Patents
Literature
335 results about "Network mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network mapping is the study of the physical connectivity of networks e.g. the Internet. Network mapping discovers the devices on the network and their connectivity. It is not to be confused with network discovery or network enumerating which discovers devices on the network and their characteristics such as (operating system, open ports, listening network services, etc.). The field of automated network mapping has taken on greater importance as networks become more dynamic and complex in nature.
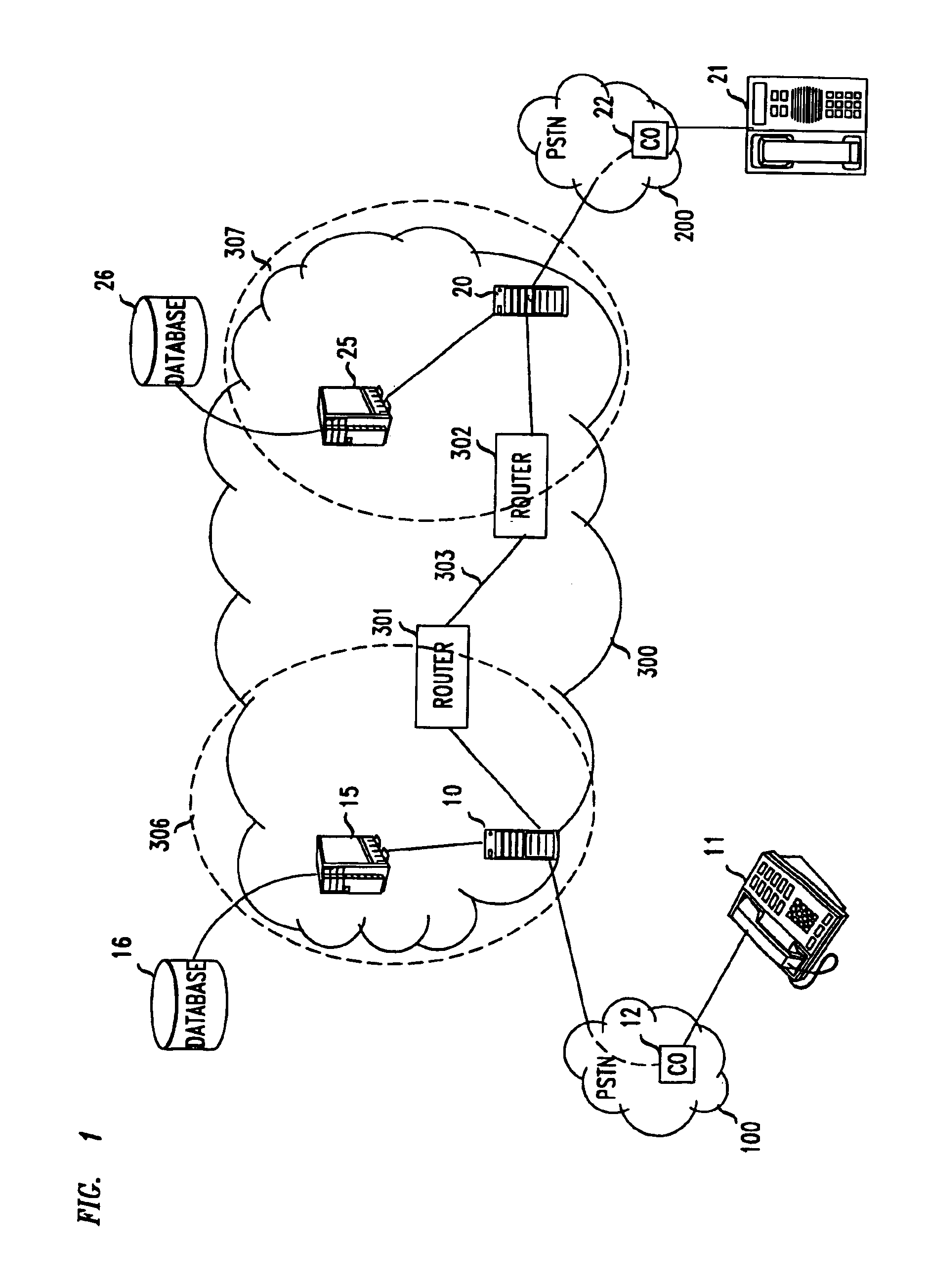
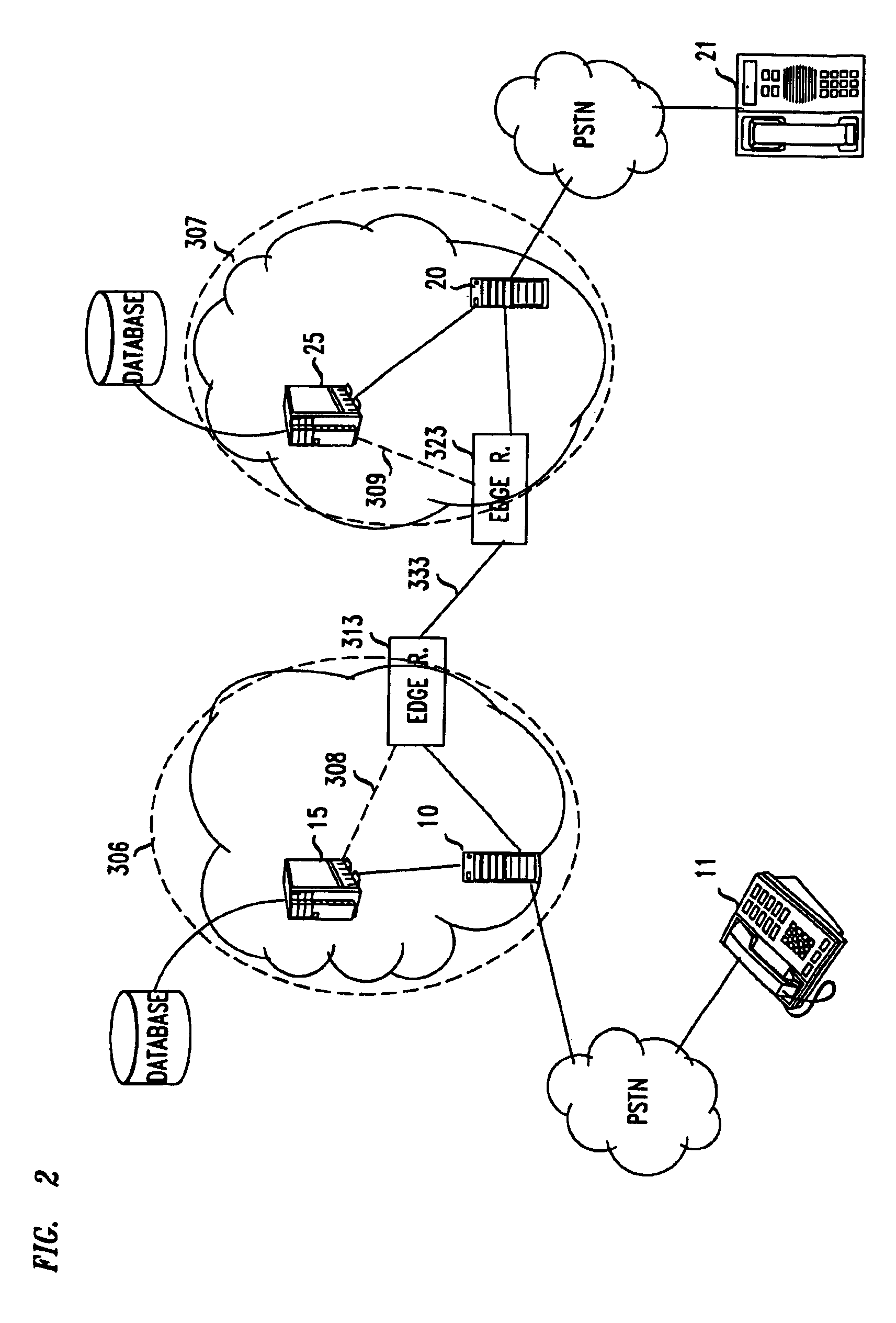
Network performance monitoring in a content delivery system
InactiveUS20100217801A1Multiple digital computer combinationsLocation information based serviceDomain nameIp address
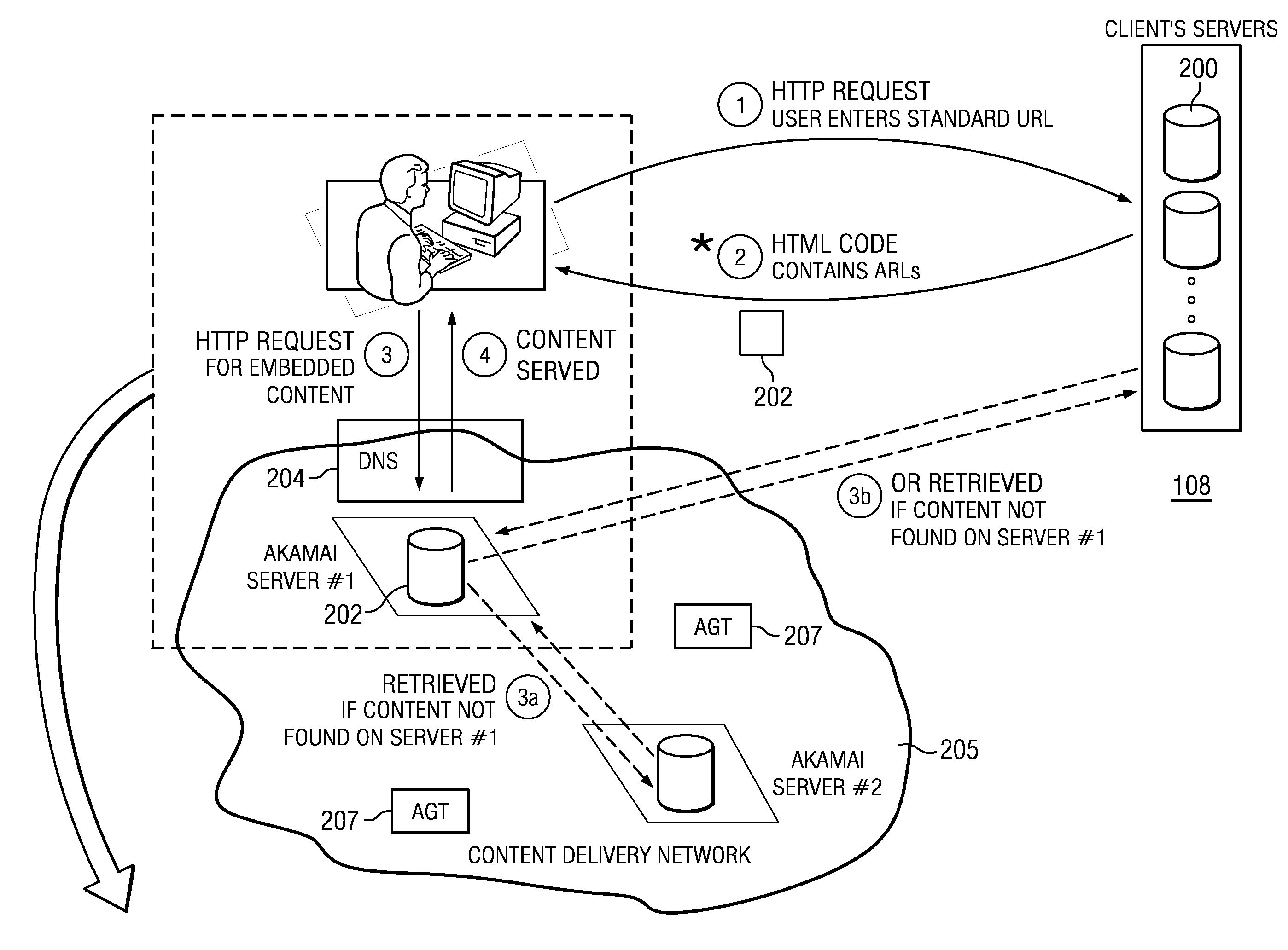
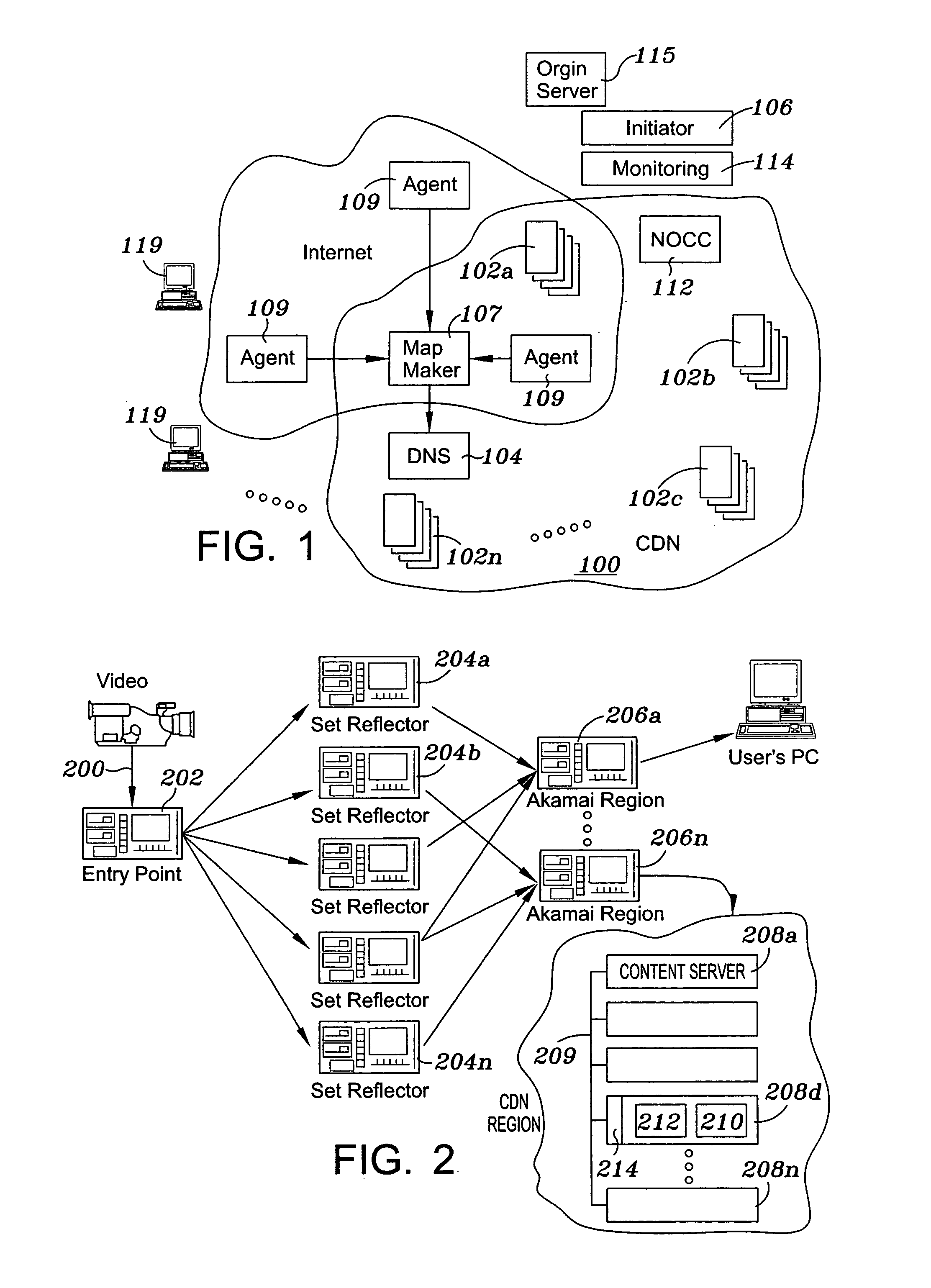
A method for Internet content delivery in a content delivery network established at network locations, the content delivery network comprising a plurality of content servers for serving content resources. The plurality of content servers includes a plurality of subsets of content servers, each subject being located at one of a plurality of Internet data centers. For each Internet Protocol (IP) address block from which requests for content resources are expected to be received, the method generates a candidate list of Internet data centers to be used to service the requests for content resources. For the IP address block, the method selects at least one of the Internet data centers from the candidate list to be used to service the requests for content resources. The selected Internet data center for the IP address block is written into a network map. The selecting step is carried out concurrently for each IP address block from which requests for content resources are expected to be received such that the network map comprises the selected Internet data center for each IP address block. The network map is then provided to a domain name service (DNS) associated with the content delivery network. In response to a DNS query received at the domain name service associated with the content delivery network, the network map is used to identify one of the Internet data centers from the candidate list to be used to service a request for a content resource.
Owner:AKAMAI TECH INC
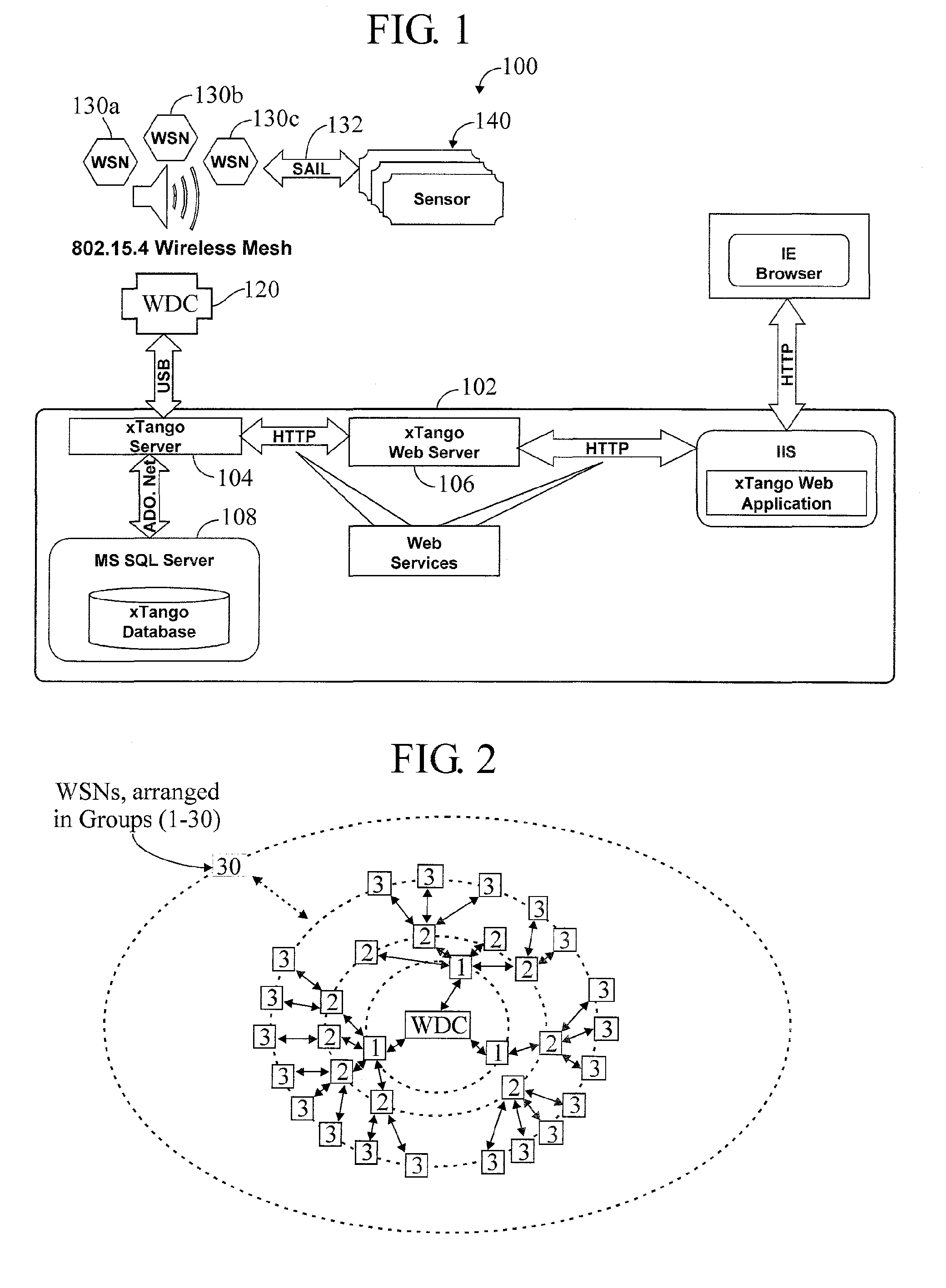
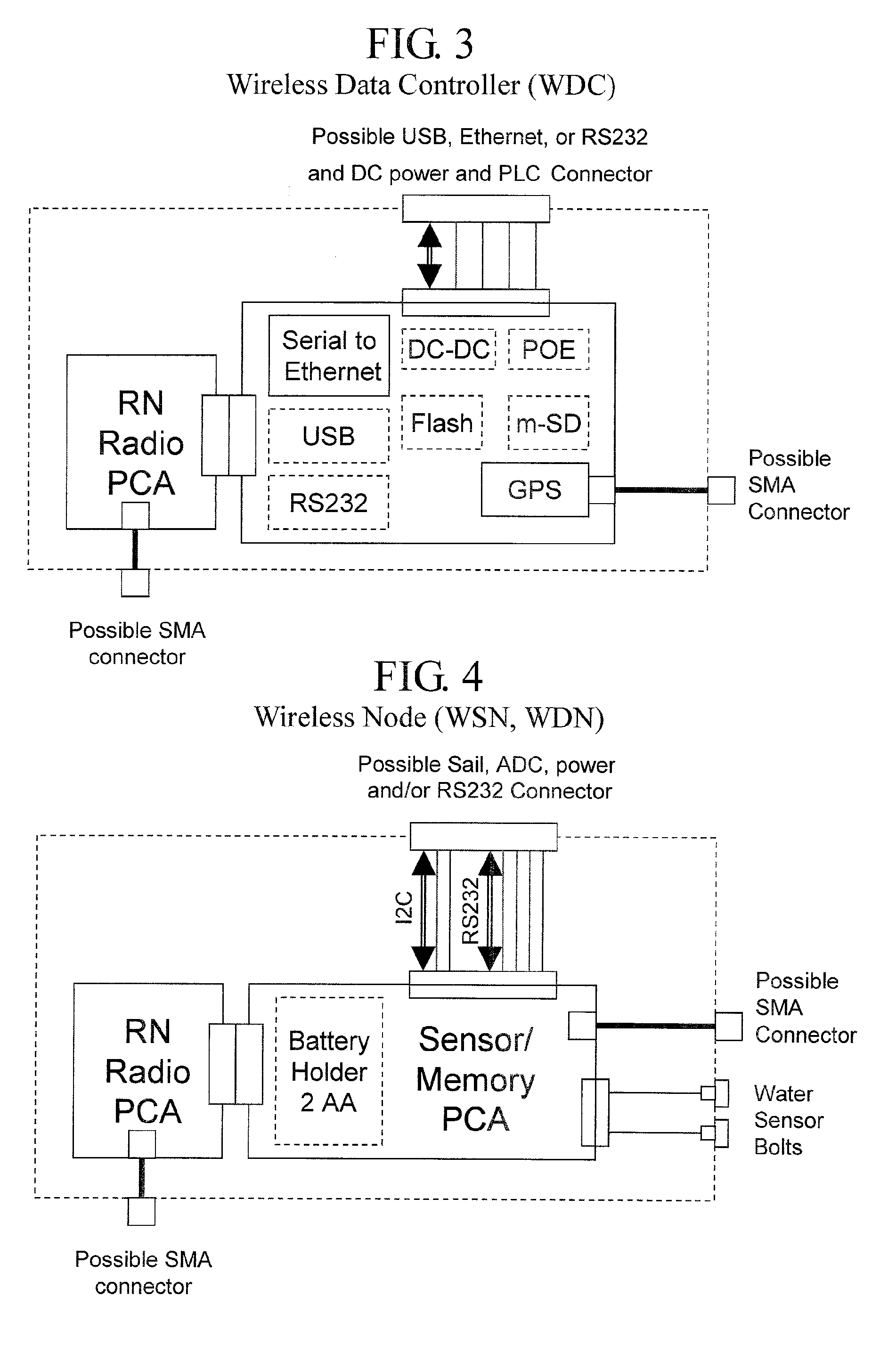
Wireless Data Networking
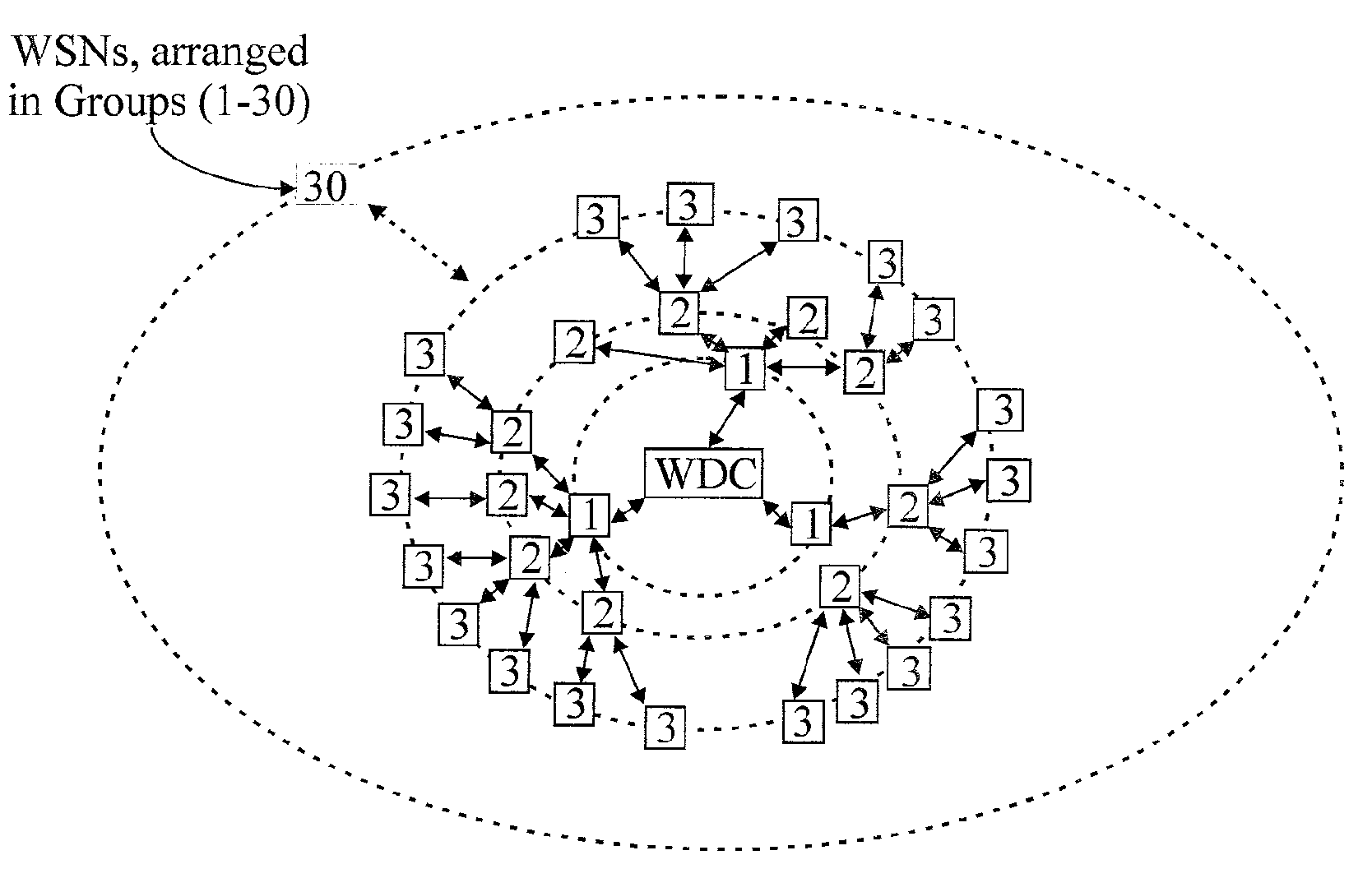
ActiveUS20080291855A1Low powerBetter read rateEnergy efficient ICTPower managementWireless dataNetwork mapping
A meshing network comprising one full function controller (WDC) and a plurality of nodes (WDN, WSN), that is RF quiet capable with very low power consumption and the ability to quickly heal itself and create new network paths. The network uses an addressing scheme that allows for each node to not have a network map but still be able to route messages. A piping scheme allows a mesh to become a high throughput network. A sensor rail protocol definition allows sensor devices to connect to nodes and route messages through the network.
Owner:RAYTHEON CO
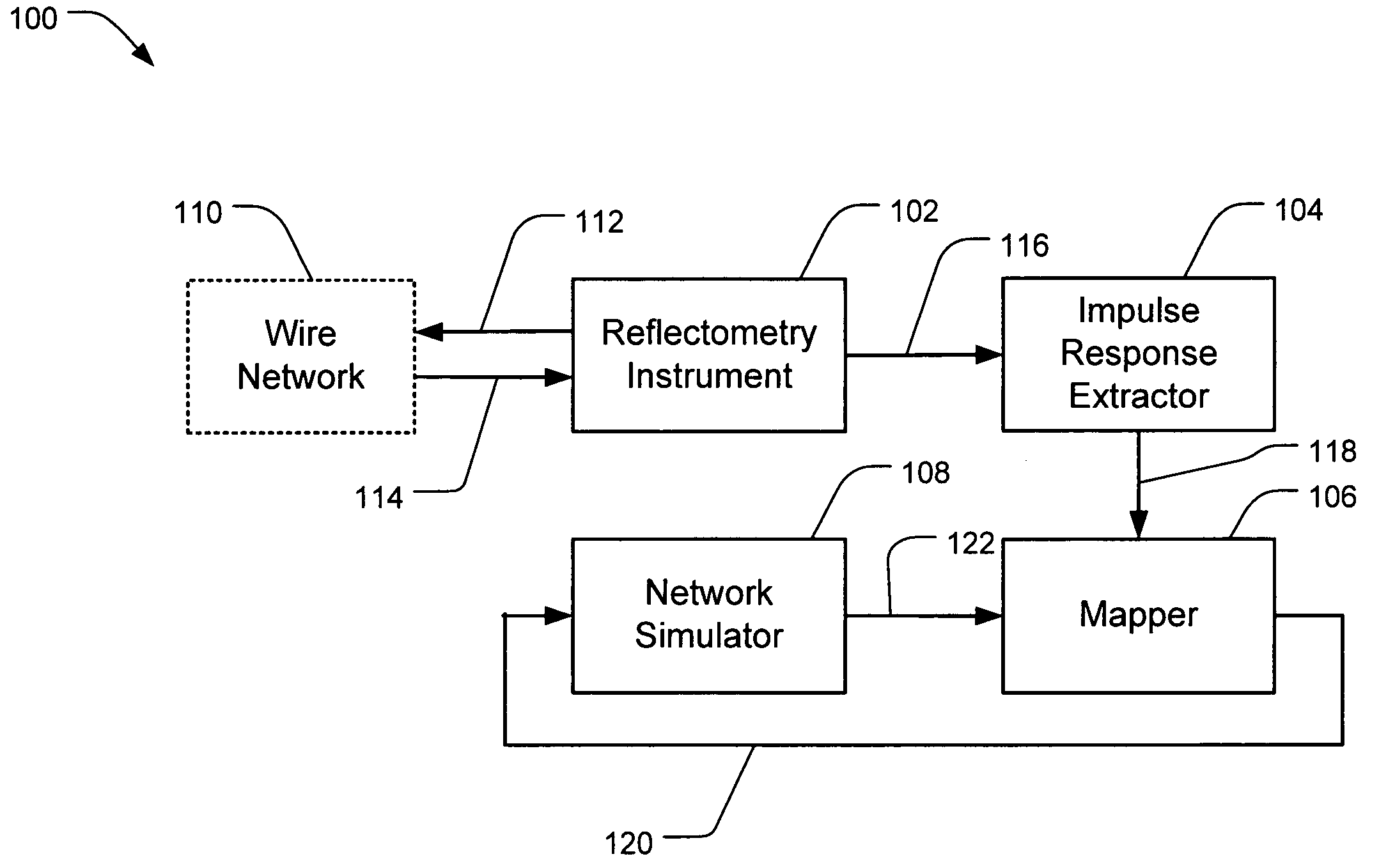
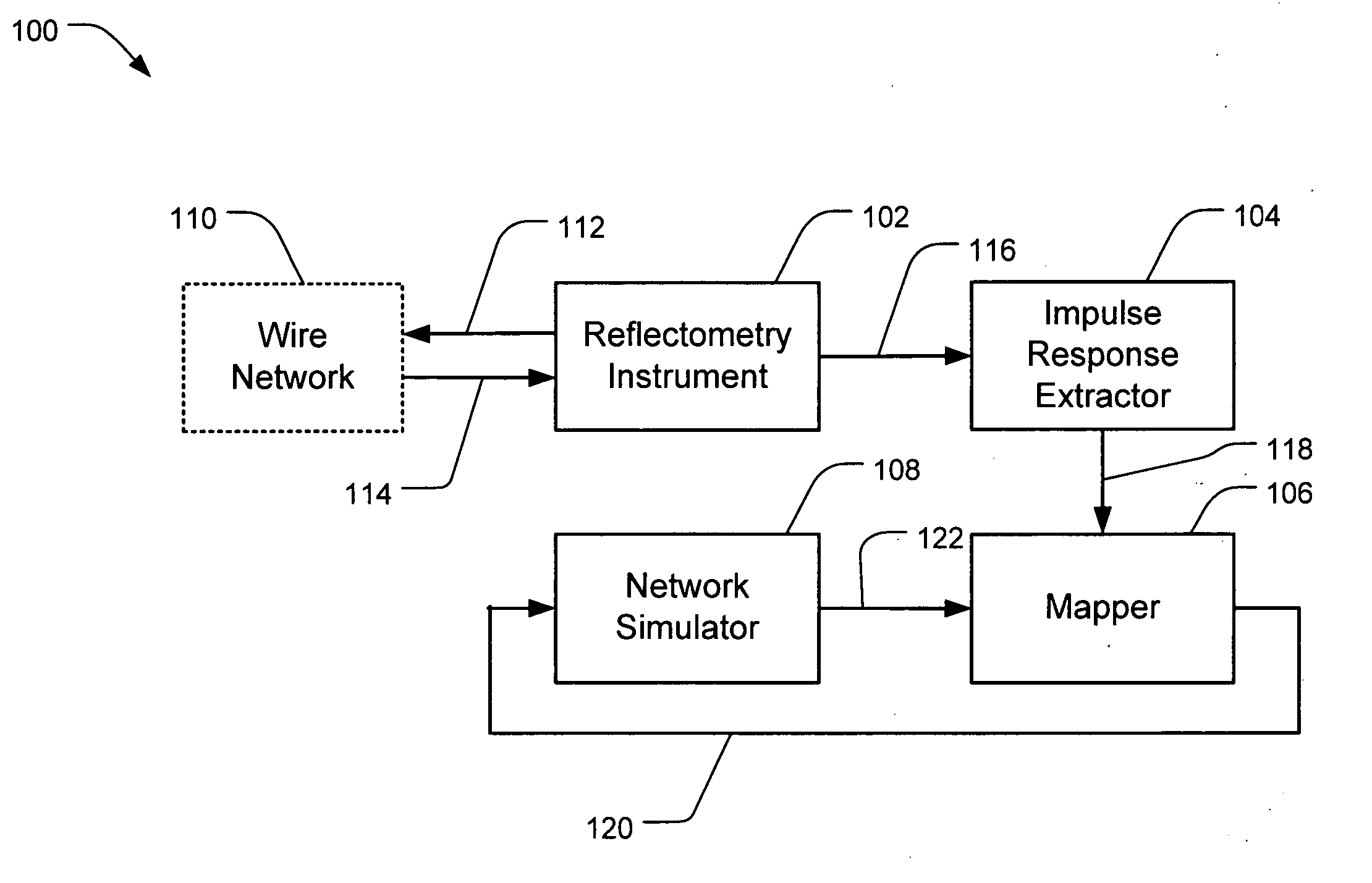
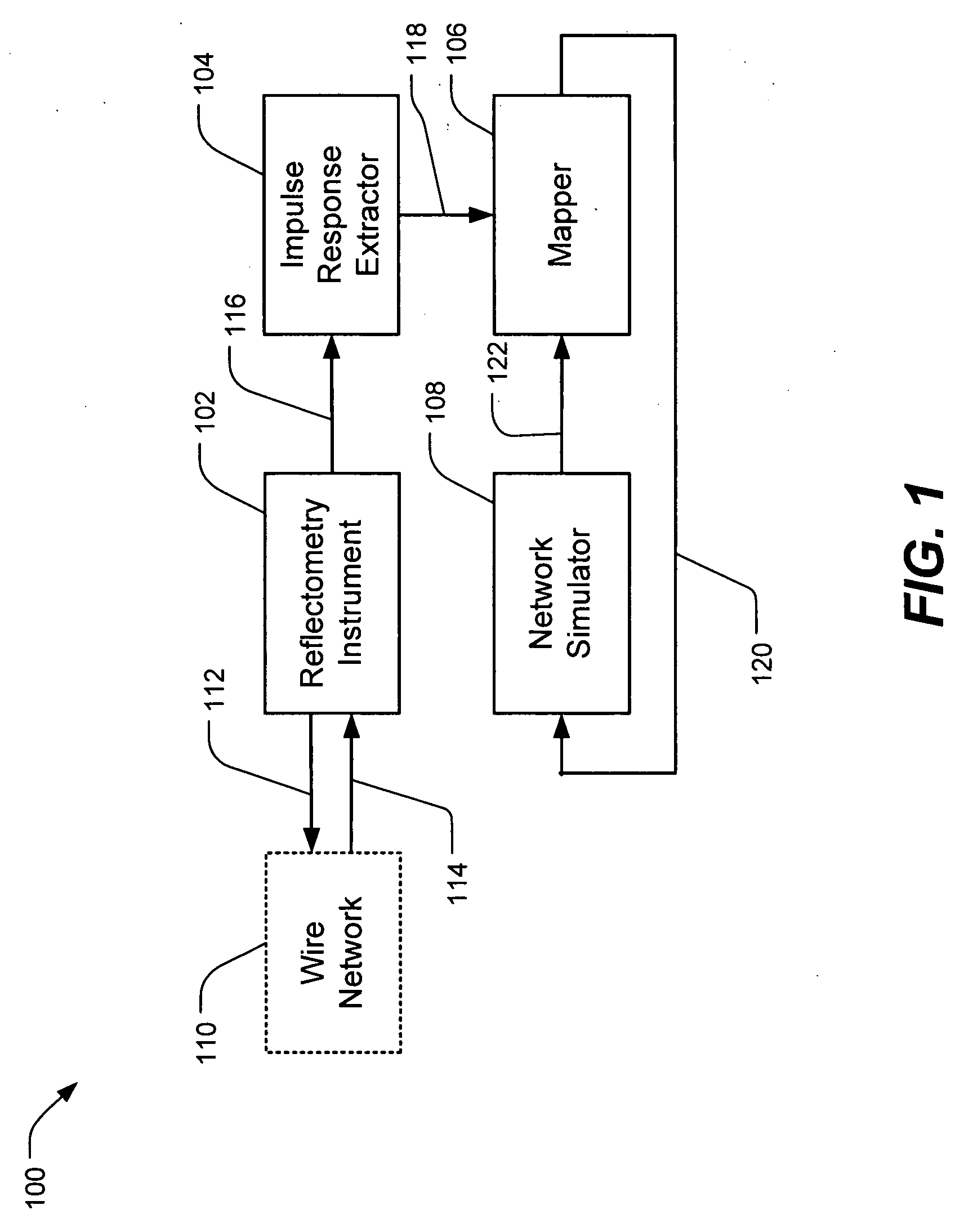
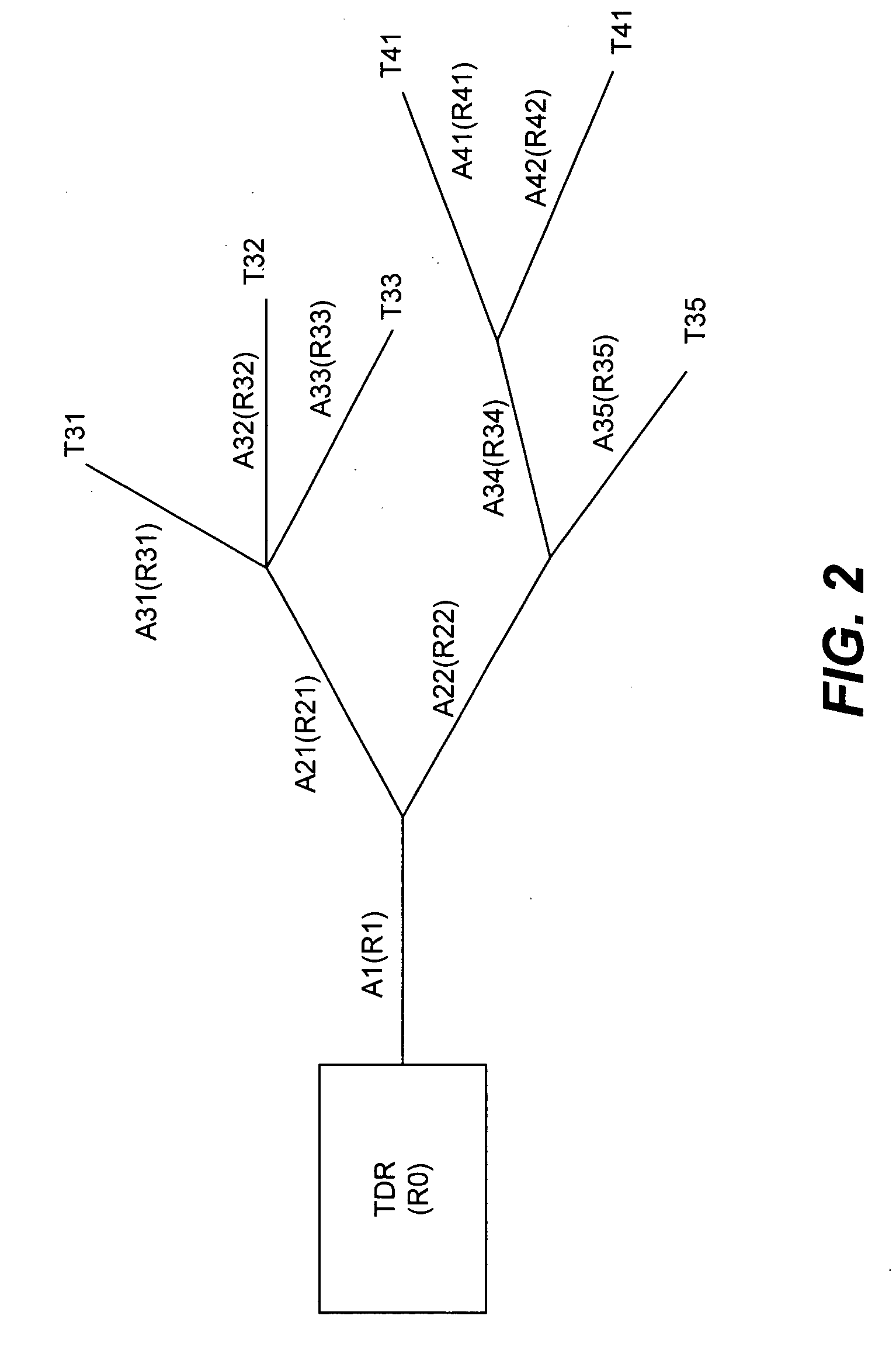
Wire network mapping method and apparatus using impulse responses
ActiveUS7282922B2Reduce the differenceFault location by pulse reflection methodsFinite impulse responseNetwork model
A method and apparatus for mapping a wire network is disclosed. The method includes obtaining a reflectometry test signal of the wire network. An estimated network impulse response is estimated from the reflectometry response. A wire network model is then initialized, and iteratively improved by simulating an impulse response of the wire network model and adjusting the wire network model to reduce differences between the simulated impulse response and estimated network impulse response.
Owner:UNIV OF UTAH RES FOUND
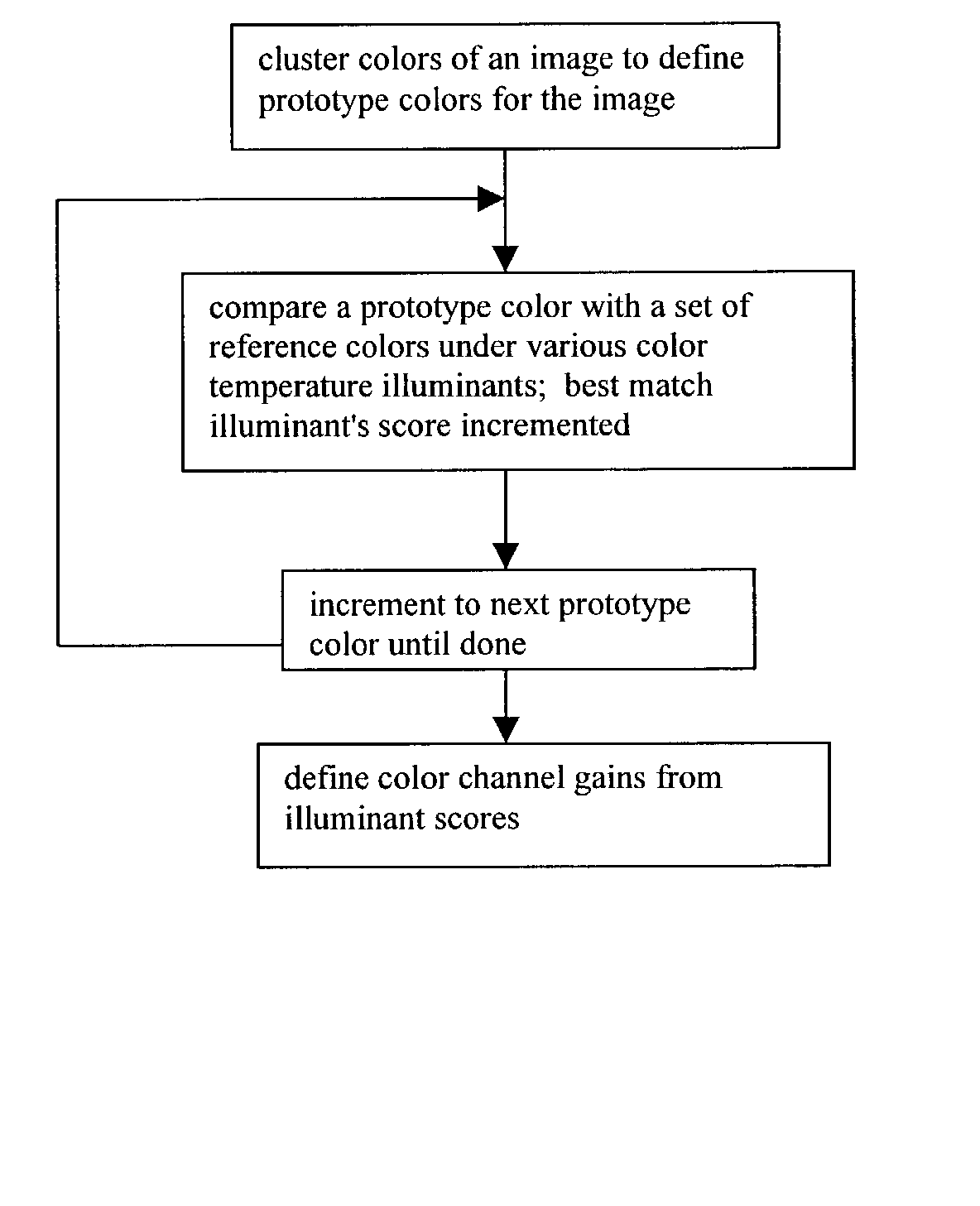
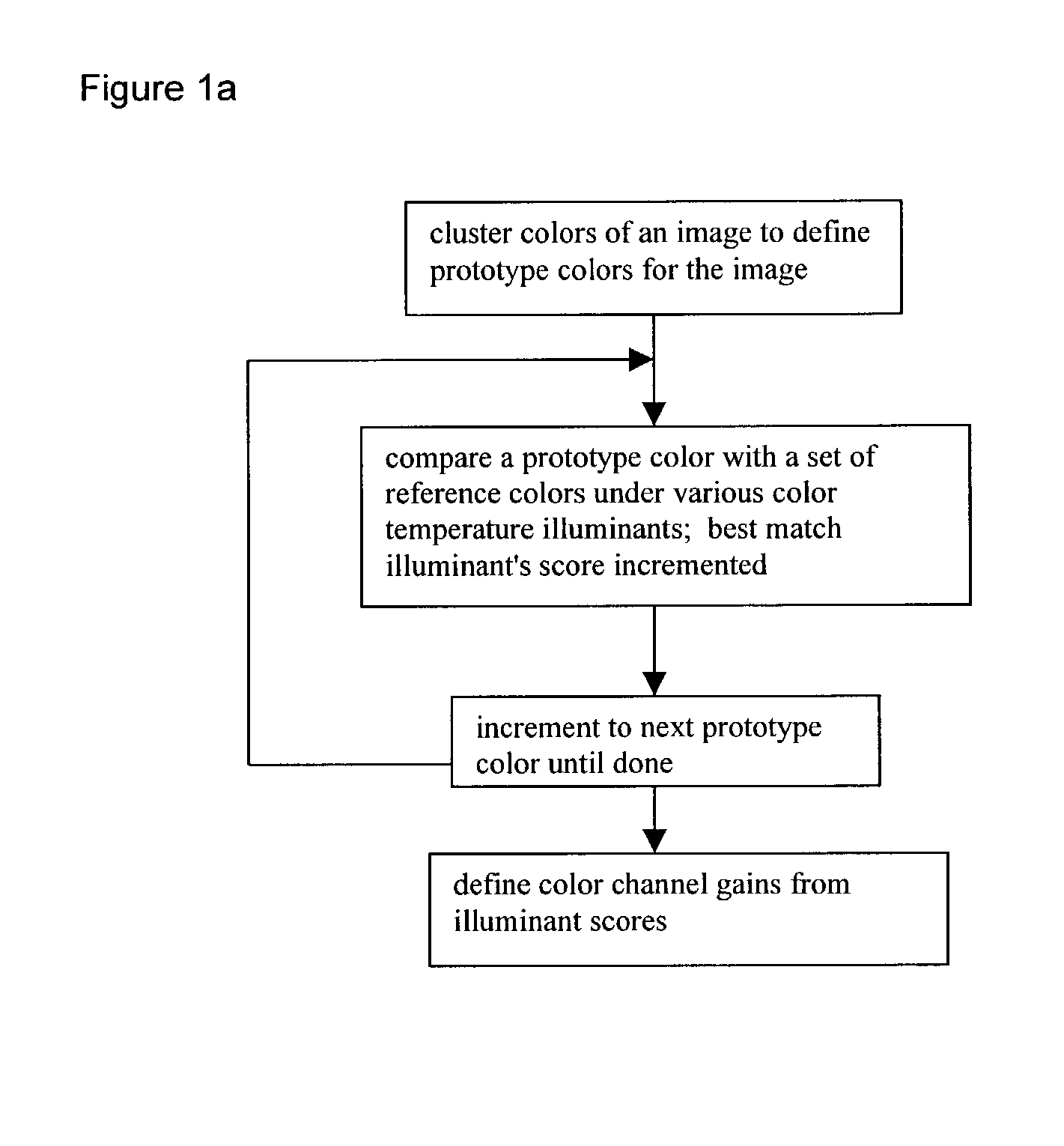
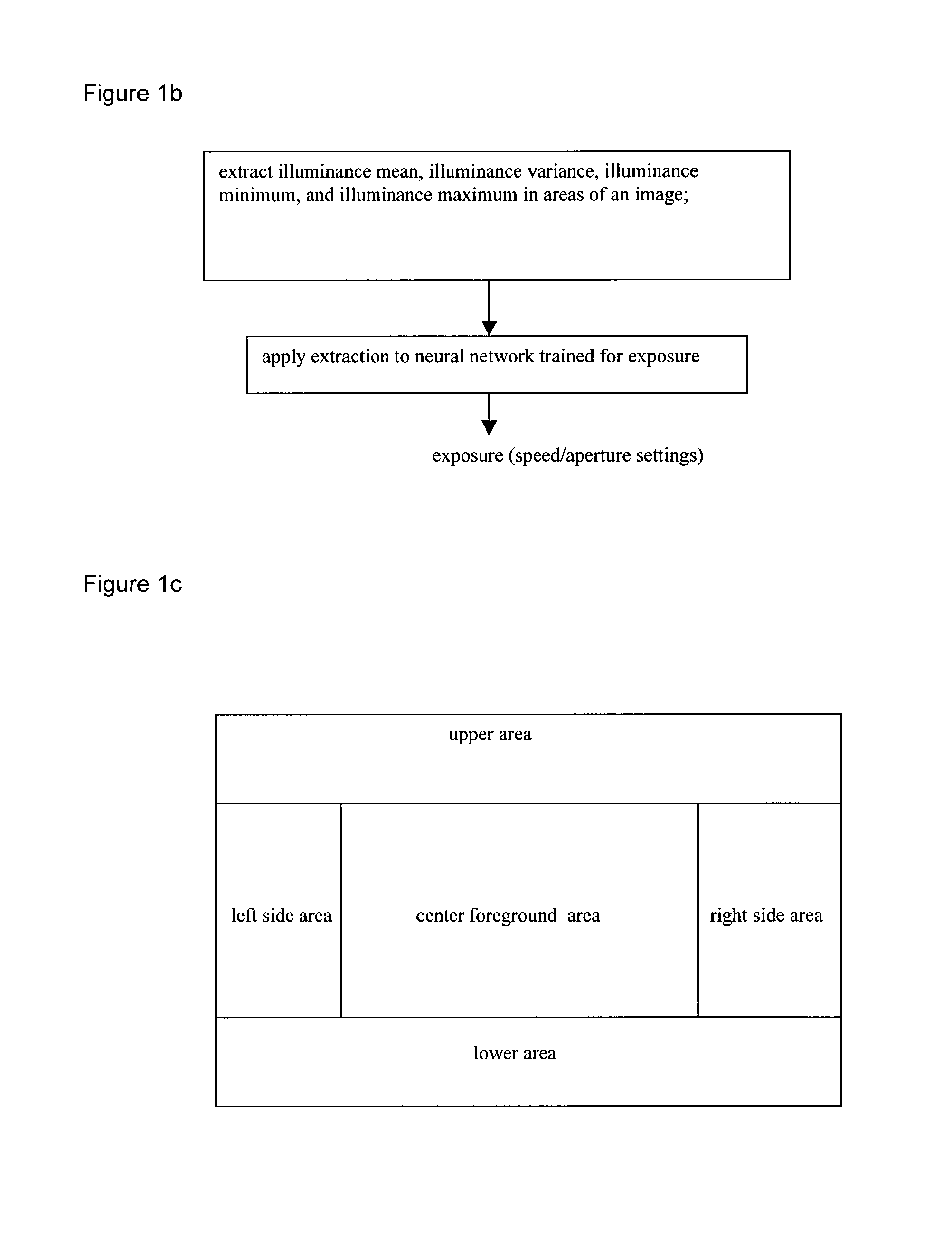
Automatic white balancing via illuminant scoring autoexposure by neural network mapping
ActiveUS20030052978A1Easy to useHigh scoreTelevision system detailsColor signal processing circuitsIlluminanceComputer science
Automatic white balancing and / or autoexposure as useful in a digital camera extracts color channel gains from comparisons of image colors with reference colors under various color temperature illuminants and / or extracts exposure settings from illuminance mean, illuminance variance, illuminance minimum, and illuminance maximum in areas of an image with a trained neural network.
Owner:TEXAS INSTR INC
Client-side method for identifying an optimum server
InactiveUS7299291B1Improve service qualityQuality improvementMultiple digital computer combinationsTransmissionTraffic capacityQuality of service
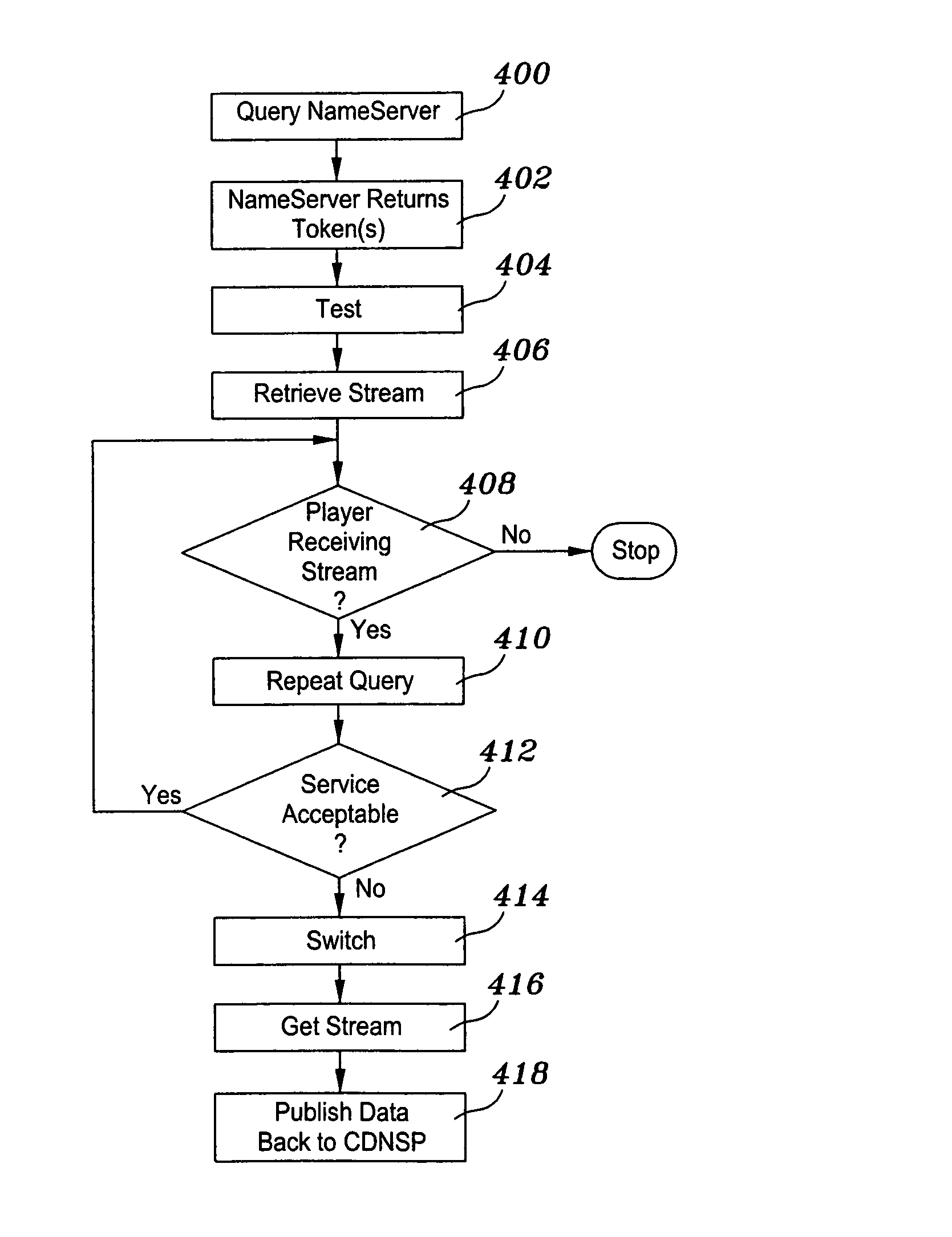
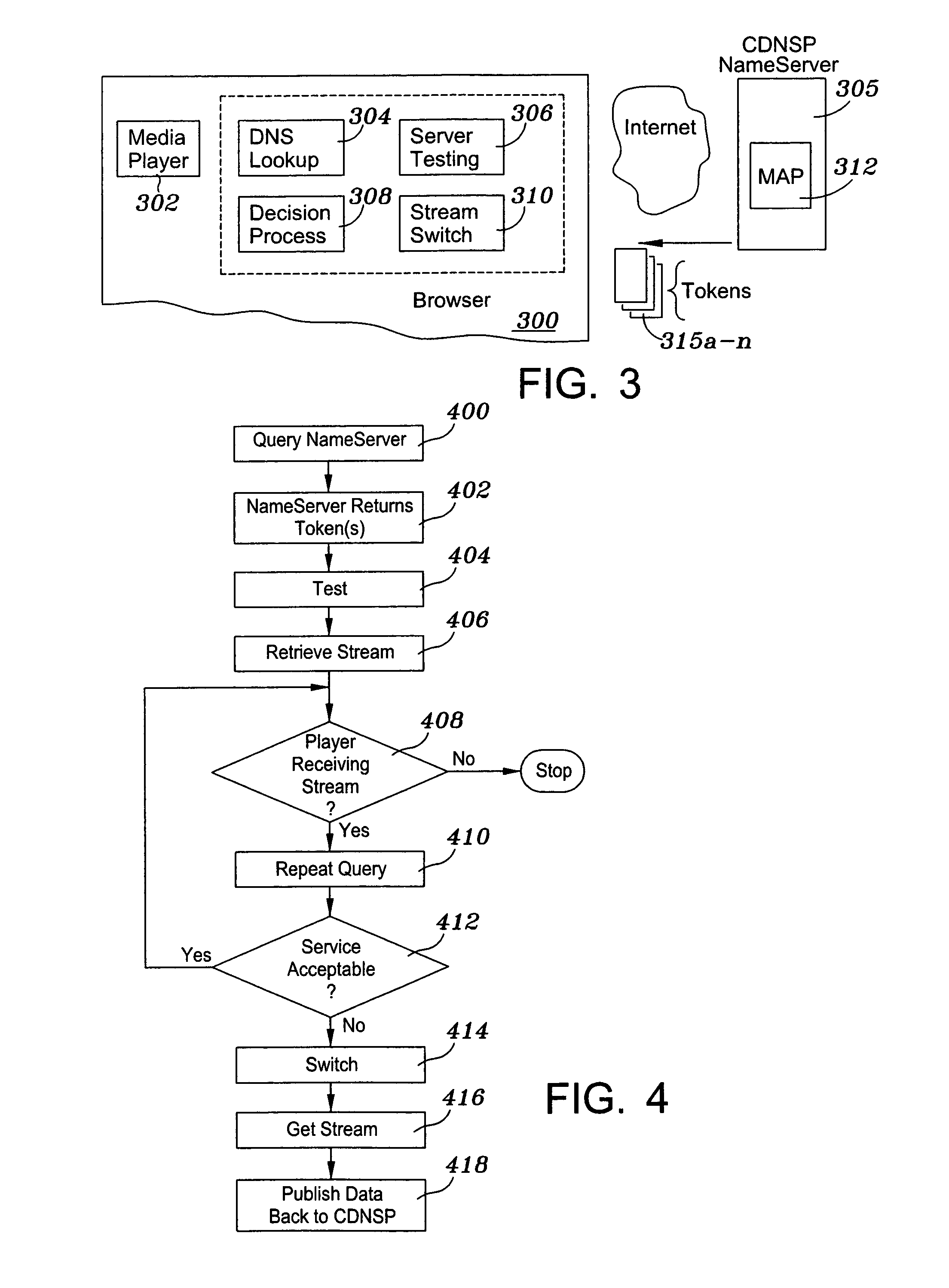
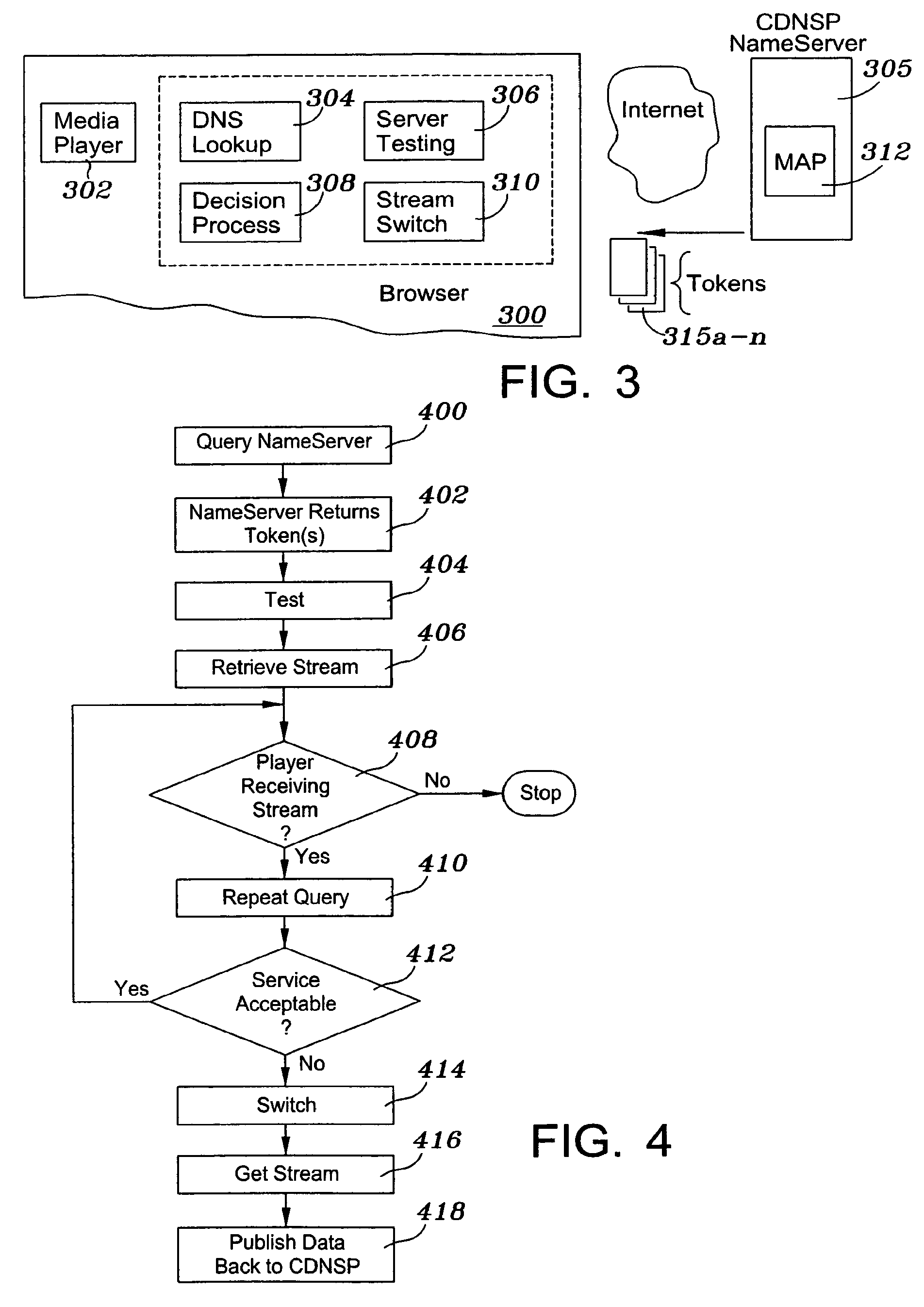
A client player performs a query to a nameserver against a network map of Internet traffic conditions. The query is made asking for a particular service (e.g., RTSP) via a particular protocol (TCP) in a particular domain. In response, the nameserver returns a set of one or more tokens, with each token defining a machine or, in the preferred embodiment, a group of machines, from which the player should seek to obtain the stream. The player may then optionally perform one or more tests to determine which of a set of servers provides a best quality of service for the stream. That server is then used to retrieve the stream. Periodically, the client player code repeats the query during stream playback to determine whether there is a better source for the stream. If a better source exists, the player performs a switch to the better stream source “on the fly” if appropriate to maintain and / or enhance the quality of service. Preferably, the client player publishes data identifying why it selected a particular server, and such data may be used to augment the network map used for subsequent request routing determinations.
Owner:AKAMAI TECH INC
Intrusion event correlation with network discovery information
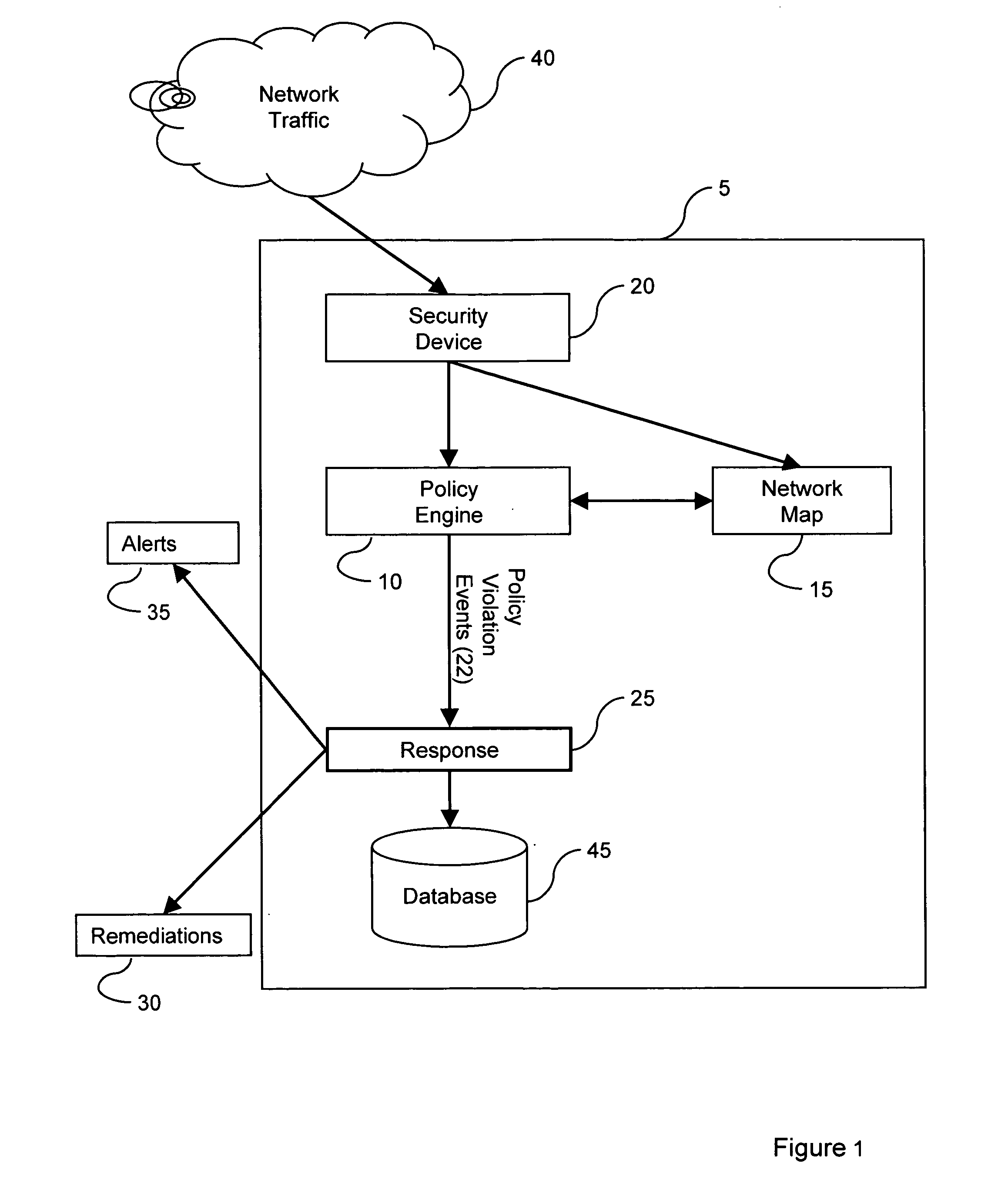
ActiveUS20080244741A1Minimize false positiveMinimize false positivesMemory loss protectionError detection/correctionNetwork topologyNetwork mapping
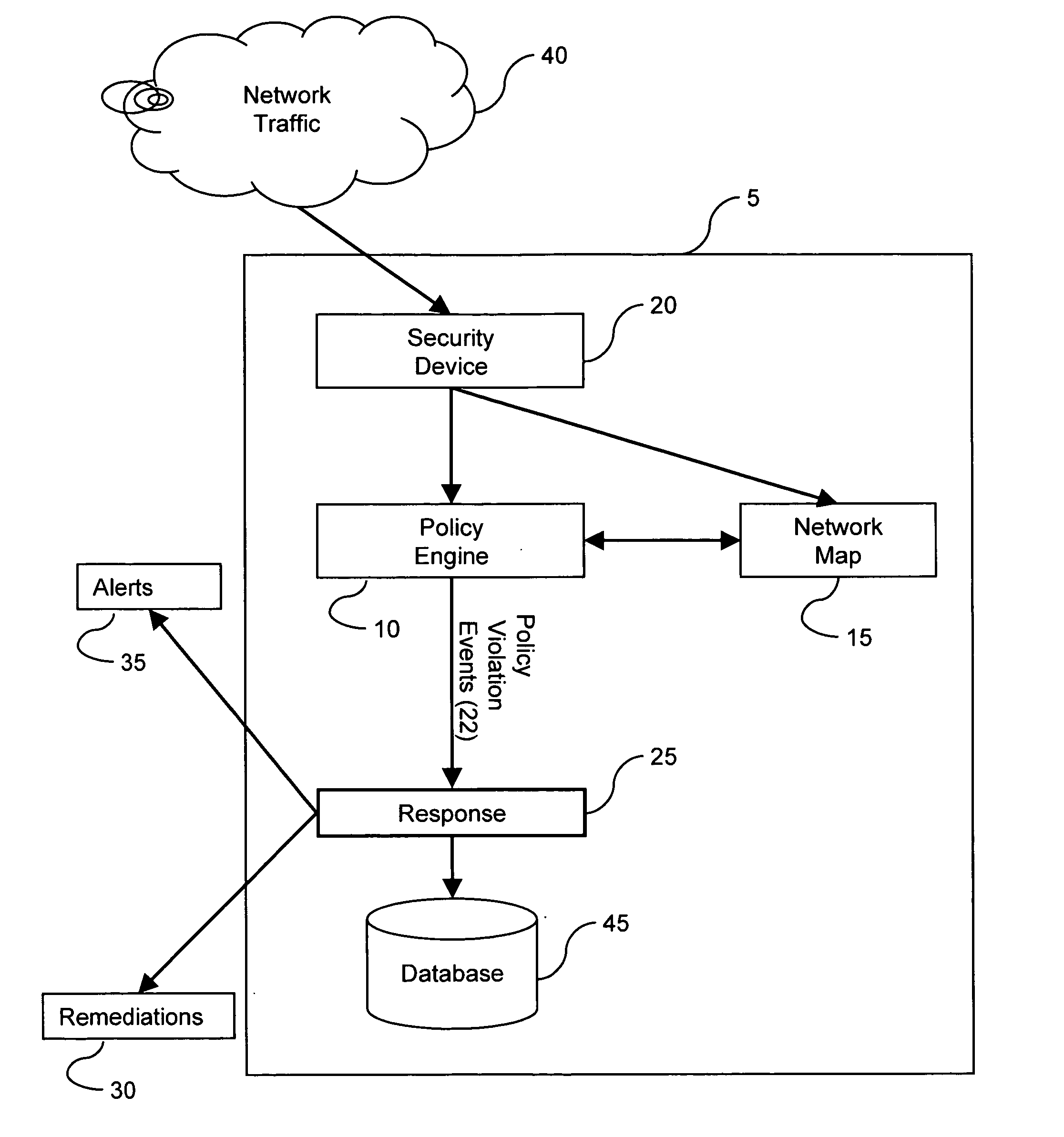
A policy component comprises policy configuration information. The policy configuration information contains one or more rules. Each rule and group of rules can be associated with a set of response actions. As the nodes on the monitored networks change or intrusive actions are introduced on the networks, network change events or intrusion events are generated. The policy component correlates network change events and / or intrusions events with network map information. The network map contains information on the network topology, services and network devices, amongst other things. When certain criteria is satisfied based on the correlation, a policy violation event may be issued by the system resulting in alerts or remediations.
Owner:CISCO TECH INC
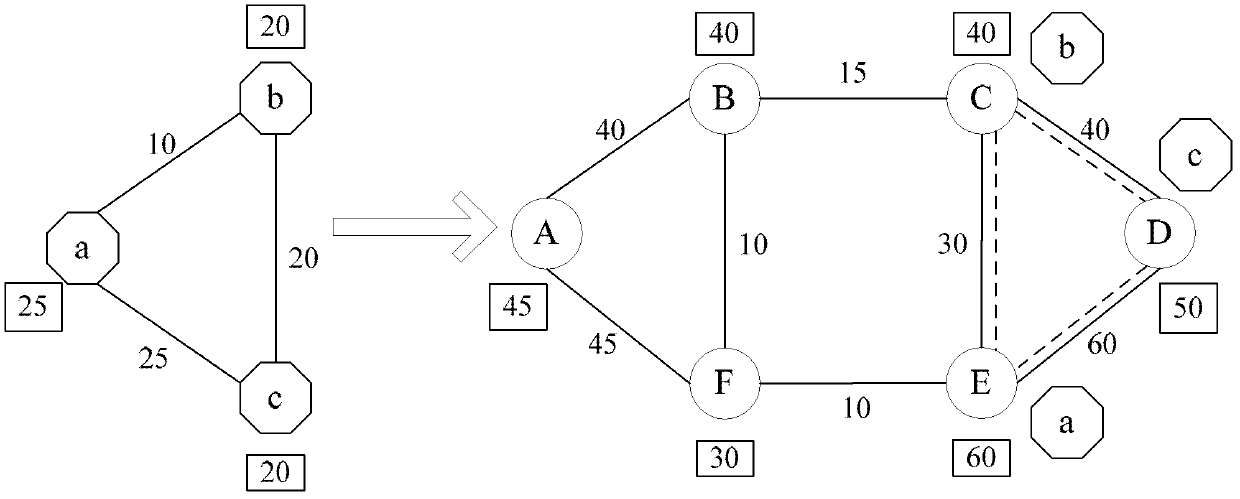
Method for generating a network map
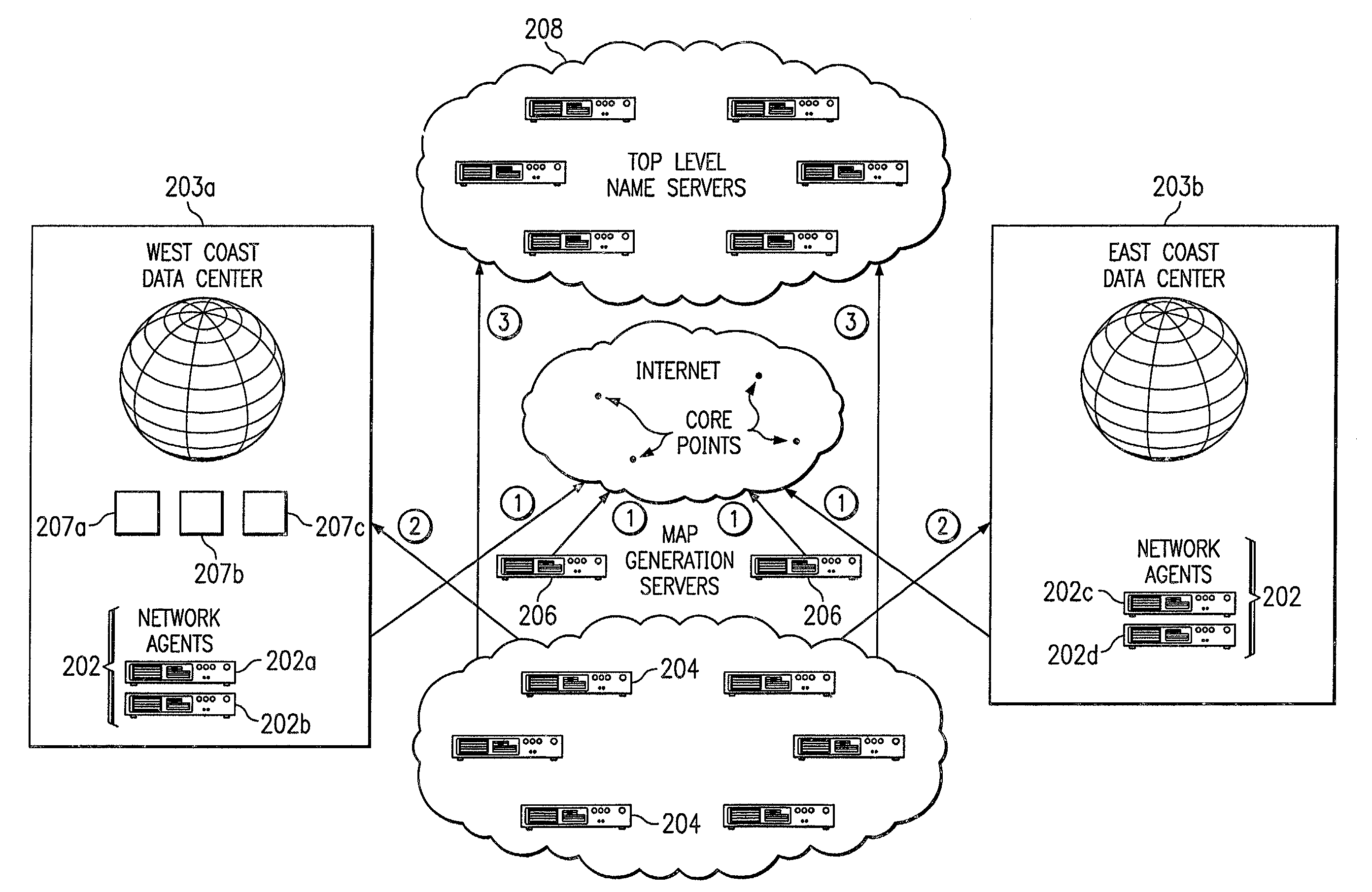
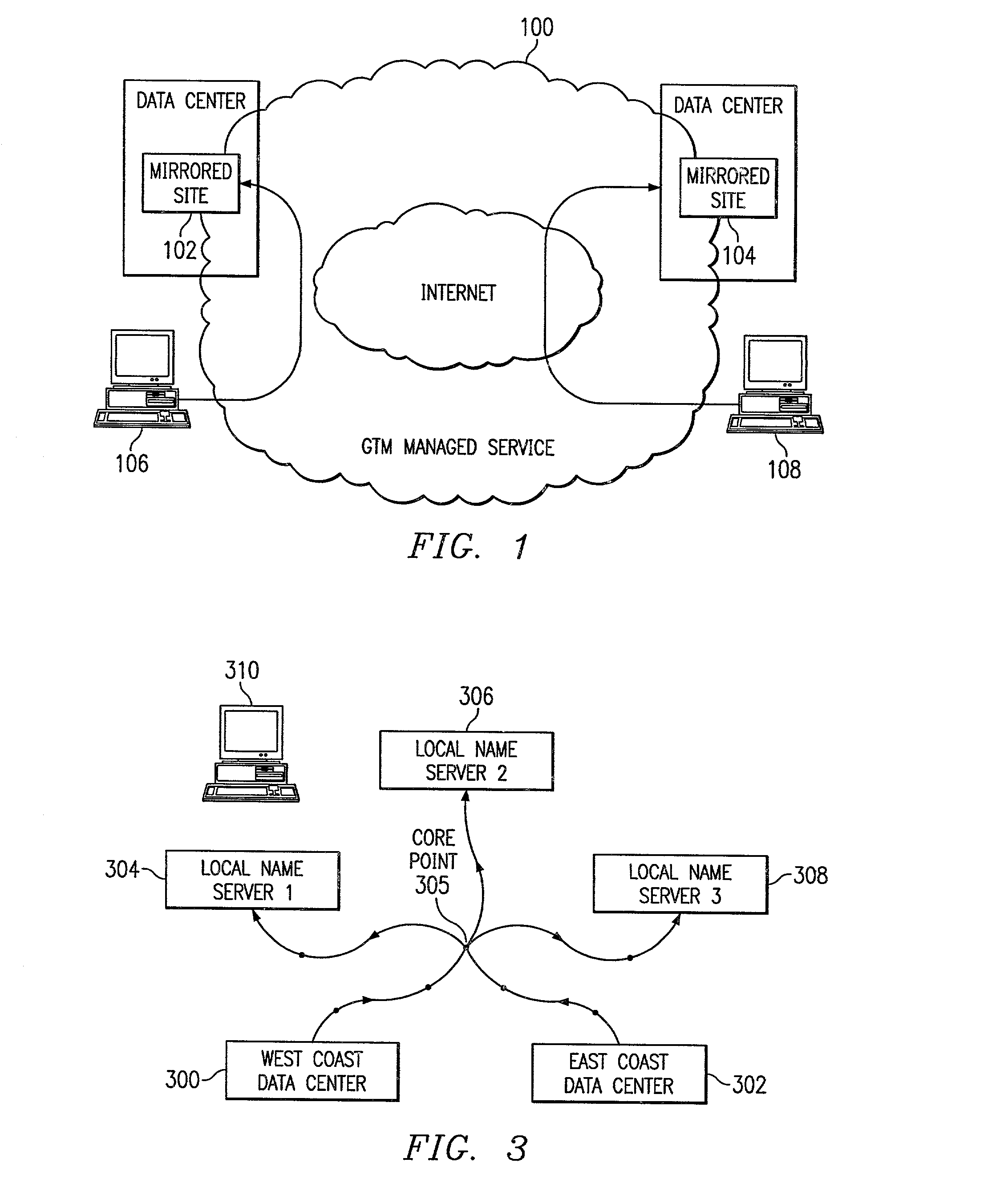
InactiveUS7251688B2Reduce dimensionalityOvercome problemsDigital computer detailsData switching networksWeb siteName server
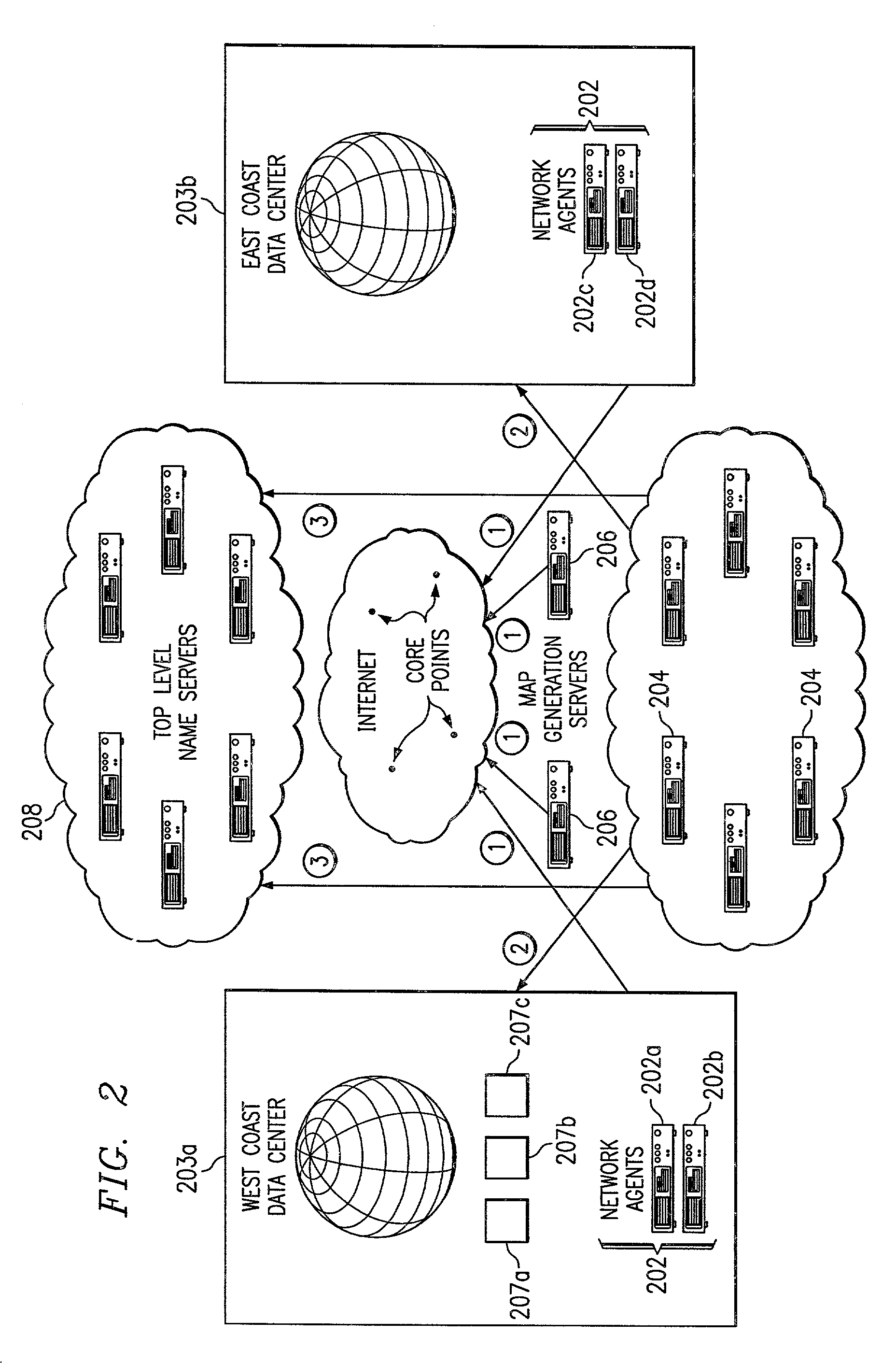
An intelligent traffic redirection system performs global load balancing for Web sites located at mirrored data centers. The system relies on a network map that is generated continuously, preferably for the user-base of the entire Internet. Instead of probing each local name server (or other host) that is connectable to the mirrored data centers, the network map identifies connectivity with respect to a much smaller set of proxy points, called “core” (or “common”) points. A core point is representative of a set of local name servers (or other hosts) that, from a data center's perspective, share the point. To discover a core point, an incremental trace route is executed from each of the set of mirrored data centers to a local name server that may be used by client to resolve a request for a replica stored at the data centers. An intersection of the trace routes at a common routing point is then identified. Thus, for example, the common routing point may be the first common point for the trace routes when viewed from the perspective of the data centers (or the last common point for the trace routes when viewed from the perspective of the local name server). The common routing point is then identified as the core point for the local name server.
Owner:AKAMAI TECH INC
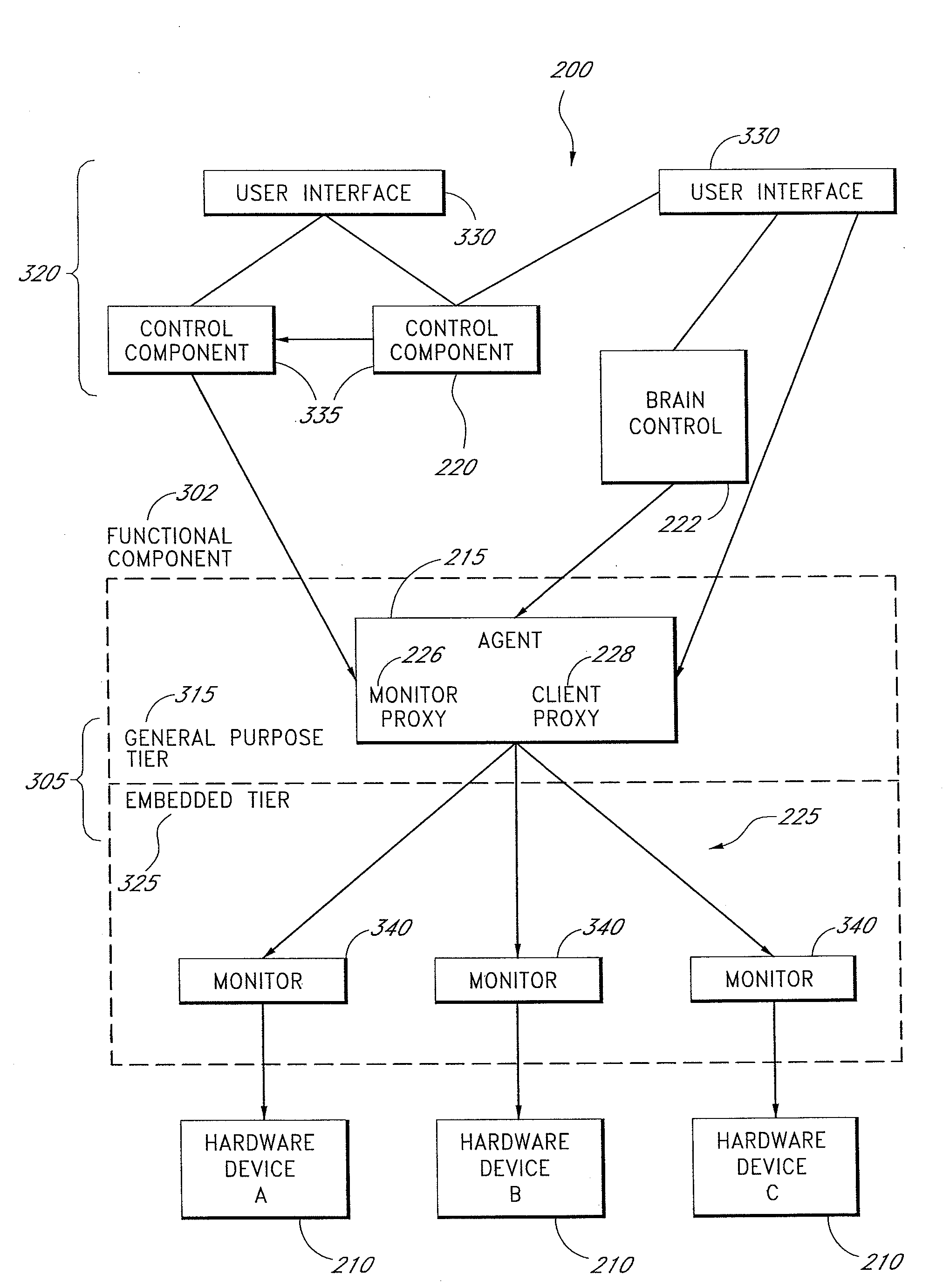
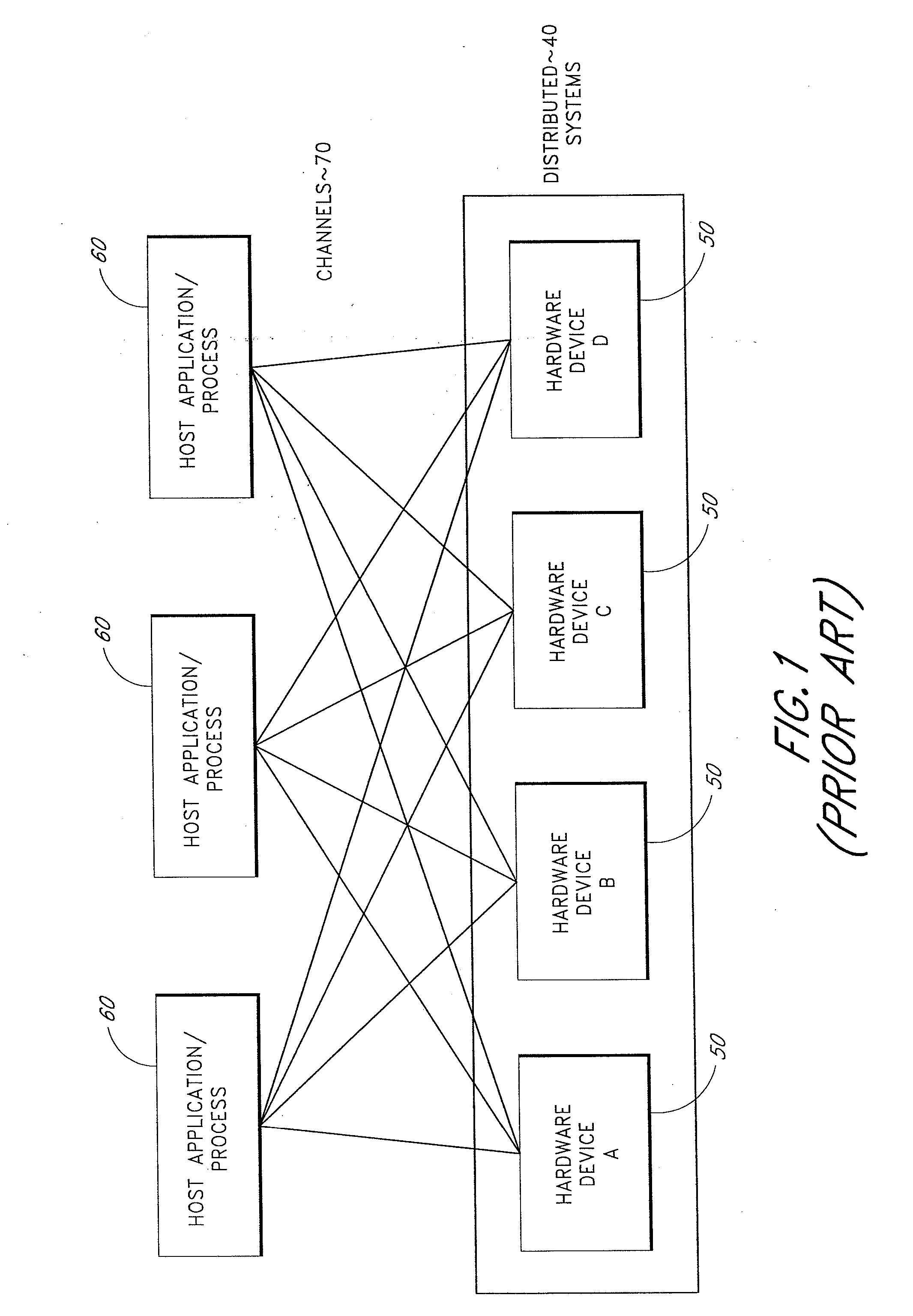
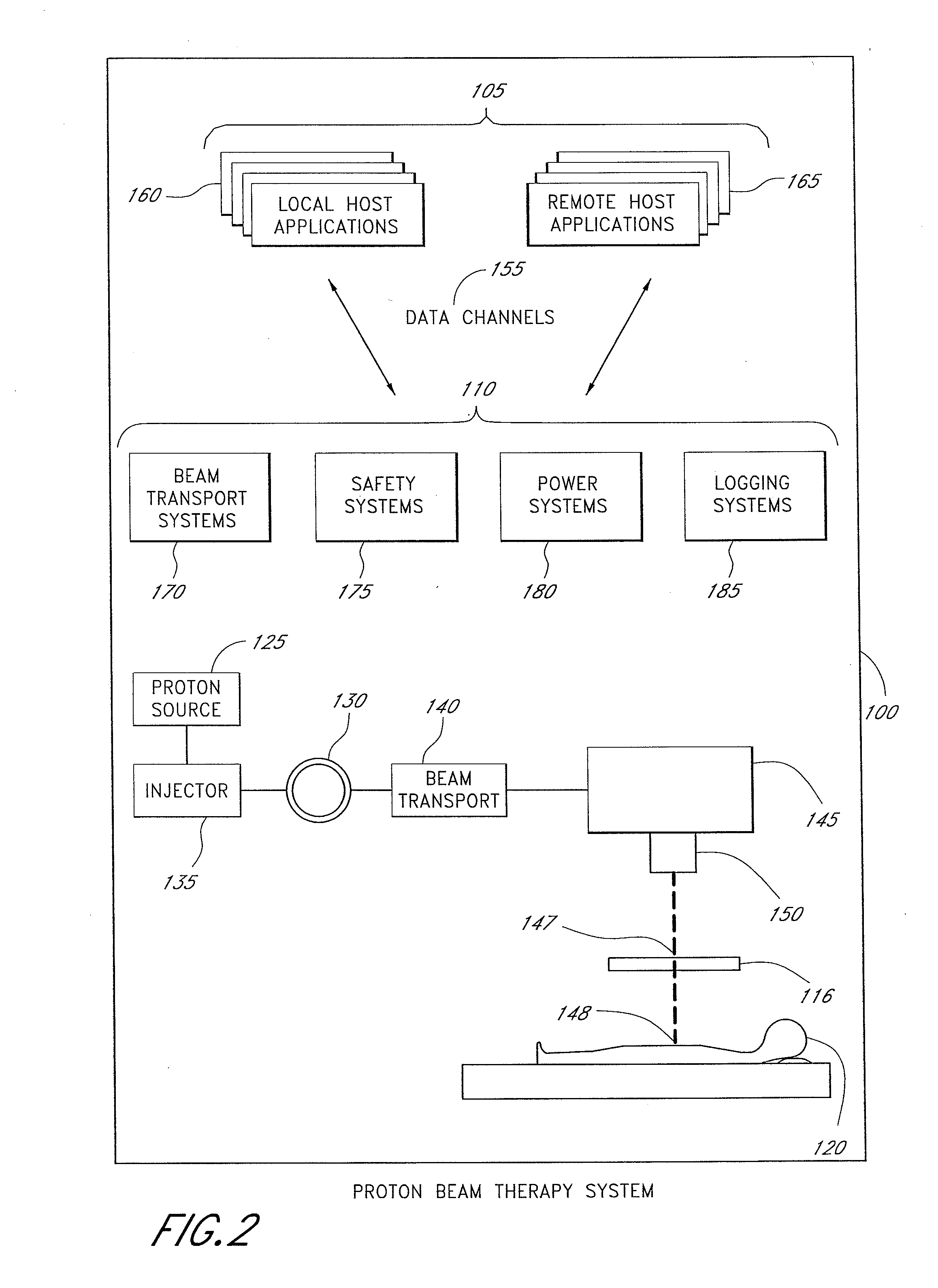
Proton beam therapy control system
InactiveUS7398309B2Reduce utilizationReduce complexityRadiation/particle handlingLocal control/monitoringTraffic capacityControl system
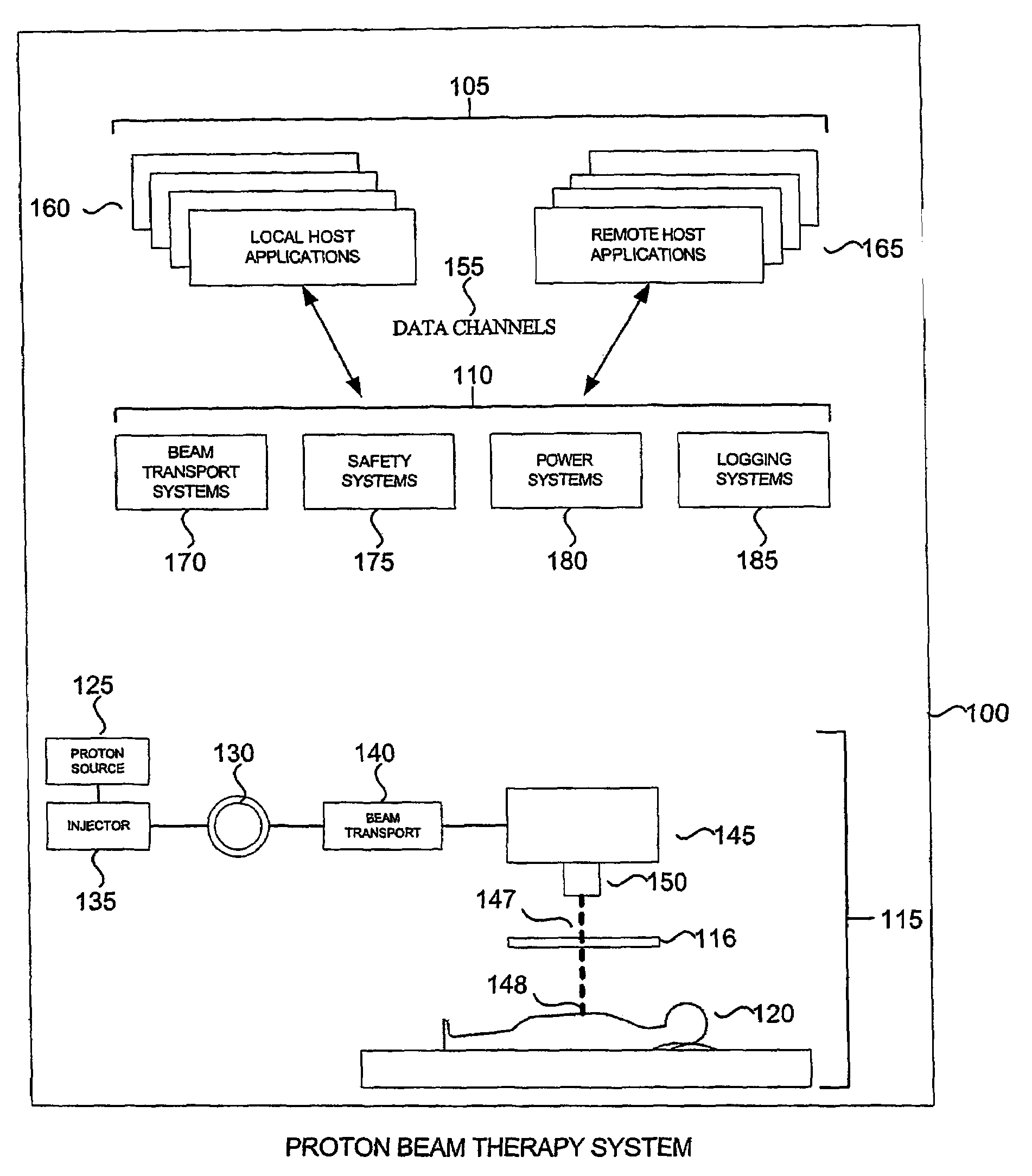
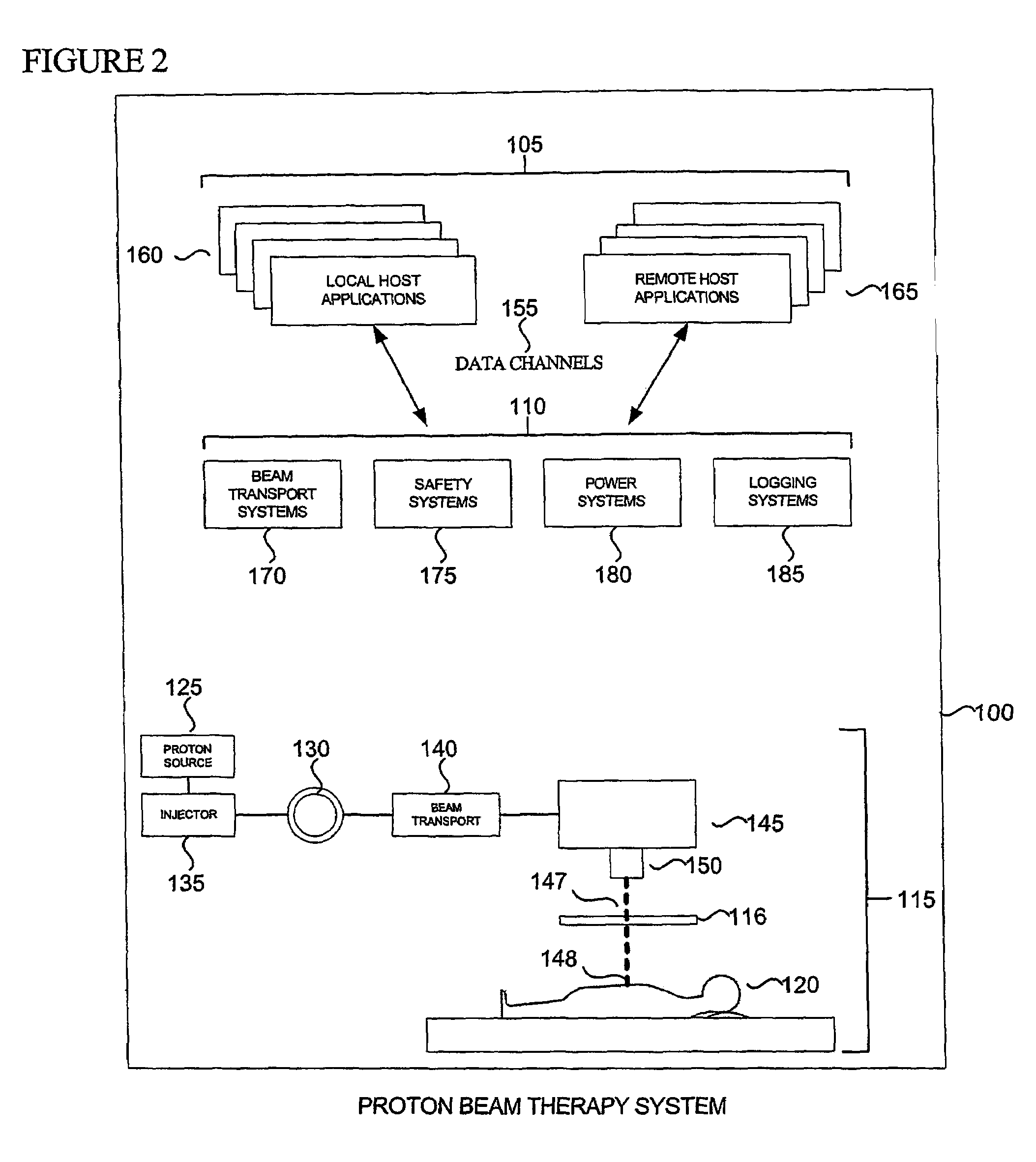
A tiered communications architecture for managing network traffic in a distributed system. Communication between client or control computers and a plurality of hardware devices is administered by agent and monitor devices whose activities are coordinated to reduce the number of open channels or sockets. The communications architecture also improves the transparency and scalability of the distributed system by reducing network mapping dependence. The architecture is desirably implemented in a proton beam therapy system to provide flexible security policies which improve patent safety and facilitate system maintenance and development.
Owner:LOMA LINDA UNIV MEDICAL CENT
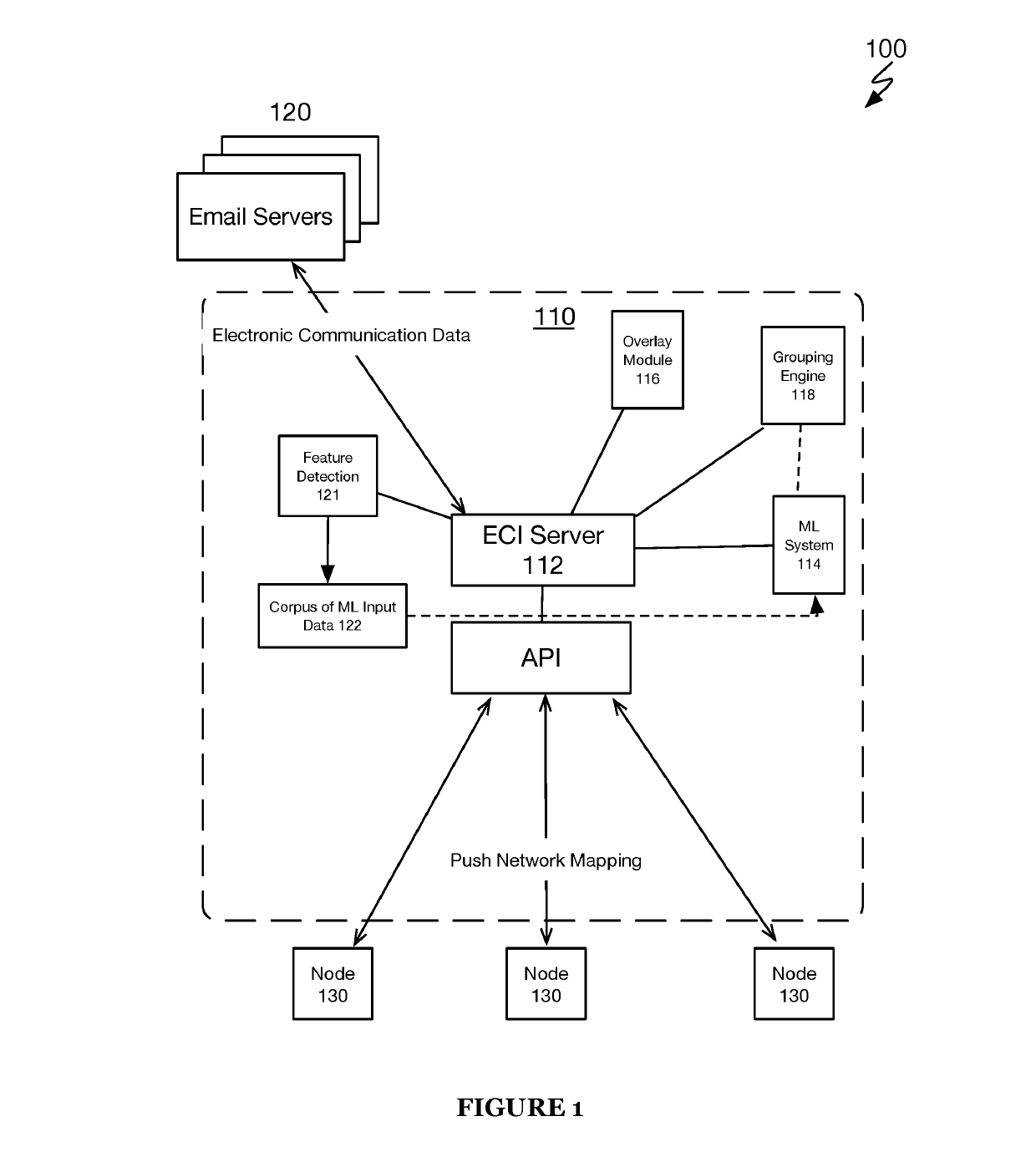
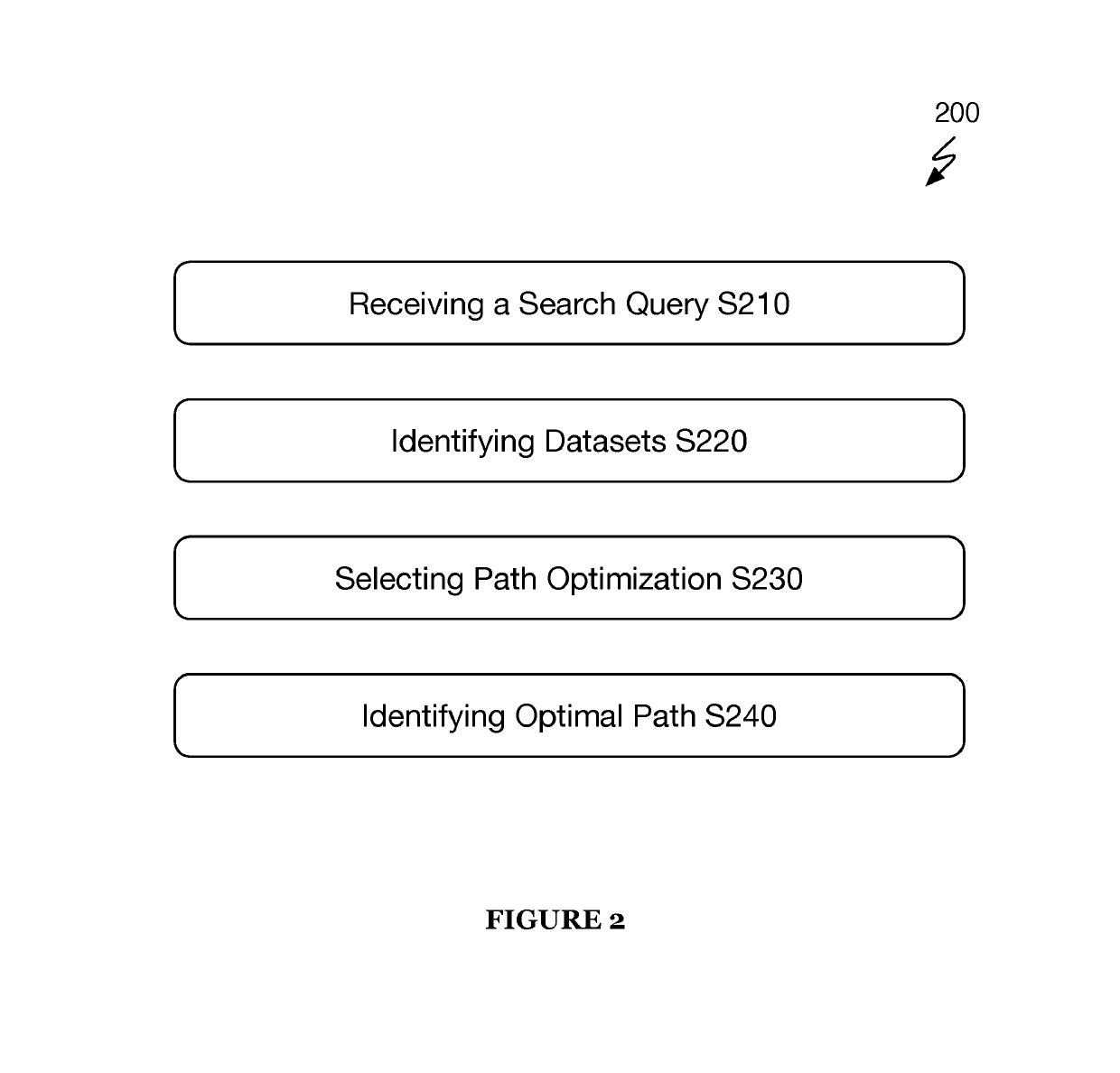
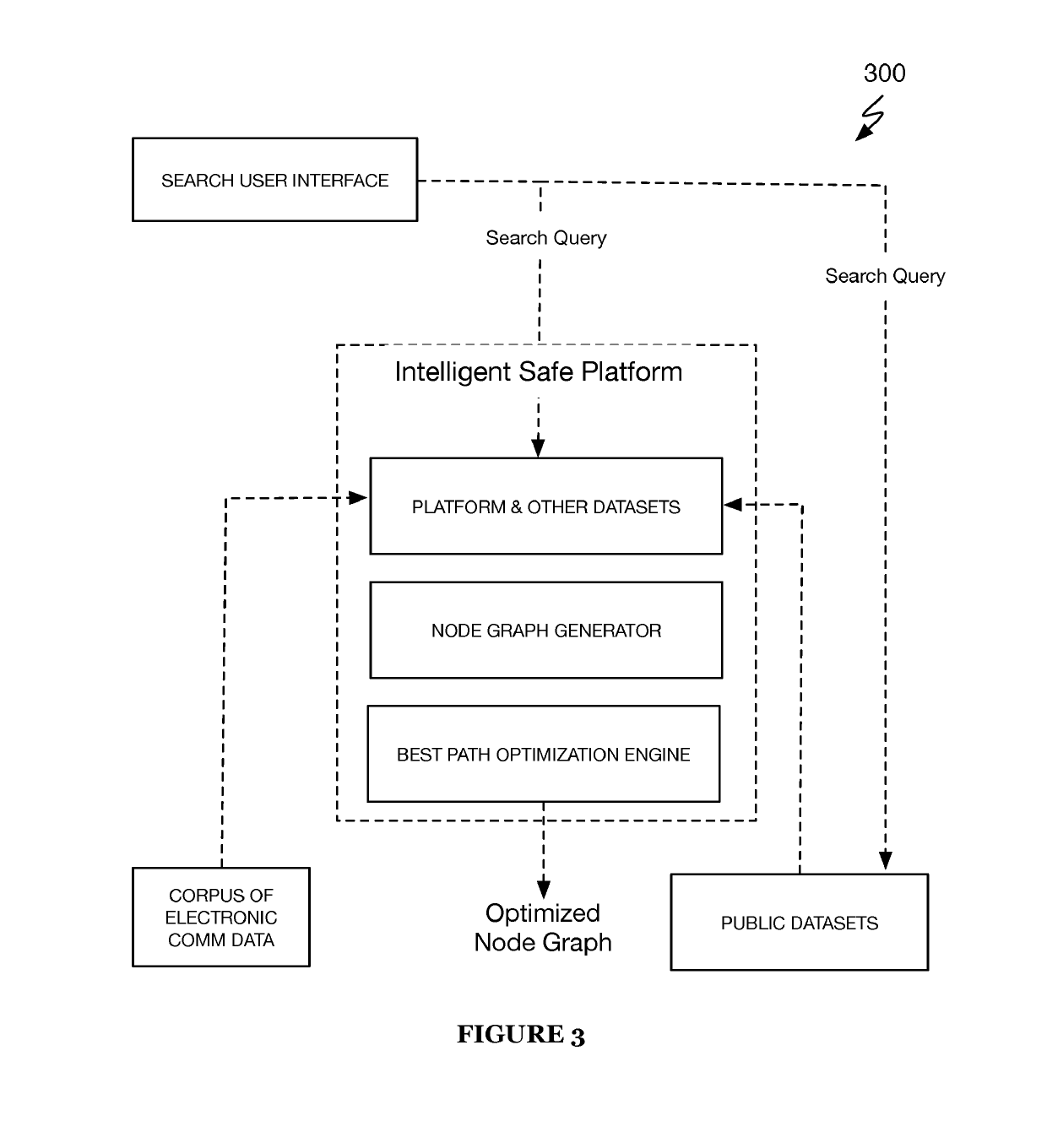
Systems and method for communications routing based on electronic communication data
ActiveUS20190140988A1Efficient routingEnsemble learningKernel methodsThird partyElectronic communication
A system and method includes at the online electronic communications service: receiving a search query from a source communication node; accessing historical electronic communication data associated with the source communication node and a plurality of online communication nodes from one or more third-party online communication services; constructing an electronic communication network mapping of communication nodes between the source communication node and each of the plurality of online communication nodes, wherein constructing includes: measuring communication metrics and / or connectivity metrics among the source communication node and the plurality of online communication nodes at least one communication metric or at least one connectivity metric between pairs of online communication nodes within the electronic communication network mapping based on the measuring; and returning an identification of one or more online communication nodes that satisfy one or more search facets of the search query based on the electronic communication network mapping.
Owner:NOTION AI
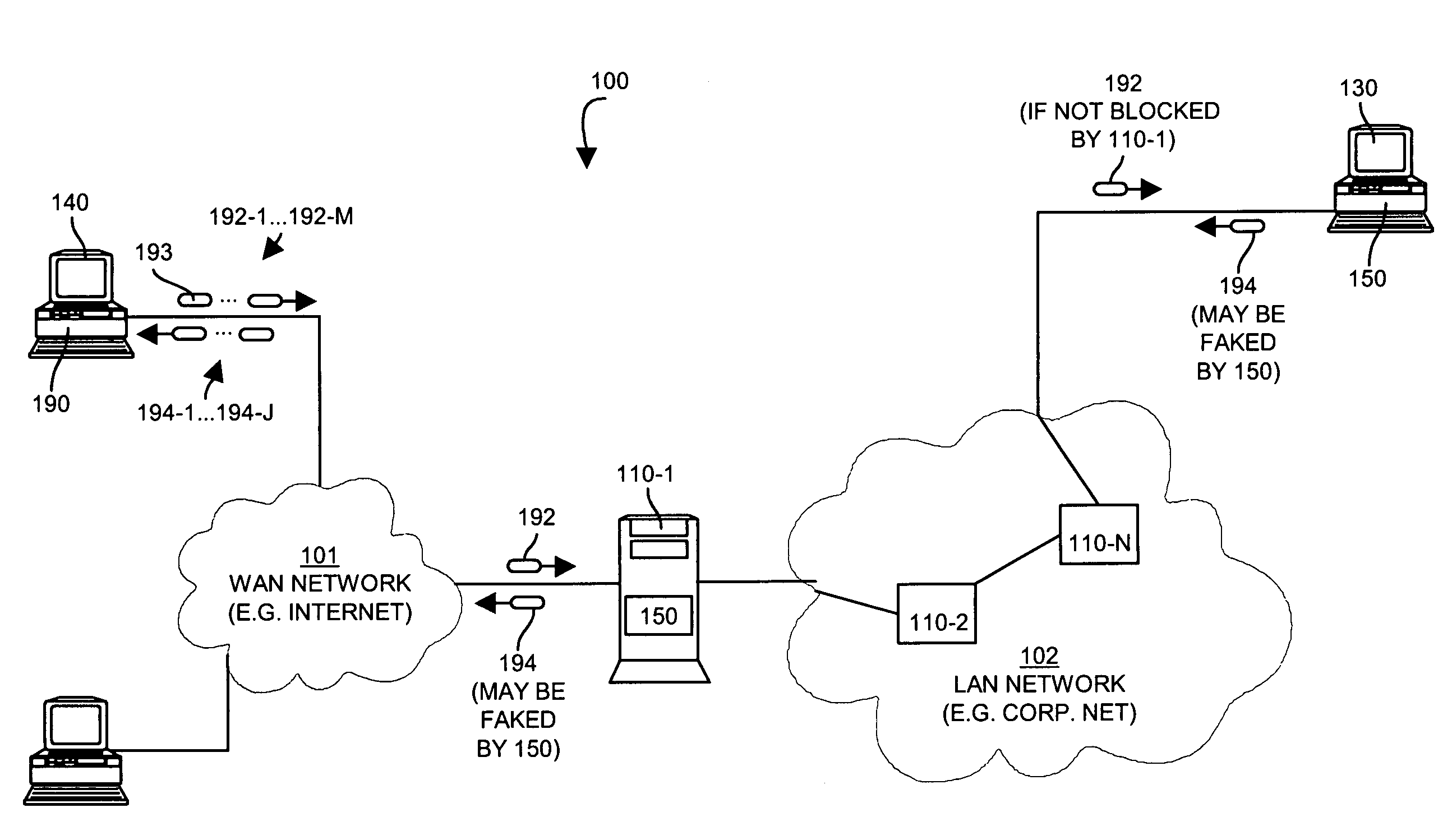
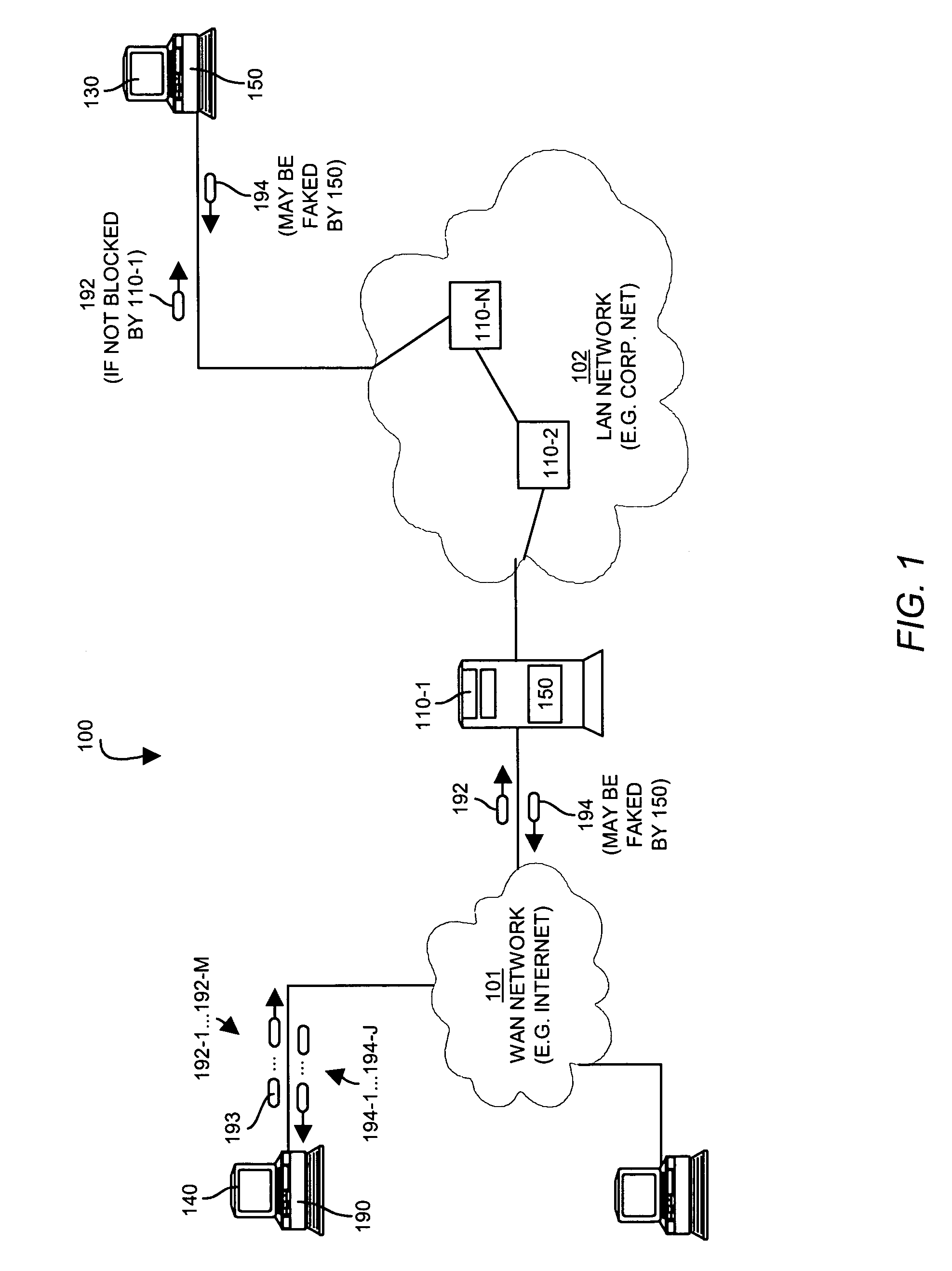
Firewall system and method with network mapping capabilities
InactiveUS6839852B1Efficiently convey informationUnauthorized memory use protectionHardware monitoringTraffic capacityRemote computer
A system, method and computer program product are provided for tracing a traffic event utilizing a firewall. Initially, a firewall is executed on a local computer. Next, traffic events between the local computer and a remote computer over a network are monitored utilizing the firewall. Further, the traffic events are displayed utilizing the firewall. In use, at least one of the traffic events is traced utilizing the firewall. Moreover, a map of the trace is displayed for effectively conveying information about the traffic event.
Owner:MCAFEE INC
Client-side method for identifying an optimal server
InactiveUS20080222243A1Multiple digital computer combinationsTransmissionTraffic capacityQuality of service
A client player performs a query to a nameserver against a network map of Internet traffic conditions. The query is made asking for a particular service (e.g., RTSP) via a particular protocol (TCP) in a particular domain. In response, the nameserver returns a set of one or more tokens, with each token defining a machine or, in the preferred embodiment, a group of machines, from which the player should seek to obtain the stream. The player may then optionally perform one or more tests to determine which of a set of servers provides a best quality of service for the stream. That server is then used to retrieve the stream. Periodically, the client player code repeats the query during stream playback to determine whether there is a better source for the stream. If a better source exists, the player performs a switch to the better stream source “on the fly” if appropriate to maintain and / or enhance the quality of service. Preferably, the client player publishes data identifying why it selected a particular server, and such data may be used to augment the network map used for subsequent request routing determinations.
Owner:AKAMAI TECH INC
Systems and methods for creating and maintaining a market intelligence portal
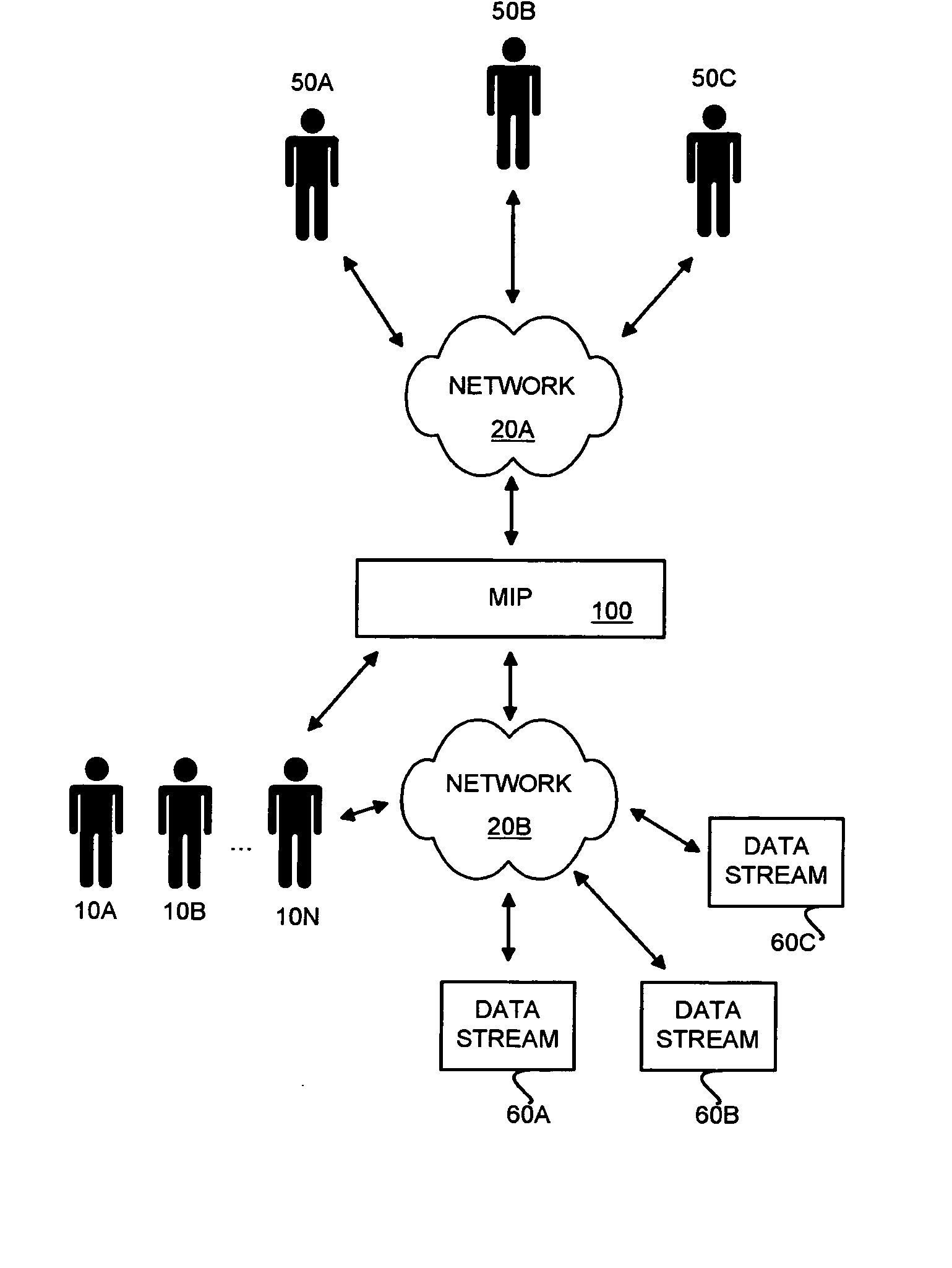
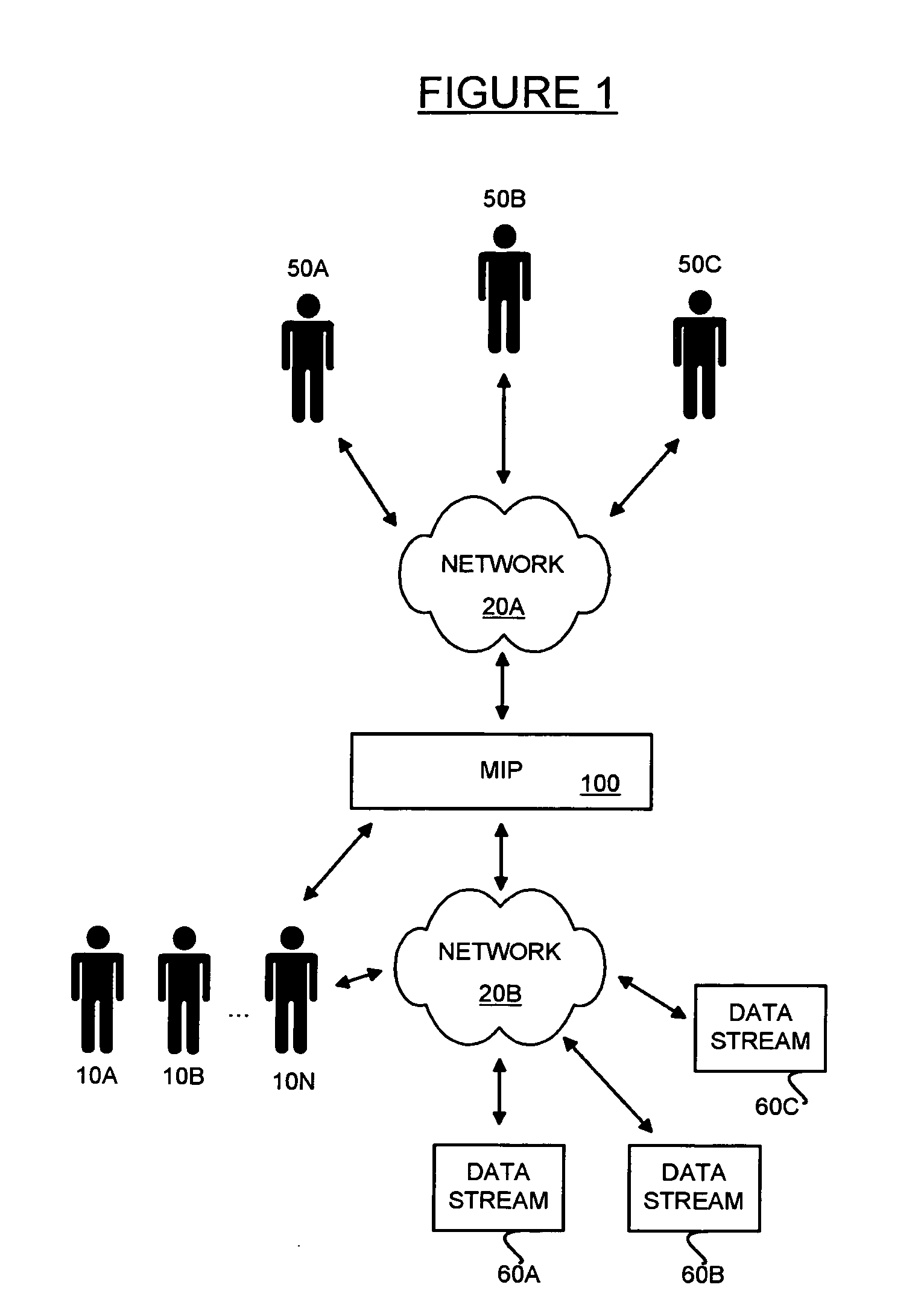
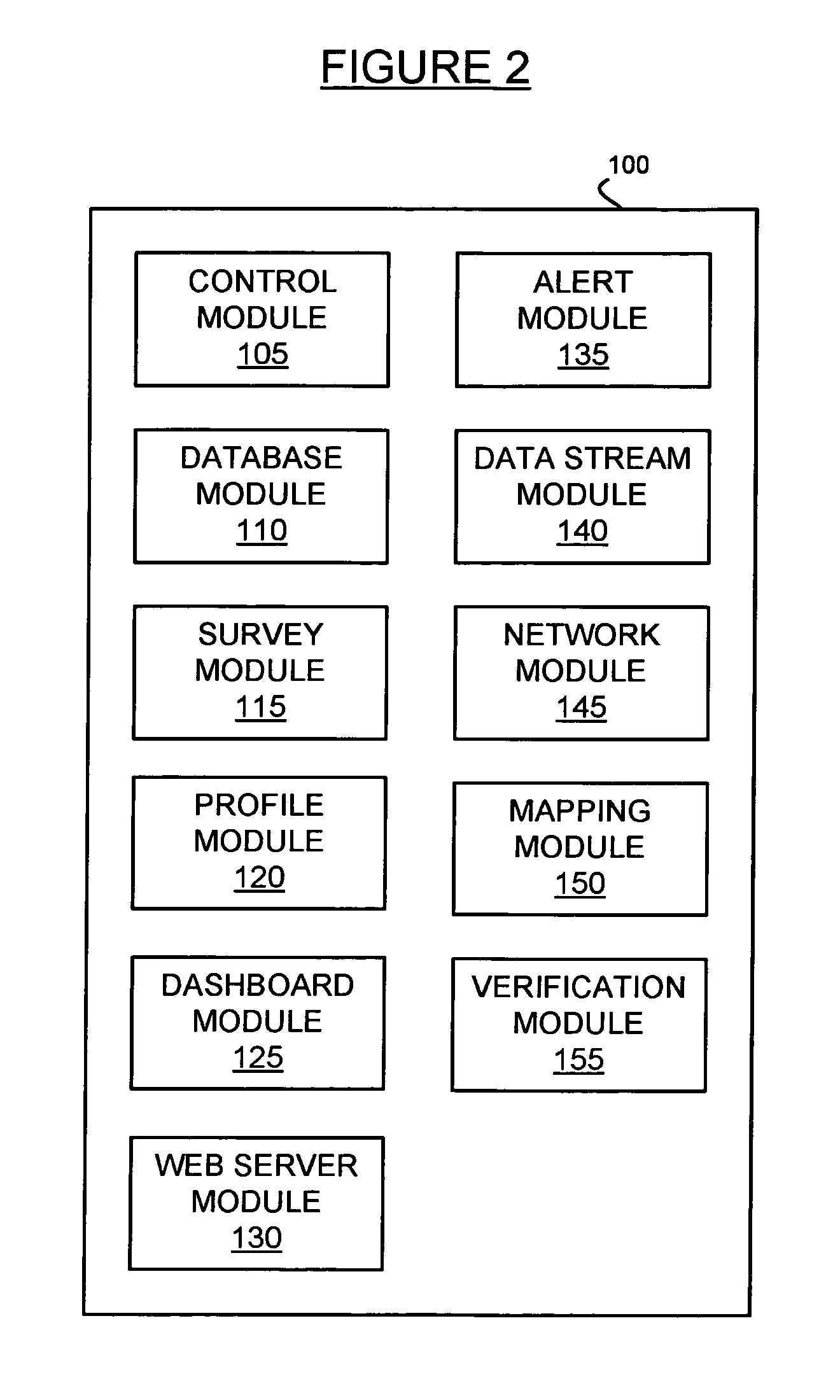
Systems and methods for creating and maintaining a market intelligence portal. Using automated data processing techniques, a market intelligence campaign is defined and executed to determine the most productive approach for marketing new products in a particular market segment. A key component of the systems and methods is identifying key opinion leaders who are deemed by their peers to be influential in a particular therapy space through surveying techniques. In addition to opinion leader information obtained through surveying, external data sources are used to create a detailed profile for each opinion leader identified through surveying. Social network mapping and other analysis is performed on the profiles. The survey results, profiles and social network diagrams are stored electronically on a network portal. An interactive dashboard interface to the portal is created so that the data can be accessed and visualized remotely, preferably using a web browser interface. One or more data streams are used to self-update the data as new data relevant to the campaign and / or the opinion leader profiles is available. The various systems and methods may have particular utility to pharmaceutical companies trying to gain market acceptance of new drug therapies.
Owner:PROLINK SERVICES
Systems, methods, and computer medium to produce efficient, consistent, and high-confidence image-based electrofacies analysis in stratigraphic interpretations across multiple wells
ActiveUS20150241591A1Improve consistencyEasy to explainElectric/magnetic detection for well-loggingBiological neural network modelsHydrocotyle bowlesioidesImaging data
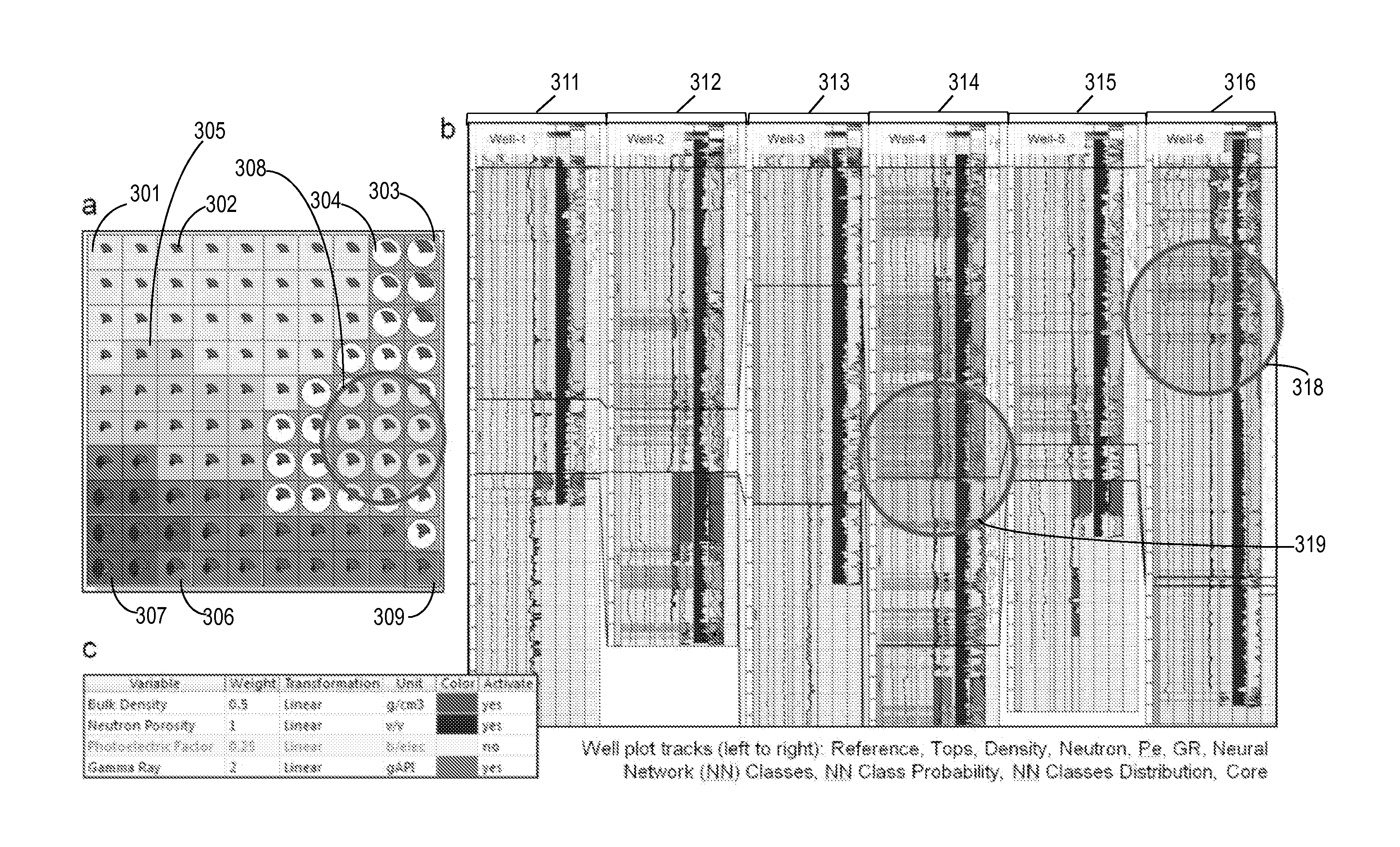
Embodiments of systems, computer-implemented methods, and non-transitory computer-readable medium having one or more computer programs stored therein are provided to enhance borehole image analysis associated with a hydrocarbon reservoir. A neural network mapping process can first be performed, responsive to openhole log data and core data, to thereby generate a material-type scheme. Then, an image-based petrophysical analysis process can distribute and calibrate borehole image data, responsive to the core data and material-type scheme. Consequently, an approximated material type and an approximated grain size can be produced for each borehole image reading. The openhole log data, the core data, the material-type scheme, and the approximated material types and grain sizes, for example, can then be displayed to thereby increase consistency in categorizing subsurface material associated with hydrocarbon wells by material type and enhance interpretation of subsurface material texture, fabric, and features to predict subsurface material composition of the hydrocarbon reservoir.
Owner:SAUDI ARABIAN OIL CO
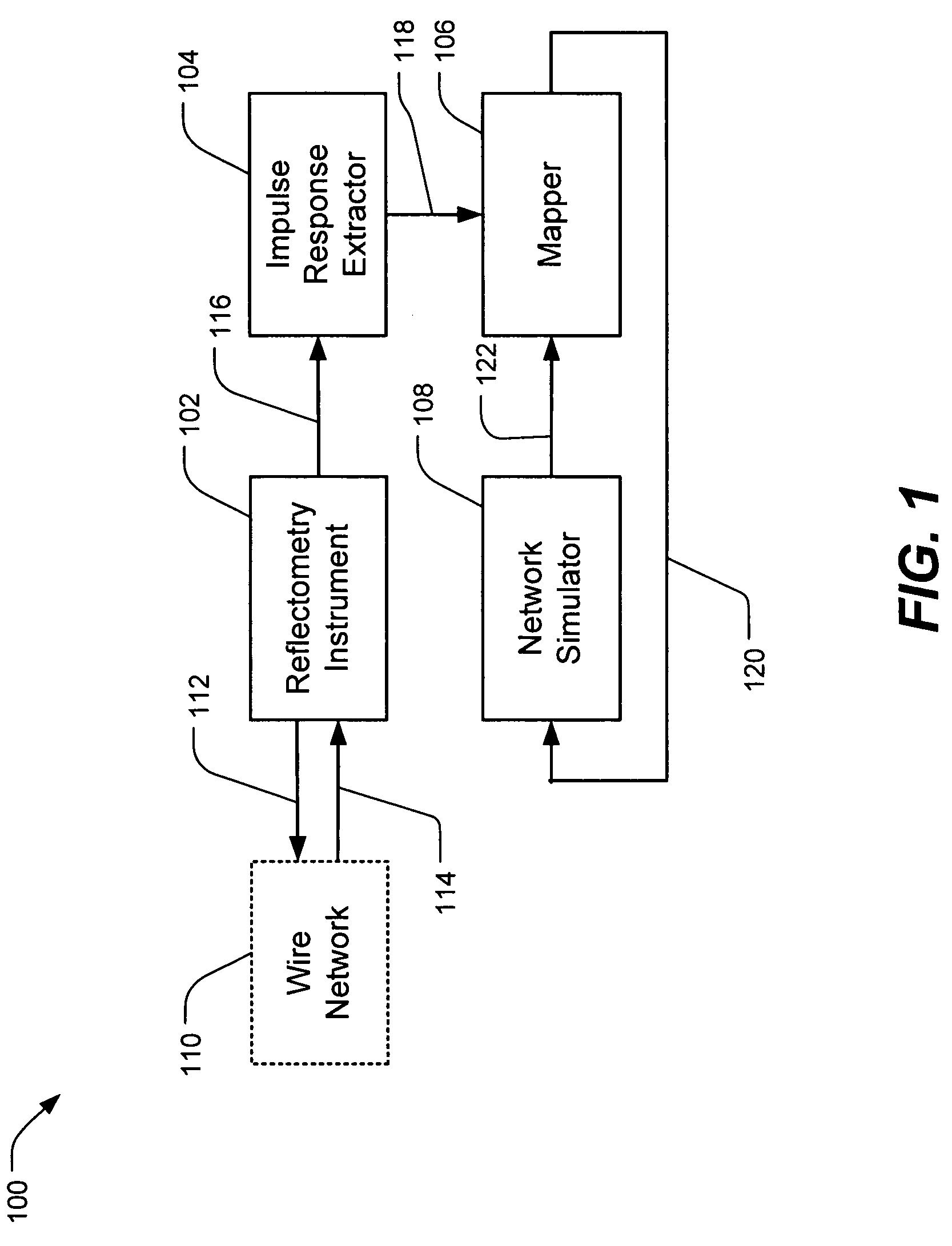
Wire network mapping method and apparatus using impulse responses
ActiveUS20060182269A1Reduce the differenceTwo-way loud-speaking telephone systemsFault location by pulse reflection methodsNetwork modelReflectometry
A method and apparatus for mapping a wire network is disclosed. The method includes obtaining a reflectometry test signal of the wire network. An estimated network impulse response is estimated from the reflectometry response. A wire network model is then initialized, and iteratively improved by simulating an impulse response of the wire network model and adjusting the wire network model to reduce differences between the simulated impulse response and estimated network impulse response.
Owner:UNIV OF UTAH RES FOUND
Systems and methods for mapping event changes in network navigation
ActiveUS20090327424A1Time-division multiplexData switching by path configurationWeb navigationNetwork mapping
Owner:PAYPAL INC
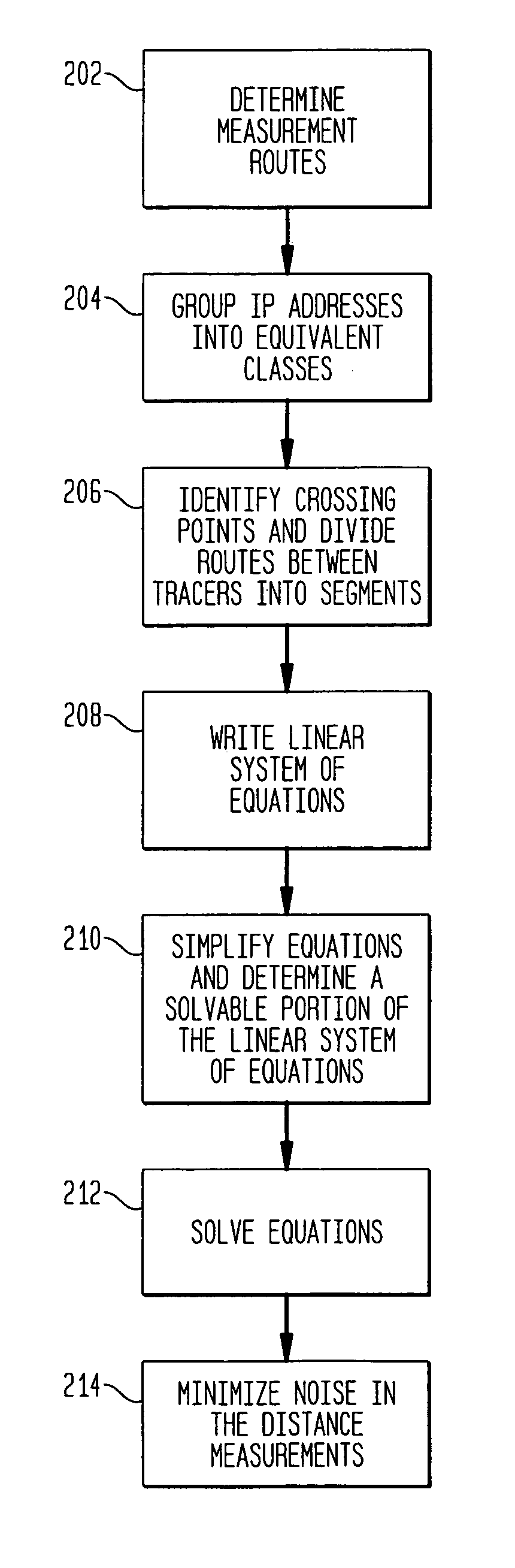
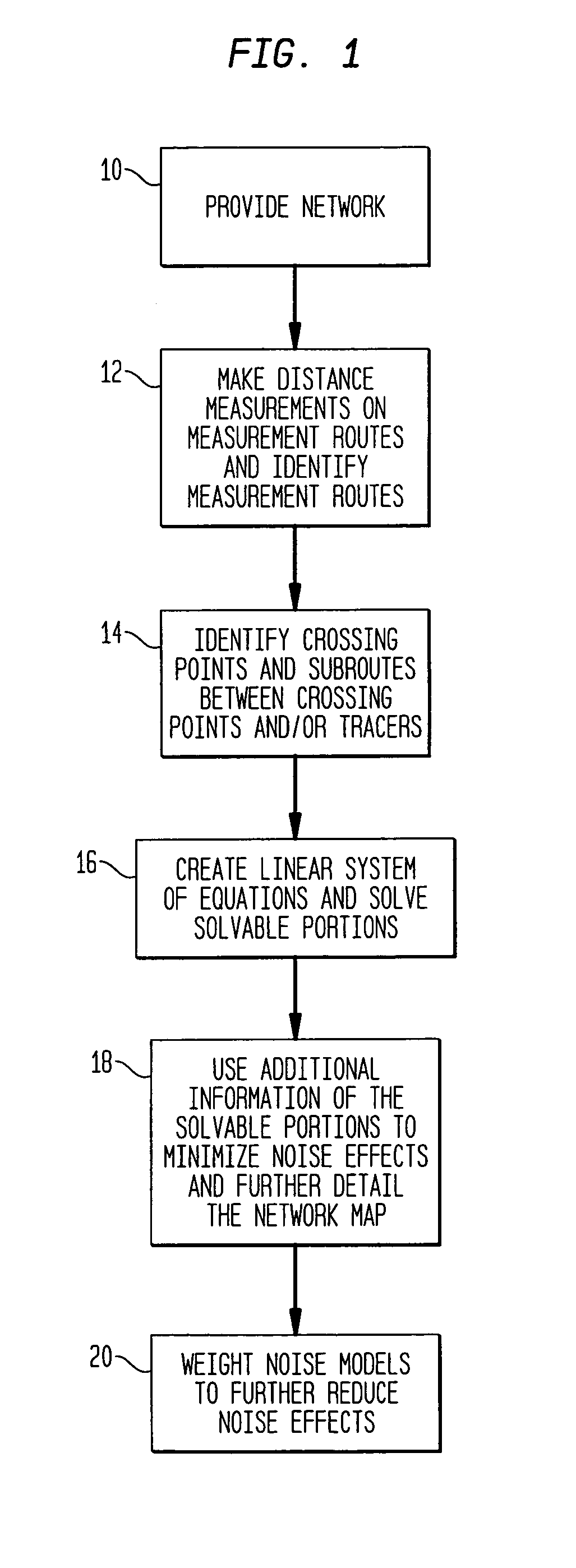
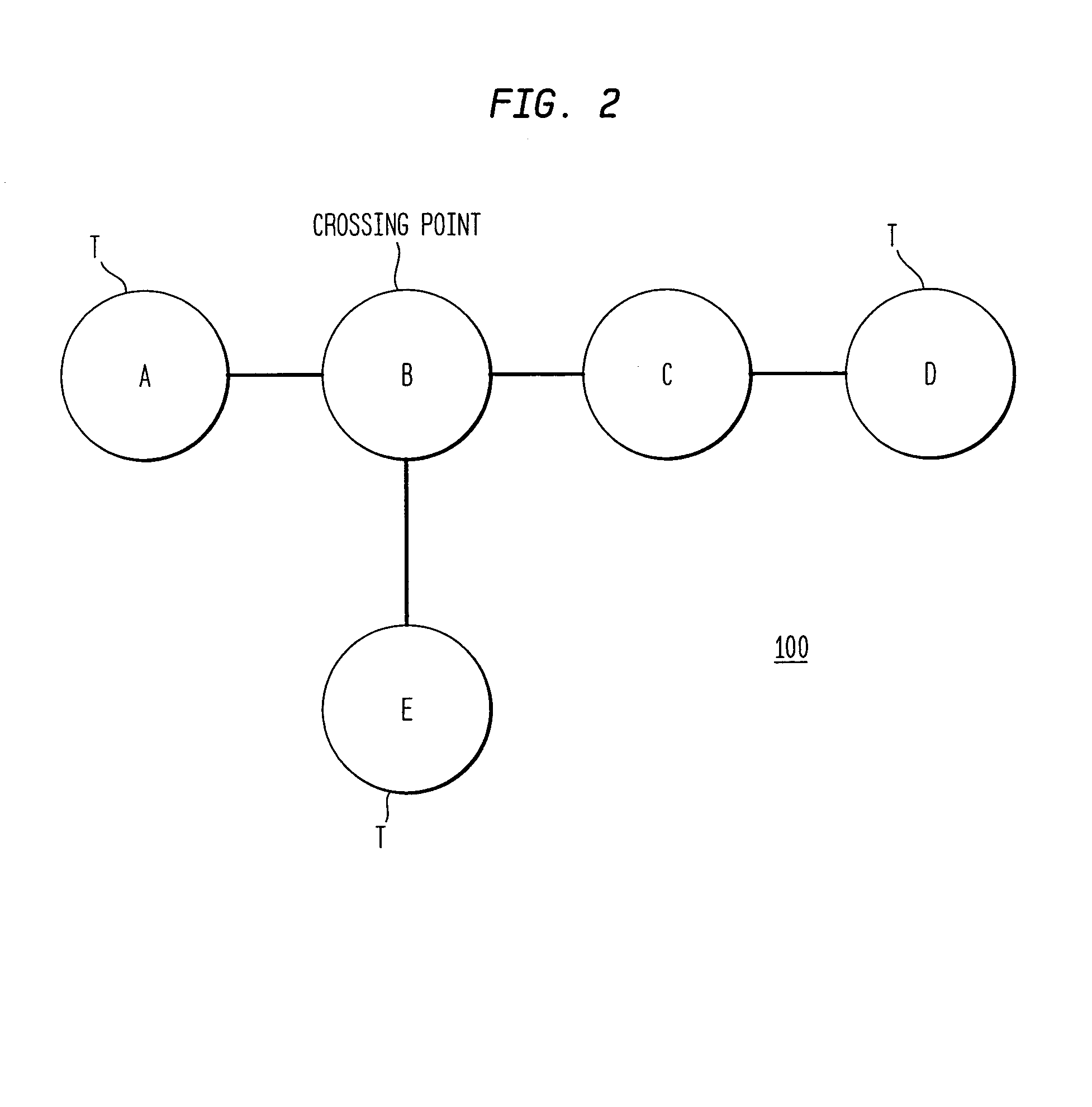
Method and apparatus for network mapping using end-to-end delay measurements
A method for mapping a network, in accordance with the present invention, includes providing distance measurements between tracers in the network, determining routes along which the distance measurements are made, and creating a system of equations which links the distance measurements between the nodes with a sum of the delays between the nodes which comprise the routes. Additional information is extracted about distances of subpaths of the routes to provide additional details to a map of the network. The additional information provides a capability of estimation of distances between nodes without tracers.
Owner:WSOU INVESTMENTS LLC +1
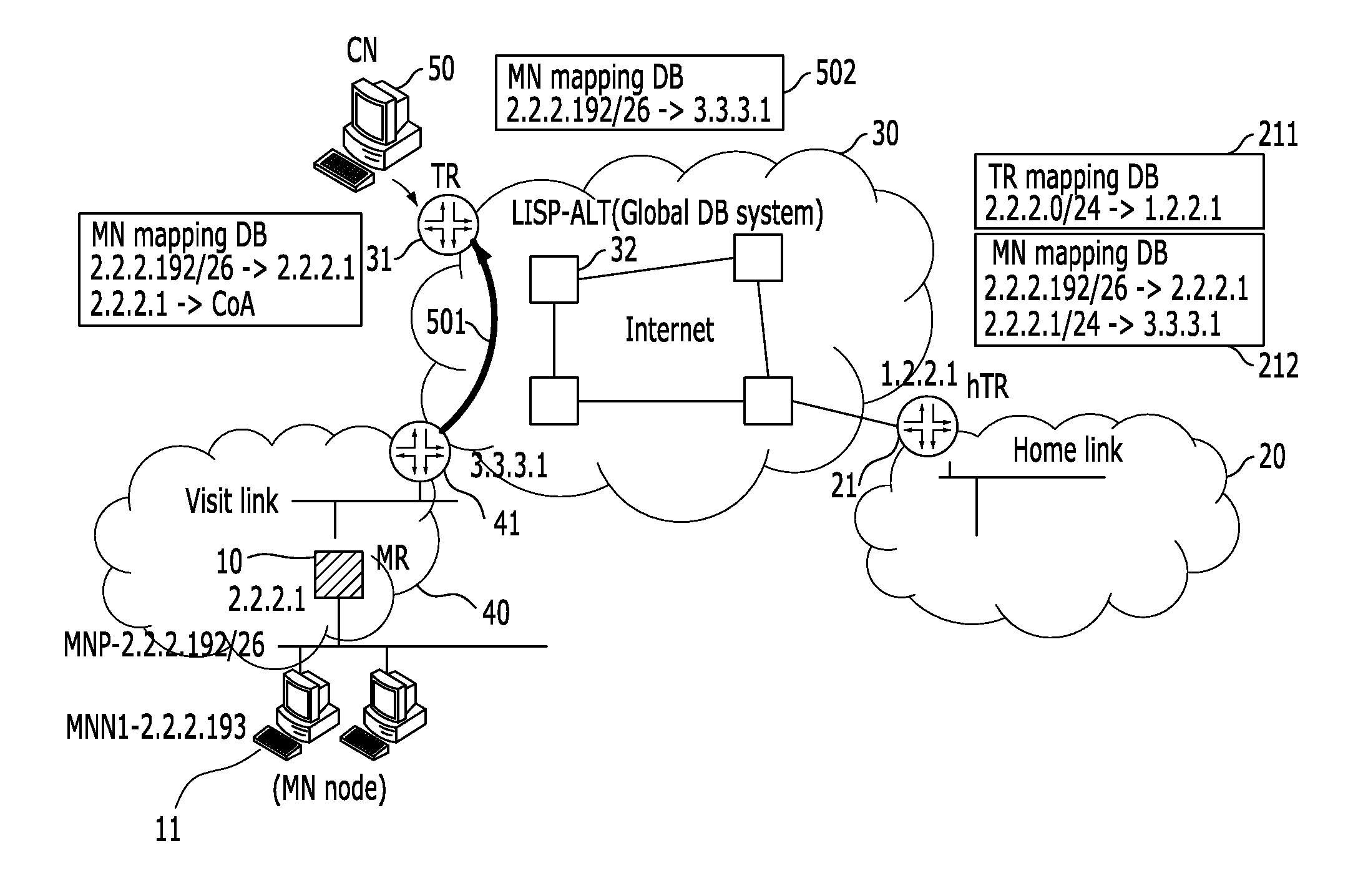
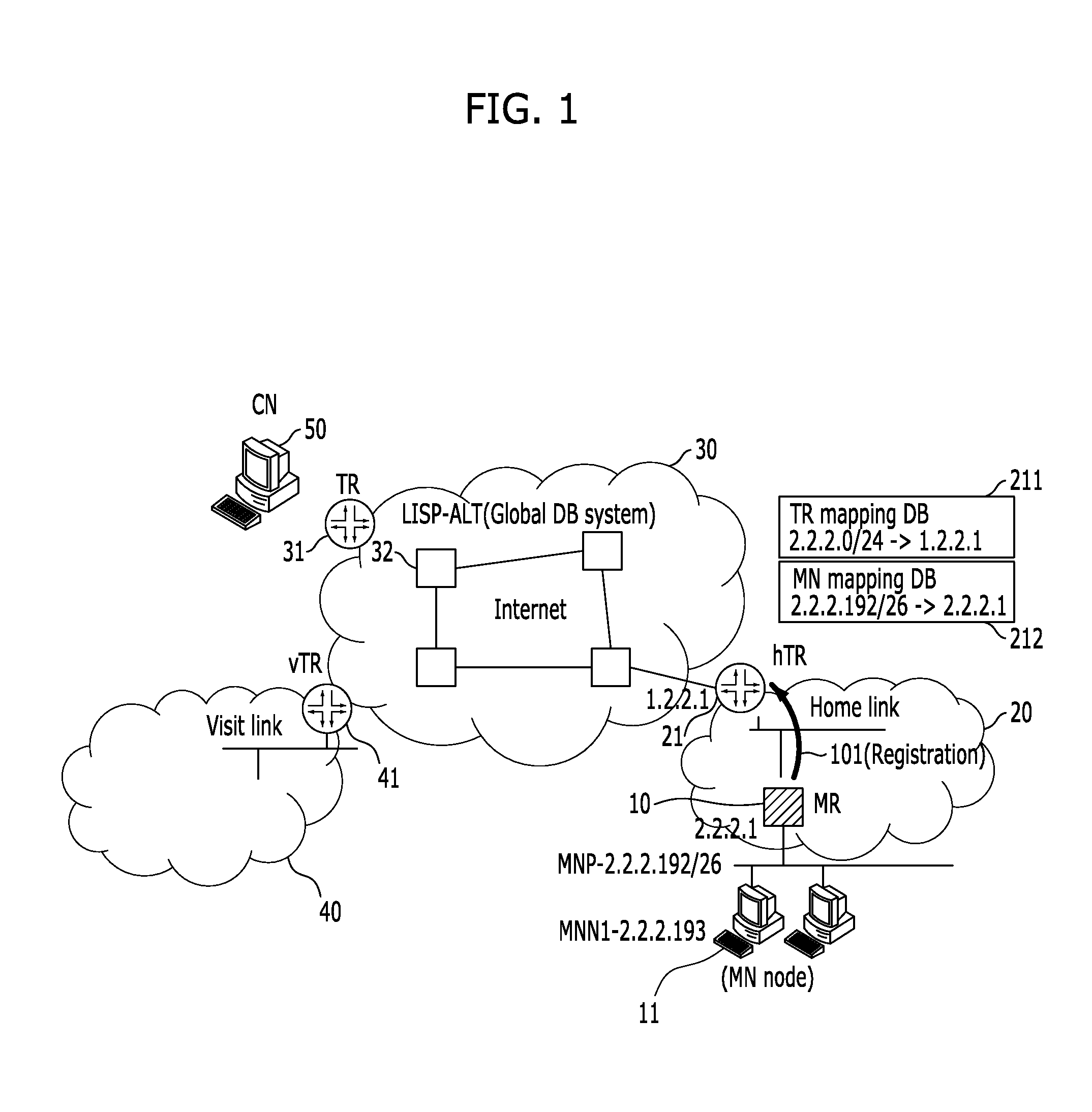
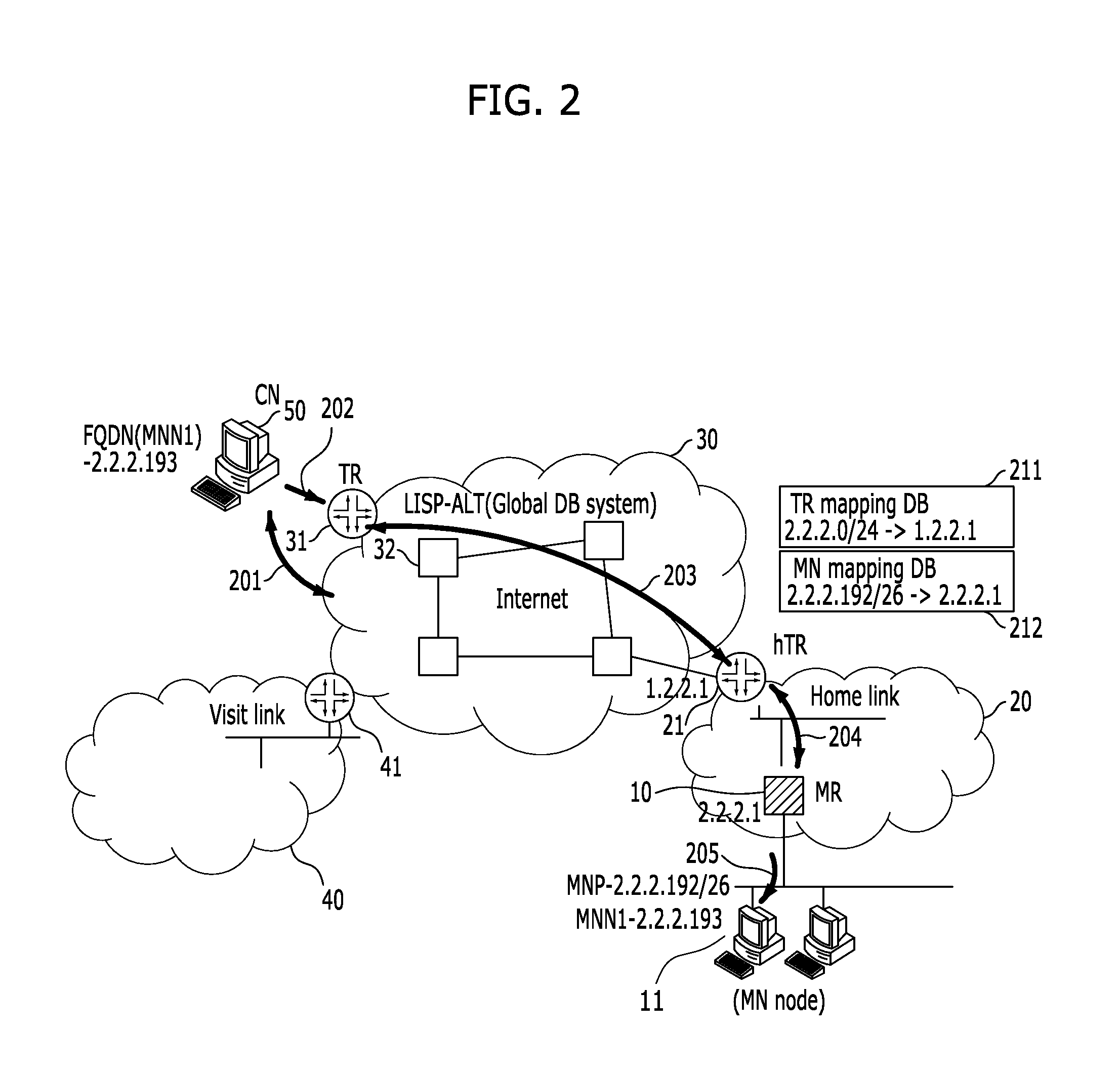
System and method for supporting network mobility based on identifier-locator separation
InactiveUS20110261800A1Problem still existExcellent stateNetwork topologiesConnection managementInformation supportNetwork mobility
A system and method for supporting network mobility based on identifier-locator separation, provides seamless session services to terminals inside the mobile network by enabling a variety of tunnel routers (home tunnel router, visit tunnel router, etc.) on network to store / manage mobile network mapping information for network mobility. The system for supporting network mobility based on identifier-locator separation includes: a mobile router configured to register mobile network identification information in a home tunnel router, and support communication with the home tunnel router, on behalf of mobile network nodes located in a home network; and a home tunnel router configured to support communication with a correspondent node by using tunnel router mapping information, and support communication with the mobile router by using mobile network mapping information.
Owner:KT CORP
Controlled transmission across packet network
InactiveUS6870841B1Eliminate needData switching by path configurationNetwork connectionsEdge nodeNetwork control
Control over the movement of packets is exercised by edge nodes of a network mapping the addresses of incoming packets in accordance with a prespecified functional mapping P. Remote sources of packets are provided address information that is mapped with a prespecified functional mapping Q, where mappings P and Q are such that P(Q(j)=j. The mapping change at regular intervals, or upon the occurrence of specified events, and with each change, the communicating the remote source is provided with a different mapped address to be used.
Owner:AT&T INTPROP II L P
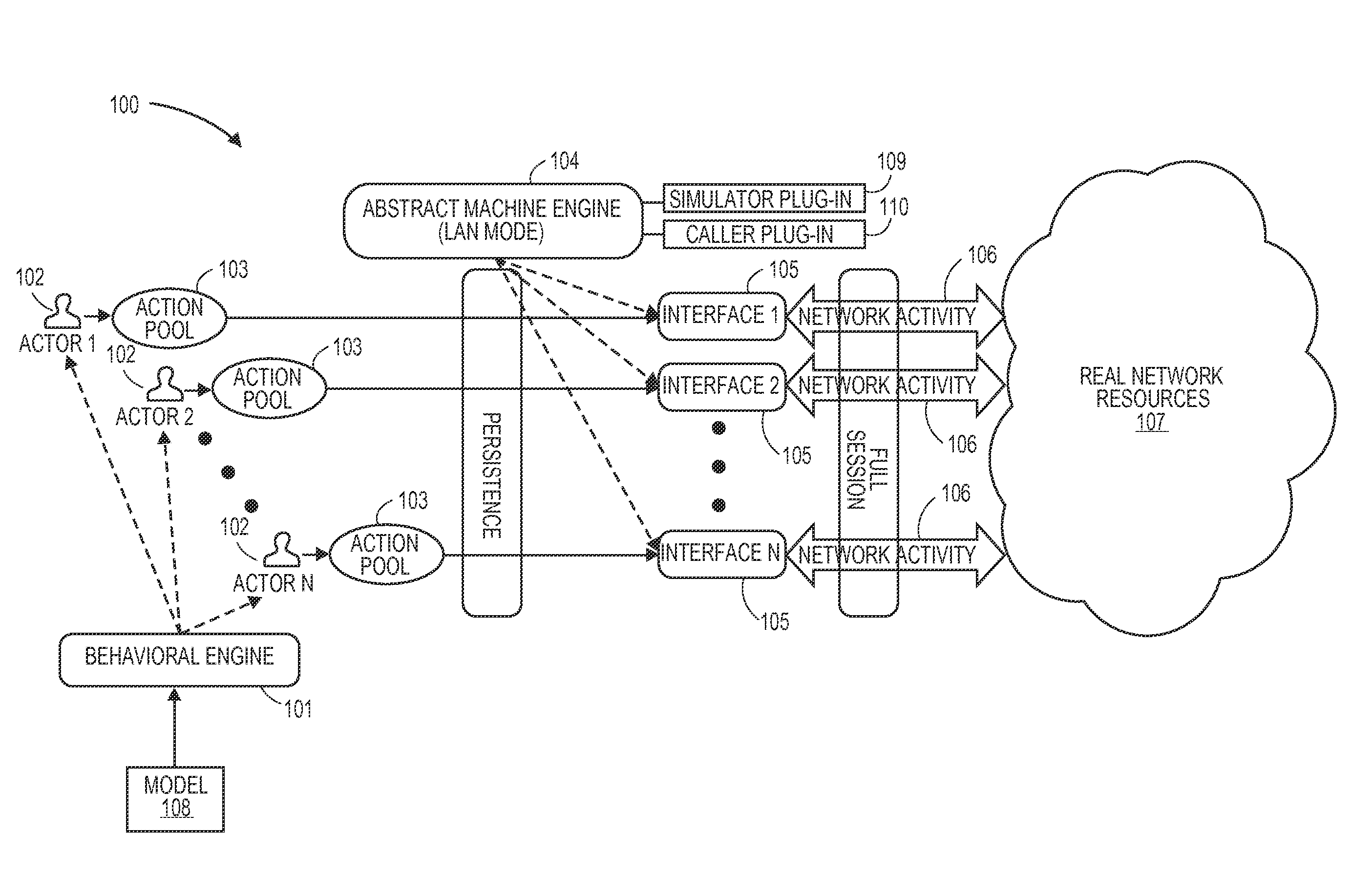
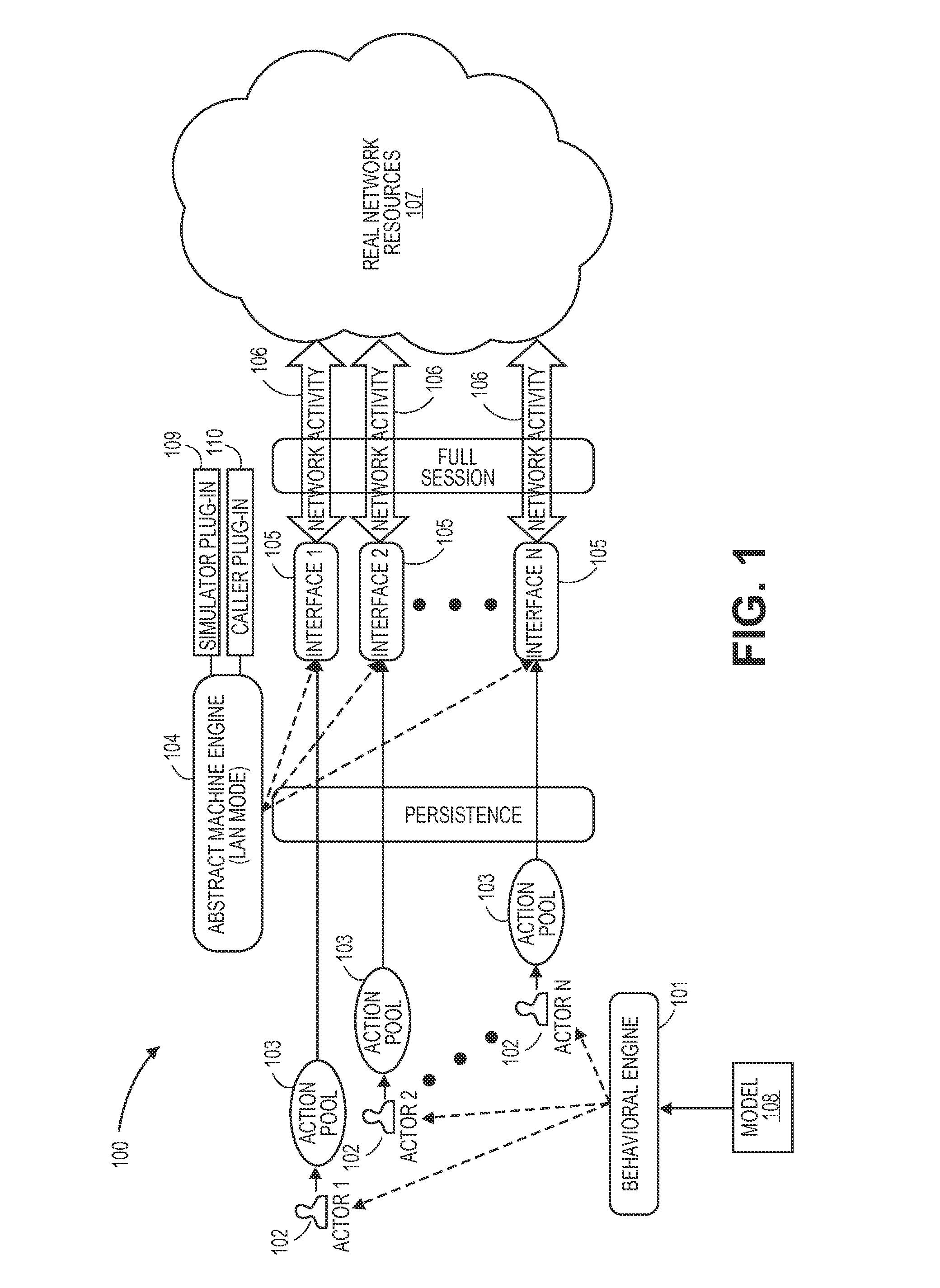
Network stimulation engine
ActiveUS20120158395A1Digital data processing detailsError detection/correctionHuman useAbstract machine
Methods, devices, and systems are disclosed for simulating a large, realistic computer network. Virtual actors statistically emulate the behaviors of humans using networked devices or responses and automatic functions of networked equipment, and their stochastic actions are queued in buffer pools by a behavioral engine. An abstract machine engine creates the minimal interfaces needed for each actor, and the interfaces then communicate persistently over a network with each other and real and virtual network resources to form realistic network traffic. The network can respond to outside stimuli, such as a network mapping application, by responding with false views of the network in order to spoof hackers, and the actors can respond by altering a software defined network upon which they operate.
Owner:ACALVIO TECH
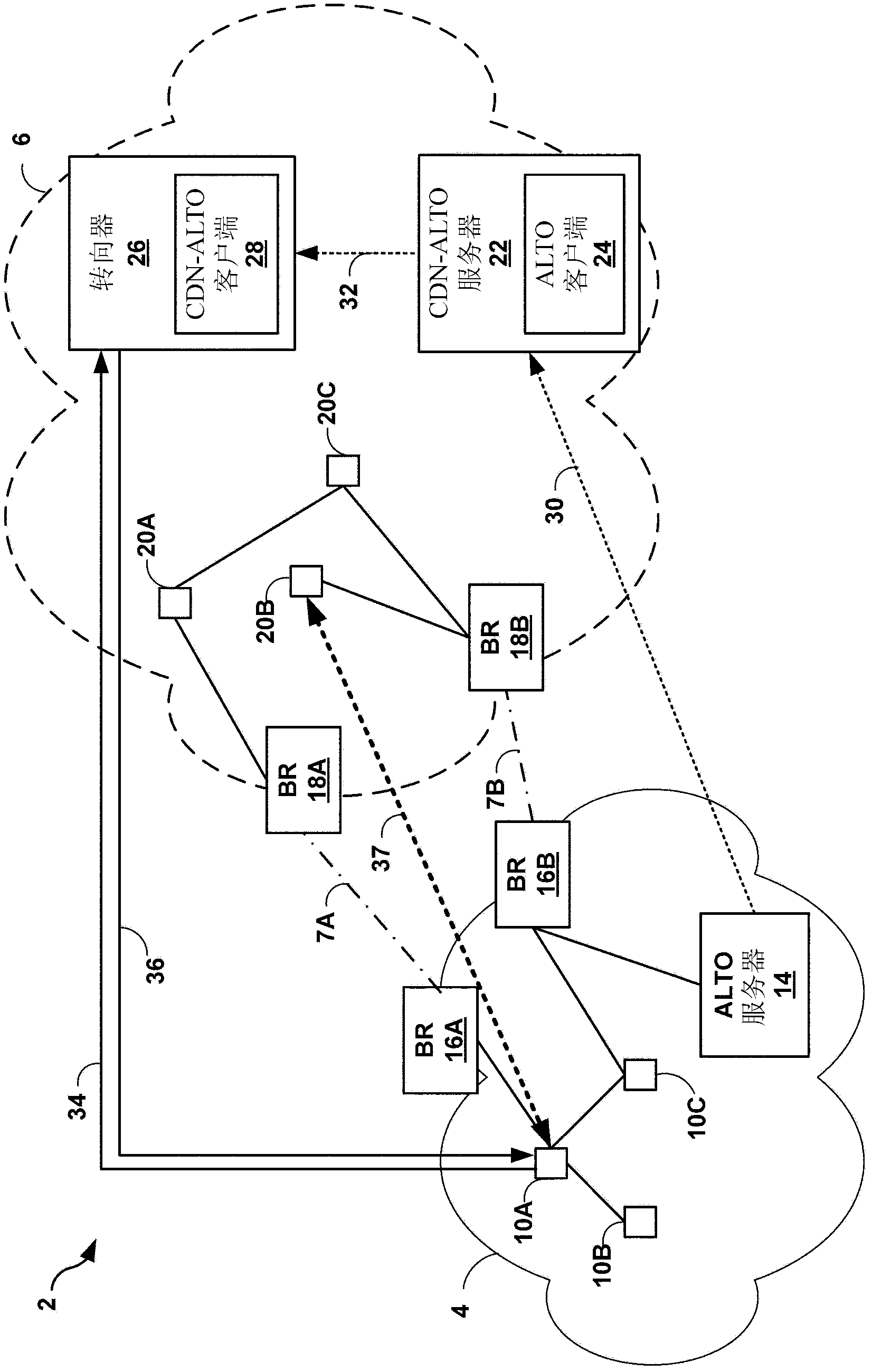
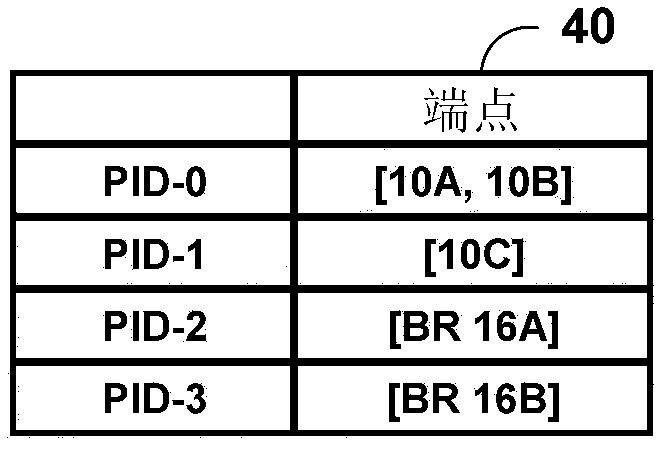
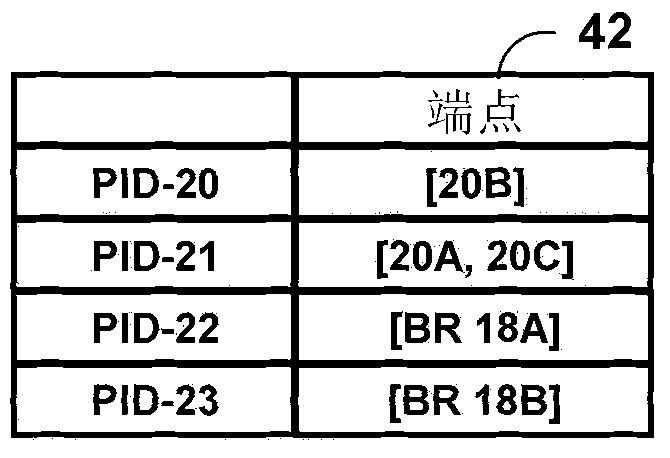
Application-layer traffic optimization enhancements for content delivery networks
ActiveCN102316091AFoster service continuityData switching networksPaper documentDocument preparation
Using the ALTO Service, networking applications can request through the ALTO protocol information about the underlying network topology from the ISP or Content Provider. The ALTO Service provides information such as preferences of network resources with the goal of modifying network resource consumption patterns while maintaining or improving application performance. This document describes, in one example, an ALTO server that intersects network and cost maps for a first network with network and cost maps for a second network to generate a master cost map that includes one or more master cost entries that each represent a cost to traverse a network from an endpoint in the first network to an endpoint in the second network. Using the master cost map, a redirector may select a preferred node in the first network with which to service a content request received from a host in the second network.
Owner:JUMIPER NETWORKS INC
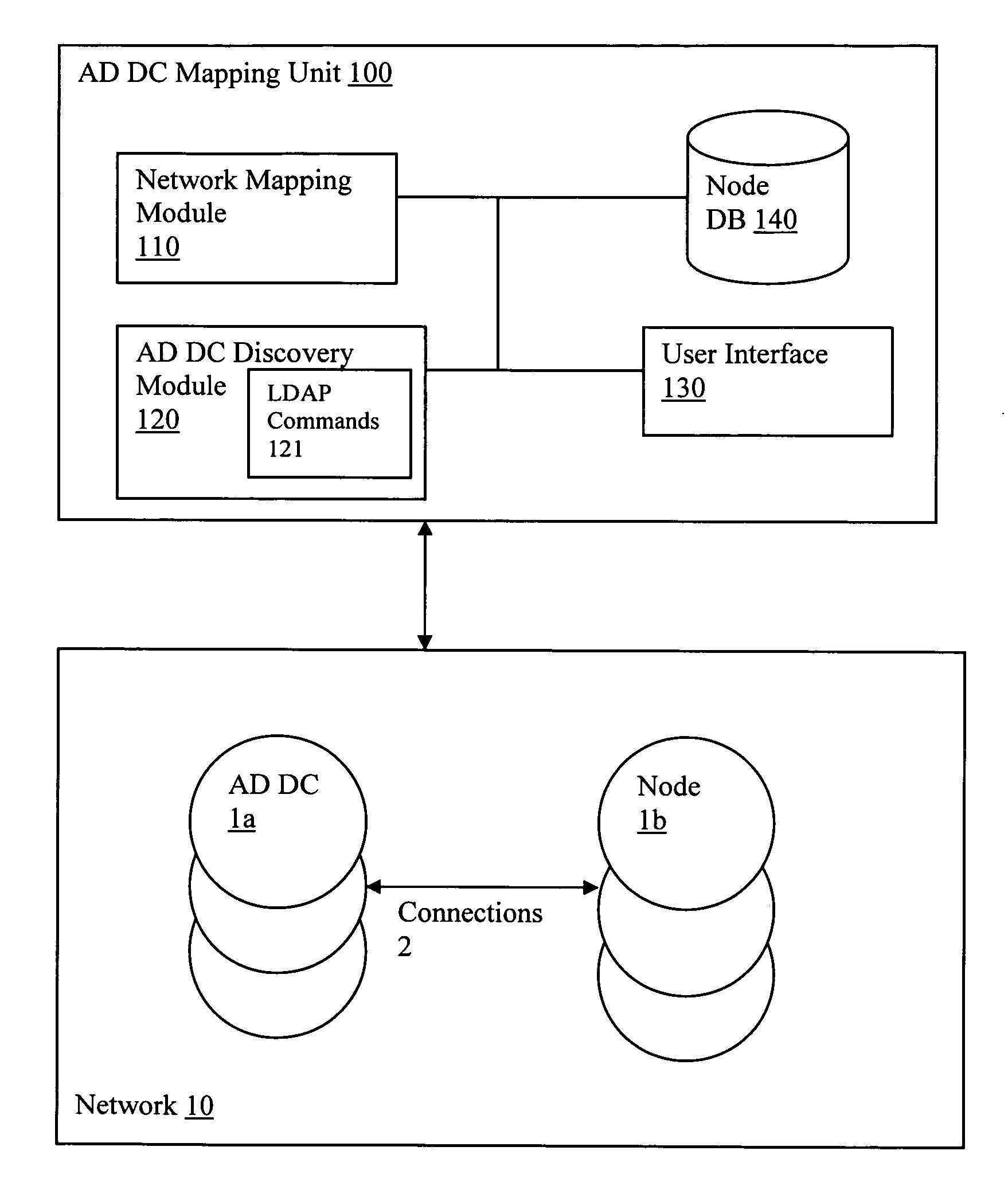
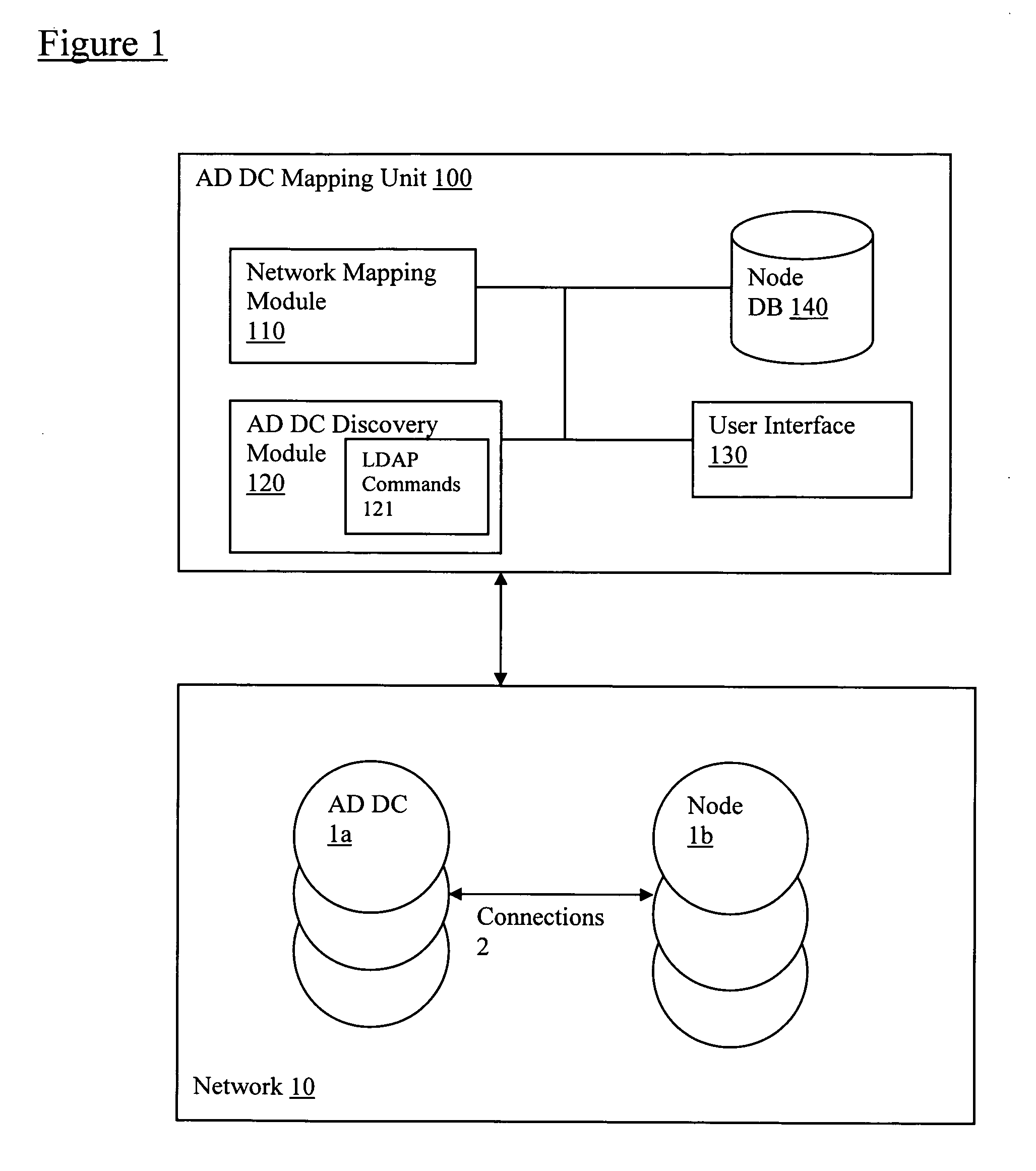
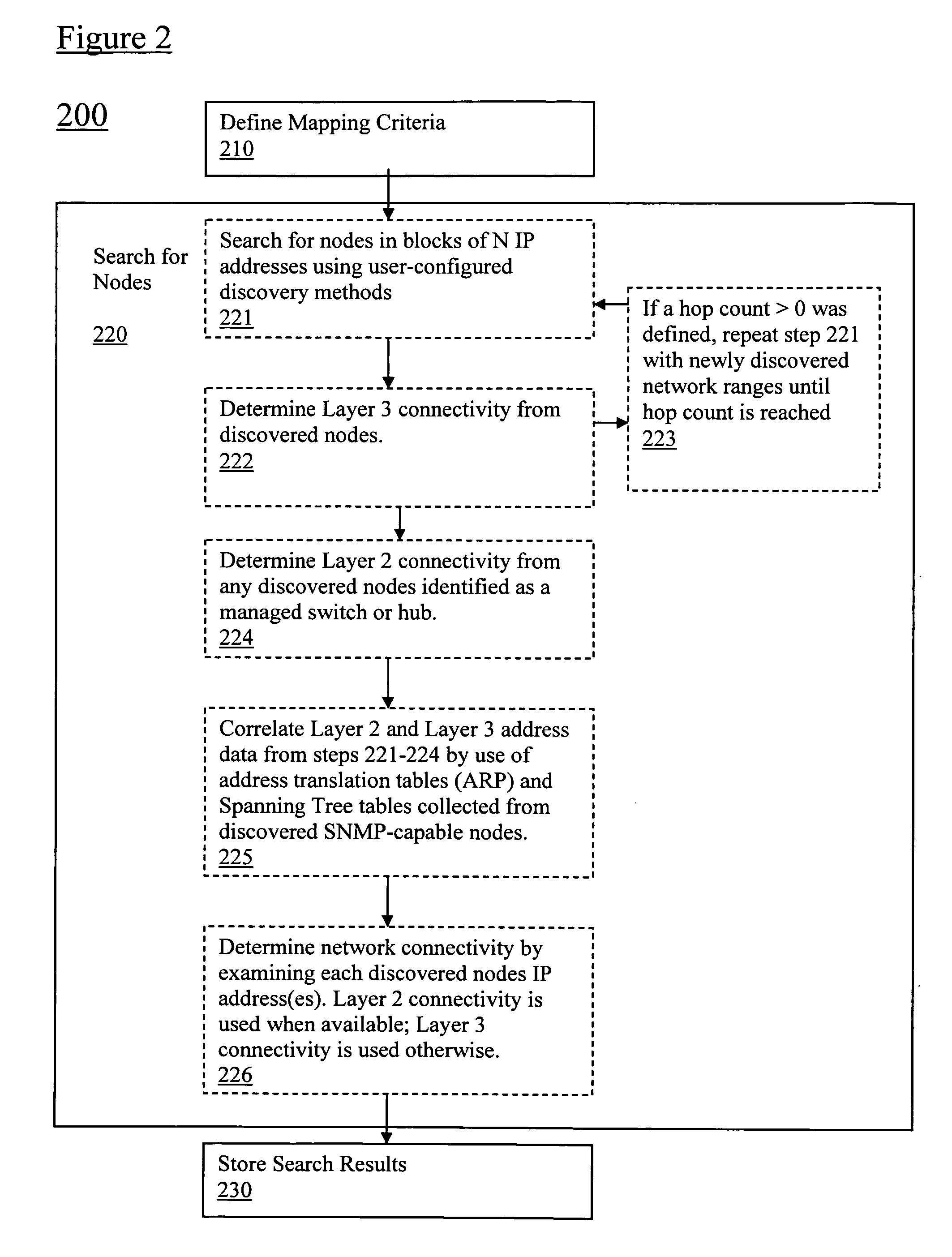
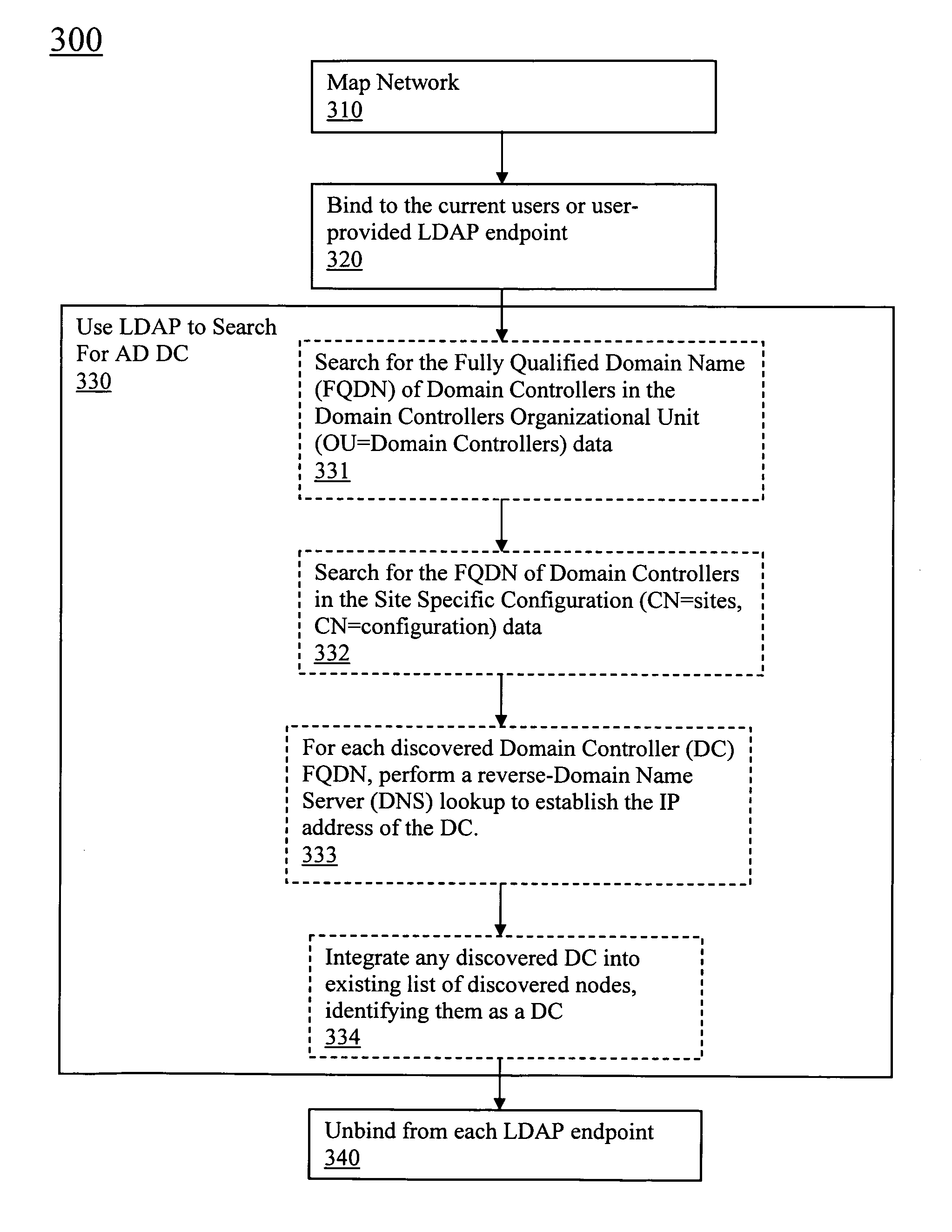
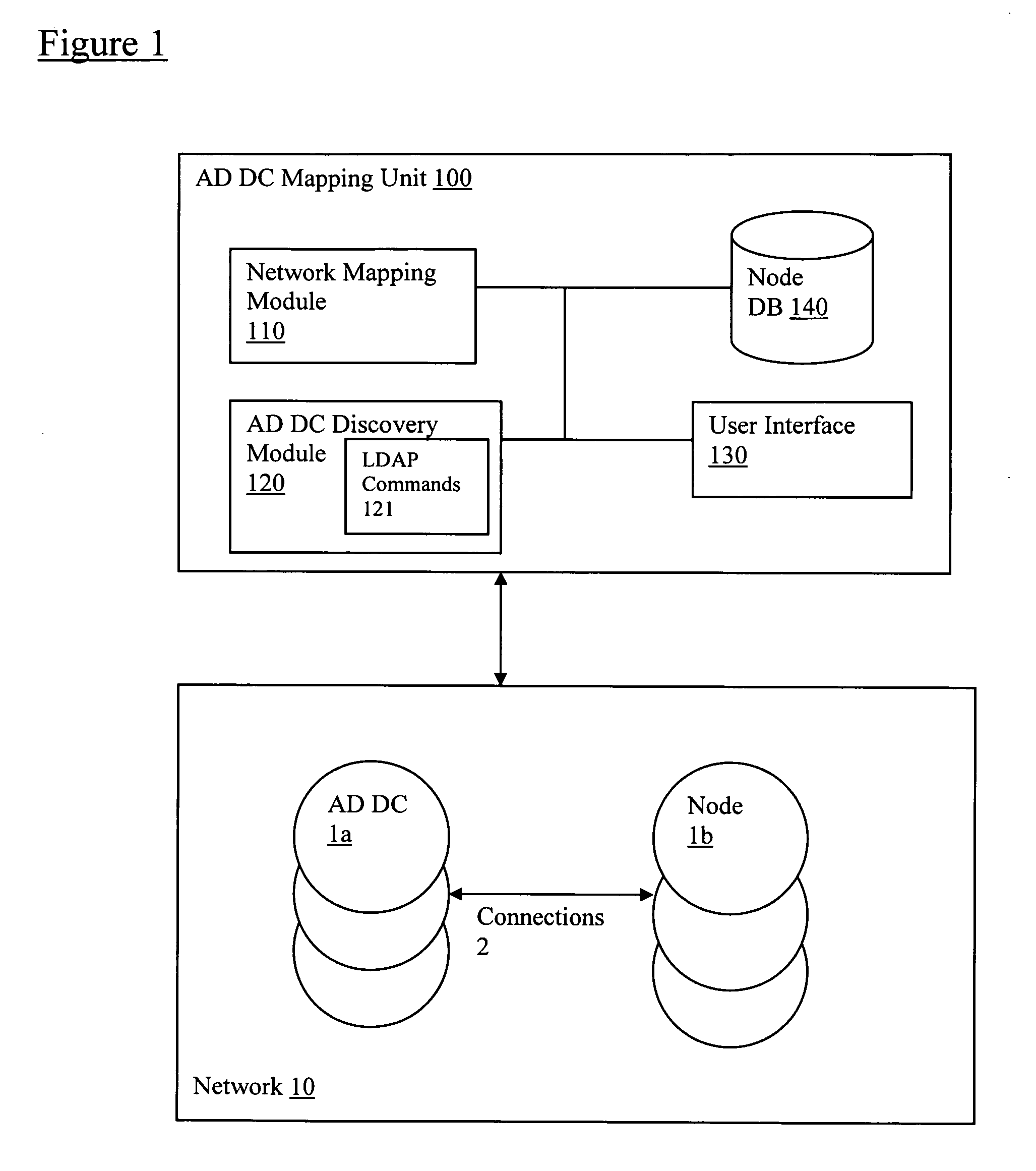
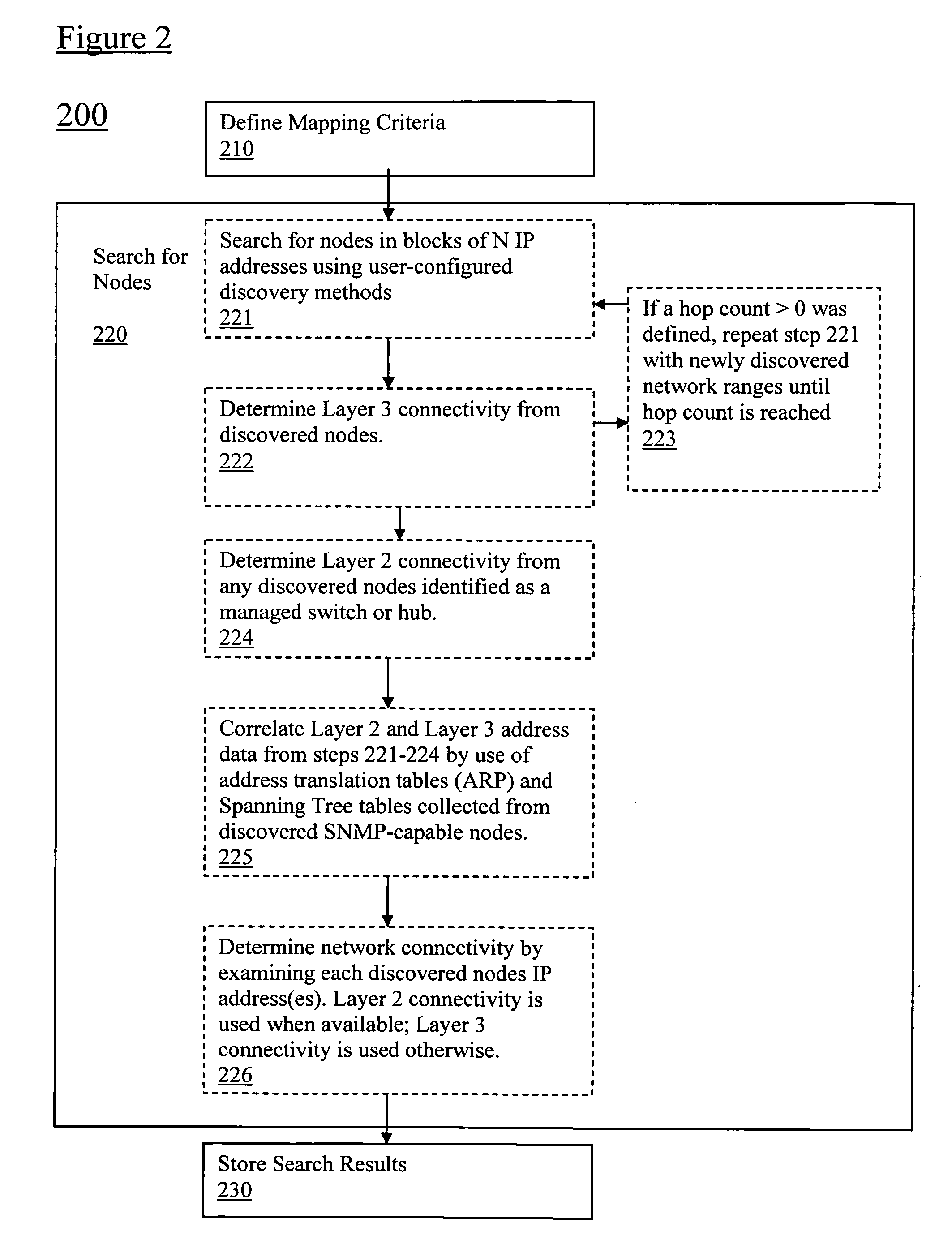
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS20090285120A1Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
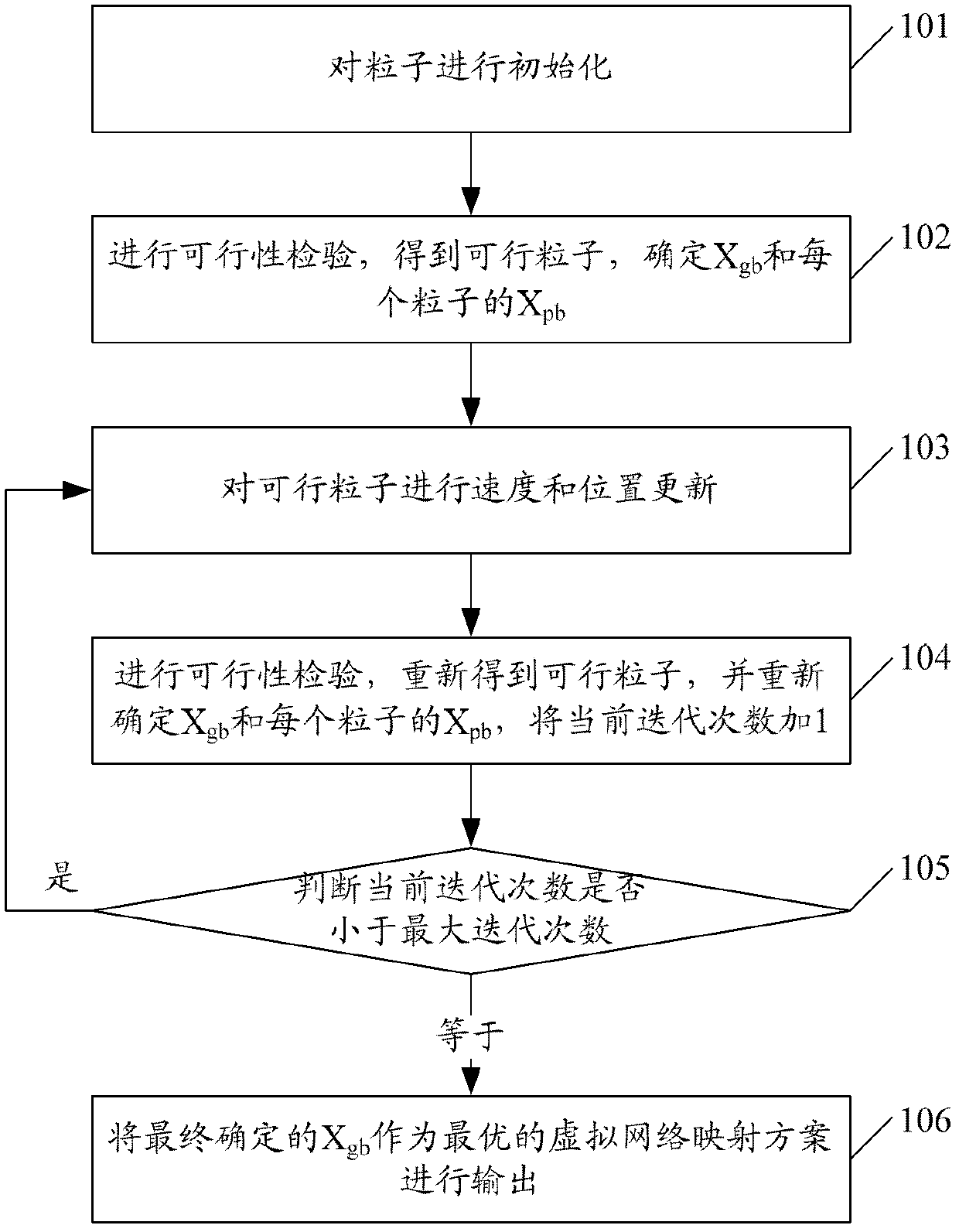
Particle-swam-optimization-based virtual network mapping method and system
InactiveCN102364899AImprove resource utilization efficiencyBalance optimizationNetworks interconnectionResource utilizationNetwork mapping
The invention provides a particle-swarm-optimization-based virtual network mapping method and a particle-swarm-optimization-based virtual network mapping system. The method comprises the following steps of: initializing position and speed parameters of particles; performing feasibility checking on the particles to obtain feasible particles, and determining an initial global optimal position and individual optimal positions of each particle; performing speed and position updating on the feasible particles, performing the feasibility checking on the updated particles to obtain feasible particles again, determining a global optimal position and individual optimal positions again, adding 1 to a current number of iterations, and repeating the operations of the step when the number of iterations is less than a maximum number of iterations; and when the number of iterations is equal to the maximum number of iterations, outputting the finally determined global optimal position as a mapping scheme. By the method and the system, the position and speed parameters of a particle swarm are initialized under the condition that a bottom-layer network does not support path splitting, and the particles are iterated to select an optimal virtual network mapping scheme, so the resource utilization efficiency of the bottom-layer network is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Methods and apparatus to prevent network mapping
ActiveUS7596097B1Blocking in networkInhibitory responseMultiplex system selection arrangementsError preventionSecurity policyNetwork mapping
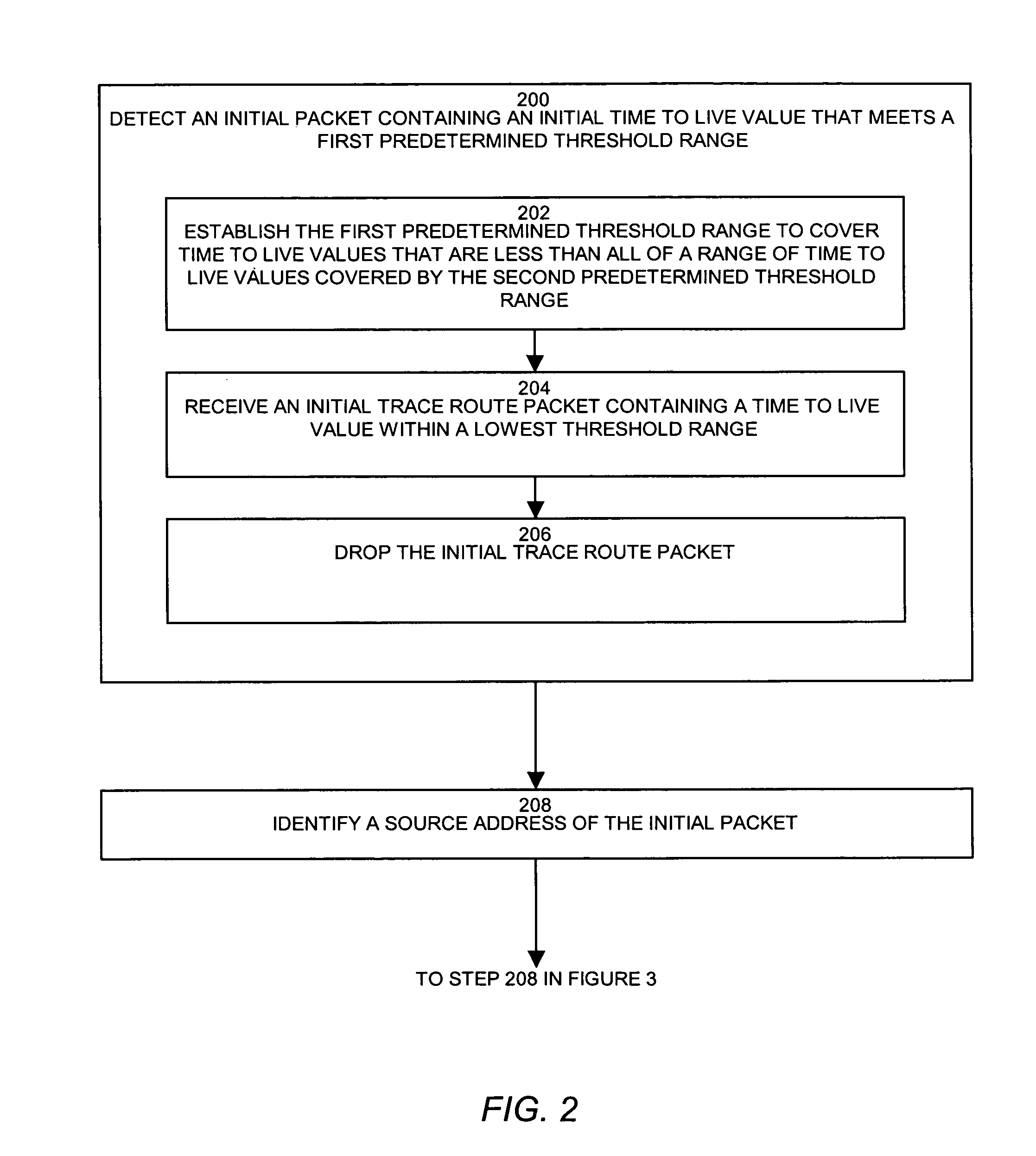
A trace detector prevents network mapping and tracing by detecting an initial packet containing an initial time to live value that meets a first predetermined threshold range. The trace detector identifies a source address of the initial packet and adjusts a threshold time to live range for detection of at least one subsequent trace route or response packet associated with the source address of the initial packet. In response to detecting the subsequent packet(s), the trace detector processes the subsequent packet(s) associated with the source address of the initial packet according to a security policy to prevent a trace process originating the initial packet from tracing a network using the at least one subsequent packet.
Owner:CISCO TECH INC
Network node failover using multicast address or port
InactiveUS6944786B2Special service provision for substationRedundant hardware error correctionFailoverMulticast address
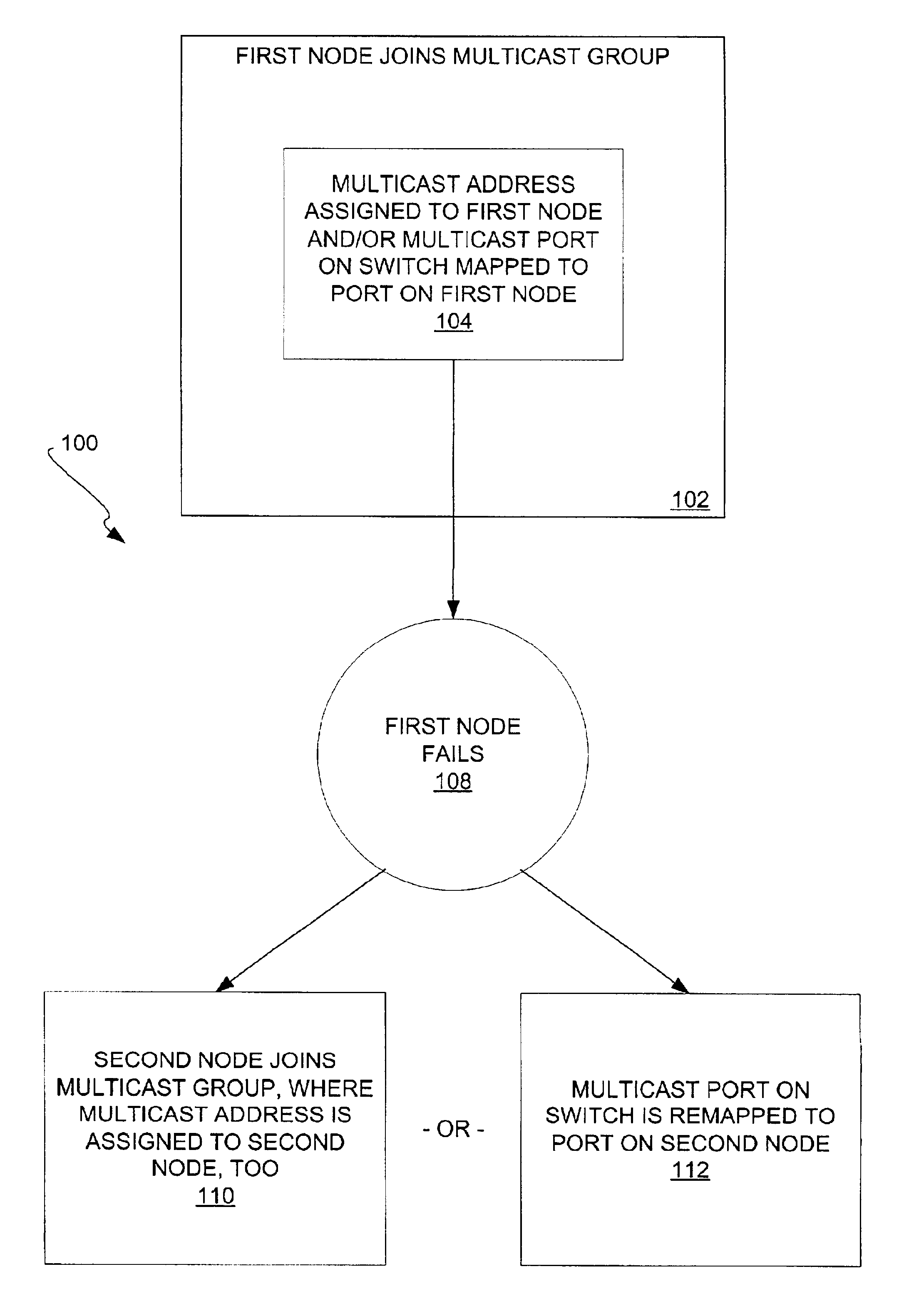
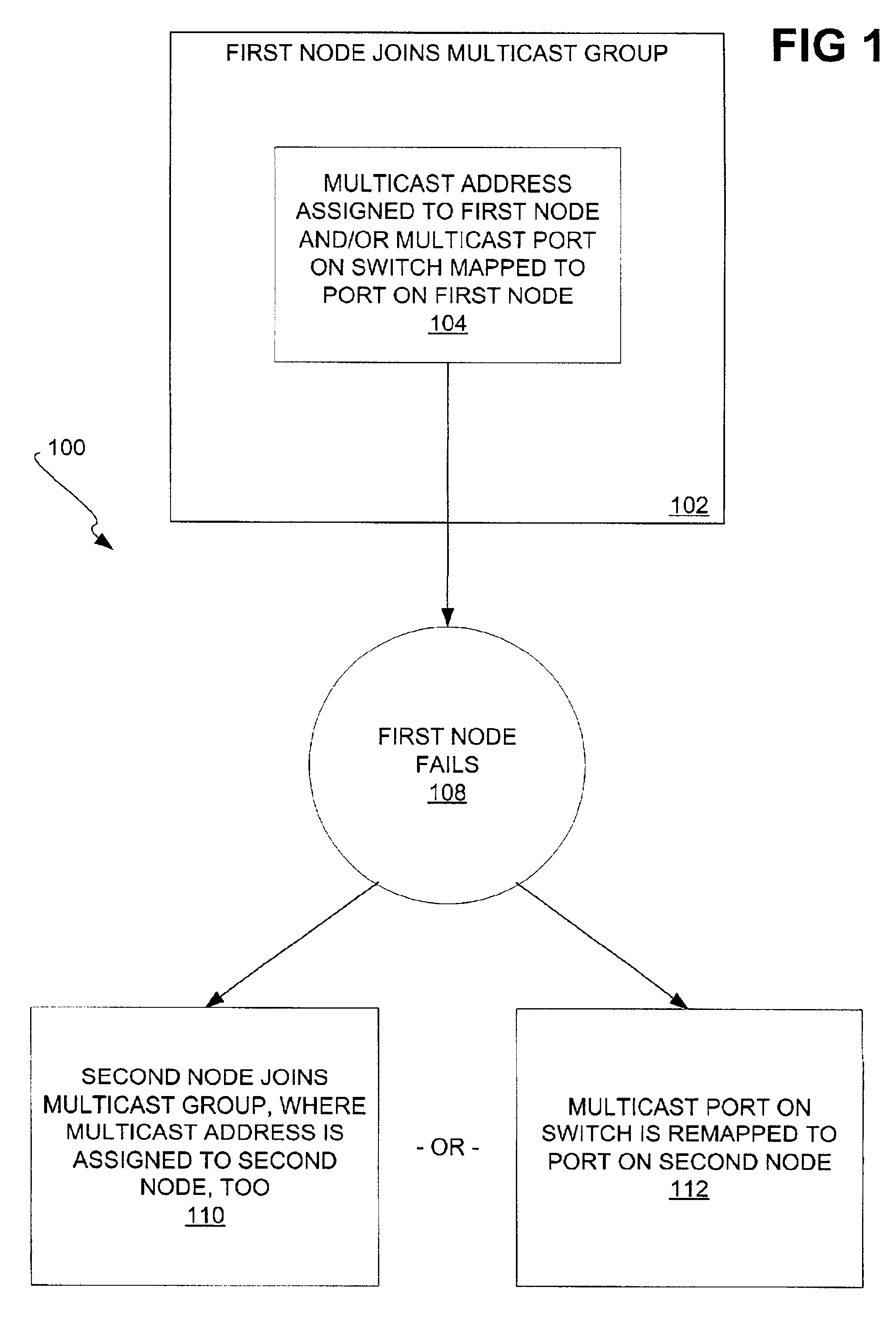
The failover of nodes within networks, using a multicast address or a multicast port, is disclosed. A first node of a network joins a multicast group having a multicast address, which is assigned to the first node. Communication to the first node is achieved via communication to the multicast address, and / or through a multicast port on a switch of the network mapping to a port on the first node. When the first node fails, one of two actions occurs. First, a second node of the network may join the multicast group, such that the multicast address is assigned to the second node, and the second node handles communication to the multicast address. Second, the multicast port on the switch may be remapped to a port on the second node, so that communication to the multicast address is directed to the port on the second node.
Owner:LENOVO GLOBAL TECH INT LTD
Method for discovering protocol and acquiring network connection information by utilization of link layer
InactiveCN101345655AHigh precisionGood discovery performanceEnergy efficient ICTData switching networksInformation repositoryManagement information base
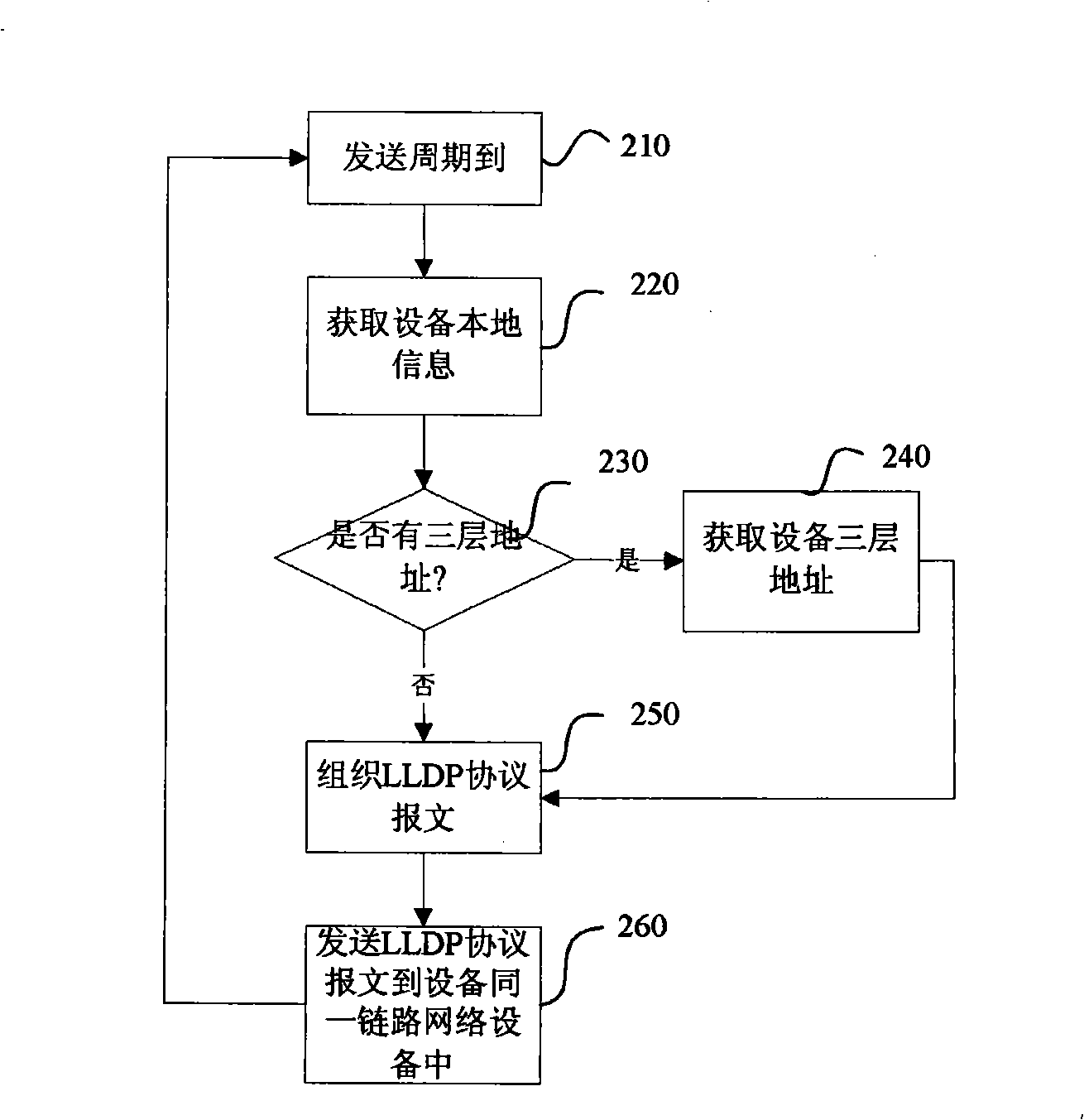
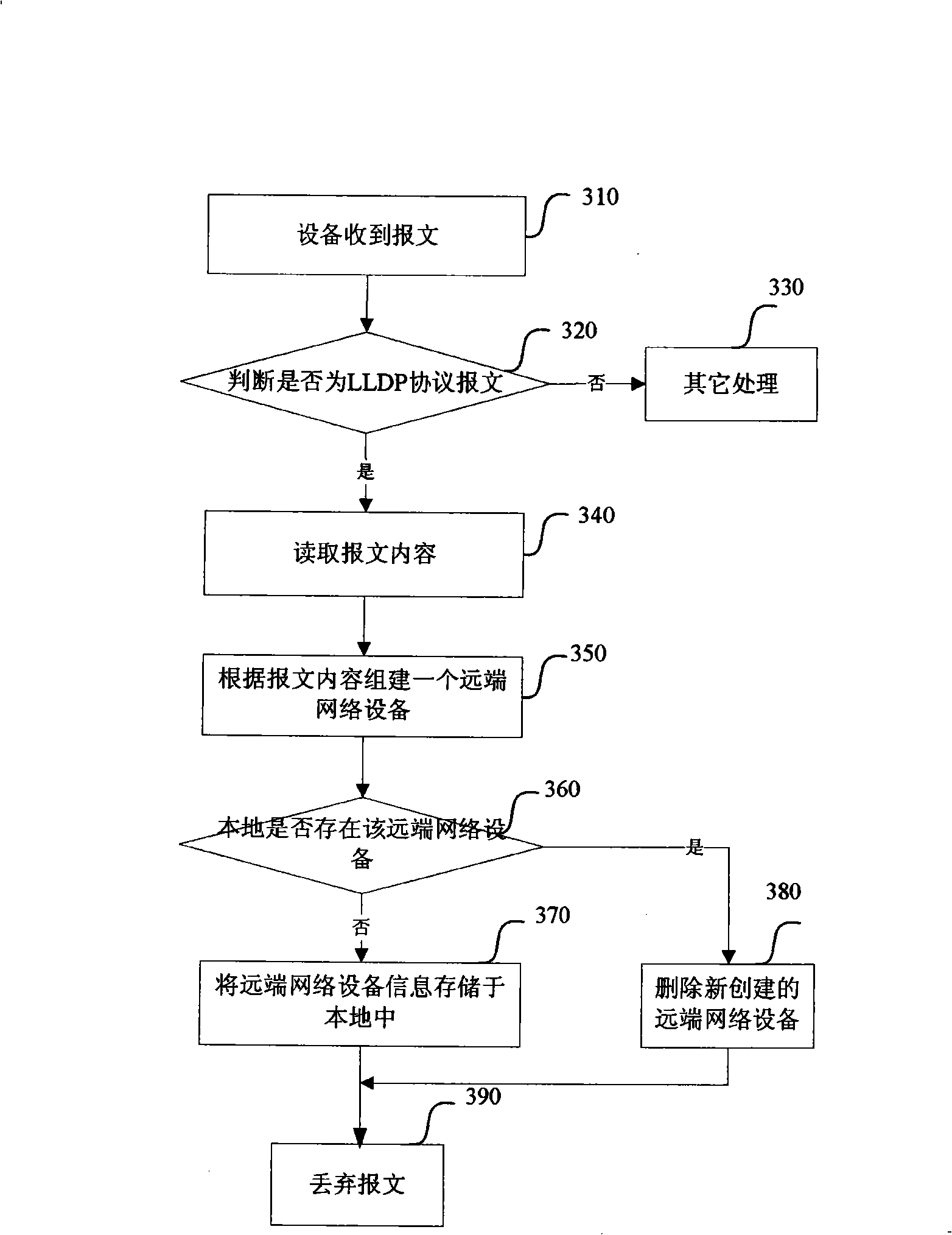
The invention provides a method of obtaining network connection information using a link layer finding protocol, comprising: transmitting link layer finding protocol message to other devices by a device, wherein the message is carried with local device information in the device; receiving the link layer finding protocol message from other devices by the device, resolving the link layer finding protocol message, composing a far-end network device information according to the local device information carried therein, storing the far-end network device information in the device; storing the far-end network device information stored locally into a link layer finding protocol management information base. The invention performs network information performs network information double ply through using LLDP protocol, stores neighbor network information in LLDP MIBs, used for network management software unified finding, thereby ensuring network mapping discovery between isomerization network, advancing accuracy of plotting topology by network management software.
Owner:ZTE CORP
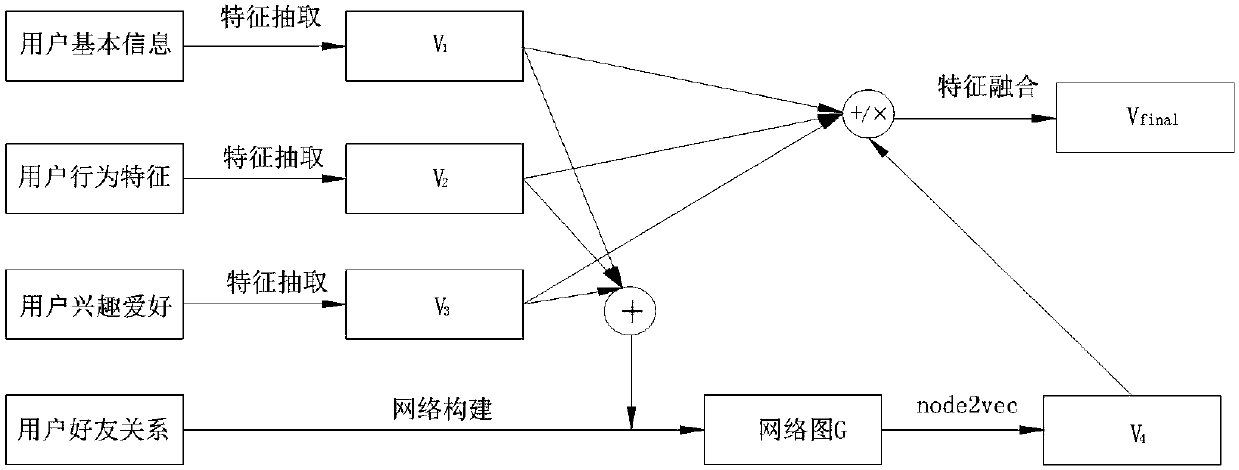
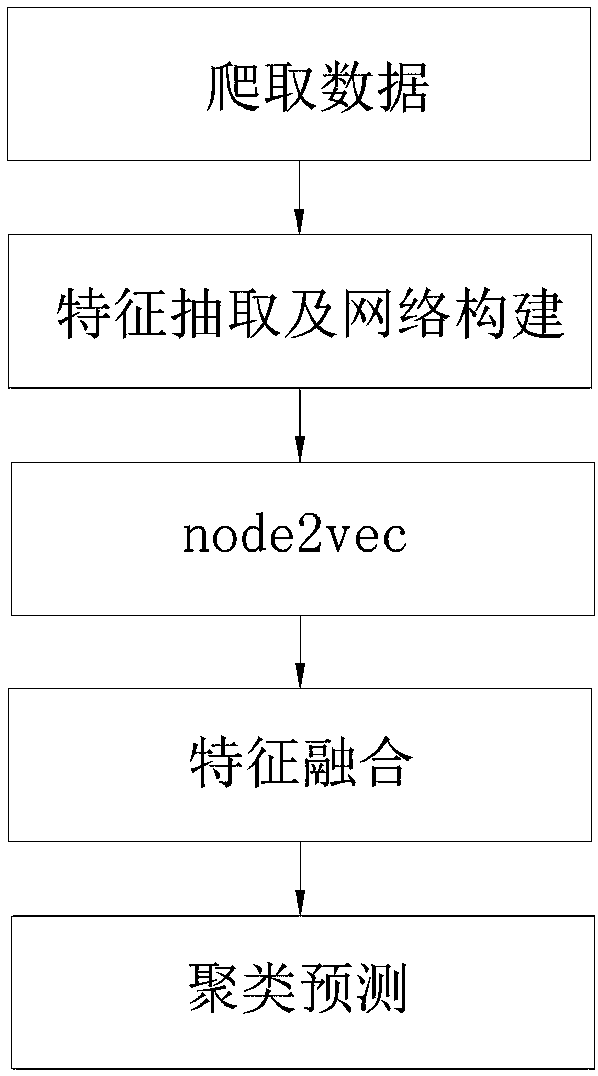
Detection method for abnormal user in social network based on network mapping
The invention relates to a detection method for an abnormal user in a social network based on network mapping. The method comprises the following steps of S1, crawling user data of a social network platform by using a web crawler technology; S2, preprocessing the crawled user data, and building a user social relation network graph G; S3, using node2vec to convert the social relation of a user intoa low-dimensional vector representation based on the user social relation network graph G; S4, fusing the multidimensional vector representations of the user to acquire a final vector representation;and S5, clustering based on feature vectors of the user, predicting the user is a normal user or the abnormal user, and if the user is the abnormal user, giving an abnormal type. The method providedby the invention has the advantages that the time and labor cost overheads are low, the various abnormal user types can be recognized, the new abnormal user type can be recognized, the multidimensional attribute features of the user can be comprehensively considered, and the accuracy is high.
Owner:SUN YAT SEN UNIV
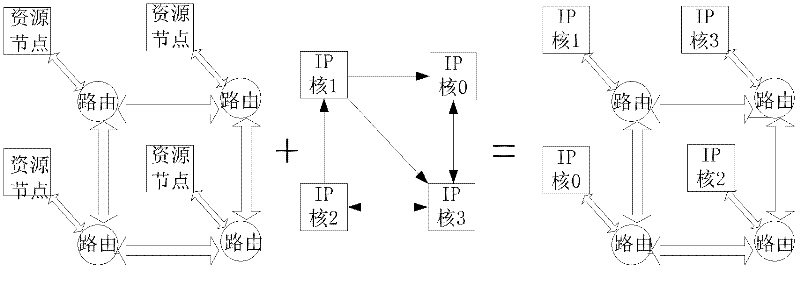
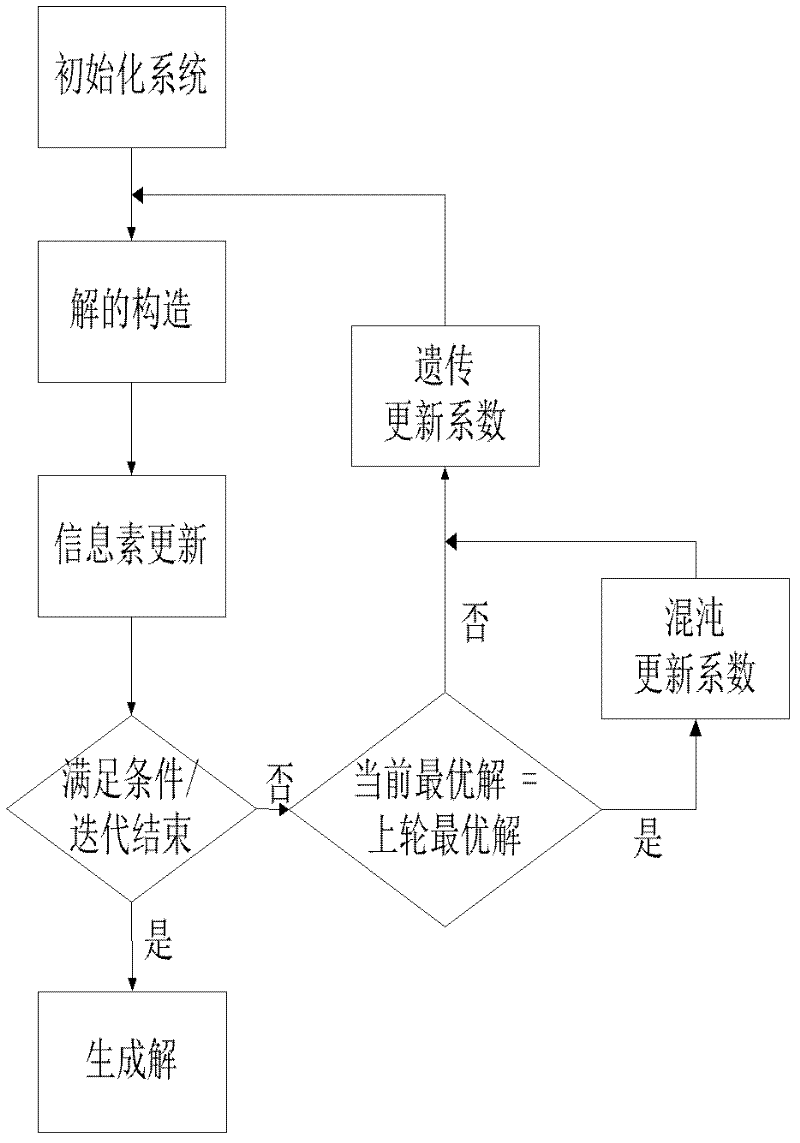
On-chip network mapping method based on ant-colony chaos genetic algorithm
InactiveCN102508935AImprove search capabilitiesGood practical valueGenetic modelsSpecial data processing applicationsLocal optimumMutation probability
Disclosed is an on-chip network mapping method based on the ant-colony chaos genetic algorithm. The standard ant-colony algorithm is basically used and the genetic algorithm is introduced in the on-chip network mapping method, parameters about each ant are coded by real numbers, codes of the ants are utilized as chromosome in the genetic algorithm, and algorithm parameters of coded ants are adjusted by the genetic algorithm in each iteration. During running of the algorithm, recycled results of each iteration of the algorithm are monitored, if the fact that the algorithm is trapped in a local optimum solution is monitored, mutation probability of the genetic algorithm is increased by a method of introducing a chaos model, and further, the parameters of the ant-colony algorithm are changed by means of the genetic algorithm. By the aid of the on-chip network mapping method, capability of the anti-colony chaos genetic algorithm for searching the solution space can be improved effectively, and trapping in the local optimum solution is avoided. In addition, the on-chip network mapping method has excellent practical values and wide application prospect for solution of massive on-chip network mapping.
Owner:NANJING UNIV
Discovery and visualization of active directory domain controllers in topological network maps
ActiveUS8045486B2Digital computer detailsData switching by path configurationIp addressSynthetic data
Active directory (AD) Domain Controllers (DC) discovery includes determining the topology of the network, such as the nodes and connections in the network. For example, synthetic data may be transferred within the network and traced to determine the presence and relationships of the various network components. Alternatively, other mapping techniques are based upon mapping a known set of nodes to determine the relationship of the nodes. Next, Lightweight Directory Access Protocol (LDAP) commands are forwarded to the various nodes to identify the AD DC within a range of IP addresses discovered during the mapping of to the topology of the network.
Owner:SOLARWINDS WORLDWIDE
Method for mapping mobile virtual network based on clustering
InactiveCN103259744AShielding effectData switching networksWireless communicationVirtual network topologyResource allocation
The invention discloses a method for mapping a mobile virtual network based on clustering. The method for mapping the mobile virtual network based on the clustering aims to improve the mapping success rate from a virtual network to a mobile physical network and virtual network revenue and to reduce mapping overhead. The method for mapping the mobile virtual network based on the clustering takes the physical network clustering as a basis and solves the problems that nodes and links in the process of virtual network mapping and in the process of resource allocation are poor in coordination, and algorithm performance is poor when virtual network topology is sparse in a mobile network environment. The method for mapping the mobile virtual network based on the clustering comprises the following steps: according to the displacement law of the nodes, predicting stability of the links among the nodes, clustering the physical network accordingly, and dividing the virtual network mapping into an inter-cluster mapping mode and an inside-cluster mapping mode. According to the method for mapping the mobile virtual network based on the clustering, due to the fact that a clustering method based on node prediction and the inter-cluster and the inside-cluster mapping modes based on the clustering are introduced, the virtual network mapping can achieve efficient and high success rate of request for the virtual network in the mobile network environment as well.
Owner:BEIHANG UNIV
Proton beam therapy control system
InactiveUS20080270517A1Reduce utilizationReduce complexityLocal control/monitoringMultiprogramming arrangementsTraffic capacityControl system
A tiered communications architecture for managing network traffic in a distributed system. Communication between client or control computers and a plurality of hardware devices is administered by agent and monitor devices whose activities are coordinated to reduce the number of open channels or sockets. The communications architecture also improves the transparency and scalability of the distributed system by reducing network mapping dependence. The architecture is desirably implemented in a proton beam therapy system to provide flexible security policies which improve patent safety and facilitate system maintenance and development.
Owner:LOMA LINDA UNIV MEDICAL CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com