Long window scaling factor-based playback voice attack detection algorithm
A scaling factor and attack detection technology, applied in speech analysis, instruments, etc., to achieve the effect of improving security issues, high detection accuracy, and improving attack capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The embodiments of the present invention will be described in detail below in conjunction with the above-mentioned drawings.
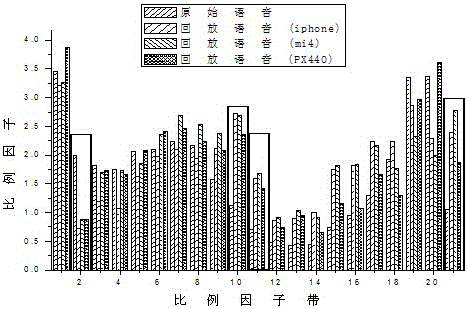
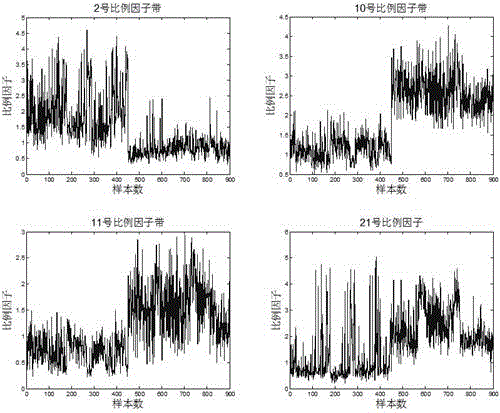
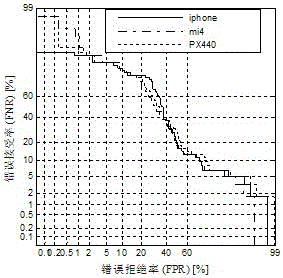
[0028] A replay voice attack detection algorithm based on the long window scale factor. It is a detection algorithm developed to prevent the legitimate user's rights and interests by using the replay voice to enter the speaker recognition system by using the replay voice. After the detection algorithm module is loaded into the GMM-UBM system, it improves the ability to resist playback voice attacks, reduces the equal error probability of the recognition system by 32%, and greatly improves the security of the recognition system.
[0029] The detection algorithm involves the basic concepts of the GMM-UBM identification system and the long window scale factor, specifically:
[0030] GMM-UBM identification system
[0031] GMM-UBM (Gaussian Mixture Model - Universal Background Model) is called the Gaussian mixture model based on the universal backgr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com