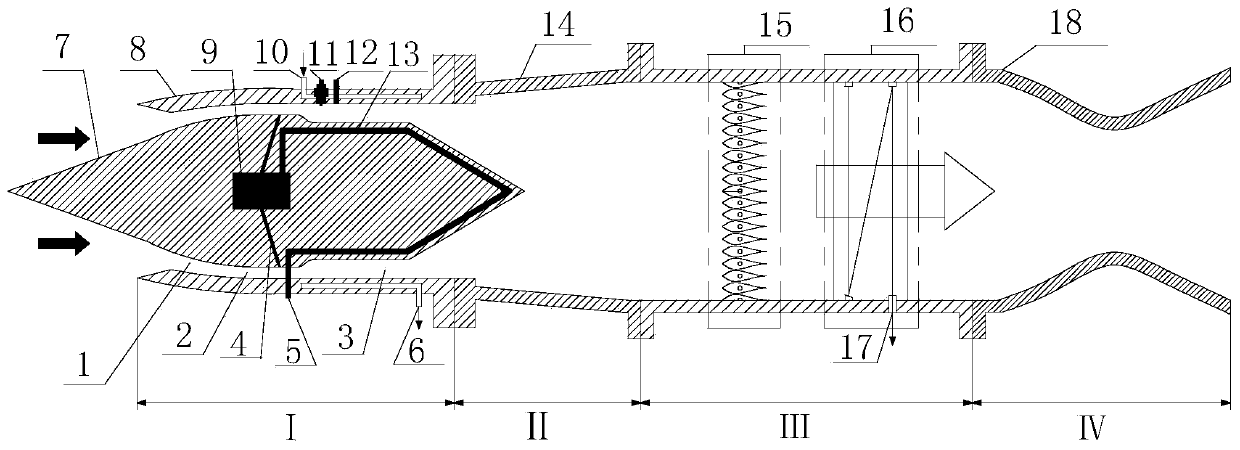
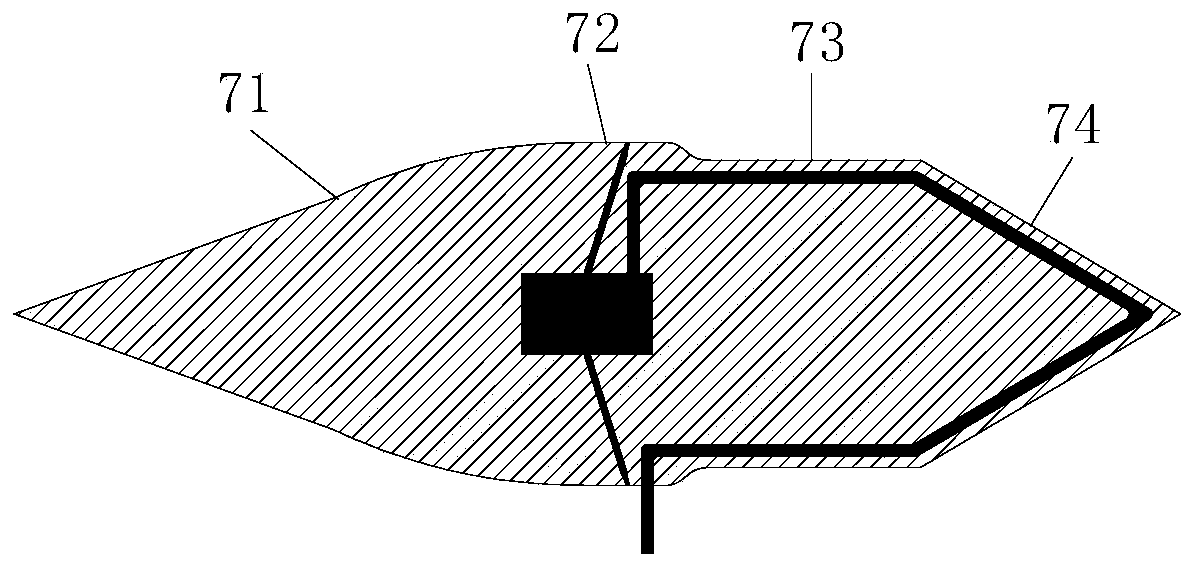
Air-breathing premixed carbon dioxide pneumatic laser driven by continuous rotary detonation combustion
ActiveCN110718843ADetonation combustion achievedDetonation combustion hasLaser detailsCombustion chamberFlight vehicle
The invention discloses an air-breathing premixed carbon dioxide pneumatic laser driven by continuous rotary detonation combustion. The laser comprises an air-breathing continuous rotary detonation combustion device, a transition section, a CO2 pneumatic laser generation device and an exhaust section. The air-breathing continuous rotary detonation combustion device is used for generating a high-temperature and high-pressure fuel gas heat source serving as total energy for downstream output laser, and comprises a center body and a cylindrical shell. The center body comprises an air inlet cone part, a large cylinder part, a small cylinder part and a tail cone part which are sequentially arranged from front to back. An air inlet channel is formed by a gap between the air inlet conical part and the front-end conical shell, and a rotary detonation combustion chamber is formed by a gap between the small cylindrical part and a rear-end cylindrical shell. The laser is applied to an air-breathing aircraft, and the air-breathing continuous rotary detonation combustion device is adopted as a pumping source; the generated laser is high in efficiency, and energy is saved. The same air-breathingcontinuous rotary detonation combustion device is adopted without increasing the load, so not only can thrust be generated, but also laser can be generated.
Owner:PLA PEOPLES LIBERATION ARMY OF CHINA STRATEGIC SUPPORT FORCE AEROSPACE ENG UNIV
Premixed carbon dioxide pneumatic laser driven by combustion of continuous rotary detonation rocket
ActiveCN110707521AImprove cycle efficiencyRealize burning and producing lightLaser detailsCombustion chamberEngineering
The invention discloses a premixed carbon dioxide pneumatic laser driven by the combustion of a continuous rotary detonation rocket. The premixed carbon dioxide pneumatic laser comprises a continuousrotary detonation combustion device, a transition section, a CO2 pneumatic laser generation device and an exhaust section. The continuous rotary detonation combustion device is used for generating a high-temperature and high-pressure fuel gas heat source as a total energy source of downstream output laser and comprises a shell, a central cone, a rotary detonation combustion chamber and an injection panel, the transition section enables the fuel gas behind the combustion device to adapt to configuration changes, and enables the fuel gas to stably flow to the front of an array spray pipe with the total pressure loss as small as possible, the CO2 pneumatic laser generating device comprises the array spray pipe and an optical cavity, and the exhaust section enables a product gas after light emitting to be rapidly exhausted to the outside. The continuous rotary detonation rocket combustion device is adopted as a pumping source, so that the produced laser is high in efficiency, and the energy is saved. The premixed carbon dioxide pneumatic laser can be used on a rocket or an aircraft boosted by a rocket, and not only can generate thrust, but also can generate laser without increasing theload, and can also be used as a high-power continuous intense laser light source on the ground.
Owner:PLA PEOPLES LIBERATION ARMY OF CHINA STRATEGIC SUPPORT FORCE AEROSPACE ENG UNIV
Mouth-open feed for rearing calves and preparation method for mouth-open feed
InactiveCN104782982AExcellent food attractantGood palatabilityAnimal feeding stuffAnimal scienceGastrointestinal tract
The invention discloses mouth-open feed for rearing calves, belongs to the field of livestock feed, and particularly relates to feed for rearing calves in weaning period. The mouth-open feed is prepared by mixing fermented milk, silage and wheat bran, and comprises the following components in percentage by weight: 20 to 50 percent of fermented milk, 30 to 60 percent of silage and 15 to 25 percent of an additive, wherein the additive is one or a mixture of one or more of wheat bran, corn meal and soybean meal. According to the mouth-open feed for rearing the calves, probiotics are directly added into fresh milk for the calves for fermentation, and the fermented milk is added into the mouth-open feed, and milk flavor has high feeding attraction performance for the weaned calves, so that the palatability is high; the fermented milk is supplemented in a preparation process, so that the calves can be easily transitioned from total milk rearing to solid rearing; due to the addition of the probiotics into the mouth-open feed, the probiotic cultivation in the stomach intestines of the calves is enhanced, the digestive absorption function of the gastrointestinal tracts is improved, and trophic diarherra and bacterial diarherra of the calves can be effectively prevented.
Owner:洱源县益新硕庆肉牛养殖有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com