Patents
Literature
126 results about "Open Systems Interconnection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
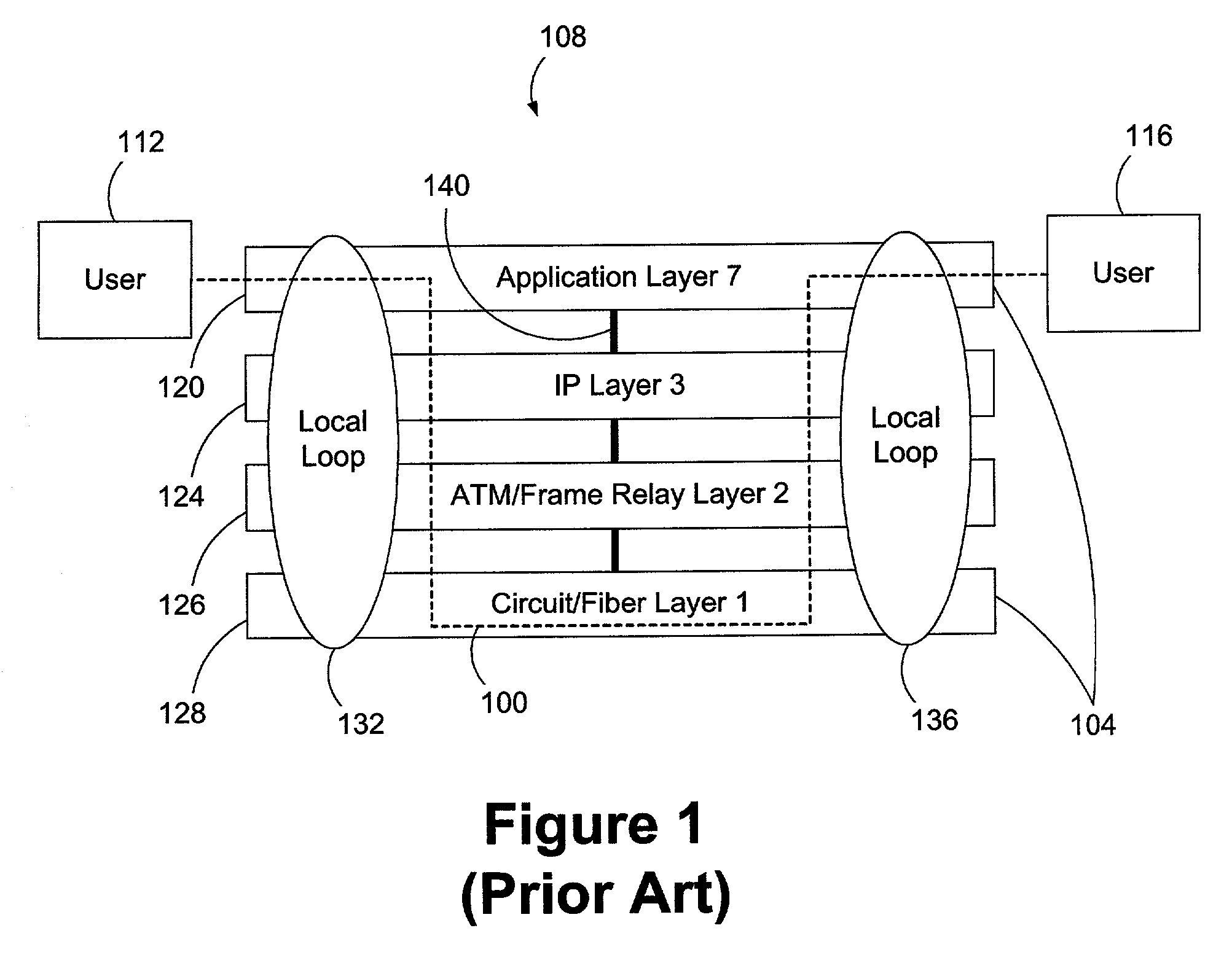
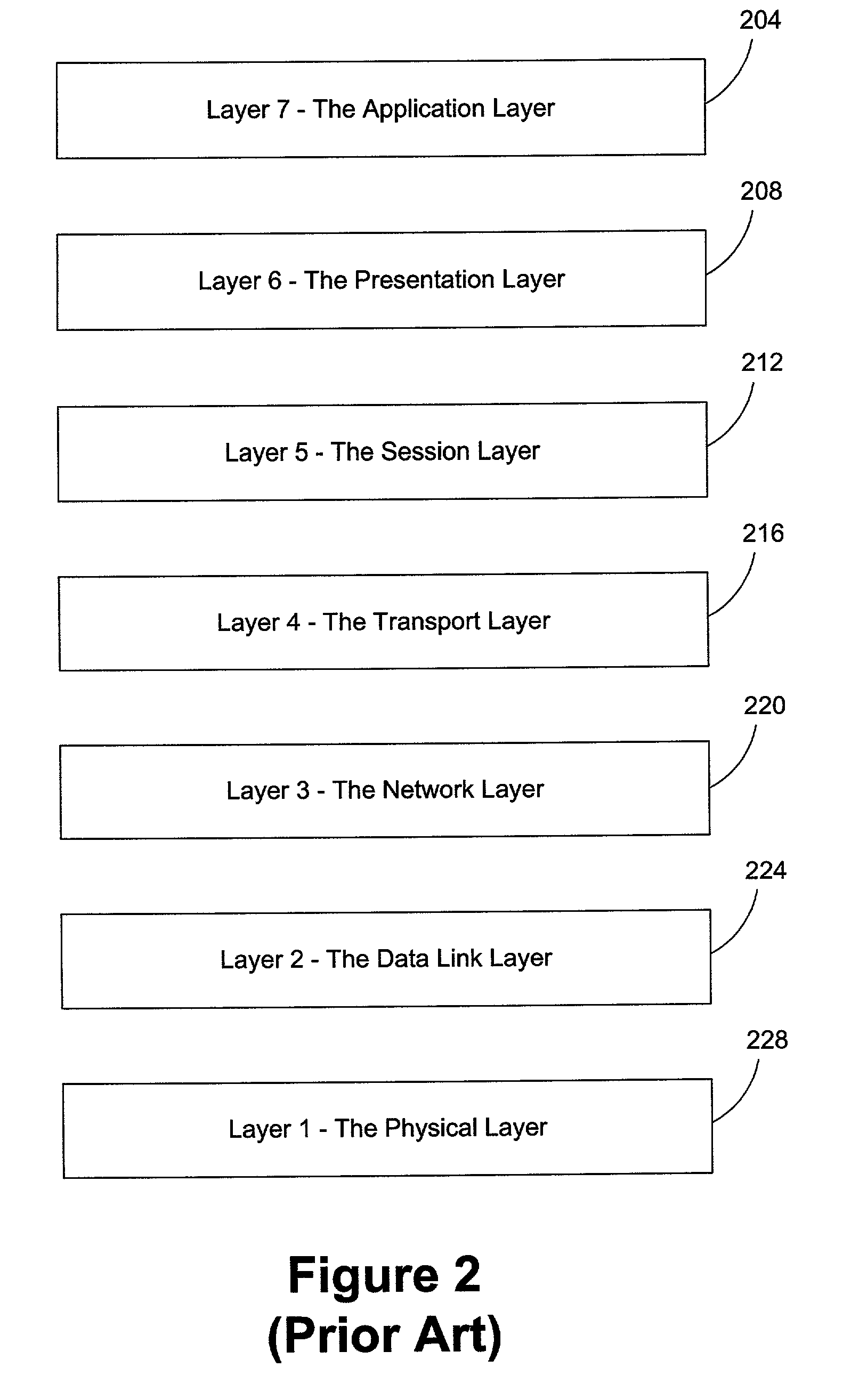
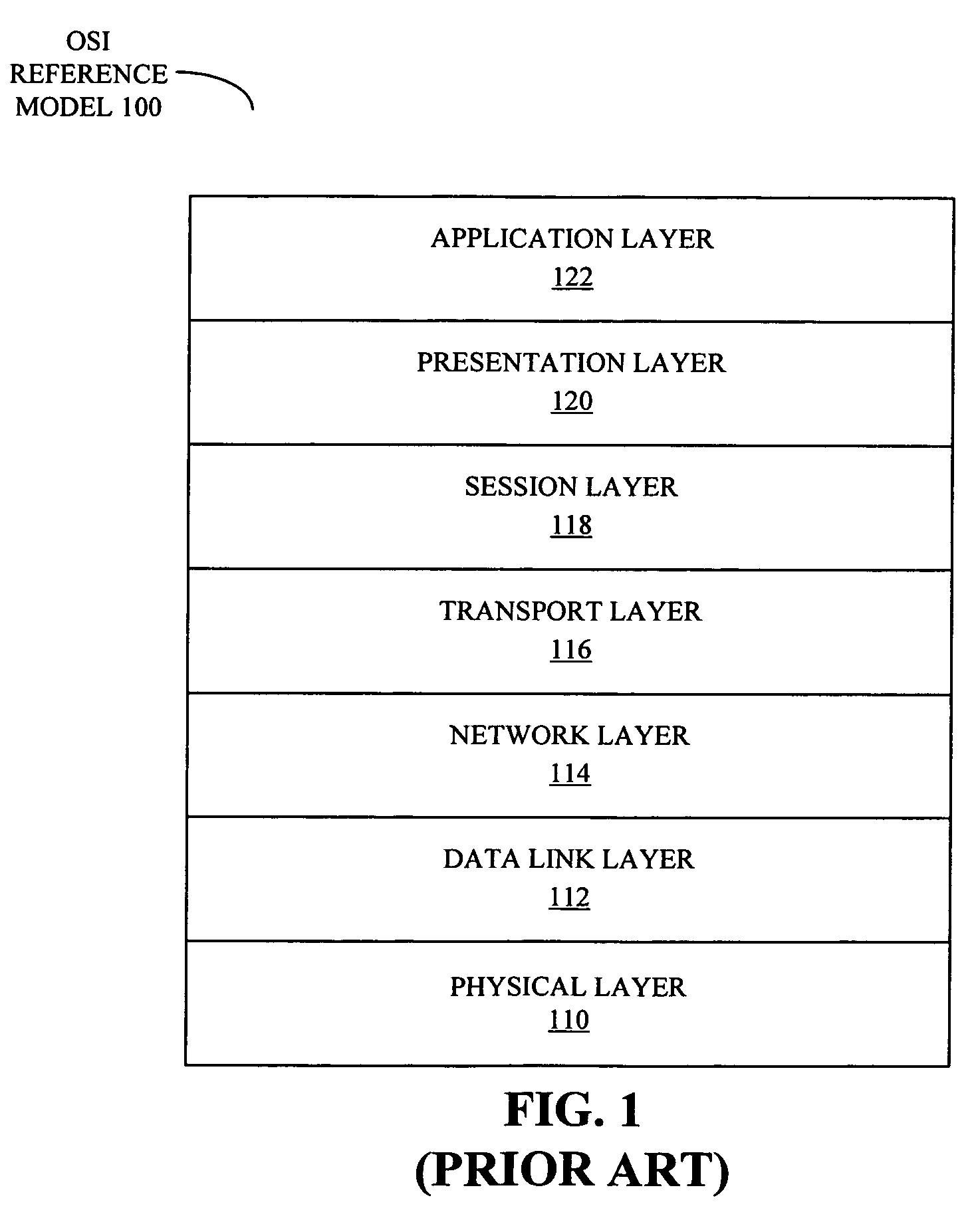
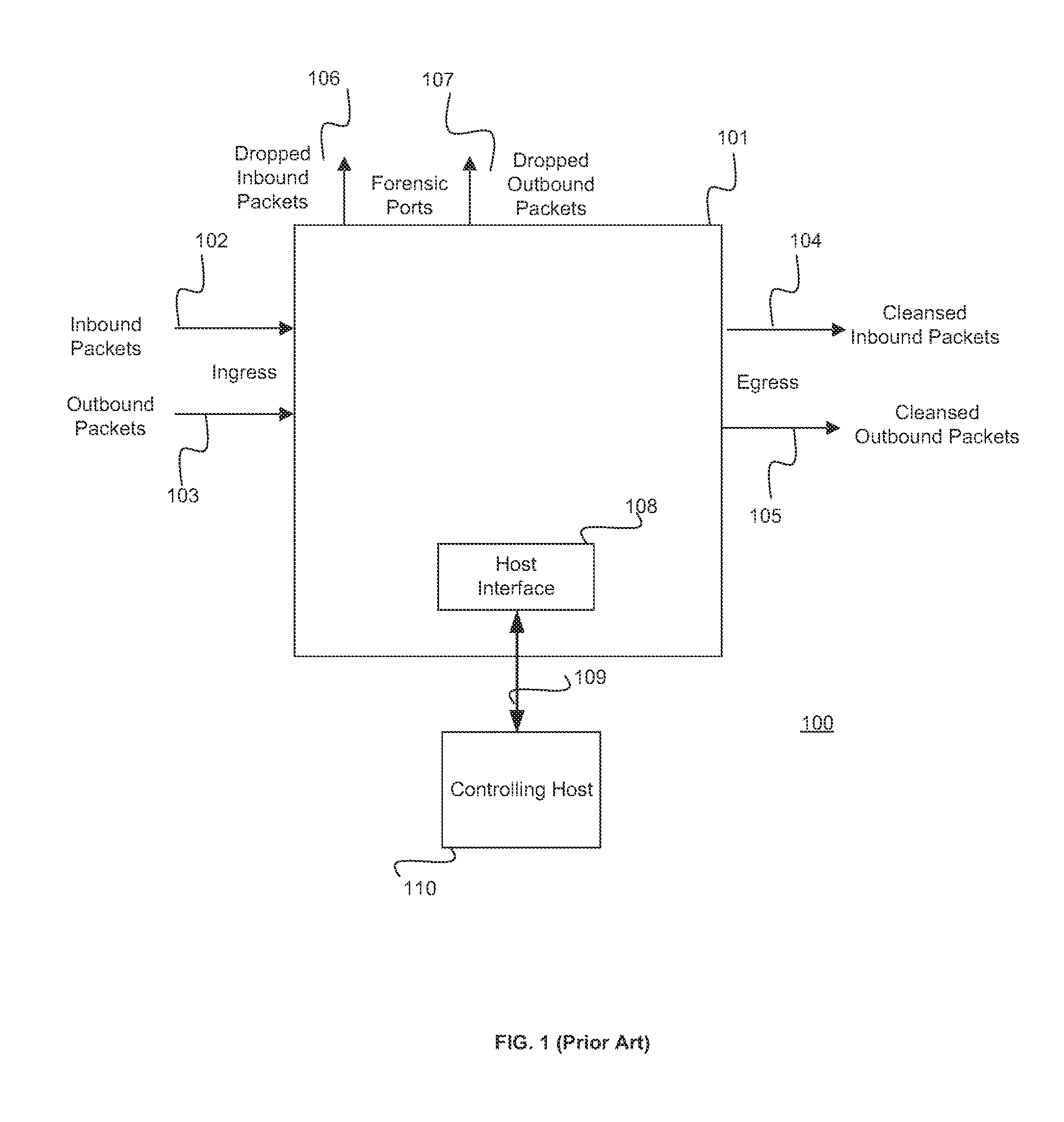
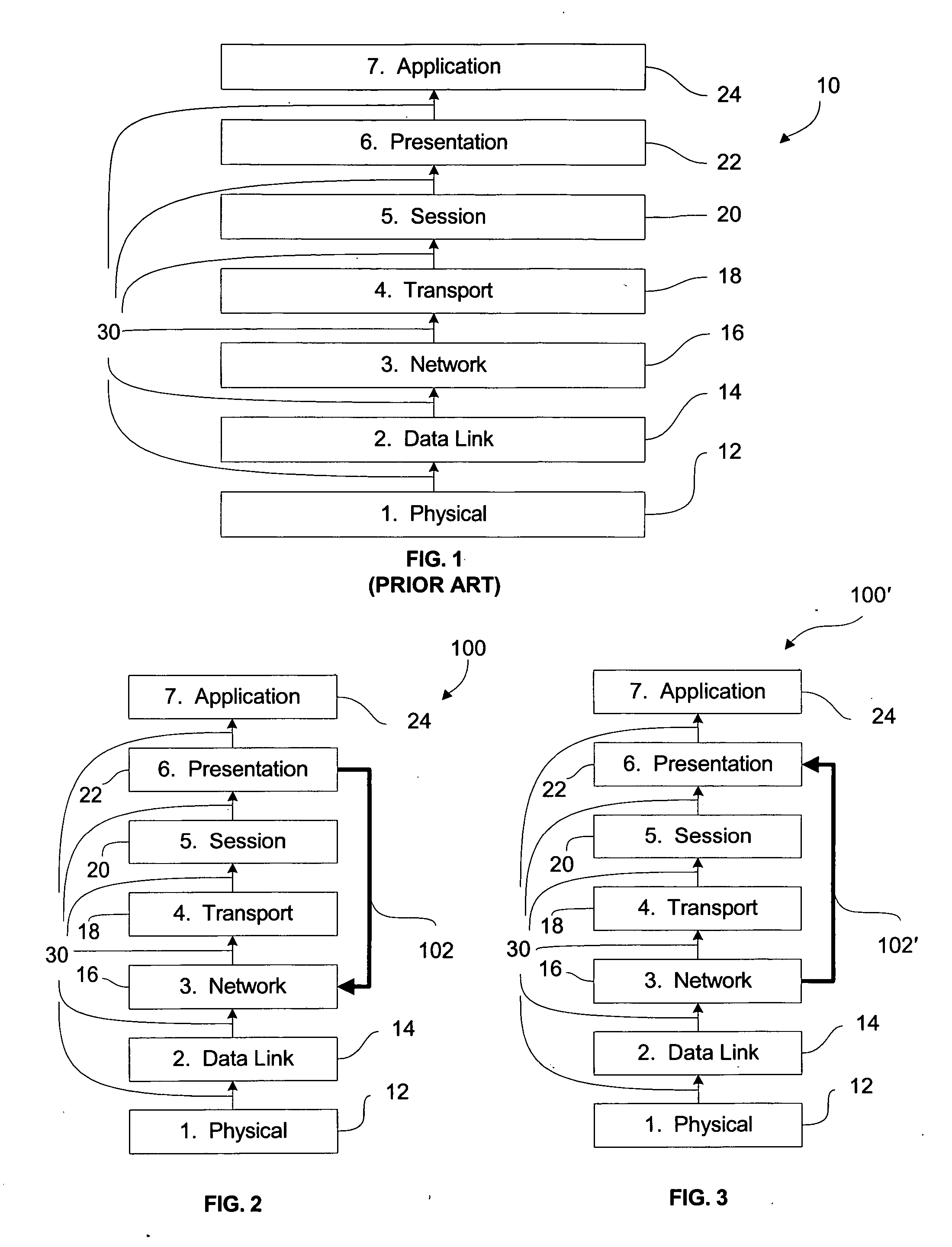
Open Systems Interconnection is an effort to standardize computer networking that was started in 1977 by the International Organization for Standardization, along with the ITU-T.
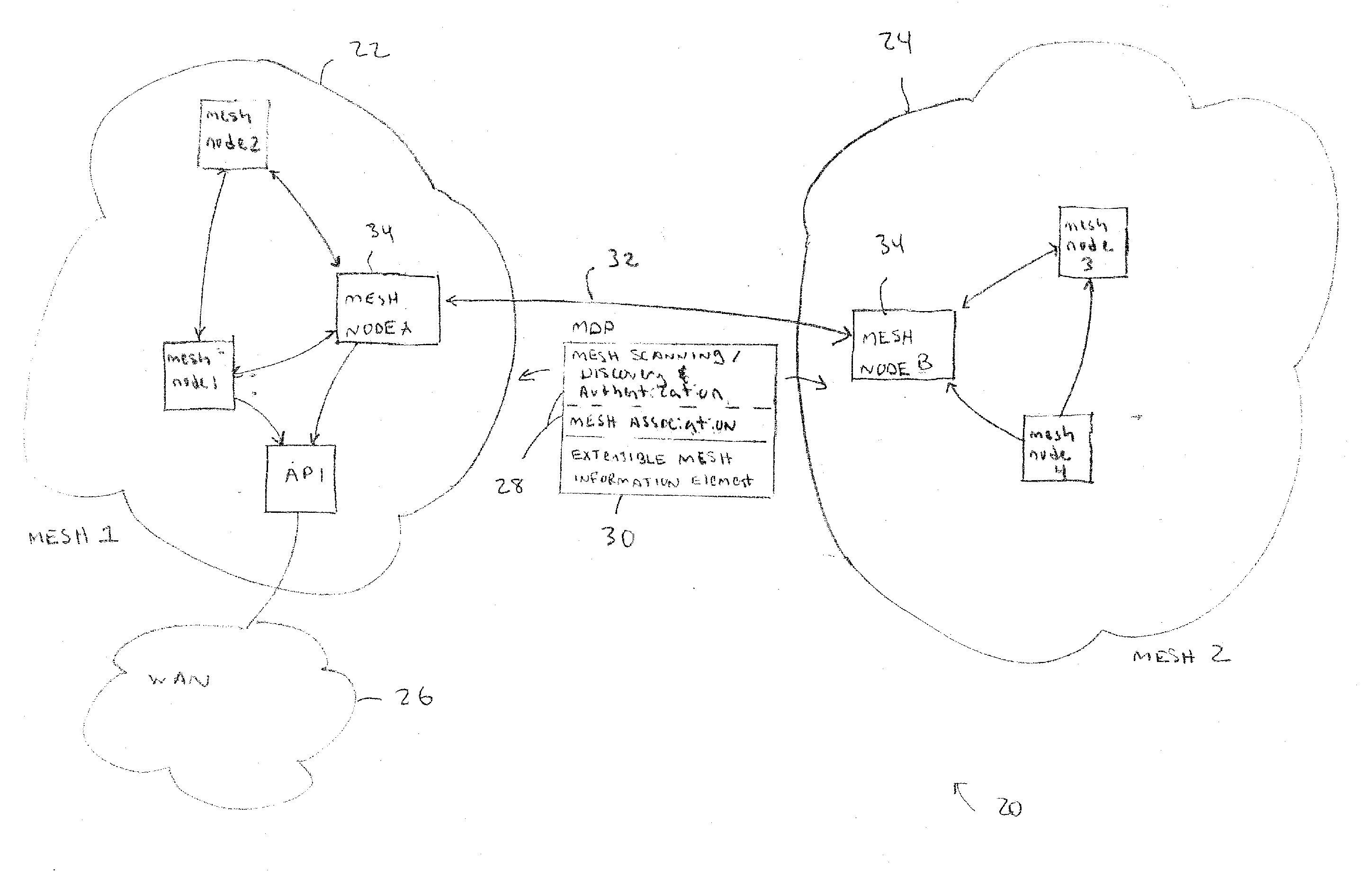
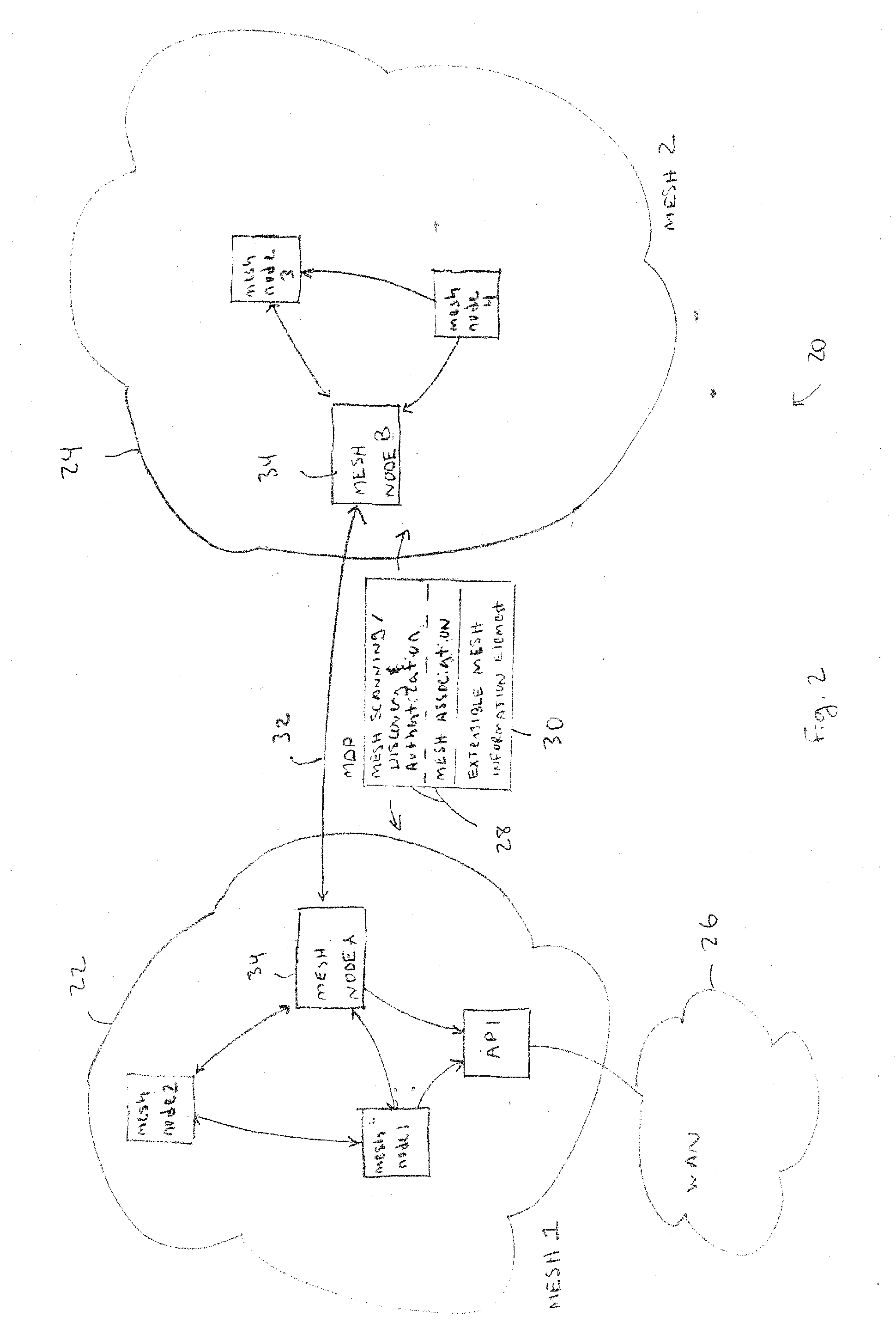
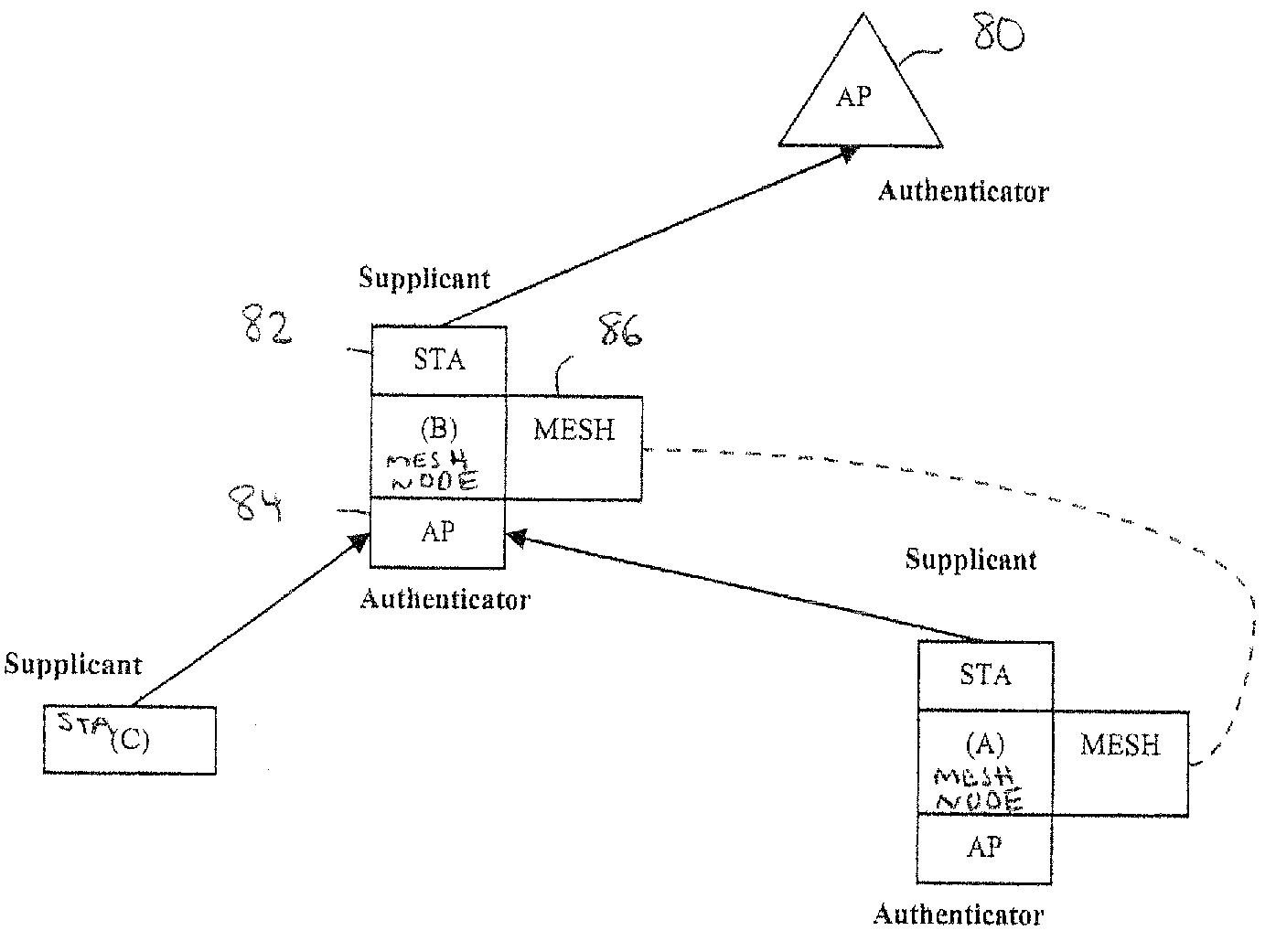
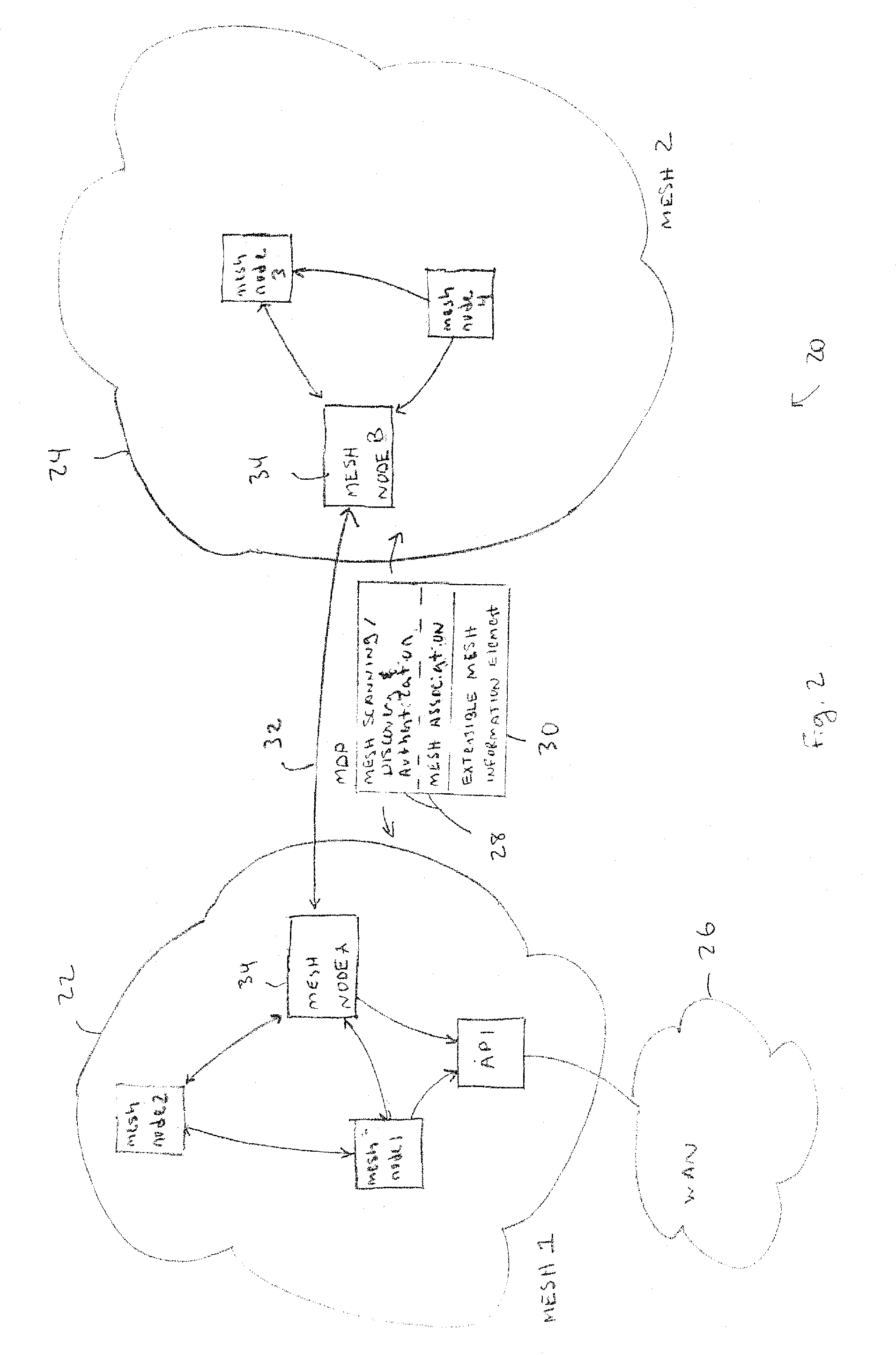
Discovery and authentication scheme for wireless mesh networks
InactiveUS20070189249A1Readily apparentError preventionFrequency-division multiplex detailsOpen Systems InterconnectionMesh node
Wireless network devices discover individual mesh nodes and networks of mesh nodes. An association is formed on the basis of peer-to-peer interactions at layer-1, layer-2 and / or higher layers of the Open System Interconnect (OSI) model. In particular, the system uses Beacon, Probe Request, Probe Response, Association Request, Association Response, and Disassociation frames and introduces a new Extensible Mesh Information Element (EMIE) used by mesh nodes to discover, authenticate, and associate with other peer nodes.
Owner:SRI INTERNATIONAL
Highly scalable architecture for application network appliances
A highly scalable application network appliance is described herein. According to one embodiment, a network element includes a switch fabric, a first service module coupled to the switch fabric, and a second service module coupled to the first service module over the switch fabric. In response to packets of a network transaction received from a client over a first network to access a server of a data center having multiple servers over a second network, the first service module is configured to perform a first portion of OSI (open system interconnection) compatible layers of network processes on the packets while the second service module is configured to perform a second portion of the OSI compatible layers of network processes on the packets. The first portion includes at least one OSI compatible layer that is not included in the second portion. Other methods and apparatuses are also described.
Owner:CISCO TECH INC
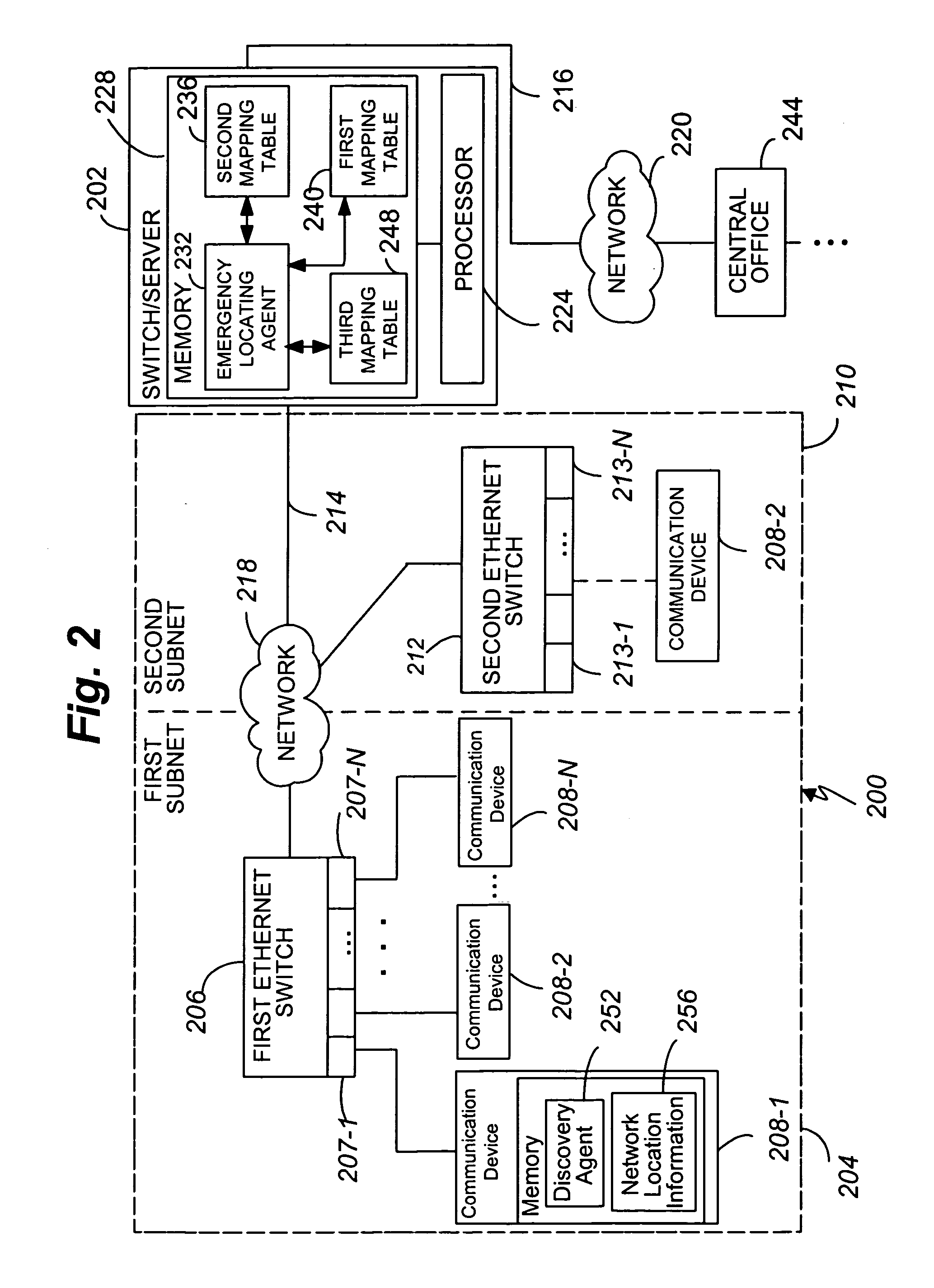
Advanced port-based E911 strategy for IP telephony
InactiveUS20060120517A1Accurate methodMaintain normalEmergency connection handlingTelephonic communicationOpen Systems InterconnectionComputer science
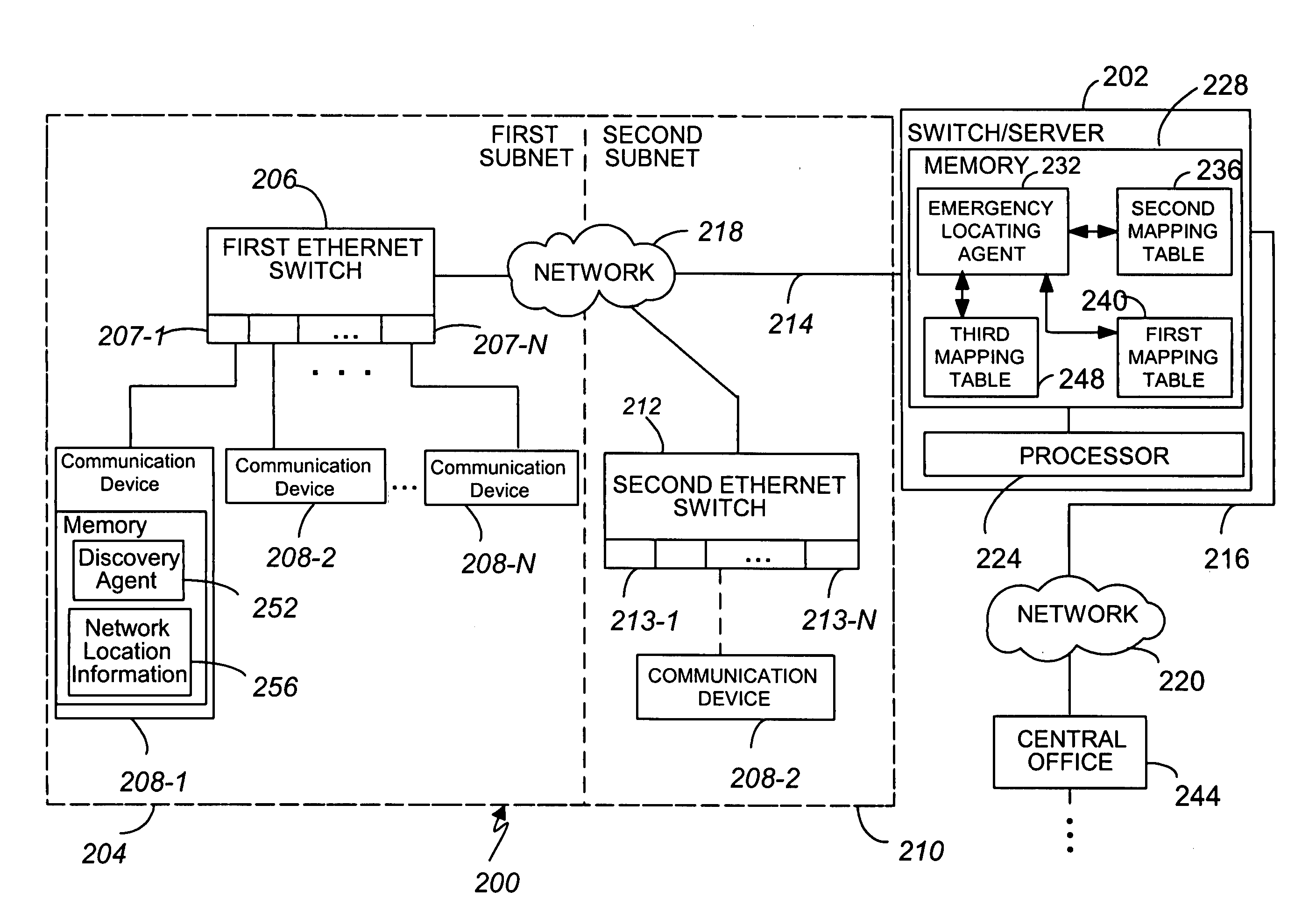
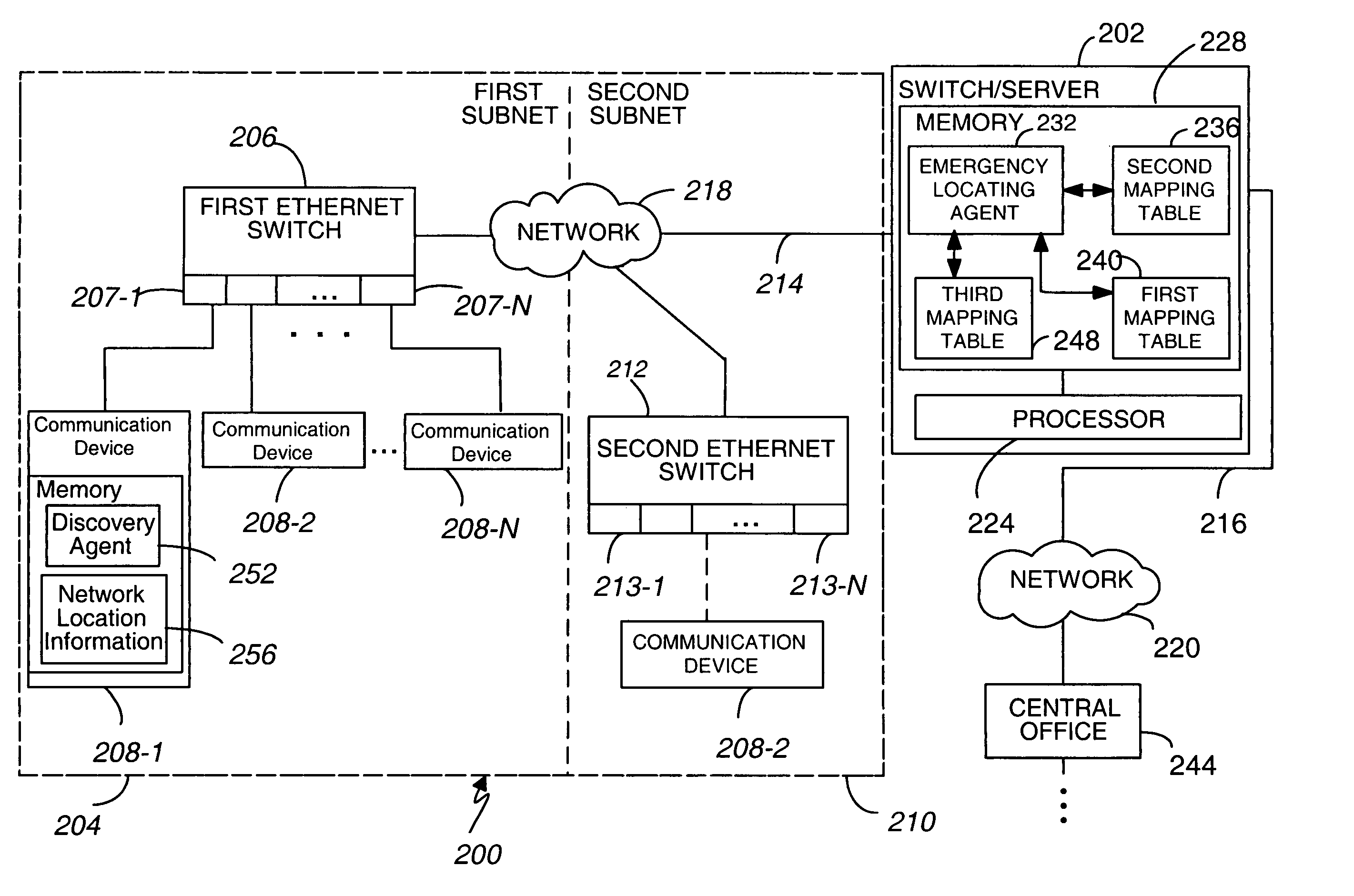
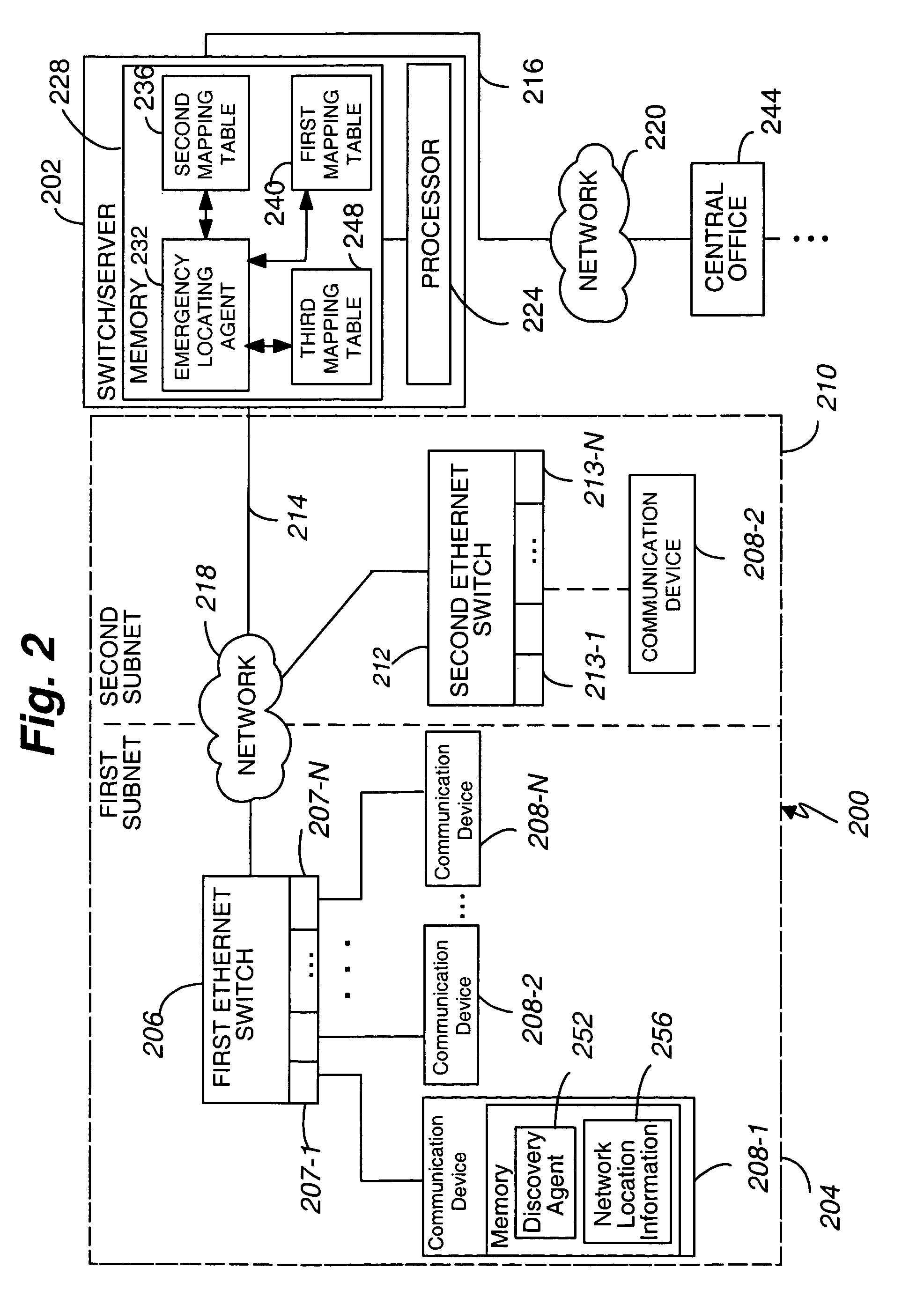
An enterprise network includes at least one communication device 208-1, an Open Systems Interconnect (OSI) Layer 2 switch 206, and a corresponding enterprise switch 208. The communication device 208-1 is connected to at least one of an access point 904-1 and a respective port 207-1 of the Layer 2 switch 206. The enterprise network includes a plurality of Emergency Location Information Numbers (ELINs) corresponding to differing segments of the enterprise network. The Layer 2 switch 206 serves at least one of the differing segments. The communication device 208-1 includes a discovery agent 252 operable, when a predetermined first event occurs, to obtain from the Layer 2 switch 206 at least one of an access point identifier, a switch identifier from the Layer 2 switch 206, and a port identifier identifying the respective port 207-1.
Owner:AVAYA INC
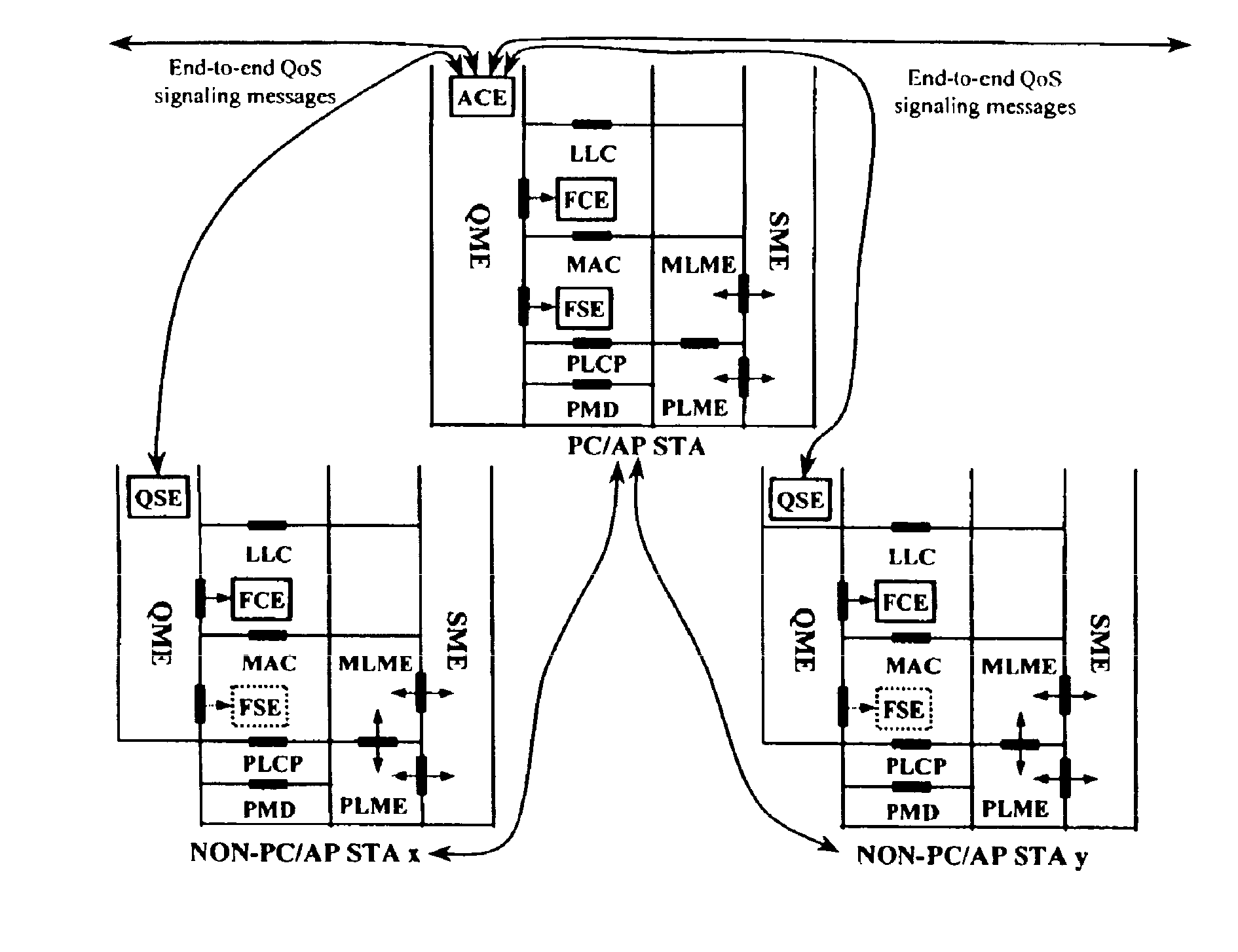
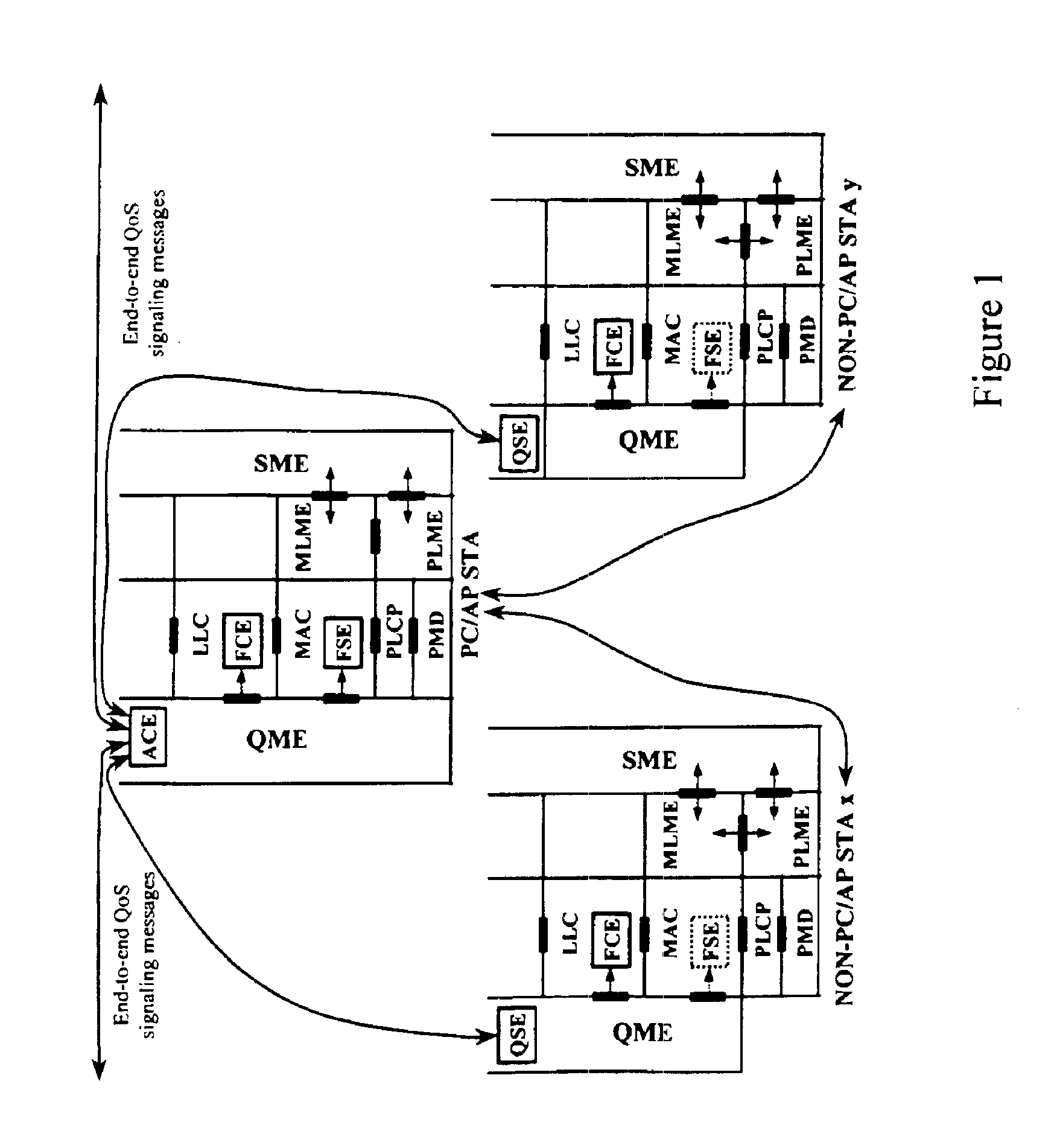
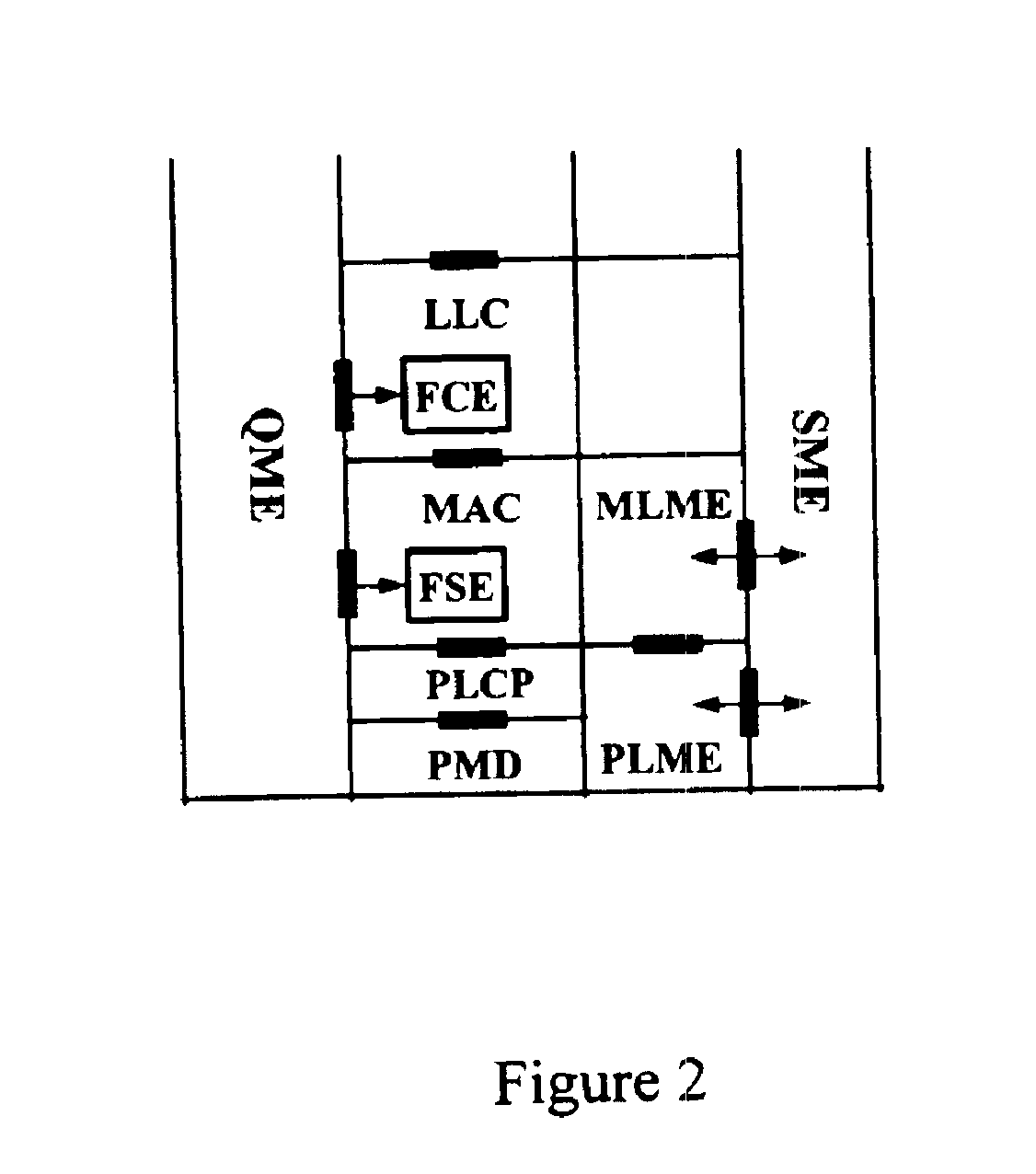
Architectural reference model for QoS-driven wireless LANs
InactiveUS6862270B1Enhanced channel accessImprove bandwidth utilizationNetwork traffic/resource managementNetwork topologiesOpen Systems InterconnectionEnd to end qos
A quality of service (QoS) station is disclosed containing a point coordinator (PC) for a basic service set (BSS) in a wireless LAN. The PC station includes a QoS management entity (QME) and an admission control entity (ACE). The QME receives at least one end-to-end QoS message that characterizes a user application, such as a voice call, a video call, a data call and a multimedia call. The at least one end-to-end QoS message includes at least one QoS parameter set that is expressed at layer 3 and higher of an ISO / IEC basic reference model of Open Systems interconnection (OSI) (ISO / IEC 7498-1) and is to be passed down to layer 2 of the PC-station for enabling QoS traffic transport of the application. The ACE performs an admission control decision relating to the application based on the at least one end-to-end QoS message characterizing the application. The ACE reserves a resource based on a QoS parameter set contained in the end-to-end QoS message. The ACE can be part of the QME and can include a resource control module that performs at least one admission control decision based on resource permission, and a policy control module that performs at least one admission control decision based on policy permission.
Owner:AT&T INTPROP I L P
Systems and methods for proactively enforcing a wireless free zone
ActiveUS20080119130A1Minimize signal bleedMinimize signalingNetwork topologiesCommunication jammingWireless intrusion prevention systemFree zone
The present disclosure is directed to systems and methods for proactively enforcing a wireless free zone over an enterprise's airspace using Open Systems Interconnect (OSI) layer one, two, and three based techniques. The systems and methods prevent wireless communications over IEEE 802.11 (WiFi), IEEE 802.16 (WiMax), and IEEE 802.15.1 (Bluetooth) networks to enable an enterprise to enforce compliance to a no-wireless policy. Smart antennas and coverage planning are included to avoid disrupting a neighbor's wireless communications. Further, the disclosed systems and methods can be combined into existing Wireless Intrusion Prevention Systems (WIPS) or in a stand-alone sensor and server configuration to offer proactive no-wireless zones.
Owner:EXTREME NETWORKS INC
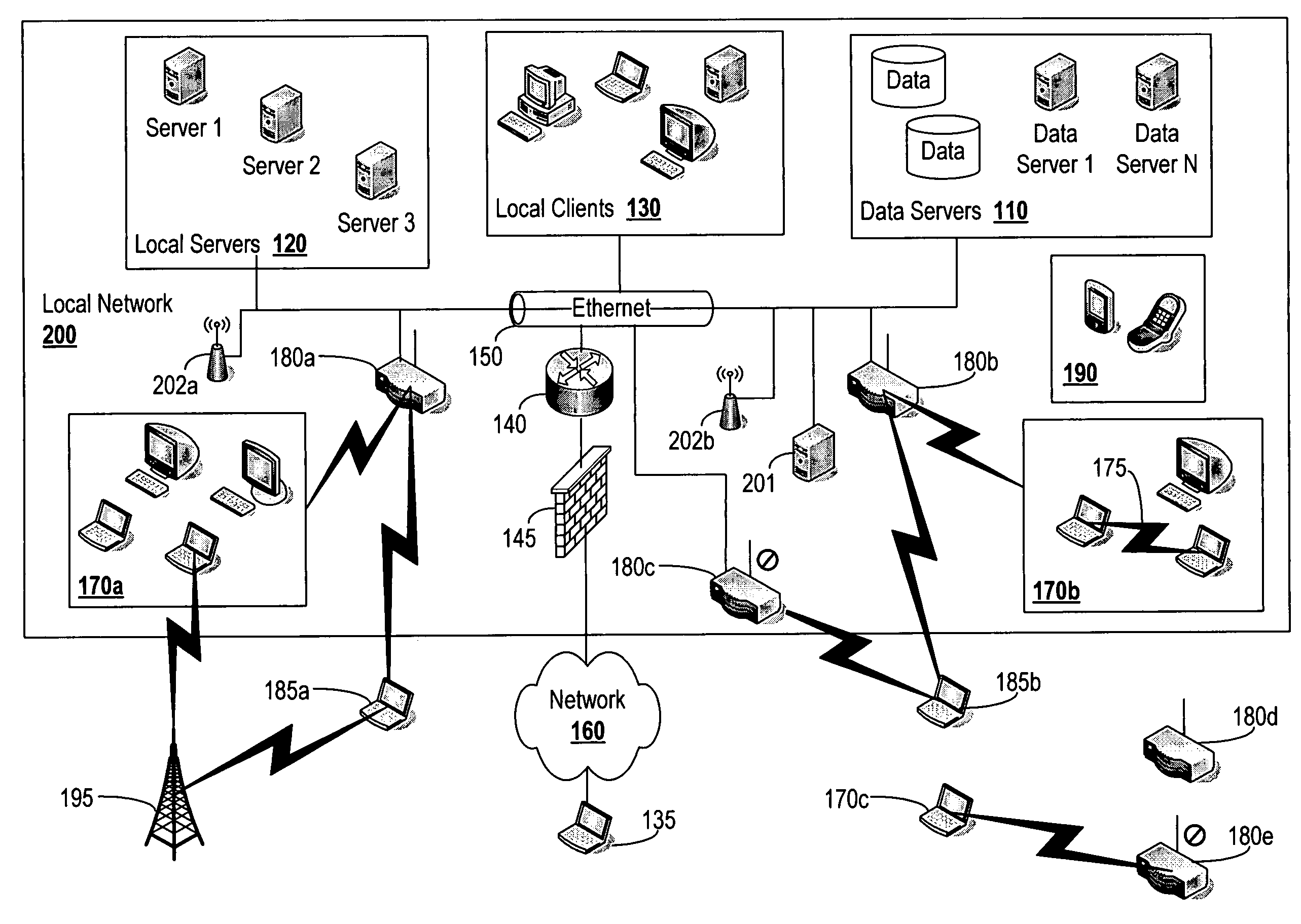
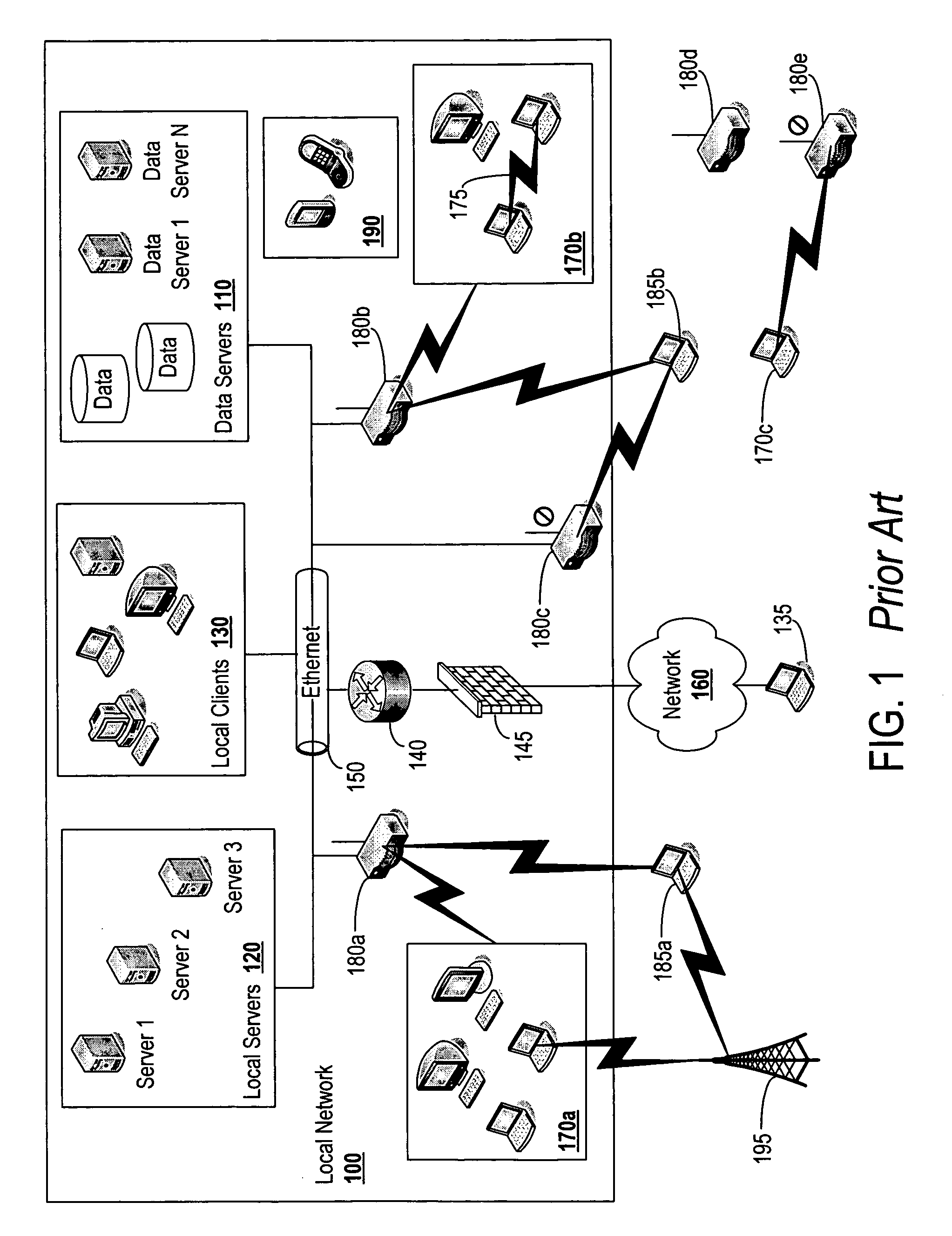
Globally accessible computer network-based broadband communication system with user-controllable quality of information delivery and flow priority
InactiveUS20020004827A1Digital computer detailsData switching networksReference modelTraffic capacity
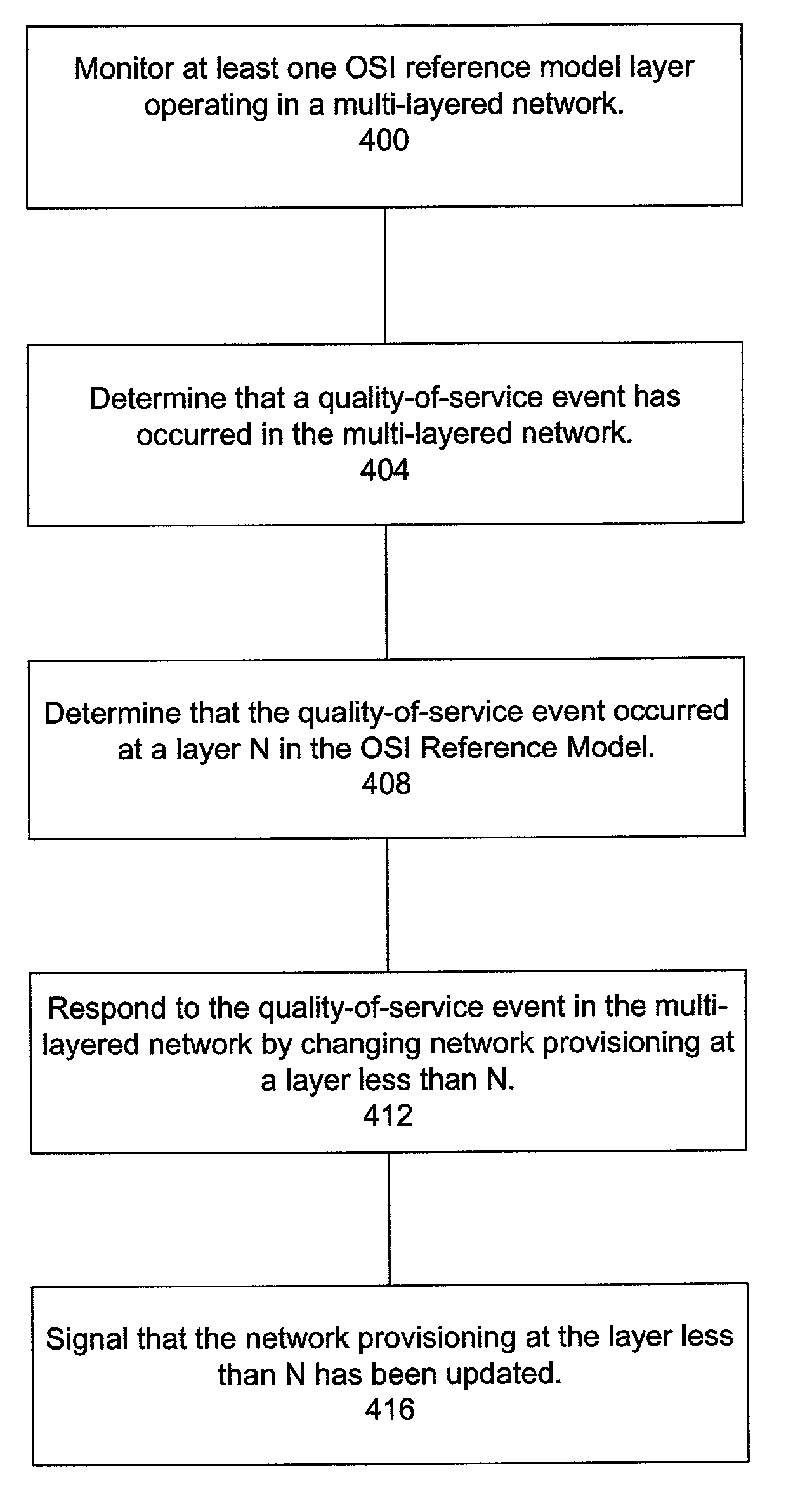
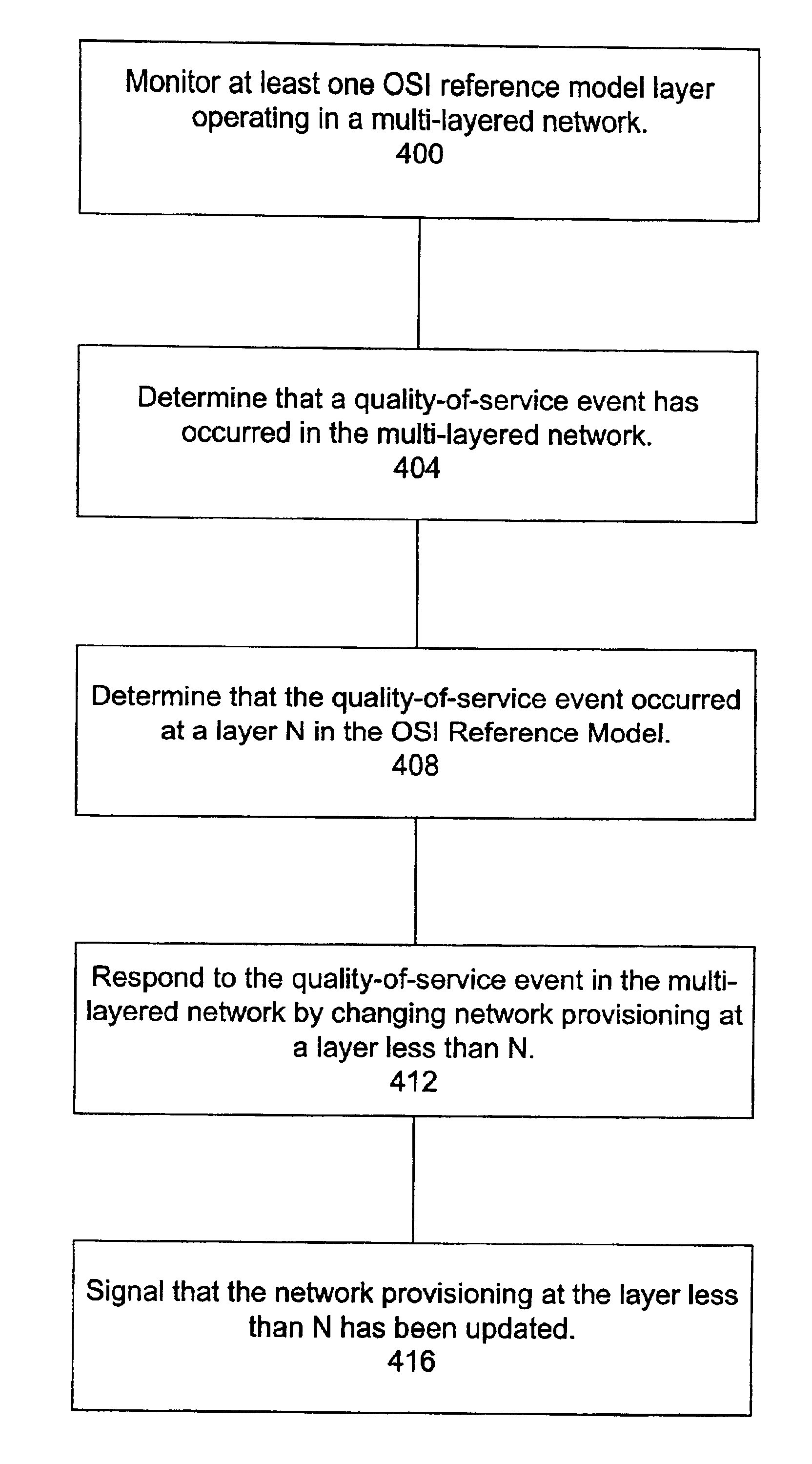
A method for providing broadband communications over a multi-layered network having a plurality of Open System Interconnection (OSI) Reference Model layers functioning therein includes monitoring at least one OSI reference model layer functioning in the multi-layered network. A quality of service event is determined whether to have occurred in the multi-layered network. The quality of service event is determined to have occurred at a layer N in the OSI reference model. Network provisioning is changed at a layer less than N in response to the quality of service event, and a signal is provided when the network provisioning at the layer less than N has been changed. A system for providing broadband communications includes a multi-layered network, a network monitor, and a network controller. The multi-layered network has a plurality of Open System Interconnection (OSI) reference model layers functioning therein. The network monitor is coupled to the multi-layered network, and the network monitor is adapted to monitor at least one OSI reference model layer functioning in the multi-layered network, determine that a quality of service event has occurred in the multi-layer network, and determine that the quality of service event occurred at a layer N in the OSI reference model. The network controller is coupled to the multi-layered network, and the network monitor is adapted to respond to the quality of service event in the multi-layered network by changing the network provisioning at a layer less than N.
Owner:UNWIRED BROADBAND INC
Discovery and authentication scheme for wireless mesh networks
InactiveUS7814322B2Error preventionFrequency-division multiplex detailsOpen Systems InterconnectionMesh node
Owner:SRI INTERNATIONAL
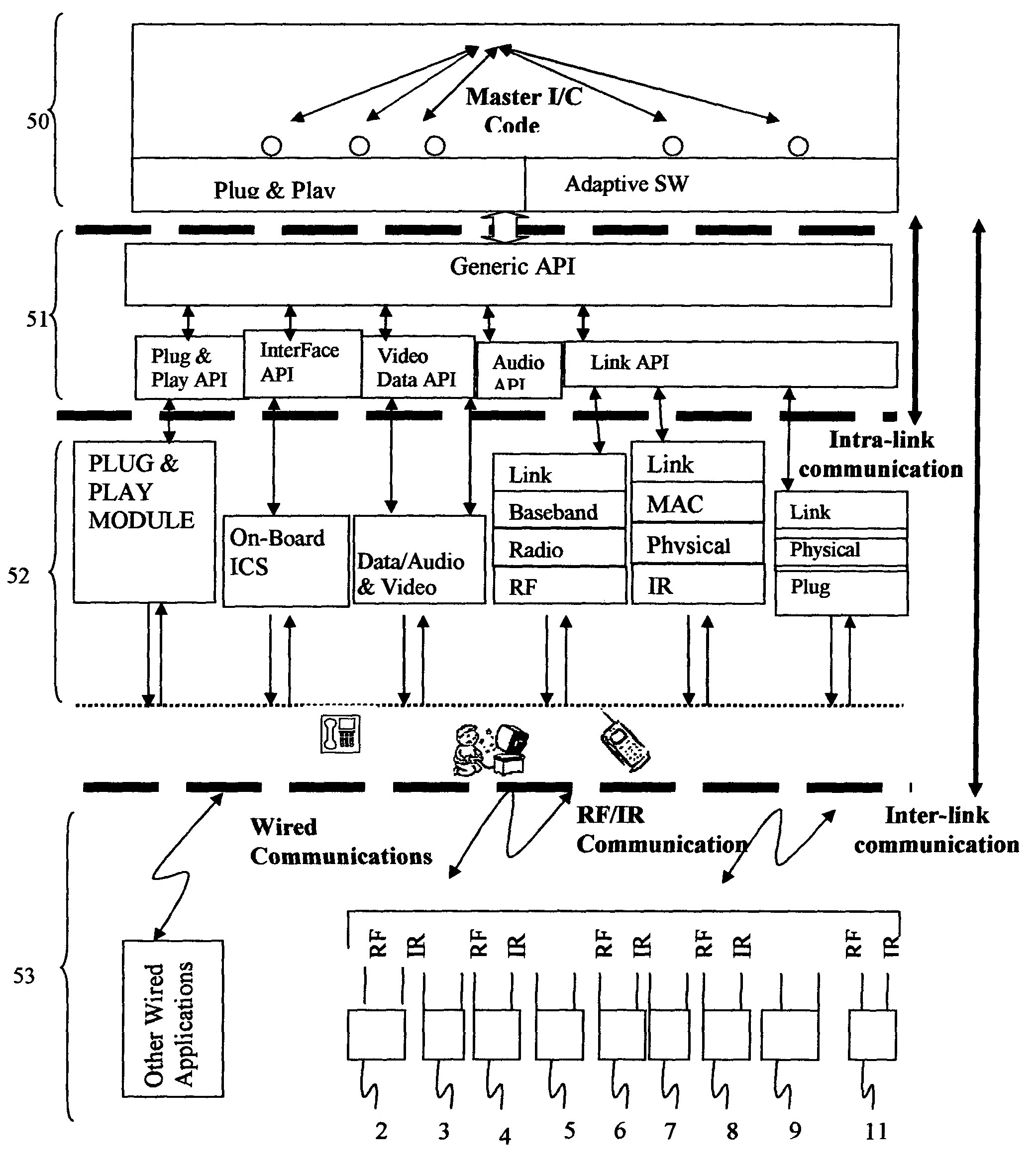
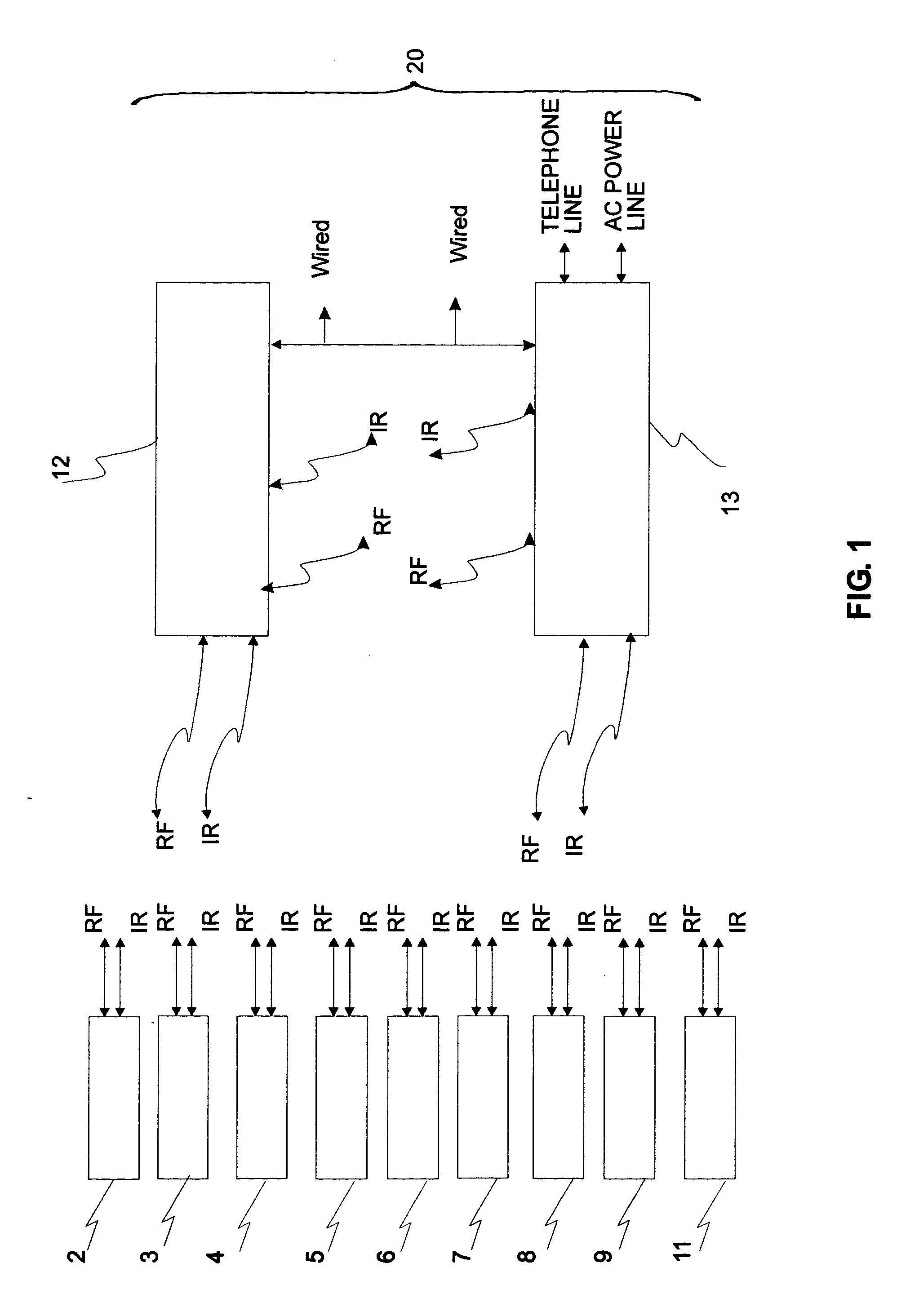
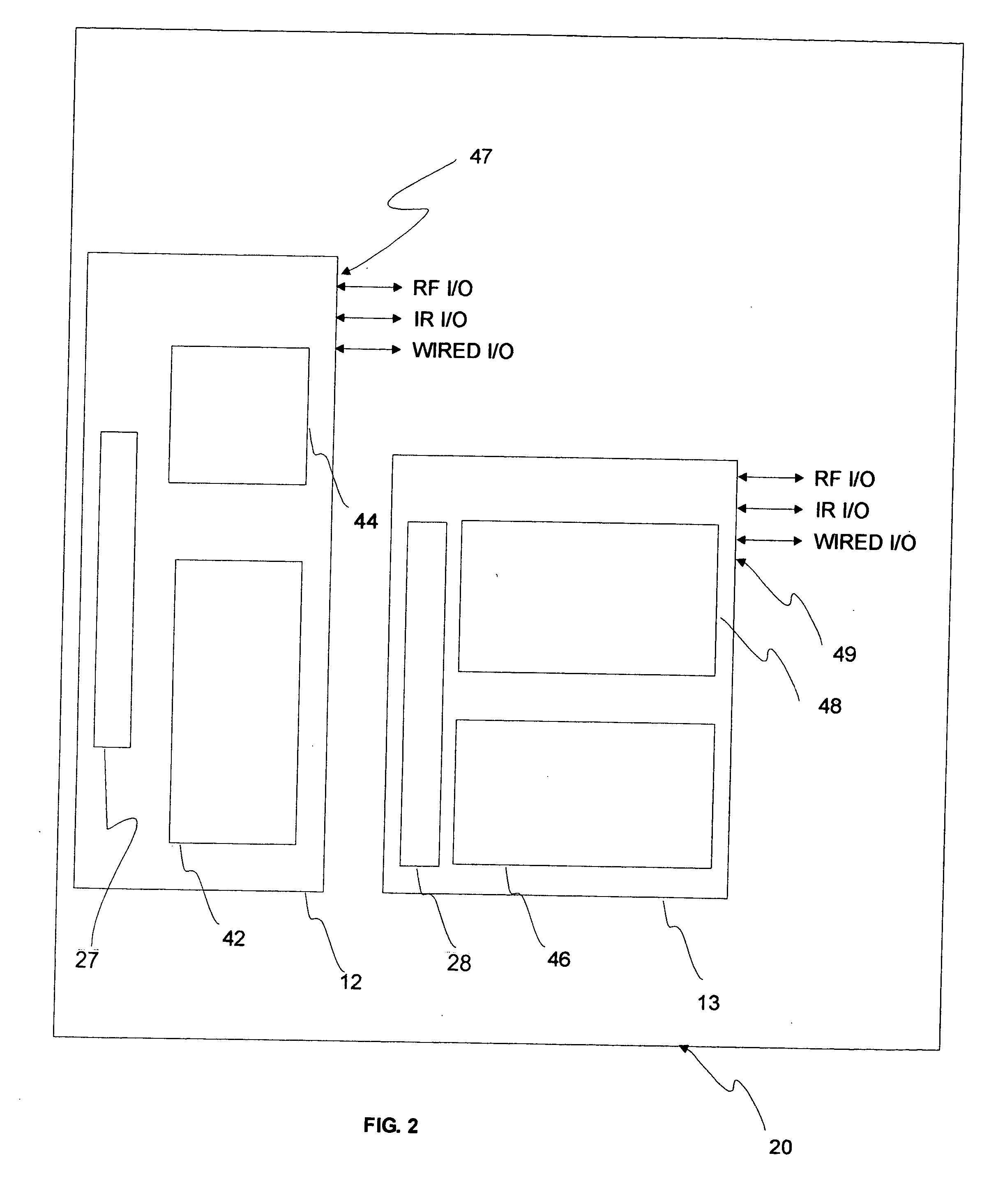
Communications, command, and control system with plug-and-play connectivity
InactiveUS20050054289A1Function increaseCordless telephonesTransmission systemsInformation processingInteroperability
A modular communications, command, and control system with plug-and-play connectivity, utilizing configurable independent base stations and portable handsets that preferably have similar components and functionality so as to be interoperable. The system utilizes an open system interconnection architecture preferably having fully integrated layers permitting inter-operability with adaptive applications and inter / intra-linking with external appliances and / or apparatuses. Optionally, the system may be utilized to perform extended information handling / processing, networking, personal assistance, industrial, commercial, medical, military, and / or security functions.
Owner:SALAZAR JOE ANDREW MR
Advanced port-based E911 strategy for IP telephony
ActiveUS7130385B1Accurate methodMaintain normalEmergency connection handlingTelephonic communicationOpen Systems InterconnectionCommunication device
An enterprise network includes at least one communication device 208-1, an Open Systems Interconnect (OSI) Layer 2 switch 206, and a corresponding enterprise switch 208. The communication device 208-1 is connected to at least one of an access point 904-1 and a respective port 207-1 of the Layer 2 switch 206. The enterprise network includes a plurality of Emergency Location Information Numbers (ELINs) corresponding to differing segments of the enterprise network. The Layer 2 switch 206 serves at least one of the differing segments. The communication device 208-1 includes a discovery agent 252 operable, when a predetermined first event occurs, to obtain from the Layer 2 switch 206 at least one of an access point identifier, a switch identifier from the Layer 2 switch 206, and a port identifier identifying the respective port 207-1.
Owner:AVAYA INC
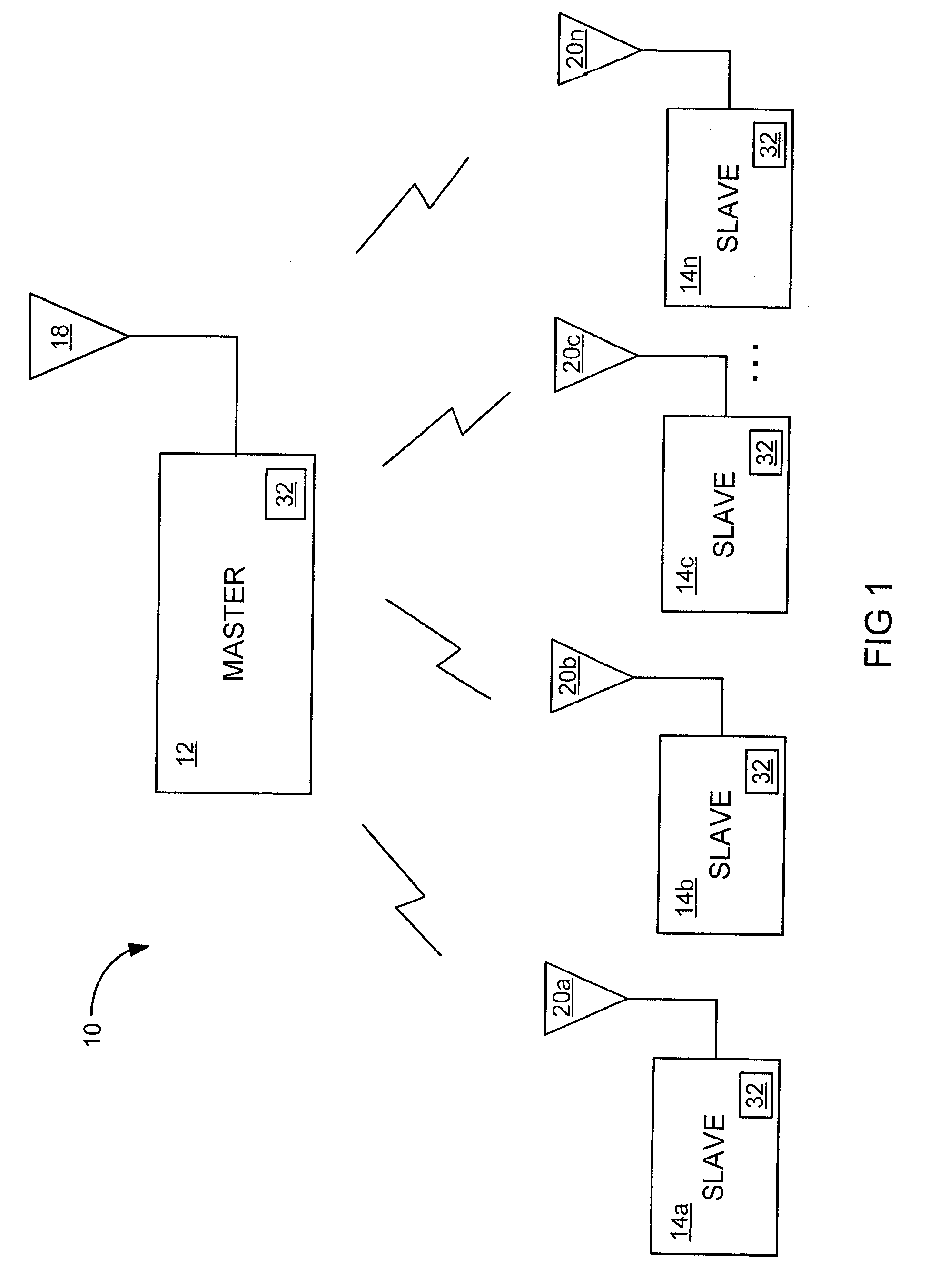
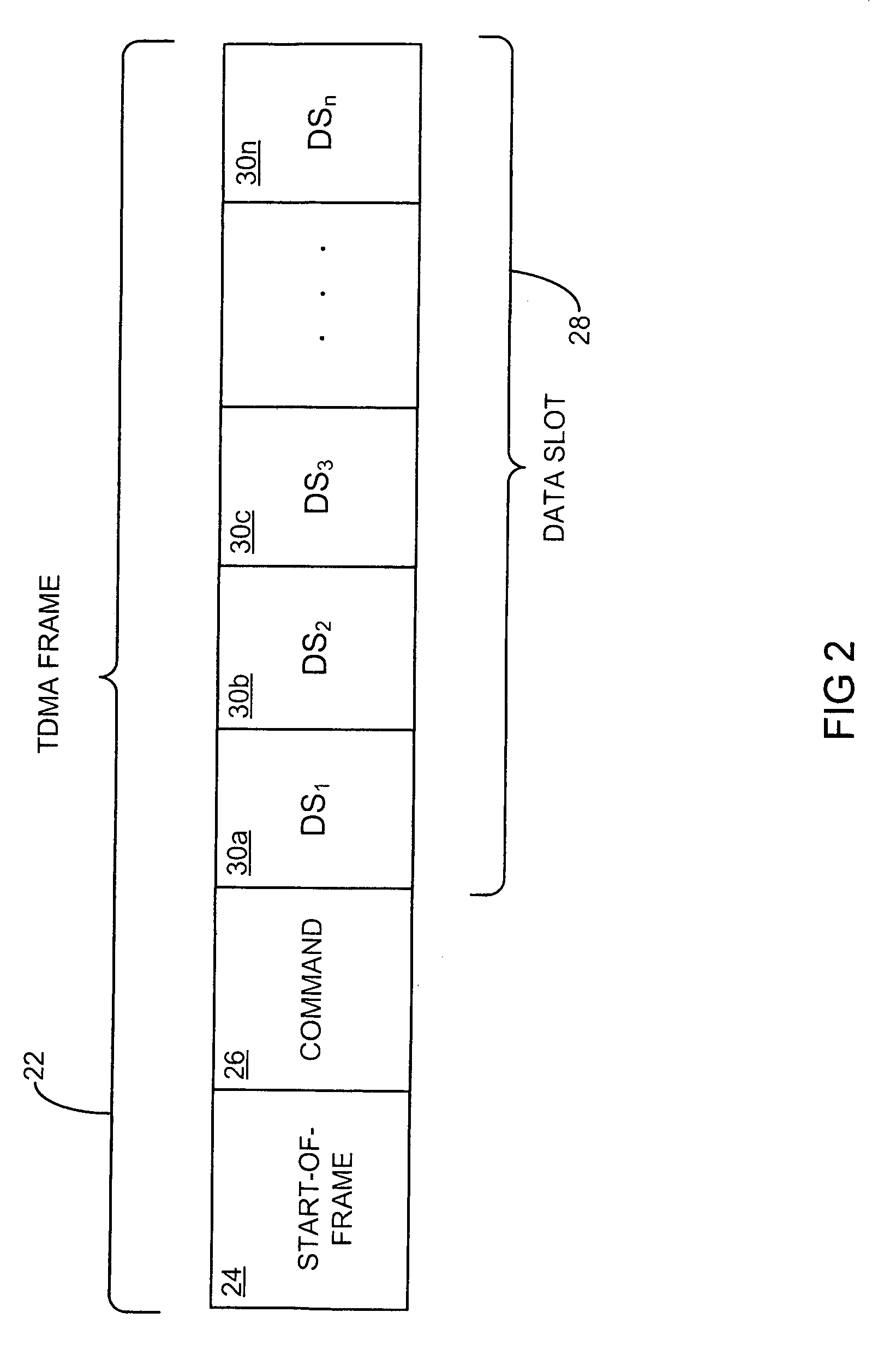
Apparatus and method for managing variable-sized data slots within a time division multiple access frame
InactiveUS6944148B1Easy to useWider transferTime-division multiplexData switching by path configurationReference modelQuality of service
A reliable Medium Access Control layer protocol and method employing centralized management of communication in a Time Division Multiple Access network architecture. The Medium Access Control layer protocol implements Quality of Service guaranties to the layers of the Open Systems Interconnection reference model above the Medium Access Control layer by providing guaranteed bandwidth links within the bandwidth range specified by those layers. The Medium Access Control layer protocol further provides variable data slot requisition, variable data slot allocation, dynamic data slot reallocation, and data slot deallocation.
Owner:HANGER SOLUTIONS LLC
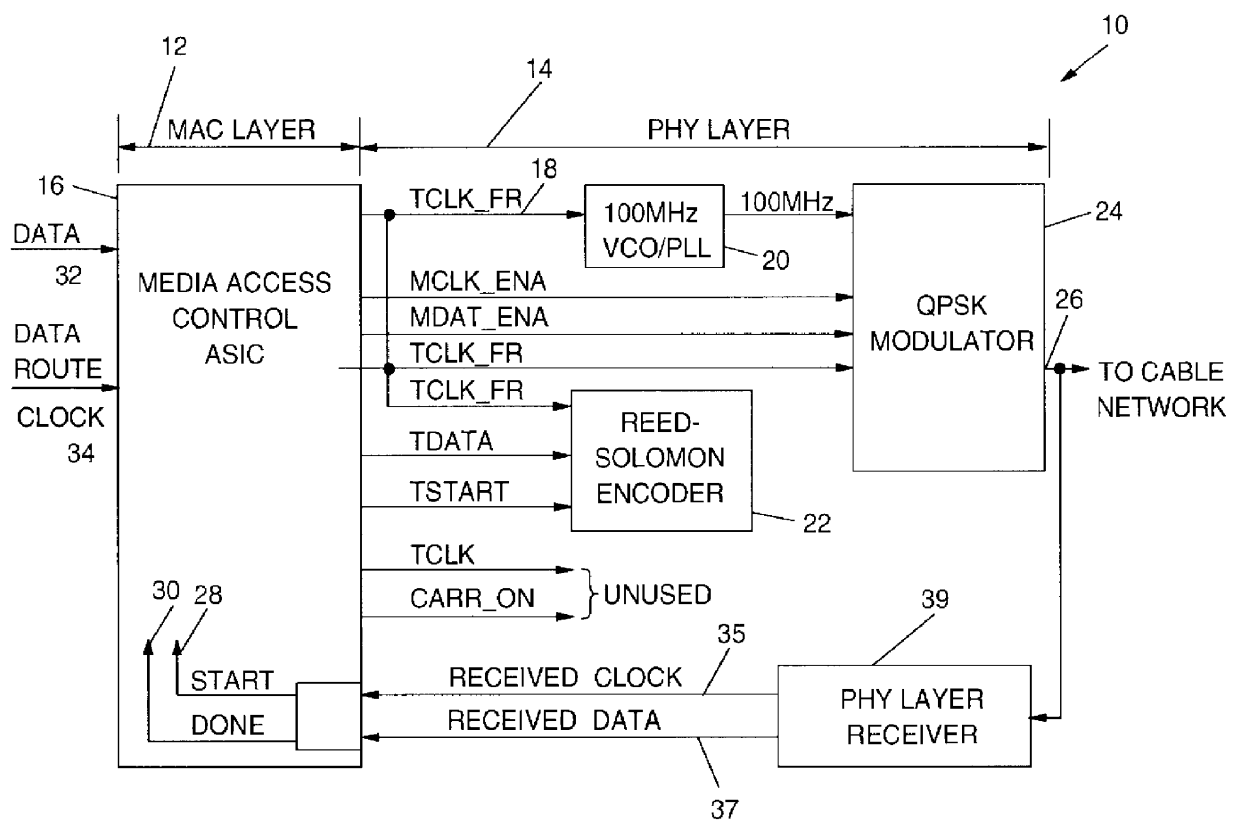
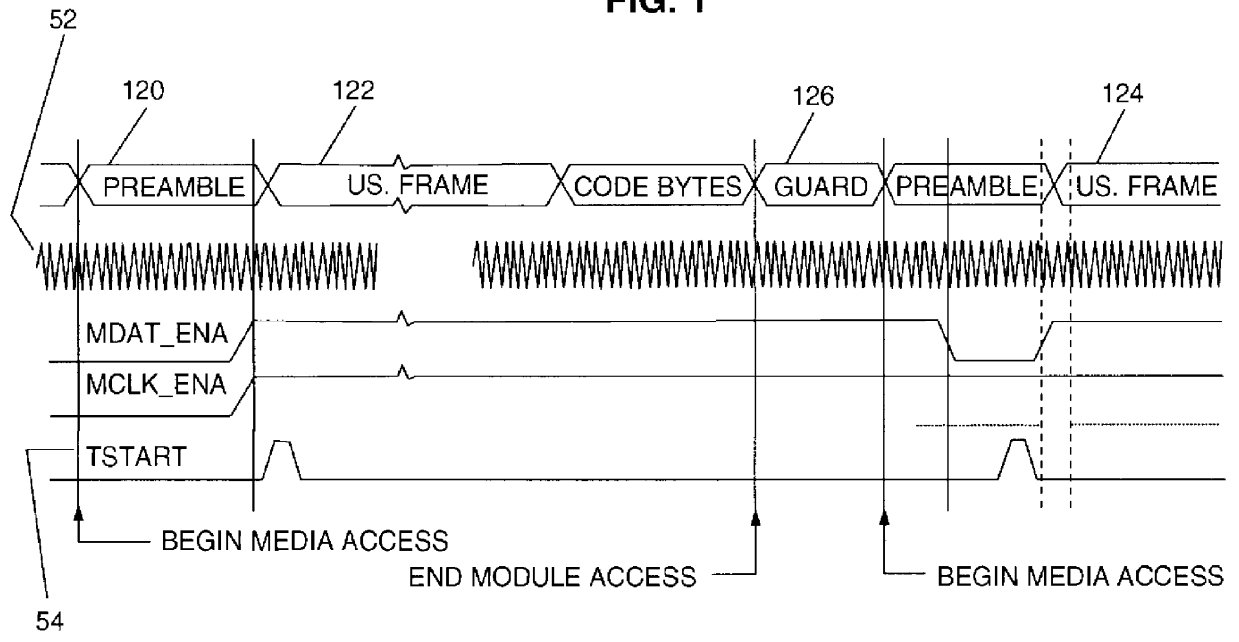
Programmable output interface for lower level open system interconnection architecture
InactiveUS6049837ABroadband local area networksMultiple digital computer combinationsControl signalData rate
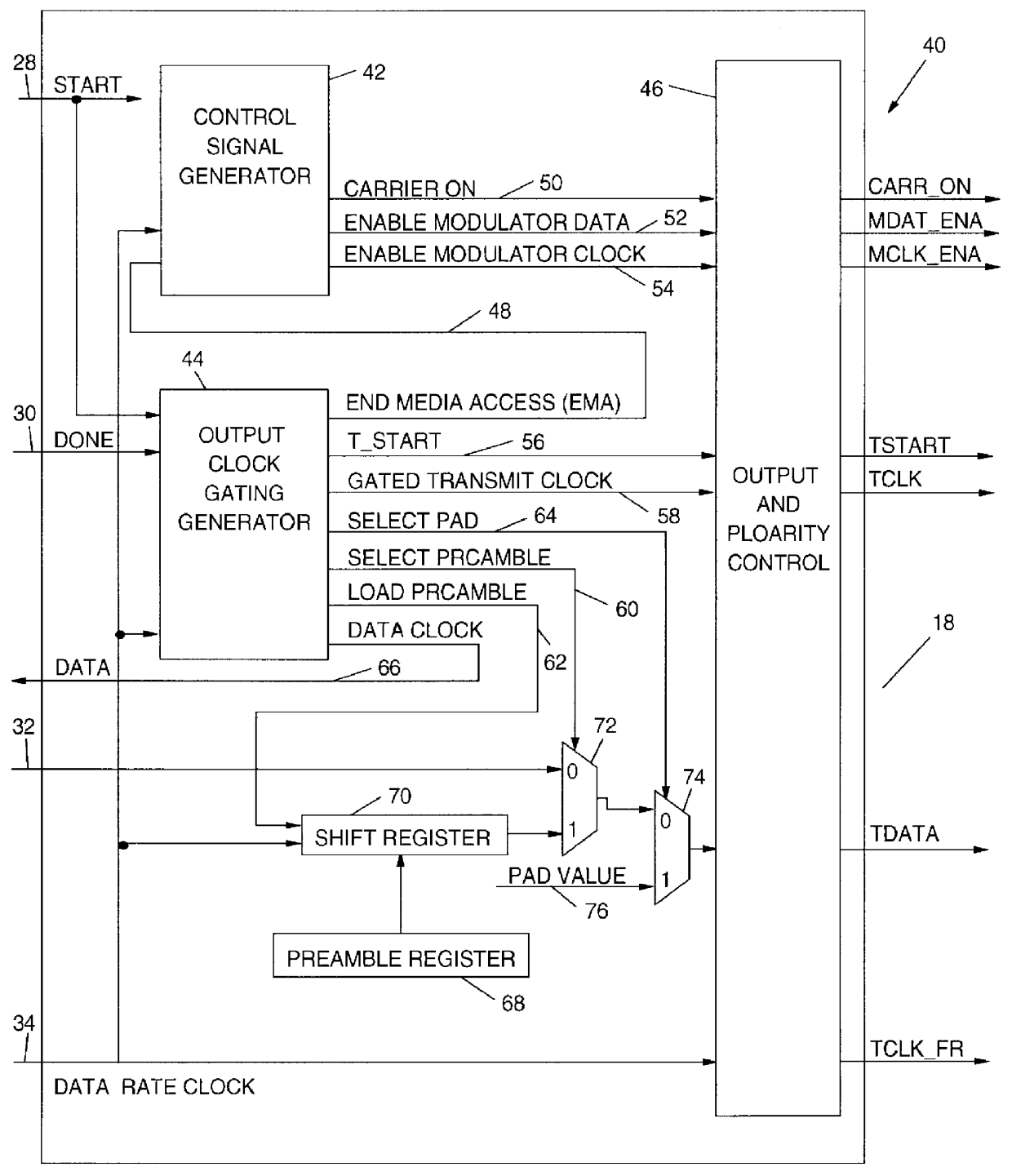
A programmable output interface in an Open System Interconnection (OSI) enables a Media Access (MAC) Layer to access a variety of Physical (PHY) Layer implementations without redesign of the interface. The programmable interface includes a control signal generator; an output clock gating generator, and an output polarity control device coupled to the PHY layer. The interface receives media access Start; media access Done signals; a Data Rate clock signal and a data signal. The control signal generator provides control signals for the physical layer components via the polarity control device. The active signal polarity and the relative timing of the control signals are controlled by programmable registers. The output clock gating generator provides clock signals to the physical layer components via the polarity control in response to the Start; Done and Data Rate signals. The output generator clock includes programmable interval registers for the various frame intervals including a User Pause Interval (UPI); Preamble Interval (PI); User Send Interval (USI), etc. The polarity control provides the correct signal polarity for each control, clock, and data signal.
Owner:IBM CORP
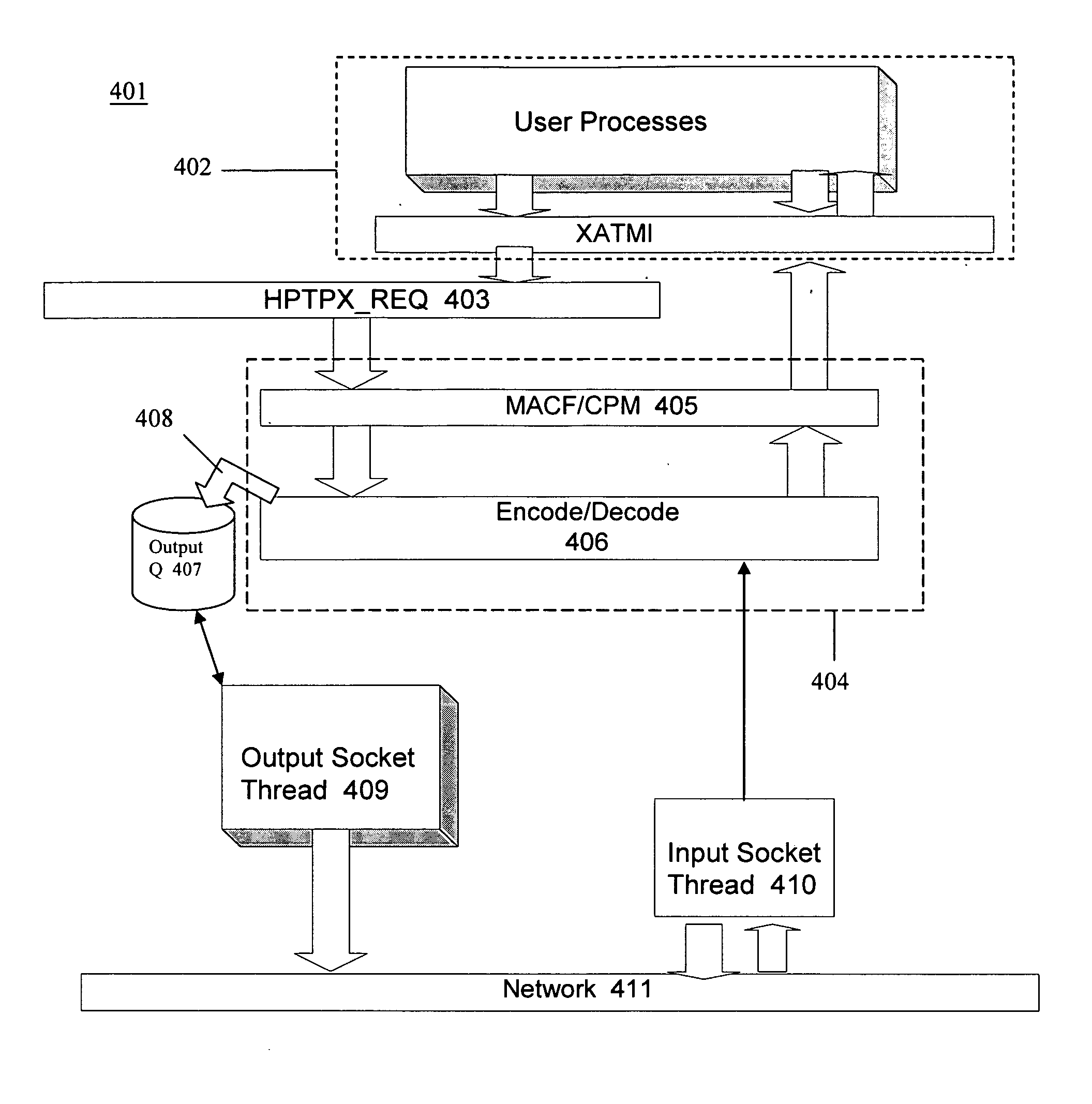
Message transfer using multiplexed connections in an open system interconnection transaction processing environment
InactiveUS20050193056A1Less complexSimpler connection creationMultiple digital computer combinationsSecuring communicationMessage lengthMultiplexing
Novel message formats for use in a distributed transaction environment are disclosed. Each message includes a message type field, a message length field, and a data field, typically in the foregoing order, and each field in the message has a fixed number of bytes. The message type and data length fields may be comprised of a single header. The data field may include novel groups of OSI TP PDUs where each grouping characterizes the content of the data in the PDU. A novel apparatus for use in a distributed transaction environment also is disclosed. The apparatus may include a peer processing machine and a multiplexed TCP / IP connection for exchanging messages with other peer processing machines in the distributed transaction environment.
Owner:UNISYS CORP
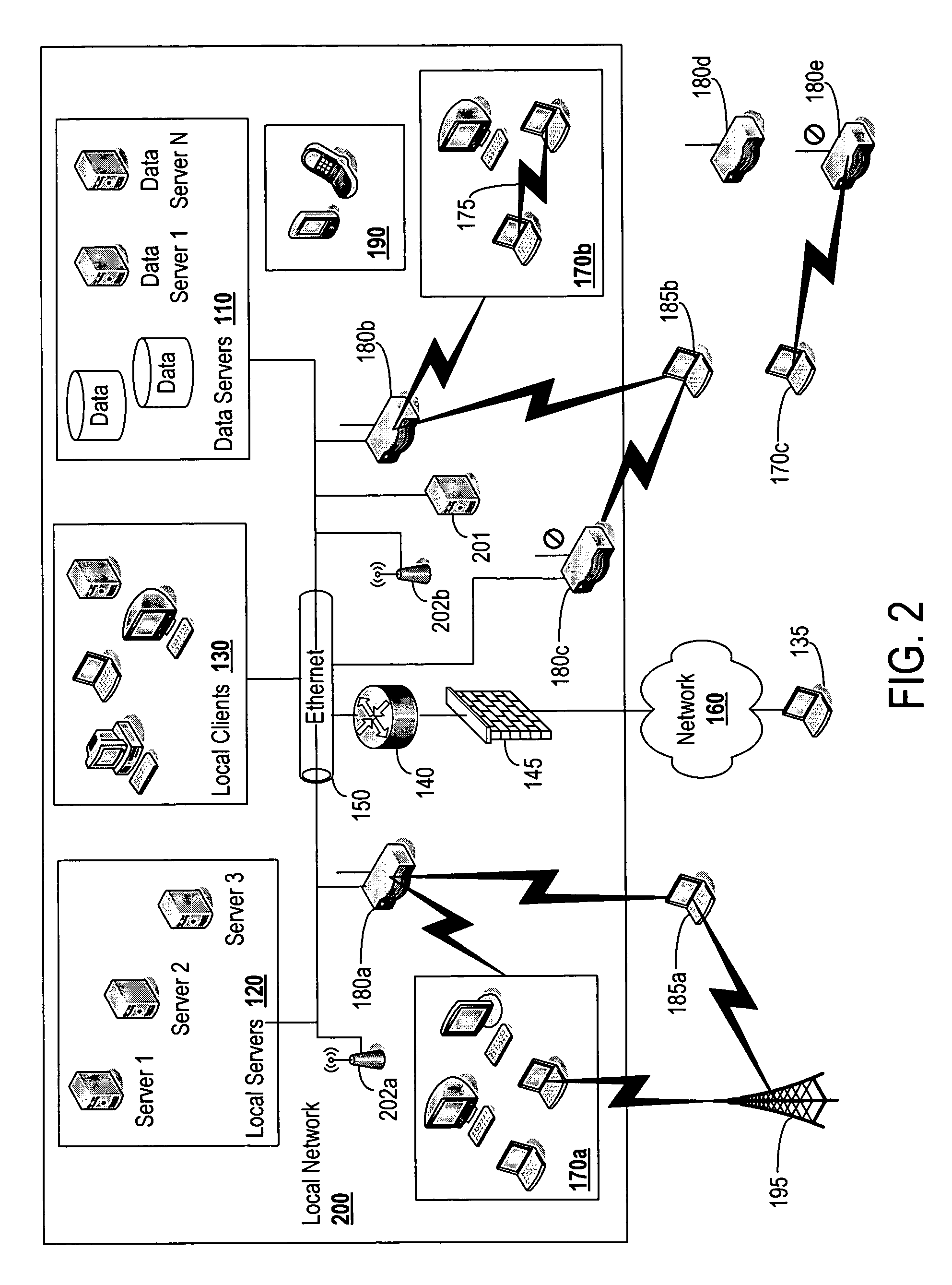
Globally accessible computer network-based broadband communication system with user-controllable quality of information delivery and flow priority
A method for providing broadband communications over a multi-layered network having a plurality of Open System Interconnection (OSI) Reference Model layers functioning therein includes monitoring at least one OSI reference model layer functioning in the multi-layered network. A quality of service event is determined whether to have occurred in the multi-layered network. The quality of service event is determined to have occurred at a layer N in the OSI reference model. Network provisioning is changed at a layer less than N in response to the quality of service event, and a signal is provided when the network provisioning at the layer less than N has been changed. A system for providing broadband communications includes a multi-layered network, a network monitor, and a network controller. The multi-layered network has a plurality of Open System Interconnection (OSI) reference model layers functioning therein. The network monitor is coupled to the multi-layered network, and the network monitor is adapted to monitor at least one OSI reference model layer functioning in the multi-layered network, determine that a quality of service event has occurred in the multi-layer network, and determine that the quality of service event occurred at a layer N in the OSI reference model. The network controller is coupled to the multi-layered network, and the network monitor is adapted to respond to the quality of service event in the multi-layered network by changing the network provisioning at a layer less than N.
Owner:UNWIRED BROADBAND INC
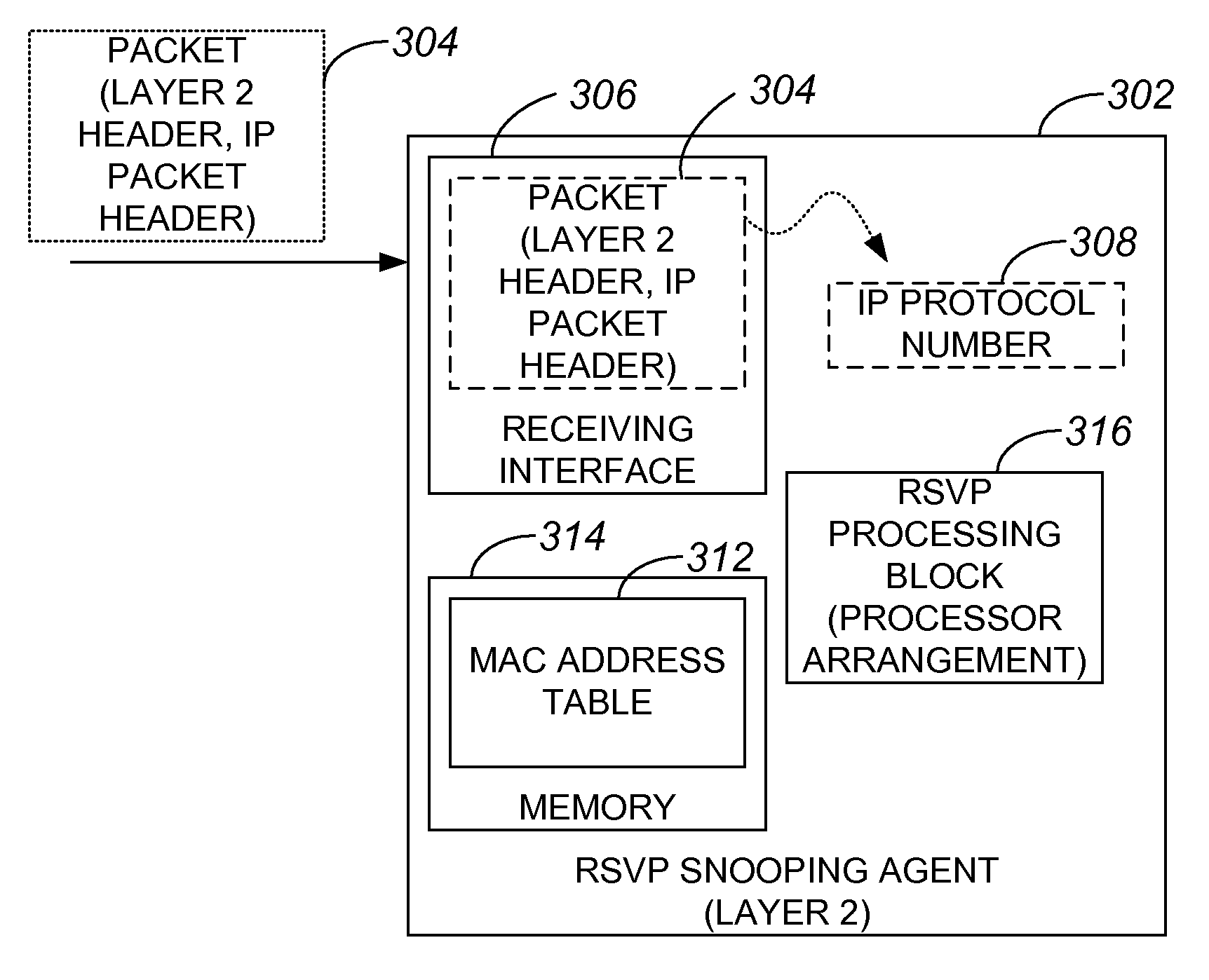
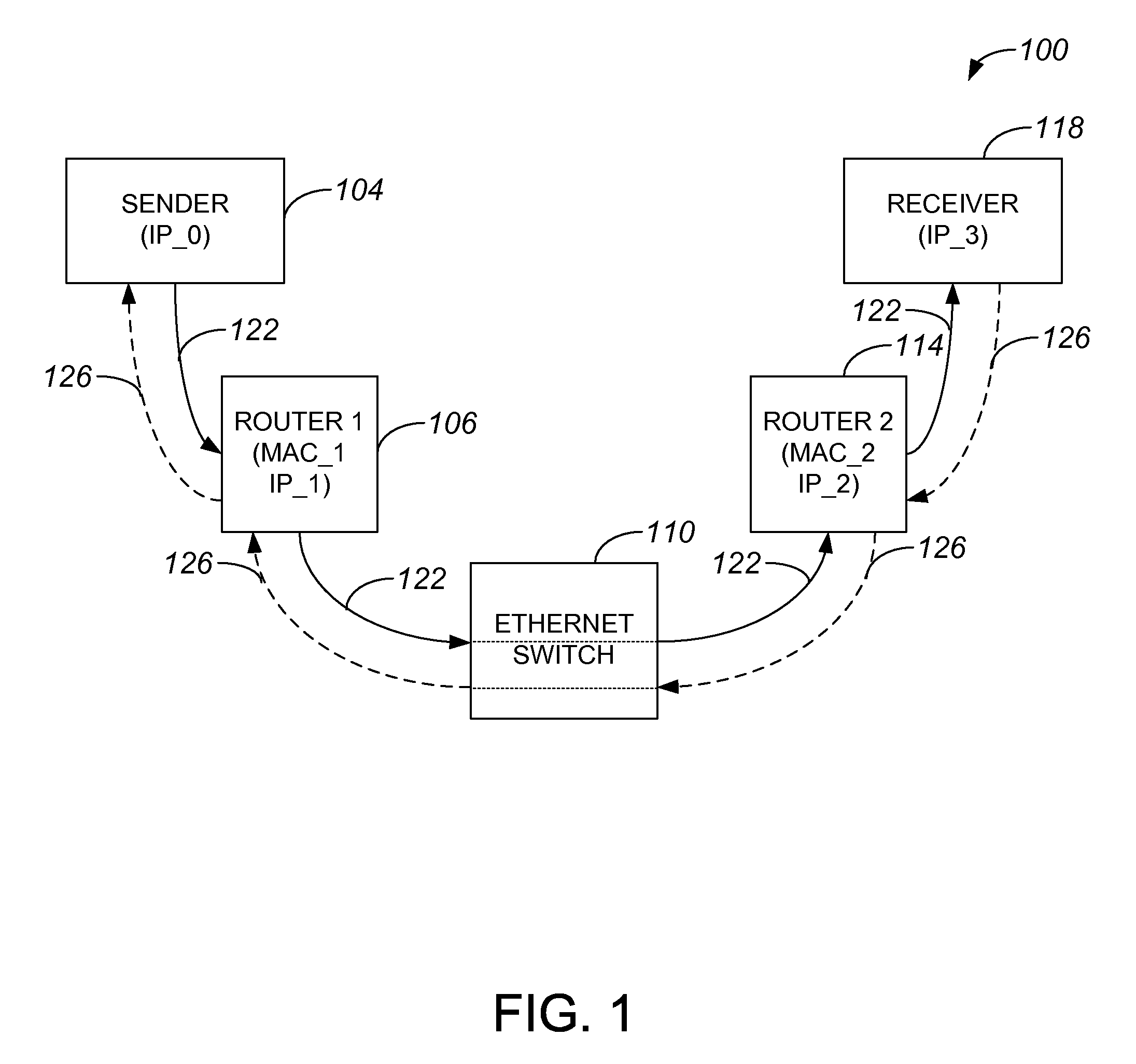
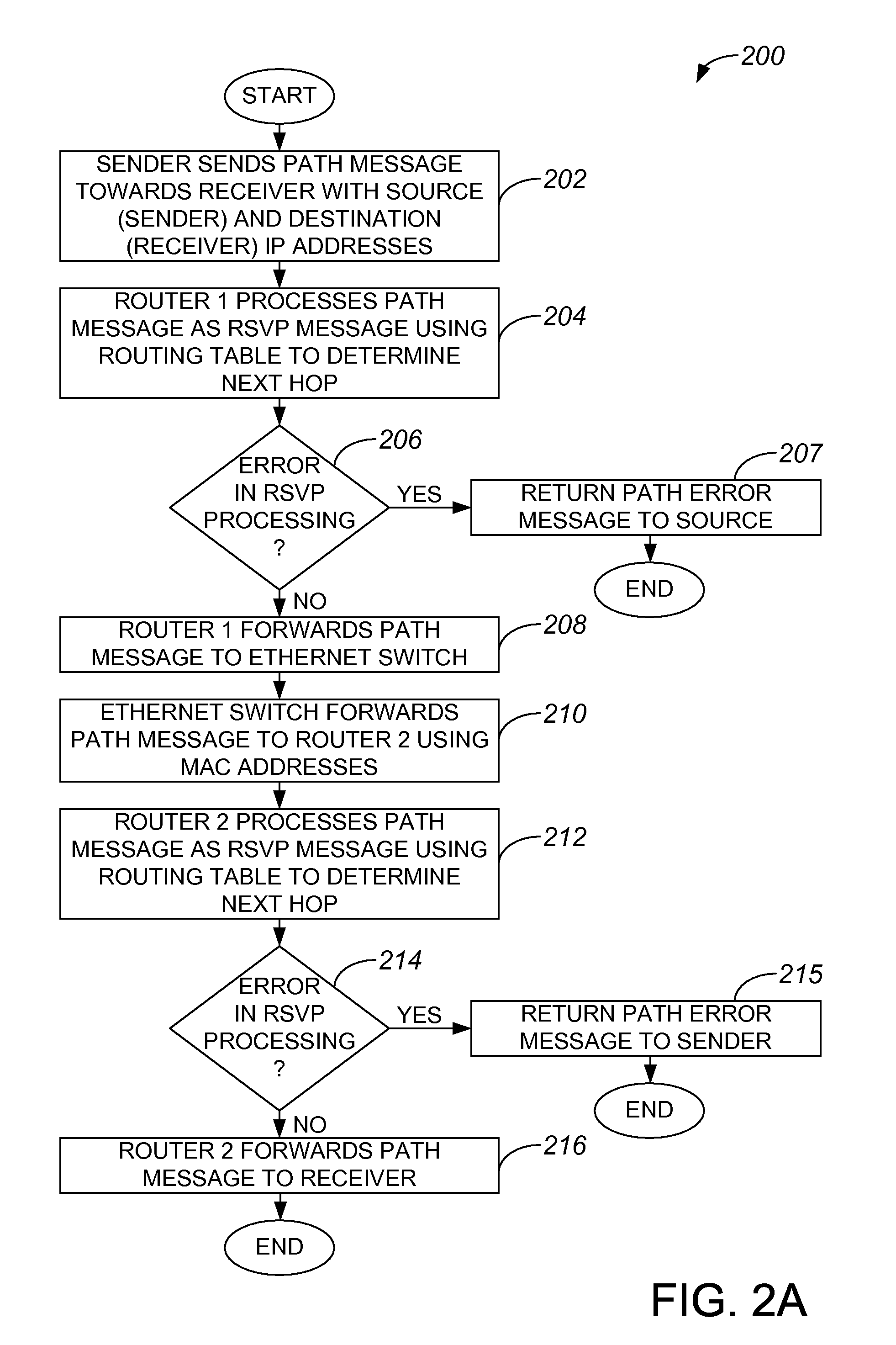
Snooping of on-path IP reservation protocols for layer 2 nodes
ActiveUS20080075089A1Data switching by path configurationReference modelOpen Systems Interconnection
Methods and apparatus for enabling a layer 2 node associated with an open systems interconnection (OSI) reference model to perform resource reservation protocol (RSVP) processing are disclosed. According to one aspect of the present invention a layer 2 device associated with an OSI reference model includes a first interface, a processing arrangement, and a second interface. The first interface intercepts a message associated with a on-path signaling protocol for at least one selected from a group including resource reservation and admission control at a layer above layer 2. The processing arrangement processes the message, and the second interface sends the message.
Owner:CISCO TECH INC
Wireless intelligent network protocol with ultra-low power consumption
ActiveCN102761941ALow costReduce power consumptionPower managementNetwork topologiesFault toleranceLine sensor
The invention discloses a wireless intelligent sensor network protocol (ATZGB-SleepTree) with ultra-low power consumption. The protocol includes a physical layer, an MAC (media access control) layer, a link layer, a network layer and an application layer according to an OSI (open system interconnection) reference model. A traditional wireless sensor protocol and even an existing ZigBee protocol are quite difficult to meet the requirements of low power consumption, low cost, high fault tolerance and the like of a wireless sensor, and under the circumstance, the ATZGB-SleepTree protocol arises at the historic moment. The ATZGB-SleepTree constructs a wireless network which is low in cost and power consumption, high in sensitivity, reliability and real-time control and transmission, highly flexible in work pattern and configuration, automated in link management, capable of achieving AES (advanced encryption standard) data encryption, supportive to multiple bands and multiple wireless rates and capable of achieving synchronous sleep and synchronous wake-up of all nodes of the whole network, routing fault-tolerance and automatic recovery and is used for substituting for traditional wireless and cable network transmission modes.
Owner:北京云天创科技有限公司
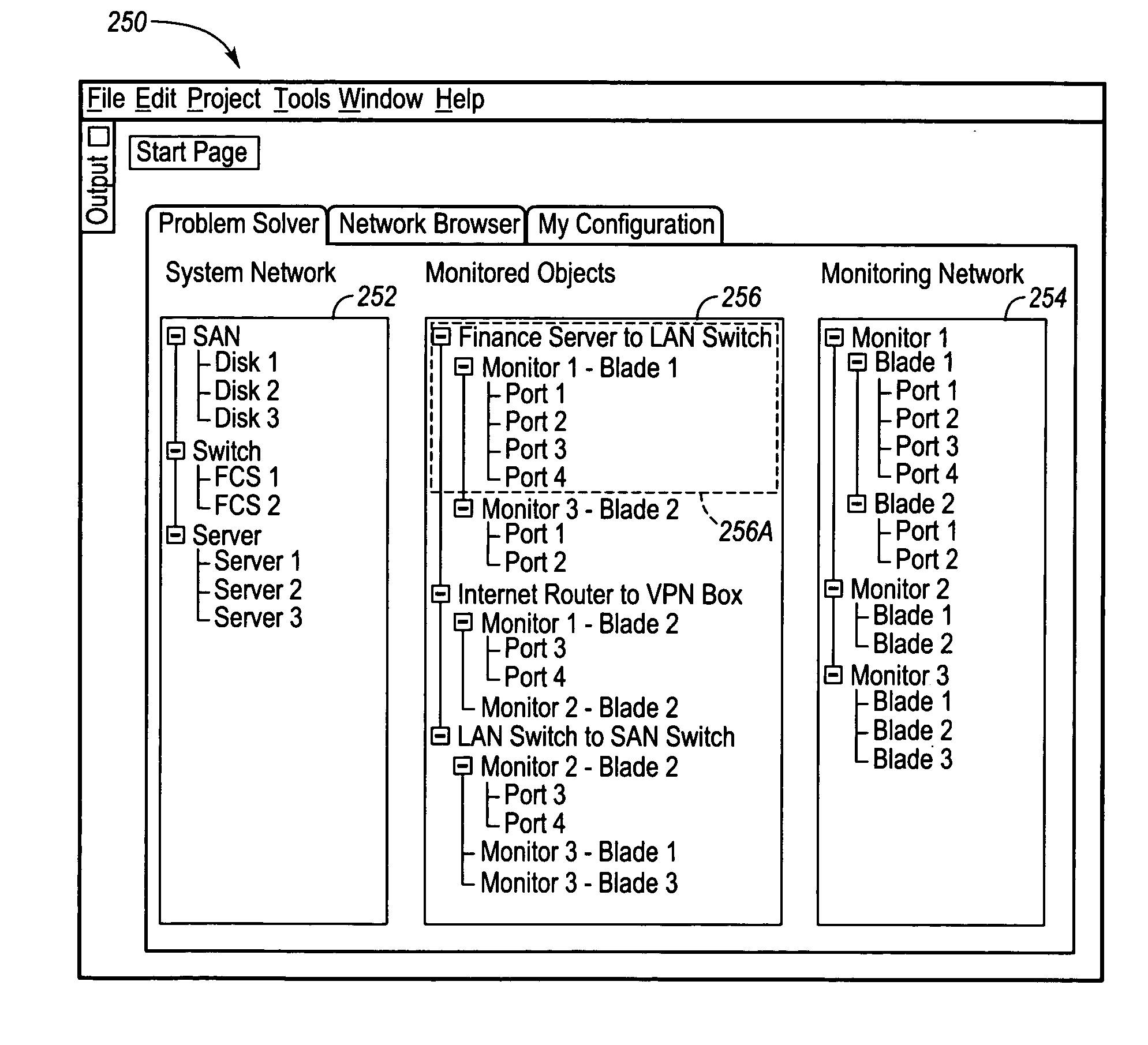
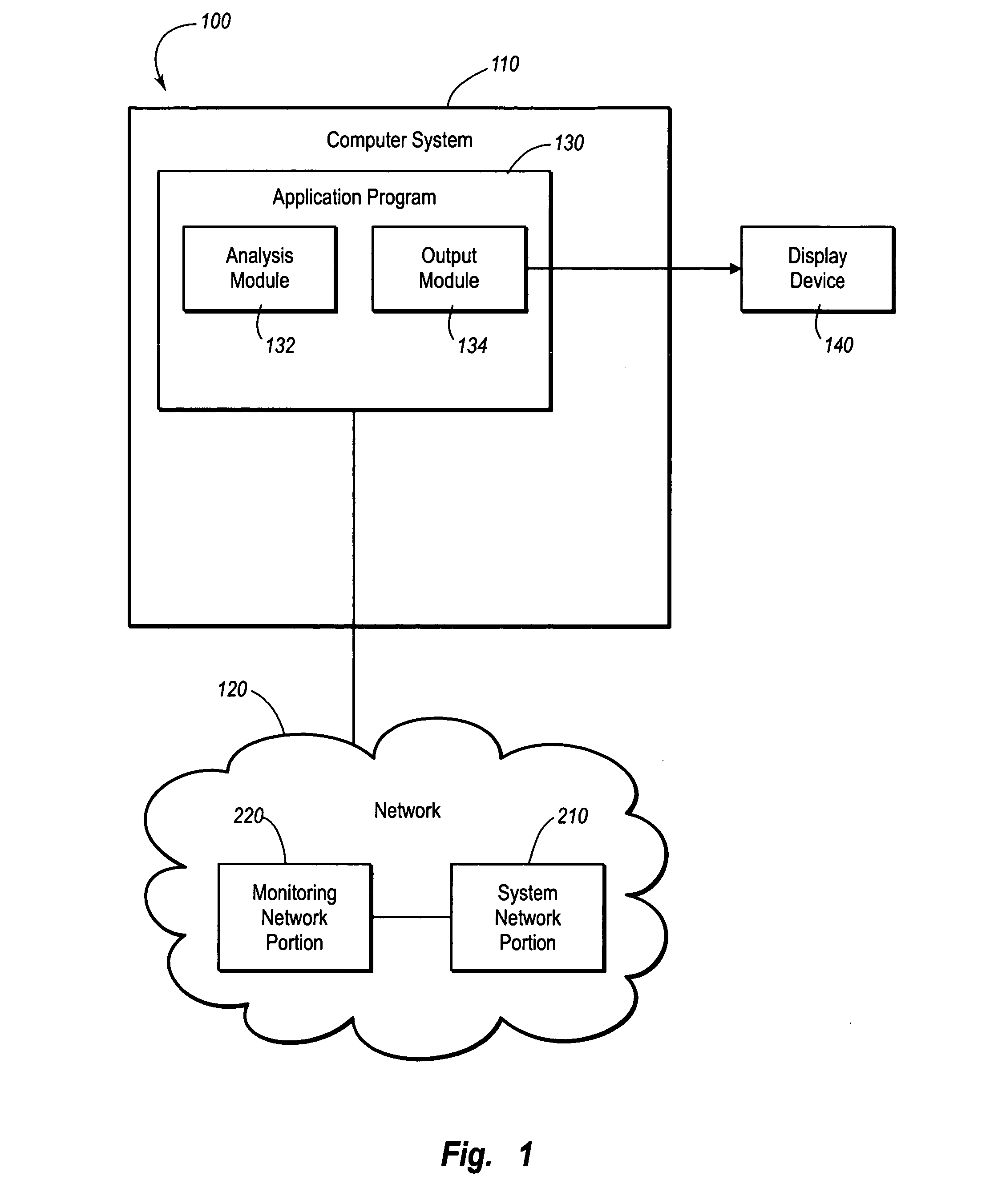
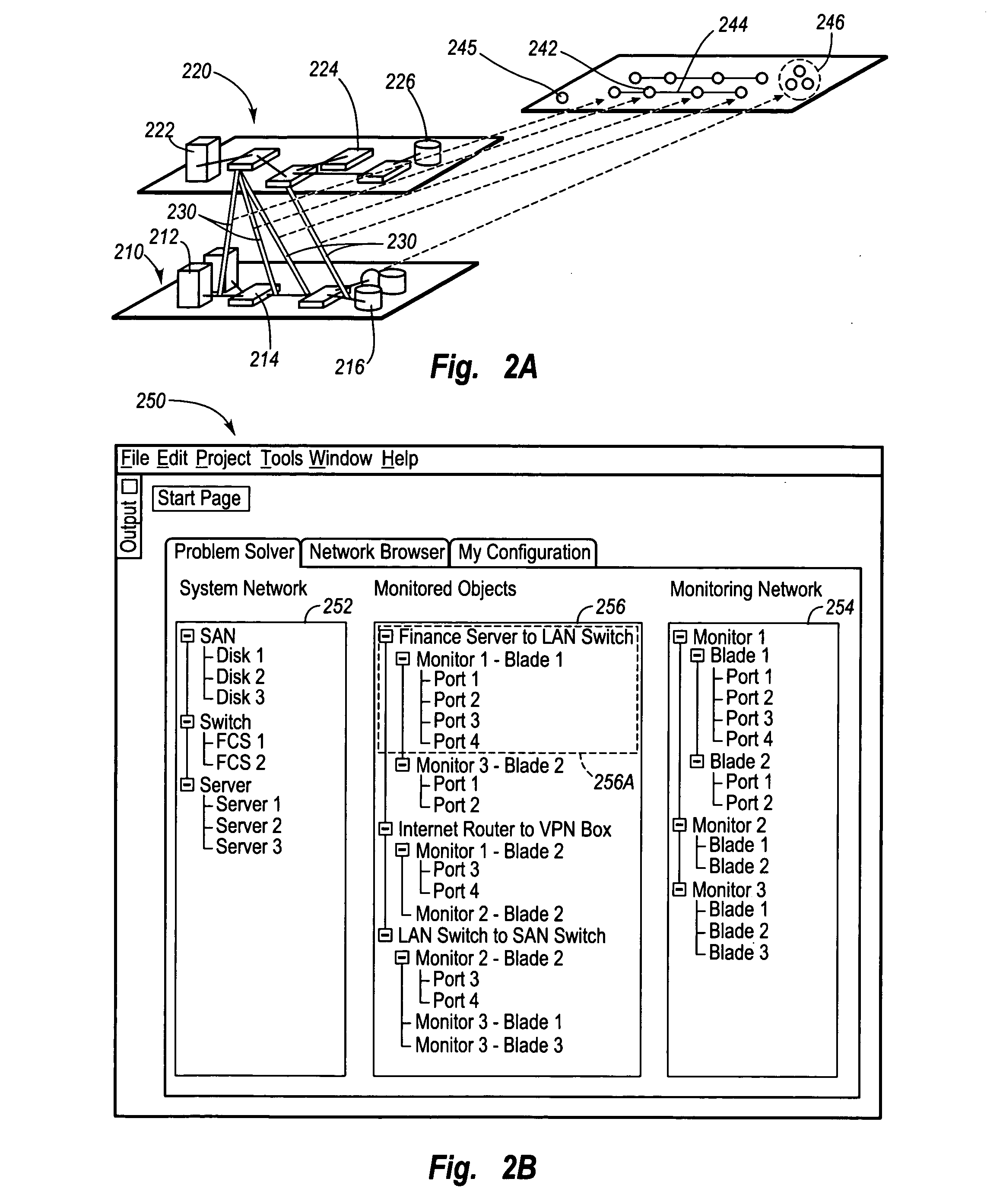
Method of creating a virtual network topology for use in a graphical user interface
InactiveUS20050091361A1Digital computer detailsData switching networksGraphicsGraphical user interface
A method of graphically depicting various network elements of a communications network in a virtual network topology via a graphical user interface (“GUI”) is disclosed. The virtual network topology depicts logical relationships between network components instead of merely depicting physical network component relationships. A system network subset and a monitoring network subset of the communications network are defined according to one layer N of the open system interconnection (“OSI”) layer model. Various logical links are established between the system network and the monitoring network. A virtual topology is defined that depicts the various logical links according to another OSI layer M. The virtual topology is displayed via a GUI that enables modification of the logical links to occur.
Owner:FINISAR
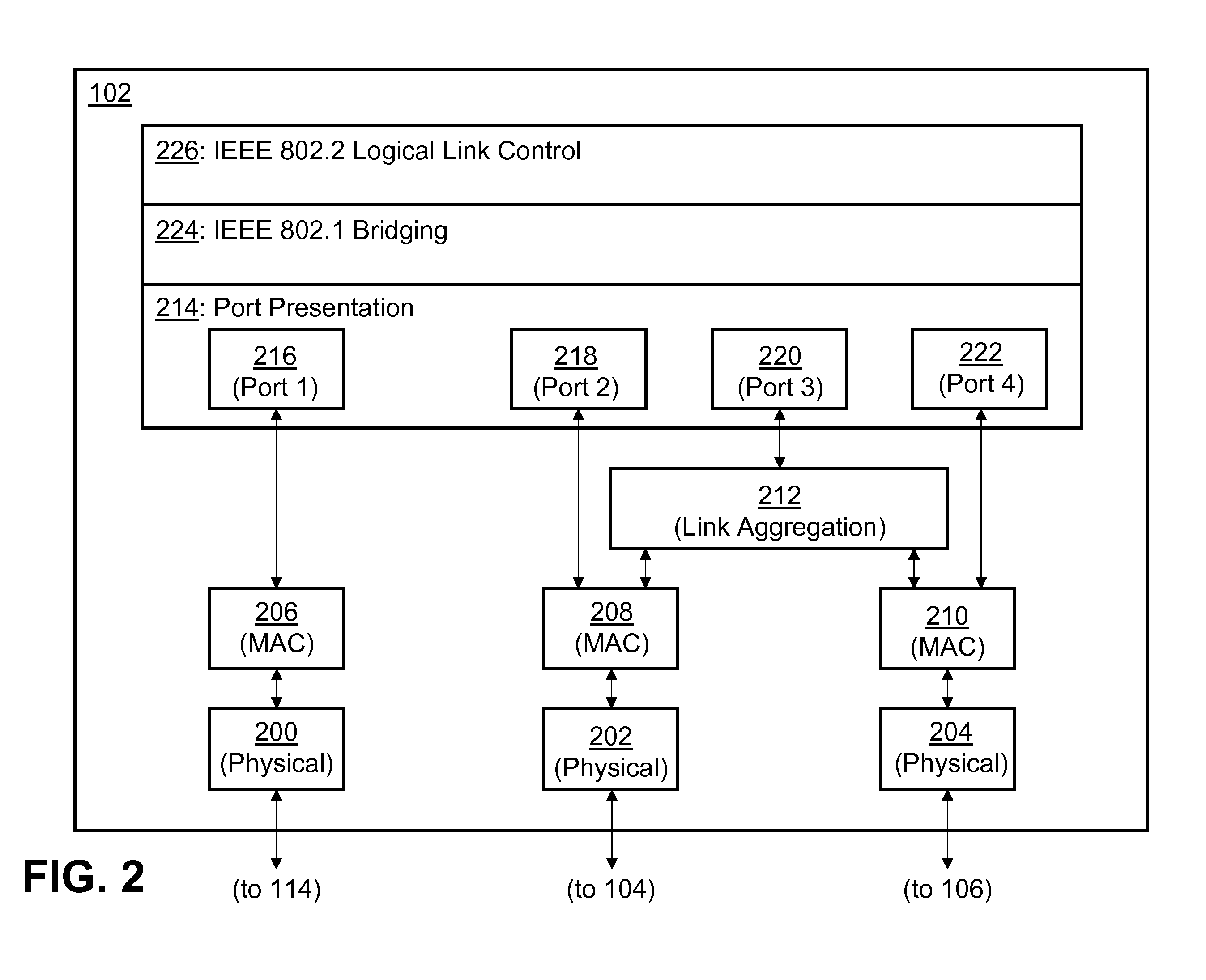
Aggregating ports while allowing access to singleton ports
InactiveUS20110085562A1Low costEnergy efficient ICTData switching by path configurationOpen Systems InterconnectionPointing device
Disclosed is a method for aggregating parallel data links connecting two end-point devices into a logical link. If one of the parallel data links is a multi-point link, then an end-point device can still access that link to route traffic to an end station on the link (that is, to a device other than the other end-point device of the logical data link). In the terminology of this disclosure, the logical aggregated link is accessed through an “aggregated port” on an end-point device, while the constituent multi-point link is accessed directly through a “singleton port.” By assigning a smaller cost to the aggregated port than to the singleton port, embodiments avoid creating routing loops. In some embodiments, the aggregation is performed at Layer 2 of the Open System Interconnection seven-layer protocol model. Then, the methods of the present invention work well with existing IEEE 802.1 bridging architectures and protocols.
Owner:GOOGLE TECH HLDG LLC
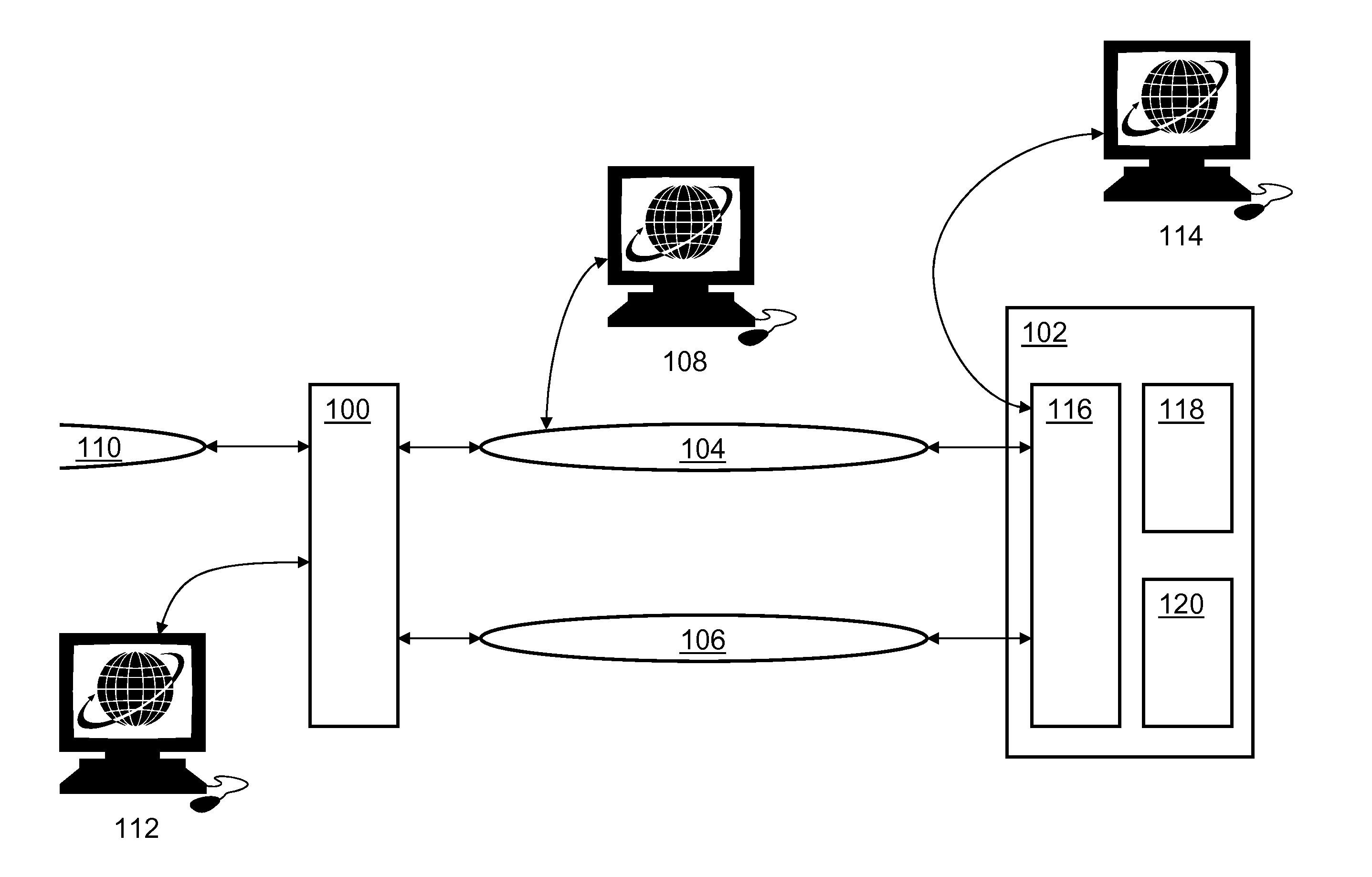
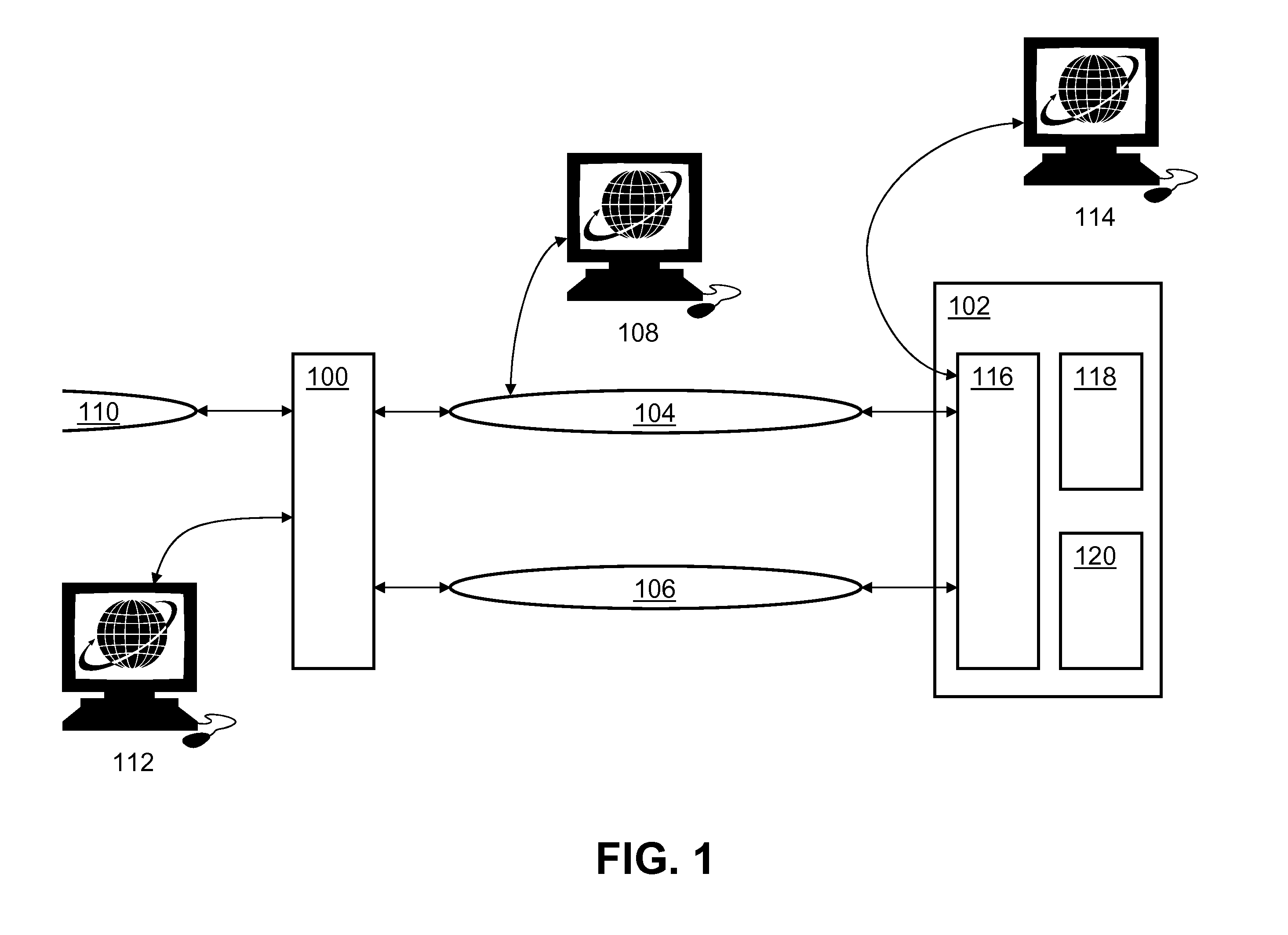
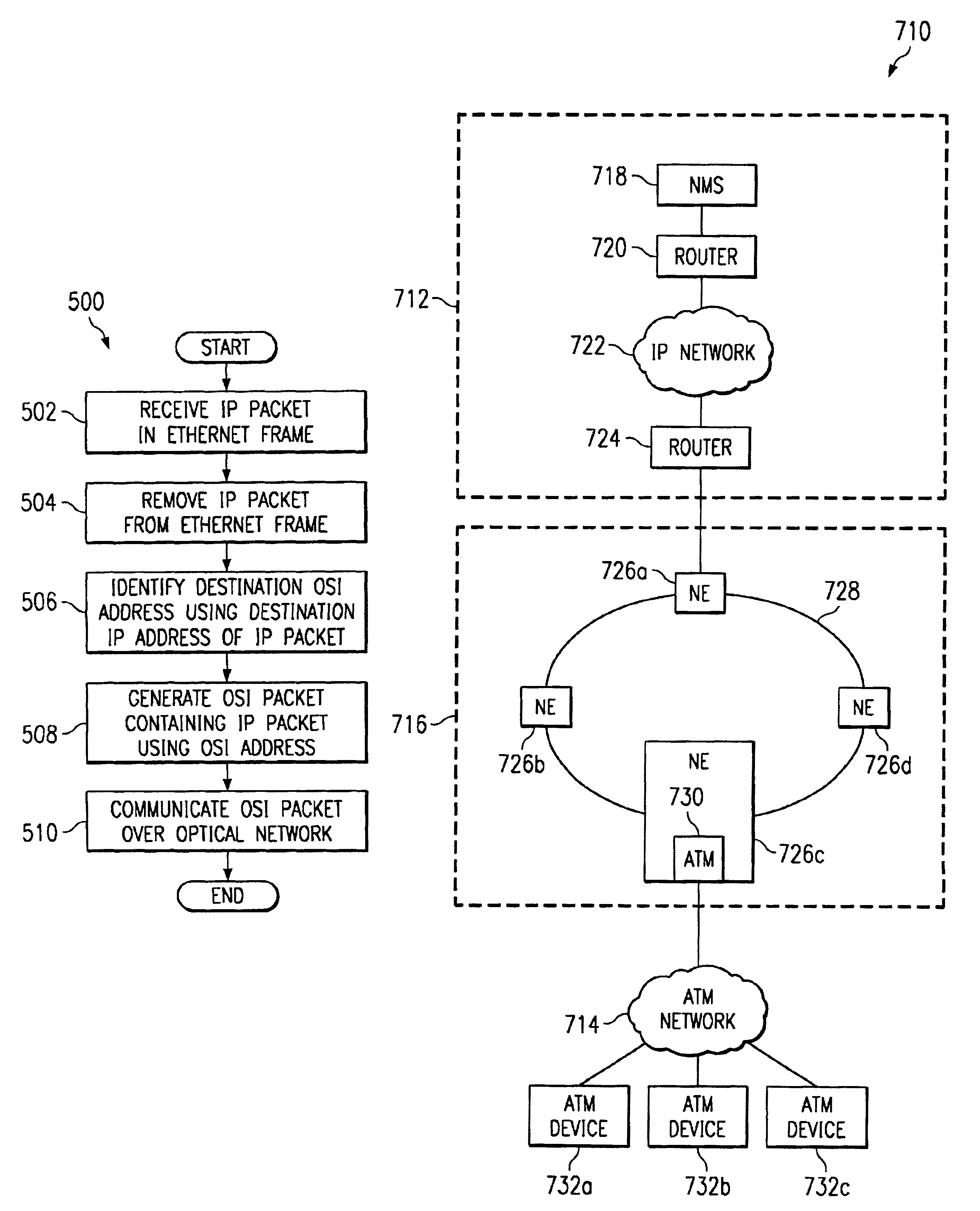
Method and system for transporting packet-switched control traffic in an optical network
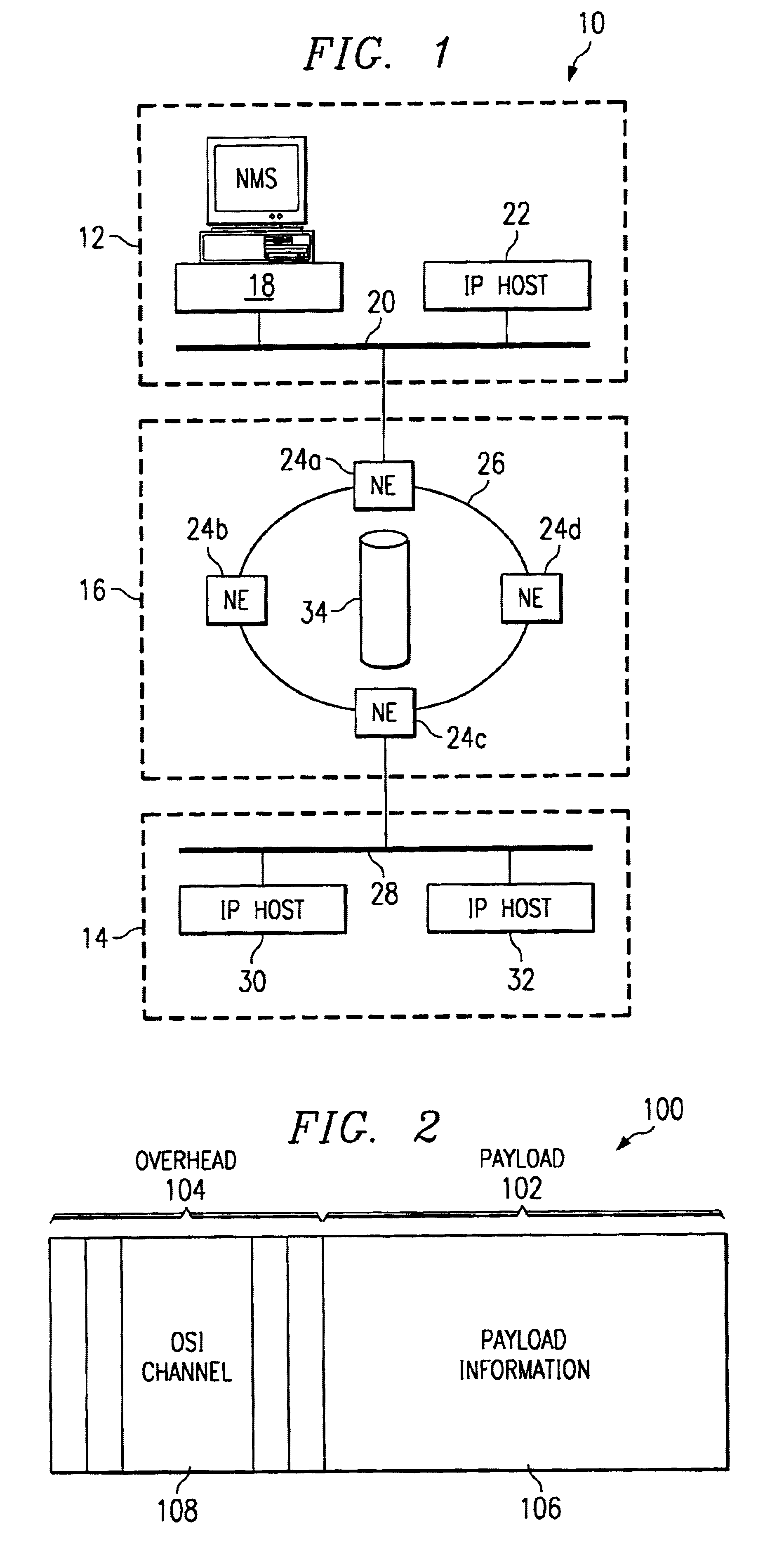
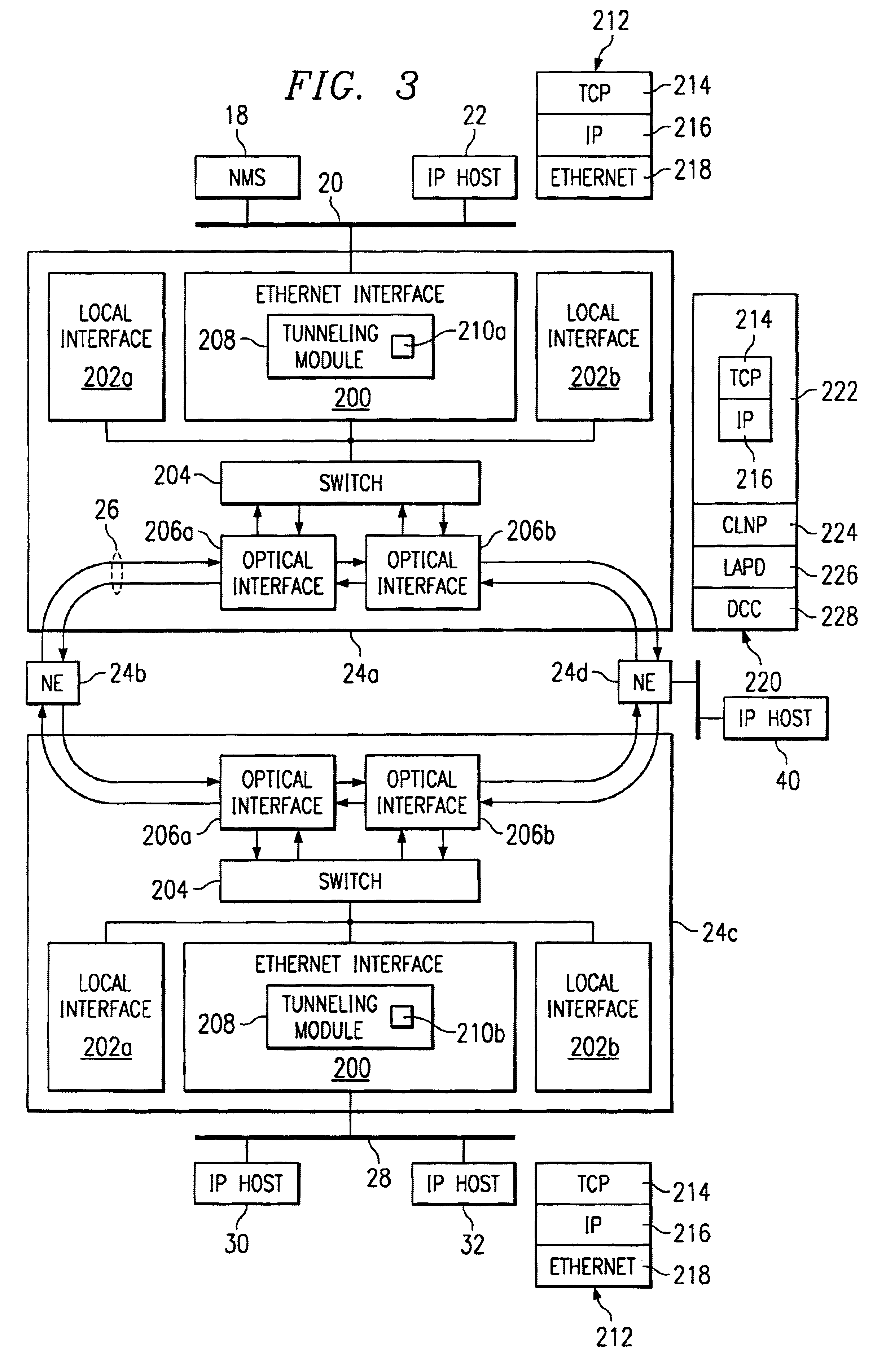
InactiveUS6856620B1Eliminate leastReduce leastTime-division multiplexData switching by path configurationOpen Systems InterconnectionDatagram
A method for transporting packet-switched control traffic in an optical network includes receiving a packet-switched datagram comprising a destination address. The method also includes identifying a destination Open Systems Interconnection (OSI) address of a destination network element in the optical network based on the destination address of the datagram. In addition, the method includes generating an OSI packet comprising the datagram and the destination OSI address, and transmitting the OSI packet on the optical network in an OSI channel of a Synchronous Optical Network (SONET) frame.
Owner:FUJITSU LTD
Routing based on dynamic classification rules
ActiveUS20080084866A1Time-division multiplexData switching by path configurationReference modelMultiple attribute
A computer system that forwards data packets is described. During operation, the system receives a data packet on a first interface and classifies the data packet to determine a corresponding destination. This classification is based on dynamically configured classification rules that include multiple attributes corresponding to multiple layers in an Open System Interconnect (OSI) Reference model. Then, the system provides the data packet on a second interface corresponding to the destination.
Owner:ORACLE INT CORP
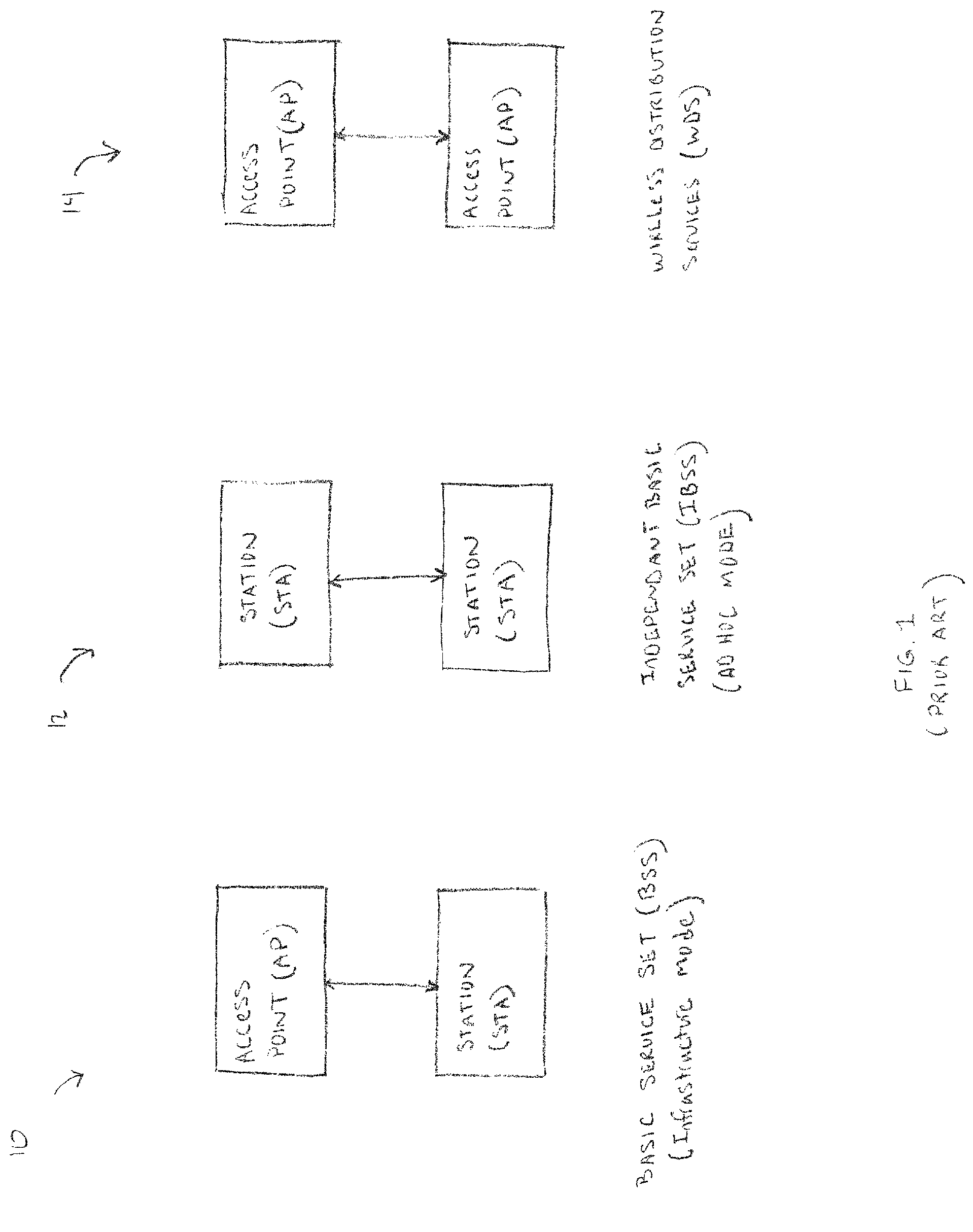
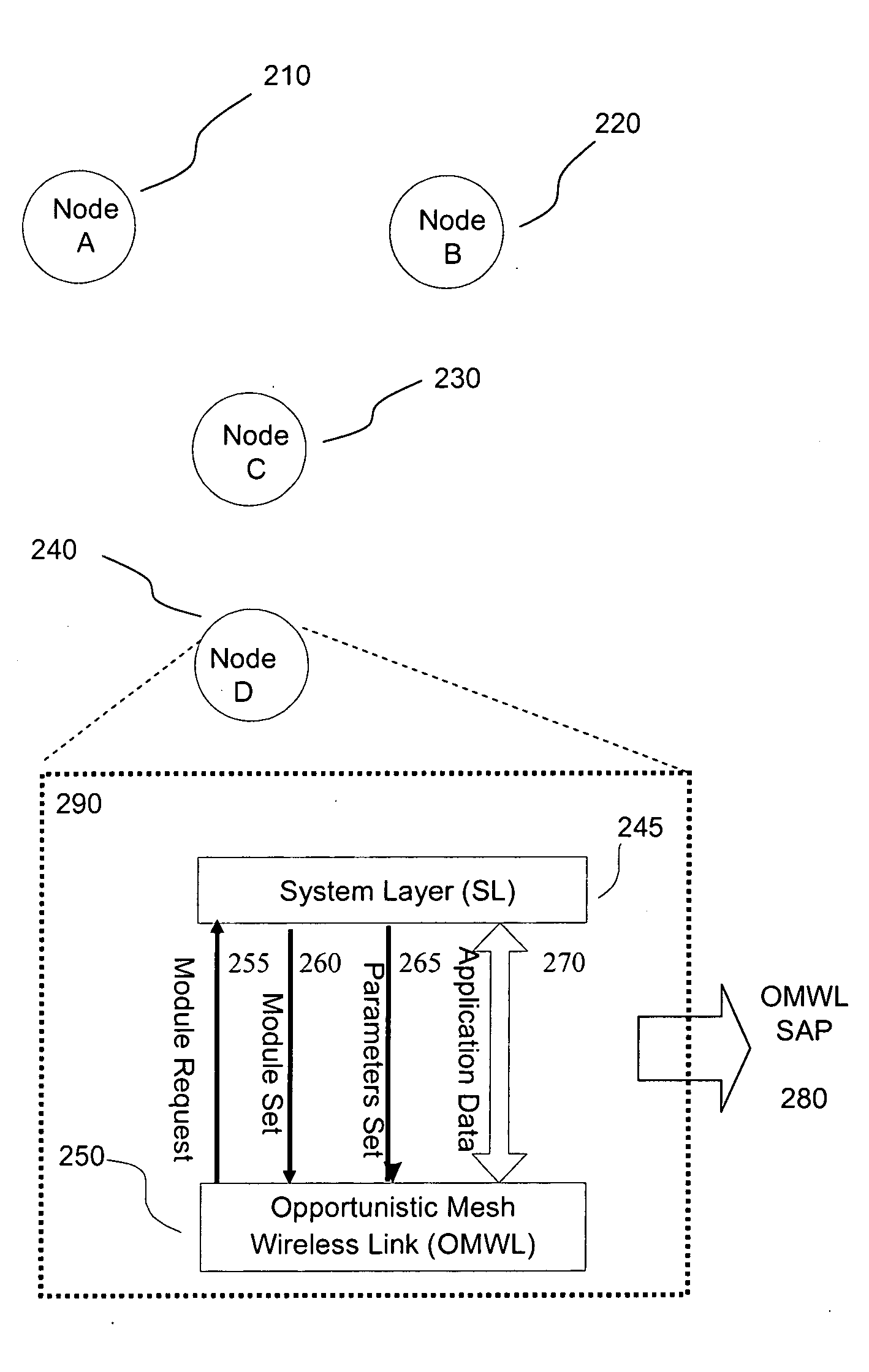
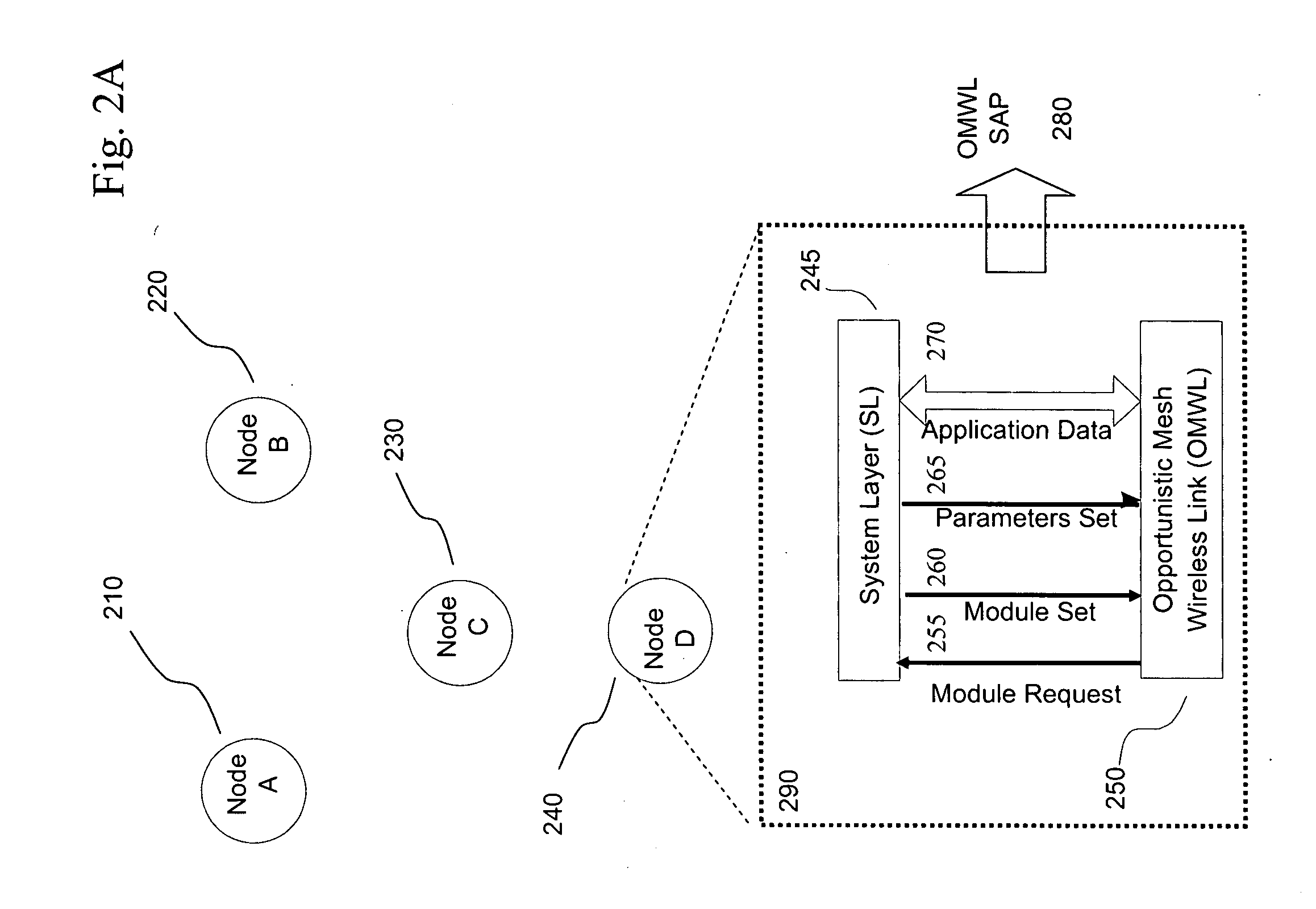
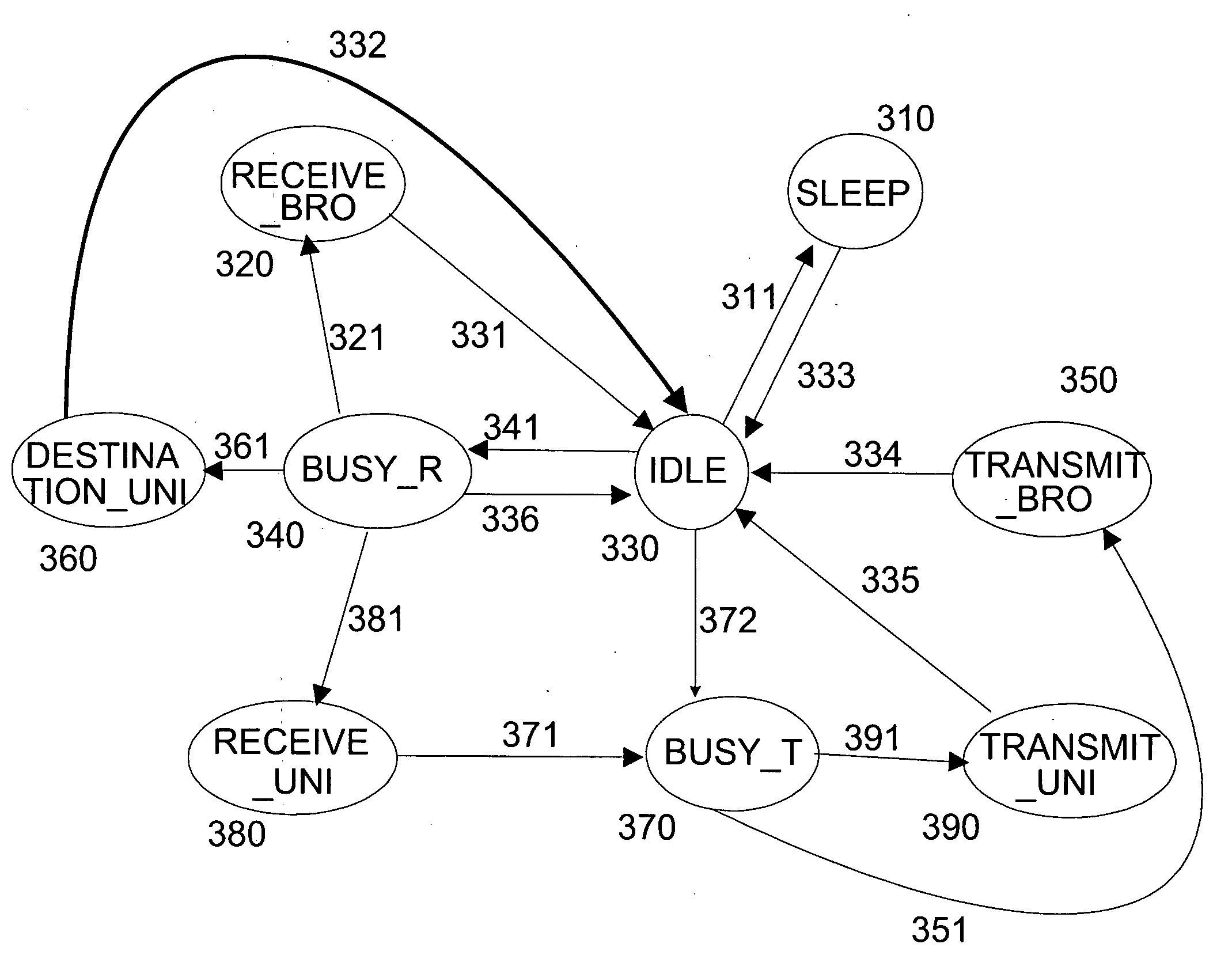
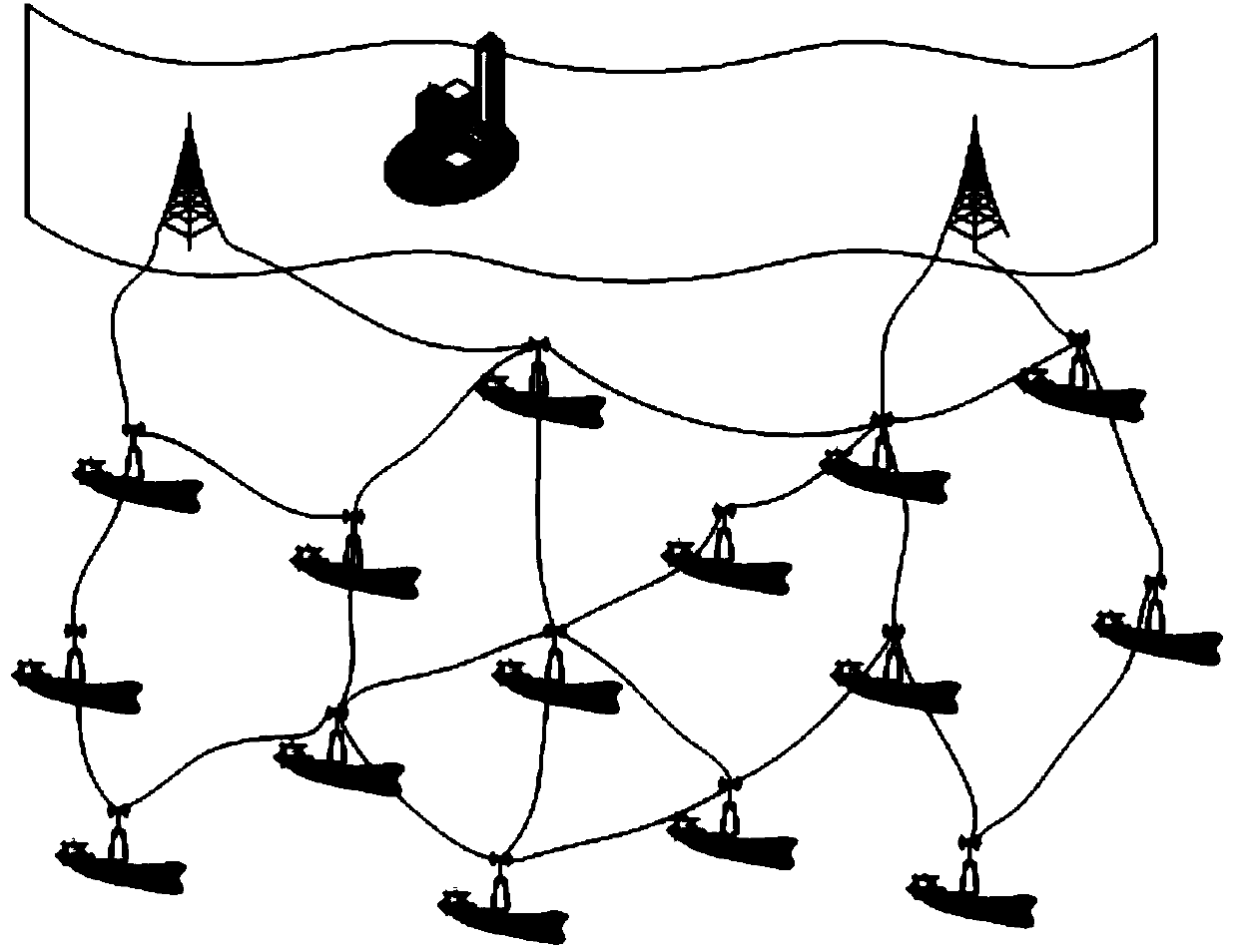
Opportunistic wireless mesh network methods
ActiveUS20080075010A1Improve performanceMinimal overheadBroadcast with distributionEnergy efficient ICTReference modelWireless mesh network
The invention relates to opportunistic wireless mesh networks which operate under random networking conditions. Such random network conditions typically limit the effectiveness of prior art wireless mesh networks, and more particularly to those supporting low power devices within the wireless network. Random network conditions include: random power supply, random node distribution, random node mobility, high mobility of nodes, random wireless link fluctuations, and random application traffic. The opportunistic wireless mesh network utilizes a two-layer architecture Embedded Wireless Interconnect (EWI) framework, which is adopted as the architecture reference model. A mesh network according to the invention supports opportunistically determining both mesh interconnections and network transmission routes by providing nodes with broadcast modules and unicast modules. The methods provide novel low power opportunistic wireless mesh networks that support interconnection with existing network infrastructures such as Open System Interconnect (OSI) based wired or wireless networks. Network embodiments provide protocol translation at network borders to allow micro- and macro-mobility management for wireless devices and their associated users. Additionally embodiments of the opportunistic wireless mesh networks address reduction in power consumption.
Owner:SENNET COMM
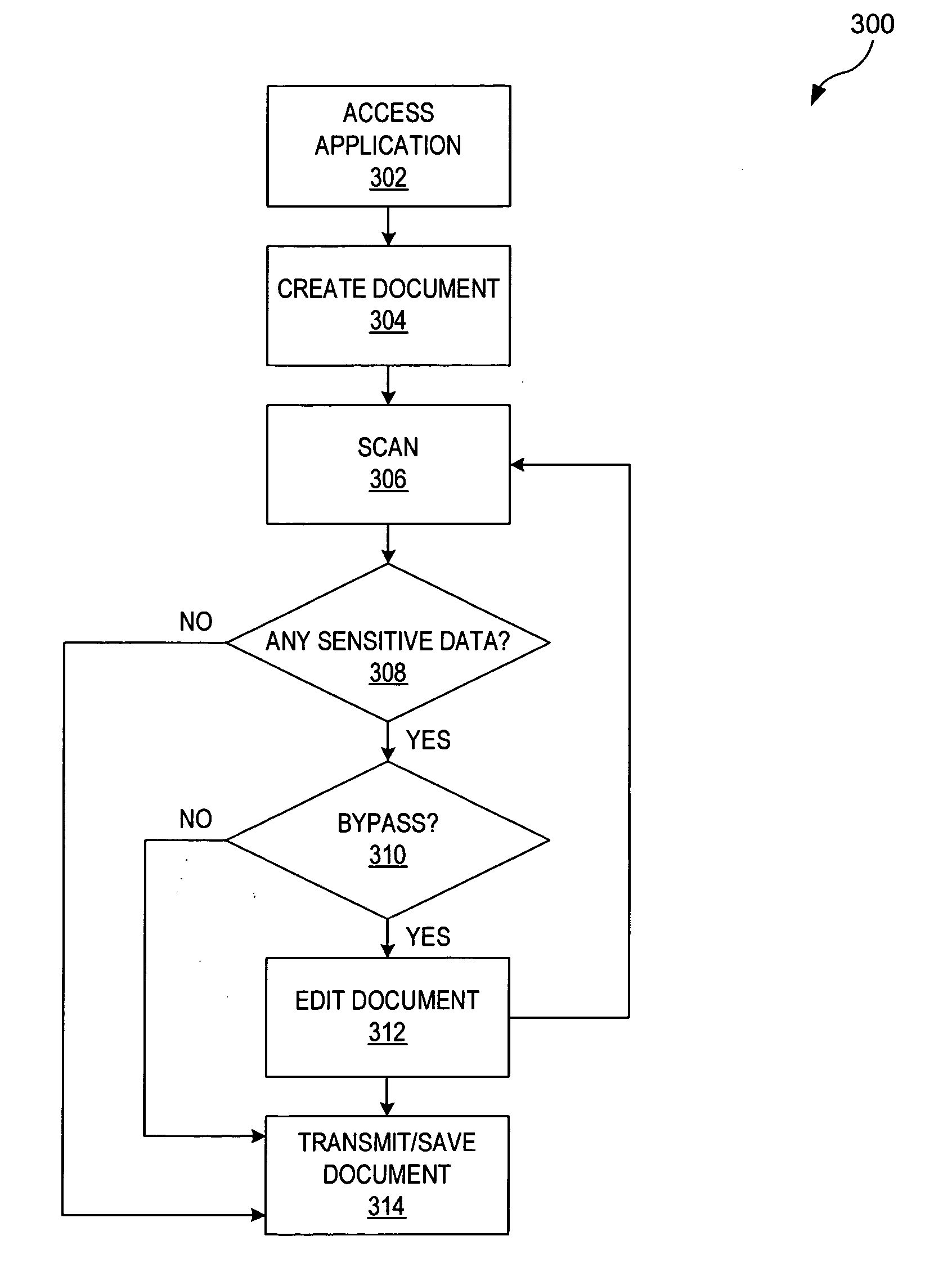
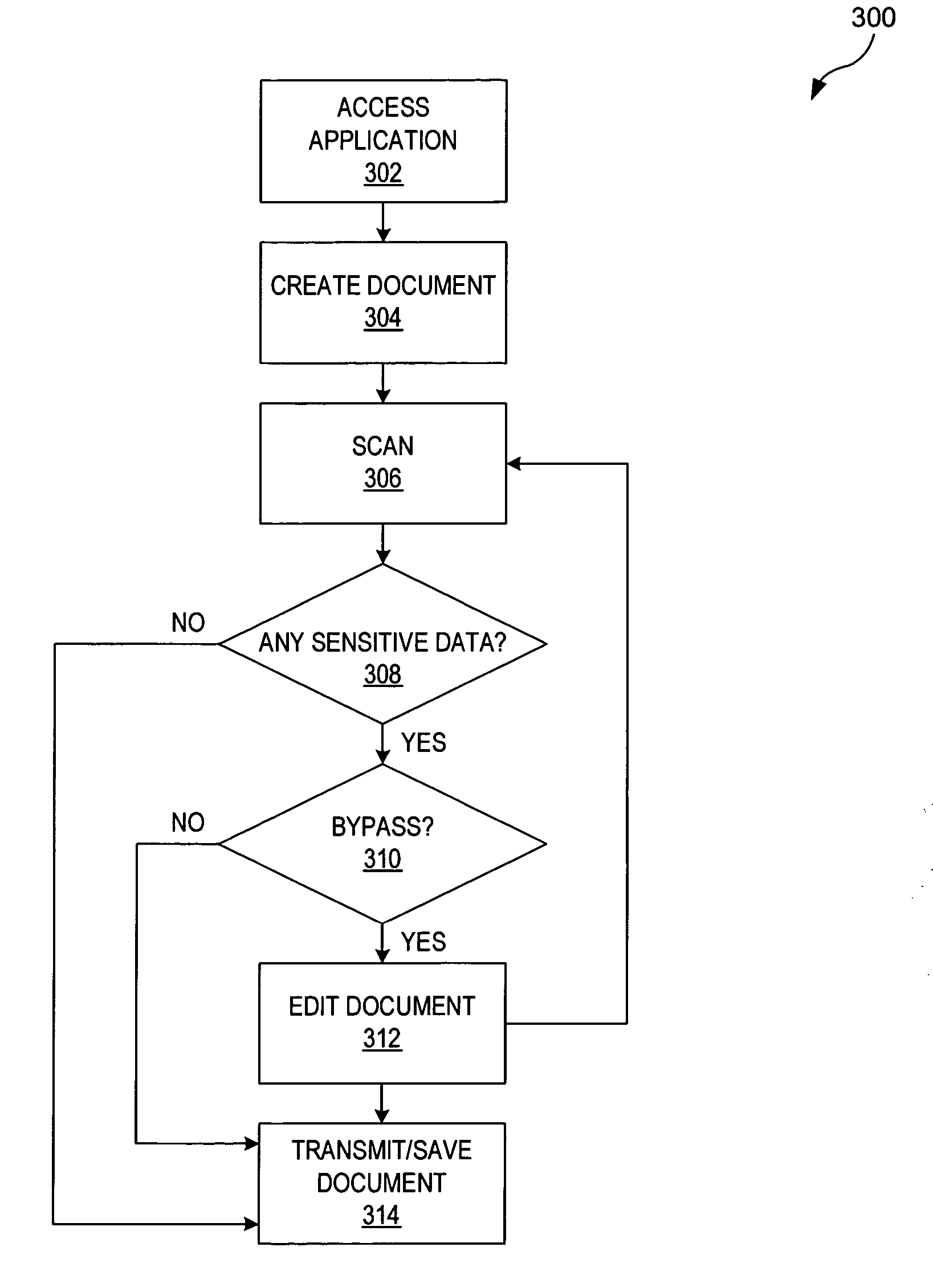
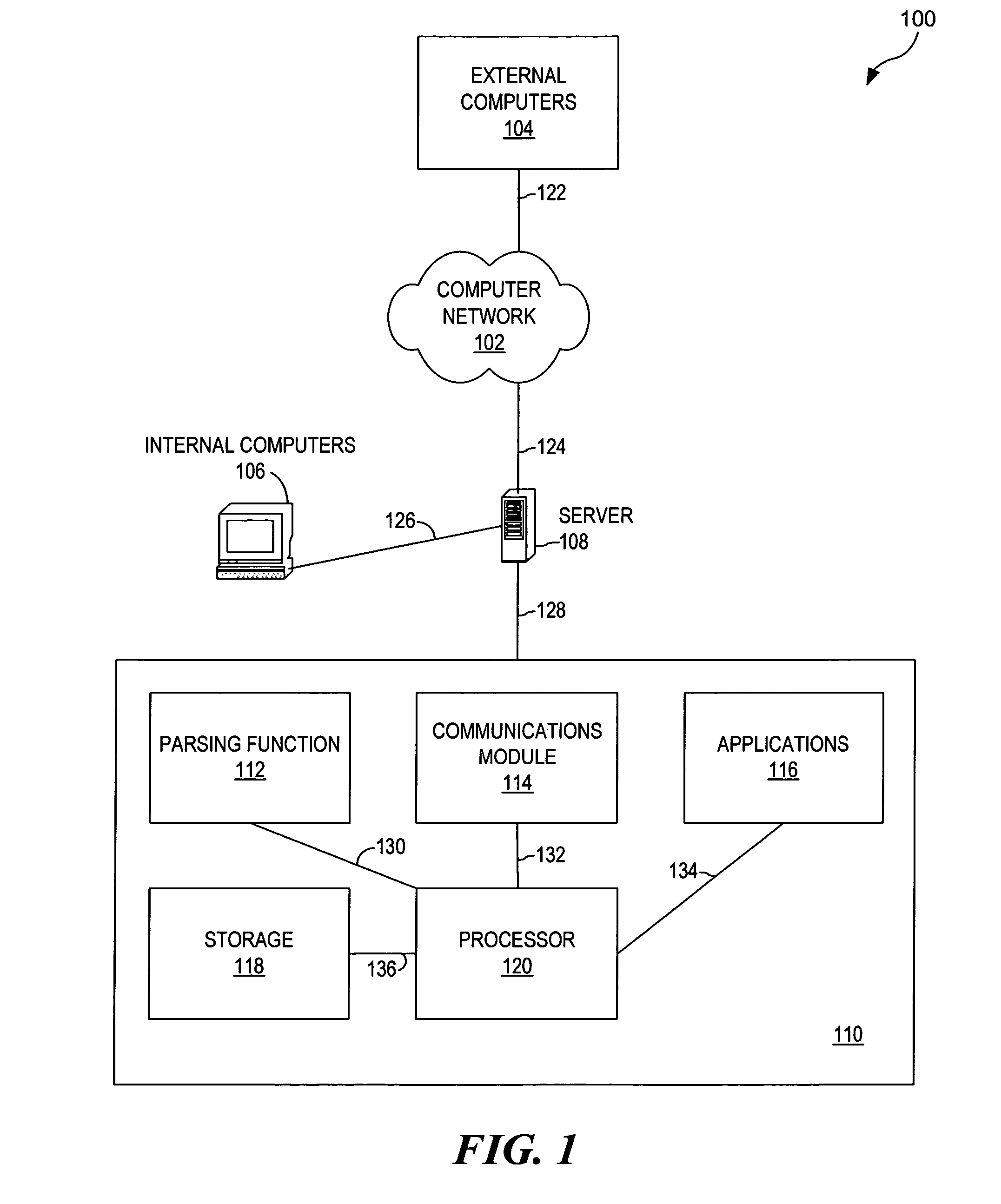
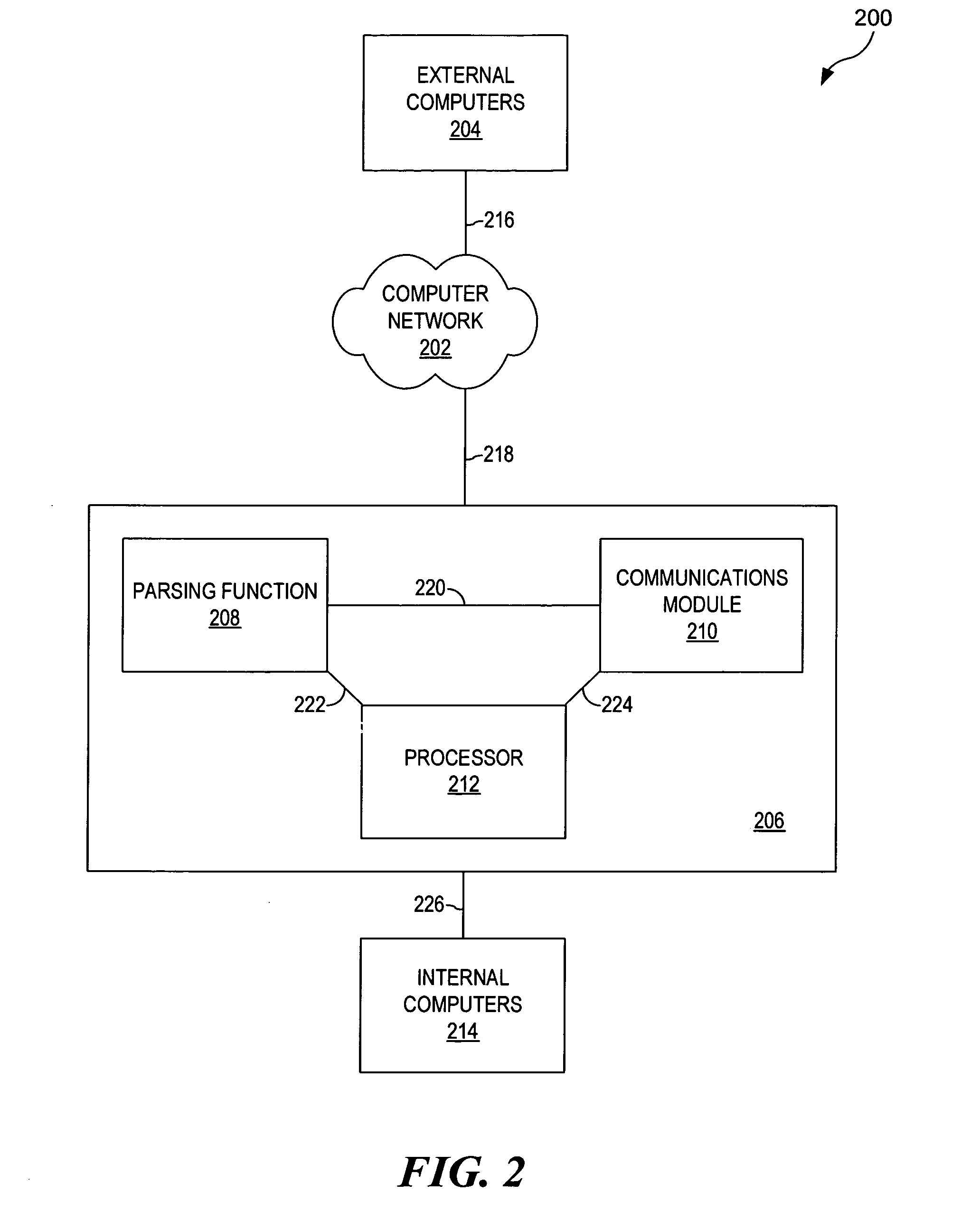
Method and system for monitoring personal computer documents for sensitive data
ActiveUS20050262557A1Memory loss protectionDigital data processing detailsUser verificationThird party
An apparatus, a method, and a computer program are provided for securing transmitted text. Once text has been produced by an application, the potential exists for an unintended third party to obtain sensitive data transmitted over computer networks. However, a parsing function can then operate either on an individual computer or on a network to scan text at an Open Systems Interconnection (OSI) Layer 1 to assist in the prevention of sensitive data transmission. By utilizing the parsing function, text can be scanned for potentially sensitive data by using a variety of techniques, such as a learning algorithm. The sensitive data can then be verified by a user, bypassed, or autostripped.
Owner:KYNDRYL INC
Method and system for monitoring personal computer documents for sensitive data
An apparatus, a method, and a computer program are provided for securing transmitted text. Once text has been produced by an application, the potential exists for an unintended third party to obtain sensitive data transmitted over computer networks. However, a parsing function can then operate either on an individual computer or on a network to scan text at an Open Systems Interconnection (OSI) Layer 1 to assist in the prevention of sensitive data transmission. By utilizing the parsing function, text can be scanned for potentially sensitive data by using a variety of techniques, such as a learning algorithm. The sensitive data can then be verified by a user, bypassed, or autostripped.
Owner:KYNDRYL INC
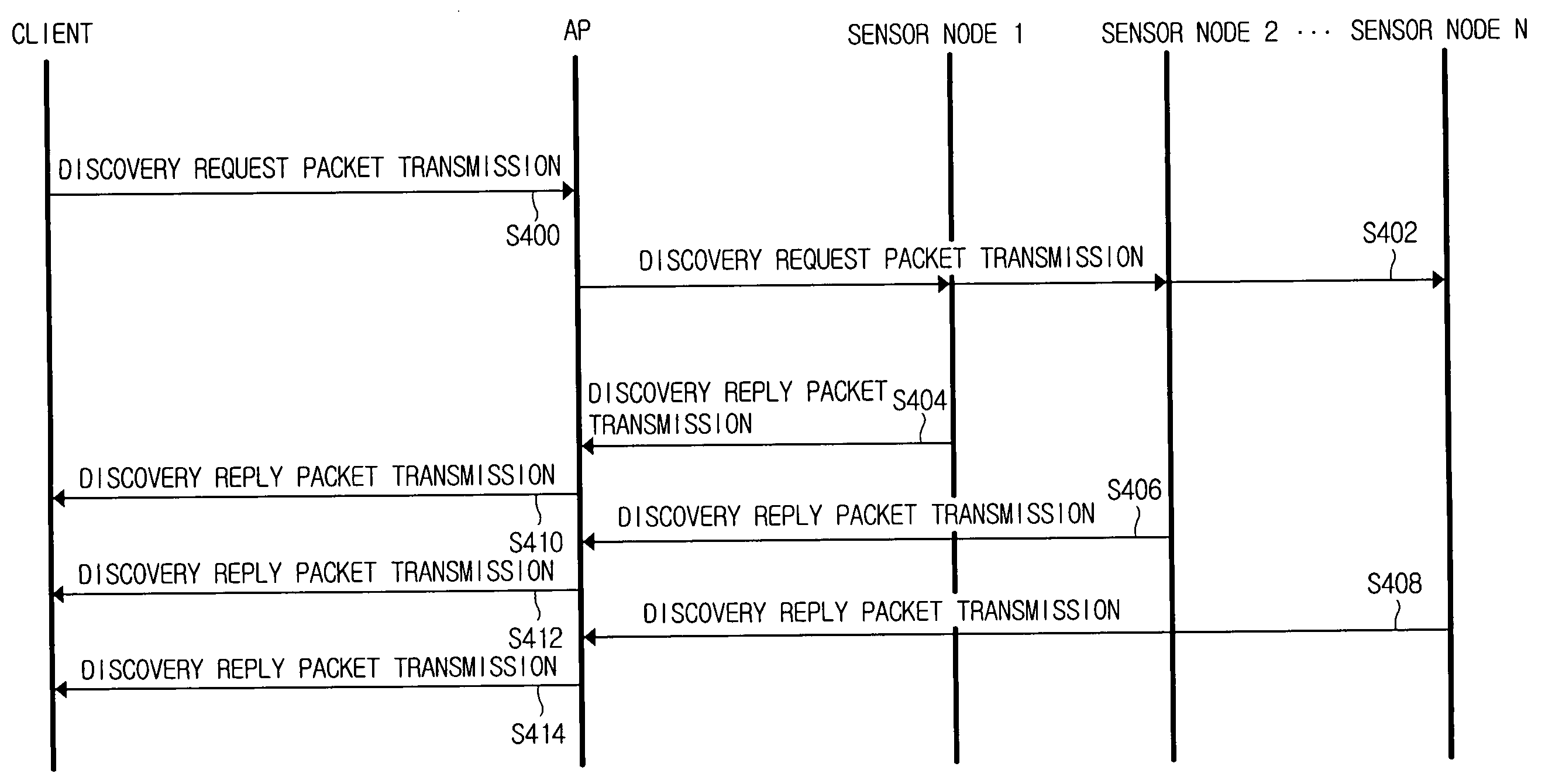
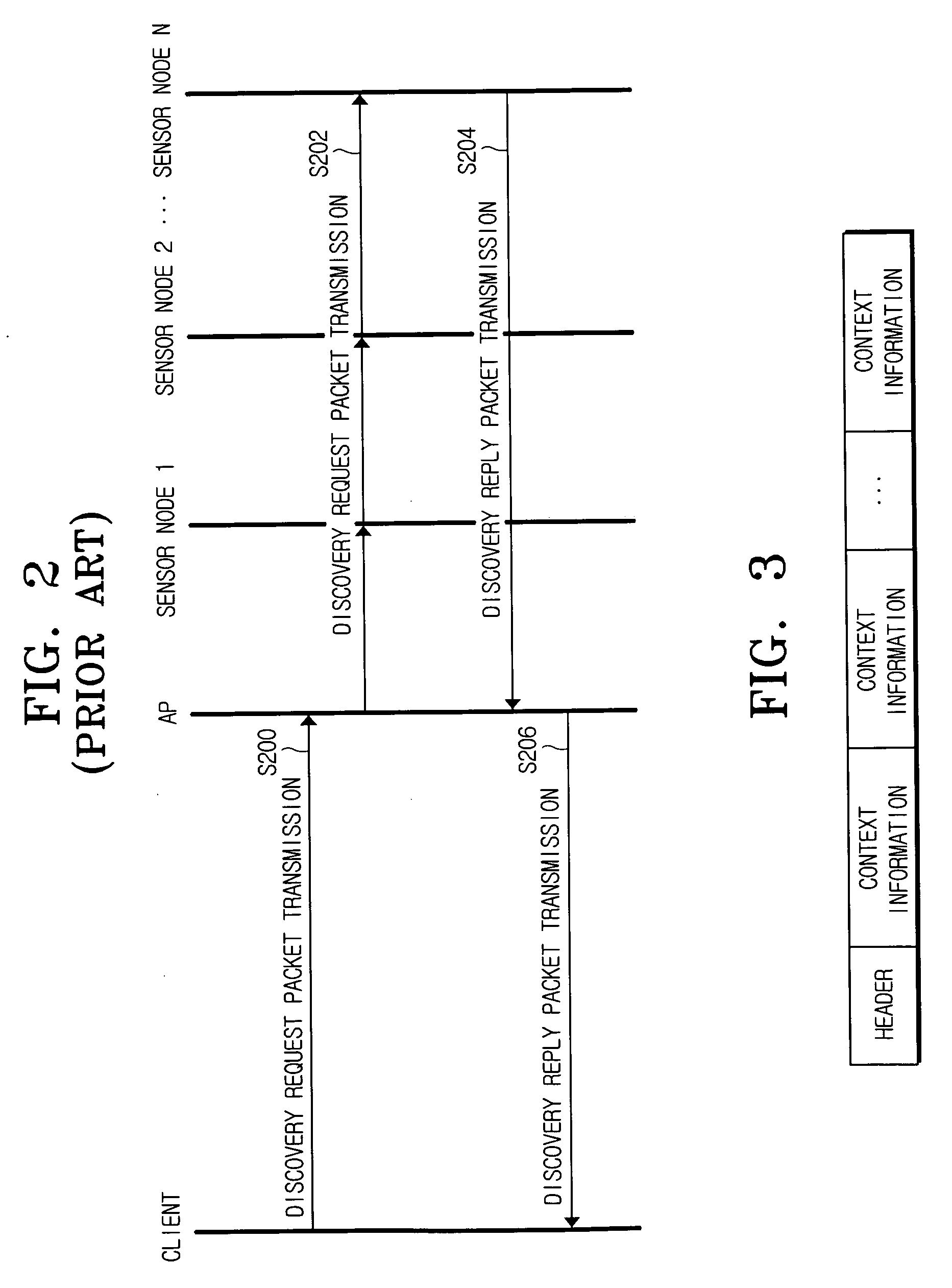
Method for discovery reply packet transmission in communication network
InactiveUS20060106753A1Ratio deterioratesFast informationNetwork topologiesData switching by path configurationCommunications systemSensor node
A method for determining a transmission time of collected context information at a sensor node in a communication system that includes a client, at least one sensor node collecting context information, and an access point (AP) forwarding the context information received from the sensor node to the client. The communication system operates in a session layer of protocol layers of open systems interconnection (OSI). The sensor node calculates a transmission period in which the collected context information is transmitted, and randomly determines a transmission time at which the context information is transmitted within the calculated transmission period. Since the collected context information is transmitted at the transmission time randomly determined by the sensor node, the load on the AP can be balanced.
Owner:SAMSUNG ELECTRO MECHANICS CO LTD
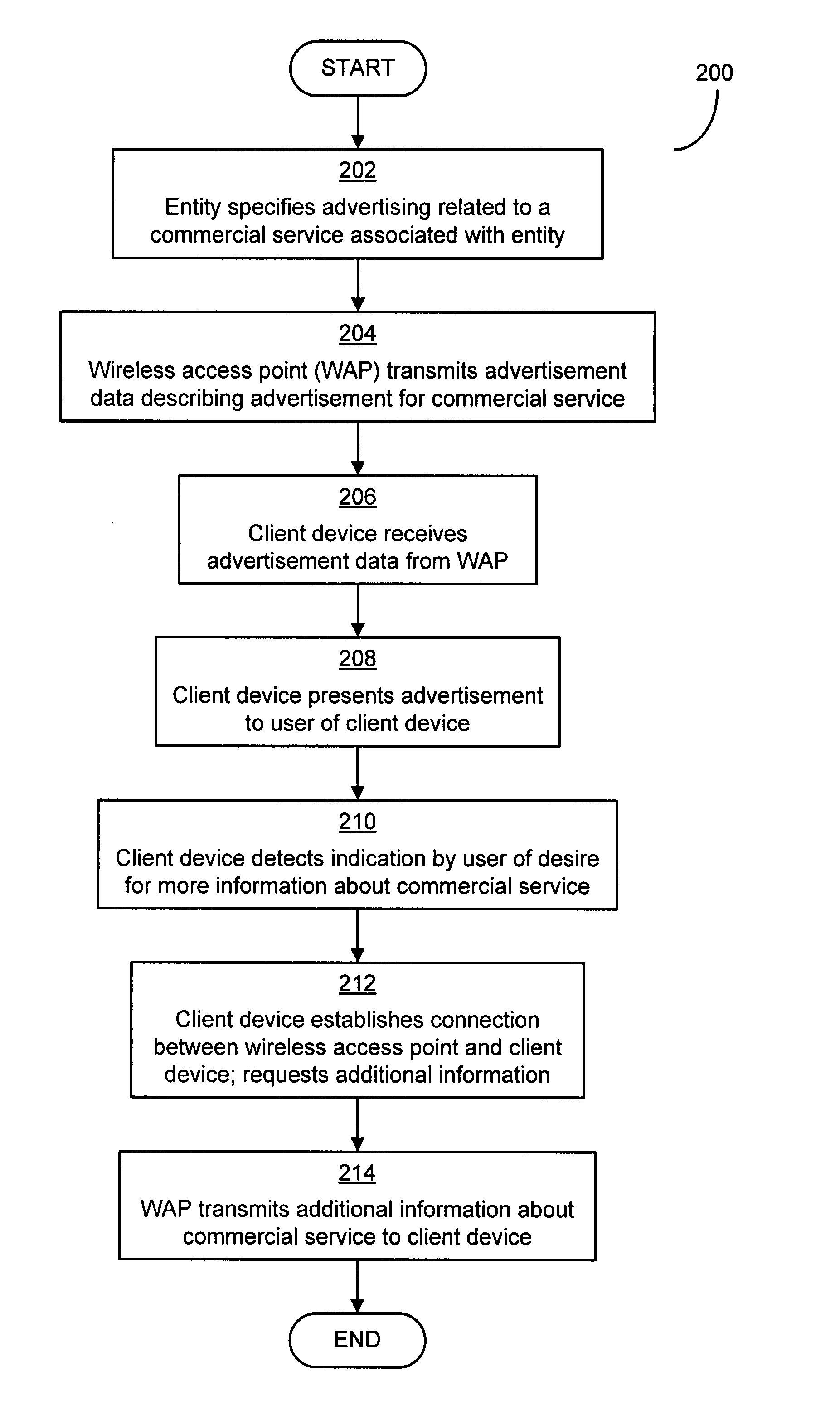
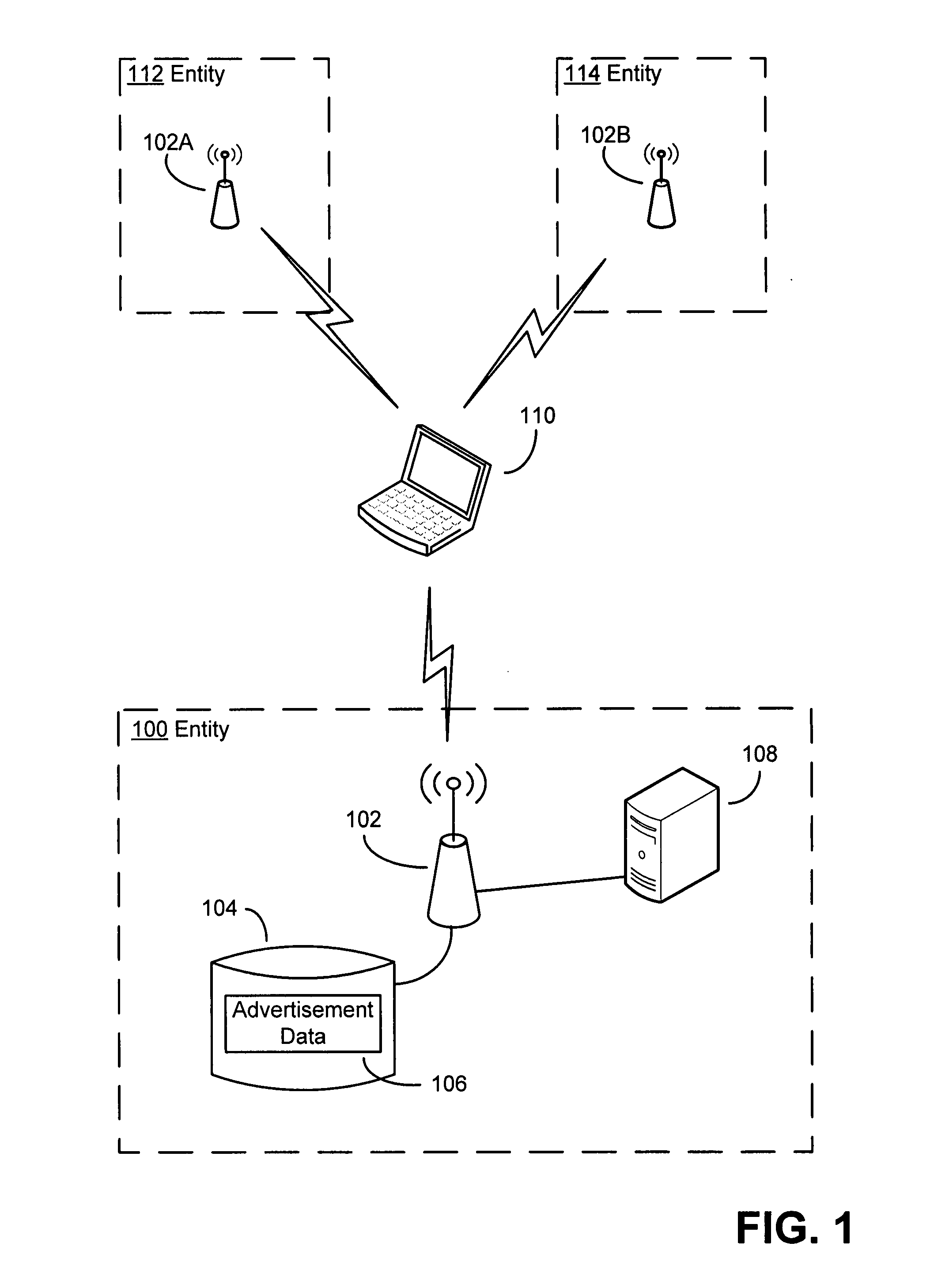
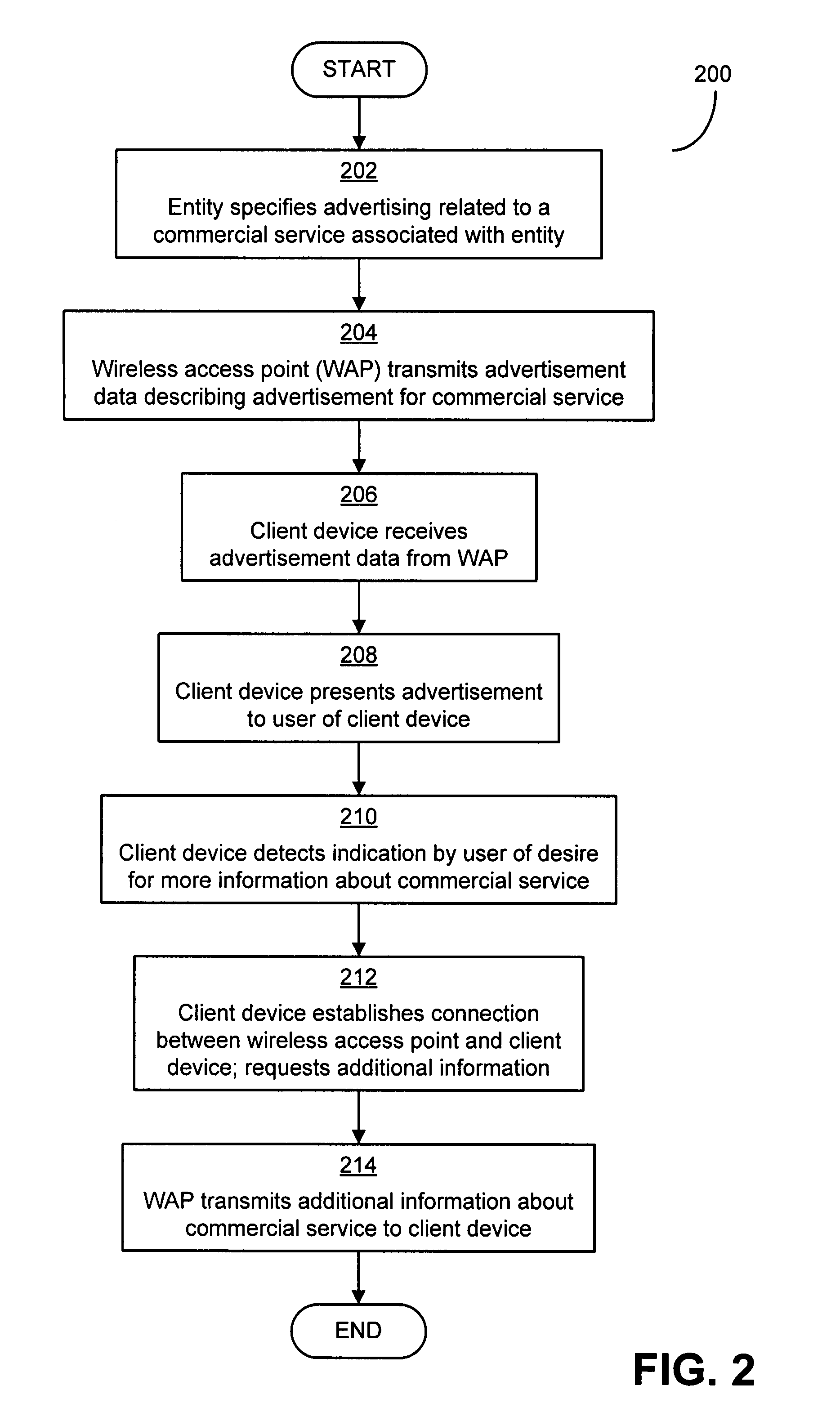
Advertising framework for wireless networks
InactiveUS20090094111A1More revenueLimited abilityDiscounts/incentivesLayered modelWireless mesh network
An advertising framework for transmitting advertisements from wireless access points to client devices that need not be connected to the wireless access point. The client device can display the advertisements on a user interface of the client device. Such advertisements may be transmitted, for example, as part of a control message transmitted by a wireless access point of a wireless network, or other message conventionally used to broadcast network characteristics necessary for a client device to establish a connection to the wireless access point. In terms of the Open Systems Interconnect (OSI) layered model of a network, layer 2 control messages, including announcement transmissions such as beacons, may be used for control messages.
Owner:MICROSOFT TECH LICENSING LLC
Octet iterator template interface for protocol transfer syntax coding services
InactiveUS6256778B1Minimal requirementSpecific program execution arrangementsMemory systemsIteratorOpen Systems Interconnection
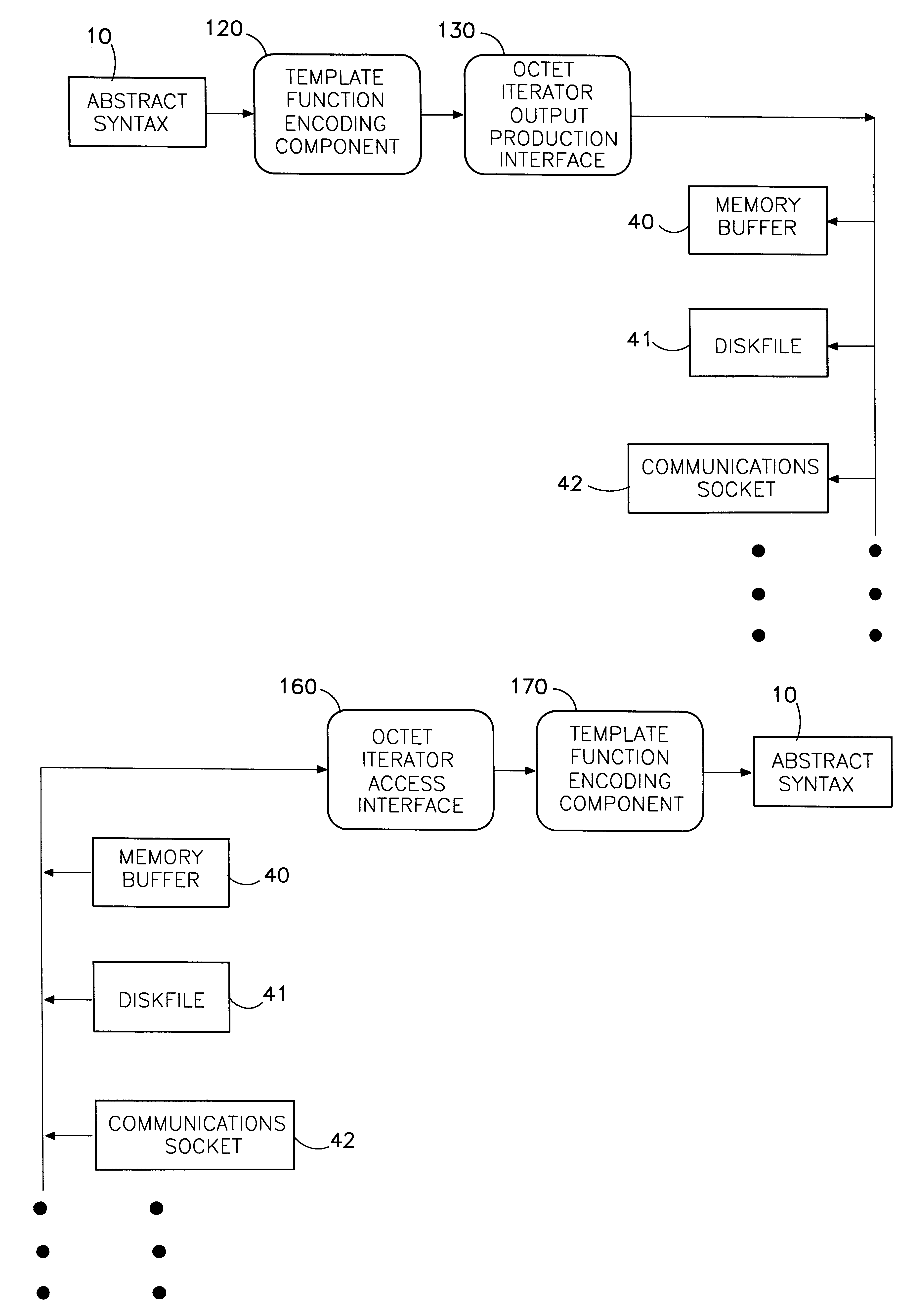
A method is disclosed that allows the concise implementation of one protocol encoding / decoding device for syntax conversion between an abstract data syntax and a transfer syntax presented in an open-ended variety of input / output / storage mediums, including, but not limited to random-access memory, disk files, communications sockets, buffer lists, and other static or dynamically-extensible storage structures. The abstract syntax is described using the Abstract Syntax Notation One standard and presented in a higher-level object-oriented programming language such as C++. The transfer syntax is specified by standardized encoding rules and results in a stream of octets (unsigned 8-bit characters) suitable for communication transport using the Open Systems Interconnection (OSI) protocol model. The result of encoding (which is also the input for decoding) is called a protocol data unit (PDU). For different applications, it may be useful to present the PDU using various input / output or storage mediums such as listed above. The disclosed method employs a template function parameterized on an octet output iterator interface to provide an ASN.1 encoding mechanism, and a corresponding template function parameterized on an octet input iterator interface to provide an ASN.1 decoding mechanism, both independent of the medium in which the PDU is presented.
Owner:OLIVER CHRISTOPHER
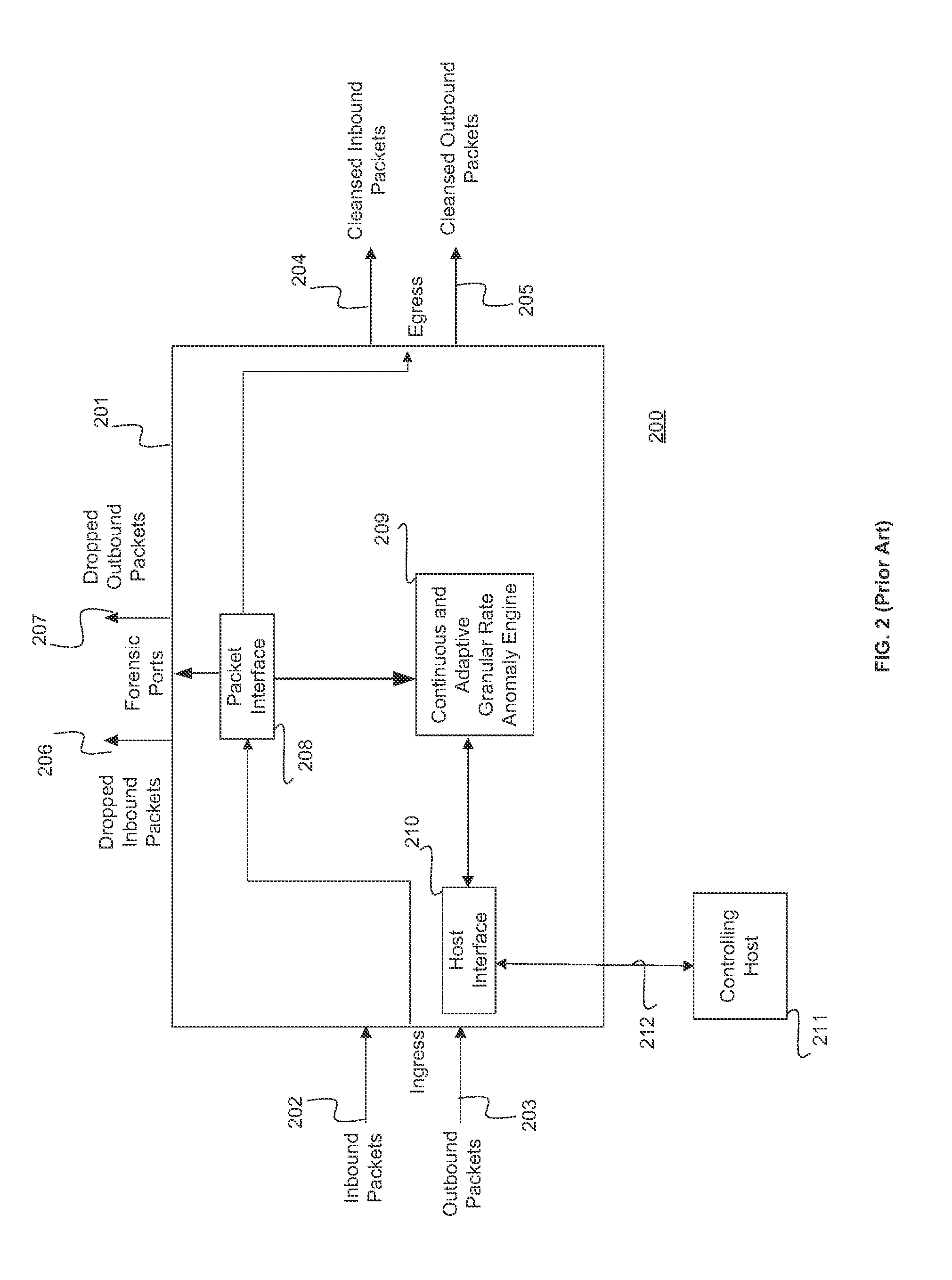
Scalable inline behavioral ddos attack mitigation
ActiveUS20150026800A1Improve throughputMemory loss protectionError detection/correctionAdaptive learningCommunications system
Methods and systems for a scalable solution to behavioral Distributed Denial of Service (DDoS) attacks targeting a network are provided. According to one embodiment, a method to determine the scaling treatment is provided for various granular layer parameters of the Open System Interconnection (OSI) model for communication systems. A hardware-based apparatus helps identify packet rates and determine packet rate thresholds through continuous and adaptive learning with multiple DDoS attack mitigation components. The system can be scaled up by stacking multiple DDoS attack mitigation components to provide protection against large scale DDoS attacks by distributing load across these stacked components.
Owner:FORTINET
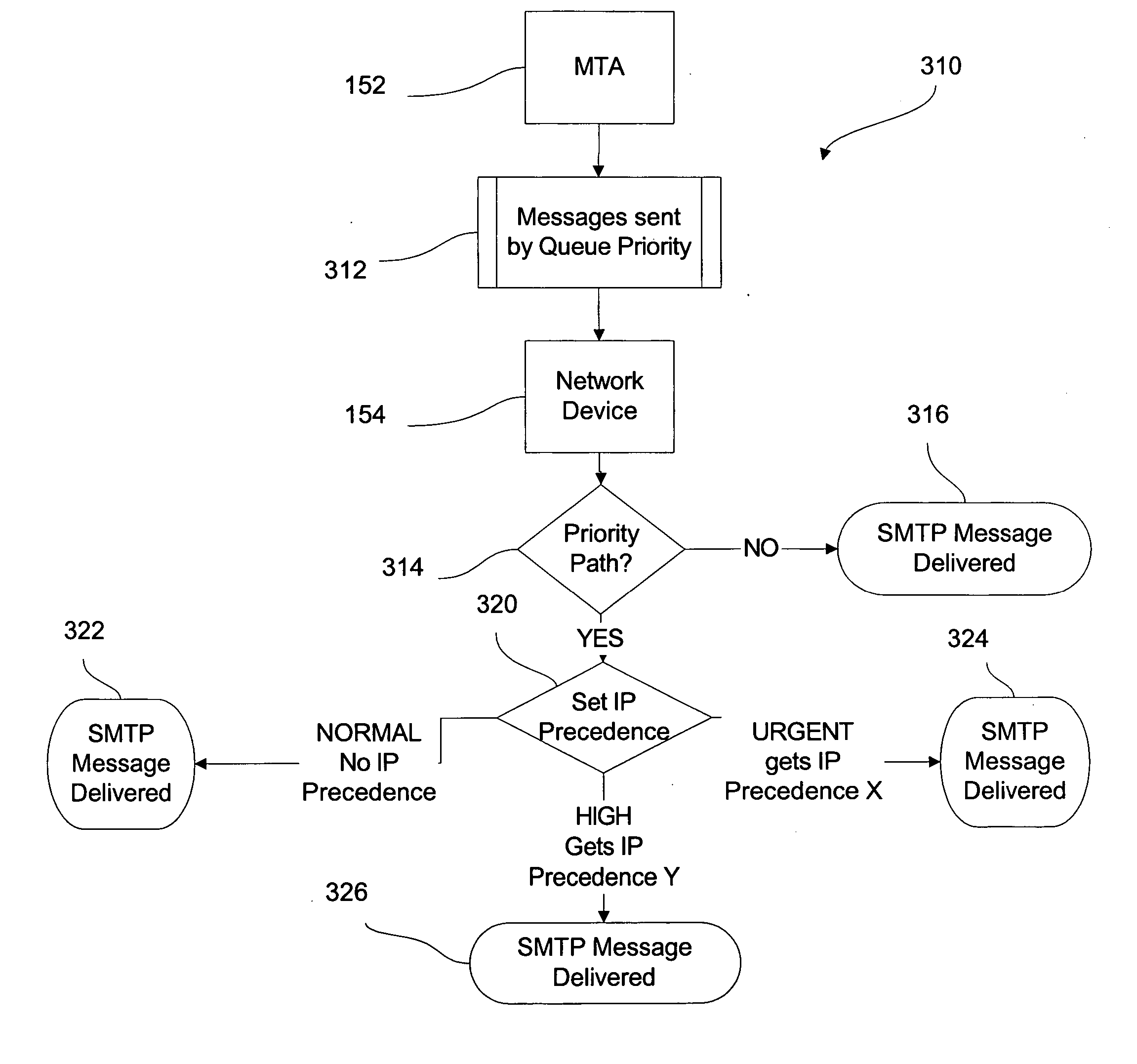
Electronic message delivery system including a network device
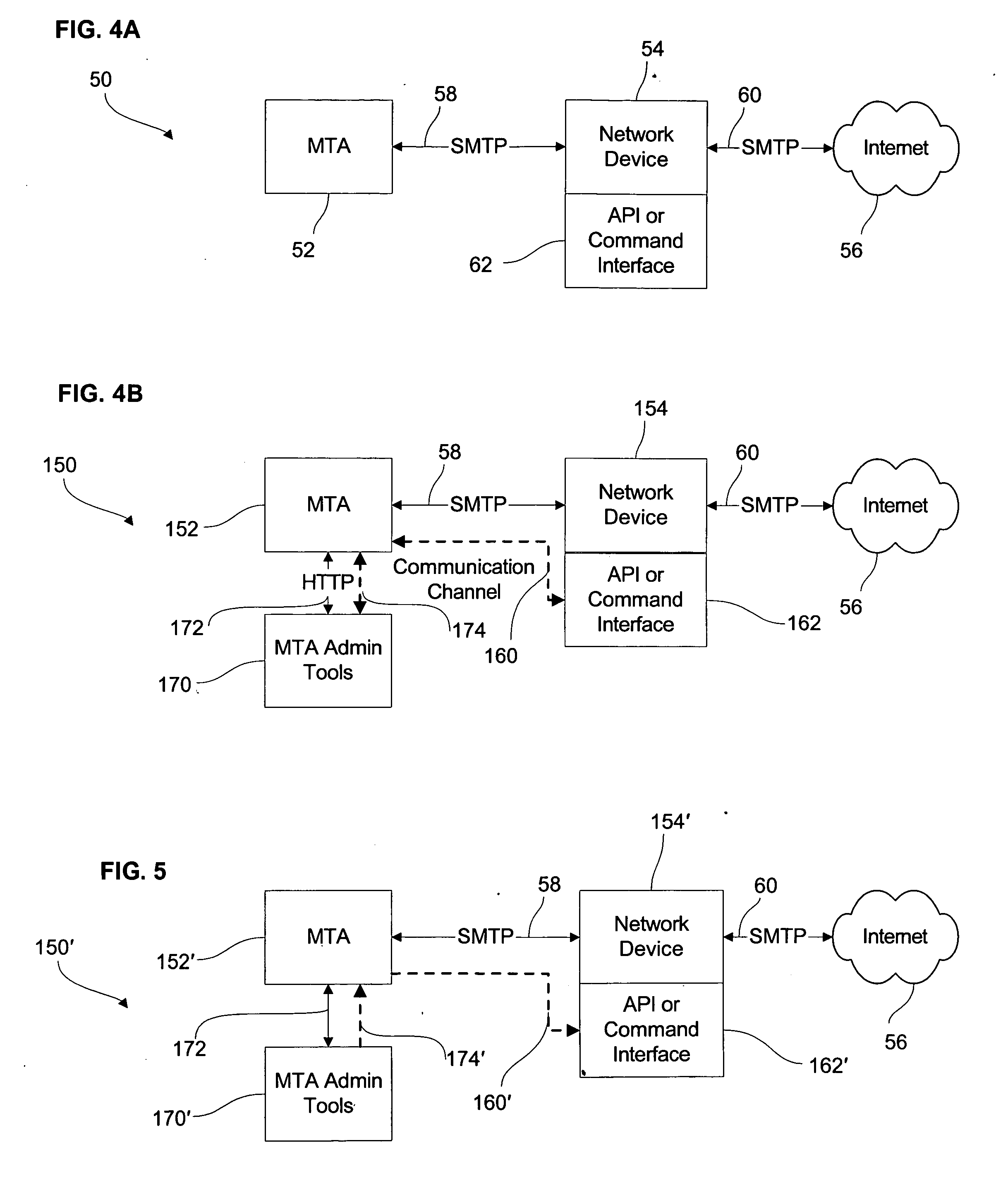
ActiveUS20060164992A1Increase output flowError preventionTransmission systemsMessage deliveryNetworked system
In a computer network system based on an open system interconnection model, where the computer network system includes at least a network layer (Layer 3) and an application layer (Layer 7), a system and a method for managing electronic message traffic into and out of the computer network system including defining a communication channel between Layer 3 and Layer 7 for exchanging data directly therebetween for use in enhancing flow of the electronic message traffic.
Owner:QUEST SOFTWARE INC
Transmitting location data in wireless networks
ActiveUS20090093956A1Navigational calculation instrumentsPosition fixationWireless mesh networkLayered model
A wireless access point in a wireless network that may be adapted to transmit location data indicating its location to other devices within range, including other wireless access points and client devices. In some embodiments of the invention, the location data may be embedded in a control message or announcement transmission transmitted by the wireless access point, or other message conventionally used to broadcast network characteristics necessary for a client device to establish a connection to the wireless access point. In terms of the Open Systems Interconnect (OSI) layered model of a network, layer 2 control messages, including beacons, probe responses, or other suitable transmissions may be used for control messages or announcement transmissions. The other wireless access points and client devices may receive the location data broadcast by the wireless access point without establishing a connection to the client device. Devices receiving the location data may use the received location data to determine their own locations, and may provide the determined locations to consumers of location data.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus for opportunistic wireless mesh networks
InactiveUS20080075029A1Improve performanceReadily detected and avoidedPower managementEnergy efficient ICTReference modelWireless mesh network
The invention relates to opportunistic wireless mesh networks which operate under random networking conditions. Such random network conditions typically limit the effectiveness of prior art wireless mesh networks, and more particularly to those supporting low power devices within the wireless network. Random network conditions include: random power supply, random node distribution, random node mobility, high mobility of nodes, random wireless link fluctuations, and random application traffic. The opportunistic wireless mesh network utilizes a two-layer architecture Embedded Wireless Interconnect (EWI) framework, which is adopted as the architecture reference model. A mesh network according to the invention supports opportunistically determining both mesh interconnections and network transmission routes by providing nodes with broadcast modules and unicast modules. The methods provide novel low power opportunistic wireless mesh networks that support interconnection with existing network infrastructures such as Open System Interconnect (OSI) based wired or wireless networks. Network embodiments provide protocol translation at network borders to allow micro- and macro-mobility management for wireless devices and their associated users. Additionally embodiments of the opportunistic wireless mesh networks address reduction in power consumption.
Owner:SENNET COMM
Routing protocol and routing method for achieving VDES
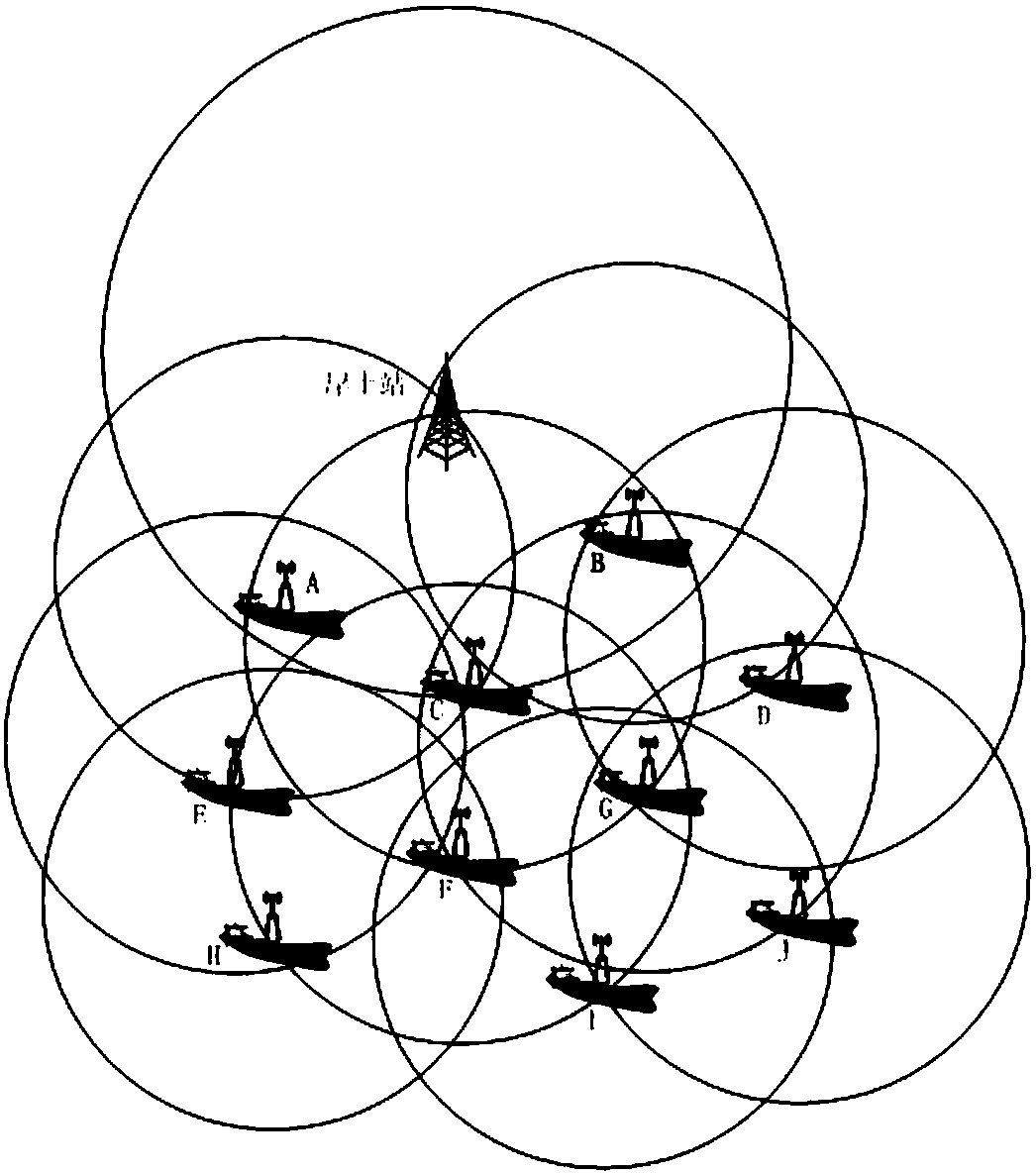
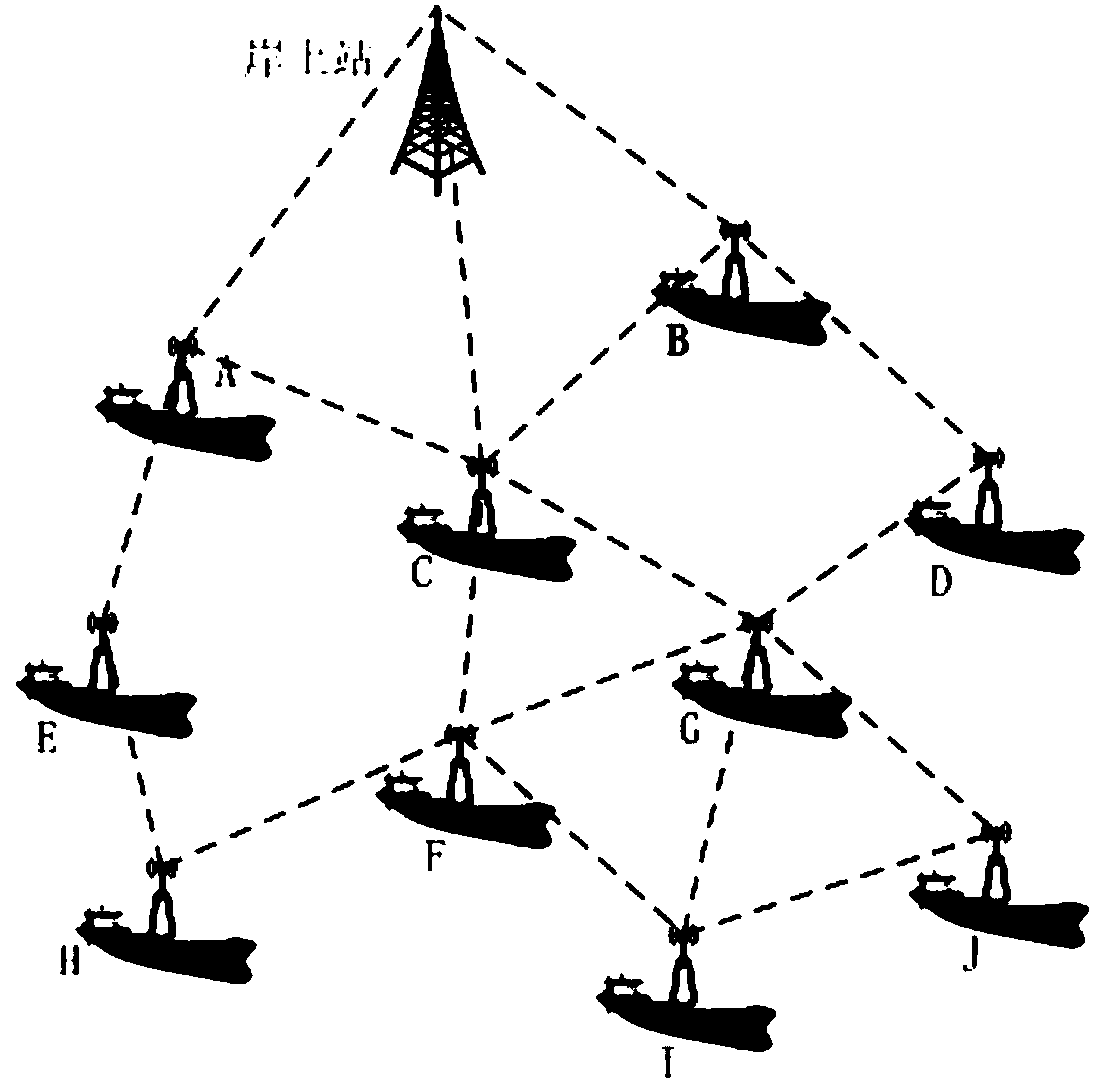
InactiveCN108055205AGuaranteed reliabilityExpand the transmission rangeNetwork topologiesData switching networksRouting tablePhysical layer
The invention provides a routing protocol for achieving a VDES. The routing protocol adopts an IEEE802.11s protocol standard, is of the structure of an open system interconnection seven-layer model and comprises a physical layer, a link layer, a network layer and a transmission layer; and the routing protocol has the automatic networking capacity and can send received information to all nodes in the coverage range of the protocol, match addresses of the various nodes with destination addresses in routing information, correct a path according to routing table information and provide a reliableand lowest-cost path between a source node and a destination node. Each node generates a routing table, the routing tables are updated once at set intervals and sent to all the nodes in the coverage range, and the path is automatically corrected according to the routing table information. In this way, the transmission range of roadbed signals can be relatively widened, and the coverage range of anexisting land broadband wireless network is expanded to the sea.
Owner:WUHAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com