Method for realizing user and network authentication and key distribution based on public key
A network authentication and key distribution technology, which is applied in the field of mutual authentication between users and the network and key distribution in communication, can solve the problems of user identity leakage, authentication vectors are easy to be intercepted, and data signatures are not supported, so as to simplify the key The effect of hierarchy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The method of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
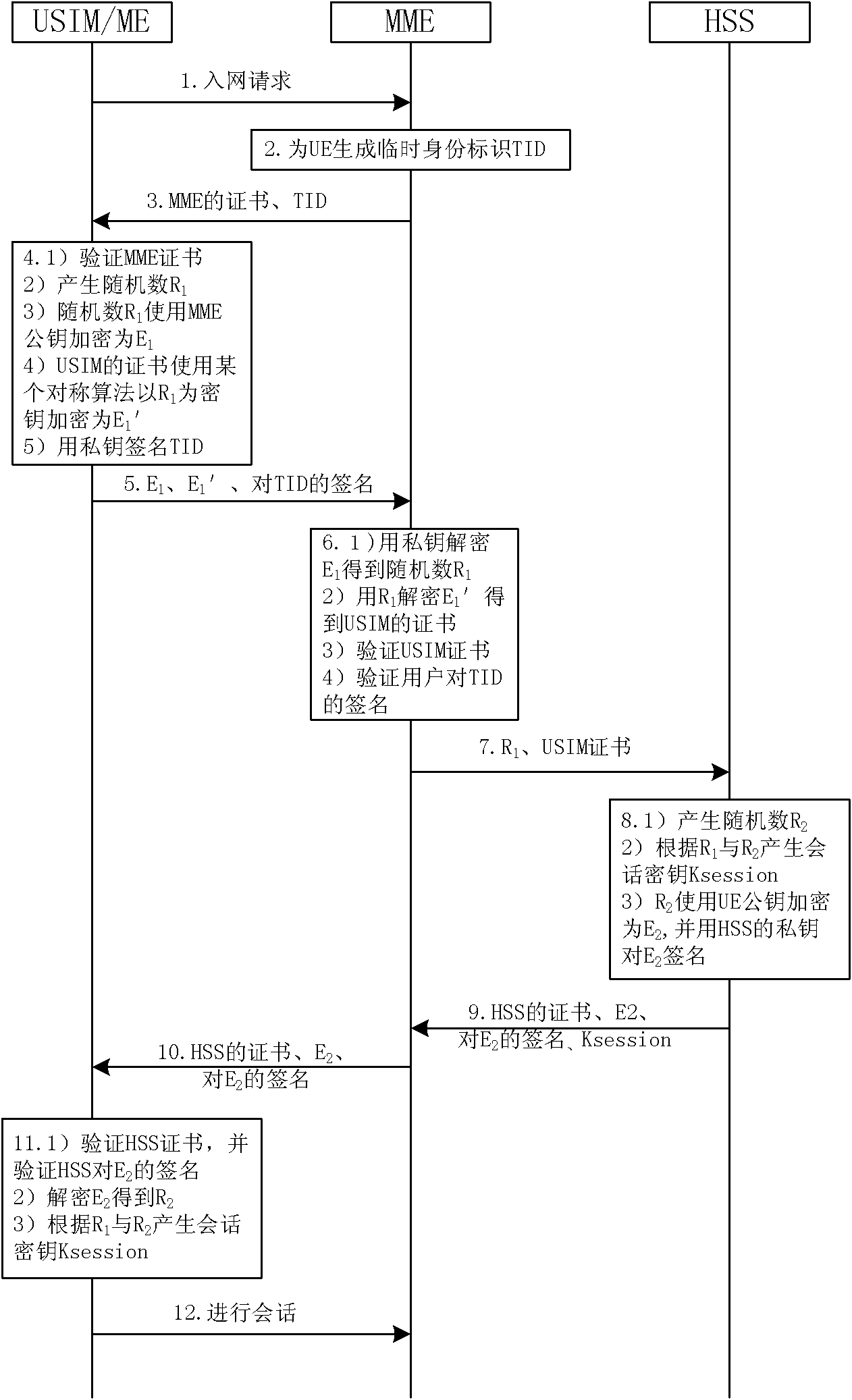
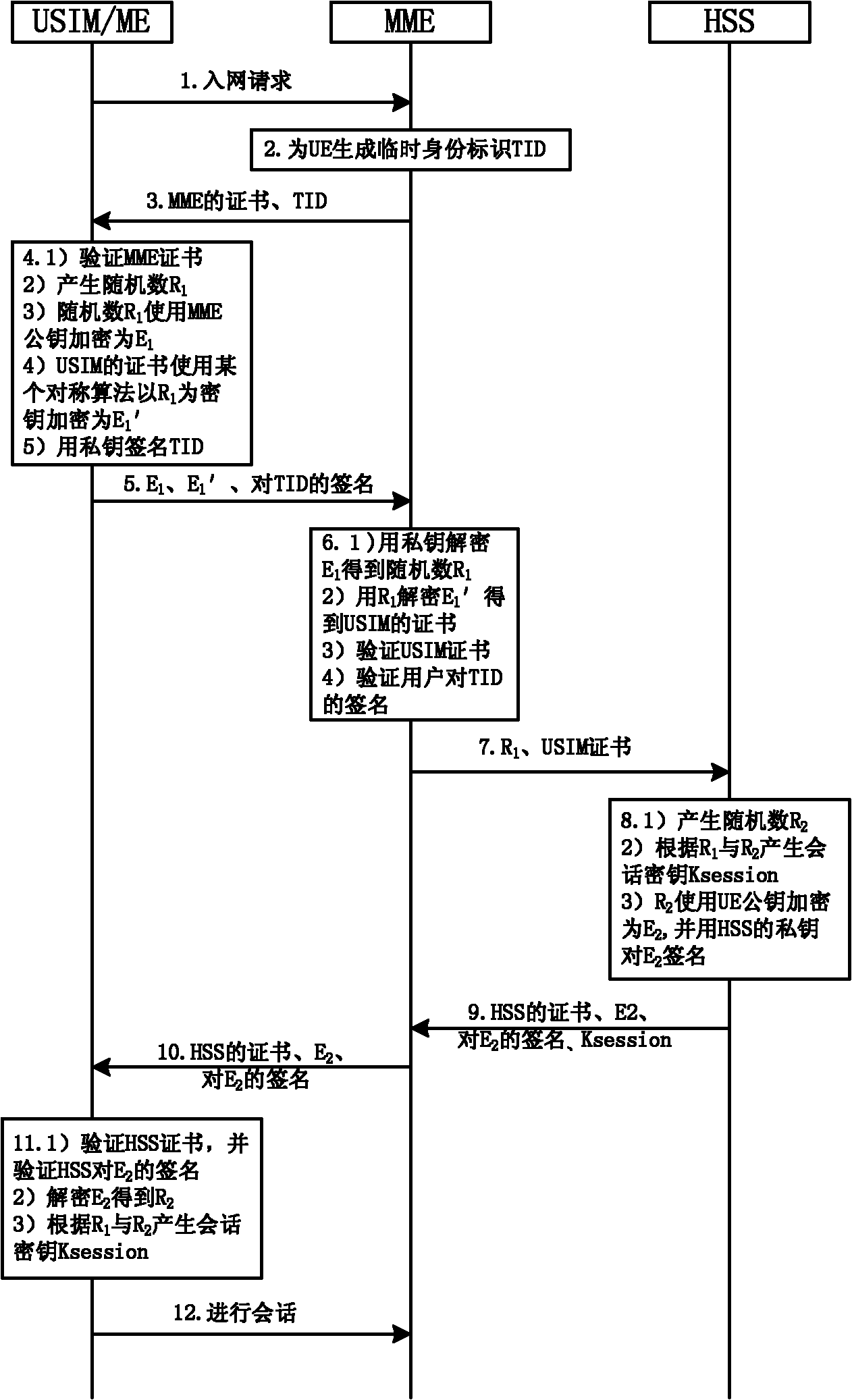
[0041] In the method of the present invention, both the UE (user equipment) and the network can obtain the other party's certificate, thereby using the other party's public key to protect the authentication message, and using their own private key to sign the message. After the sender's message is transmitted to the receiver, the receiver uses the sender's public key to perform signature verification, and then uses the receiver's private key to decrypt the message. In this way, two-way authentication between the user and the network can be achieved.
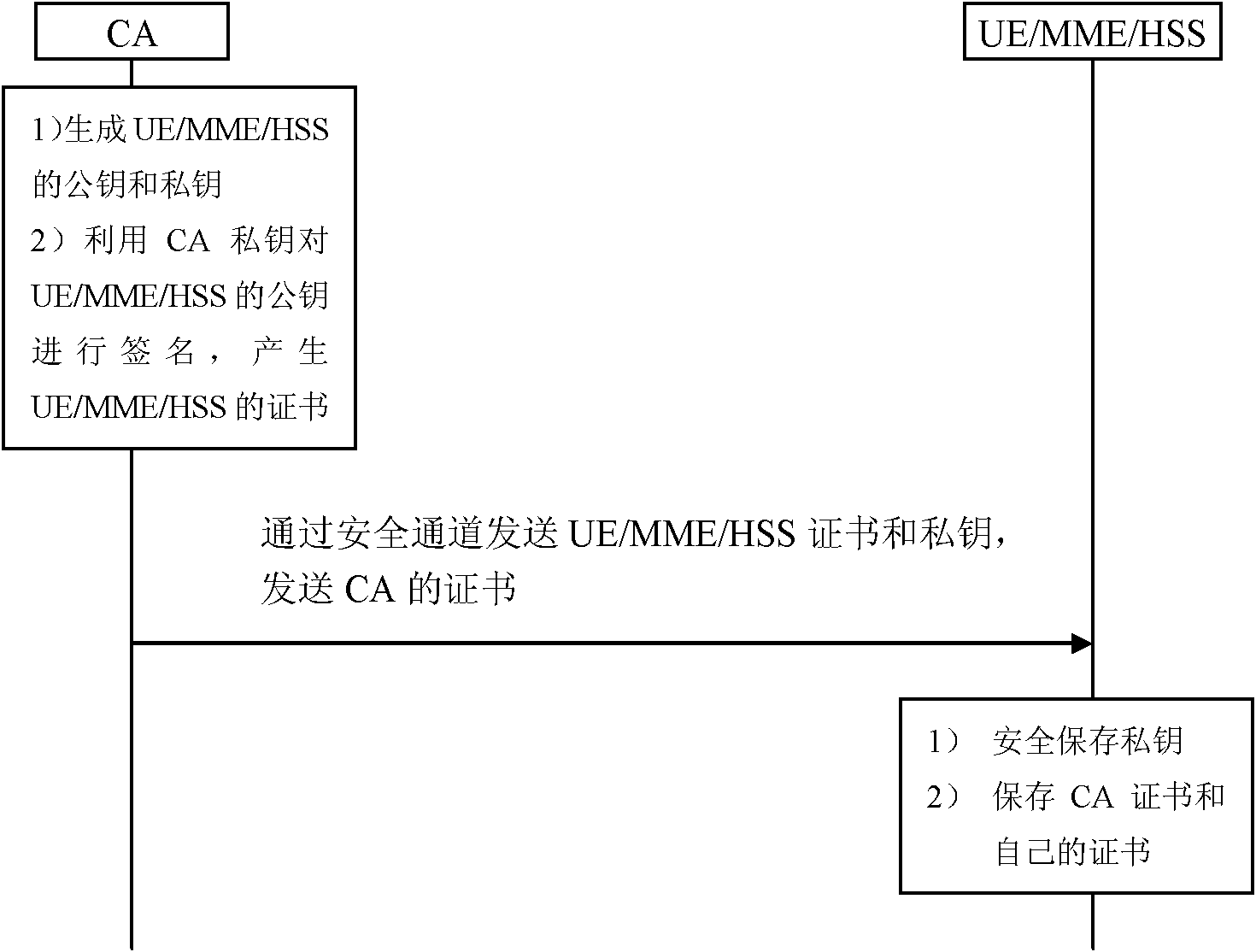
[0042] The present invention is based on the public key authentication and key distribution mechanism, and the premise is that a set of public key infrastructure PKI needs to be configured in the communication network. On this basis, as figure 1 As shown, the CA generates the pub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com