ASN (attack security interaction) and implementation method thereof
A technology of linkage system and implementation method, which is applied in the direction of transmission system, digital transmission system, electrical components, etc., can solve the problems of poor network control ability and weak defense attack ability, and achieve convenient operation, improved active operability, and avoidance of management chaotic effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
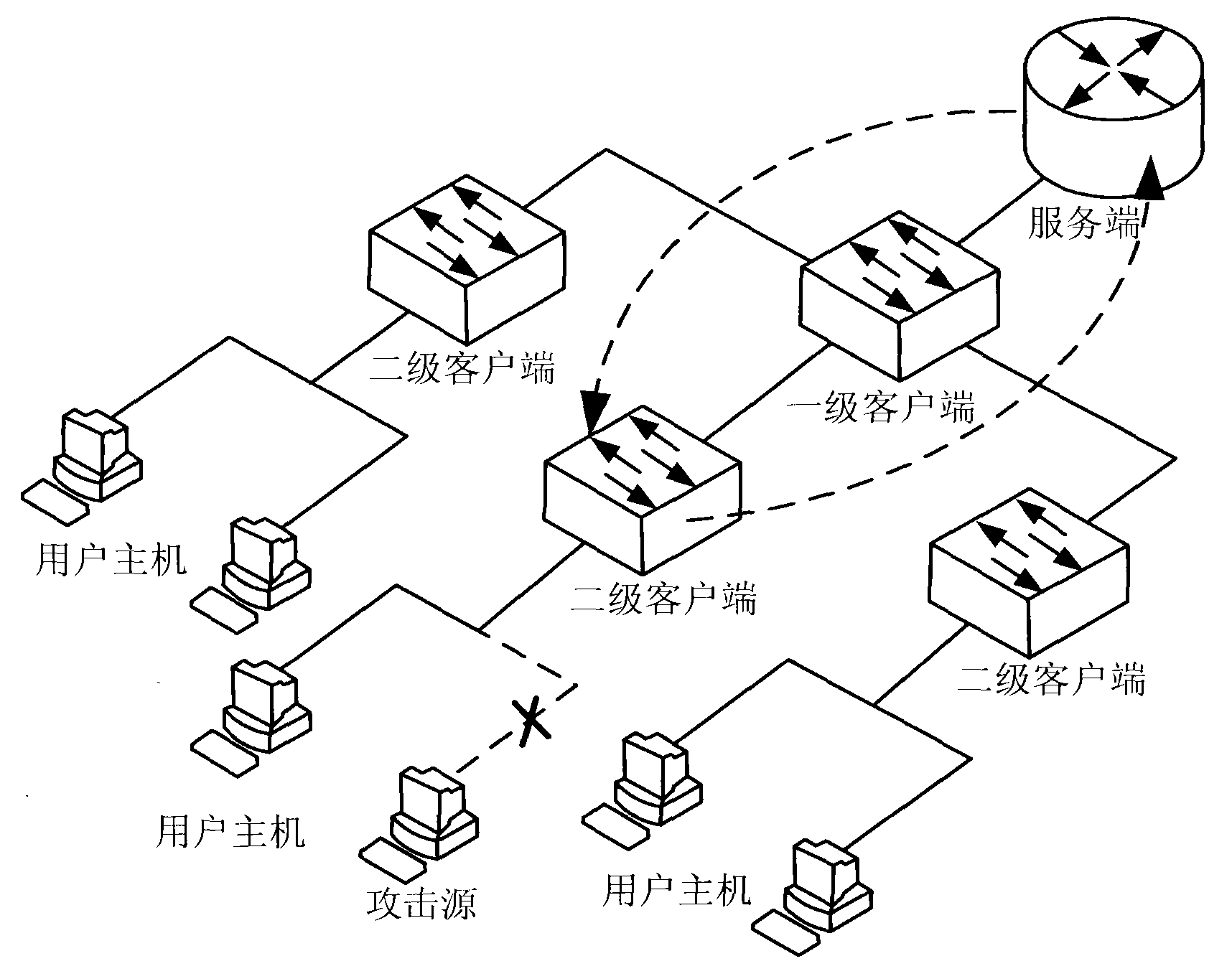
[0038] In this embodiment, the present invention is described by taking the server side including two-level clients connected by ladders as an example.
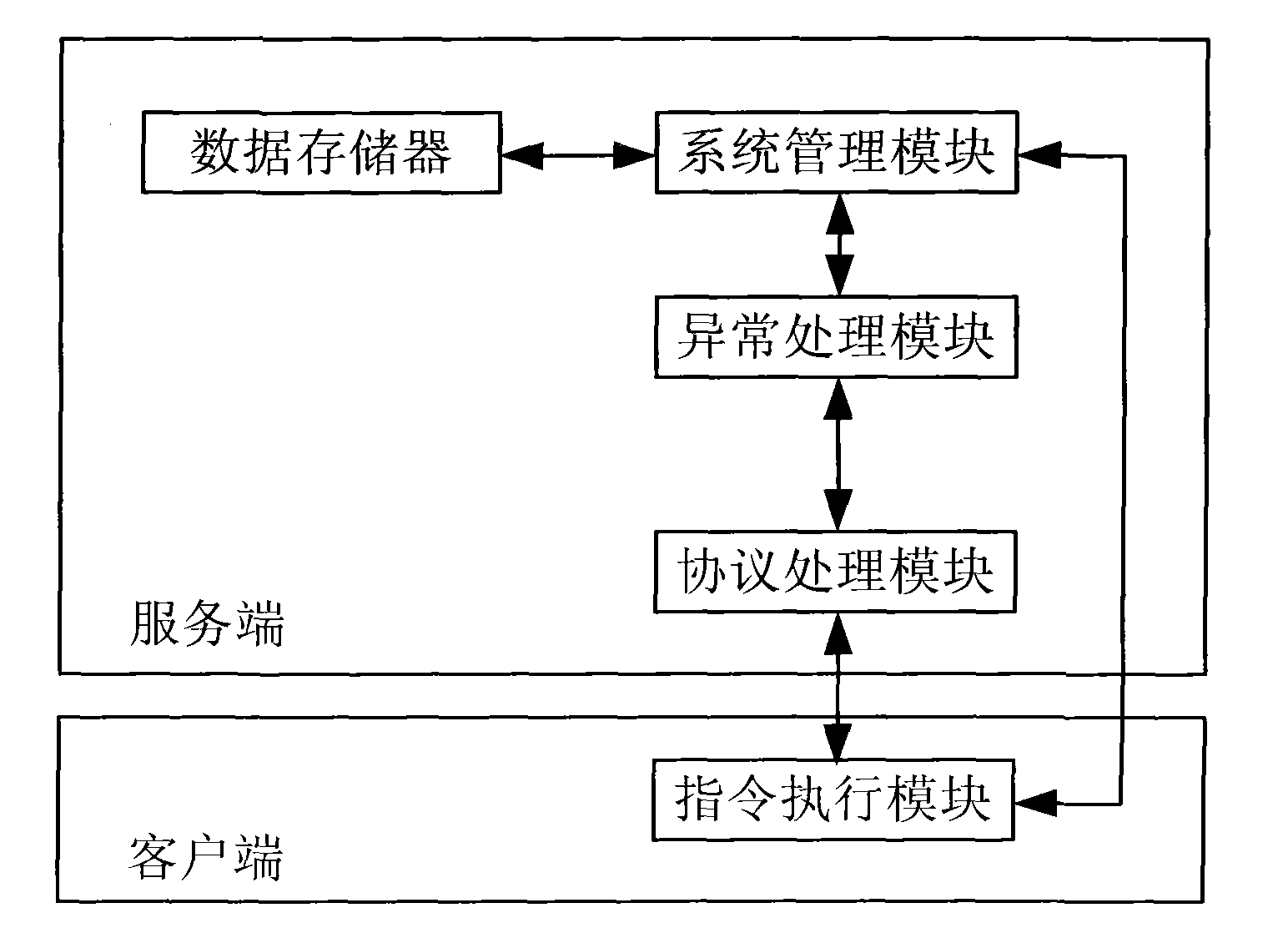
[0039] Such as Figure 1 ~ Figure 3 As shown, the ASN anti-attack security linkage system mainly includes a server and a first-level client connected to the server. The first-level client has three second-level clients, and each second-level client has Set up two user hosts. Wherein, the server is embedded with a system management module, an exception processing module, a protocol processing module and a data storage, and the first-level client and the second-level client are respectively embedded with an instruction execution module. The implementation method of the system is as follows:
[0040] 1. The server implements restrictions on all clients
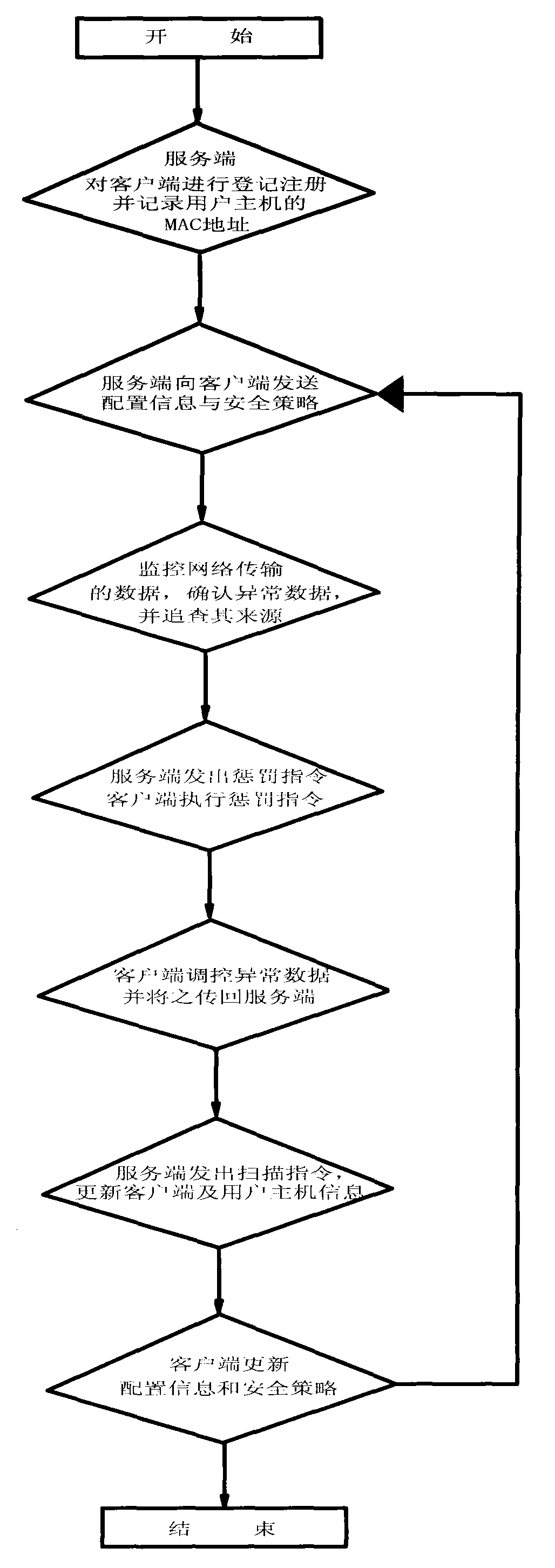
[0041] 1. Client registration: The server periodically sends out scanning instructions from the system management module, and transmits it to clients at all levels according to the ...
Embodiment 2
[0055] Such as figure 1 , Figure 4 As shown, the ASN anti-attack security linkage system mainly includes a server and three first-level clients connected to the server, and each first-level client has two user hosts. Wherein, the server is embedded with a system management module, an exception processing module, a protocol processing module and a data memory, and all first-level clients are embedded with an instruction execution module.
[0056] Regarding the implementation method, the main difference between the two embodiments is that in this embodiment, when the server actively defends and attacks the attack source, the exception handling module directly sends the operation instructions to the first-level client directly connected to the attack source. Data is no longer transmitted through other clients in the middle. After filtering the data transmitted by the attack source, the first-level client also directly transmits data back to the server without passing through other c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com