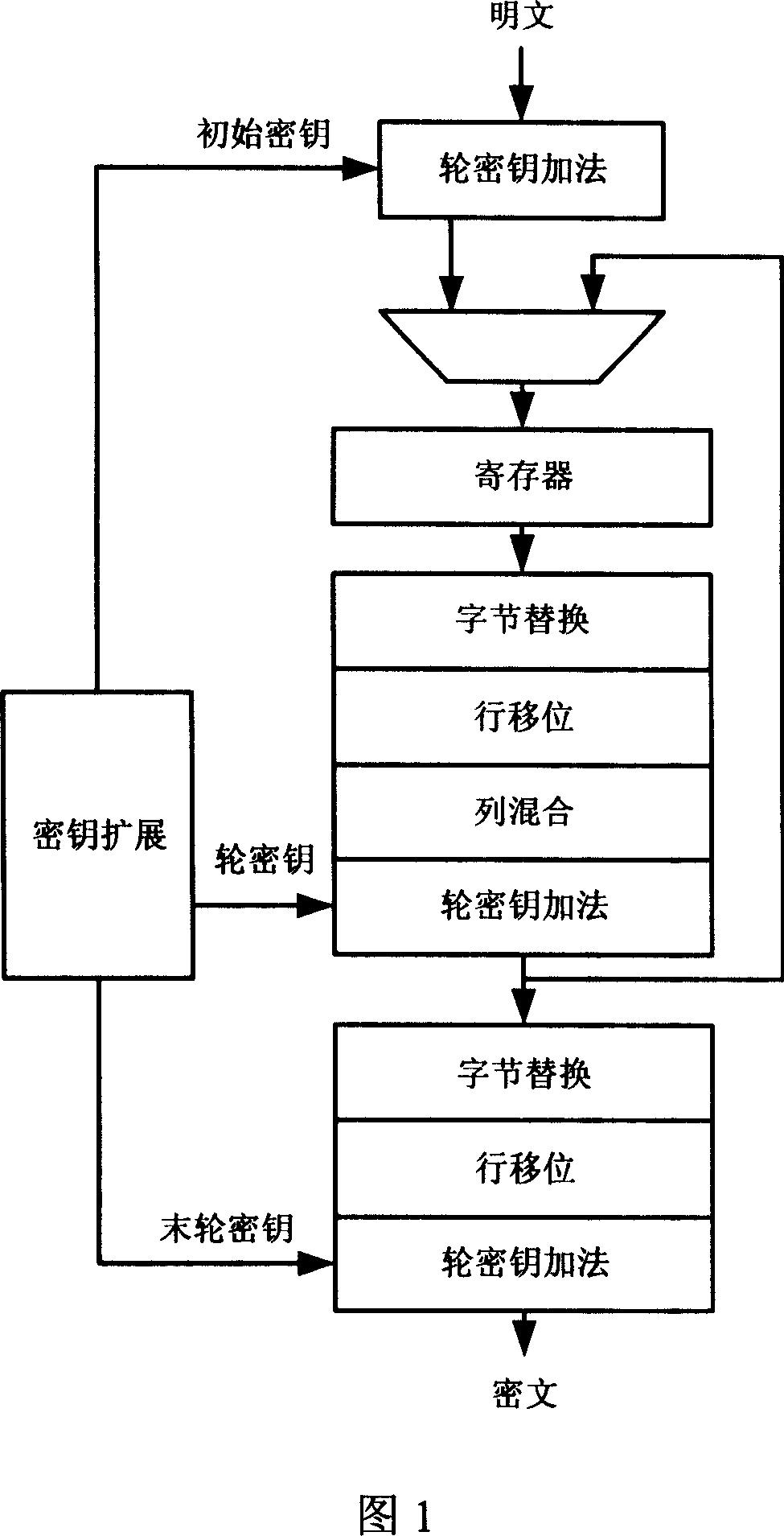
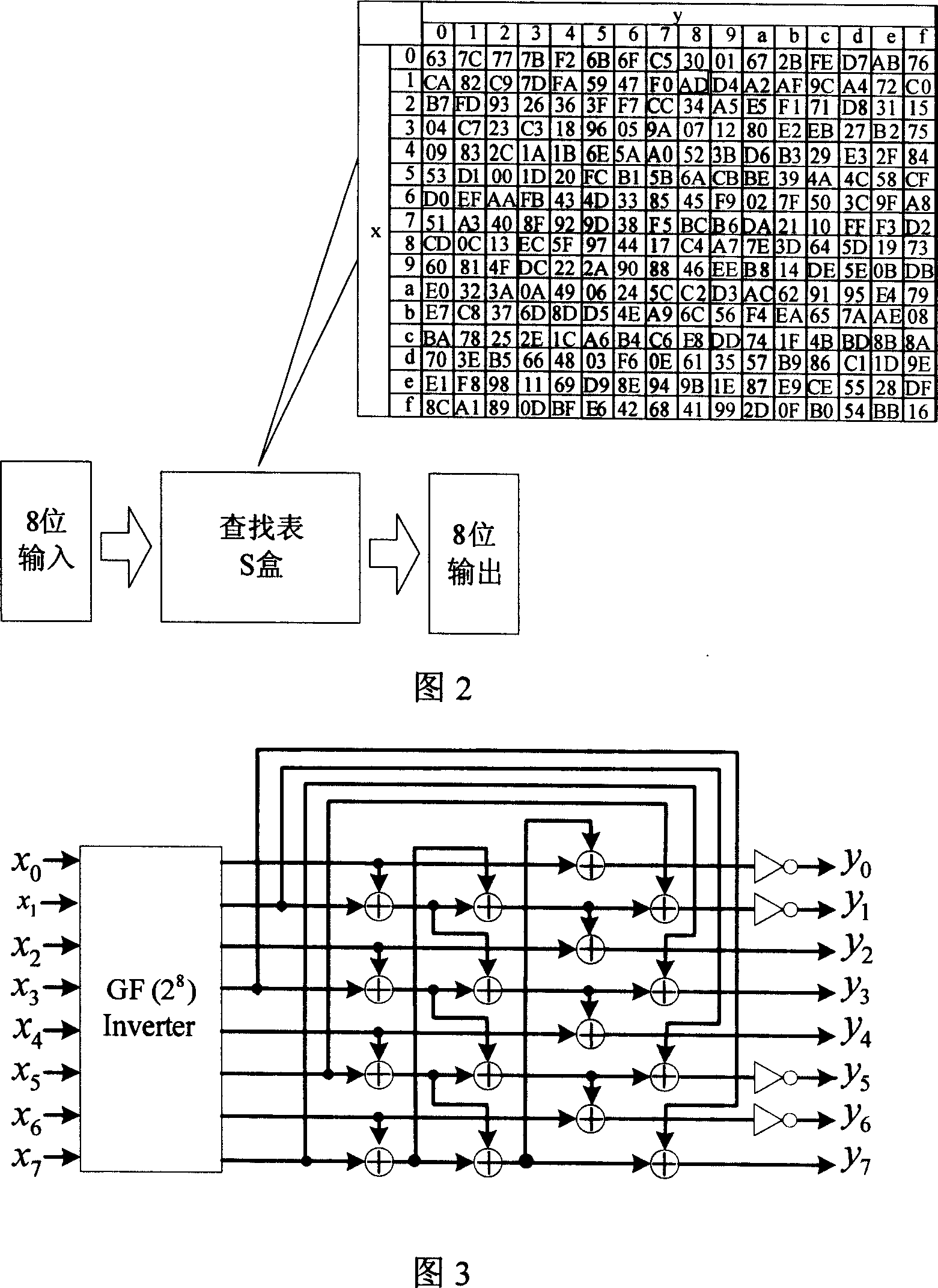
A byte replacement circuit for power consumption attack prevention
A byte replacement and anti-power consumption technology, applied in electrical components, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as high cost, increased hardware implementation cost, and cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
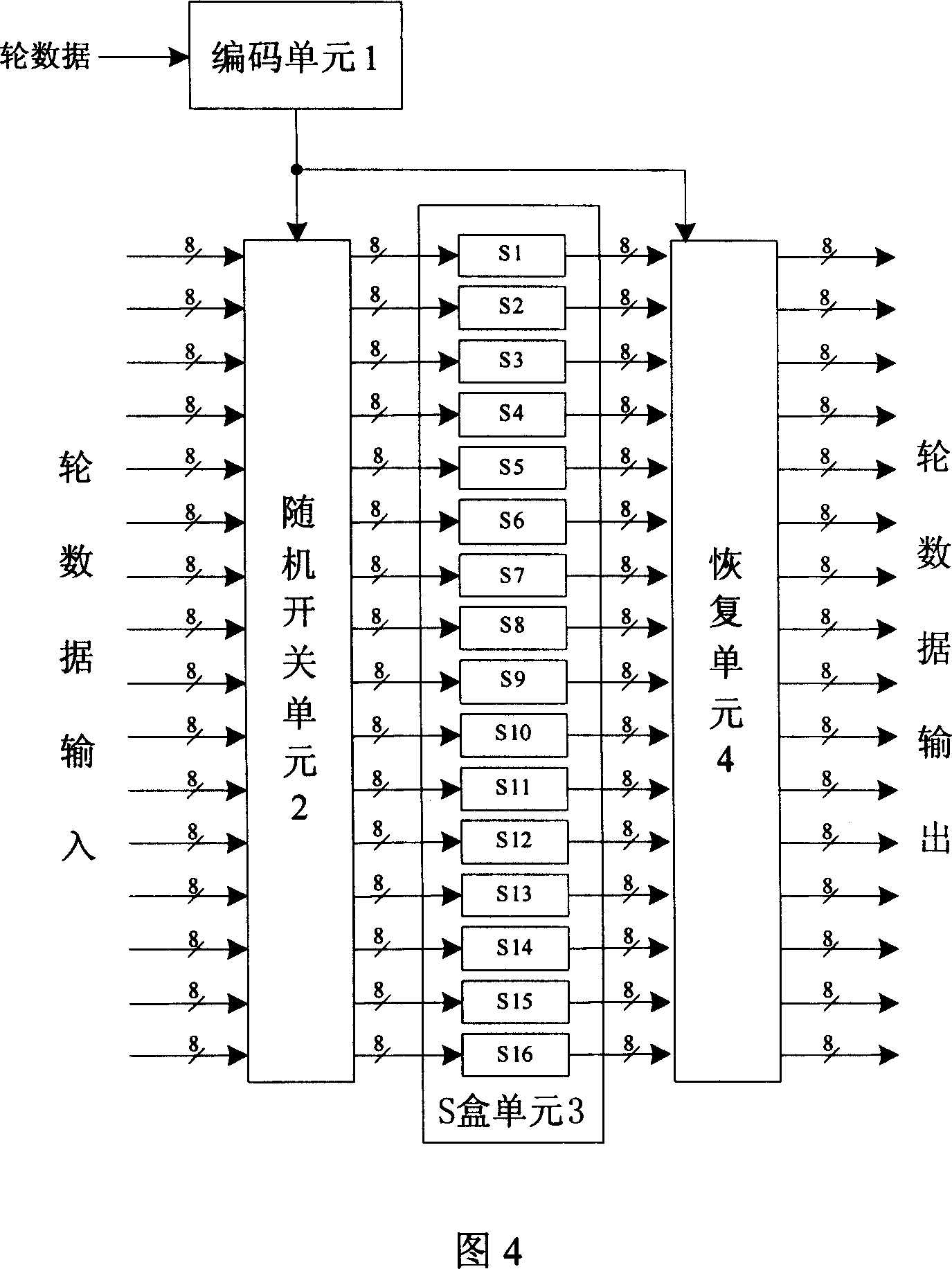
[0041] As shown in Figure 5, the encoding unit 1 selects the lower 16 bits of the round data and adds them bit by bit to obtain a random number output. S-boxes S1-S16 adopt the five S-box structures and arrangement sequences shown in Figure 6 above. As mentioned above, when the random number output by the encoding unit 1 is 4, the first group of 8-bit data is input to the random switch unit 2, shifted to the right by 4 times and enters S5, and enters the recovery unit 4 after completing the byte replacement transformation, and then circulates Shift left 4 times, restore to the 8bit data processed by the first group. Similarly, the 2nd group, the 3rd group, ..., the 16th group of input data will be operated in a similar process. At this time, the encoding unit 1 is an adder structure, the random switch unit 2 is a 17-input and 16-output circular right-shift structure, and the recovery unit 4 is a 17-input and 16-output circular left-shift structure.
[0042] Compared with the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com