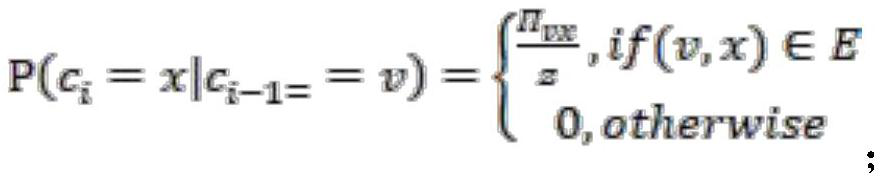Patents
Literature
133 results about "Session layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
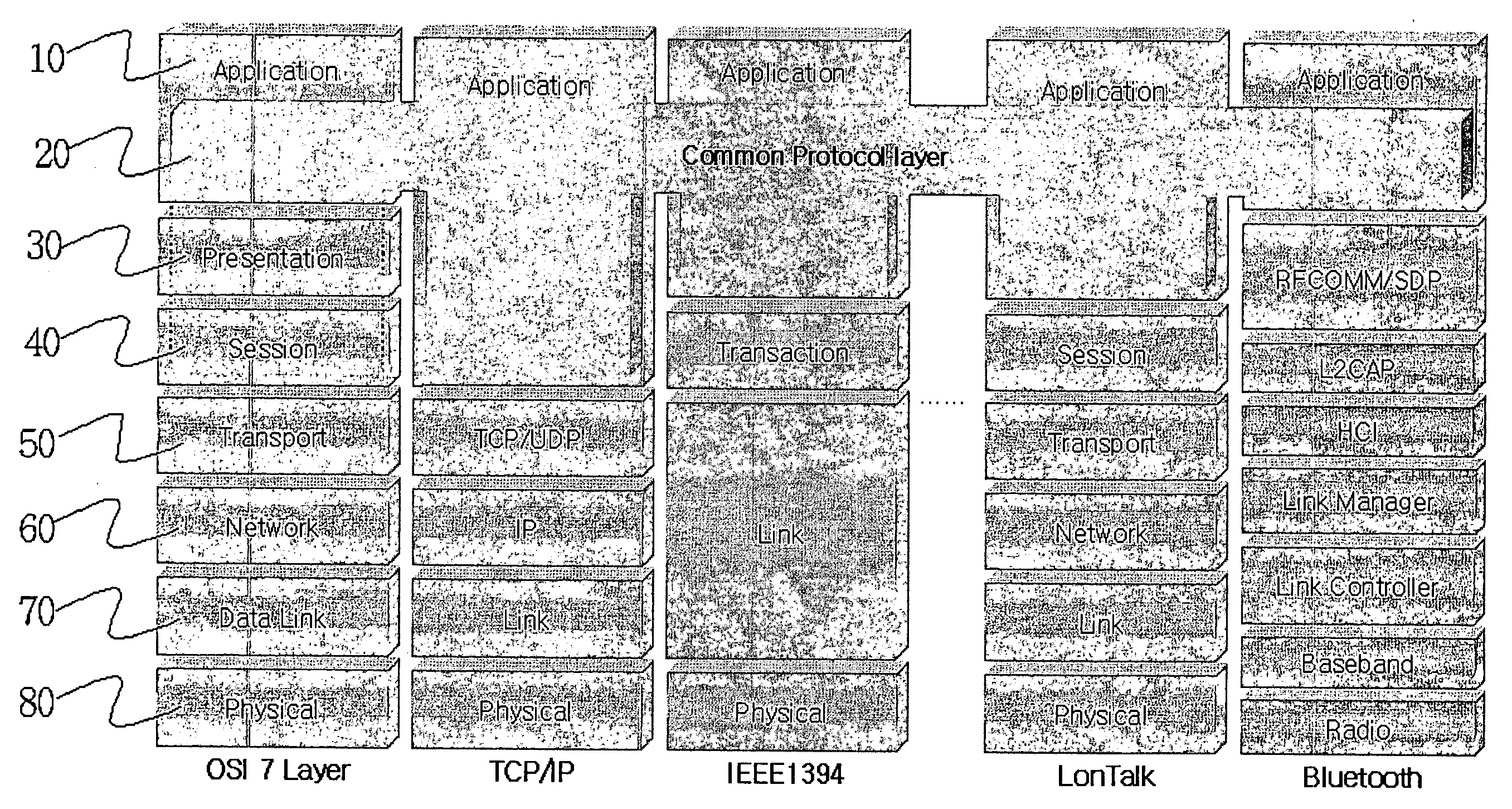
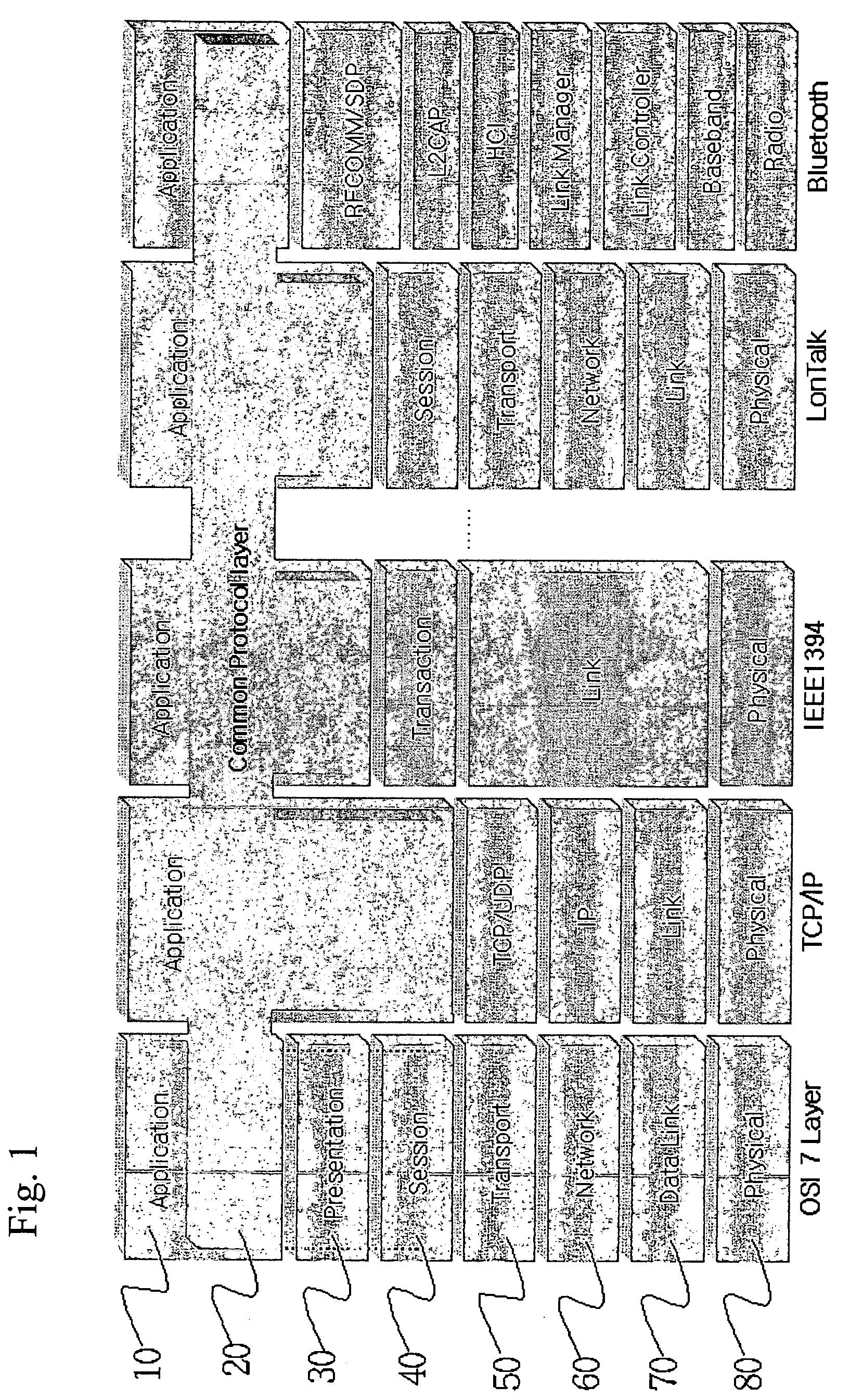
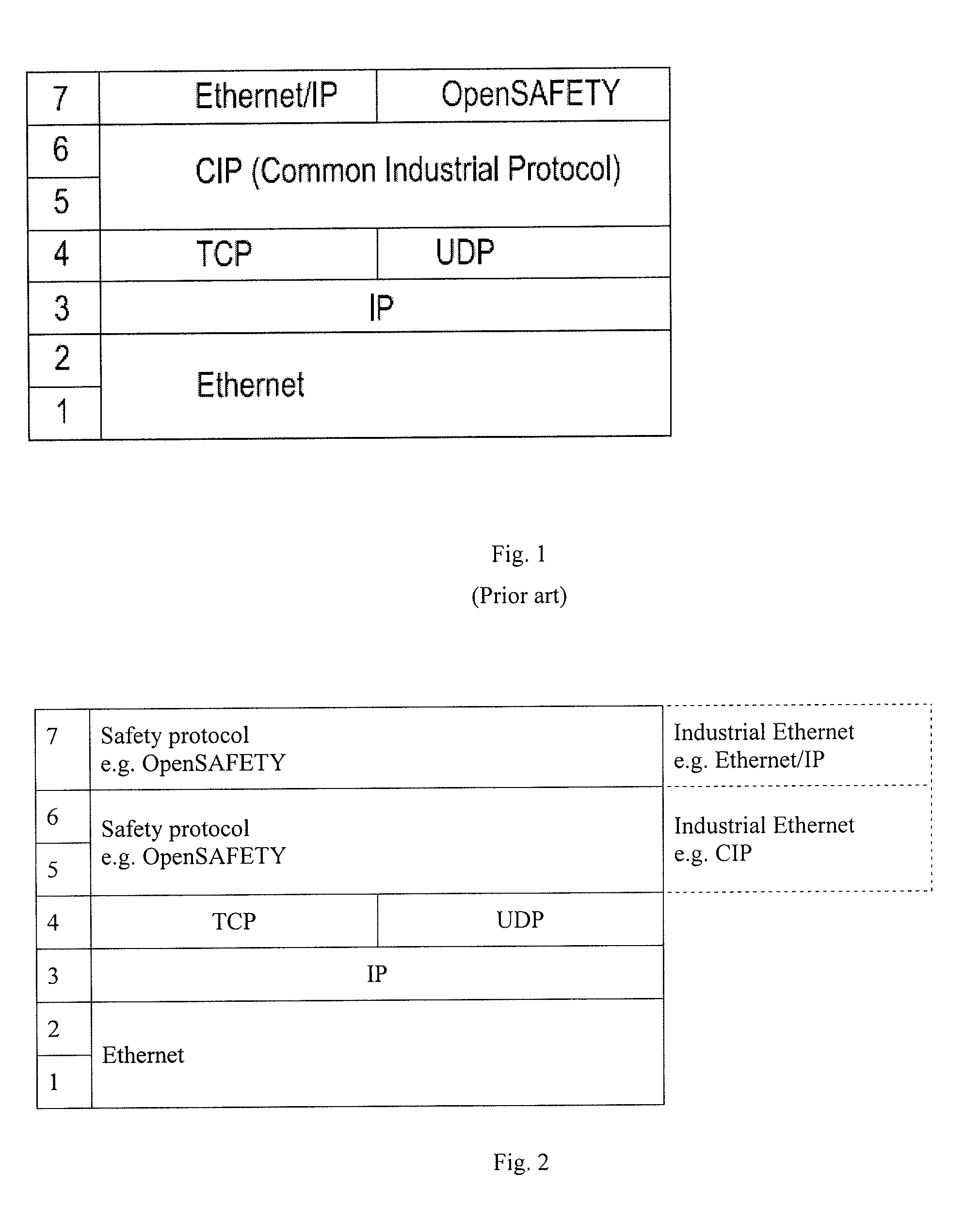
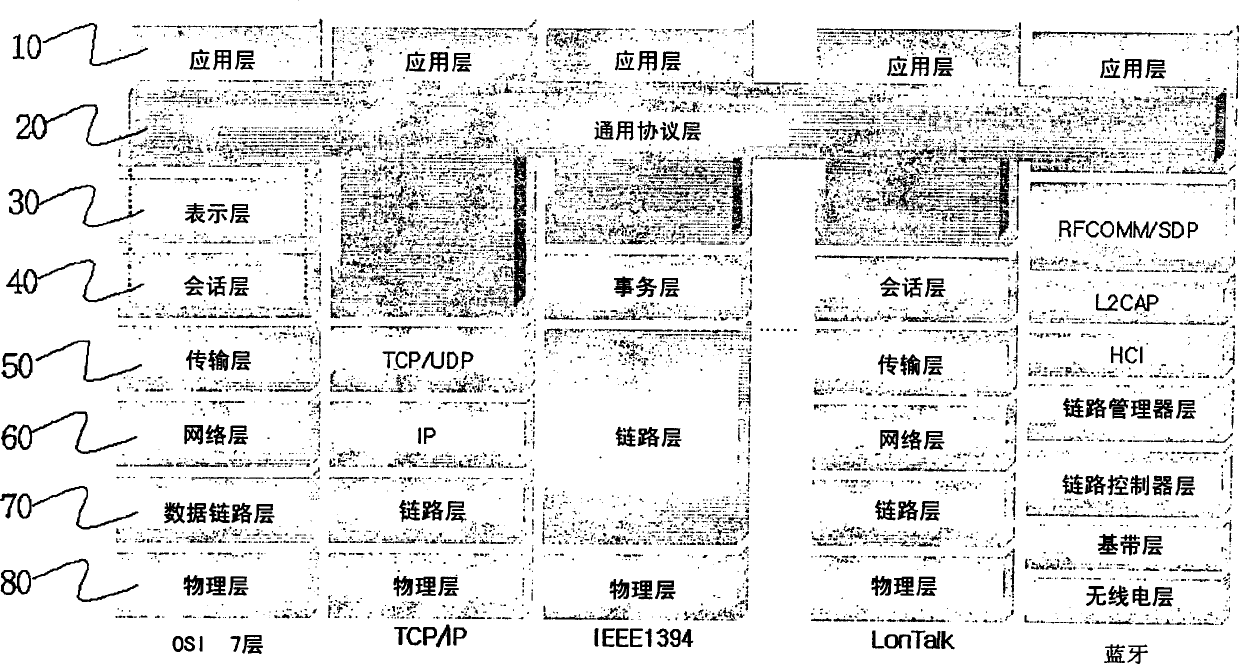
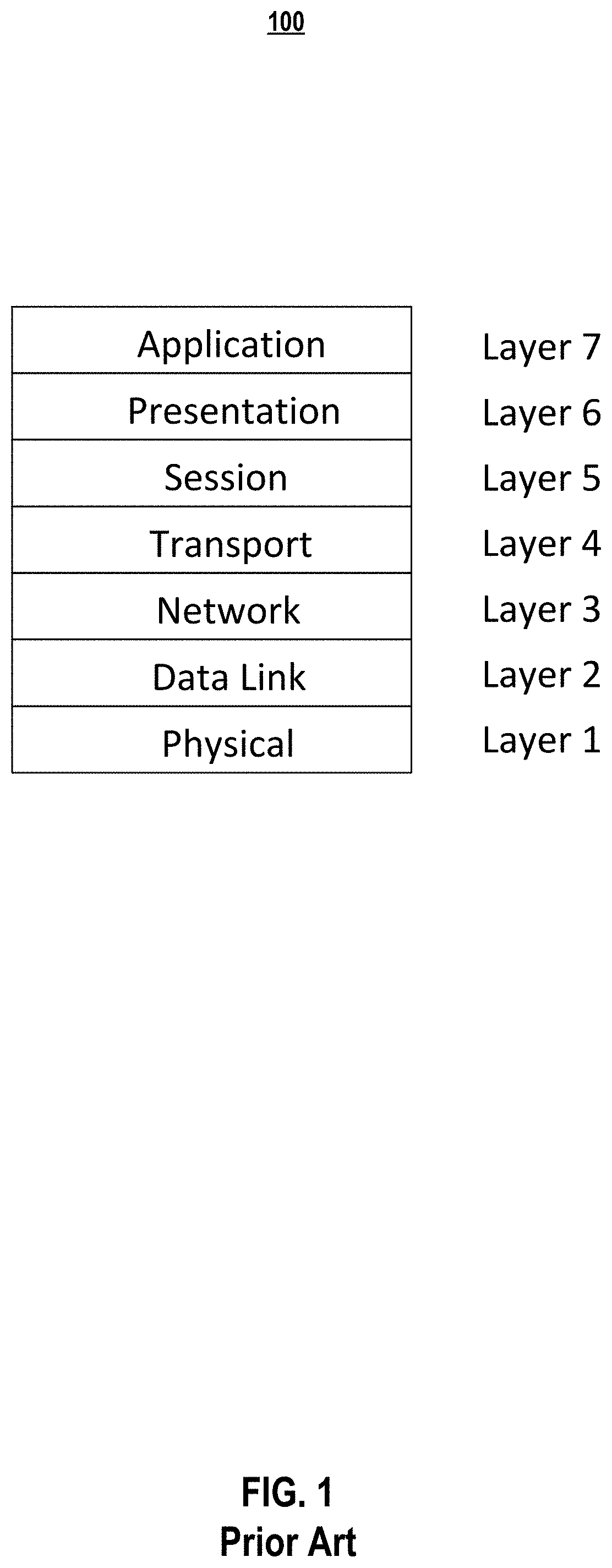
In the seven-layer OSI model of computer networking, the session layer is layer 5. The session layer provides the mechanism for opening, closing and managing a session between end-user application processes, i.e., a semi-permanent dialogue. Communication sessions consist of requests and responses that occur between applications. Session-layer services are commonly used in application environments that make use of remote procedure calls (RPCs).
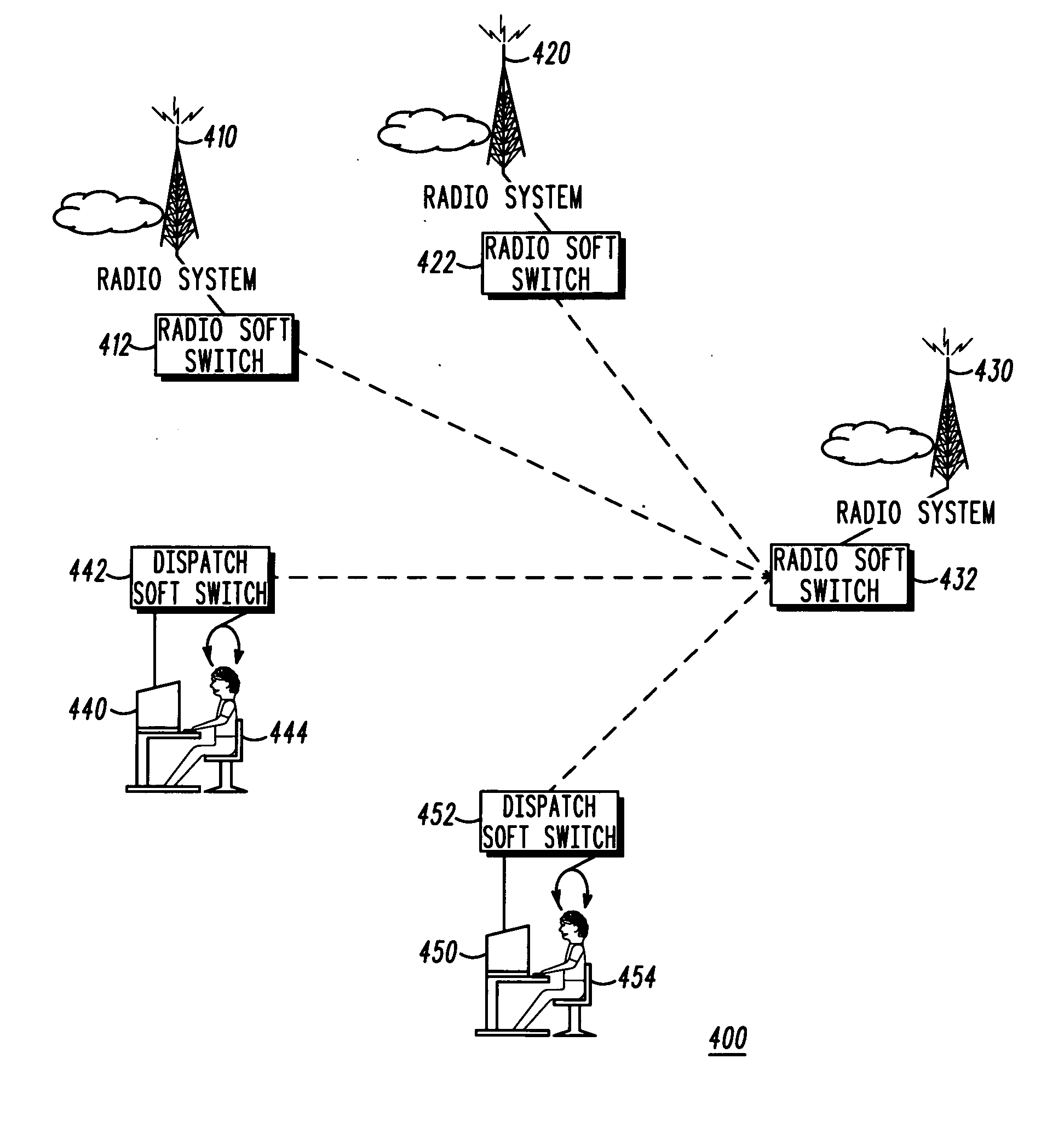
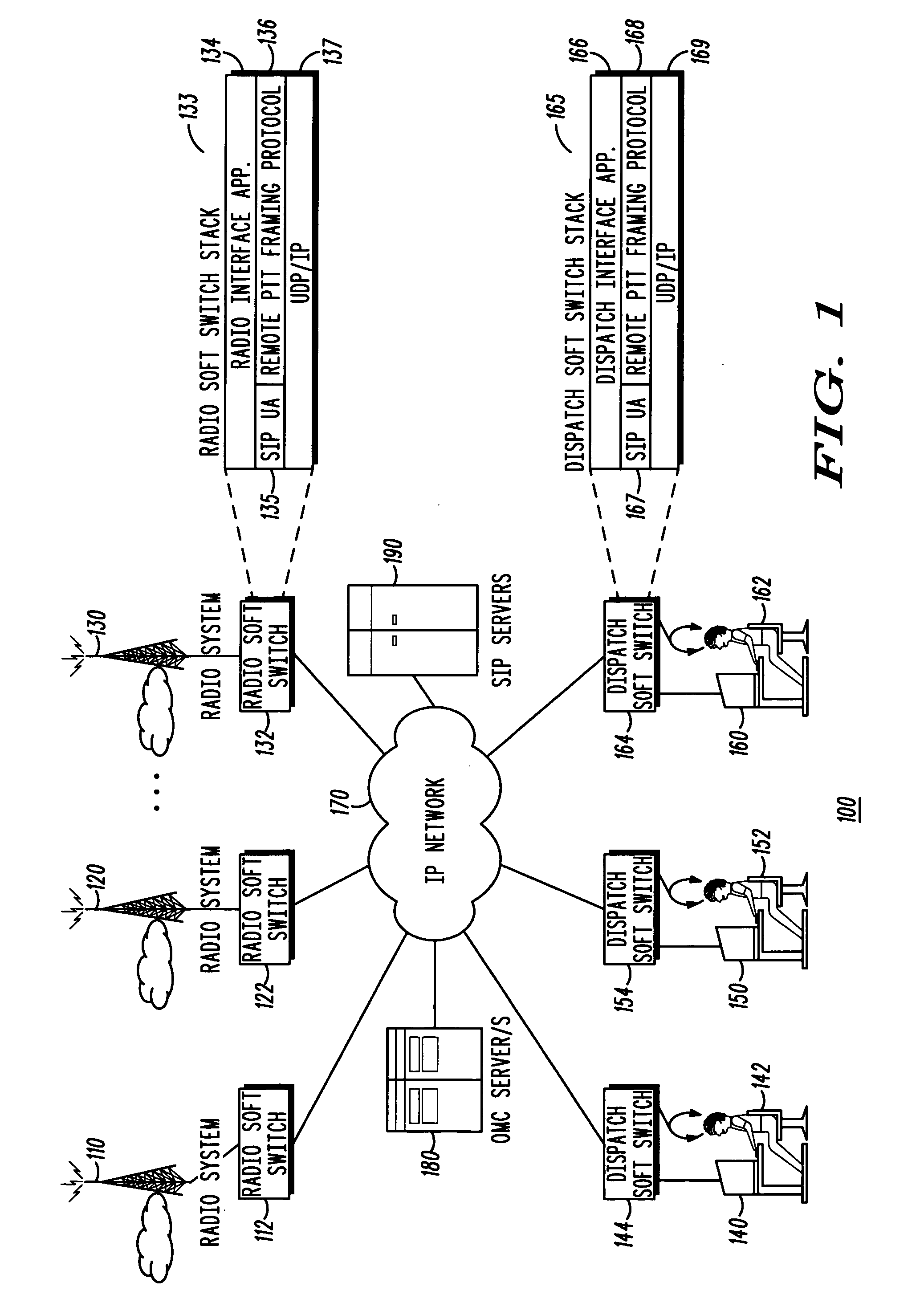
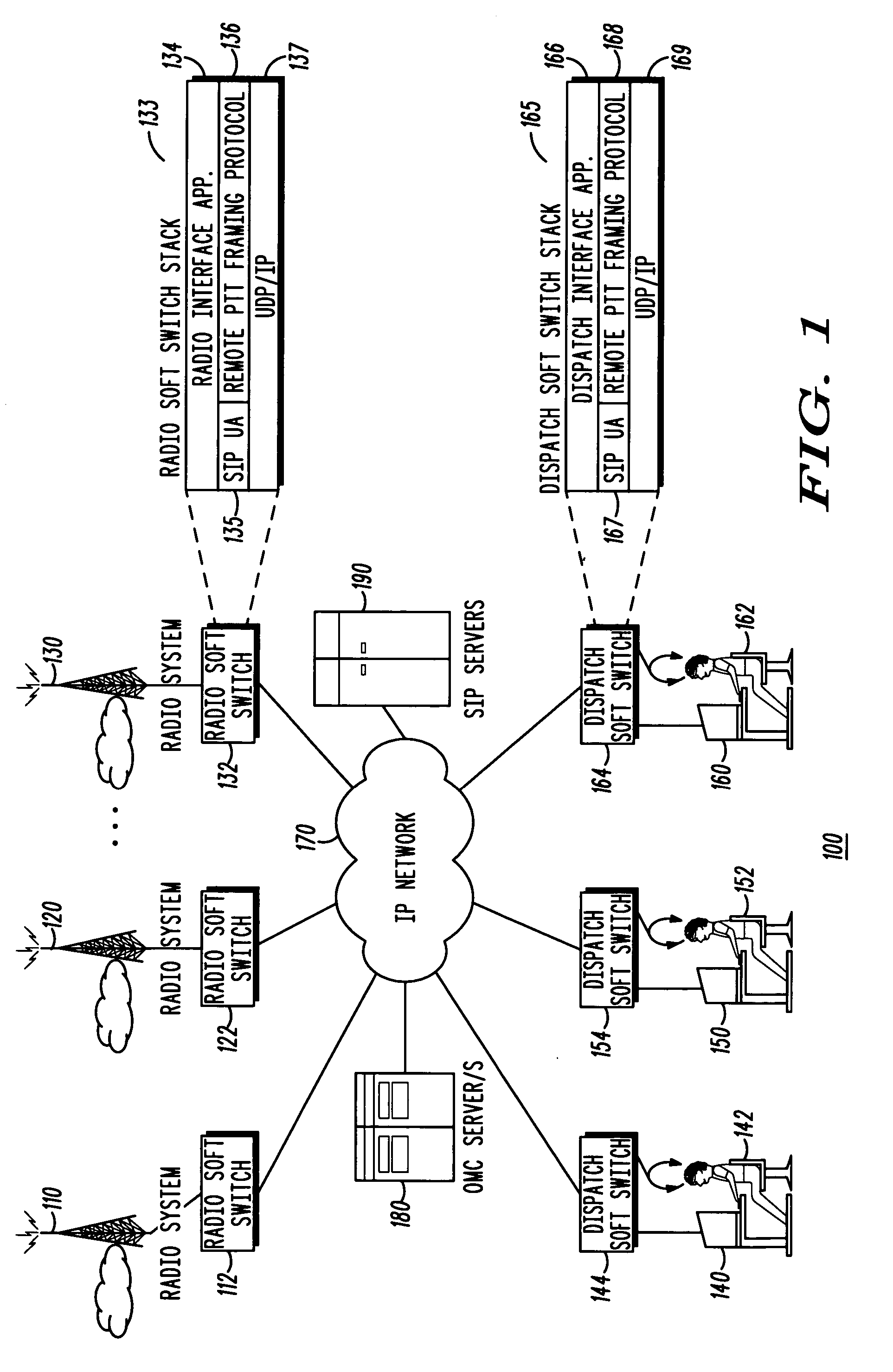
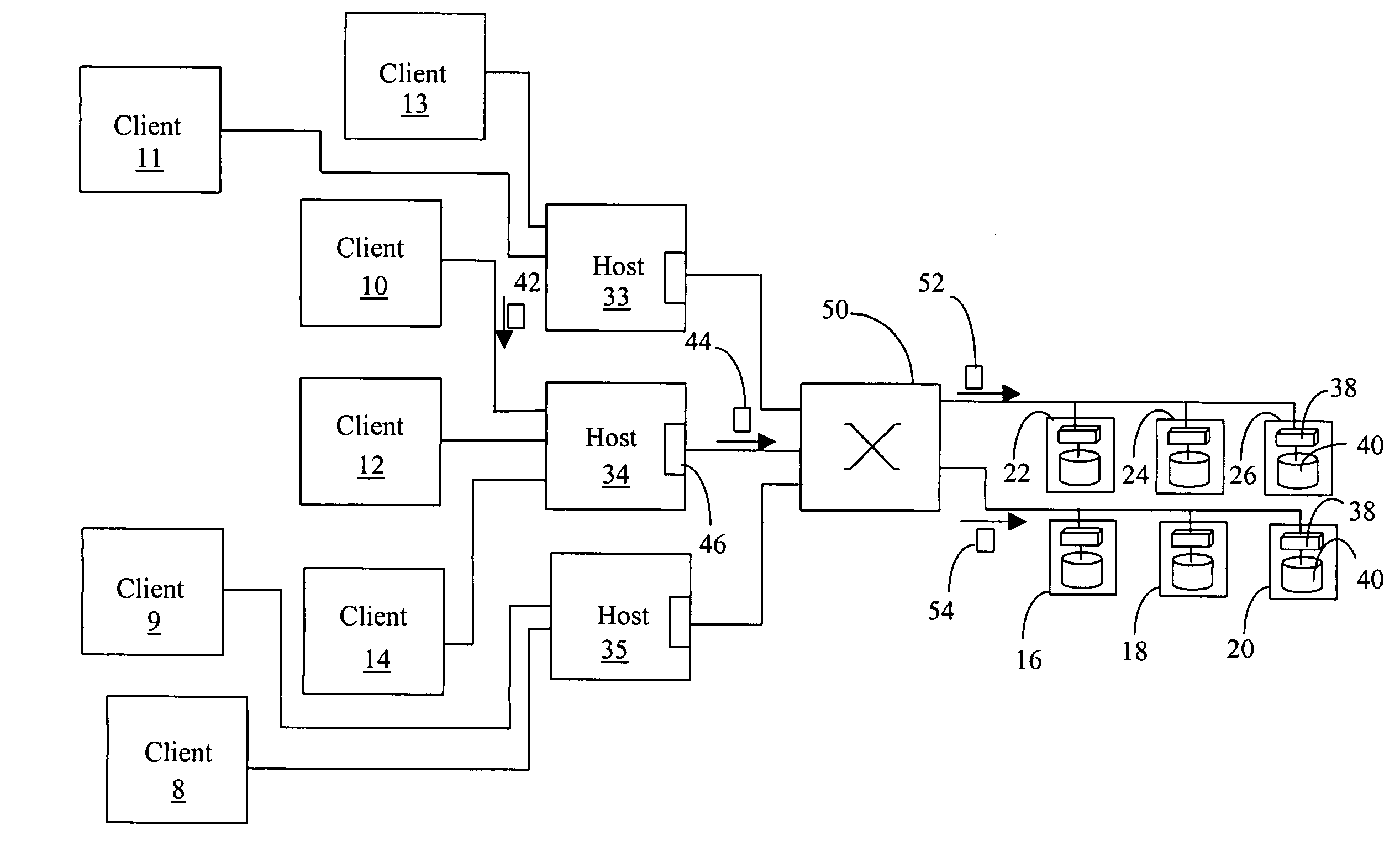
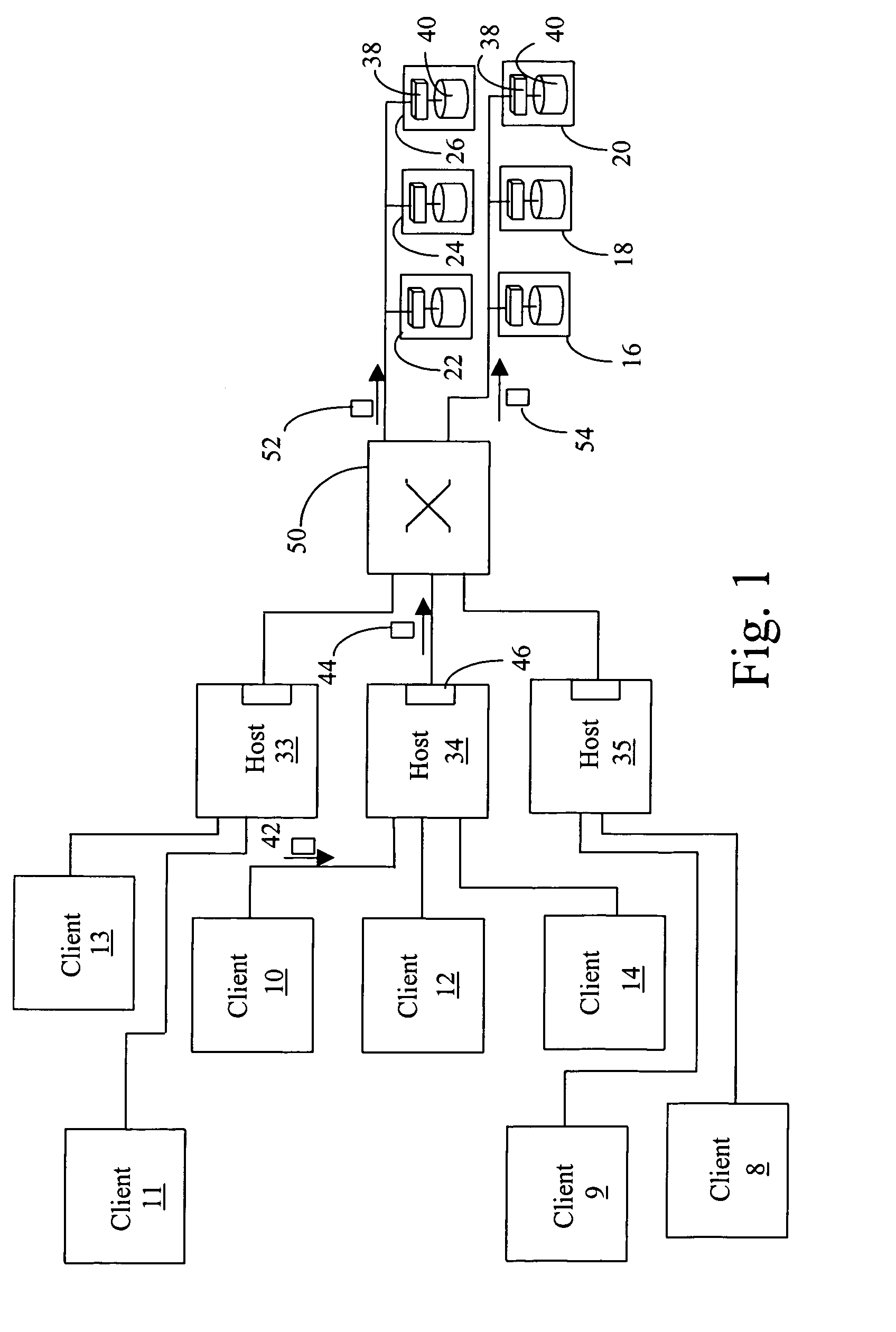
Method and apparatus for session layer framing to enable interoperability between packet-switched systems
ActiveUS20060023747A1Network traffic/resource managementTime-division multiplexControl signalInteroperability Problem
A method and apparatus for session layer framing for interoperability between packet-switched systems is described. The method includes the steps of: generating (1210) a communication frame at the session layer including a plurality of fields; providing (1220) for a payload field in the plurality of fields for carrying a payload; and providing (1230) for a signal field in the plurality of fields for carrying a control signal.
Owner:MOTOROLA SOLUTIONS INC
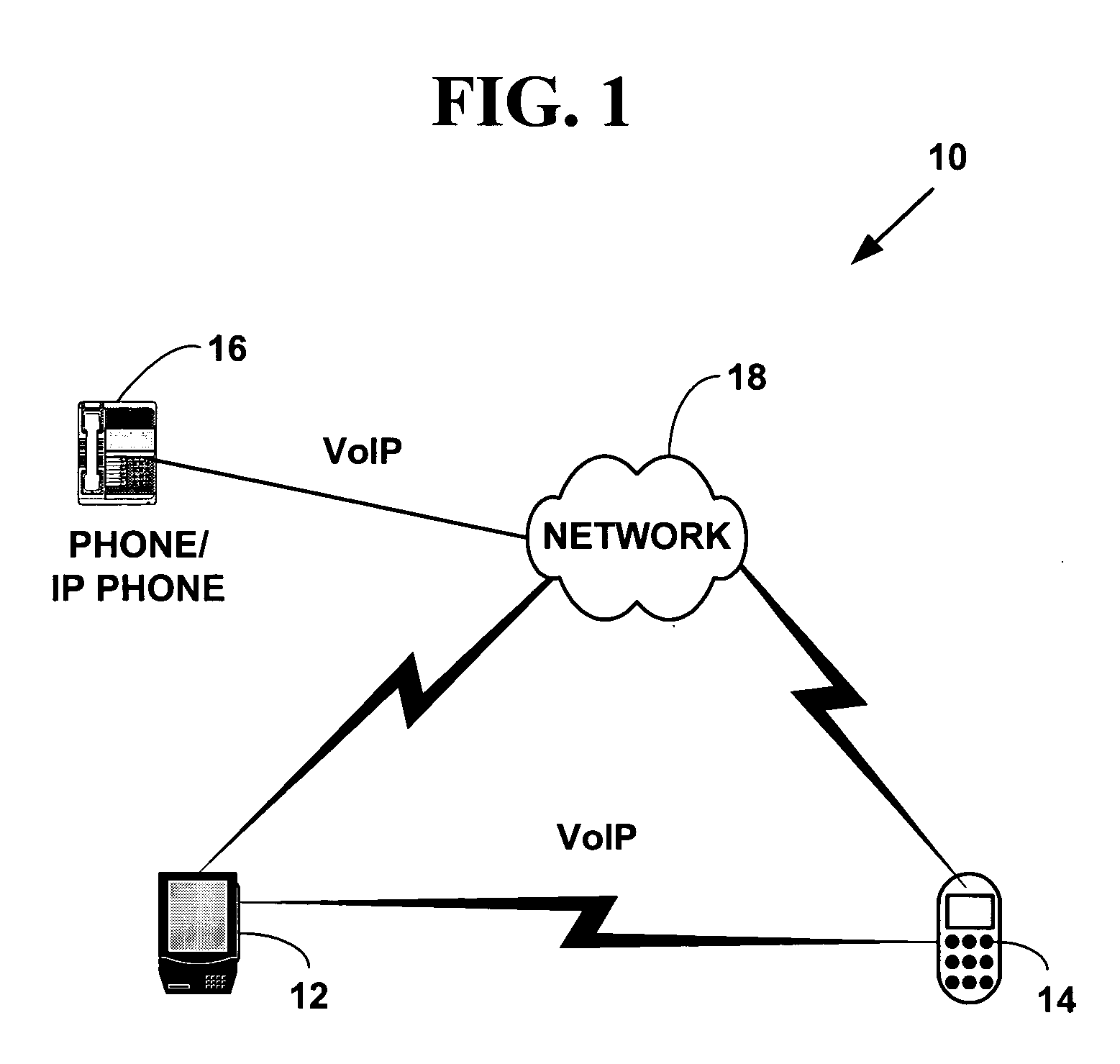
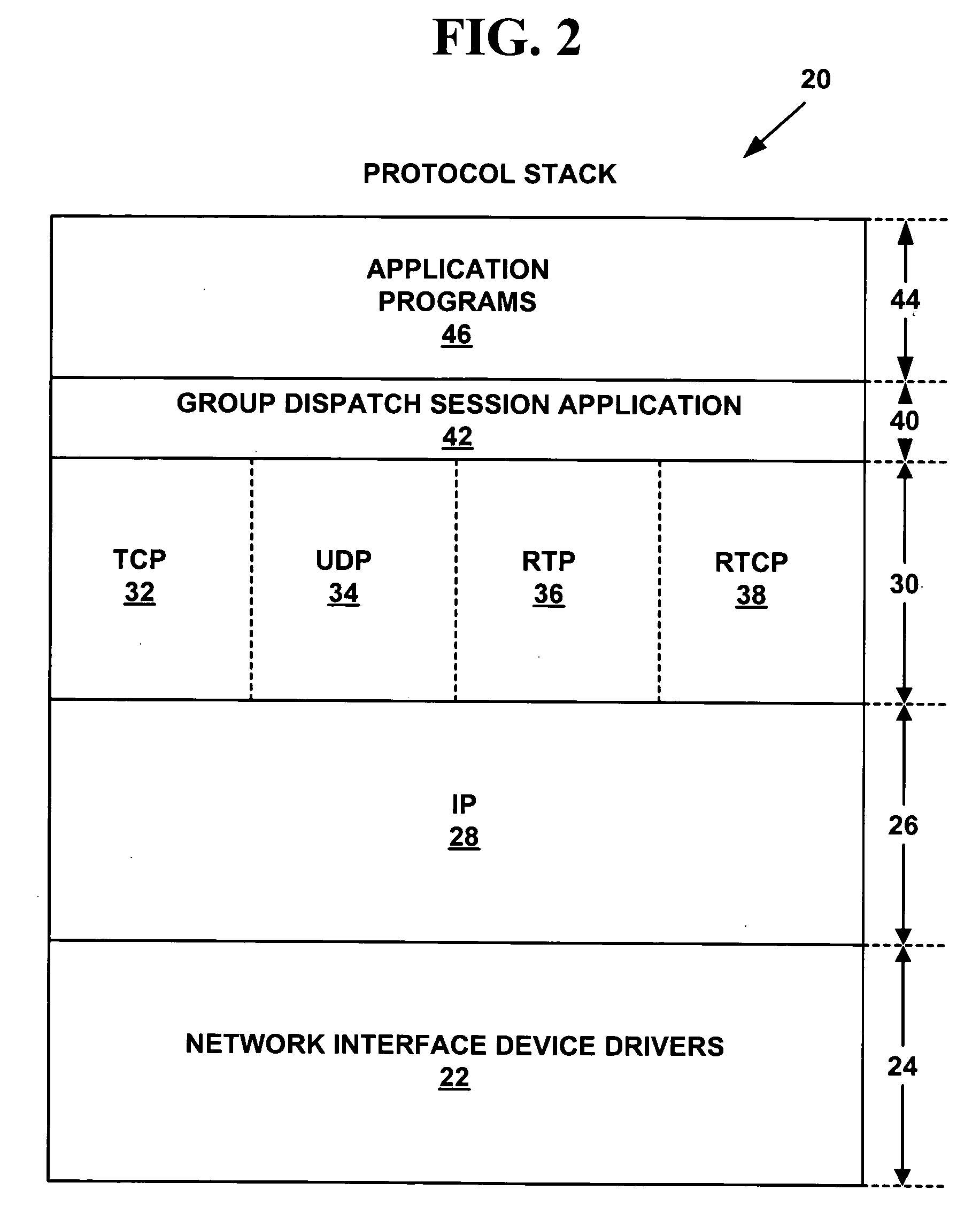
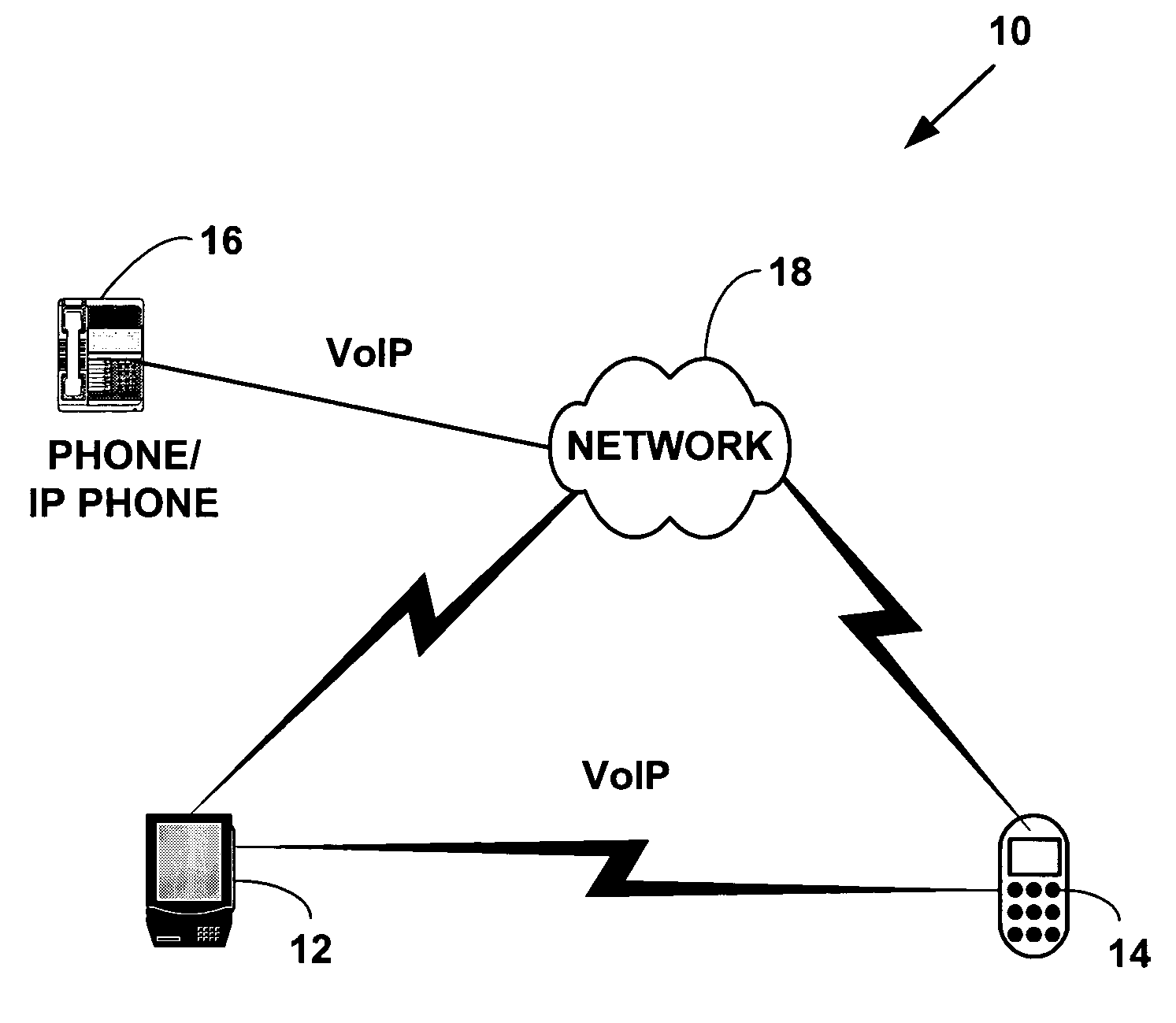
Method and system for fast setup of group voice over IP communications
ActiveUS20050073964A1Faster setup-timeReduce signaling overheadSpecial service provision for substationMultiplex system selection arrangementsTransport layerVoice over internet protocol voip
A method and system for fast setup of group Voice over Internet Protocol (VoIP) communications. The method and system provide a lower VoIP signaling overhead and a faster setup-time of group calls such as N-way audio and / or audio-video conference calls. Multi-party VoIP connections are quickly set-up over one or more virtual communications channels established between plural network devices using a session layer application, one or more group transport layer ports and a broadcast destination network address.
Owner:ZHIGU HLDG
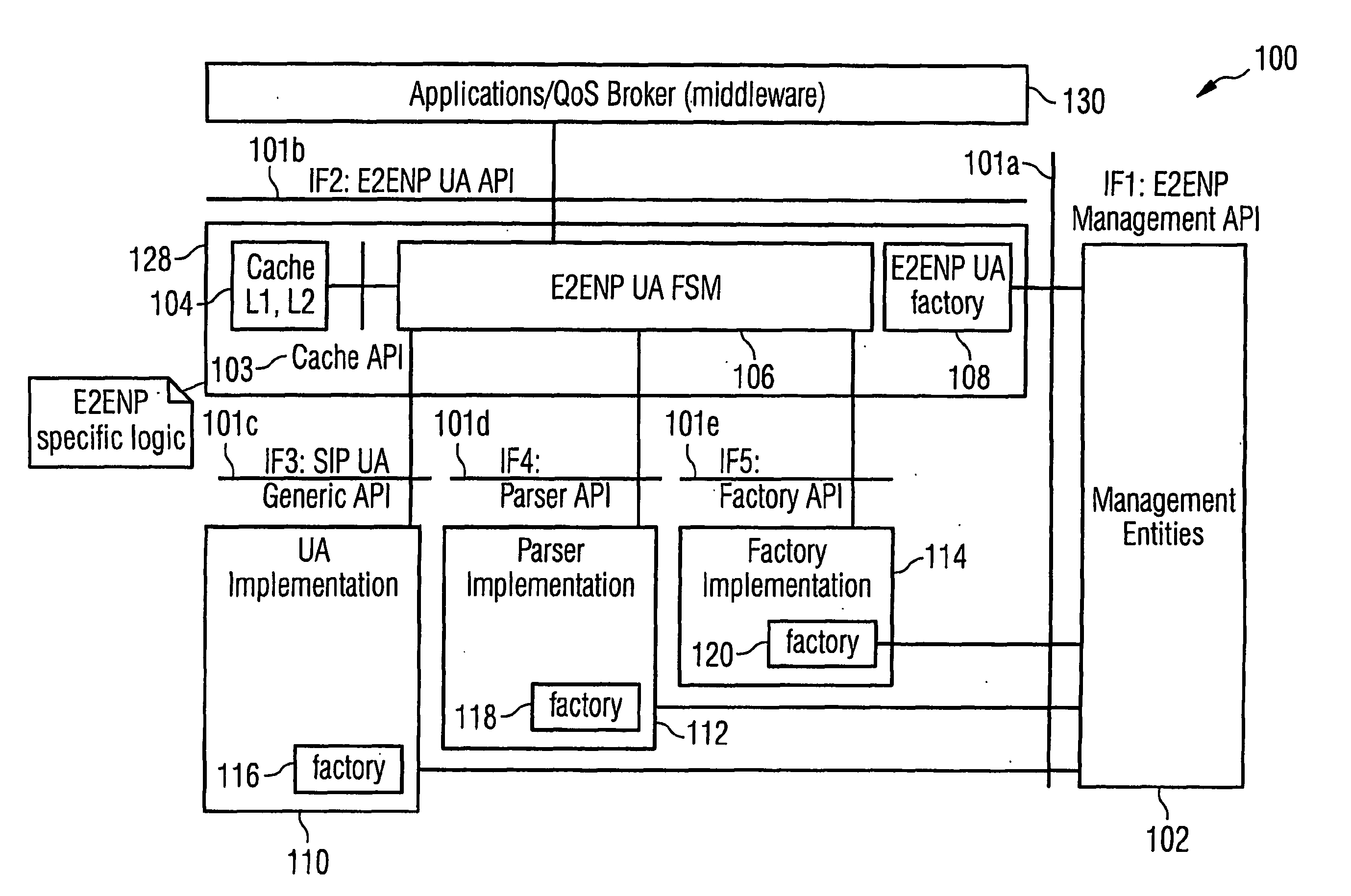
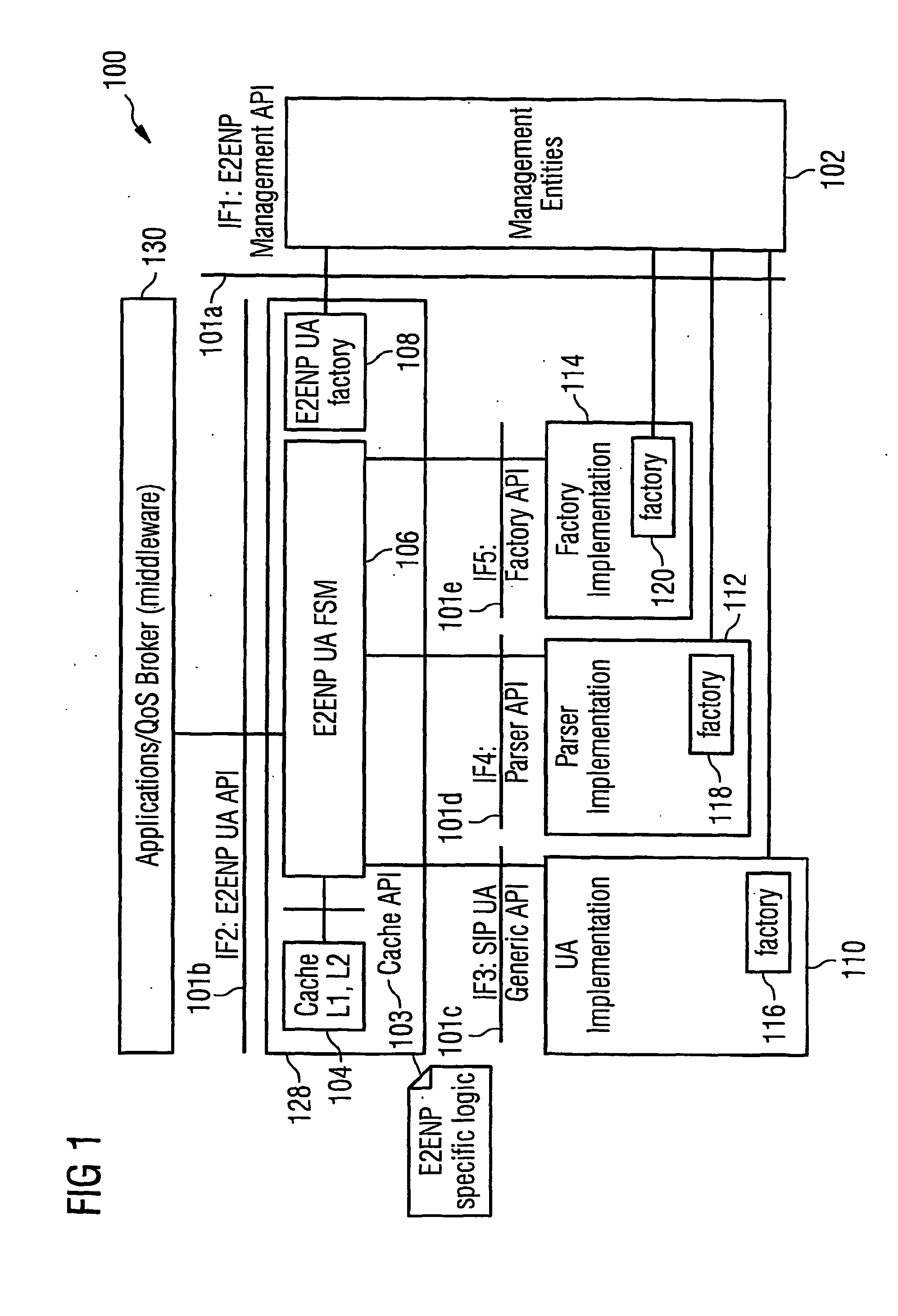
Specification of a software architecture for capability and quality-of-service negotiations and session establishment for distributed multimedia applications
InactiveUS20060294112A1Efficiently and timely reactError preventionTransmission systemsExtensible markupMiddleware
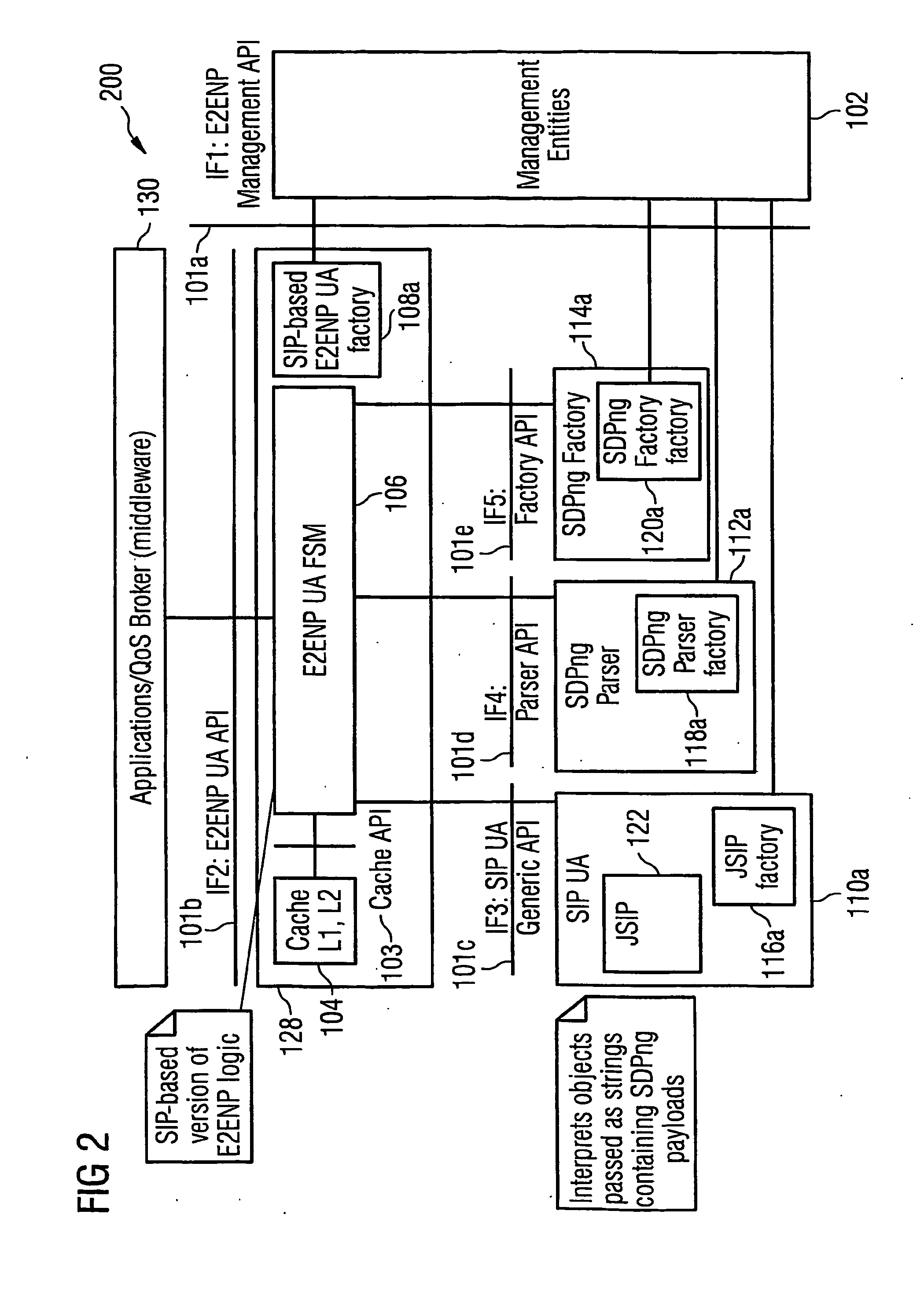
The underlying invention generally relates to the field of mobile computing in a wireless mobile networking environment with distributed multimedia applications (130). More specifically, it is directed to the field of Quality-of-Service (QOS) management for adaptive real-time services running on mobile devices and an End-to-End Negotiation Protocol (E2ENP) based on a novel usage of a session-layer protocol (SIP) in conjunction with extensions of a session description protocol implementation (SDP, SDPng) and the Extensible Markup Language (XML) for defining user profile and terminal capability information which allow to enforce and use hierarchical QOS Contract specifications. Thereby, said End-to-End Negotiation Protocol (E2ENP) is applied to derive negotiable information, which enables a prenegotiation, fast negotiation and a fast, dynamic re-negotiation of the end-to-end quality and capabilities for a telecommunication session, for multiple configurations of two or a multiplicity of end peers and / or middleware in a consistent, reliable, and incremental way by enabling the mobile applications to efficiently and timely react to QoS violations. Furthermore, the invention pertains to the concept and realization of a novel E2ENP User Agent (128) which encapsulates the signaling part of E2ENP and expresses the information to be negotiated in an interchangeable format in such a way that heterogeneous applications (130) can easily agree on a reference model applied to orchestrate local, peer, and network resources according to the preferences and profiles of the respective user in a coordinated manner. According to one embodiment of the invention, the employed E2ENP sessionlayer protocol Application Programming Interfaces (101a-e) are independent of the actually used session-layer protocol and session description protocol implementations.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG +1
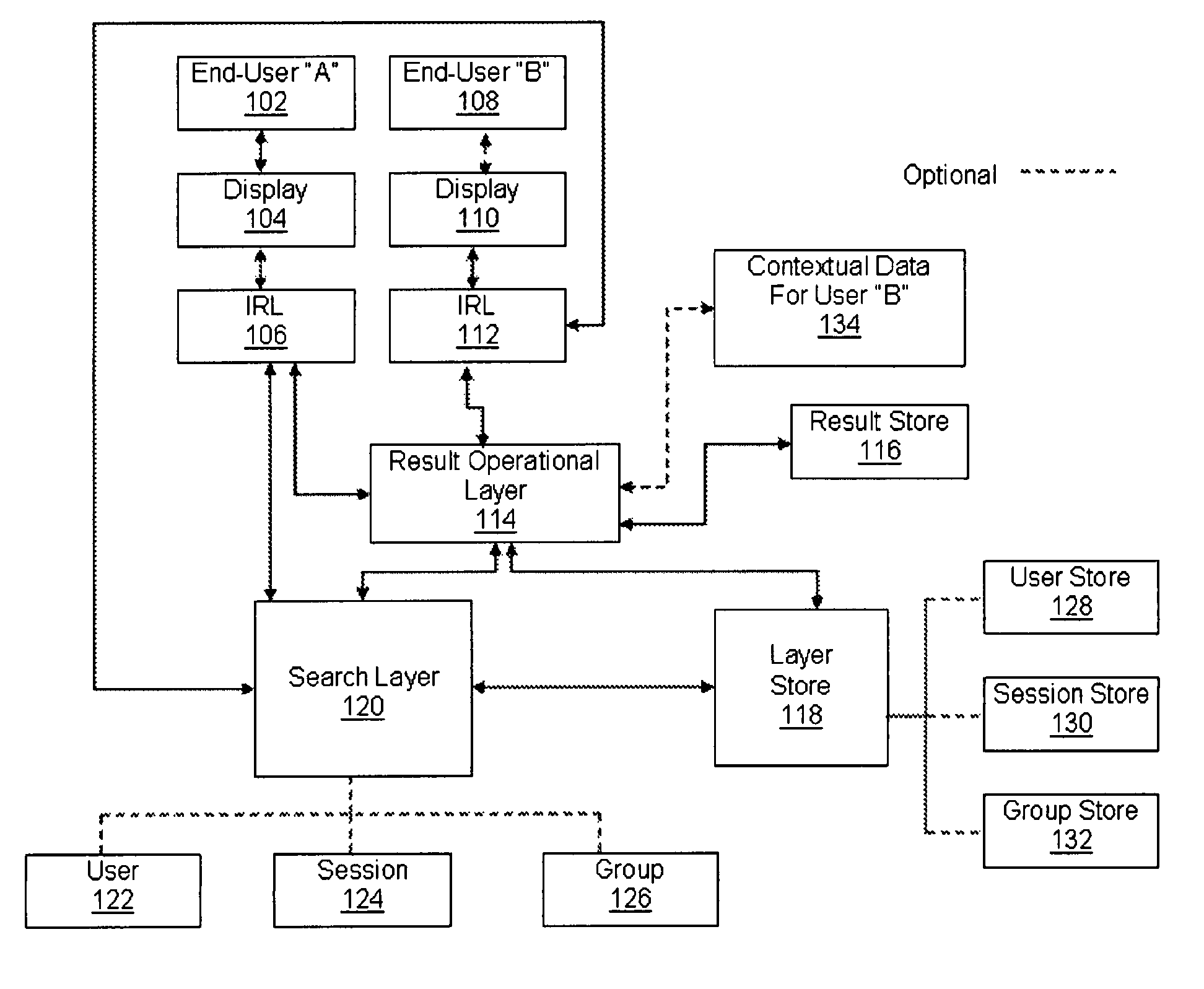
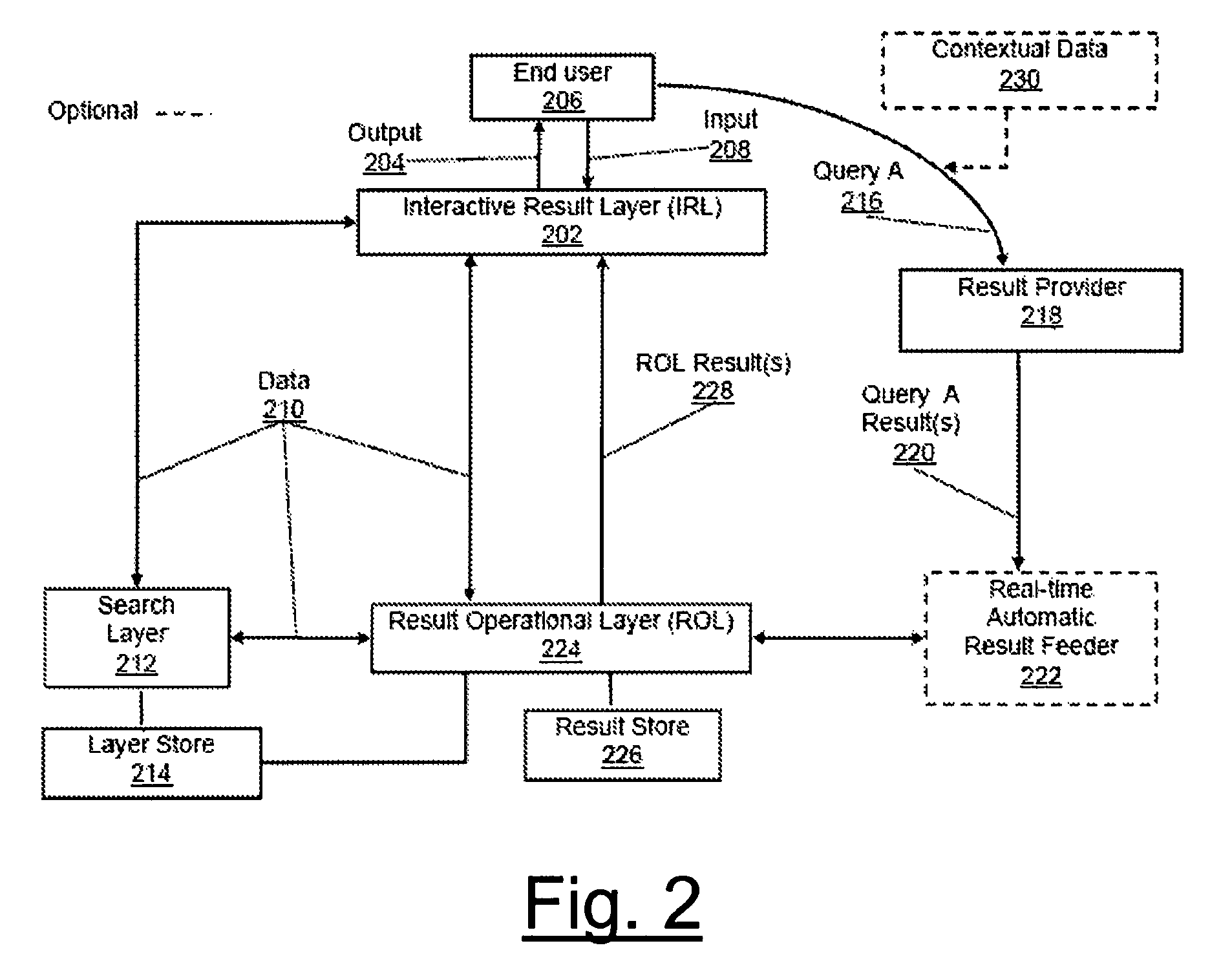
Systems, methods, and apparatus for seamless integration for user, contextual, and social awareness in search results through layer approach
InactiveUS20090055355A1Improve overall utilizationEasy to operateWeb data indexingDigital data processing detailsLoopbackUser awareness
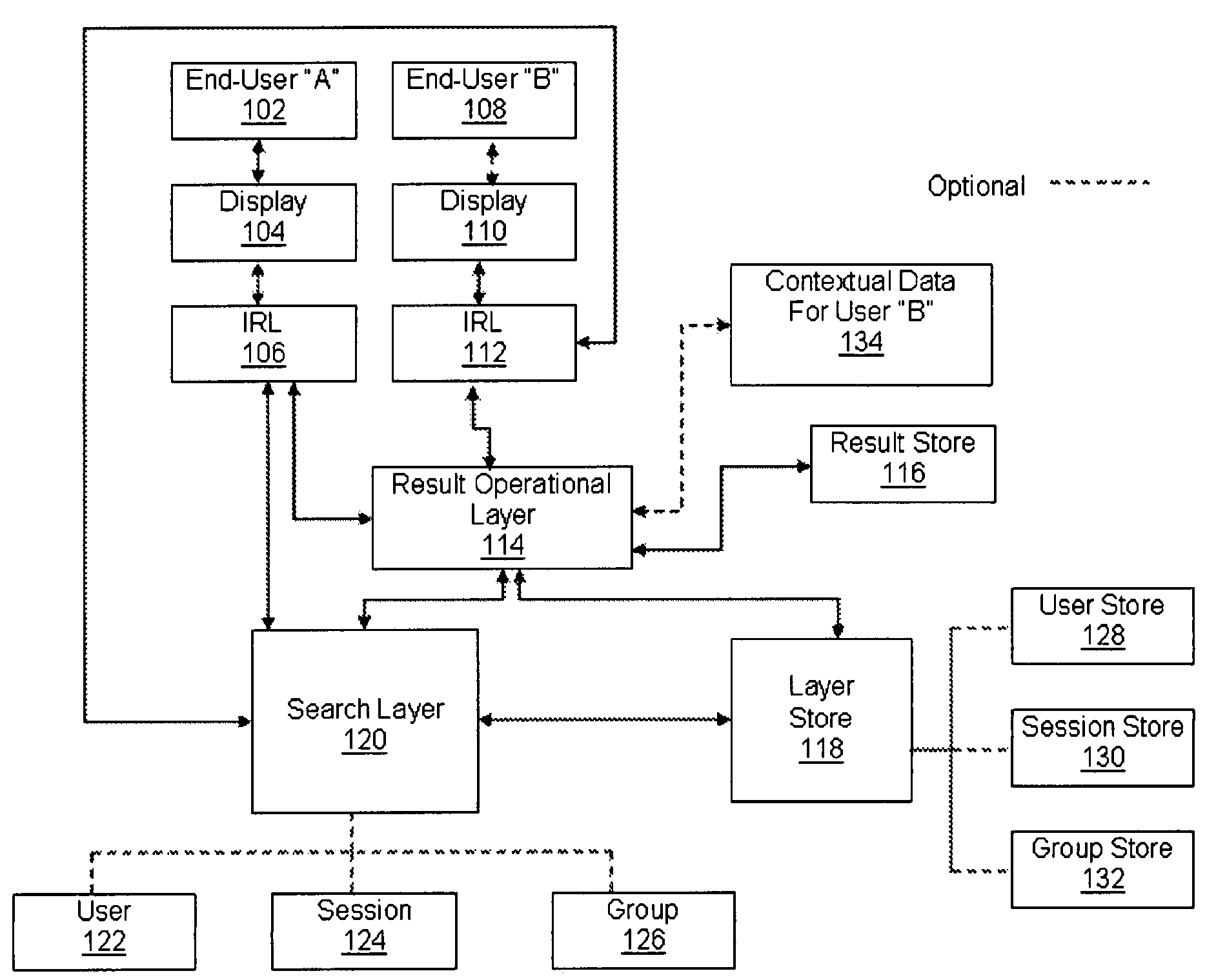
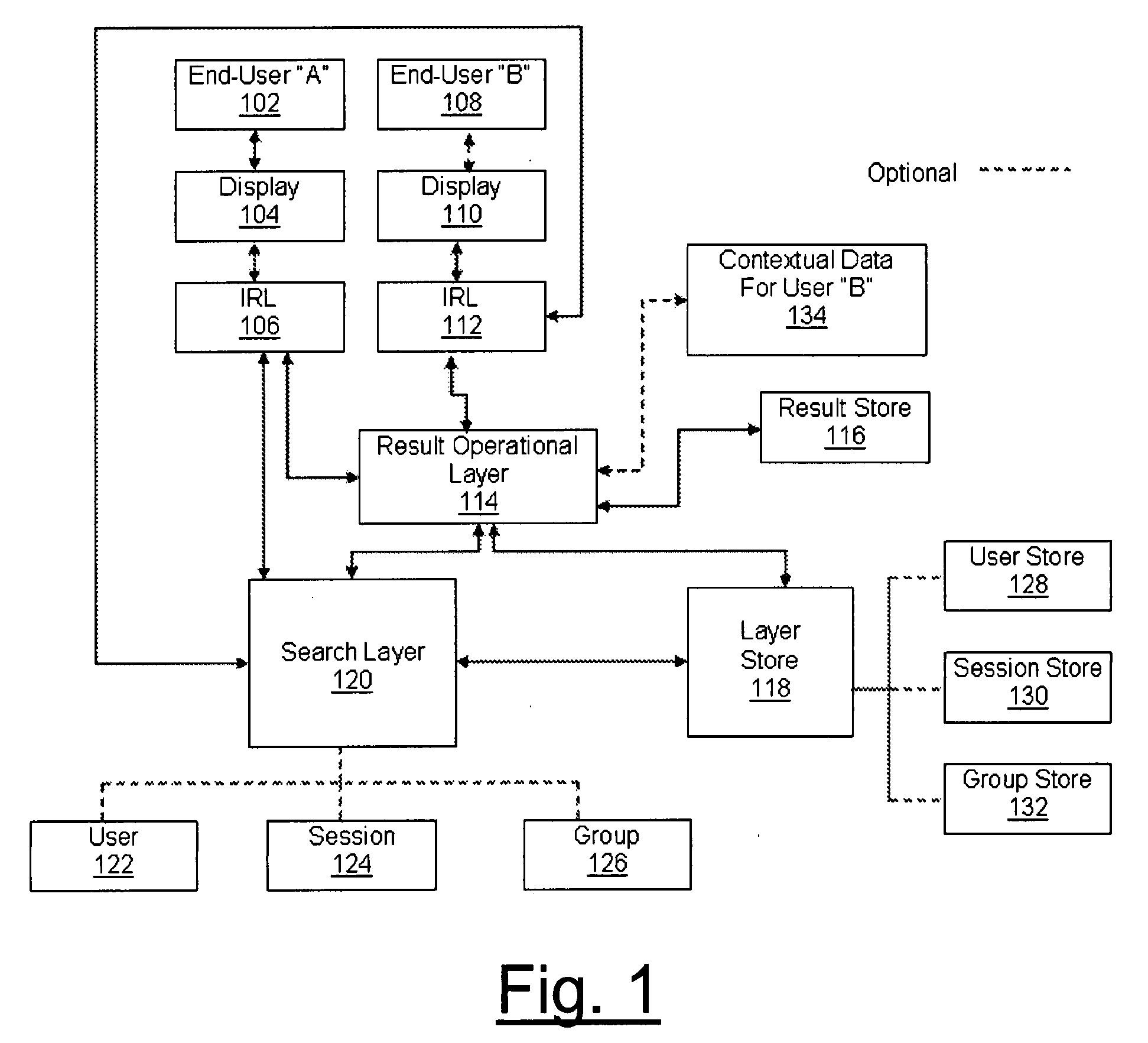
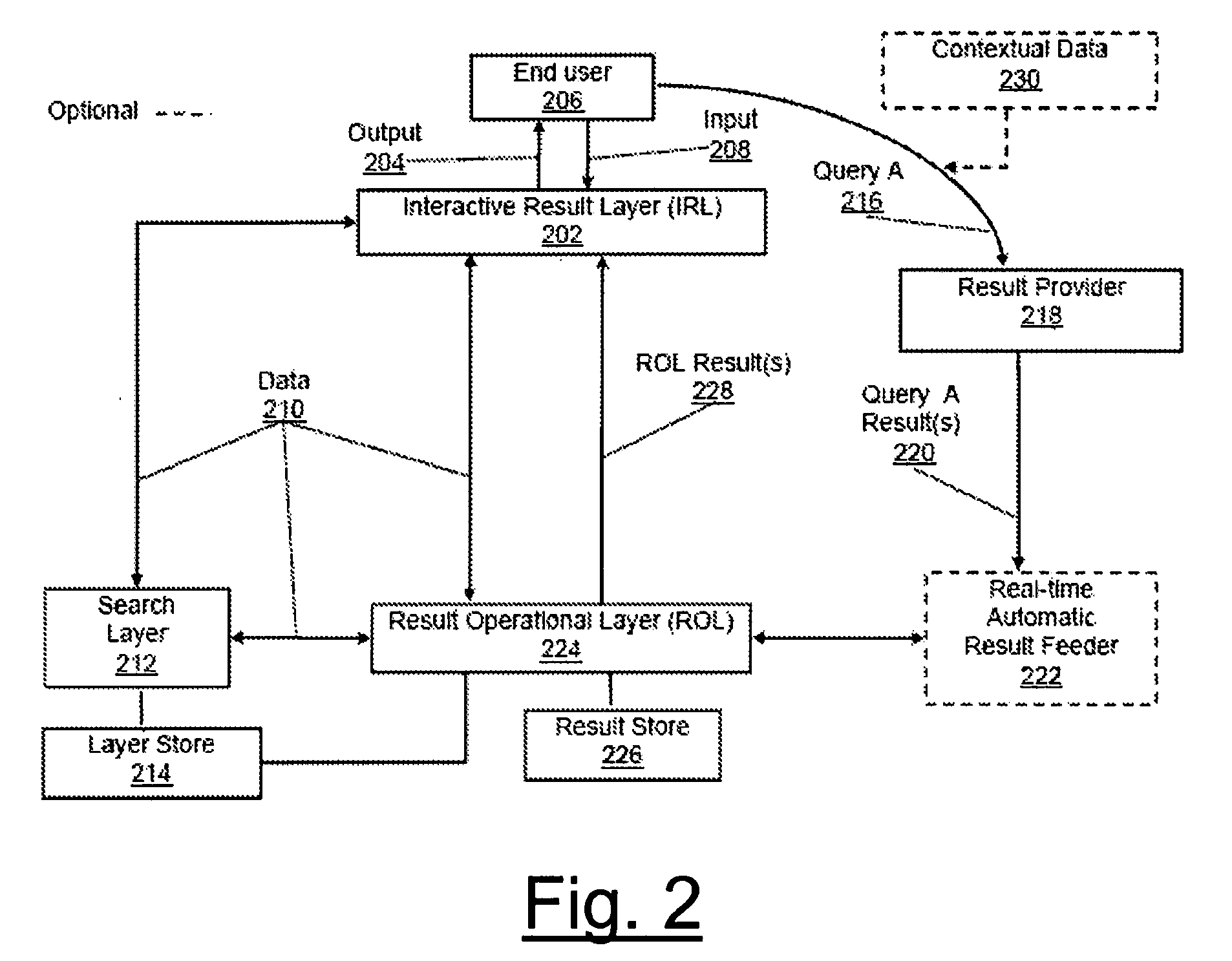
Systems, methods, and apparatus for providing contextual and social awareness in search results through a layer approach are herein disclosed. Awareness in search results is provided through one or more search layers, result operational layer, an interactive result layer, and loopback feedback among embodied layers. Specifically, the system provides collective and contextual intelligence to the presentation of search results. The present invention establishes end-user awareness by way of user layer, contextual awareness by way of session layer, and group awareness by way of group layer. Each layer can work independently of one another or can be integrated for further utility. Further provided are methods of search layer lens, search layer bins, and search layer funneling. The present invention also provides an apparatus providing contextual and / or social awareness for search to be utilized by methods disclosed herein.
Owner:BRUNNER JOSIE C +1
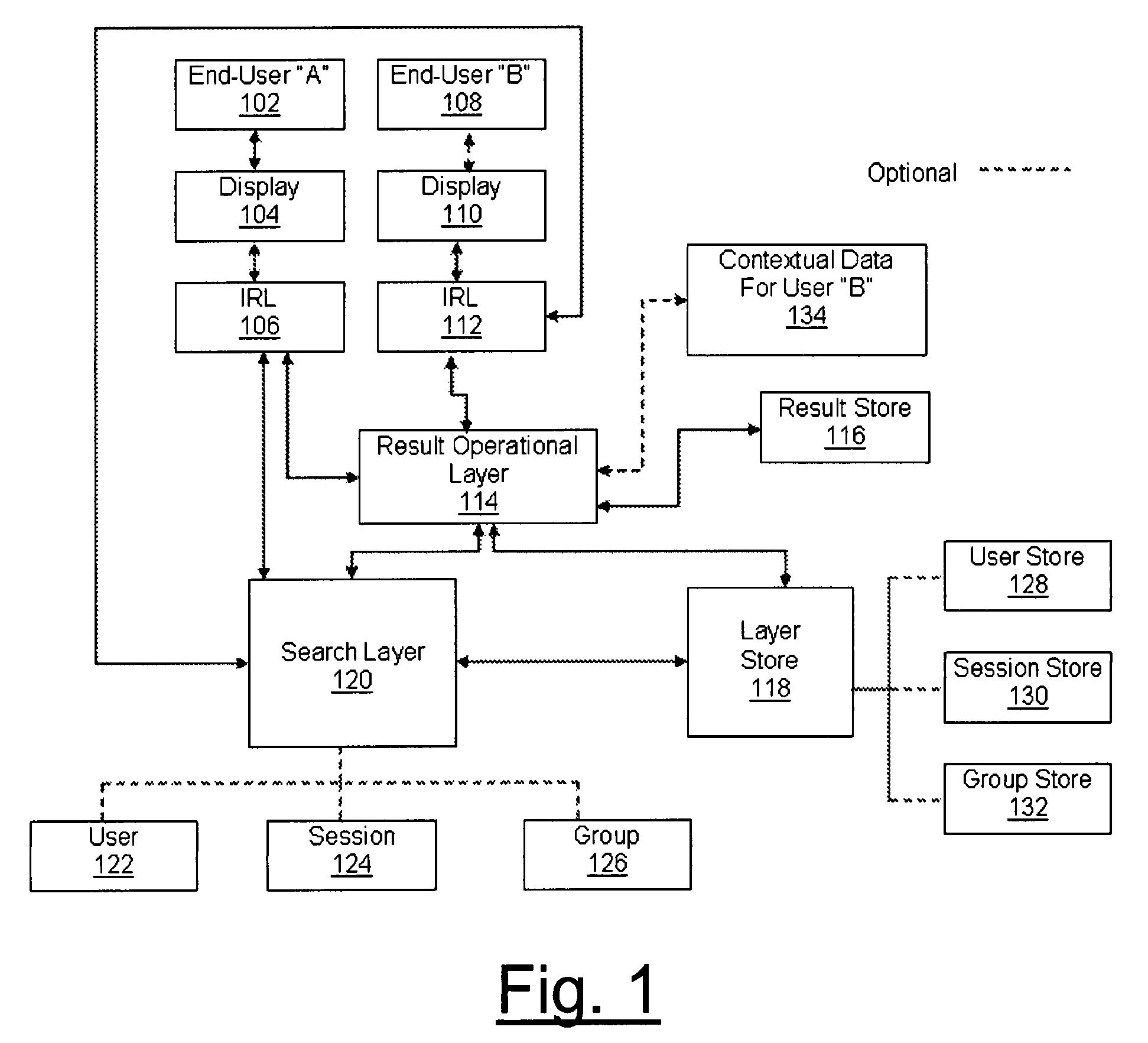
Systems and apparatuses for seamless integration of user, contextual, and socially aware search utilizing layered approach
InactiveUS7860852B2Improve overall utilizationEasy to operateWeb data indexingDigital data processing detailsUser awarenessLoopback
Systems and apparatuses for providing contextual and social awareness in search results through a layer approach are herein disclosed. Awareness in search results is provided through one or more search layers, result operational layer, an interactive result layer, and loopback feedback among embodied layers. Specifically, the system provides collective and contextual intelligence to the presentation of search results. The present invention establishes end-user awareness by way of user layer, contextual awareness by way of session layer, and group awareness by way of group layer. Each layer can work independently of one another or can be integrated for further utility. Further provided are methods of search layer lens, search layer bins, and search layer funneling. The present invention also provides apparatuses providing contextual, end-user, social awareness, or combination thereof for search to be utilized by methods disclosed herein.
Owner:BRUNNER JOSIE C +1
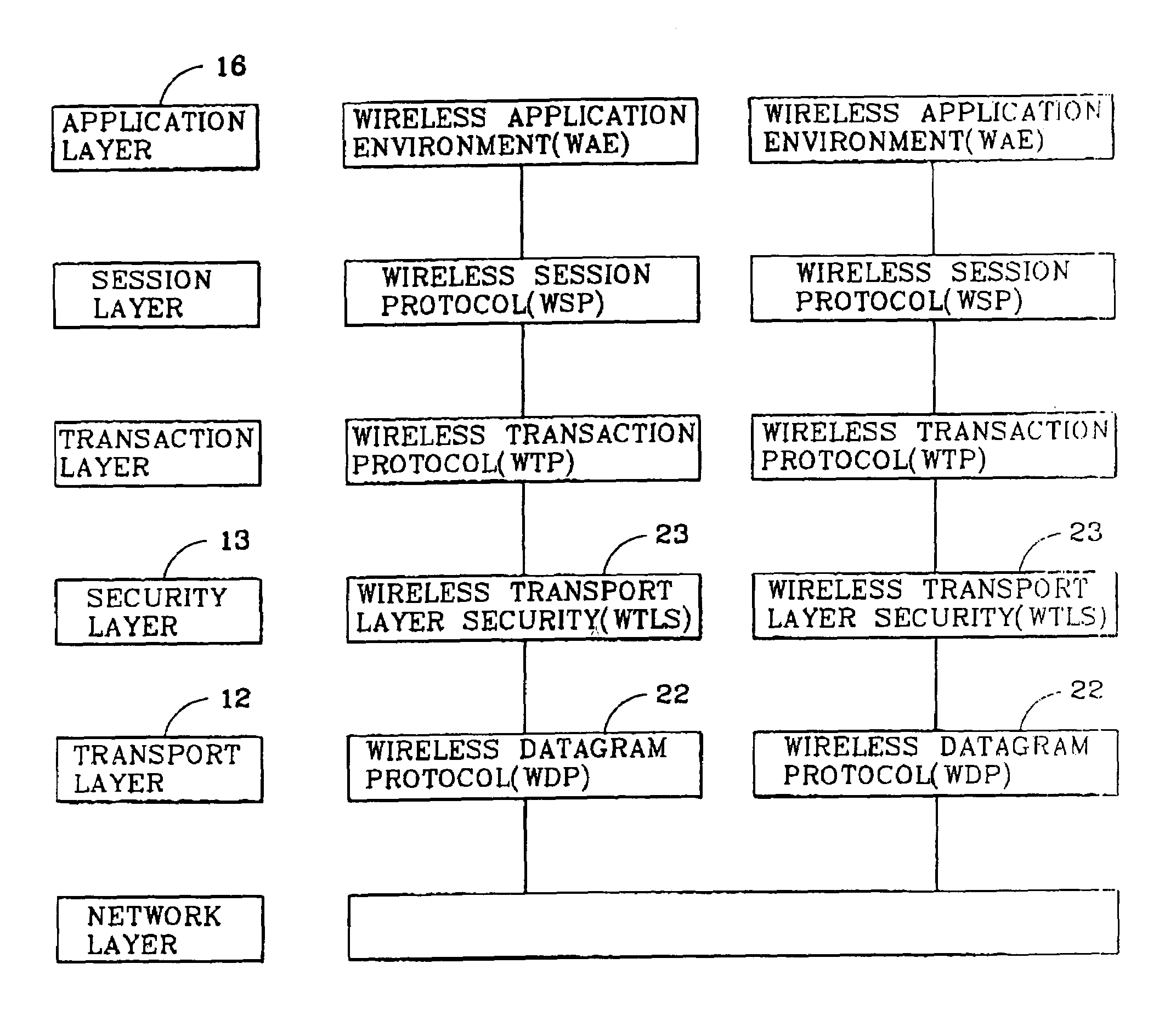
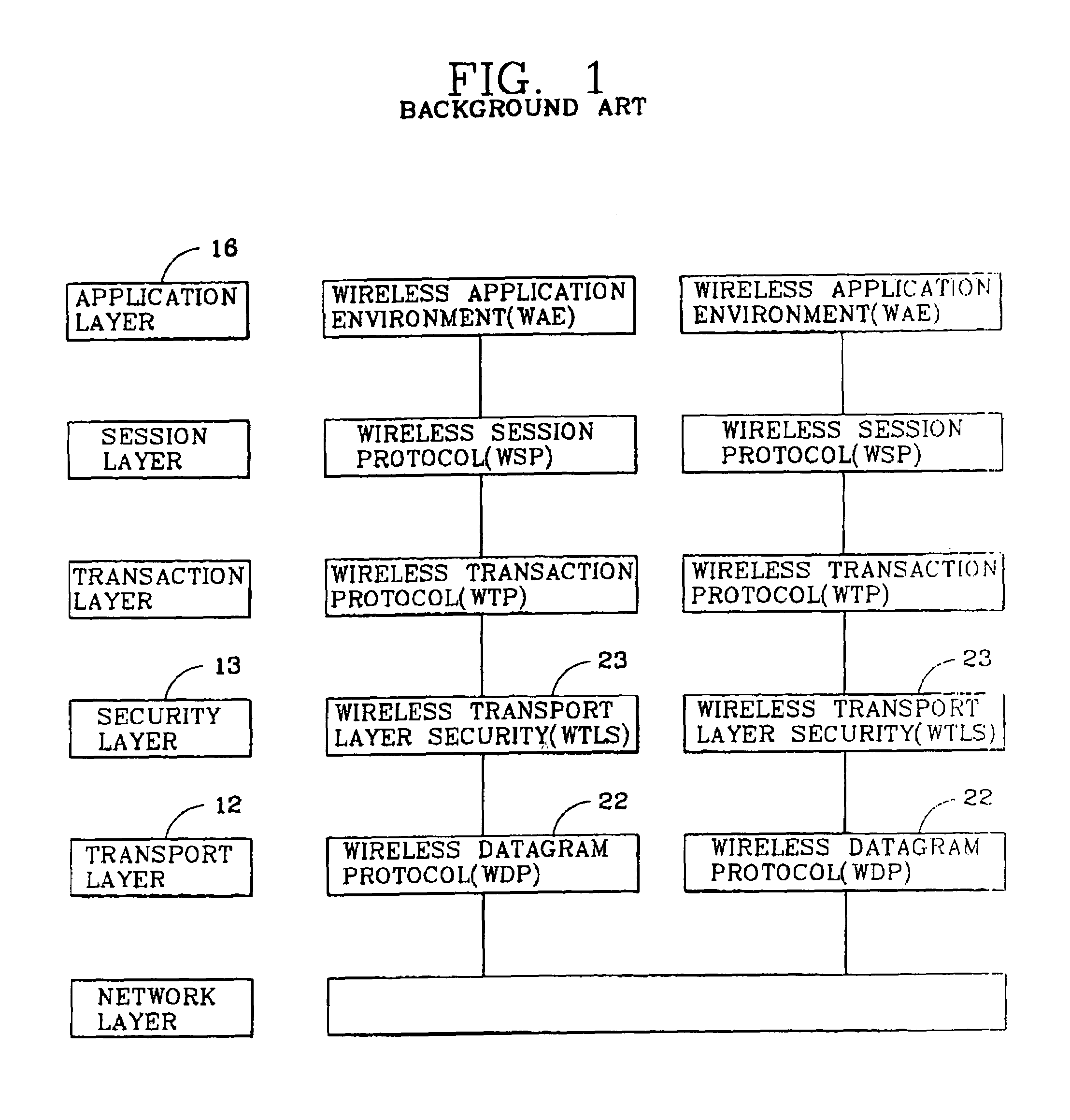
Security protocol structure in application layer
InactiveUS7096352B2Public key for secure communicationUser identity/authority verificationWireless Application ProtocolCryptographic protocol
A security protocol structure for a Wireless Application Protocol (WAP) standard structure is disclosed. The security protocol structure provides a data security function in an application layer by providing a secret session having a secured session layer security (SSLS) protocol for providing a secret session interface to an application program between the session layer and the application layer.
Owner:LG ERICSSON
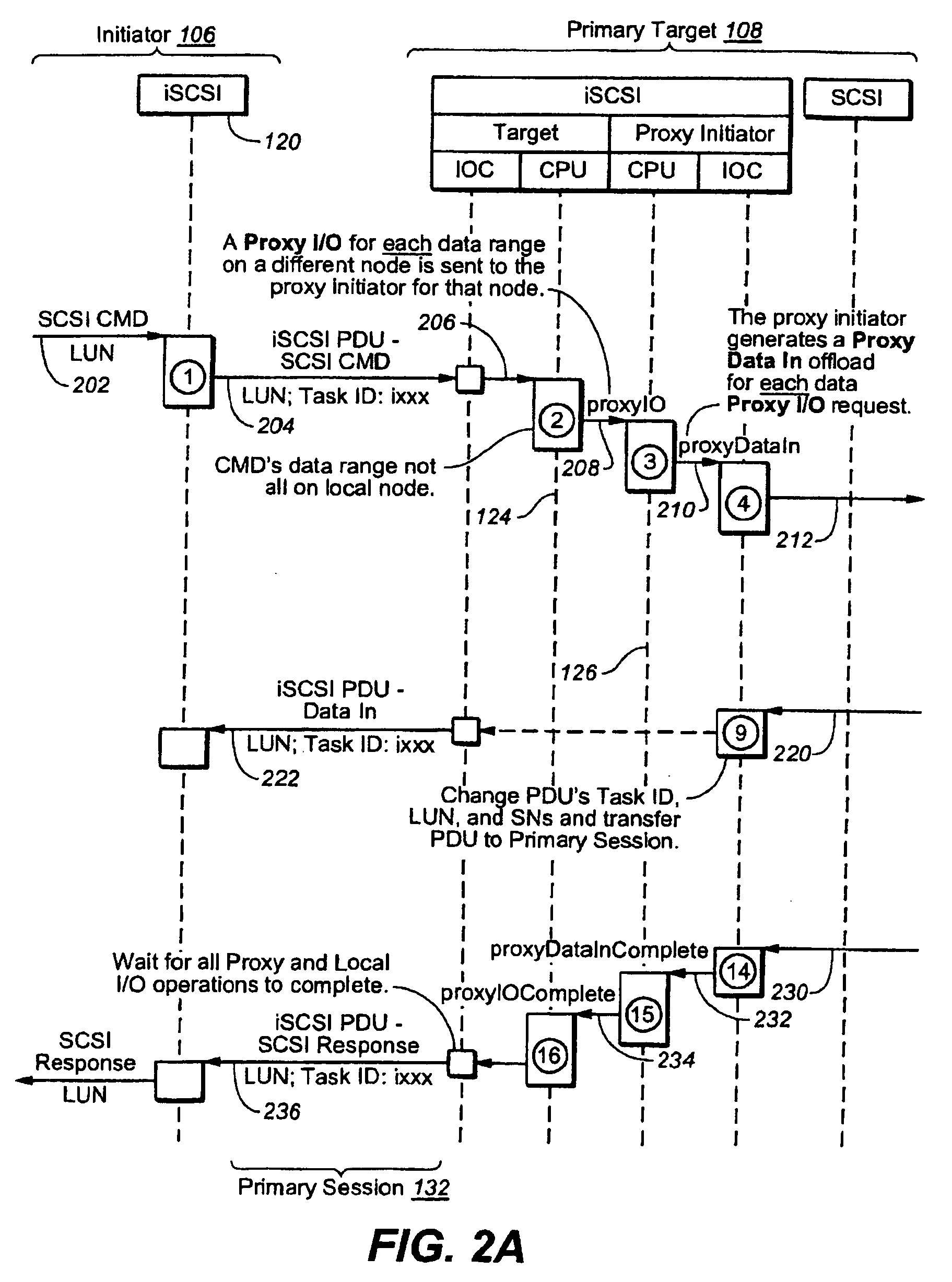
Accelerating internet small computer system interface (iSCSI) proxy input/output (I/O)
The present invention is a method for accelerating proxy Input / Output (proxy I / O). The method includes the step of receiving a command at a primary target storage system. The primary target storage system may be part of a clustered storage array. The command may be a command which was transmitted by an initiator system via a storage area network, and may include a request for data. The method further includes the step of forwarding the command to a session layer of the primary target storage system. Further, when a virtualization layer of the primary target storage system determines that a portion of the data requested in the data request is not stored by the primary target storage system, but is stored by a proxy target storage system included in the plurality of storage systems, the method further includes providing a proxyIO request to a proxy initiator of the primary target storage system. Further, the method may further include, based on the proxyIO request, generating a proxyDataIn request and providing the proxyDataIn request to an I / O controller for the primary target storage system.
Owner:NETWORK APPLIANCE INC
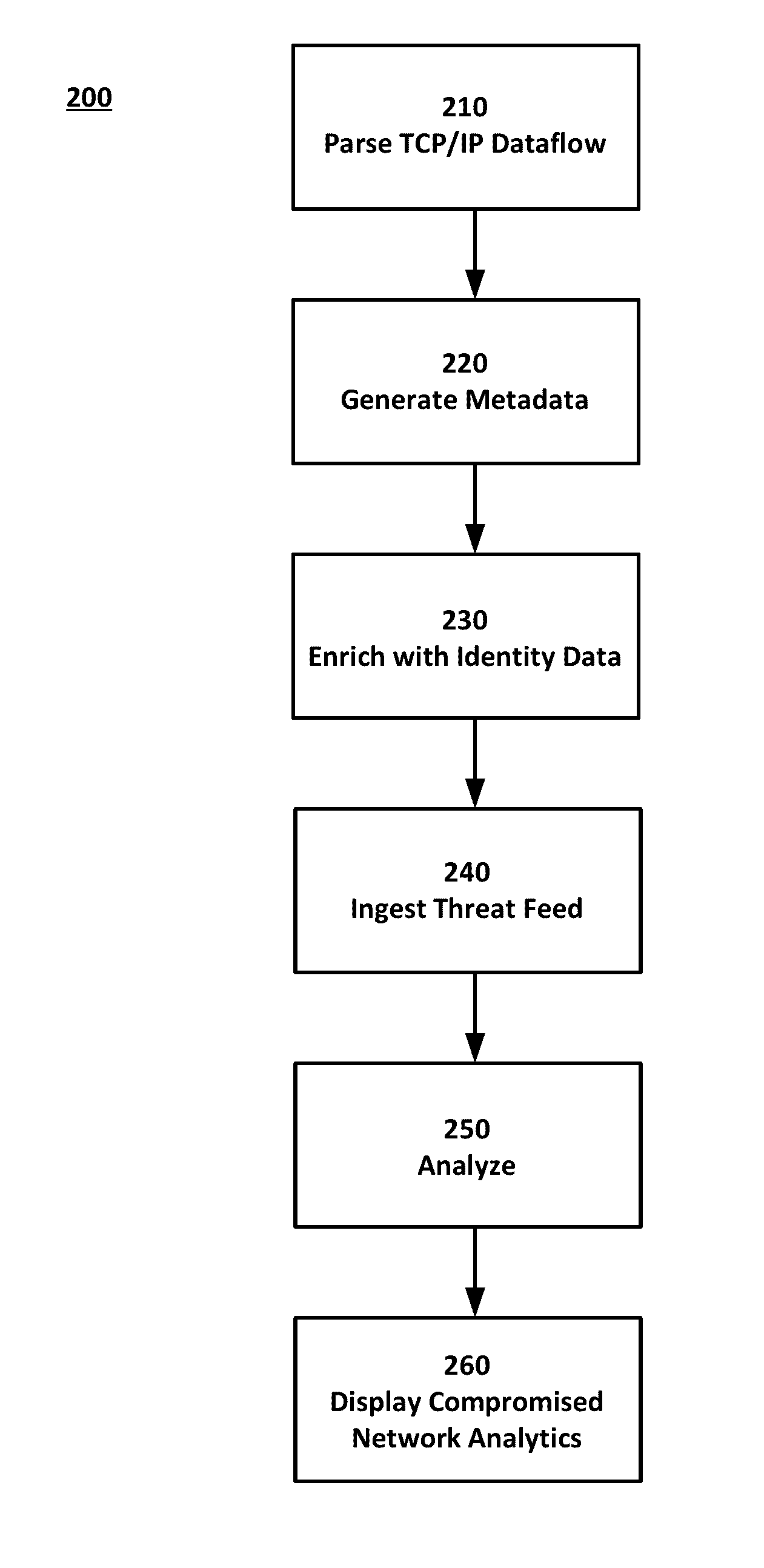
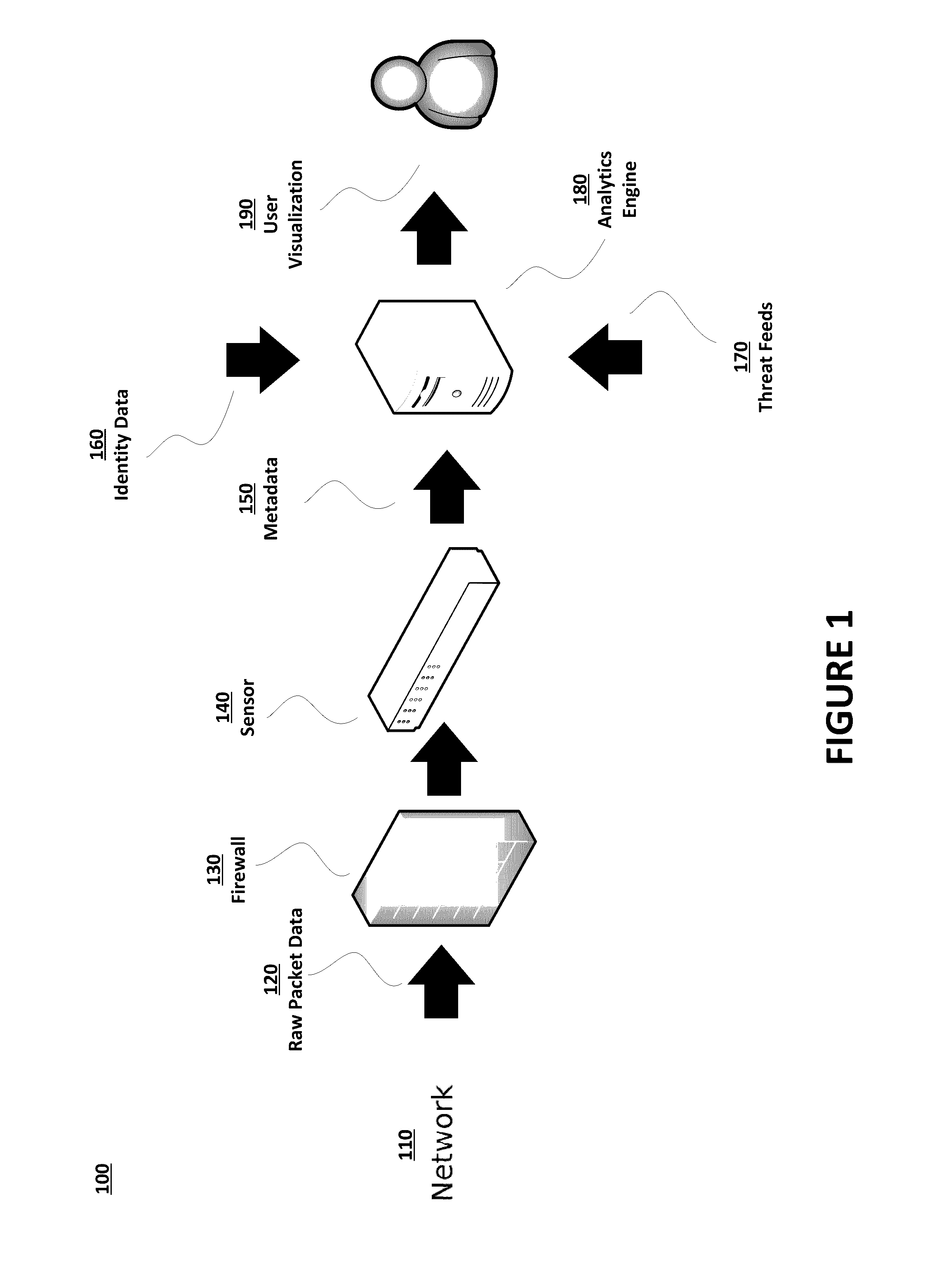
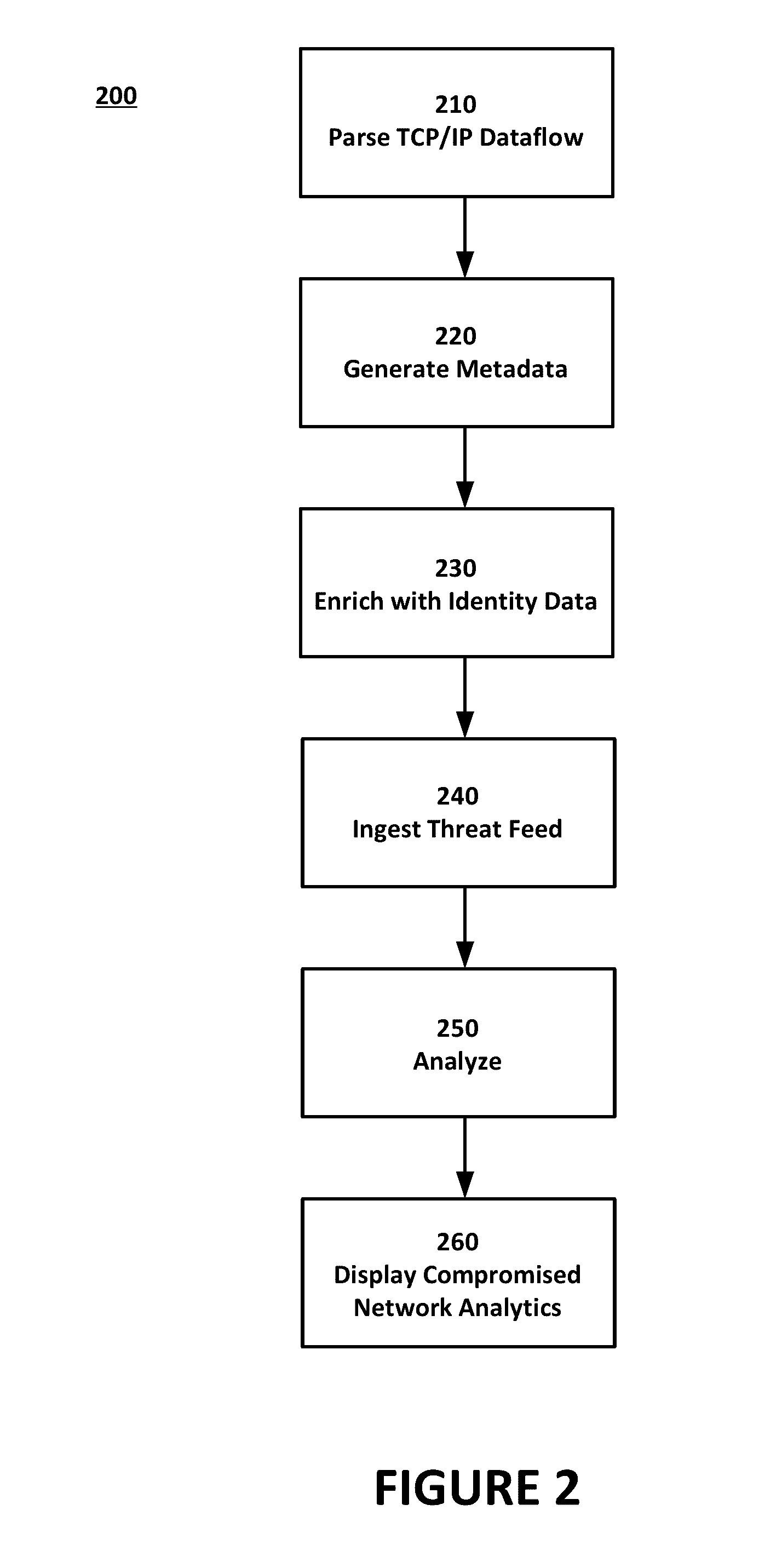
Identifying network intrusions and analytical insight into the same
InactiveUS20160381049A1Digital data information retrievalMemory loss protectionWeb threatTraffic capacity
The present invention collects raw packet data related to network traffic flow over the course of time. By combining metadata from the application layer and / or session layer with user and device identity data as well as indicators of a network threat that are received from threat feeds, information concerning pre-existing or post-mortem network incidents may be identified. Based on the nature of a particular network threat and a collective history of network traffic flow over the course of time, analytics may allow for identification of compromised users, files, and network nodes. Such an identification may in turn allow for removal, rehabilitation, or further investigation.
Owner:SS8
Method and system for fast setup of group voice over IP communications
ActiveUS7529200B2Faster setup-timeReduce signaling overheadSpecial service provision for substationMultiplex system selection arrangementsTransport layerVoice over internet protocol voip
A method and system for fast setup of group Voice over Internet Protocol (VoIP) communications. The method and system provide a lower VoIP signaling overhead and a faster setup-time of group calls such as N-way audio and / or audio-video conference calls. Multi-party VoIP connections are quickly set-up over one or more virtual communications channels established between plural network devices using a session layer application, one or more group transport layer ports and a broadcast destination network address.
Owner:ZHIGU HLDG
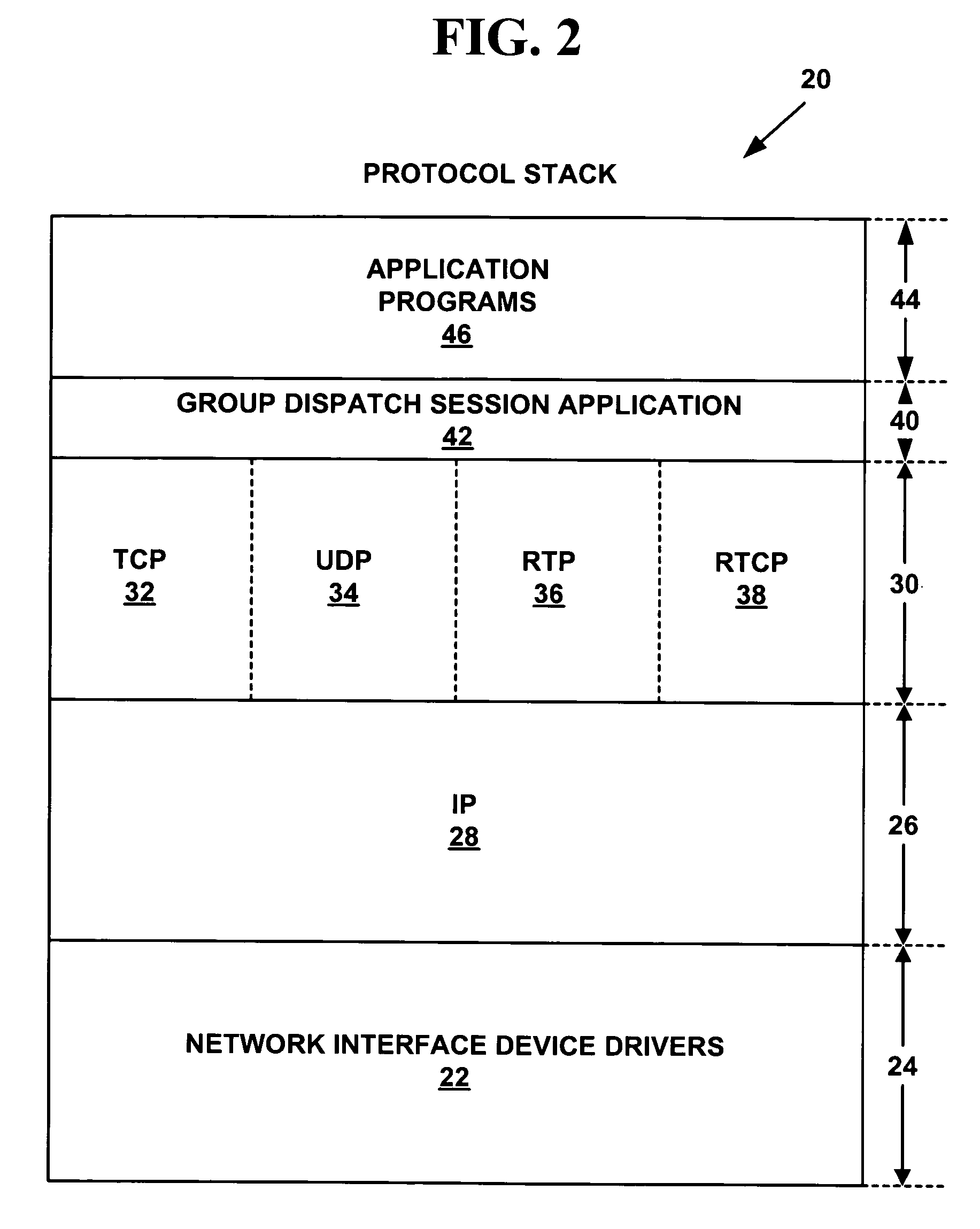
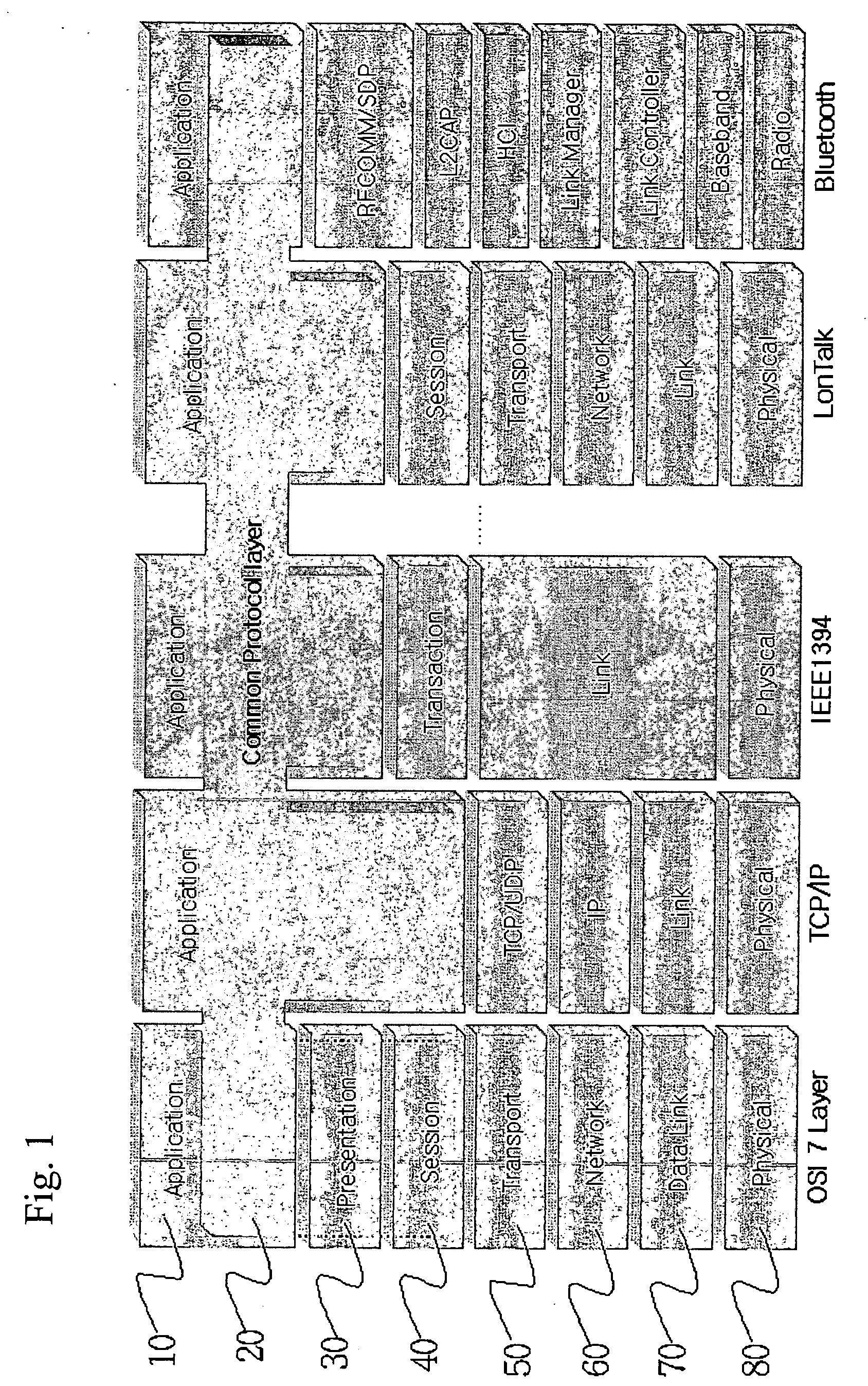
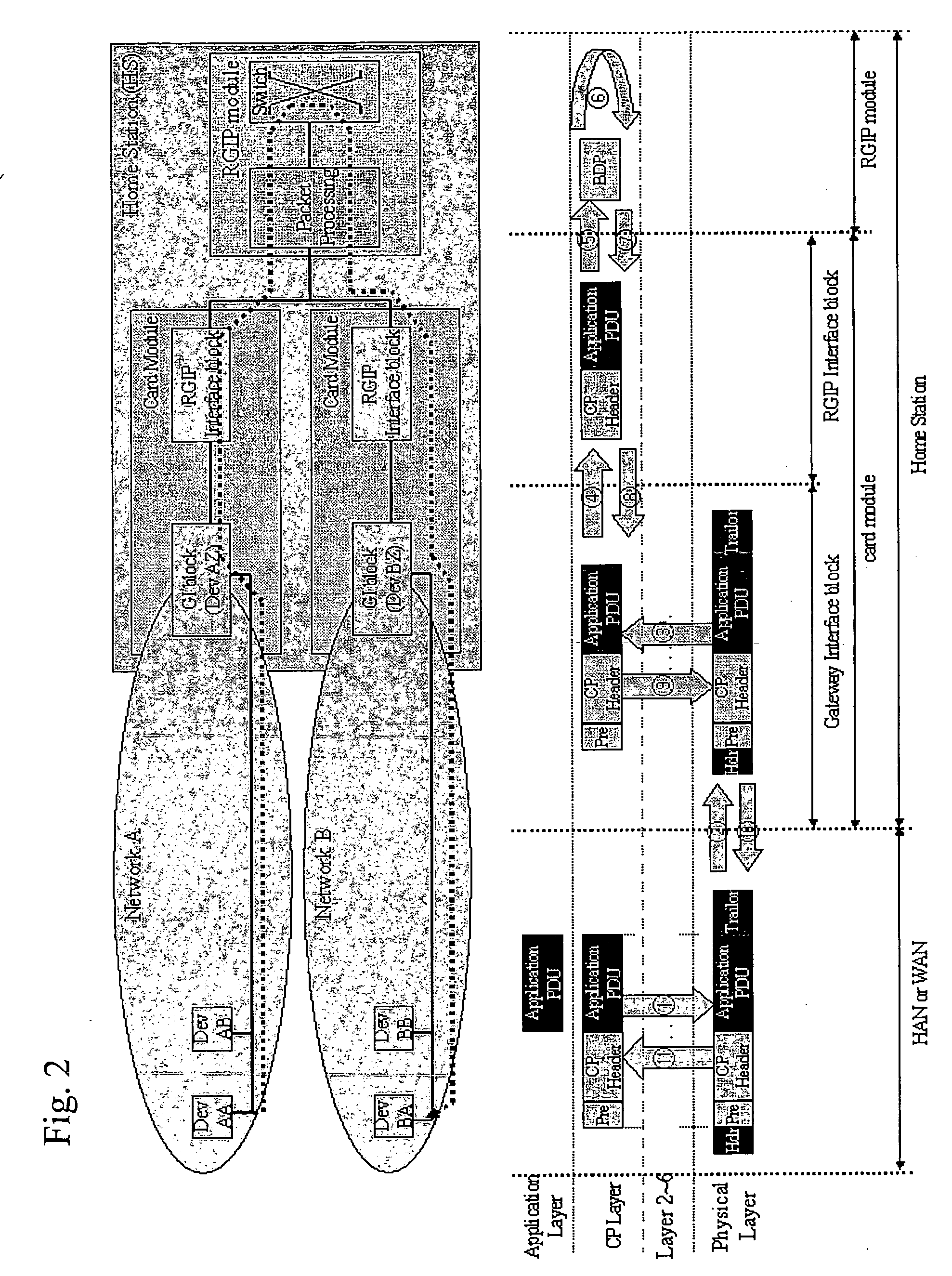
Common protocol layer architecture and methods for transmitting data between different network protocols and a common protocol packet
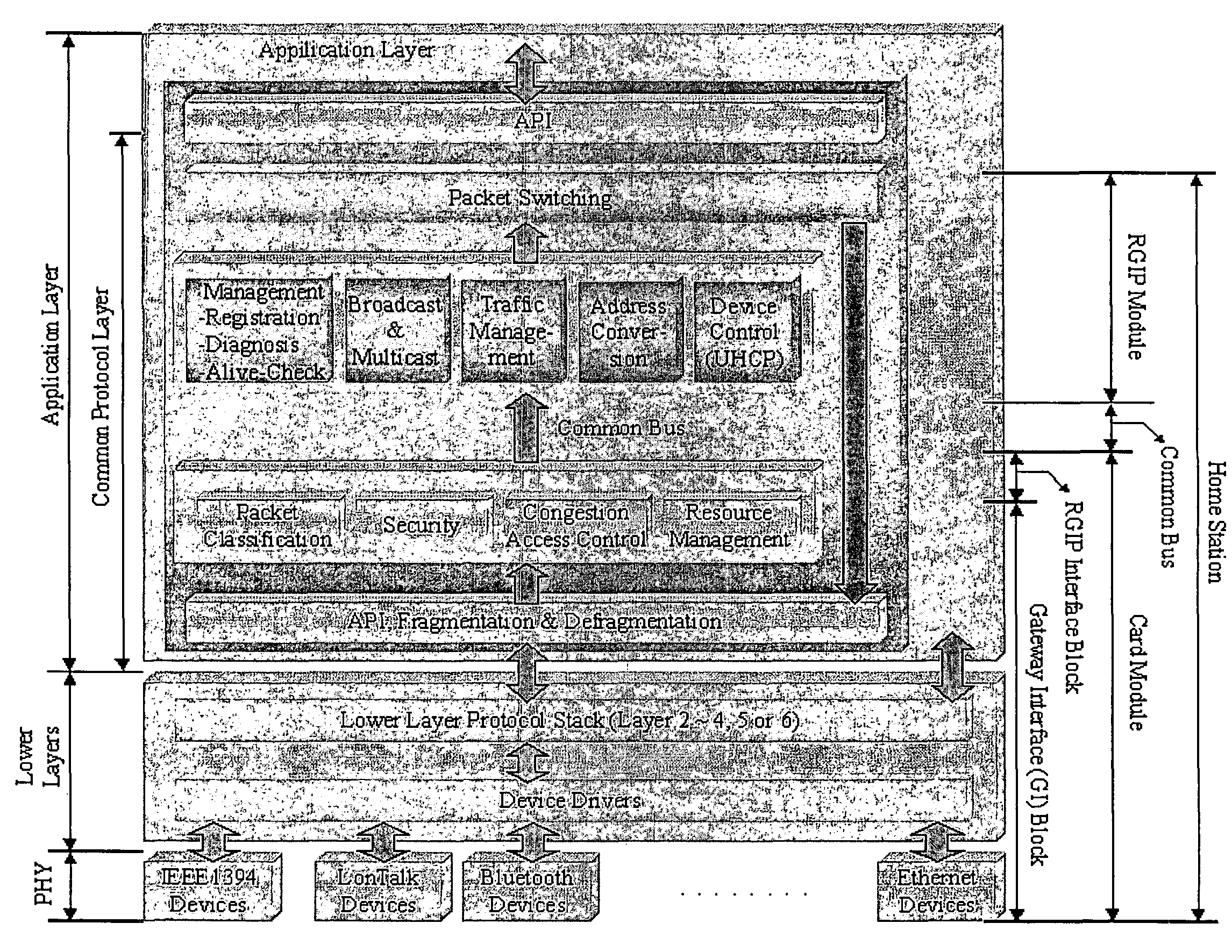
ActiveUS20060053229A1Enhance interestMultiple digital computer combinationsWireless network protocolsNetworking protocolTransport layer
The present invention provides common protocol architecture and methods for transmitting data between different network protocols and a common protocol packet. The common protocol architecture comprises an application layer; a common protocol layer positioned under the application layer, the common protocol layer enabling data communications between the different protocols; a presentation layer positioned under the common protocol layer; a session layer positioned under the presentation layer; a transport layer positioned under the session layer; a network layer positioned under the transport layer; a data link layer positioned under the network layer; and a physical layer positioned under the data link layer. The common protocol packet comprises a common protocol header with information about a packet and a payload with the contents of data. By designing the common protocol layer and the common protocol packet accepting various. protocols simultaneously, the present invention can improve compatibility between different protocols.
Owner:KOREA ELECTRONICS TECH INST
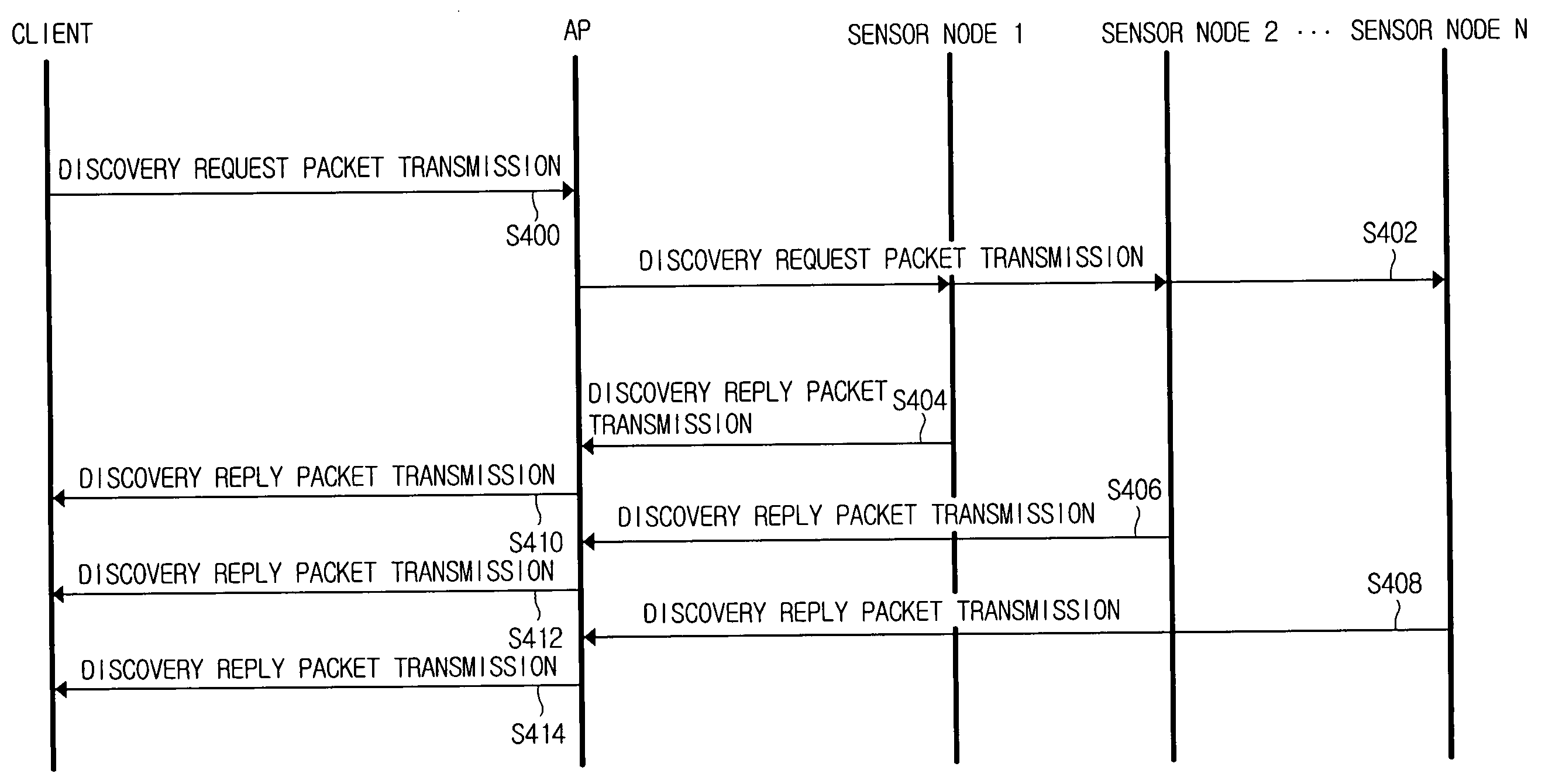
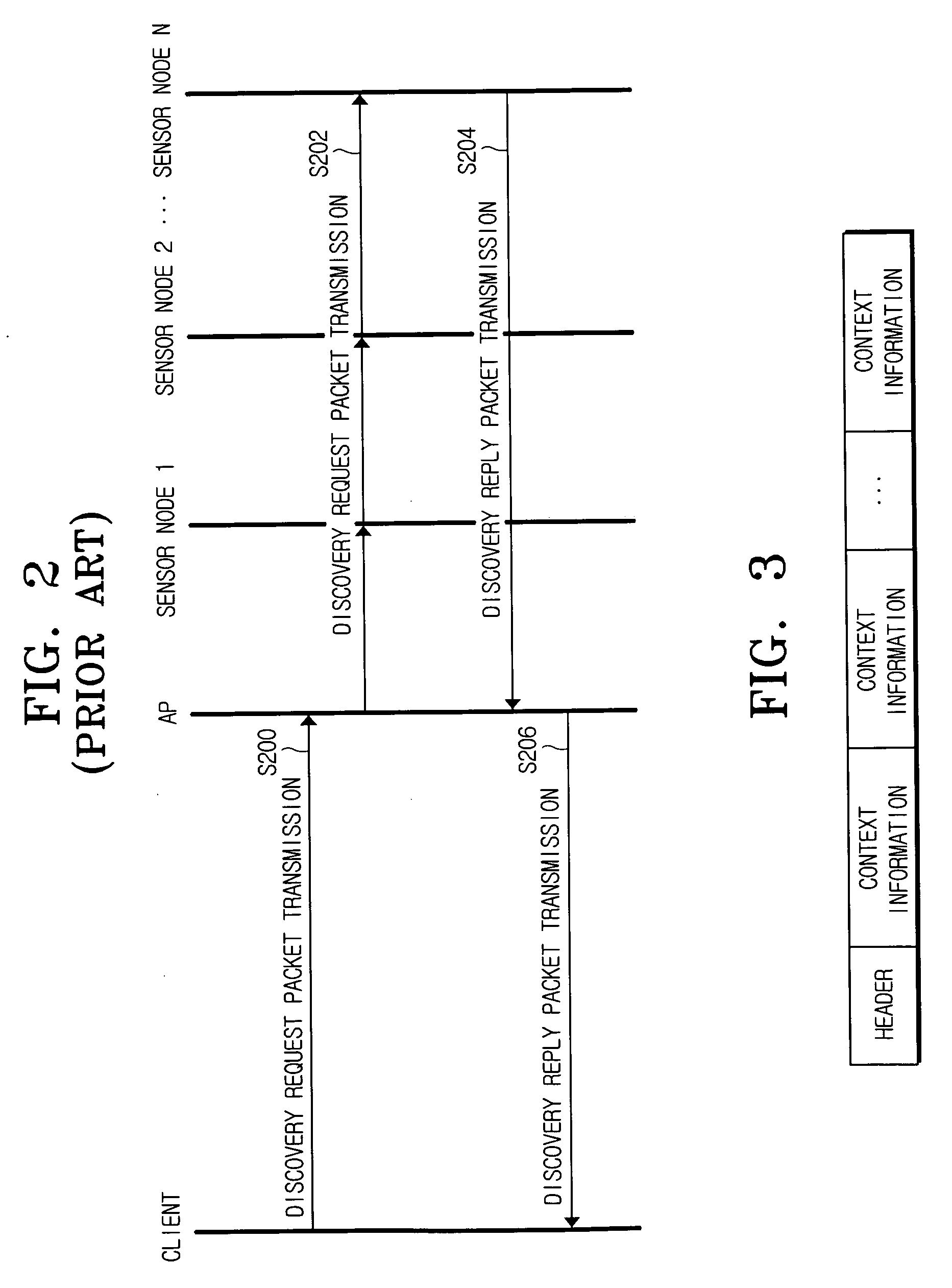
Method for discovery reply packet transmission in communication network
InactiveUS20060106753A1Ratio deterioratesFast informationNetwork topologiesData switching by path configurationCommunications systemSensor node
A method for determining a transmission time of collected context information at a sensor node in a communication system that includes a client, at least one sensor node collecting context information, and an access point (AP) forwarding the context information received from the sensor node to the client. The communication system operates in a session layer of protocol layers of open systems interconnection (OSI). The sensor node calculates a transmission period in which the collected context information is transmitted, and randomly determines a transmission time at which the context information is transmitted within the calculated transmission period. Since the collected context information is transmitted at the transmission time randomly determined by the sensor node, the load on the AP can be balanced.
Owner:SAMSUNG ELECTRO MECHANICS CO LTD
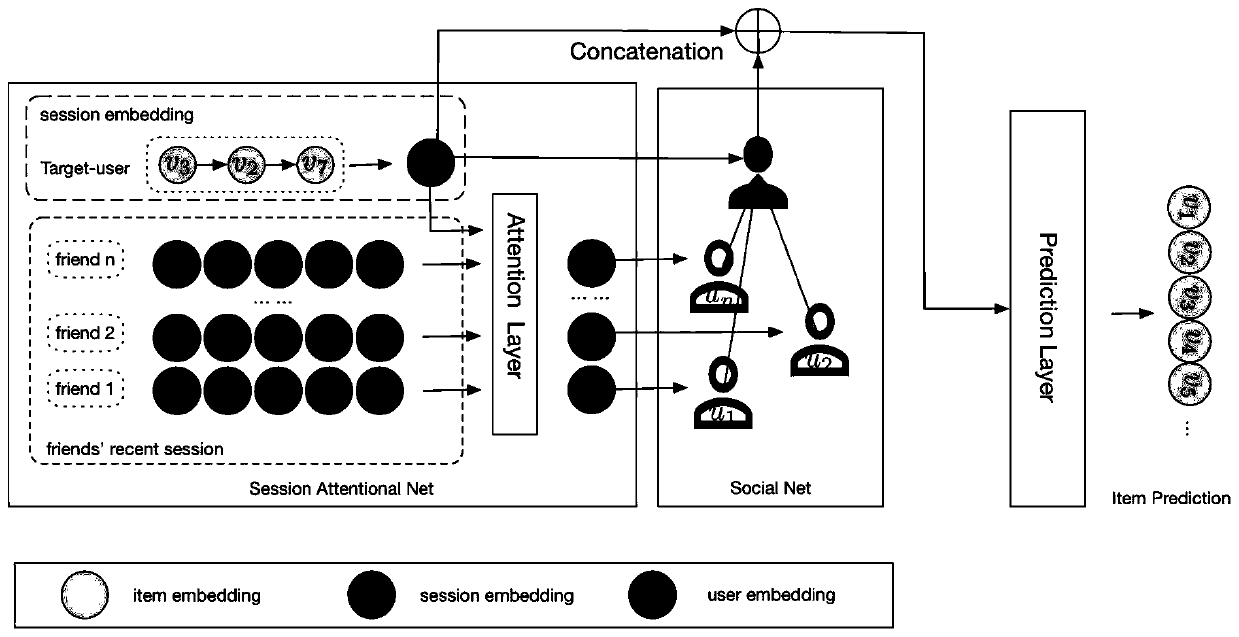
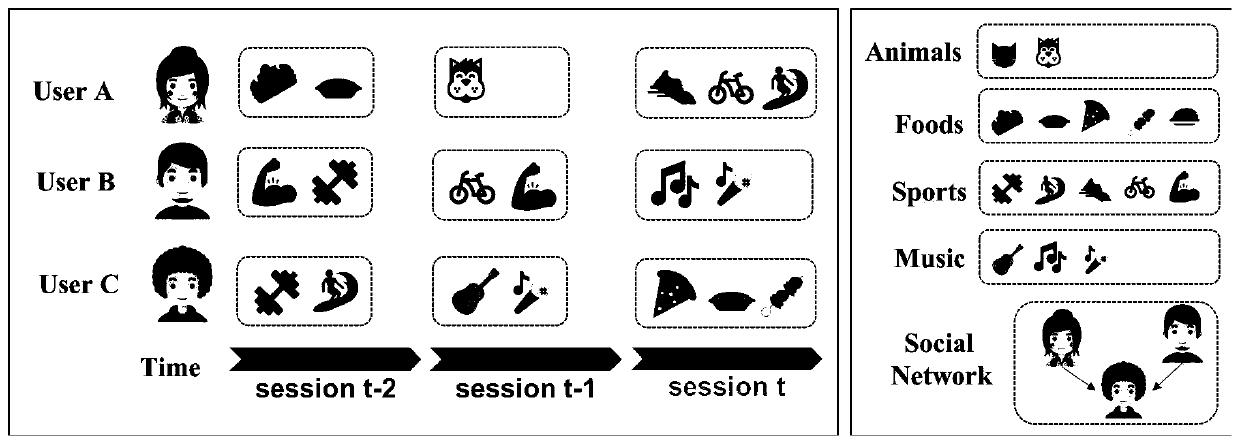
Session social recommendation method based on context neighborhood modeling
ActiveCN111222054AIncrease influenceDigital data information retrievalCharacter and pattern recognitionNeighbor relationData mining
The invention discloses a session social recommendation method based on context neighborhood modeling. According to the method, based on historical interaction data and social network information of agiven target user, the next item most likely to be interacted by the target user is found out. According to the method, firstly, user interests are modeled, and then the representation of each friendin a social network corresponding to a target user is obtained by adopting a session-level attention mechanism. And the social influence of friends on the user is learned by using a social network. And finally, article recommendation is performed in combination with the social influence of friends on the target user and the interest of the target user. The method overcomes the defects in the existing method that the interests between the target user and friends are ignored and only partially coincide. Therefore, compared with an existing method, the recommendation effect implemented by the method is remarkably improved.
Owner:CHINA JILIANG UNIV
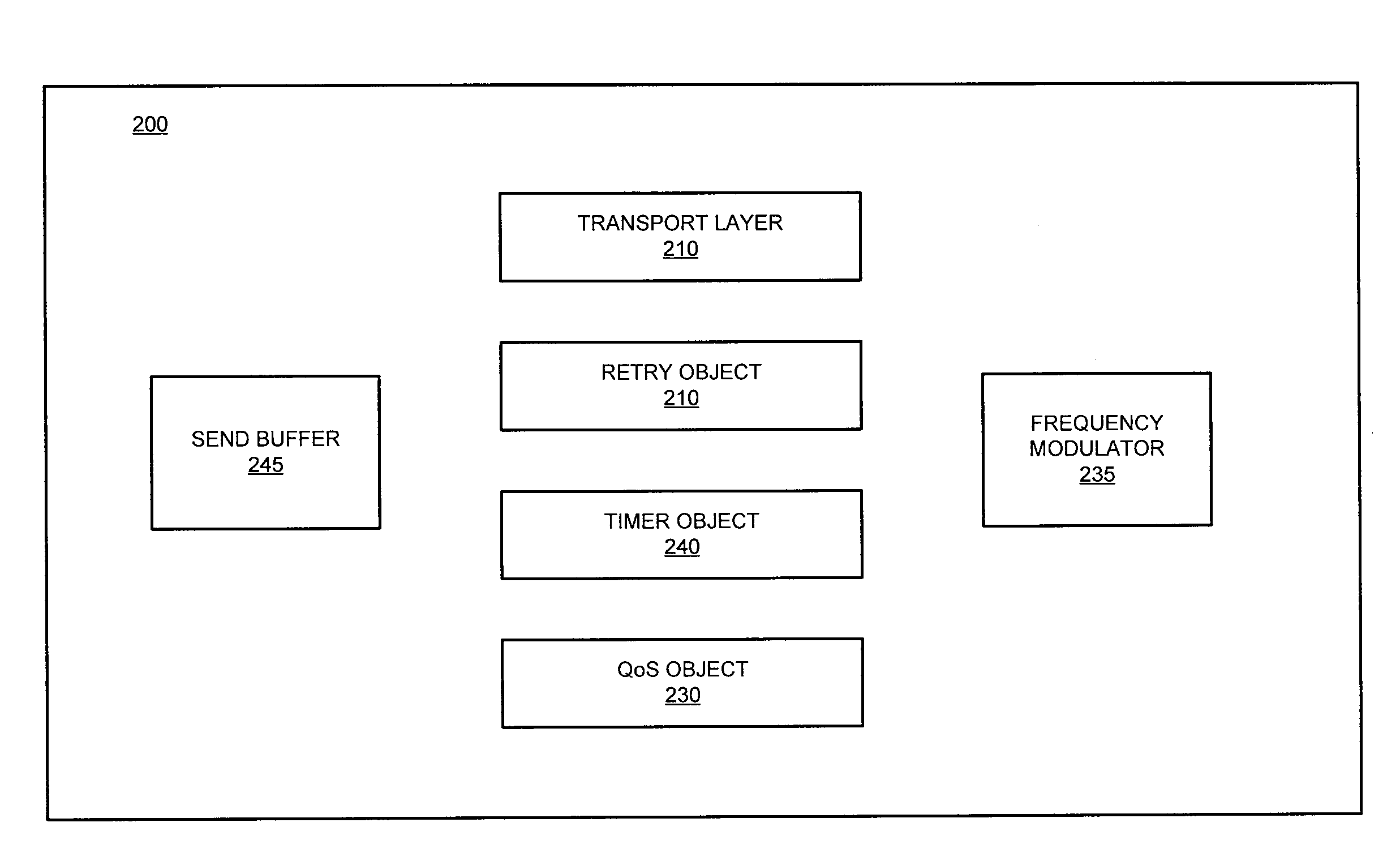
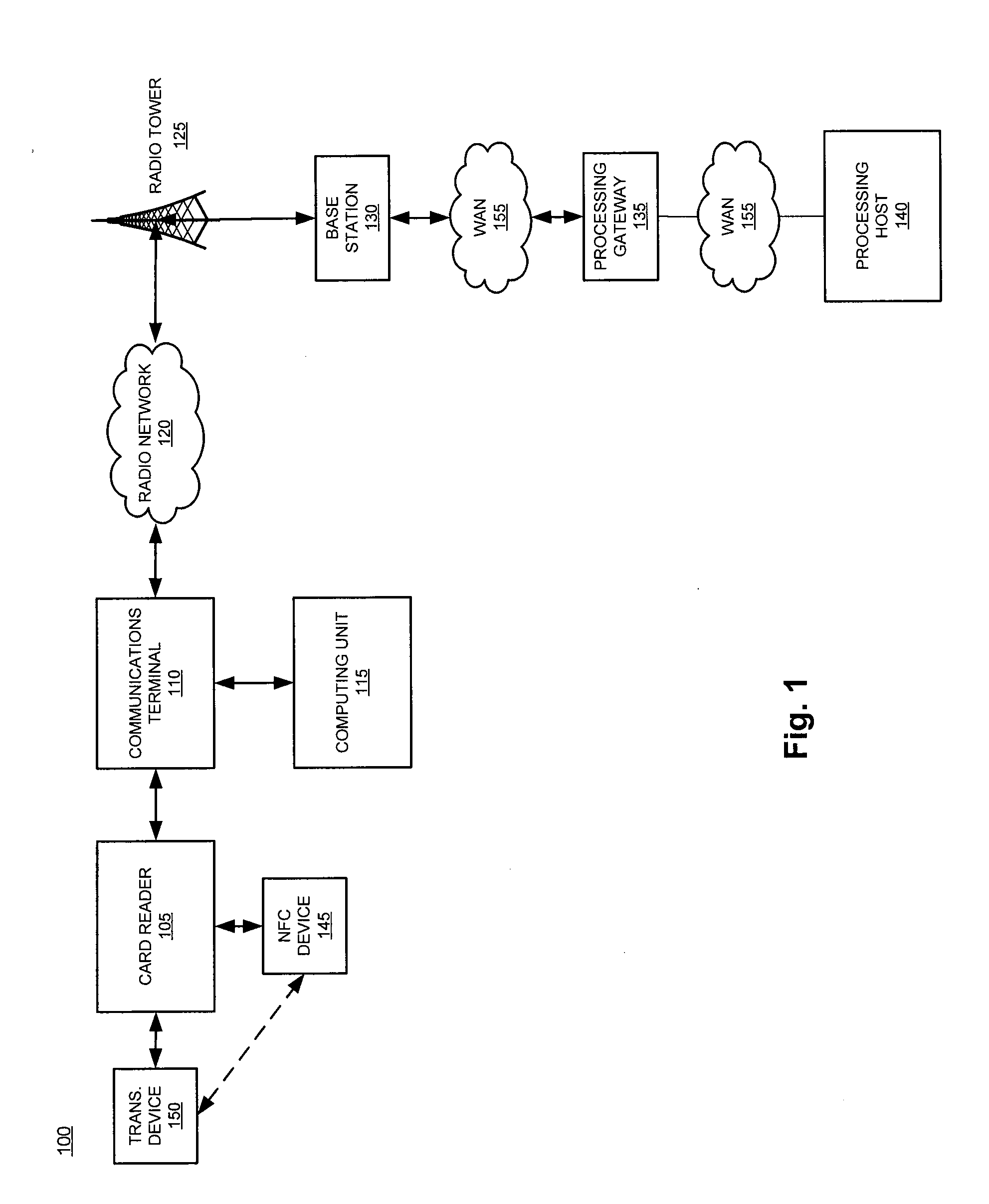
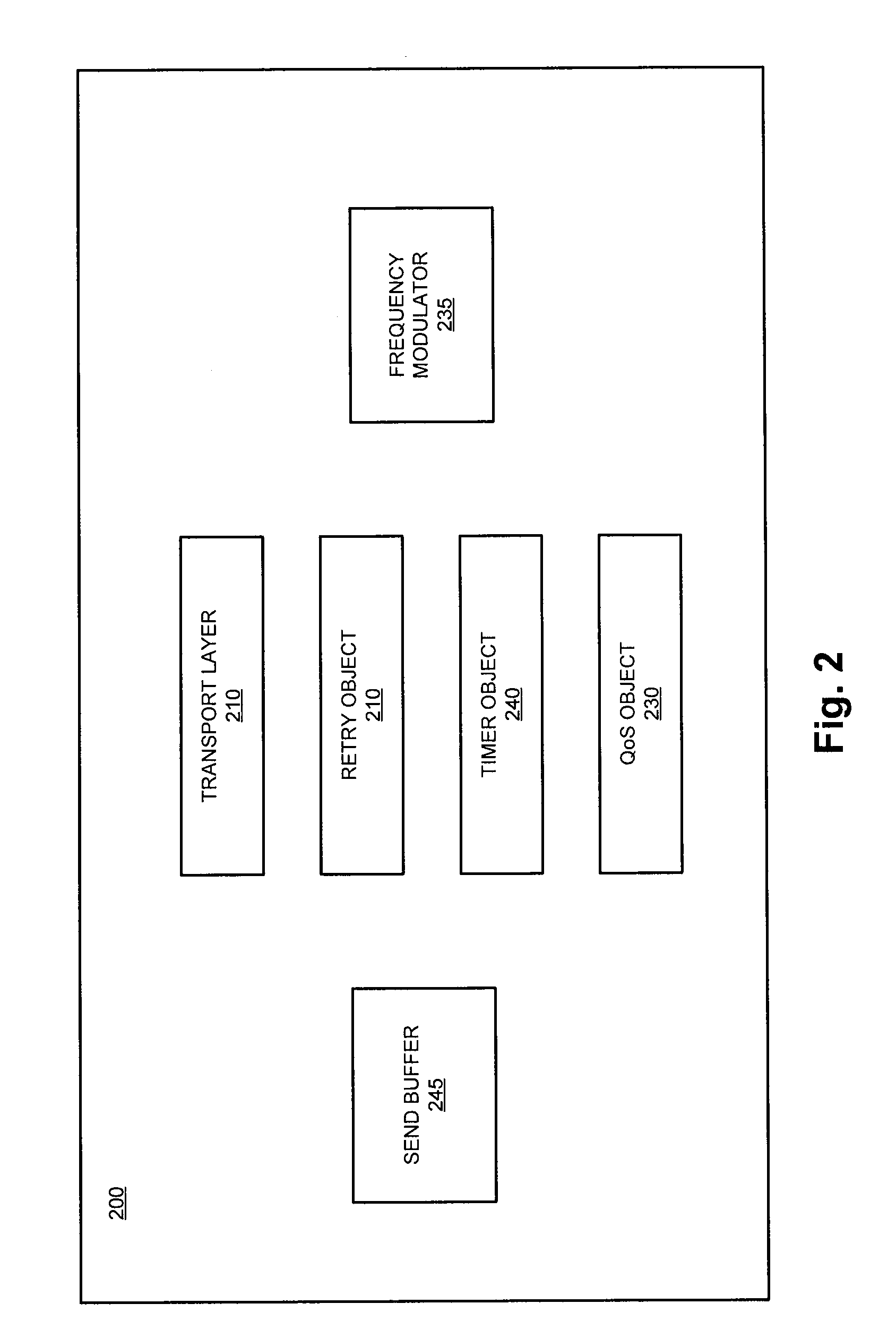
System and method for dynamic configuration of session layer retry logic based on signal quality
The present invention involves the dynamic modification of network connection parameters based on signal conditions, and specifically, based on signal Quality of Service (QoS) measurements. Specifically, the disclosed systems and methods enable a remote communications terminal to best ensure a reliable wireless connection to a transaction-processing gateway in order to send and receive data packets relating to merchant transactions. The communications terminal is configurable, allowing a user to define threshold values that serve as triggering events for modifying and / or implementing a change to policies governing network connection attempts.
Owner:APRIVA
Method for handover between heterogeneous communications networks
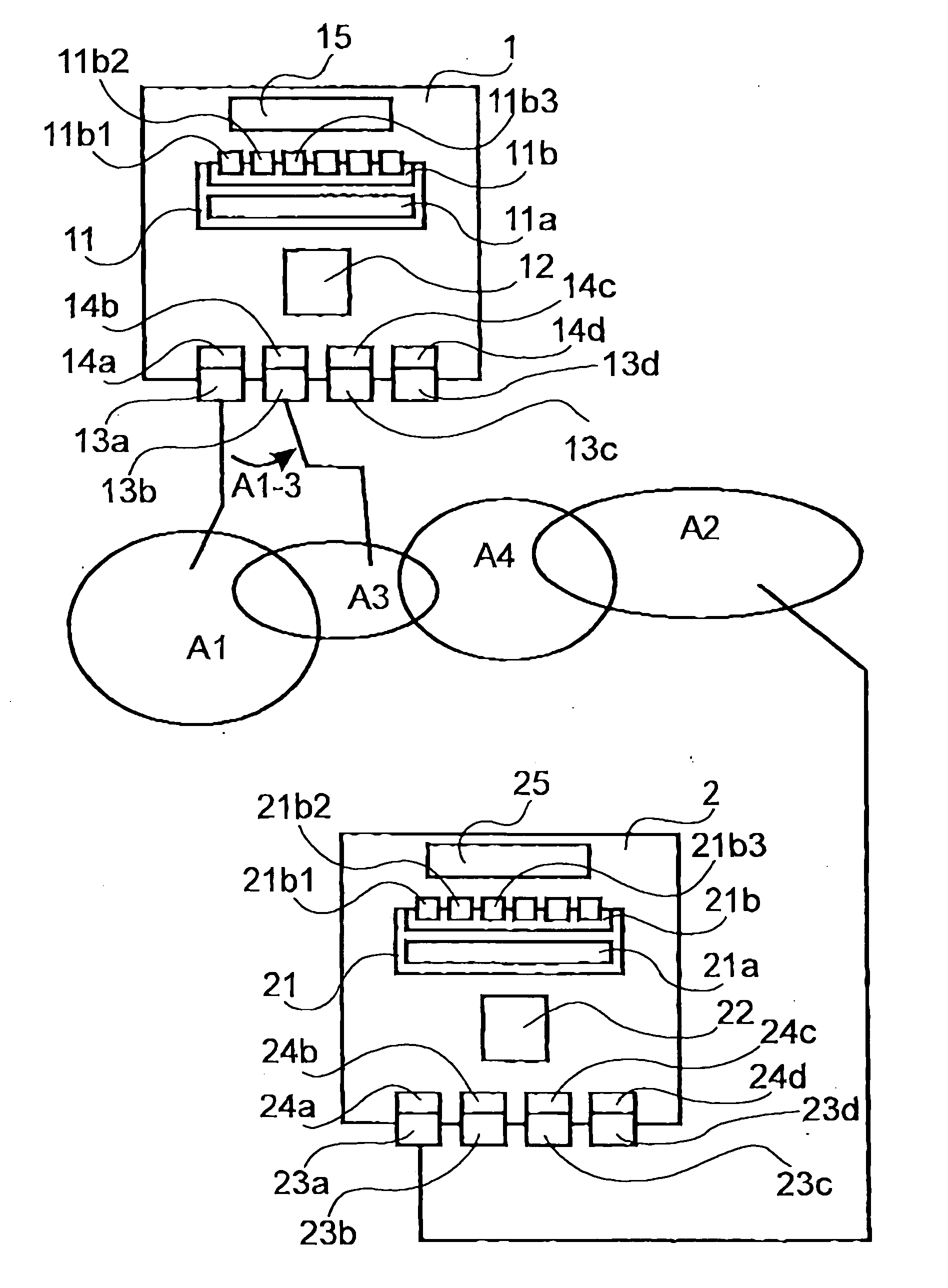
ActiveUS20040202128A1Quick changeEfficient compressionMultiple digital computer combinationsWireless network protocolsHandoverProtocol stack
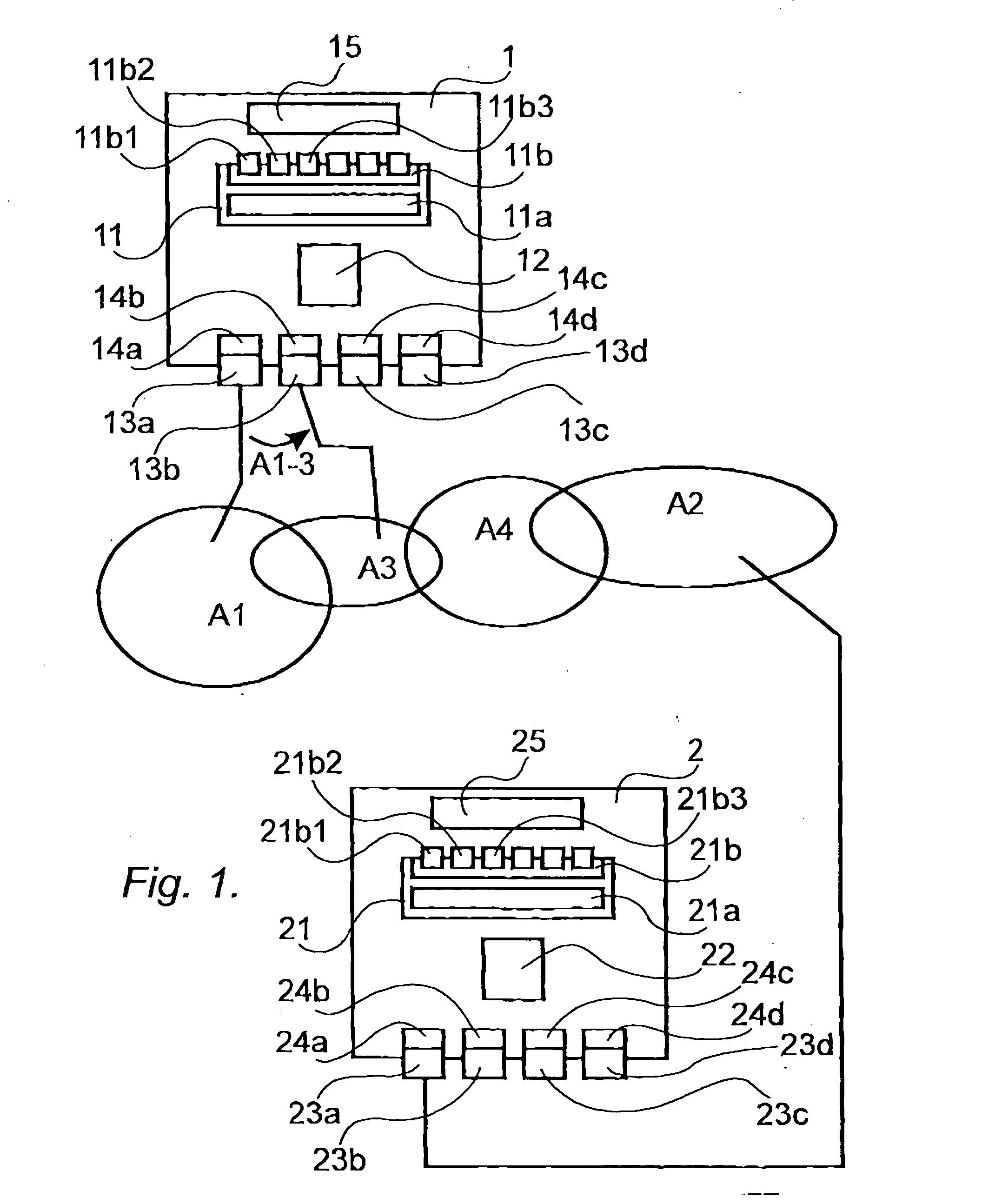
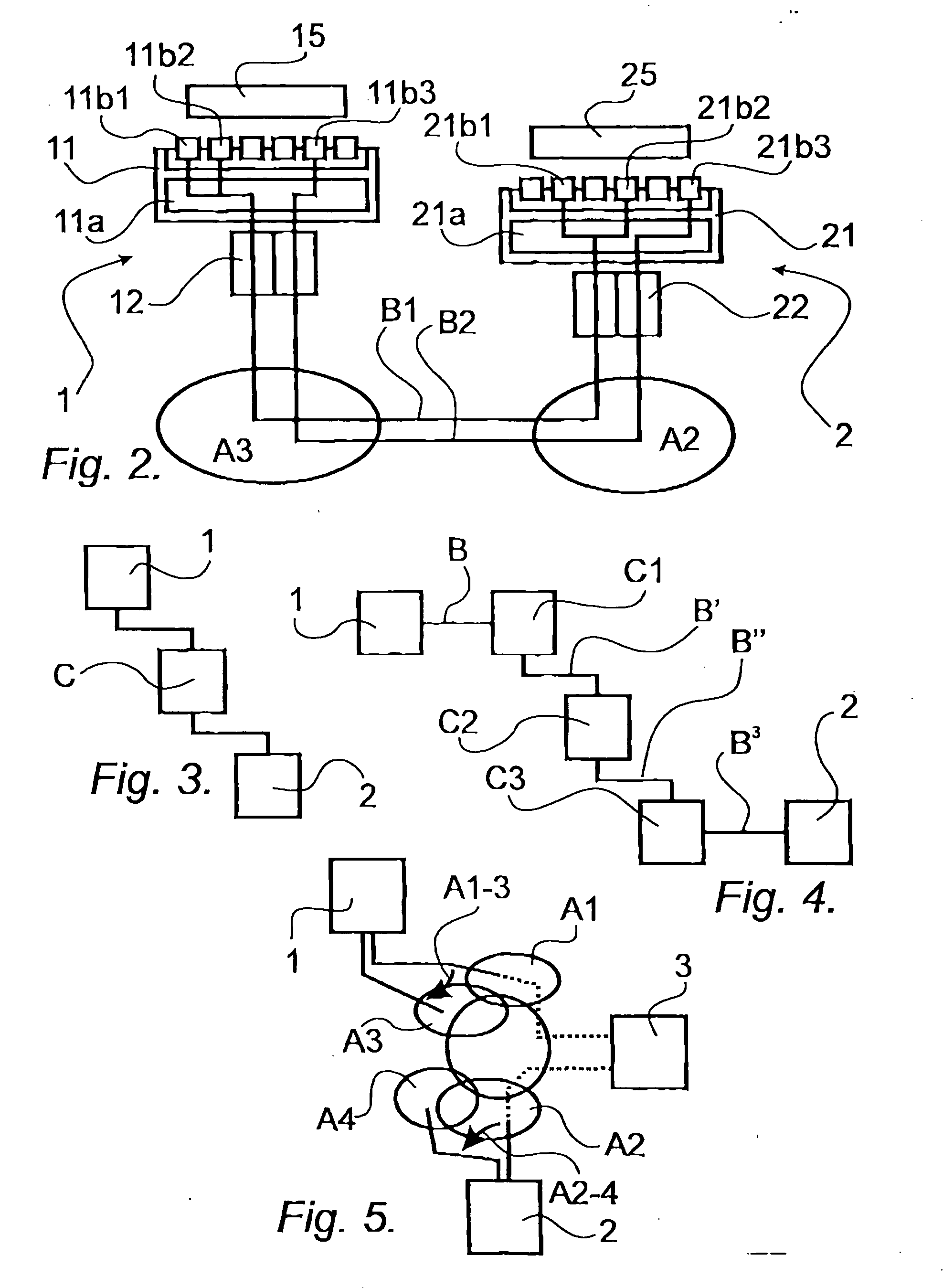
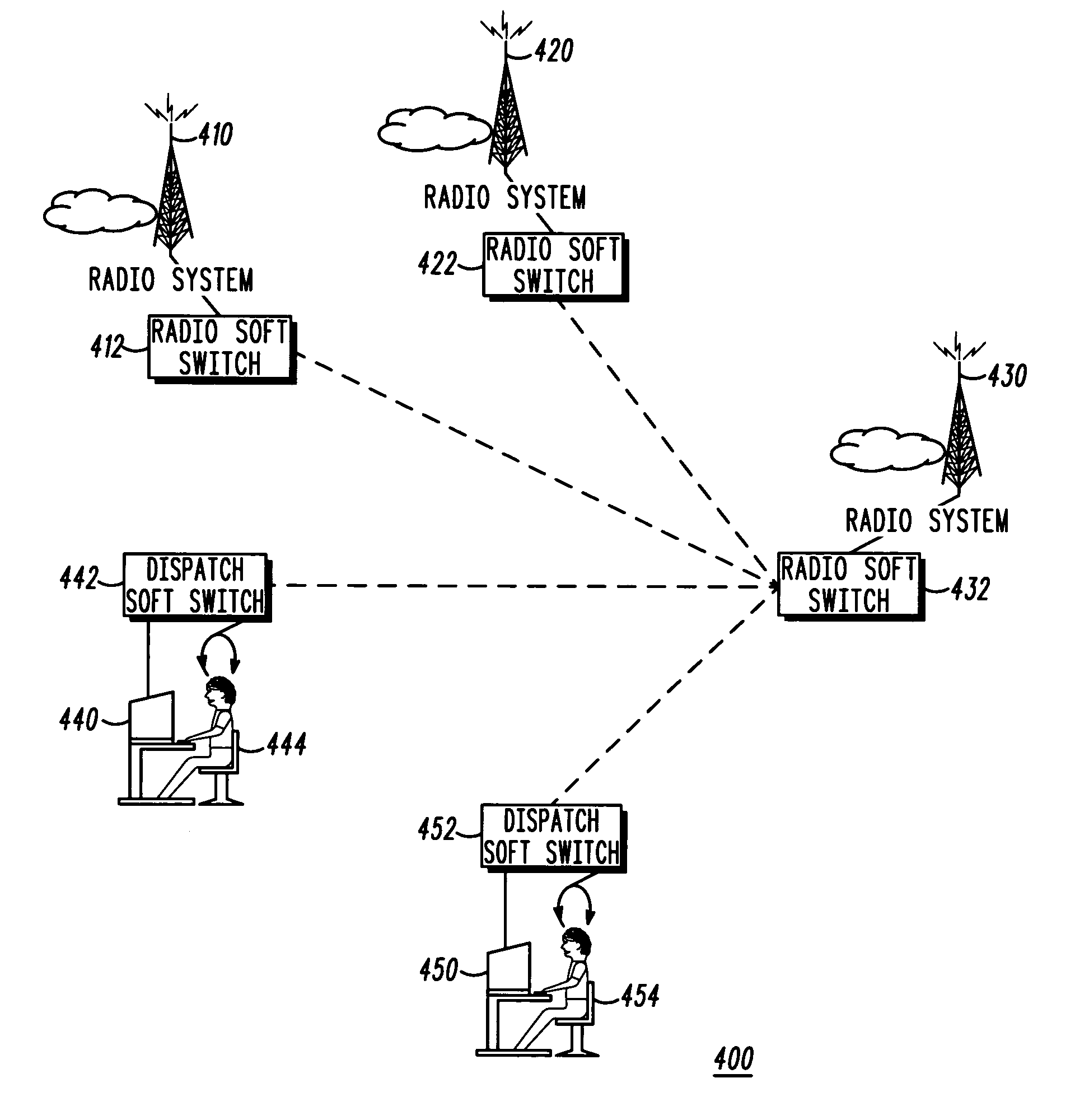
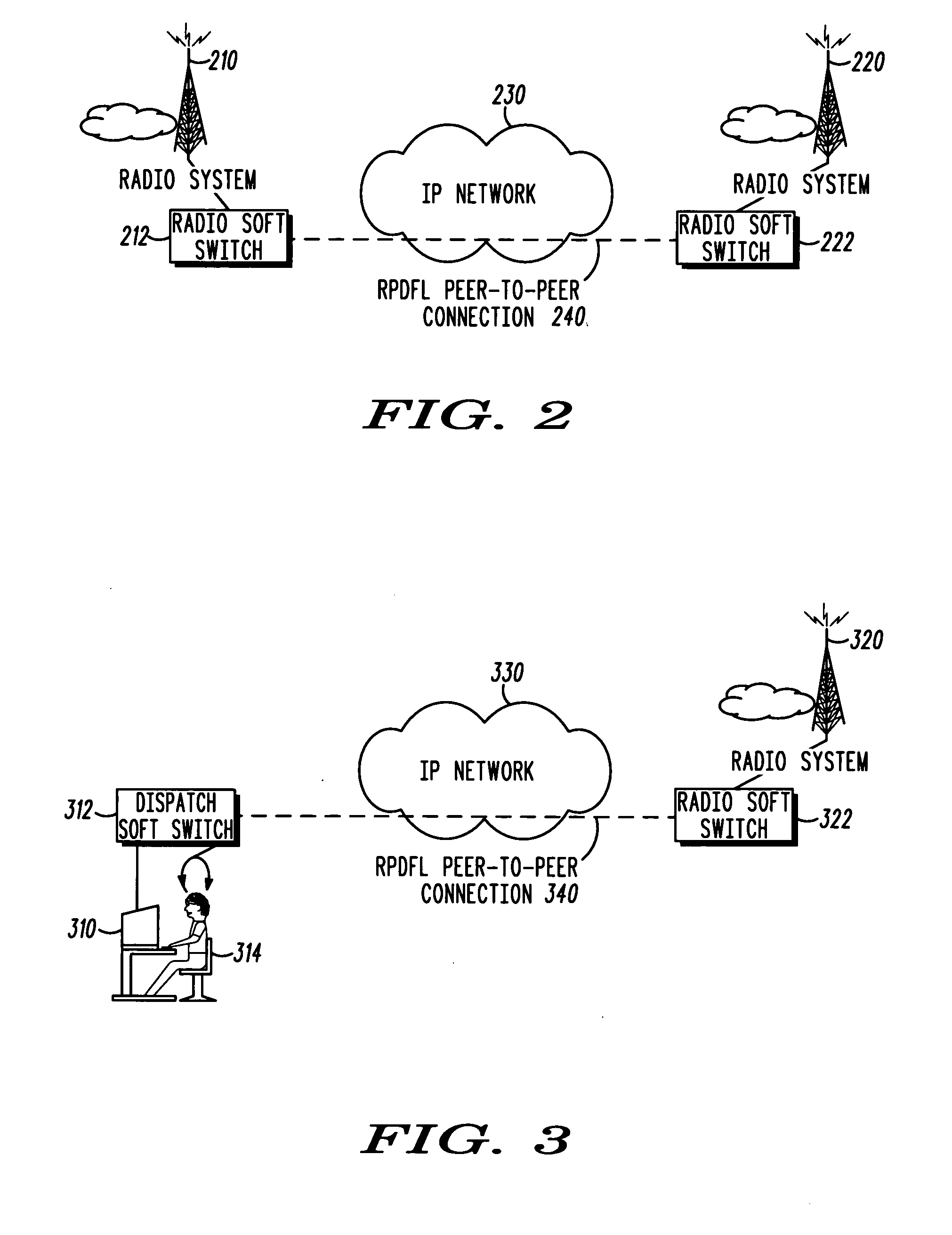
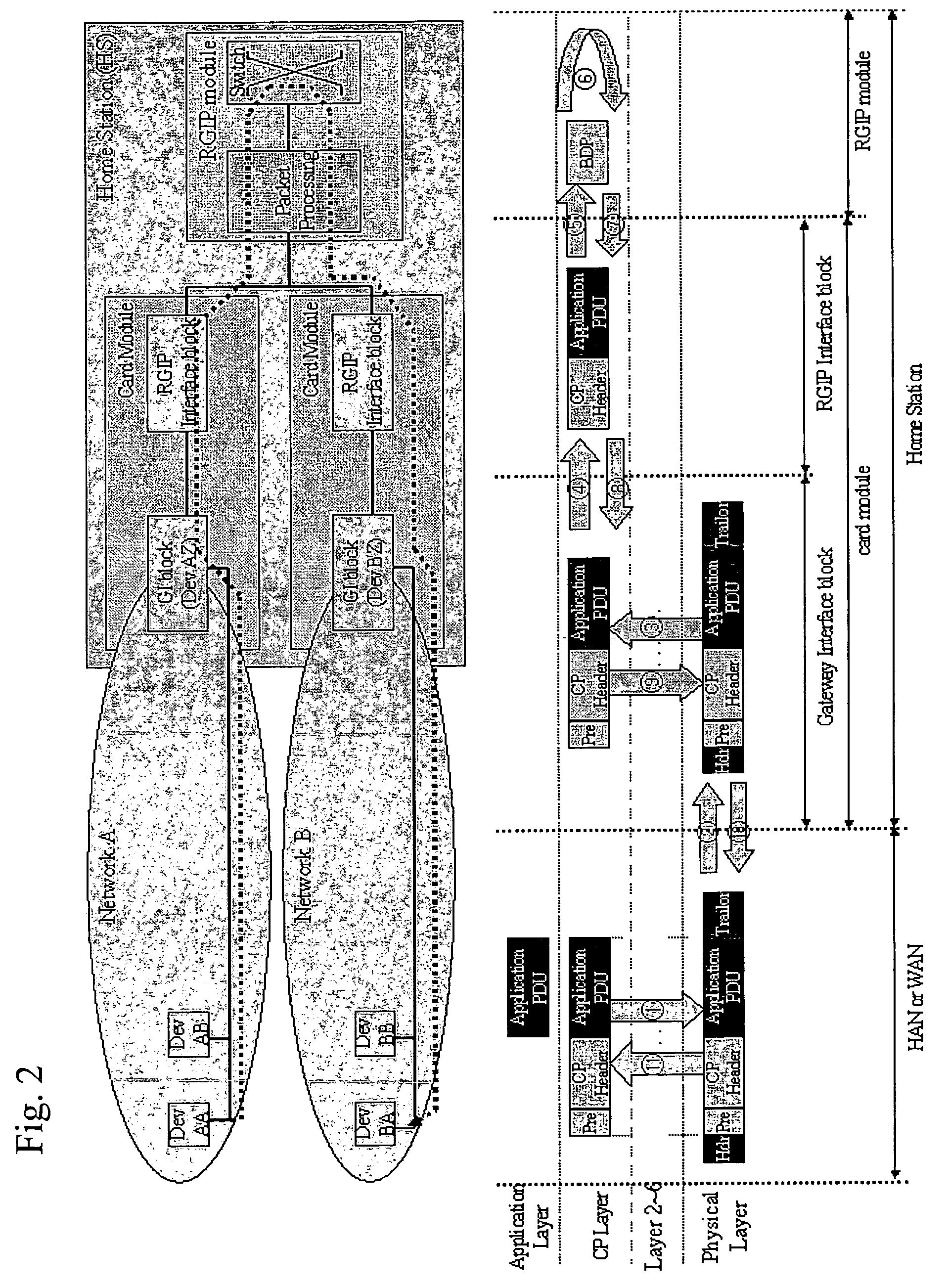
The present invention relates to a method, computer program products, and a computer readable medium, for maintaining communication between a first mobile unit (1) and a second unit (2), where said first unit (1) communicates via a first communications network (A1) and the second unit (2) communicates via a second communications network (A2). The first unit (1) includes a first protocol stack (12) and the second unit (2) includes a second protocol stack (22). The first unit (1) includes a first session layer (11) which is adapted to function as an interface between the first protocol stack (12) and first software components (15) acting within the first unit (1). Similarly, the second unit (2) includes a second session layer (21) which is adapted to function as an interface between the second protocol stack (22) and second software components (25) acting within the second unit (2). The first unit (1) includes one or more first communications hardwares (133a, 13b, 13c, 13d) with associated drive routines (12a, 12b, 12c, 12d) adapted to different communications networks (A1, A2, A3, A4). When the first unit (1) switches (A1-3) from a first communications network (A1) to a third communications network (A3), the first session layer (11) functions to maintain communication by selecting first communications hardware (13b) and drive routine (14b) required for the third communications network (A3). The respective identities of the first and second units (1, 2) are maintained by the first and the second session layer (11, 21) and these identities are retained during switching of communications networks by the first unit (1).
Owner:BENETTON GROUP SPA +1
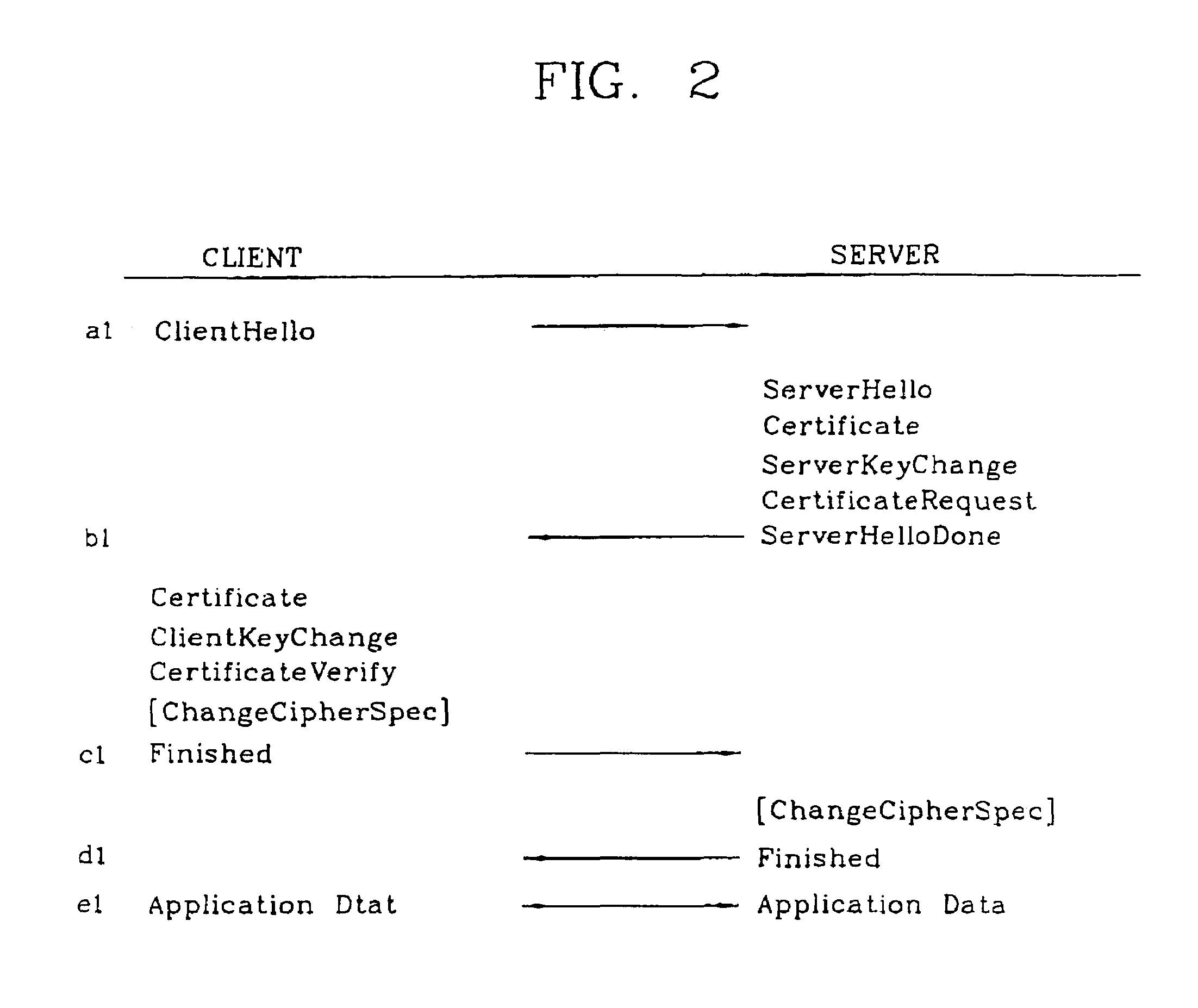
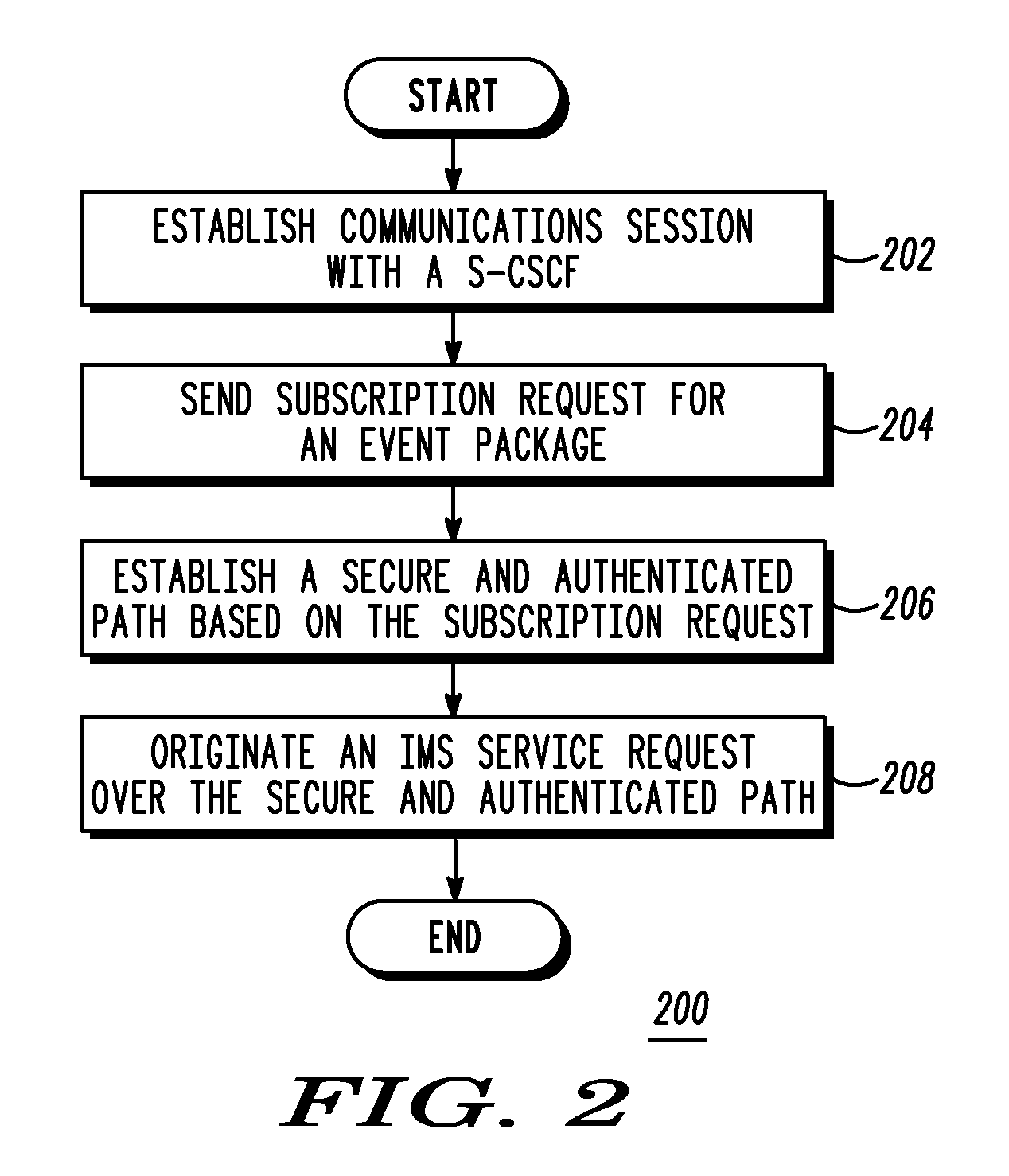
Pre-registration secure and authenticatedsession layer path establishment
InactiveUS20080092226A1Computer security arrangementsMultiple digital computer combinationsSession Initiation ProtocolSession control
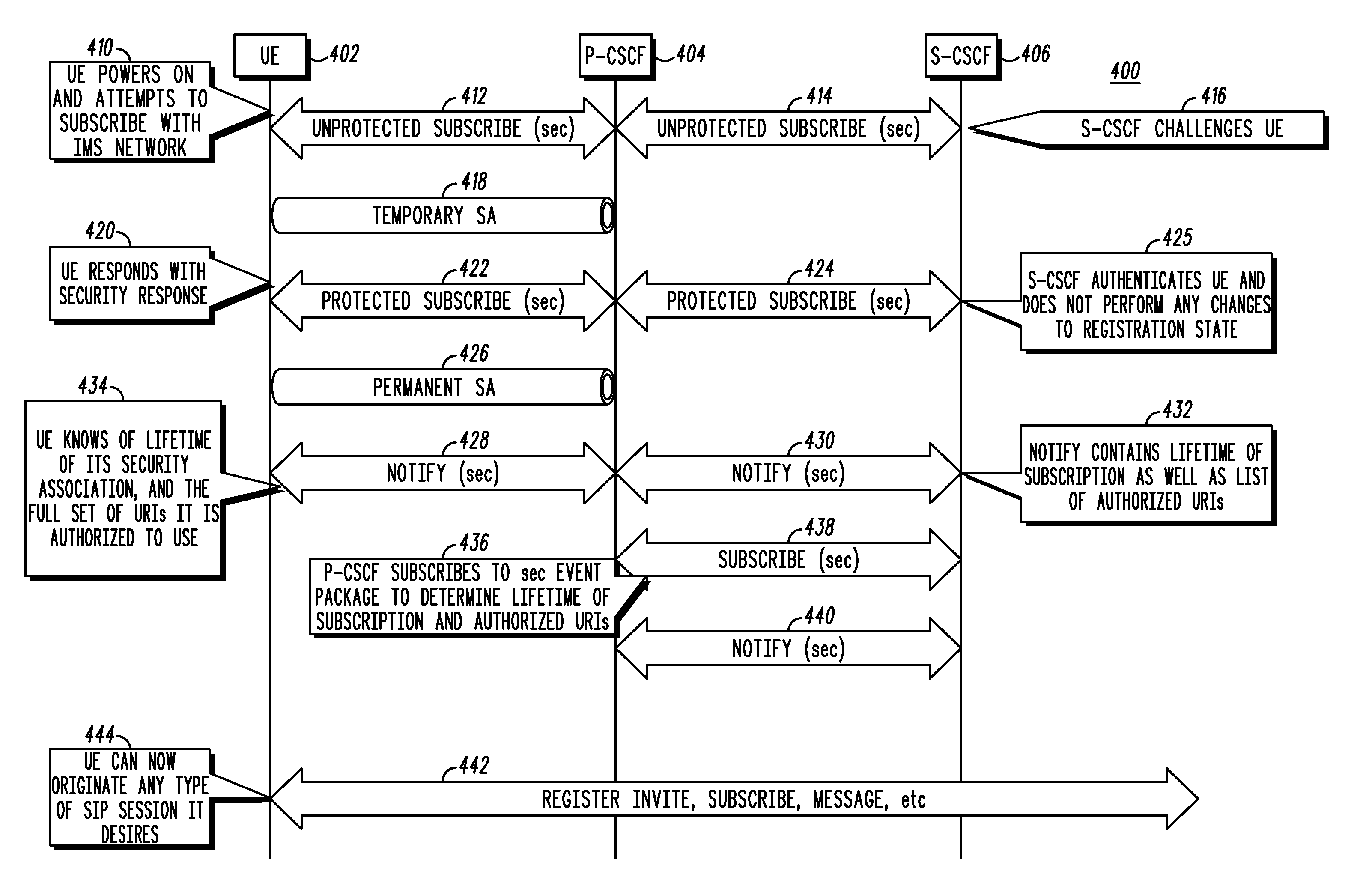
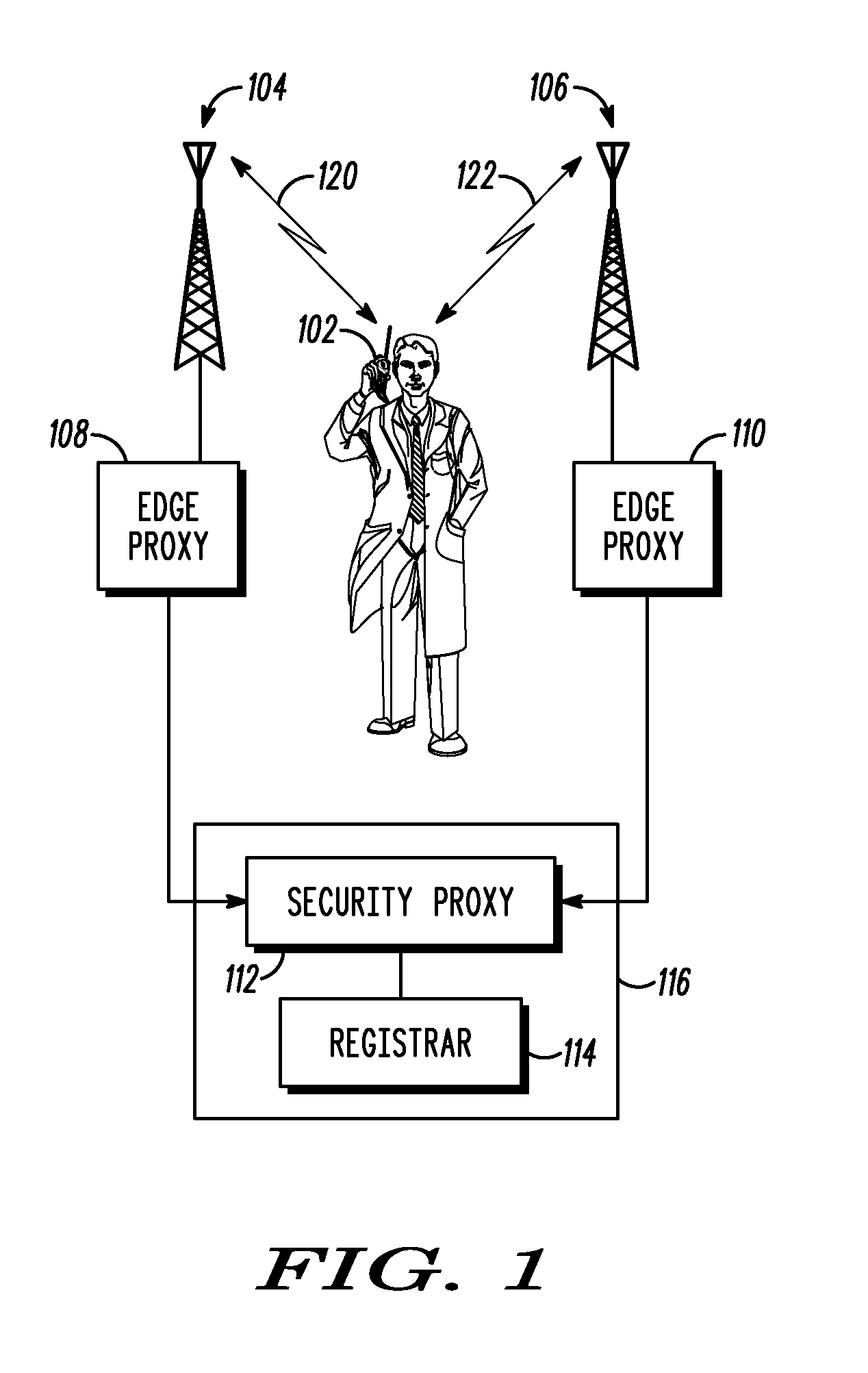
A system and method for establishing a secure and authenticated session layer path between user equipment (102) and a security proxy (112), such as a serving call session control function (116). A communications session is established at a user equipment node (102), prior to registering with the security proxy (112). The user equipment (102) subscribes, through the communications session prior to registering with the security proxy (112), to an event package from the security proxy (112). A secure and authenticated session layer path (426) is established, based upon the subscription, through the communications session from the user equipment node to the security proxy (112) and therefore the serving call session control function (116). A session initiation protocol session (442) is originated, at the user equipment node (102), over the secure and authenticated session layer path (426) based upon authentication provided by the secure and authenticated session layer path (426).
Owner:MOTOROLA SOLUTIONS INC
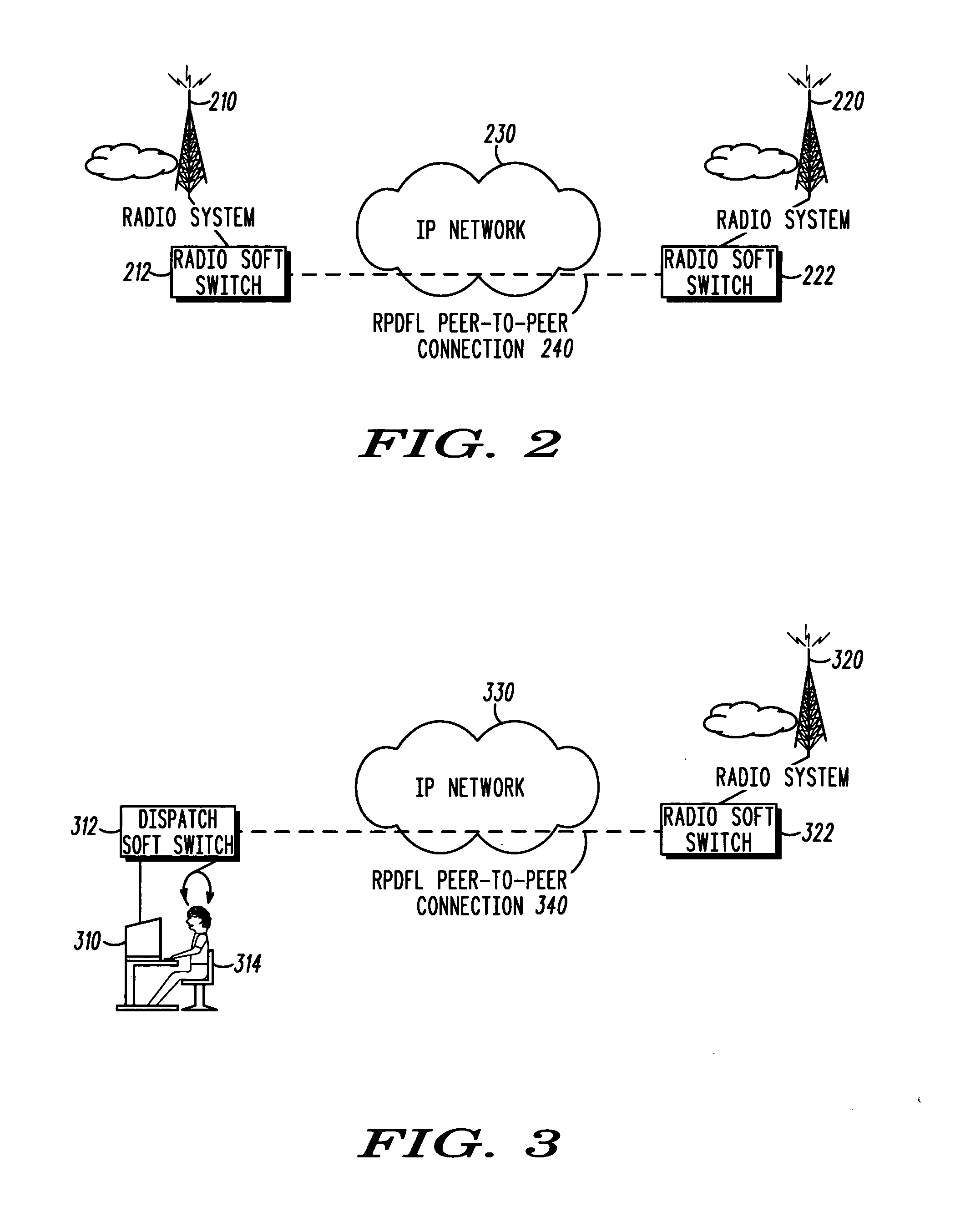
Method and apparatus for enabling interoperability between packet-switched systems
A method and apparatus for interoperability between packet-switched systems is described. The method includes the steps of: establishing (810) a connection with at least one packet-switched apparatus; generating (820) at least one communication frame at a session layer including a payload field for carrying a payload and a signal field for carrying a control signal; and transmitting (830) the at least one communication frame to the at least one packet-switched apparatus.
Owner:MOTOROLA SOLUTIONS INC
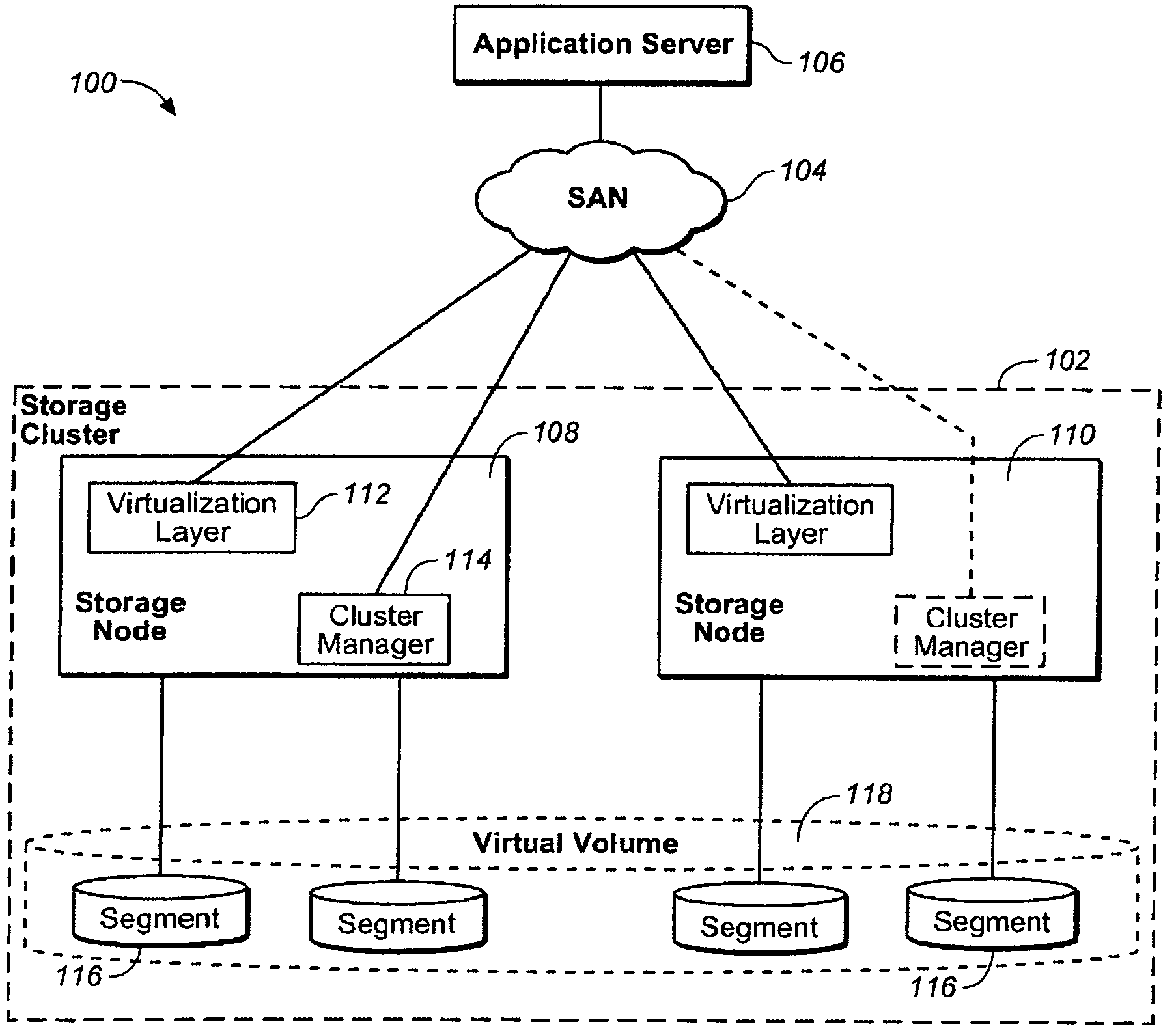
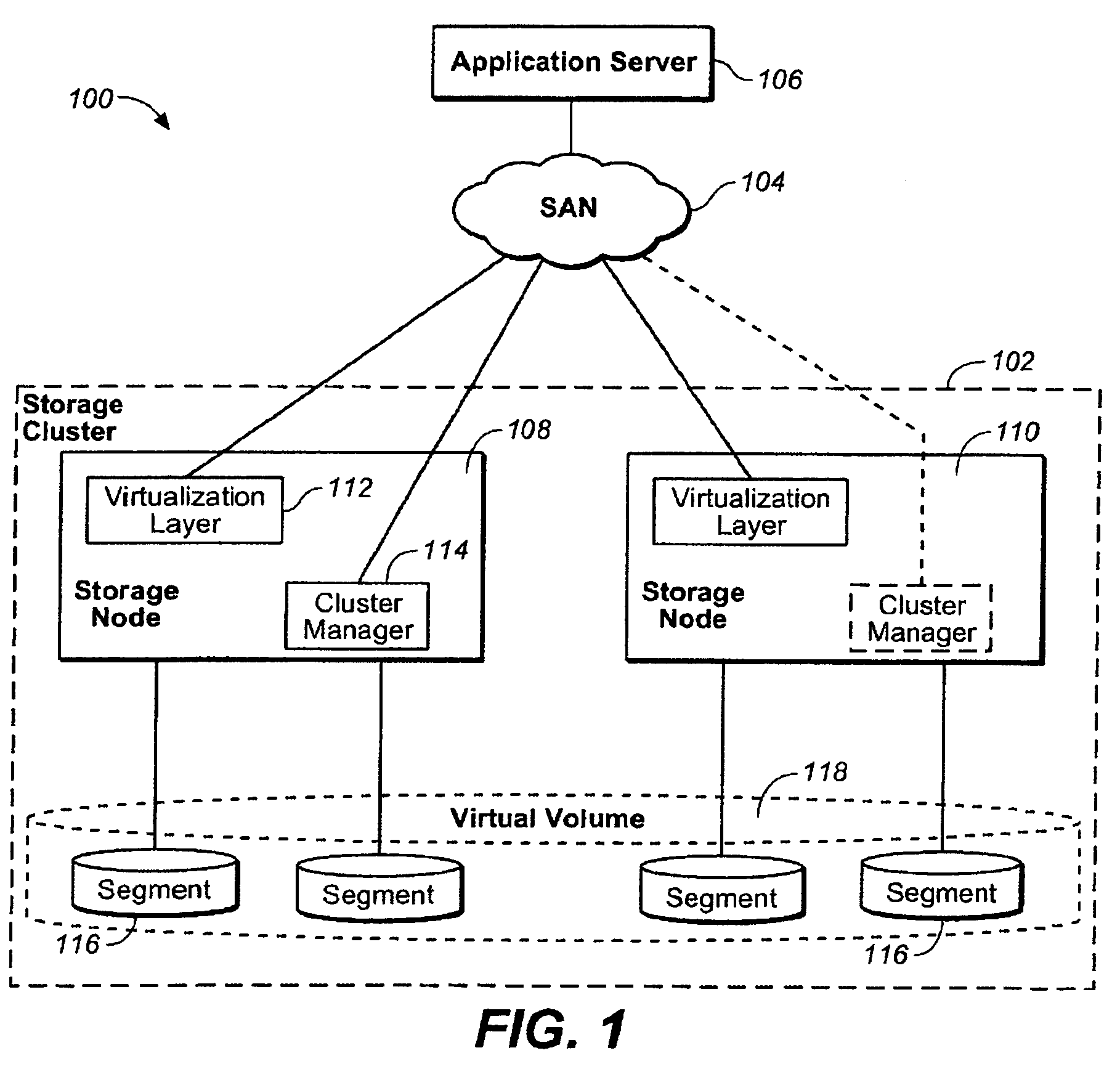
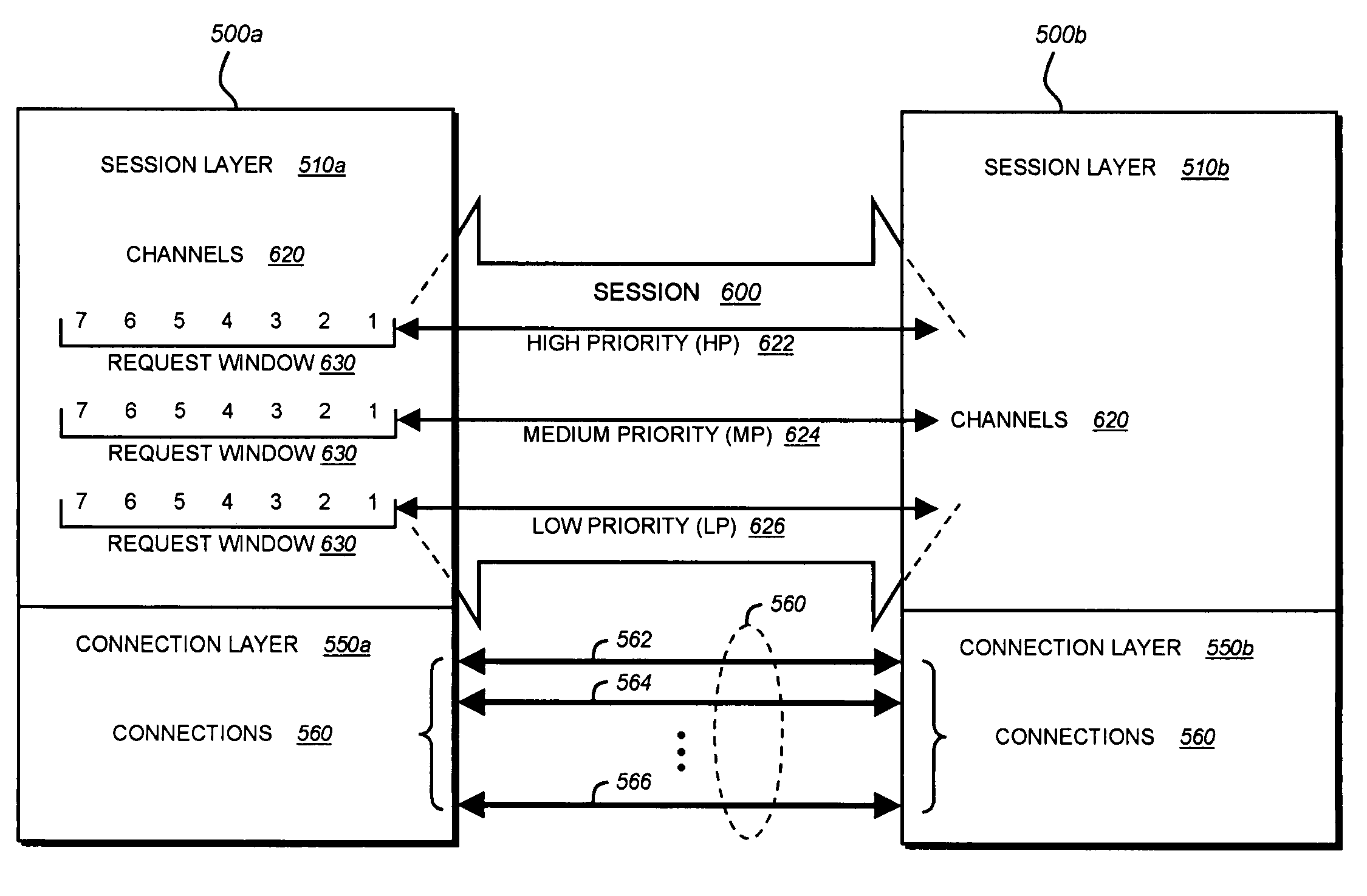
System and method for multiplexing channels over multiple connections in a storage system cluster
ActiveUS7443872B1Guaranteed normal executionTime-division multiplexData switching by path configurationNetworking protocolData access
A system and method multiplexes channels over multiple connections between one or more nodes. Each node includes a cluster fabric interface module adapted to implement a novel network protocol that enables intra-cluster communication among the nodes. The network protocol is a multi-layered protocol that integrates a session infrastructure and an application operation set into a session layer. The network protocol is illustratively a request / response protocol wherein a node (requester) receiving a data access request from a client redirects that request to another node (responder) that services the request and, upon completion, returns a response.
Owner:NETWORK APPLIANCE INC
Server arbitrated reliable multicast system and a process for accessing the same
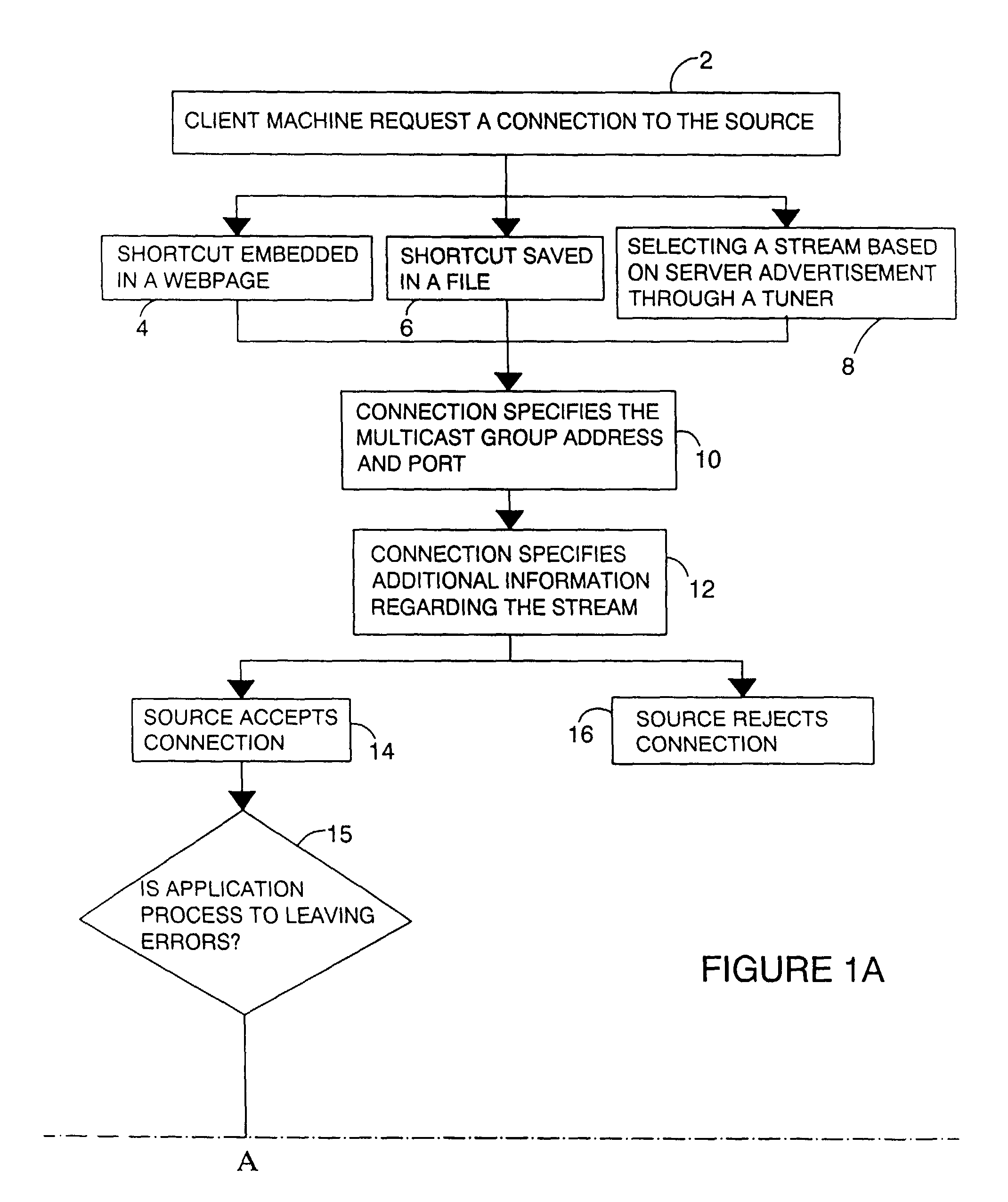
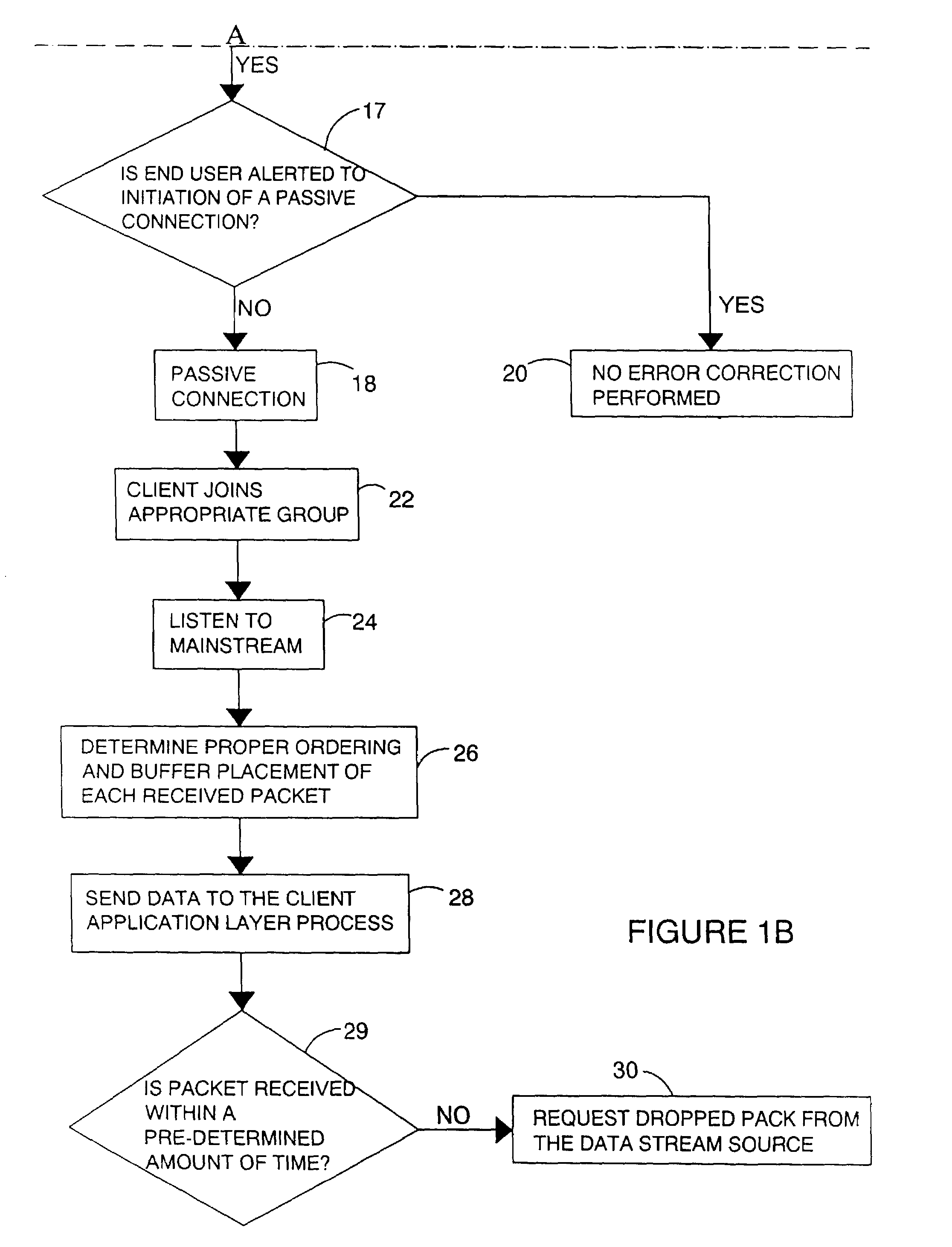
ActiveUS7177312B2Cost efficientEffective timeSpecial service provision for substationError detection/correctionData streamReliable multicast
A system and a process for a session layer protocol allows a large number of client machines to receive a reliable data stream over inherently unreliable multicast connections in a highly efficient and scalable manner. More specifically, streaming of high-quality video, audio, stock and news tickers, or any other application specific data that requires a reliable data stream is described. The streaming allows for the source to instruct individuals to drop their connection to the stream to prevent noisy individuals from disrupting the operating efficiency of the stream.
Owner:VECTORMAX CORP
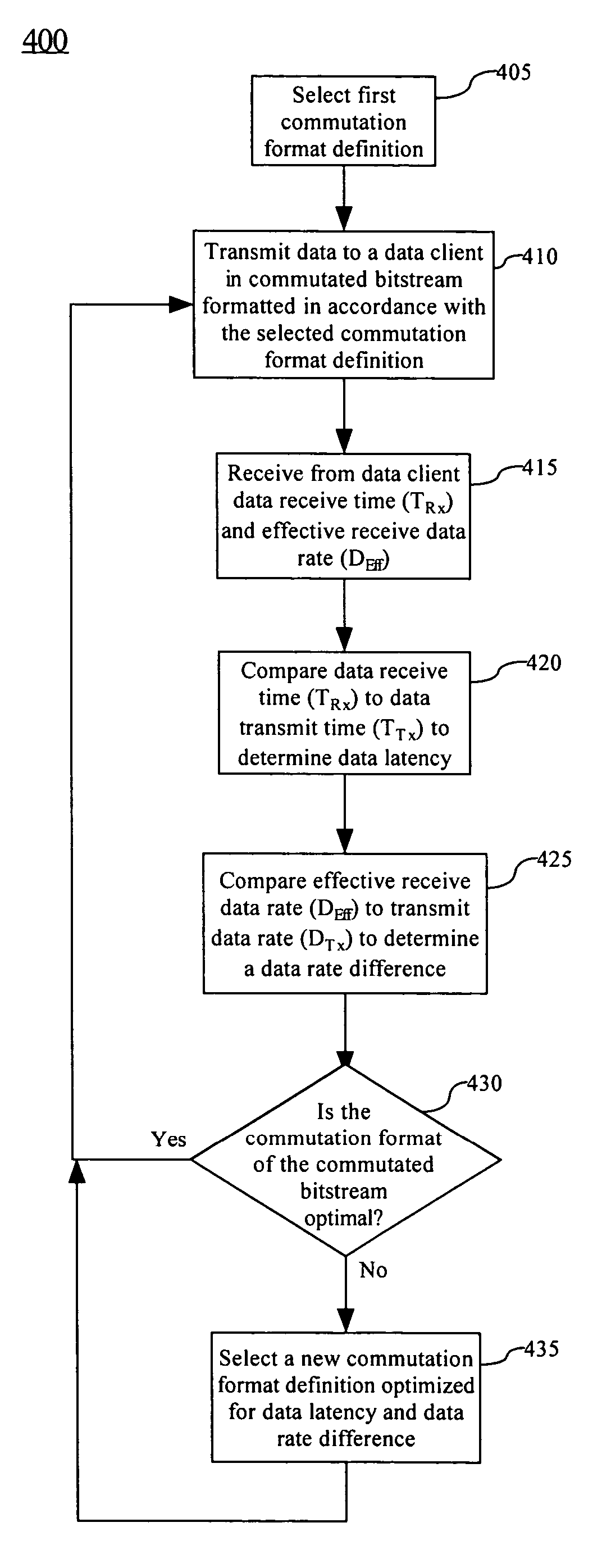
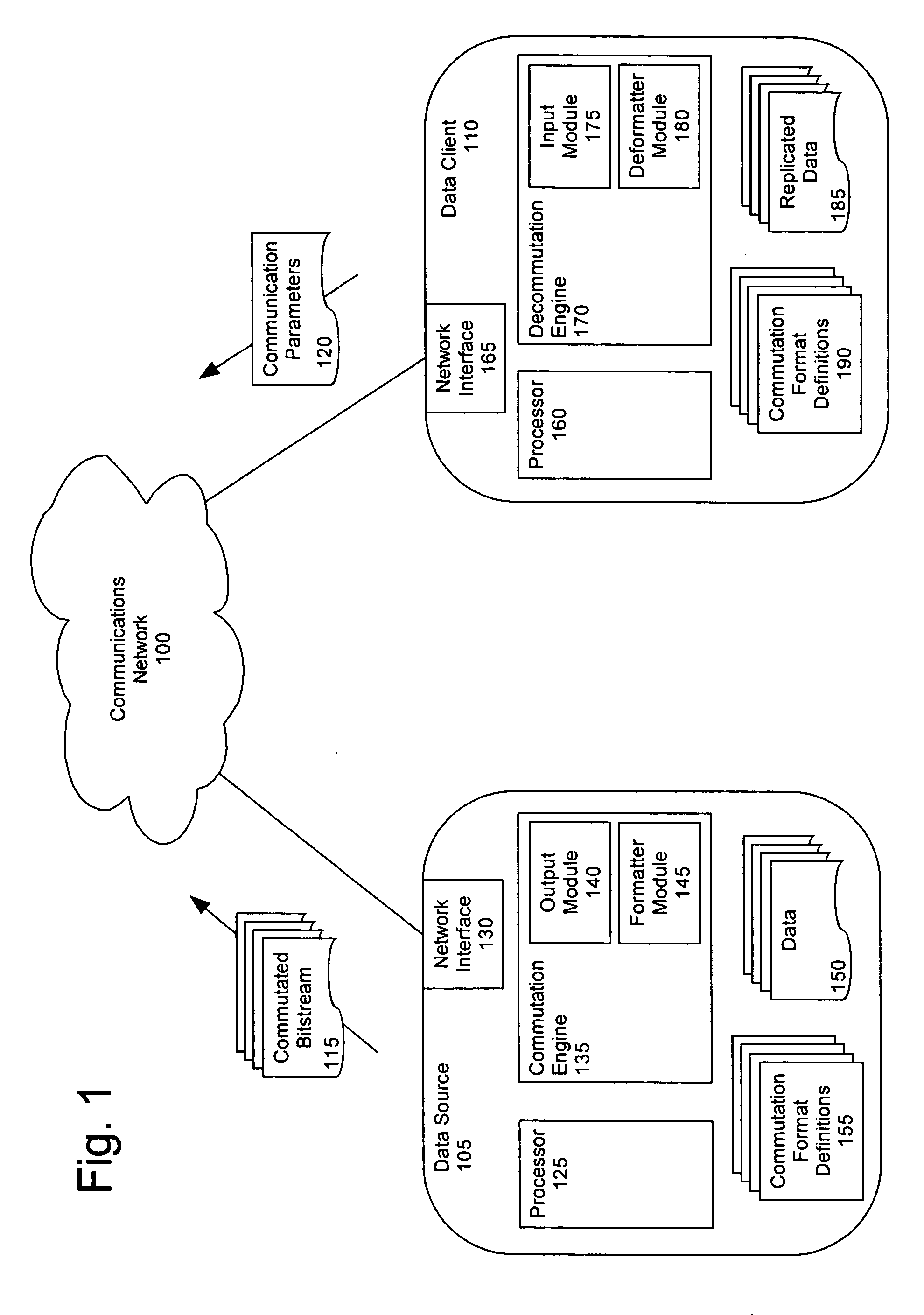
Adaptive bandwidth utilization for telemetered data
A method (400) for optimizing bandwidth utilization in a communications network (100). The communications network can include a data source (105) and a data client (110). Responsive to a measurement of at least one communication parameter (120) of a commutated bitstream (115) which is transmitted to the client, the data source can change a commutation format of the commutated bitstream. The communication parameters can include a data receive time (TRx), a data latency and / or an effective receive data rate (DEff) of the commutated bitstream. The communication parameters can be transmitted to the data source as telemetry. The change of commutation format can occur in an open systems interconnection (OSI) layer such as a session layer and / or a transport layer.
Owner:HARRIS CORP
Common protocol layer architecture and methods for transmitting data between different network protocols and a common protocol packet
ActiveUS7882254B2Enhance interestTime-division multiplexMultiple digital computer combinationsNetworking protocolTransport layer
The present invention provides common protocol architecture and methods for transmitting data between different network protocols and a common protocol packet. The common protocol architecture comprises an application layer; a common protocol layer positioned under the application layer, the common protocol layer enabling data communications between the different protocols; a presentation layer positioned under the common protocol layer; a session layer positioned under the presentation layer; a transport layer positioned under the session layer; a network layer positioned under the transport layer; a data link layer positioned under the network layer; and a physical layer positioned under the data link layer. The common protocol packet comprises a common protocol header with information about a packet and a payload with the contents of data. By designing the common protocol layer and the common protocol packet accepting various protocols simultaneously, the present invention can improve compatibility between different protocols.
Owner:KOREA ELECTRONICS TECH INST
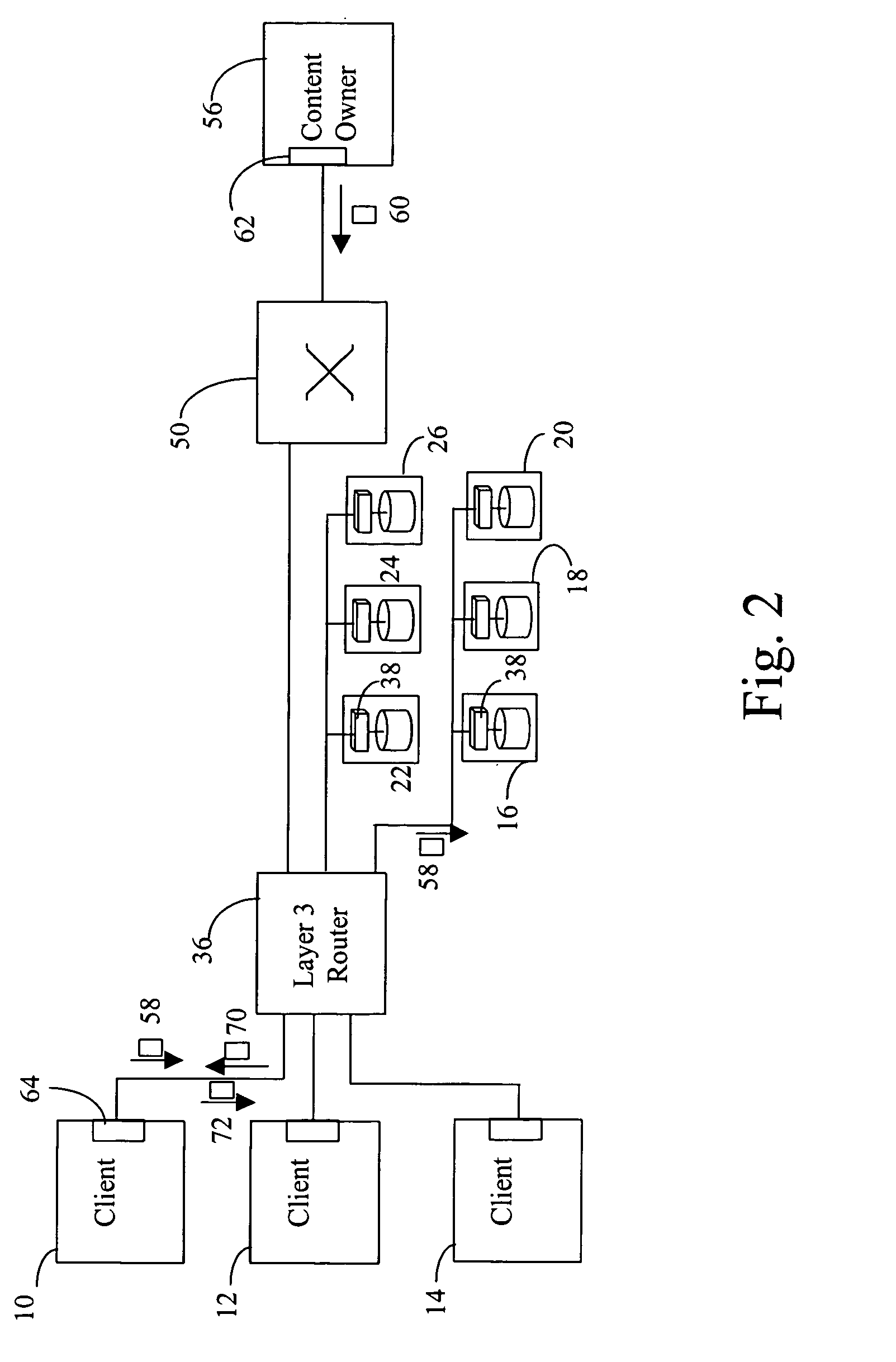
Applications for networked storage systems
InactiveUS7113984B1Improve performanceReduce the possibilityDigital data information retrievalTime-division multiplexNetworking protocolRemovable media
At least one network device that moves storage blocks based upon a session layer or higher protocol set is employed to facilitate communication between at least one host and at least one target storage device. The at least one network device may include a server and a switch. Transactions related to data storage access are expressed in a non-network protocol and transmitted via a network protocol data unit across at least a portion of the network by employing encapsulation. An adapter card associated with the data storage unit is employed to extract the non-network protocol transaction. Multiple, mirrored data storage units that are separated by relatively large physical distance may be employed to reduce the likelihood of catastrophic data loss due to an event such as a fire. Further, READ transactions may be facilitated by preloading data storage units with READ metadata for subsequent transmission to a client device to enable expedited access to data stored on the data storage units.
Owner:CIENA
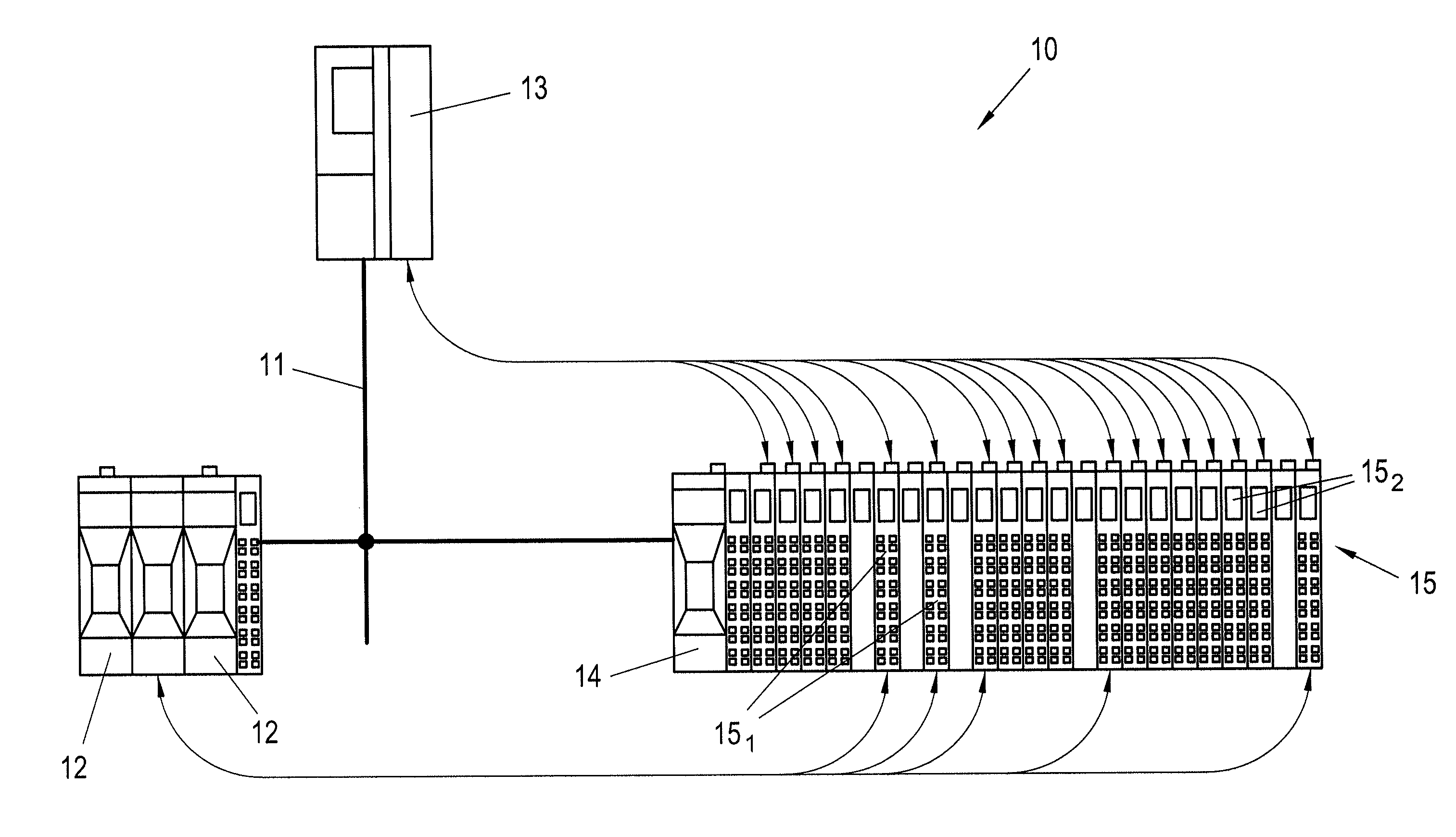
Method and a bus device for transmitting safety-oriented data
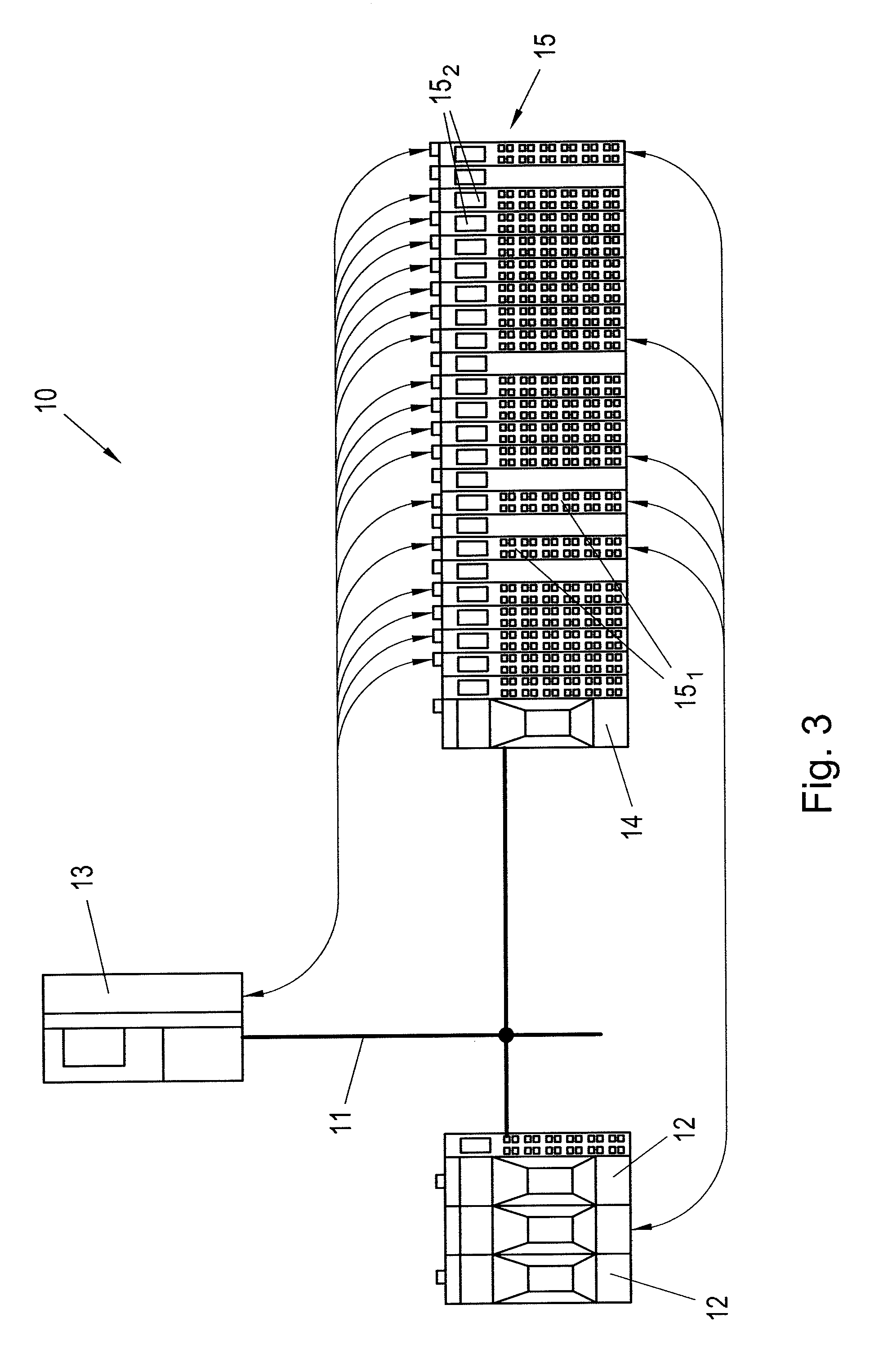
ActiveUS20130111087A1Eliminate disadvantagesReduce development costsElectric digital data processingBus networksIndustrial EthernetCryptographic protocol
Safe bus devices use a safety protocol in order to transmit safe data encapsulated in an industrial Ethernet message via an Ethernet-based field bus. However, this restricts the safe bus device to a certain combination of safety protocol and industrial Ethernet protocol. In order to be able to use a safe bus device 12, 14, 151 more flexibly, it is provided that, to transmit the safety-oriented data, the industrial Ethernet protocol uses the session layer 5 and / or presentation layer 6 of the safety protocol, which is independent of the industrial Ethernet protocol, instead of the session layer 5 and / or presentation layer 6 which is implemented in the industrial Ethernet protocol, whereby such a bus device 12, 14, 151 becomes independent of the industrial Ethernet protocol.
Owner:B&R IND AUTOMATION GMBH
Broadcasting and TV program recommendation method based on knowledge graph and user microcosmic behaviors
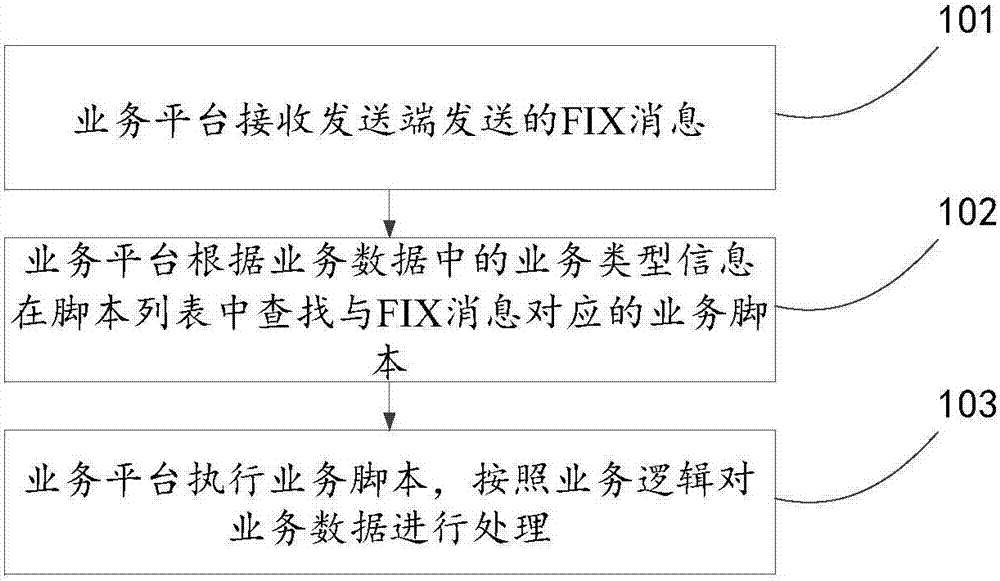
ActiveCN112732936AStrong correlationFully consider the densityDatabase management systemsWeb data indexingSemantic representationTheoretical computer science
The invention provides a broadcasting and TV program recommendation method based on a knowledge graph and a user microcosmic behavior. The method comprises the steps: combining intem2vec with random walk, training a random walk sequence of an attribute subgraph and a user behavior sequence, and obtaining an embedded vector which integrates the similarity of a program content attribute layer and a user interaction session layer. Then, under the condition that program embedding and classified fusion microscopic behavior embedding are obtained, behavior embedding and corresponding program embedding are spliced according to historical interaction records of a user and a program, semantic representation of behavior programs with the same dimension is obtained through semantic space network mapping, and an embedding sequence of historical behaviors of the user is formed; and finally, based on a Transformer encoding and decoding mechanism, carrying out self-attention encoding and mapping on the historical behavior sequence of the user to obtain user semantic features implicit with dynamic preferences, and decoding the user semantic features by utilizing target program attention to carry out mapping to obtain user semantic preferences.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
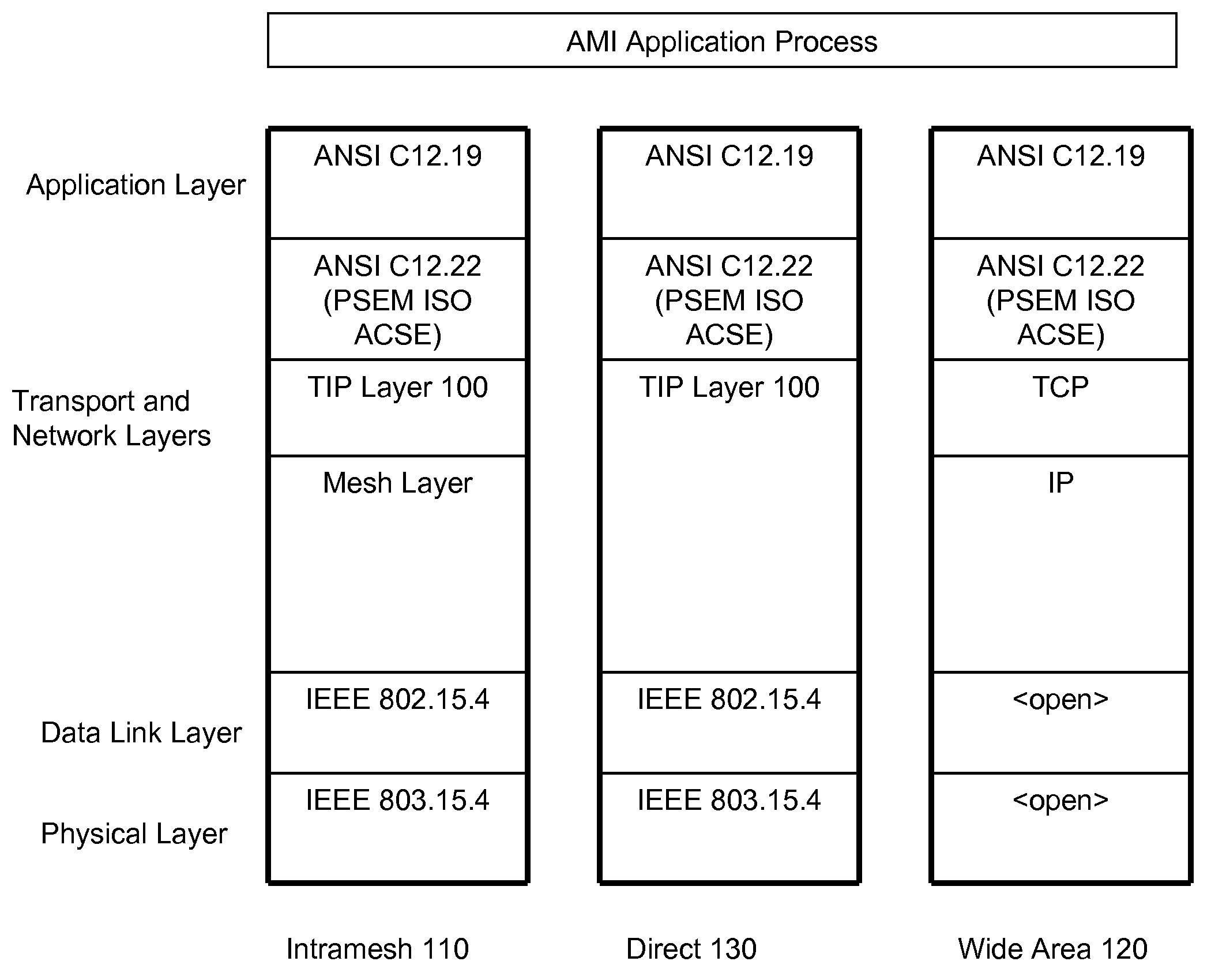
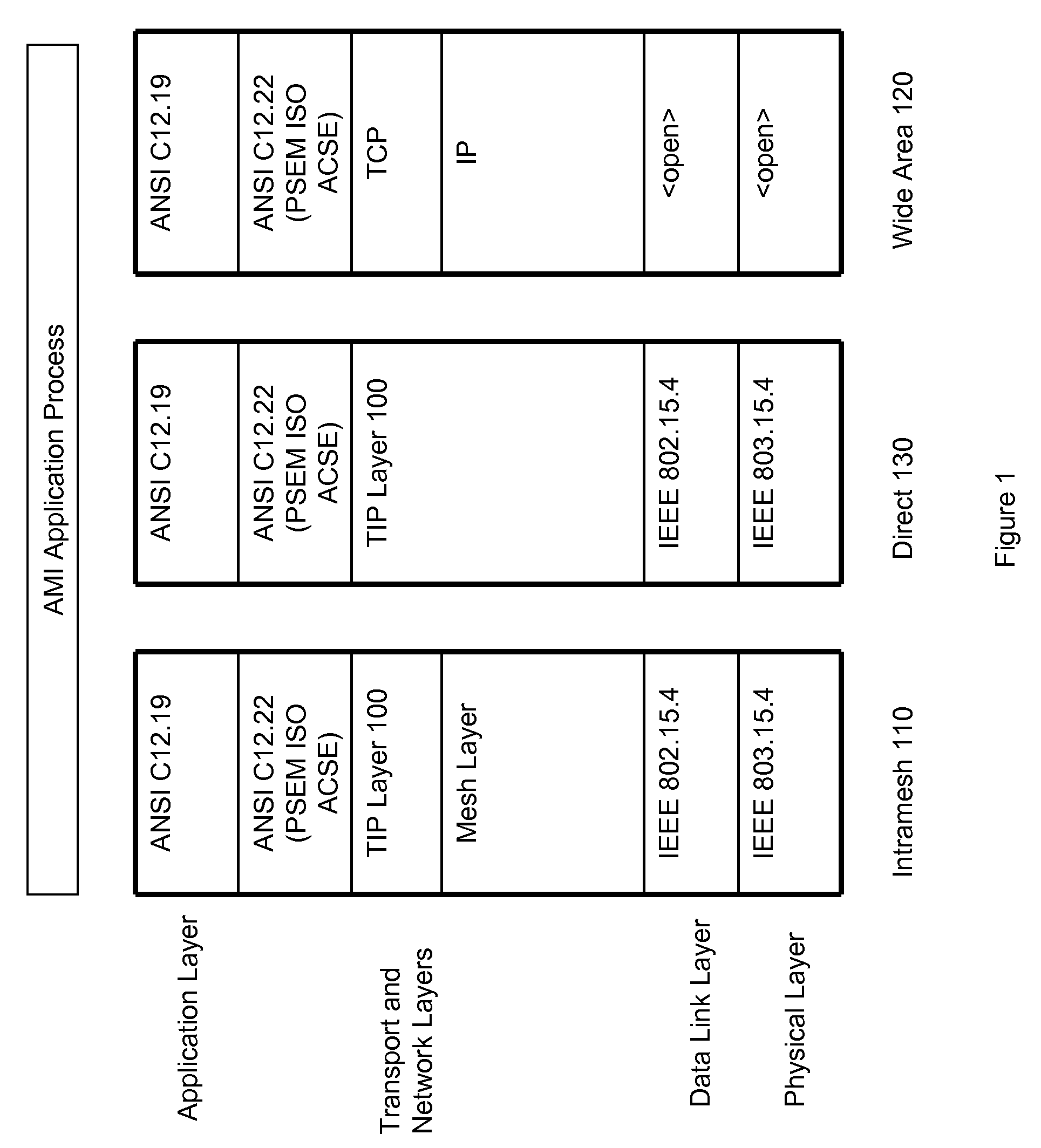
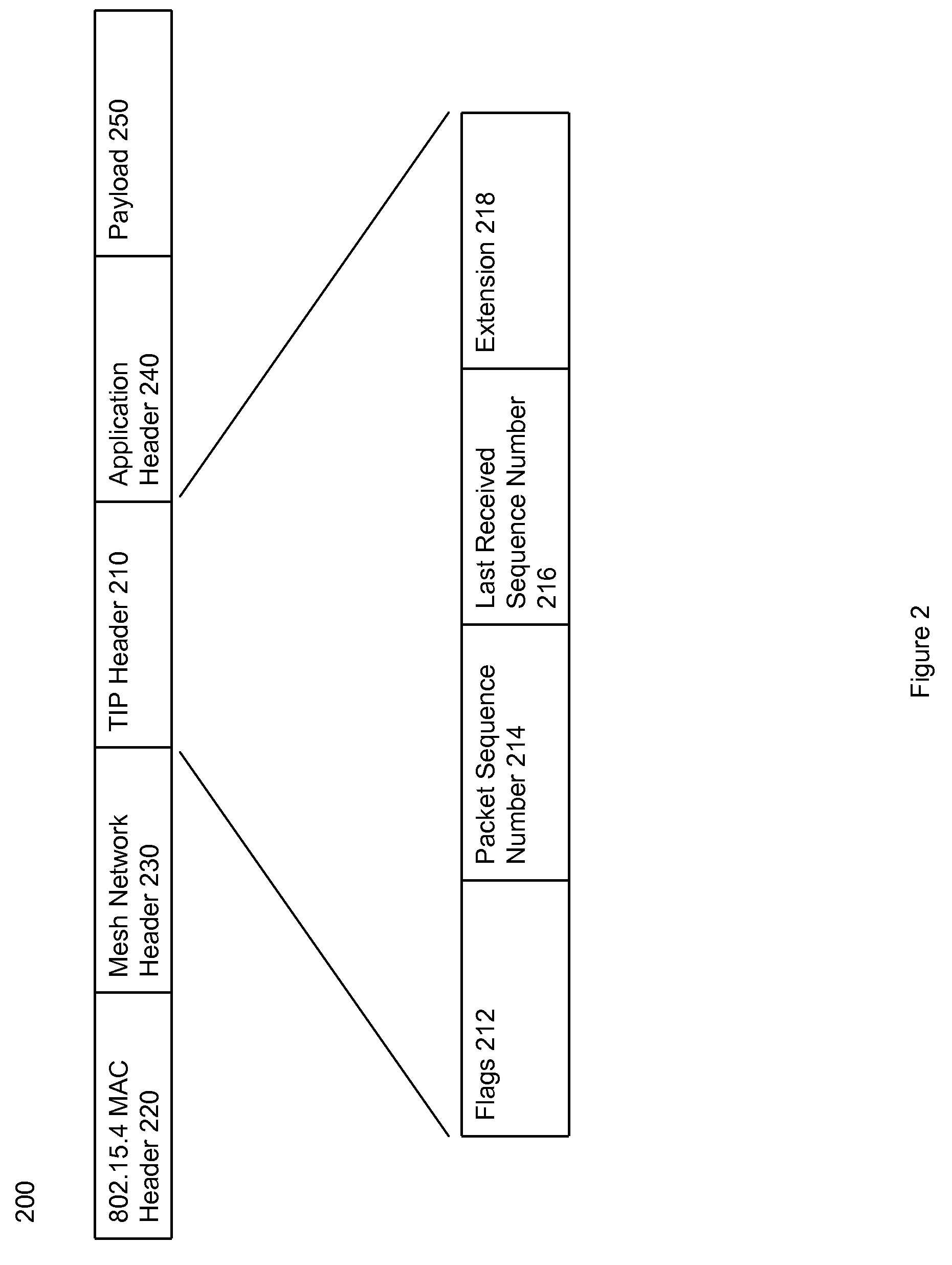
Transport layer and model for an advanced metering infrastructure (AMI) network
InactiveUS20090135851A1Simplify the communication processElectric signal transmission systemsTariff metering apparatusTransport layerProtocol Application
Mesh networks, network devices, and computer program products for implementing a transport layer. The transport layer is operable to provide connection oriented transport layer services to at least one of an application layer, a presentation layer, and a session layer. The transport layer header flags essentially consist of: SYN, ACK, PSH, and RST.
Owner:TRILLIANT NETWORKS
Common protocol layer architecture and methods for transmitting data between different network protocols and a common protocol packet
The present invention provides common protocol architecture and methods for transmitting data between different network protocols and a common protocol packet. The common protocol architecture comprises an application layer; a common protocol layer positioned under the application layer, the common protocol layer enabling data communications between the different protocols; a presentation layer positioned under the common protocol layer; a session layer positioned under the presentation layer; a transport layer positioned under the session layer; a network layer positioned under the transport layer; a data link layer positioned under the network layer; and a physical layer positioned under the data link layer. The common protocol packet comprises a common protocol header with information about a packet and a payload with the contents of data. By designing the common protocol layer and the common protocol packet accepting various protocols simultaneously, the present invention can improve compatibility between different protocols.
Owner:KOREA ELECTRONICS TECH INST
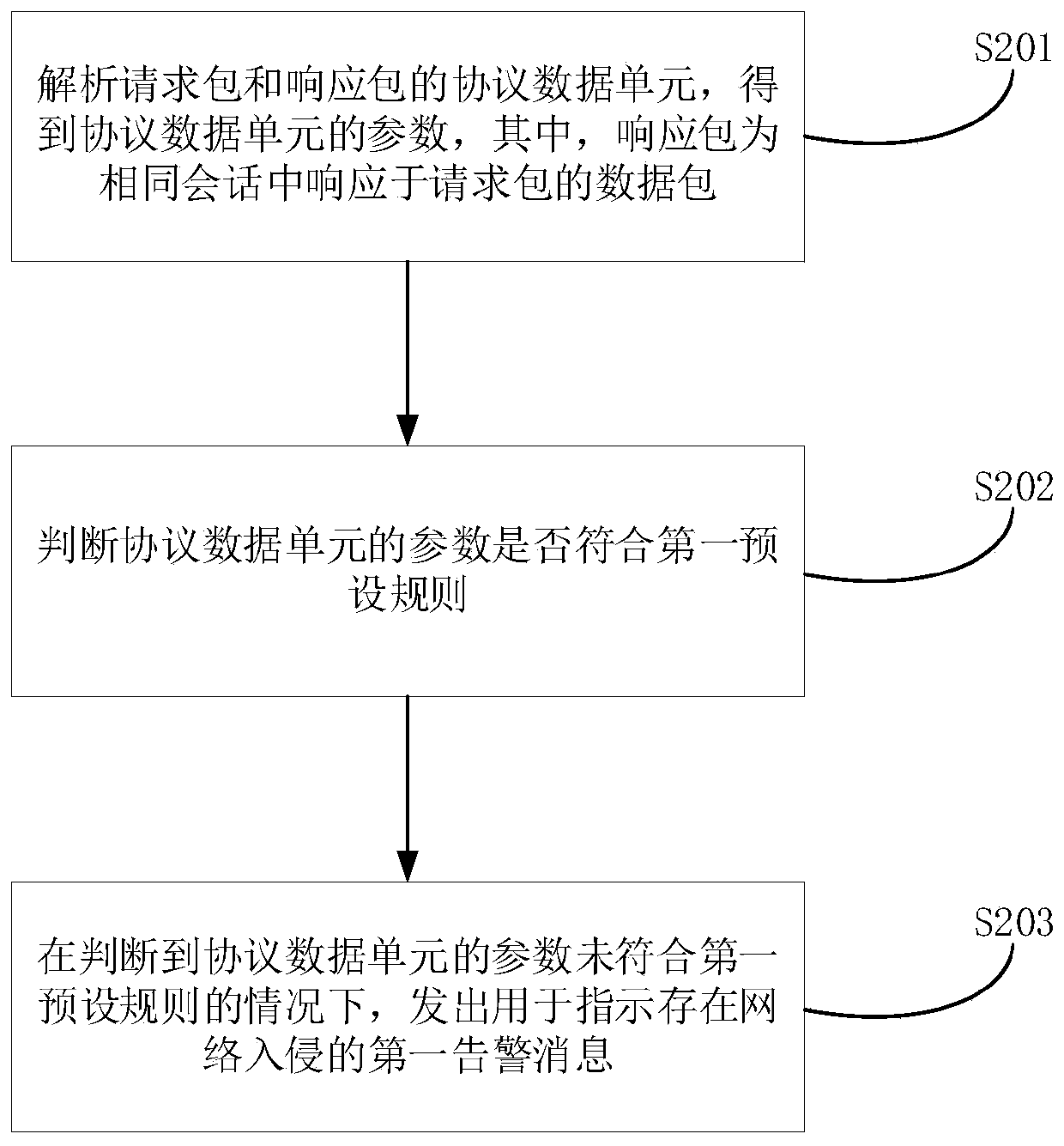
Network intrusion detection method, device, system and storage medium
ActiveCN111600863ASolve the problem of inability to support intrusion detection at the session levelTransmissionAlarm messageData pack
The invention relates to a network intrusion detection method, a device, a system and a storage medium. The network intrusion detection method comprises the steps of: analyzing protocol data units ofa request packet and a response packet to obtain parameters of the protocol data units, wherein the response packet is a data packet responding to the request packet in the same session; judging whether the parameters of the protocol data unit accord with a first preset rule or not; and when judging that the parameters of the protocol data unit do not accord with the first preset rule, transmitting a first alarm message used for indicating that network intrusion exists. Through adopting the network intrusion detection method, the problem that intrusion detection of a session level cannot be supported in related technologies is solved, and the beneficial effect of intrusion detection of the session level is realized.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
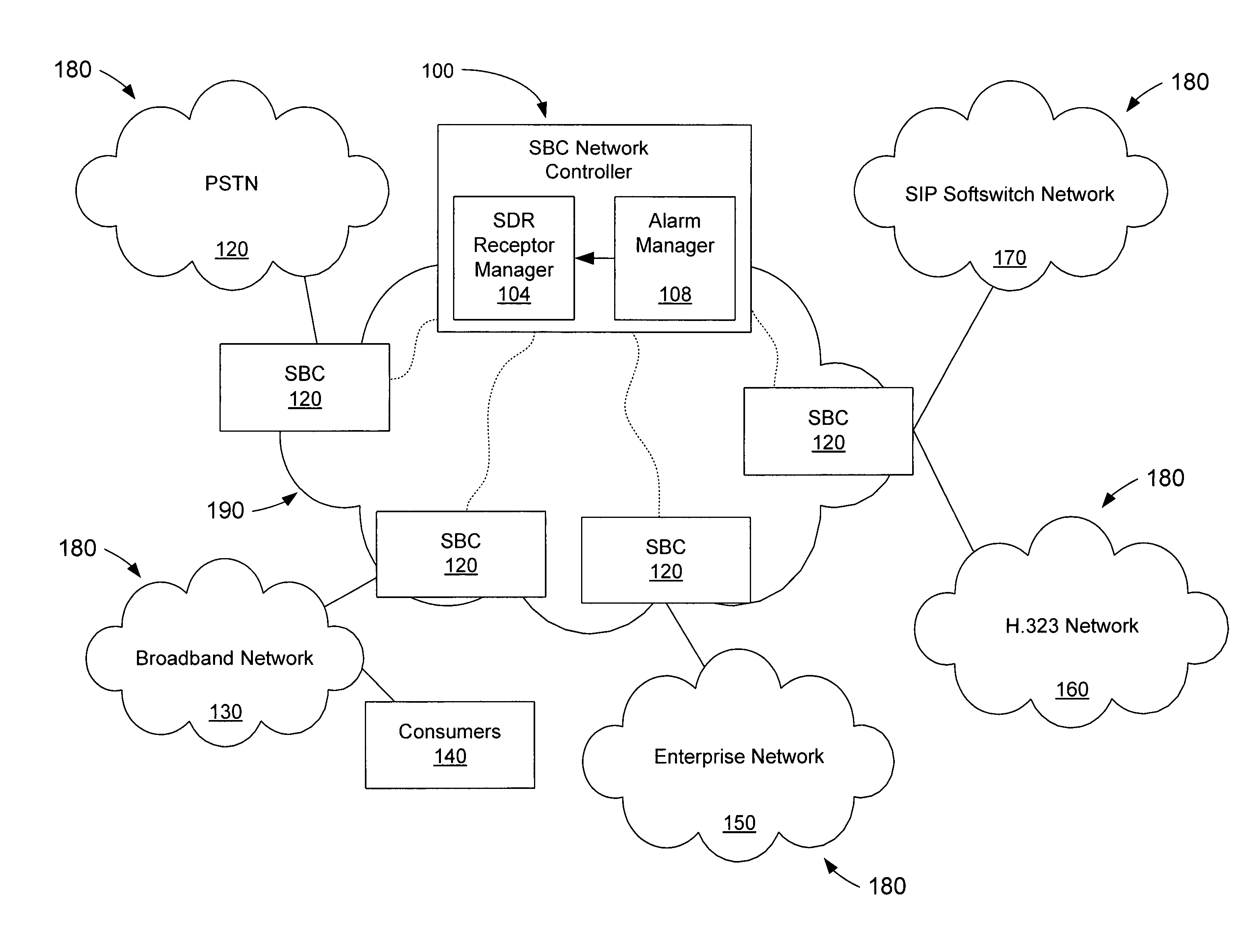
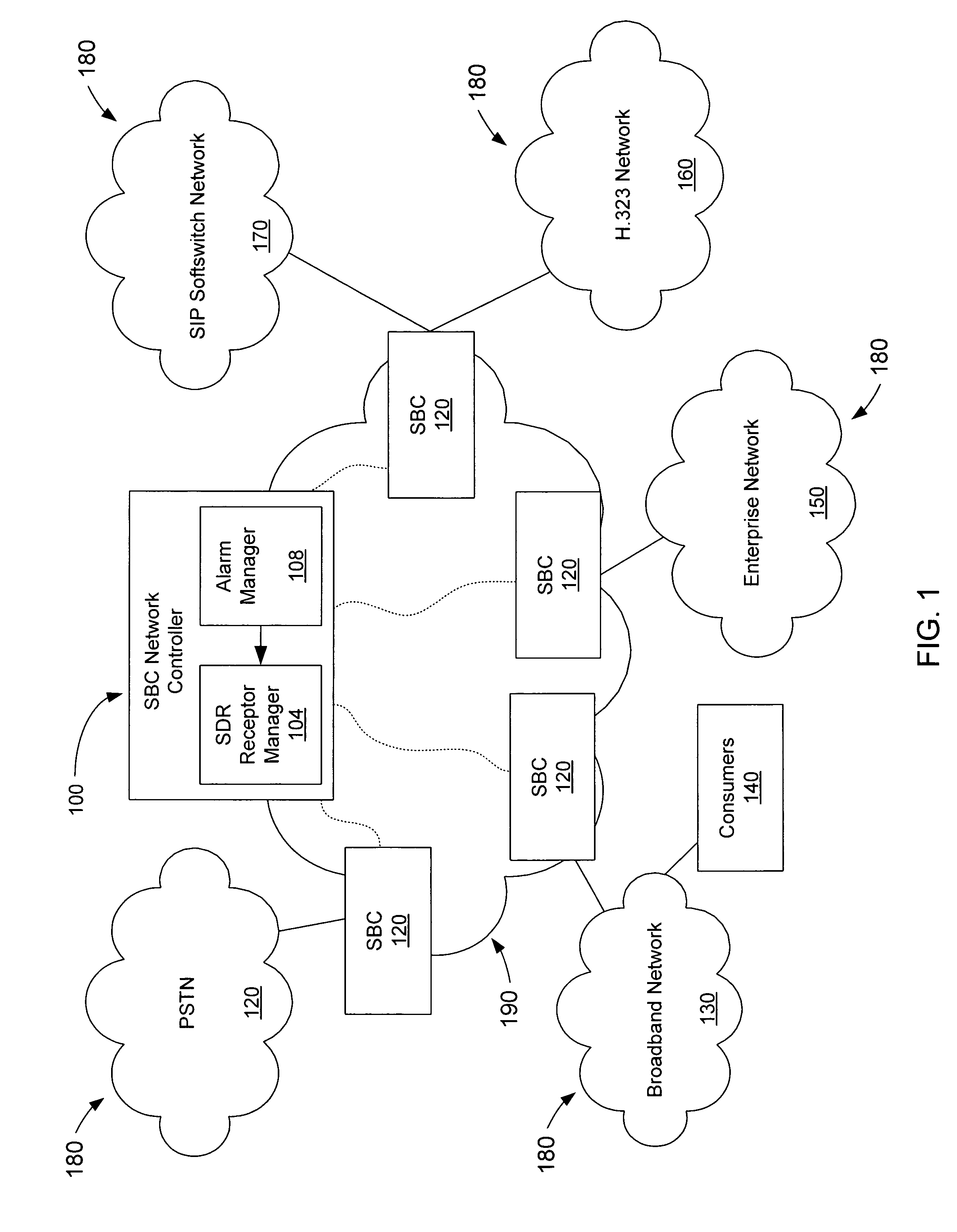
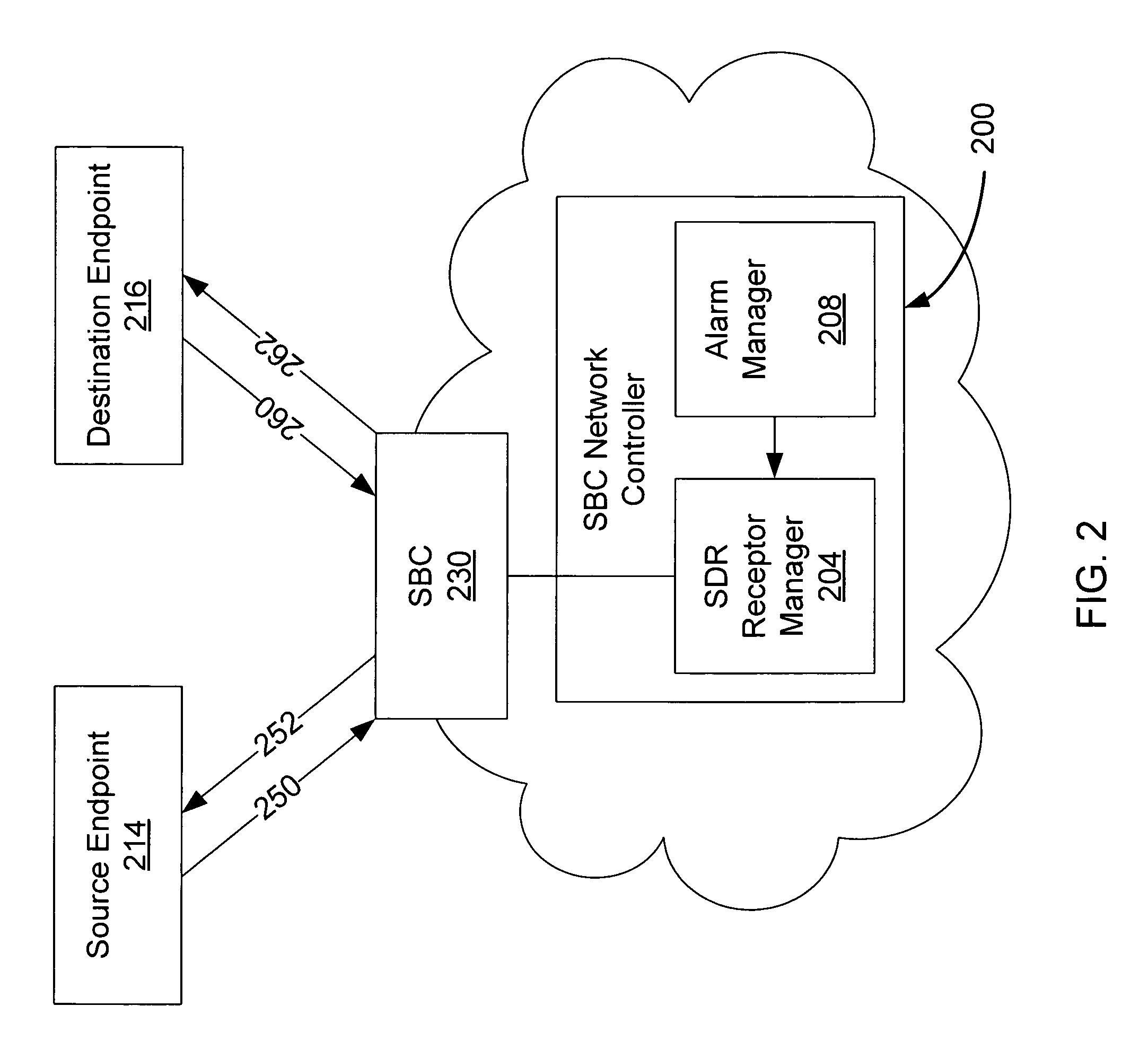
Session data records and related alarming within a session over internet protocol (SOIP) network
ActiveUS7860990B2Multiple digital computer combinationsTransmissionInternet protocol suiteComputer science
Owner:GENBAND US LLC
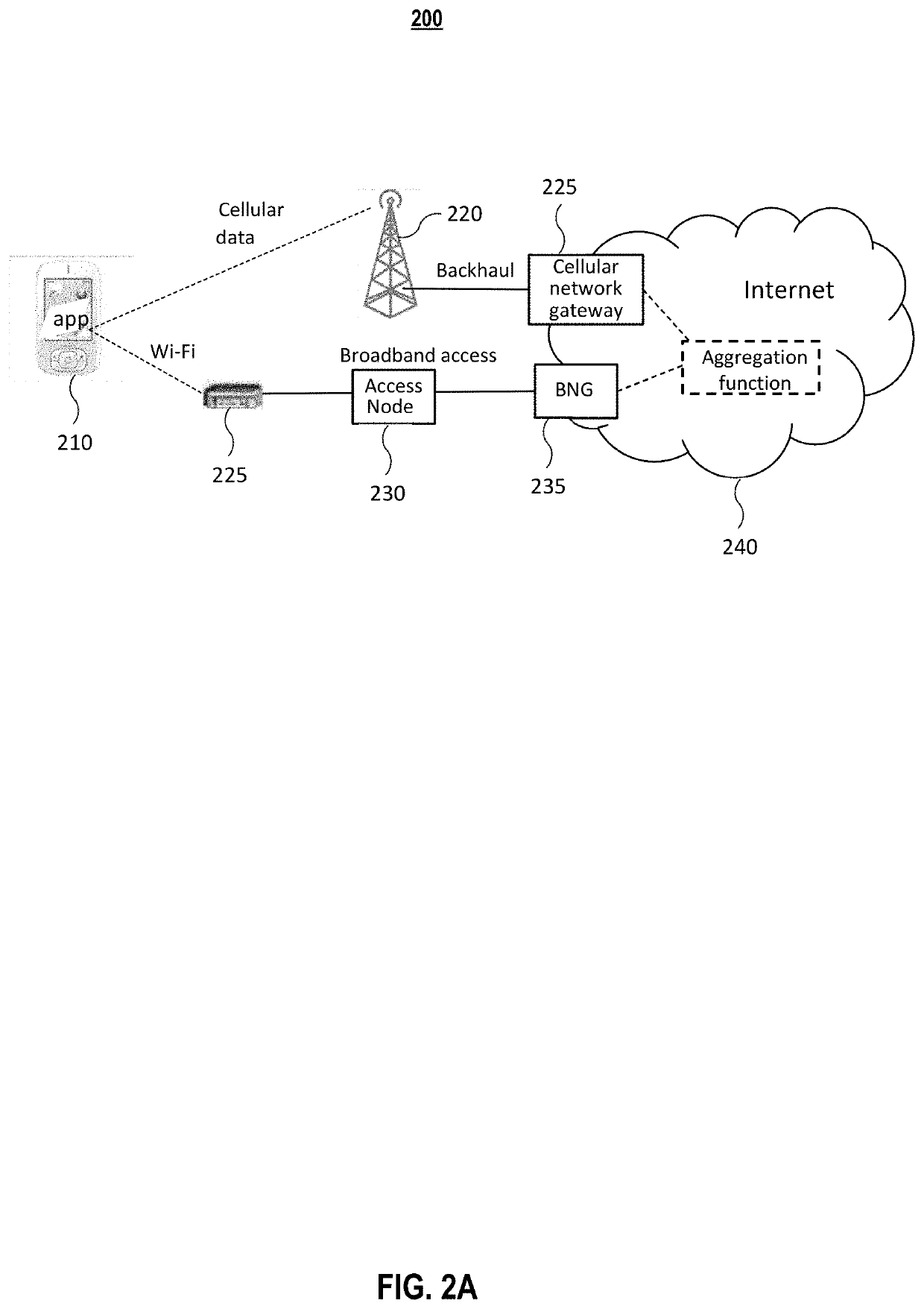
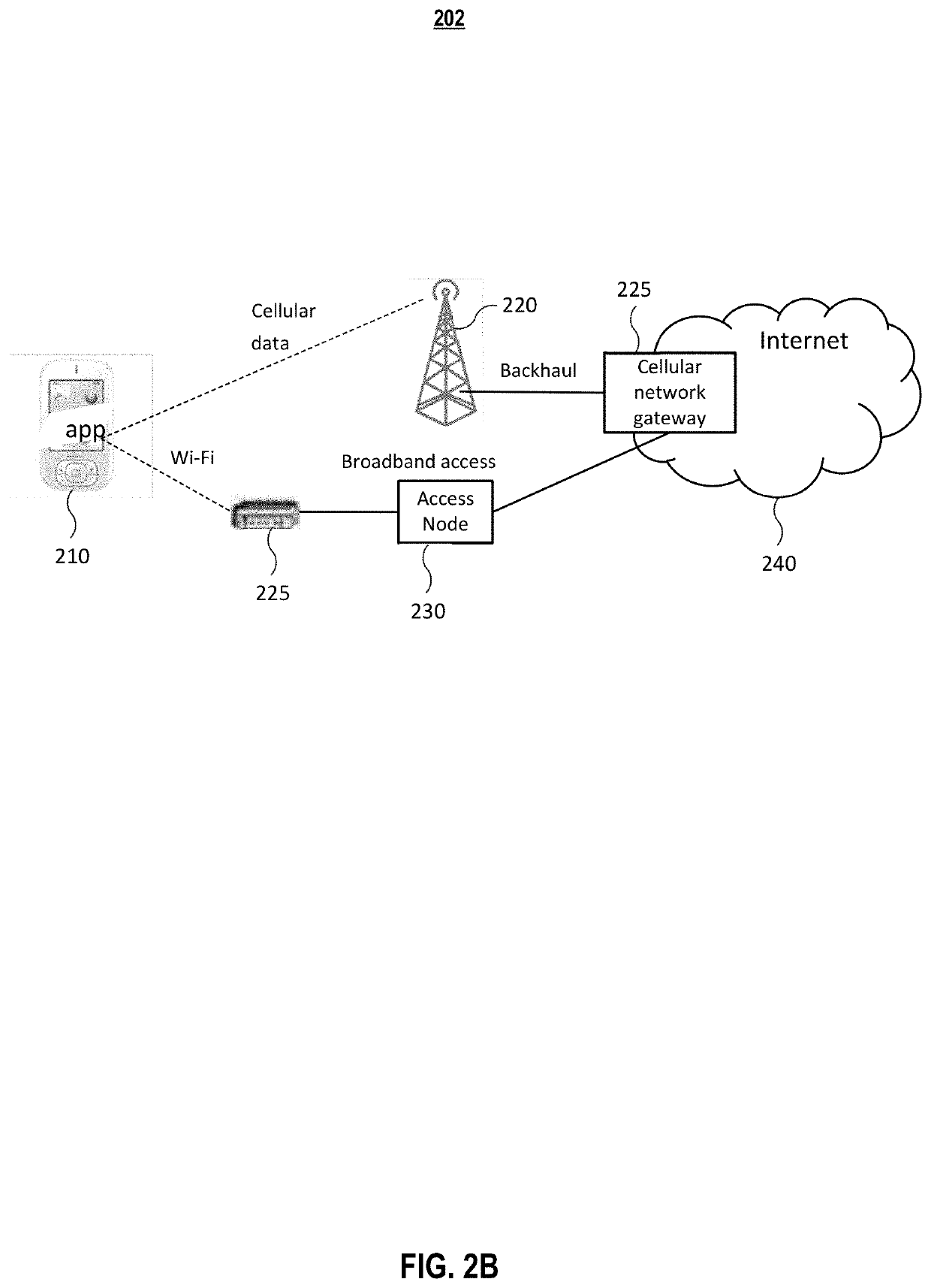
Systems and methods for combined management with user preferences of wi-fi and cellular data
PendingUS20200404540A1Provide controlService quality varyNetwork traffic/resource managementNetwork topologiesPhysical layerEngineering
Various embodiments of the invention relate to system and method for combined management with user preferences of Wi-Fi and cellular data. The system presents diagnostics data to users in one or more ways showing the impact on their applications, and allows the user to provide high-level control of the use of the two or more connections. Embodiments of the system diagnose both Wi-Fi / broadband and cellular data; at both low layers, such as physical, link, or network layers; and high layers, such as session, presentation, or application layers. Joint cellular data and Wi-Fi diagnostics are determined, and the impact of the diagnostics to application performances may also be shown. Recommendations may be further provided for network policies and configurations aimed at the user's preferences and applications.
Owner:ASSIA SPE LLC
Service implementation method, device and system for financial information exchange (FIX) protocol
ActiveCN107135188AWeakened strong type traitsWeaken decouplingFinanceProgram loading/initiatingService implementationThe Internet
The invention discloses a service implementation method, device and system for a financial information exchange (FIX) protocol, relates to the technical field of Internet, and aims to solve the problem of too high cost on deployment of an FIX service environment on a service platform side. The method disclosed by the invention comprises the following steps that: a transmitting end encapsulates an FIX message into FIX information, and transmits the FIX information to a service platform; the service platform receives the FIX information transmitted by the transmitting end, wherein the FIX information consists of different types of service data, and the service data are in character string forms; a service script corresponding to the FIX information is found in a script list according to the service type information in the service data, wherein service scripts corresponding to different FIX protocol versions are saved in the script list, and the service scripts include service logics; and the service scripts are executed, and the service data are processed according to the service logics. The service implementation method, device and system are mainly applied to a process for implementing FIX protocol session layer service logic.
Owner:ADVANCED NEW TECH CO LTD
Smartphone data backup and restoration system
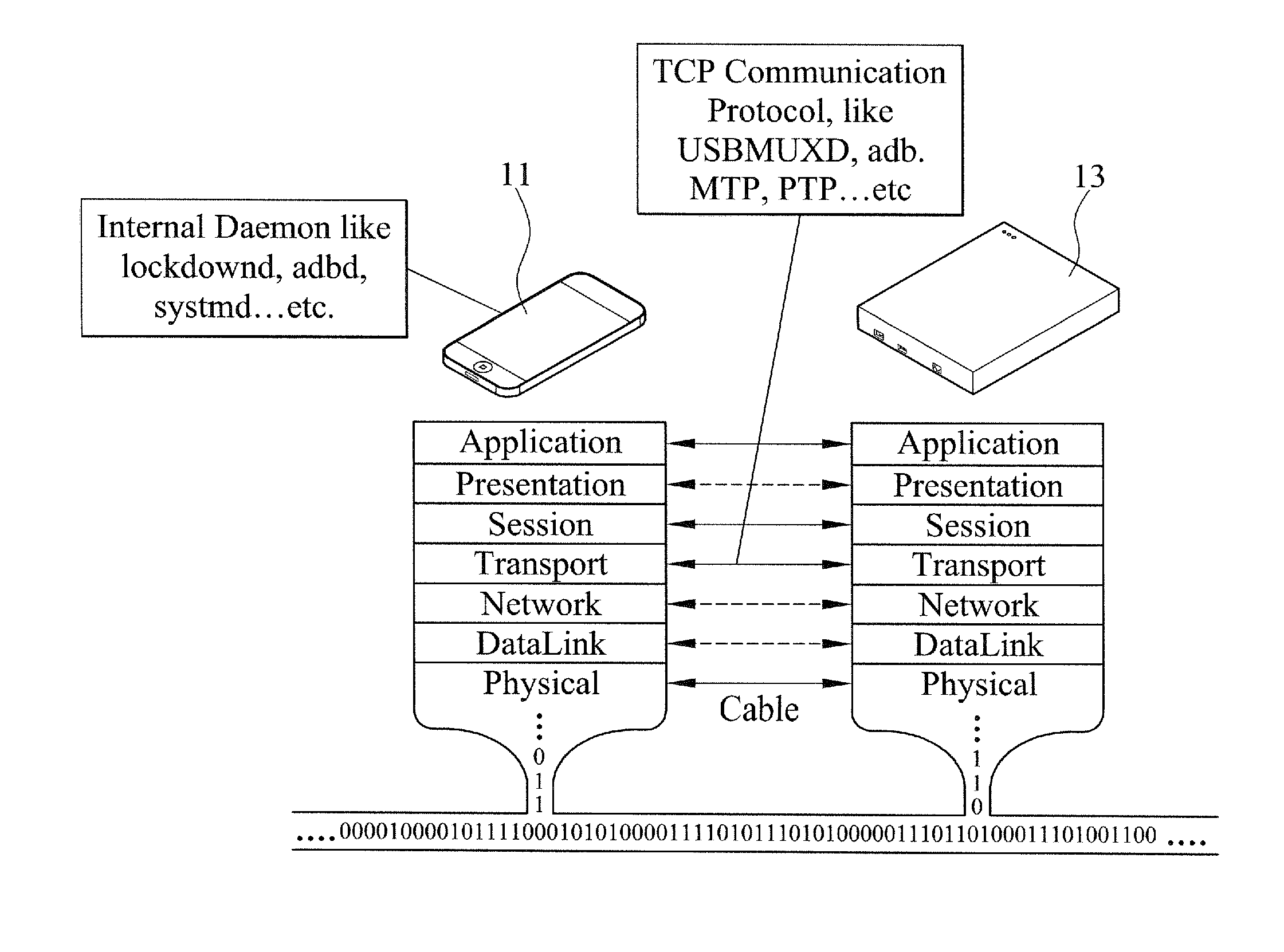
InactiveUS20140250324A1Digital data processing detailsDigital data authenticationTransmission protocolTransport layer
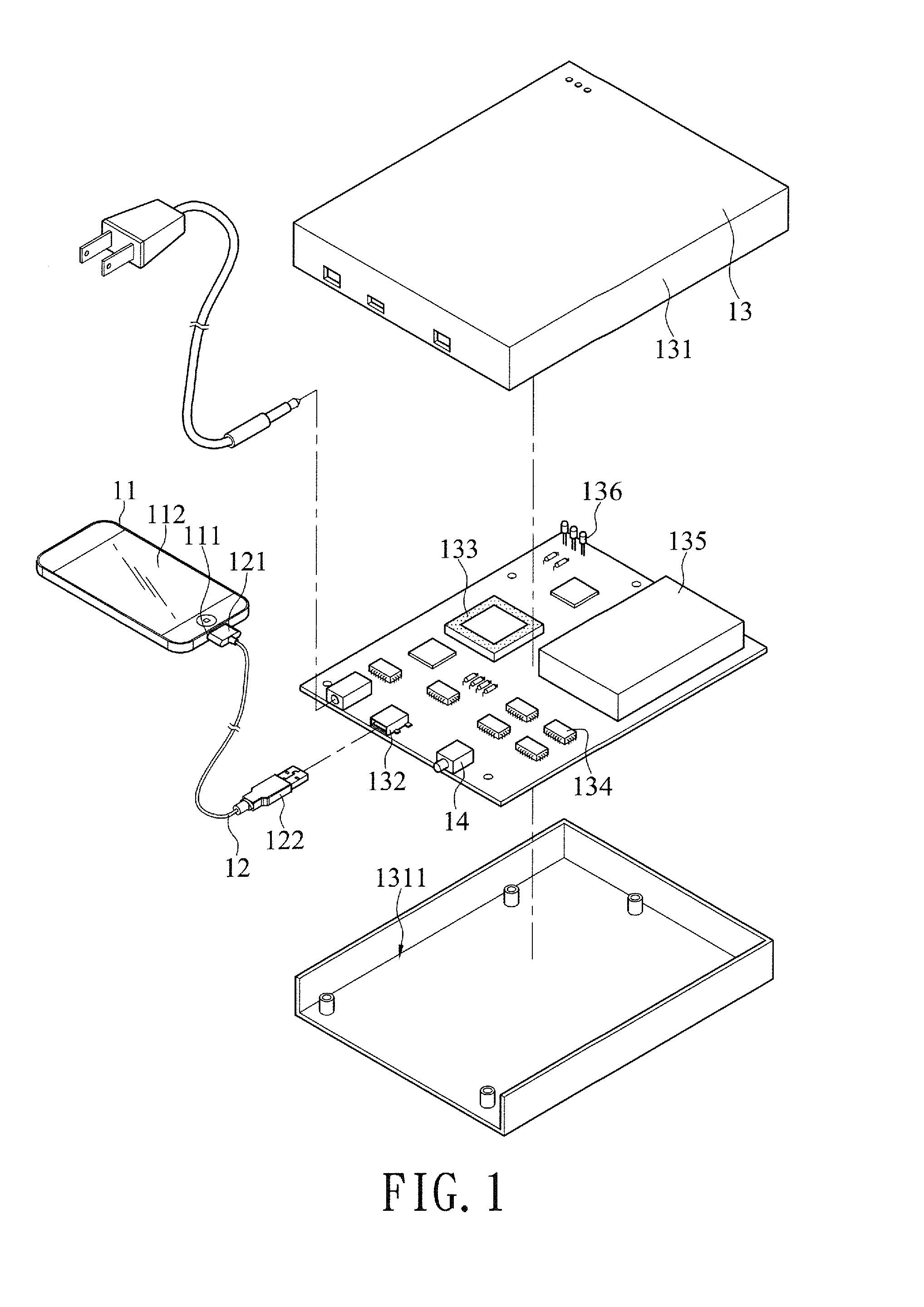
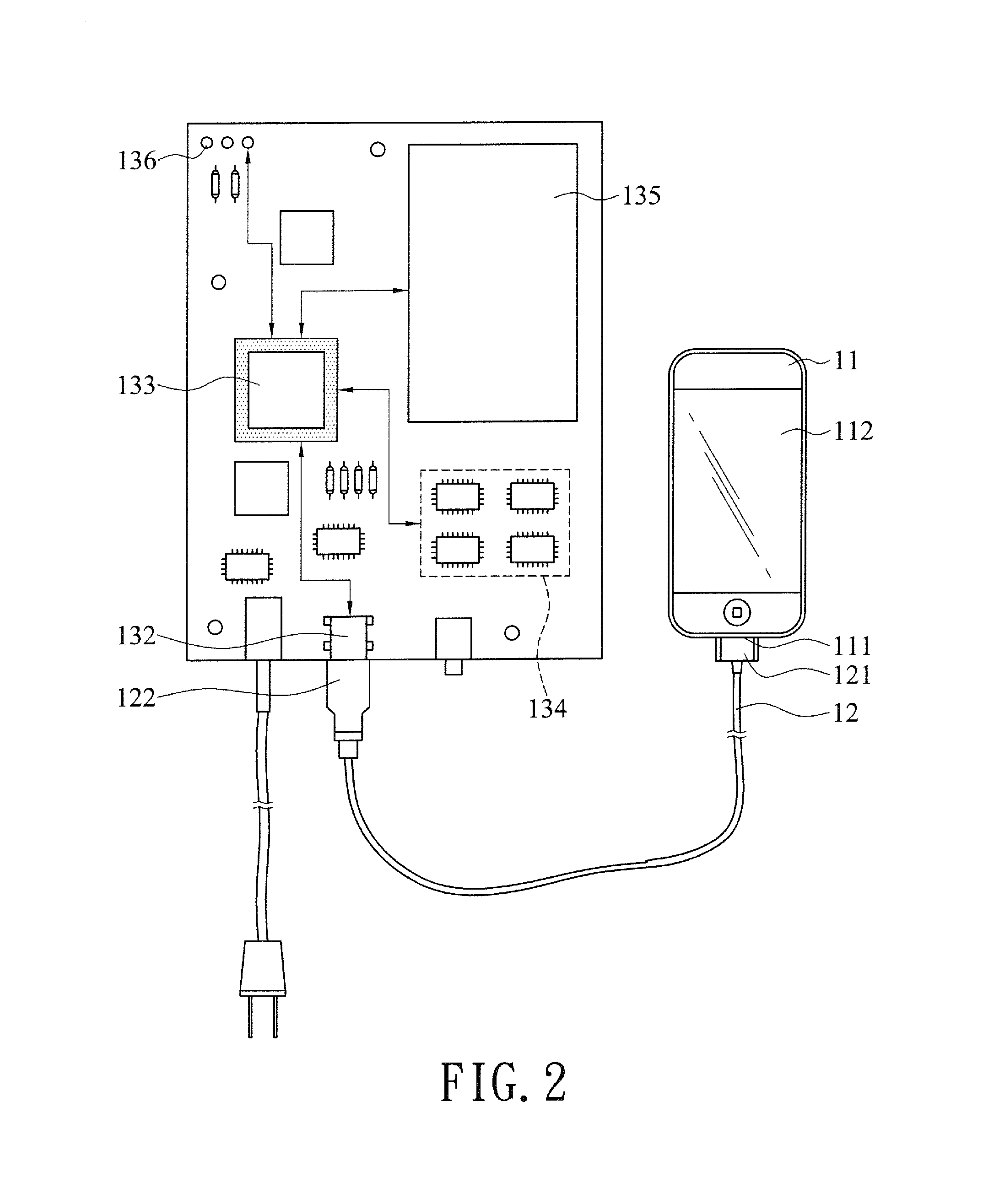
A Smartphone data backup and restoration system on a physical layer is connected to a Smartphone through a data transmission line, and the data backup and restoration system and the Smartphone are identified and paired by a datalink layer and a network layer, and then a transport layer transmits an identification program to the Smartphone, and a session layer completes a trusted connection according to a TCP communication and transmission protocol such as USBMUXD, ADB, MTP, and PTP, so that the Smartphone is capable of performing a data transmission operation including data backup and restoration at a presentation layer and an application layer to improve the convenience of operation and use.
Owner:SHIH SHENG YUAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com