Early warning method and device for ARP table entry spoofing attack in local area network
An ARP entry and spoofing attack technology, applied in the field of network communication, can solve problems such as user network connection failures, and achieve the effect of preventing spoofing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
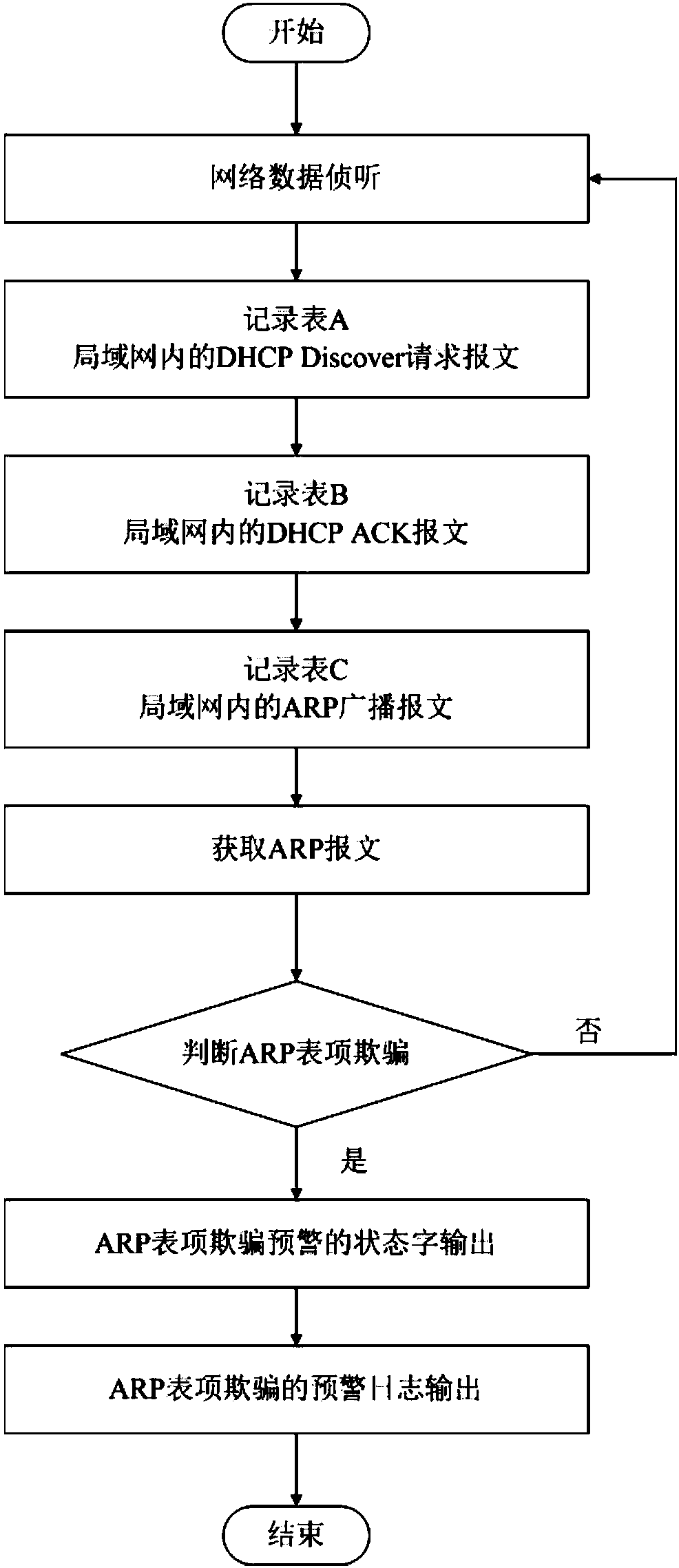
[0015] Embodiment 1: An early warning method for ARP entry spoofing attacks on a local area network, including the following steps:
[0016] S1. Network data interception;
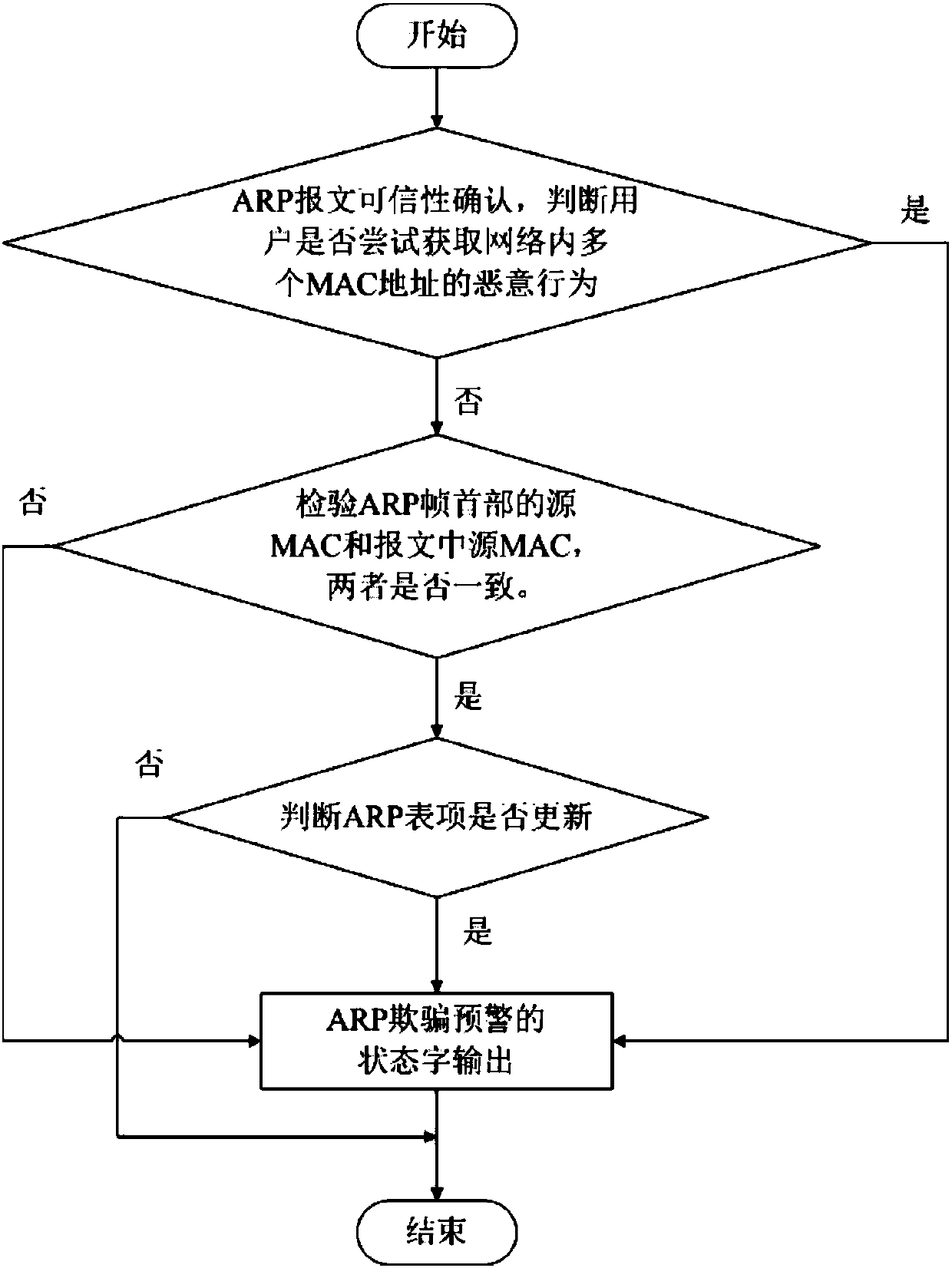
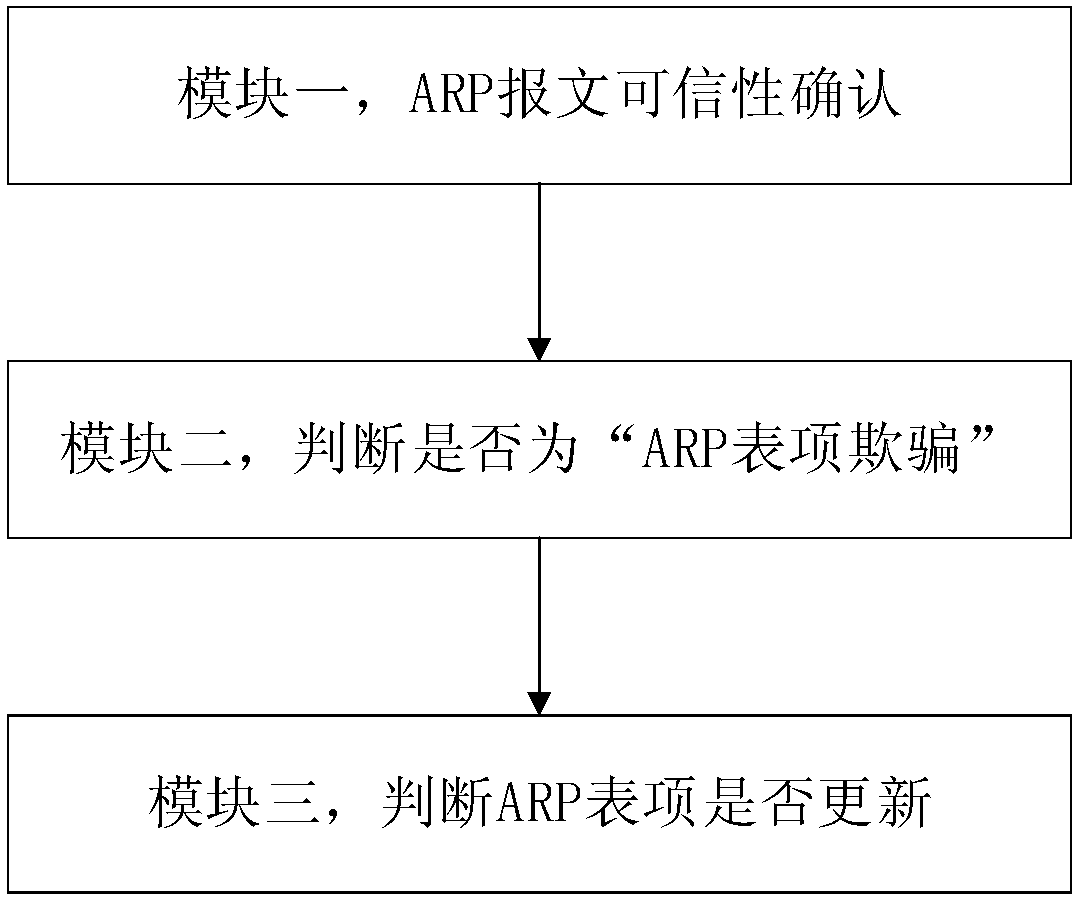
[0017] S2. ARP message credibility confirmation;
[0018] S2.1. When the ARP message is untrustworthy, the ARP entry spoofing early warning judgment is performed;
[0019] S2.2. When the ARP message is credible, analyze the ARP message table entry to determine the ARP table entry spoofing.
[0020] As an embodiment, in the step S1, the network data interception is: obtain the DHCPDiscover request message in the network and record it in table A; obtain the DHCP ACK message in the network and record it in table B; obtain ARP broadcast messages in the network are recorded in Table C.
[0021] As an embodiment, the specific steps of step S2 are: analyzing the IP address of the ARP request packet sent by the user, judging whether it appears in Table A and Table C, and at the same time judging whether it is stored in a st...
Embodiment 2
[0040] Embodiment 2: As a supplement to the technical solution of Embodiment 1, or a separate embodiment, this embodiment provides an early warning method for ARP entry spoofing attacks in a local area network. First listen through network data frames. Obtain the DHCPDiscover request message in the network and record it in Table A; at the same time, obtain the DHCPACK message and record it in Table B; at the same time, obtain the ARP broadcast message in the network and record it in Table C. Then compare the data in the above record table to confirm the credibility of the ARP message, analyze the ARP message table entries, and analyze whether the source MAC in the header of the ARP frame and the source MAC in the message are consistent. Whether to update the ARP table entry and whether it meets the characteristics of ARP spoofing. If it meets the characteristics of ARP spoofing, output the status word of the ARP spoofing attack alarm. Then output the log of ARP spoofing attac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com