Patents
Literature
1911 results about "Information element" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
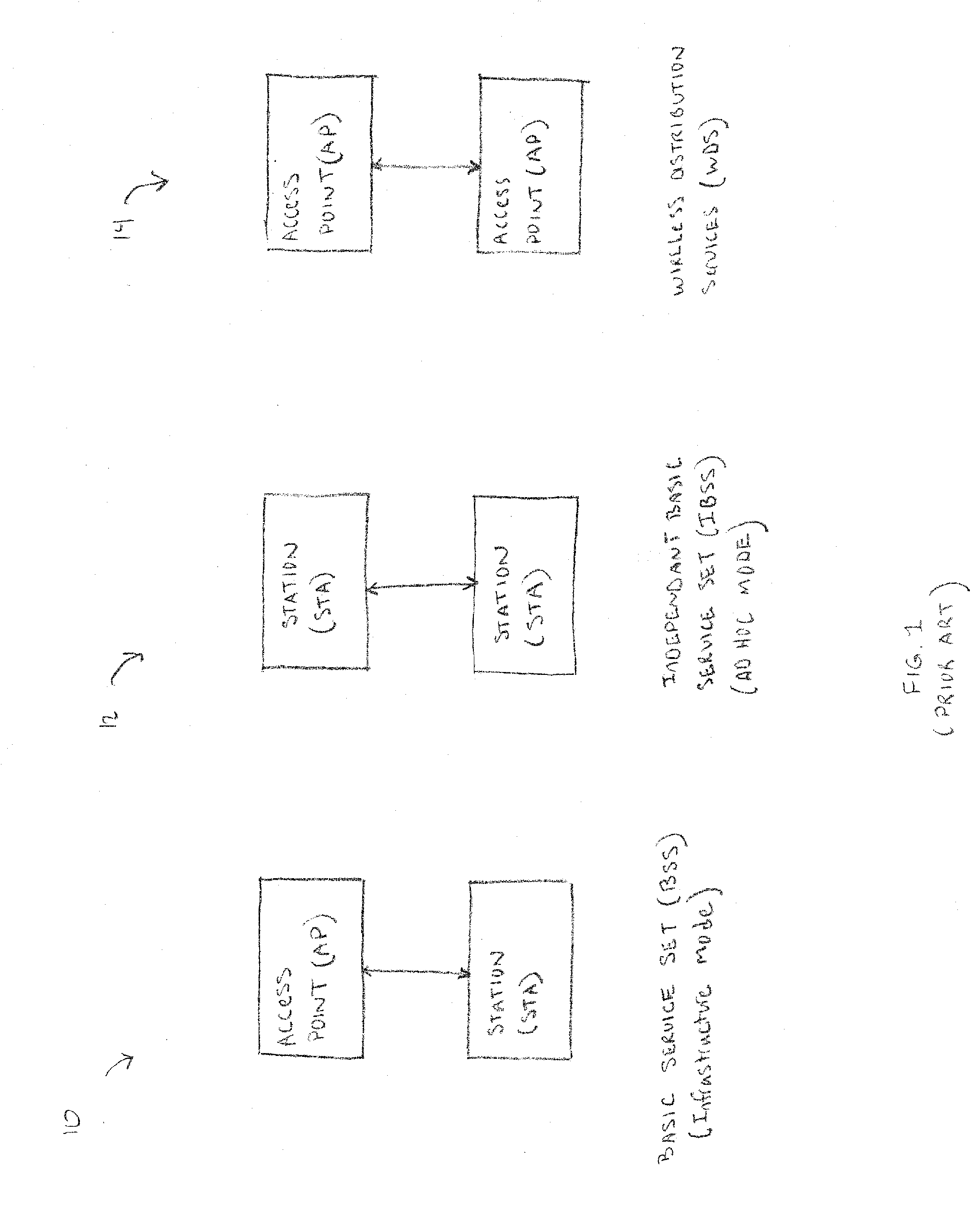
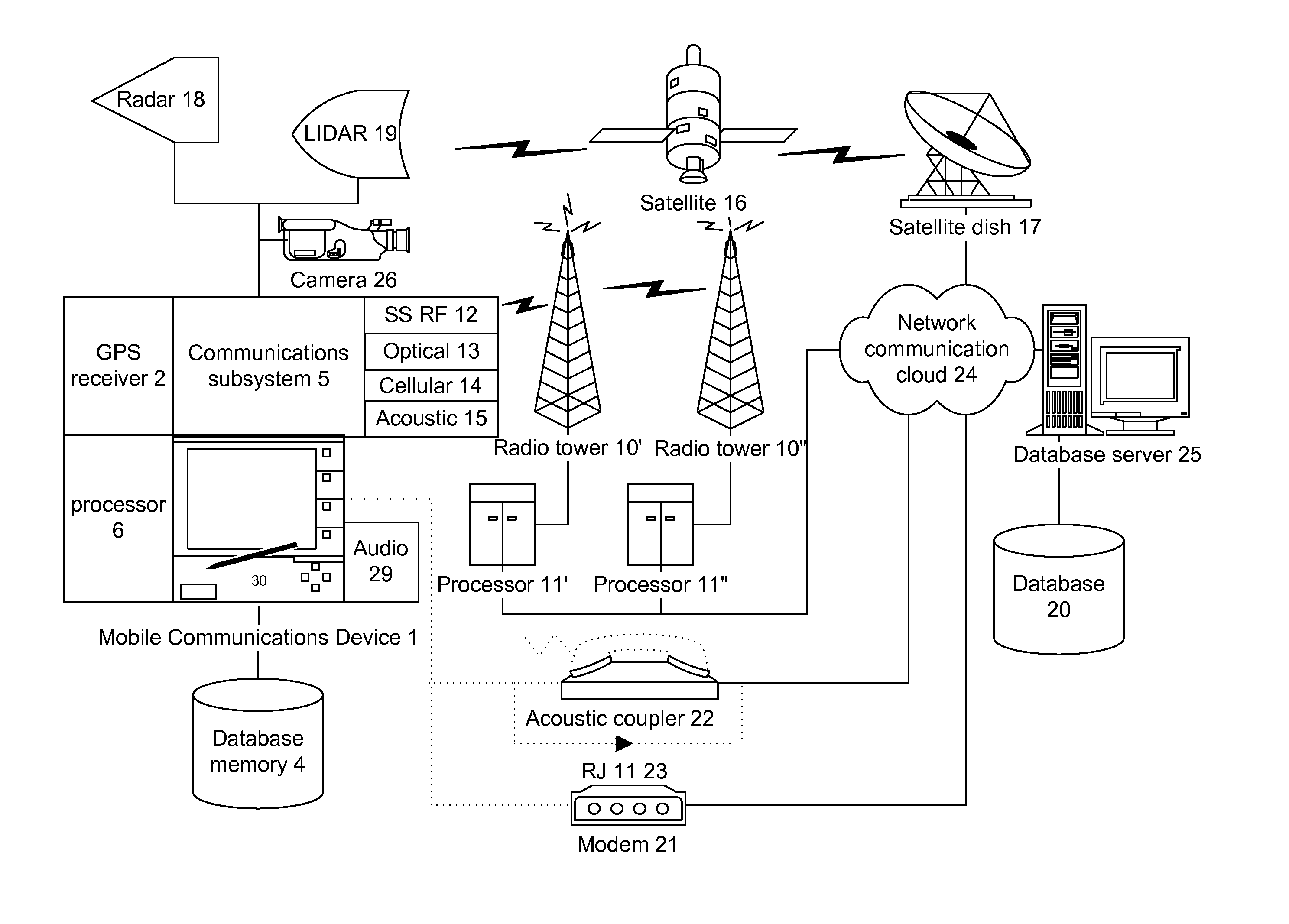
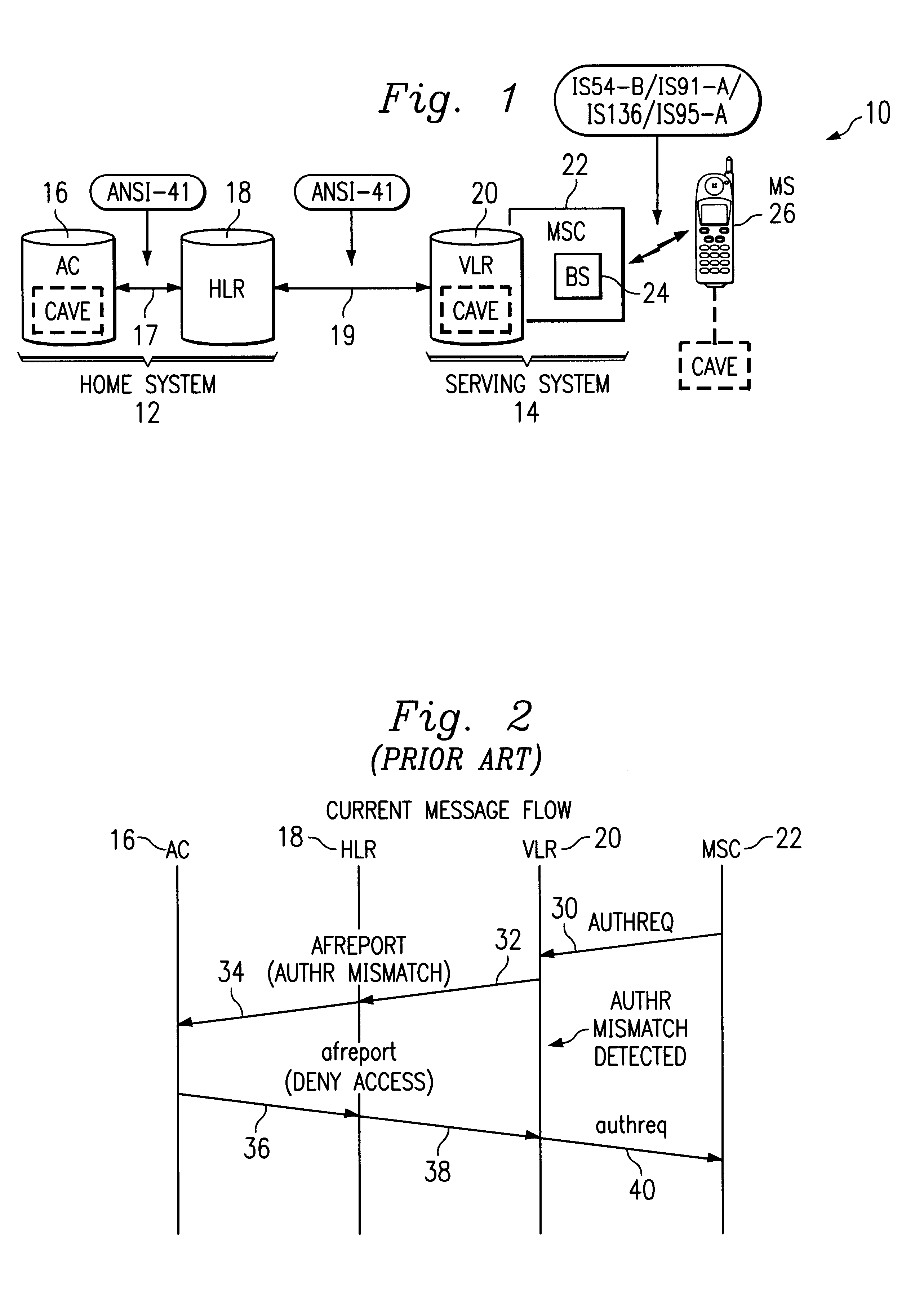
Information element. An information element, sometimes informally referred to as a field, is an item in Q.931 and Q.2931 messages, IEEE 802.11 management frames, and cellular network messages sent between a base transceiver station and a mobile phone or similar piece of user equipment.
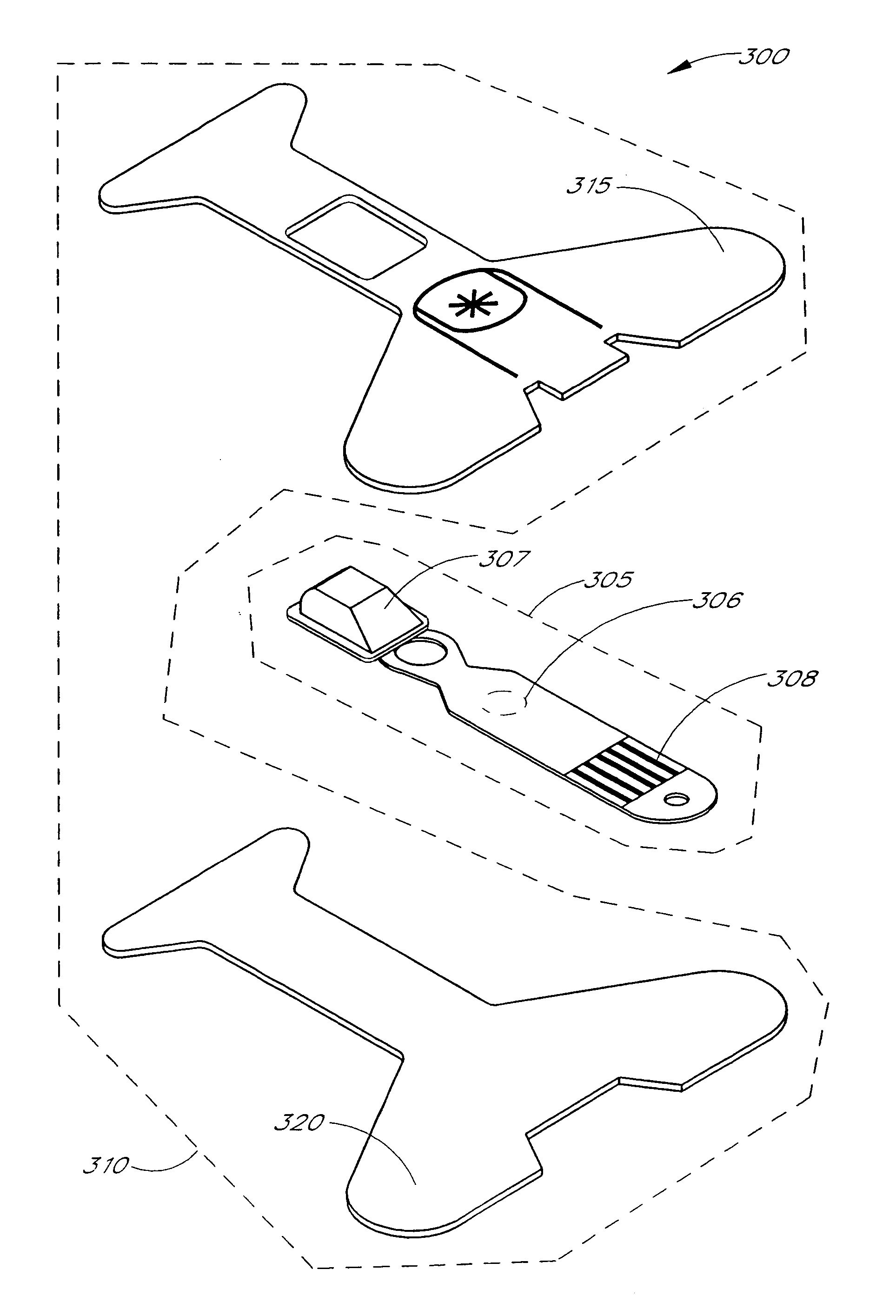
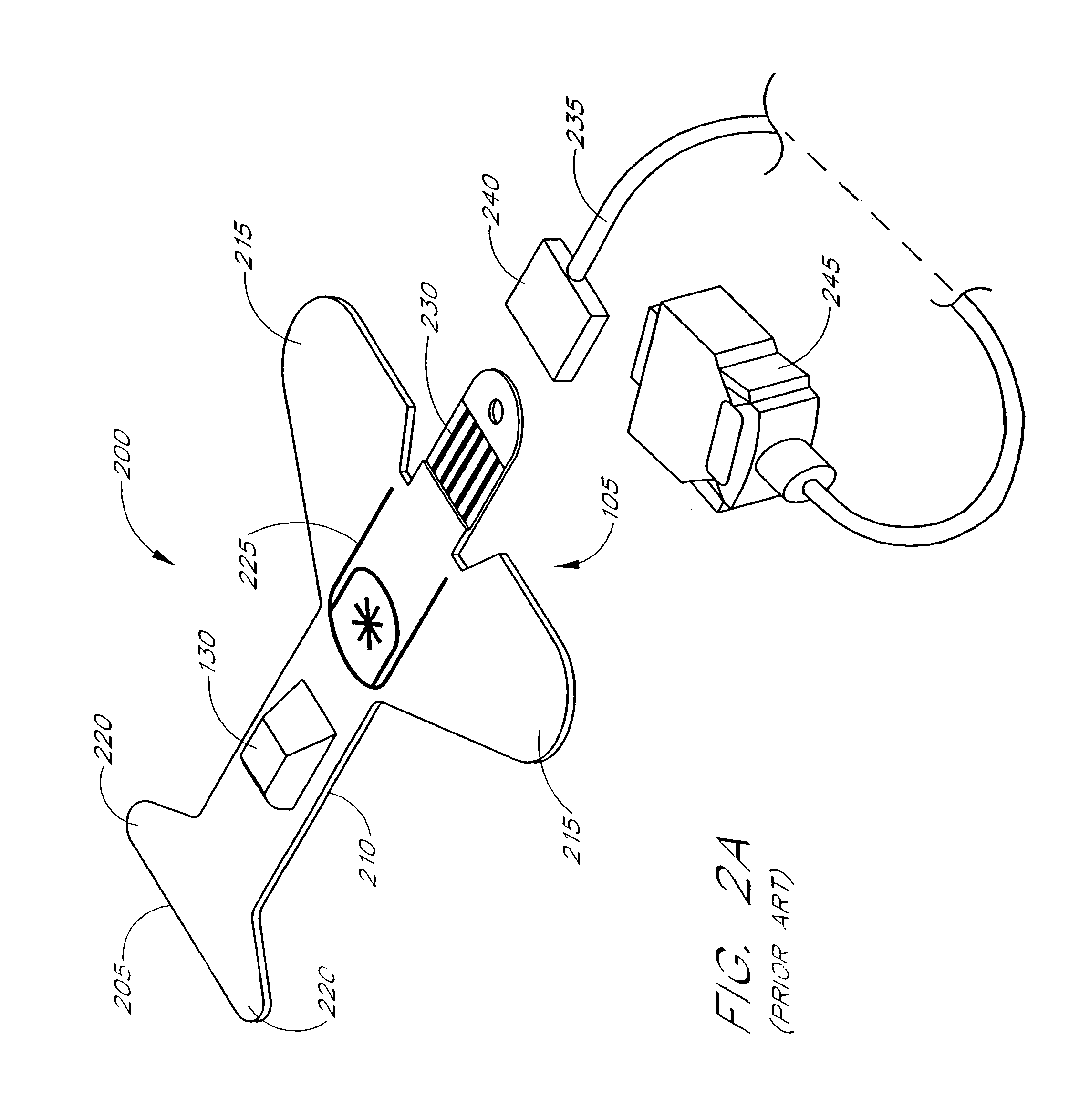
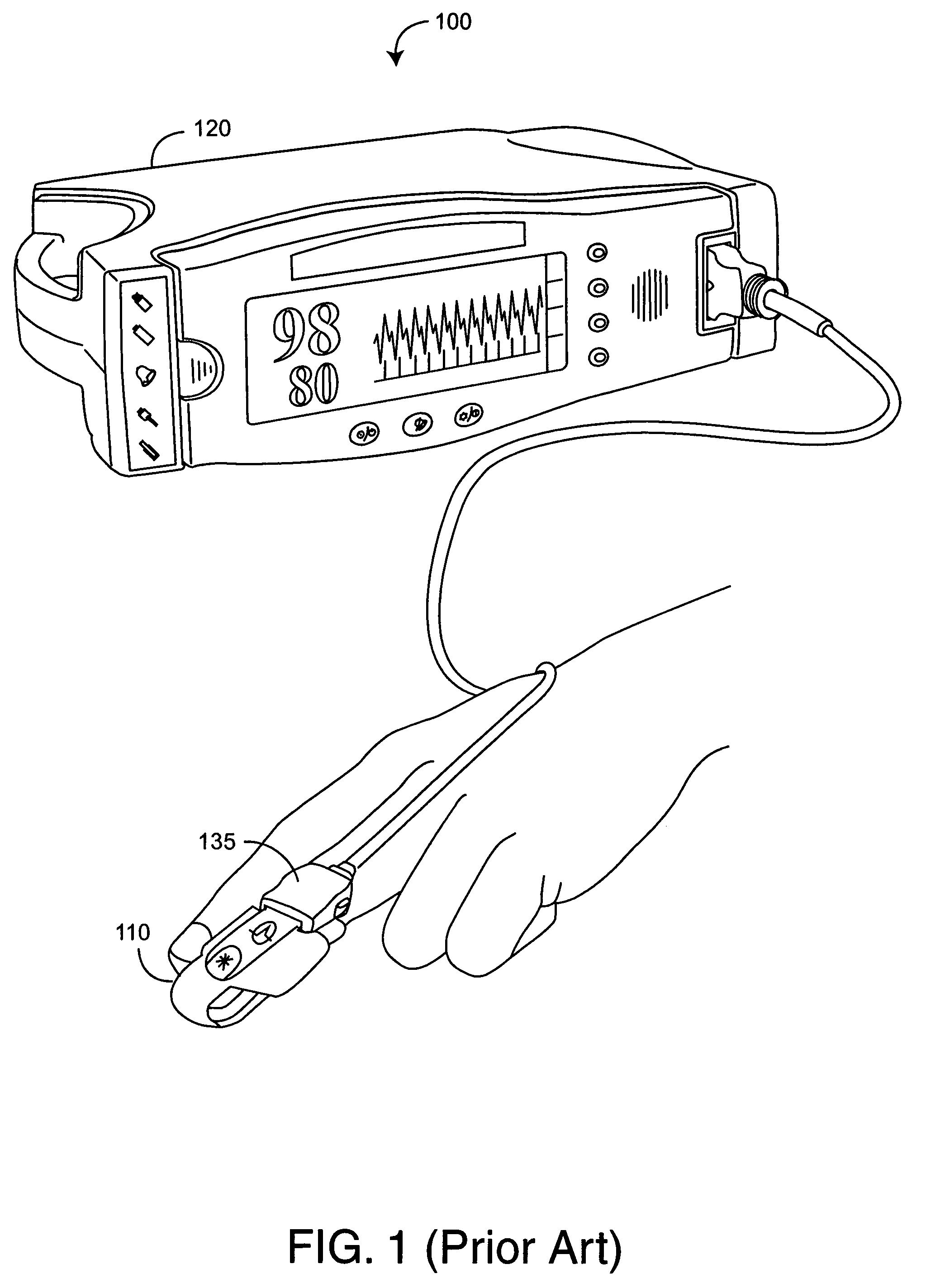
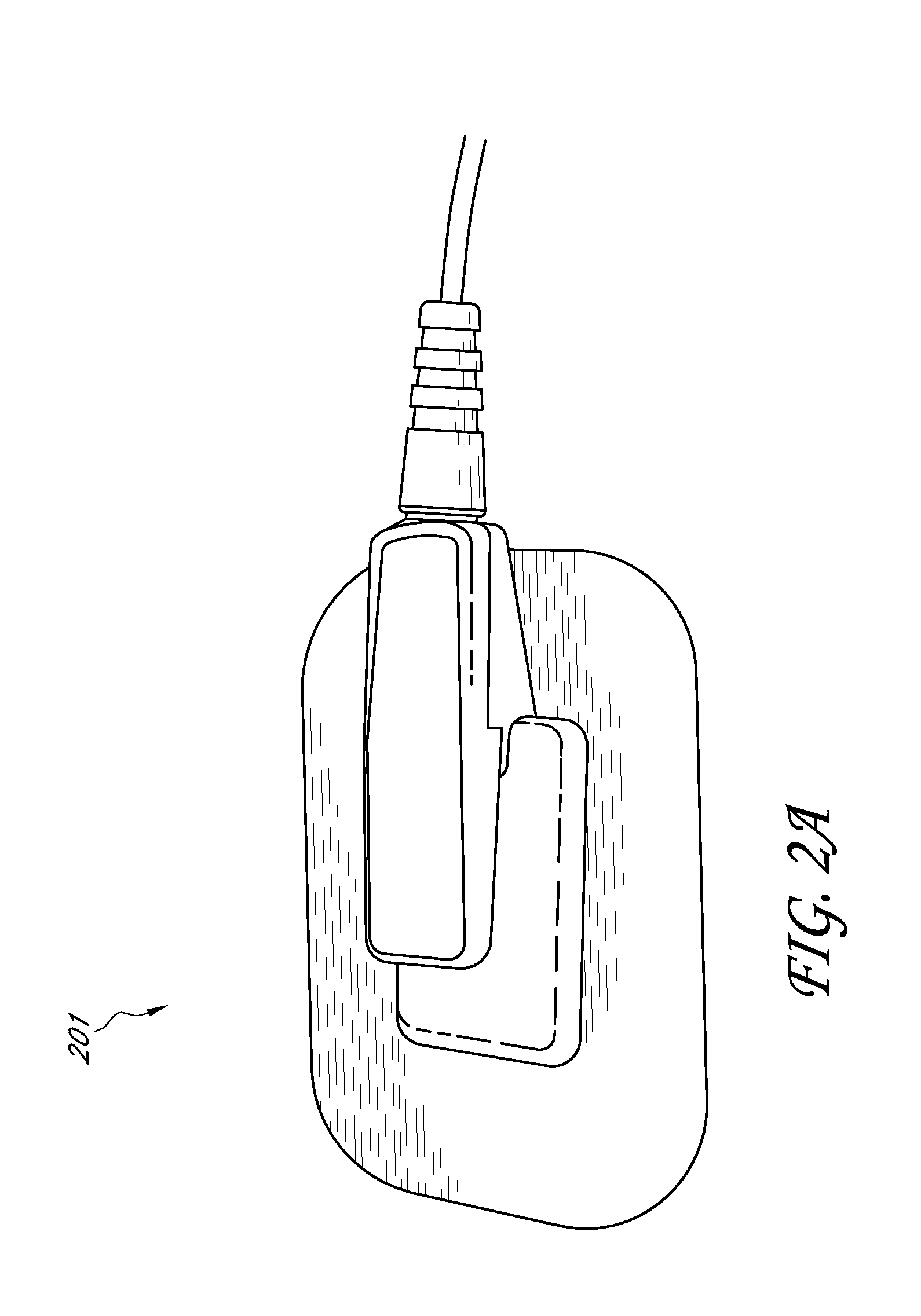
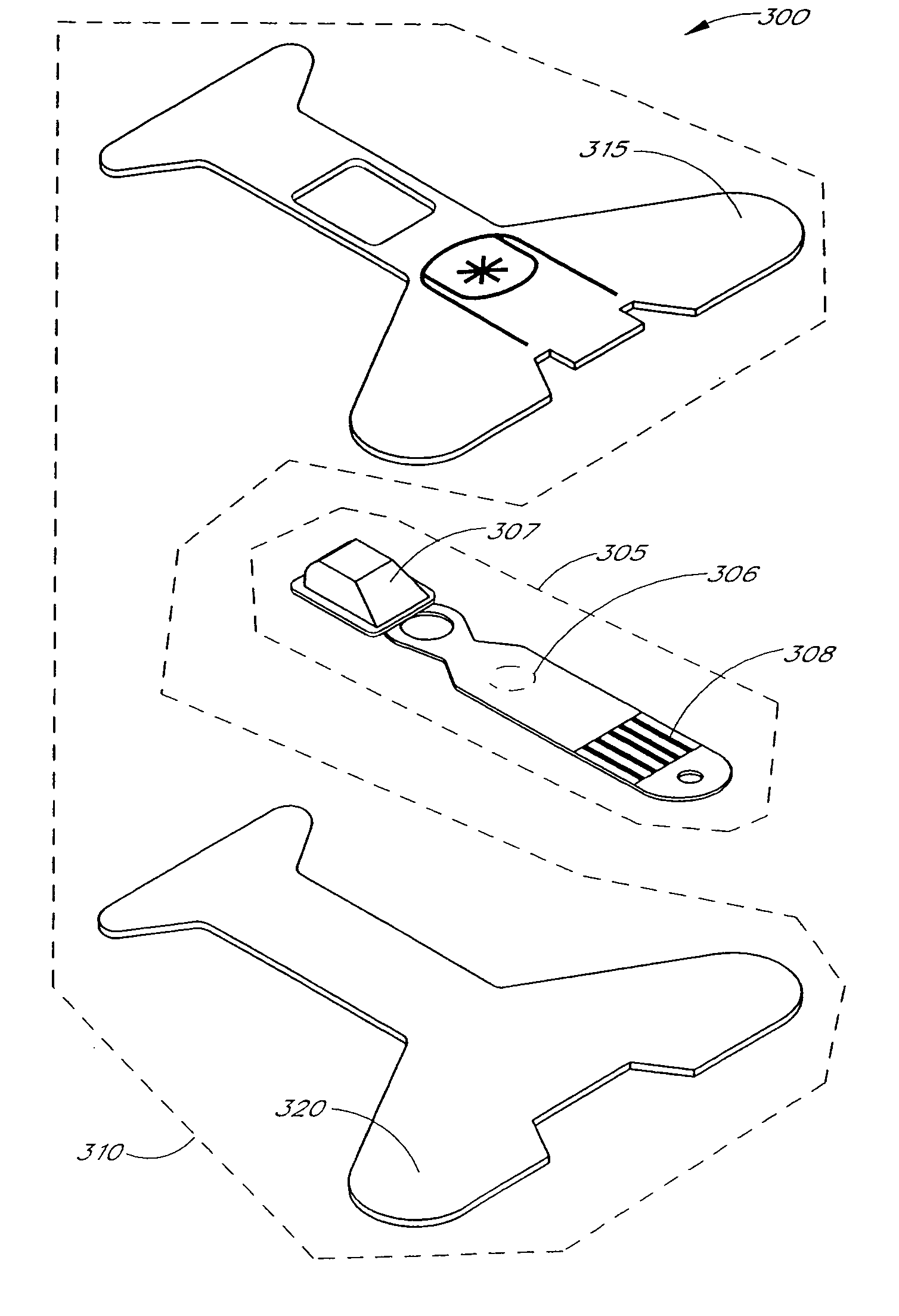
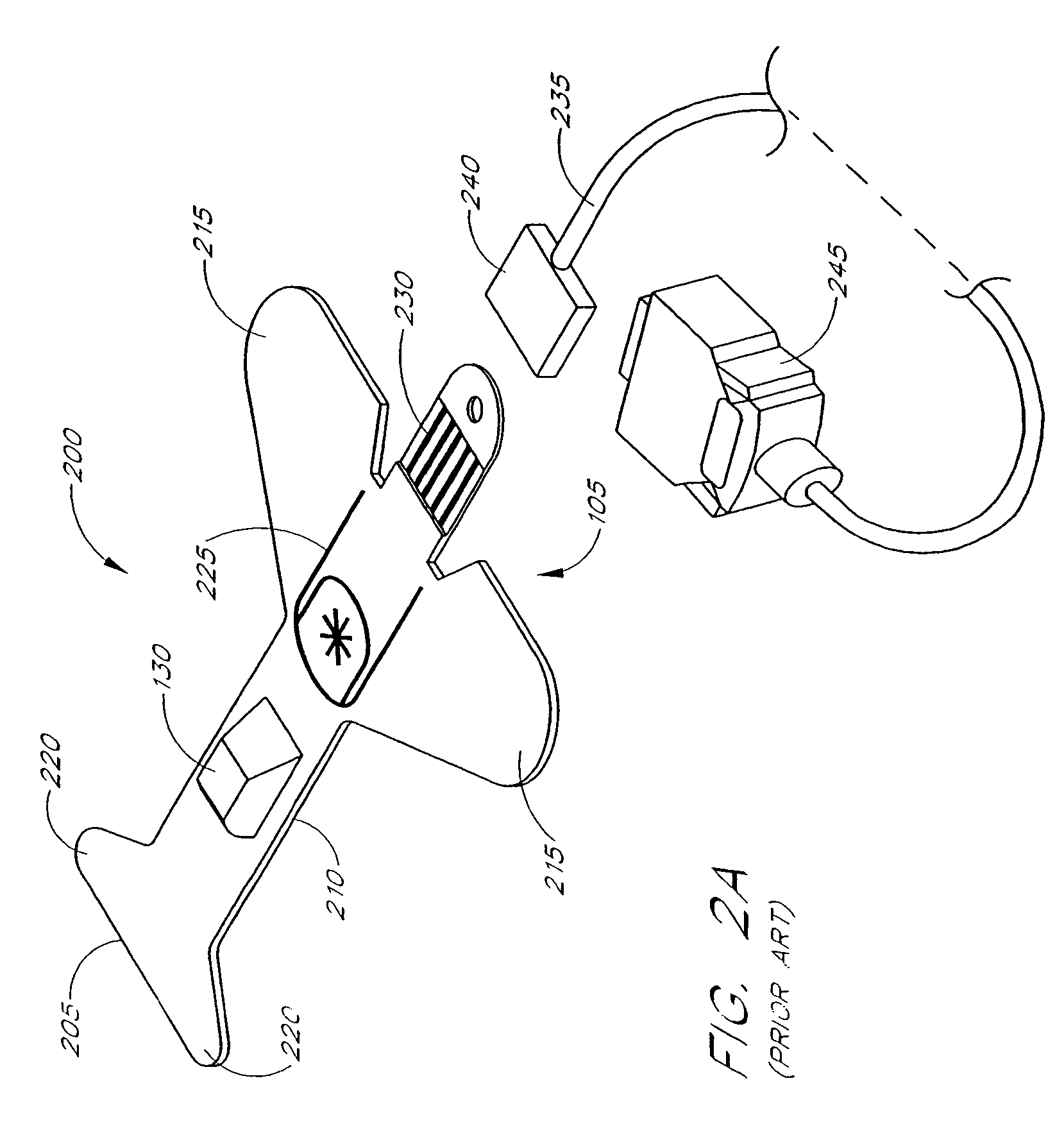
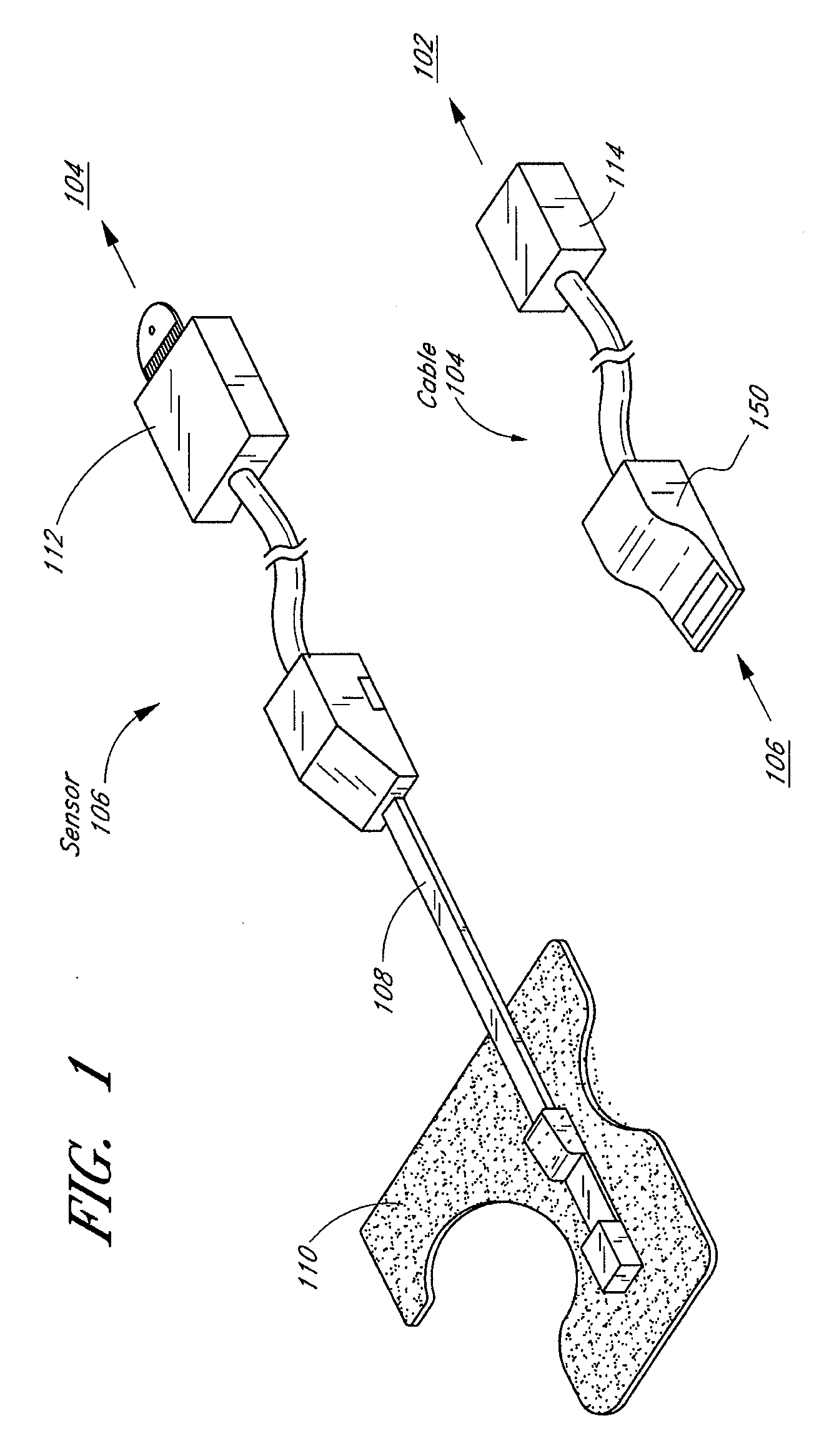
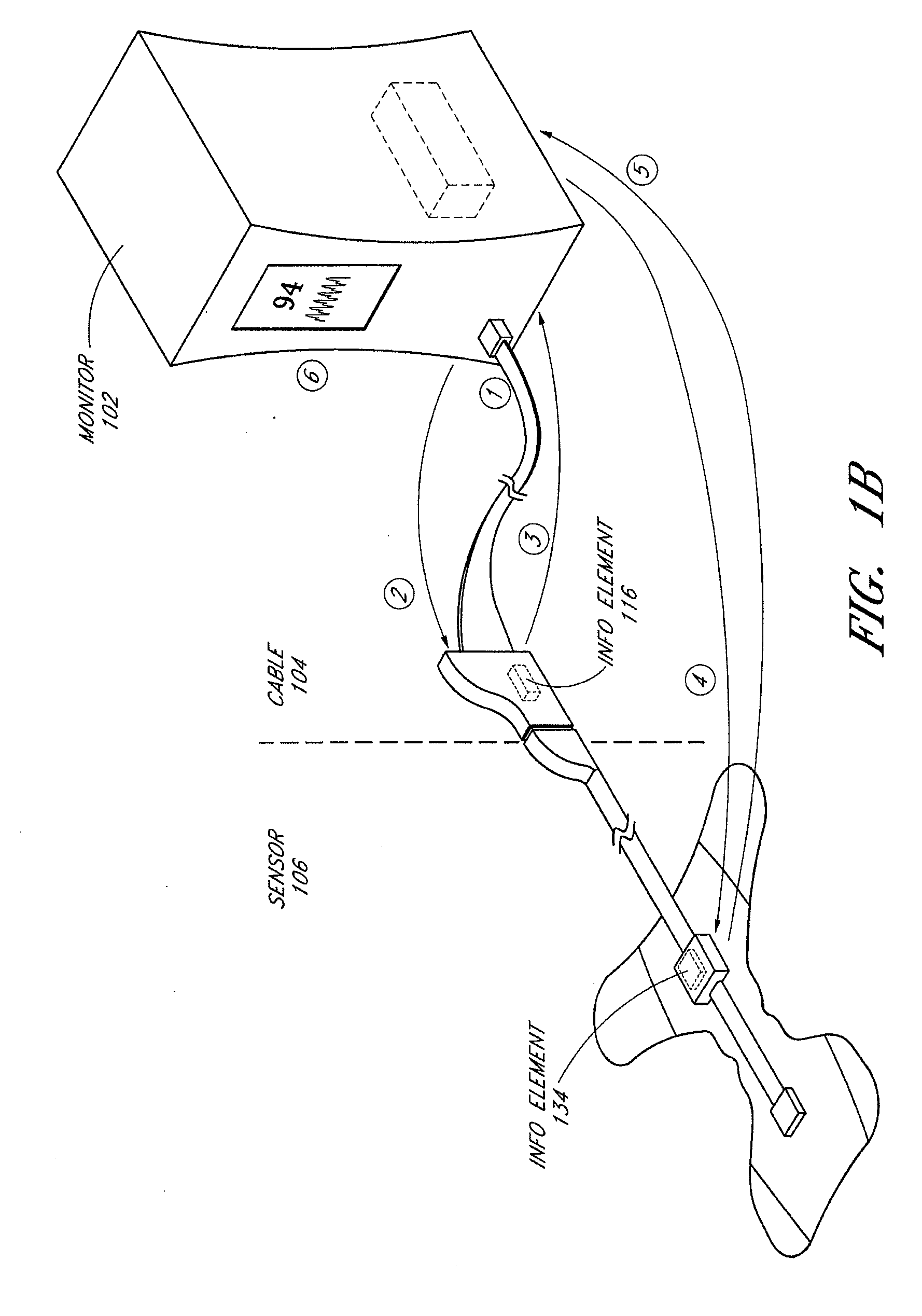
Resposable pulse oximetry sensor
InactiveUS7039449B2Longevity and associated costSensorsBlood characterising devicesAdhesivePulse oximetry
A pulse oximeter sensor has both a reusable and a disposable portion. The reusable portion of the sensor preserves the relatively long-lived and costly emitter, detector and connector components. The disposable portion of the sensor is the relatively inexpensive adhesive tape component that is used to secure the sensor to a measurement site, typically a patient's finger or toe. The disposable portion of the sensor is removably attached to the reusable portion in a manner that allows the disposable portion to be readily replaced when the adhesive is expended or the tape becomes soiled or excessively worn. The disposable portion may also contain an information element useful for sensor identification or for security purposes to insure patient safety. A conductive element that allows a pulse oximeter monitor to read the information element is located on the disposable portion in such a way that continuity is broken when the adhesive tape become torn, such as upon removal from the measurement site.
Owner:JPMORGAN CHASE BANK NA +1
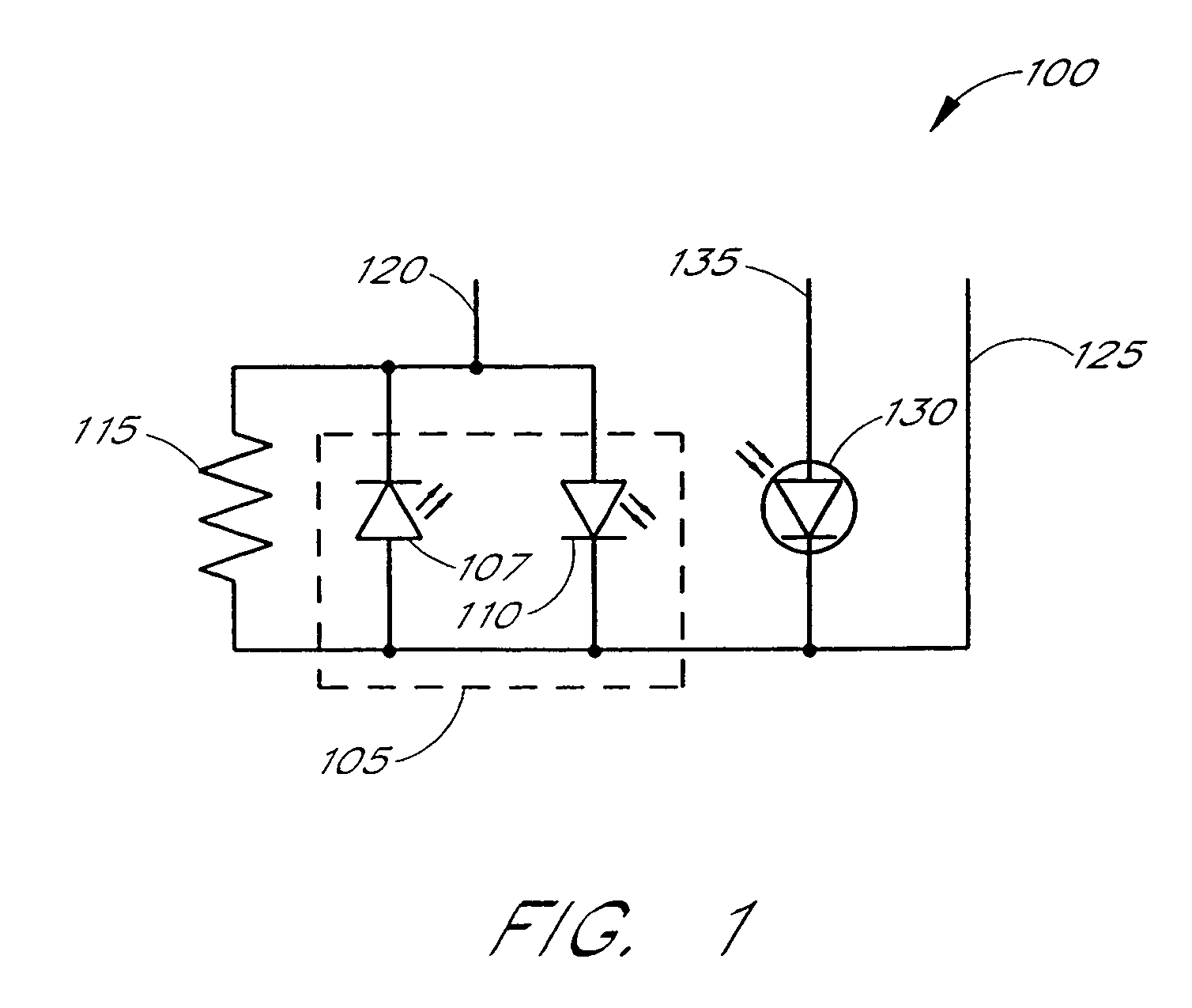
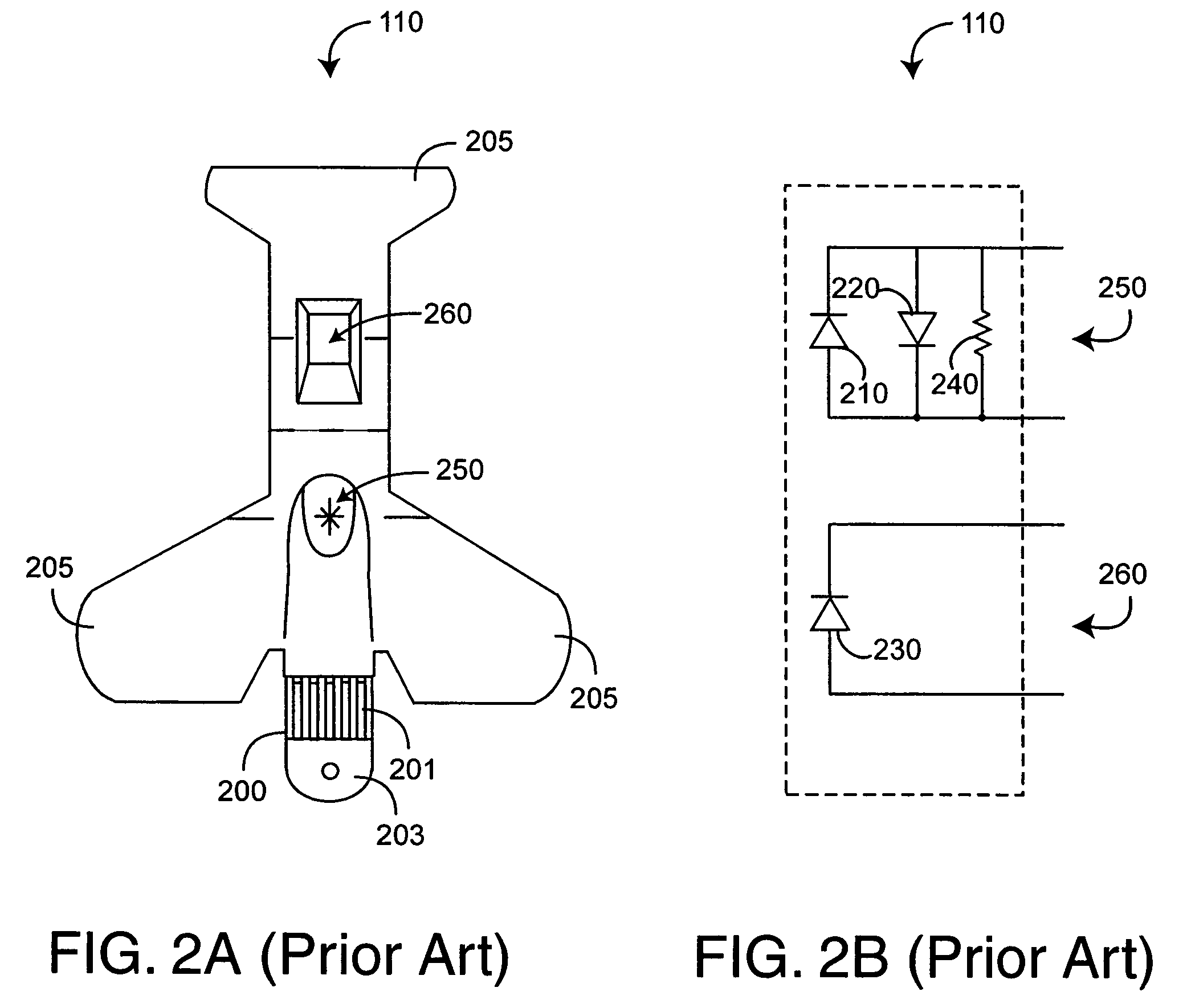
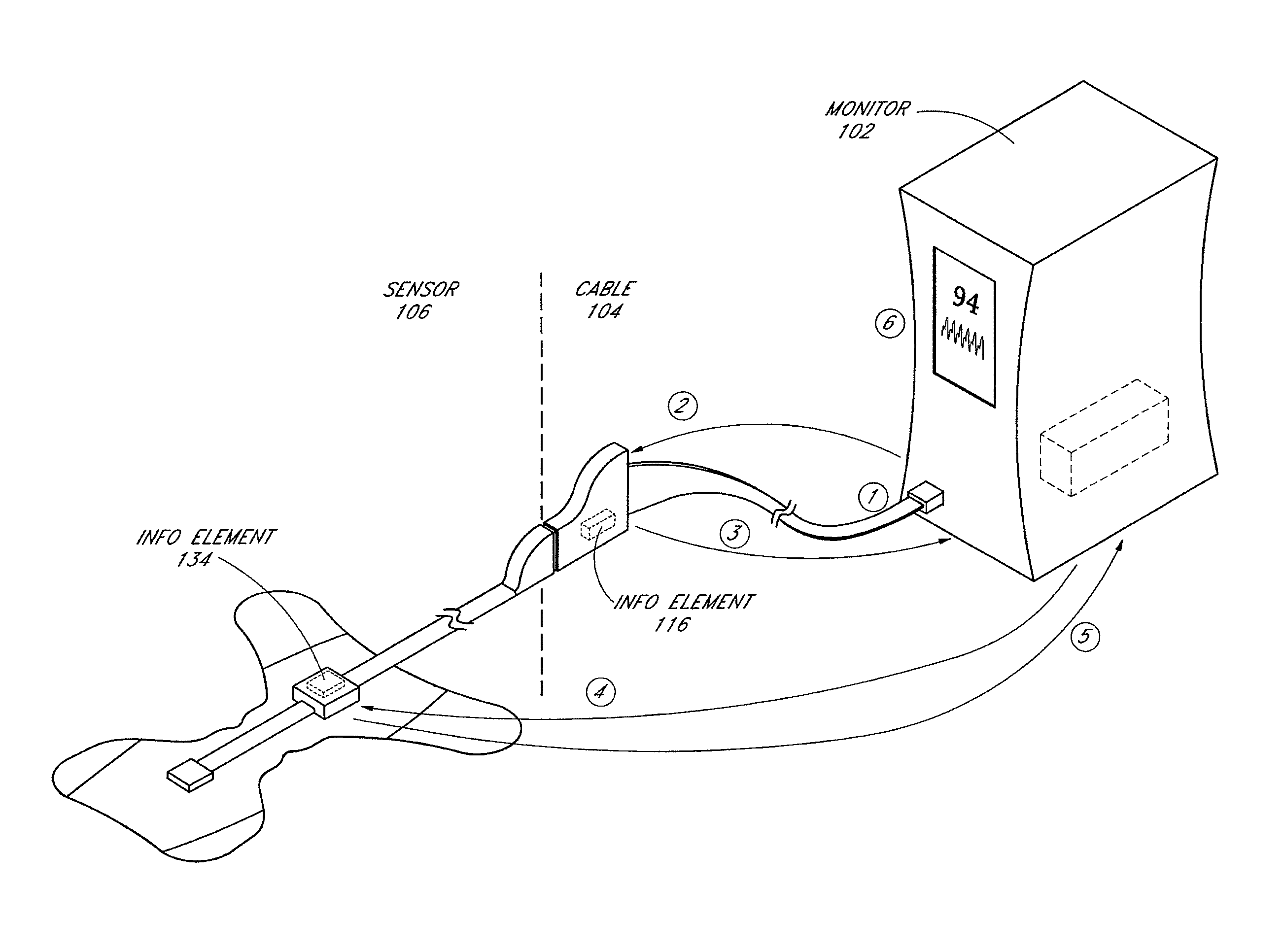
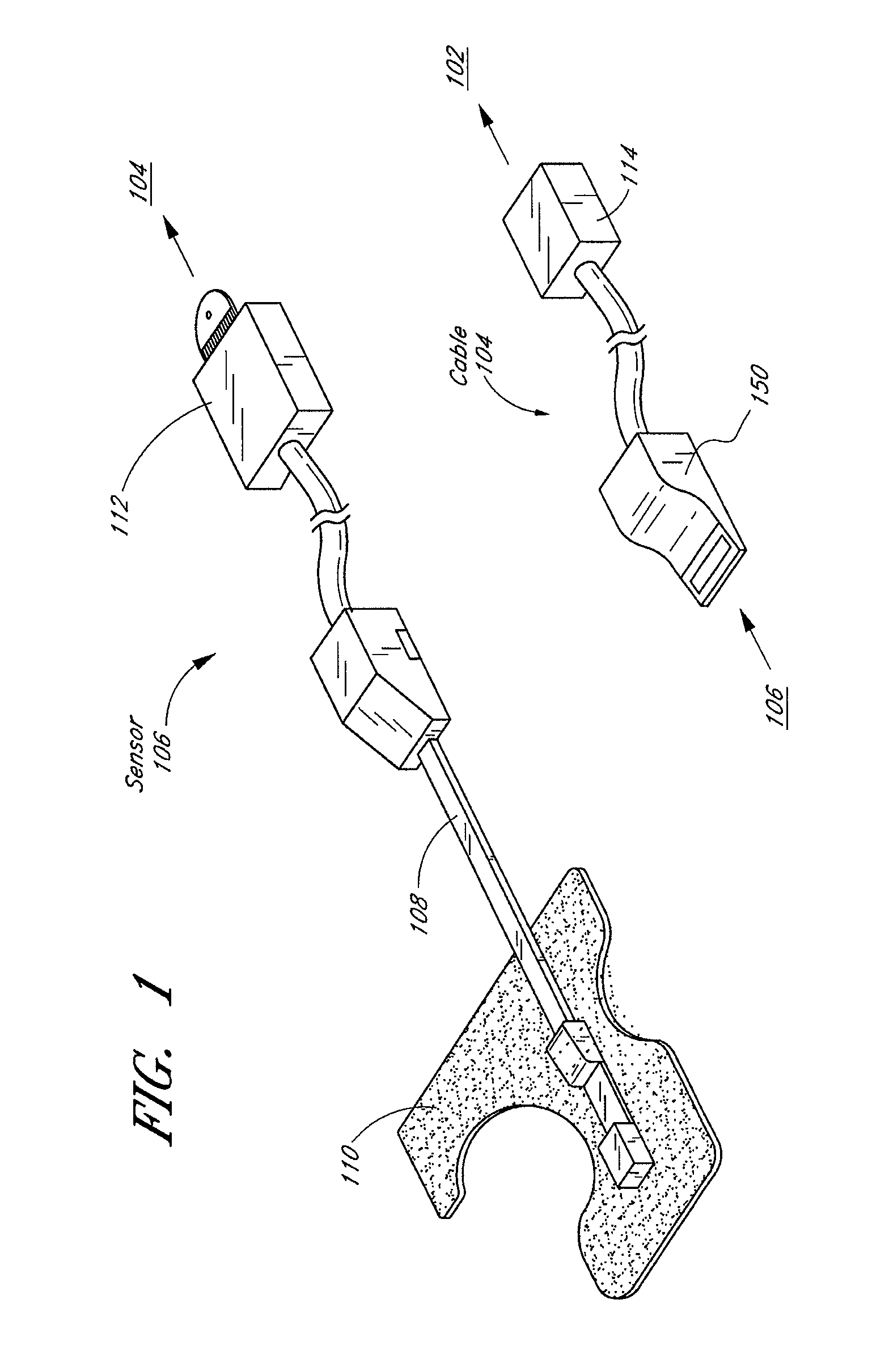
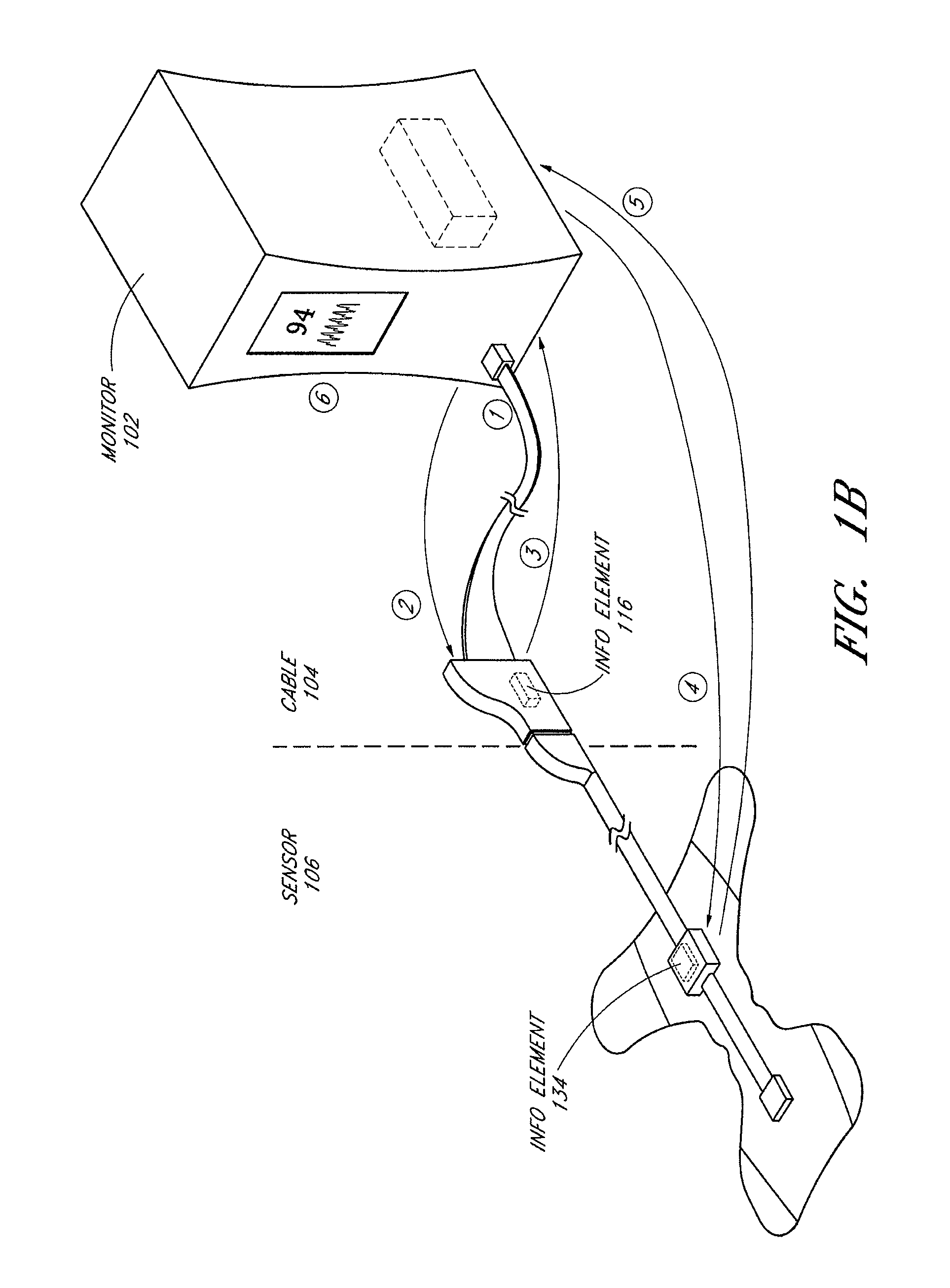
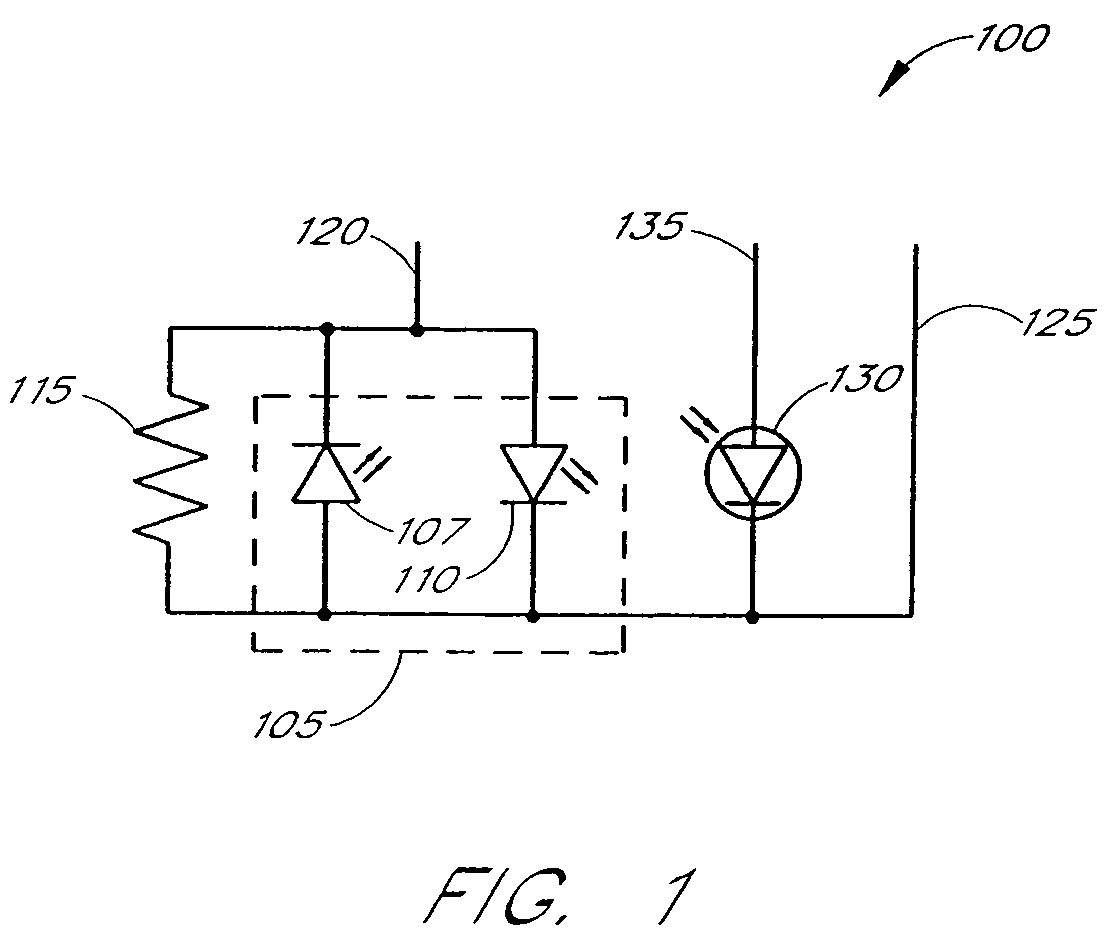
Connector switch
An interconnection between a sensor and a monitor has a cable, an information element and a switch. The cable has conductors providing electrical communication between a sensor connector and a monitor connector. The information element is readable by the monitor and mounted in the sensor connector, the monitor connector or the cable. A switch is mounted in the sensor connector and is responsive to the sensor connecting to and disconnecting from the sensor connector so as to alter the readability of said information element.
Owner:JPMORGAN CHASE BANK NA
Systems and methods for determining a physiological condition using an acoustic monitor
InactiveUS20090093687A1Avoid enteringQuick releaseElectrocardiographyCatheterElectrical conductorElectric power
A method of communicating with a physiological sensor is disclosed. In an embodiment, the method includes supplying power through a first conductor in a first mode to the physiological sensor and communicating with an information element through the first conductor in a second mode. The physiological sensor includes the information element, a power supply configured to receive and store power from the first conductor in the first mode, and sensing circuitry configured to receive power from the first conductor in the first mode. The power supply releases the stored power to the sensing circuitry in the second mode.
Owner:JPMORGAN CHASE BANK NA
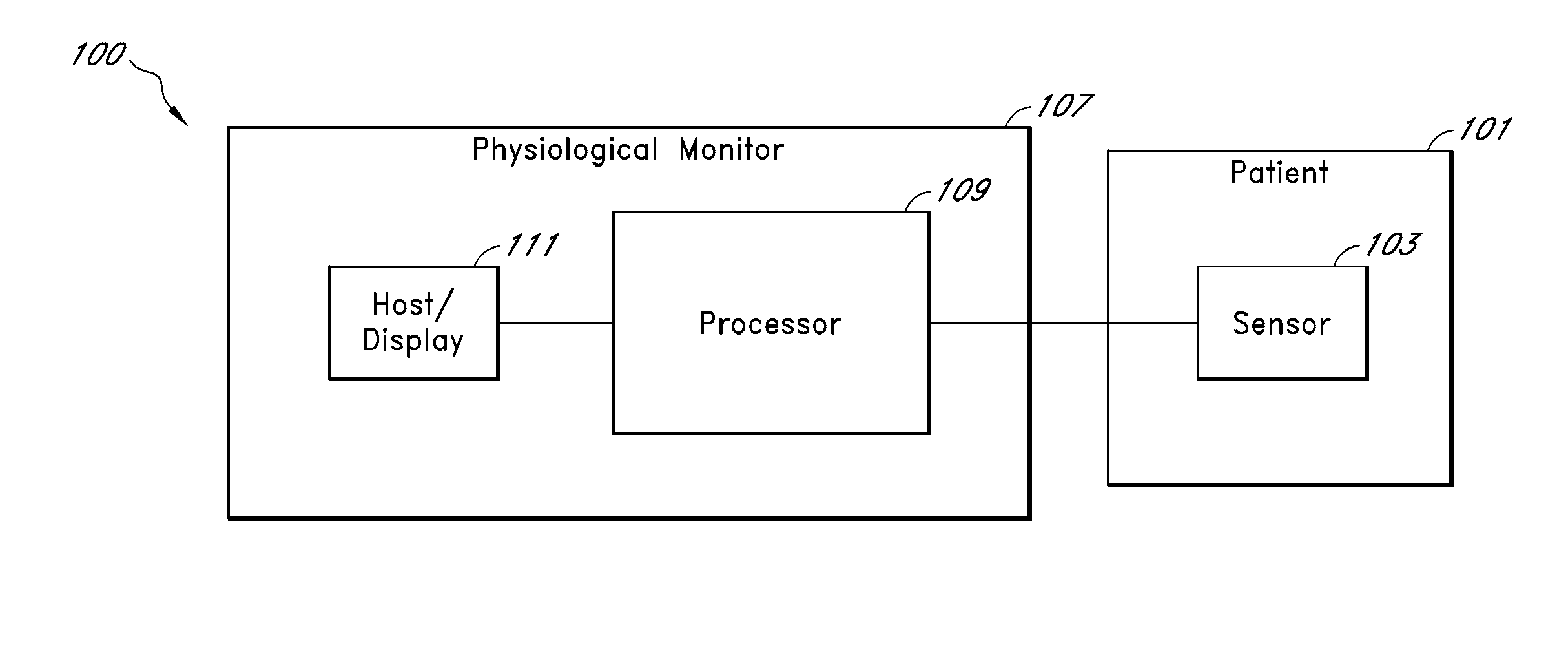
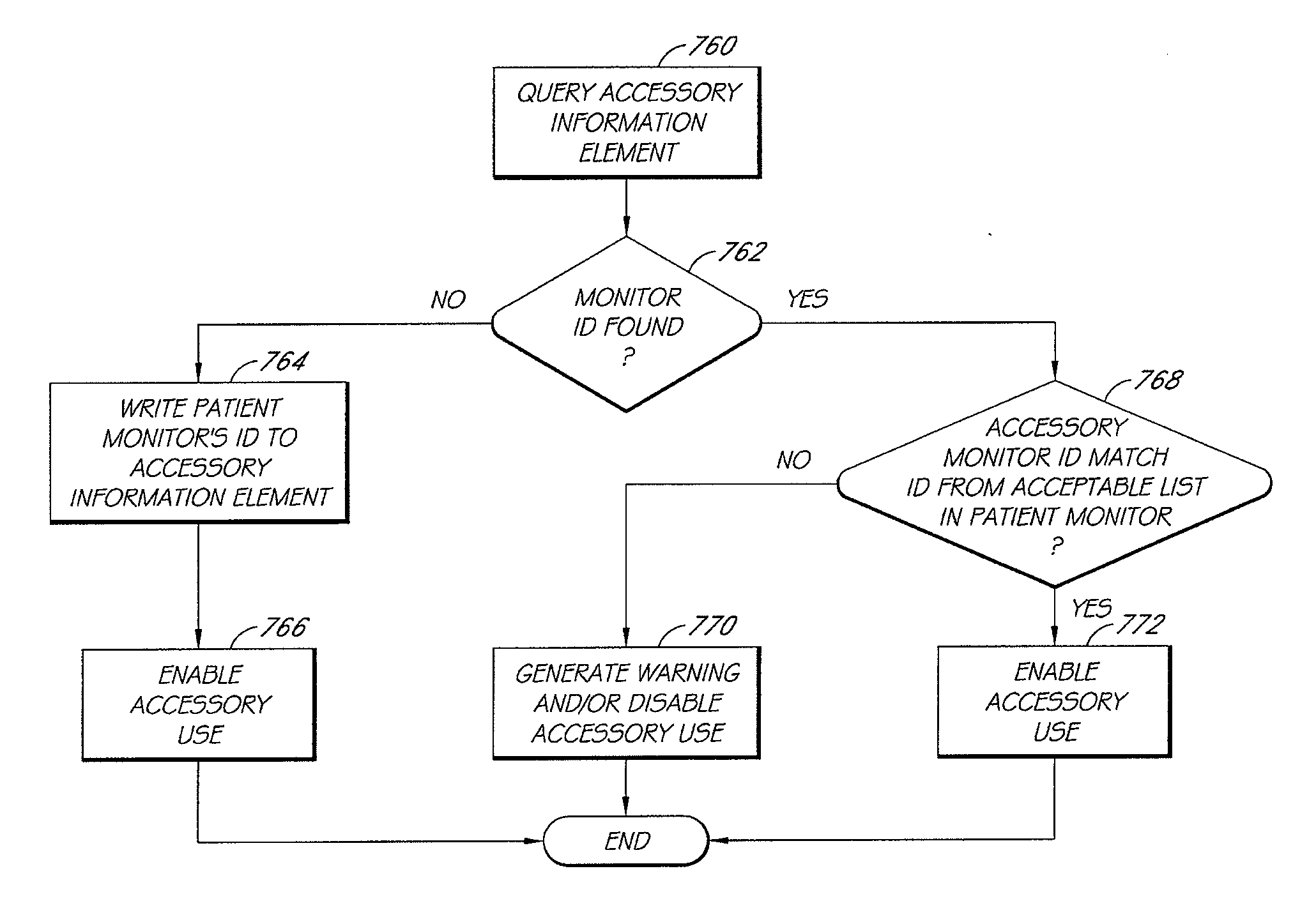
Patient monitor capable of monitoring the quality of attached probes and accessories
ActiveUS8255026B1Reduce capacityReduce the possibilityDiagnostic recording/measuringSensorsQuality controlPulse oximetry
A system and method to help maintain quality control and reduce cannibalization of accessories and attached probes in a highly sensitive patient monitor, such as a pulse oximetry system. One or more attached components may have information elements designed to designate what quality control mechanisms a patient monitor should look to find on that or another component or designate other components with which the one component may properly work. In a further embodiment, such information elements may also include data indicating the appropriate life of the component.
Owner:JPMORGAN CHASE BANK NA
Resposable pulse oximetry sensor
InactiveUS8000761B2Longevity and associated costSensorsBlood characterising devicesAdhesivePulse oximetry
A pulse oximeter sensor has both a reusable and a disposable portion. The reusable portion of the sensor preserves the relatively long-lived and costly emitter, detector and connector components. The disposable portion of the sensor is the relatively inexpensive adhesive tape component that is used to secure the sensor to a measurement site, typically a patient's finger or toe. The disposable portion of the sensor is removably attached to the reusable portion in a manner that allows the disposable portion to be readily replaced when the adhesive is expended or the tape becomes soiled or excessively worn. The disposable portion may also contain an information element useful for sensor identification or for security purposes to insure patient safety.
Owner:JPMORGAN CHASE BANK NA
Patient monitor capable of monitoring the quality of attached probes and accessories
ActiveUS20120319816A1Reduce capacityReduce the possibilityProgramme controlElectric signal transmission systemsQuality controlPulse oximetry
A system and method to help maintain quality control and reduce cannibalization of accessories and attached probes in a highly sensitive patient monitor, such as a pulse oximetry system. One or more attached components may have information elements designed to designate what quality control mechanisms a patient monitor should look to find on that or another component or designate other components with which the one component may properly work. In a further embodiment, such information elements may also include data indicating the appropriate life of the component.
Owner:JPMORGAN CHASE BANK NA
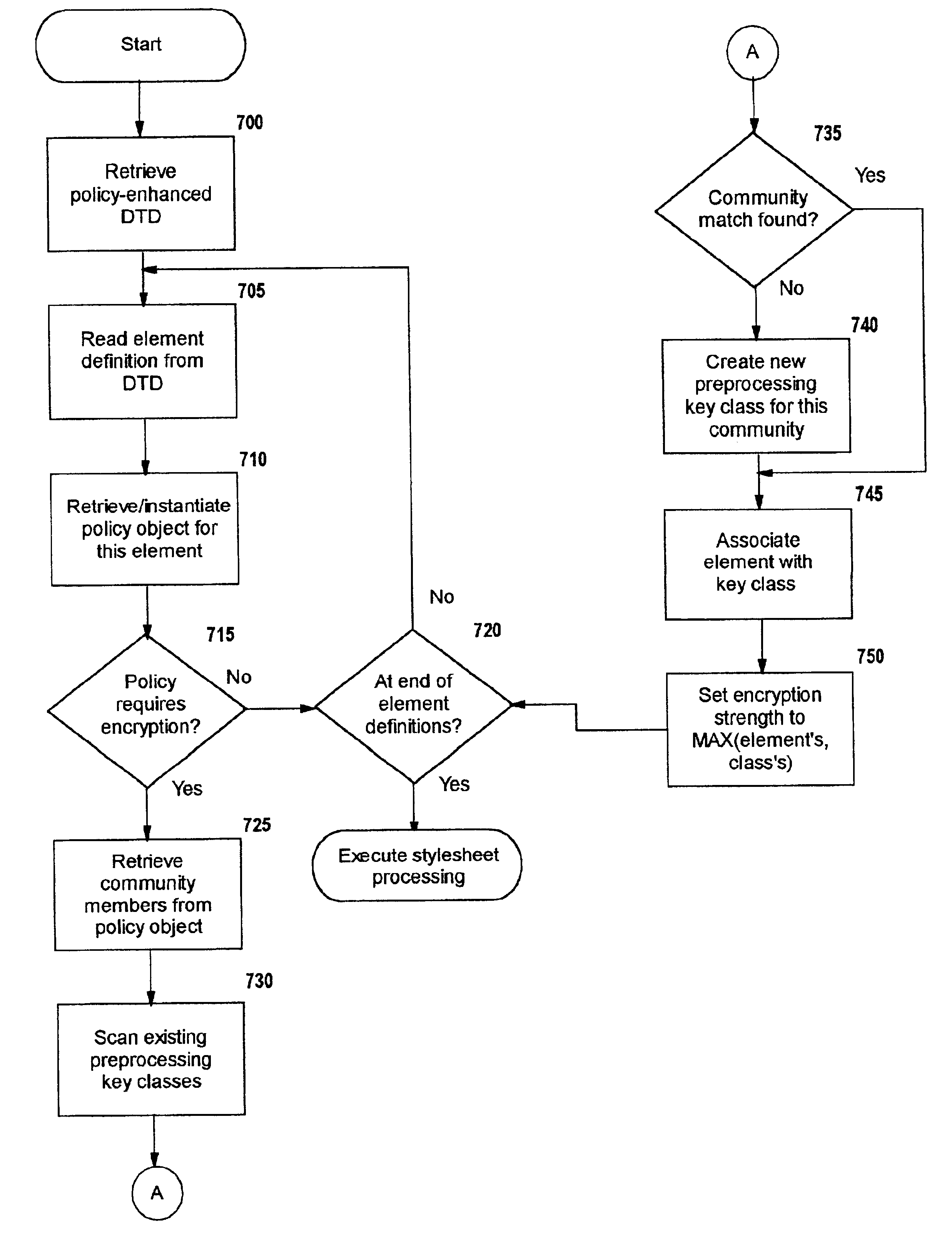
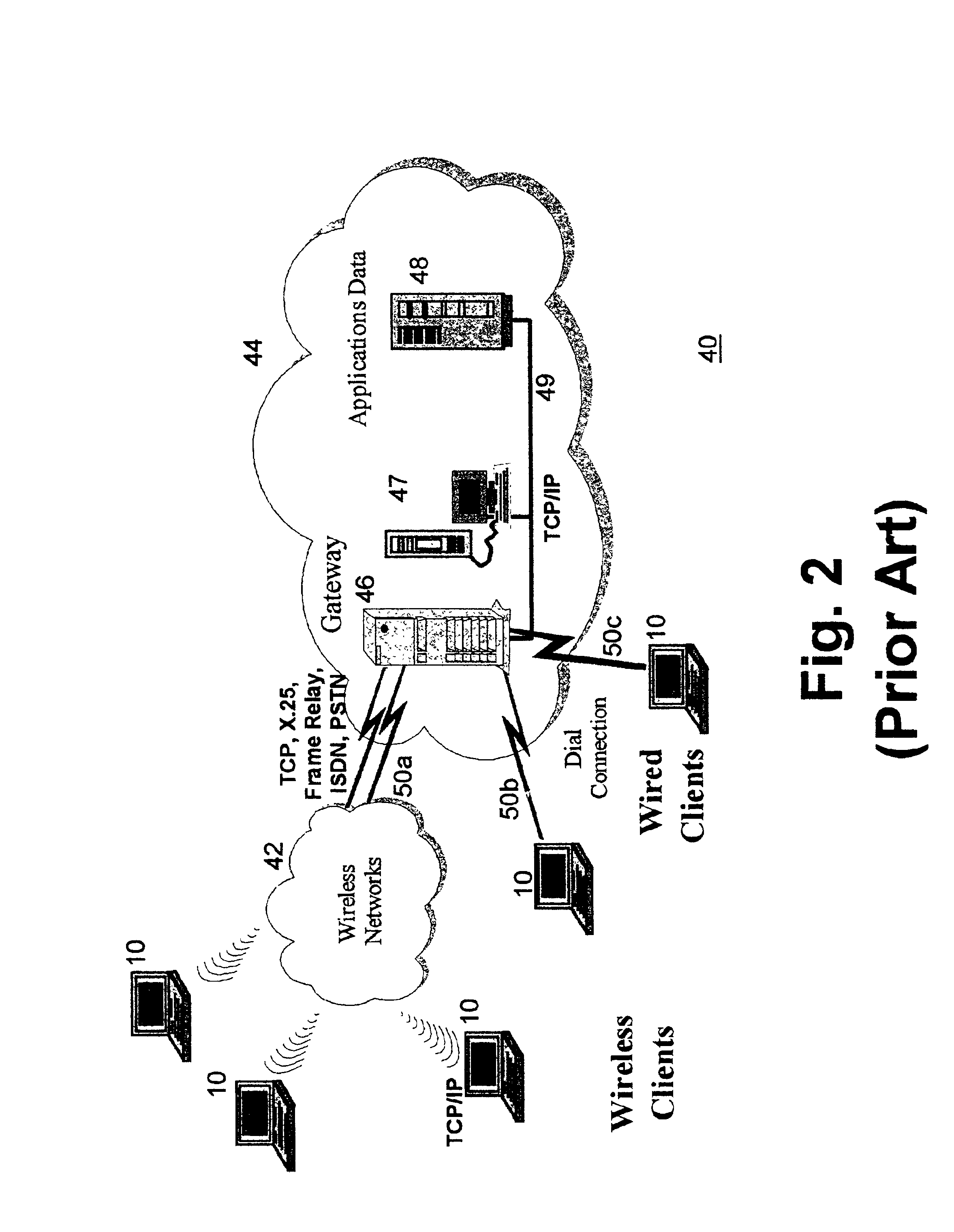
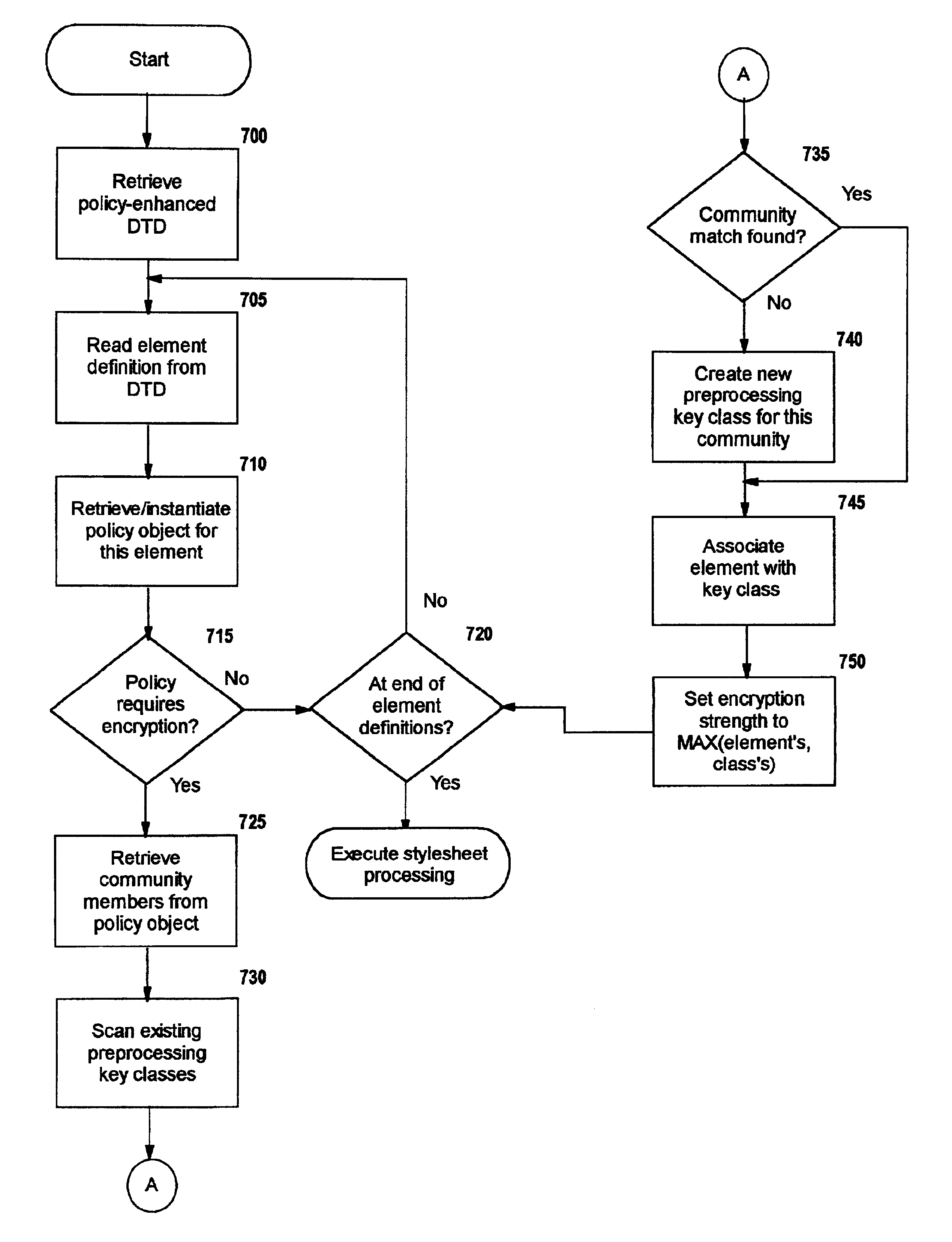
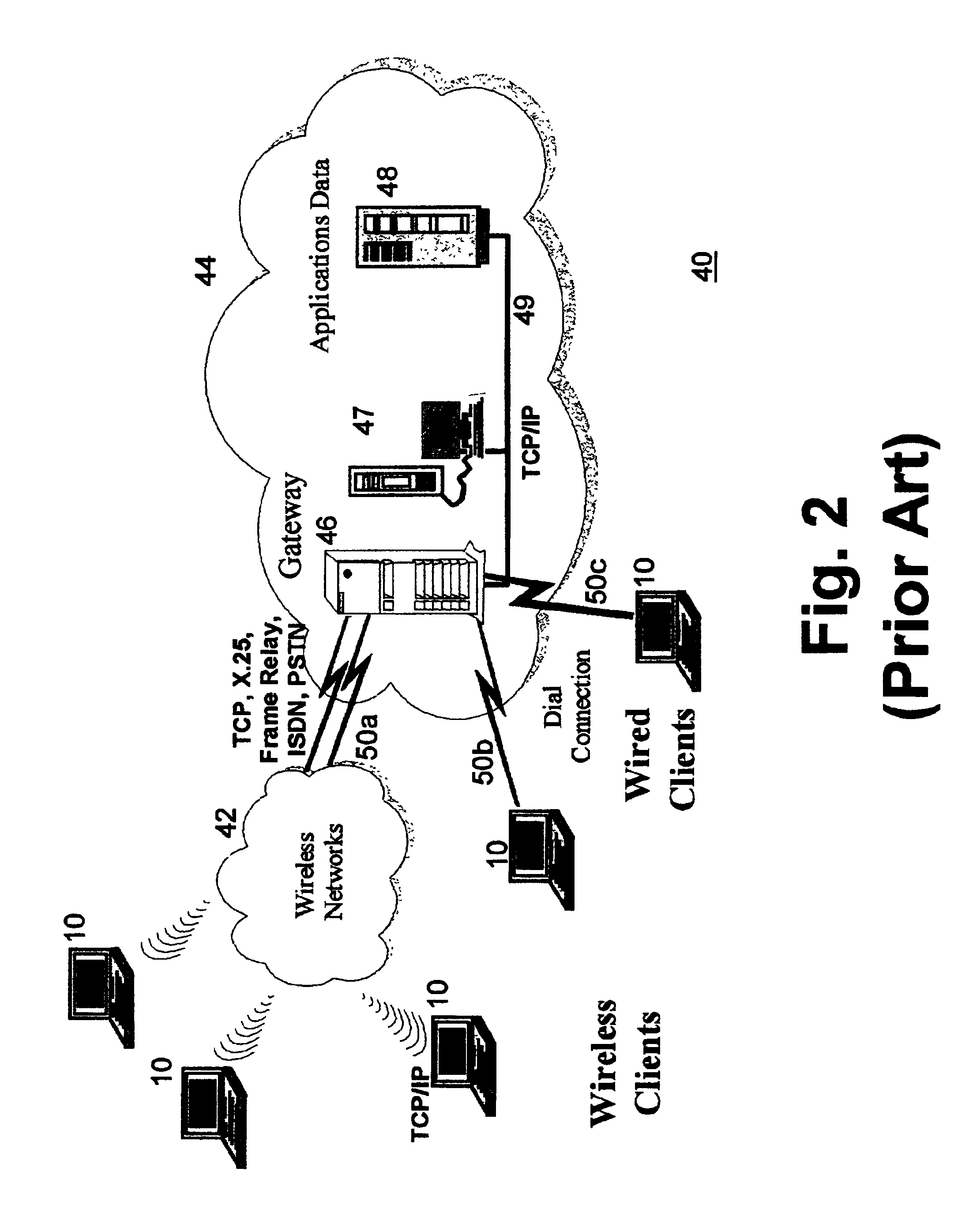
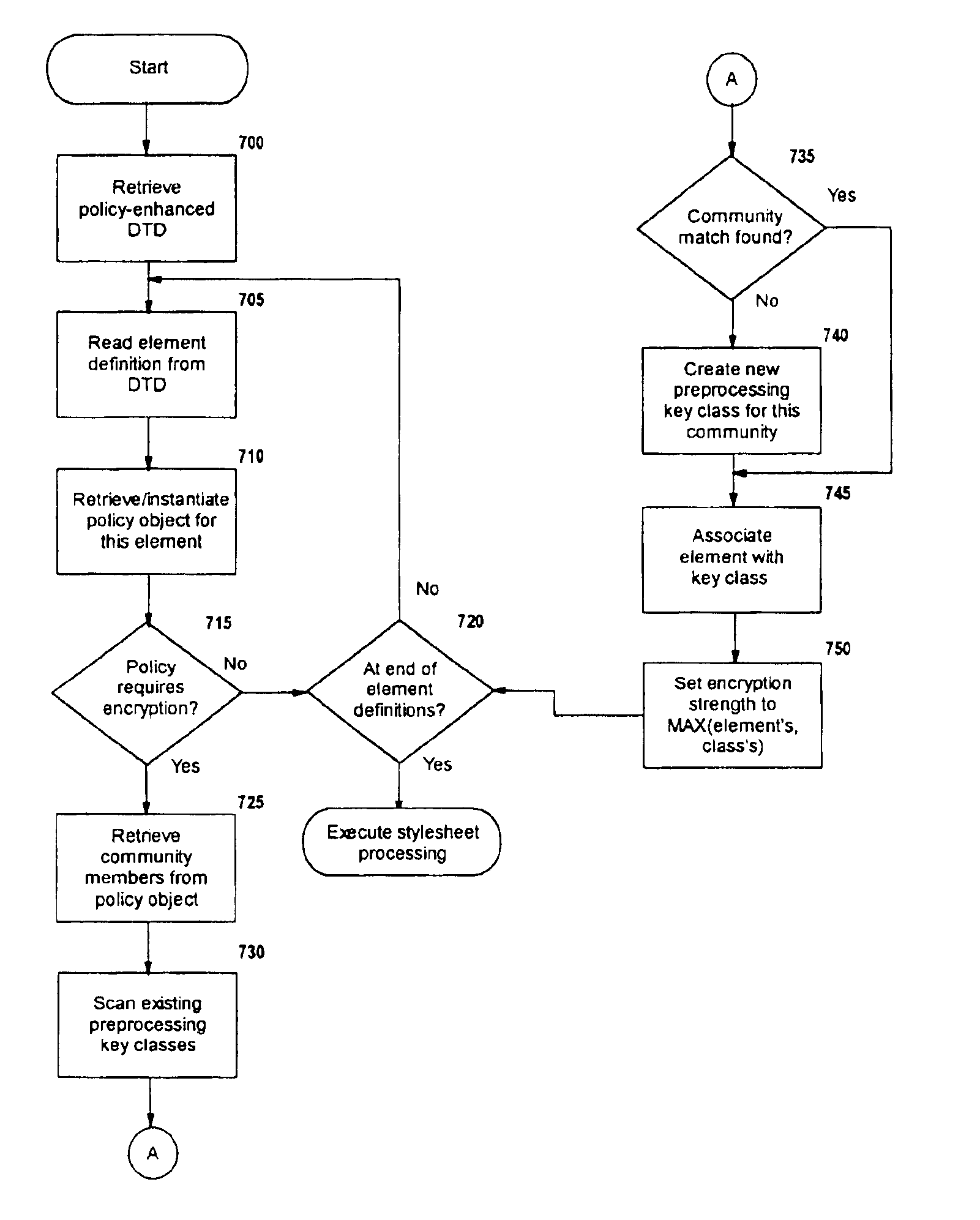
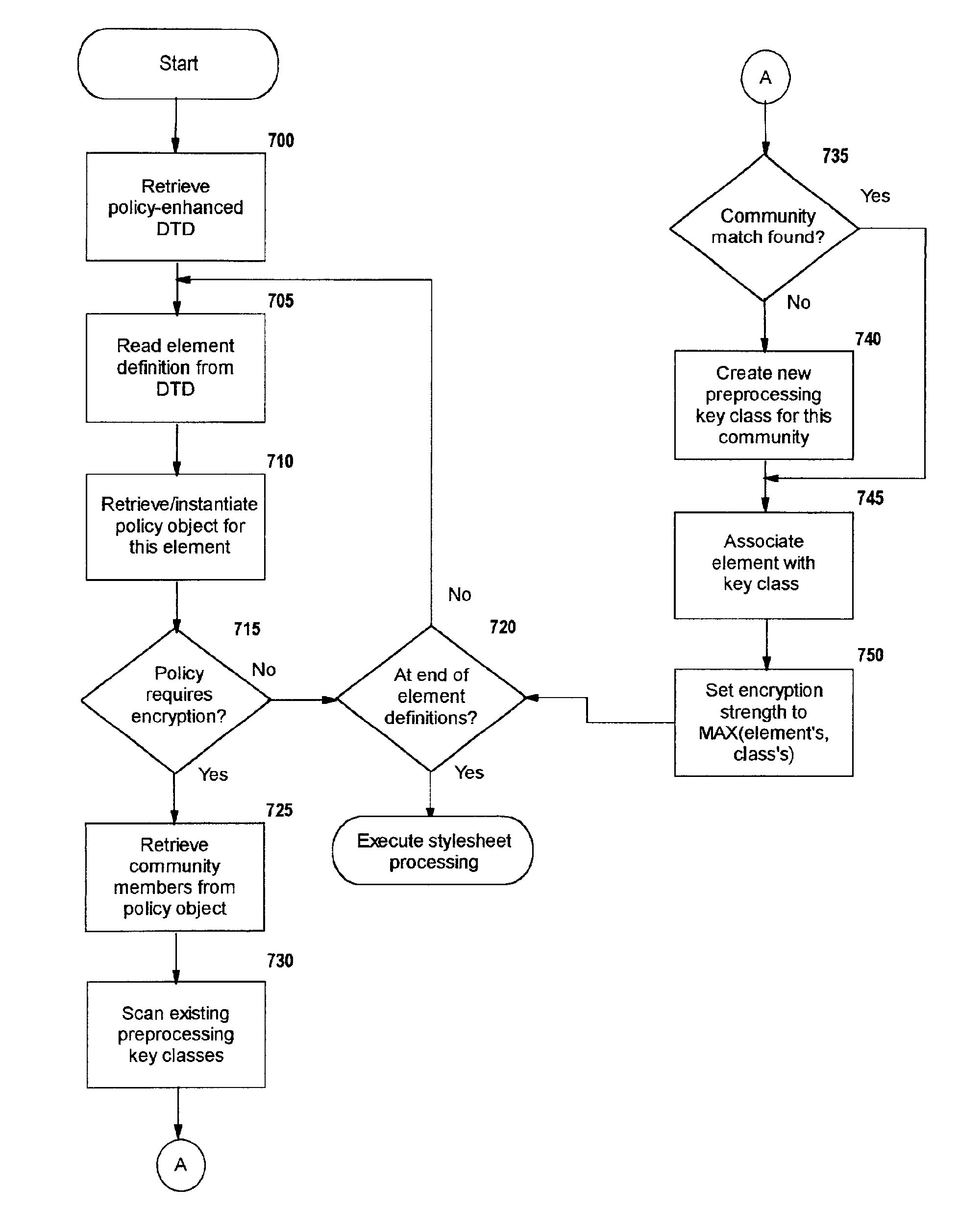
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Storage, management and distribution of consumer information
InactiveUS7257581B1Digital data processing detailsBuying/selling/leasing transactionsApplication softwareProprietary software
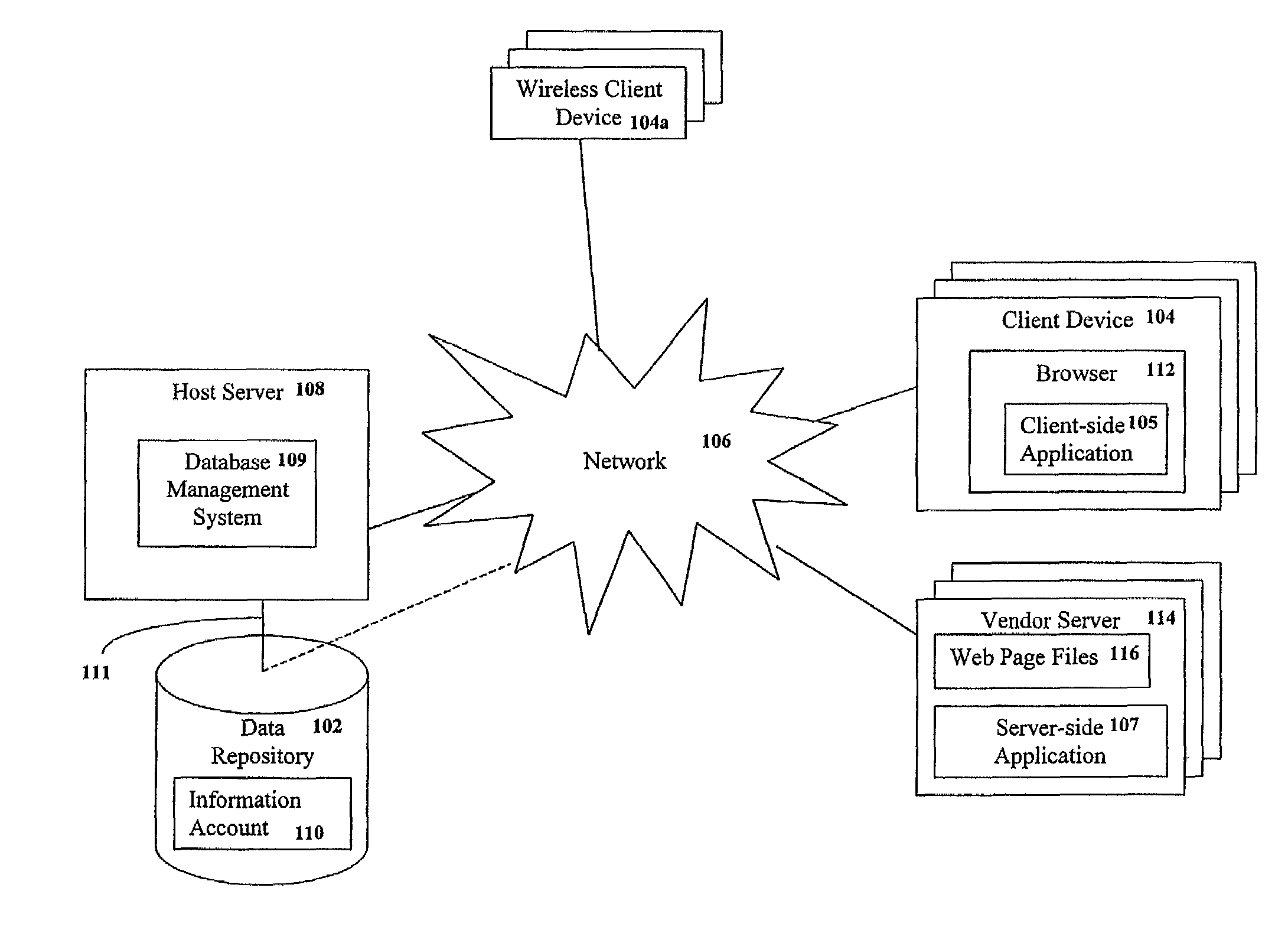
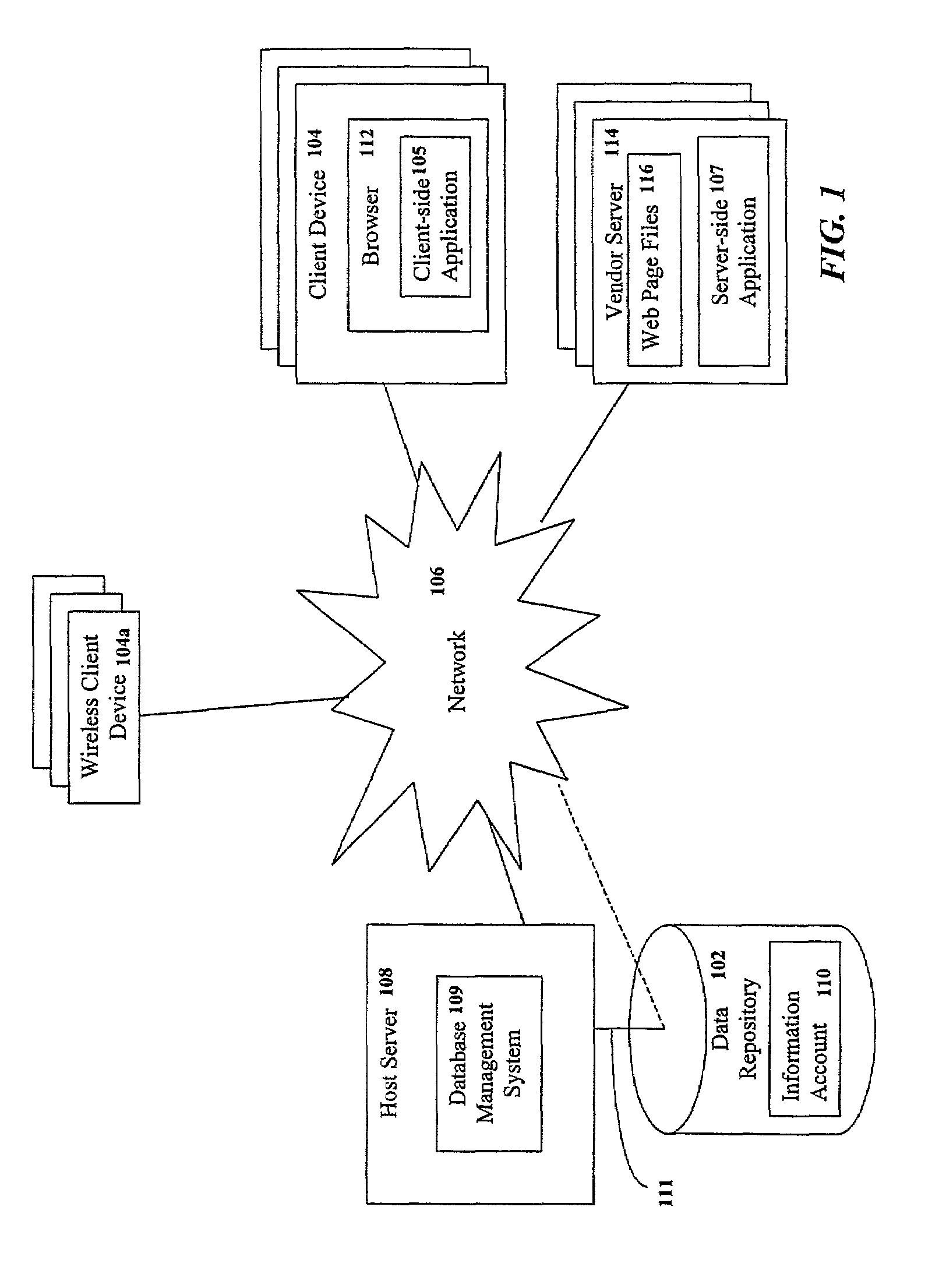
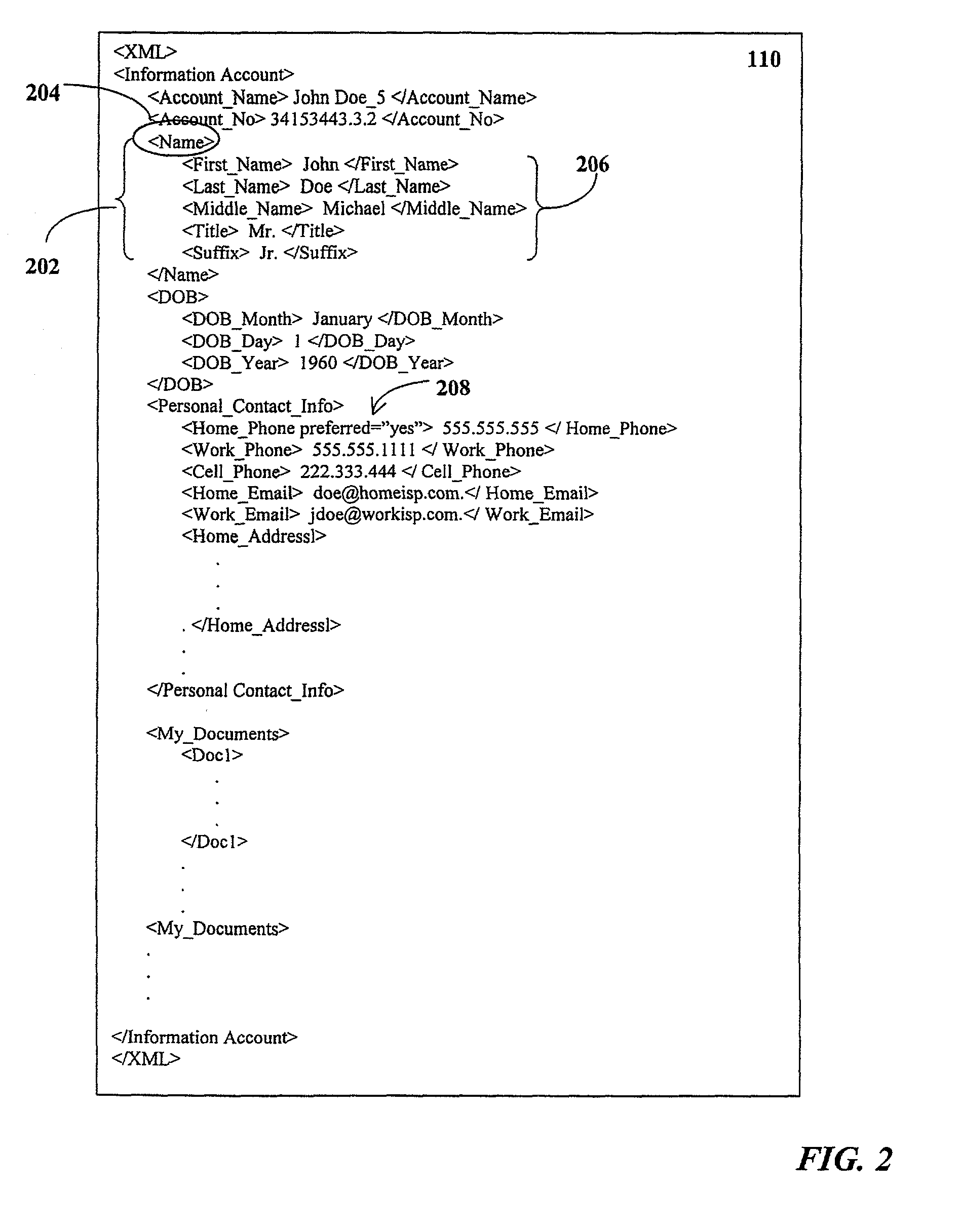
Consumers may centrally store, manage and distribute information using an information account stored in a central data repository. The information account is accessible from any client device, without the need to permanently store or install proprietary software thereon. The information account comprises a plurality of consumer information elements stored in a tagged data format. A host server hosts a database management system for accessing the information account. A client-side application may manage communications with host server. Alternatively, the client device may interact with a vendor server that executes a server-side application for managing communications with the host server. In response to a request from the consumer, the host server may filter selected consumer information elements from the information account and transmit the filtered consumer information elements to the client-side or server-side application. The filtered consumer information elements may then be automatically integrated into a vendor business process on behalf of the consumer, if desired.
Owner:CXT SYST INC
Discovery and authentication scheme for wireless mesh networks
InactiveUS20070189249A1Readily apparentError preventionFrequency-division multiplex detailsOpen Systems InterconnectionMesh node
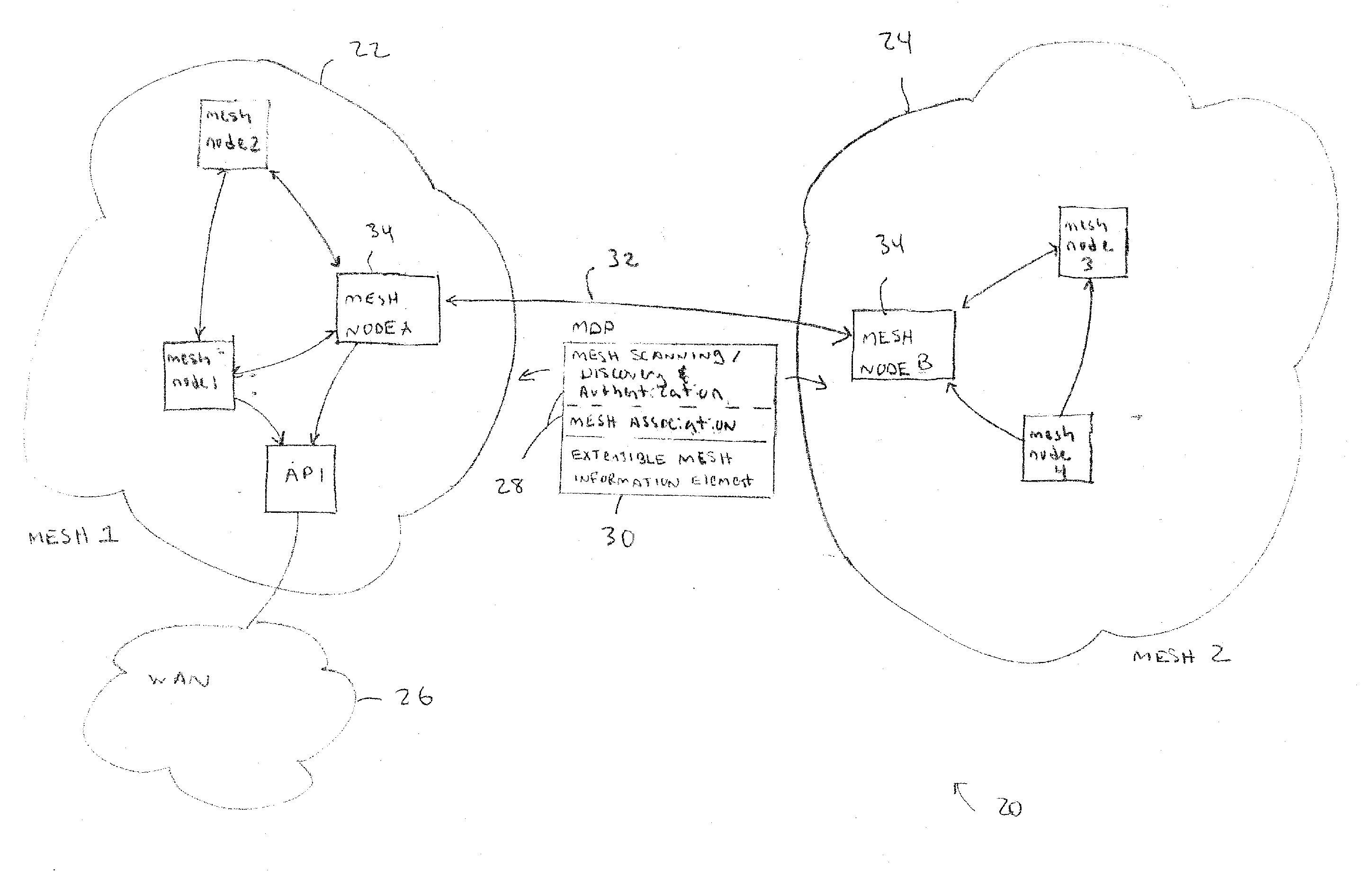
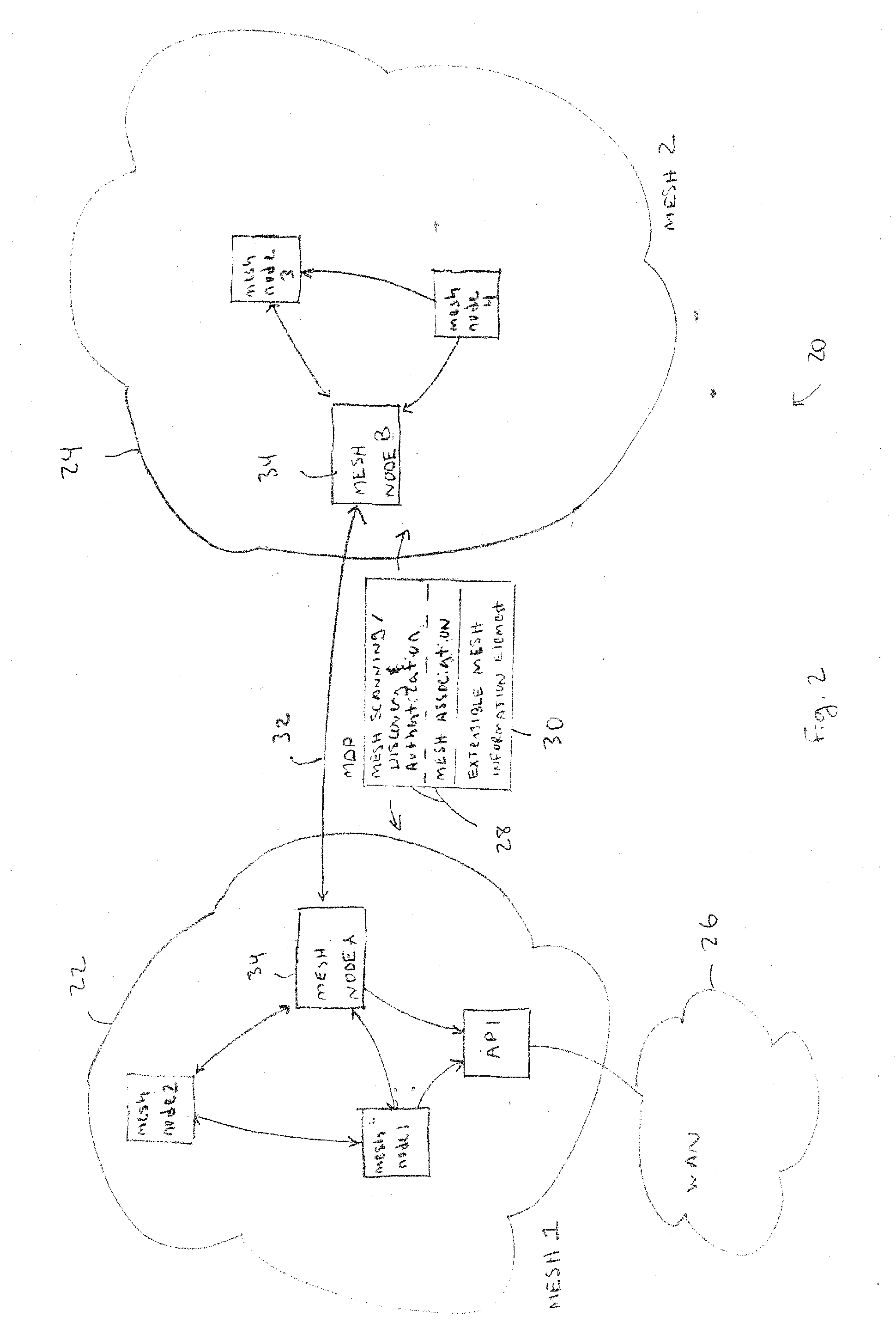
Wireless network devices discover individual mesh nodes and networks of mesh nodes. An association is formed on the basis of peer-to-peer interactions at layer-1, layer-2 and / or higher layers of the Open System Interconnect (OSI) model. In particular, the system uses Beacon, Probe Request, Probe Response, Association Request, Association Response, and Disassociation frames and introduces a new Extensible Mesh Information Element (EMIE) used by mesh nodes to discover, authenticate, and associate with other peer nodes.
Owner:SRI INTERNATIONAL
User interface for a mobile device using a user's gesture in the proximity of an electronic device
InactiveUS20090265670A1Cathode-ray tube indicatorsInput/output processes for data processingMode controlDisplay device
An electronic device having a user interface on a display and method for controlling the device, the method including: detecting a proximity of an object to the display; detecting a two-dimensional motion pattern of the object; and controlling the user interface according to the detected two-dimensional motion pattern. Also, a method including: detecting an object in a space over a border between first and second zones of a plurality of touch-sensitive zones and outputting a detection signal; and simultaneously displaying first and second information elements corresponding to the first and second zones in response to the detection signal.
Owner:LG ELECTRONICS INC
Universal mobile telecommunications system (UMTS) quality of service (QoS) supporting variable QoS negotiation
InactiveUS7668176B2Eliminate, delays in establishing user connectionsNetwork traffic/resource managementTime-division multiplexQuality of serviceDistributed computing
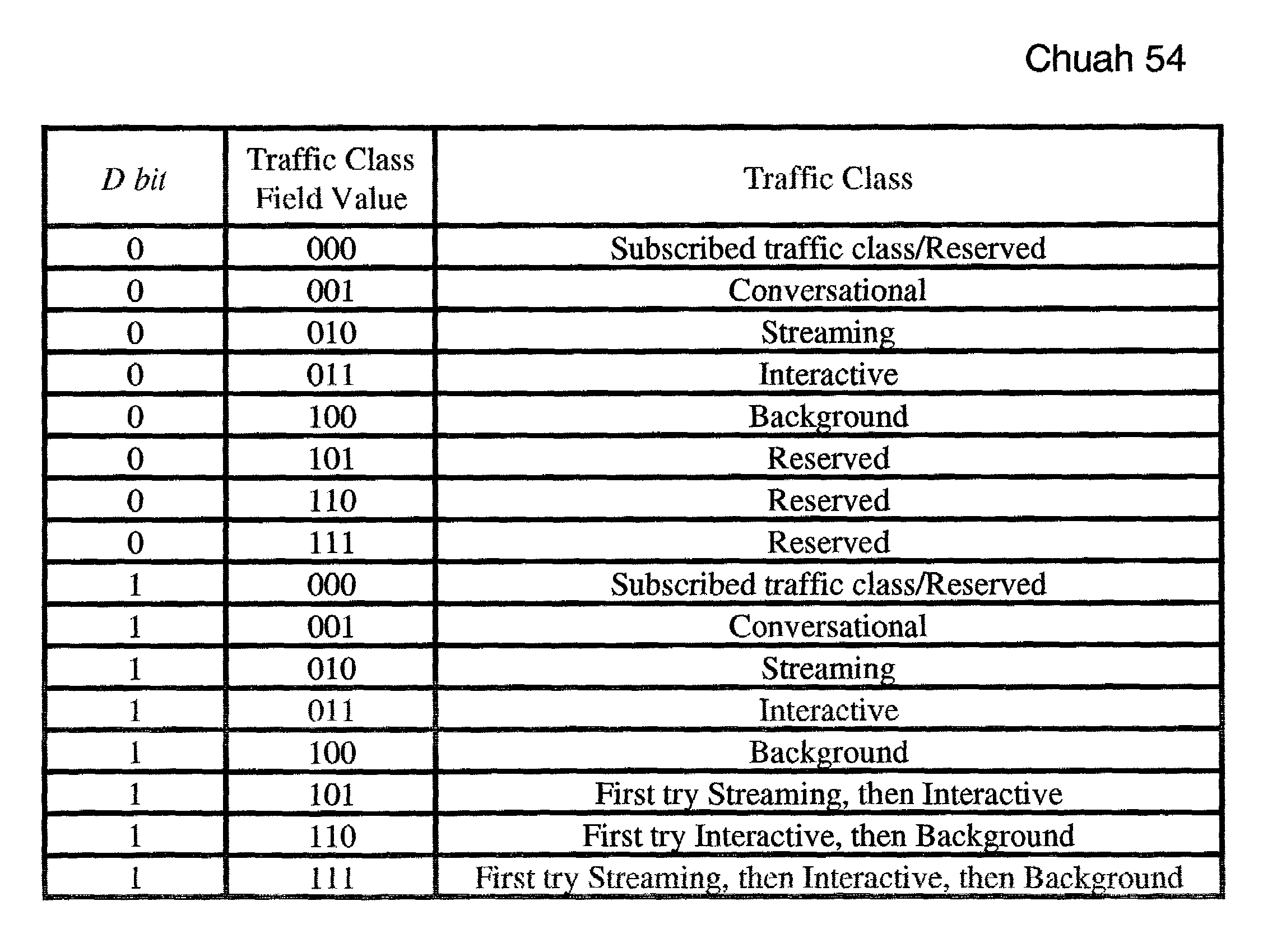
A UMTS (Universal Mobile Telecommunications System) core network supports the negotiation of variable quality of service (QoS). A QoS information element (IE) is defined that supports downgradeable QoS requirements by allowing multiple traffic classes to be specified in a priority order. Similarly, a QoS information element (IE) is defined that supports upgradeable QoS requirements.
Owner:ALCATEL-LUCENT USA INC
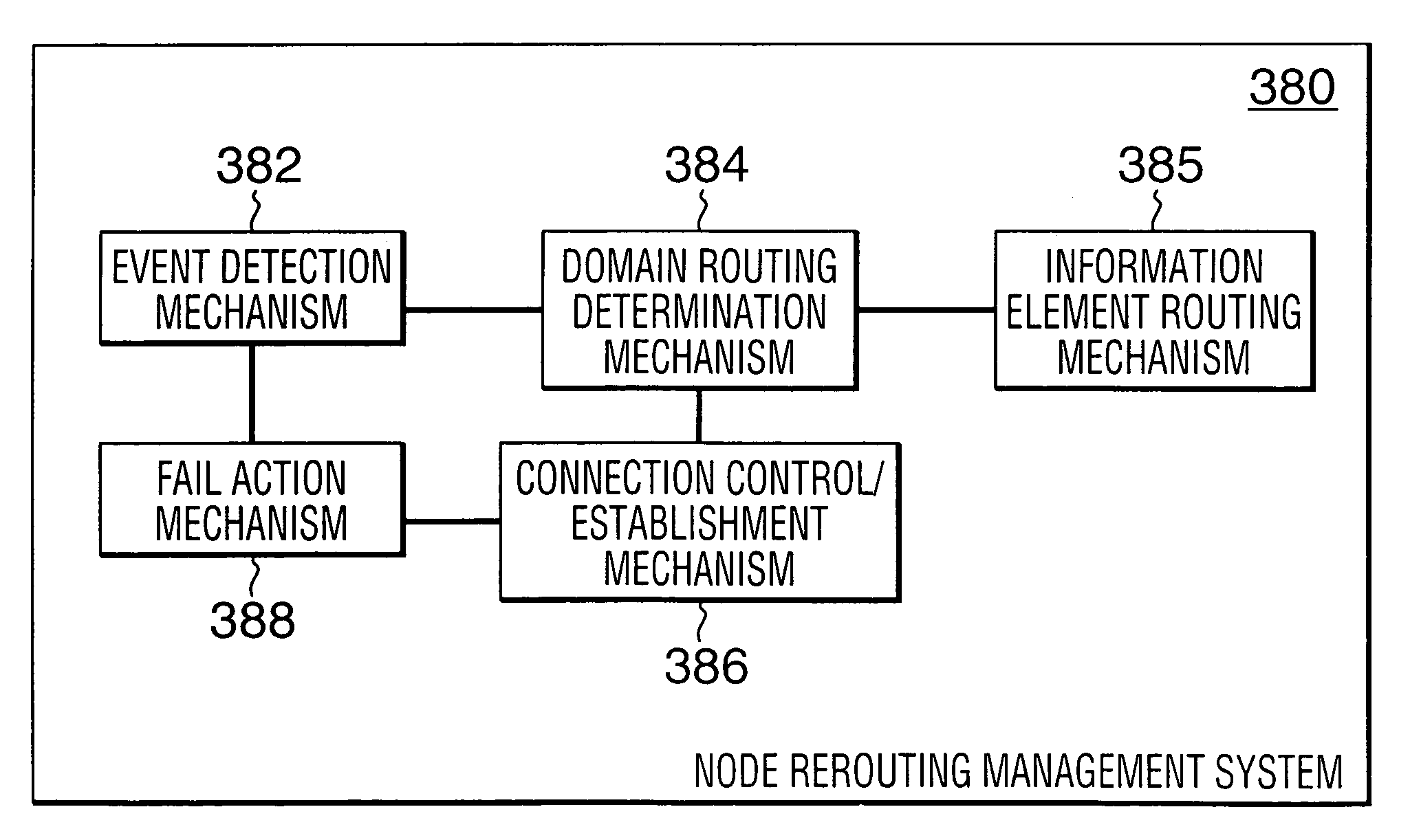
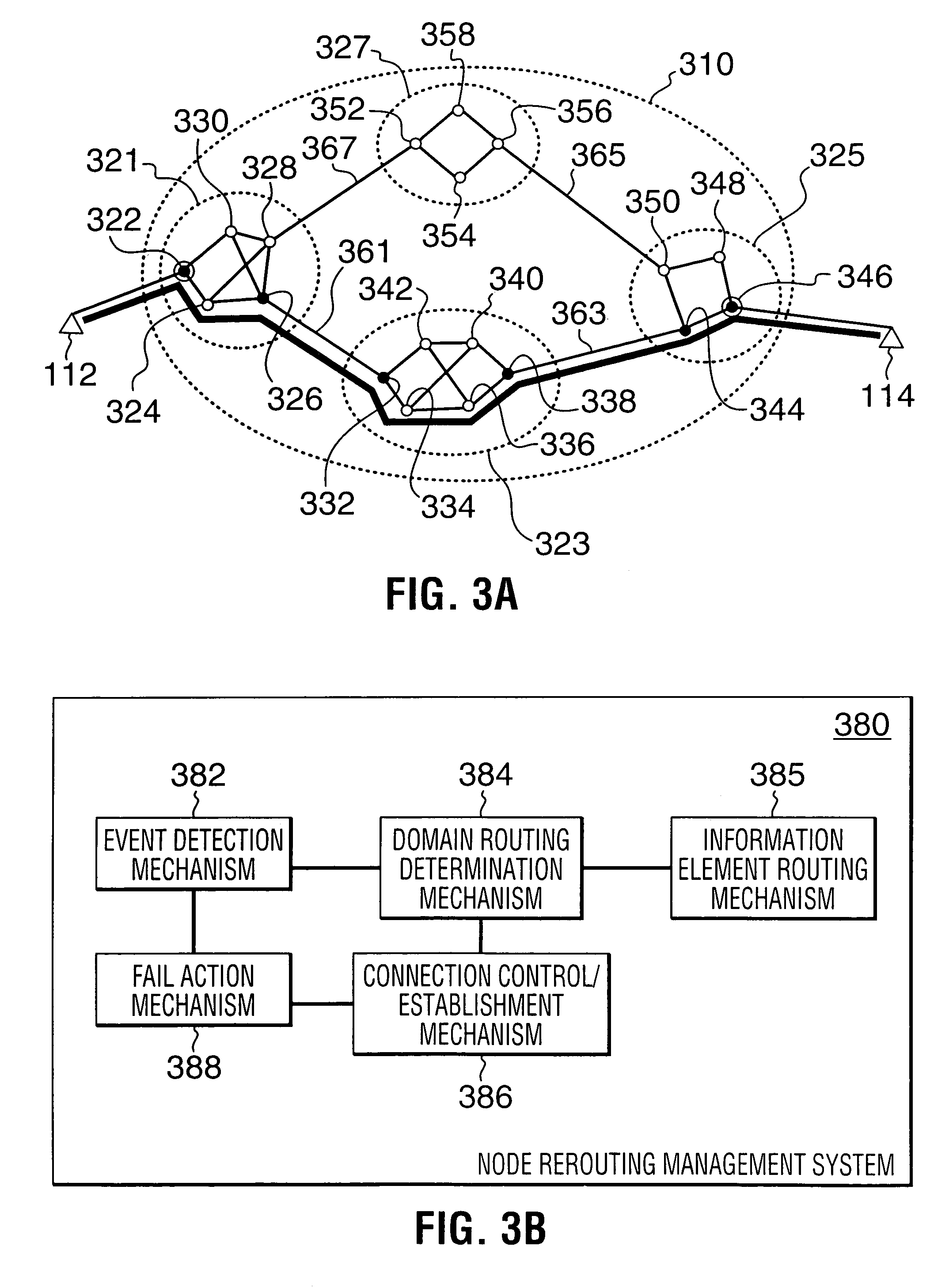
Rerouting in connection-oriented communication networks and communication systems
InactiveUS7180866B1Multiplex system selection arrangementsError preventionDouble faultCommunications system
A Private Network-Network Interface (PNNI) network including interconnected nodes is defined as a single rerouting domain (“global domain”) and the global domain is further defined by multiple divided domains (“local domains”). Each of the local domains is defined to include multiple nodes that are included in the network. Connection recovery and path optimization in the global domain (the entire PNNI network) are performed in accordance with a global rerouting protocol. The global rerouting protocol is a modification of the standard Domain-Based Rerouting (DBR) protocol, by adding information elements of domain identifier, rerouting for the global domain. The DBR protocol does not support the connection recovery from a link failure between local domains (“inter-domains”) and the global path optimization. The global rerouting method is capable of connection recovery and path optimization outside of any rerouting local domains. The global rerouting provides double fault recovery within the rerouting domain (“intra-domain”) as covered by the DBR and outside of the domains (“inter-domain”) or when the initial fault recovery within the domain has failed. Also, the global rerouting method provides maximum path optimization across all domains and within the rerouting local domain.
Owner:RPX CLEARINGHOUSE
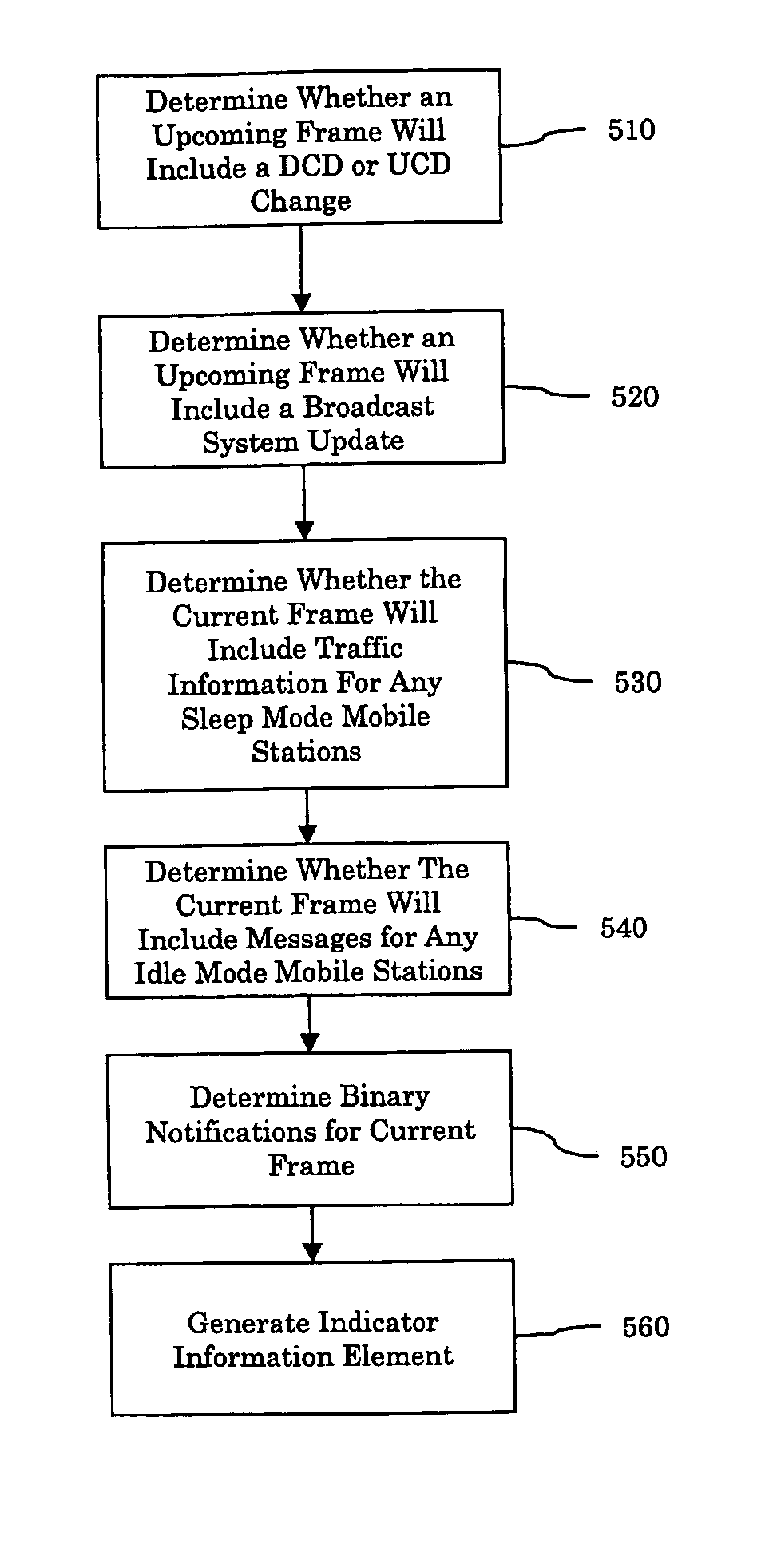
Method and apparatus for providing information to mobile stations in inactive states
ActiveUS20060029011A1Reduce processing timeFast and efficient techniquePower managementTransmission systemsMobile stationBroadcast system
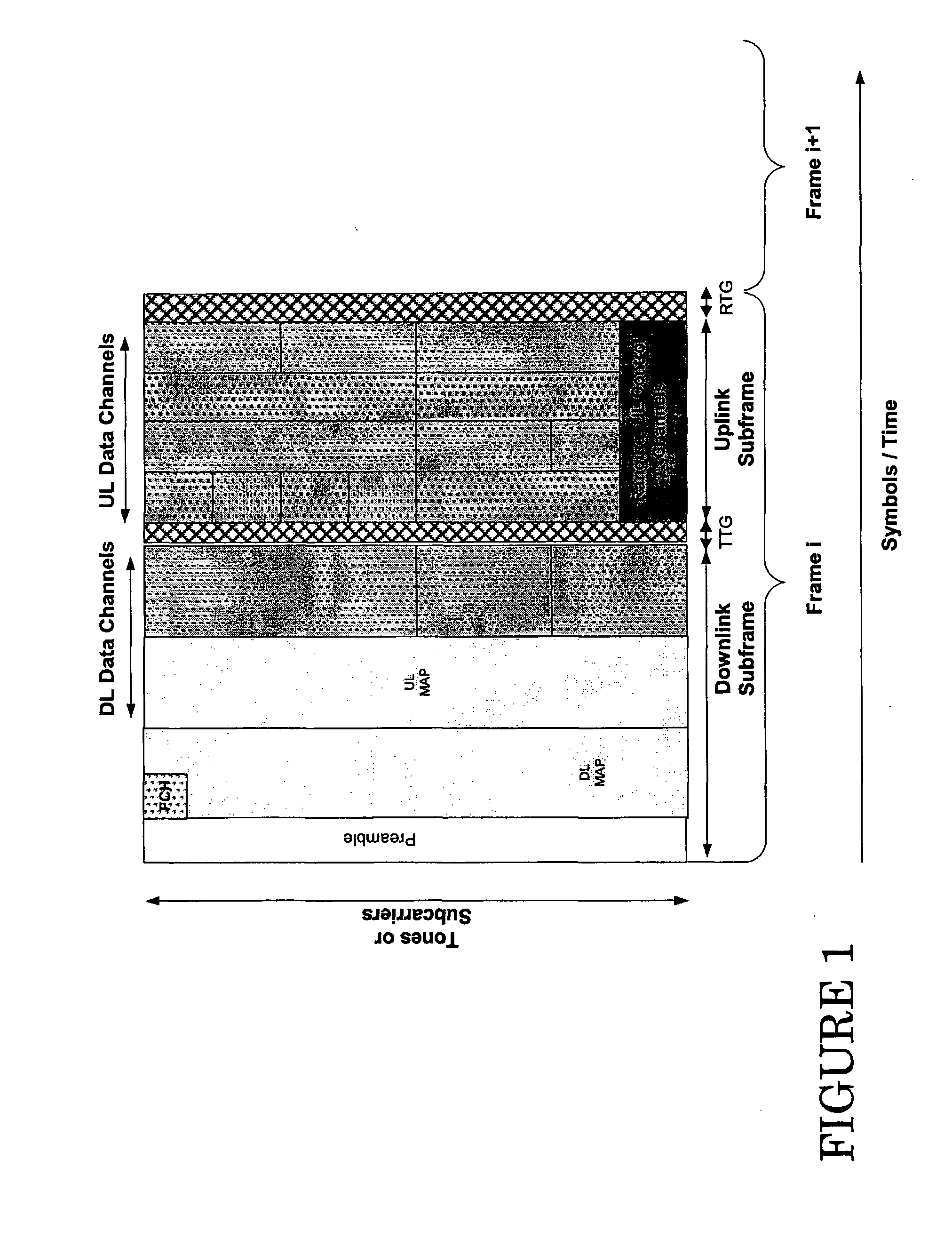
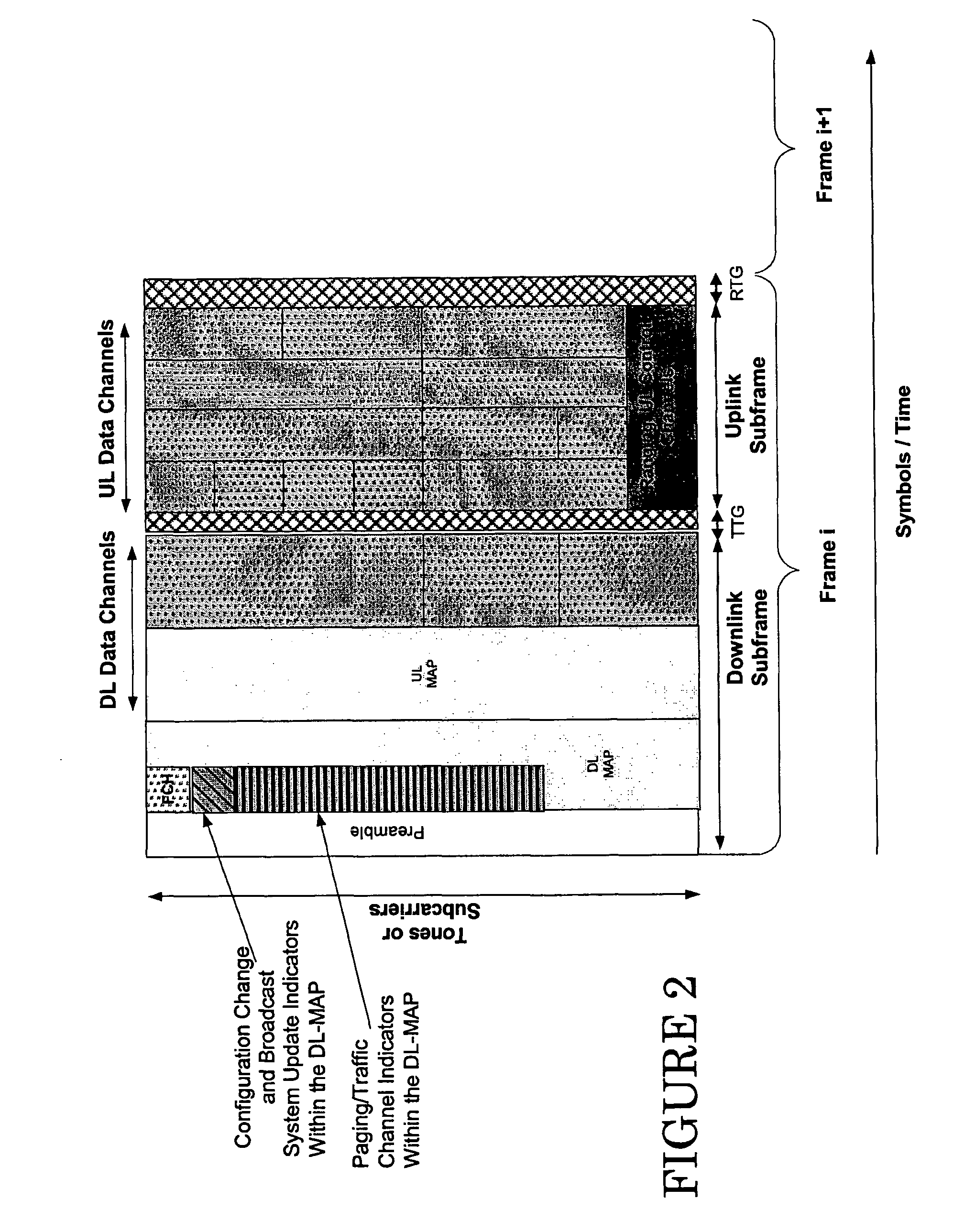
Methods and apparatus for notifying mobile stations in an inactive state of the presence of uplink or downlink channel configuration, broadcast system updates, traffic channel allocations and paging messages are provided. The notification can be provided in an information element in the same channel as the frame, or in a different channel. The information element identifies a subsequent frame which includes broadcast or configuration changes. The notifications for traffic channel allocations can include a first field, which identifies whether there are any traffic channel allocations for any sleep mode mobile station, and a second field for identifying the particular sleep mode mobile stations which are to receive traffic channel allocations. Notifications for paging messages can include a field, which identifies whether there are any paging messages for any idle mode mobile stations, and use second field to identify the particular idle mode mobile stations, which are to receive the paging messages.
Owner:NEXTEL COMMUNICATIONS
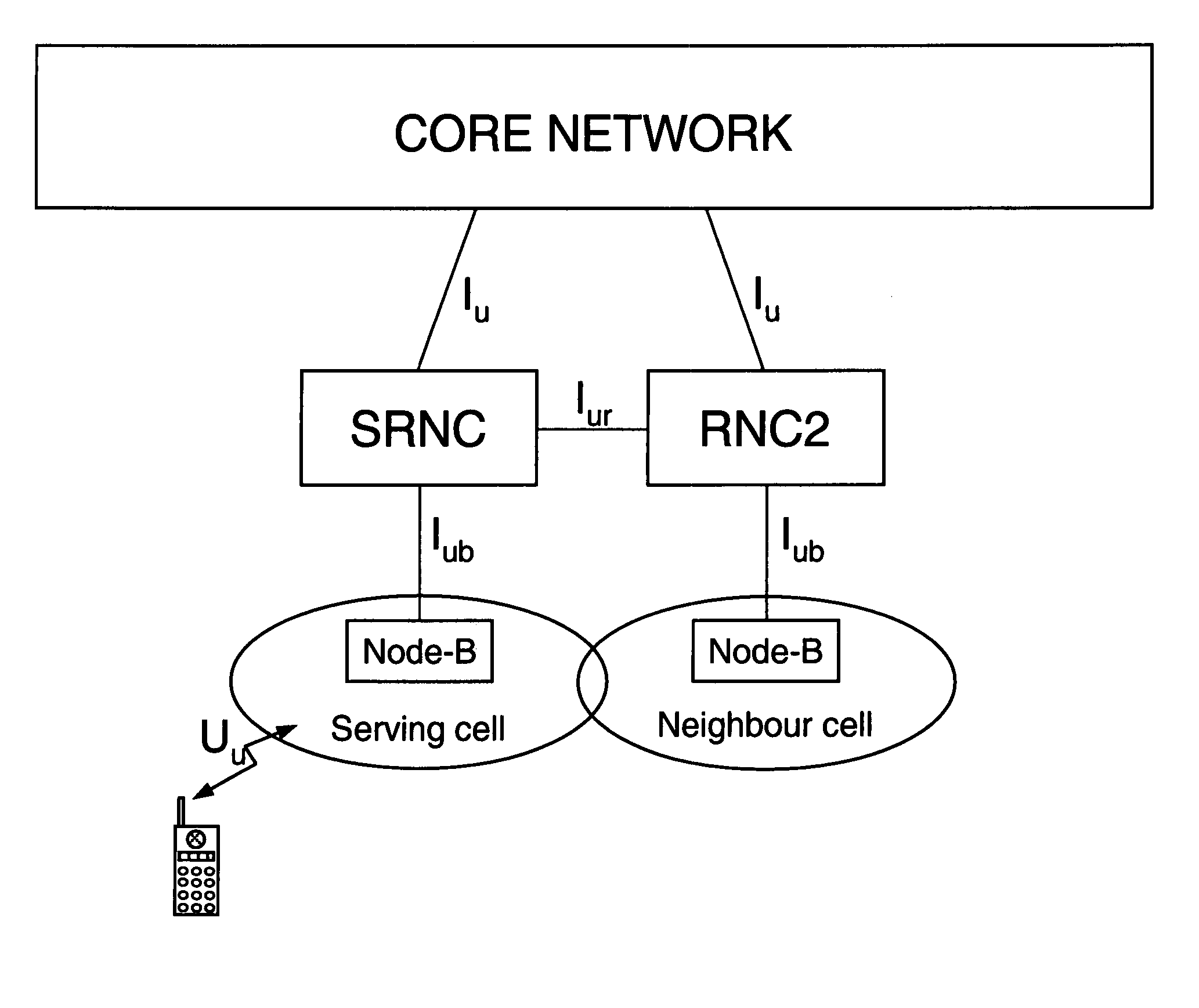
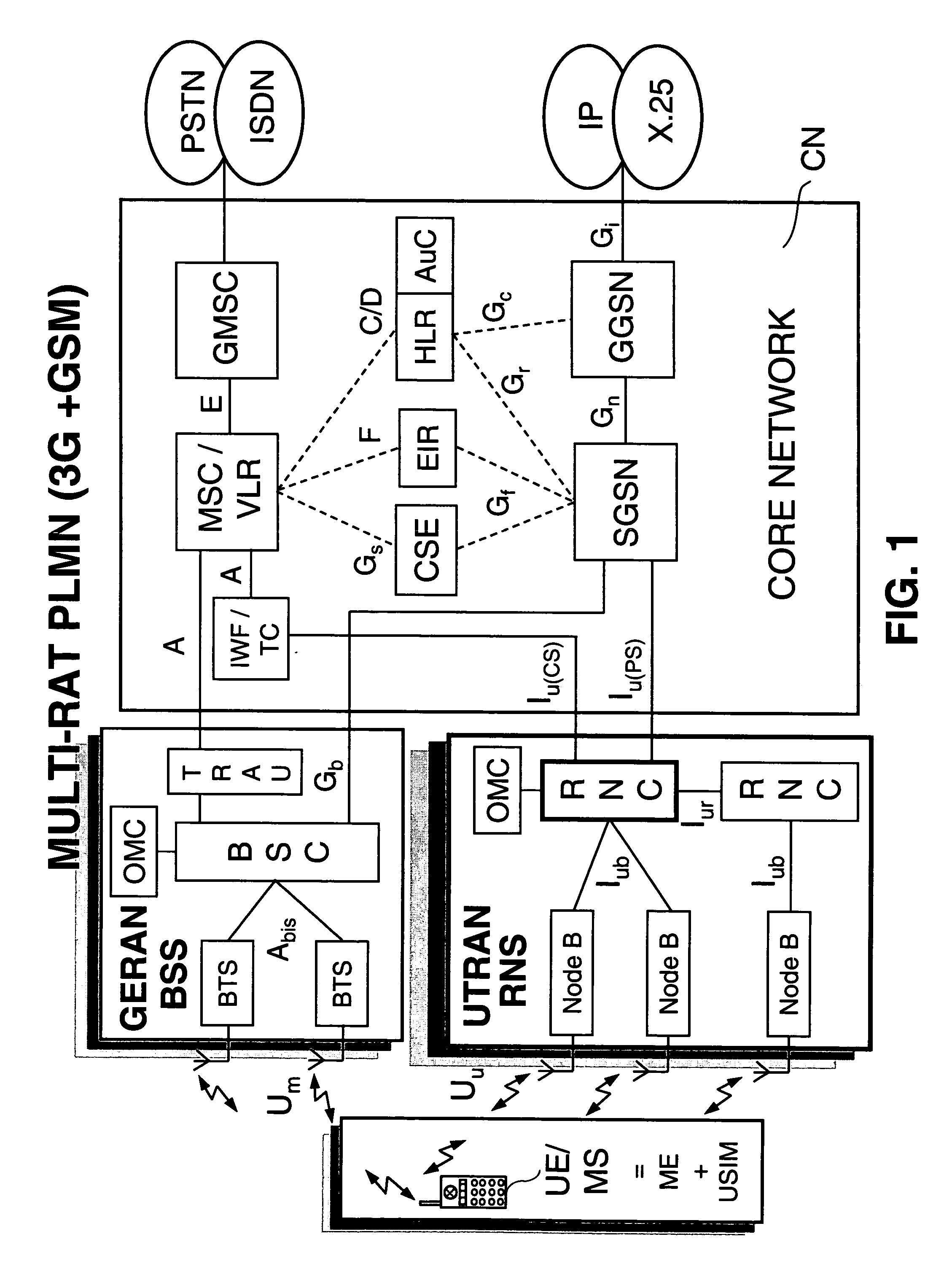
Common radio resource management method in a multi-RAT cellular telephone network
ActiveUS20050026616A1Avoid complex processAvoid problemsNetwork traffic/resource managementRadio/inductive link selection arrangementsCellular telephoneHandover
A Common radio resource management method is performed in a mobile radio communication network employing different radio access technologies that overlap over a geographic area subdivided into cells belonging to the domains of respective controllers which are connected to each other in overlapping or adjacent domains and to a core network by means of relevant interfaces. The controllers calculate new traffic-related Information Elements to be exchanged over the existing interfaces to the aim of planning handovers and / or cell reselections towards adjacent cells either of the same or different RAT. Cell capabilities and mobile terminal capabilitiess being also specified by respective IEs. Diversely from the conventional traffic-related IEs based on Cell Load parameters or Free Capacity, the new IEs include indications of the “availability” of bearer services in the cell in terms of maximum bitrate, either guaranteed or not guaranteed, that can currently be allowed to each bearer service.
Owner:RPX CORP +1
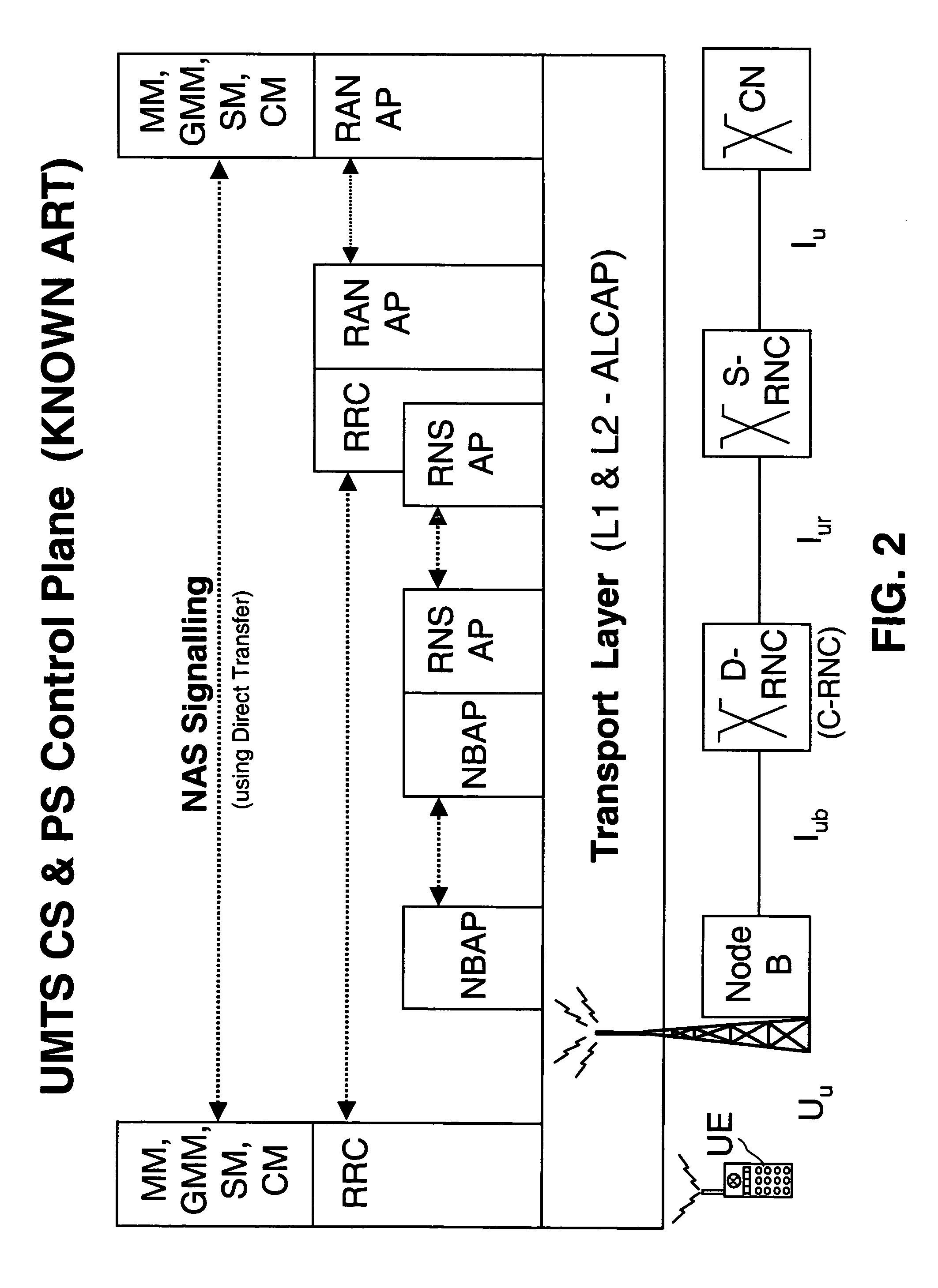
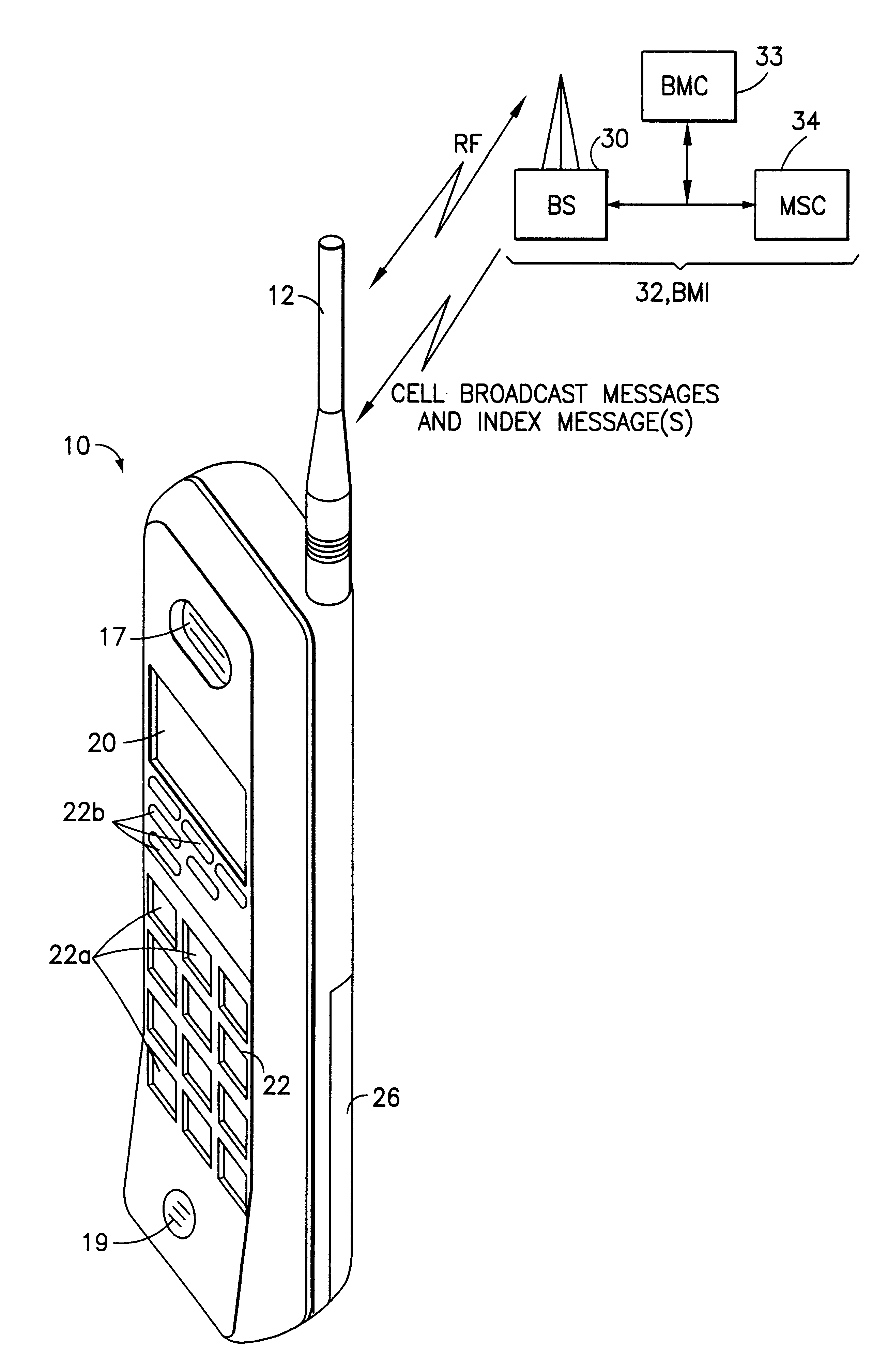
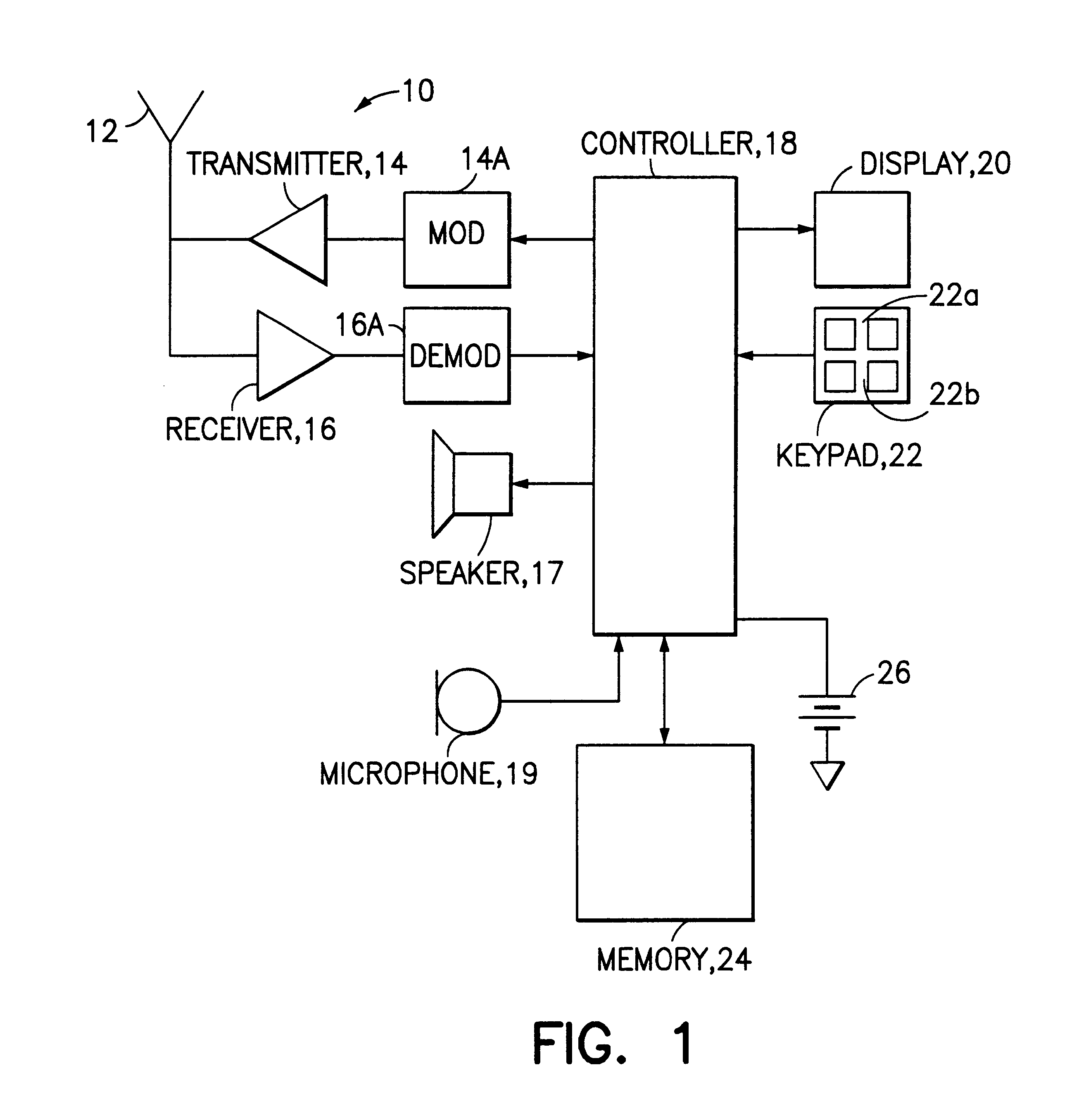
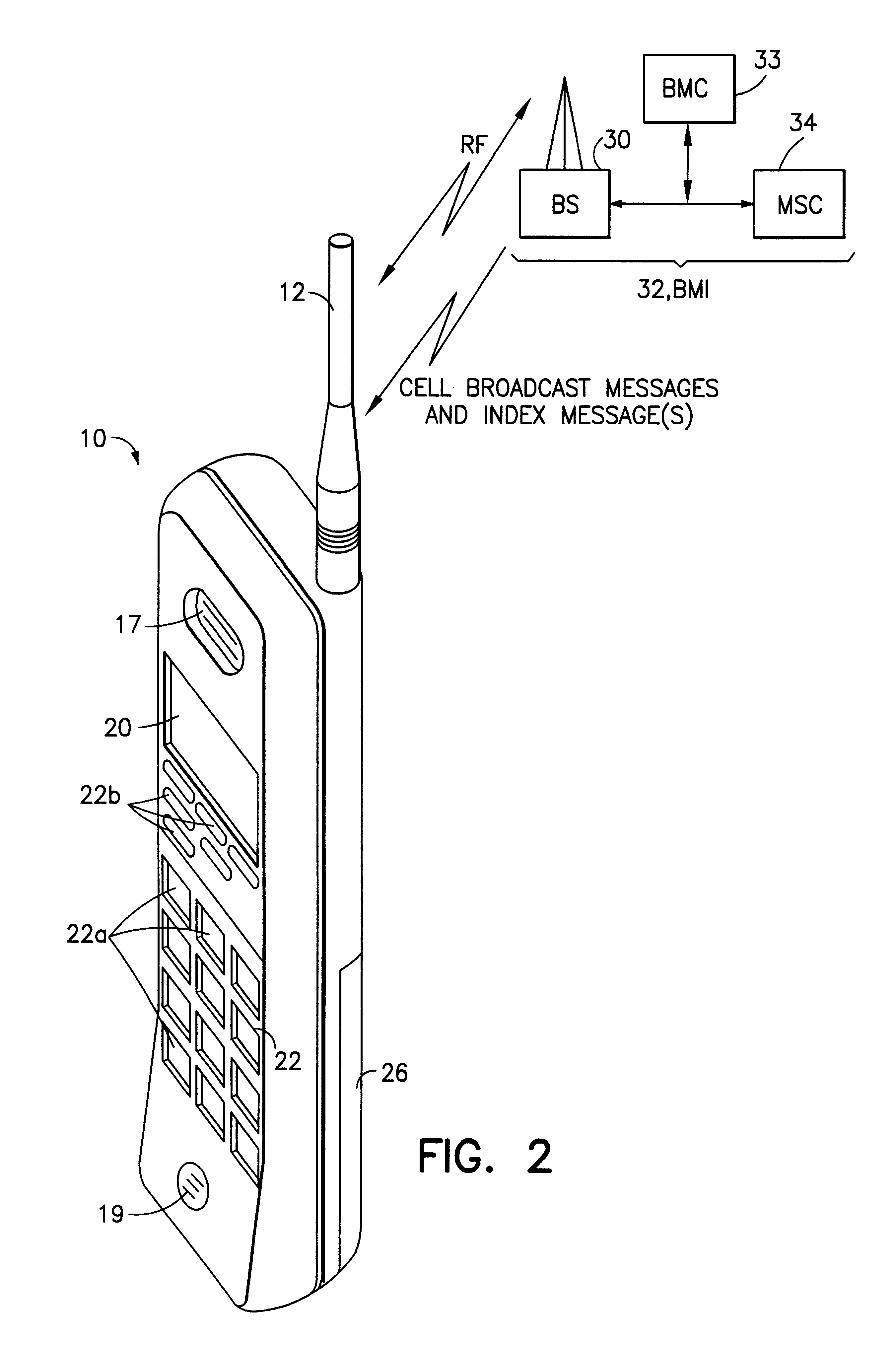
Mobile station and network having hierarchical index for cell broadcast service
InactiveUS6201974B1Easy to useEmergency connection handlingTime-division multiplexBroadcast domainMobile station
This invention provides for the use of an index message in a Cell Broadcast Service. An index message is considered to be a special type of Cell Broadcast message which contains general information about actual broadcast messages. The index message is transmitted in a predetermined logical S-BCCH subchannel, and contains information elements such as (a) message overviews or summaries for each cell broadcast message, (b) information concerning emergency messages, (c) information concerning the language used in different broadcast messages, (d) an alphanumeric broadcast domain operator name and a specific operator greeting, (e) information concerning changes in broadcast messages, and (f) information concerning subchannels.
Owner:NOKIA TECHNOLOGLES OY
Post production visual alterations
InactiveUS7444659B2Simple and easy mannerTelevision system detailsColor signal processing circuitsPersonalizationVisual alteration
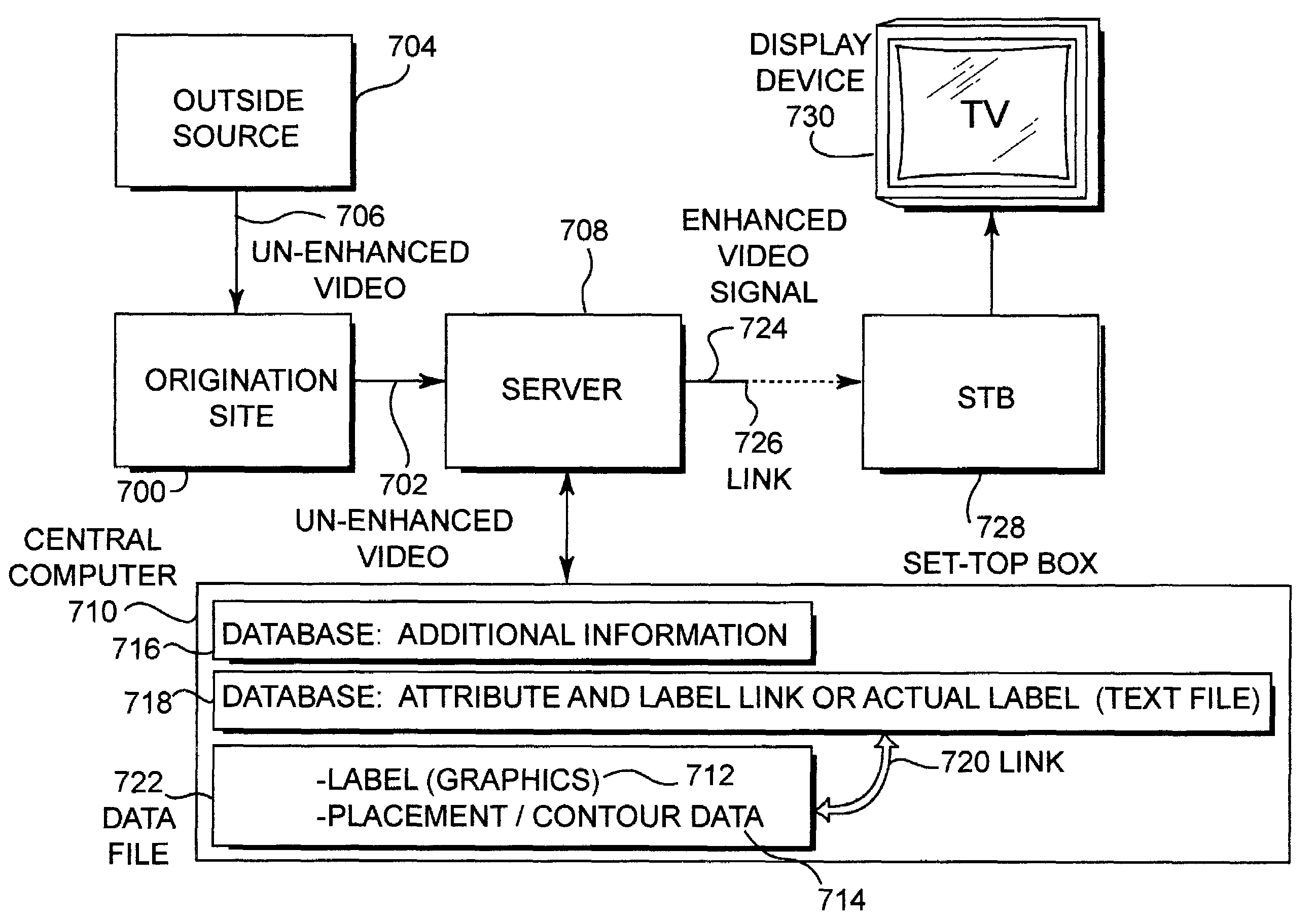
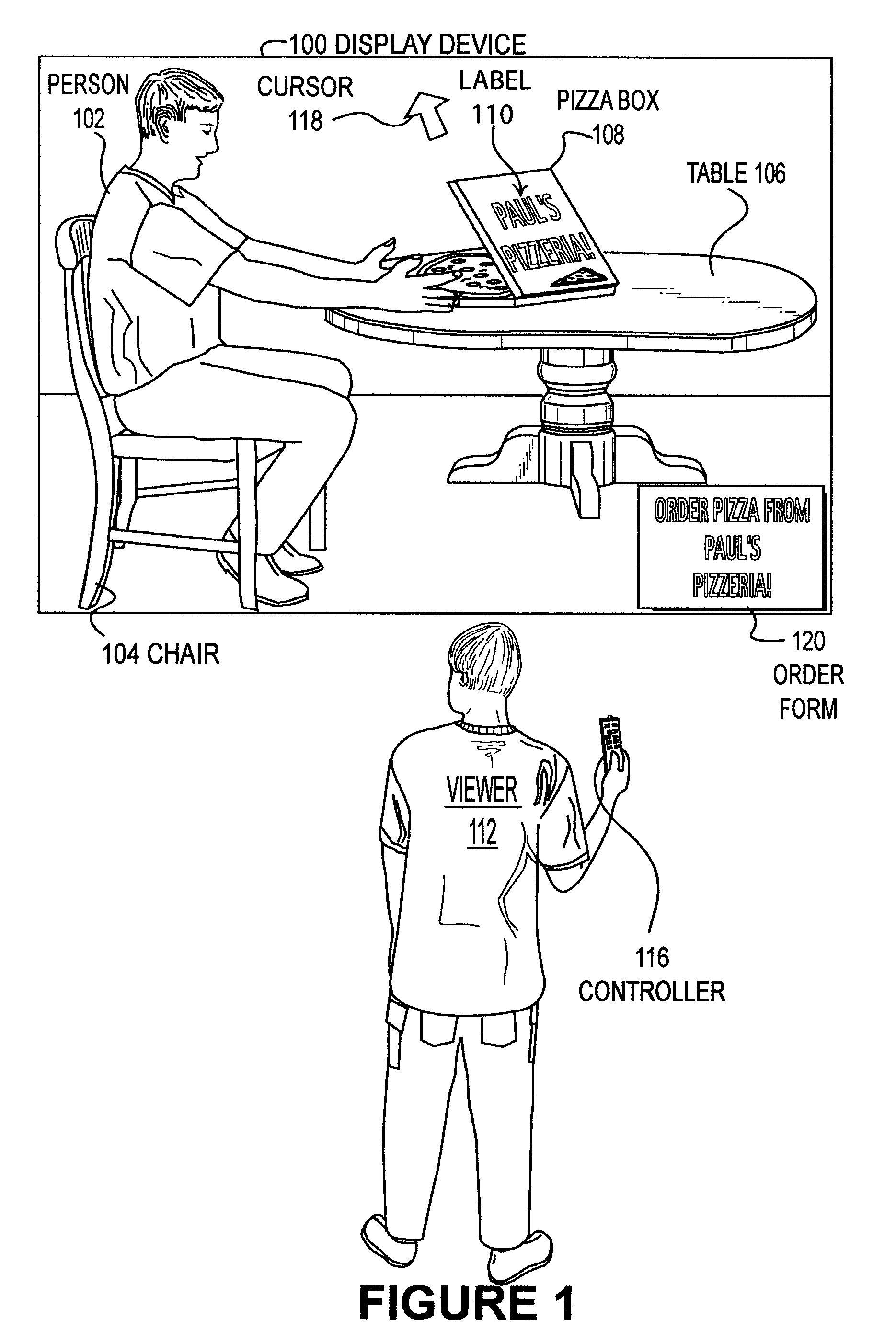
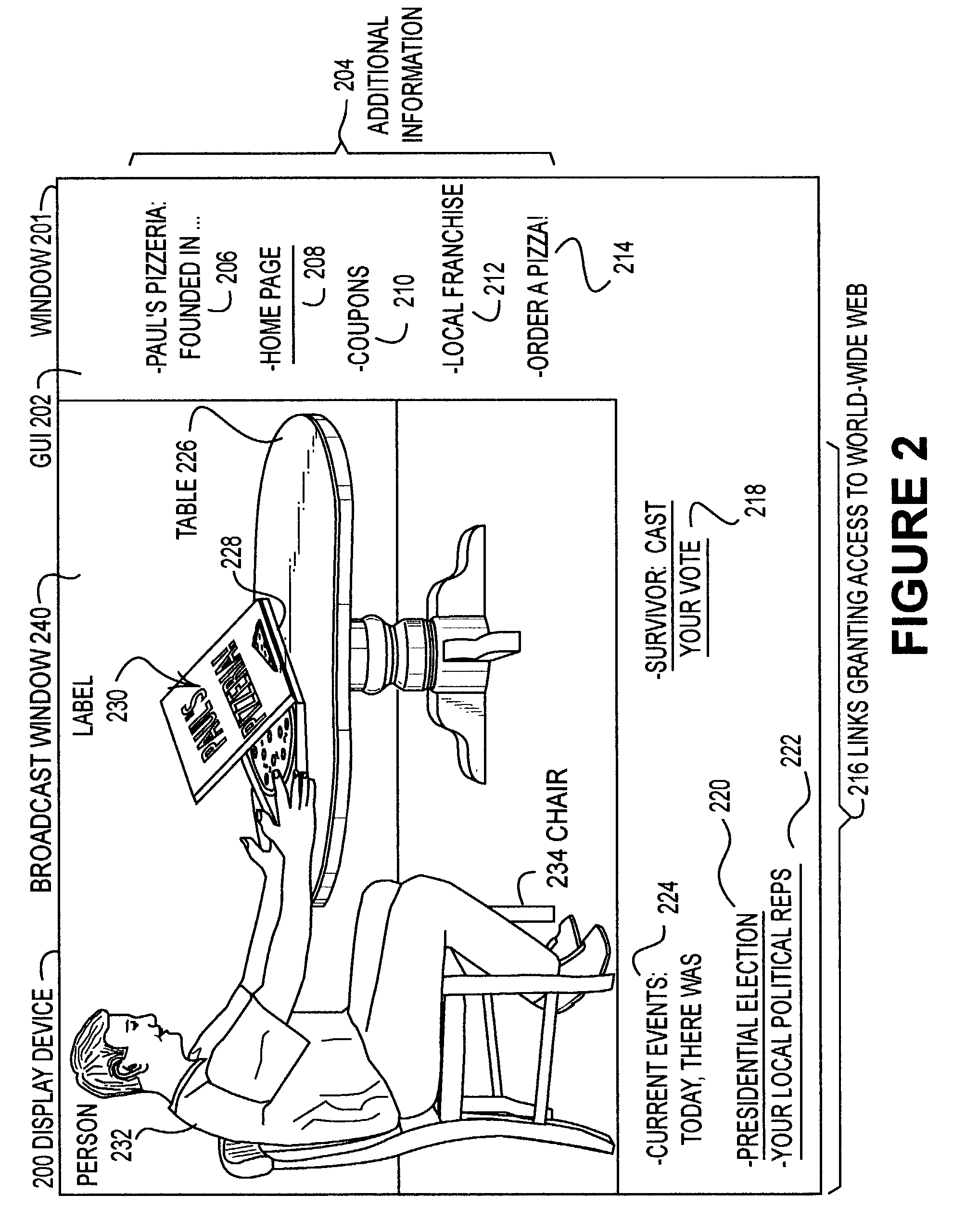
Disclosed is a method and system in which “labels,” comprising supplemental information such as advertising, promotional, or informational elements including interactive elements, may be superimposed post-production into a video stream. This can be done by using overlay screens including interactive overlay screens or by combining video segments. As such, the labels do not have to physically be part of the actual scene during filming. Once a video stream is created, a space for available advertising is designated either manually or automatically by pattern recognition techniques. A list of available advertising space is generated. During viewing of television broadcasts, advertisements are placed in the video signal. Labels are displayed by superimposing an HTML page that is blank except for the advertisement onto the video signal. Advertisements can be superimposed post-production, and can be personalized and localized. The advertisements can be customized on a per-household basis.
Owner:OPEN TV INC
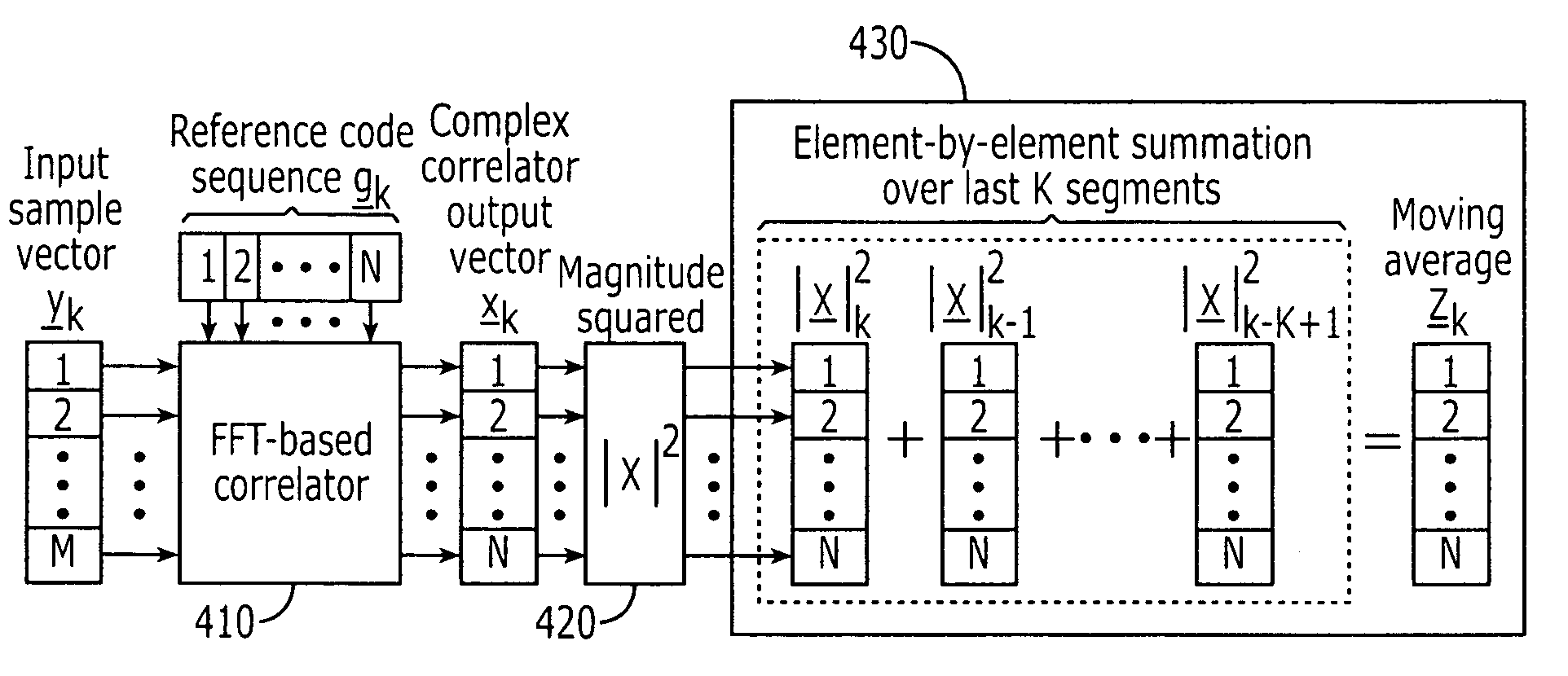
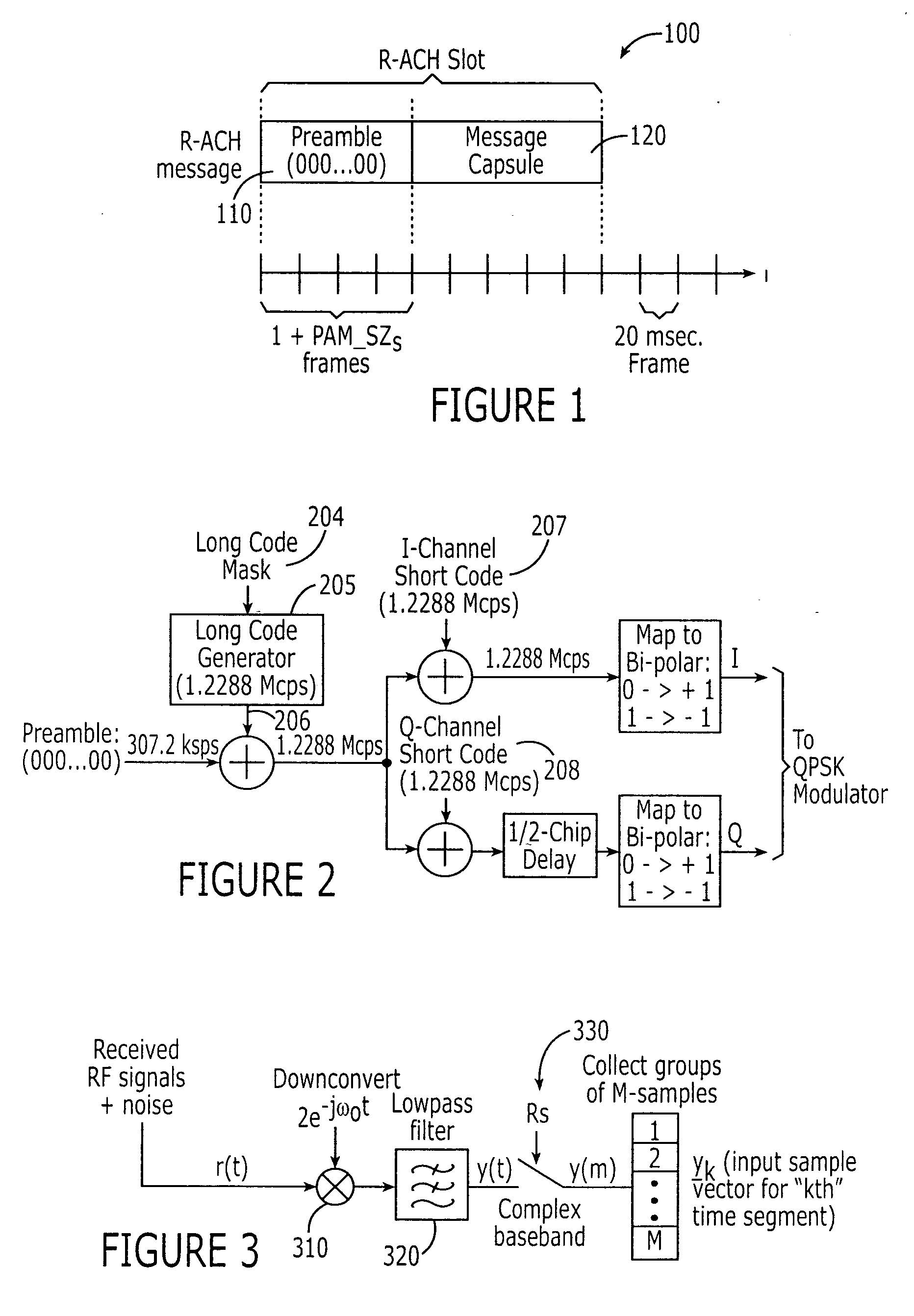
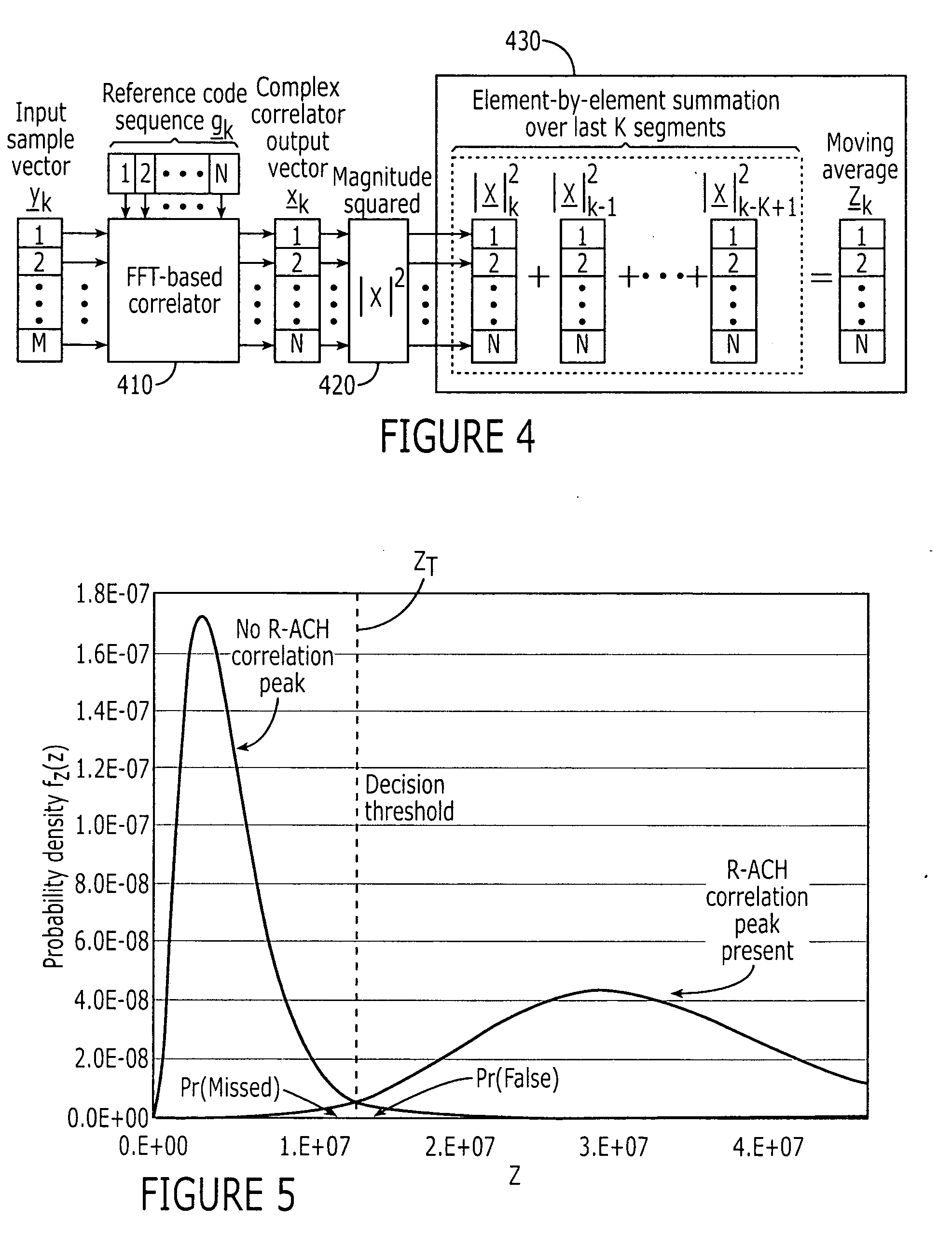
Code synchronization in CDMA satellite wireless communications system using uplink channel detection
ActiveUS20050201449A1Time-division multiplexRadio transmission for post communicationCommunications systemTime shifting
An uplink signal transmitted by a terminal is received by a satellite wireless communications system. The uplink signal includes a known information element, e.g., a reverse access channel (R-ACH) preamble, spread according to a spreading code specific to a component of a satellite wireless communications system, e.g., a pseudonoise (PN) sequence associated with a satellite beam. A correlation of the received uplink signal with the spreading code over a range of time shifts is determined. The known information element is detected from the determined correlation. The satellite wireless communications system is synchronized with the terminal responsive to detection of the known information element. For example, a delay may be assigned to a receiver of the satellite wireless communications system responsive to detection of the known information element.
Owner:MOBILE SATELLITE VENTURES LP
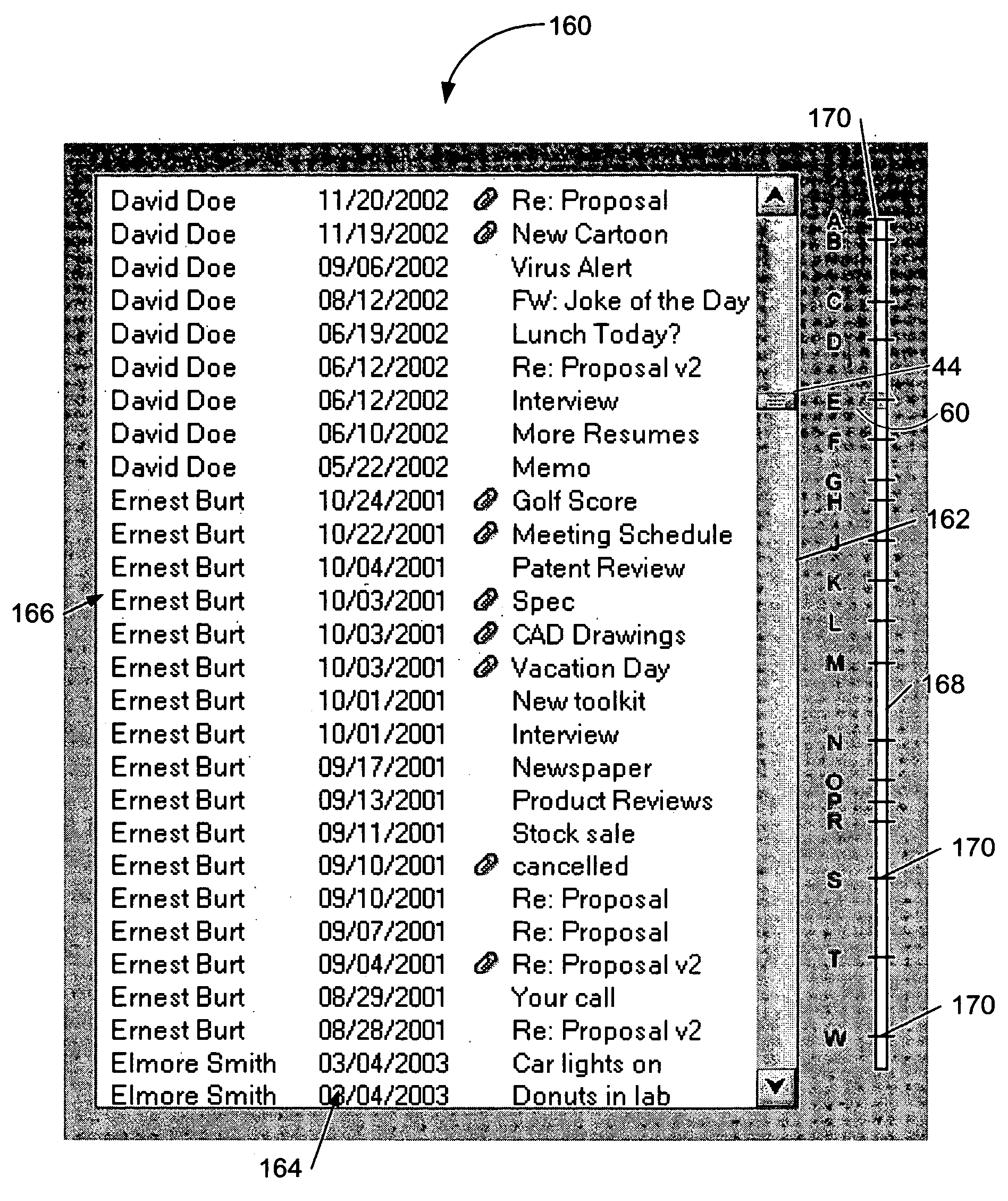
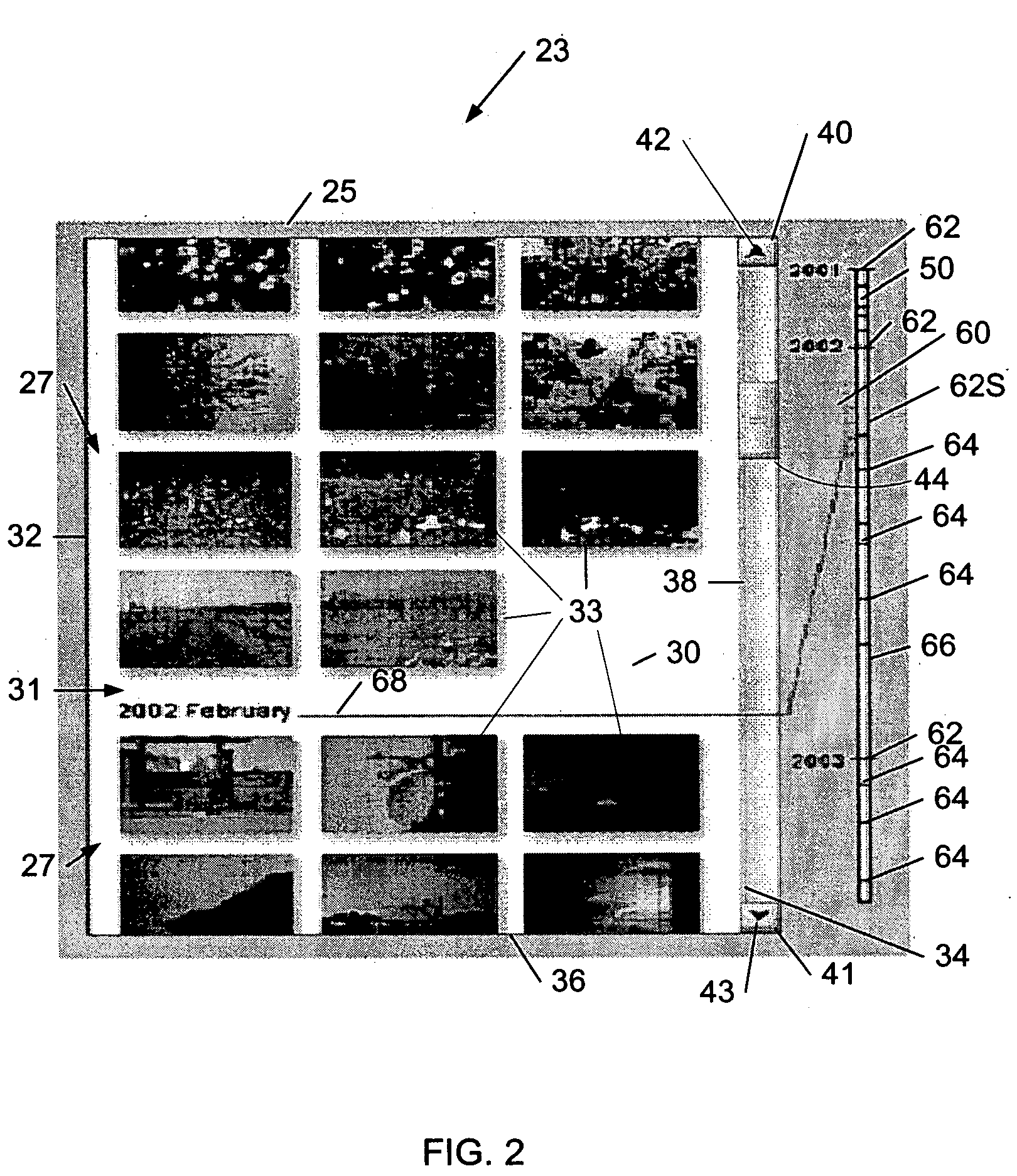
Scrollbar enhancement for browsing data
InactiveUS20050210403A1Not satisfactoryInput/output processes for data processingGraphicsGraphical user interface
A graphical user interface for browsing information displayed to a user. The information displayed includes zero or more elements and may be displayed in a display window. The display window has a perimeter and a scrollbar is positioned along the perimeter. The scrollbar may have a first end and a second end and a slider located between the ends. The slider may be configured such that movement of the slider causes information in the display area to be scrolled. In one embodiment, the size of the slider is based on the size of the one more elements of information displayed in the display window. A data-line may be positioned adjacent the scrollbar and may have a plurality of tick marks. A graphical element, which may be displayed in phantom, may be used to associate the slider to the data-line.
Owner:LEXMARK INT INC
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
System and method
ActiveUS20110004513A1Discounts/incentivesApparatus for meter-controlled dispensingDependabilityData mining
A system and method providing for communication and resolution of utility functions between participants, wherein the utility function is evaluated based on local information at the recipient to determine a cost value thereof. A user interface having express representation of both information elements, and associated reliability of the information. An automated system for optimally conveying information based on relevance and reliability.
Owner:HOFFBERG FAMILY TRUST 2
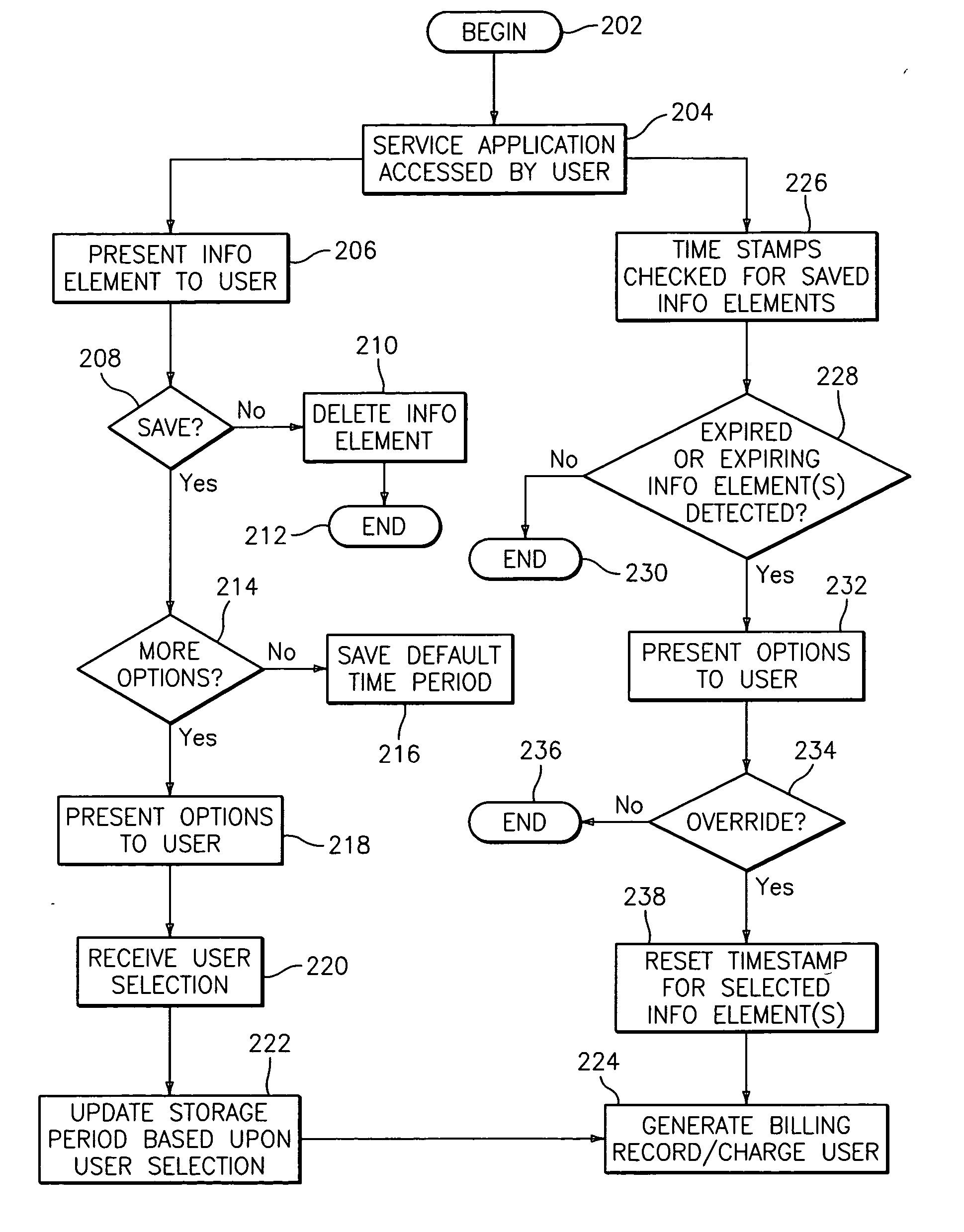
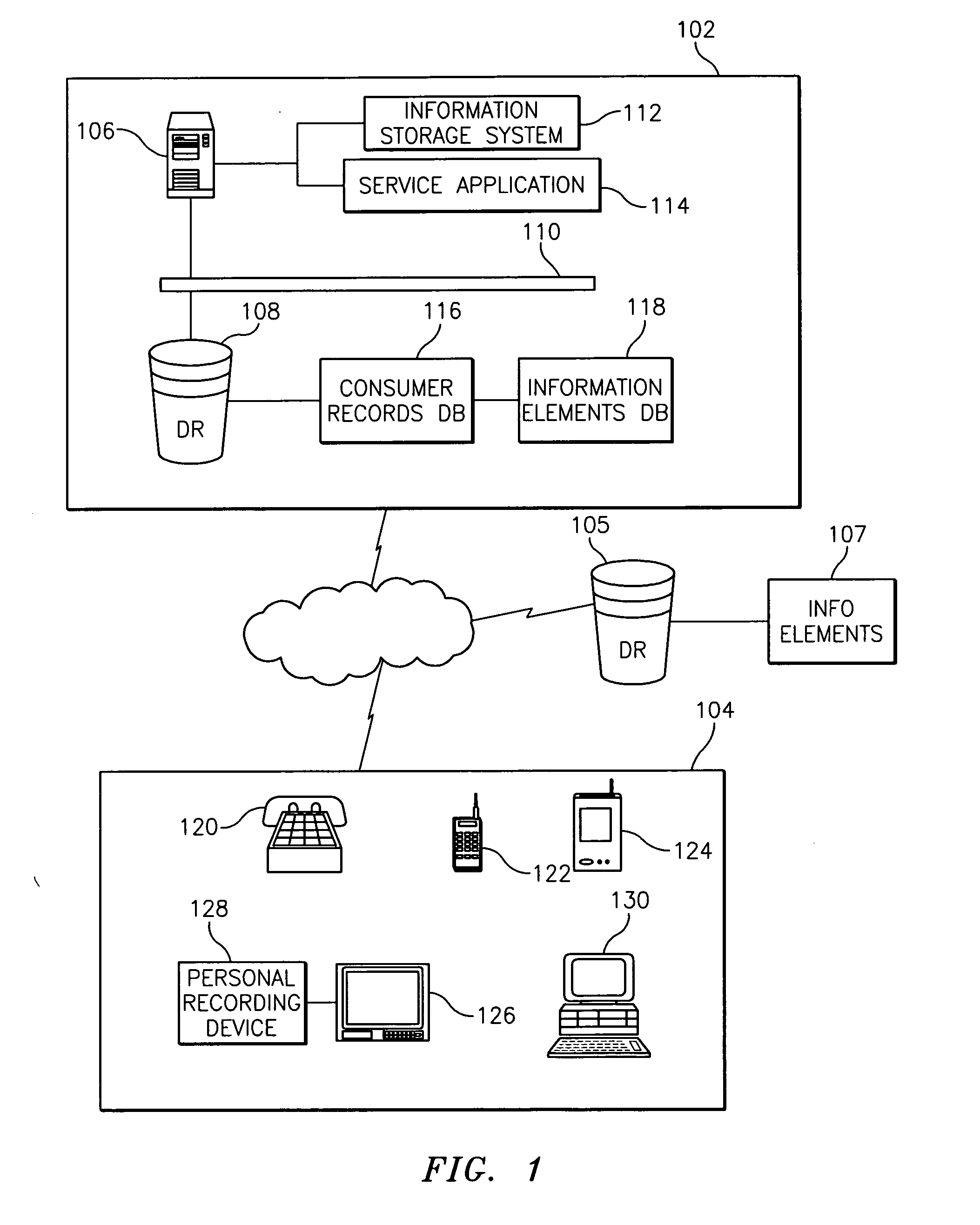
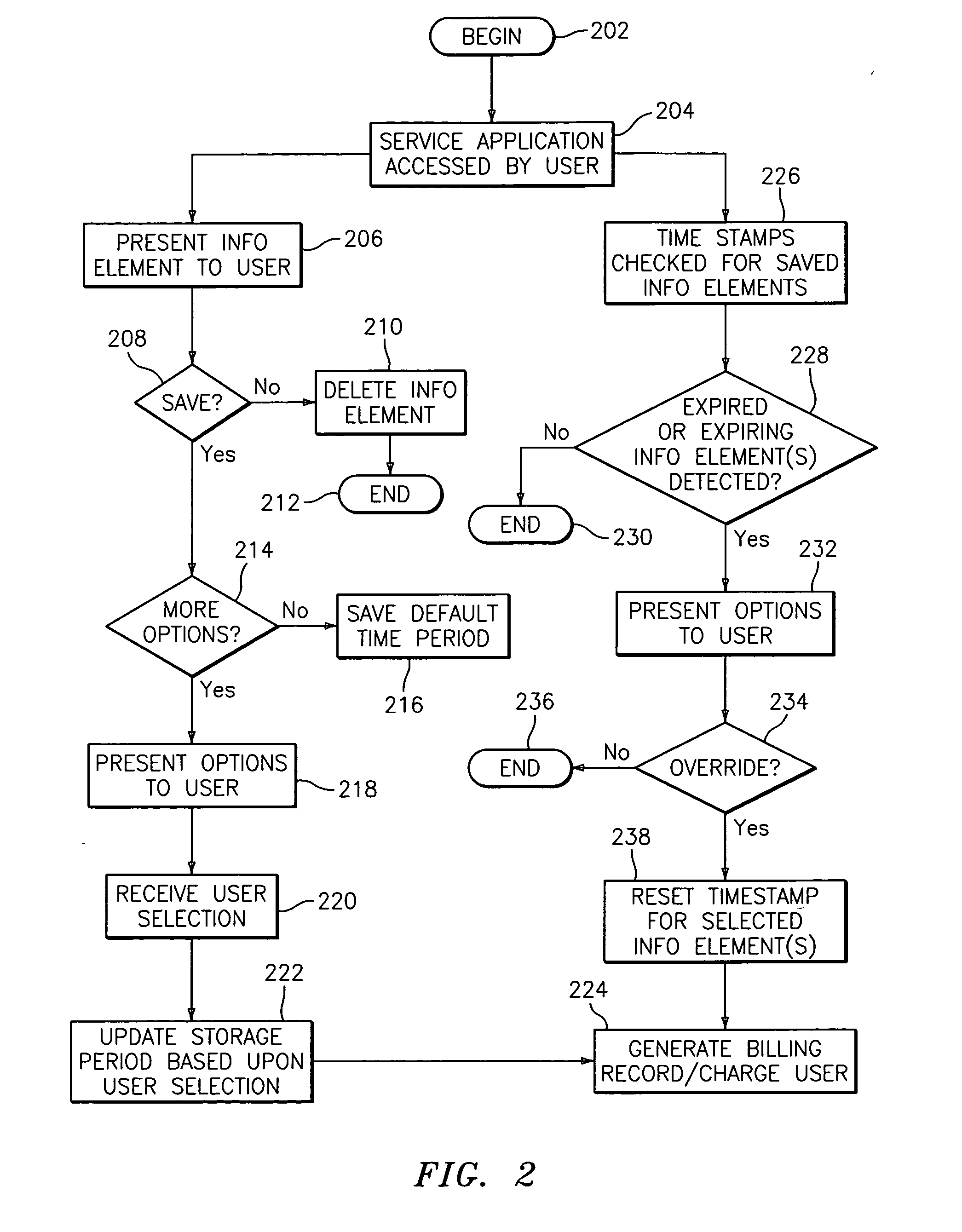
Methods, systems, and storage mediums for providing information storage services
InactiveUS20050138305A1Automatic exchangesMessaging/mailboxes/announcementsService provisionWorld Wide Web
Embodiments relate to a method, system, and storage medium for providing information storage services to a service application user via a service provider. The method includes presenting options to the service application user operable for specifying a duration of time for storing an information element at a remote location. The method further includes receiving a selection from the service application user in response to options presented and assigning a storage period to the information element based upon the selection. Embodiments also include a system and a storage medium.
Owner:BELLSOUTH INTPROP COR
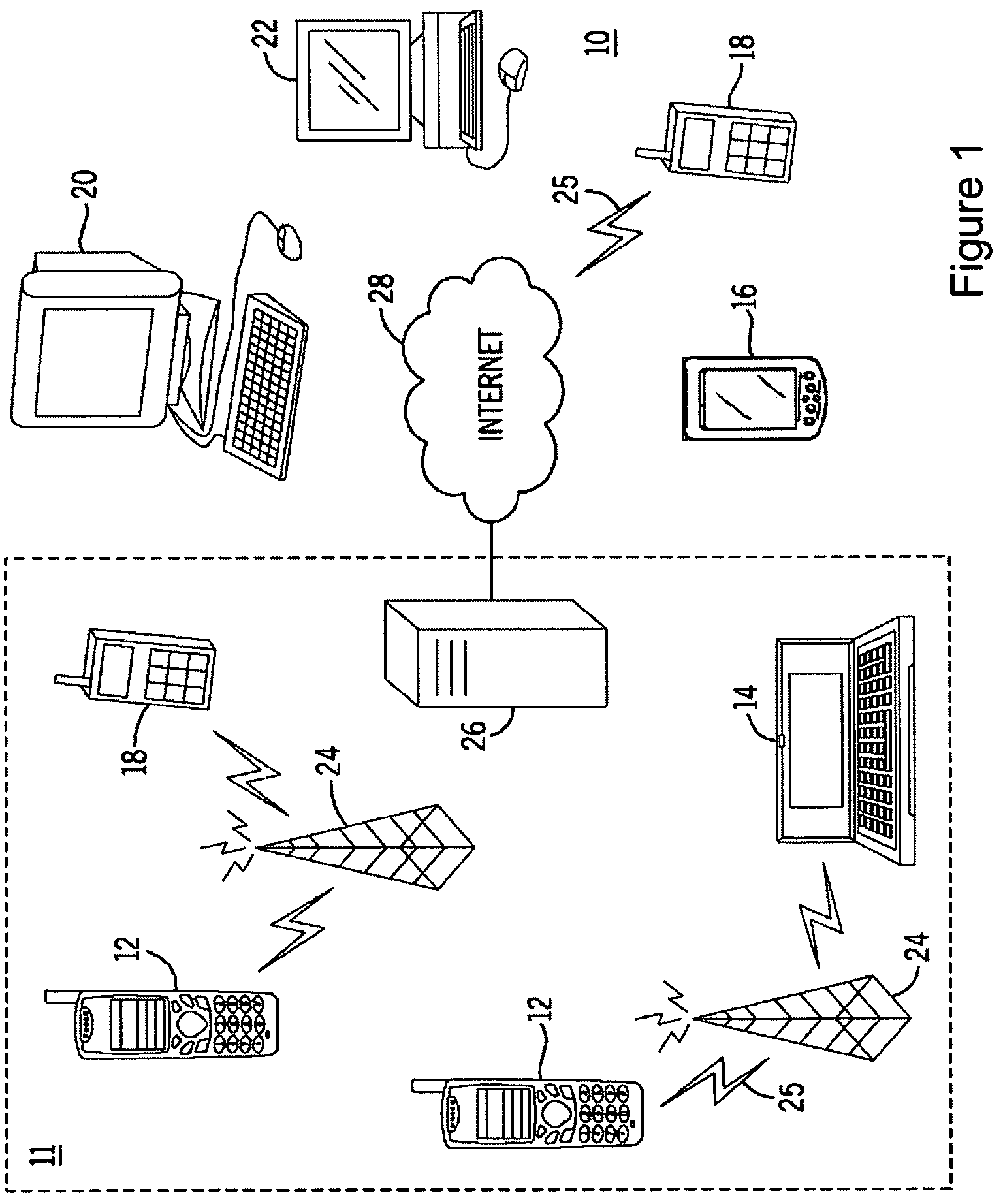
Method providing positioning and navigation inside large buildings
ActiveUS20100008337A1Particular environment based servicesNetwork topologiesNative QueriesMedia access control
Positioning and / or navigation of an electronic device within a building when GPS signals are unavailable is provided. The electronic device scans for available Wireless Local Area Network (WLAN) Access Points (APs) upon, e.g., entering a building. The electronic device detects a signal (e.g., beacon) from at least one available WLAN AP, whereupon the electronic device retrieves the indoor location of the available WLAN AP. The location information can be directly downloaded from the WLAN AP while in state-1 via, e.g., a Native Query Protocol which includes an extension to currently defined Native Query info elements that returns location information. Alternatively, the Media Access Control (MAC) address of the WLAN AP can be read from the beacon signal, which is then used to retrieve the location of the WLAN AP from an associated database. Additionally, various embodiments may be implemented with or via a mapping application or service, where the mapping application is able to display any floor's floor plan of a building and determine / obtain the position of the electronic device inside the building relative to the floor plan.
Owner:NOKIA TECHNOLOGLES OY
Method and apparatus for redirection of server external hyper-link references
InactiveUS6859833B2Minimum delayMinimum visibility of the redirection protocolMetering/charging/biilling arrangementsAdvertisementsGraphicsHyperlink
A message is provided to a tracking server system in response to a client system referencing a predetermined resource locator that corresponds to a resource external to the tracking server system. The tracking server system indirectly provides for the client system to have an informational element selectable by the client system, where the informational element is graphically identified on the client system with informational content obtainable from a content server system through use of a content resource locator. The informational element includes a tracking resource locator, referencing the tracking server system, and data identifying the informational element. The selection of the informational element causes the client system to use the tracking resource locator to provide the data to the tracking server system and to use the content resource locator to obtain the informational content from the content server system.
Owner:DISNEY ENTERPRISES INC
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
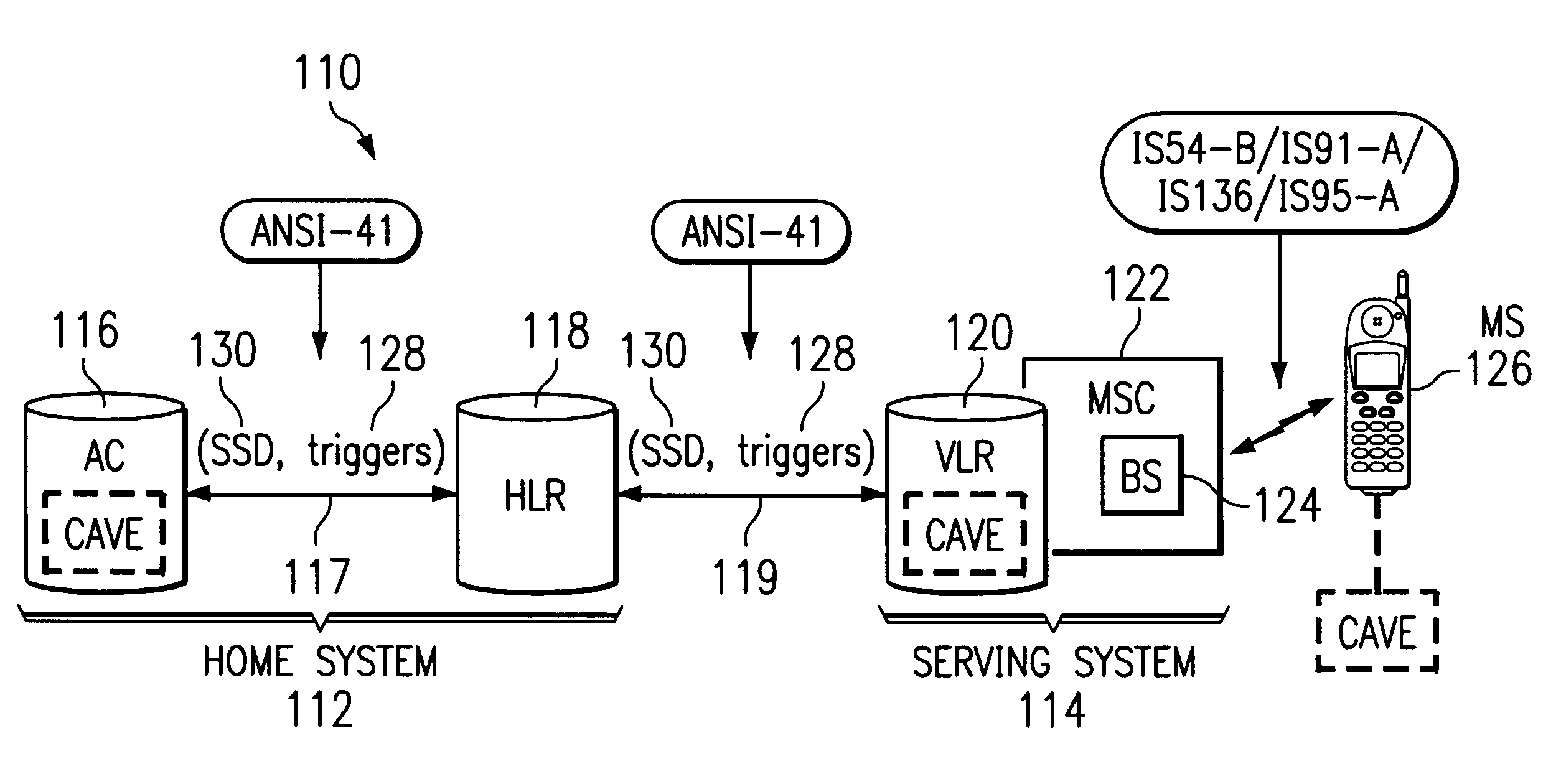
Authentication failure trigger method and apparatus
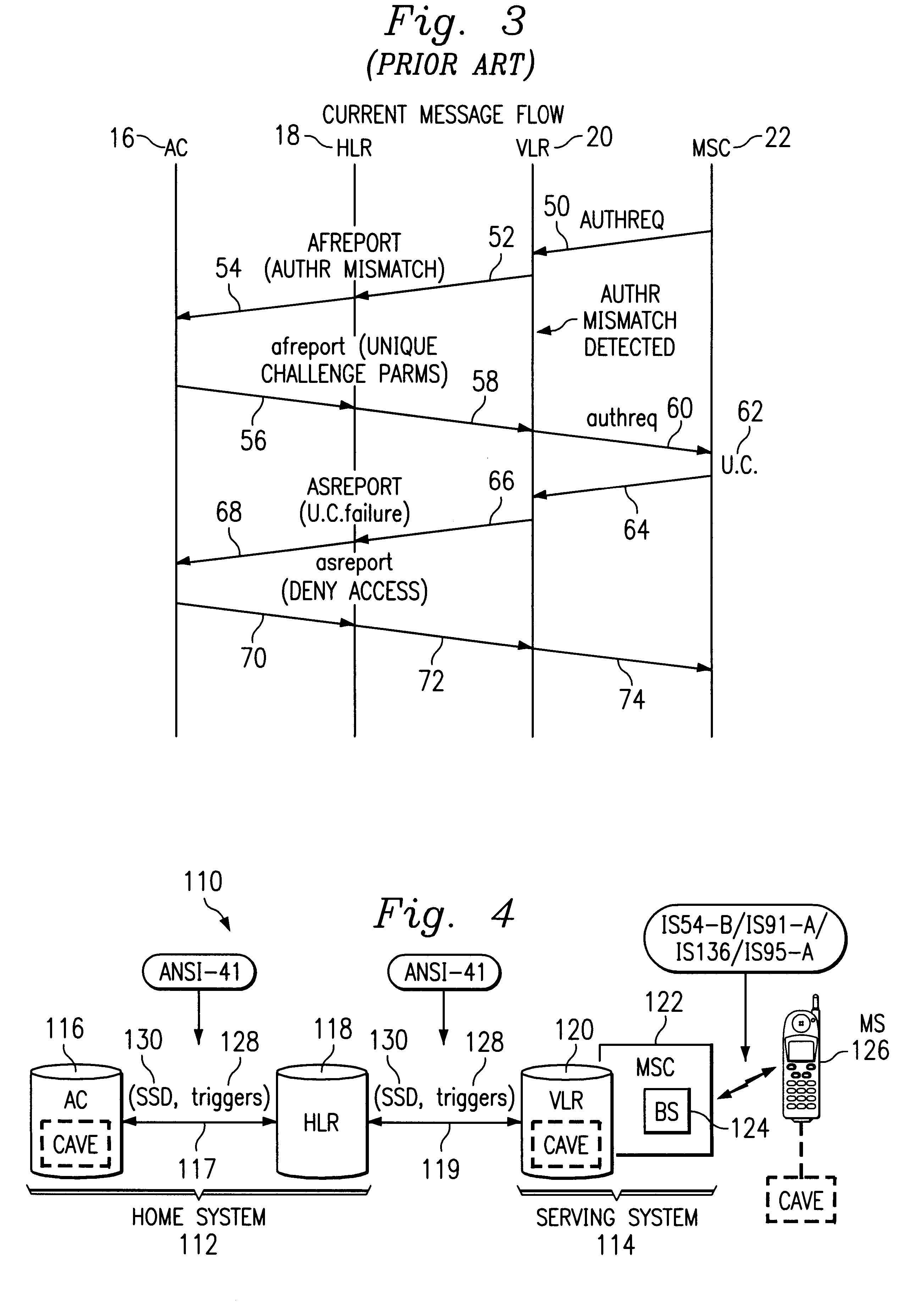
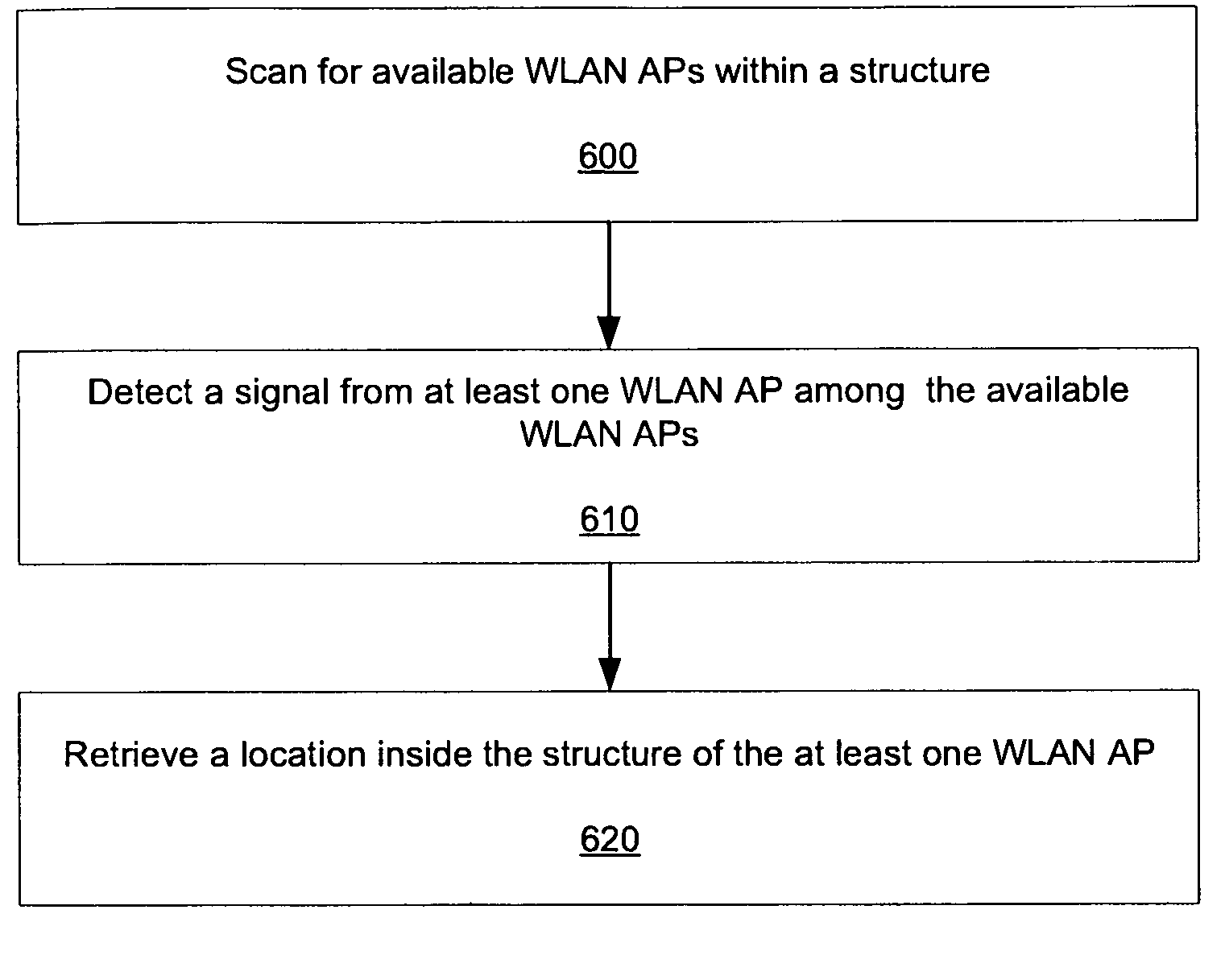
InactiveUS6236852B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile stationService system
A wireless communications network and method include a home system, a serving system, and authentication failure triggers. The home system includes an authentication center, a network information element, and a prescribed authentication capable mobile station. The authentication center performs an authentication of the prescribed mobile station upon a network access by the mobile station. Authentication includes use of shared secret data particular to the prescribed mobile station. The serving system includes a network access element and a network information element associated therewith. The serving system is capable of performing authentication upon authentication capable mobile stations. Lastly, the authentication failure triggers and shared secret data are shared with the serving system by the authentication center of the home system upon the mobile station's initial system access. The authentication failure triggers include instructions for use by the serving system with respect to authentication failures which may occur during a subsequent serving system access. The authentication triggers direct the serving system to handle authentication failures according to the authentication policies of the home system's authentication center. Therefore, the requirement for the authentication failure report operation is advantageously reduced.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method providing positioning and navigation inside large buildings
Owner:NOKIA TECH OY
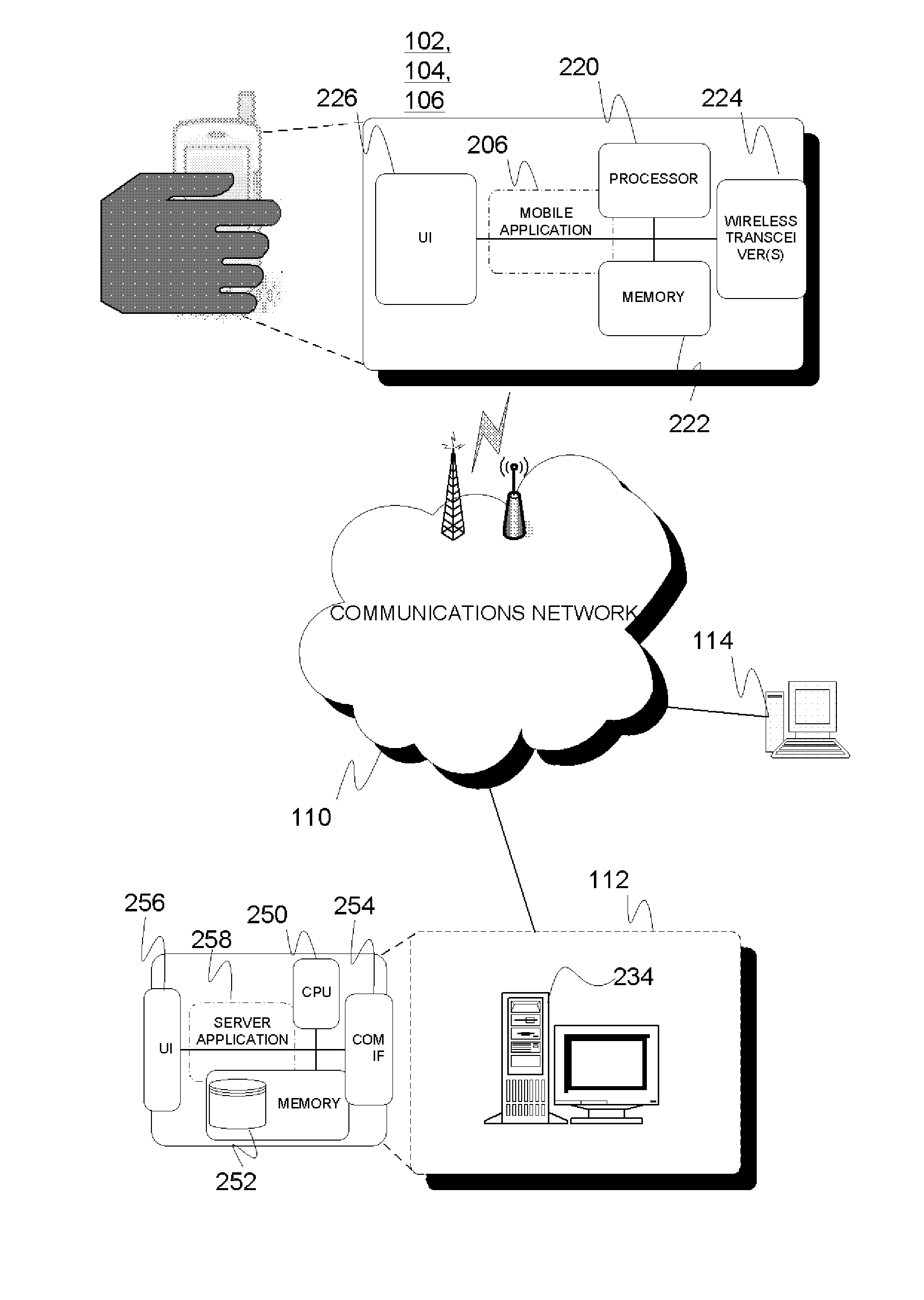
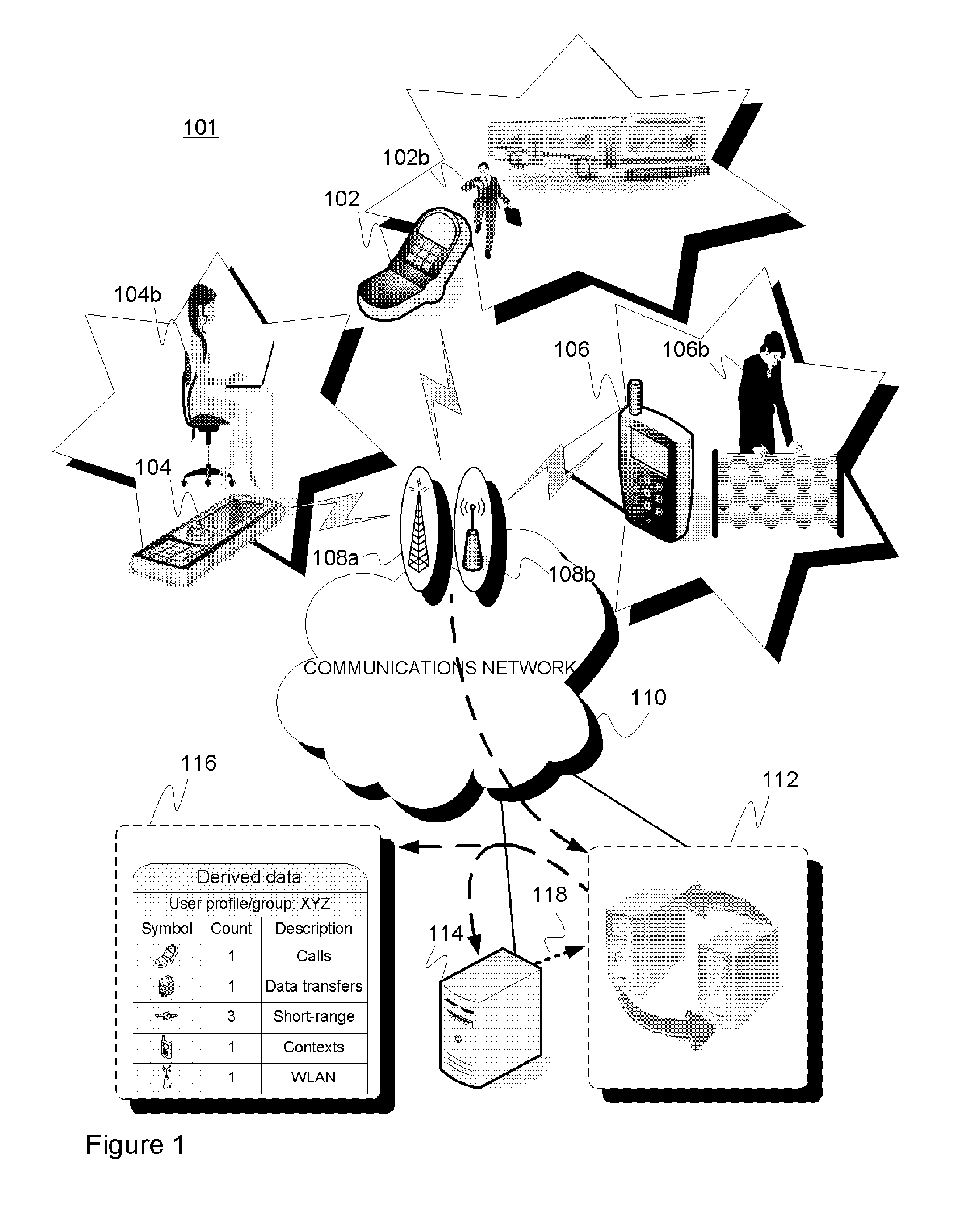
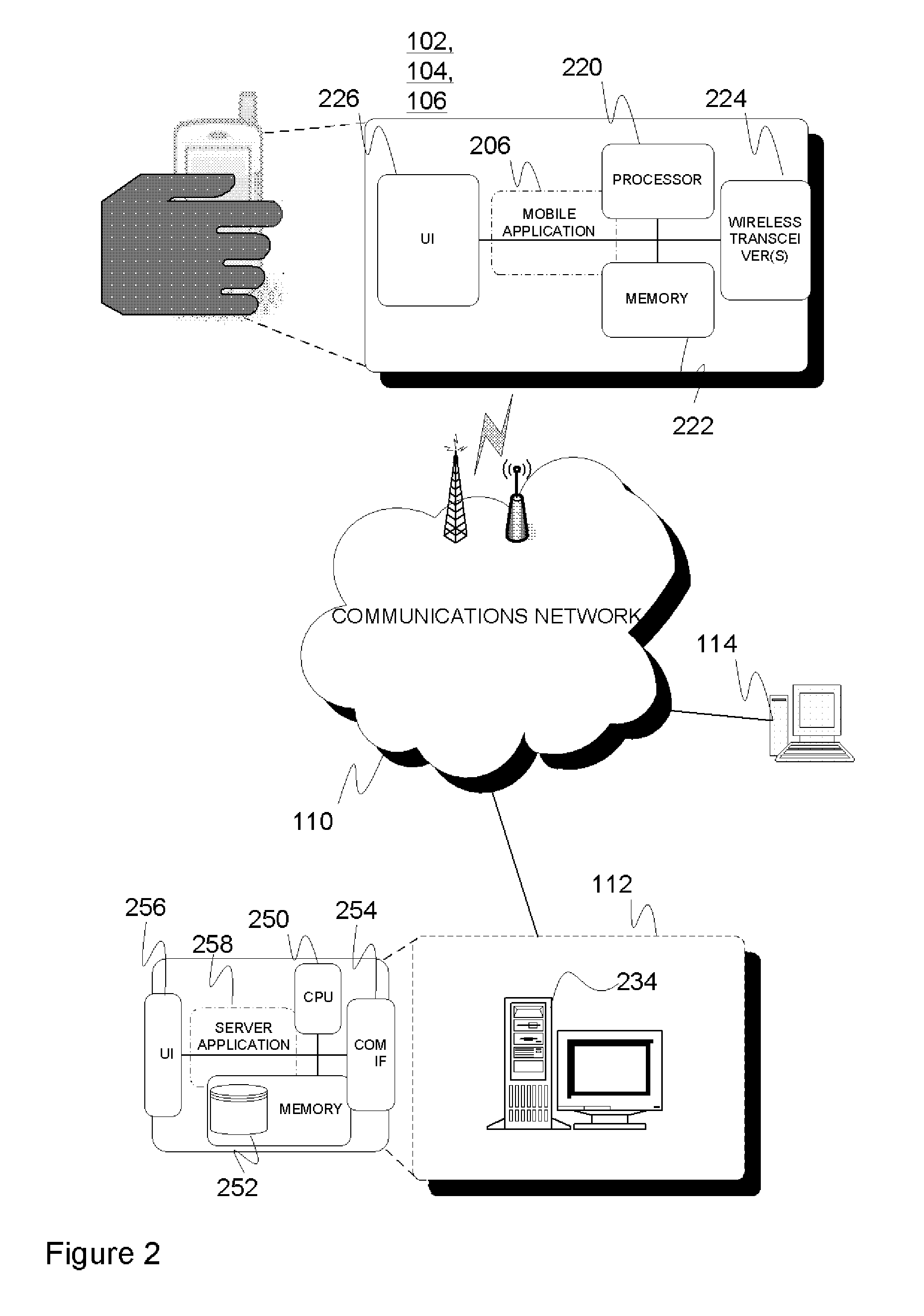
System and method for behavioural and contextual data analytics
ActiveUS20110264663A1Easy to customizeUseful for promotionDigital data processing detailsVisual data miningData packContext data
A server arrangement for managing observation data of wireless devices, including data input logic for obtaining observation data from wireless devices, the obtained data including behavioral and contextual raw data relative to the wireless devices, data mining logic for establishing a number of derived data elements, on the basis of processing and analyzing the obtained observation and optional supplementary data, the processing and analyzing incorporating aggregation procedures. At least one derived data element includes usage metrics with contextual dimension relative to applications or other features of wireless devices and users, data storage for storing the obtained data and the number of derived information elements, and a data distribution logic providing derived data. The distribution logic may serve a data query constructed by an external entity through provision of derived information from derived data elements according to the query parameters. A corresponding method for execution by the server arrangement is presented.
Owner:THE NIELSEN CO (US) LLC
Method for supporting various multi-antenna schemes in BWA system using multiple antennas
Disclosed is a method for using various multiple antenna schemes in a baseband wireless access system is provided. According to the method, a downlink MAP message is constructed in order to support various multiple antenna schemes based on a multiple-input multiple output (MIMO), which is one of the multiple antenna schemes, so that compatibility with exiting MIMO technology having no MIMO feedback can be achieved and overhead occurring in transmission of an MAP information element can be reduced. Further, it is possible to efficiently support spatial multiplexing technology capable of transmitting multiple layers having different modulation and coding in a MIMO system.
Owner:SAMSUNG ELECTRONICS CO LTD
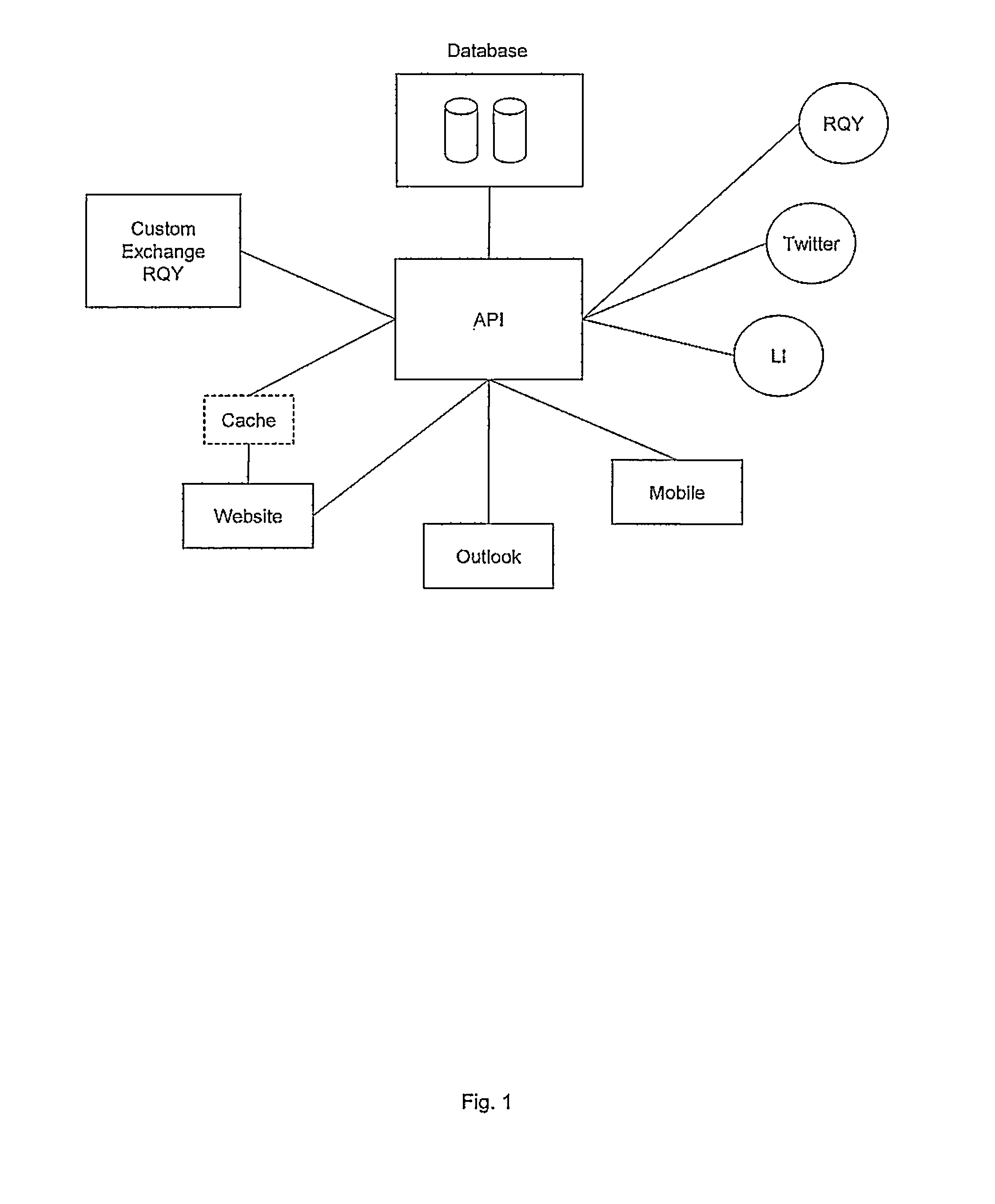
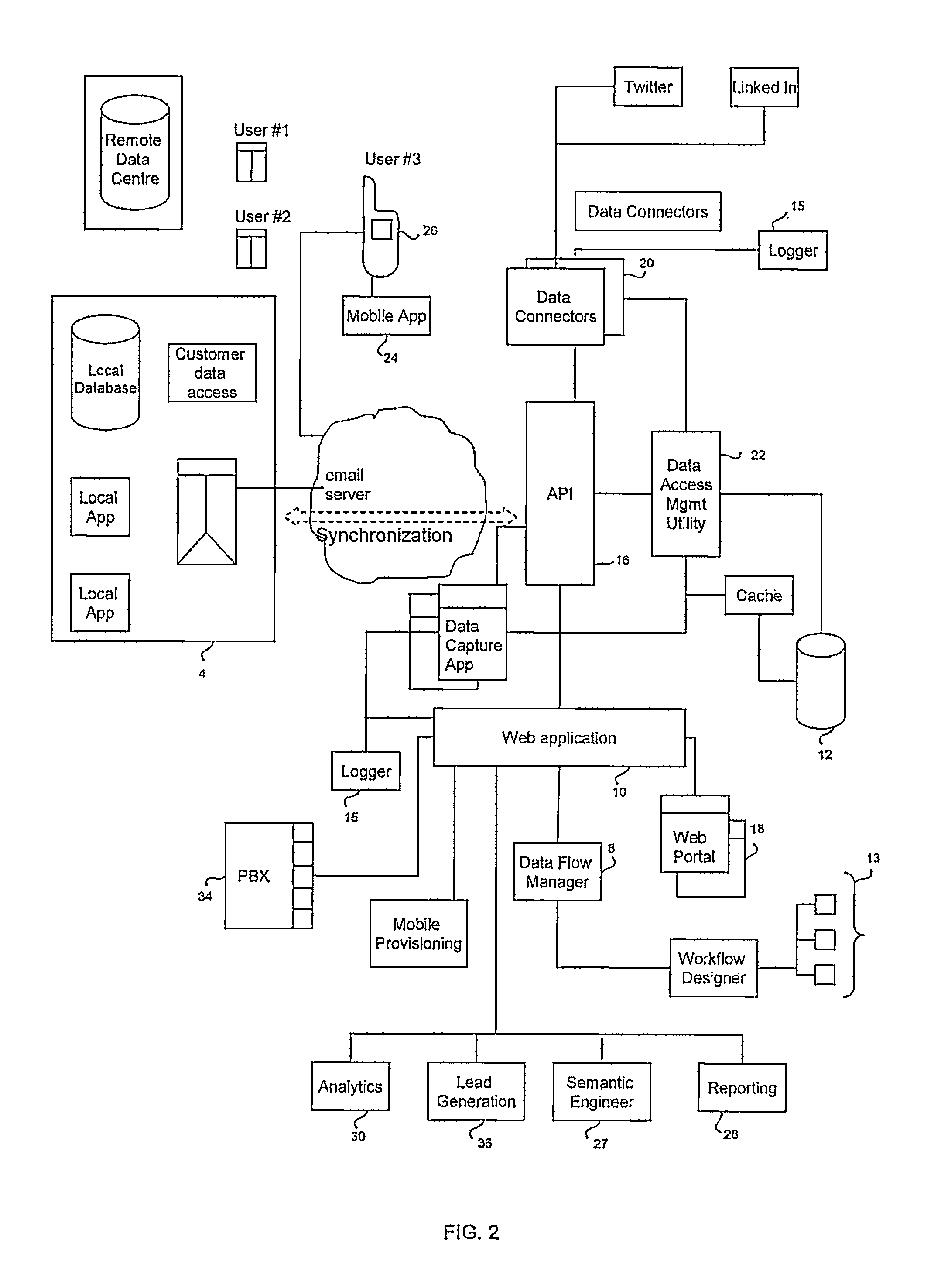
System and method for providing unified workflows integrating multiple computer network resources
A computer network implemented system is provided comprising a workflow designer that is operable to enable the design of one or more workflows that utilize information or functions from one or more (i) business systems, (ii) applications, or (iii) databases; and an application programming interface (API) that is configured to connect to the (i) business systems, (ii) applications or (iii) databases so as to monitor user actions, and based on such user interactions applying one or more workflow overlays that incorporate one or more intelligent features for enhancing functions of the business systems and the applications. A related computer implemented method is also provided. A computer network service is also provided that acquires information relevant to sales processes and processes the information to generate insights for improving sales performance. A sales forecasting utility is provided that applies data analysis operations to information elements relevant to a sales process. Insights may be presented to a sales representative on a real time or near real time basis so as to guide sales related activities.
Owner:SALESCHOICE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com