Network security method based on wireless firewall
A network security and firewall technology, applied in wireless communications, security devices, electrical components, etc., can solve the problems of not reaching the perfect state, not reaching the perfect level, etc., to improve the ability to resist hacker attacks, improve usability, and enhance usability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
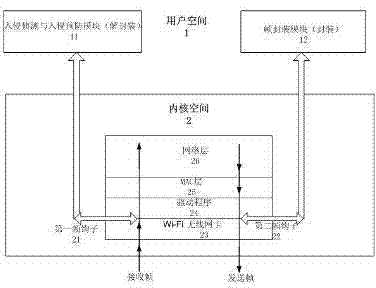
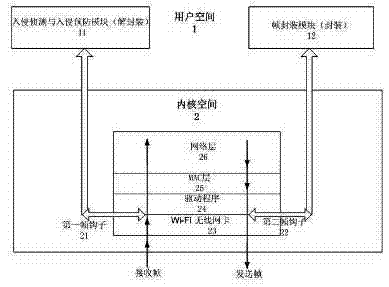
[0011] It is realized through a wireless firewall, mainly using wireless network intrusion detection and prevention technology. The wireless firewall function acts on the second layer of OSI, that is, MAC layer 25 (MAC layer is the data connection layer, OSI includes Wi-Fi wireless network card 23, driver program 24, MAC layer 25, network layer 26 and layers above the network layer), A new type of wireless firewall architecture, such as figure 1 As shown, the wireless firewall includes an intrusion detection and intrusion prevention module 11, a first frame hook (Frame Hook) 21 and a second frame hook 22, the intrusion detection and intrusion prevention module 11 is located in the user space 1 of the system, and the first frame hook 21 Connect the kernel space 2 (Kernel Space) of the operating system and the user space (User Space) 1, one end of the first frame hook 21 is in the wireless network card driver 24 of the operating system kernel space 2, and the other end of the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com