A routing method with metadata privacy protection and source accountability capabilities
A privacy protection and source accountability technology, applied to electrical components, digital transmission systems, and key distribution, can solve problems such as inability to explain EphID, reduce anonymity sets, and lack of accountability capabilities, so as to improve verification efficiency and prevent address spoofing Attacks, broad accountability effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
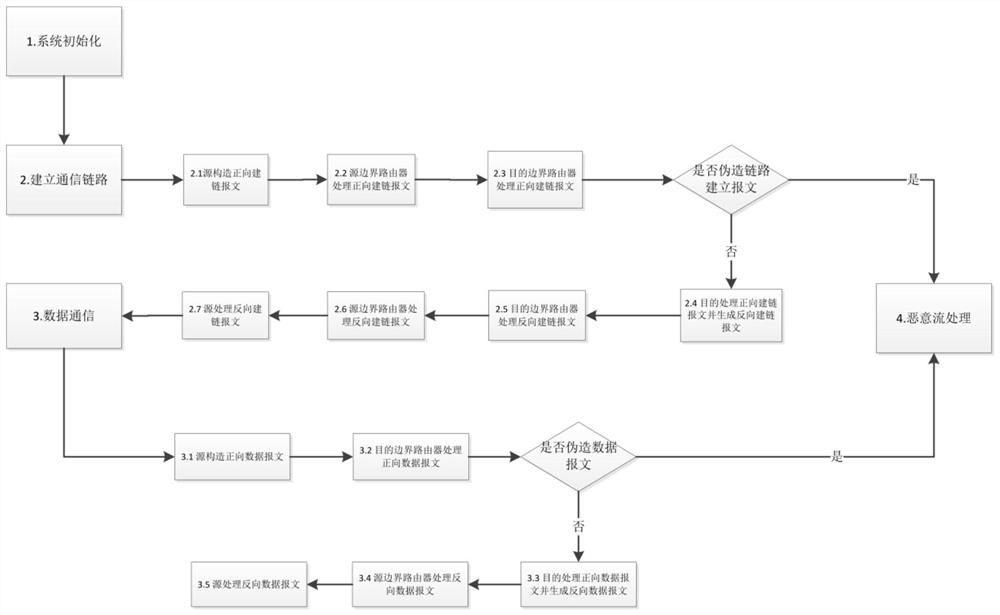
[0108] The present invention will be further described below in conjunction with accompanying drawing of description and specific preferred embodiment, figure 1 It is a general flowchart of the present invention, and the steps of the present invention include:
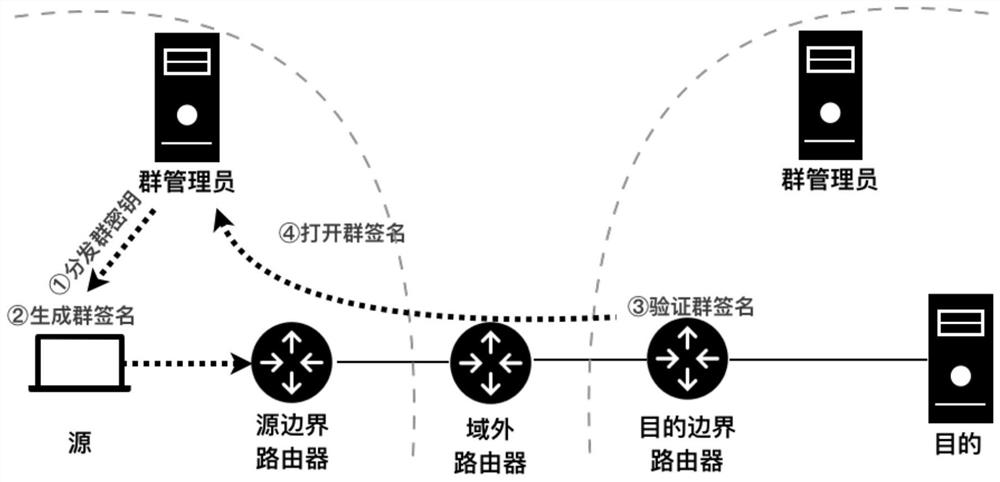
[0109] The first step: system initialization. figure 2 The network topology of the present invention is shown. Before opening the session, the group administrator first generates key keys in the group: group management private key, group public key and group user private key, and distributes the group user private key to legitimate users in the group. At the same time, the nodes on each path are initialized.
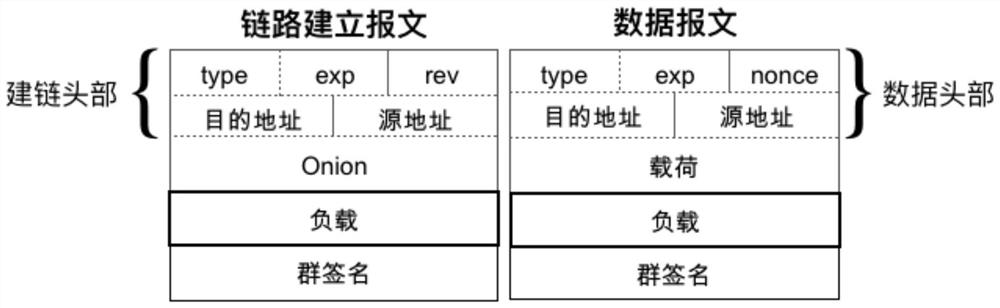
[0110] The second step: link establishment. The flow chart of message forwarding in the link establishment phase is as follows: Figure 4 shown. Link establishment packet structure reference image 3 .
[0111] 2.1) The source S first constructs the forward link building message SP → . Source S first co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com