A dynamic host configuration protocol monitoring and protection method and system
A dynamic host configuration and protocol technology, applied in transmission systems, electrical components, etc., can solve problems such as address exhaustion, DHCP user's MAC address/IP address theft, and failure to assign IP addresses to DHCP clients, so as to prevent starvation attack, prevent spoofing attack, and guarantee the effect of normal network connection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
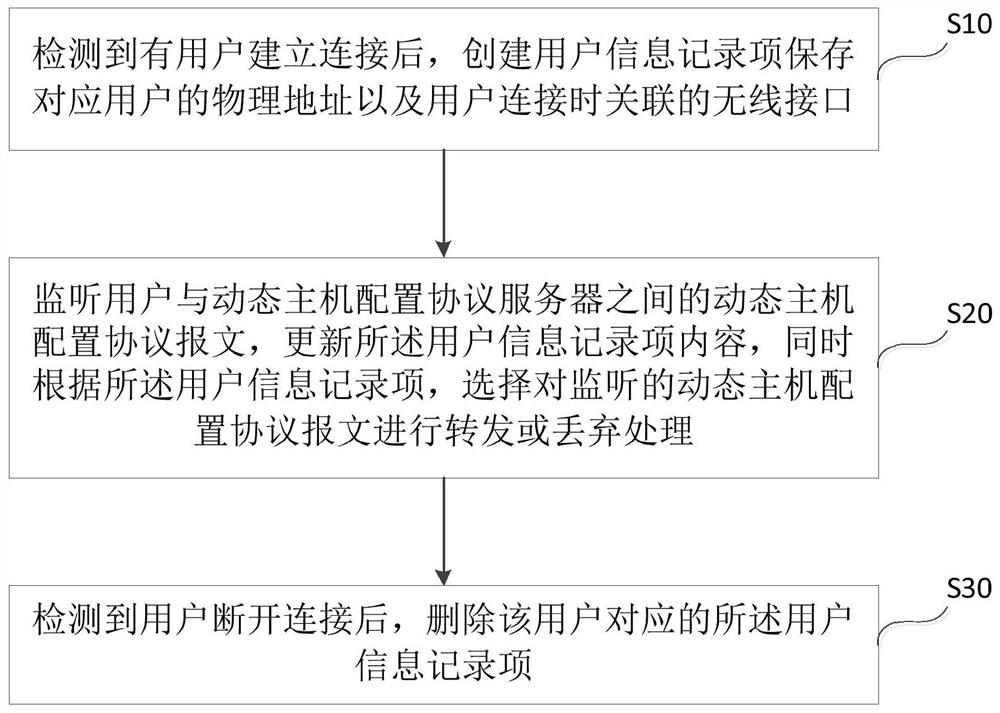
[0053] Such as figure 1 As shown, this embodiment provides a dynamic host configuration protocol monitoring and protection method, which is applied to a wireless access point, commonly known as AP in English, and the method includes:
[0054] S10: After detecting that a user has established a connection, create a user information record item to save the physical address of the corresponding user and the wireless interface associated when the user connects;
[0055] In this step, after it is detected that a user establishes a connection, it is detected that a user (STA) is online, rather than a previously connected STA. Specifically: STA1 finds the wireless network name (SSID) of AP1 and associates it with the SSID of AP1. AP1 will receive the CLIENT_IN message that STA1 goes online. After STA1 goes online (STA1 associates with AP1), AP1 will create a user information record corresponding to STA1. Item, which stores the physical address (that is, the MAC address) of STA1 and t...
Embodiment 2
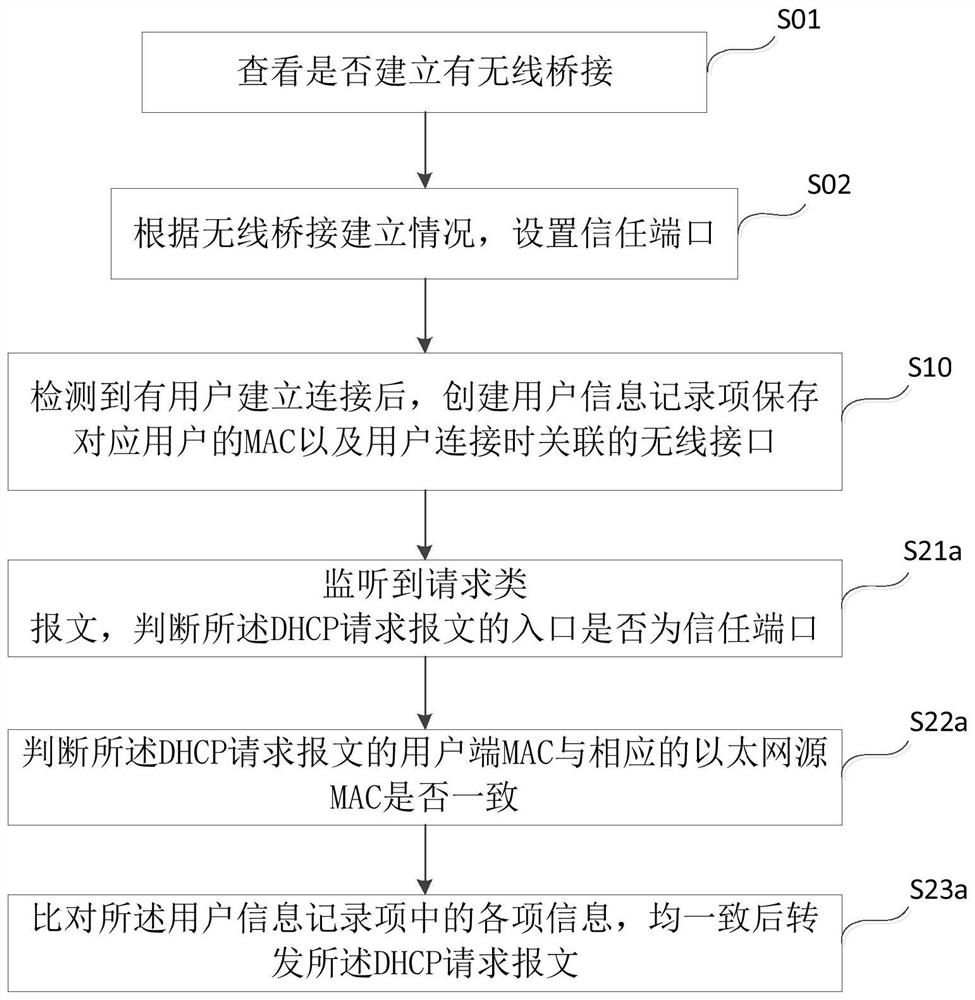
[0063] Such as figure 2 As shown, the difference between this embodiment and the previous embodiments is that this embodiment provides a more detailed method that can prevent terminals from forging DHCP messages (including forging DHCP messages of other terminals under the same wireless interface) to cheat or starve to death. method of attack.
[0064] Before said step S10 includes:
[0065] S01: check whether a wireless bridge is established;
[0066] Considering that wireless bridging is generally used to bridge wired APs to APs in widening wireless networks at present, and STAs are connected to wireless bridging APs, and information exchange is also required. However, due to the limitation of the data transmission distance, the wireless bridged AP cannot actively monitor the DHCP message, and can only transmit it through the wired AP.
[0067] S02: Set a trusted port according to the establishment of the wireless bridge.
[0068] In this step, whether the wireless brid...
Embodiment 3
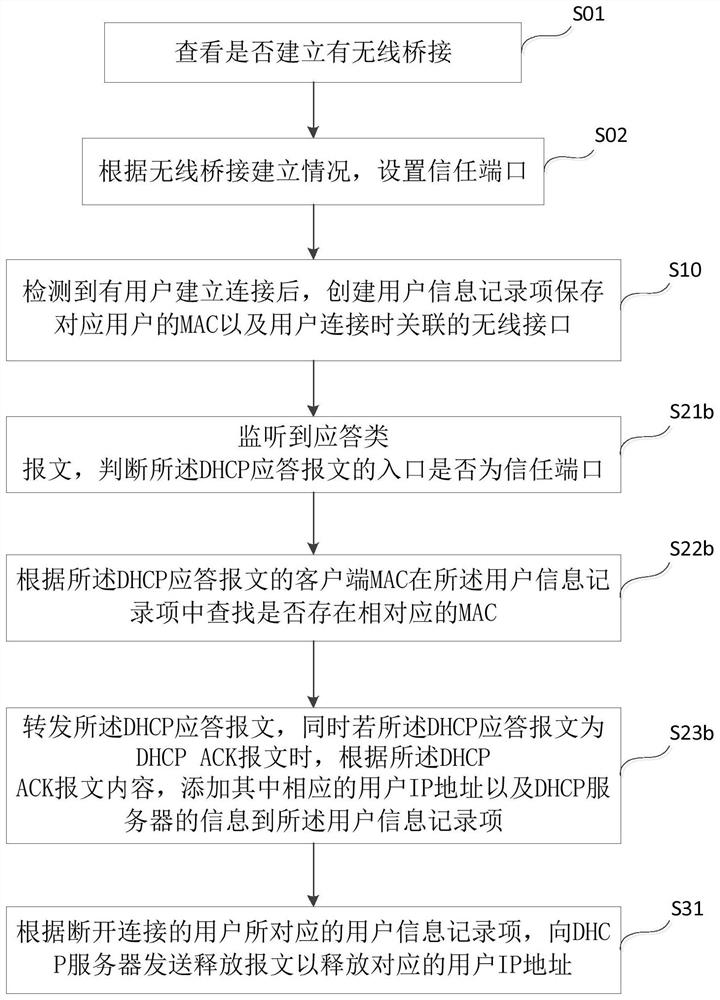
[0081] Such as image 3 As shown, the difference between this embodiment and Embodiment 2 is that this embodiment also provides a method that can prevent the terminal from frequently going online and offline by modifying the local physical address and prevent the terminal from forging a DHCP server. DHCP response message, perform the following steps:
[0082] S21b: Determine whether the entry of the DHCP response message is a trusted port, if not, discard the DHCP response message, and if so, execute S22b;
[0083] S22b: Search whether there is a corresponding MAC in the user information record item according to the client MAC of the DHCP response message, if not, discard or forward according to the establishment of the wireless bridge, and if it exists, execute Step S23b;
[0084] S23b: Forward the DHCP response message, and if the DHCP response message is a DHCP ACK message in response to finding a corresponding lease record, add the corresponding user IP address and DHCP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com