Patents
Literature
34 results about "Stateful firewall" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
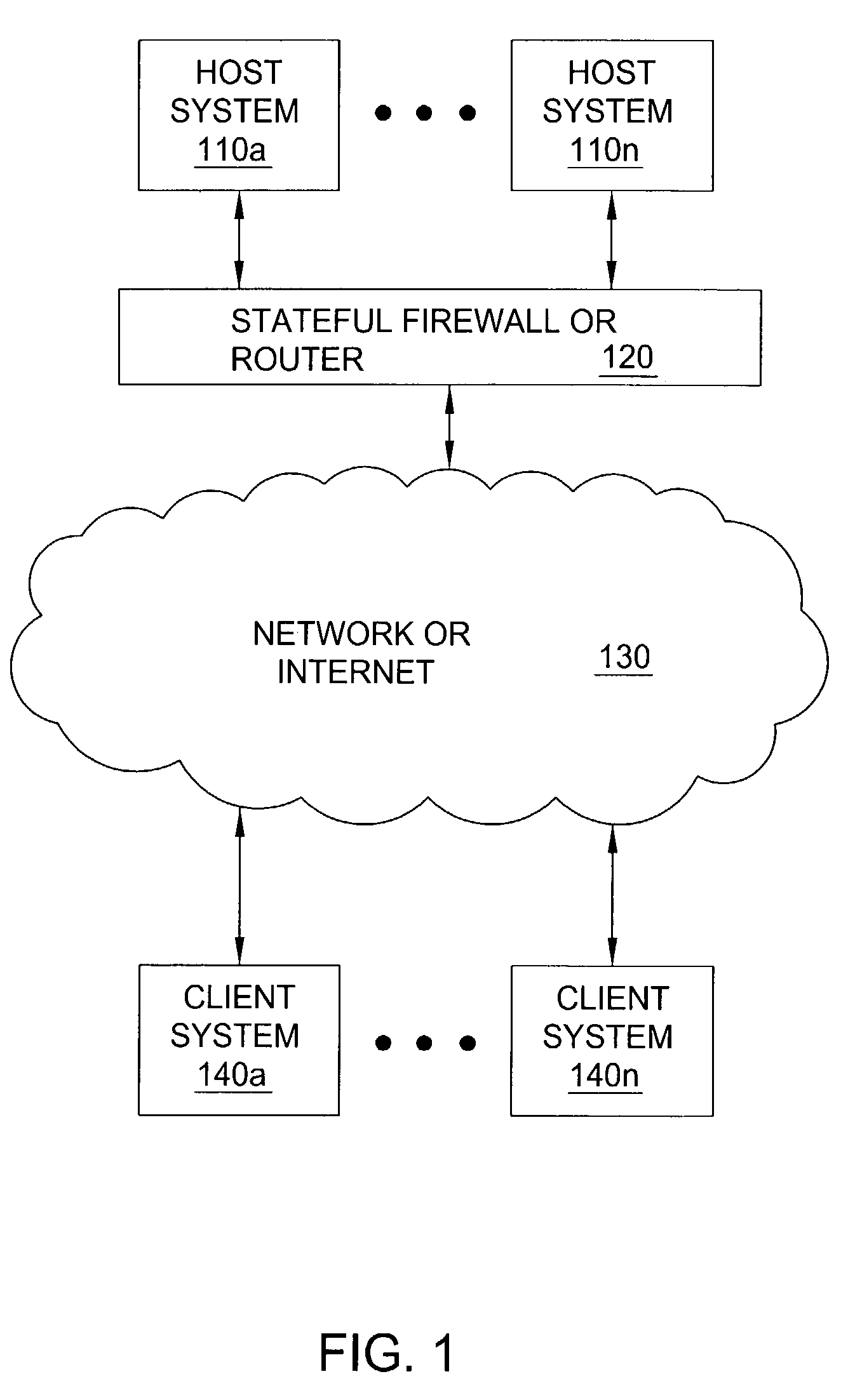
In computing, a stateful firewall is a network firewall that tracks the operating state and characteristics of network connections traversing it. The firewall is configured to distinguish legitimate packets for different types of connections. Only packets matching a known active connection are allowed to pass the firewall.
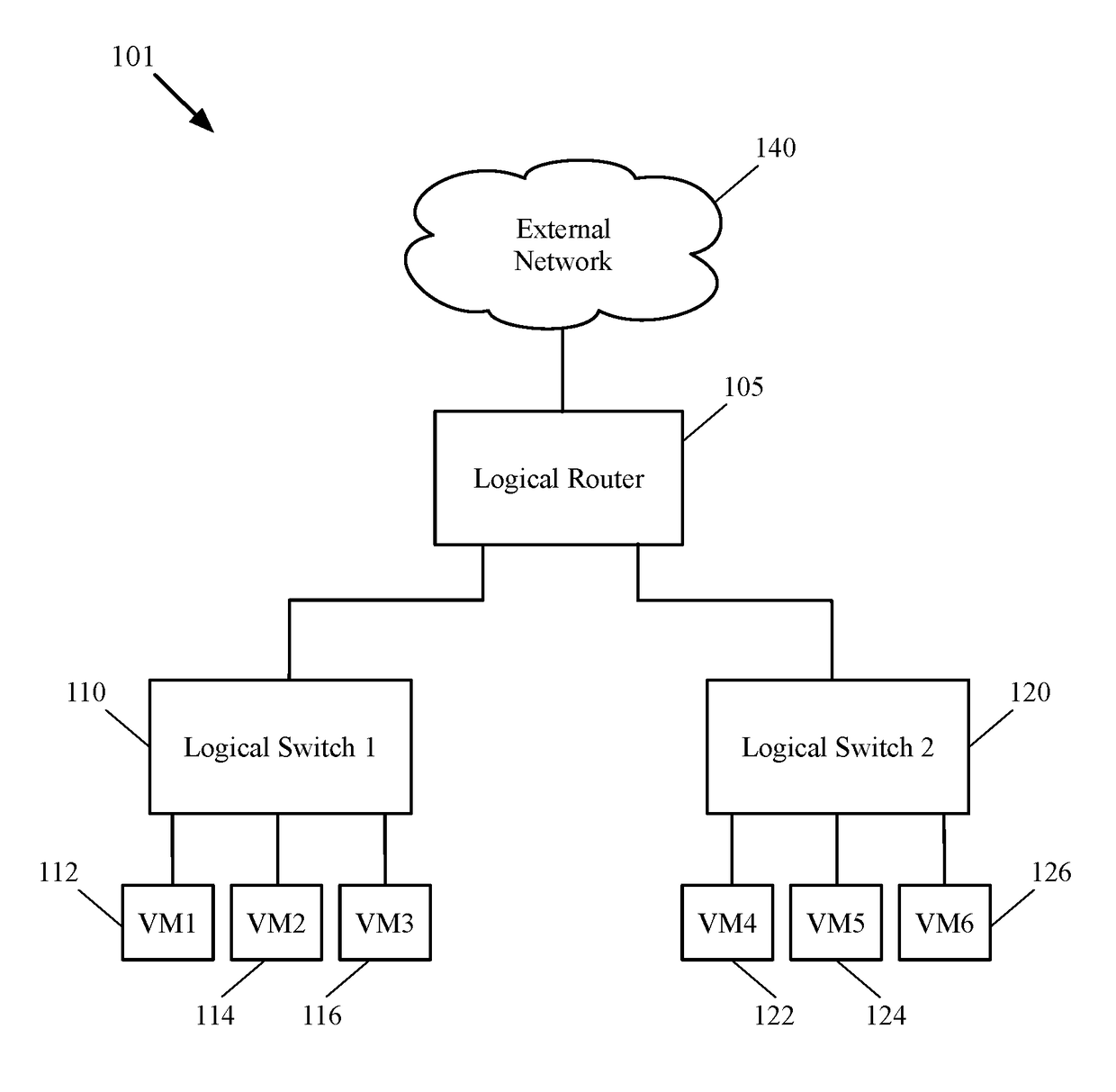
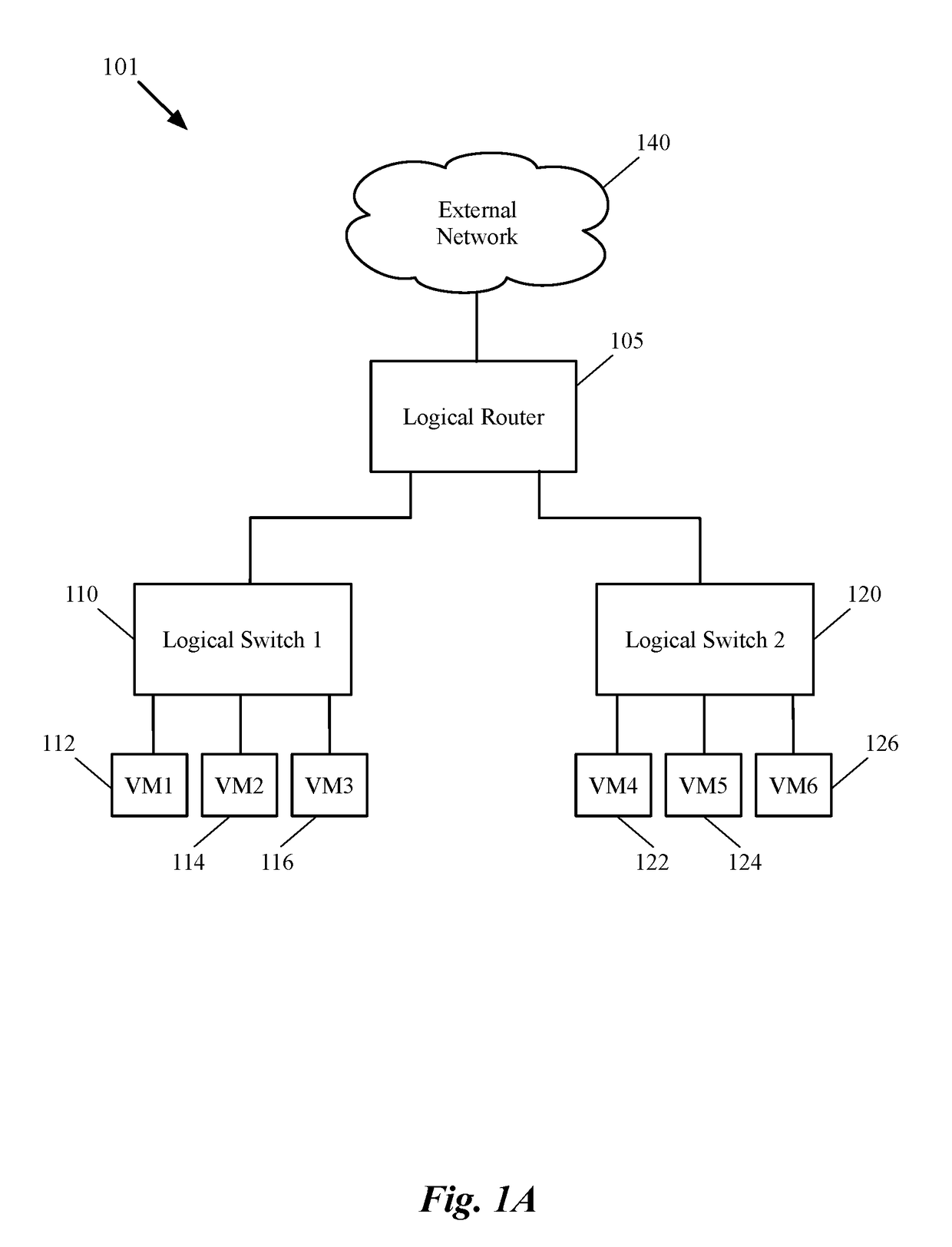
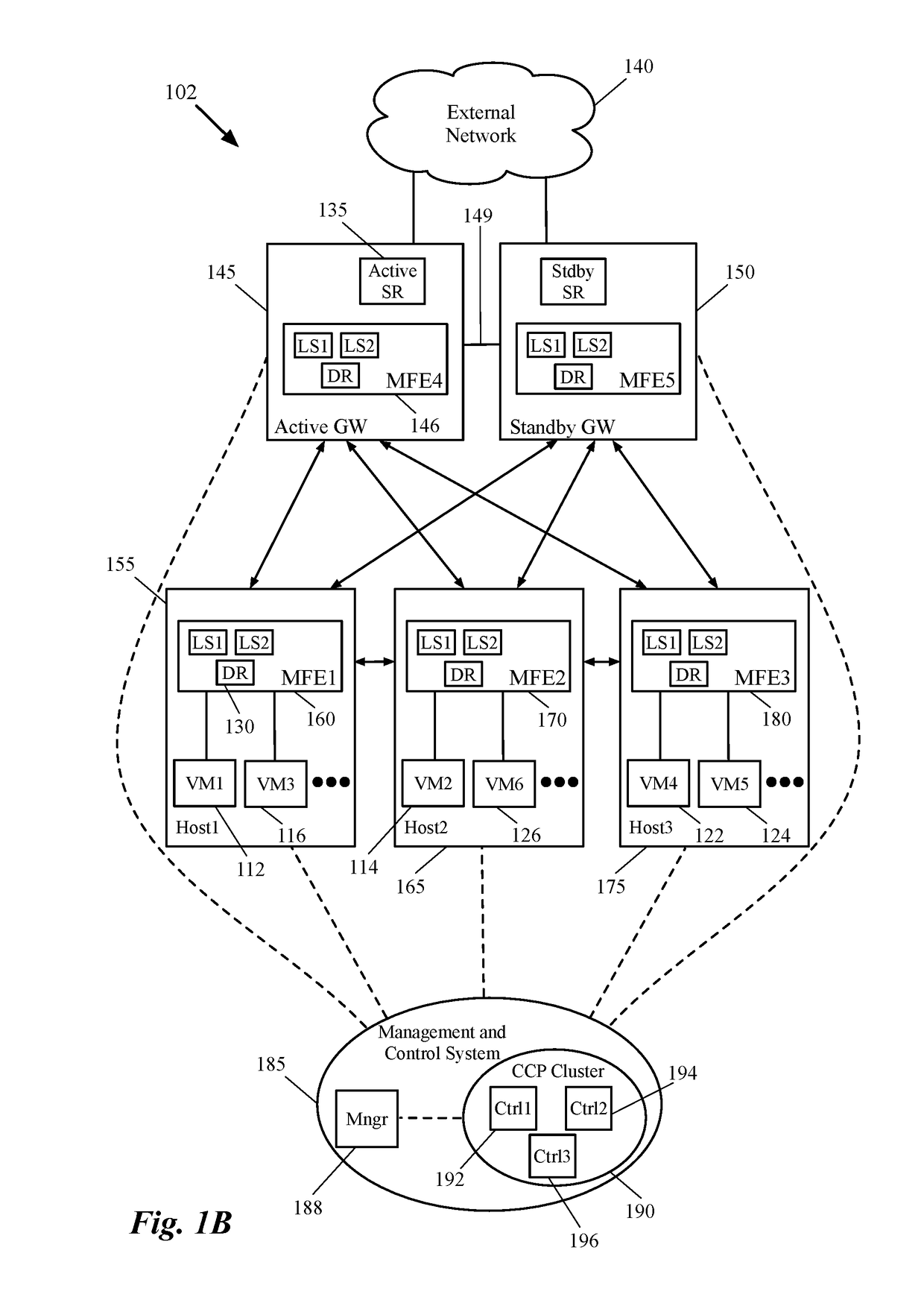
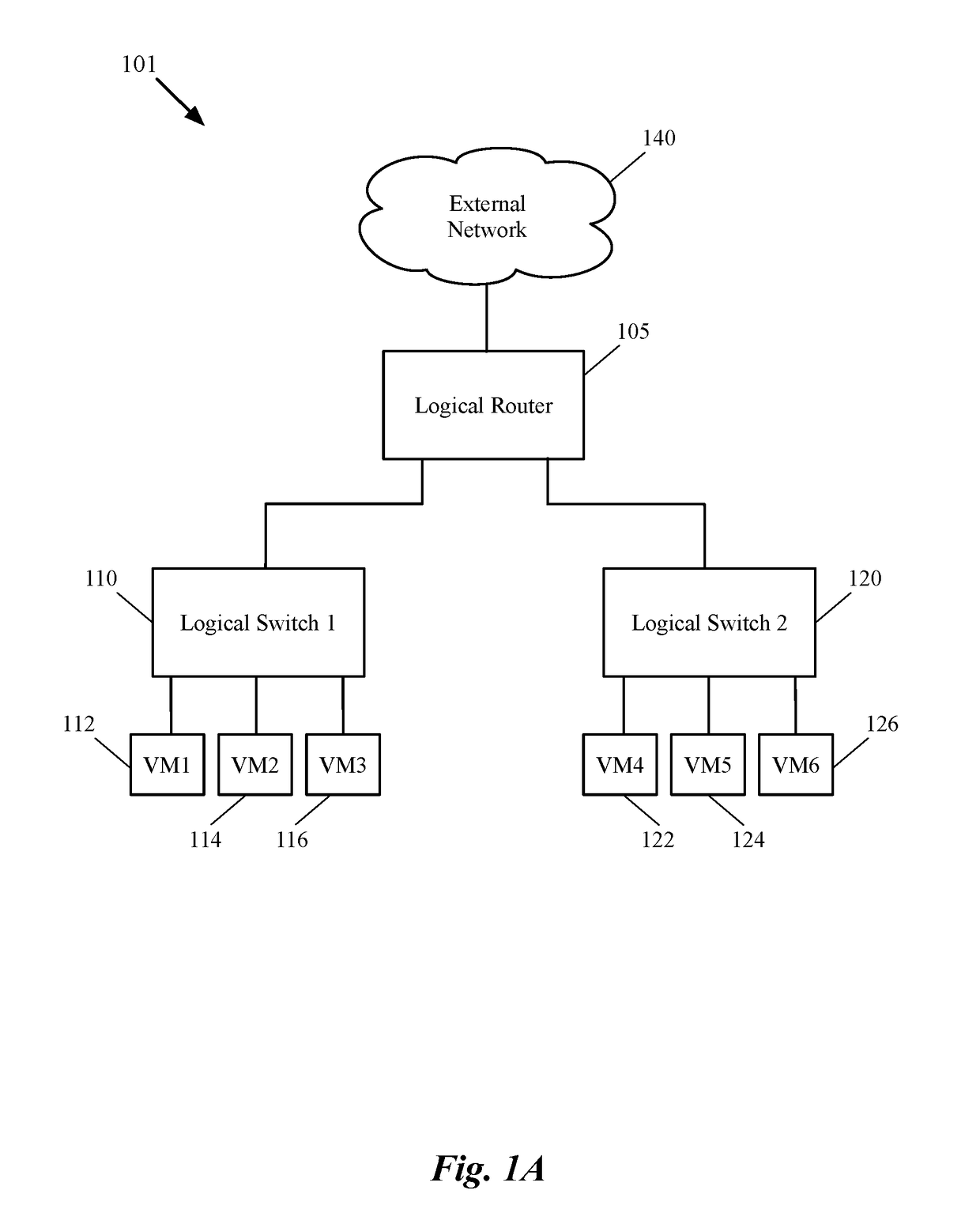
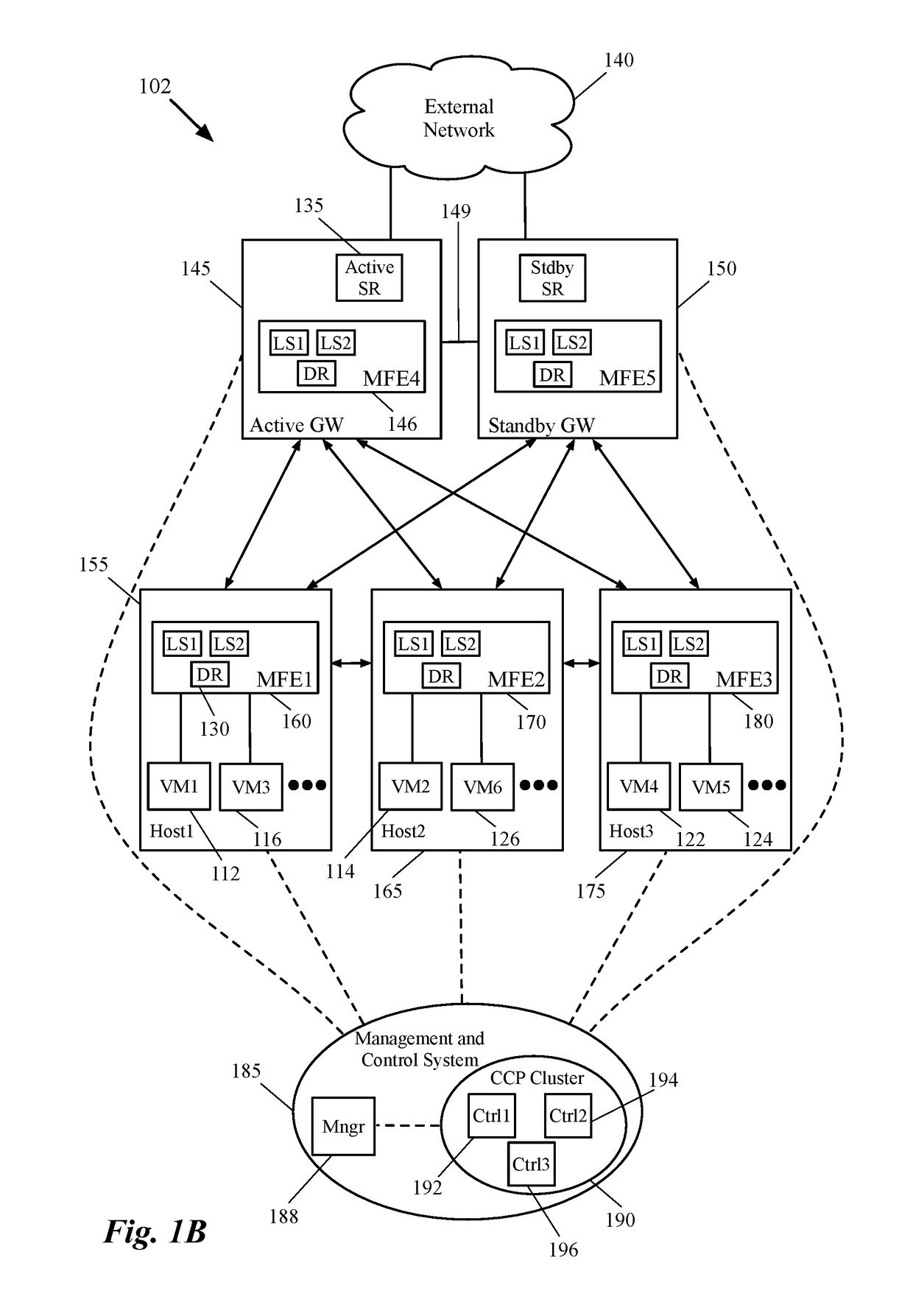
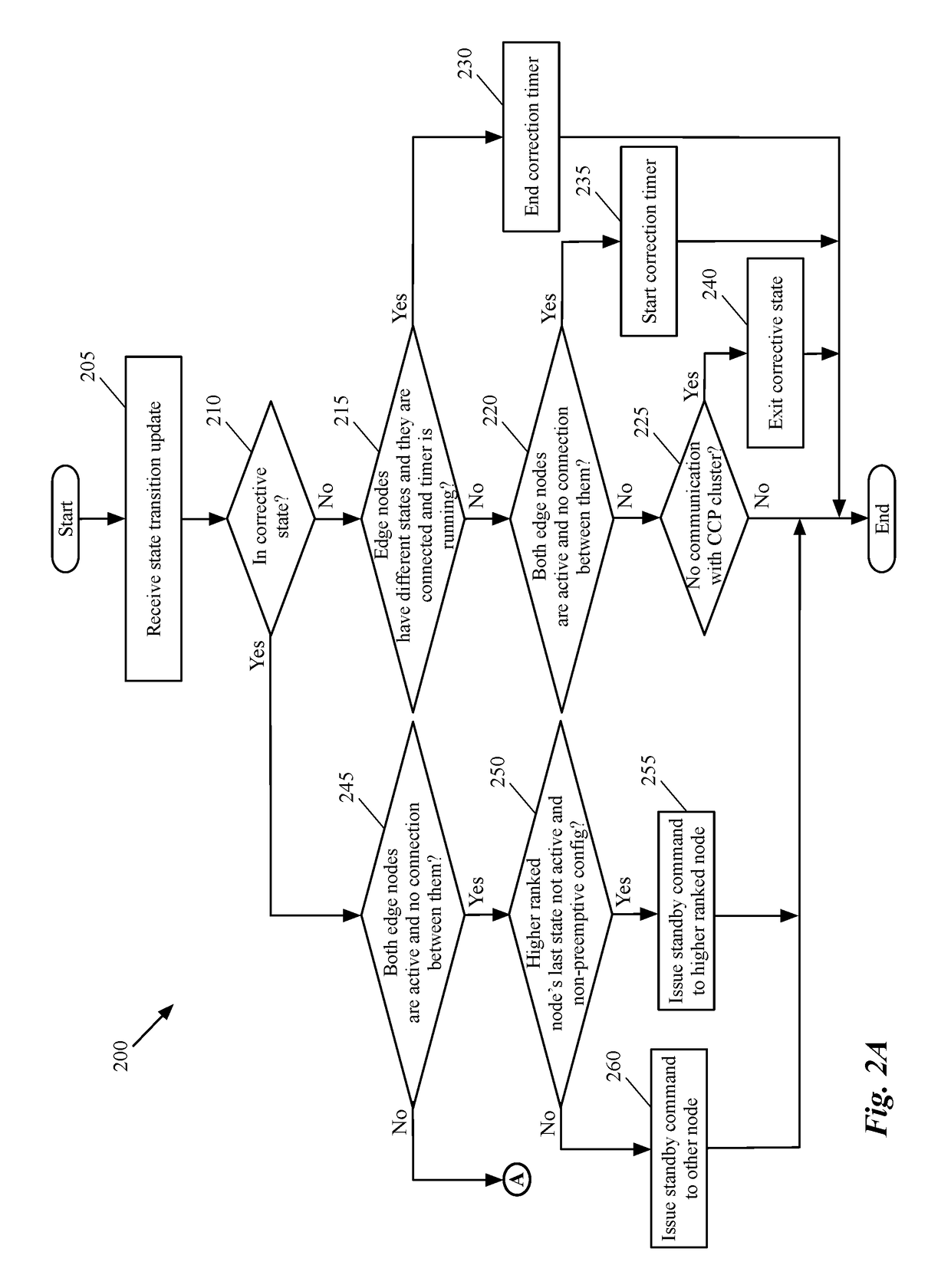
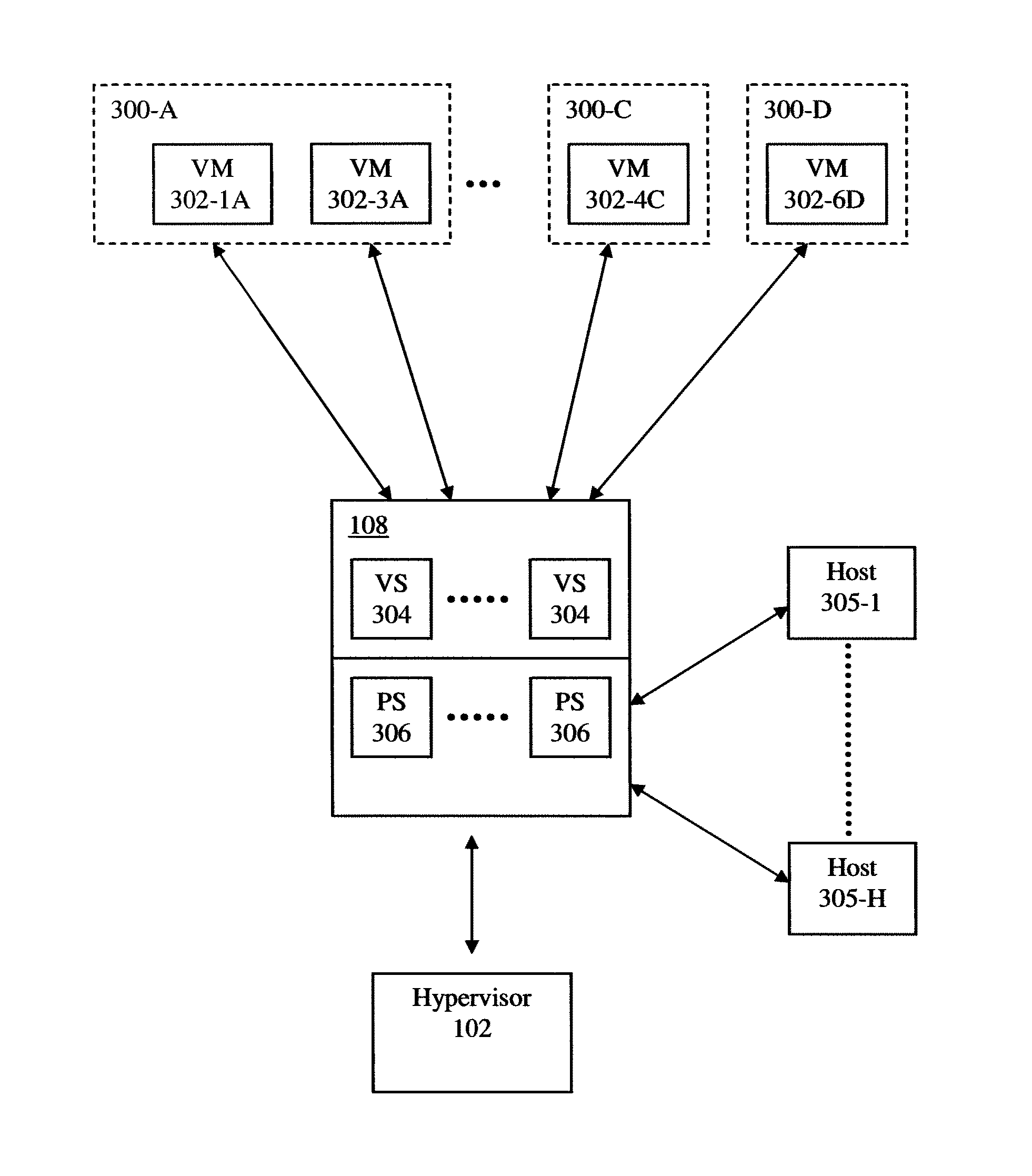
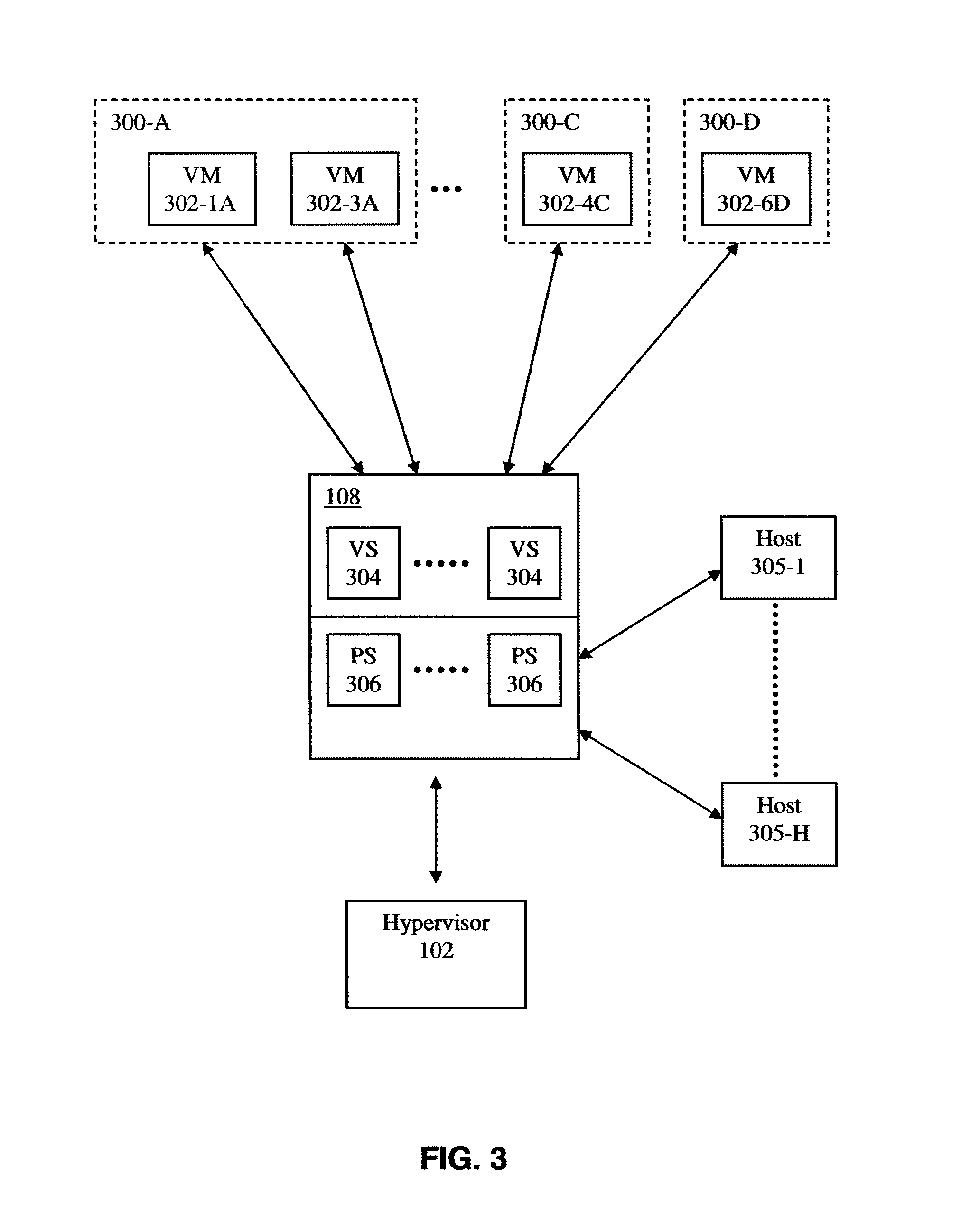
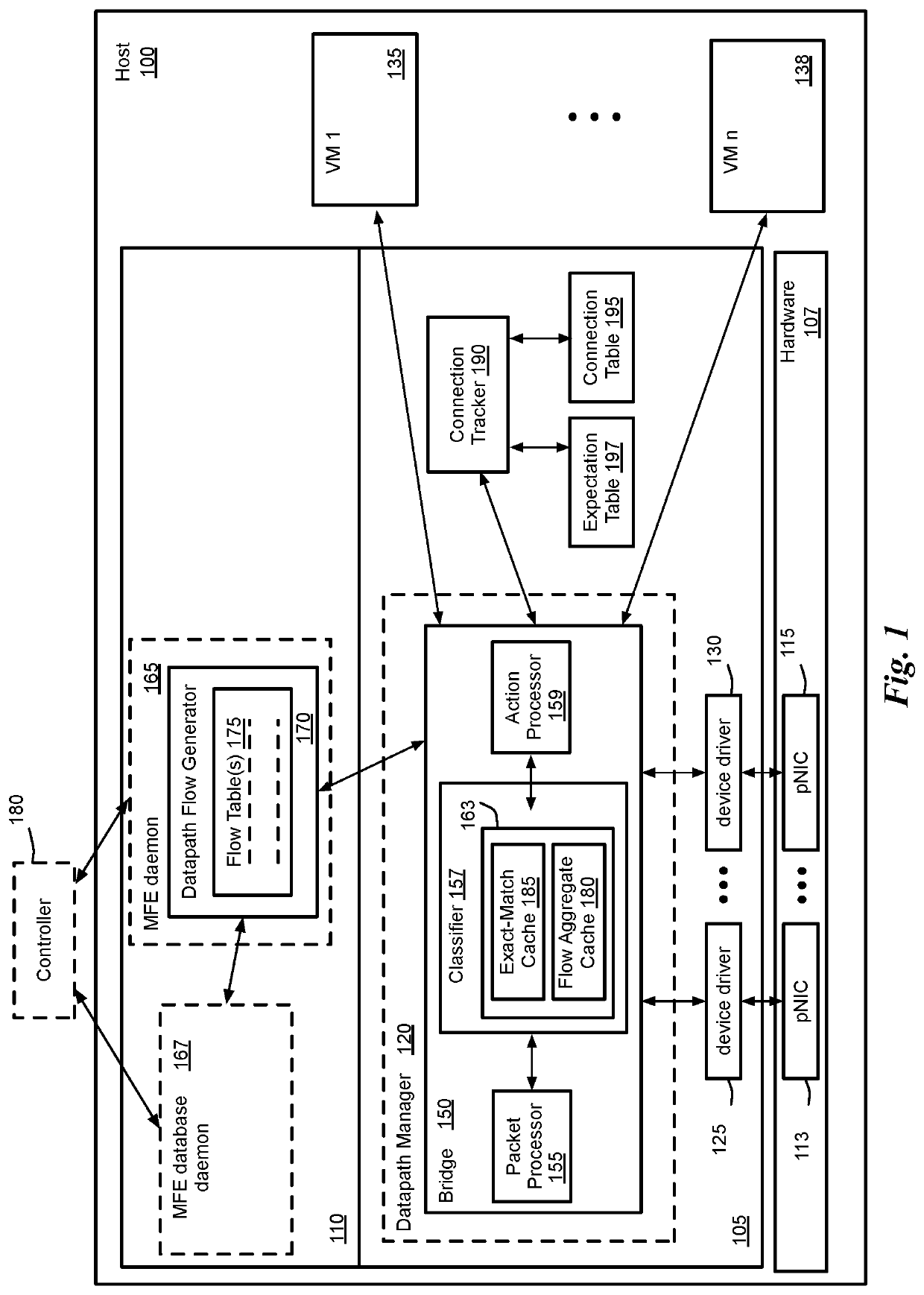
Dynamic recovery from a split-brain failure in edge nodes
ActiveUS20180176073A1Reduce the possibilityIncrease the number ofError detection/correctionSignal allocationActive edgeLoad Shedding
Some embodiments provide a method for employing the management and control system of a network to dynamically recover from a split-brain condition in the edge nodes of the network. The method of some embodiments takes a corrective action to automatically recover from a split-brain failure occurred at a pair of high availability (HA) edge nodes of the network. The HA edge nodes include an active machine and a standby machine. The active edge node actively passes through the network traffic (e.g., north-south traffic for a logical network), while the standby edge node is synchronized and ready to transition to the active state, should a failure occur. Both HA nodes share the same configuration settings and only one is active until a path, link, or system failure occurs. The active edge node also provides stateful services (e.g., stateful firewall, load balancing, etc.) to the data compute nodes of the network.
Owner:NICIRA
Dynamic recovery from a split-brain failure in edge nodes
ActiveUS10237123B2Reduce the possibilityIncrease the number ofSignal allocationData switching networksNODALTraffic capacity
Some embodiments provide a method for employing the management and control system of a network to dynamically recover from a split-brain condition in the edge nodes of the network. The method of some embodiments takes a corrective action to automatically recover from a split-brain failure occurred at a pair of high availability (HA) edge nodes of the network. The HA edge nodes include an active machine and a standby machine. The active edge node actively passes through the network traffic (e.g., north-south traffic for a logical network), while the standby edge node is synchronized and ready to transition to the active state, should a failure occur. Both HA nodes share the same configuration settings and only one is active until a path, link, or system failure occurs. The active edge node also provides stateful services (e.g., stateful firewall, load balancing, etc.) to the data compute nodes of the network.
Owner:NICIRA
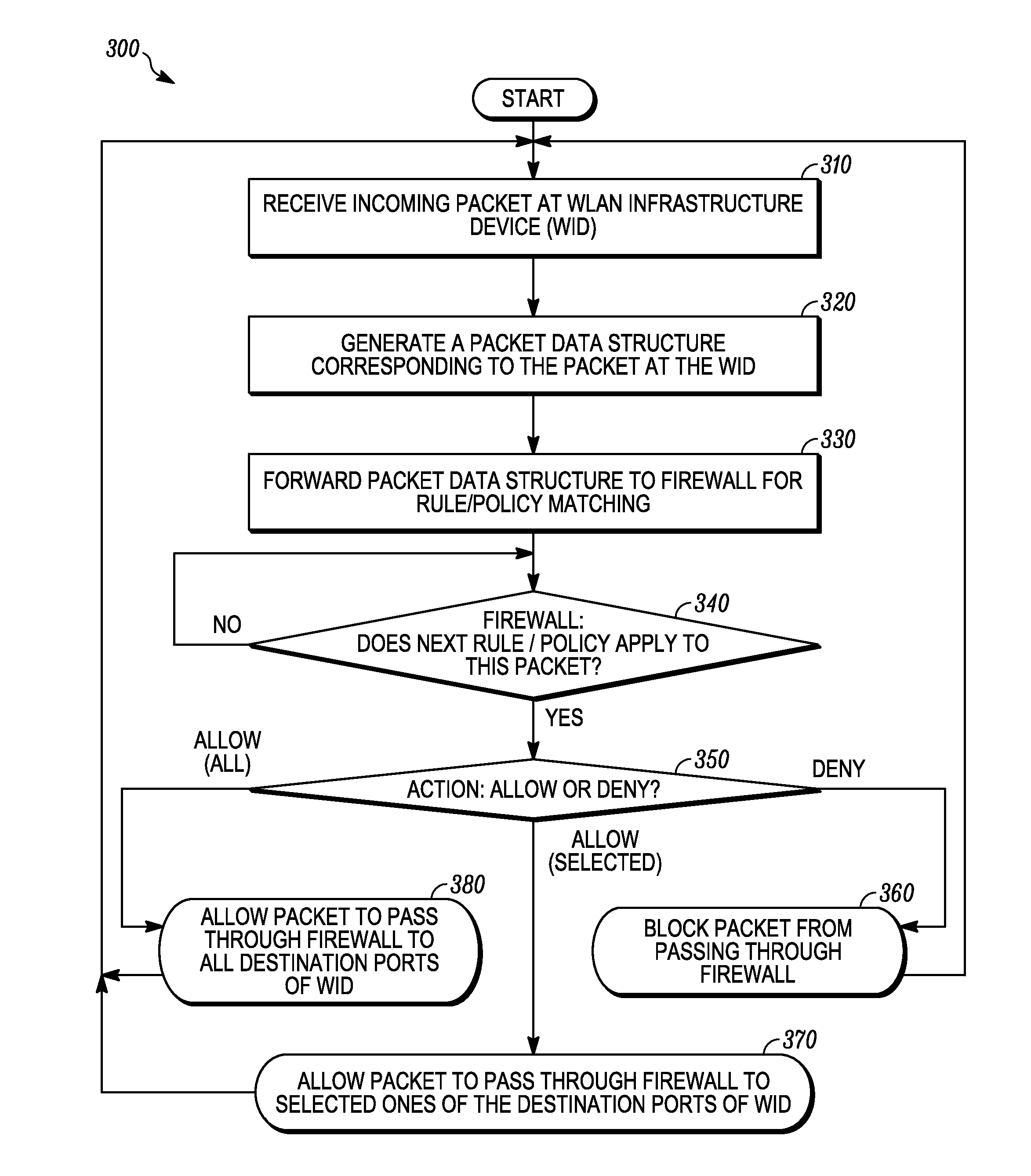
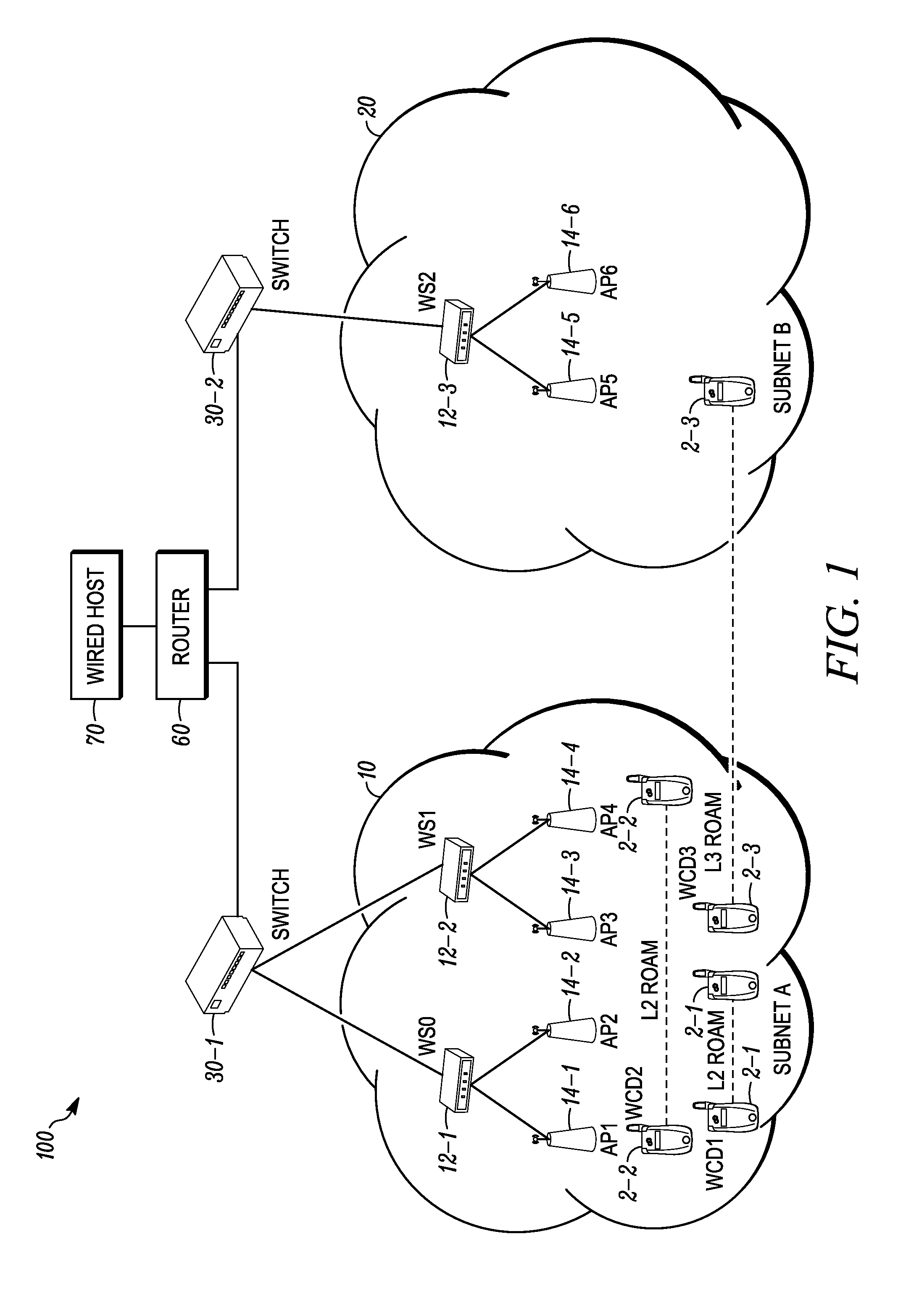
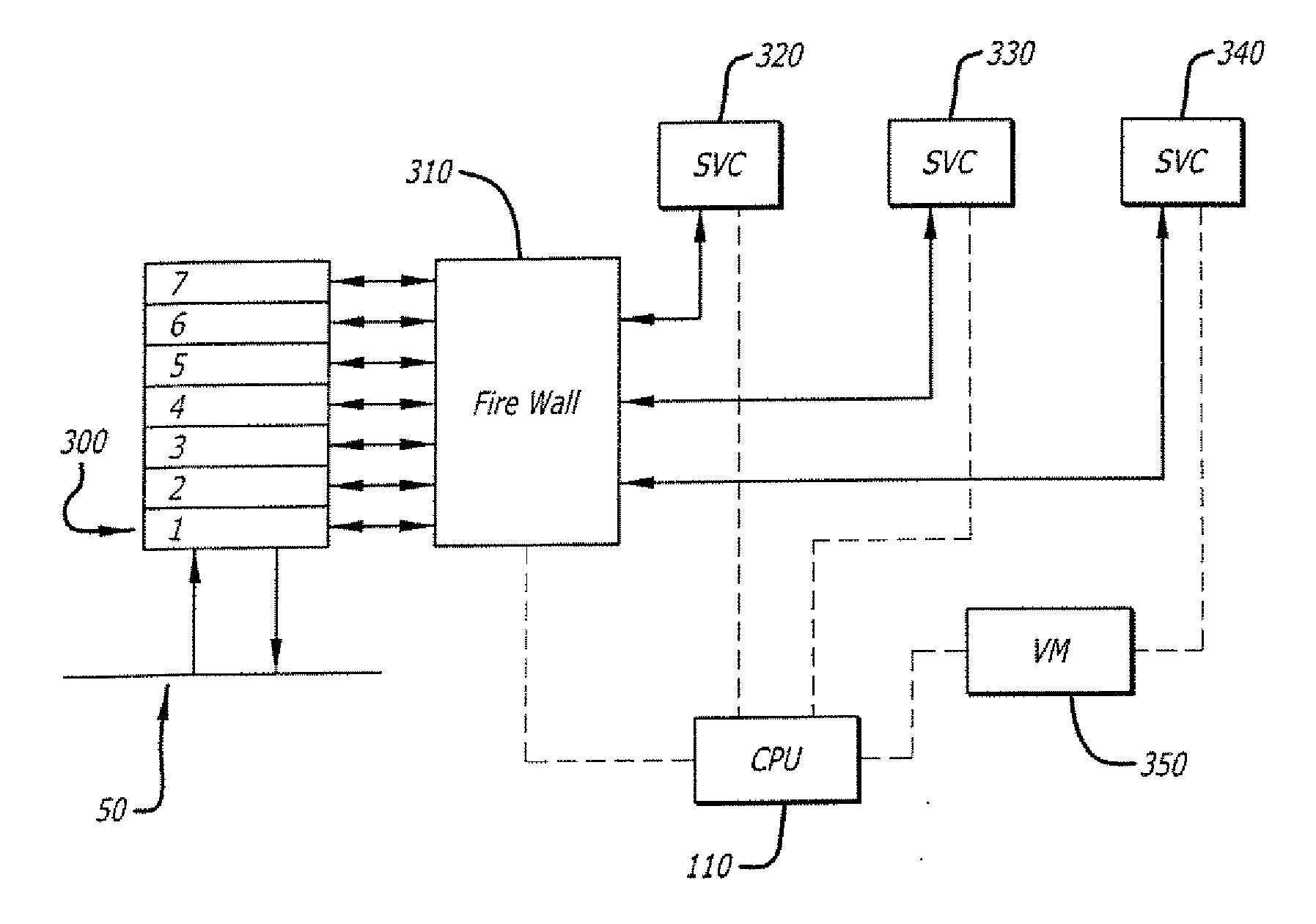
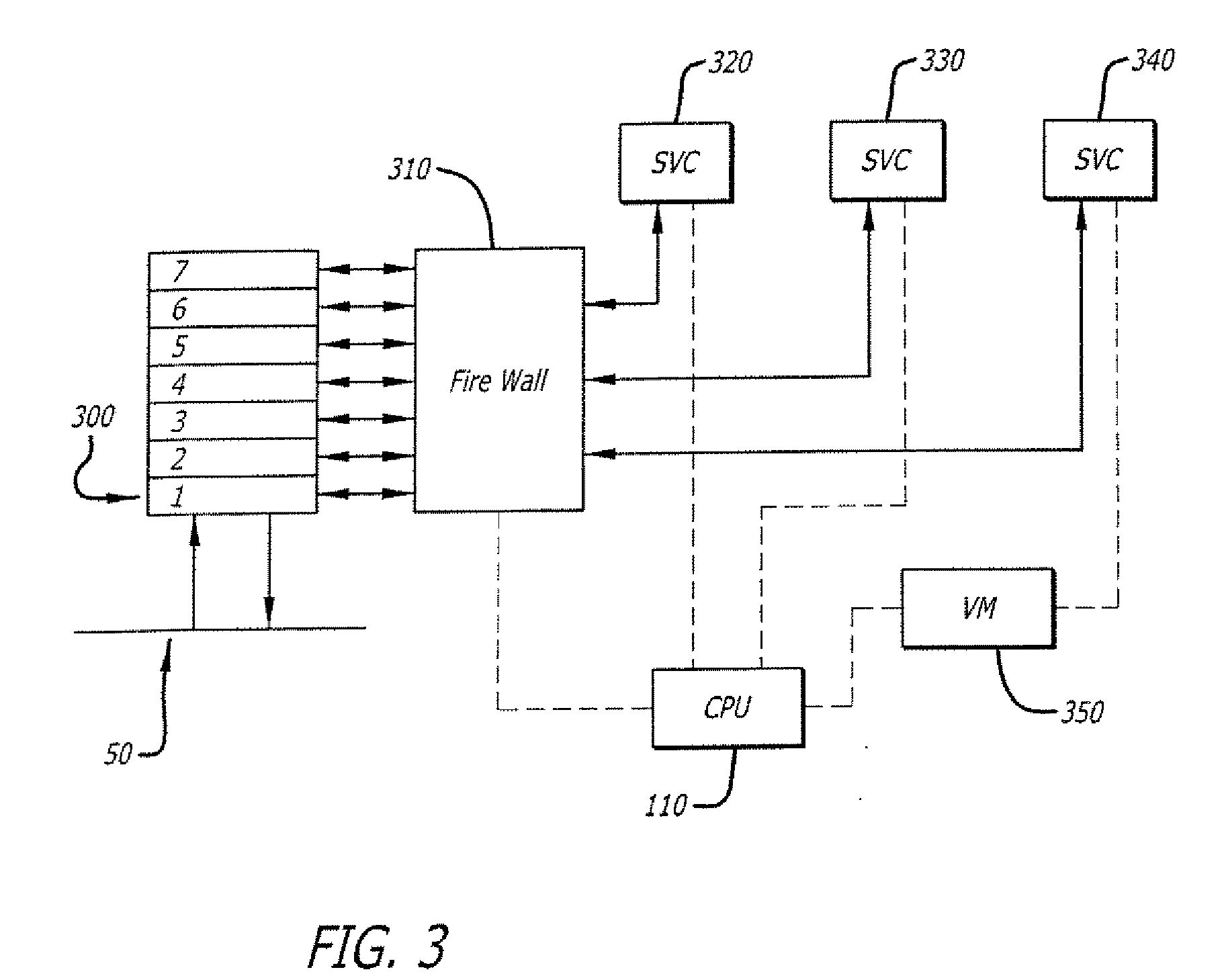
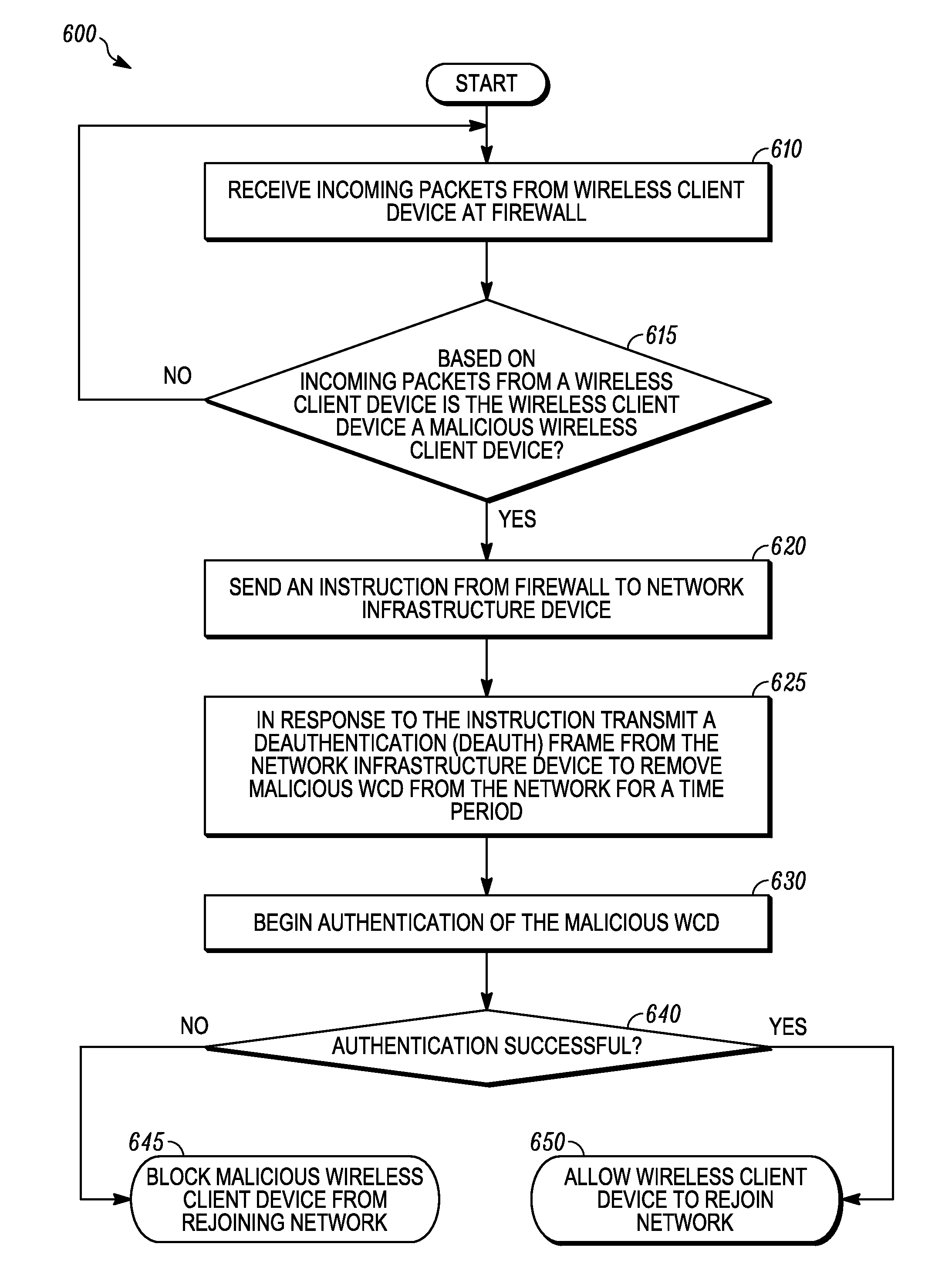
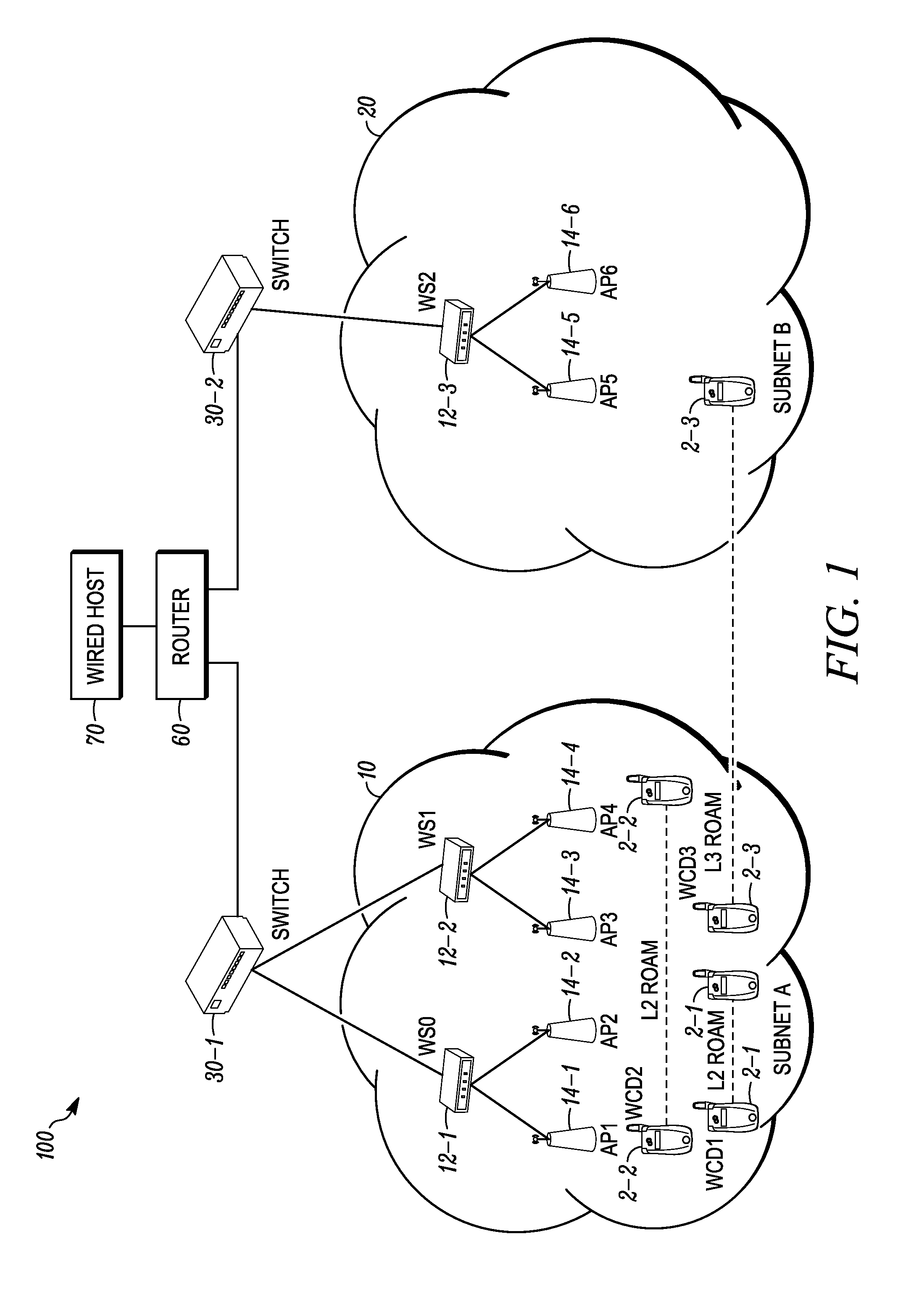
Wireless local area network infrastructure devices having improved firewall features
ActiveUS20110162060A1Multiple digital computer combinationsProgram controlTraffic capacityComputer science
Methods and systems are provided for improving a firewall implemented at a WLAN infrastructure device (WID). The WID includes a stateful firewall that implements firewall rules based on an ESSID of the WID to specify whether traffic is allowed to or from the ESSID. For example, in one implementation of such a firewall rule, packets that are required to be sent out on all wired ports can be blocked from being flooded out on WLANs (e.g., the packet is allowed to pass only to the wired ports). A method and system are provided for preventing a malicious wireless client device (WCD) that is transmitting undesirable traffic from using RF resources by deauthenticating the malicious WCD to remove it from the WLAN and blacklisting it to prevent it from rejoining the WLAN for a time period. Method and systems are also provided for either “on-demand” and / or predicatively communicating state information regarding an existing firewall session.
Owner:EXTREME NETWORKS INC
Method and apparatus for deflecting flooding attacks
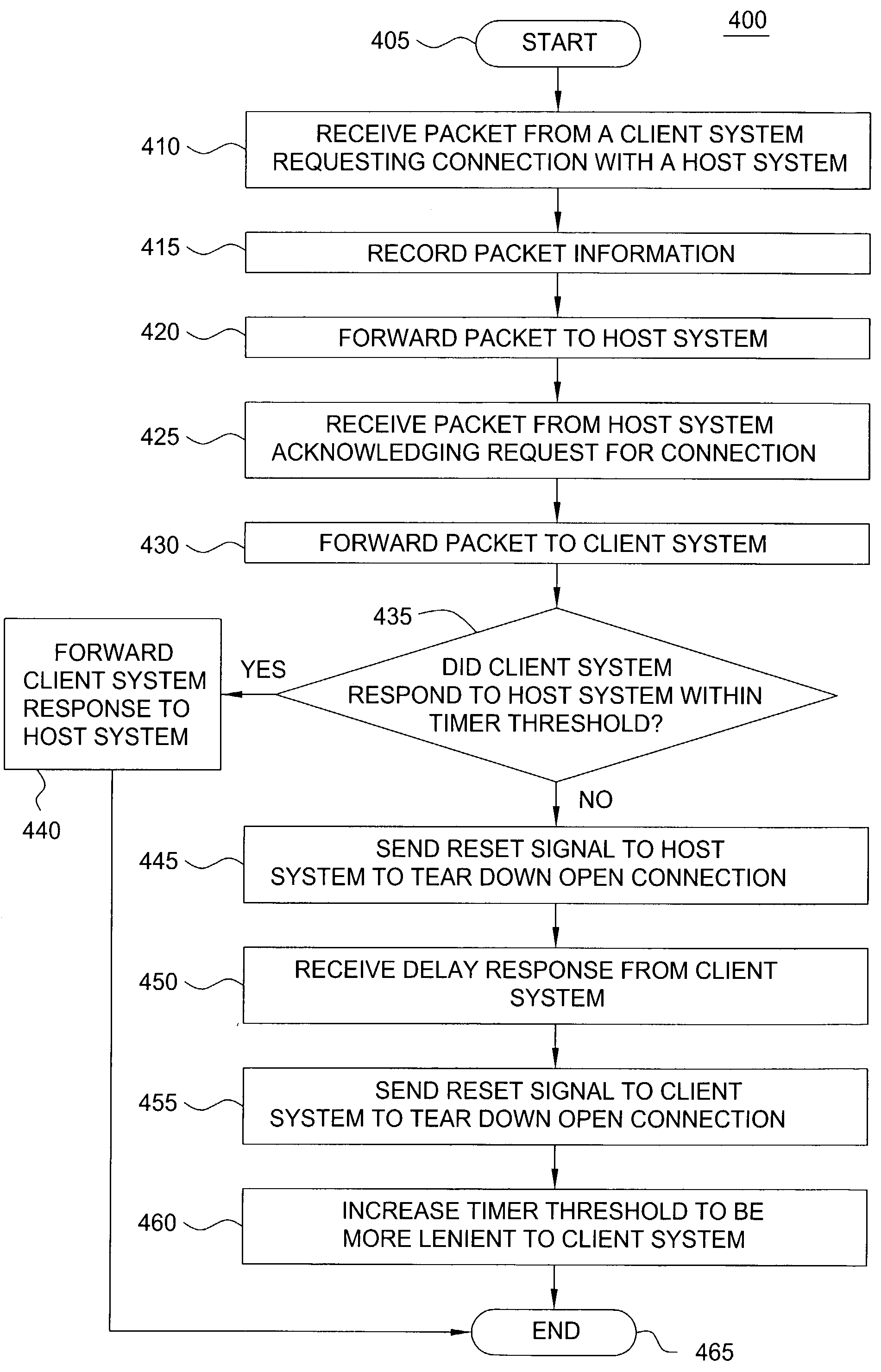
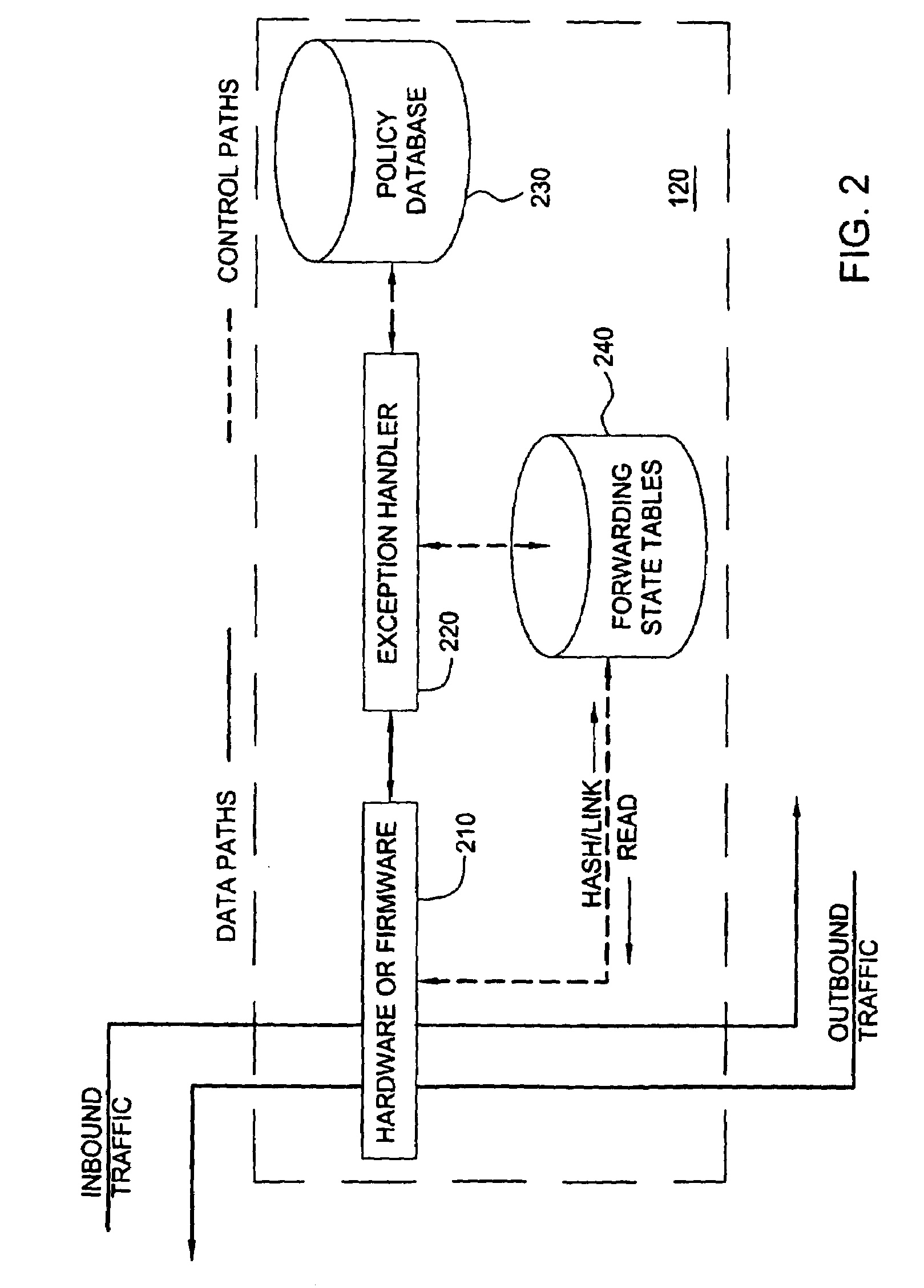
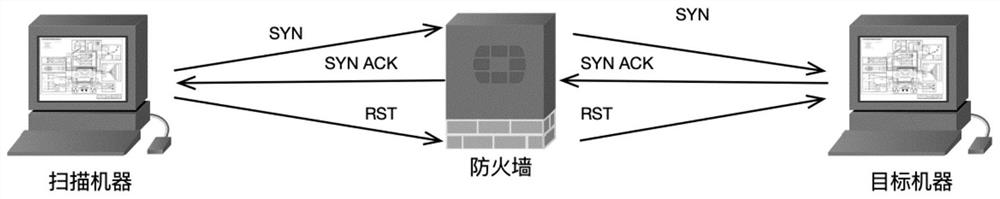
Method and apparatus for deflecting connection flooding attacks. Specifically, the stateful firewall allows all connection attempts to flow into the destination host, but monitors the connection attempts to ensure that only legitimate connections are allowed. If the firewall detects that a connection is half-open for longer than a certain timer threshold, it will instruct the destination host to tear down the half-open connection, thereby freeing up resources in the destination host for other connection attempts. The timer threshold can be dynamically adjusted if a connection flooding attack is detected.
Owner:NVIDIA CORP
Method and apparatus for implementing and managing distributed virtual switches in several hosts and physical forwarding elements
ActiveUS8966035B2Readily, securely, and efficiently communicate with each otherDigital computer detailsData switching by path configurationData centerVirtual switch
In general, the present invention relates to a virtual platform in which one or more distributed virtual switches can be created for use in virtual networking. According to some aspects, the distributed virtual switch according to the invention provides the ability for virtual and physical machines to more readily, securely, and efficiently communicate with each other even if they are not located on the same physical host and / or in the same subnet or VLAN. According other aspects, the distributed virtual switches of the invention can support integration with traditional IP networks and support sophisticated IP technologies including NAT functionality, stateful firewalling, and notifying the IP network of workload migration. According to further aspects, the virtual platform of the invention creates one or more distributed virtual switches which may be allocated to a tenant, application, or other entity requiring isolation and / or independent configuration state. According to still further aspects, the virtual platform of the invention manages and / or uses VLAN or tunnels (e.g, GRE) to create a distributed virtual switch for a network while working with existing switches and routers in the network. The present invention finds utility in both enterprise networks, datacenters and other facilities.
Owner:NICIRA
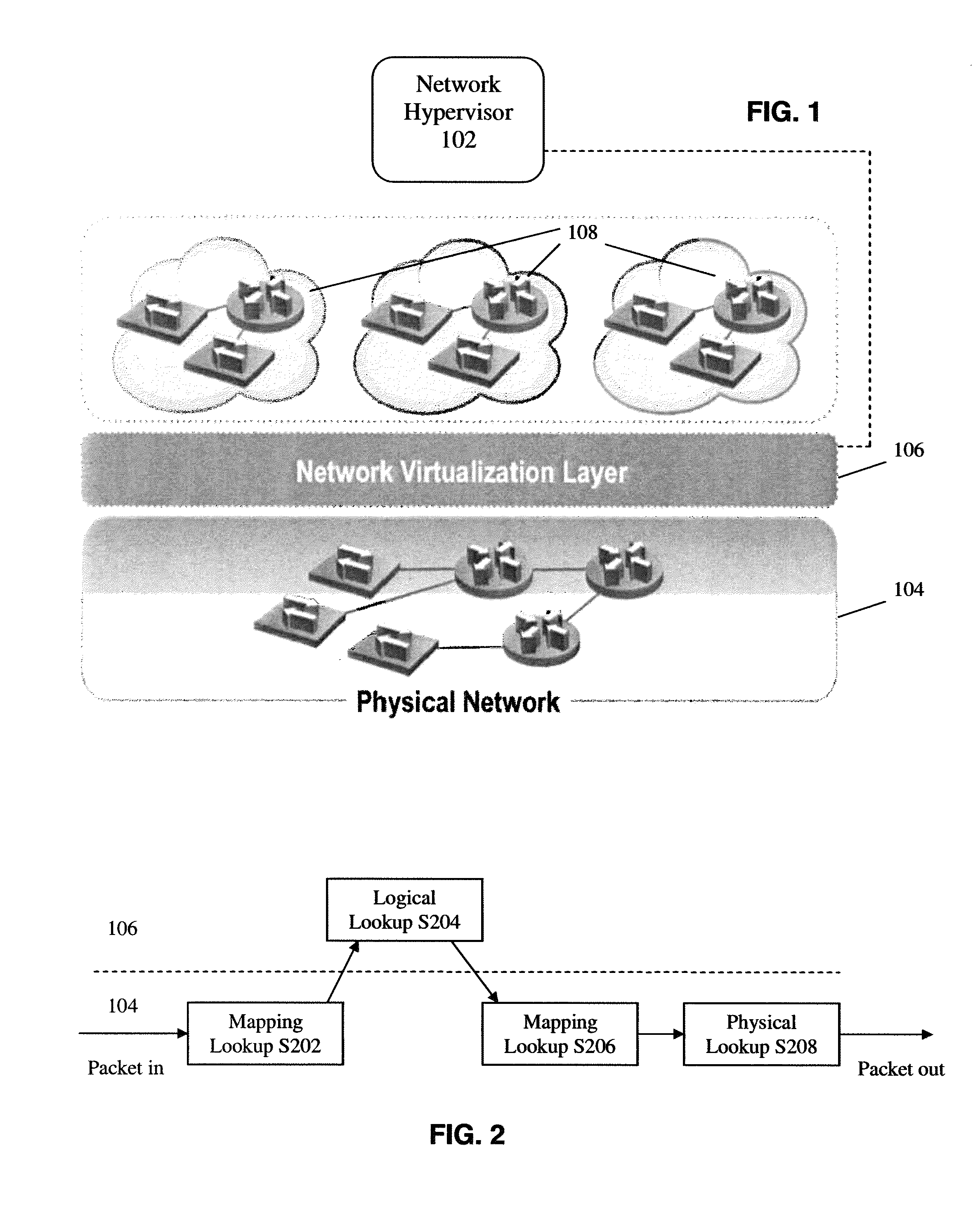
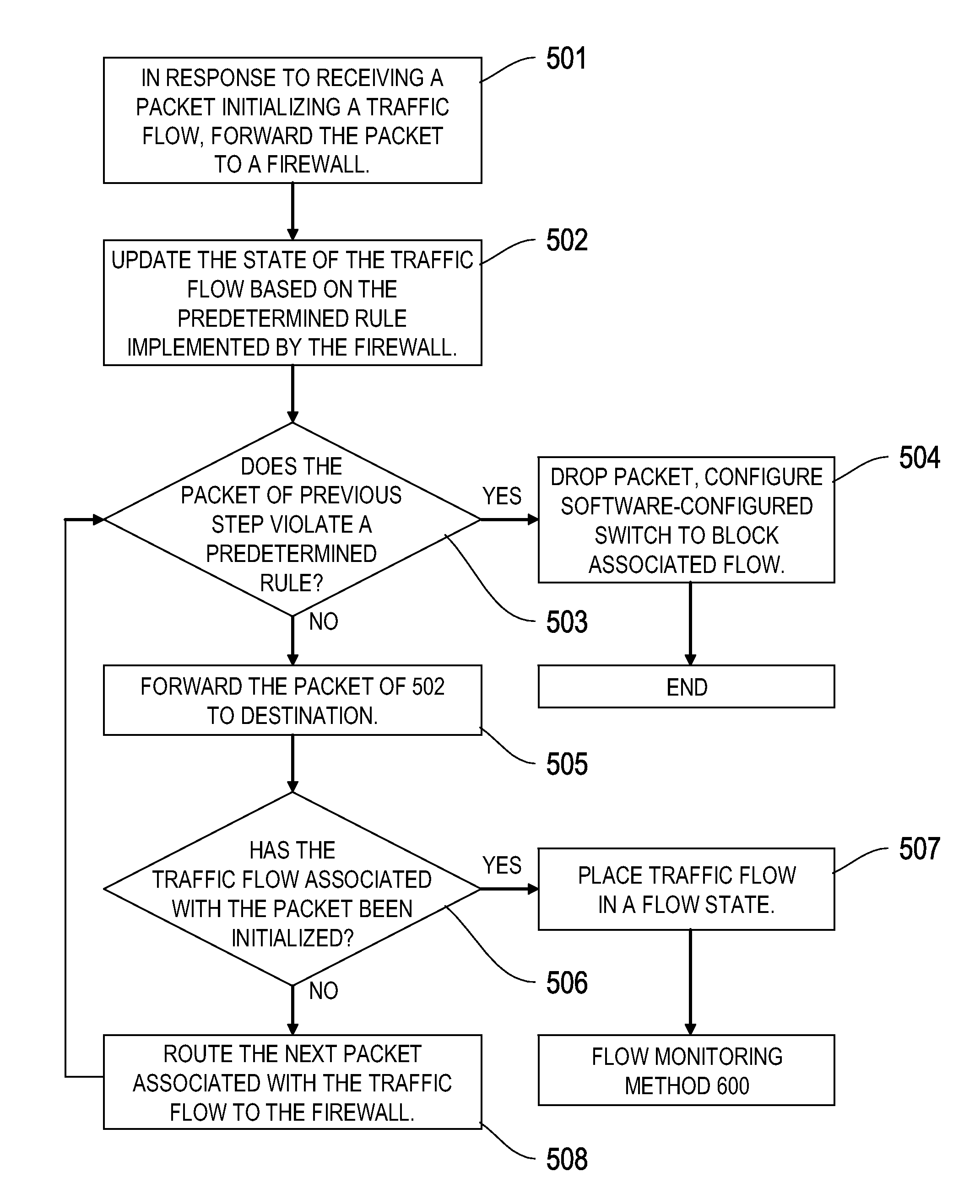
Scalable stateful firewall design in openflow based networks
ActiveUS8789135B1Reduce network trafficError preventionFrequency-division multiplex detailsTraffic capacityNetwork activity
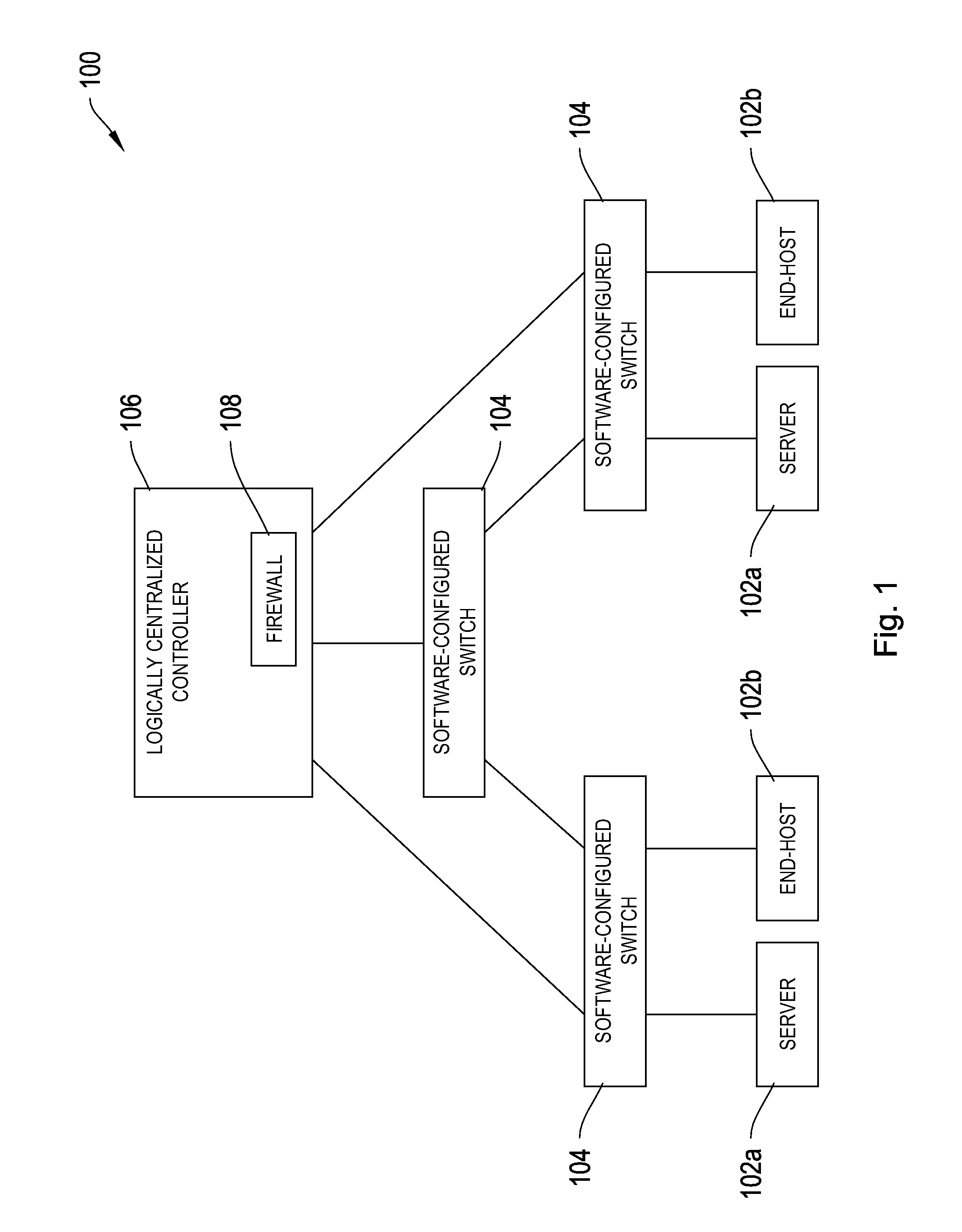
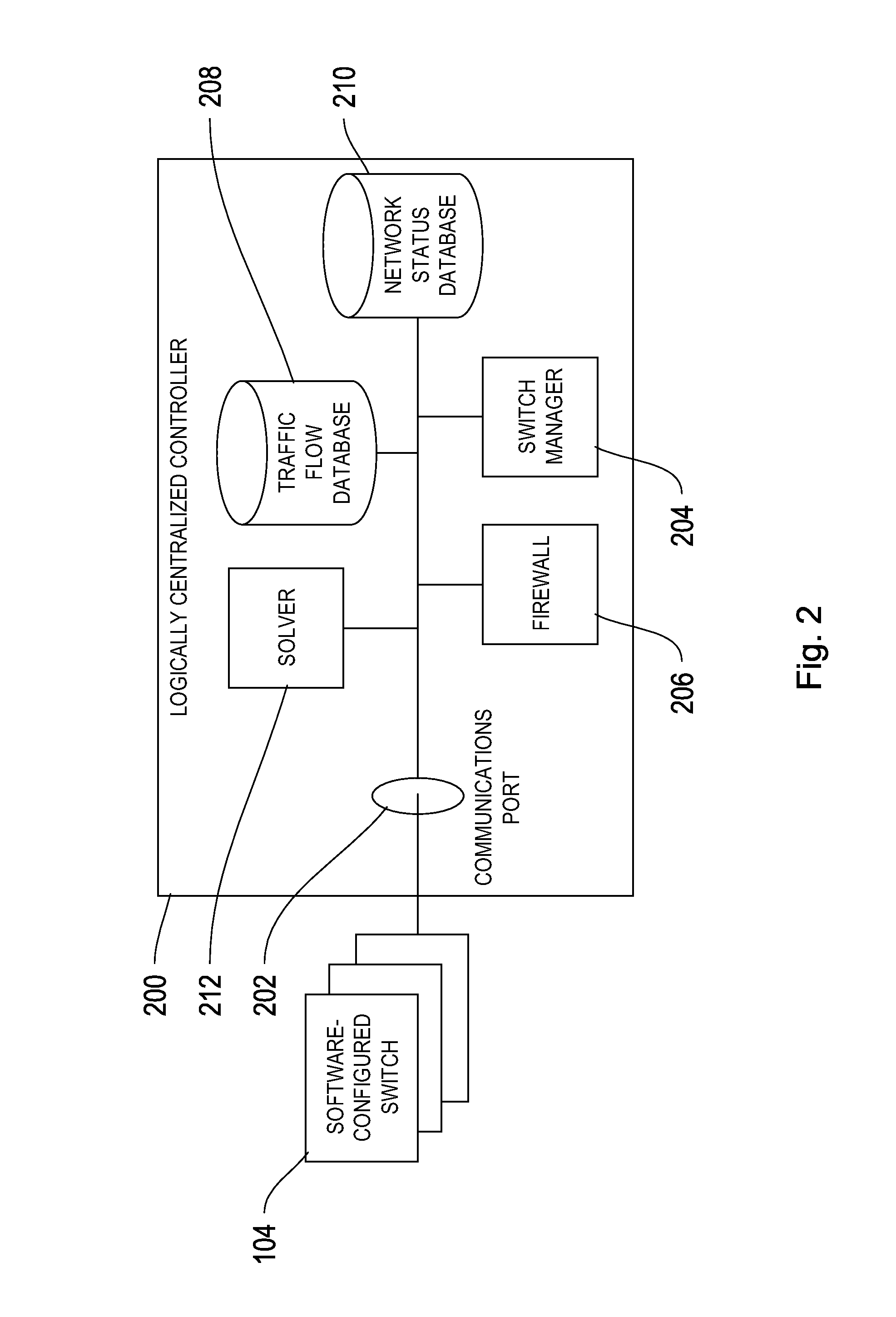
A logically centralized controller provides a stateful firewall service provider on a network. The logically centralized controller routes a plurality of packets associated with a traffic flow to a firewall, and blocks, allows, or further monitors the traffic flow based on the inspection of the plurality of packets by the firewall. The logically centralized controller thereby prevents unauthorized network activity while allowing network traffic to bypass the bottleneck created by the firewall.
Owner:GOOGLE LLC
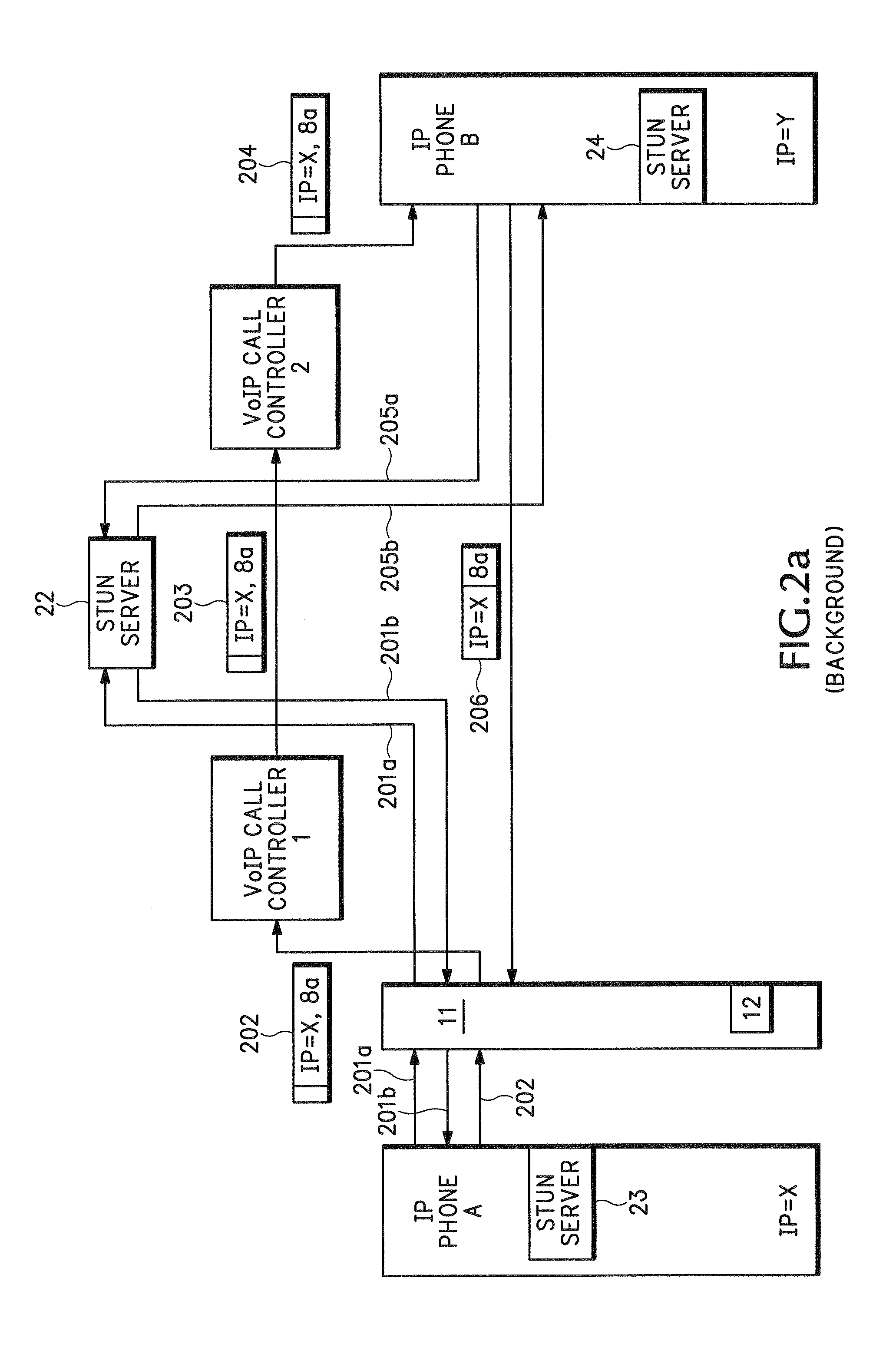
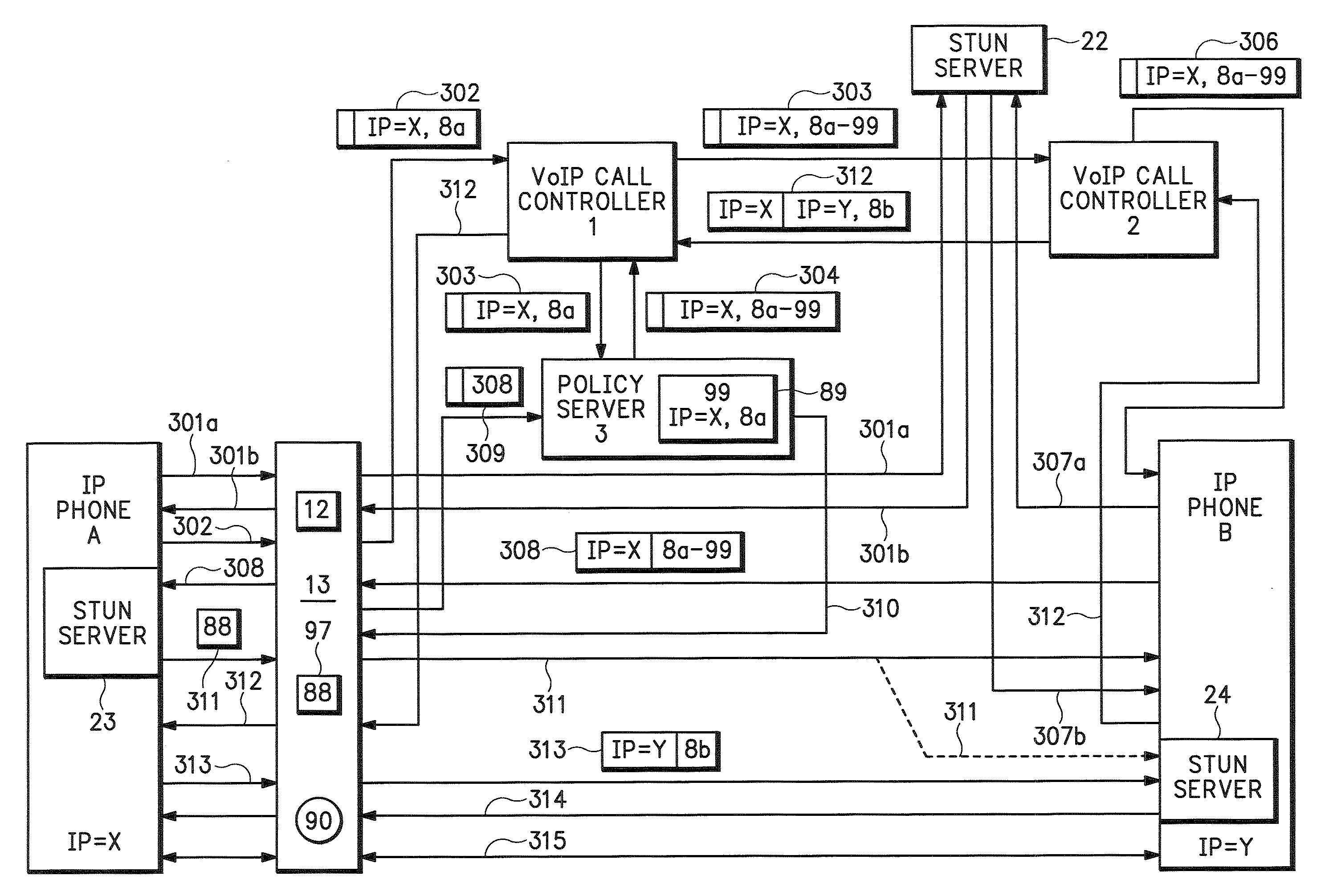
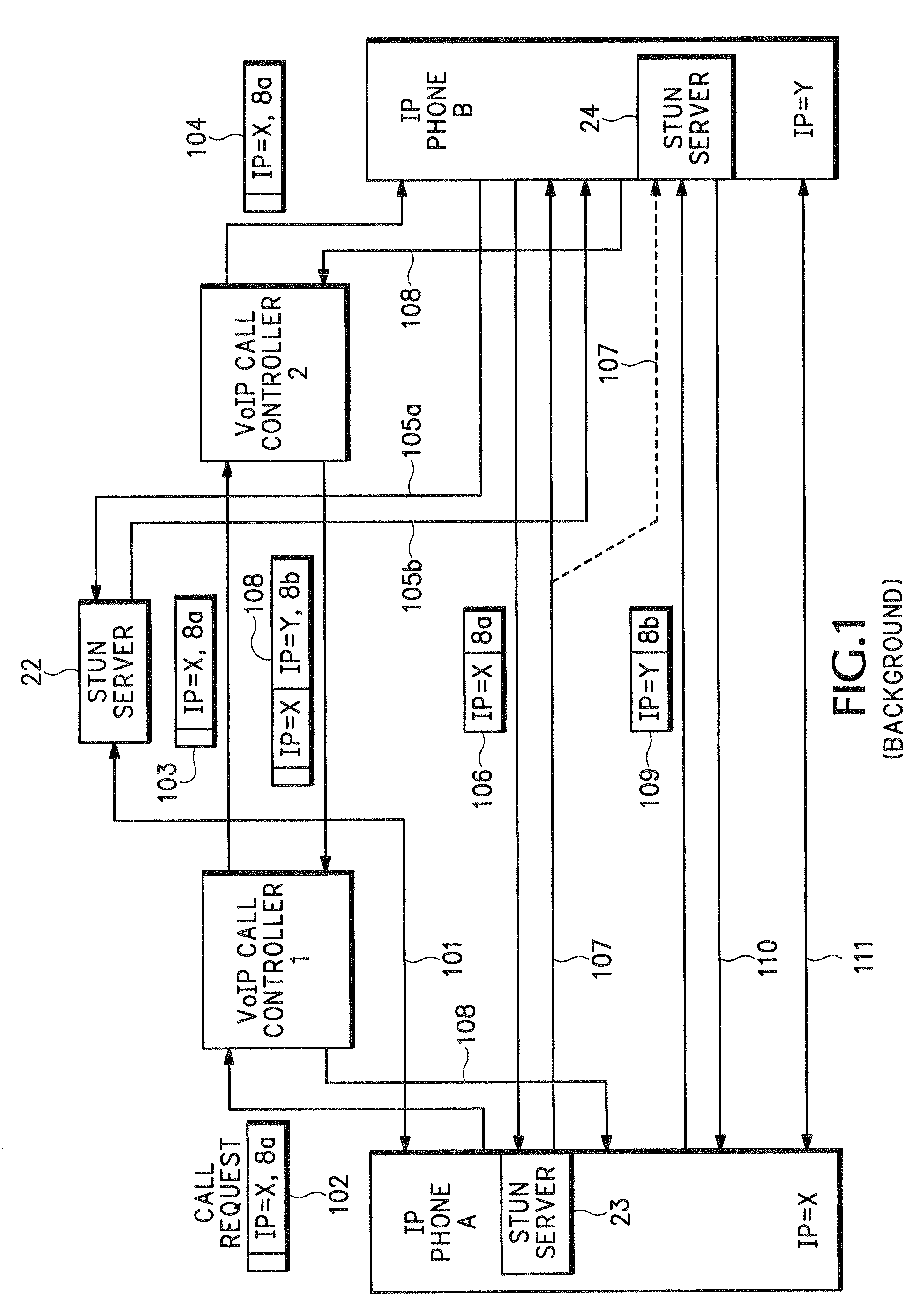
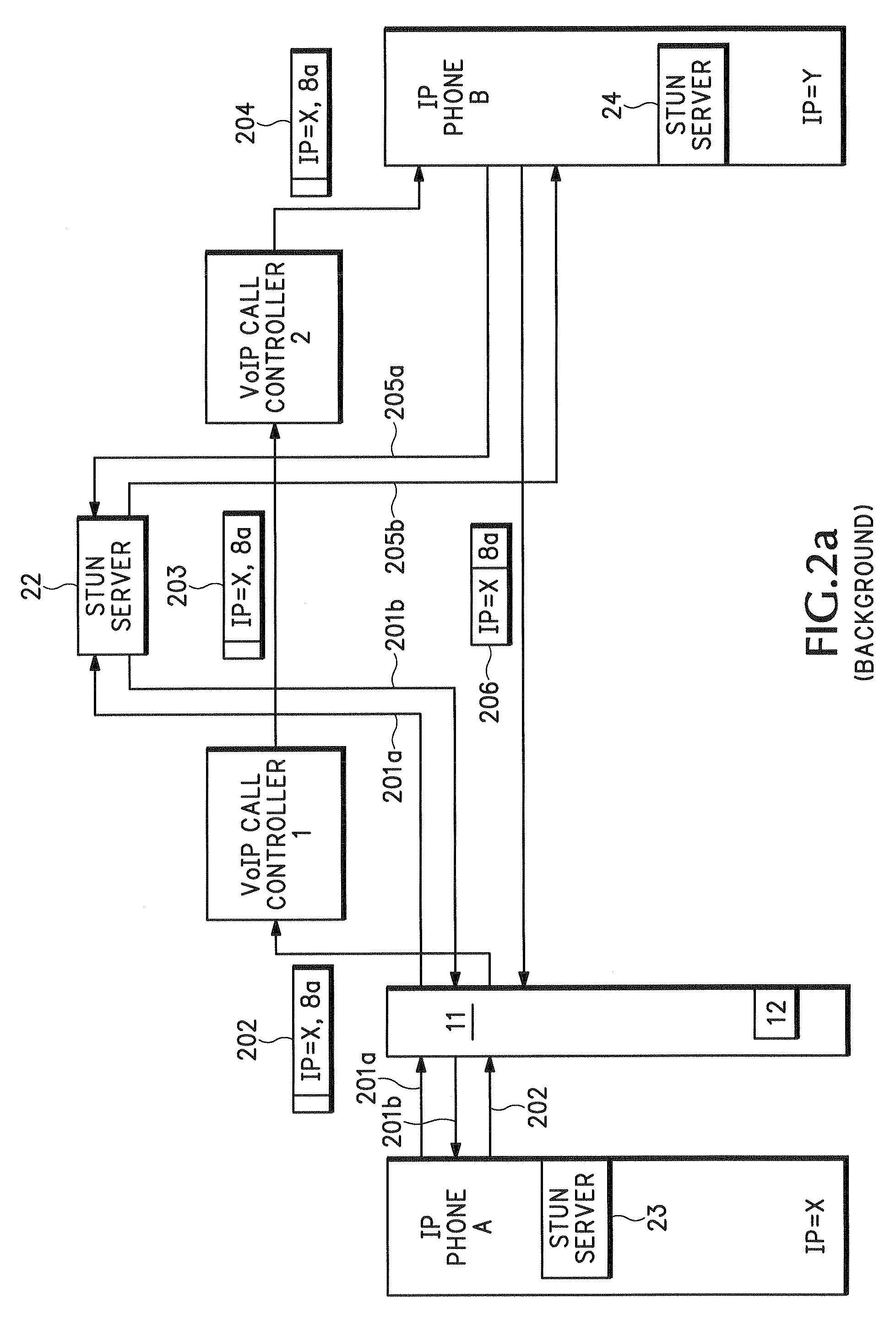
Method for stateful firewall inspection of ICE messages
ActiveUS7472411B2Digital data processing detailsComputer security arrangementsInteractive Connectivity EstablishmentNetwork addressing
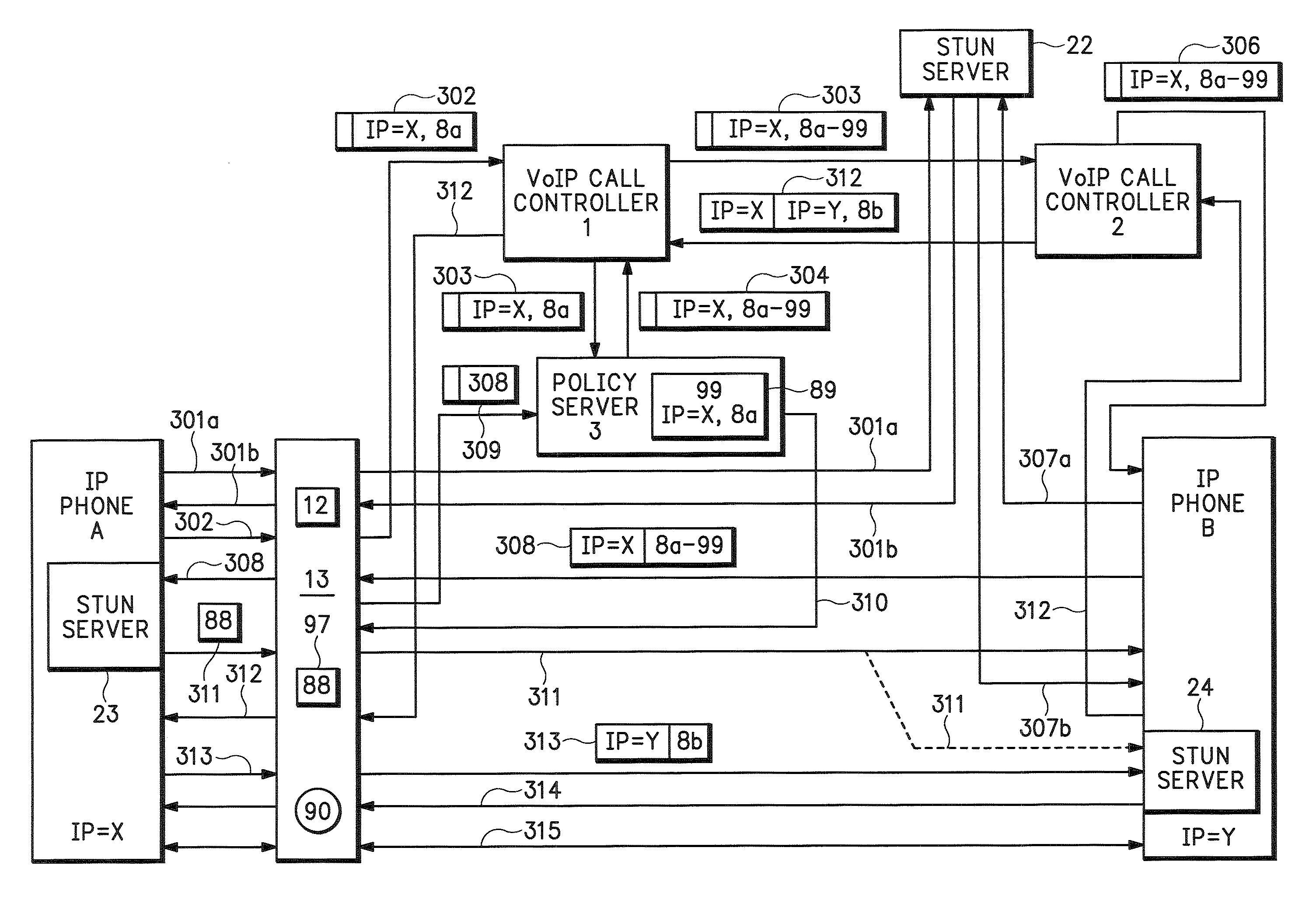
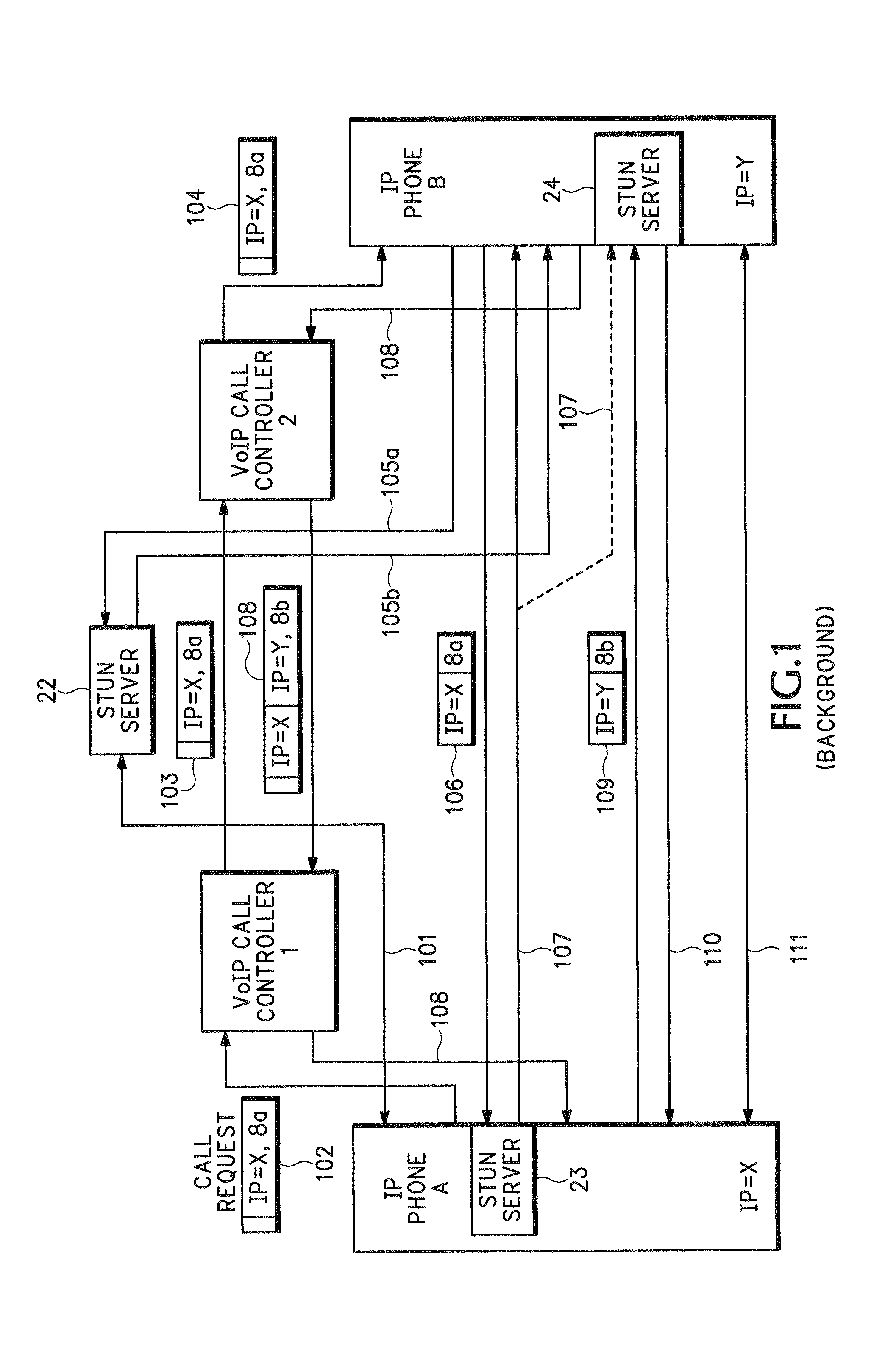
An endpoint uses Interactive Connectivity Establishment (ICE) to enable multimedia communications to traverse Network Address Translators (NATs). A security policy enables security devices and asymmetric security devices to forward ICE messages. A management device stores information about an initial message. Later, a security device receives an ICE message and sends and authorization request to the management device. The management device compares information in the authorization request to information in memory. According to the comparison, the management device authorizes the security device to forward the ICE message.
Owner:CISCO TECH INC
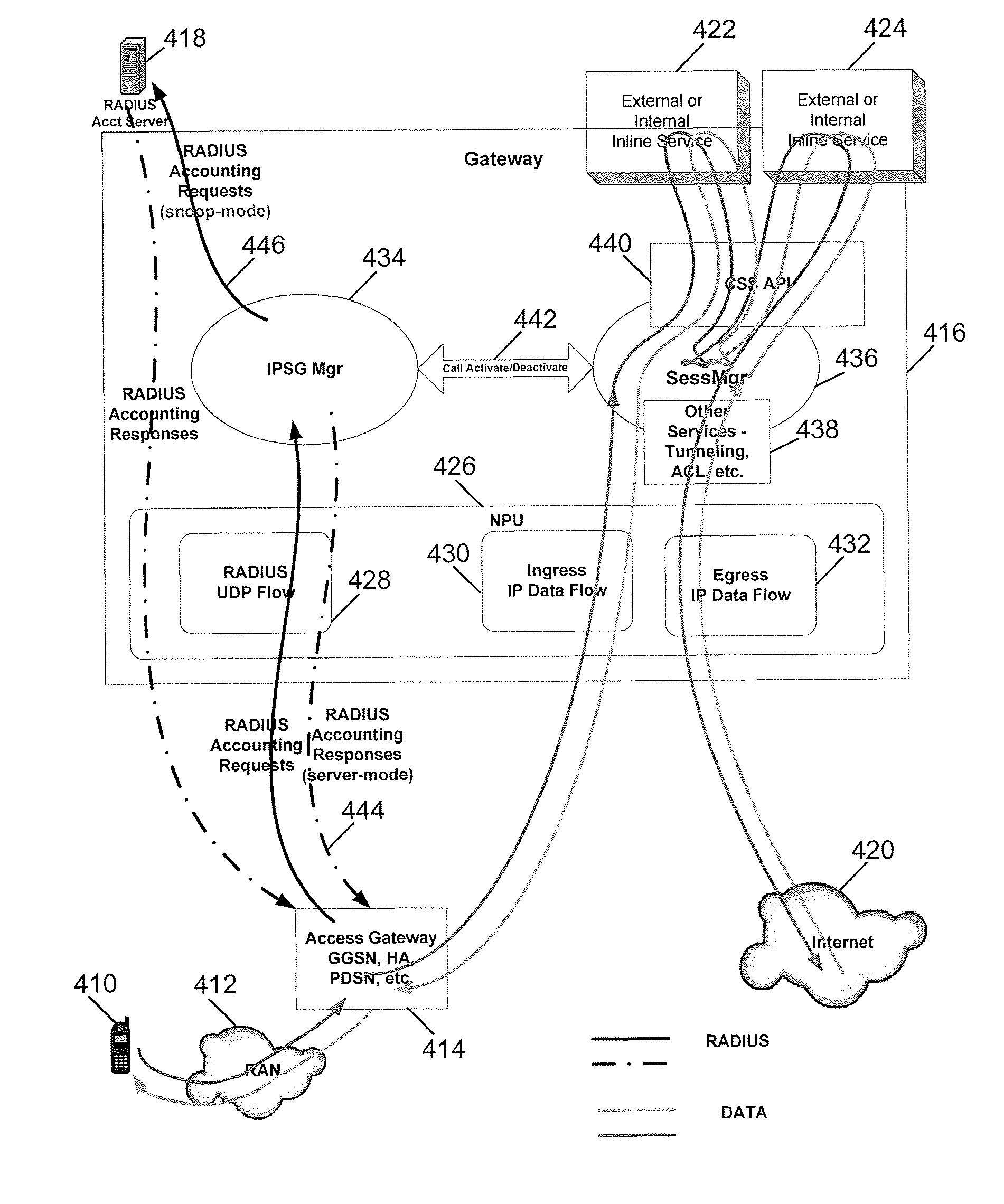
Providing services to packet flows in a network
ActiveUS7855982B2Reduce delaysSpecial service provision for substationMultiplex system selection arrangementsTraffic capacityNetwork packet
A system and method for providing services to packet flows in a communication network. The services include enhanced charging, stateful firewalls, traffic performance optimization (TPO) and advanced services such as content differentiated charging, per-subscriber stateful firewalls, and VPNs, for example. A gateway can be used to route each packet flow through the services on a per-subscriber basis by inspecting accounting messages and checking subscriber profiles prior to setting up a new packet flow session. By directing the packet flow through the services requested latency can be reduced as well as the need to have equipment for each session regardless of whether the service is provided to the packet flow. The services can be provided in-line as well.
Owner:CISCO TECH INC
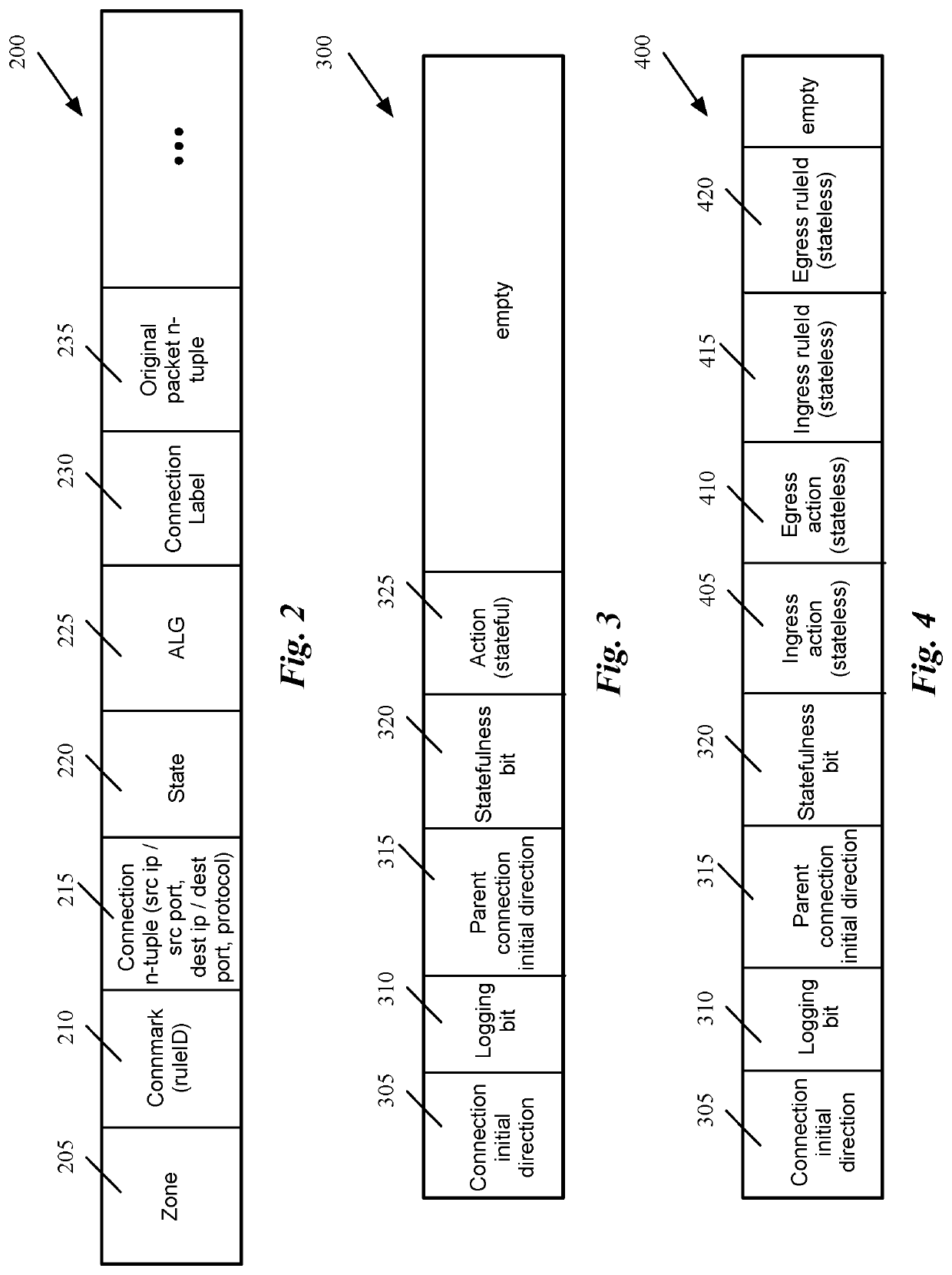
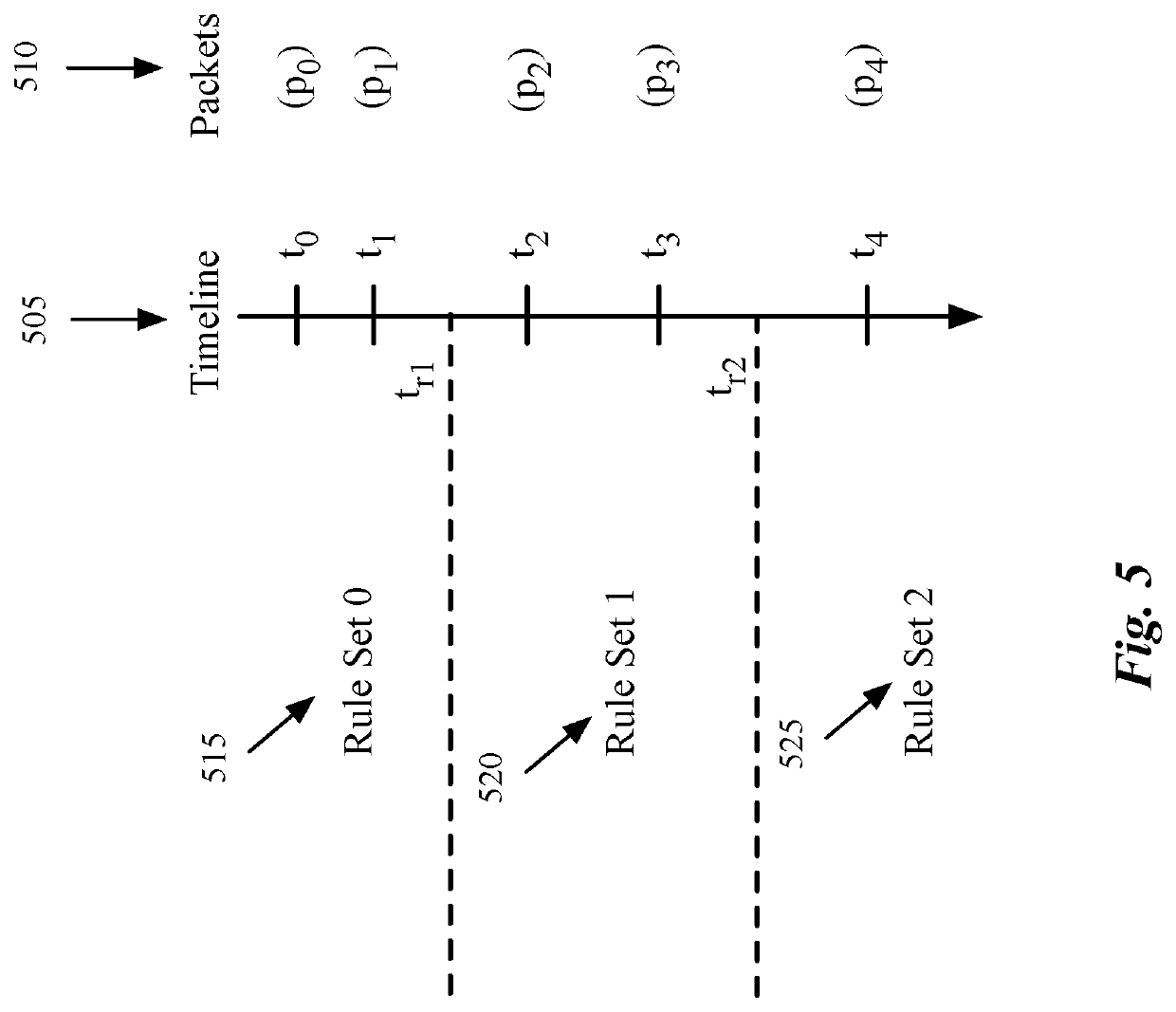
Packet induced revalidation of connection tracker
A method of revalidating a connection tracking table of a flow-based managed forwarding element (MFE) that stores a set of firewall rules associated with each of a set of network connections and a connection table that stores a firewall rule identification and a set of state values associated with each of said network connections. The method receives a change in one or more firewall rules stored at the MFE. The method receives a packet that requires stateful firewall rule check on a particular connection after the change in the firewall rules. When the rule identification retrieved from the connection table is not the same as the new firewall rule associated with the particular connection, the method updates the firewall rule identification and the set of state values associated the particular connection using the new firewall rule identification associated with the particular connection.
Owner:NICIRA
Method for stateful firewall inspection of ice messages
ActiveUS20070101414A1Digital data processing detailsUser identity/authority verificationInteractive Connectivity EstablishmentNetwork addressing
An endpoint uses Interactive Connectivity Establishment (ICE) to enable multimedia communications to traverse Network Address Translators (NATs). A security policy enables security devices and asymmetric security devices to forward ICE messages. A management device stores information about an initial message. Later, a security device receives an ICE message and sends and authorization request to the management device. The management device compares information in the authorization request to information in memory. According to the comparison, the management device authorizes the security device to forward the ICE message.
Owner:CISCO TECH INC
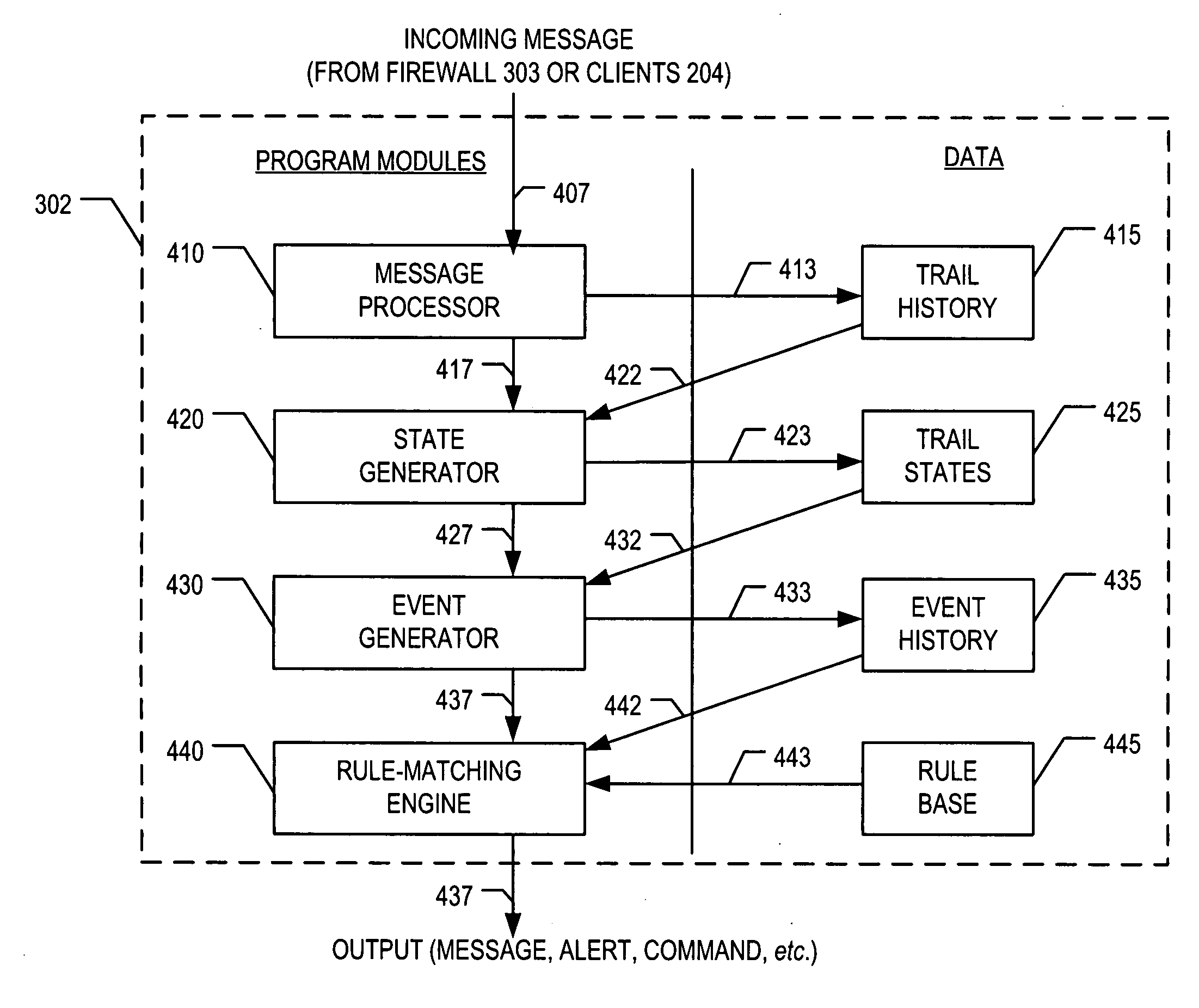
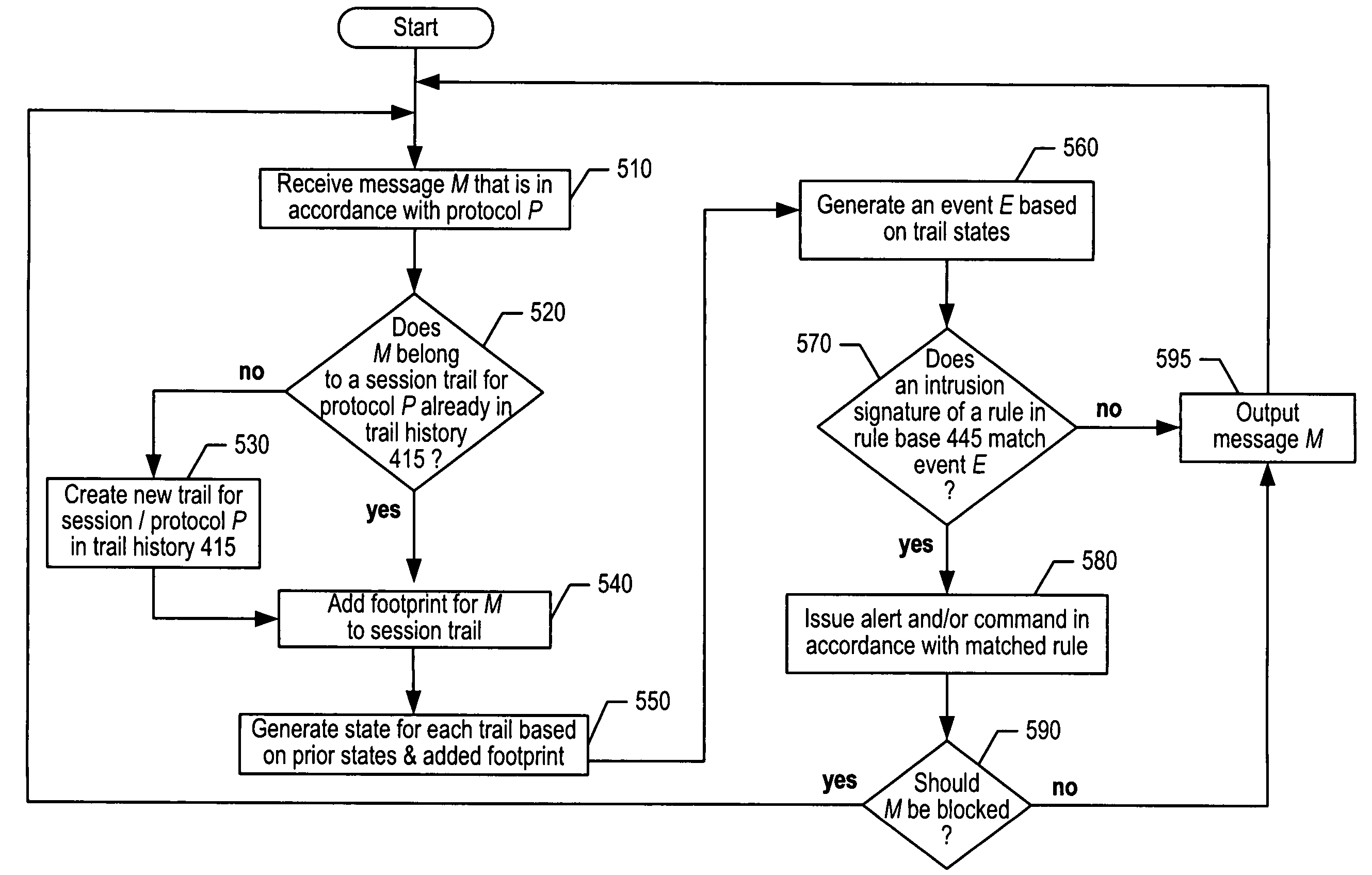
Stateful and cross-protocol intrusion detection for Voice over IP
A method for detecting intrusions that employ messages of two or more protocols is disclosed. Such intrusions might occur in Voice over Internet Protocol (VoIP) systems, as well as in systems in which two or more protocols support some service other than VoIP. In the illustrative embodiment of the present invention, a stateful intrusion-detection system is capable of employing rules that have cross-protocol pre-conditions. The illustrative embodiment can use such rules to recognize a variety of VoIP-based intrusion attempts, such as call hijacking, BYE attacks, etc. In addition, the illustrative embodiment is capable of using such rules to recognize other kinds of intrusion attempts in which two or more protocols support a service other than VoIP. The illustrative embodiment also comprises a stateful firewall that is capable of employing rules with cross-protocol pre-conditions.
Owner:PURDUE RES FOUND INC
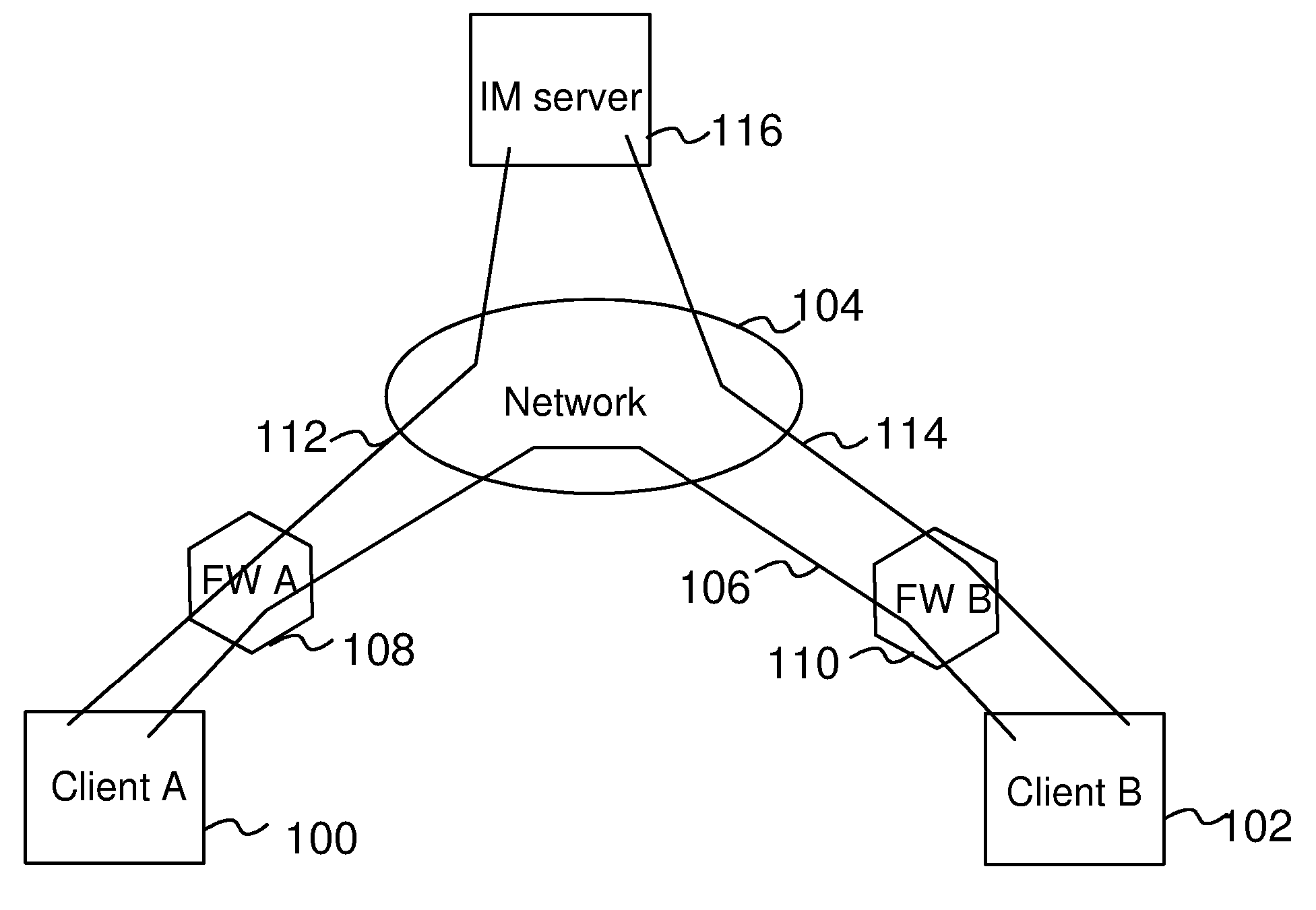
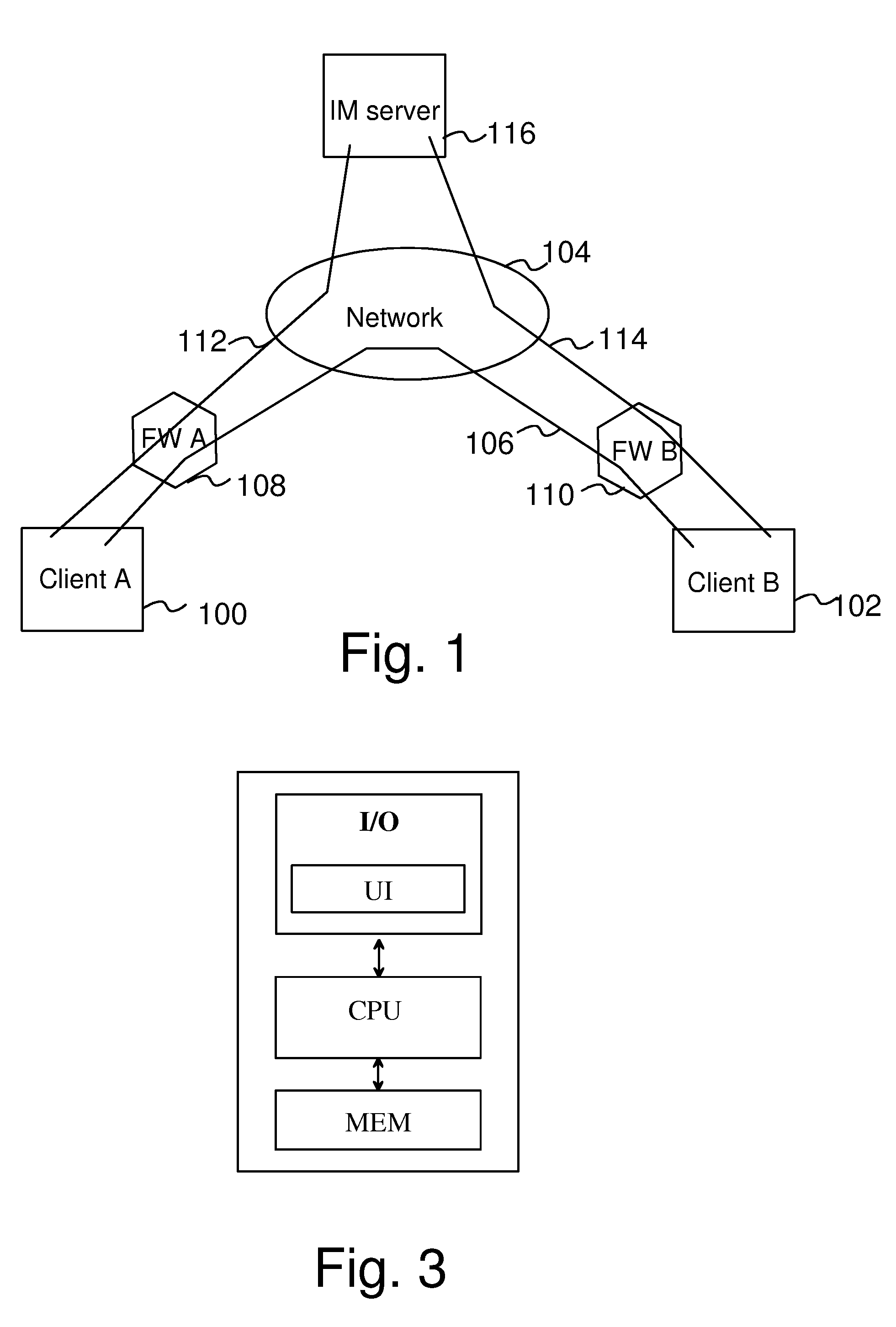
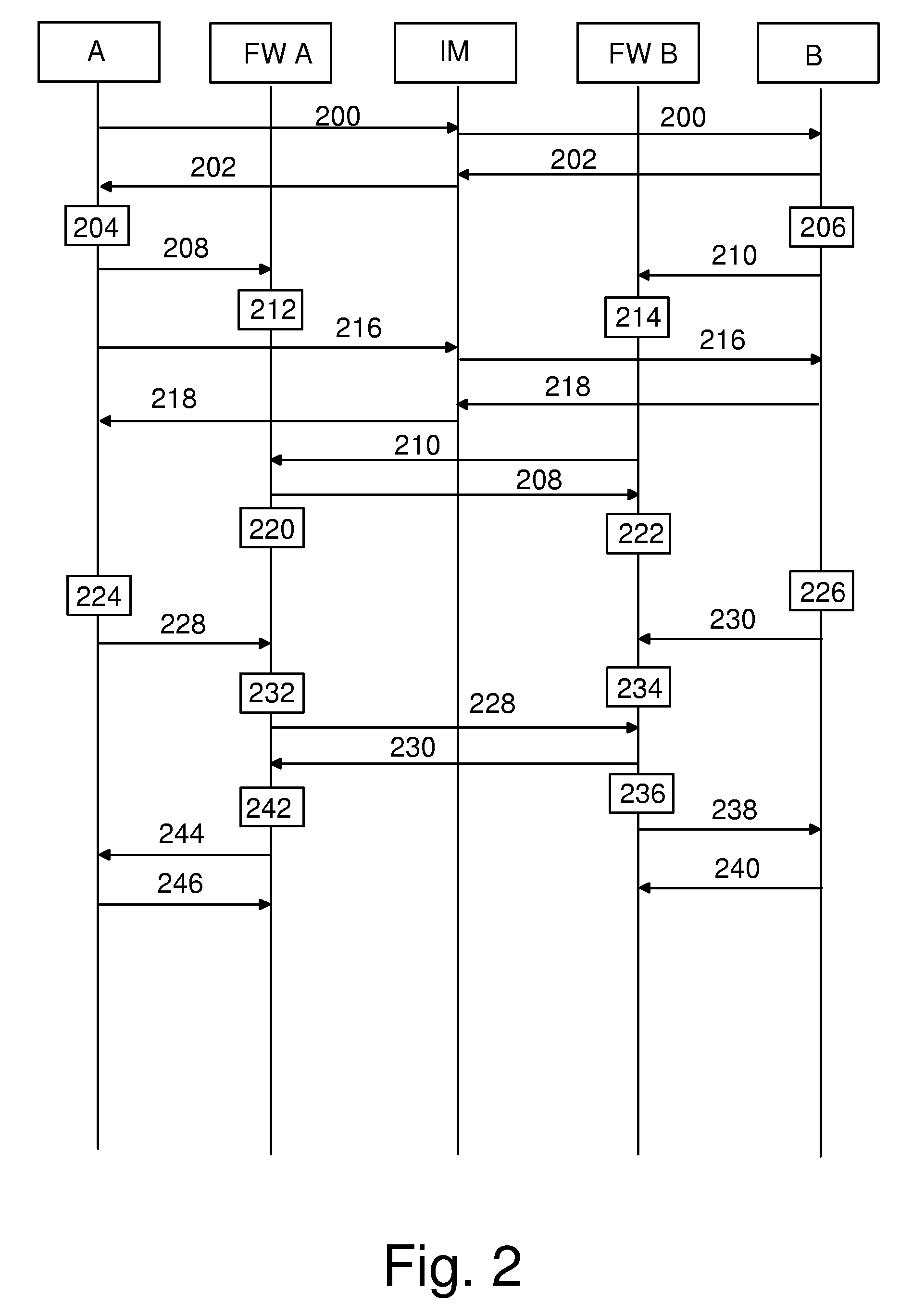
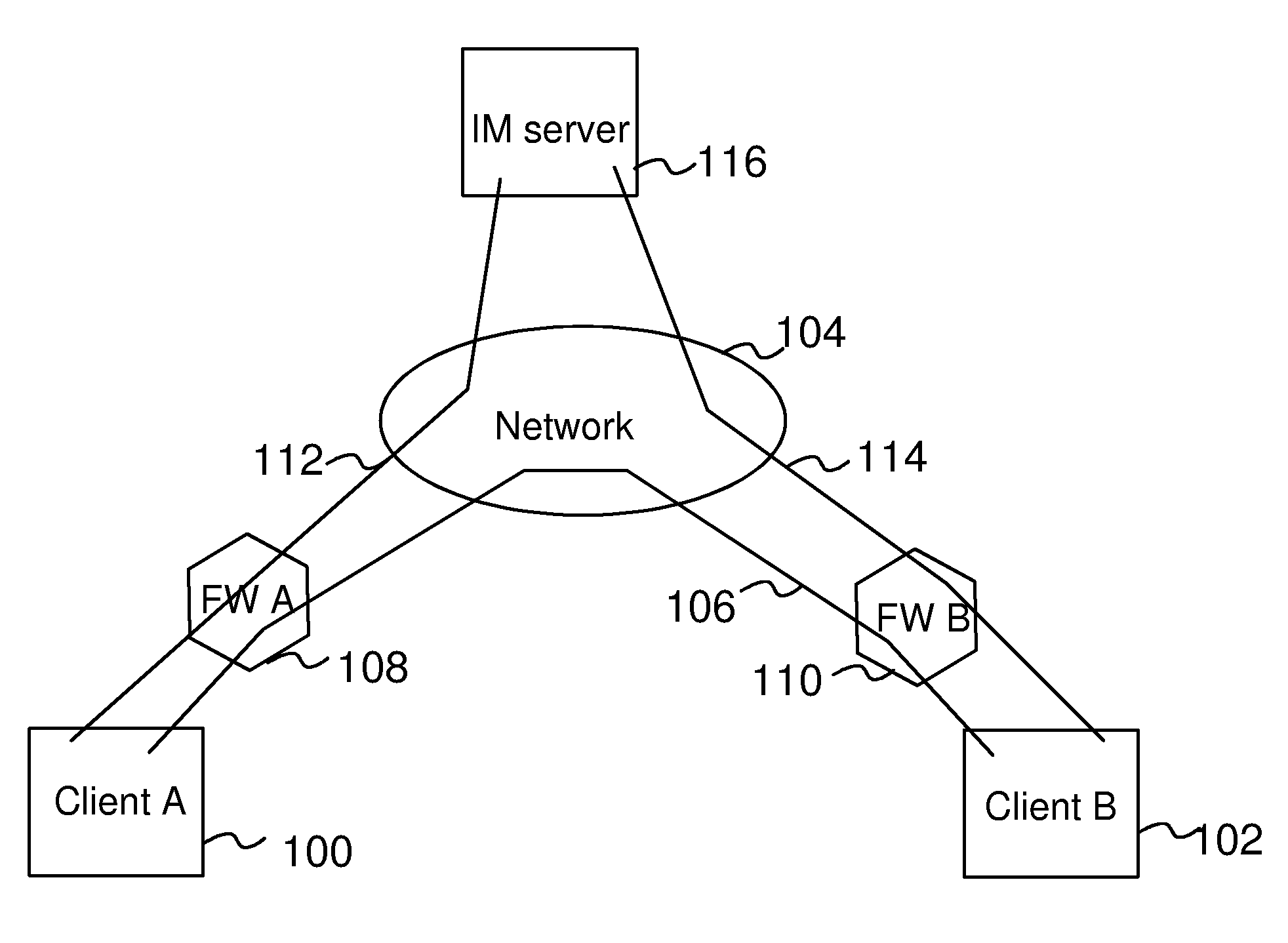
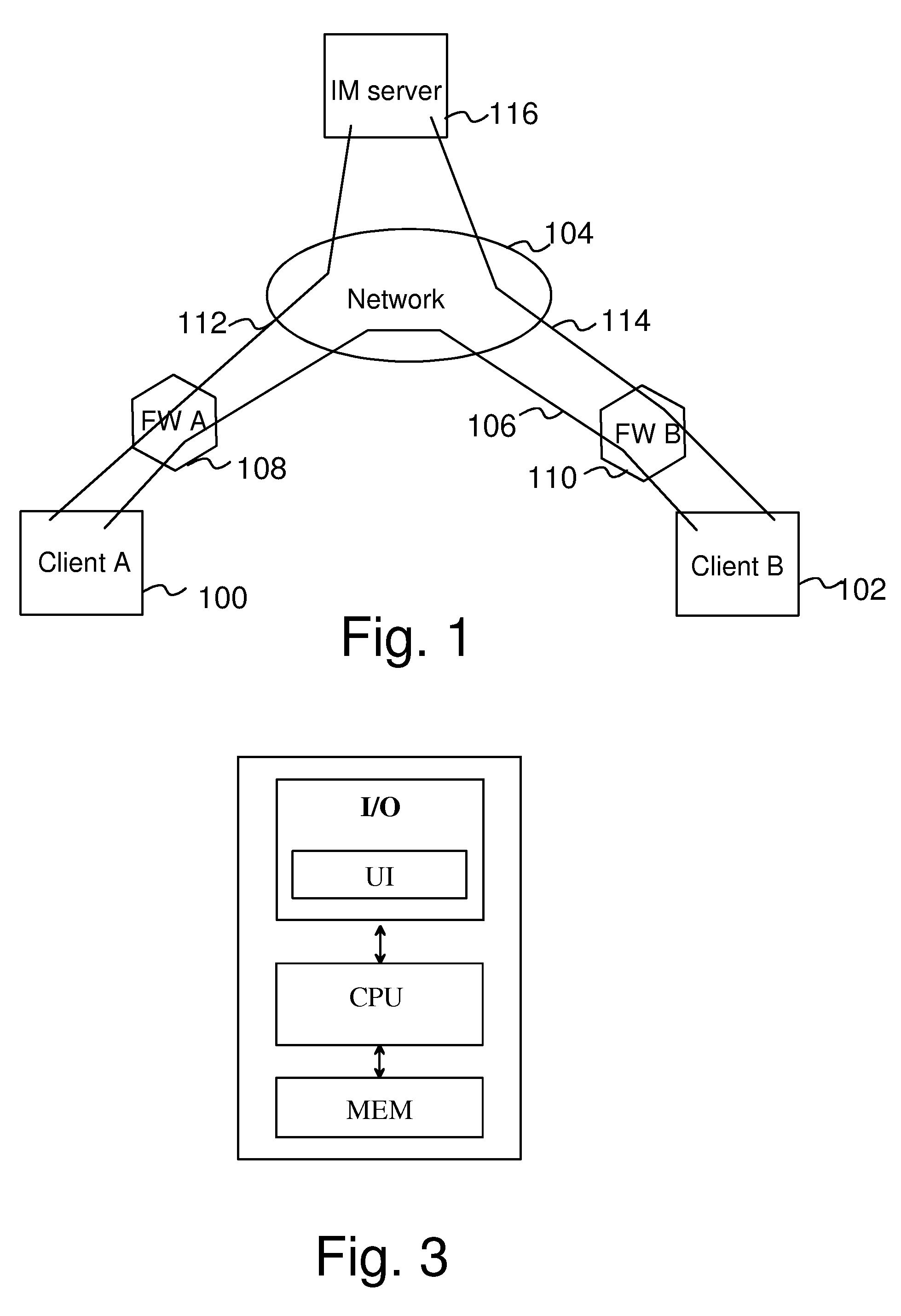
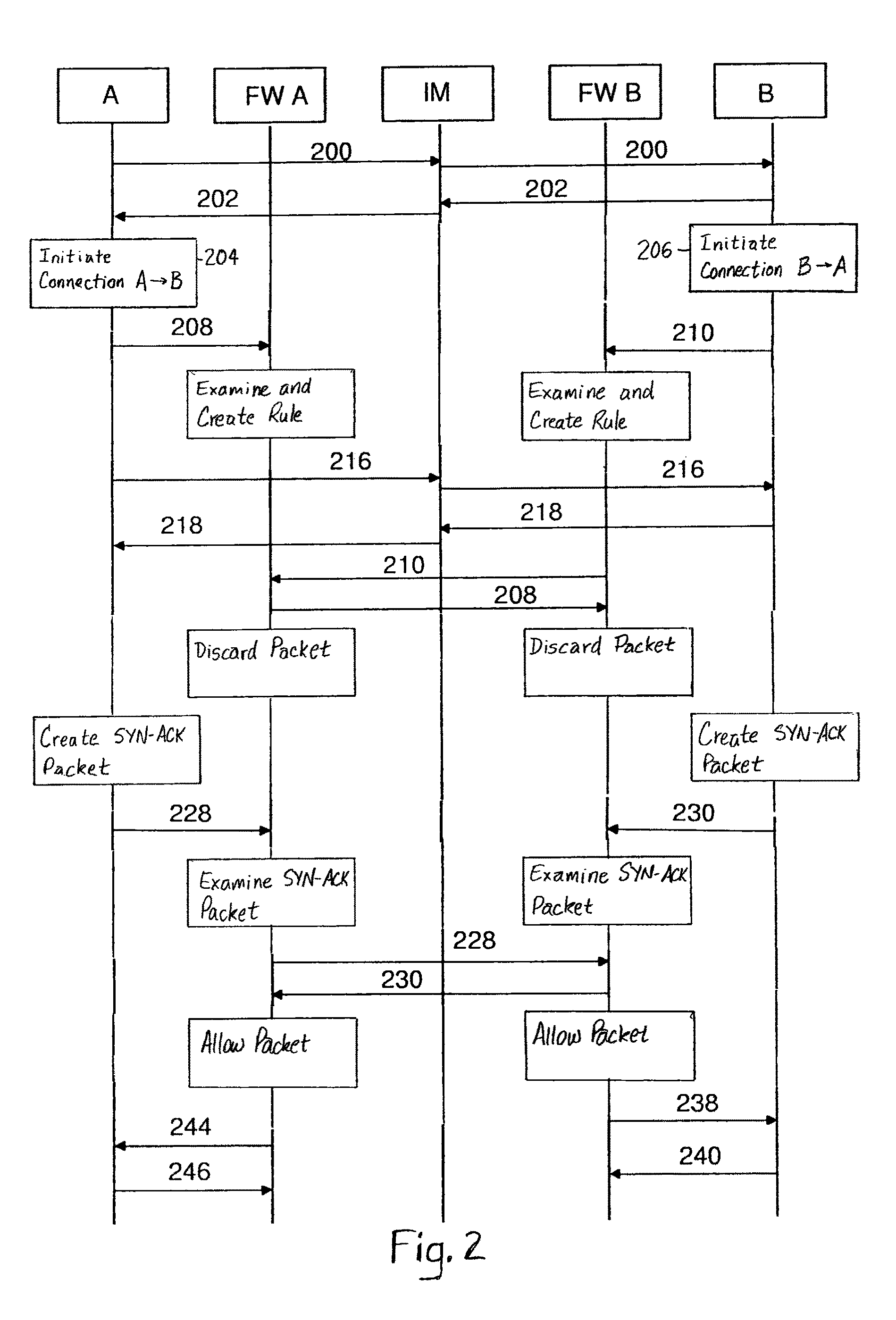
Connectivity Over Stateful Firewalls
InactiveUS20080028097A1Easy to implementMultiple digital computer combinationsTransmissionTelecommunicationsRaw socket
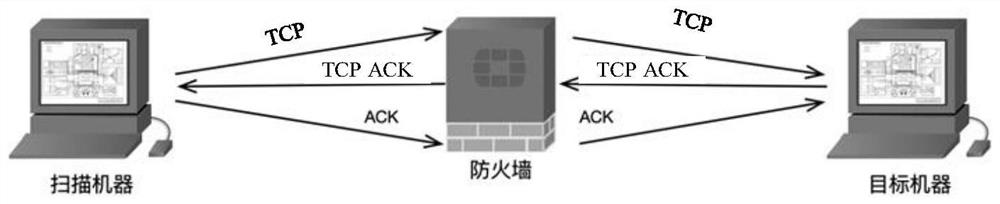
A method for establishing a TCP connection between two client terminals protected by stateful firewalls and comprising means for sending messages to each other via a messaging server. The client terminals agree on establishing a mutual TCP connection by sending a message, which indicates port numbers to be used on said connection. A TCP connection establishment procedure is started in both client terminals. After sending a first handshake message, a message indicating a sequence number of the first handshake message is sent from both client terminals to each other. When the firewalls of the opposite client terminals reject the first handshake message, an acknowledgement message to the first handshake message is created in both client terminals using a raw socket, which acknowledgement message includes the received sequence number as an acknowledgement number. Finally, the raw socket based acknowledgement message is sent to the opposite client terminal for completing the establishment of the TCP connection.
Owner:TELIASONERA
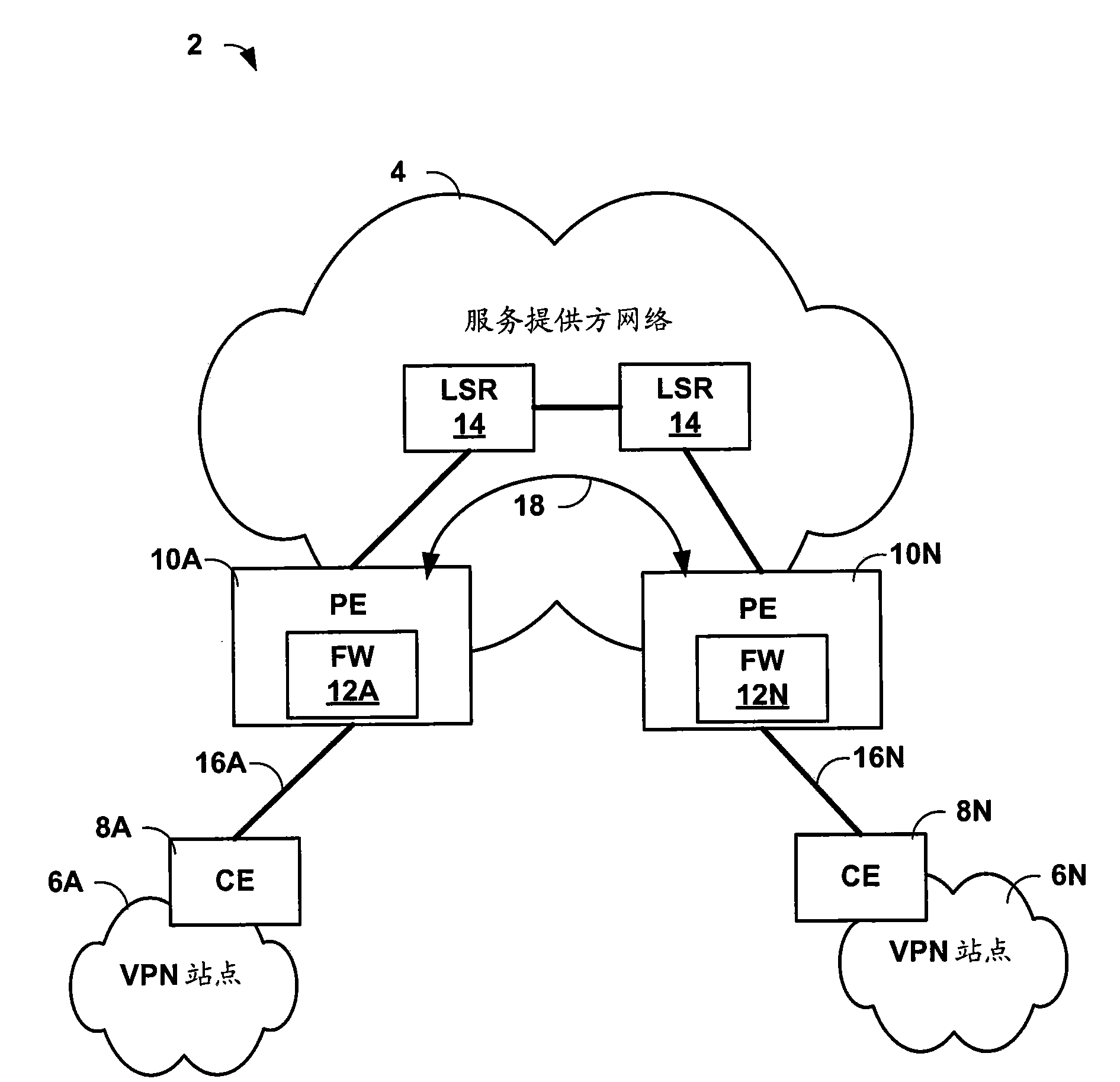
Routing device having integrated MPLS-aware firewall
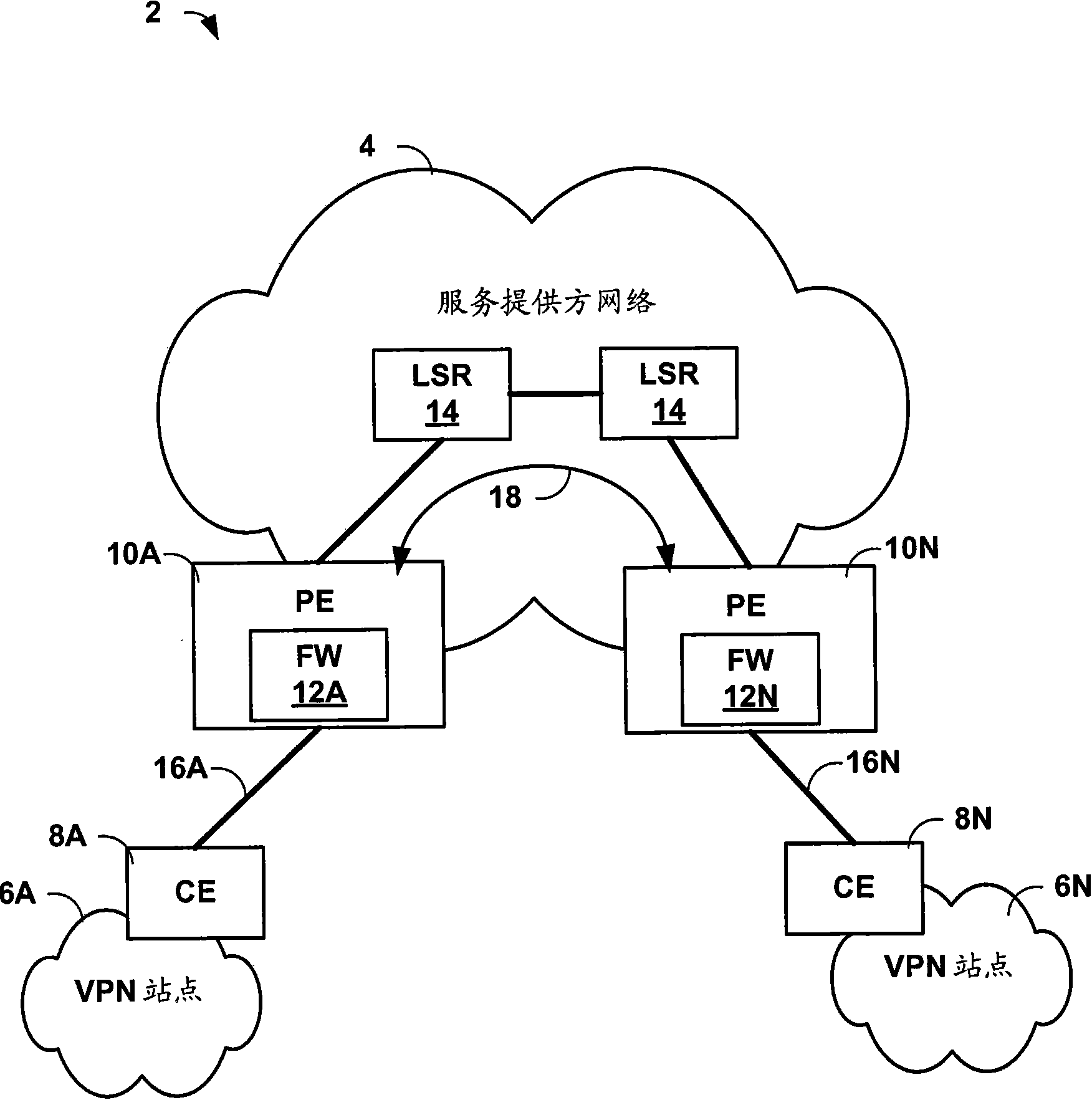
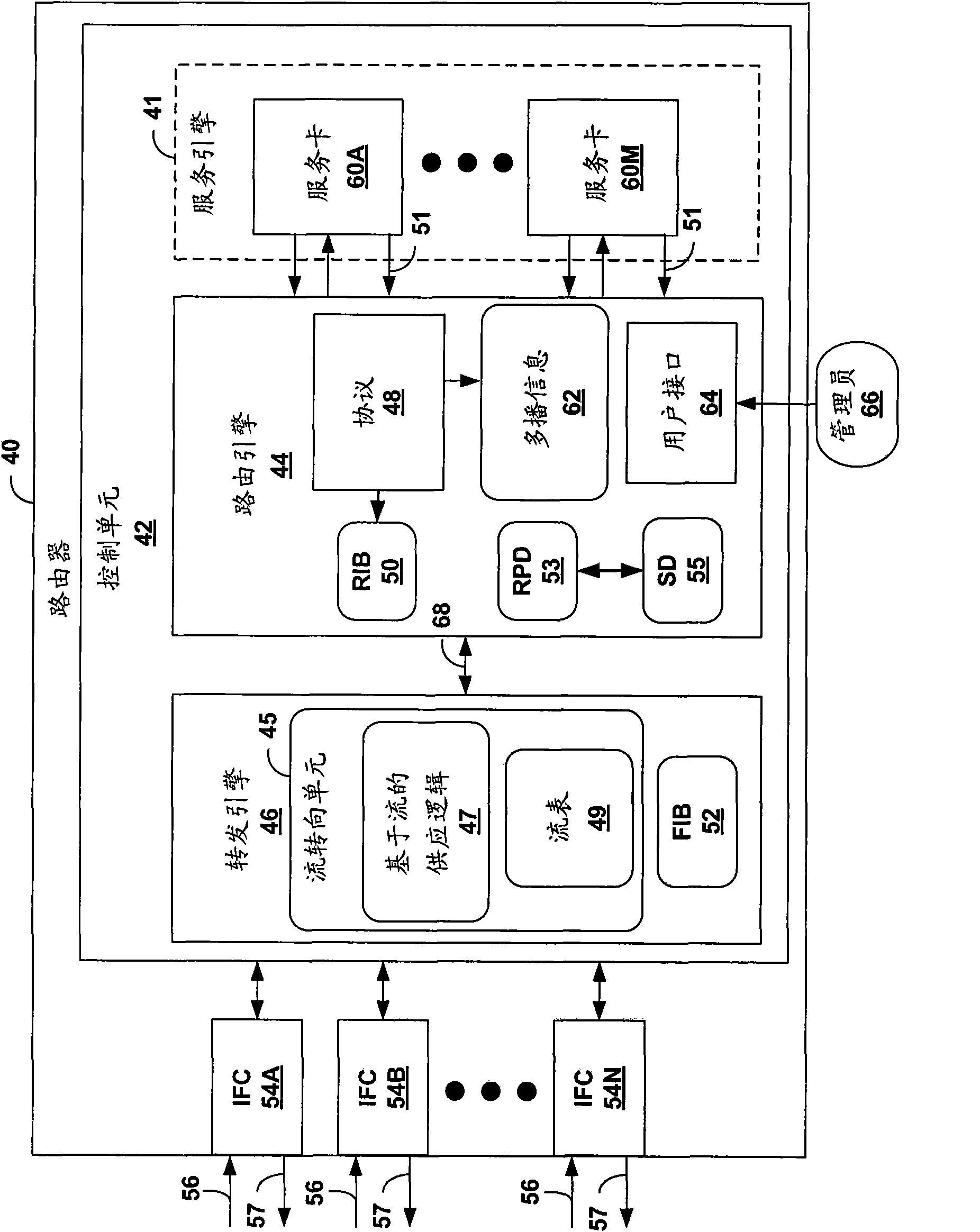
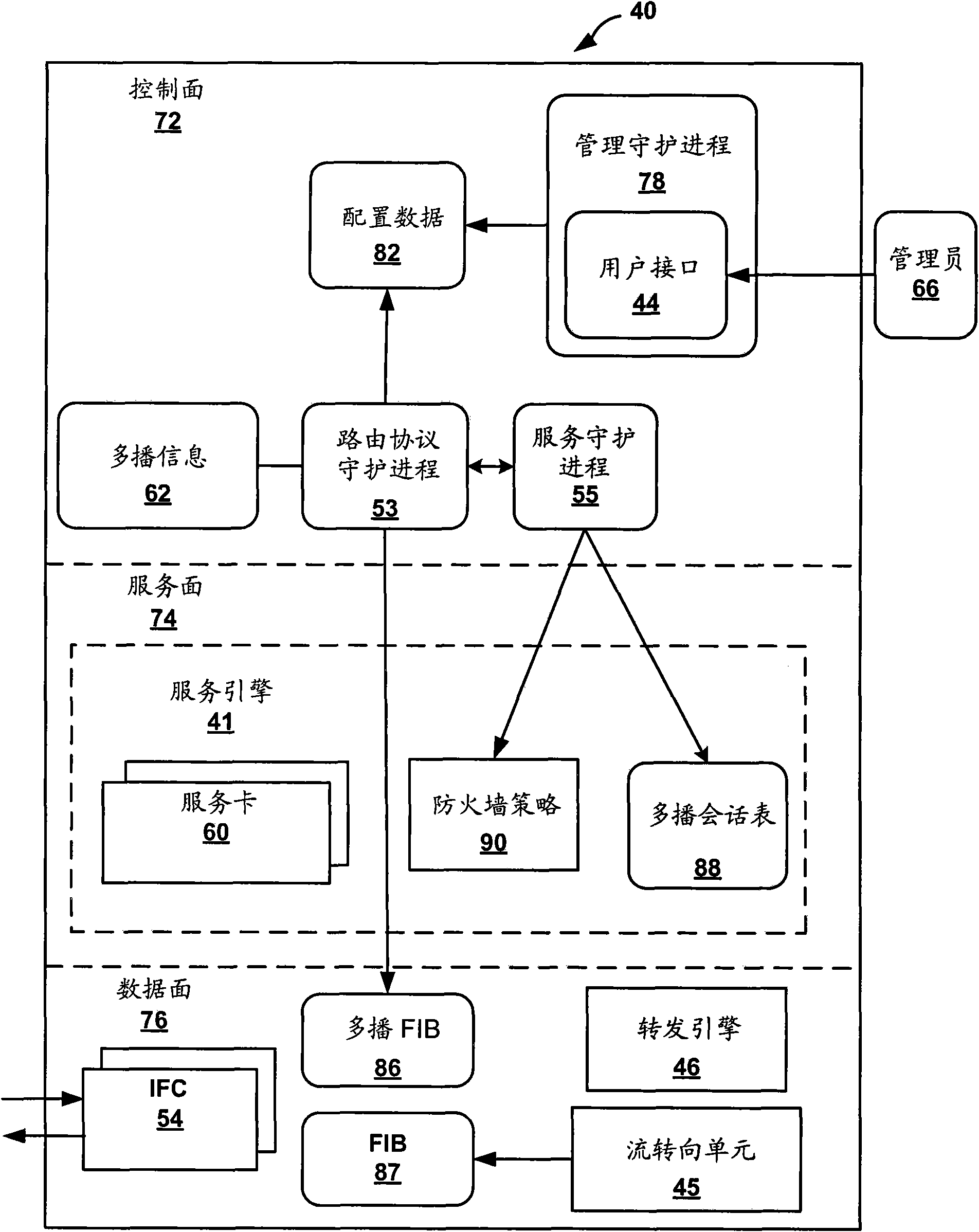
An MPLS-aware firewall allows firewall security policies to be applied to MPLS traffic. The firewall, which may be integrated within a routing device, can be configured into multiple virtual security systems. The routing device provides a user interface by which a user specifies one or more zones to be recognized by the integrated firewall when applying stateful firewall services to the packets. The user interface allows the user to define different zones and policies for different ones of the virtual security systems. In addition, the user interface supports a syntax that allows the user to define the zones for the firewall by specifying the customer VPNs as interfaces associated with the zones. The routing device generates mapping information for the integrated firewall to map the customer VPNs to specific MPLS labels for the MPLS tunnels carrying the customer's traffic.
Owner:JUMIPER NETWORKS INC
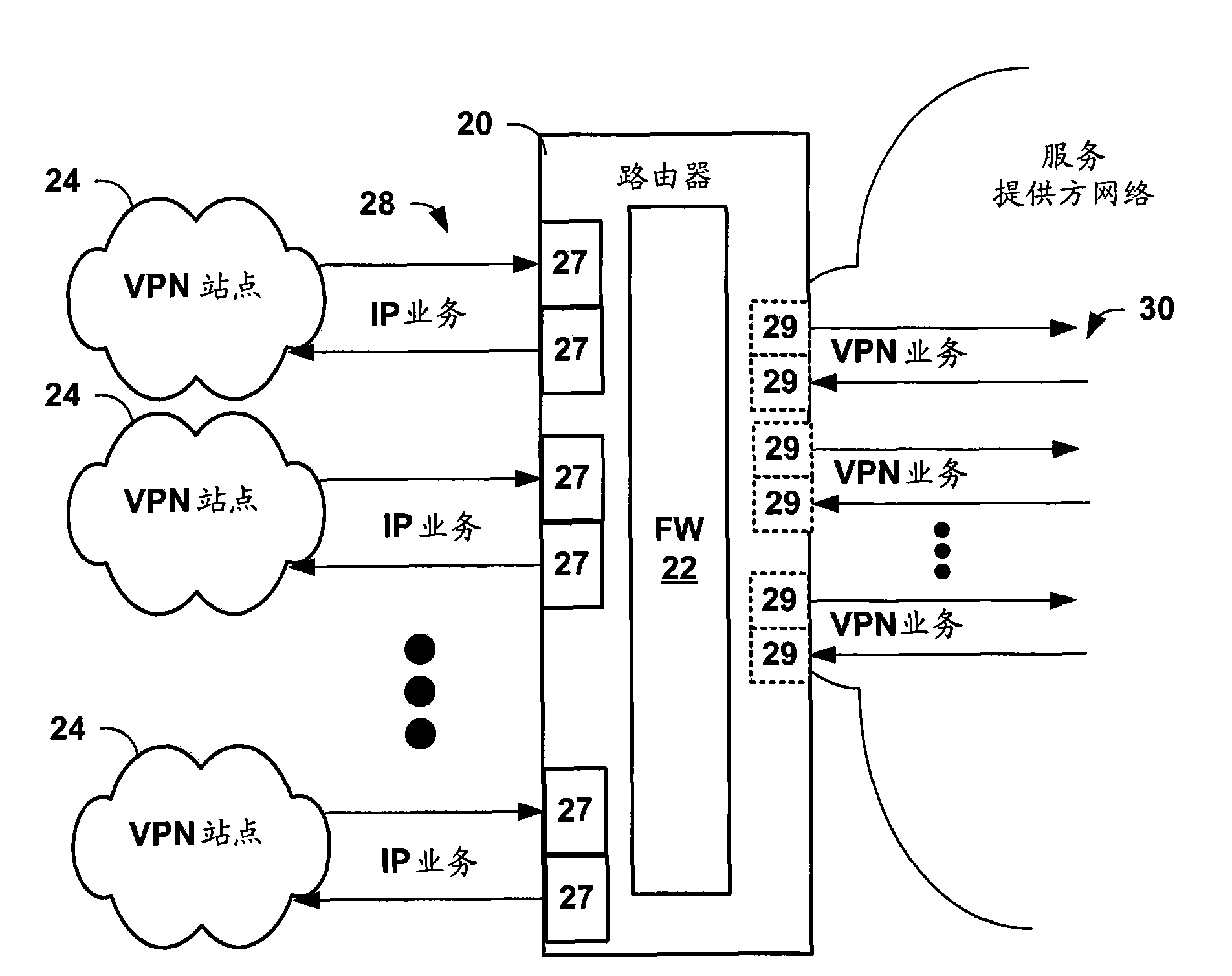
Scalable security services for multicast in a router having integrated zone-based firewall
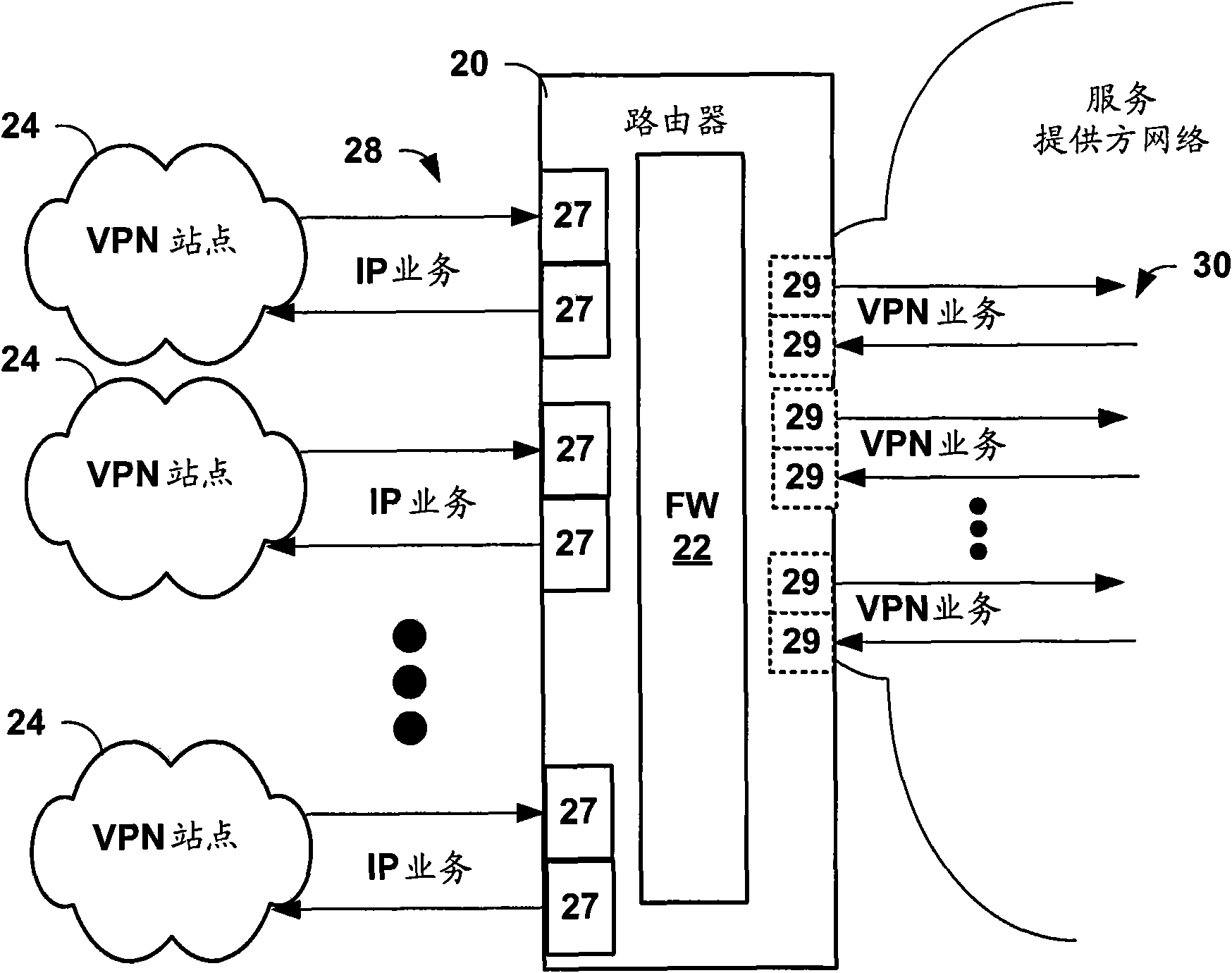
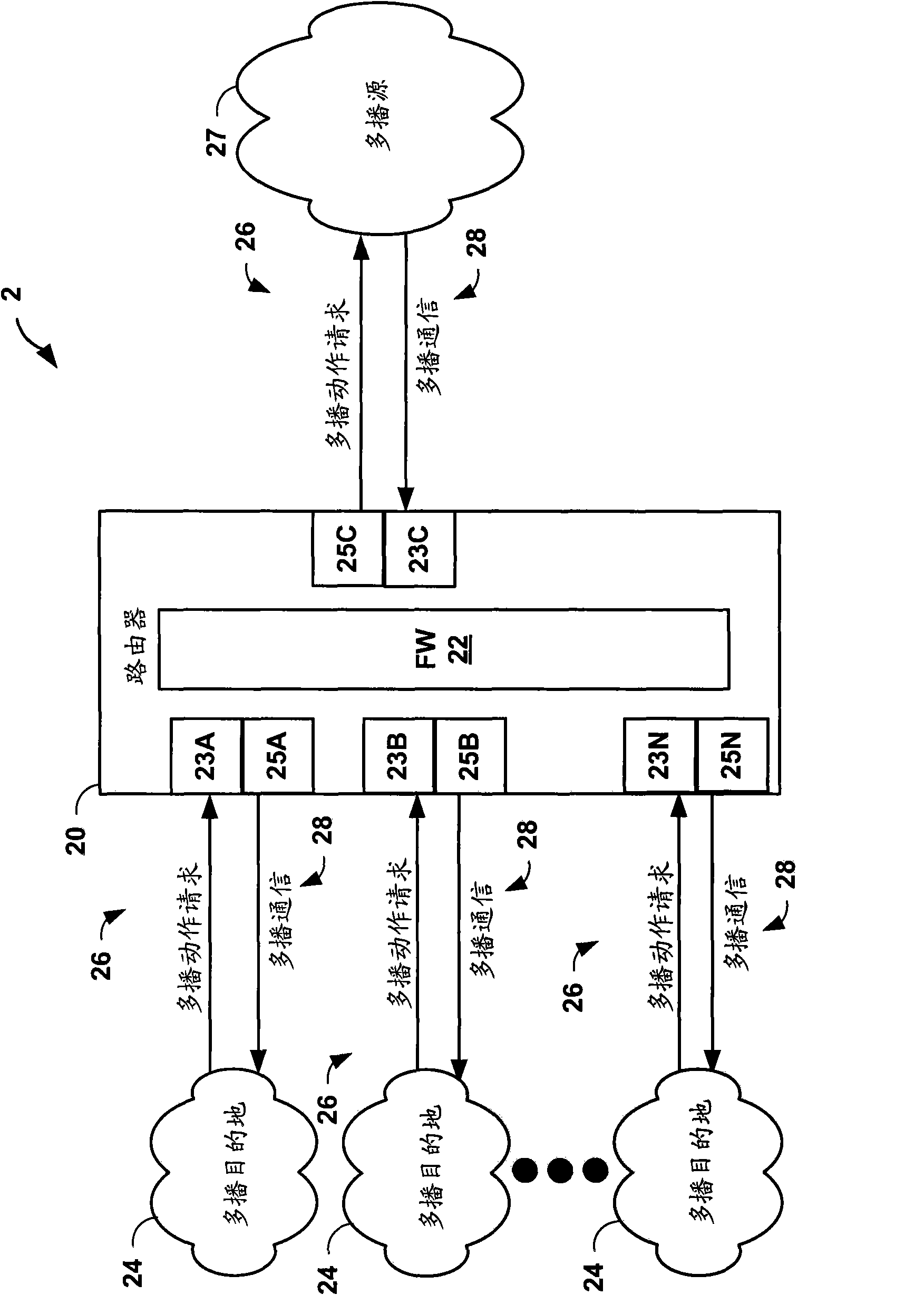
A multicast-capable firewall allows firewall security policies to be applied to multicast traffic. The multicast-capable firewall may be integrated within a routing device, thus allowing a single device to provide both routing functionality, including multicast support, as well as firewall services. The routing device provides a user interface by which a user specifies one or more zones to be recognized by the integrated firewall when applying stateful firewall services to multicast packets. The user interface supports a syntax that allows the user to define subsets of the plurality of interfaces associated with the zones, and define a single multicast policy to be applied to multicast sessions associated with a multicast group. The multicast policy identifies common services to be applied pre-replication, and exceptions specifying additional services to be applied post-replication to copies of the multicast packets for the one or more zones.
Owner:JUMIPER NETWORKS INC
Method for bi-directional symmetric routing in multi-homed networks with stateful firewalls
There are provided systems and methods for symmetric bi-directional routing in multi-homed IP networks which includes sending an IP packet having a source address from a first host and substituting the source address with an exterior routing address by a first network address translation gateway or firewall of the first host using conditional substitution. The IP packet, with the exterior routing address, is optionally routed via intermediate networks and firewalls and received by a first gateway or firewall of a second host. The second host responds to the first host along a route which traverses the same set of firewall gateways as the initial IP packet by using the exterior routing address as a destination address. The exterior routing address is converted back to the source address by the first network address translation gateway of the first host.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
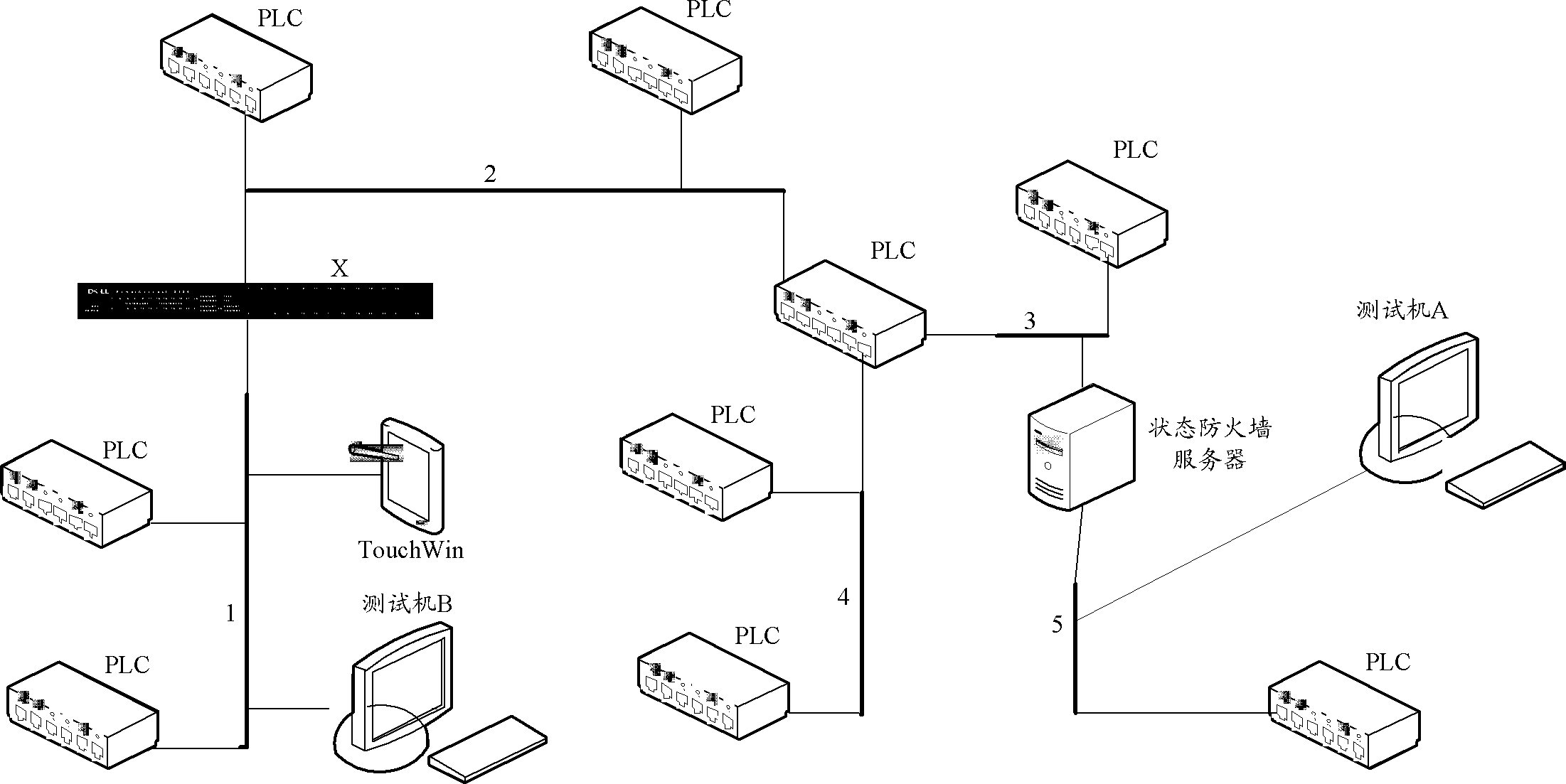
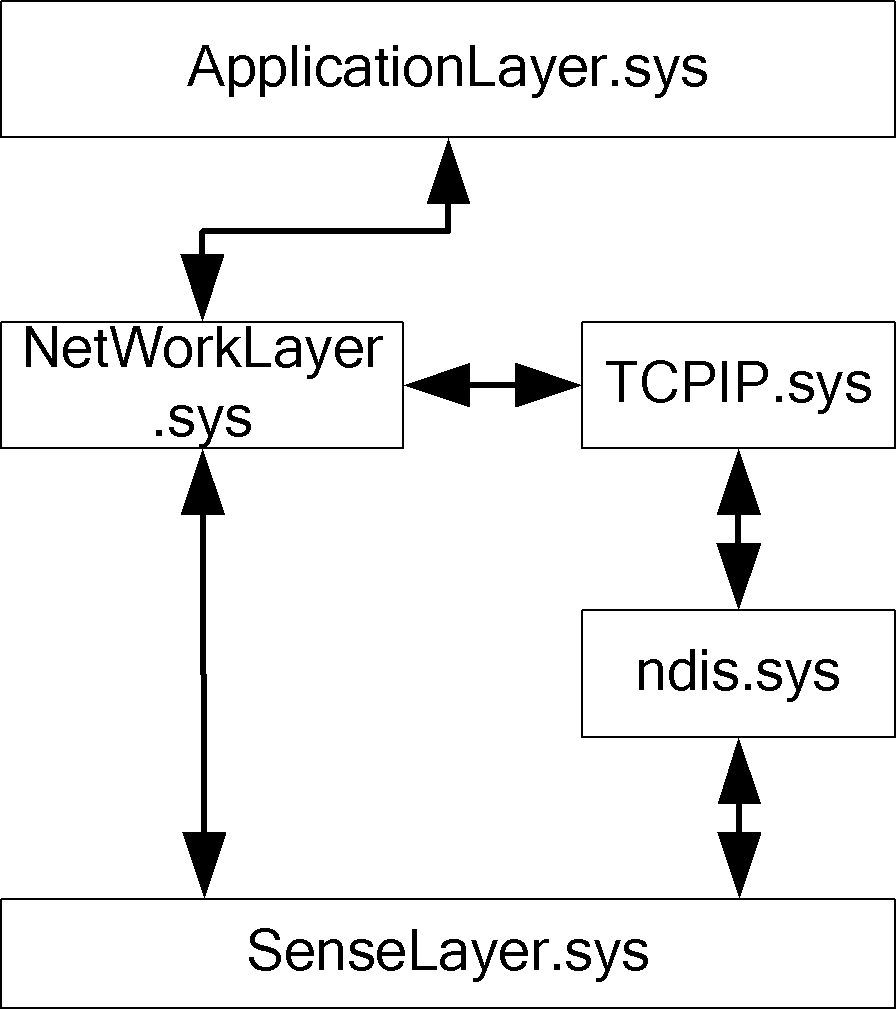
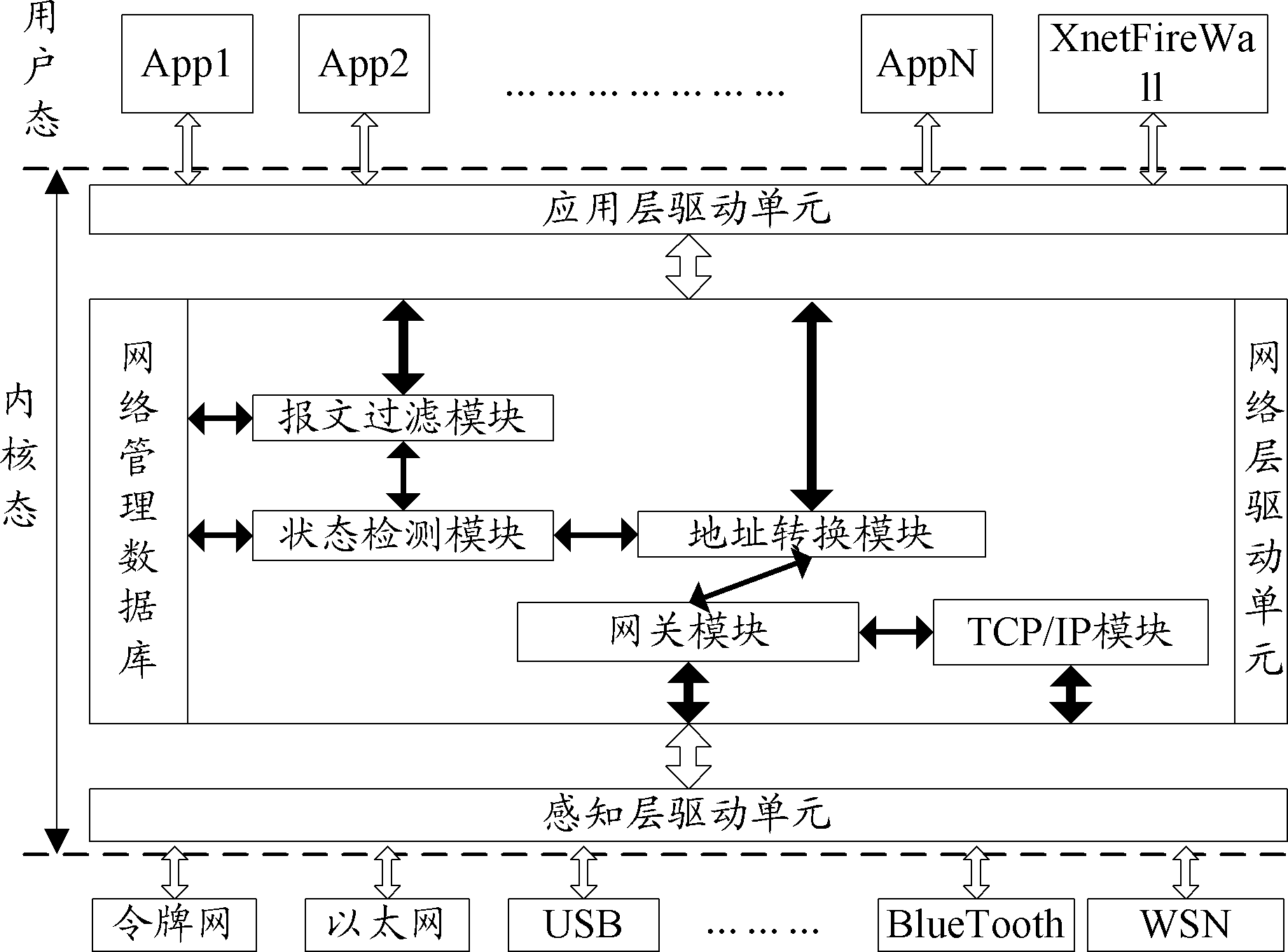
State firewall state detection system and method based on industrial Internet of Things
InactiveCN103607316AOvercome strengthOvercome speedData switching networksState of artNetwork management
The invention discloses a state firewall state detection system and a method based on the industrial Internet of Things. The system comprises an application layer drive unit used for driving user side application layer programs and / or files, a sensing layer drive unit used for driving information interaction ports, a network state detection unit used for detecting and processing the network state of the industrial Internet of Things, and a network management database used for serving the network state detection unit and matched therewith and a network layer drive unit, wherein the application layer drive unit, the network state detection unit and the sensing layer drive unit are in communication connection in sequence. The state firewall state detection system and the method based on the industrial Internet of Things in the invention can overcome the defects of weak protocol stack architecture support force, slow detection speed, and poor flexibility in the prior art, so as to realize the advantages of strong protocol stack architecture support force, fast detection speed and good flexibility.
Owner:WUXI XINJIE ELECTRICAL
Securely Virtualizating Network Services
ActiveUS20090113535A1Multiplex system selection arrangementsMultiple digital computer combinationsTraffic capacityNetwork service
Services in a network device are added through providing virtual environments. Virtualization allows services based on other platforms or architectures to be run with minimum modification and in a secure manner. Connecting services to the host through a stateful firewall allows dynamic integration, and passes only traffic of interest to the service. Virtualization allows services written for different instruction architectures to be supported. Multiple virtualized environments each supporting a service may be run.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Wireless local area network infrastructure devices having improved firewall features
ActiveUS8826413B2Broadcast transmission systemsMultiple digital computer combinationsClient-sideBlack list
Methods and systems are provided for improving a firewall implemented at a WLAN infrastructure device (WID). The WID includes a stateful firewall that implements firewall rules based on an ESSID of the WID to specify whether traffic is allowed to or from the ESSID. For example, in one implementation of such a firewall rule, packets that are required to be sent out on all wired ports can be blocked from being flooded out on WLANs (e.g., the packet is allowed to pass only to the wired ports). A method and system are provided for preventing a malicious wireless client device (WCD) that is transmitting undesirable traffic from using RF resources by deauthenticating the malicious WCD to remove it from the WLAN and blacklisting it to prevent it from rejoining the WLAN for a time period. Method and systems are also provided for either “on-demand” and / or predicatively communicating state information regarding an existing firewall session.
Owner:EXTREME NETWORKS INC
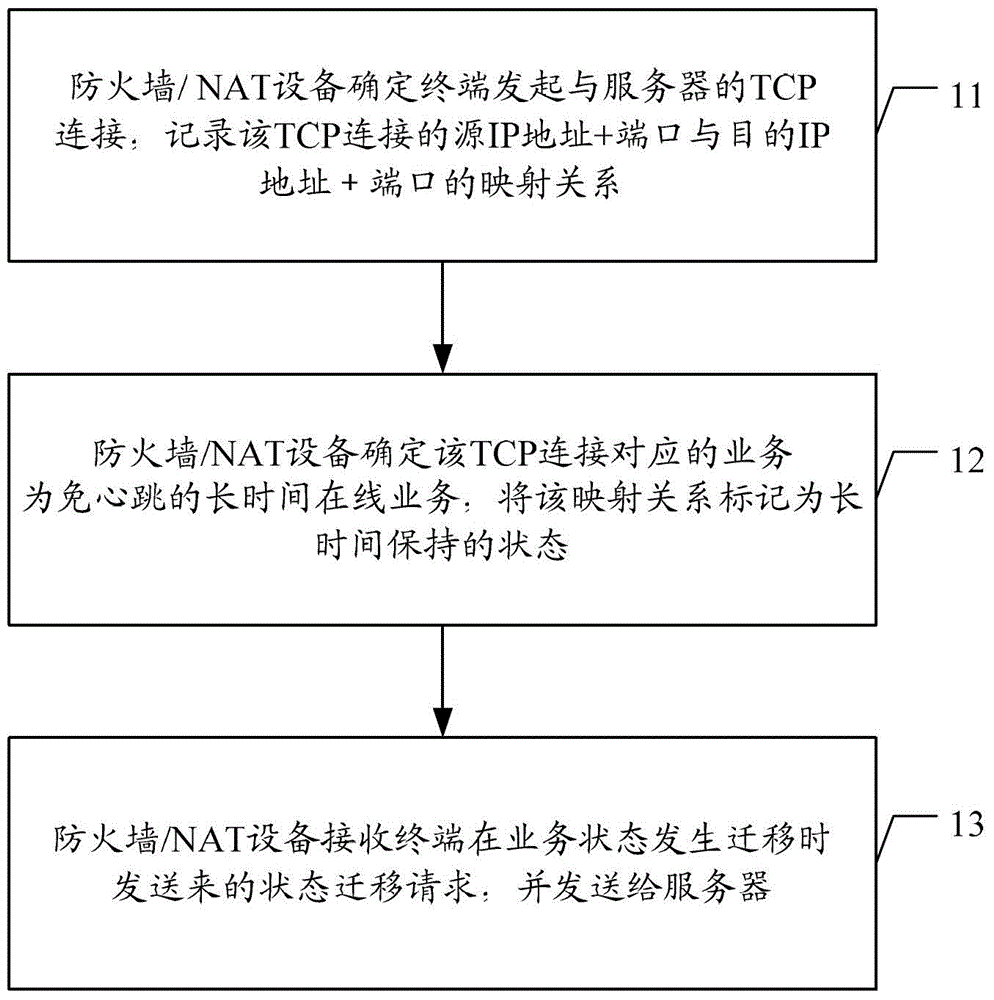
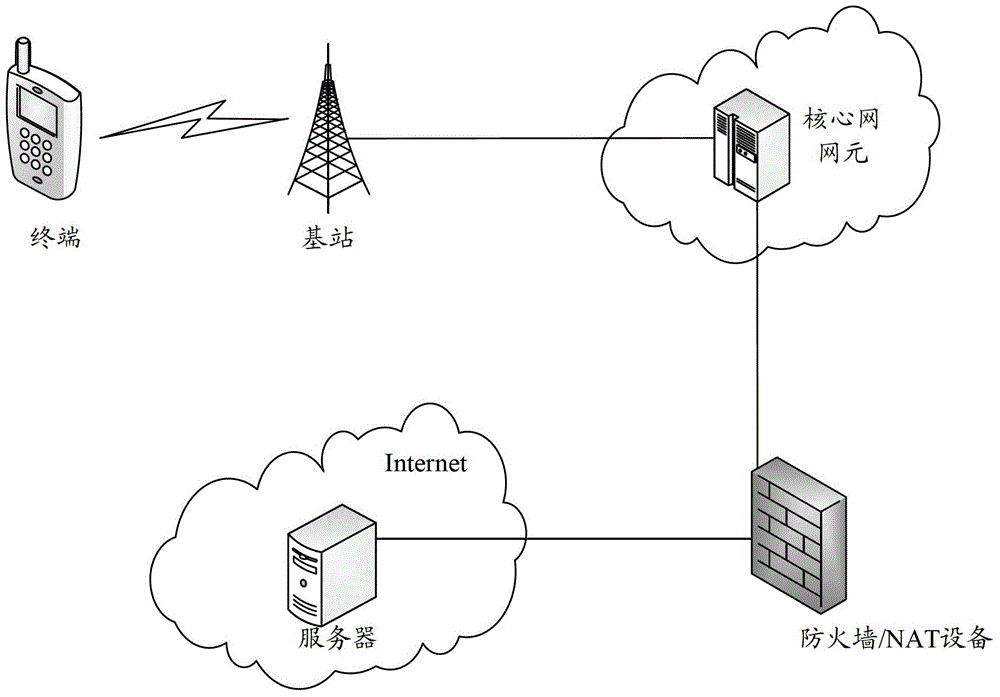
Heartbeat-free method and device for long-term online service
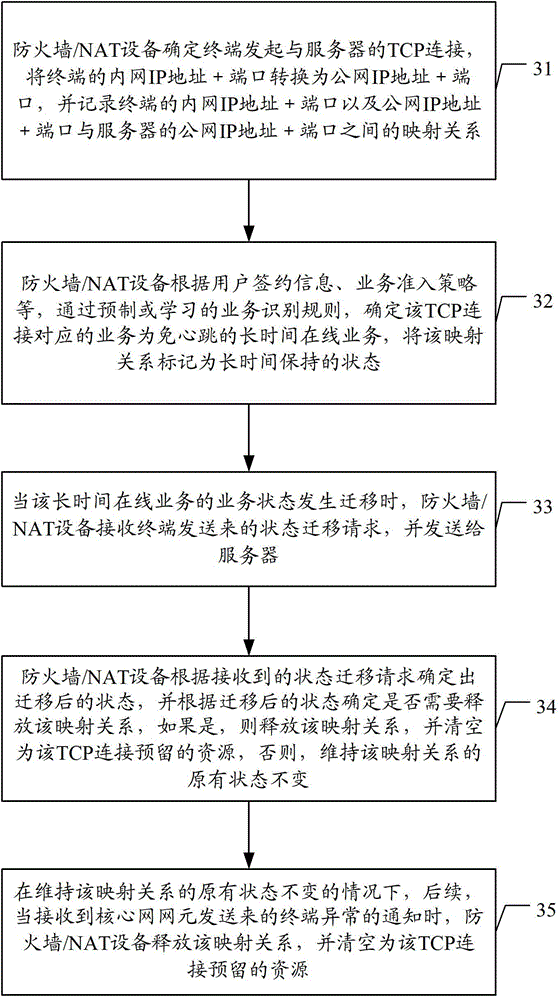
ActiveCN104427598AGuaranteed connectivityReduce consumptionPower managementTransmissionIp addressNetwork address translation
The invention discloses a heartbeat-free method and device for long-term online service. The method comprises the following steps: determining, by a firewall / NAT (Network Address Translation) equipment, that a terminal initiates TCP (Transmission Control Protocol) connection with a server, and recording mapping relation of an IP (Internet Protocol) address as well as a port and a destination IP address as well as a port connected by the TCP; determining, by the firewall / NAT equipment, that the service corresponding to the TCP connection is heartbeat-free long-term online service, marking the mapping relation to be a long-term hold state; receiving, by the firewall / NAT equipment, a state migration request transmitted when the terminal migrates in a service state, and transmitting to the server. By applying the scheme, the power consumption of the terminal can be reduced, the occupation of a wireless channel resource and the consumption of processing resources of the equipment are reduced and the like.
Owner:CHINA MOBILE COMM GRP CO LTD
Method for mobile ipv6 data traversing state firewall
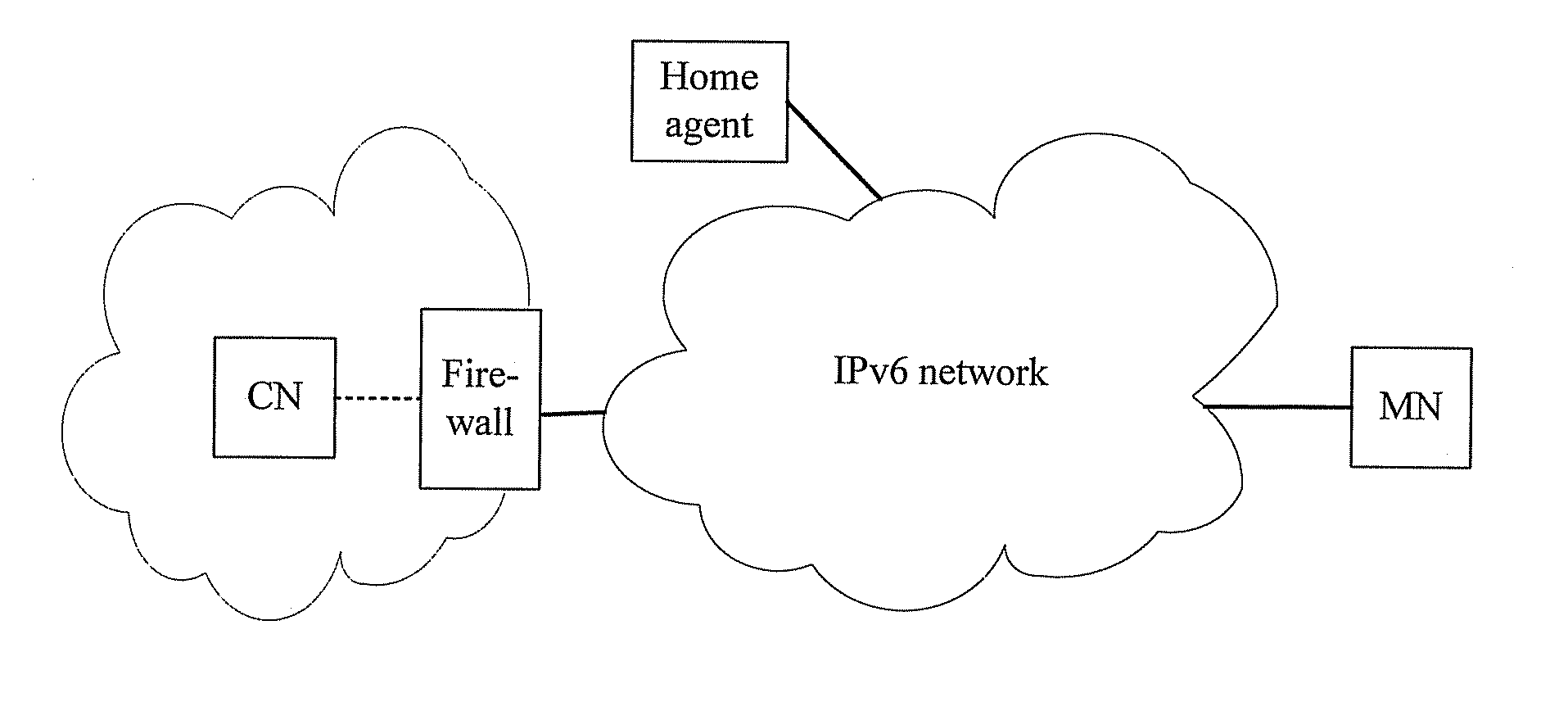
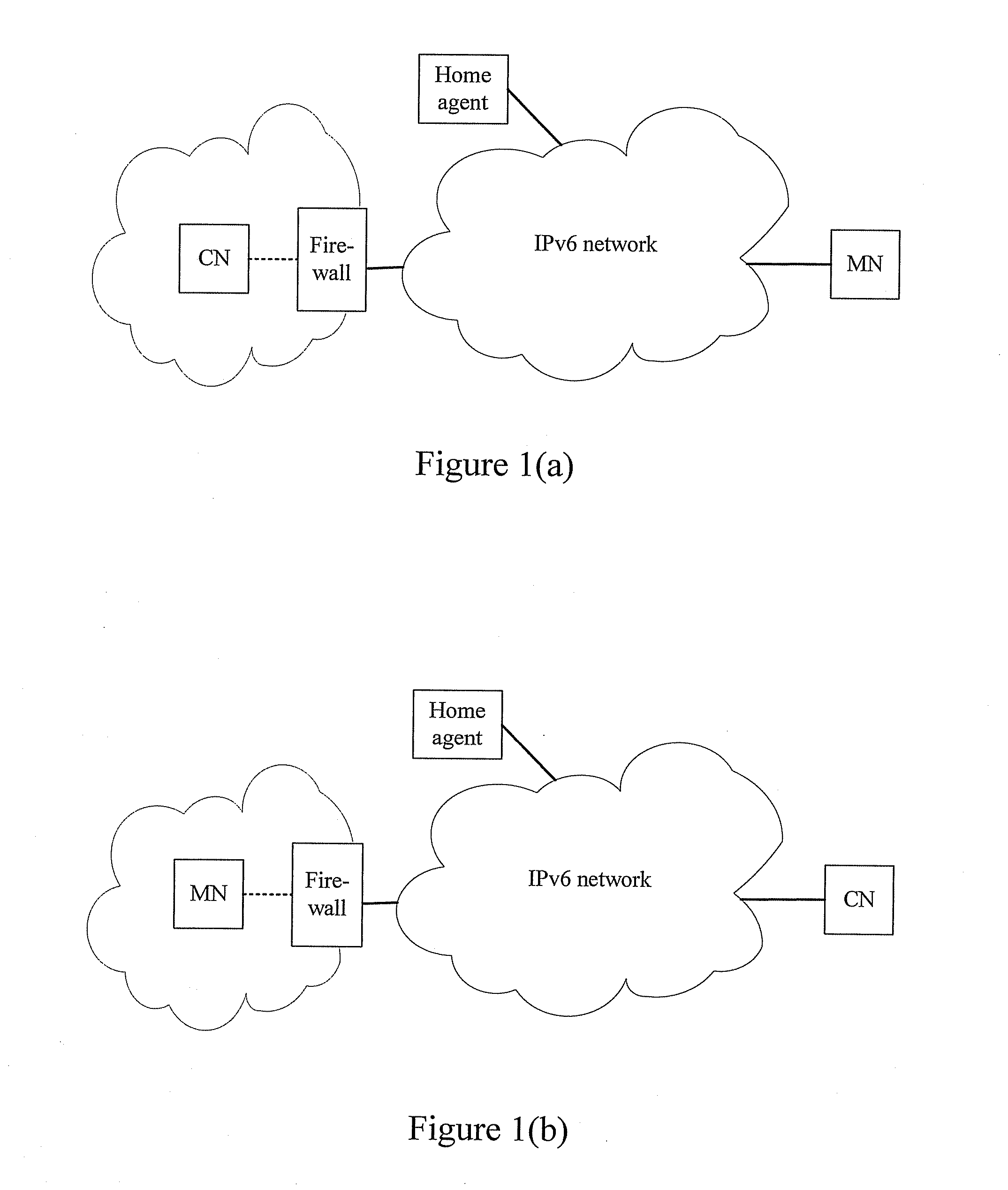
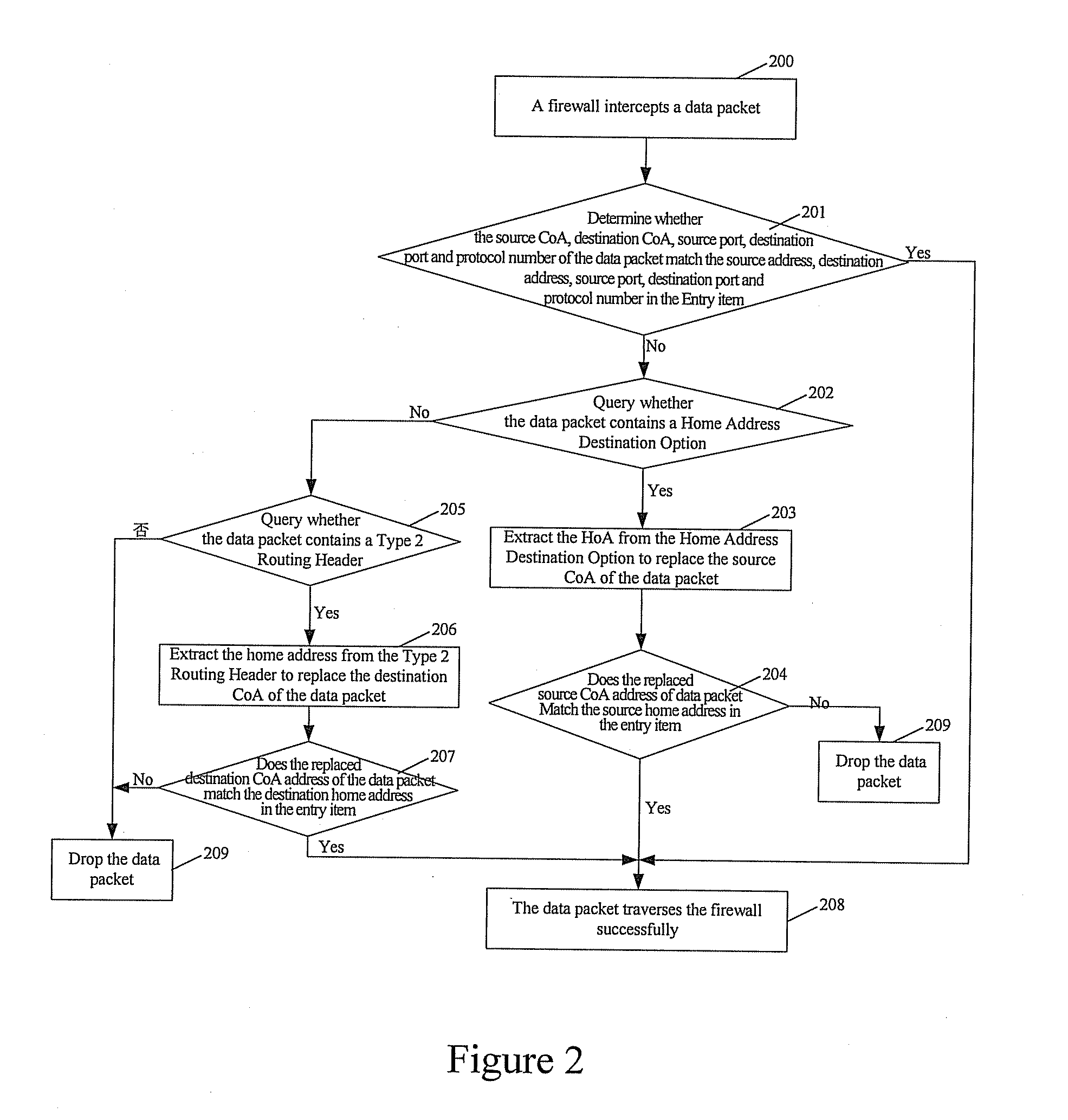
ActiveUS20080056252A1Reduce processing timeHigh data efficiencyData switching by path configurationMultiple digital computer combinationsComputer networkIPv6
A method for mobile IPv6 data traversing a state firewall includes: creating an entry item of a firewall including a source HoA, a source CoA, a destination HoA, a destination CoA, a source port, a destination port and a protocol number; matching the source CoA, destination CoA, source port, destination port and protocol number of the data packet with those in the entry item; if unsuccessful, matching the source HoA or CoA, destination CoA or HoA, source port, destination port and protocol number of the data packet with those in the entry item; if successful, replacing the source CoA or destination CoA in the entry item by those of the data packet, and allowing the data packet to traverse the firewall, which improves the efficiency of a data packet traversing a firewall and guarantees that the data packet passing the filtering of firewall is able to traverse the firewall normally.
Owner:HUAWEI TECH CO LTD
Stateful and cross-protocol intrusion detection for voice over IP
A method for detecting intrusions that employ messages of two or more protocols is disclosed. Such intrusions might occur in Voice over Internet Protocol (VoIP) systems, as well as in systems in which two or more protocols support some service other than VoIP. In the illustrative embodiment of the present invention, a stateful intrusion-detection system is capable of employing rules that have cross-protocol pre-conditions. The illustrative embodiment can use such rules to recognize a variety of VoIP-based intrusion attempts, such as call hijacking, BYE attacks, etc. In addition, the illustrative embodiment is capable of using such rules to recognize other kinds of intrusion attempts in which two or more protocols support a service other than VoIP. The illustrative embodiment also comprises a stateful firewall that is capable of employing rules with cross-protocol pre-conditions.
Owner:PURDUE RES FOUND INC
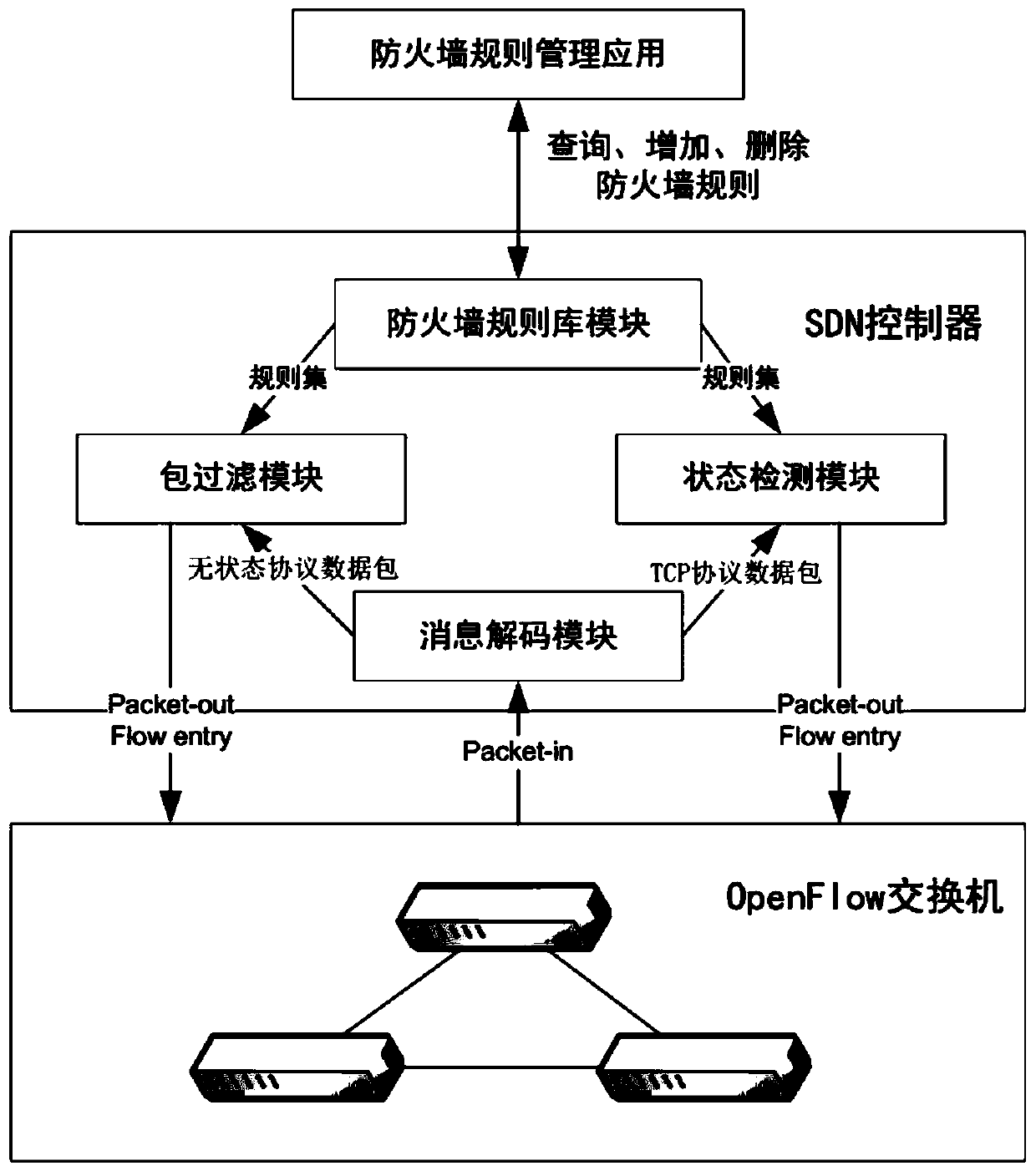
Implementation method of software-defined firewall system
ActiveCN110381025AReduce computationImprove versatilityTransmissionConnection tableComputer network technology
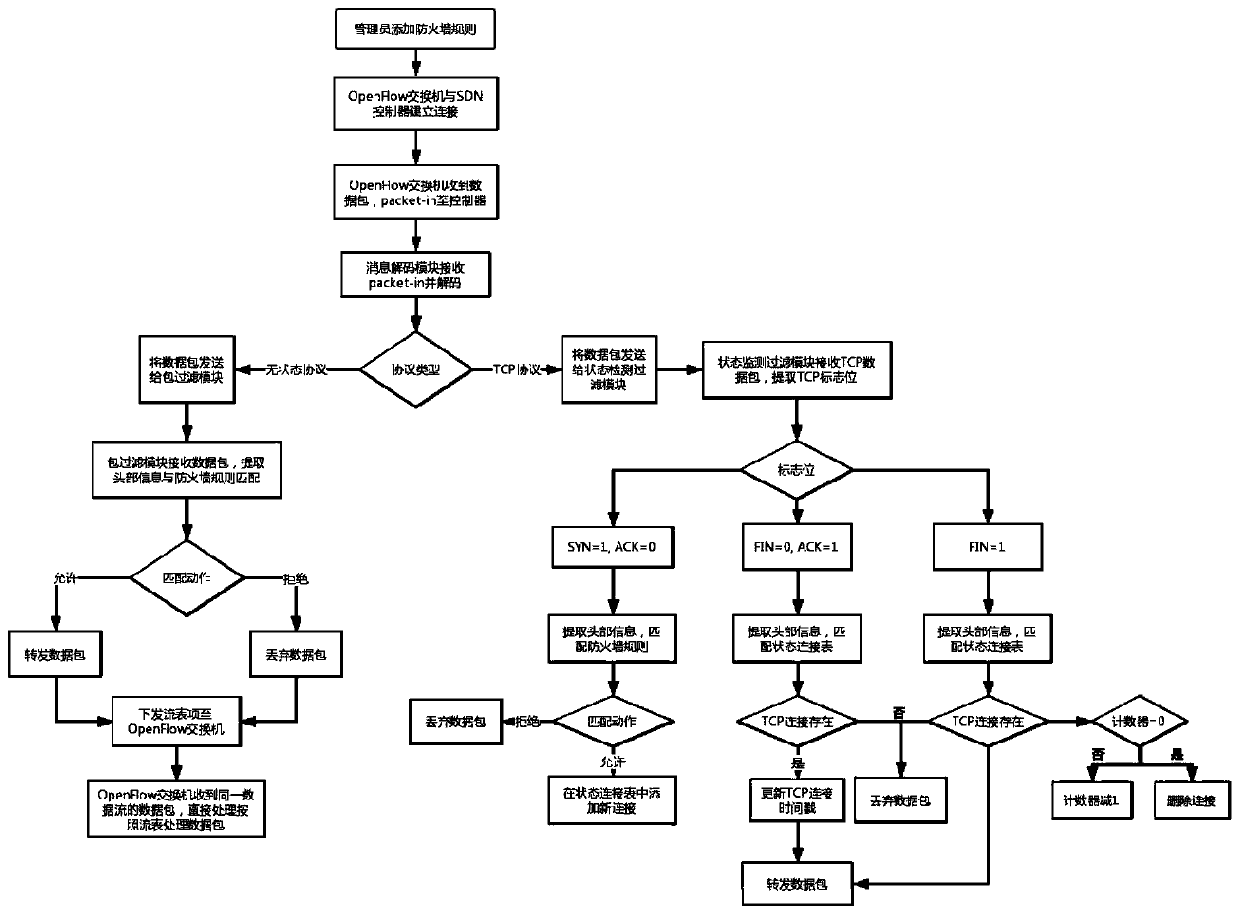
The invention discloses an implementation method of a software-defined firewall system, which belongs to the technical field of computer networks. The method comprises the following steps: establishing connection between an OpenFlow switch and an SDN controller, and receiving a table-miss flow table entry and an initial flow table entry; sending the data packet by the OpenFlow switch to the SDN controller; performing state detection filtering on the TCP data packet by a state detection filtering module in the SDN controller through combinations with the firewall rule and the state of the datapacket, and maintaining a state connection table; and performing packet filtering on the stateless IP protocol data packet by a packet filtering module in the SDN controller according to a firewall rule, and issuing a flow table entry to the OpenFlow switch to guide subsequent data packet processing. According to the method, stateless packet filtering and stateful state detection filtering can berespectively carried out on data packets of different protocol types, the state firewall function is achieved, the operand of the SDN controller is reduced by issuing the flow table item in the packetfiltering process, in addition, an OpenFlow protocol does not need to be modified when state detection filtering is achieved, and higher universality is achieved.
Owner:ZHEJIANG UNIV
Connectivity over stateful firewalls
InactiveUS8332532B2Easy to implementMultiple digital computer combinationsTransmissionTelecommunicationsRaw socket
A method for establishing a TCP connection between two client terminals protected by stateful firewalls and comprising means for sending messages to each other via a messaging server. The client terminals agree on establishing a mutual TCP connection by sending a message, which indicates port numbers to be used on said connection. A TCP connection establishment procedure is started in both client terminals. After sending a first handshake message, a message indicating a sequence number of the first handshake message is sent from both client terminals to each other. When the firewalls of the opposite client terminals reject the first handshake message, an acknowledgement message to the first handshake message is created in both client terminals using a raw socket, which acknowledgement message includes the received sequence number as an acknowledgement number. Finally, the raw socket based acknowledgement message is sent to the opposite client terminal for completing the establishment of the TCP connection.
Owner:TELIASONERA
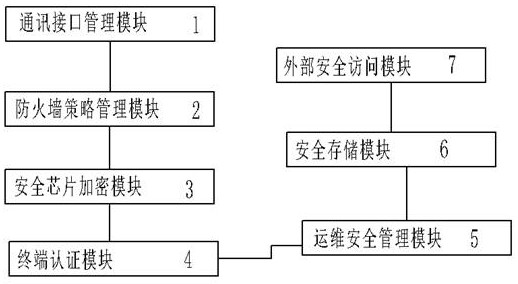
Edge internet-of-things proxy basic service security management system
PendingCN114726576AStrengthen the security effect of basic servicesImprove securitySecuring communicationCommunication interfaceData terminal
The invention relates to an edge internet-of-things proxy basic service security management system, which comprises a communication interface management module used for controlling the start and stop states of various communication interfaces and monitoring the communication states of the various communication interfaces in real time; the firewall strategy management module is used for monitoring the state of the firewall in real time and controlling the start-stop state of the firewall; the security chip encryption module is used for encrypting transmission data and storage data; the terminal authentication module is used for carrying out identity authentication and authorized access on the terminal equipment in a remote user dialing authentication mode; the operation and maintenance safety management module is used for being connected with an operation and maintenance terminal through a CONSOLE interface, wherein the operation and maintenance terminal is authenticated in a remote user dial-up authentication mode and then is accessed to an upper-layer internet-of-things operation center; the secure storage module is used for encrypting and storing the database data; and the external security access module is used for connecting the upper layer Internet of Things operation center and the message bus to realize subscription and forwarding of the theme data.
Owner:SHANDONG LUNENG SOFTWARE TECH
Securely virtualizating network services
ActiveUS8949965B2Multiplex system selection arrangementsMultiple digital computer combinationsVirtualizationNetwork service
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and device for realizing high-performance state firewall
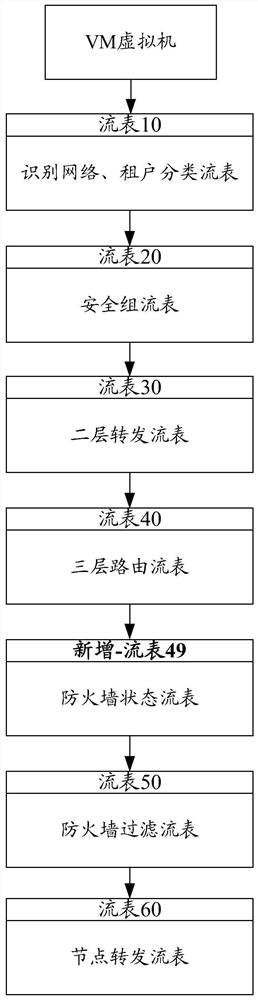
PendingCN113765858AImprove throughputImprove the ability to process packetsData switching networksData packData stream
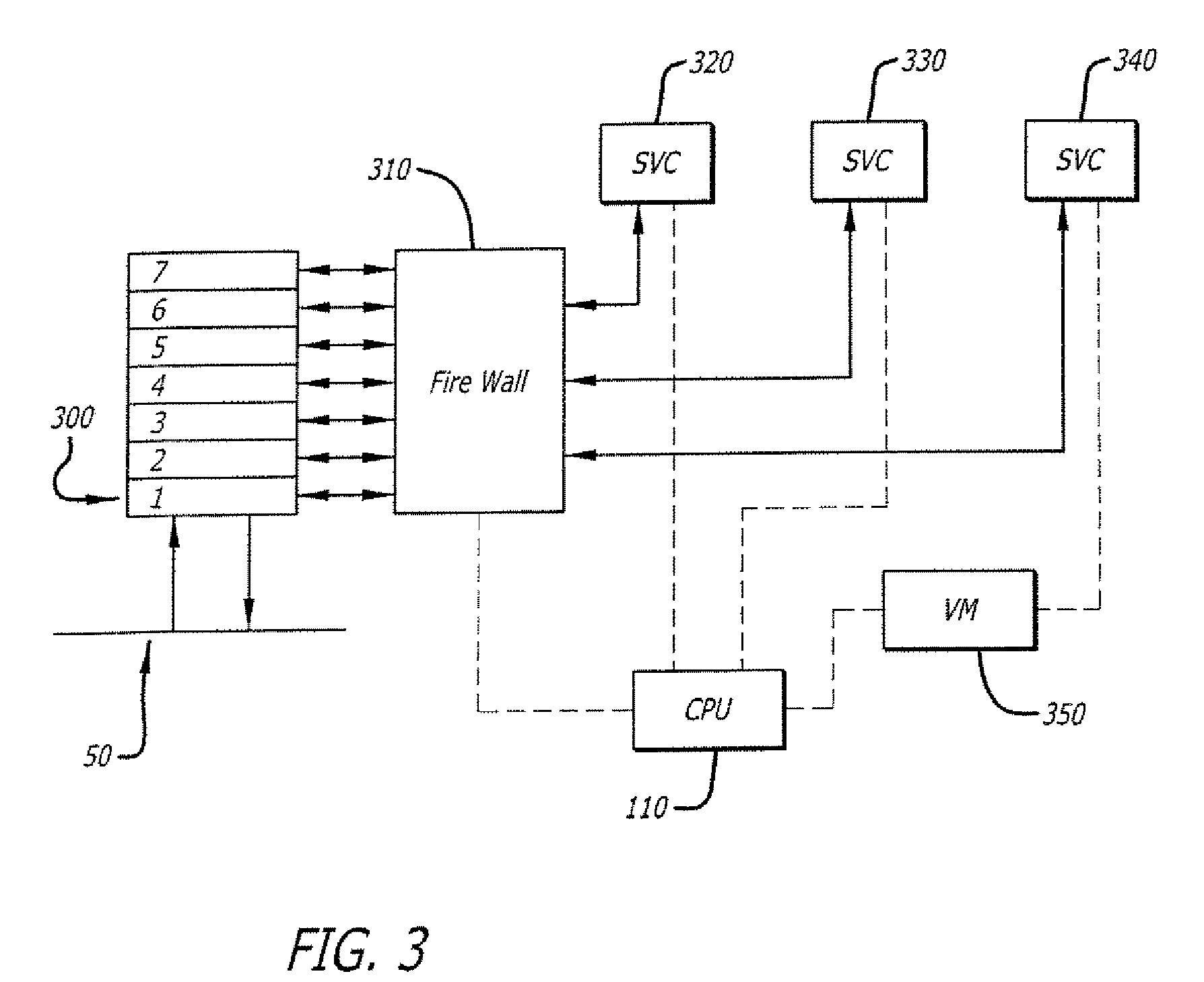
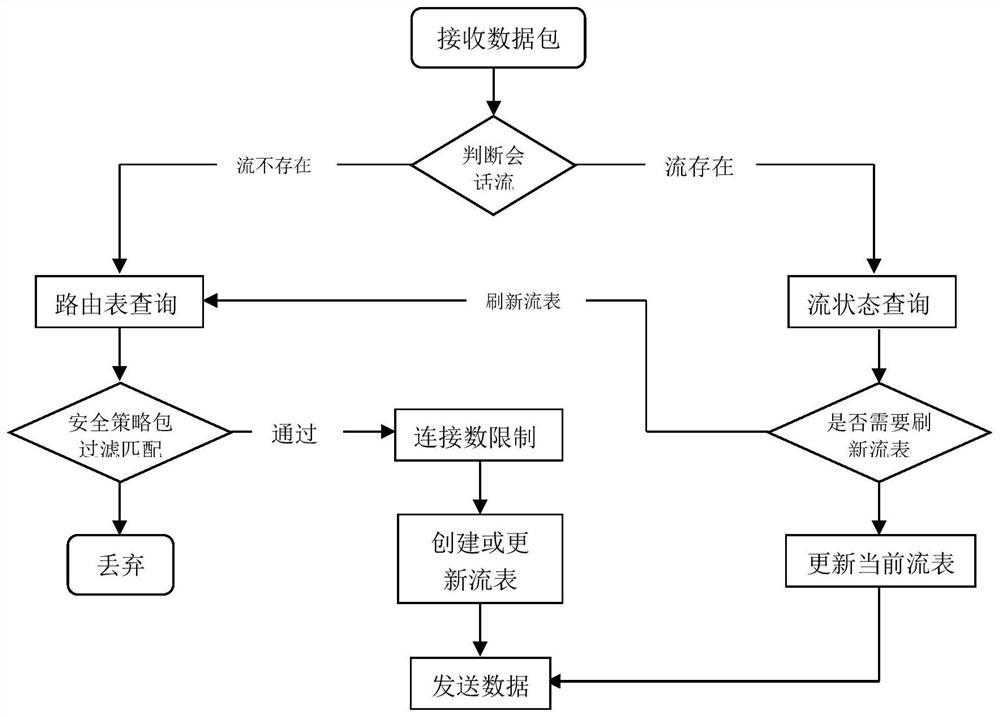
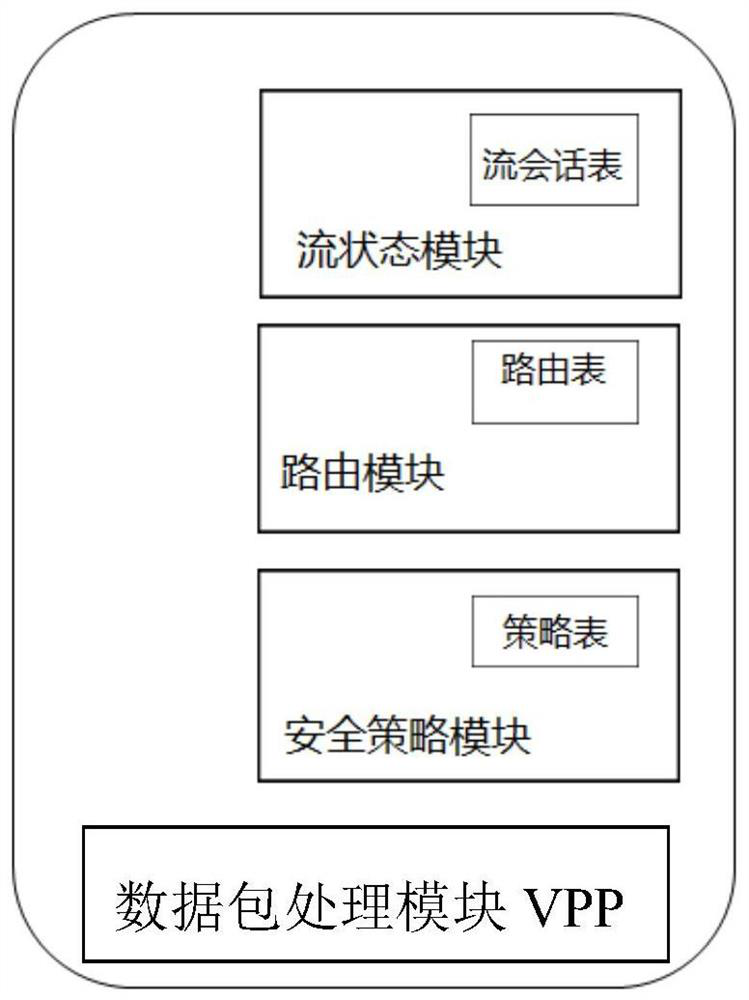
The invention provides a method and a device for realizing a high-performance state firewall. The device comprises a data packet processing module VPP, a routing module, a firewall policy module and a flow state module. The data packet processing module (VPP) is configured to receive transmission data from a network interface. And the routing module queries routing information and forwards data. And the firewall policy module is used for matching a firewall policy issued by a user, and performing security policy matching on the data flow of the session established for the first time according to an IP address, a protocol and a port number. And the flow state module is used for creating a flow session for the data flow successfully passing through the firewall policy, carrying out flow state detection on the flow in which the session is established, refreshing the flow table when the firewall policy is changed and the route is changed, periodically checking the flow table, and deleting the flow of which the state is not updated in a life cycle from the flow table. By reducing the repeated query matching of the firewall security policy table and the query of the routing table, the data packet processing capability of the VPP is improved, the throughput rate of the firewall is improved, and the data forwarding performance of the firewall is effectively improved.
Owner:中创为(成都)量子通信技术有限公司
Implementation method and device of a cloud computing stateful firewall
Owner:CHINA MOBILE SUZHOU SOFTWARE TECH CO LTD +1
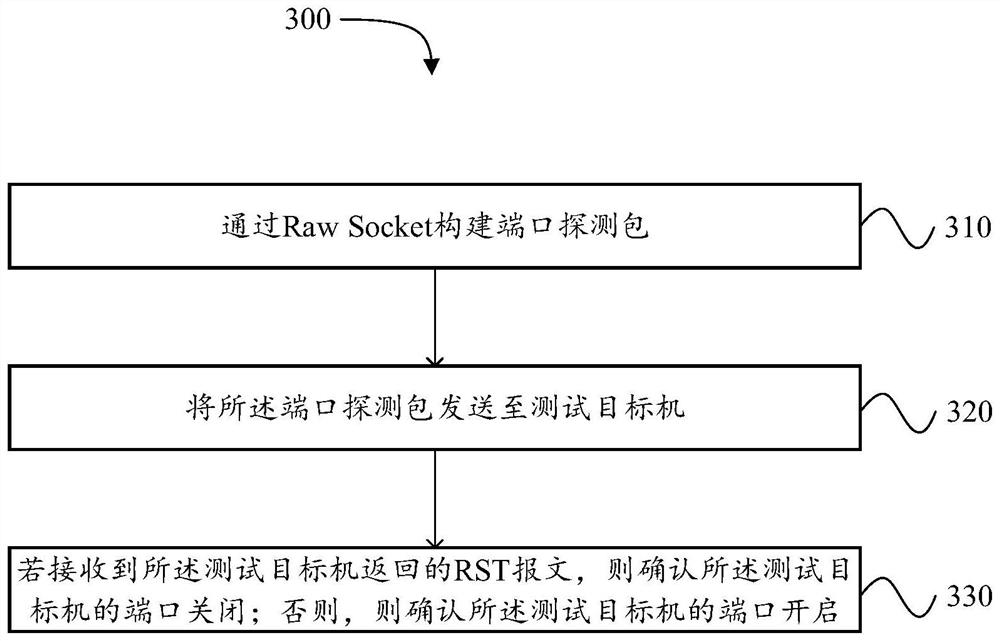
Raw Socket-based port detection method and device
The embodiment of the invention provides a port detection method and device based on Raw Socket. The method comprises the following steps: constructing a port detection packet through Raw Socket; sending the port detection packet to a test target machine; if the RST message returned by the test target machine is received, confirming that the port of the test target machine is closed; and otherwise, confirming that the port of the test target machine is opened. In this way, the Raw Socket message can be utilized to bypass port detection of the stateless firewall / IDS system so as to prevent the scanning machine from being blocked as much as possible.
Owner:北京华云安信息技术有限公司
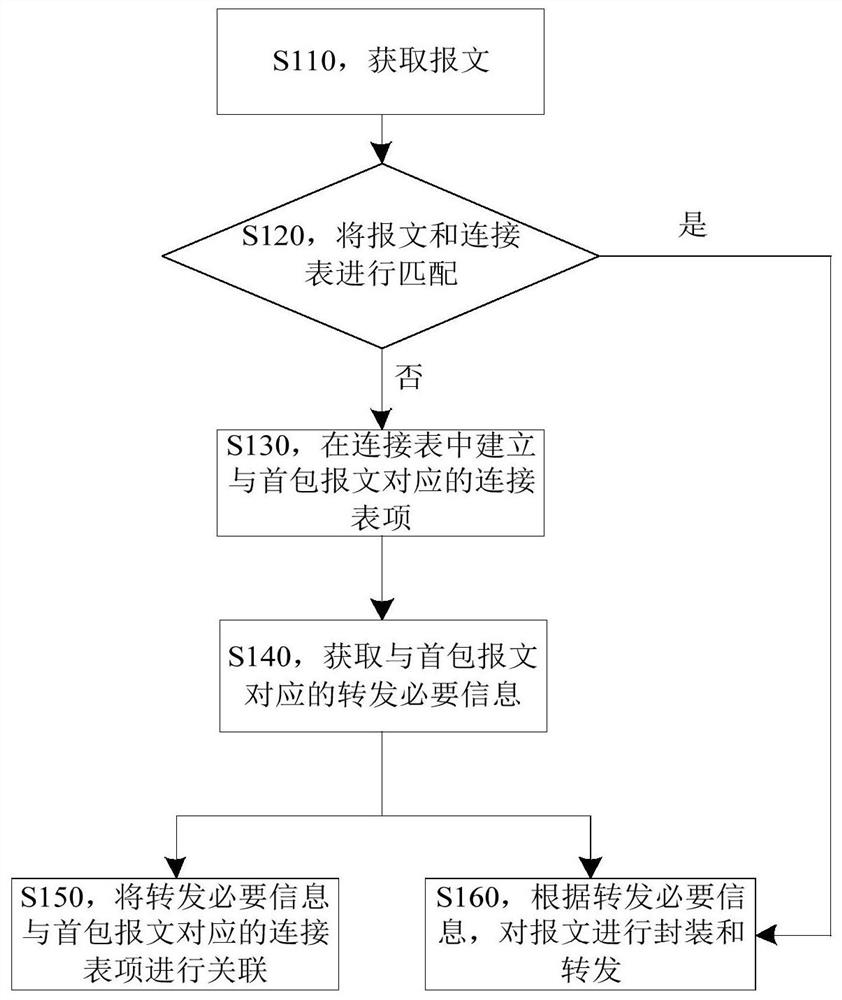
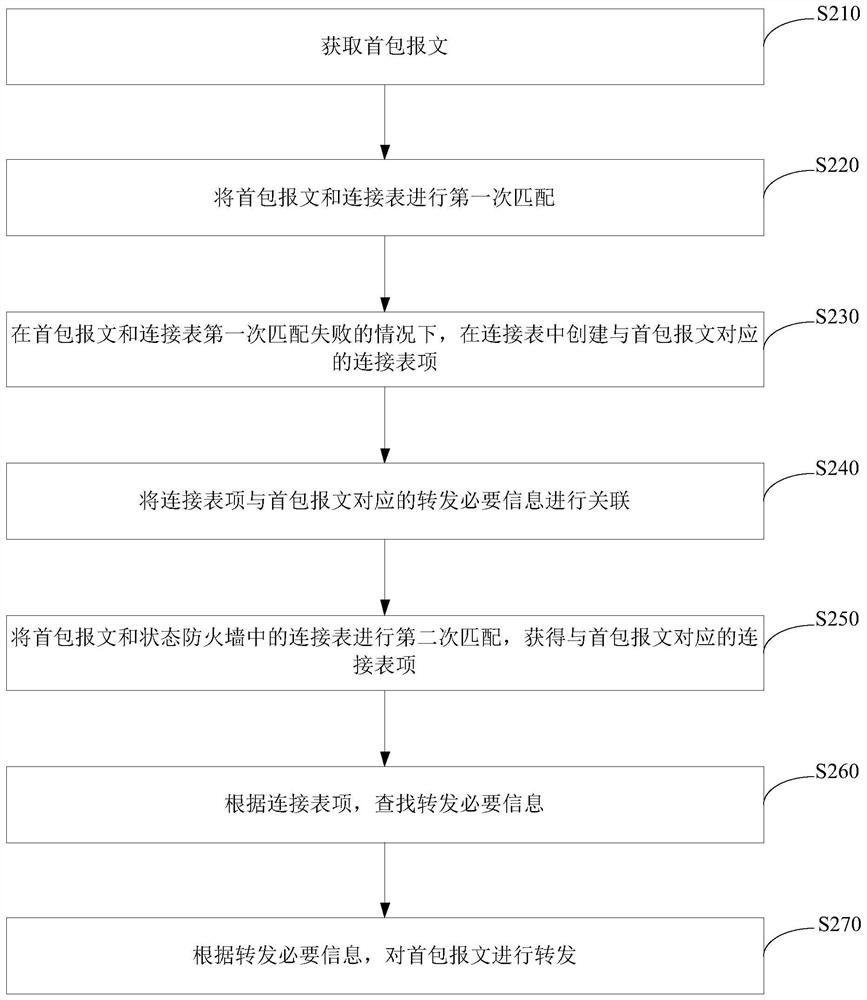
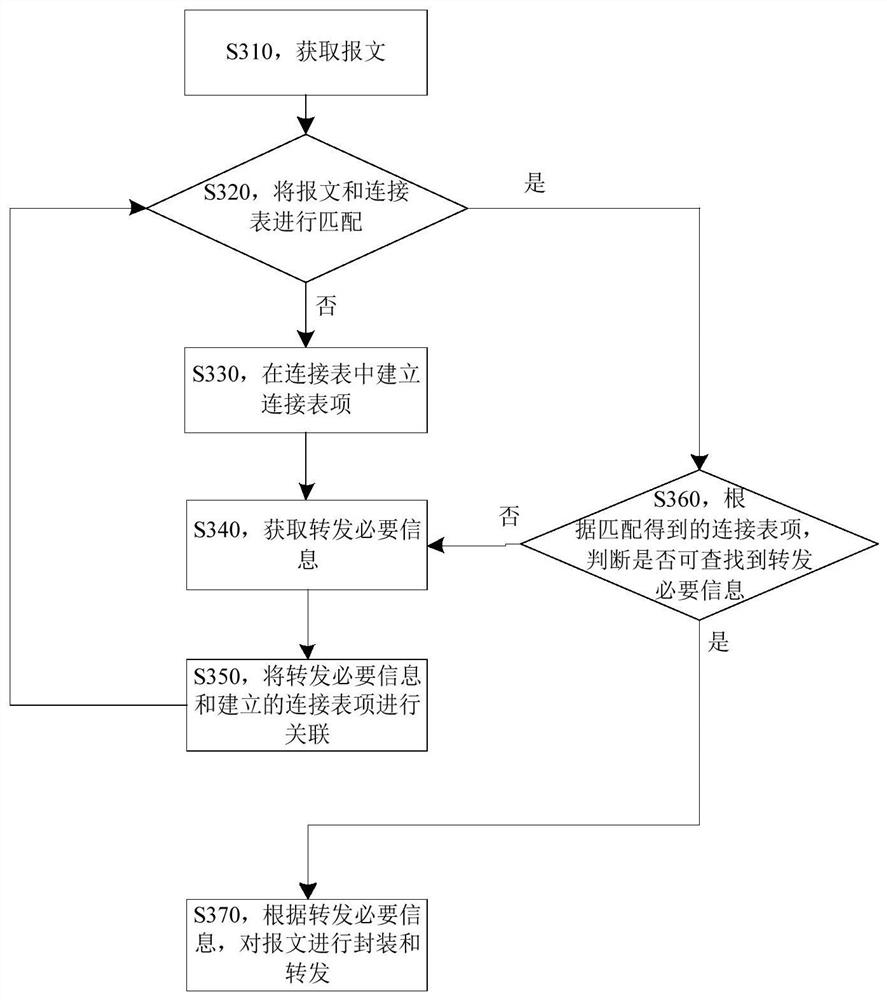
Message forwarding method and device for state firewall
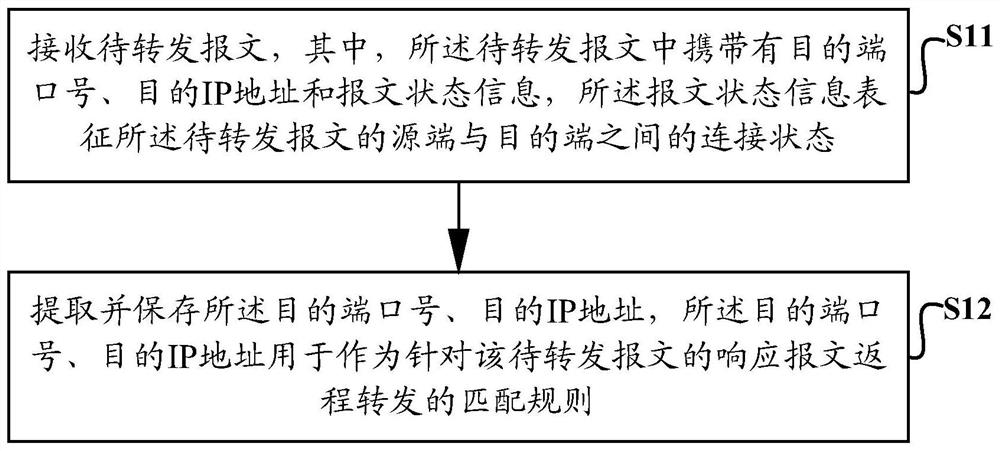
The embodiment of the invention provides a message forwarding method and device for a state firewall. The message forwarding method comprises the following steps: acquiring a first packet message; matching the first packet message with a connection table in a state firewall for the second time to obtain a connection table item corresponding to the first packet message, the connection table item comprising a connection table item, the connection table item being associated with forwarding necessary information corresponding to the first packet message, and the connection table item being established when the first matching of the first packet message fails; searching and forwarding necessary information according to the connection table entry; and forwarding the first packet message according to the forwarding necessary information. By means of the technical scheme, verification of the connection table can be achieved, it is ensured that subsequent non-first-packet messages can inquirecorresponding necessary forwarding information according to the connection table, and then the problem that the stability of the state firewall is poor is solved.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Routing device having integrated MPLS-aware firewall
An MPLS-aware firewall allows firewall security policies to be applied to MPLS traffic. The firewall, which may be integrated within a routing device, can be configured into multiple virtual security systems. The routing device provides a user interface by which a user specifies one or more zones to be recognized by the integrated firewall when applying stateful firewall services to the packets. The user interface allows the user to define different zones and policies for different ones of the virtual security systems. In addition, the user interface supports a syntax that allows the user to define the zones for the firewall by specifying the customer VPNs as interfaces associated with the zones. The routing device generates mapping information for the integrated firewall to map the customer VPNs to specific MPLS labels for the MPLS tunnels carrying the customer's traffic.
Owner:JUMIPER NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com