Detection method for abnormal user in social network based on network mapping
A network mapping and social network technology, applied in the field of network data detection, can solve the problems of low accuracy, inability to accurately detect, and difficult to distinguish abnormal users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described below in conjunction with specific embodiment:
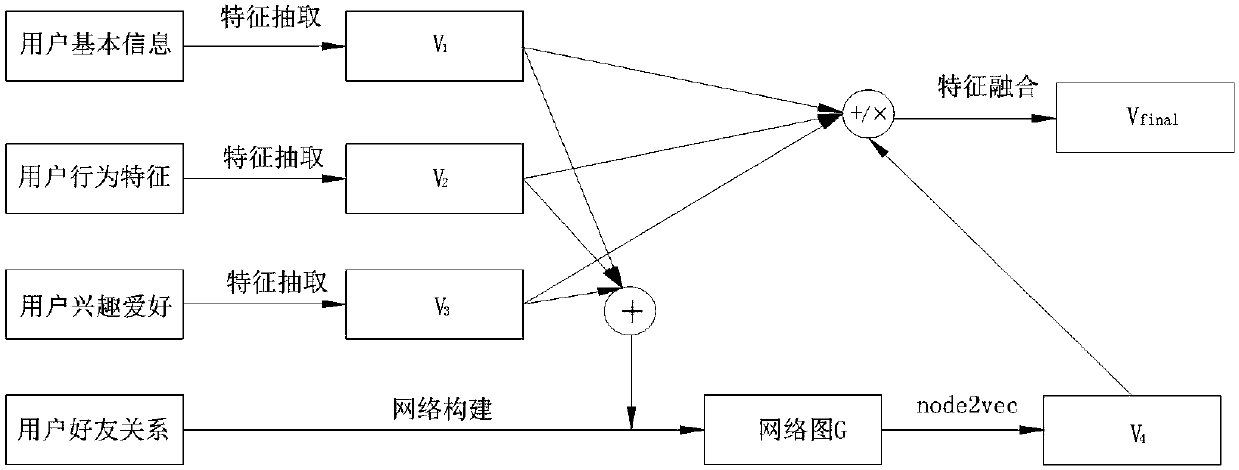
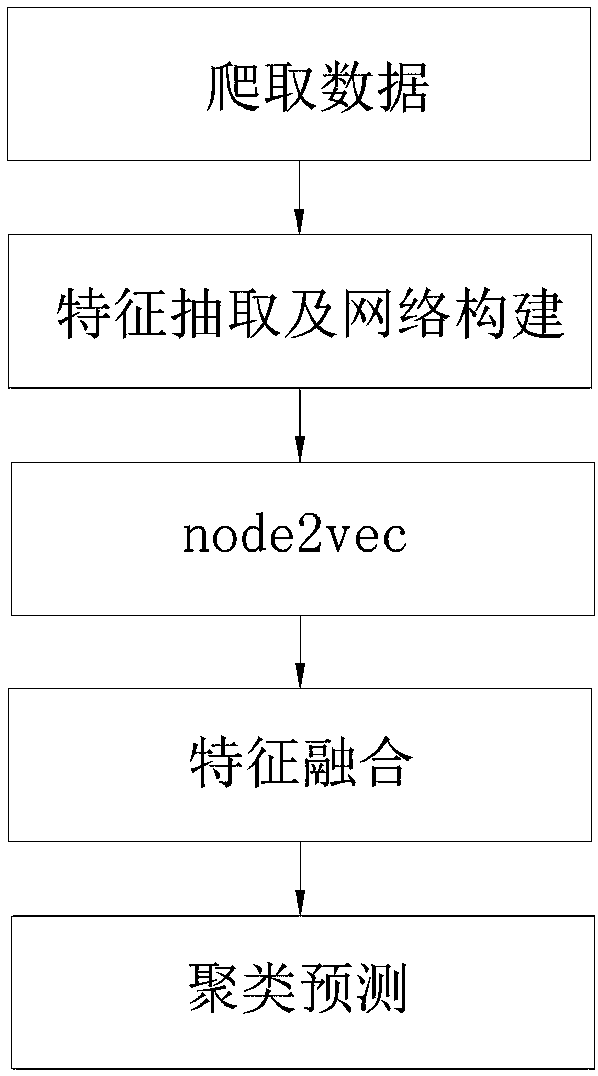
[0051] See attached Figure 1-3 As shown, a method for detecting abnormal users in a social network based on network mapping described in this embodiment includes the following steps:
[0052] S1. Using web crawler technology to crawl the user data of the WeChat social network platform, see Table 1 for detailed data to be crawled.
[0053]
[0054]
[0055] Table 1 Feature types and corresponding user data
[0056] S2. Preprocessing the crawled user data to construct a user social relationship network graph G; the preprocessing steps are as follows:
[0057] S21. Divide the crawled user data into four dimensions, which are user basic information, user behavior characteristics, user hobbies, and user friendship;
[0058] S22. The user data in the three dimensions of user basic information, user behavior characteristics, and user interests and hobbies described in ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com