Patents
Literature
137 results about "Network mobility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
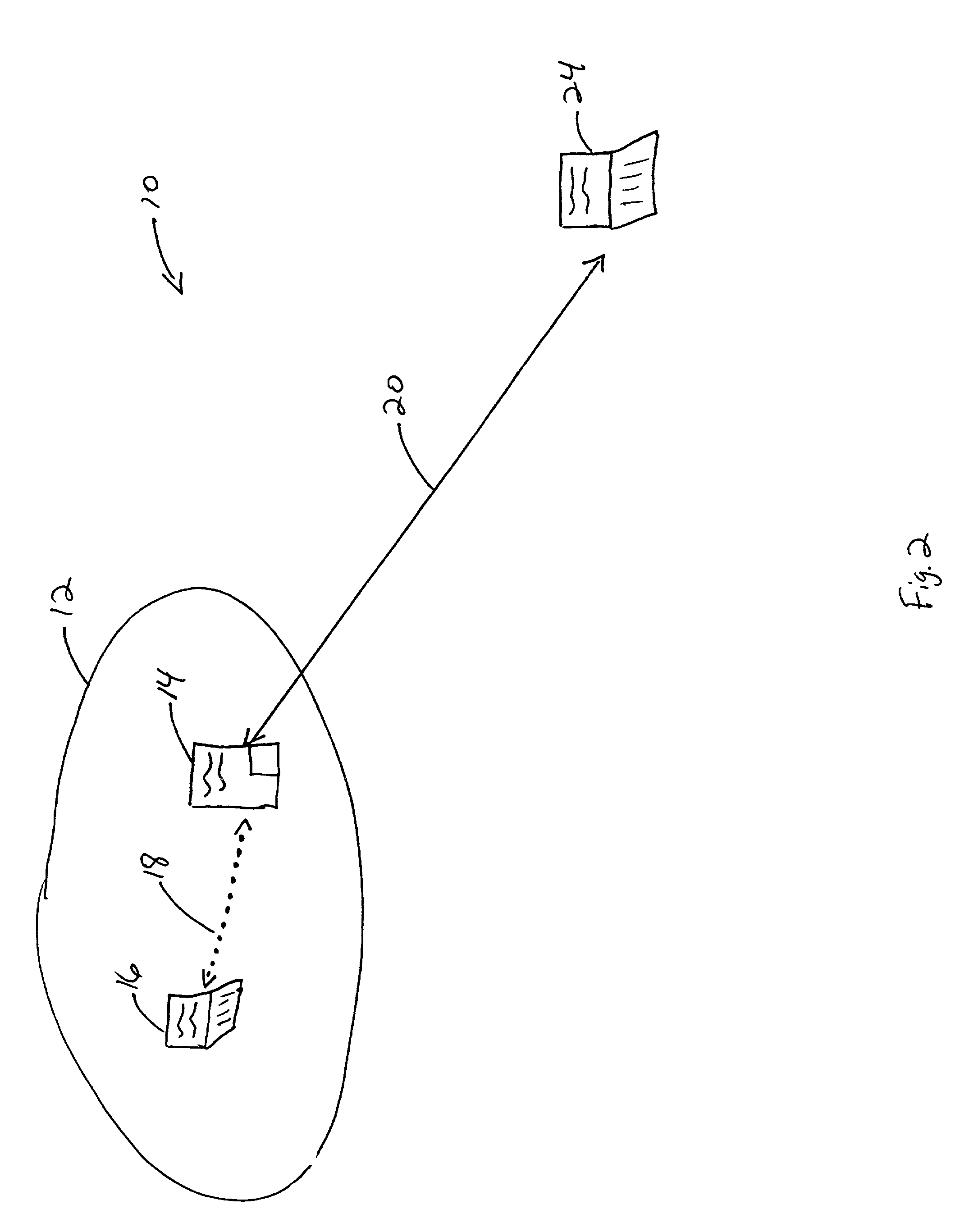
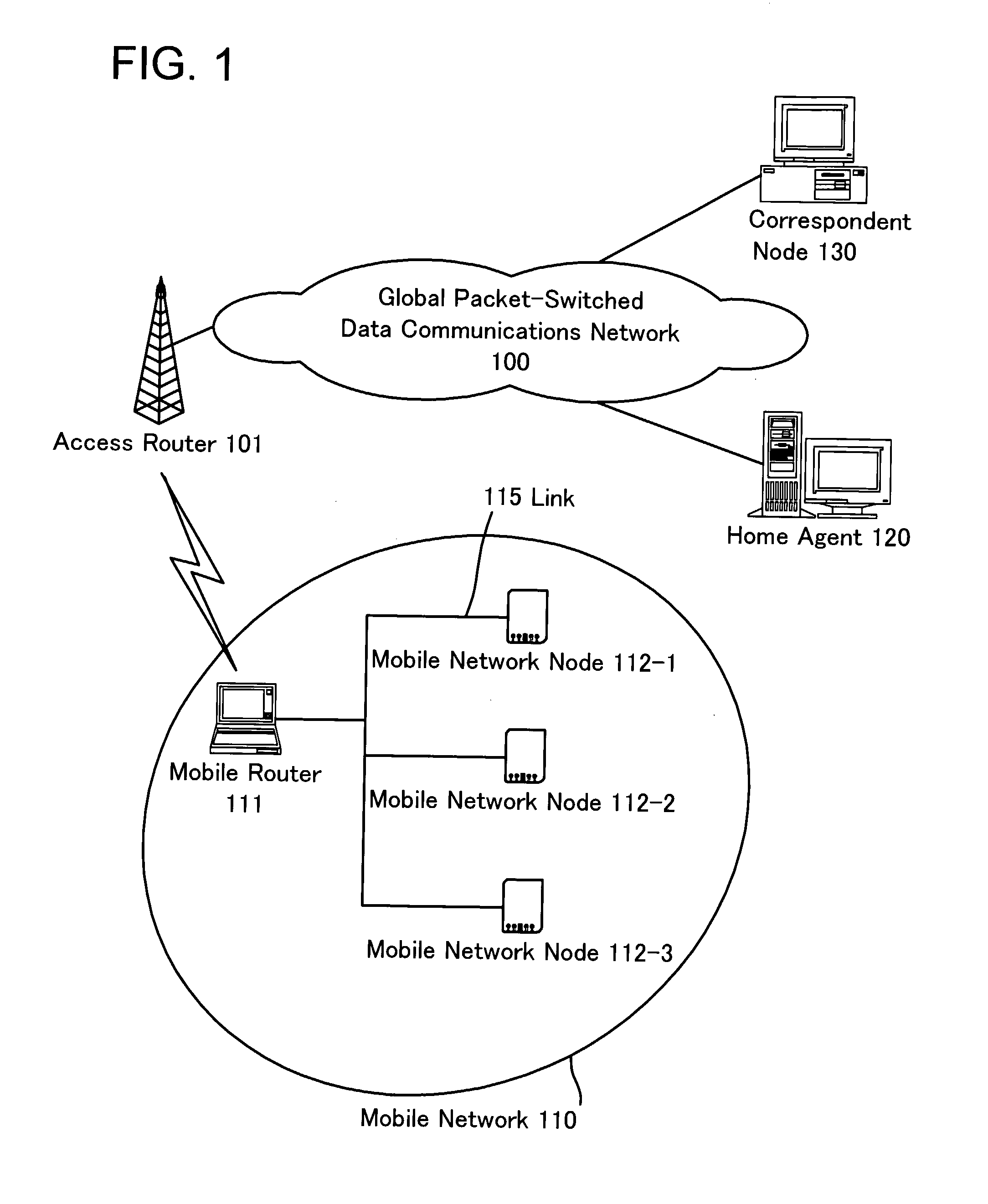
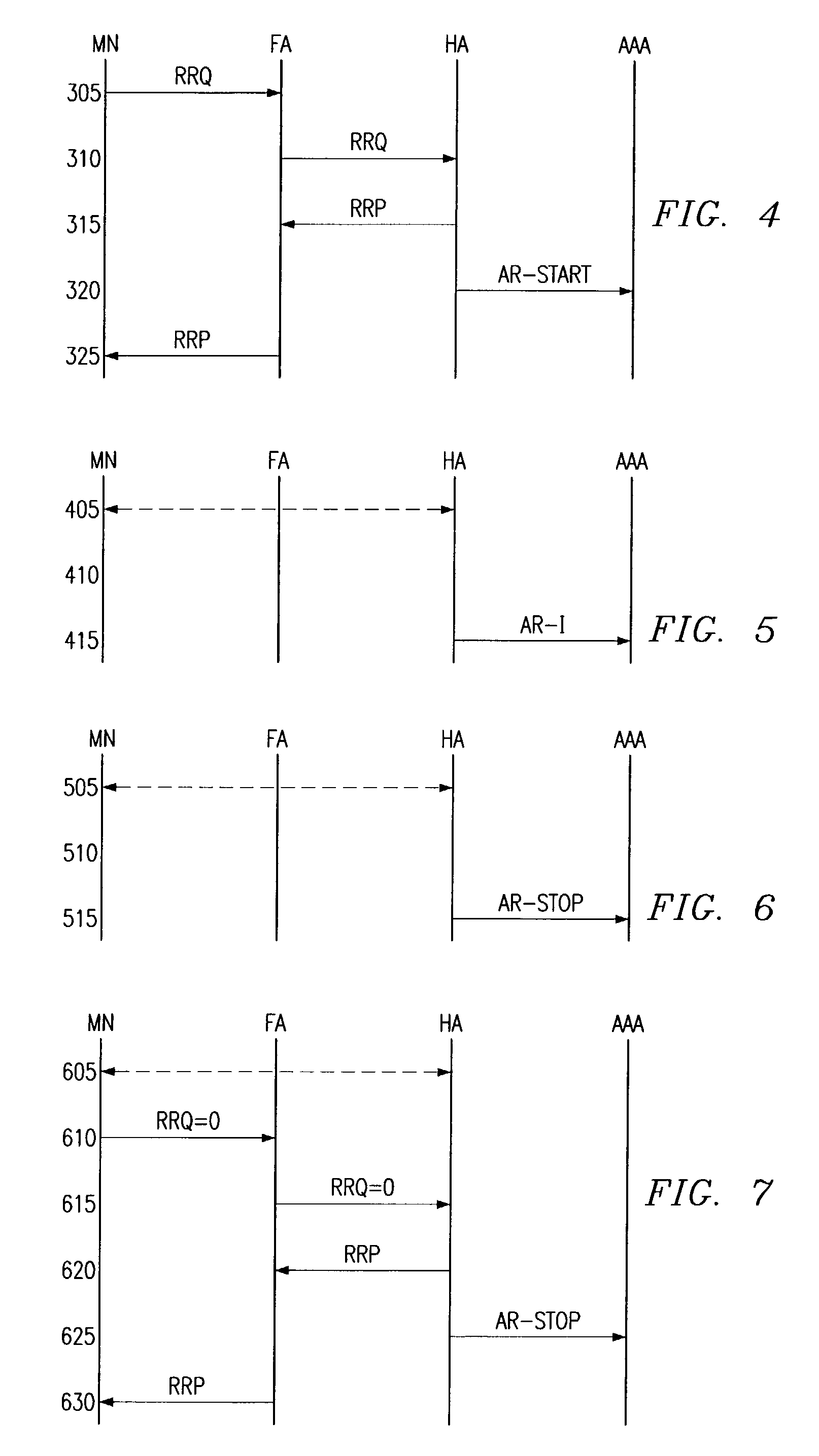
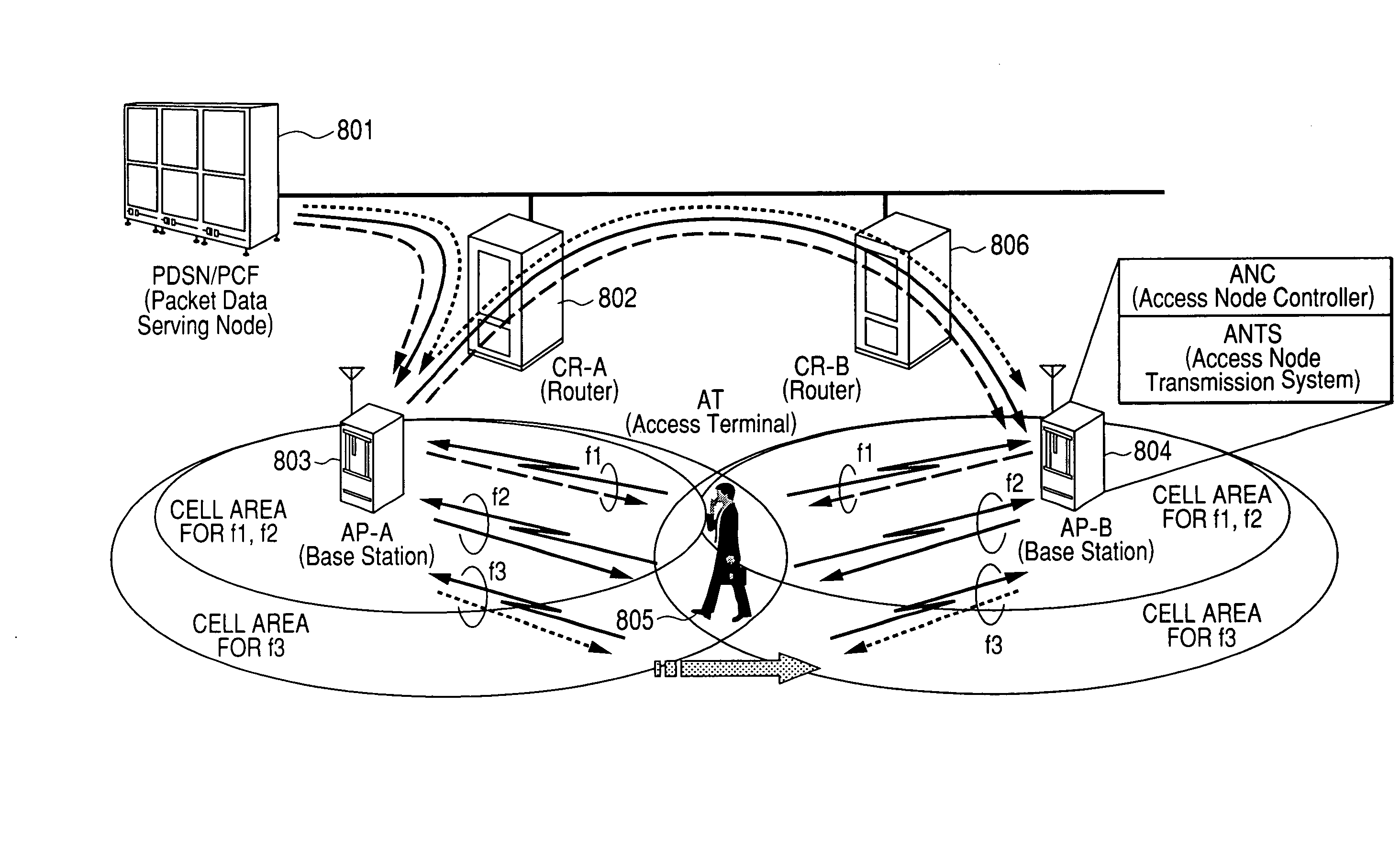
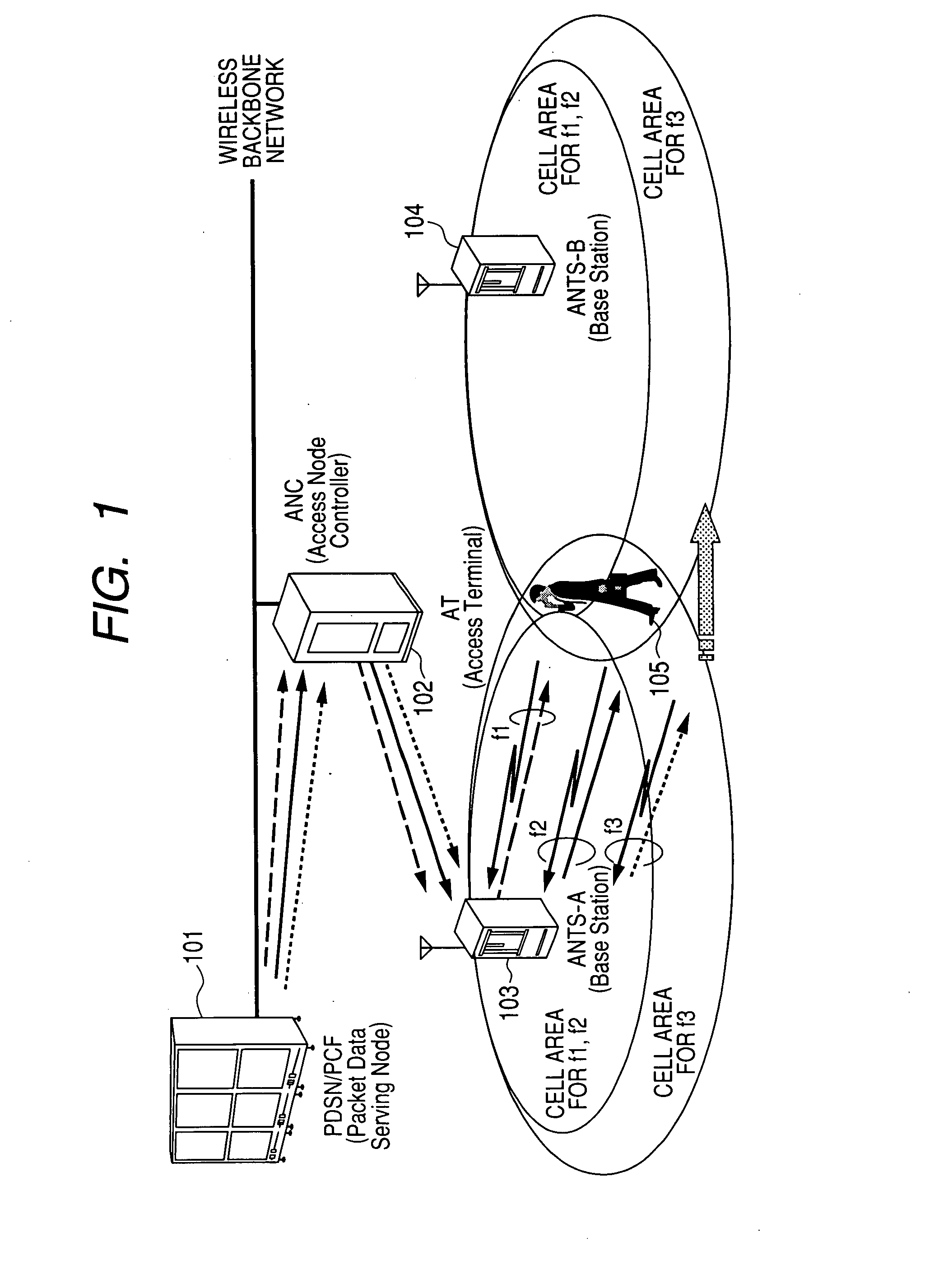
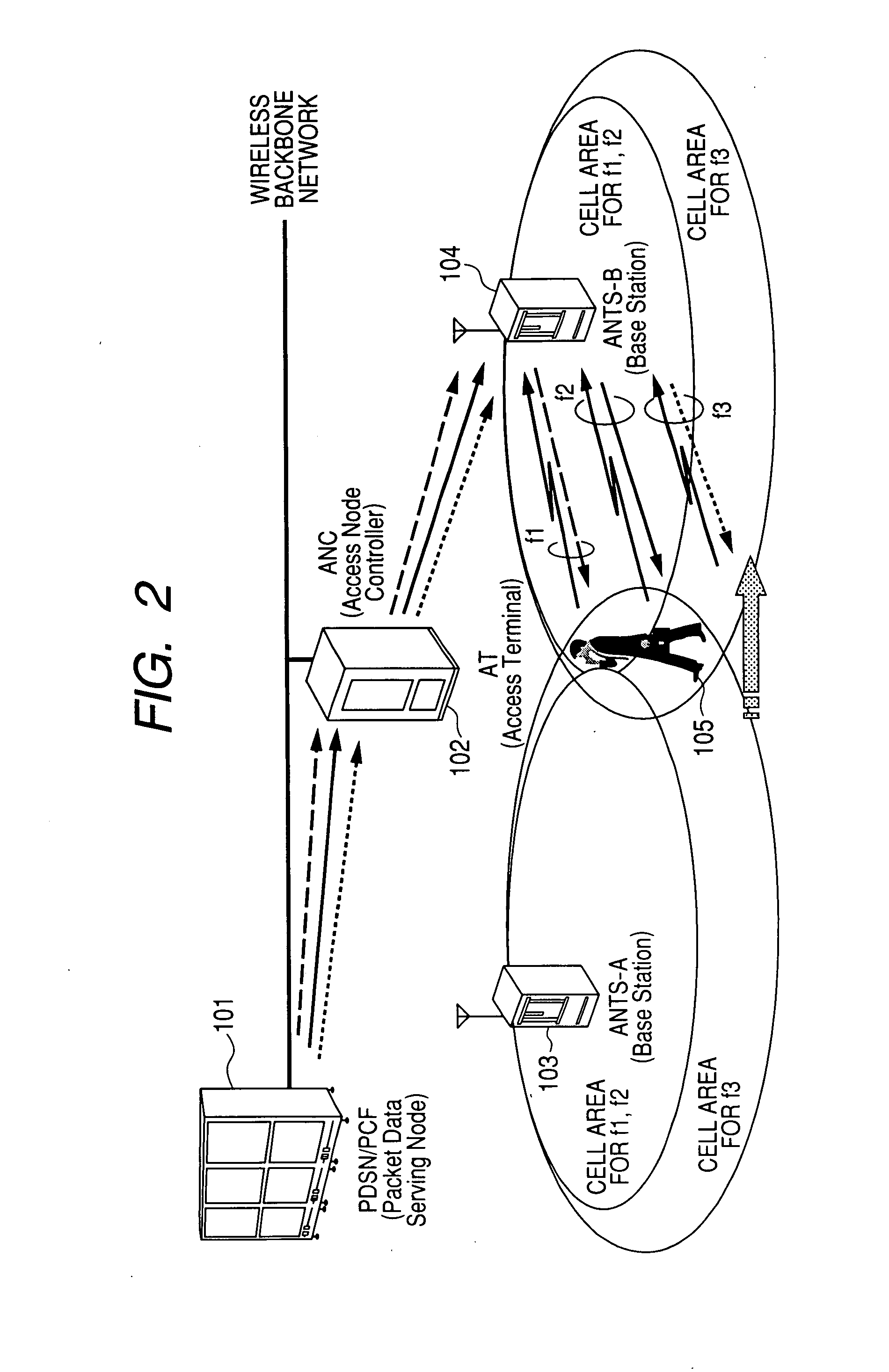
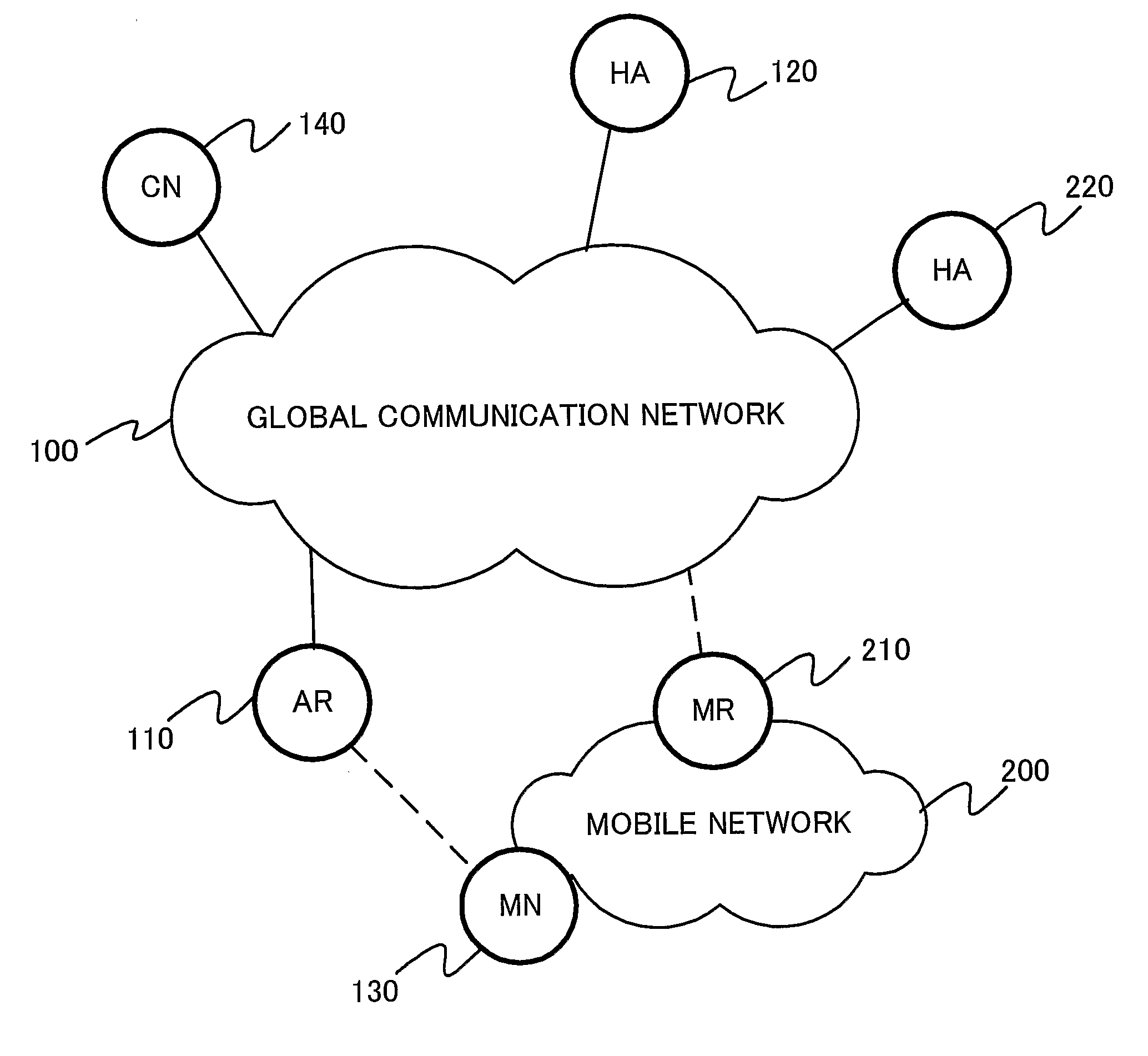
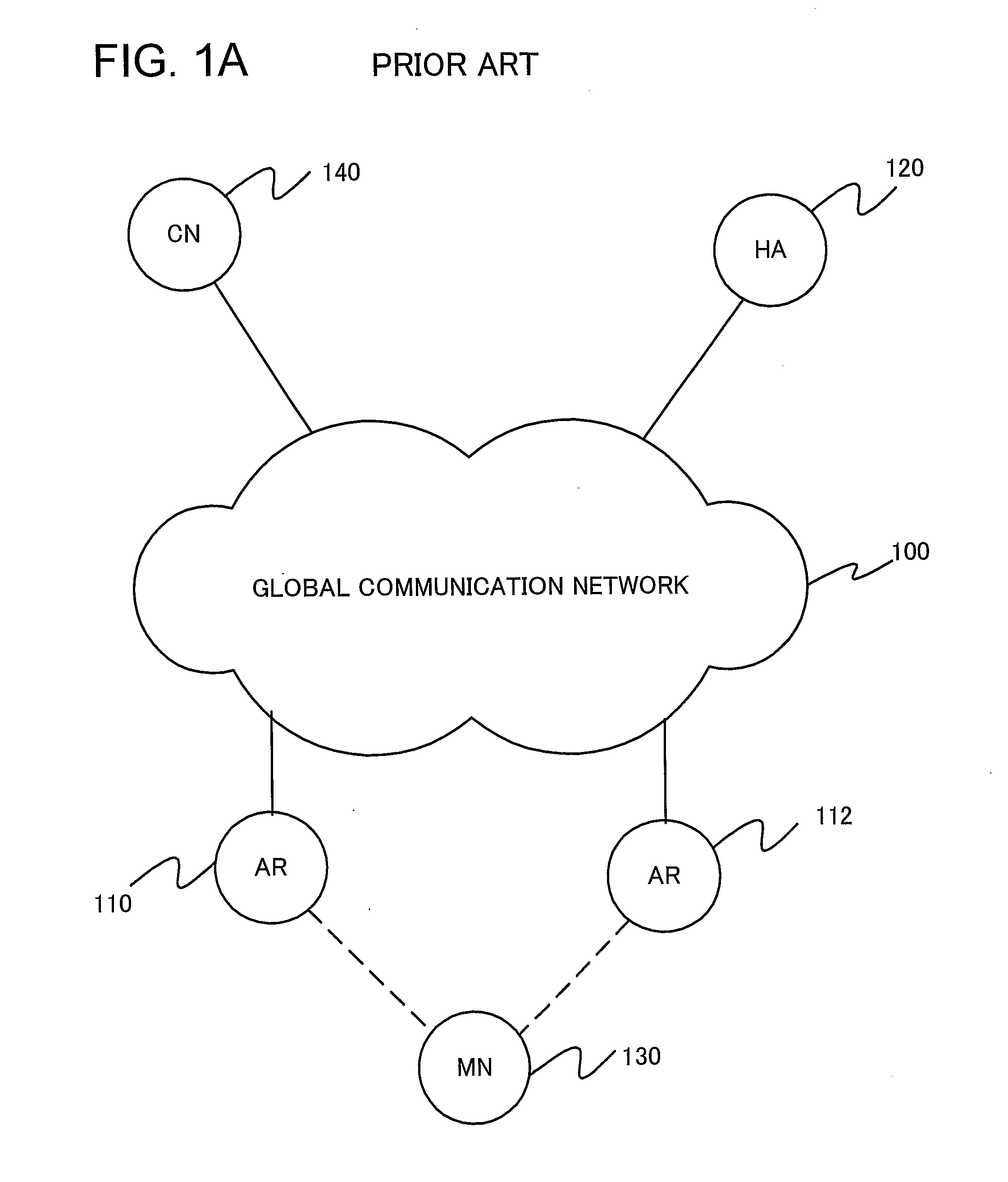
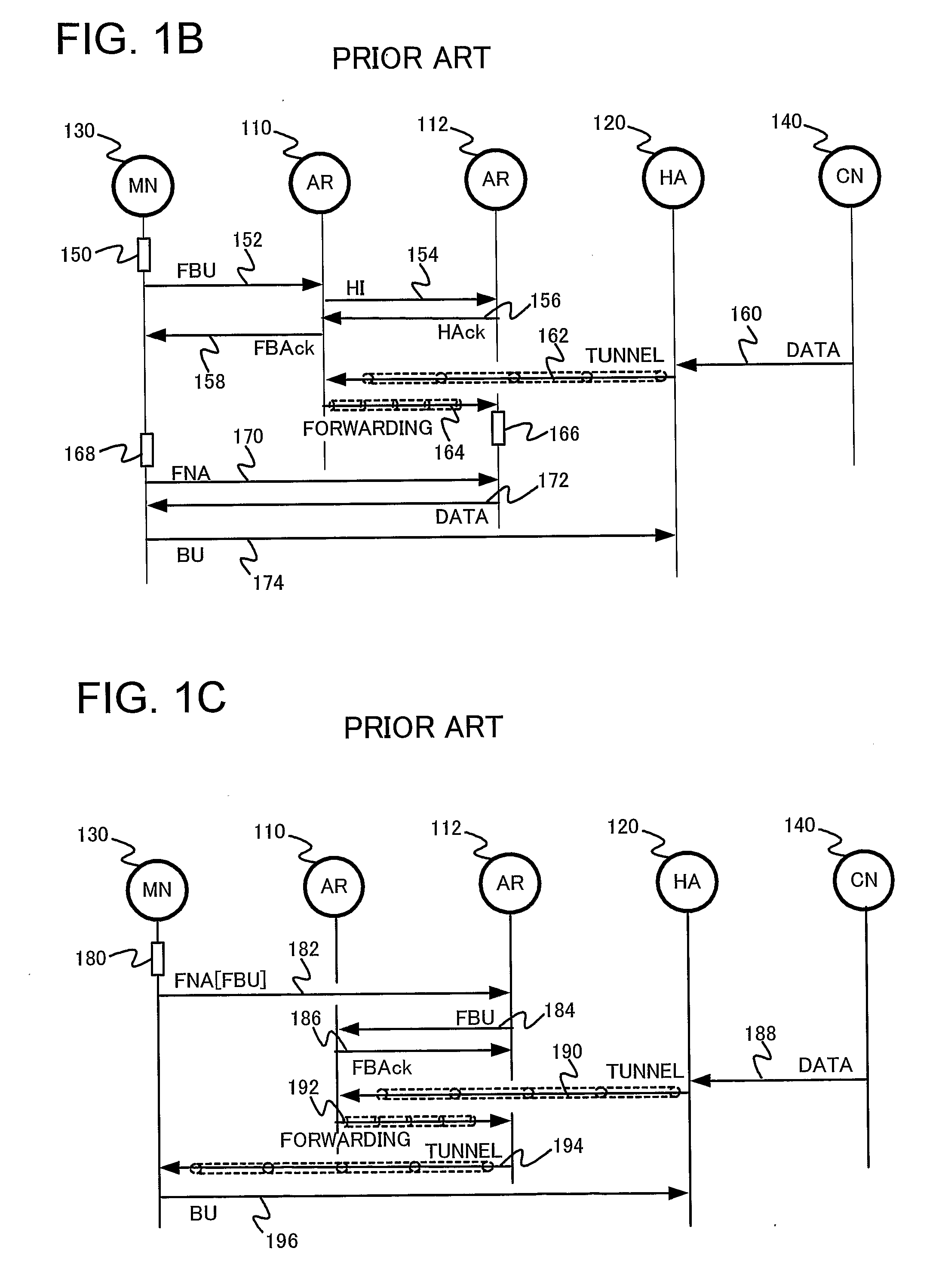
Network Mobility (NEMO) is an Internet standards track protocol defined in RFC 5177. The protocol allows session continuity for every node in a mobile network as the network moves. NEMO requires a service provider, e.g. Verizon Wireless Private Network with DMNR (Dynamic Mobile Network Routing).
Network mobility
InactiveUS20060159088A1Reduces encapsulation overheadShort transport layer connection/transmission durationNetwork topologiesData switching by path configurationNetwork addressingNetwork mobility
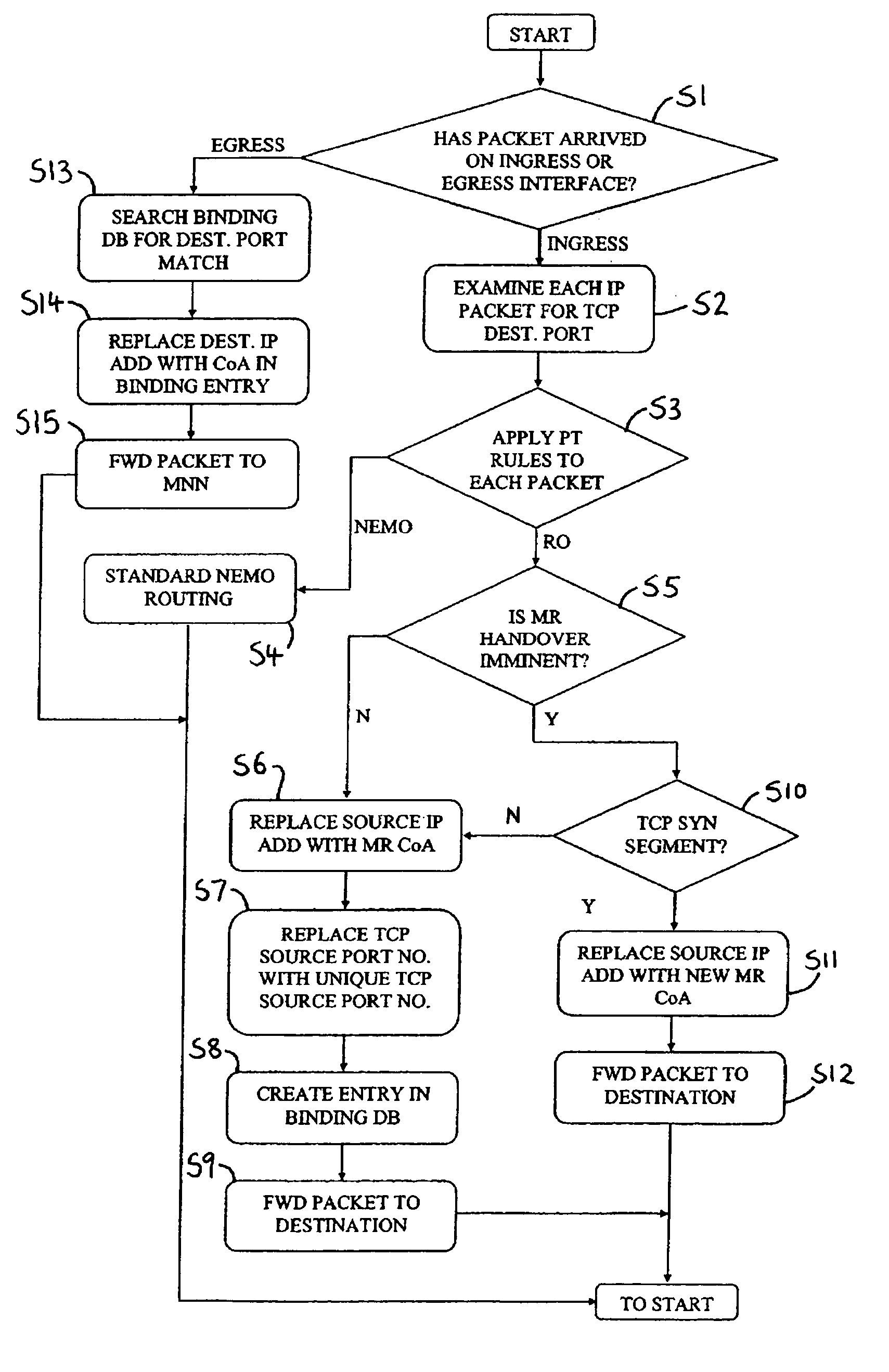
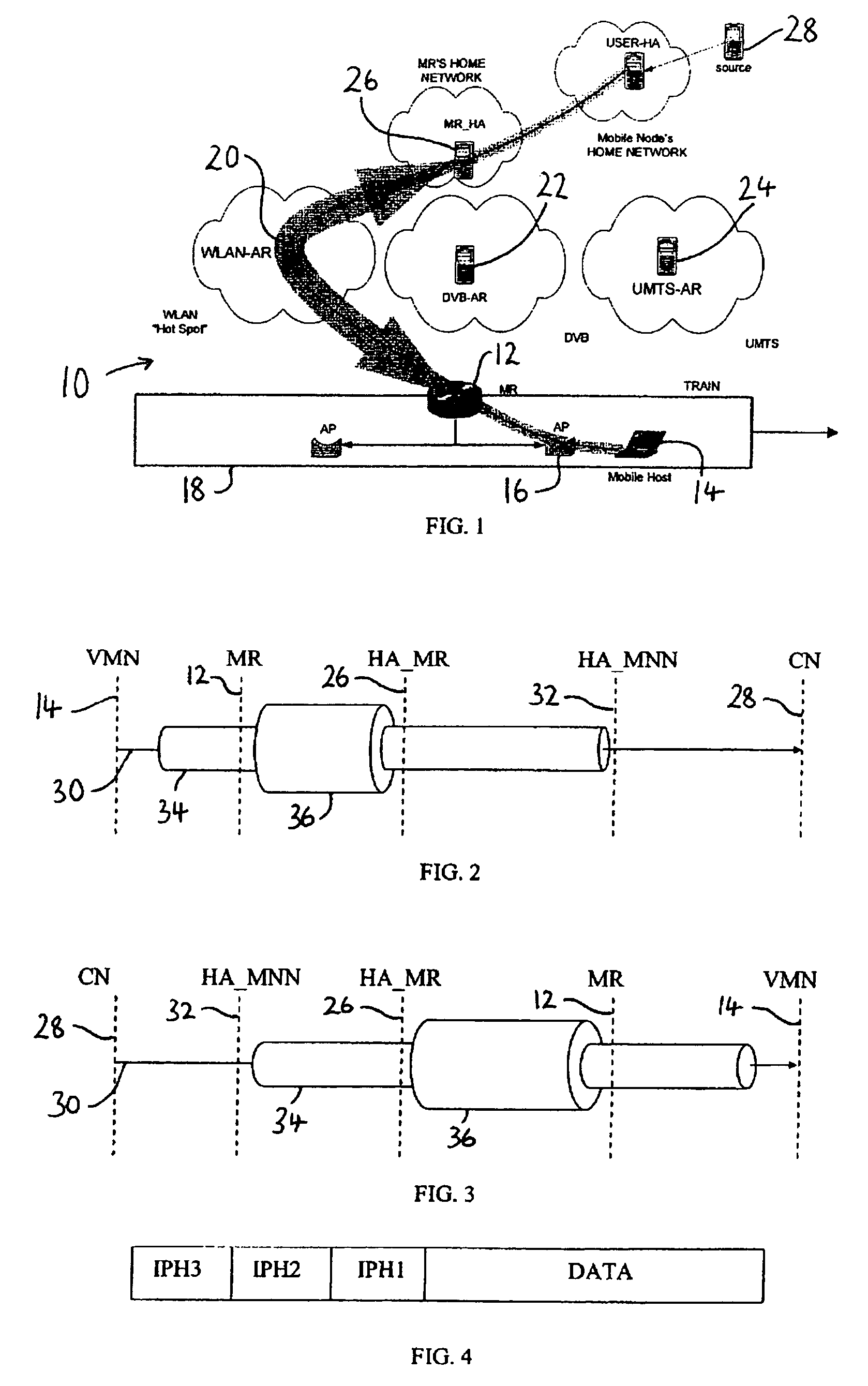
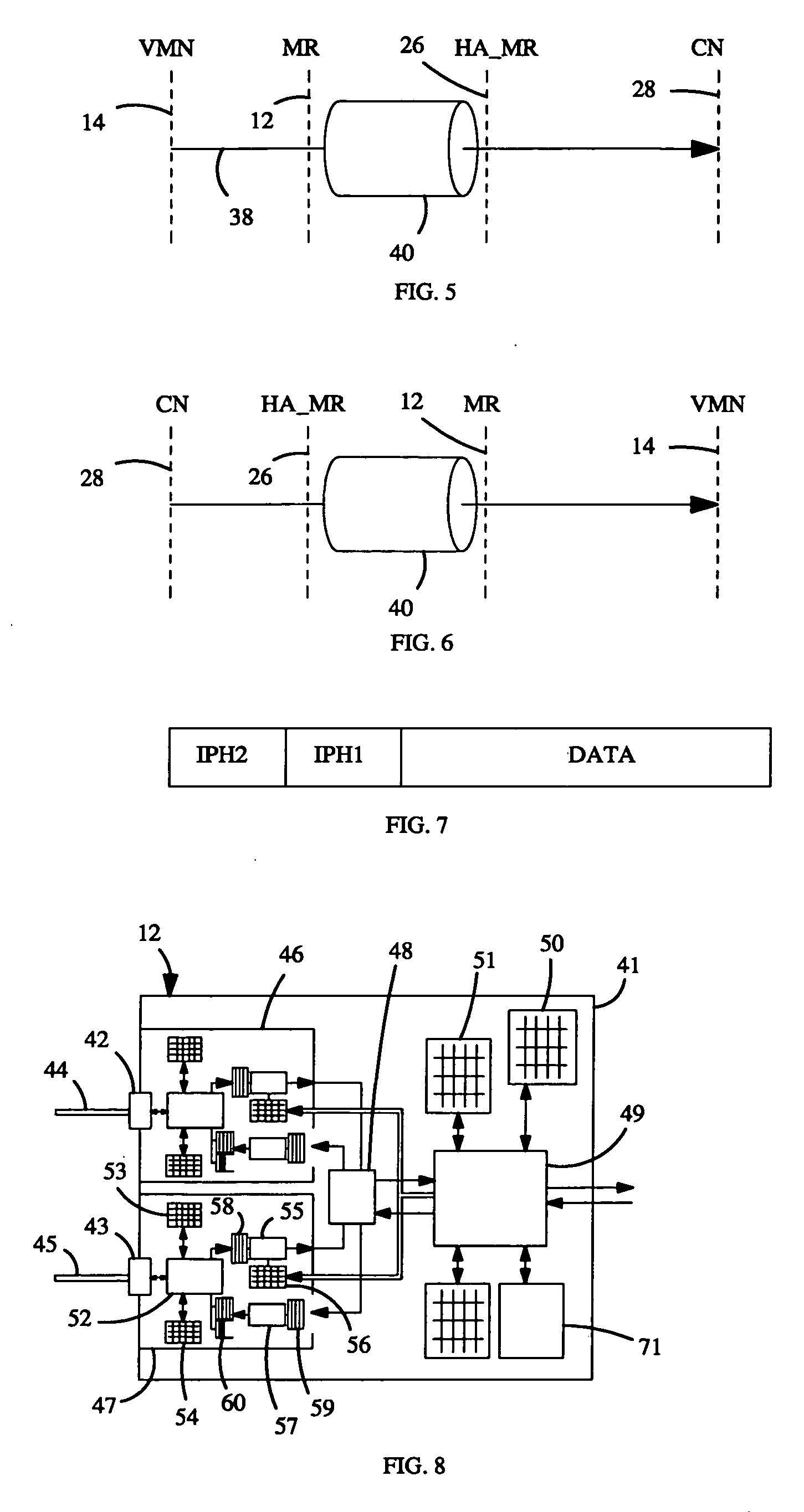
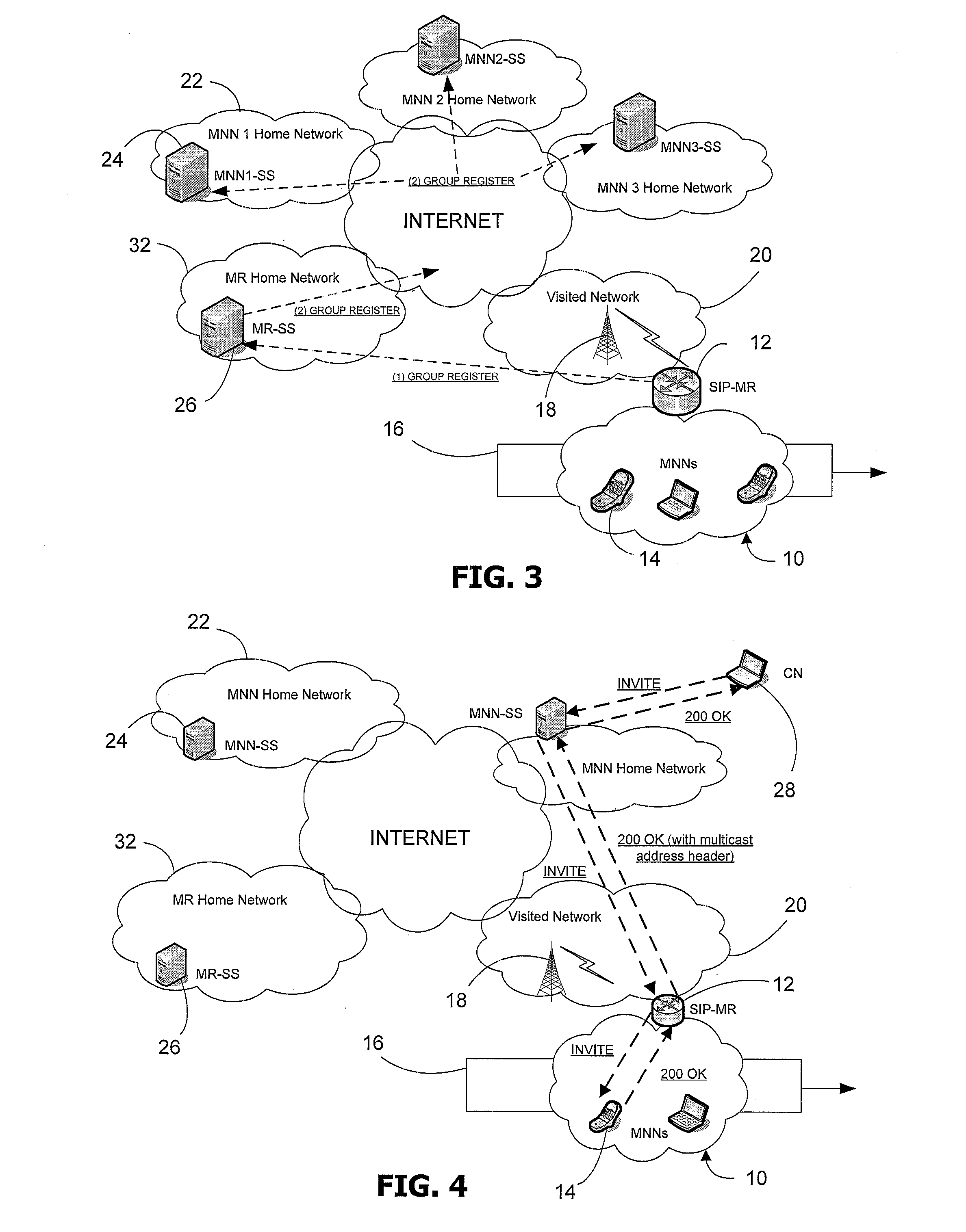
A method of routing data packet flows from a mobile router in a mobile network, which mobile network comprises one or more network node attached to said mobile router, said mobile router for providing transparency at the network layer for said one or more network node to movement of said mobile network relative to a fixed network infrastructure, which method comprises the steps of: (a) receiving a data packet from a first host within said mobile network addressed to a second host; (b) estimating which type of traffic is present in said data packet; and (c) forwarding said data packet by applying a first routing method for a first type of traffic and a second routing method for a second type of traffic.
Owner:KING'S COLLEGE LONDON
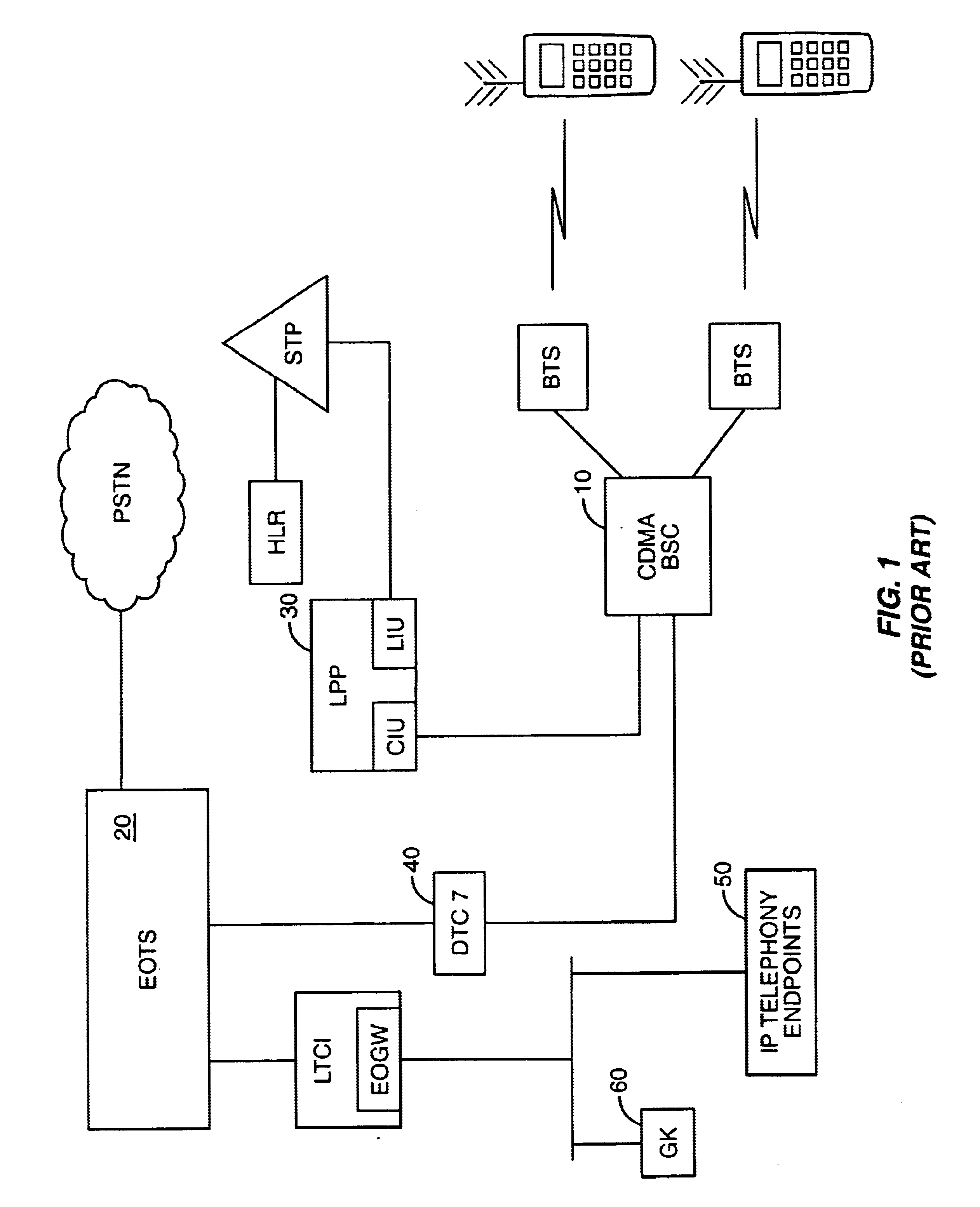
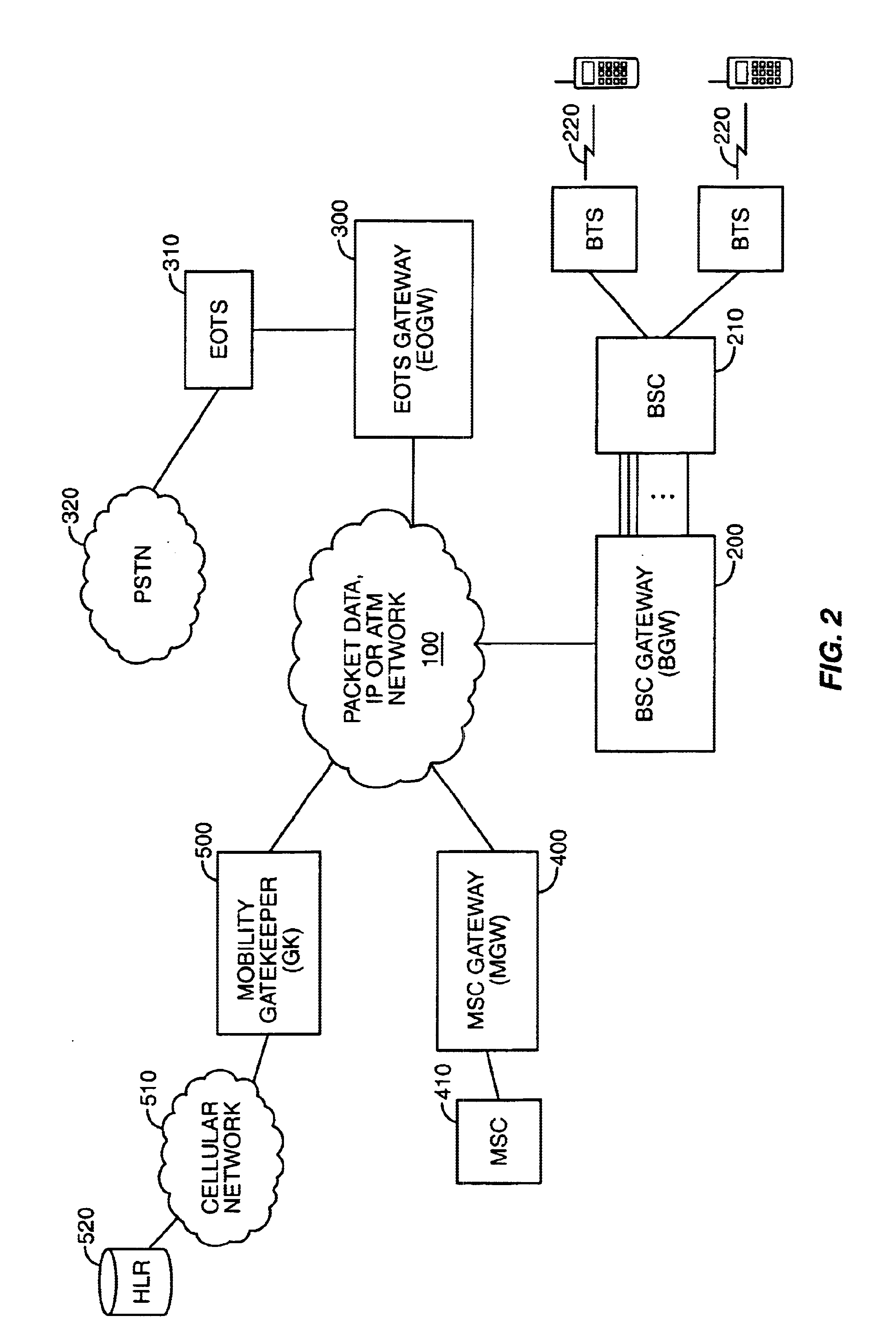
System, method, and computer program product for connectivity of wireless base station to PSTN via an IP data network
InactiveUS6888803B1Special service provision for substationMultiplex system selection arrangementsCable telephonySystem call
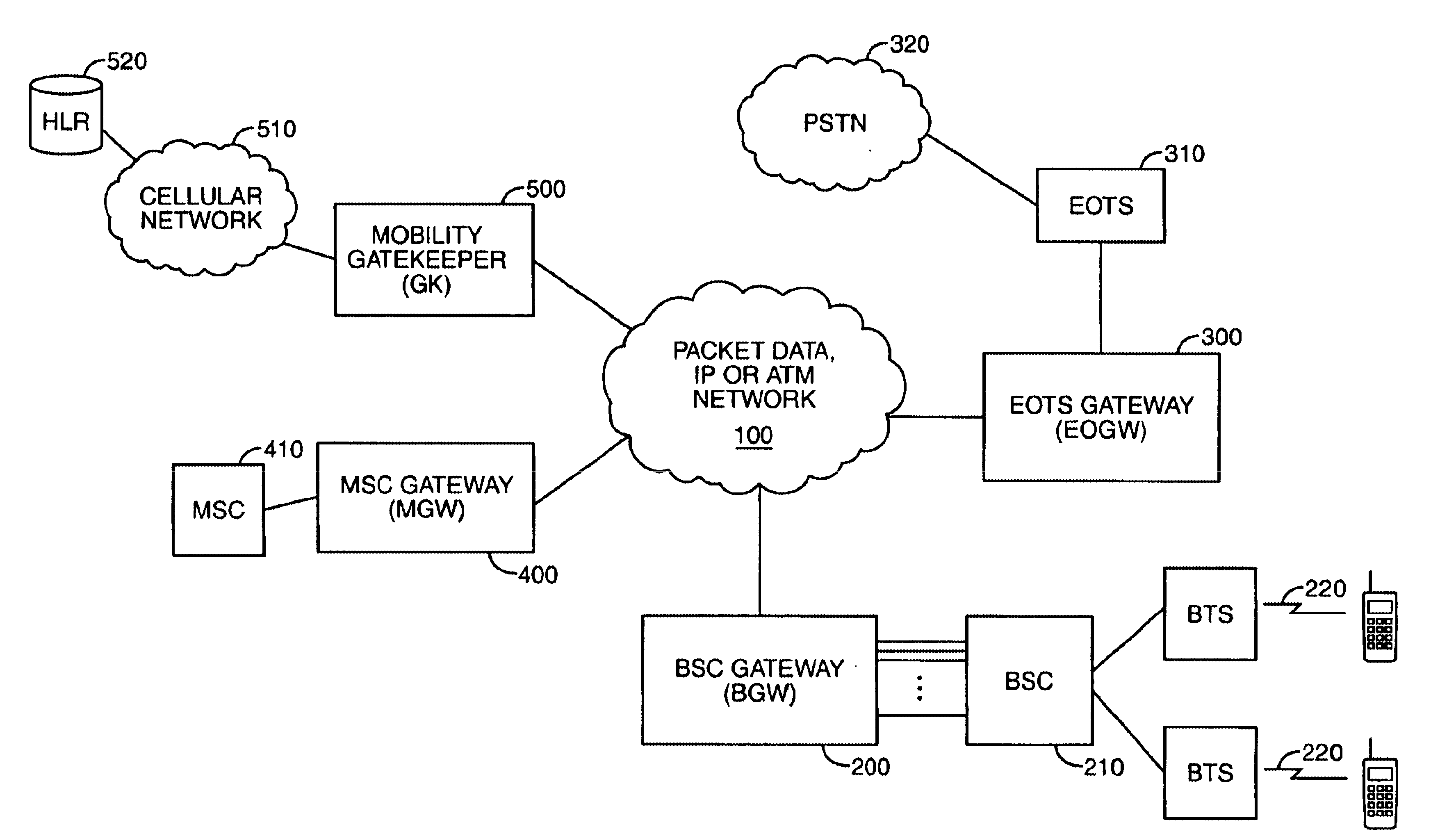
A system for providing wireline telephone services to wireless subscribers utilizing a packet data network 100. The system includes a base station controller (BSC) 210 a base station controller gateway (BGW) 200 for providing client based services to mobile subscribers and providing protocol mapping between a mobile protocol and a packet data network protocol. The system further comprises a mobility gatekeeper (GK) 500 for managing network mobility services for each wireless call including the establishment of a call control path and a speech path between said base station controller and a serving end office telephone point. The system also comprises a end office gateway (EOGW) 300 for providing protocol conversion between the packet data network protocol and the end office point data protocol such that a wireless subscriber has access to all wireline services provided by the end office point. A mobile switching center (MSC) 410 and mobile switching center gateway (MGW) 400 are included to facilitate inter-system call handoffs into an existing circuit-switched wireless telephony network.
Owner:BLACKBERRY LTD
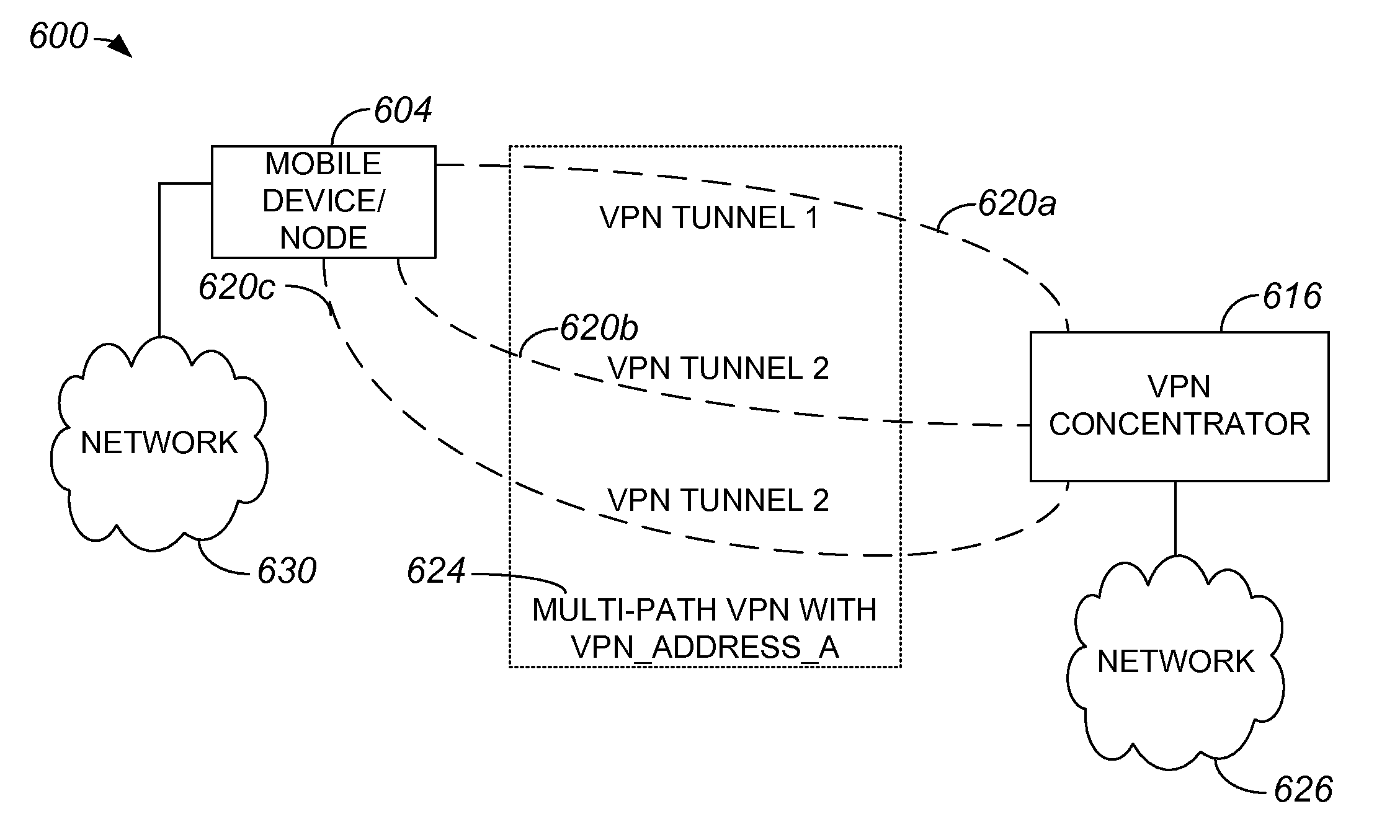
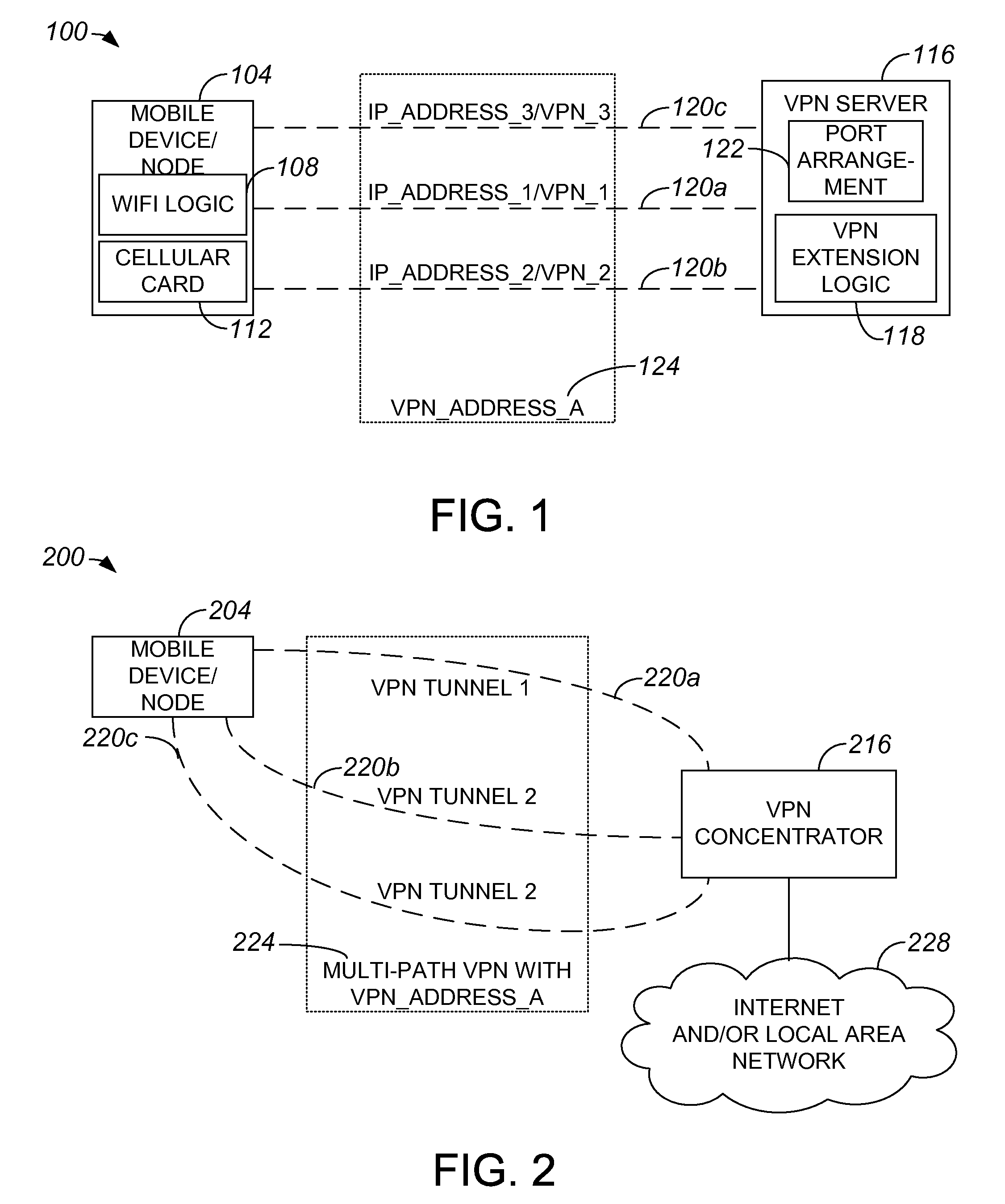
Network mobility over a multi-path virtual private network
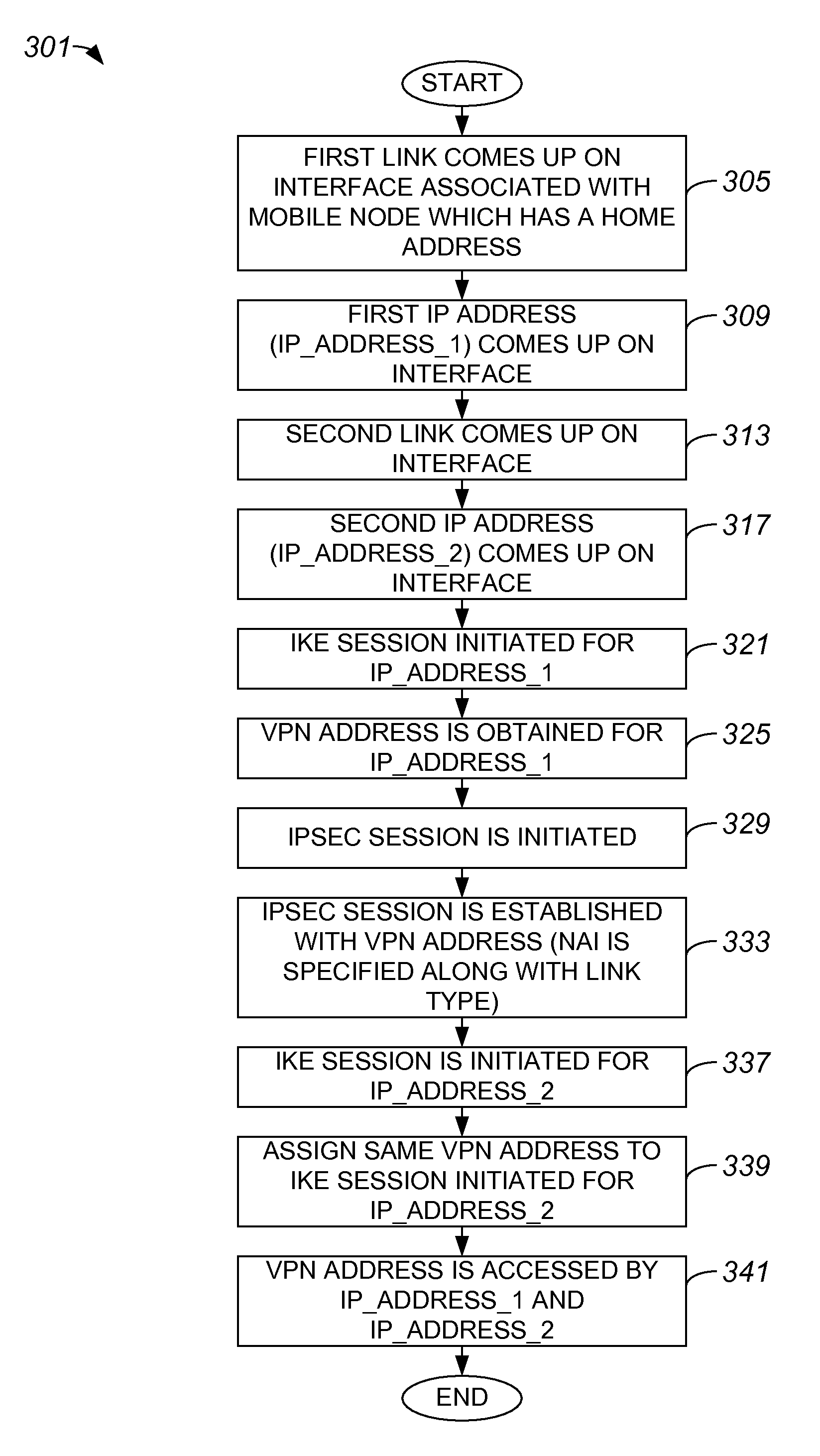
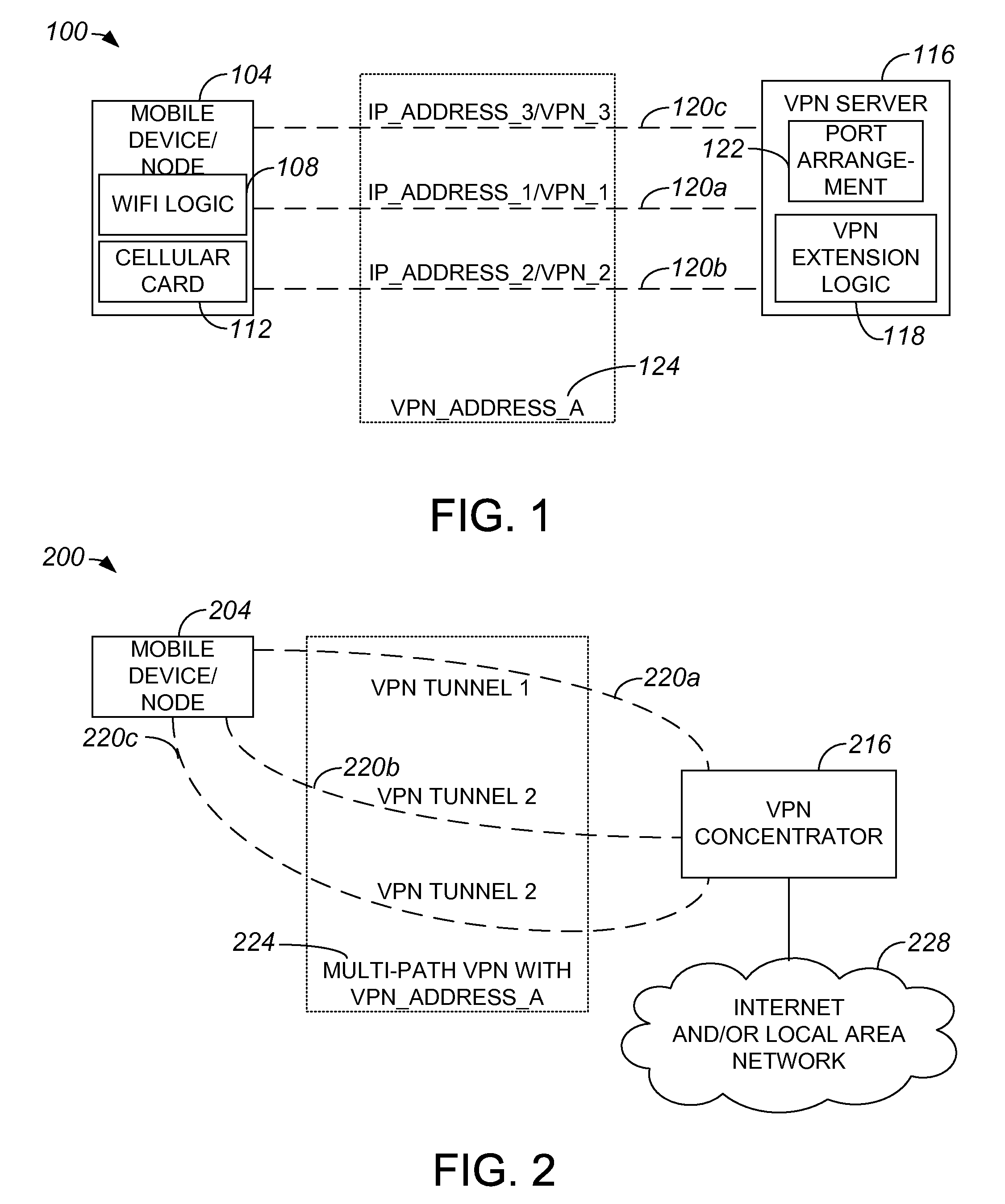
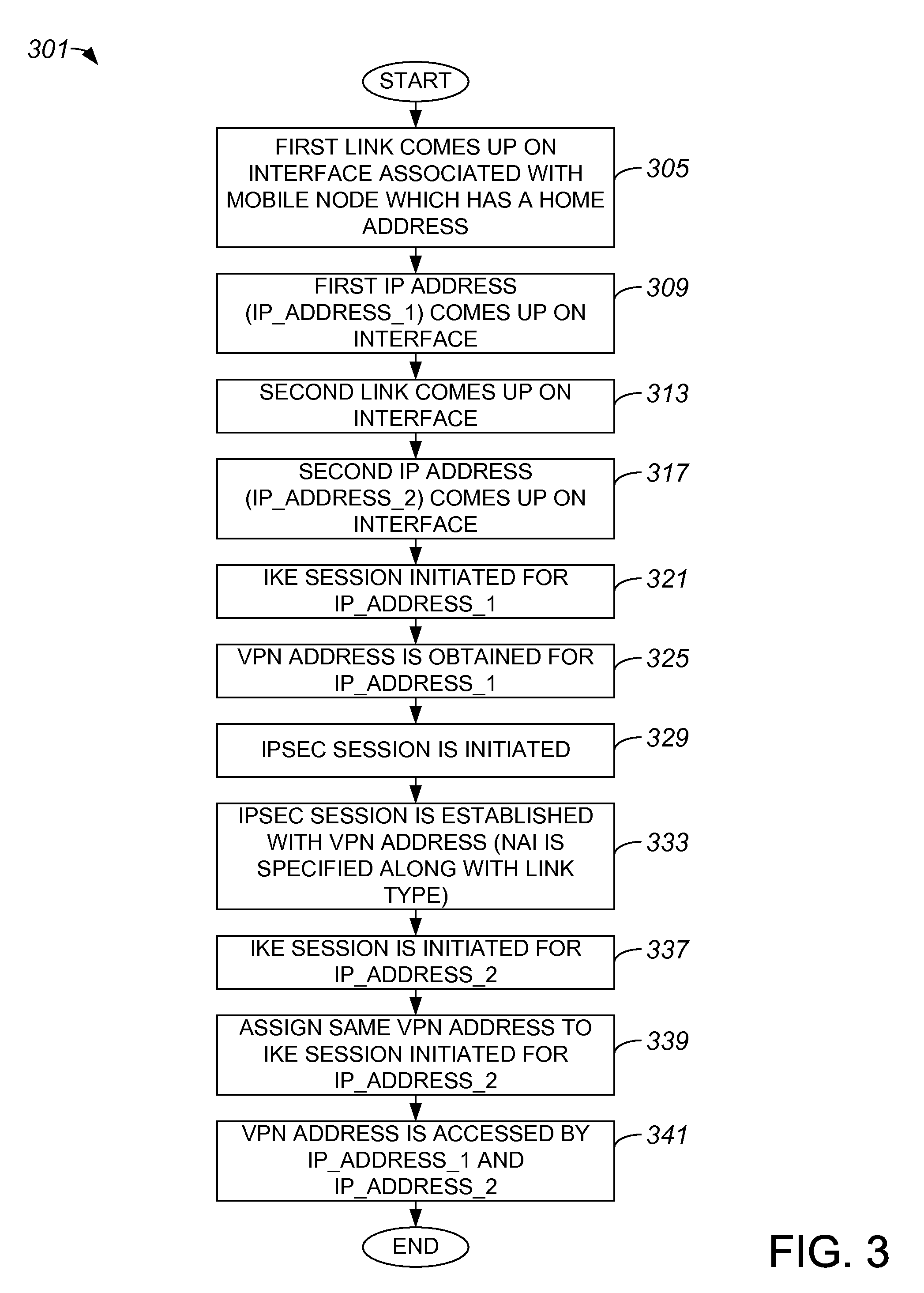
ActiveUS20090122990A1Key distribution for secure communicationDigital data processing detailsPrivate networkNetwork mobility
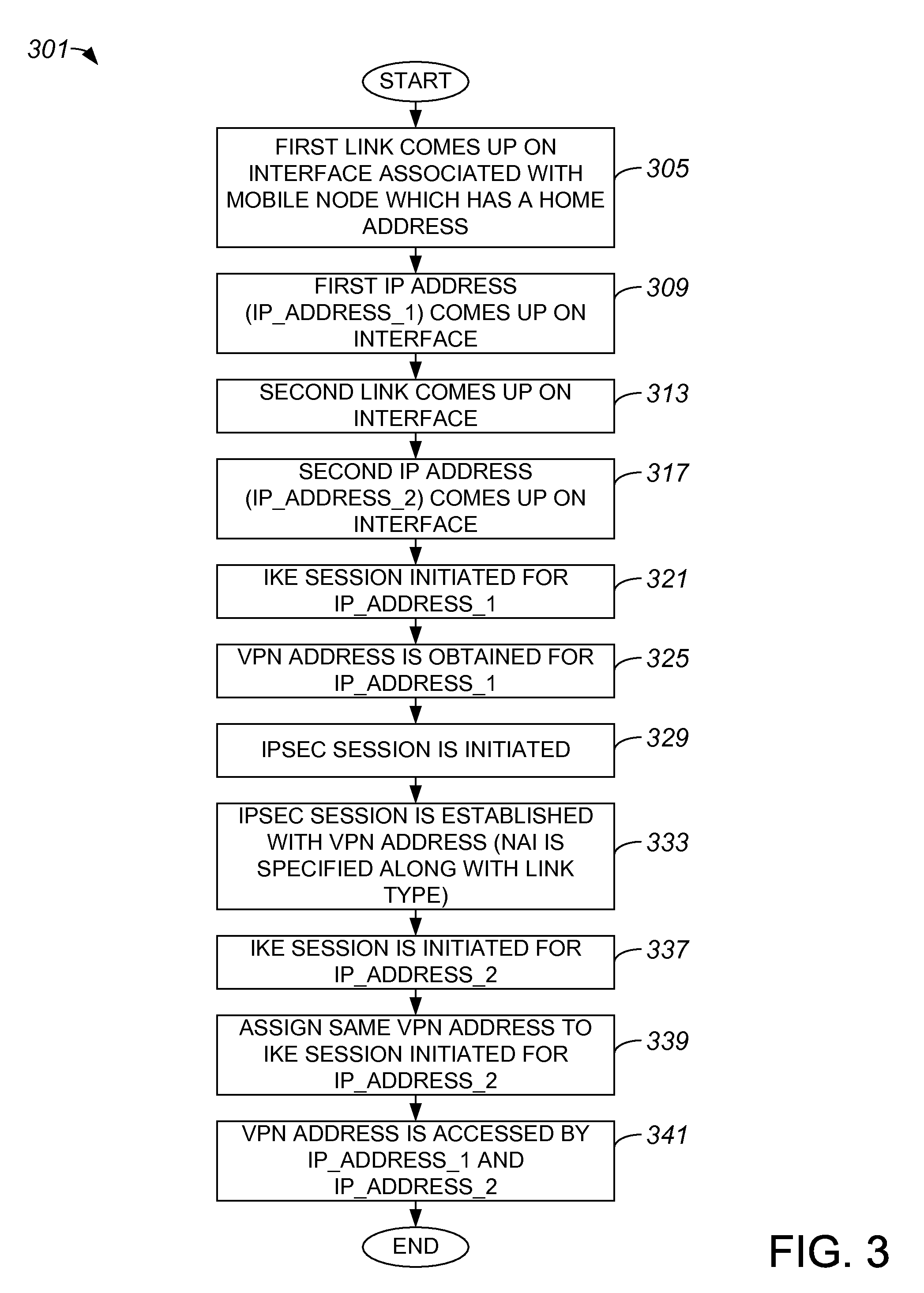
Methods and apparatus for applying a single virtual private network (VPN) address to tunnels or connections associated with different access interfaces are disclosed. In one embodiment, a method includes establishing a first tunnel between a node and a VPN server. The first tunnel has a first address. The method also includes assigning a VPN address to the first tunnel, as well as establishing a second tunnel between the node and the VPN server. The second tunnel has a second address. The VPN address is assigned to the second tunnel, and VPN address is accessed by both the first address and the second address.
Owner:CISCO TECH INC
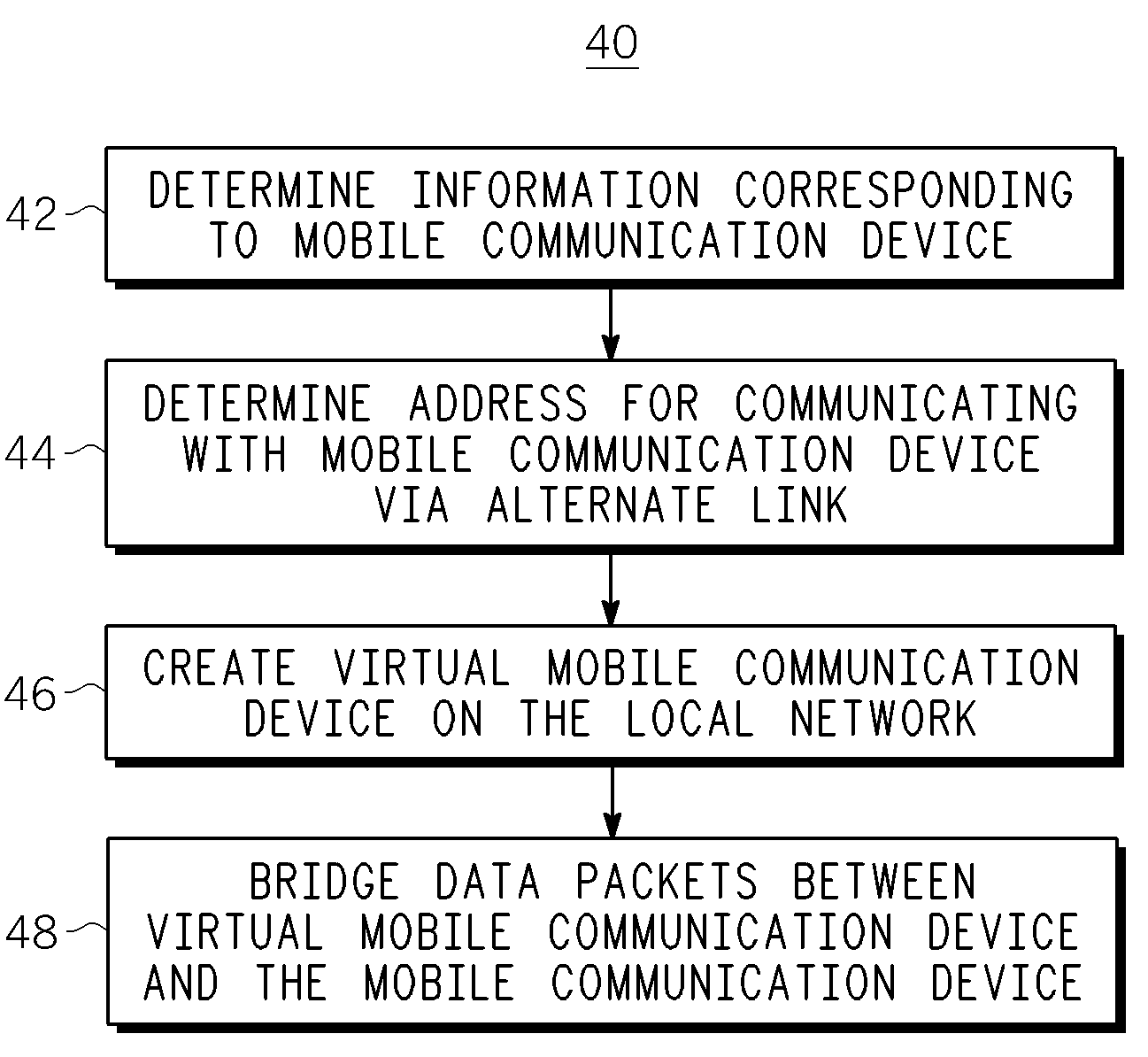
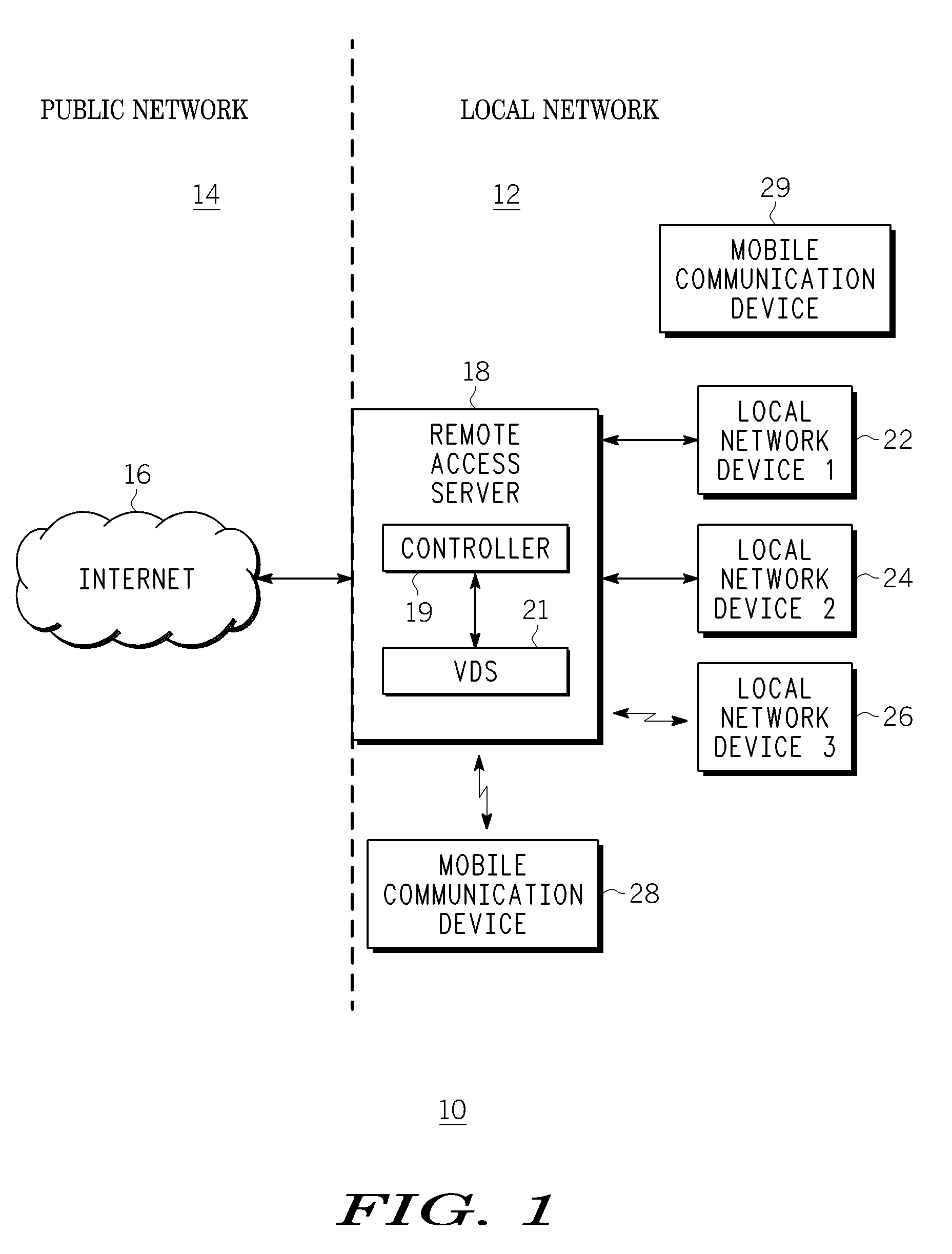
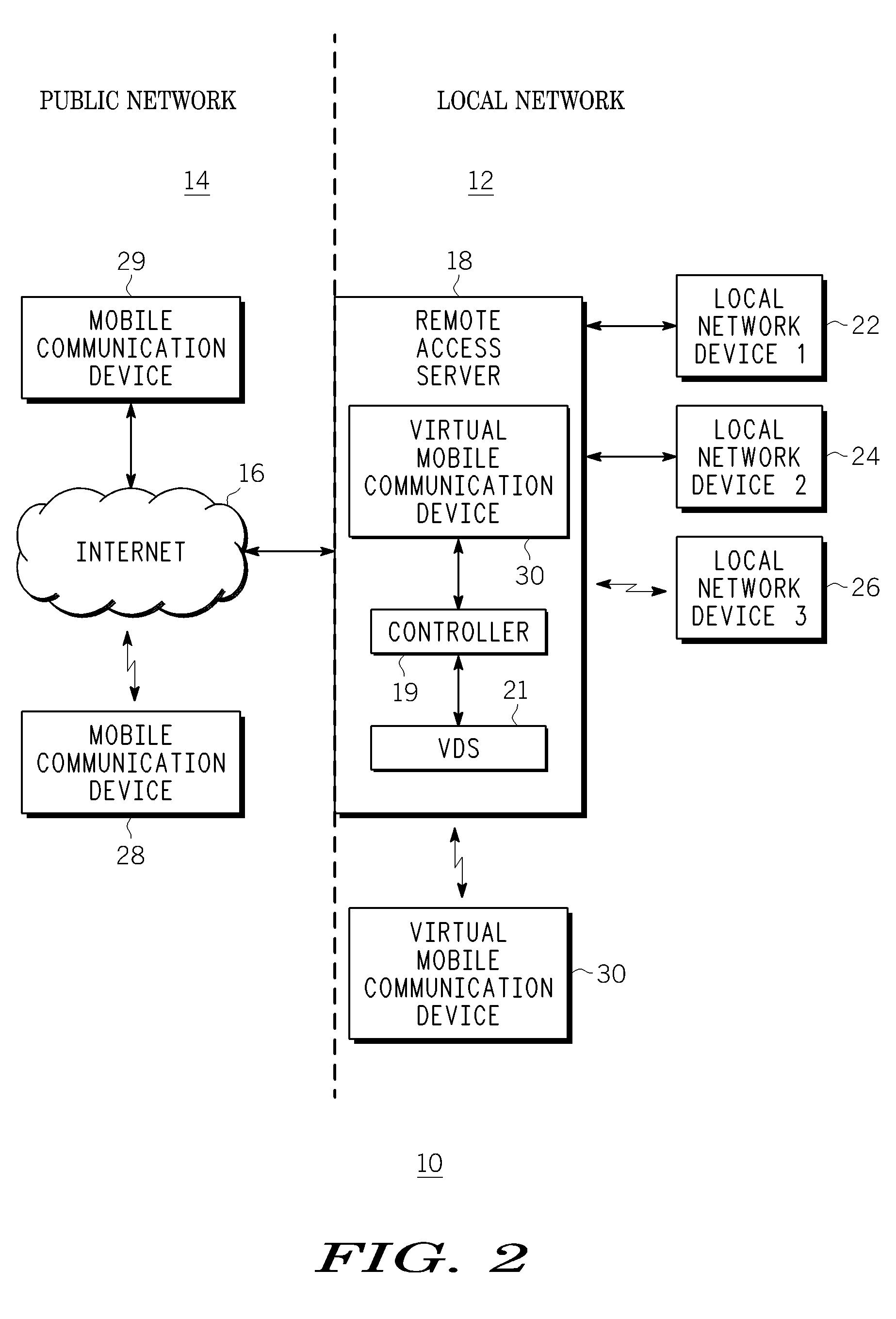
Method, apparatus and system for network mobility of a mobile communication device
ActiveUS7729366B2Time-division multiplexData switching by path configurationIp addressNetwork mobility
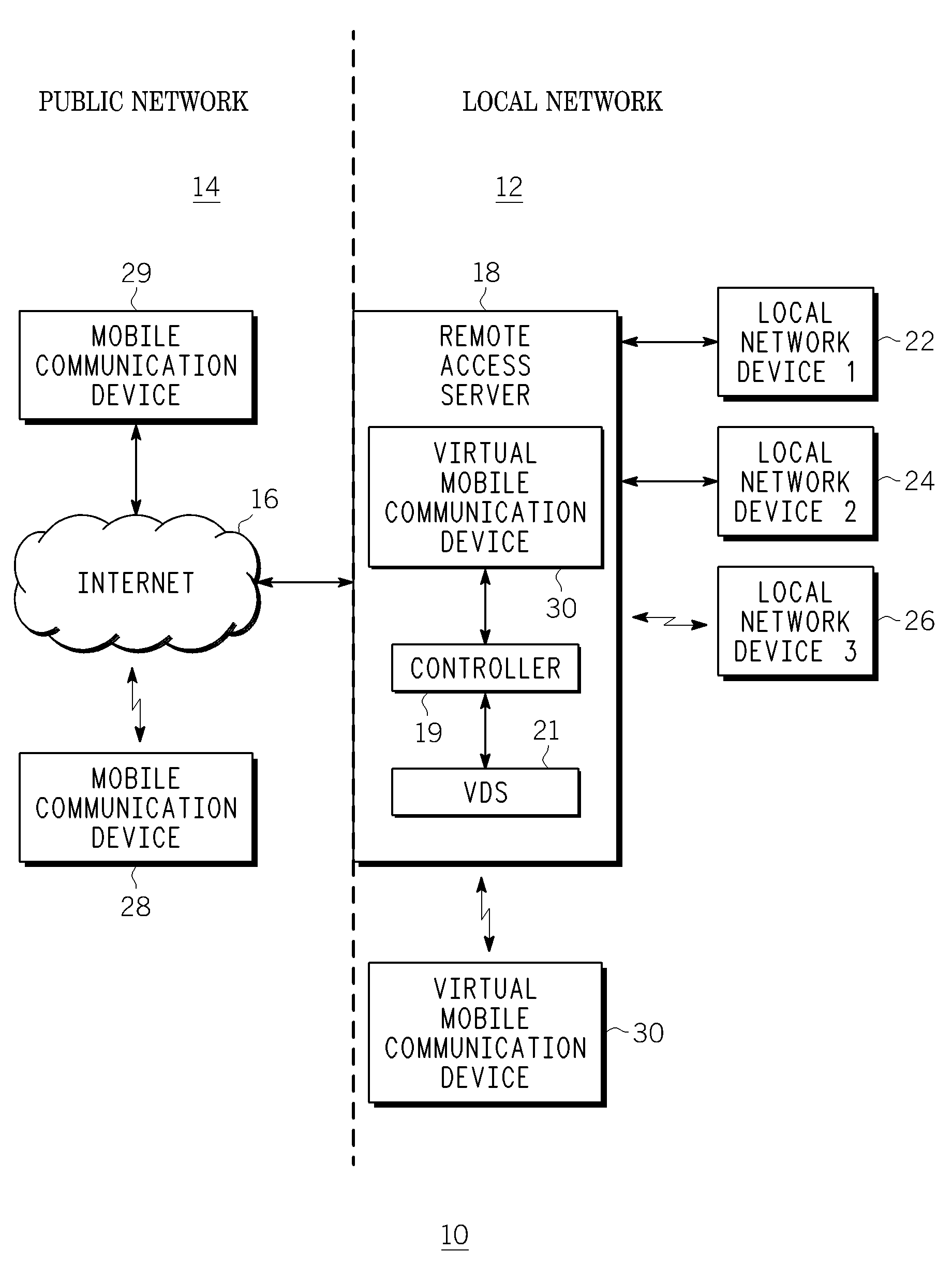
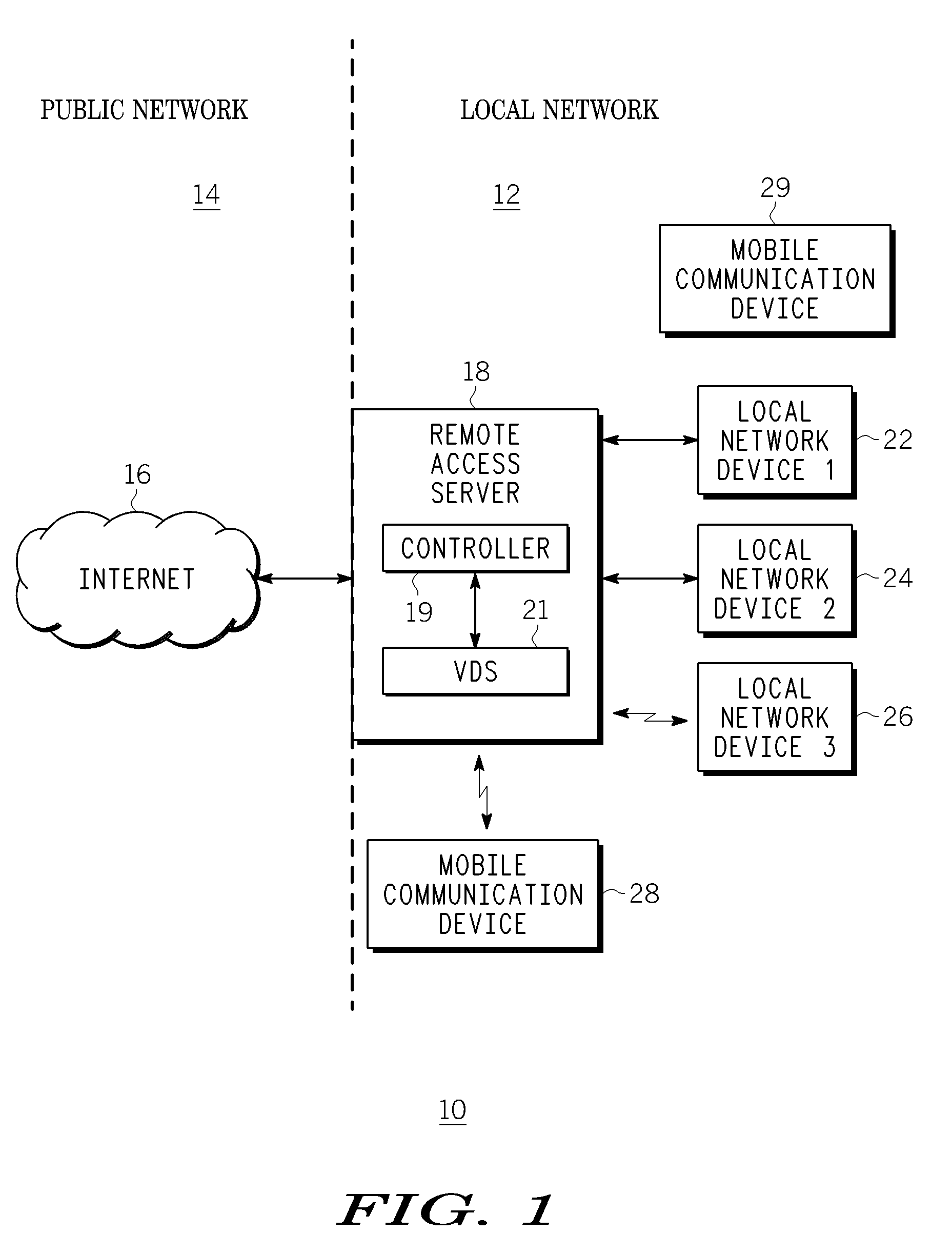
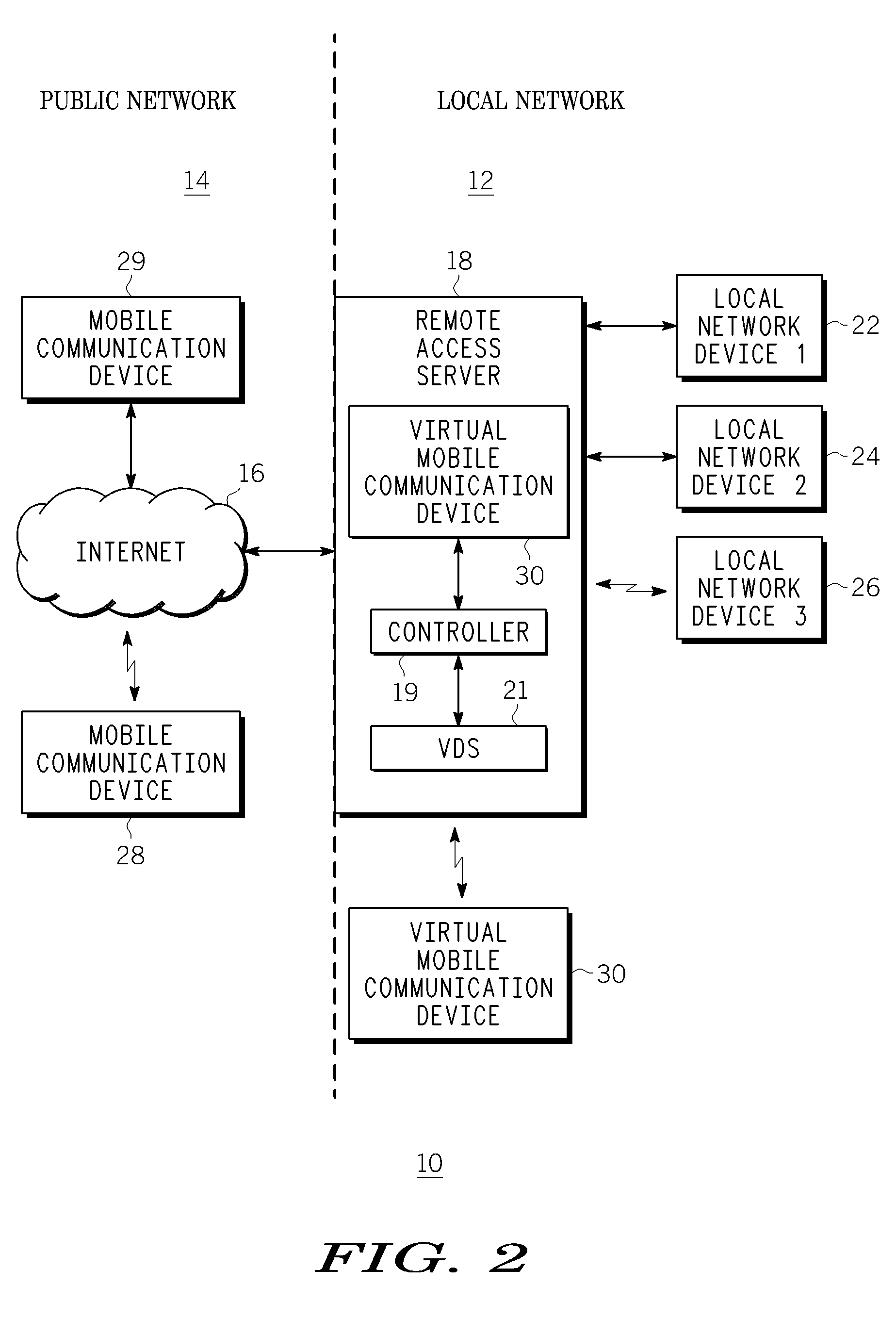
A method, device and system for allowing a mobile communication device, such as a DLNA / UPnP device, to continue to communicate with its local network, even when the mobile device leaves or loses contact with the local network. The method includes providing information to a remote access server to create a virtual mobile device in a local network. The virtual device communicates with other devices within the local network as if it is the actual mobile device. The remote access server is configured to route data packets between the virtual device and the mobile device via a second network that does not rely on the mobile nodes connection to the local network. A public IP address of the remote access server provided to the mobile device before the device leaves the local network is used to communicate with the virtual device via an IP-based public network coupled to the local network.
Owner:GOOGLE TECH HLDG LLC
Network adapted for mobile devices
ActiveUS7779069B2Ticket-issuing apparatusHand manipulated computer devicesNetwork mobilityData acquisition module
Owner:WELLS FARGO BANK NAT ASSOC
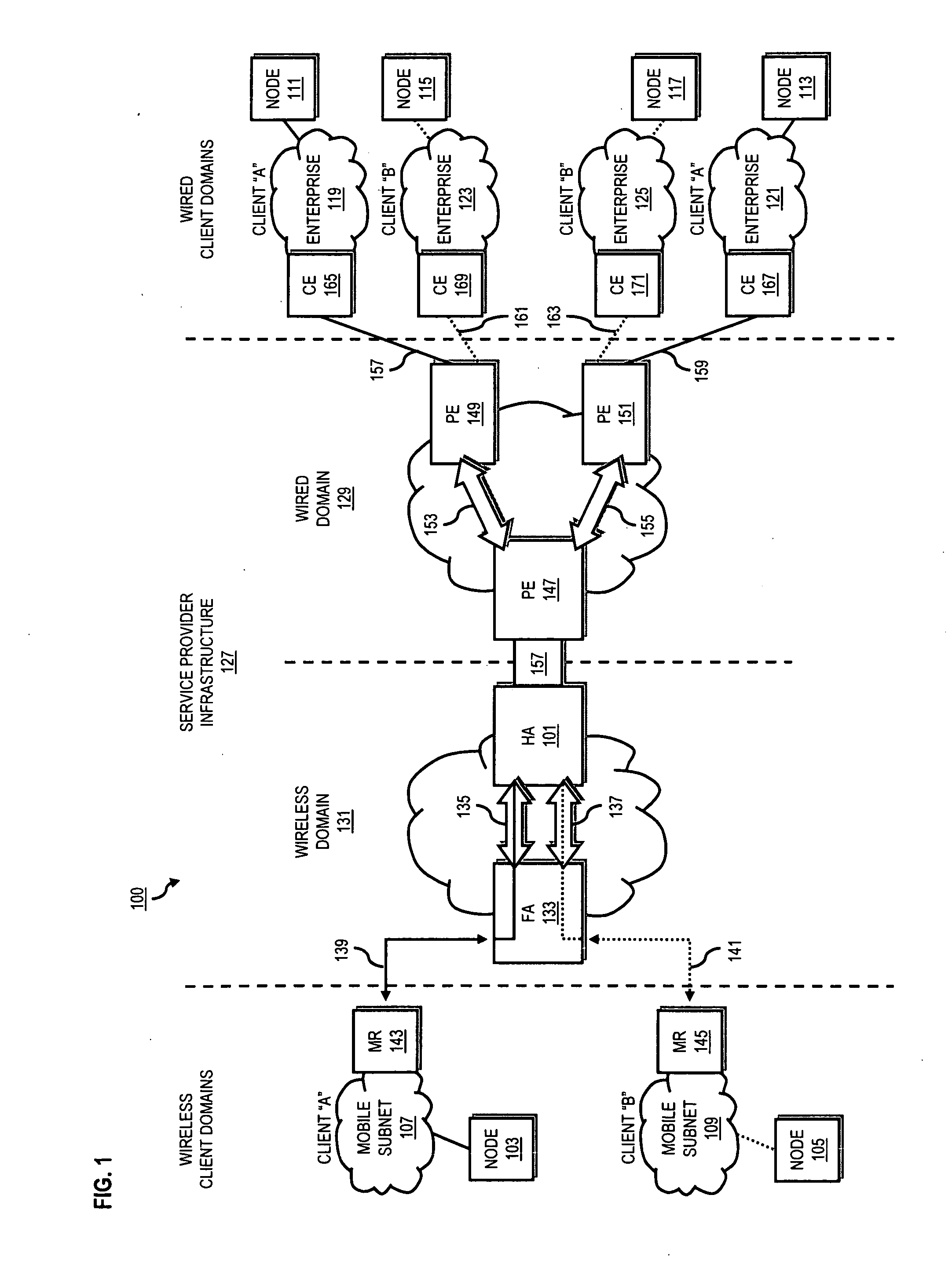
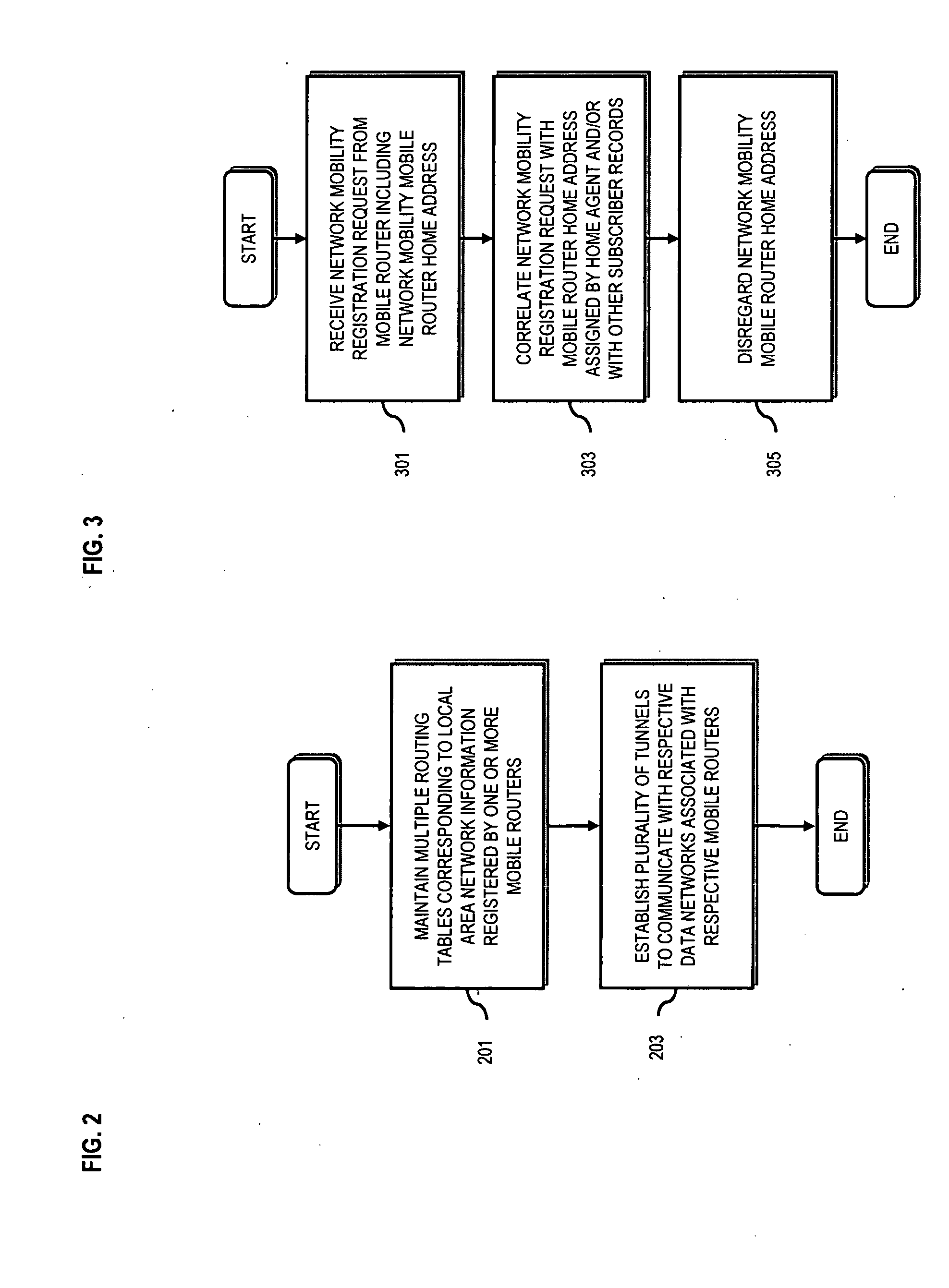
System and method for providing network mobility
An approach is provided for extending private enterprise networking to wireless interconnecting domains. A home agent maintains a first routing table for a first wireless router configured to route according to a first address space. The home agent also maintains a second routing table for a second wireless router configured to route according to a second address space. The first address space and the second address space are overlapping.
Owner:VERIZON PATENT & LICENSING INC
Method, apparatus and system for network mobility of a mobile communication device
ActiveUS20090092133A1Data switching by path configurationWireless communicationIp addressNetwork mobility
A method, device and system for allowing a mobile communication device, such as a DLNA / UPnP device, to continue to communicate with its local network, even when the mobile device leaves or loses contact with the local network. The method includes providing information to a remote access server to create a virtual mobile device in a local network. The virtual device communicates with other devices within the local network as if it is the actual mobile device. The remote access server is configured to route data packets between the virtual device and the mobile device via a second network that does not rely on the mobile nodes connection to the local network. A public IP address of the remote access server provided to the mobile device before the device leaves the local network is used to communicate with the virtual device via an IP-based public network coupled to the local network.
Owner:GOOGLE TECH HLDG LLC
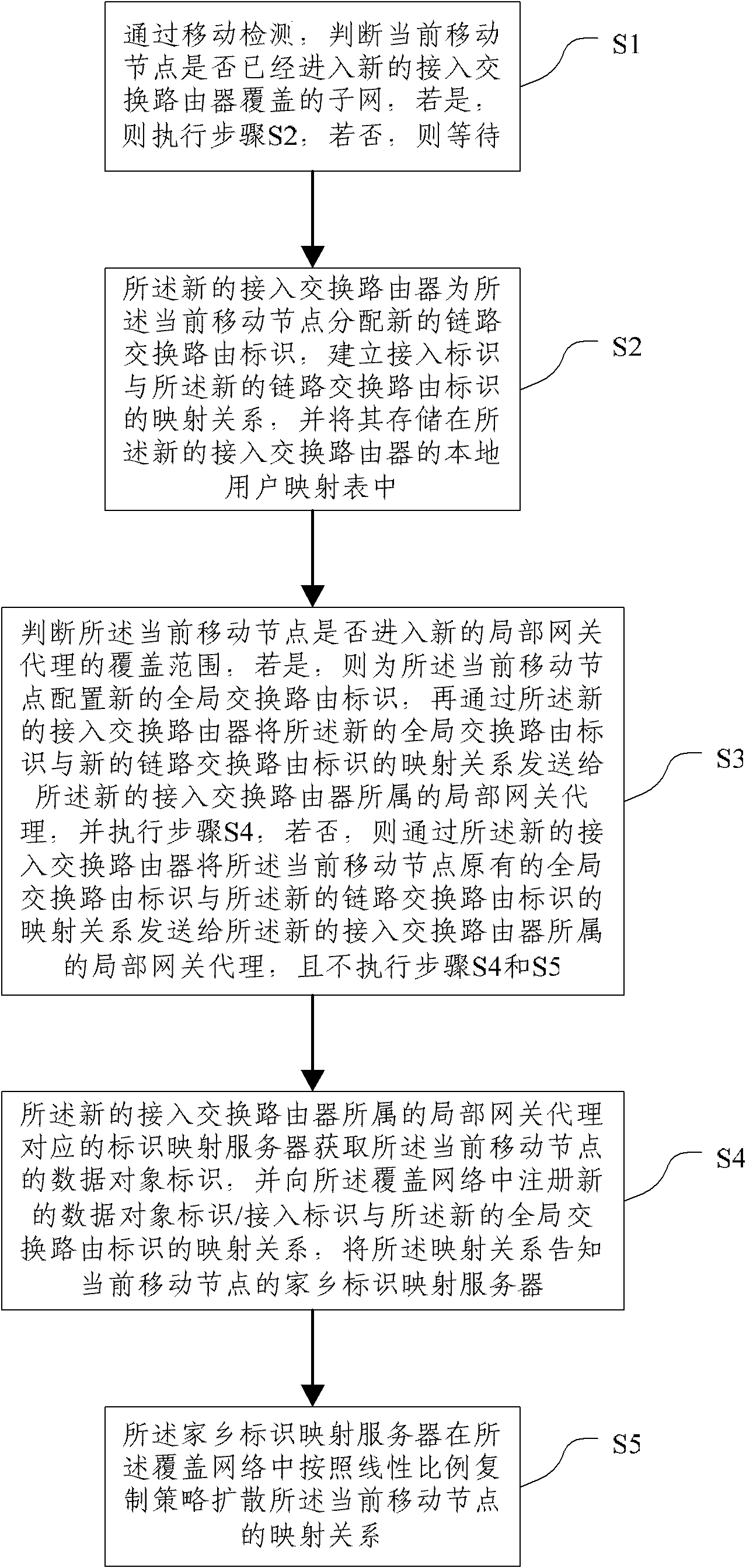
Information center network mobility management method based on content popularity
InactiveCN103581019AEnable mobilityReduce the number of nodesData switching networksTechnology researchNetwork mobility
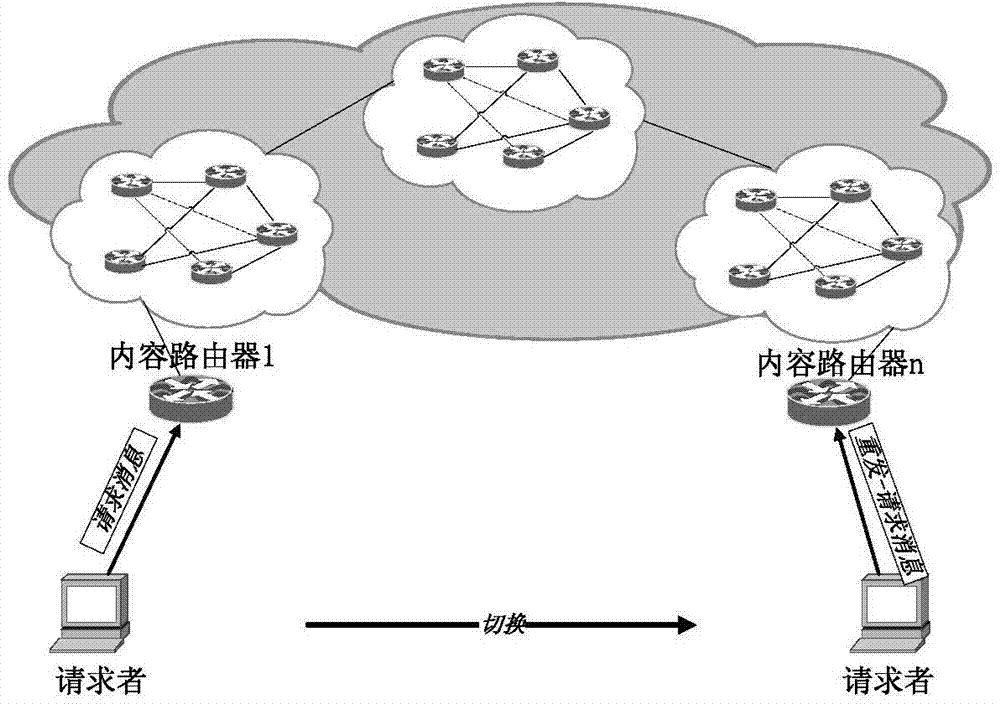
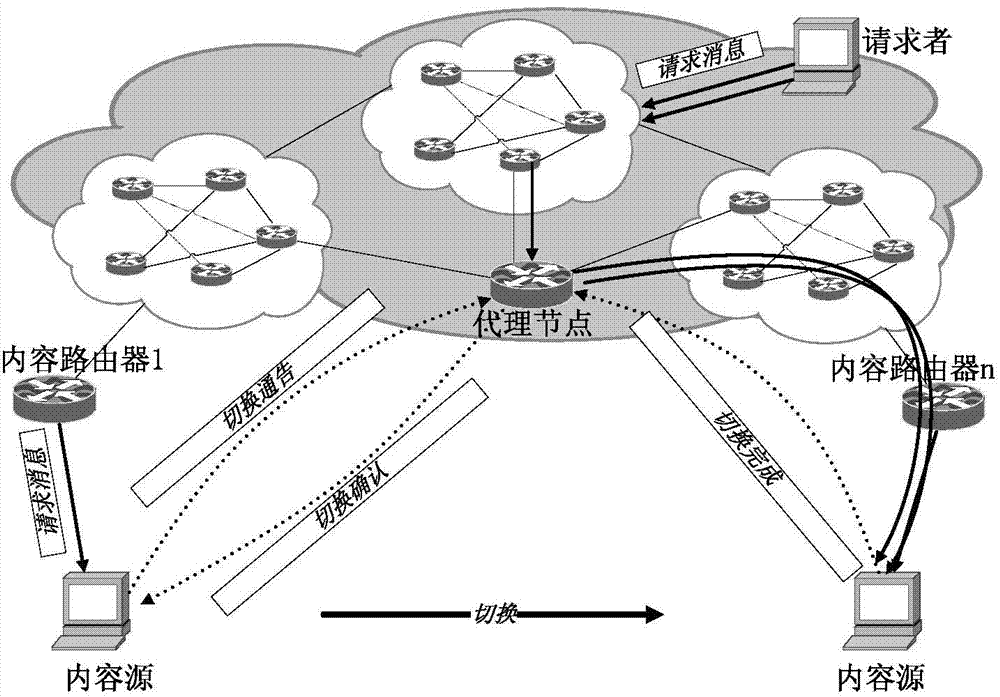
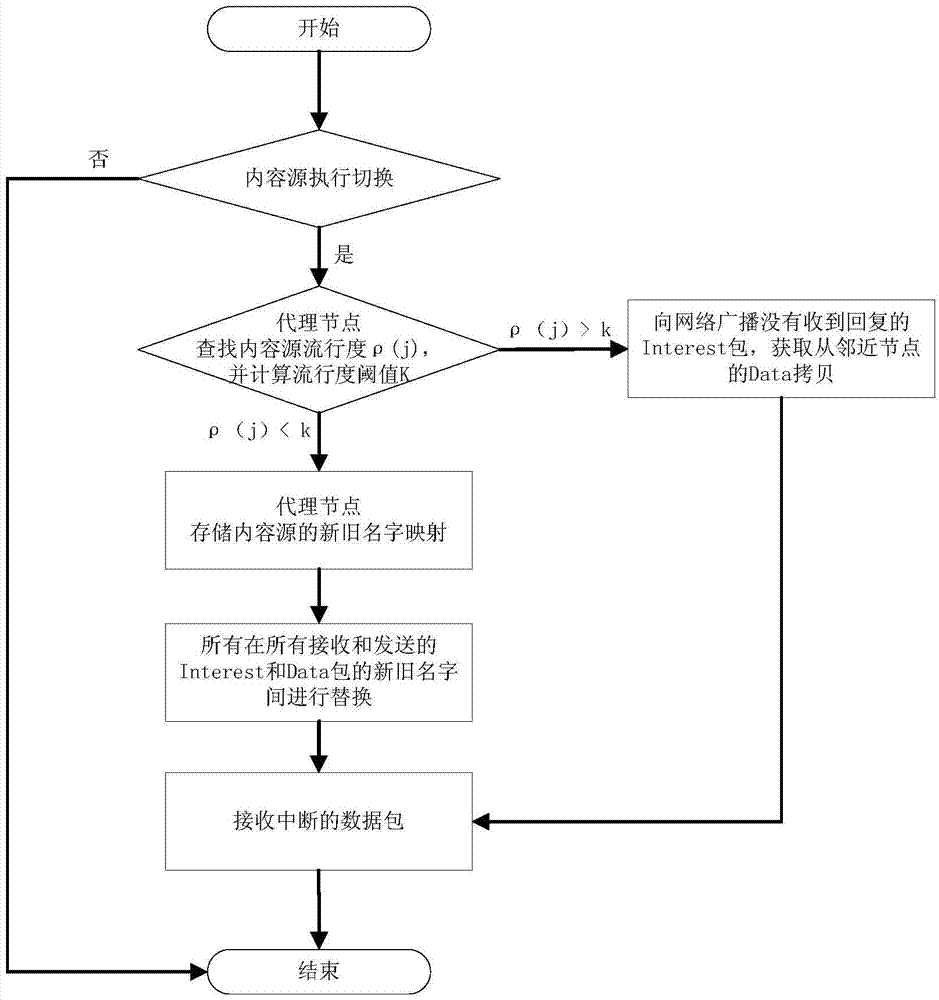
The invention discloses an information center network mobility management method based on content popularity and belongs to the technical field of next-generation internet technology research. The method includes the steps that, a requester side moves, specifically, the content requester sends an Interest package request, a router in a network receives the Interest message, the local cache is searched first, the Interest message is directly returned to the requester if the content exists in the local cache, and otherwise a PIT table is searched; a proxy node compares the popularity of the content with a popularity threshold value K; a content source moves to a new position and sends a 'handoff completion' message to the proxy node, wherein it is indicated that handoff is completed if an M marking position is '2', and a K marking position is 'NULL'. According to the method, the mobility of mobile nodes in the content center network is achieved, and the mobility management method based on the proxy node and the web cache avoids communication outage caused by single-fault nodes and link failure; once the proxy node fails and can not serve any more, the network can automatically carry out handoff in a web cache mode, and therefore it is guaranteed that communications are conducted normally.
Owner:BEIJING JIAOTONG UNIV
System and method for supporting network mobility based on identifier-locator separation
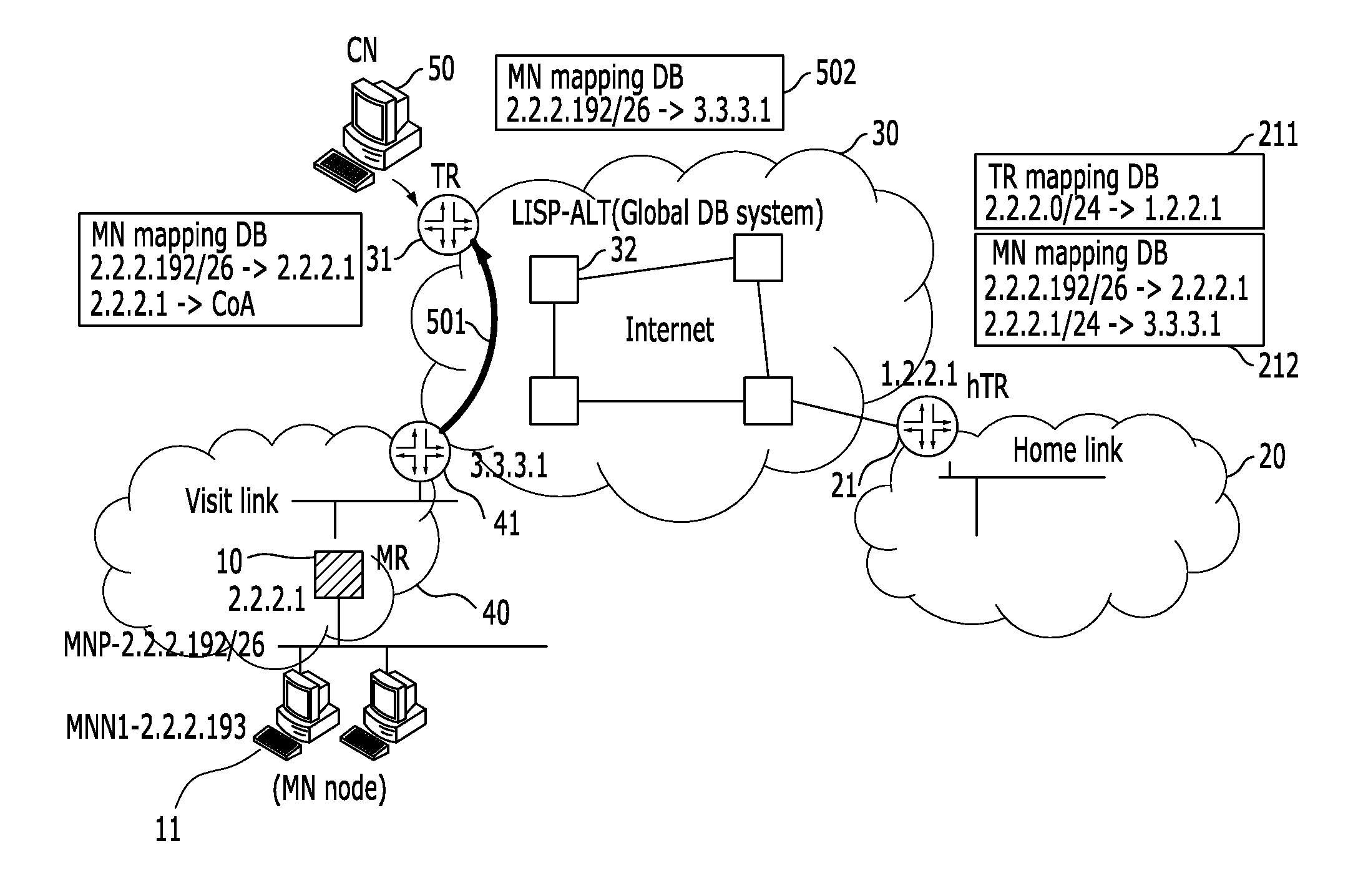
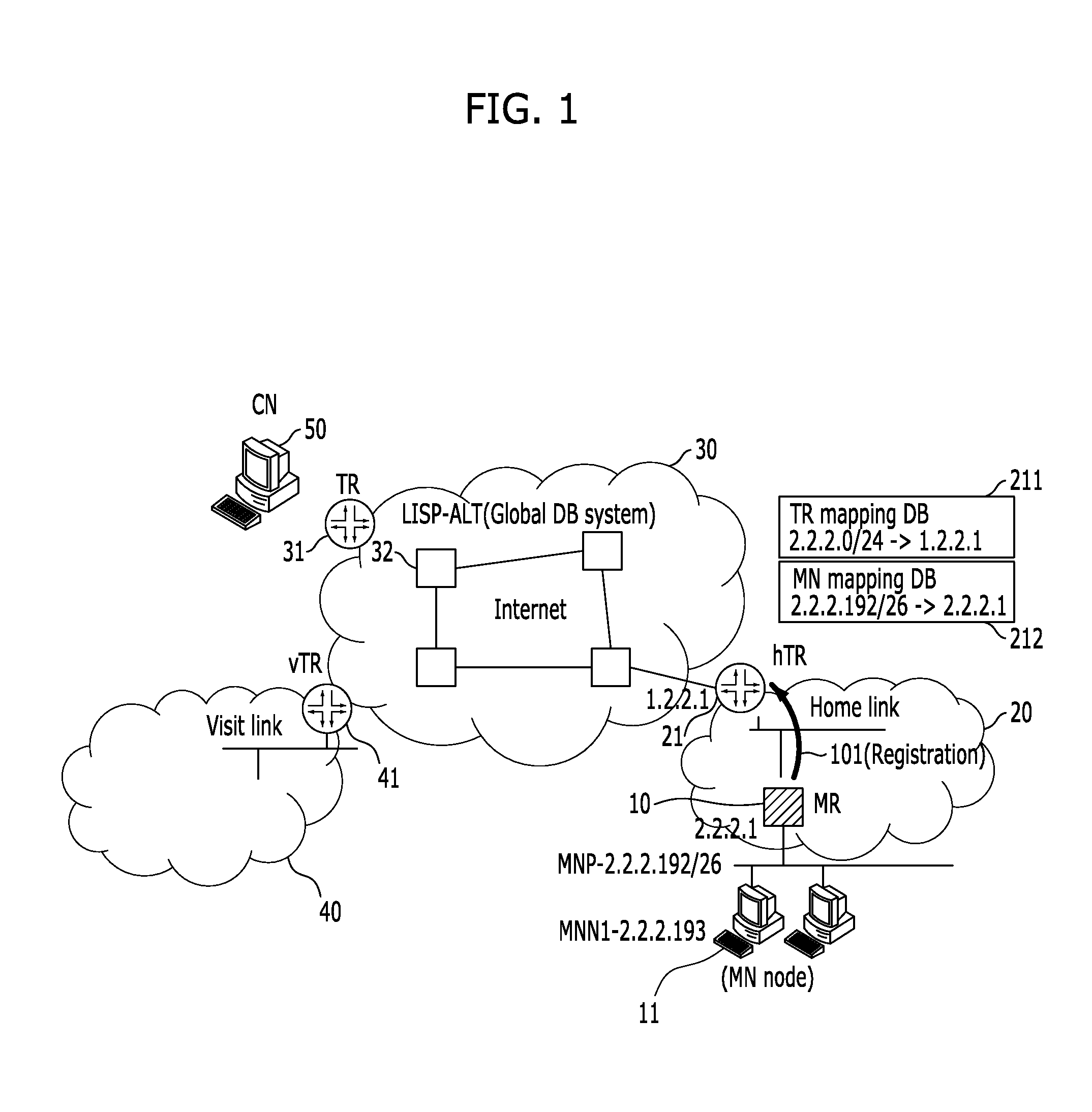
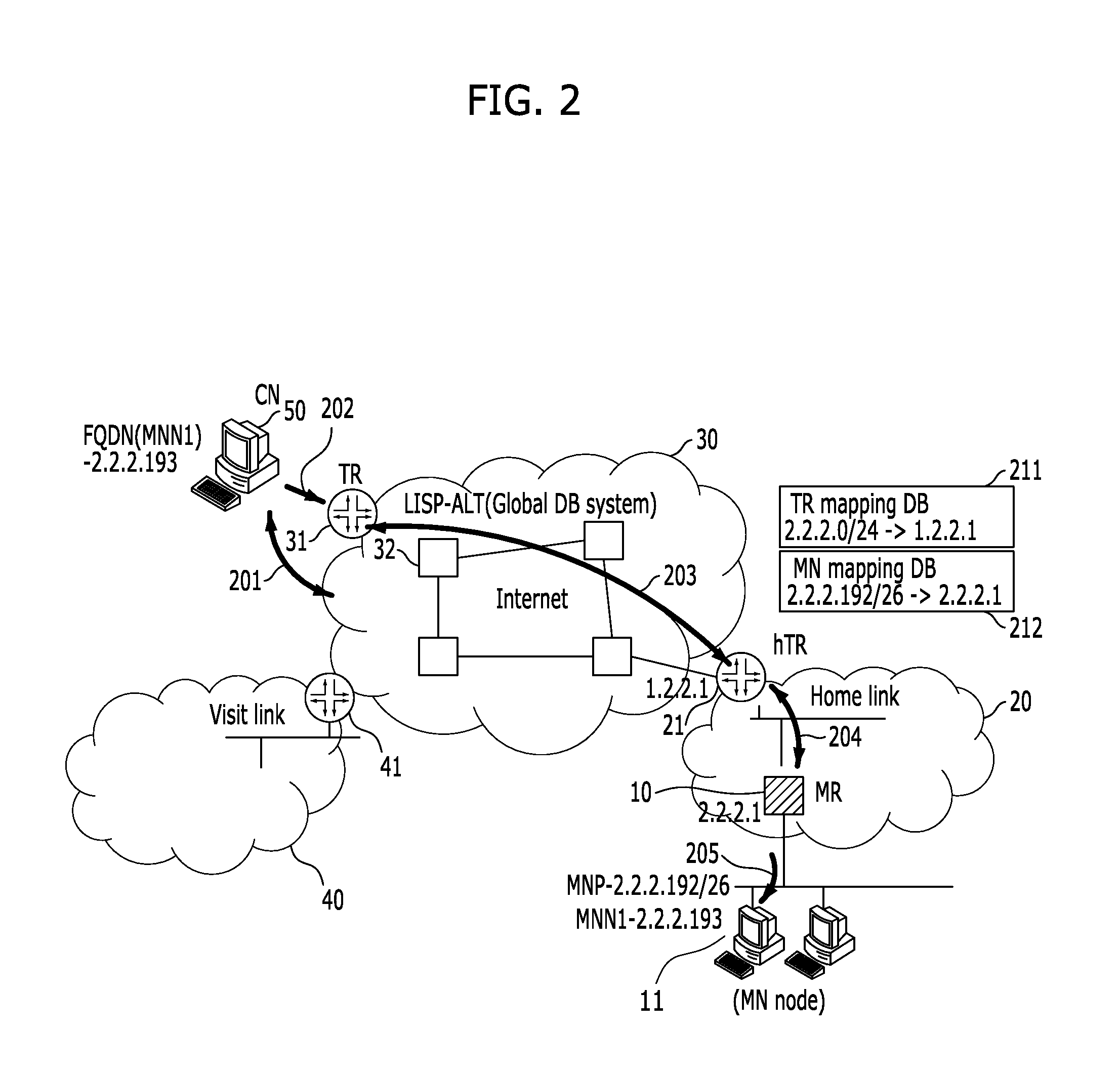
InactiveUS20110261800A1Problem still existExcellent stateNetwork topologiesConnection managementInformation supportNetwork mobility
A system and method for supporting network mobility based on identifier-locator separation, provides seamless session services to terminals inside the mobile network by enabling a variety of tunnel routers (home tunnel router, visit tunnel router, etc.) on network to store / manage mobile network mapping information for network mobility. The system for supporting network mobility based on identifier-locator separation includes: a mobile router configured to register mobile network identification information in a home tunnel router, and support communication with the home tunnel router, on behalf of mobile network nodes located in a home network; and a home tunnel router configured to support communication with a correspondent node by using tunnel router mapping information, and support communication with the mobile router by using mobile network mapping information.
Owner:KT CORP
Systems and Methods for Improving Network Mobility
InactiveUS20080181188A1Reduce needExtended routeRadio/inductive link selection arrangementsWireless commuication servicesComputer networkNetwork mobility
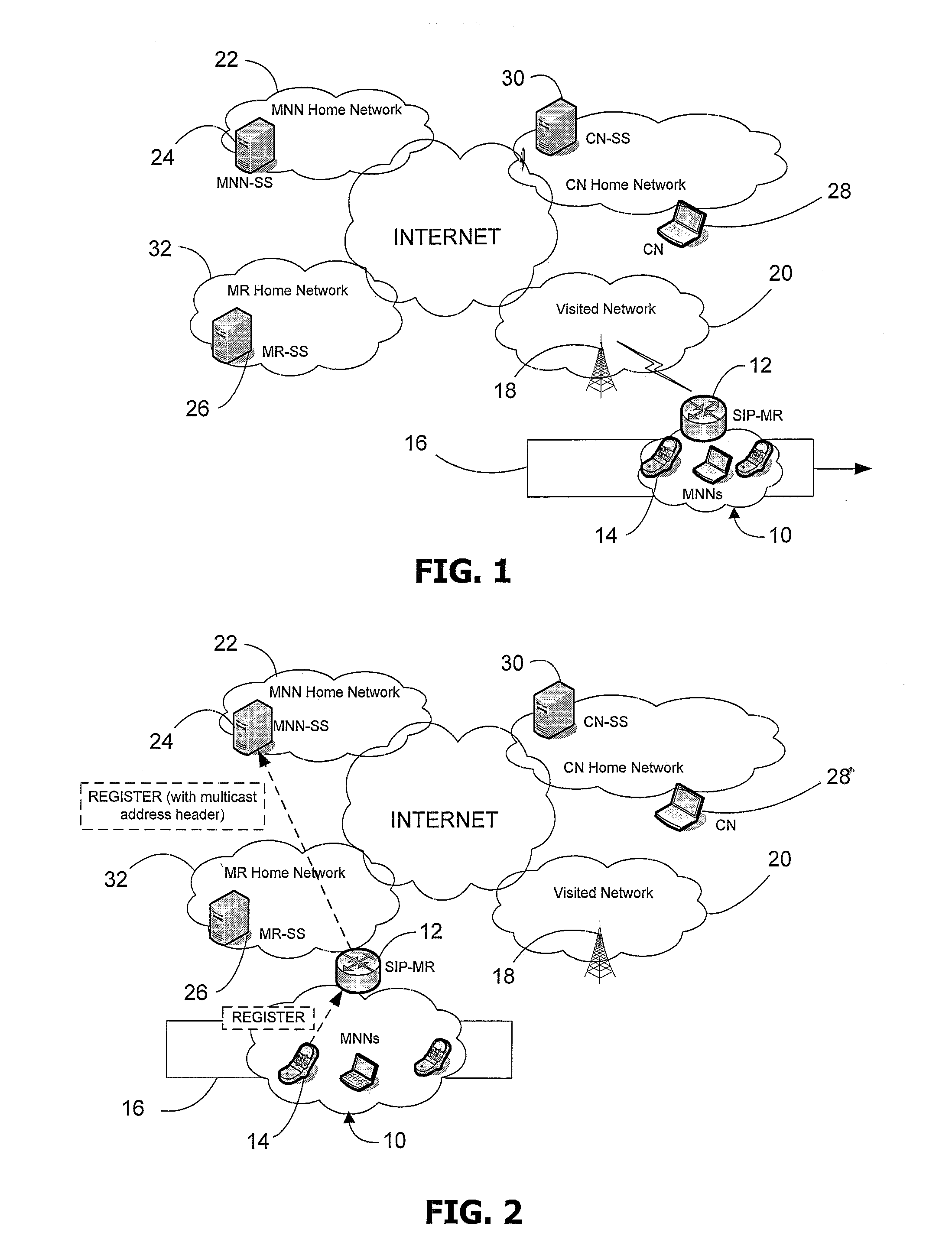
A method of providing mobility between network subnets for a plurality of mobile network nodes attached to a mobile router, which mobile router hides any change in network subnet from said plurality of mobile network nodes and which network subnets provide access for said mobile router to a fixed network infrastructure, which method comprises the steps of (a) providing a signaling channel for each of said plurality of mobile network nodes; and (b) providing a data channel for each of said plurality of mobile network nodes; characterized in that said signalling channel utilises a multicast communication protocol to perform a mobility function on behalf of one or more of said plurality of mobile network nodes.
Owner:KING'S COLLEGE LONDON
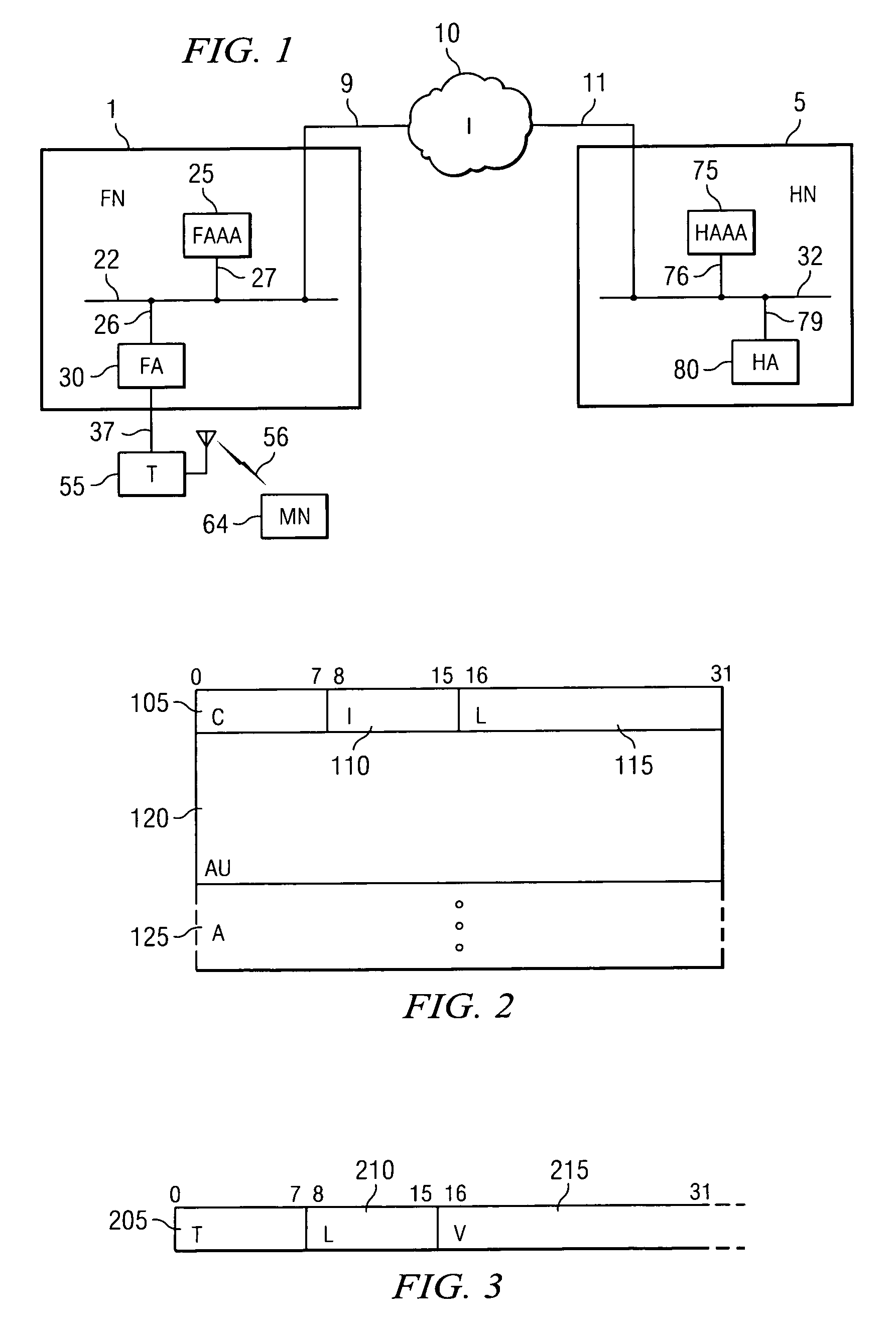
System and method for secure network mobility
ActiveUS7213263B2Improve mobilityMultiple digital computer combinationsWireless network protocolsSecure communicationSecurity association
A system and method are provided for use in maintaining secure communications between a home network and a mobile client when the client roams outside of the home network to a new location. One method of the present invention includes the steps of: establishing a new IP address for the new client location; sending a registration message identifying the new IP address location; authenticating the registration message; encapsulating and transmitting the registration message to the home server; registering the new IP address as a care-of-address for the client at the home server; confirming the registration of the new IP address with the client; establishing a security association between the home server and the relay server on behalf of the client; performing network address translation between the client's permanent IP address client and the client's new IP address; tunneling packets addressed for the client between the home server based and the relay server based on the established security association and the address translation for the client; and decapsulating the packets at the relay server and forwarding the packets to the client.
Owner:MCDONNELL & ASSOC LP +3
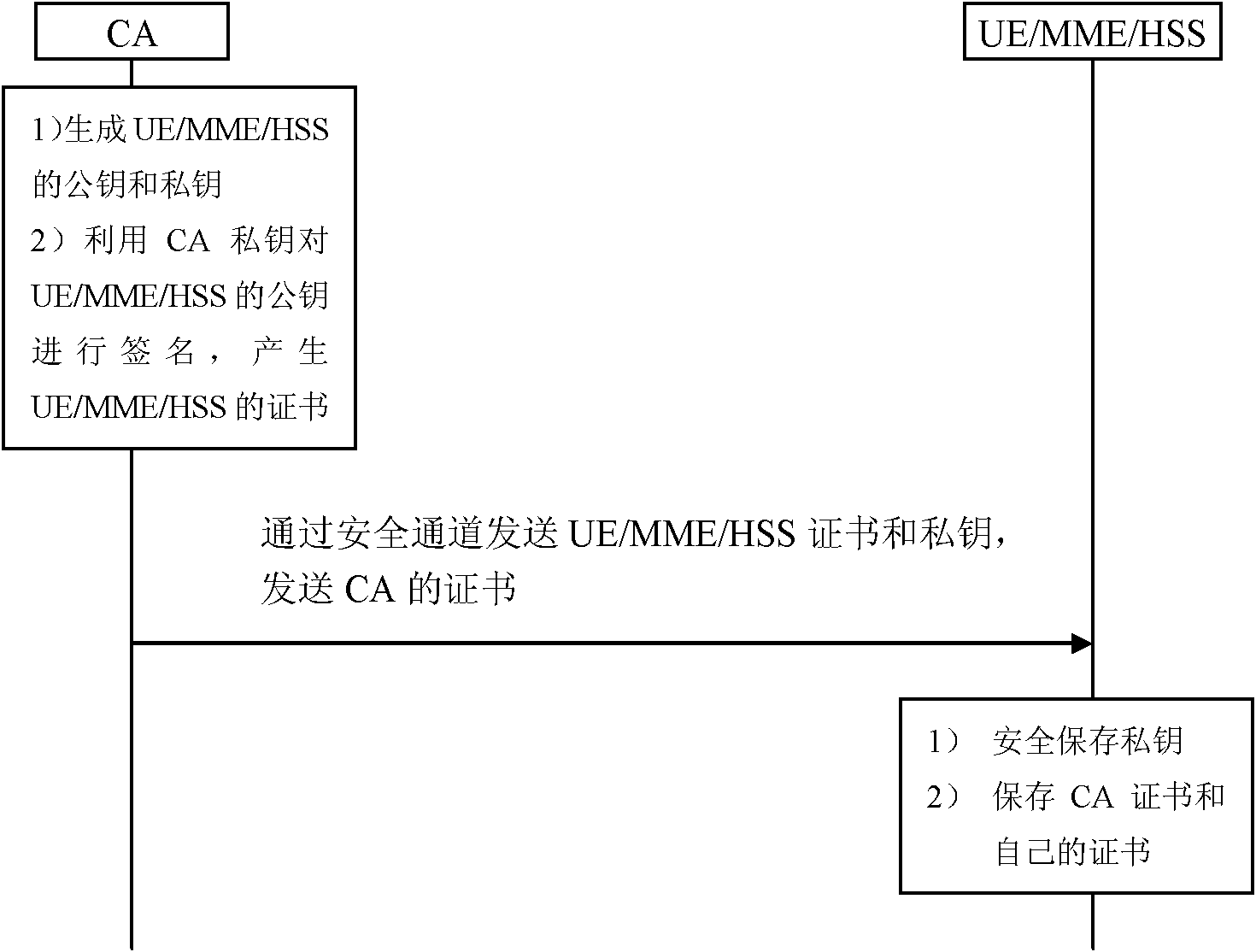
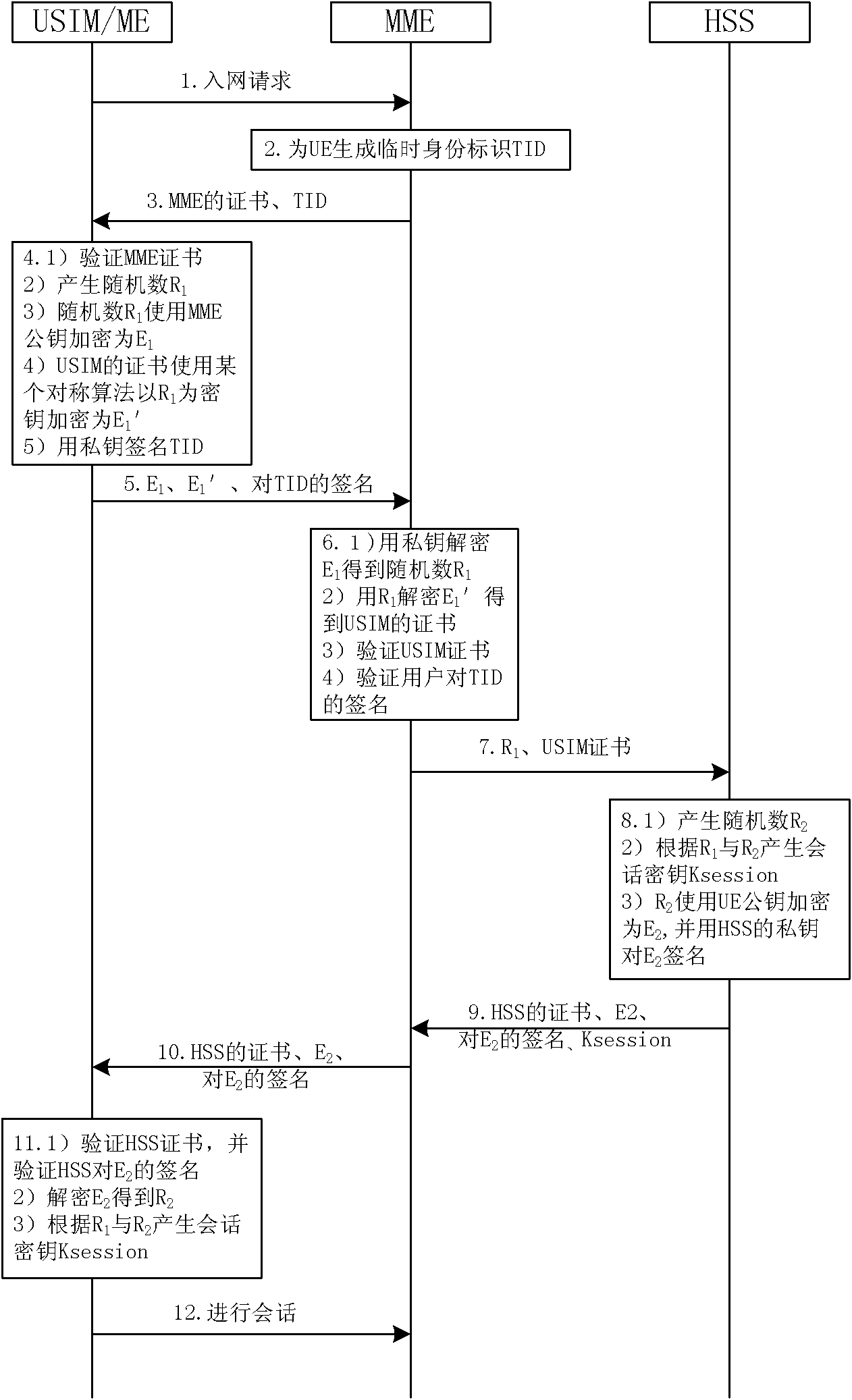
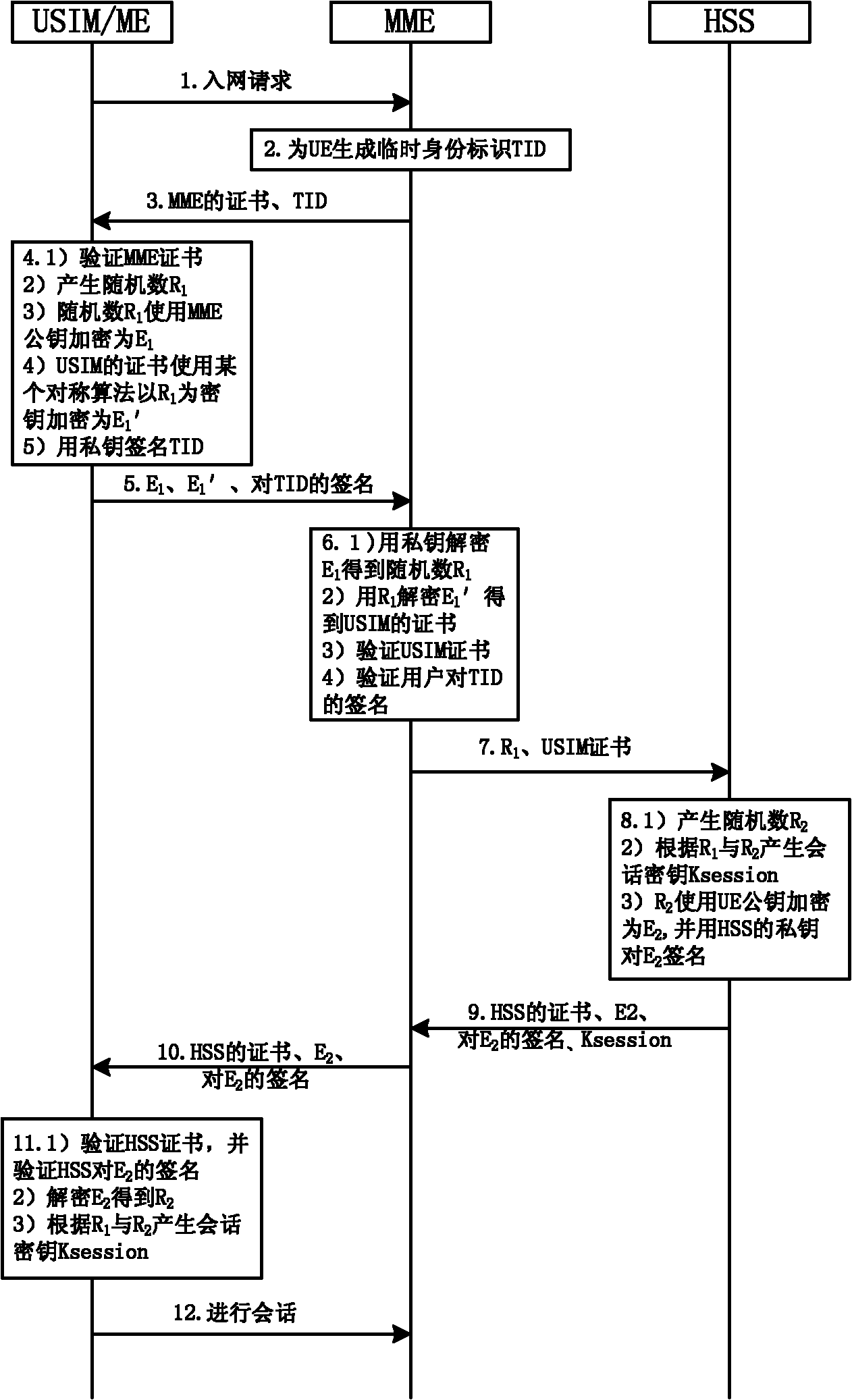
Method for realizing user and network authentication and key distribution based on public key
InactiveCN102036238AMeet software and hardware requirementsEasy to carry outSecurity arrangementWeb authenticationNetwork mobility
The invention provides a method for realizing user and network authentication and key distribution based on a public key. The method comprises the following steps that: 1) a set of public key infrastructure (PKI) is installed in a communication network, and a certificate authentication centre issues a public key certificate to a communication entity in the network; 2) user equipment and a network mobility management entity perform mutual authentication by checking the public key certificates; 3) the user equipment and a network affiliation user server respectively generate a random number and a session key, wherein the session keys are deduced by the user equipment and the network affiliation user server according to the two random number; and the session keys deduced by the network affiliation user server is transmitted to the network mobility management entity; and 4) the user equipment and the network mobility management entity protect communication data through the session keys. The method can further solve the problem that the existing system easily leaks user identifies, that the authentication vector is easily captured, that the key K is shared for a long time and that a data sign is not supported, and enhance the safety of communication.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
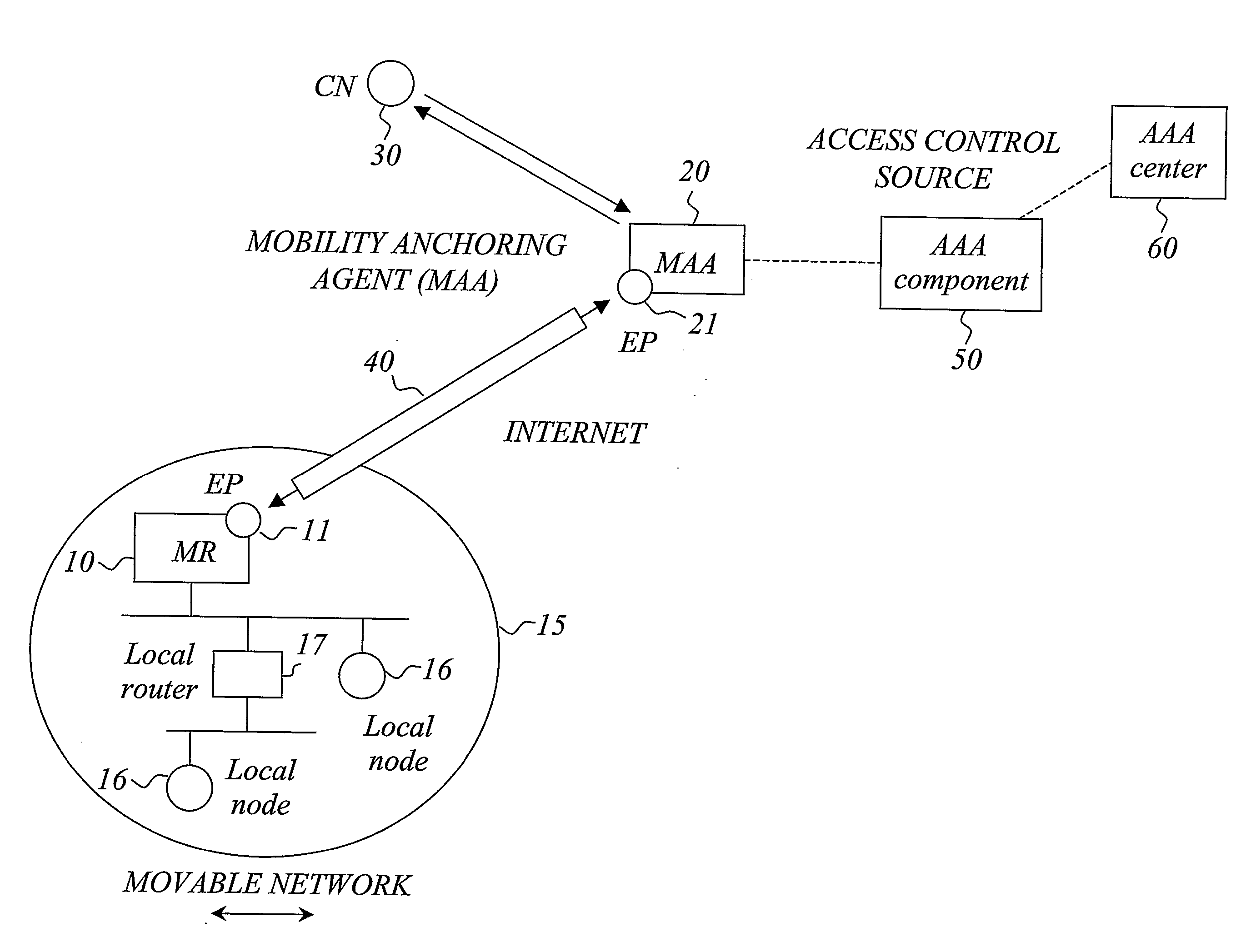
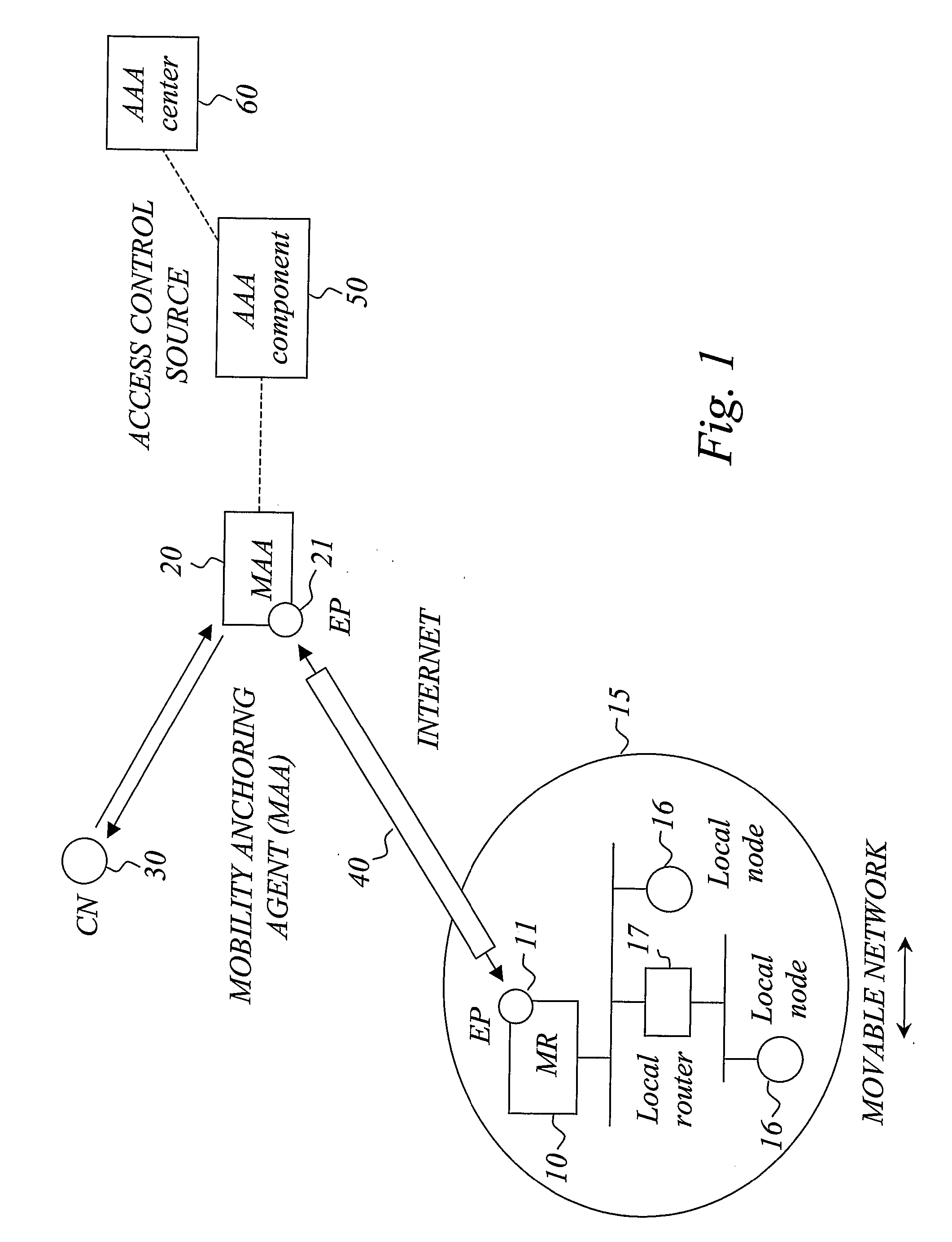
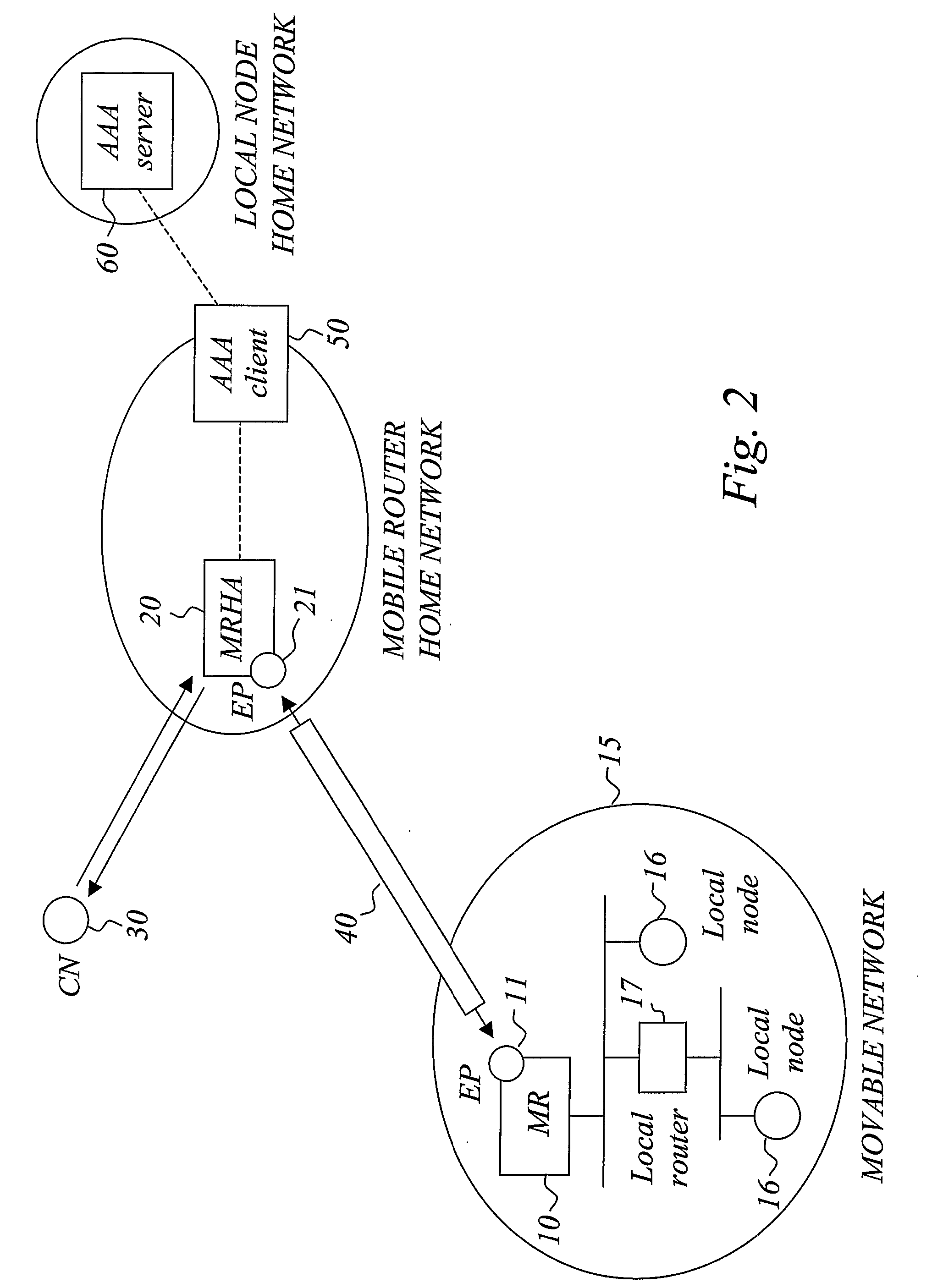
Network Mobility Support and Access Control for Movable Networks
ActiveUS20070223410A1Increase profitAvoid wastingNetwork traffic/resource managementNetwork topologiesAir interfaceEngineering
The invention relates to access control for a movable network (15) managed by a mobile router (10), wherein said mobile route is interconnected through a bi-directional link (40) with a mobility anchoring agent (20) that anchors the network mobility for the mobile router. According to the invention, access control enforcement points (11, 21) are located at both the mobile router (10) and the mobility anchoring agent (20). Access control is exercised at the mobility agent (20) to filter downlink packets to the mobile router (10) and access control is exercised at the mobile router (10) to filter uplink packets to the mobility anchoring agent (20). In this way, unauthorized packets, both uplink and downlink, do not have to cross the air interface before being filtered away, thereby preventing waste of valuable radio resources. The access control modules are typically provisioned with access control filter information, preferably by means of a hierarchical provisioning structure.
Owner:TELEFON AB LM ERICSSON (PUBL)
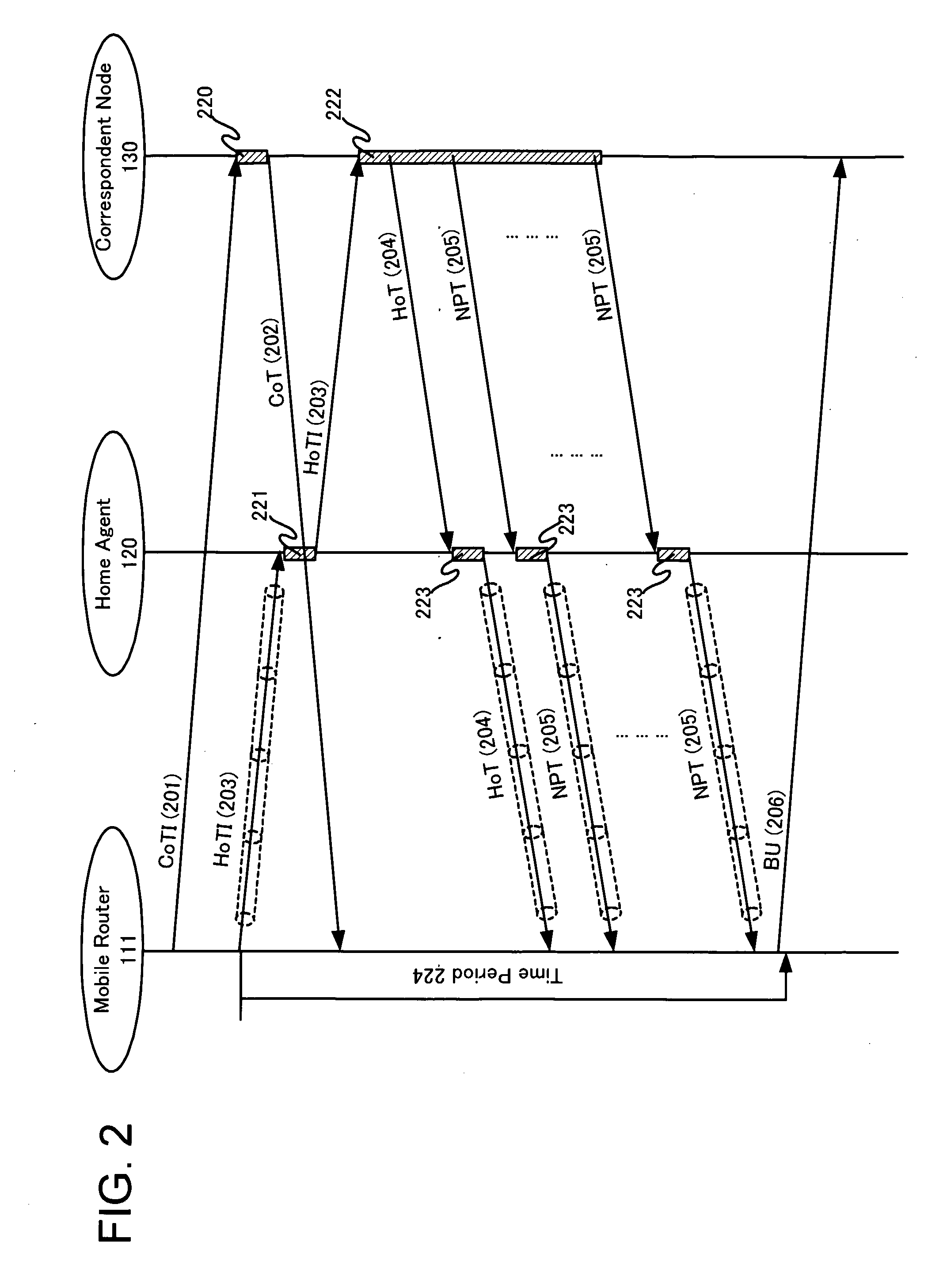
Network mobility management method and corresponding apparatus
InactiveUS20110090842A1Network traffic/resource managementData taking preventionSecure communicationChecksum
The present invention discloses a technique for realizing more secure communication and more efficient communication. According this technique, mobile router 111 informs correspondent node 130 of network prefix of a mobile network which mobile router includes behind, by sending HoTI message 203. Correspondent node sends NPT message 205 including the token which is cryptographically generated based on the network prefix in the HoTI message. Mobile router extracts this token and sends BU message 206 which comprises the checksum which is generated by this token and the conventional RR procedure tokens. Instead of the above mobile router, correspondent router can be also applied.
Owner:PANASONIC CORP
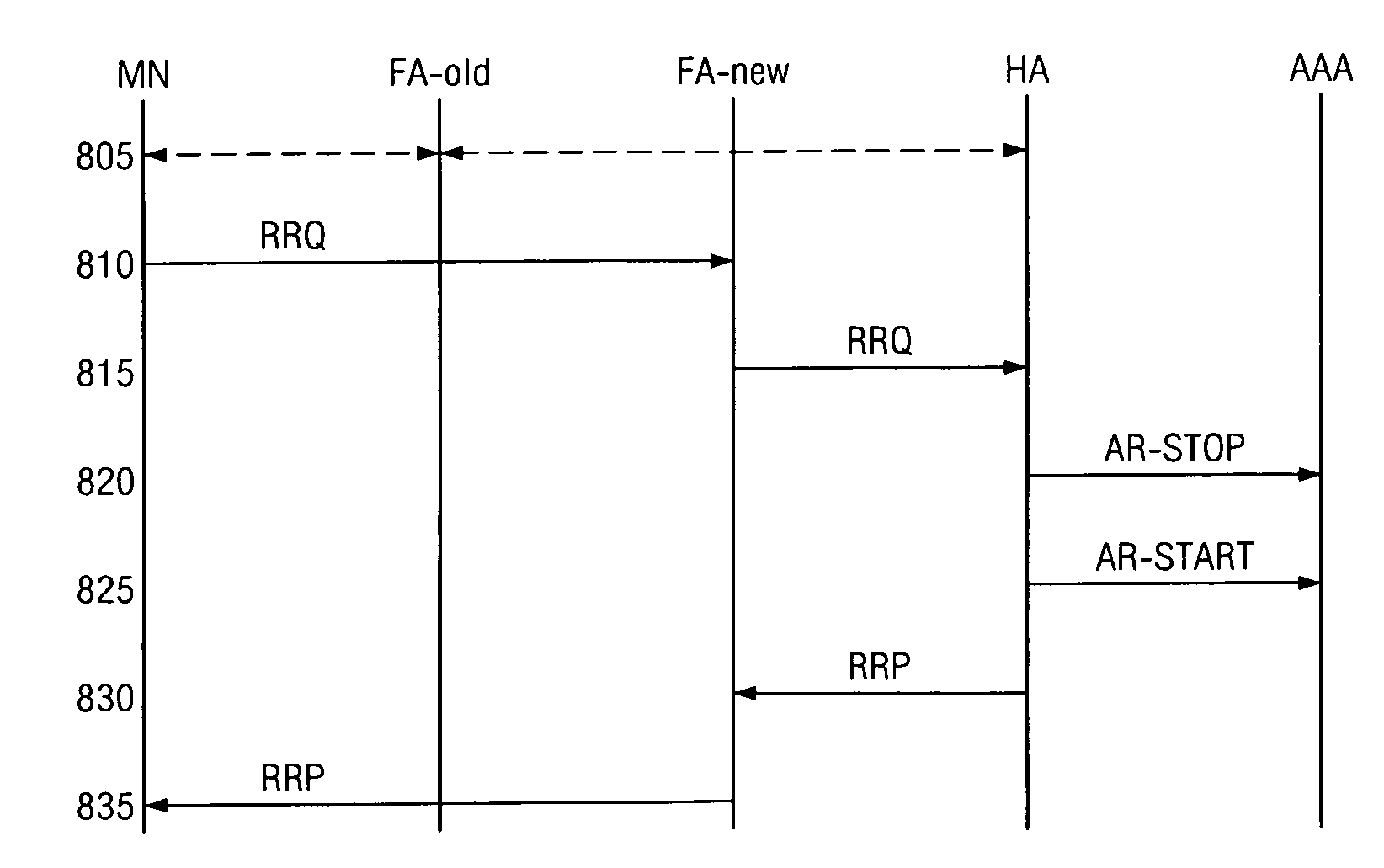
Method for generation of a single accounting stream during heterogeneous access network mobility
ActiveUS7471634B1Avoid problemsError preventionFrequency-division multiplex detailsAccess networkNetwork mobility
The present invention supports account monitoring for a mobile node by a home agent communicating with an AAA server computer. The home agent maintains accounting attribute information on system usage by a mobile node on a network. Attribute information is maintained and metered on the home agent in a data table. The home agent generates and transmits accounting messages containing the accounting attributes to the AAA server computer. The AAA server computer stores the attribute information in a memory for later billing.
Owner:APPLE INC
Mobility management method based on clustered superdense small network in 5G system
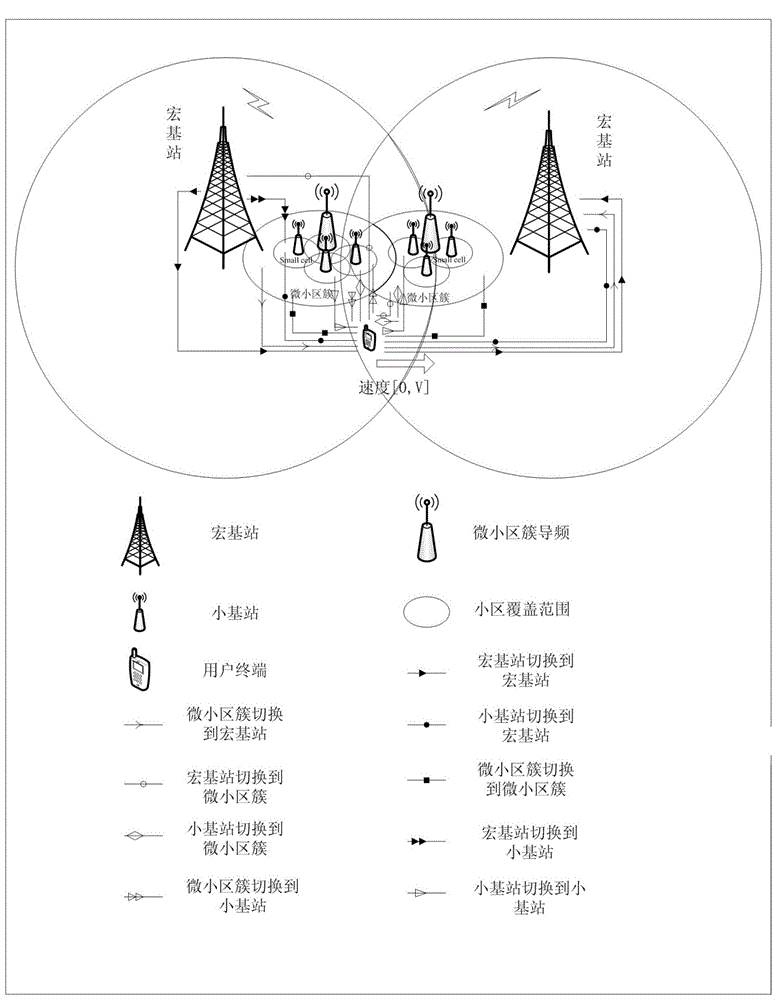
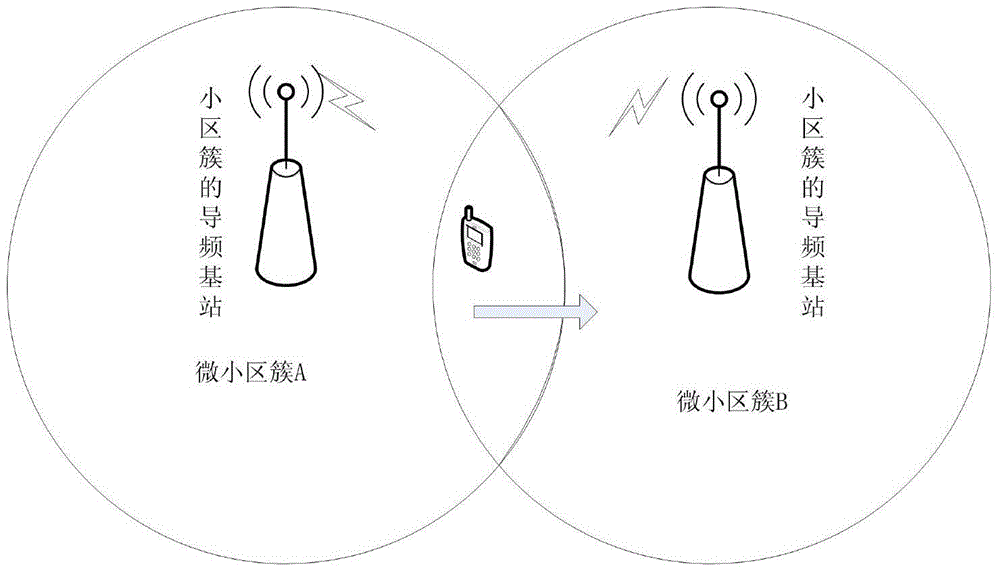
ActiveCN104581845AImprove web experienceReduce call drop rateWireless communicationMacro base stationsNetwork mobility
The invention provides a mobility management method based on a clustered superdense small network in a 5G system. The mobility management method comprises the following steps: dividing a superdense cell into a plurality of microcell clusters, wherein each microcell cluster has a common pilot frequency; predicting the channel condition of the cell by using a birth-death model, and according to the quality of a received cell signal, comprehensively considering the business condition and the mobility state of a user terminal and selecting a proper base station as a switching target, wherein the blocking rate of new equipment calling and switching can be obtained, a correct switching strategy is established, the switching success rate is improved, and the call drop rate of the user terminal and the blocking rate of calling are reduced; when equipment is in an idle state and the user terminal is in a low-speed state, switching to a pilot frequency base station of a microcell; when the user terminal is in a medium-speed or high-speed state, switching to a macro base station; when the equipment is in a connection state, namely when a business service exists, if the user terminal is in the low-speed state, switching to a small base station of the microcell; when the user terminal is in the medium-speed or high-speed state, switching to the macro base station.
Owner:CERTUS NETWORK TECHNANJING
Method of optimizing network mobility
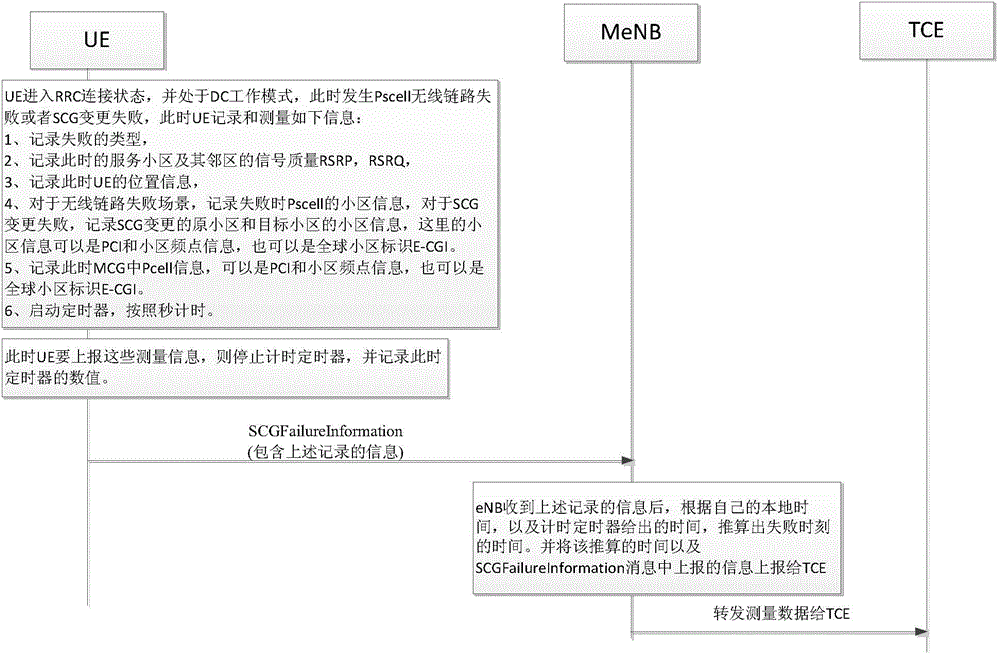
The present invention provides a method of optimizing network mobility. The method comprises the steps of measuring and recording the failure types, the signal quality of the service cell and adjacent cell signal quality, the position information, the time stamp information, the cell information and the Pcell information of an MeNB when a UE generates the wireless link failure or SCG change failure in a Pscell, then reporting to a network side to be used as the input data of the network side optimization. By utilizing the method of the present invention, the network optimization data under a DC scene can be collected by a commercial terminal, thereby perfecting the problems, such as the network optimization processing, the problem positioning, etc.
Owner:BEIJING XINWEI TELECOM TECH
Method for reconfiguring mobility platform, and device applying the method
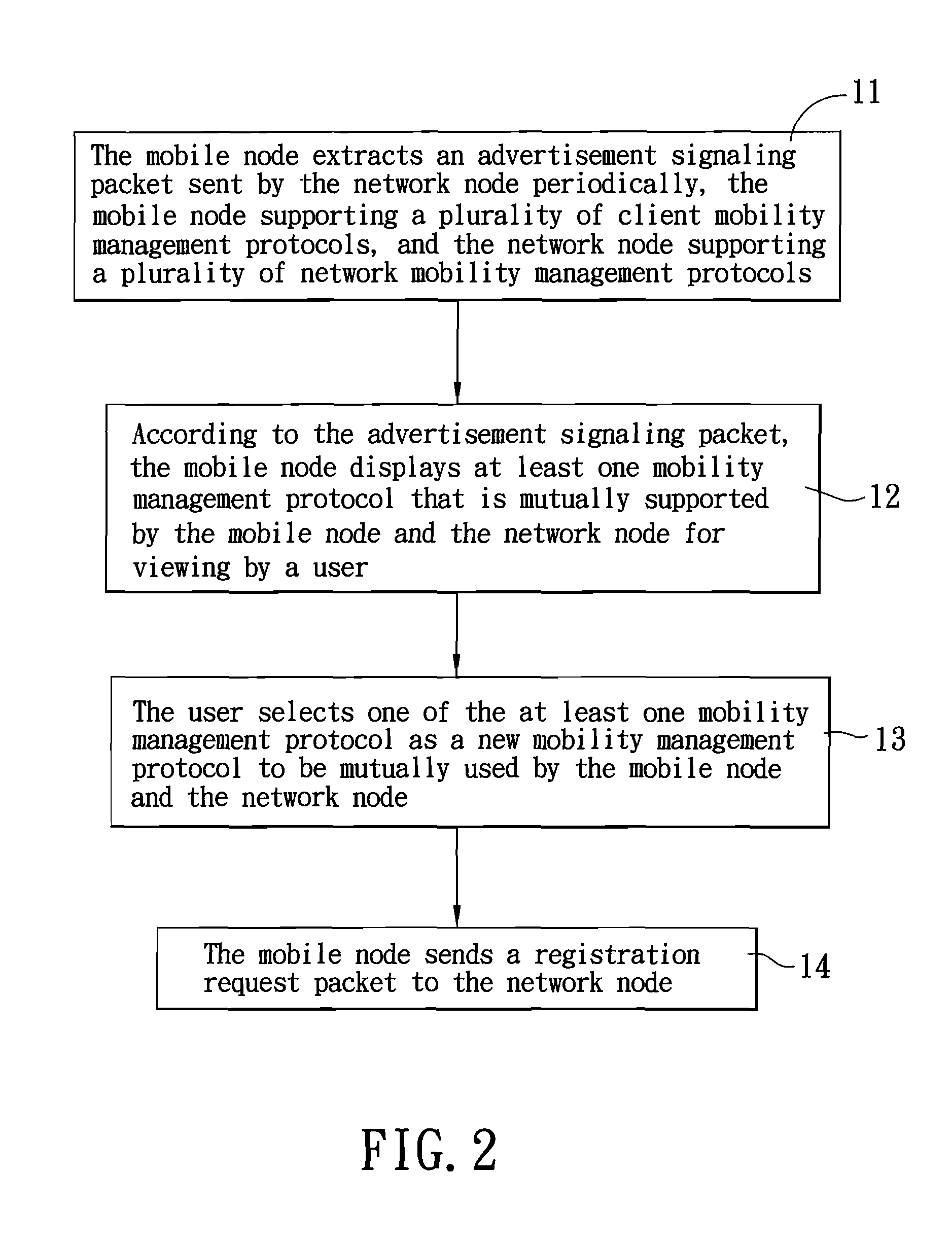
InactiveUS20070248054A1Wireless network protocolsRadio/inductive link selection arrangementsNetwork mobilityClient-side
A method for reconfiguring a mobility platform includes: enabling a mobile node to extract an advertisement signaling packet sent periodically by a network node, wherein the mobile node supports a plurality of client mobility management protocols, and the network node supports a plurality of network mobility management protocols; according to the advertisement signaling packet, enabling the mobile node to display at least one mobility management protocol that is mutually supported by the mobile and network nodes for viewing by a user; enabling the user to select one of the at least one mobility management protocol to serve as a new mobility management protocol to be mutually used by the mobile and network nodes; and enabling the mobile node to send a registration request packet to the network node.
Owner:NATIONAL TSING HUA UNIVERSITY
Method, device and system for recovering data after restarting of device
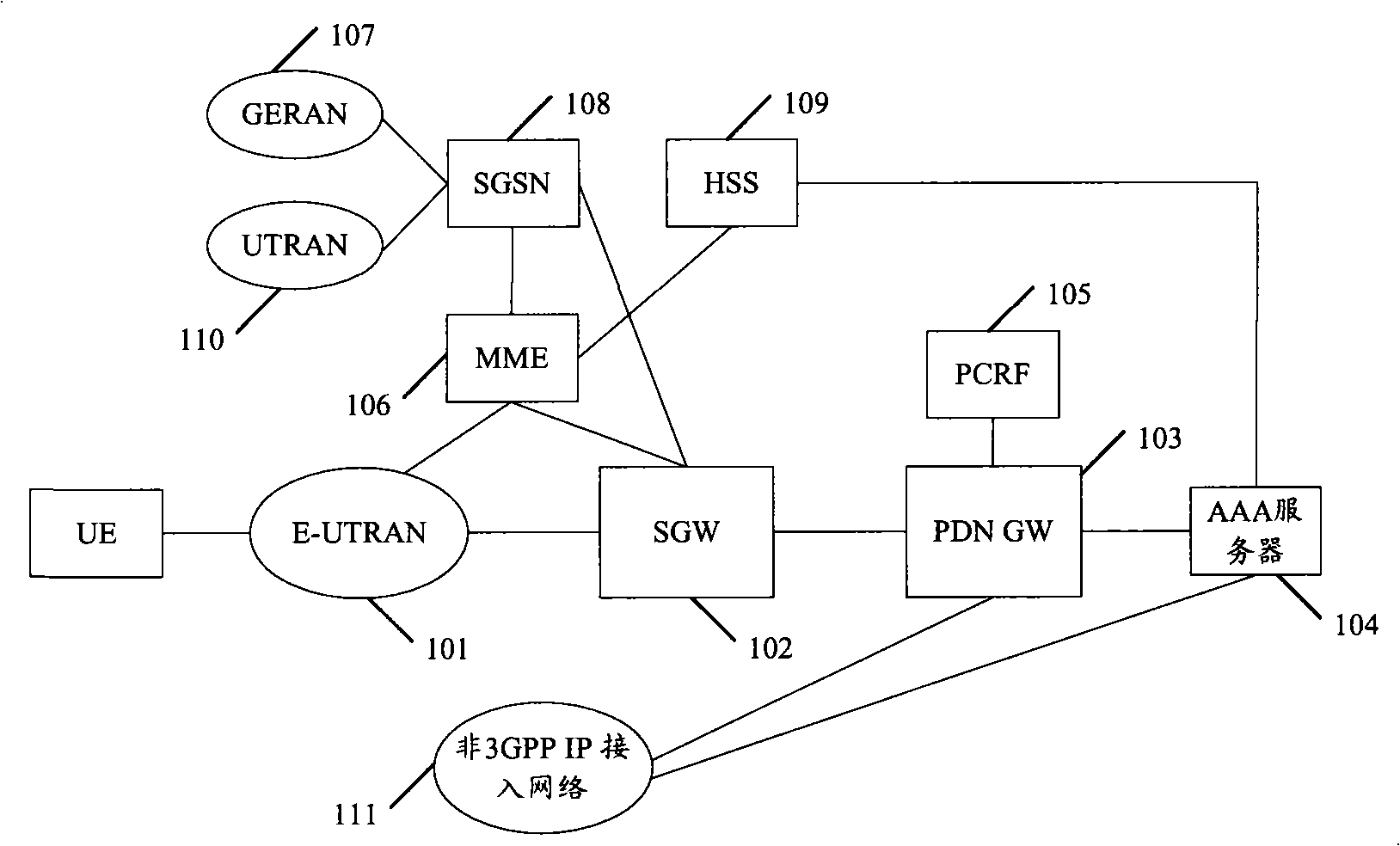
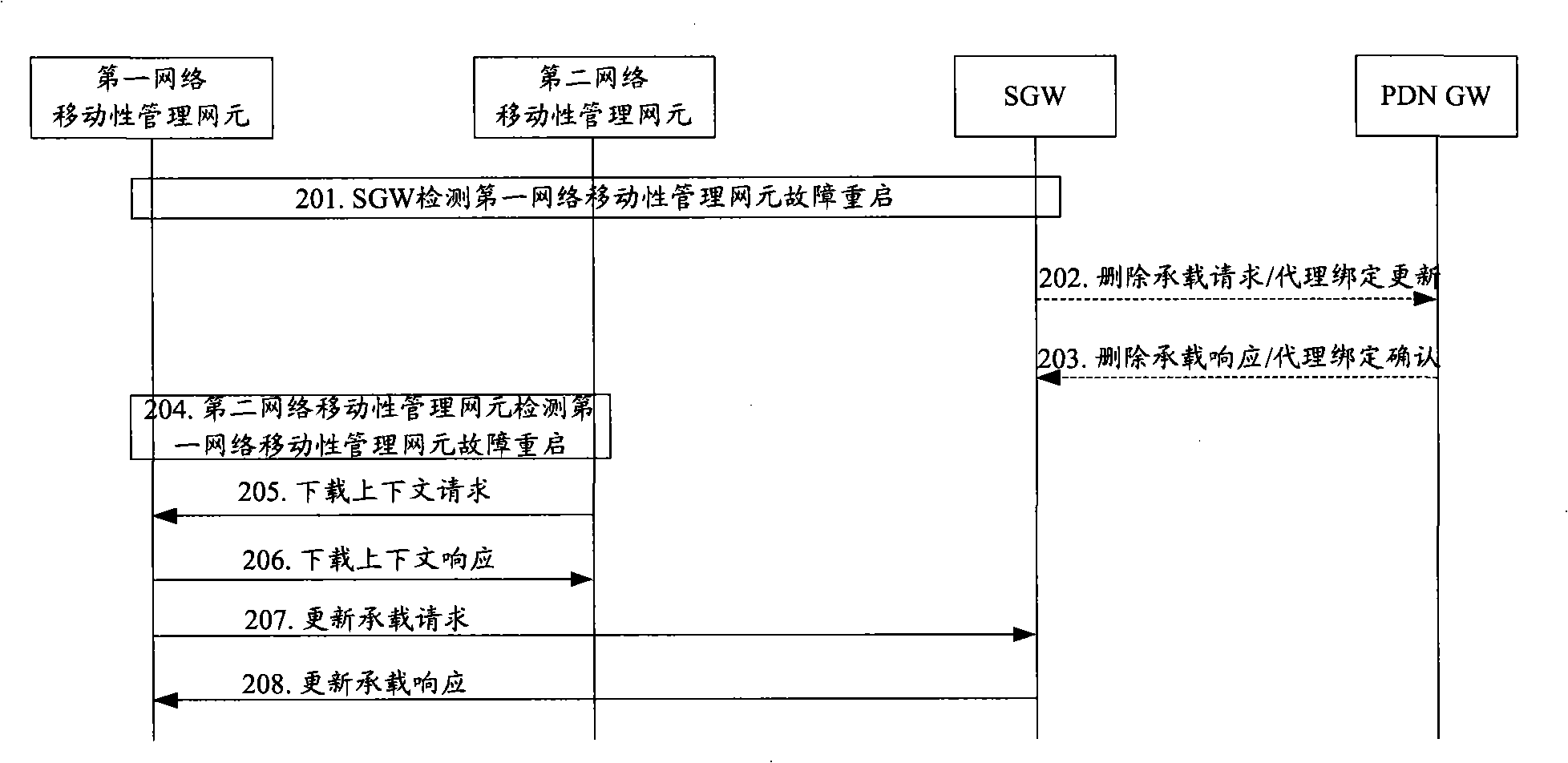
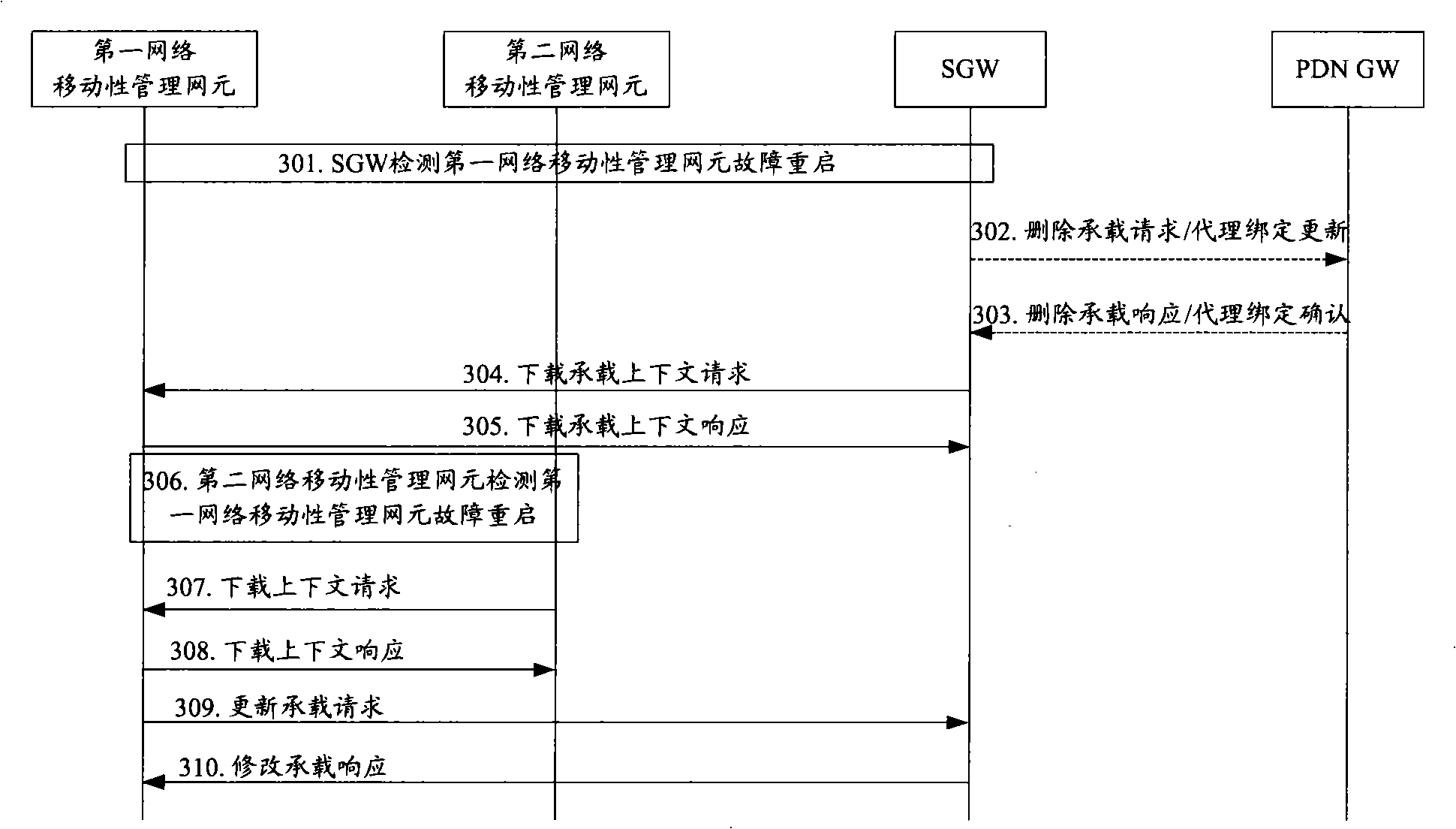
ActiveCN101540989AAvoid reinitiating the attach processReduce signaling loadNetwork data managementNetwork mobilityMobility management
The embodiment of the invention discloses a method, a device and a system for recovering data after restarting of a device. The method of the embodiment of the invention comprises the following steps: detecting the restarting of a first network mobility management network element, determining user equipment (UE) related with the first network mobility management network element, sending information which is carried with context information of the UE to the first network mobility management network element by a second mobility management network element, and recovering the context of the UE by the first network mobility management network element according to the acquired context information. Because the context of the UE in the device is recovered after the device is restarted, SGSN can receive a position updating request of the UE when the subsequent UE initiates position updating flow, and avoids the UE initiating attachment flow again; therefore, idle signaling can be reduced, and idle signaling load can be reduced.
Owner:HUAWEI TECH CO LTD
Integrated management system for mobility of identification network and method thereof
InactiveCN102098228AReduce the frequency of map updatesReduce the impactData switching networksNetwork data managementTime delaysNetwork mobility
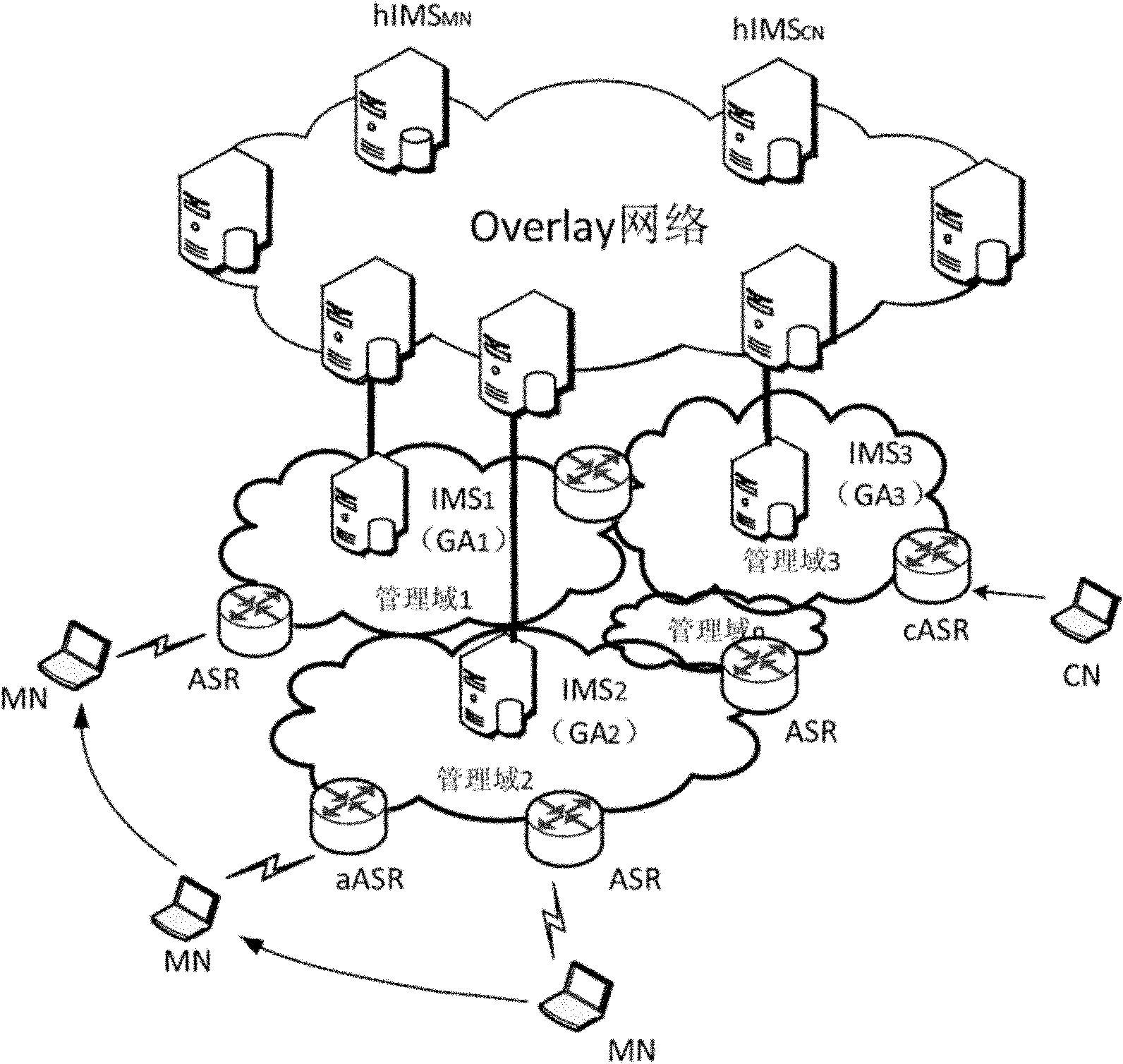
The invention discloses an integrated management system for the mobility of an identification network. The system comprises a plurality of identification mapping servers, each identification mapping server is responsible for managing a plurality of subnetworks, all identification mapping servers form a distributed hash table-based Overlay network, and the identification mapping servers realize the function of local gateway agency in a physical network. By copying the identification mapping relationship of a plurality of mobile nodes in proportion in the Overlay network, the influence of the mobility management caused by the inconsistent topology between the physical network and the Overlay network is reduced, the query time delay is reduced, and a query load is balanced; and due to a hierarchic registering mechanism, the updating frequentness of the mapping in the Overlay network is reduced, and the performance for updating and querying the mapping relationships is balanced.
Owner:TSINGHUA UNIV
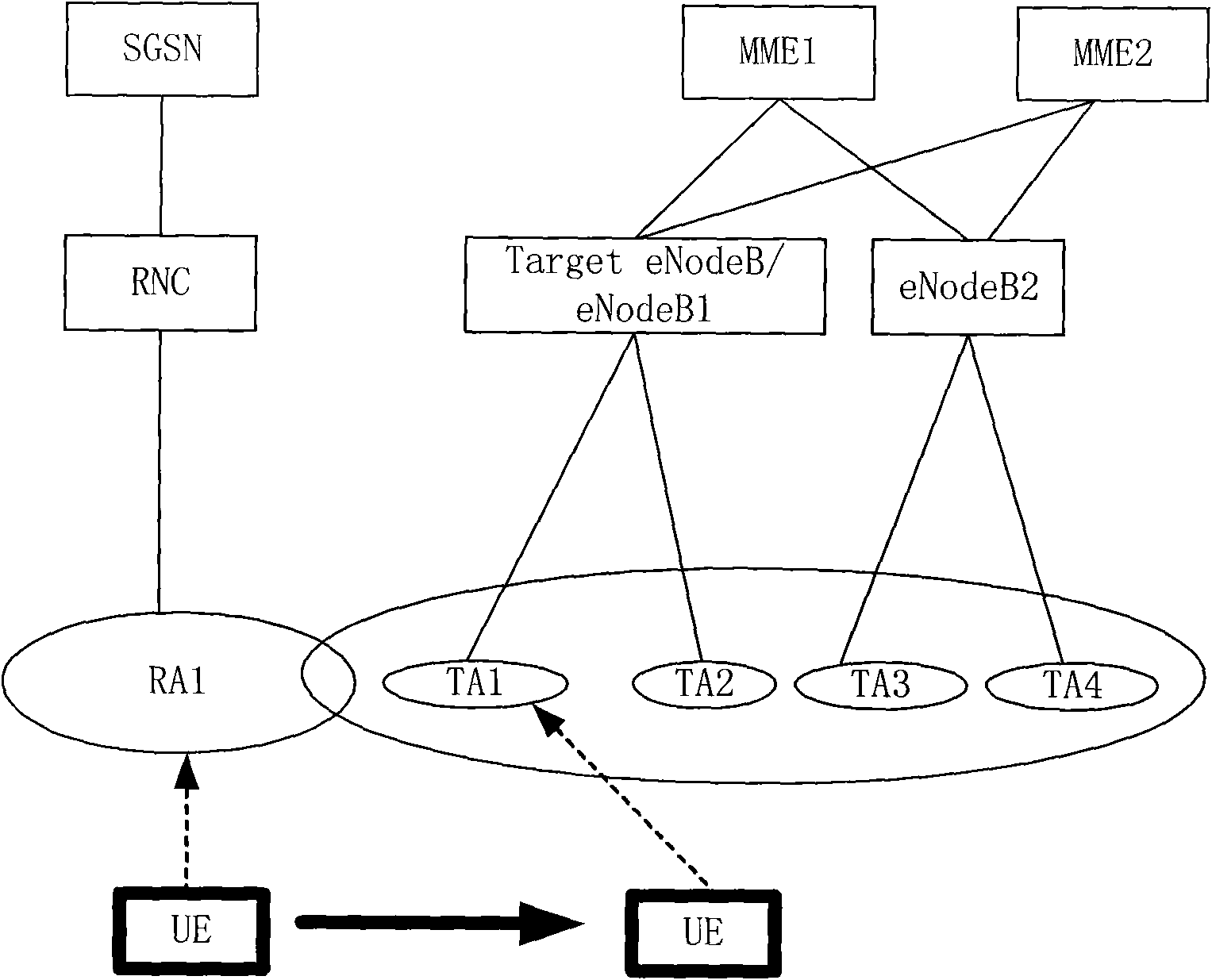
Tracking area management method and apparatus for long term evolution telecommunication systems
ActiveUS20110294524A1Minimize total traffic cost functionWireless commuication servicesNetwork data managementTraffic capacityTransition probability matrix
An MME keeps track of network tracking mobility characteristics by periodically updating a TA transition probability matrix derived from a global table that maintains UE movement data in the network by noting current TA and most recently known previous TA of each EU for every TAU event and paging event. The MME also maintains data of the number of paging events and TAUs performed by each UE and stores a paging ratio versus TAU for each UE. The UE characteristics, UE paging ratio, and network mobility characteristic are utilized in an algorithm that constructs a TA list for each UE designed to minimize the overall traffic cost function for paging events and TAU events for that UE and the overall network. Optionally, the TA list for each EU is constrained to meet certain minimum performance characteristics such as a predetermined paging success rate target and / or a predetermined delay bound target.
Owner:APPLE INC +1
Network adapted for mobile devices
ActiveUS20070058597A1Ticket-issuing apparatusHand manipulated computer devicesNetwork mobilityData acquisition module
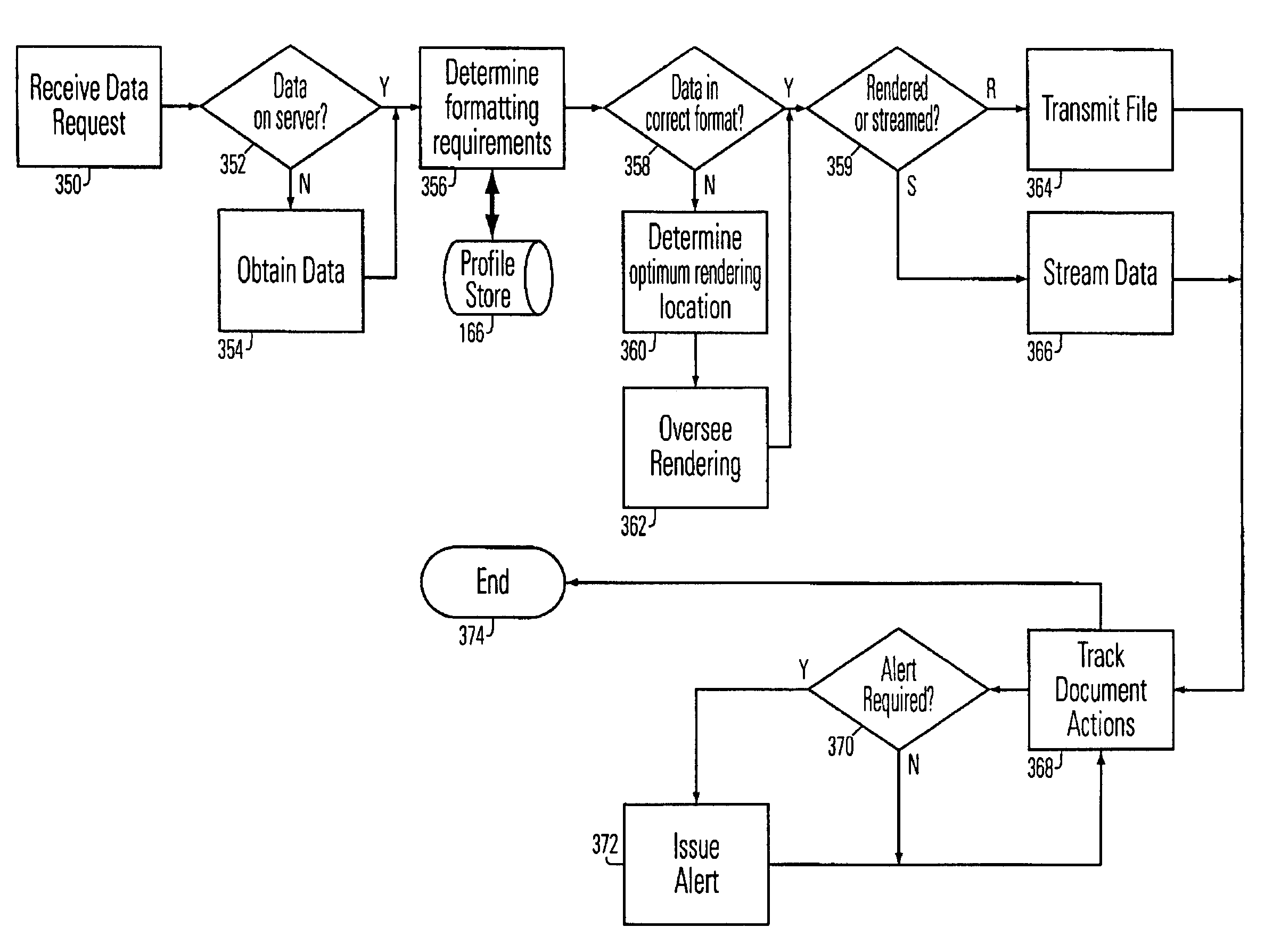
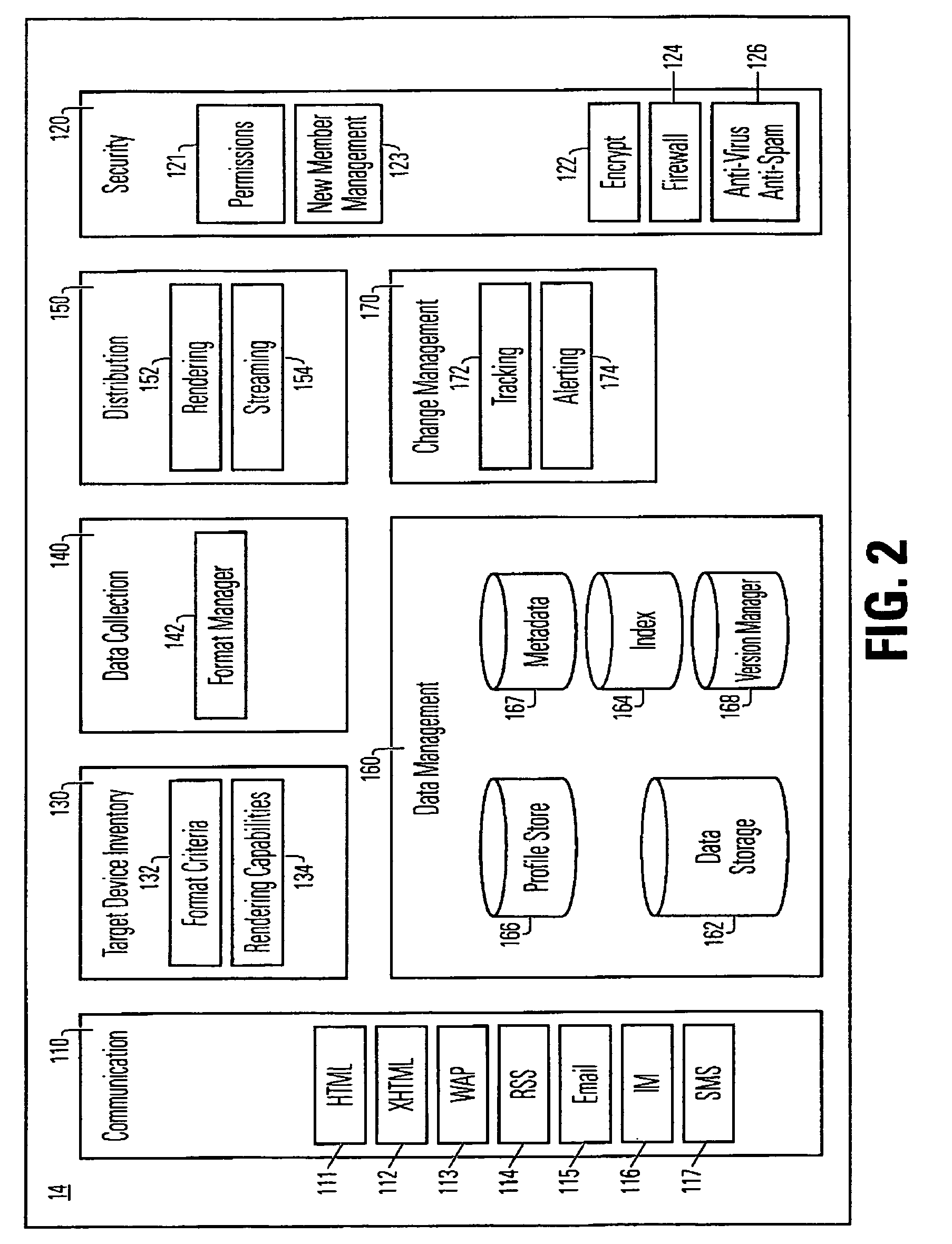
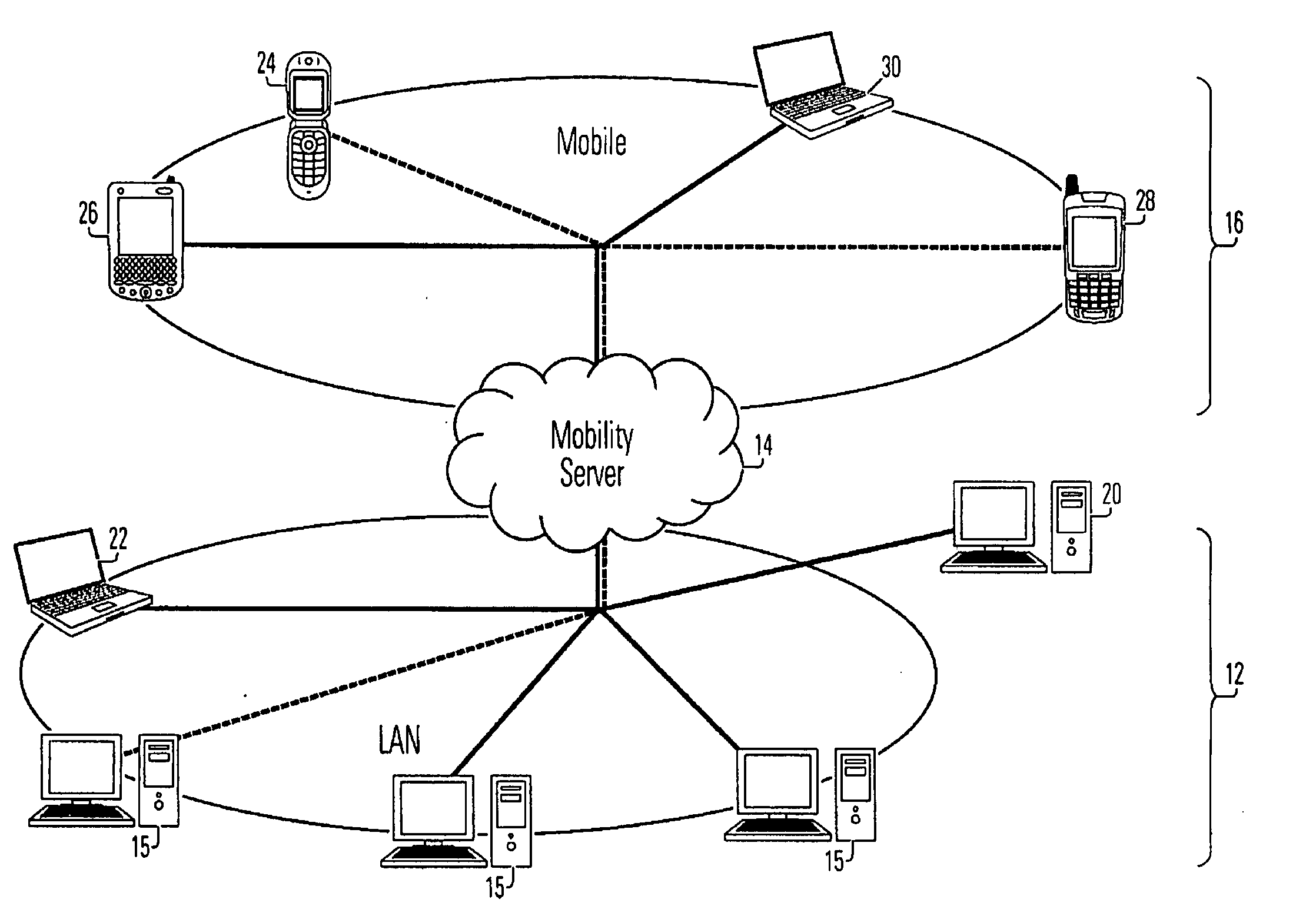
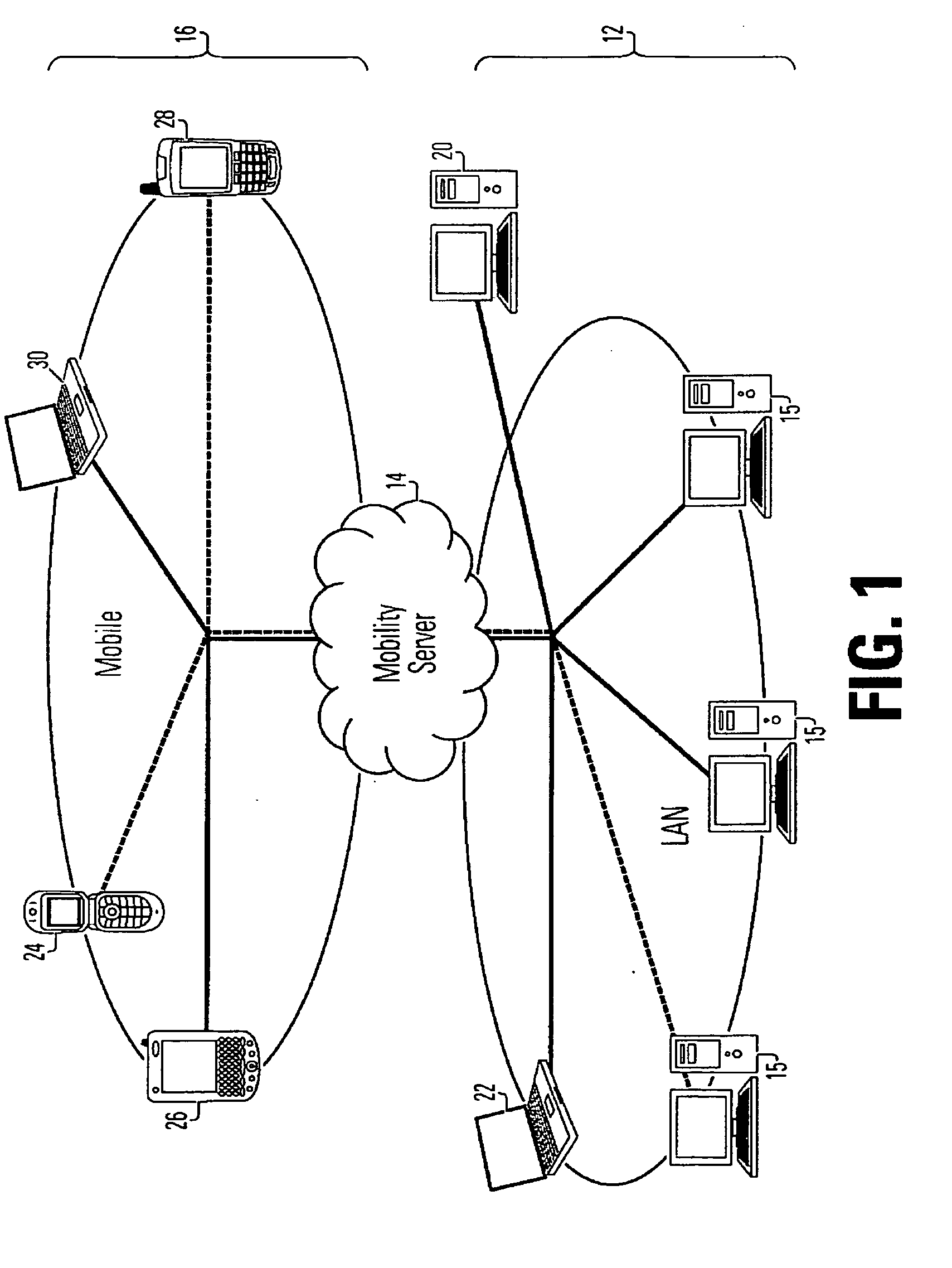
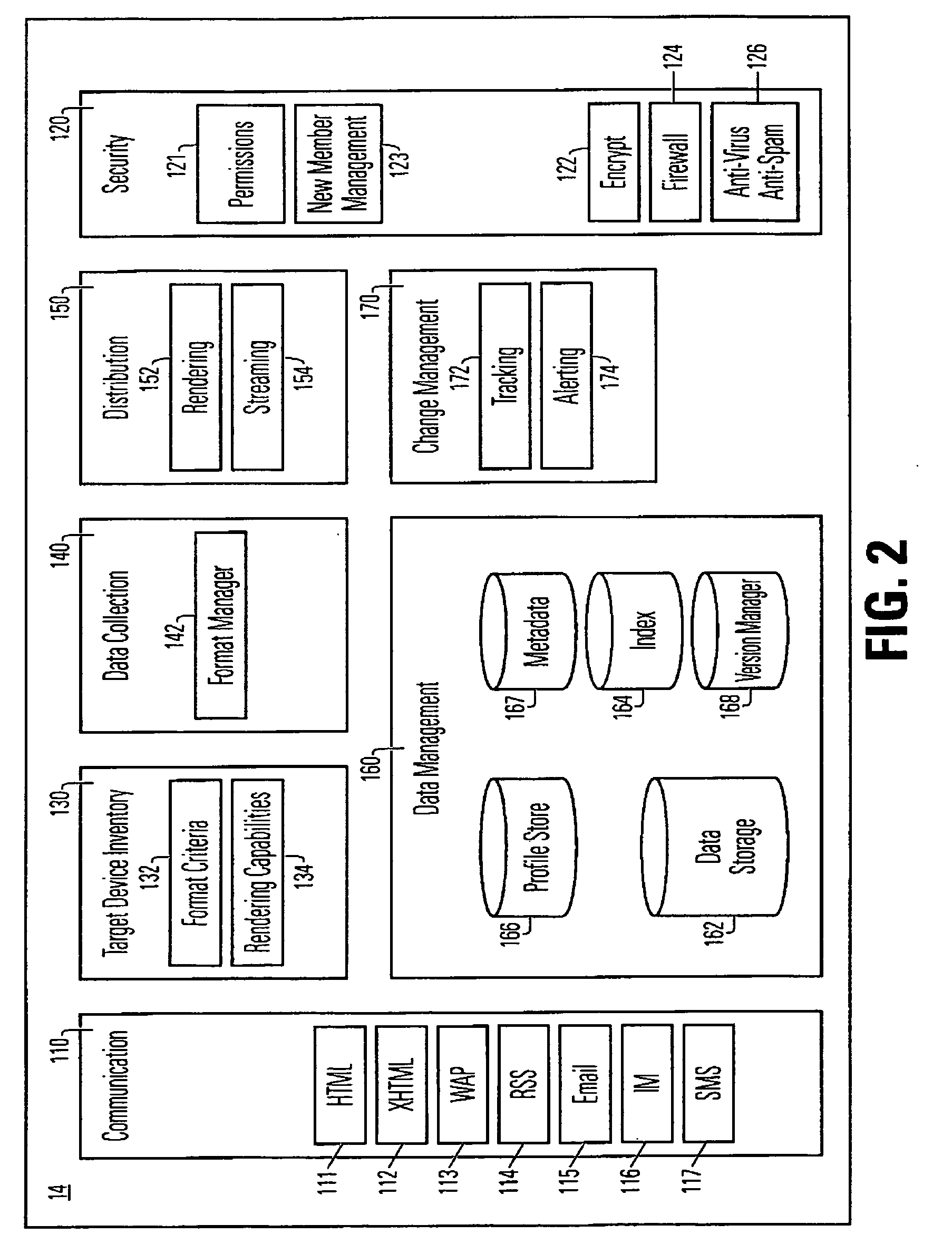
A network mobility server, which includes a target device inventory module, a data collection module, a data management module and a distribution module. The data management module, includes at least one data storage module, in which at least a portion of the data stored therein are identical data items stored in different selected formats suitable for use on mobile computing and telecommunication devices. The network also includes network agents, resident on numbers of the network members.
Owner:WELLS FARGO BANK NAT ASSOC
Handoff method for communication system using multiple wireless resources
InactiveUS20080057970A1Increase reception strengthGuaranteed mobilityError preventionTransmission systemsCommunications systemViewpoints
In a wireless communications system operating according to CDMA or the like, when one terminal simultaneously performs communication using multiple wireless resources (e.g., multiple carriers), there was a problem that when it was attempted to guarantee network mobility by the same soft handoff system as in the case where communication was performed using only one wireless resource, efficiency suffered from the viewpoint of network forwarding load, processing load and wireless resource occupancy time. Soft handoff termination is judged and soft handoff is forcibly terminated according to whether or not the data rate obtained for all resources on the network side satisfies a requested rate, based on a reception state notification from a terminal concerning wireless resources. By performing this processing, the soft handoff period is shortened, sufficient received strength in the terminal is maintained and terminal mobility is guaranteed, while at the same time network forwarding load, terminal processing load and wireless resource occupancy time are suppressed to the absolute minimum.
Owner:HITACHI LTD
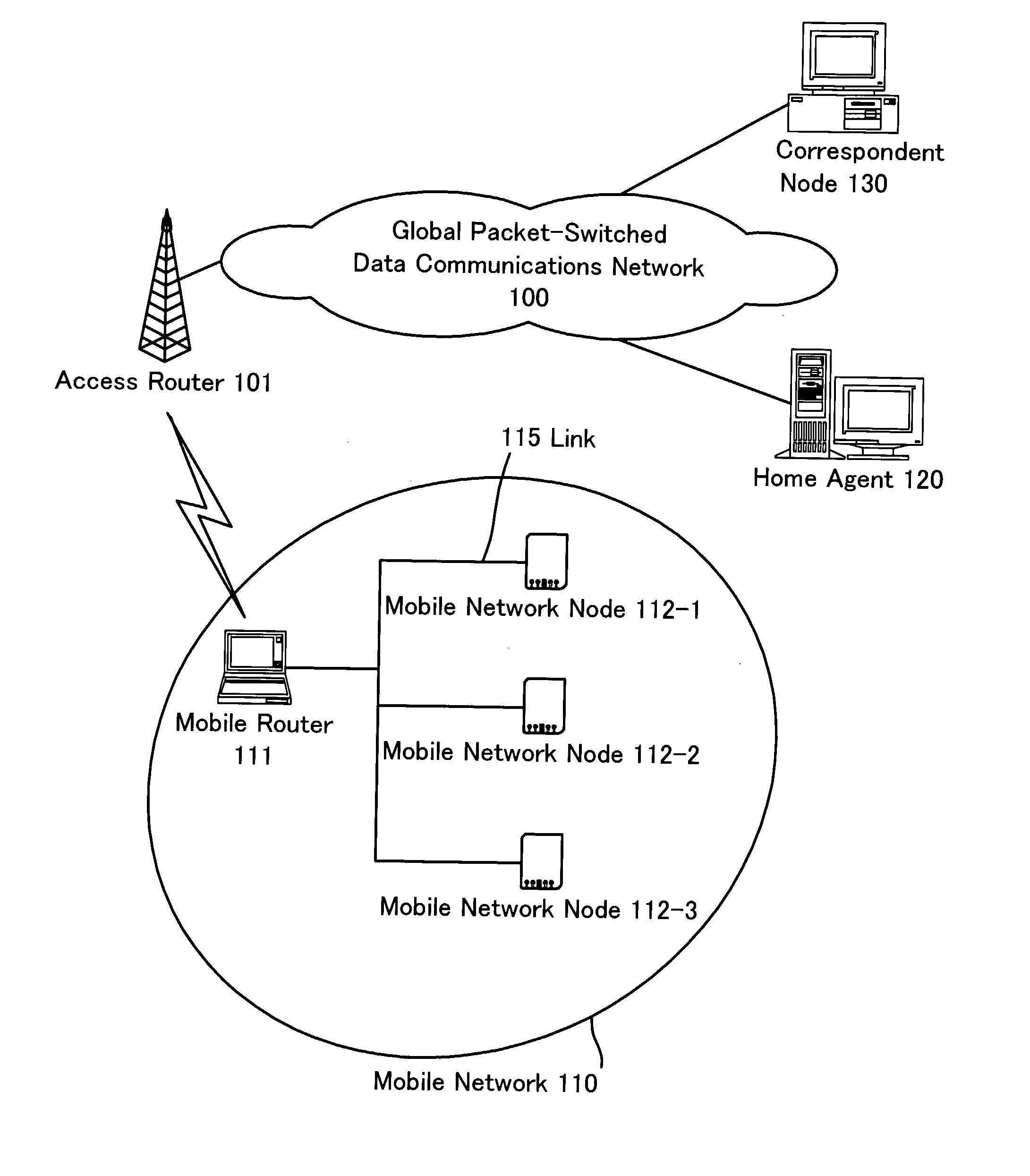
Communication system, mobile router and home agent
InactiveUS20090257401A1Reduce and eliminate inefficient and redundant routingNetwork topologiesWireless network protocolsAccess networkFast handover
The present invention provides a new technique, according to which inefficient and redundant routing can be eliminated, which may occur when the fast handover is applied to network mobility and which may cause delay. According to this technique, a mobile router (MR) 210 makes the mobile node grasp the care-of address of the mobile router by performing route optimization to and from the mobile node (MN) 130 connected to the mobile network under its control. When the mobile node performs handover to another access network by fast handover, the mobile router tunnels a packet by using own care-of address as a source address—i.e. the packet, which has been sent from a correspondent node (CN) 140 and which is to be sent to an address before the handover of the mobile node (old care-of address)—and the packet is directly forwarded to the mobile node without passing through the home agent of the mobile router.
Owner:PANASONIC CORP
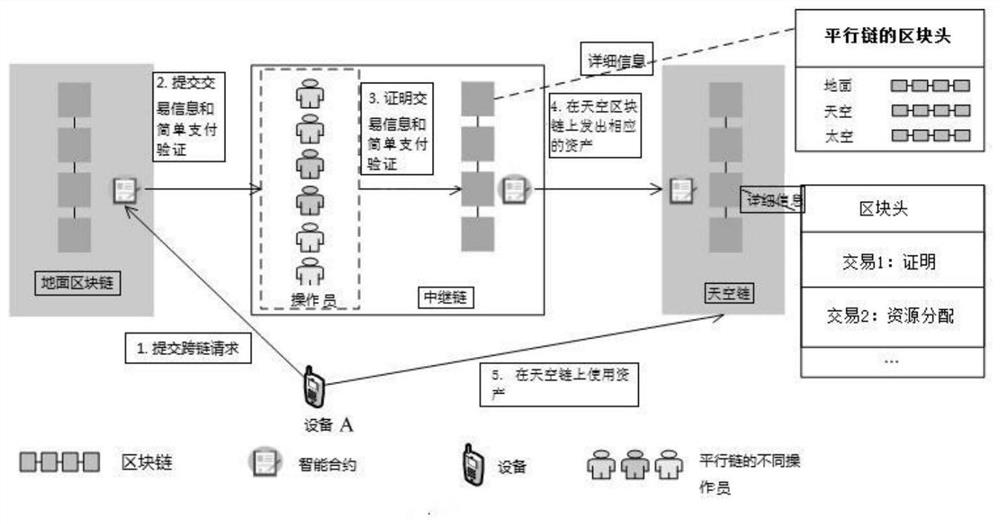
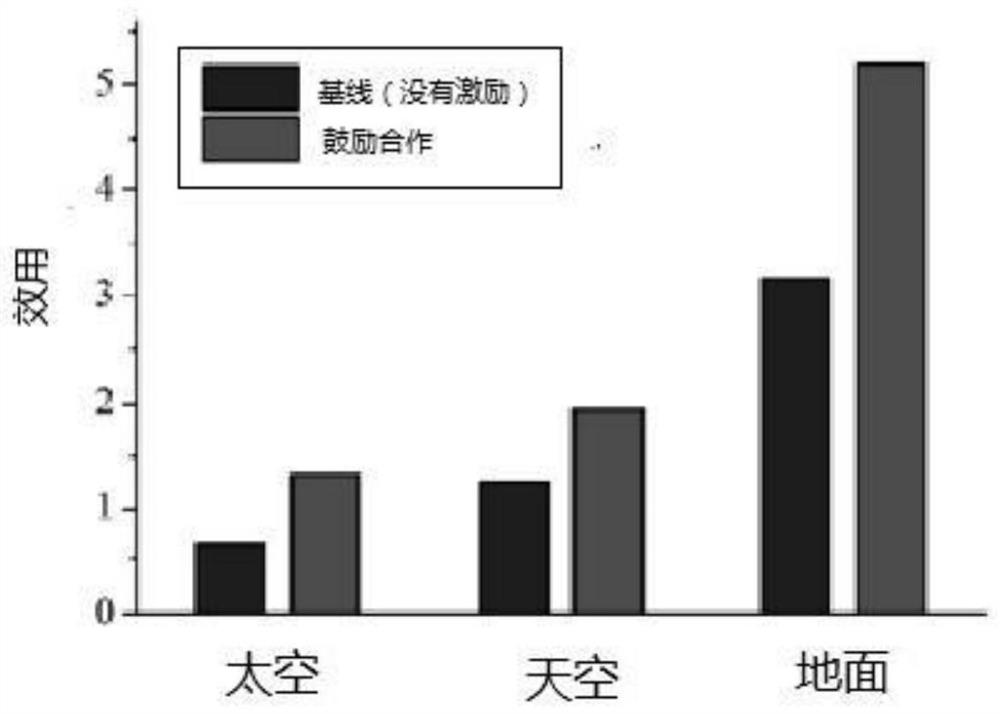
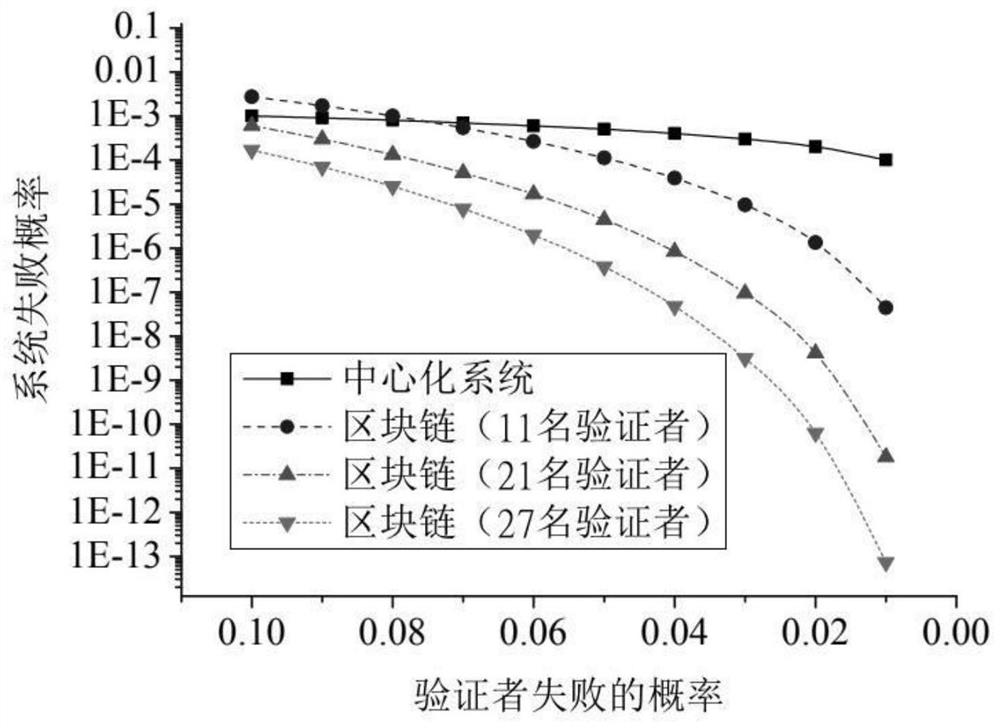
Space-air-ground network mobility management architecture based on blockchain cross-chain technology
ActiveCN112073222AAvoid failureAvoid attackDatabase distribution/replicationDigital data protectionTrunkingEngineering
The invention discloses a space-air-ground network mobile management architecture based on a blockchain cross-chain technology. A blockchain is established for each network, a Byzantine fault-tolerantconsensus mechanism is utilized to establish the blockchain, equipment with strong capability and trustworthiness is used as a verifier to serve as a full node, and other equipment communicates withthe verifier and joins in the network in the identity of a light node. In order to encourage all airplanes and satellites to actively participate, reverse Vickrey-Clarke-Groves mechanism auction is simulated, so that the system efficiency is improved to the maximum extent. Block chain cooperation is realized by using a side chain / relay chain technology, and the determined price is securely transmitted to a target network. The blockchain can effectively prevent each node from breaking down, and can also prevent attacks for each network server. Through block chain cooperation, the information transmitted across the block chains is tamper-proof and audible. The blockchain can independently and privately maintain in-segment management. The cooperative block chain supports the inter-segment interconnection of the space-air-ground network to adapt to the dynamic network at low cost.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
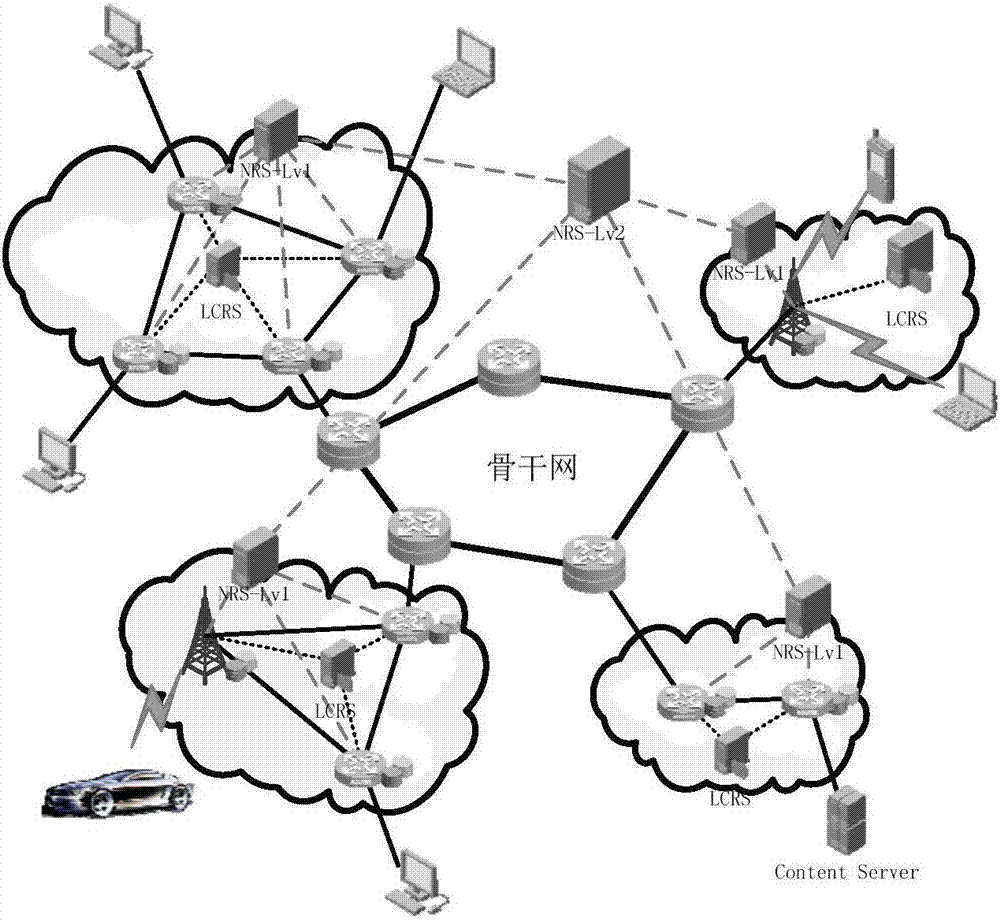
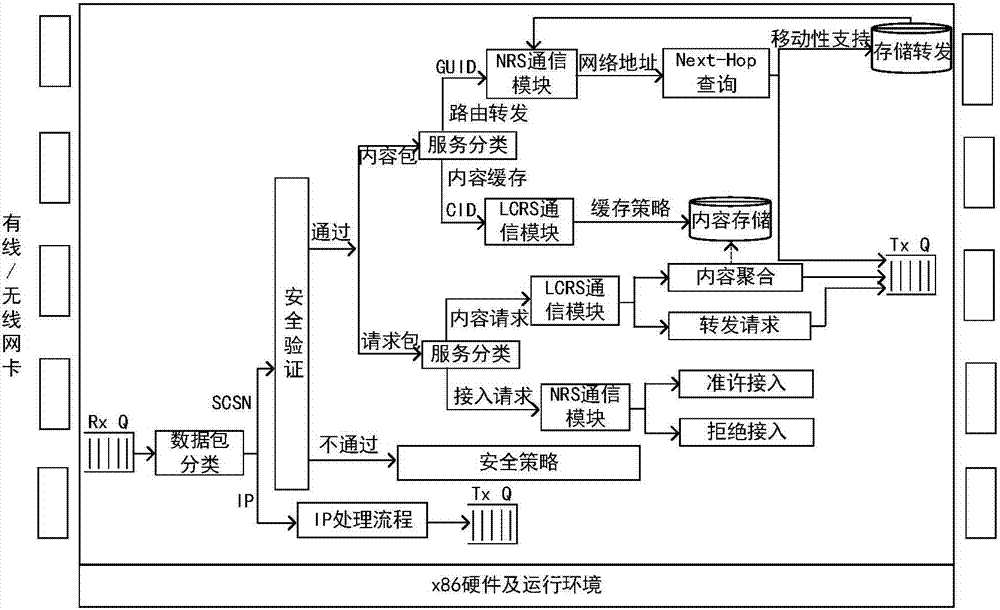
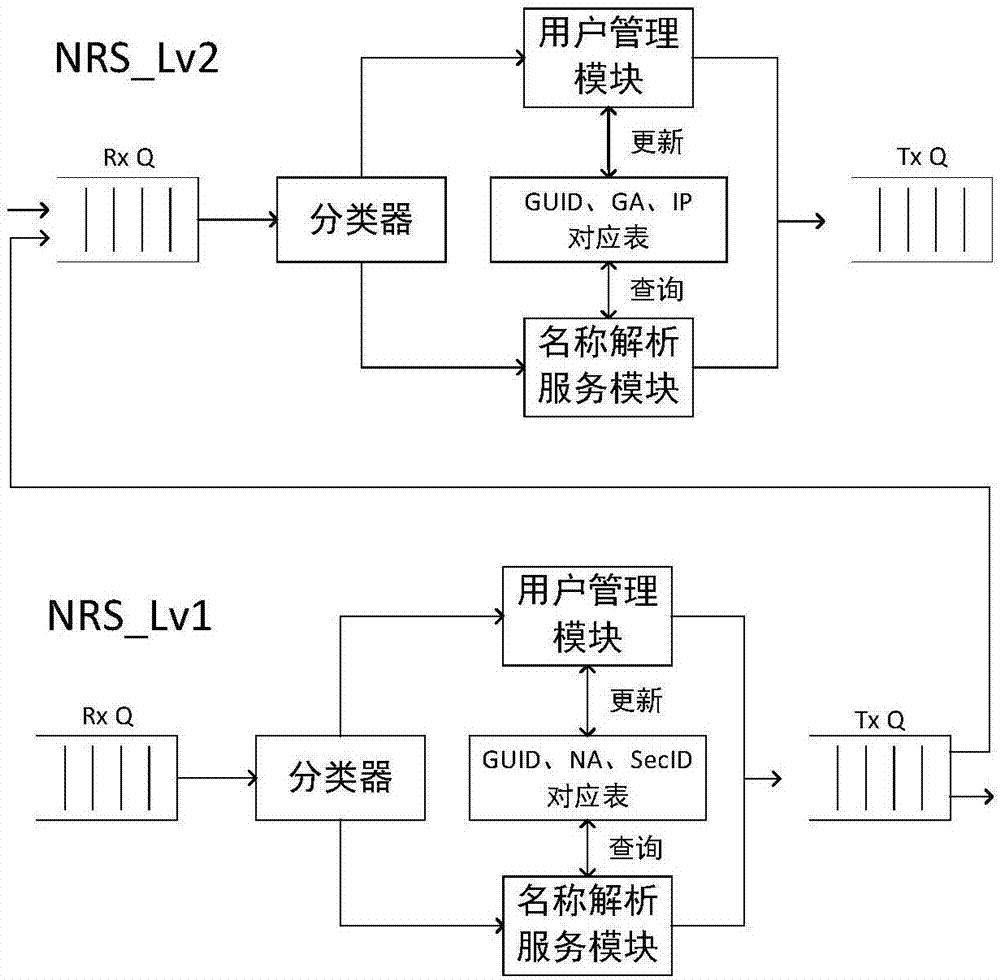
Intelligent network architecture integrated with perceptual computing and storage, and implementation method of the same
ActiveCN107395500AAchieve sharingRealize multiplexingData switching networksContent IdentifierNetwork mobility
The invention discloses intelligent network architecture integrated with perceptual computing and storage, and an implementation method of the same. The intelligent network architecture integrated with perceptual computing and storage utilizes a model combined with a content identifier (CID), an equipment identifier (GUID) and a security identifier (SecID), and is characterized in that the content is stored in the network in a distributed manner; a content caching strategy is deployed in LCRS; a clustering strategy is deployed in a router; through mutual coordination between nodes, sharing and reuse of resources can be realized; a hybrid routing mode of device identifier / address is utilized, and NRS provides two levels of name analysis service to enable the network to support seamless host and network mobility; and an active defense security authentication mechanism is utilized, and an edge router is taken as a root of trust, with combination of the device identifier and the security identifier, access control and authentication are performed on the user, and effective interception of the illegal content is performed through combination of the content identifier. The intelligent network architecture integrated with perceptual computing and storage can percept the content of network transmission, changes of the network environment, and the behavior of the network user, can support seamless host and network mobility, and has the expandable ability and the evolution capability, and can realize active defense, thus having network security.
Owner:UNIV OF SCI & TECH OF CHINA
Method and system for providing conversation switch in multi-access mode
InactiveCN101247637AFix switching issuesImprove practicalityNetwork topologiesRadio/inductive link selection arrangementsAccess methodNetwork mobility
The present invention discloses a method and system for providing conversation switch in multiple access methods, and switch entity, user equipment, which includes: marking conversation of user equipment by using first sign, marking conversation of switch entity by using second sign, establishing reflection relationship of fist sign and second sign; when conversation is switched, conversation request carrying first sign is transmitted to switch entity, and second sign corresponding to said first sign in switch entity is determined according with reflection relationship; switch entity switches conversation after conversation determined by second sign. The invention solves switch problem that present voice calling continuous technology only supports single conversation in IP multimedia sub-system, and increase practicability of voice calling continuous technology, increase competition in internet mobile operation.
Owner:HUAWEI TECH CO LTD
Method, system and device for switching between networks, updating location area and establishing ISR
ActiveCN101610554ANormal businessRadio transmission for post communicationWireless communicationTerminal equipmentNetwork mobility
The invention discloses a method, a system and a device for switching between networks, updating location area and establishing ISR, and belongs to the field of communication. The method comprises that: a terminal device judges an initiating condition meeting a location area update flow, and initiates the location area update flow to a mobility management network element in a target network, wherein the initiating condition of the location area update flow comprises that the terminal access technology is changed; a source network mobility management network element selects a mobility management network element, which is positioned in the target network and establishes the ISR with the source network mobility management network element, as a target mobility management network element; and a forward switching request is sent to the selected target mobility management network element. The method ensures that the target mobility management network element is registered in HSS and acquires signed data, also ensures that terminal UE acquires novel temporary identity (P-TMSI / GUTI) allocated to the UE by the target mobility management network element so as to effectively guarantee the normal service of follow-up terminal UE.
Owner:HUAWEI TECH CO LTD
Network mobility over a multi-path virtual private network
ActiveUS8272046B2Key distribution for secure communicationDigital data processing detailsPrivate networkNetwork mobility
Owner:CISCO TECH INC
Method and equipment for updating service quality
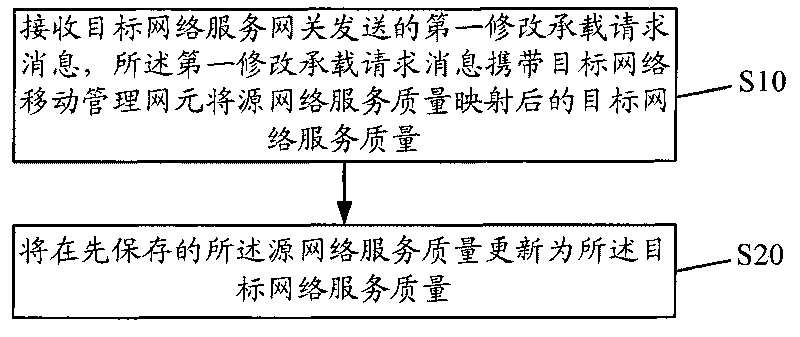
InactiveCN101765090AAvoid Duplicate Quality of Service Mapping ProcessReduce complexityNetwork traffic/resource managementNetwork data managementQuality of serviceNetwork mobility
The embodiment of the invention discloses a method for updating service quality and equipment thereof; the method for updating service quality in the invention comprises the following steps: a first modification loading request message transmitted by a target network service gateway is received, and the first modification loading request message carries target network service quality after source network service quality is mapped by a target network mobility management network element; the source network service quality which is stored in advance is updated into the target network service quality, so as to carry out corresponding transmission according to the target network service quality. In the embodiment of the invention, the equipment for updating service quality comprises a first receiving module and an updating module; by adopting the method and the equipment for updating service quality, repeated service quality mapping on a plurality of network elements is avoided, so as to lead the product to realize easily; in addition, the processing load of the product can be lightened, so as to lead the product processing speed to be fast.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com