Patents
Literature
953results about How to "Reduce access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
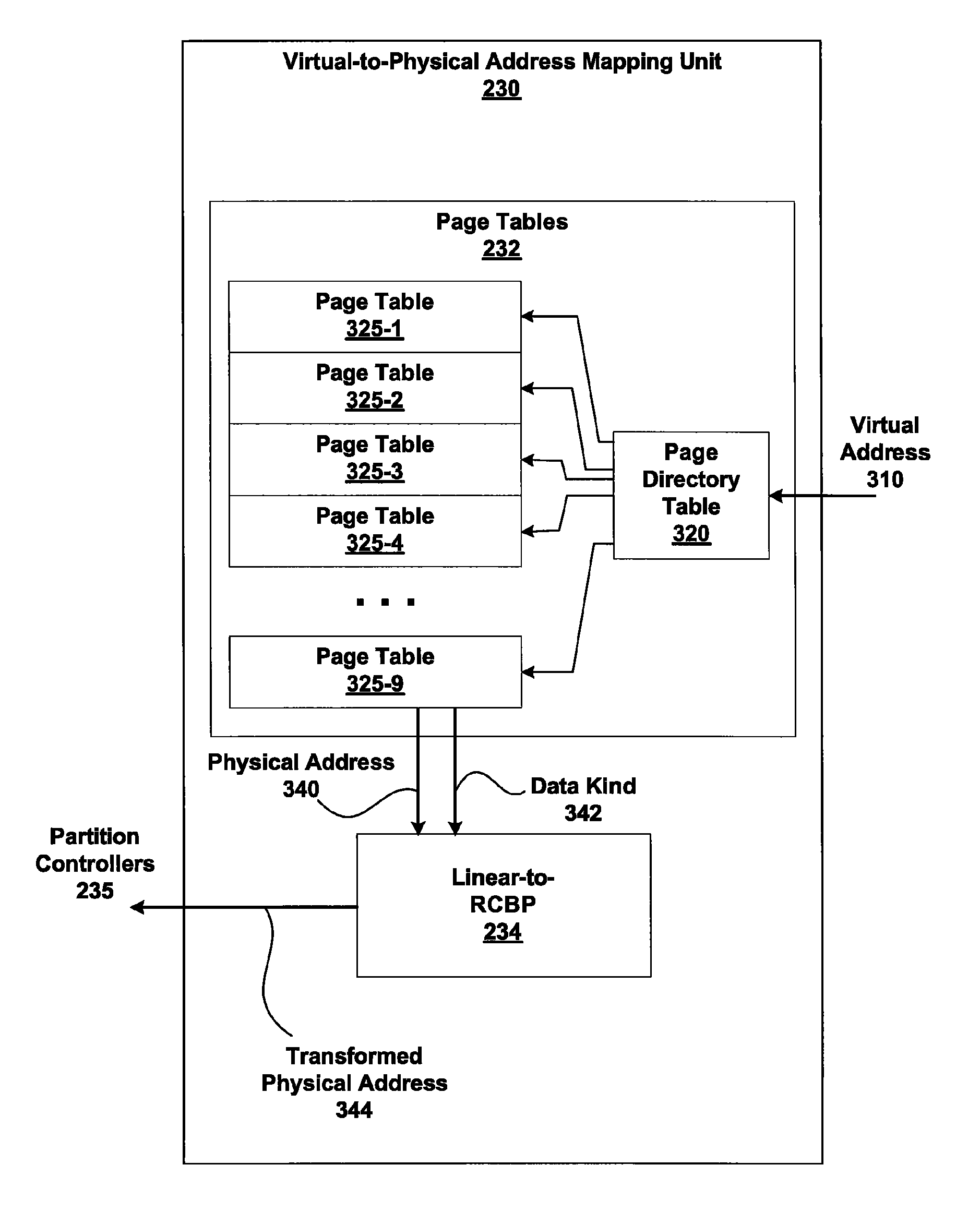
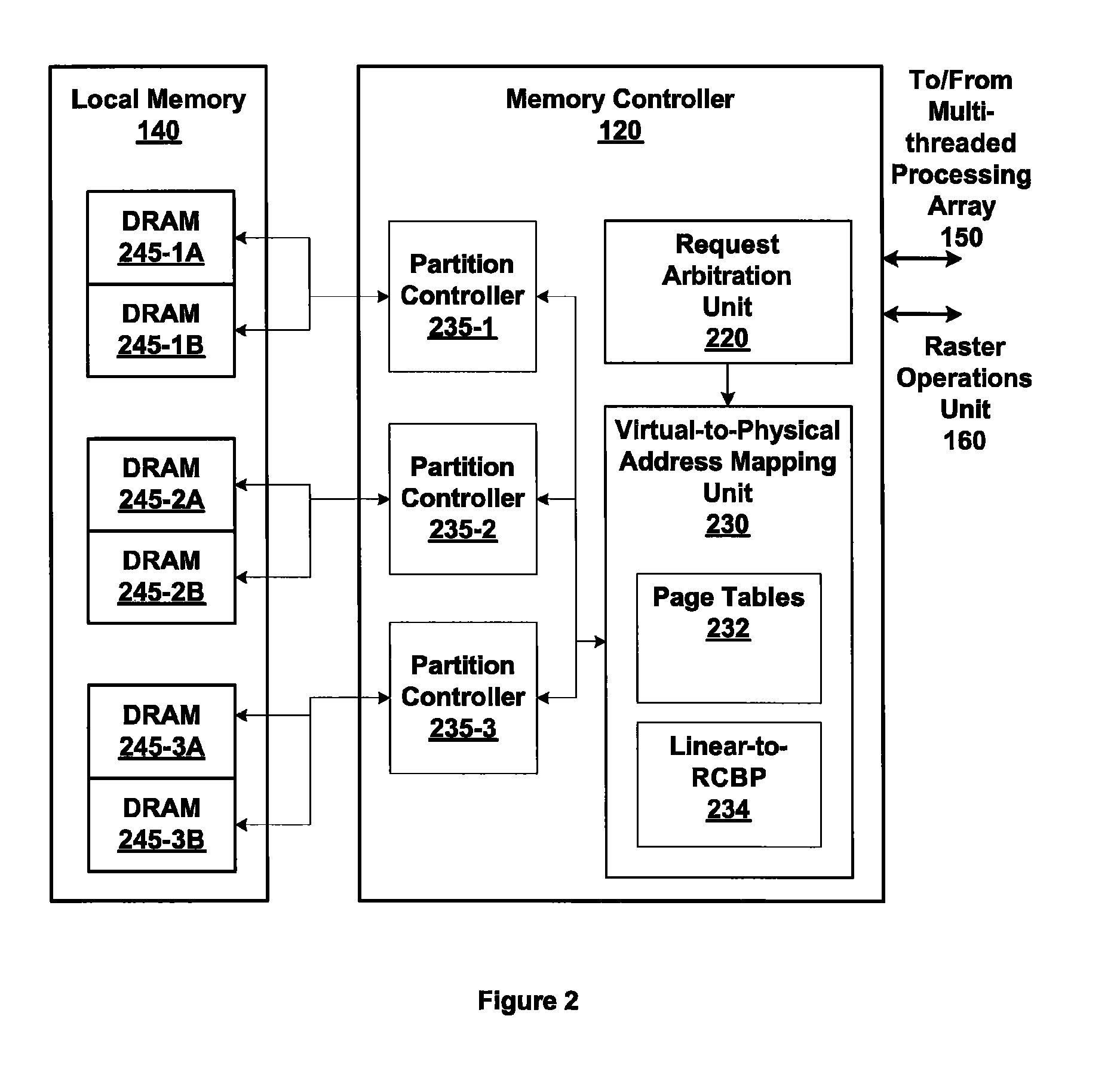
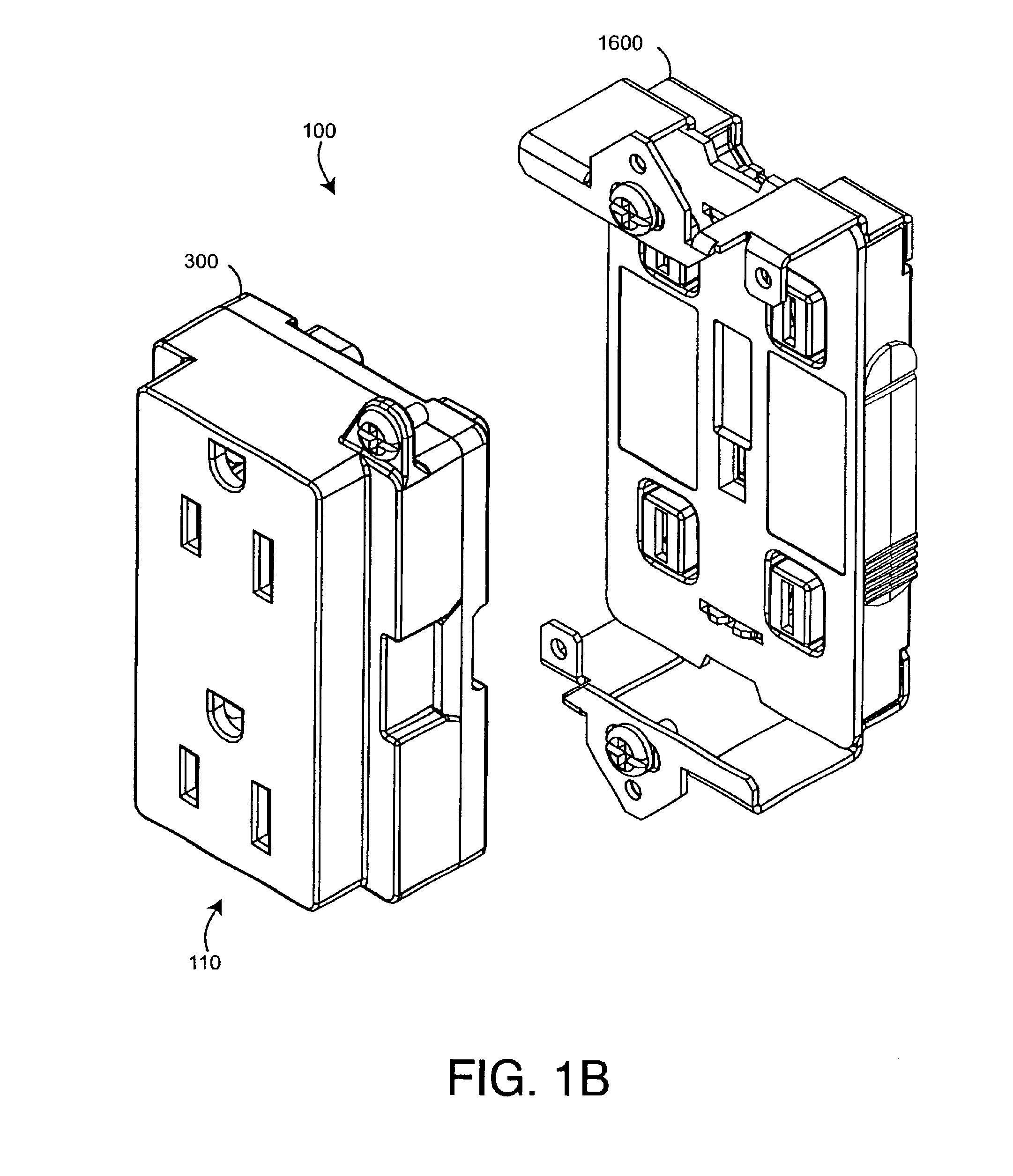
Memory addressing controlled by PTE fields
ActiveUS7805587B1Reduce accessMemory adressing/allocation/relocationComputer security arrangementsMemory addressDram memory
Embodiments of the present invention enable virtual-to-physical memory address translation using optimized bank and partition interleave patterns to improve memory bandwidth by distributing data accesses over multiple banks and multiple partitions. Each virtual page has a corresponding page table entry that specifies the physical address of the virtual page in linear physical address space. The page table entry also includes a data kind field that is used to guide and optimize the mapping process from the linear physical address space to the DRAM physical address space, which is used to directly access one or more DRAM. The DRAM physical address space includes a row, bank and column address. The data kind field is also used to optimize the starting partition number and partition interleave pattern that defines the organization of the selected physical page of memory within the DRAM memory system.
Owner:NVIDIA CORP
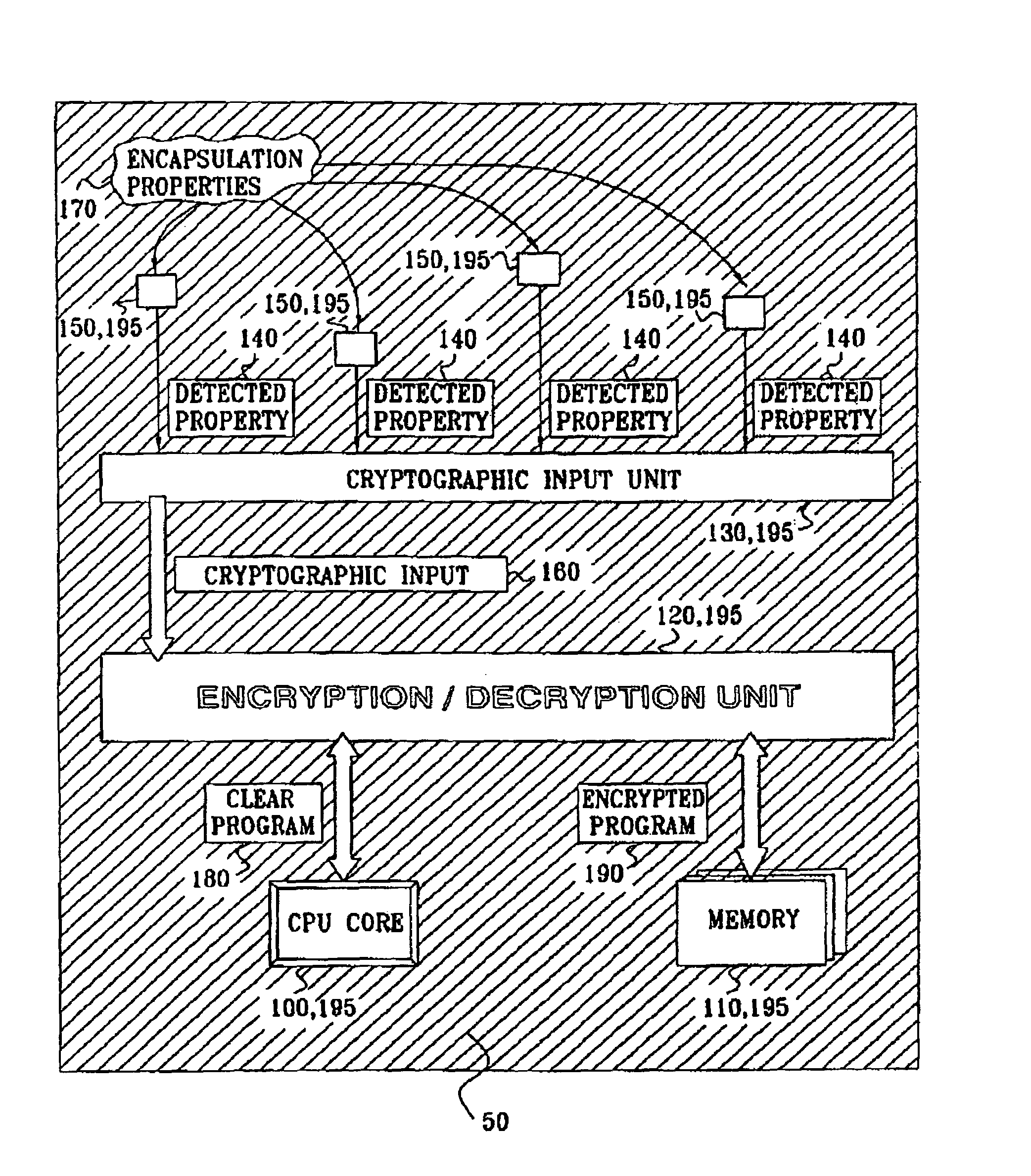
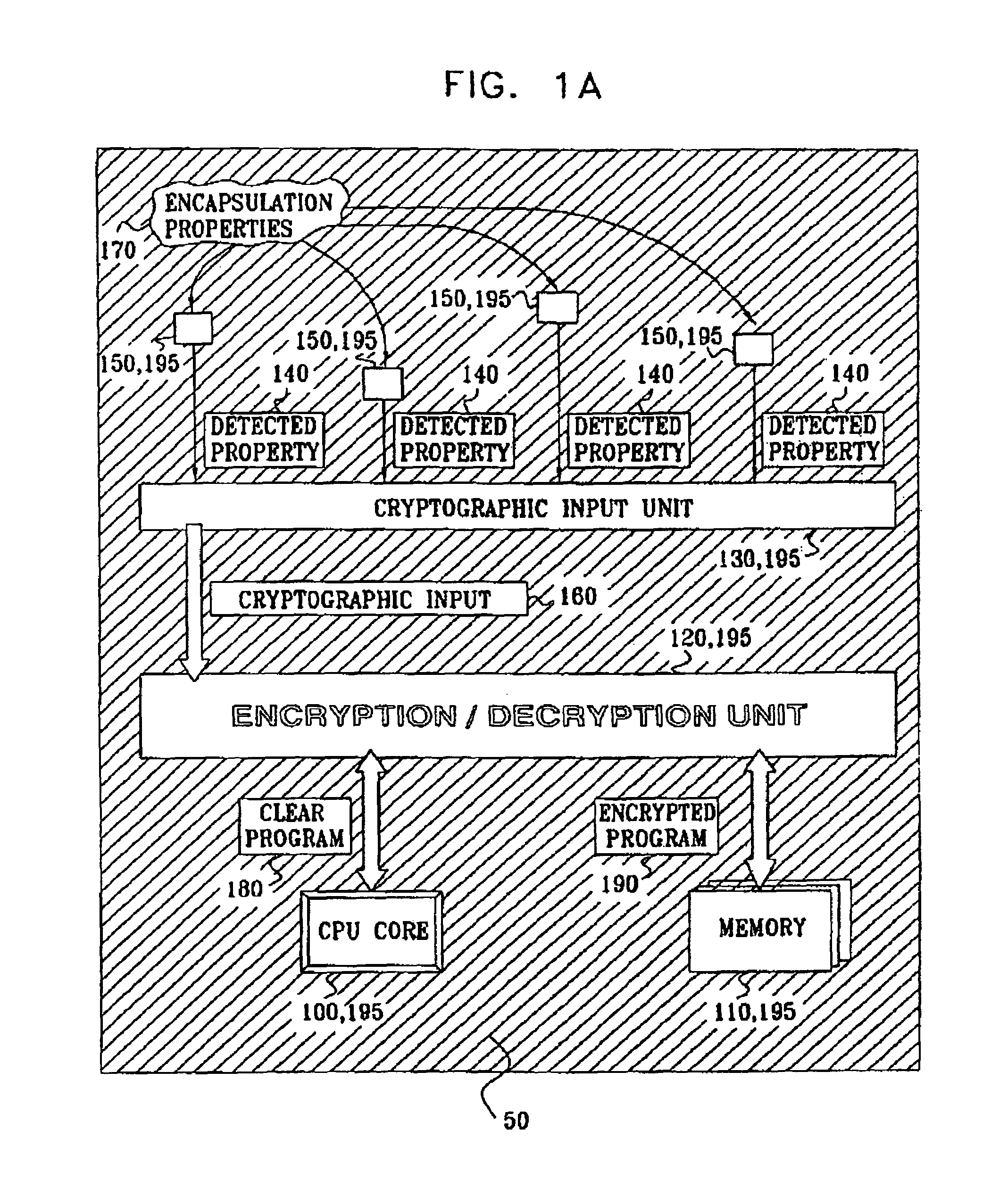
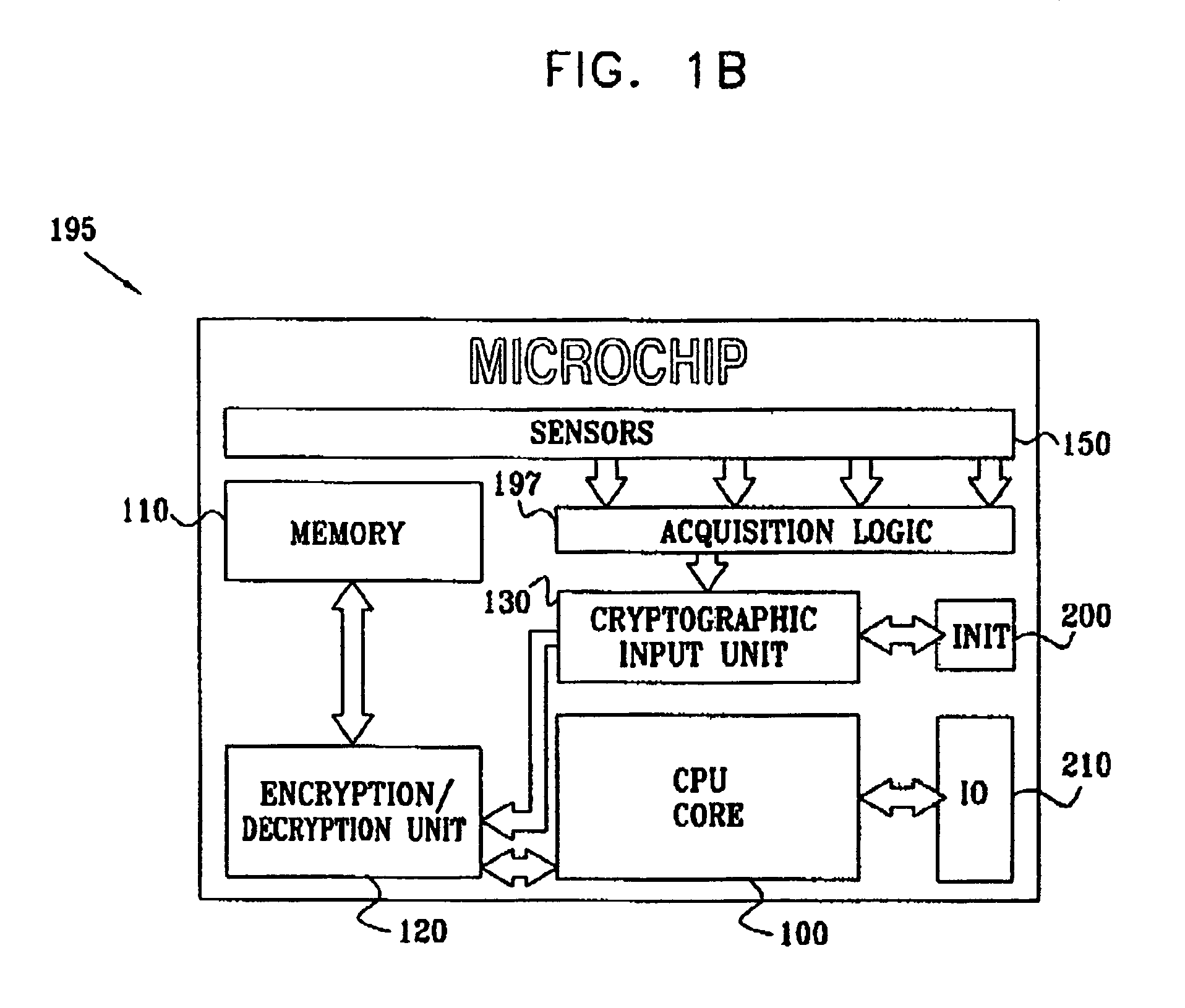
Anti tamper encapsulation for an integrated circuit
InactiveUS7005733B2Protected contentReduce accessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareEncryption
An integrated circuit device comprising: a circuit which uses encryption; and an encapsulation packaging layer; in which the circuit is responsive to at least one physical parameter of the encapsulation to apply the encryption and / or decryption by reading the key therefrom, so that tampering with the encapsulation to gain access to the circuit causes the encryption and / or decryption to fail.
Owner:UNIVERSAL IMAGING IND LLC
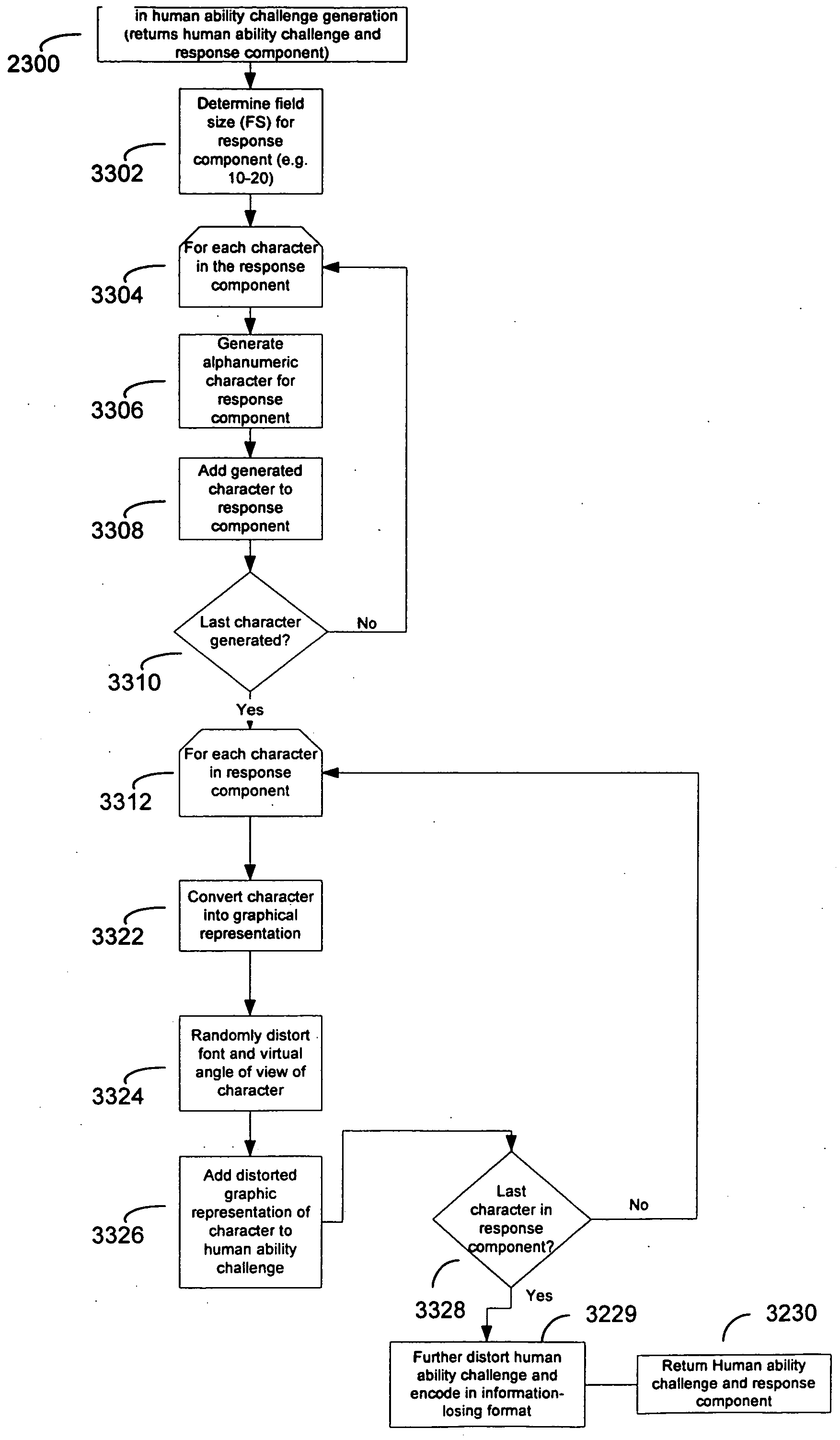
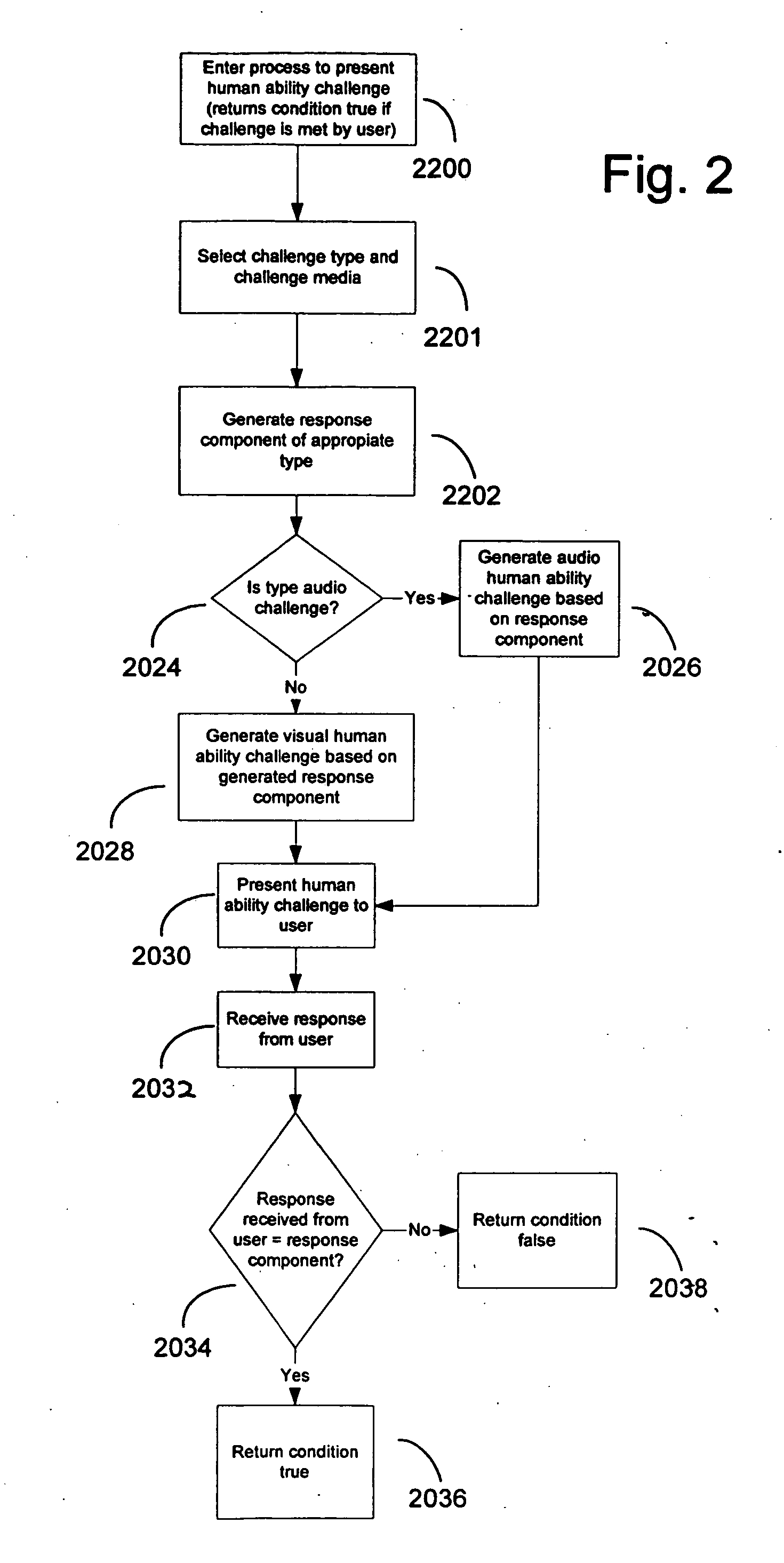
Method and system for discriminating a human action from a computerized action
InactiveUS20050114705A1Reduce it effectivenessEnhanced authenticationDigital data processing detailsUser identity/authority verificationCognitive skillNatural language
A method and system are disclosed for discriminating automatic computerized action from a human performed action. The invention is based on applying human advantage in applying sensory and cognitive skills to solving simple problems that prove to be extremely hard for computer software. Such skills include, but are not limited to processing of sensory information such as identification of objects and letters within a noisy graphical environment, signals and speech within an auditory signal, patterns and objects within a video or animation sequence. Human skills also include higher level cognitive processing such as understanding natural language and logical assignments. The method for discriminating between humans and computerized actions can be used during authentication, to limit access by automated agents, and for confirmation of actions.
Owner:IBM CORP
Valve port and method for vascular access
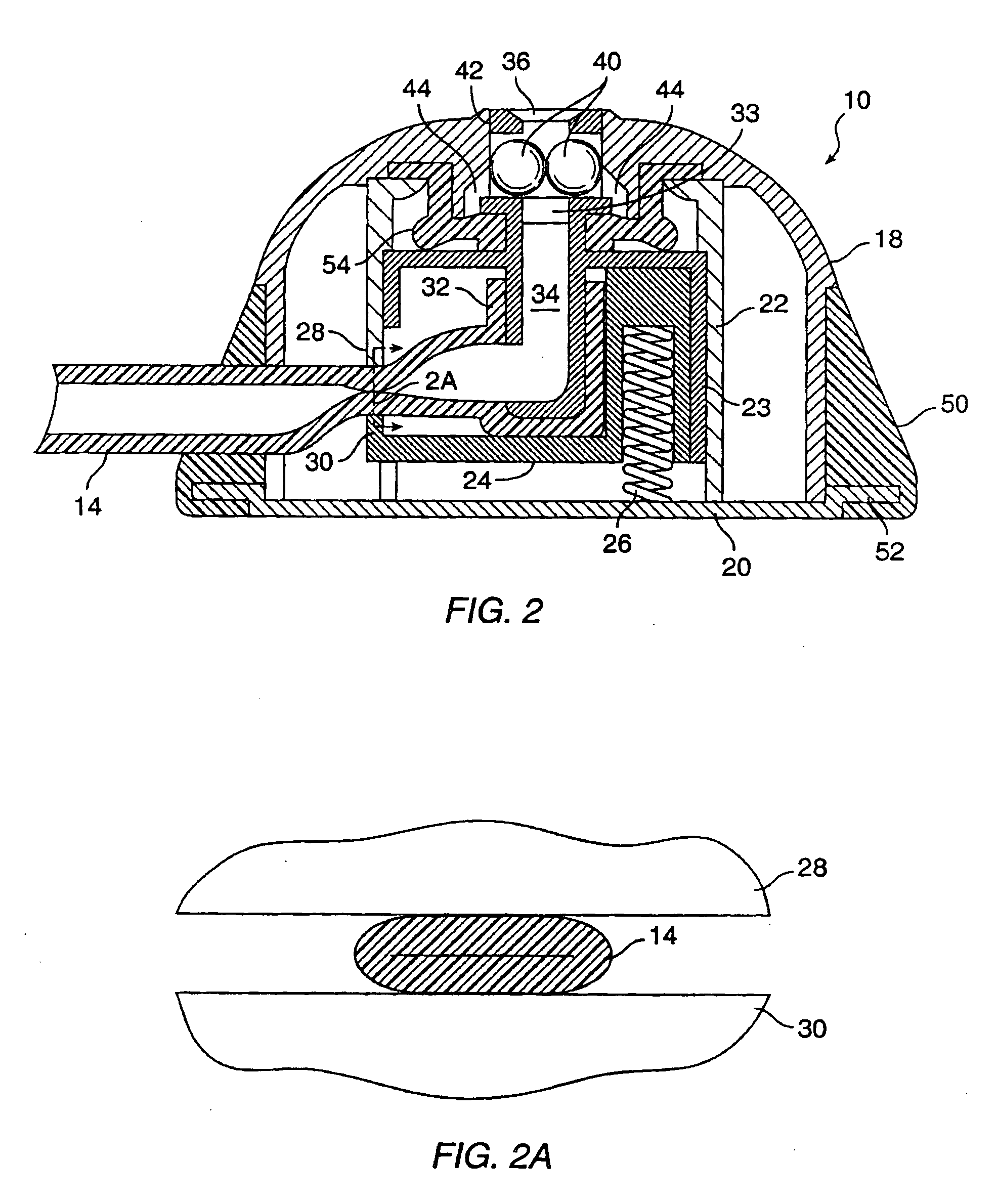
InactiveUS7056316B1Reduce accessReduce riskPharmaceutical delivery mechanismMedical devicesLocking mechanismBiomedical engineering
Owner:VASCA
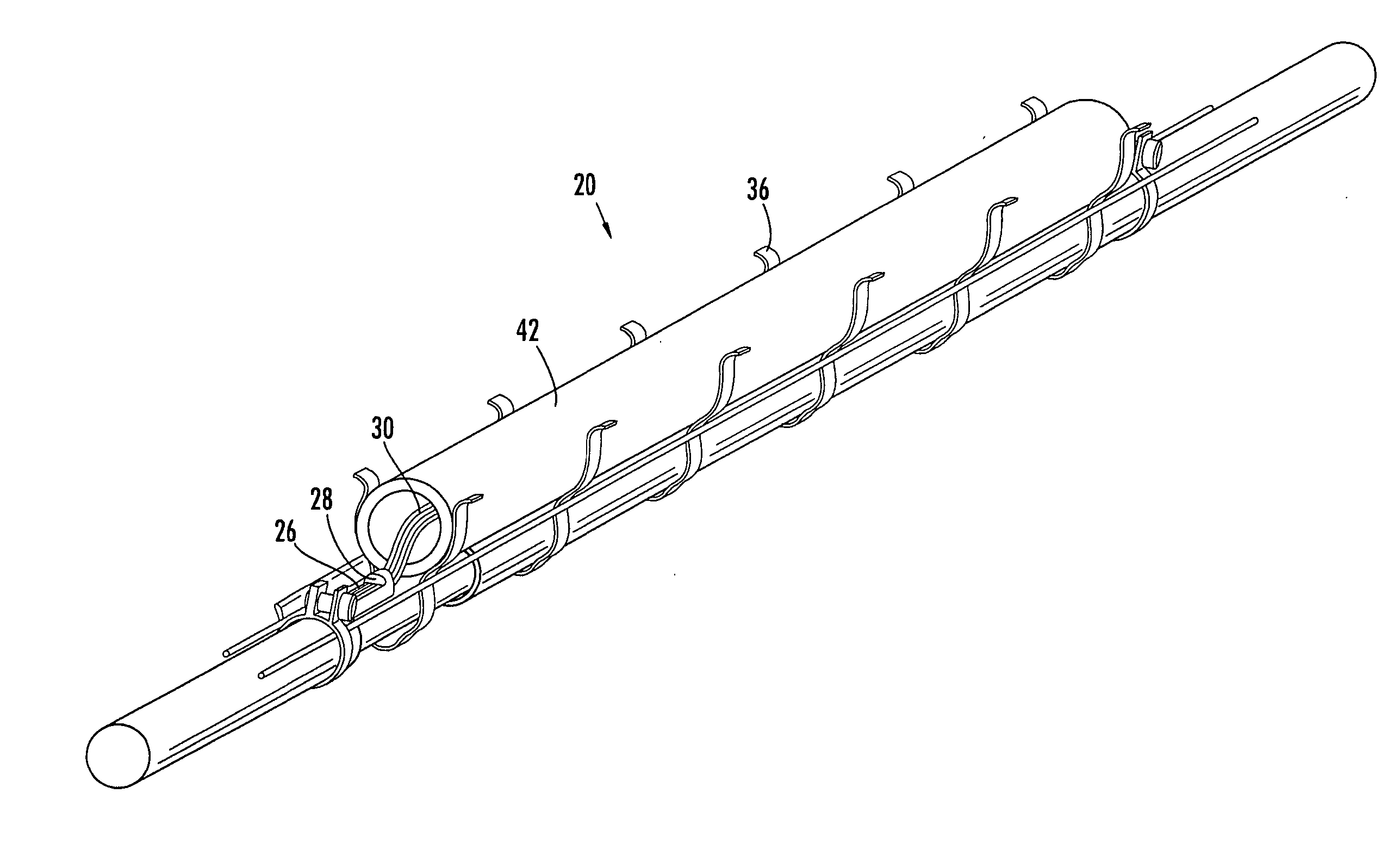
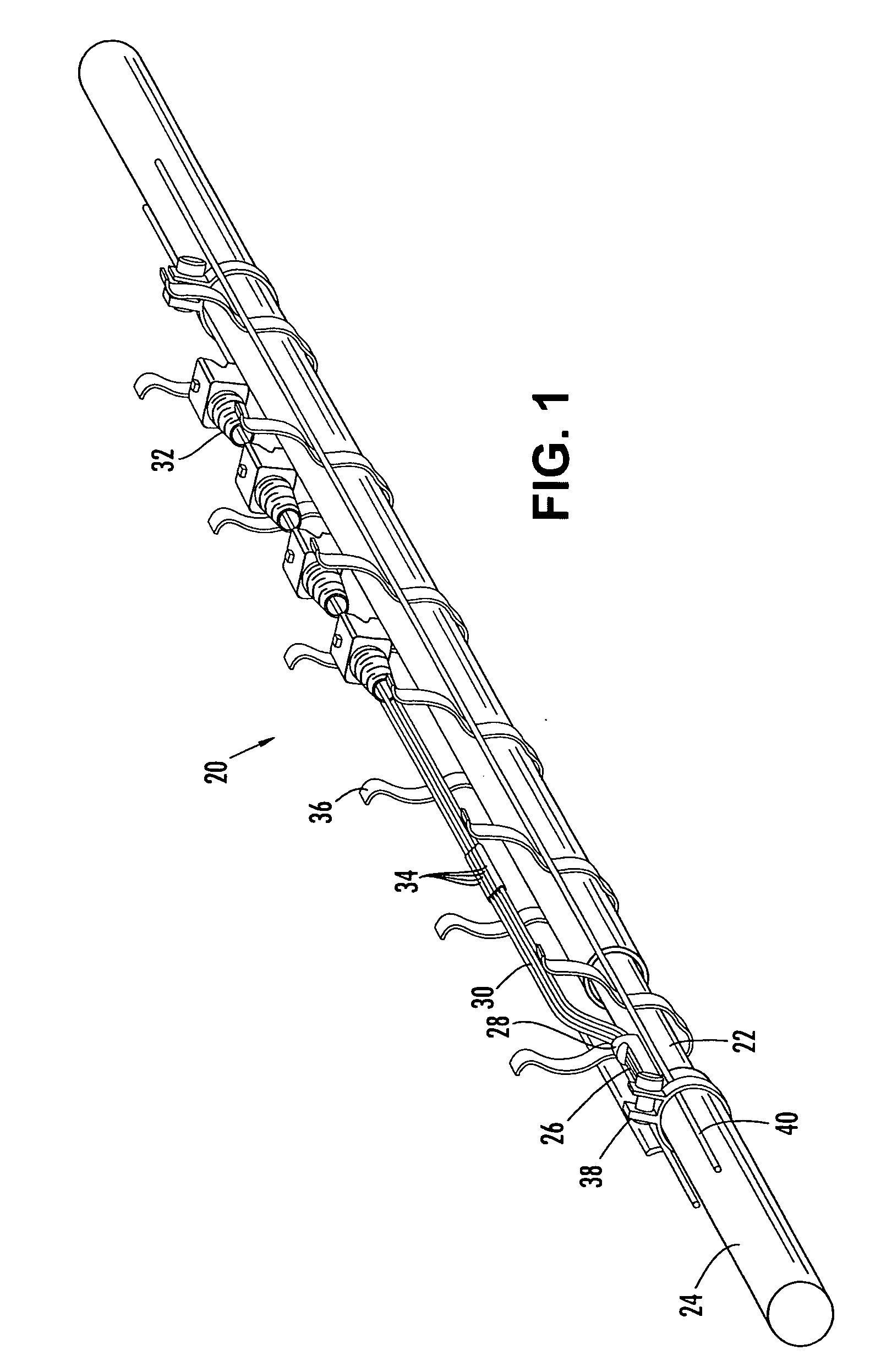
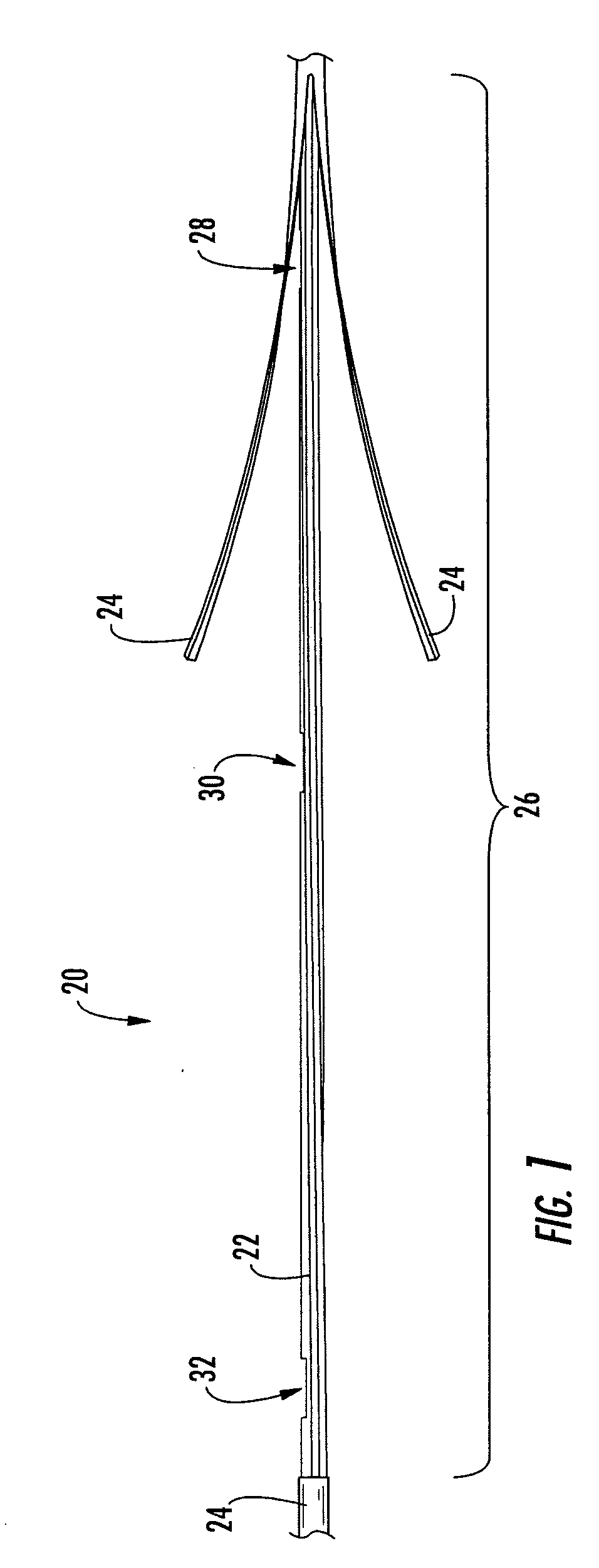
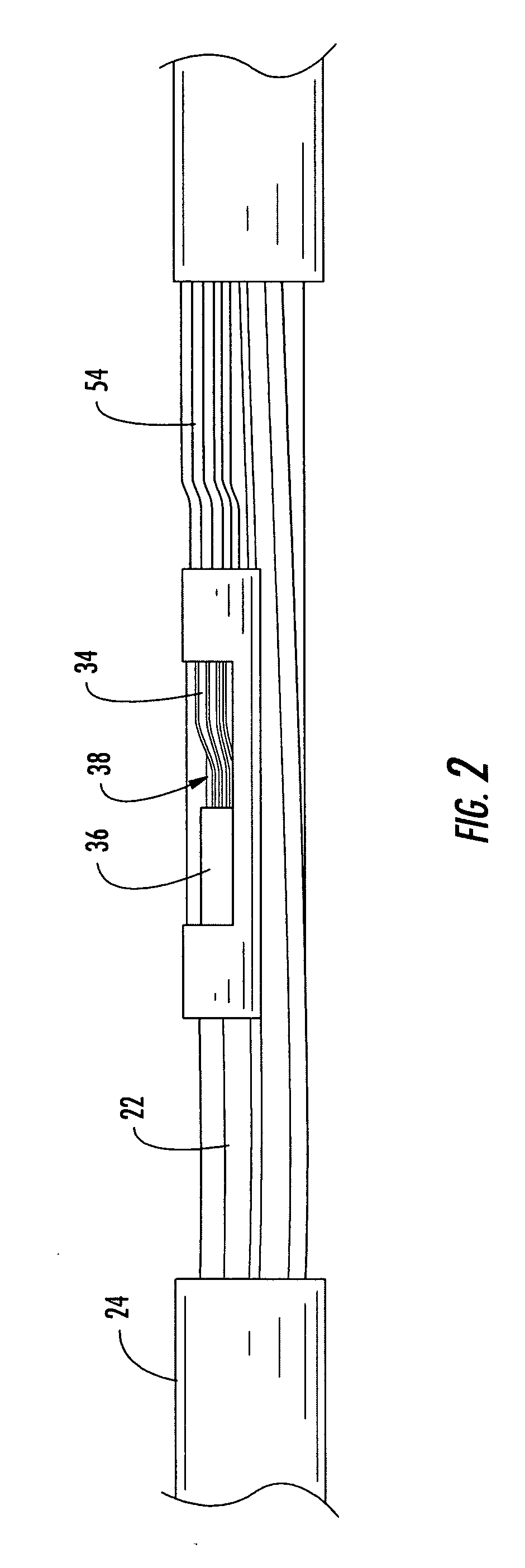
Pre-connectorized fiber optic distribution cable
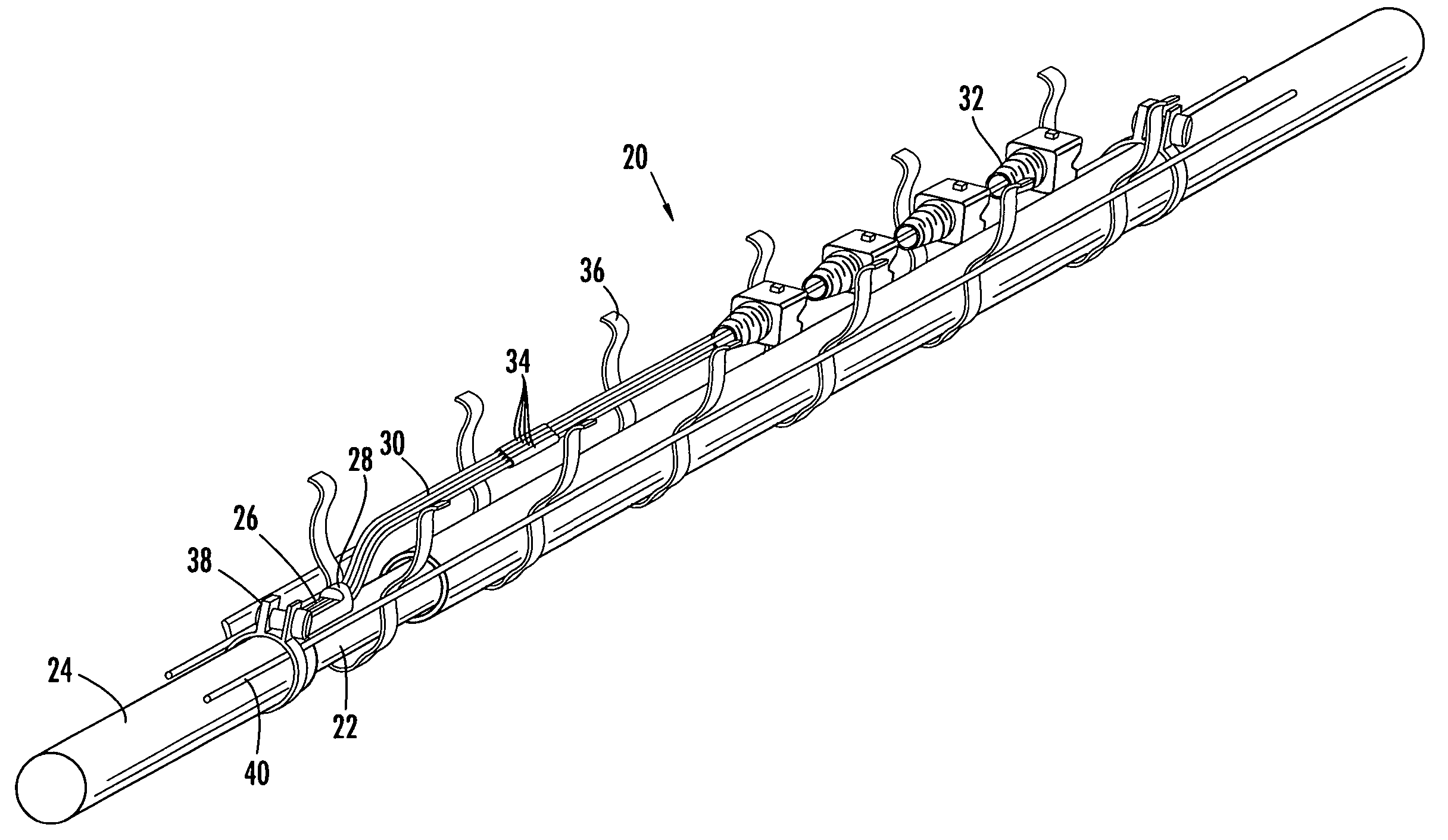
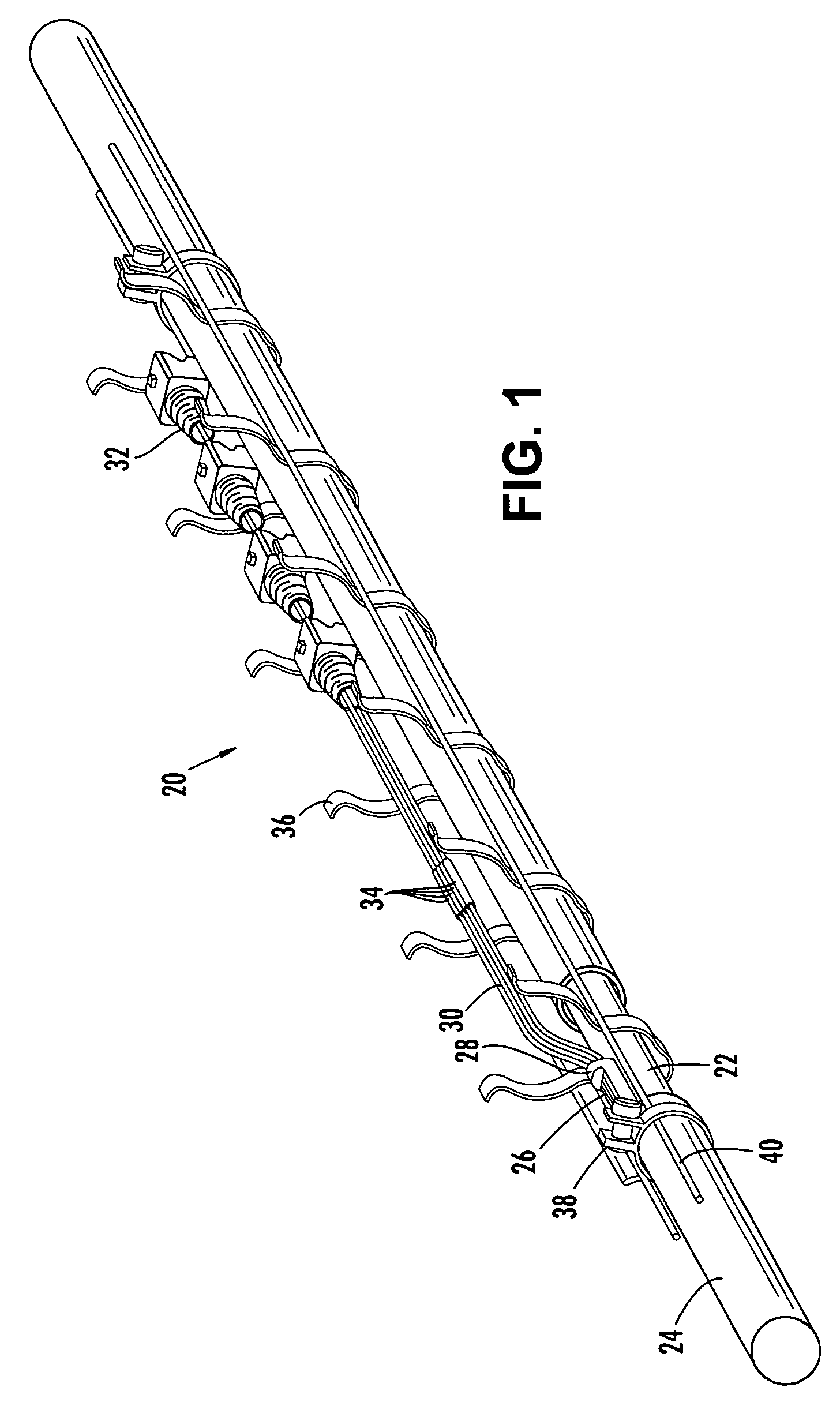
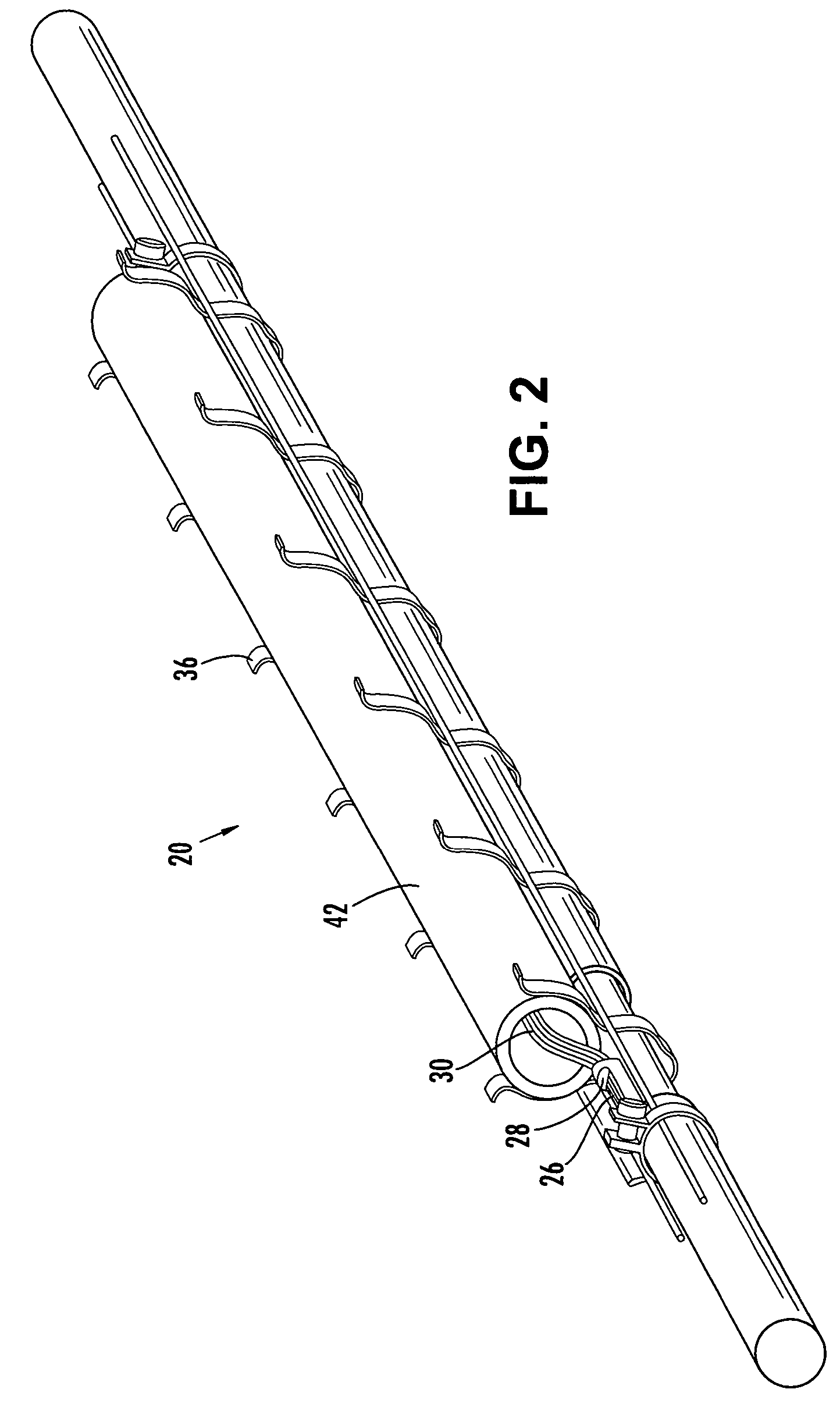
ActiveUS20050129375A1Low profile mid-span accessShorter overall optical lengthFibre mechanical structuresFiberEngineering
A factory prepared fiber optic distribution cable has at least one predetermined access location for providing access to at least one pre-connectorized optical fiber. The fiber optic distribution cable includes at least one preterminated optical fiber withdrawn from a tubular body at the access location, a connector attached to the preterminated optical fiber, a transition piece for transitioning the preterminated optical fiber from the tubular body into a protective tube, and a protective shell encapsulating the access location for protecting the pre-connectorized optical fiber. Alternatively, the fiber optic distribution cable includes at least one preterminated optical fiber withdrawn from a tubular body, a transition piece for transitioning the preterminated optical fiber from the tubular body into a protective tube, a connector attached to the preterminated optical fiber, a plurality of cable centralizers, and a protective shell for encapsulating the access location and protecting the pre-connectorized optical fiber.
Owner:CORNING OPTICAL COMM LLC
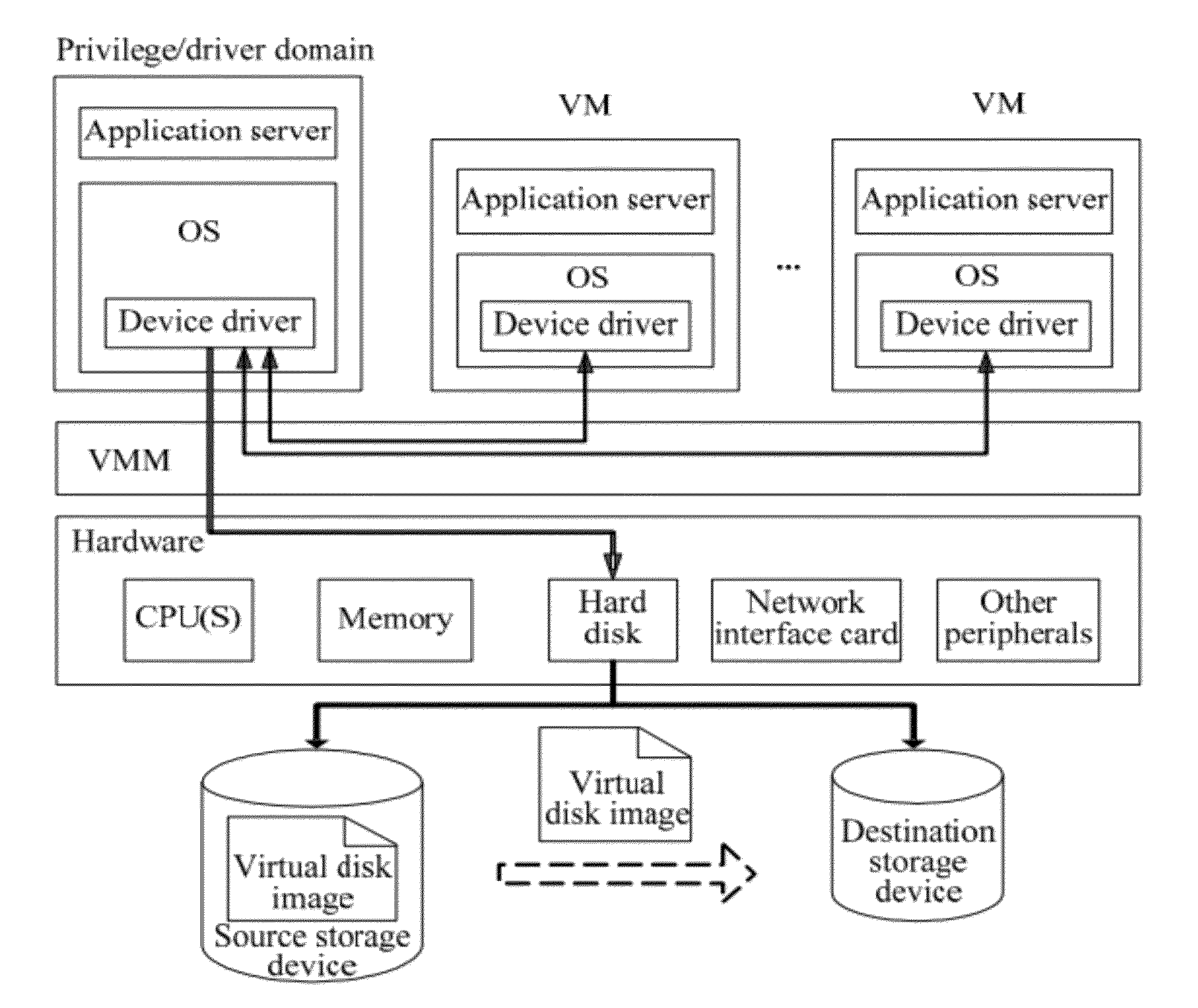
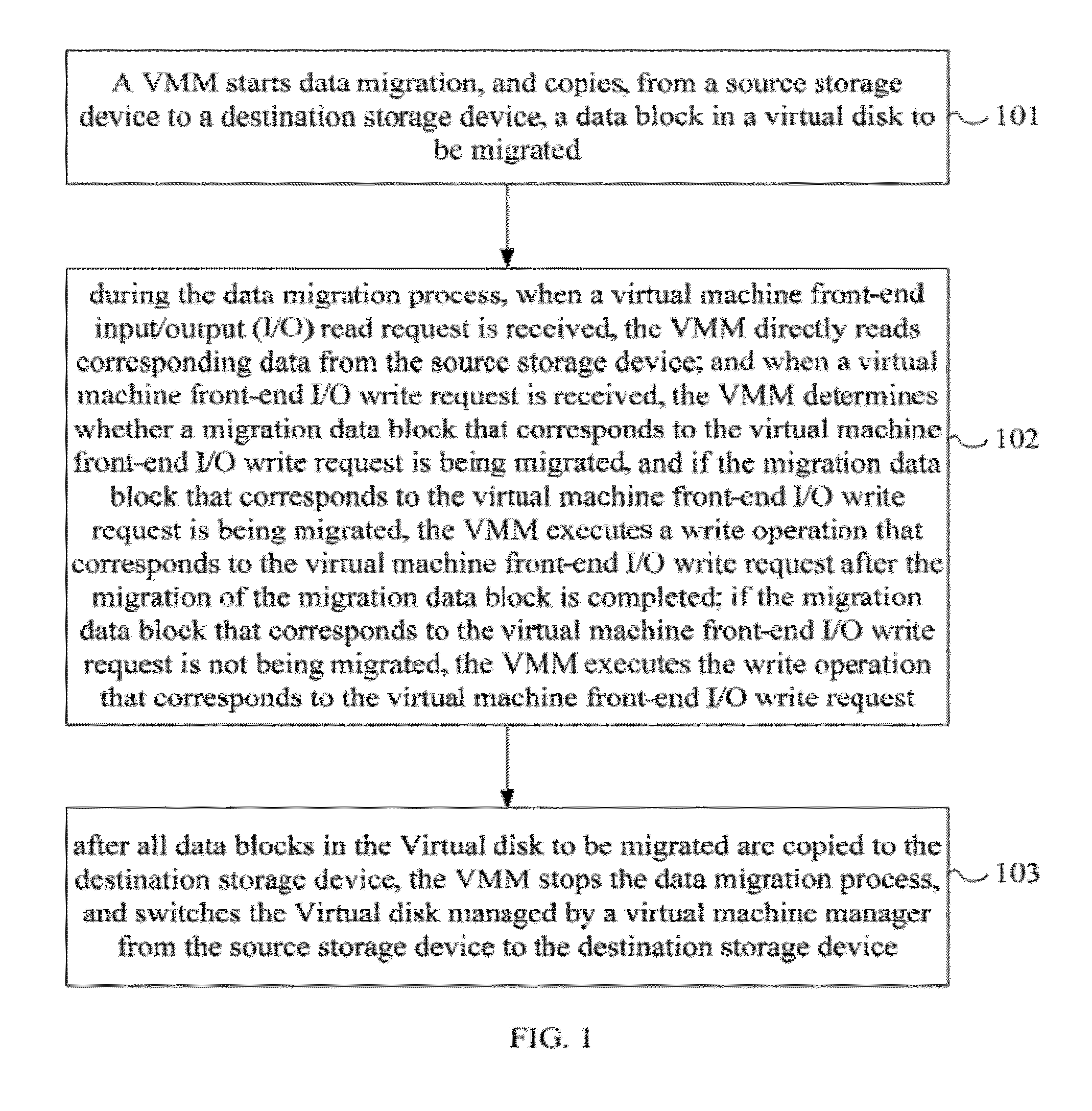
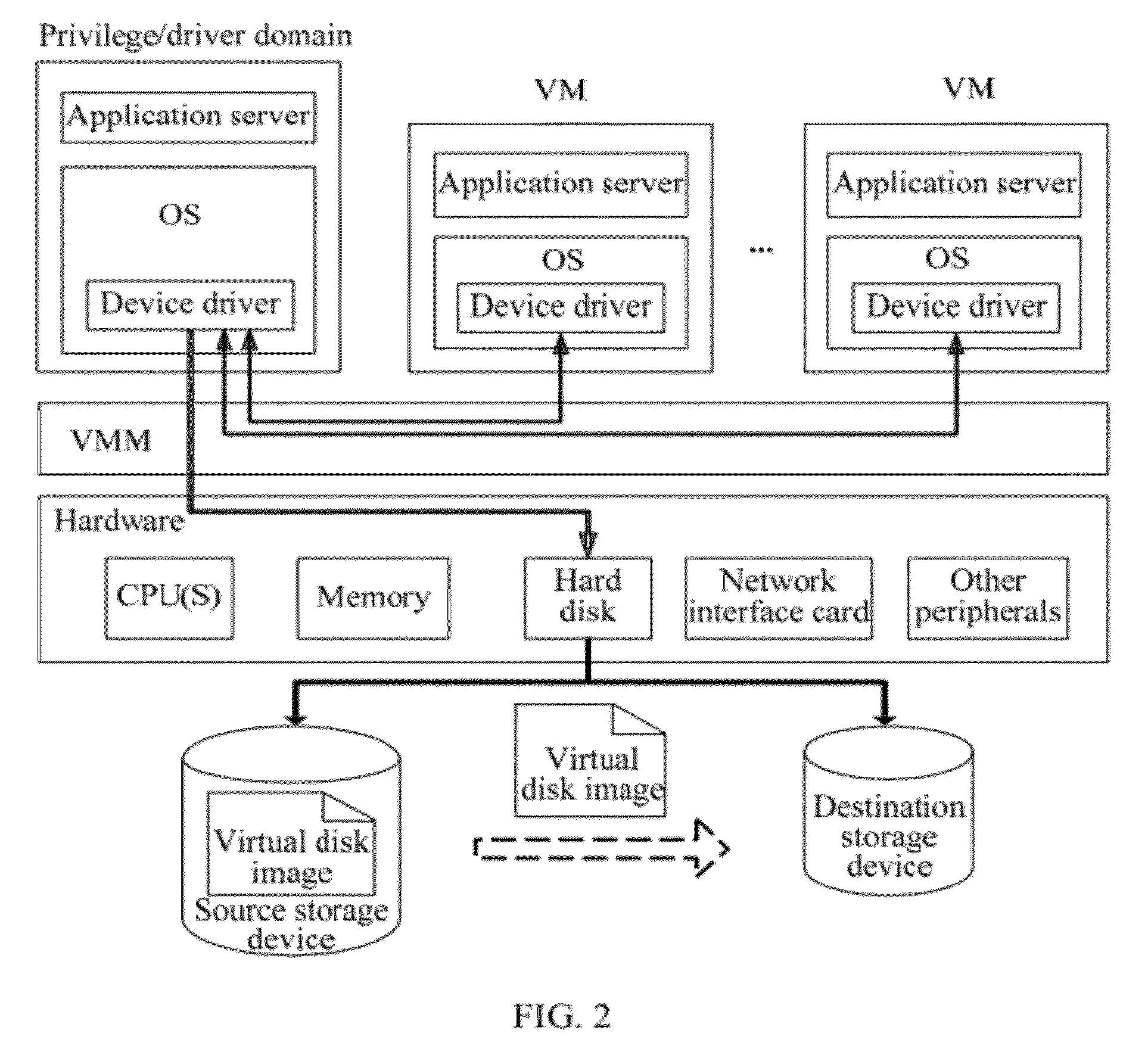
Virtual storage migration method, virtual storage migration system and virtual machine monitor
ActiveUS20120137098A1Decrease of access performanceReduce migration timeProgram control using stored programsMemory adressing/allocation/relocationVirtual storageVirtual machine
A virtual storage migration method is provided, including: starting a data migration process, and copying, from a source storage device to a destination storage device, a data block in a virtual disk to be migrated; when a VM front-end I / O read request is received, directly reading, corresponding data from the source storage device; when a VM front-end I / O write request is received, determining whether a migration data block that corresponds to the write request is being migrated, if yes, executing a write operation that corresponds to the write request after the migration of the migration data block is completed, if no, executing a write operation that corresponds to the write request; and after all the data blocks in the virtual disk to be migrated are copied to the destination storage device, stopping the data migration, and switching the virtual disk from the source storage device to the destination storage device.
Owner:HUAWEI TECH CO LTD
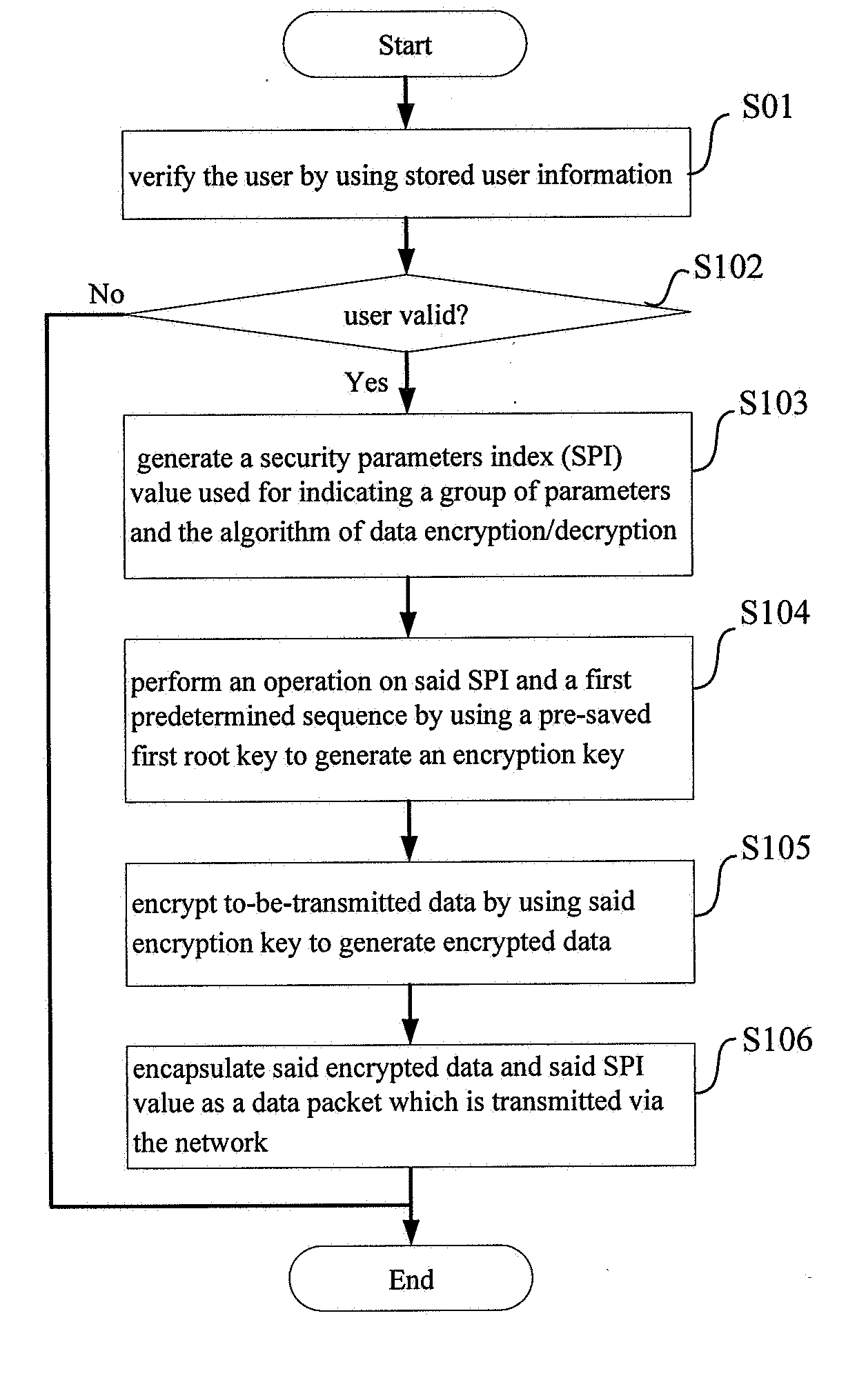
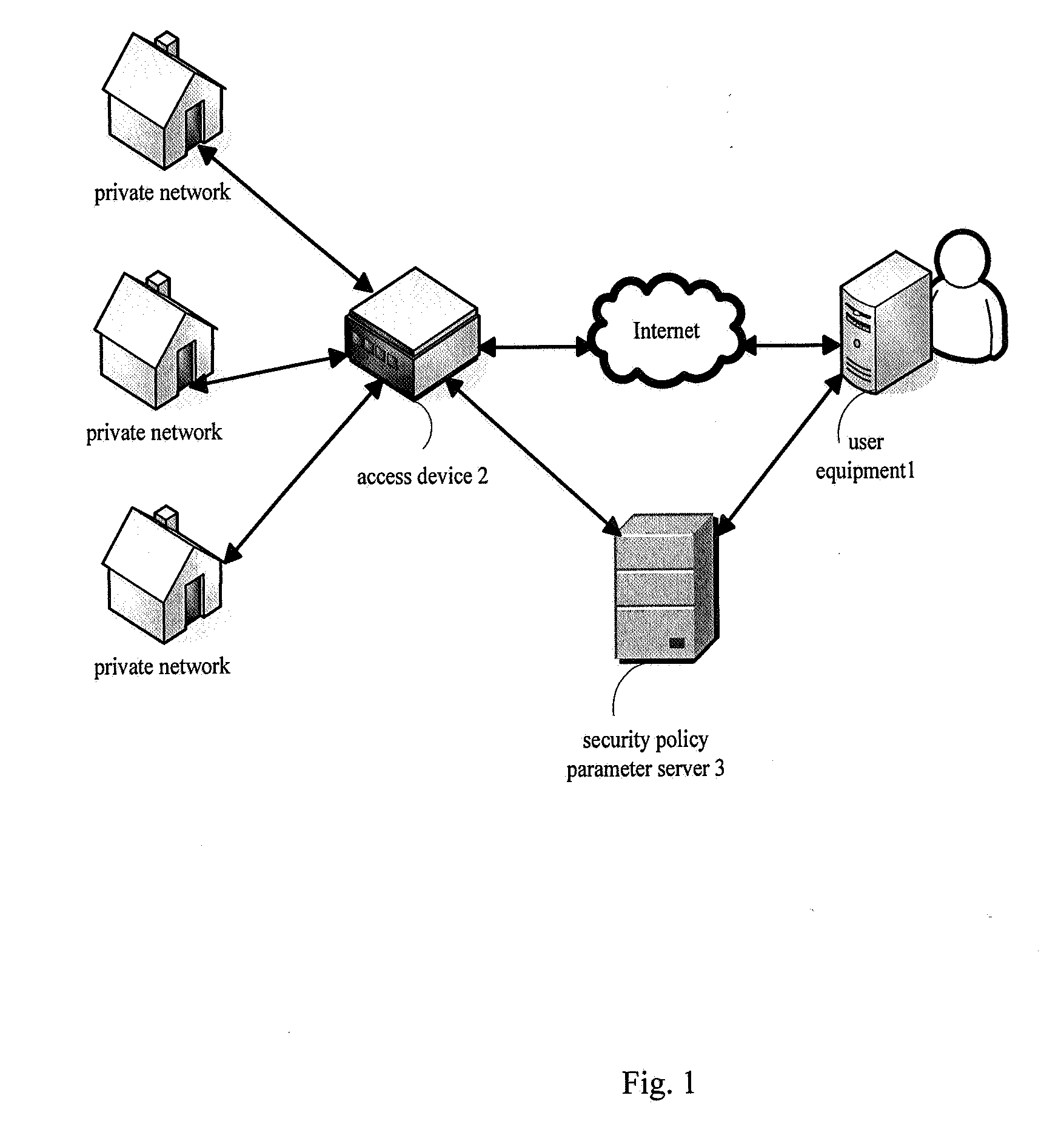
Method and apparatus for secure communication between user equipment and private network
ActiveUS20070157309A1Simple secure communication schemeAuthentication is simpleUser identity/authority verificationUnauthorized memory use protectionSecure communicationPrivate network
It is an object of the present invention to provide a new technical solution of supporting special secure communication between user equipment which is located in an external network and an private network the user equipment belongs to. Specifically, transmitted data is encrypted / decrypted and authenticated by using pre-stored root keys corresponding to specific private networks and the agreed encryption / decryption and authentication algorithm at the user equipment and an access device. The manner of generating the encryption / decryption keys and authentication key is simplified, and the complexity of the access device at the private network end is reduced on the premise of not degrading the security grade. The technical solution of the present invention is highly flexible and extensible and can achieve better user experience.
Owner:ALCATEL LUCENT SAS
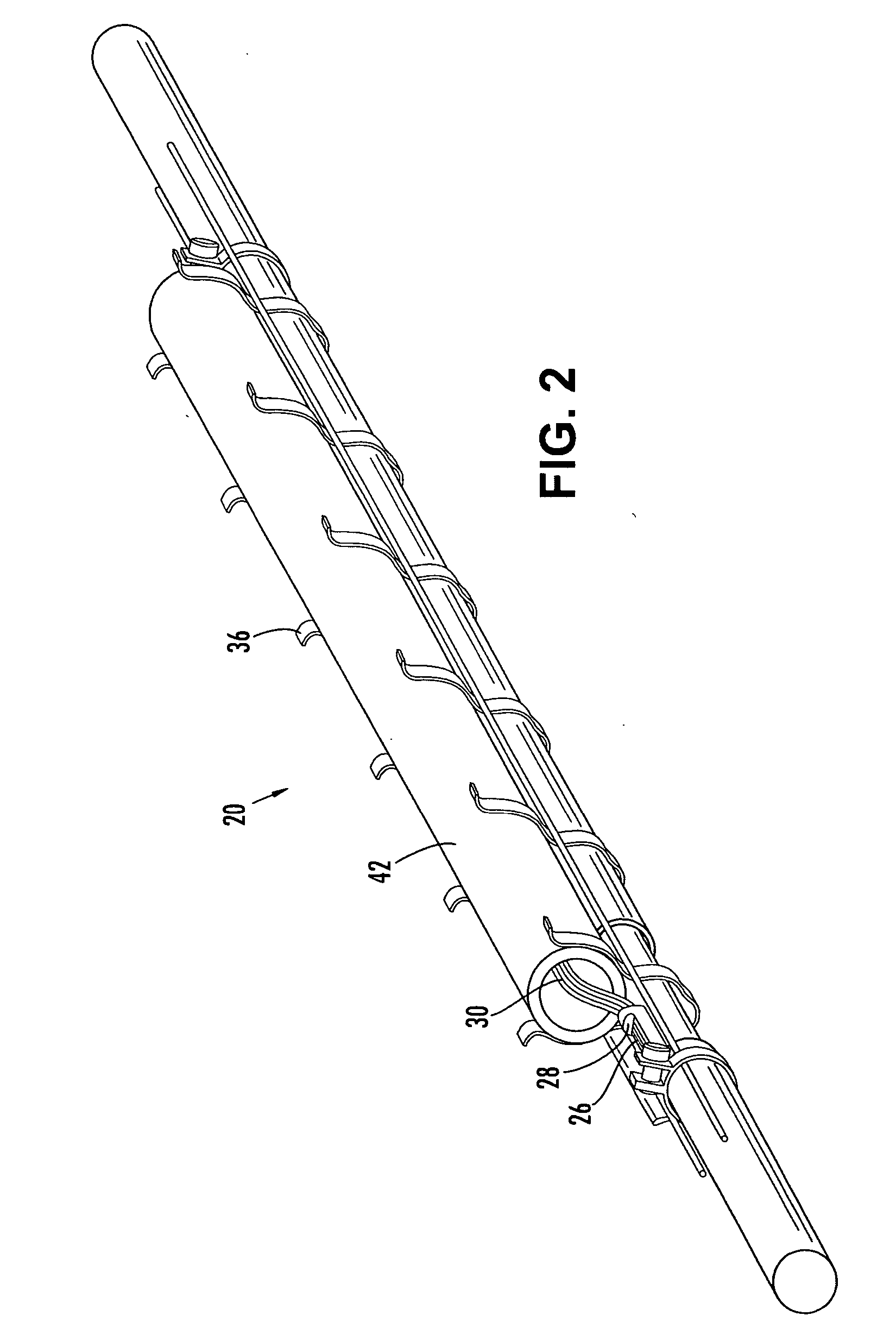
Pre-connectorized fiber optic distribution cable
A factory prepared fiber optic distribution cable has at least one predetermined access location for providing access to at least one pre-connectorized optical fiber. The fiber optic distribution cable includes at least one preterminated optical fiber withdrawn from a tubular body at the access location, a connector attached to the preterminated optical fiber, a transition piece for transitioning the preterminated optical fiber from the tubular body into a protective tube, and a protective shell encapsulating the access location for protecting the pre-connectorized optical fiber. Alternatively, the fiber optic distribution cable includes at least one preterminated optical fiber withdrawn from a tubular body, a transition piece for transitioning the preterminated optical fiber from the tubular body into a protective tube, a connector attached to the preterminated optical fiber, a plurality of cable centralizers, and a protective shell for encapsulating the access location and protecting the pre-connectorized optical fiber.
Owner:CORNING CABLE SYST LLC
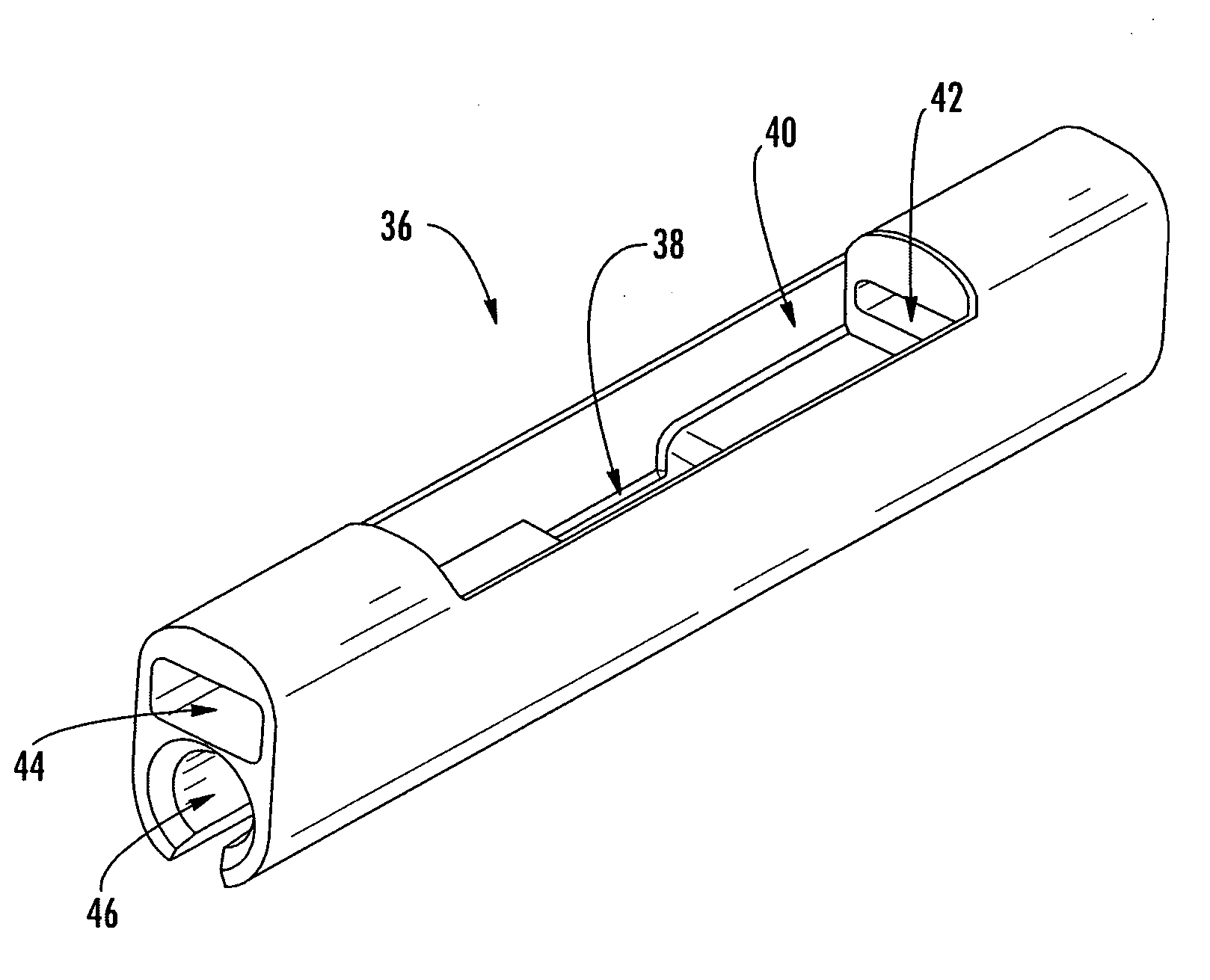
Preterminated fiber optic distribution cable
ActiveUS20050111799A1Low profile mid-span accessLong fiber lengthFibre mechanical structuresFiberEngineering
A factory-manufactured, preterminated fiber optic distribution cable having at least one predetermined access location for providing access to at least one preterminated optical fiber. A preterminated fiber optic distribution cable comprising at least one buffer tube comprising at least one optical fiber, a buffer tube transition piece operable for transitioning the at least one optical fiber from the at least one buffer tube into at least one protective tube, a C-shaped molded member defining a longitudinally extending optical fiber guide channel operable for storing a length of the at least one preterminated optical fiber and a protective means. A method of mid-span accessing at least one optical fiber from a fiber optic distribution cable. A buffer tube transition piece operable for transitioning a plurality of preterminated optical fibers from a buffer tube into protective tubing.
Owner:CORNING OPTICAL COMM LLC
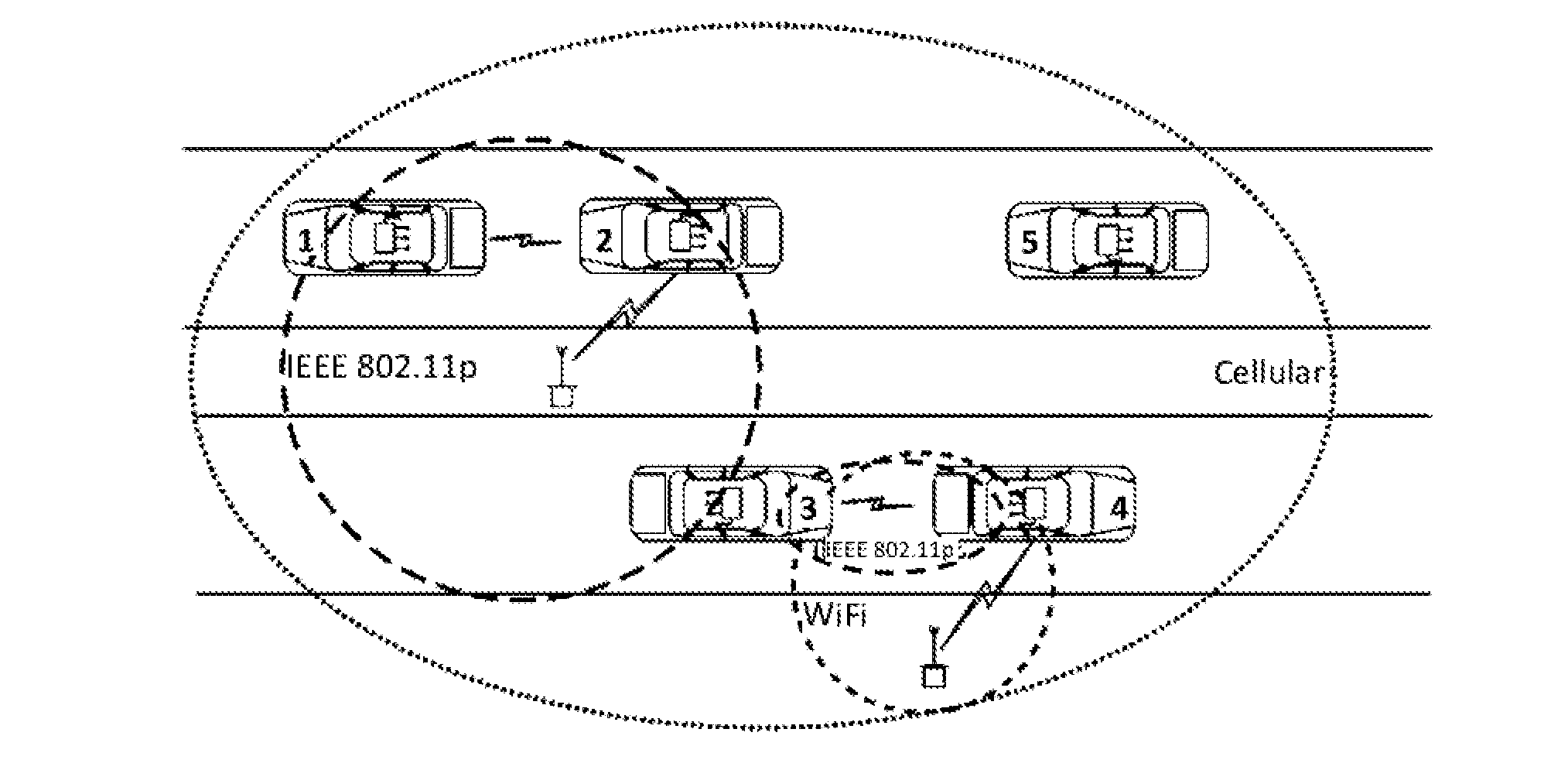
Method and apparatus for multi-network communication in vehicular networks
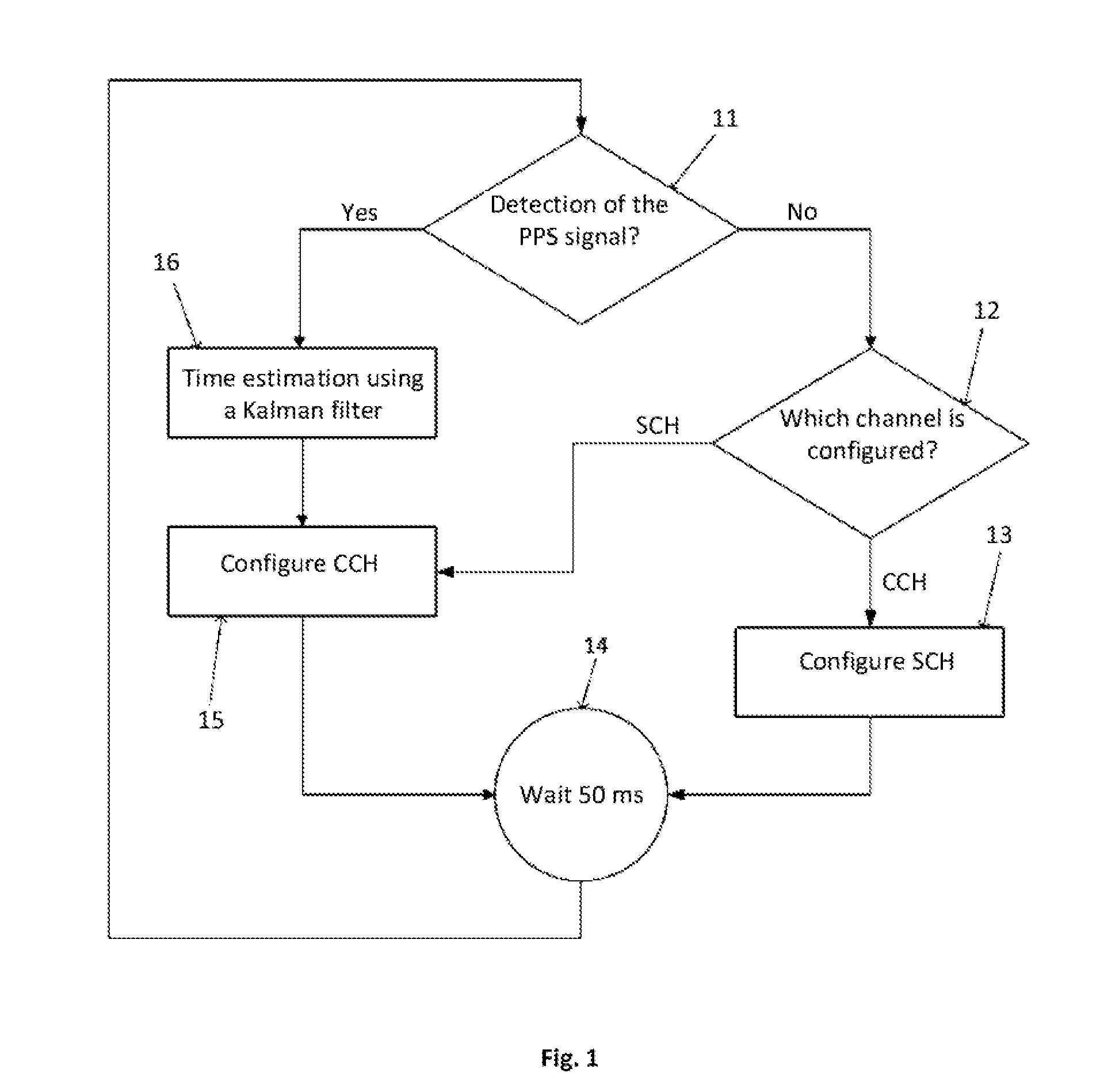
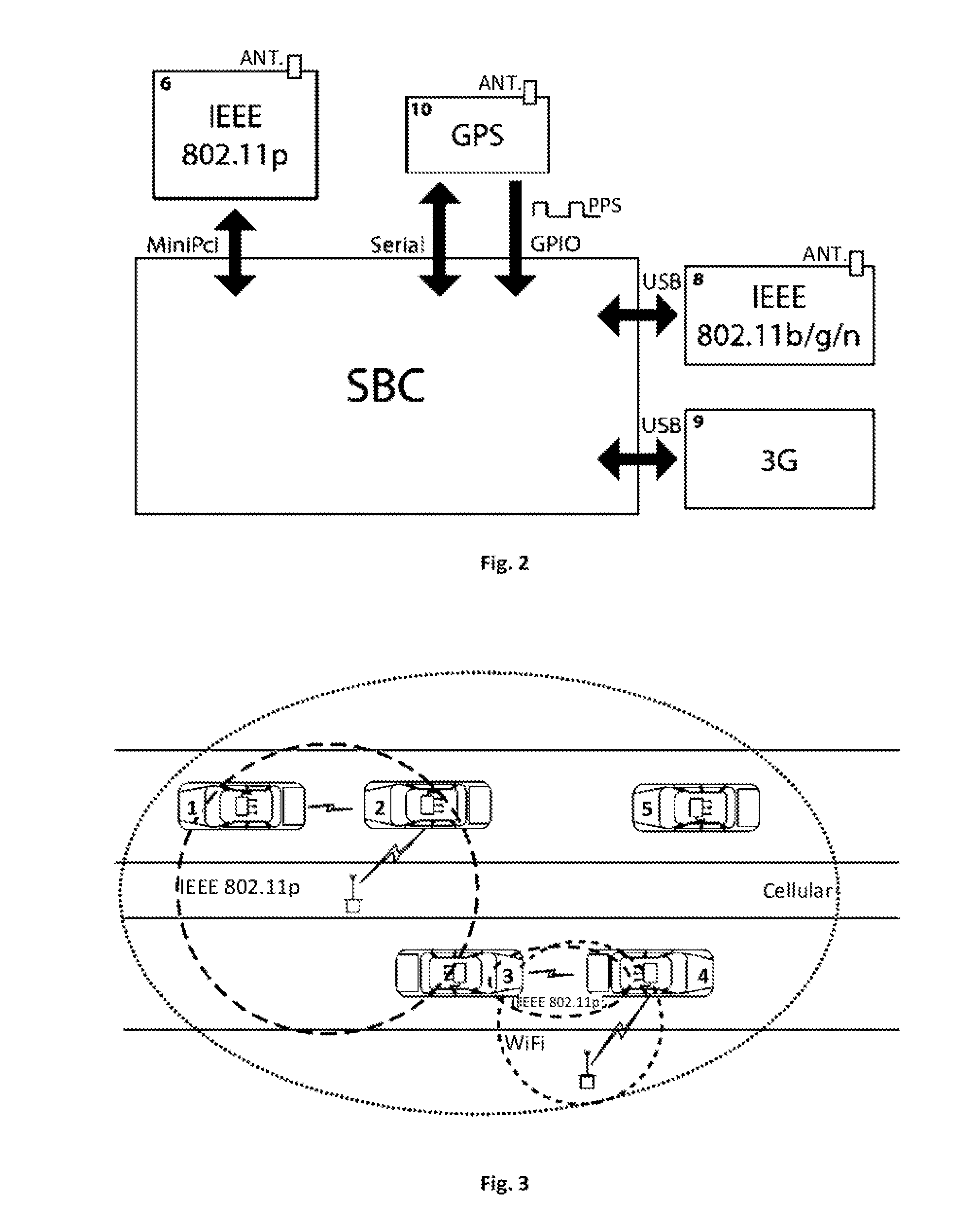
Wireless network data router for a vehicle, and operating method thereof, comprising: a multi-connection interface for wireless access in vehicular environments, herewith WAVE; a wireless local area network, herewith Wi-Fi, interface; a mobile network data interface; a downlink data connection for the vehicle and / or users in the vehicle and its vicinity; a data processing unit for routing data between said interfaces; wherein the data processing unit is configured to: calculate a score for each reachable network on the WAVE, Wi-Fi and mobile network interfaces; switch the uplink connection of the wireless network data router to the reachable network with the best score. Also a wireless network data router for vehicles for connecting vehicles to the Internet through a multi-network device, said router being a mobile router suitable to form a mesh network of connected vehicles, wherein the router is arranged for using parked cars for redistributing Wi-Fi signal from fixed hotspots.
Owner:UNIV AVEIRO +2
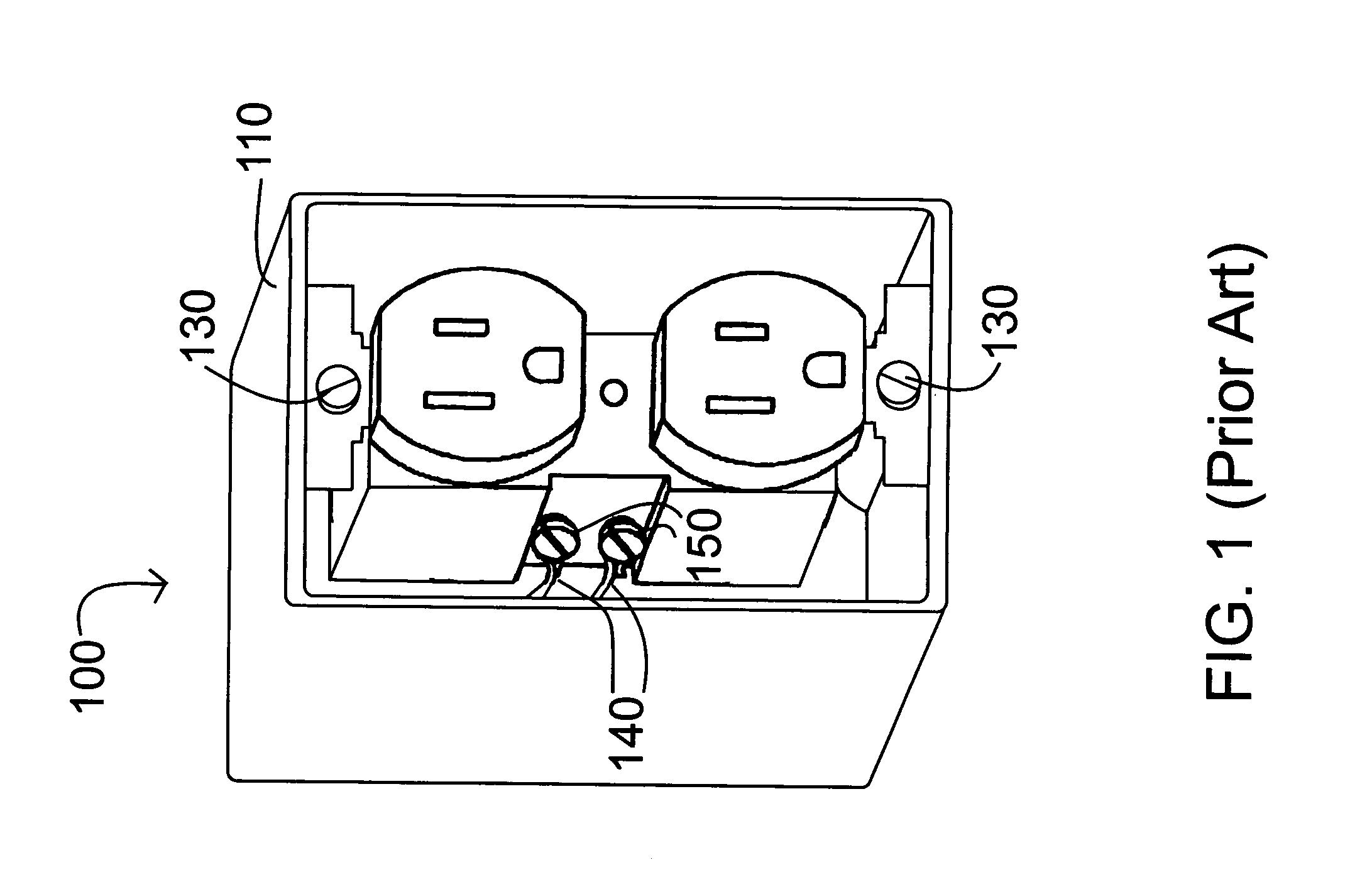
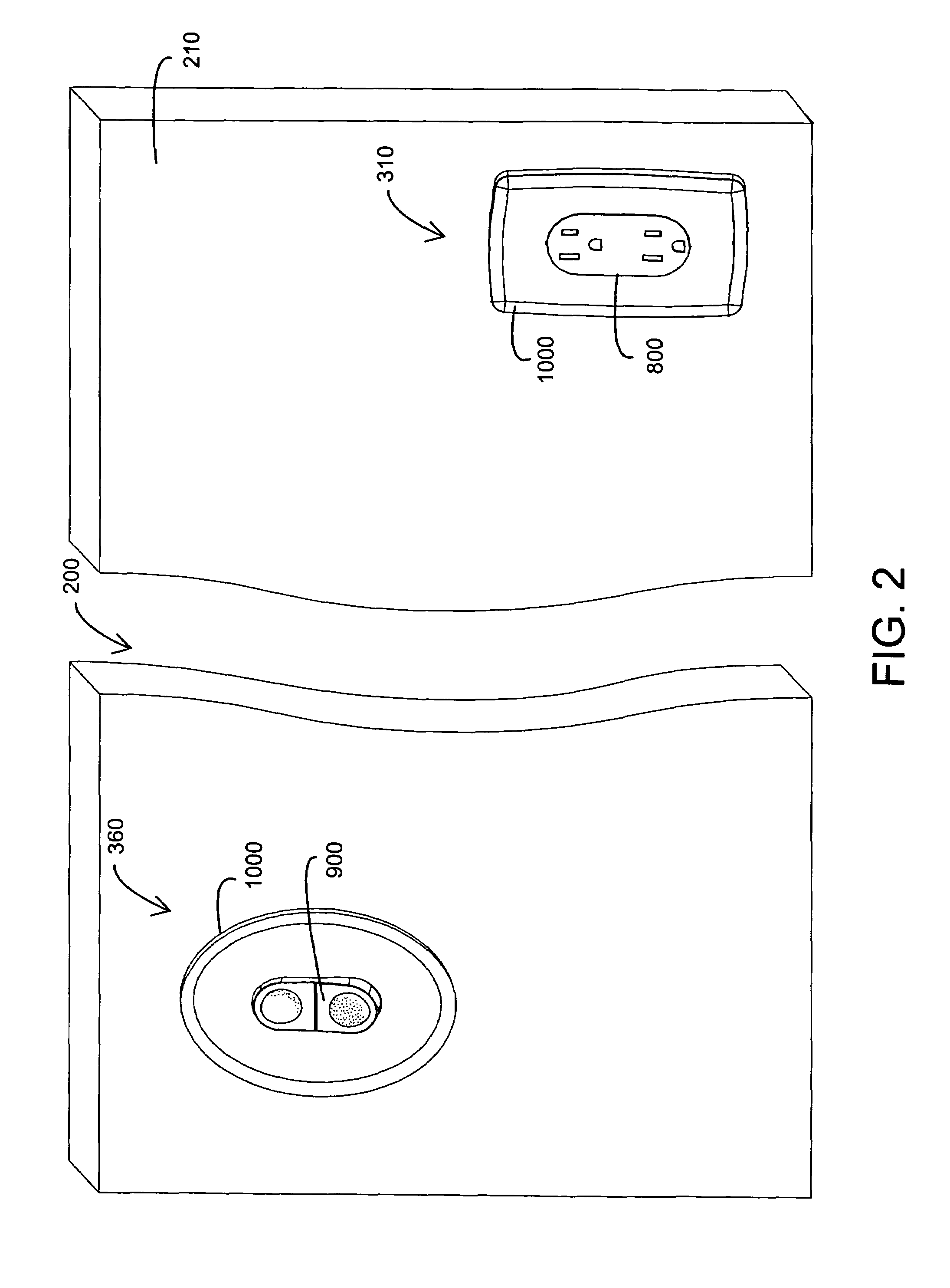
Safety module electrical distribution system
InactiveUS6884111B2Eliminating cutEliminating patch repairDc network circuit arrangementsTwo pole connectionsPower cableDistribution system
A safety module electrical distribution system comprises a wiring module adapted to mount within an electrical box, the wiring module having a functional side and a wiring side. A terminal set is disposed at least partially within the wiring module and is adapted to terminate a power cable proximate the wiring side. A plurality of structured sockets are disposed on the functional side, the structured sockets incorporate a portion of the terminal set. A functional module having a front side and a back side is adapted to removably install in the wiring module proximate the functional side. A contact set is disposed at least partially within the functional module and is adapted to conduct electrical power to an electrical distribution function accessible from the front side. A plurality of shielded plugs are disposed on the back side. The shielded plugs incorporate a portion of the contact set. The structured sockets are configured to interlock with the shielded plugs so as to provide electrical communication between the terminal set and said contact set.
Owner:BAUM FAMILY TRUST DTD 1 11 2001 +143
Electrical wiring method
InactiveUS7367121B1Prevent scalingEliminating cutContact member manufacturingSubstation/switching arrangement detailsPower stripElectrical wiring
An electrical box is mounted on a wall stud, and a wiring panel is installed within the electrical box so as to partition the interior of the electrical box into a user inaccessible wiring compartment and a user accessible module compartment. A protective cover is attached to the wiring panel so as to protect the wiring panel during a makeup phase of wall panel installation and painting. After the makeup phase, the protective cover is removed from the wiring panel and a module having a user operable electrical function is mounted to the wiring panel within the user accessible module compartment.
Owner:BAUM FAMILY TRUST DTD 1 11 2001 +143
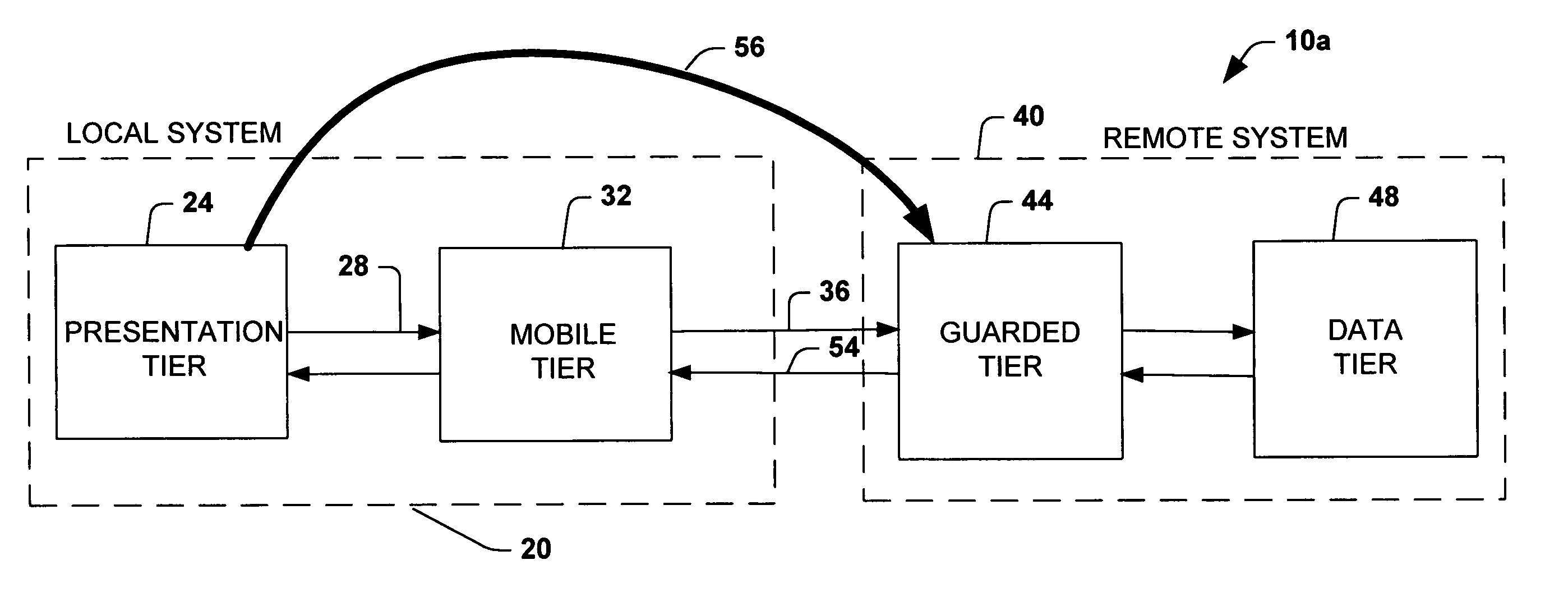
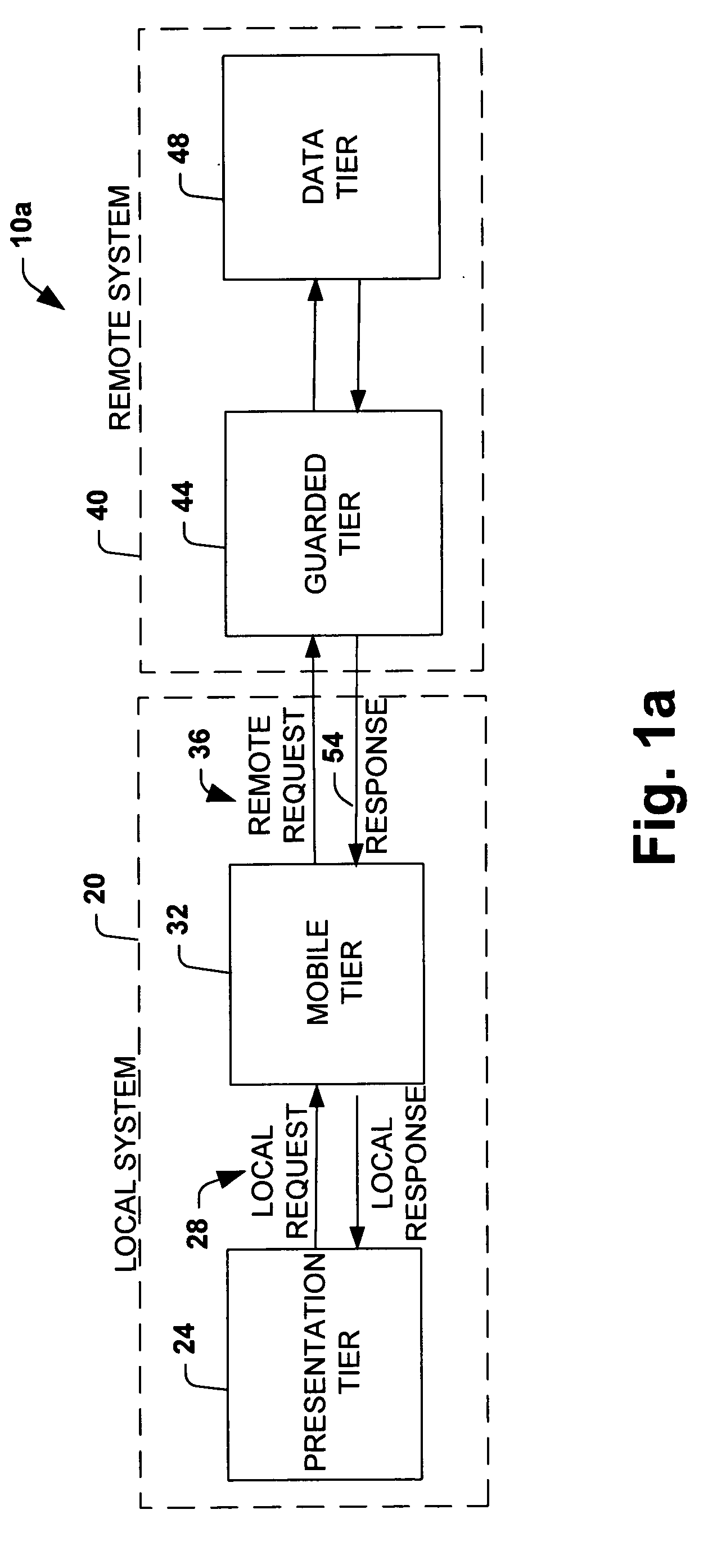
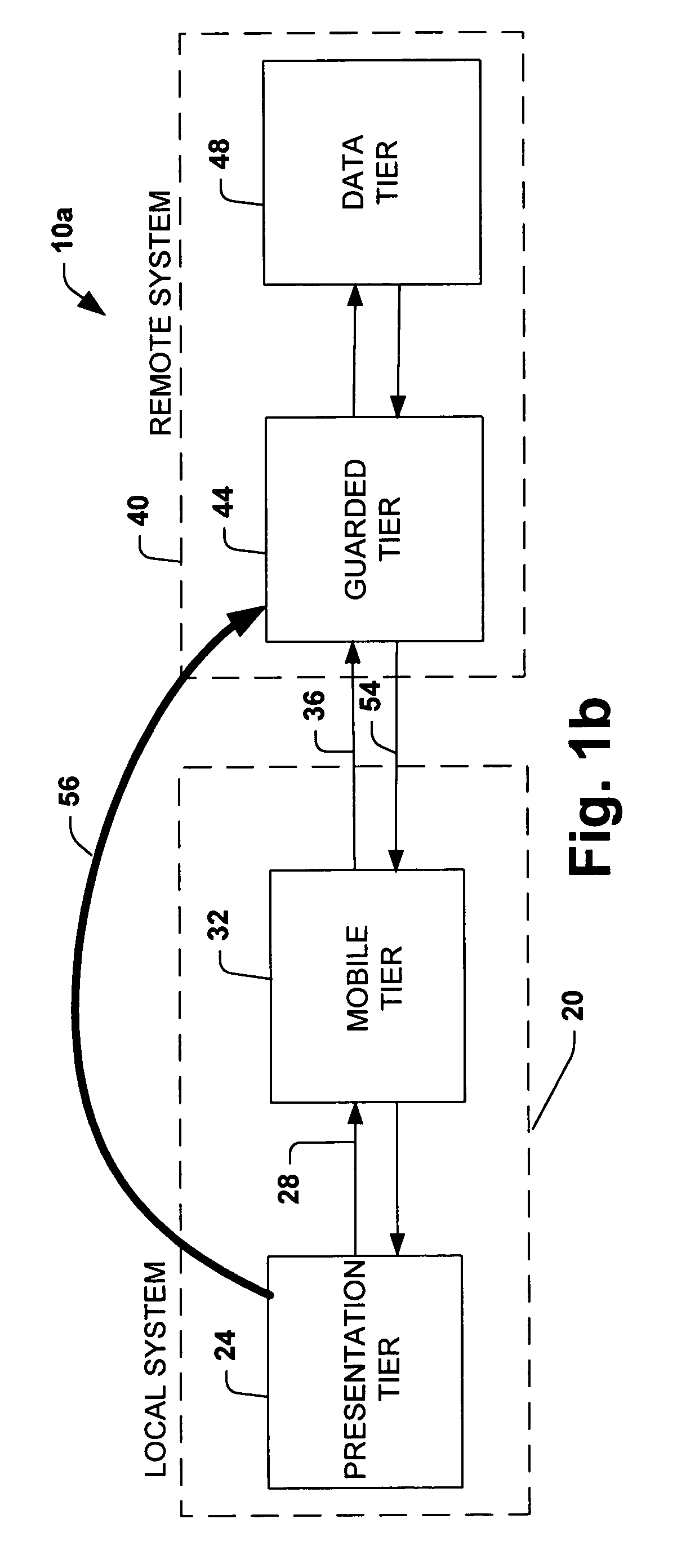
System and method providing multi-tier applications architecture
InactiveUS6996599B1Capability facilitatedImprove performanceMultiple digital computer combinationsProgram loading/initiatingApplication softwareClient-side
A network-based distributed application system is provided in accordance with the present invention for enabling services to be established locally on a client system. The system may include an application and presentation logic, at least a portion of which is interchangeably processed by a server or a client without modification to the portion. The core functionality provided by the application may be preserved between the client and the server wherein improved network performance may provided along with improved offline service capabilities.
Owner:MICROSOFT TECH LICENSING LLC
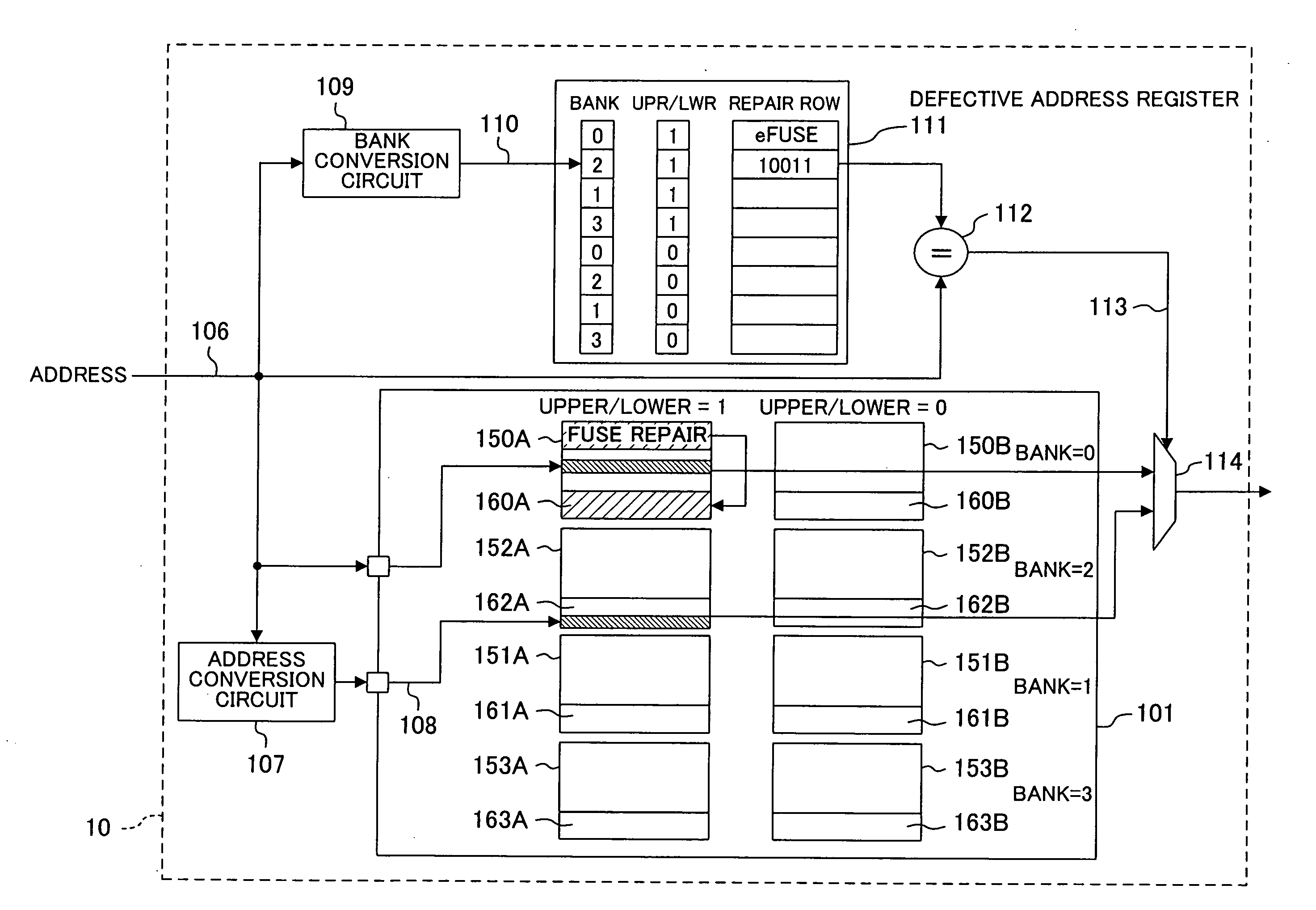
Memory system
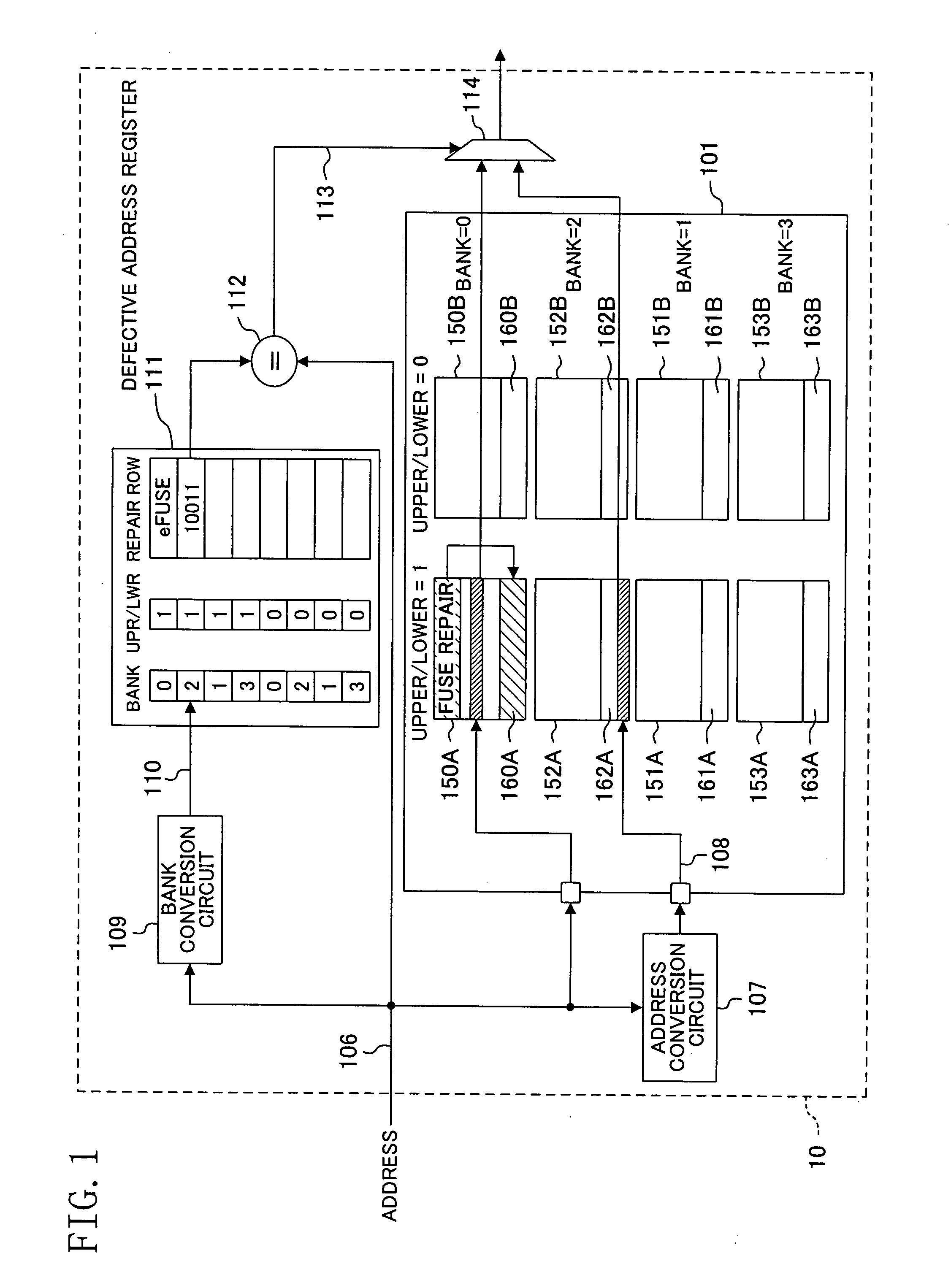
InactiveUS20080028260A1Decrease in memory access speedReduce circuit sizeStatic storageRedundant hardware error correctionMemory bankComputer science
A memory system includes a memory having memory banks each having a redundant region for repairing a defect. When a plurality of defects occur in one of the memory banks, at least one of the defects is repaired by using the redundant region of the memory bank with the defects and at least one other of the defects is repaired by using the redundant region of another of the memory banks.
Owner:PANASONIC CORP
Efficient data transfer between computers in a virtual NUMA system using RDMA
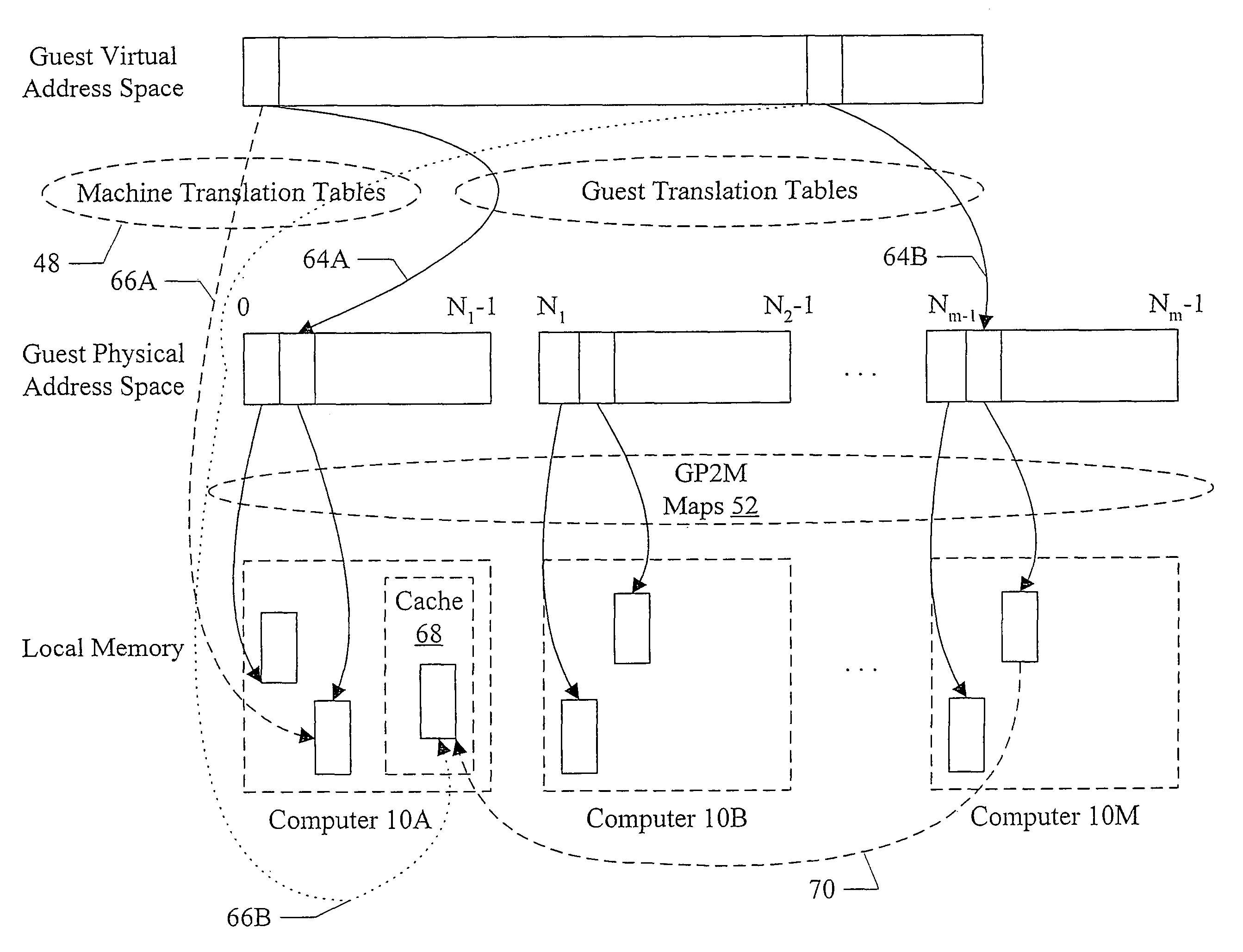
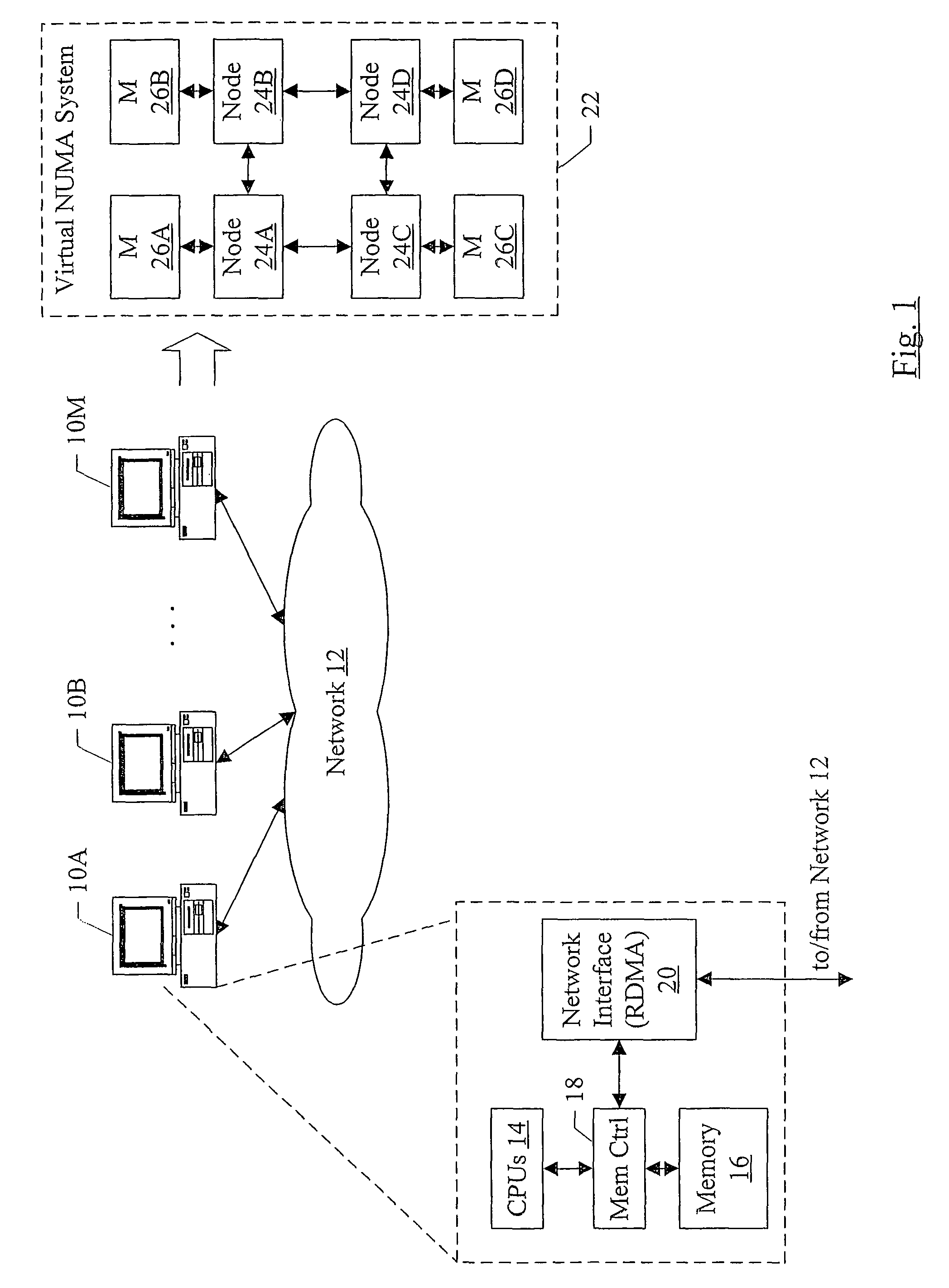
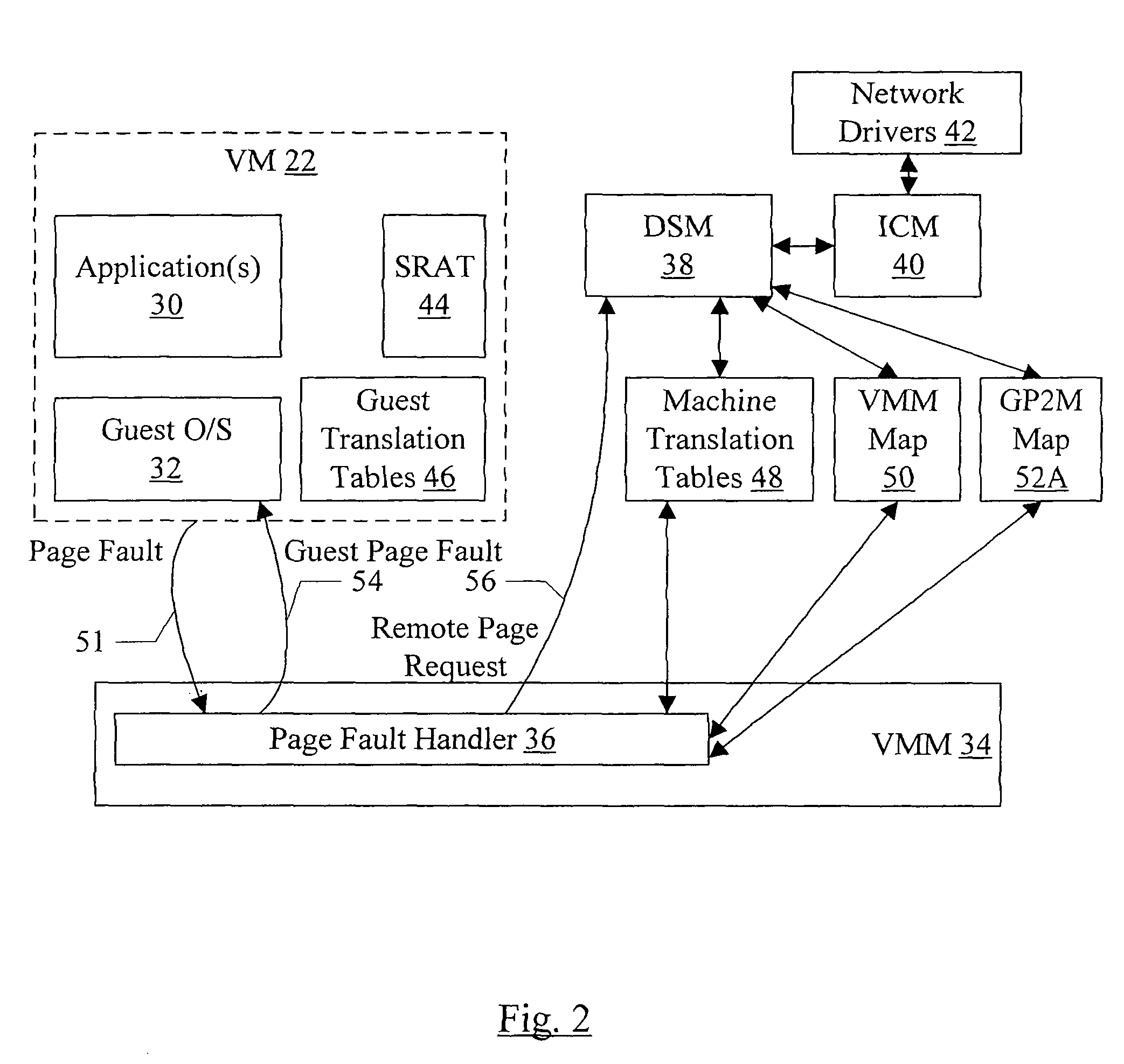
InactiveUS7756943B1Remote access be reducedImprove performanceDigital computer detailsProgram controlPhysical addressRemote direct memory access
In one embodiment, a virtual NUMA machine is formed from multiple computers coupled to a network. Each computer includes a memory and a hardware device coupled to the memory. The hardware device is configured to communicate on the network, and more particularly is configured to perform remote direct memory access (RDMA) communications on the network to access the memory in other computers. A guest physical address space of the virtual NUMA machine spans a portion of the memories in each of the computers, and each computer serves as a home node for at least one respective portion of the guest physical address space. A software module on a first computer uses RDMA to coherently access data on a home node of the data without interrupting execution in the home node.
Owner:SYMANTEC OPERATING CORP
Multistage reception of code division multiple access transmissions
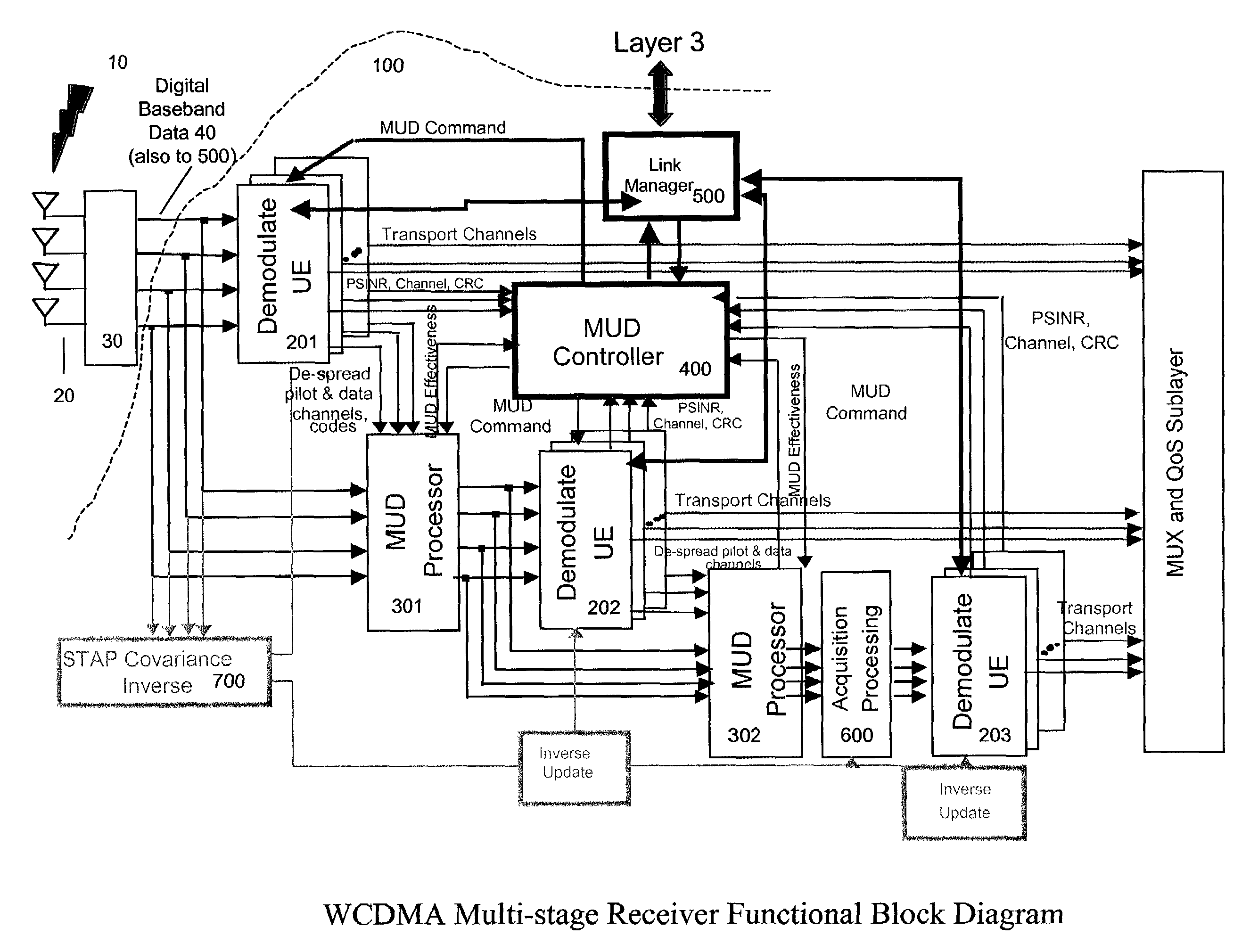
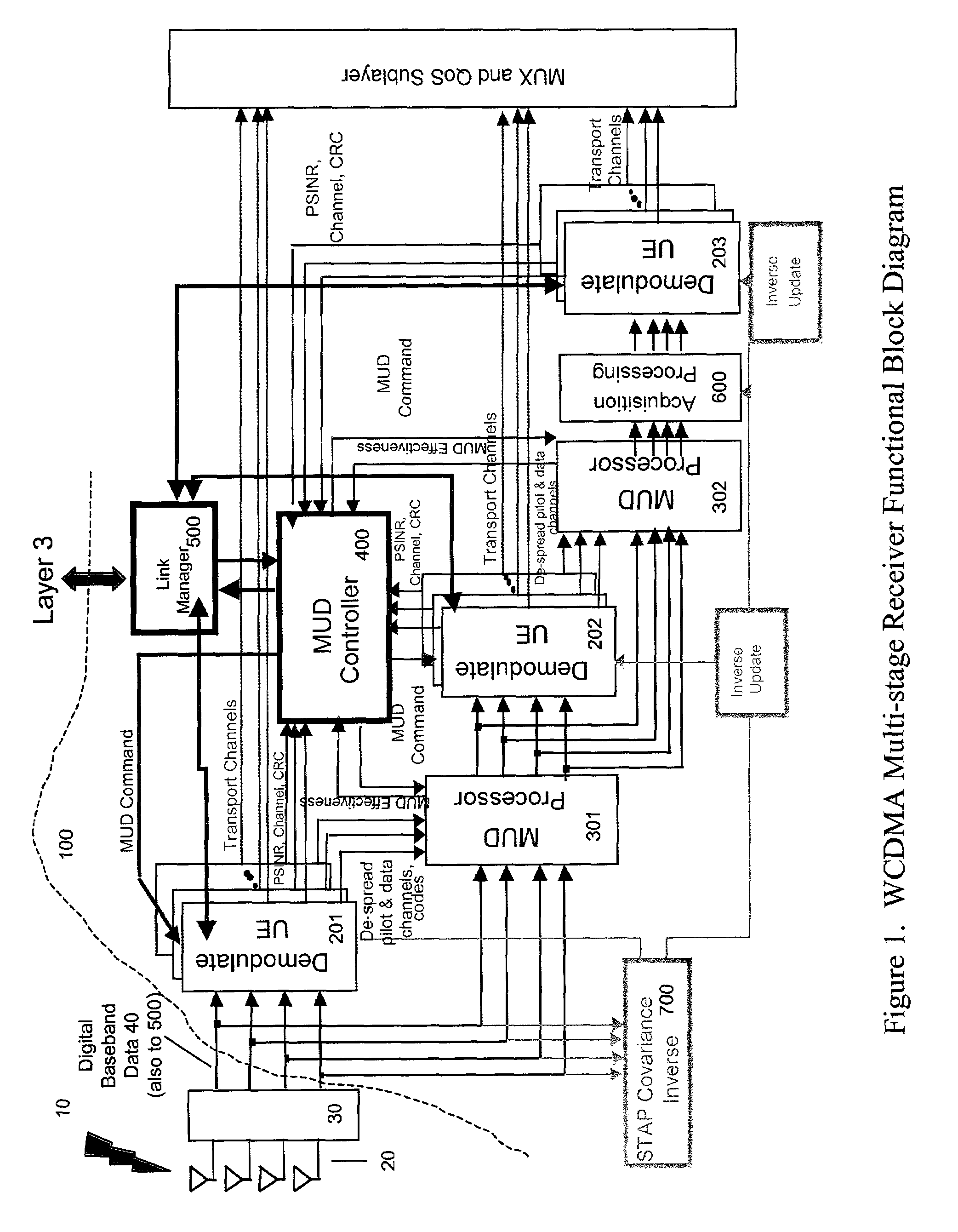
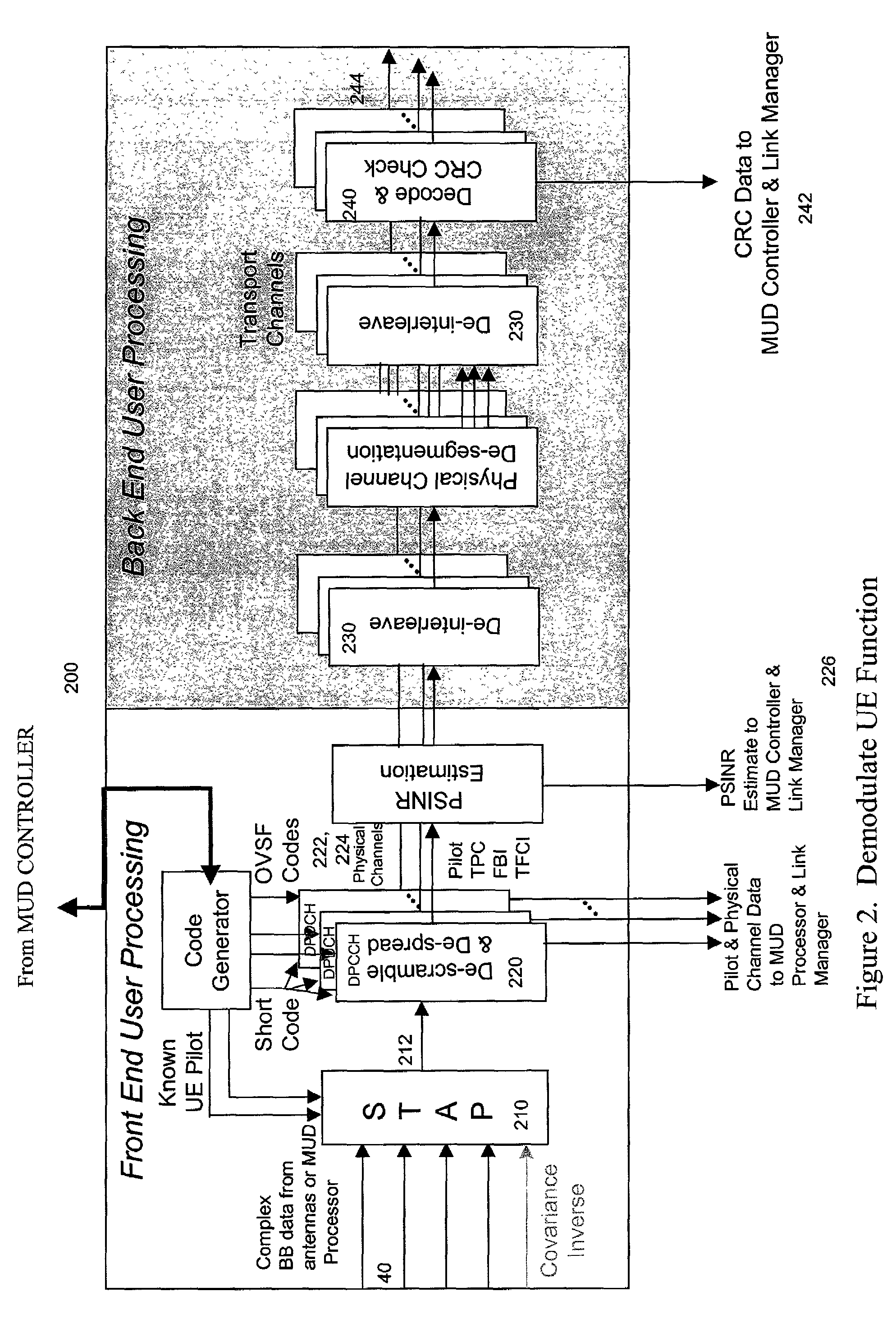
ActiveUS7209515B2Reducing multiple access interferenceReduce accessPower managementTransmission control/equalisingCode division multiple accessTransmitted power
Reducing multiple access interference in the radio frequency communications path between the network base station and UE. The preferred methods include interleaving STAP and MUD in a plurality of stages in a base station receiver. Specific embodiments accomplish this by selecting certain UE connections for MUD processing by stage. Then, in two or more stages, demodulating the UE connections selected for MUD processing using STAP, and MUD canceling UE connections selected for MUD processing. Within the latency requirements of the network, preferred embodiments of the present invention also command a transmit power for each UE connections in order to exploit the effect of interleaved STAP and MUD processing.
Owner:LEIDOS
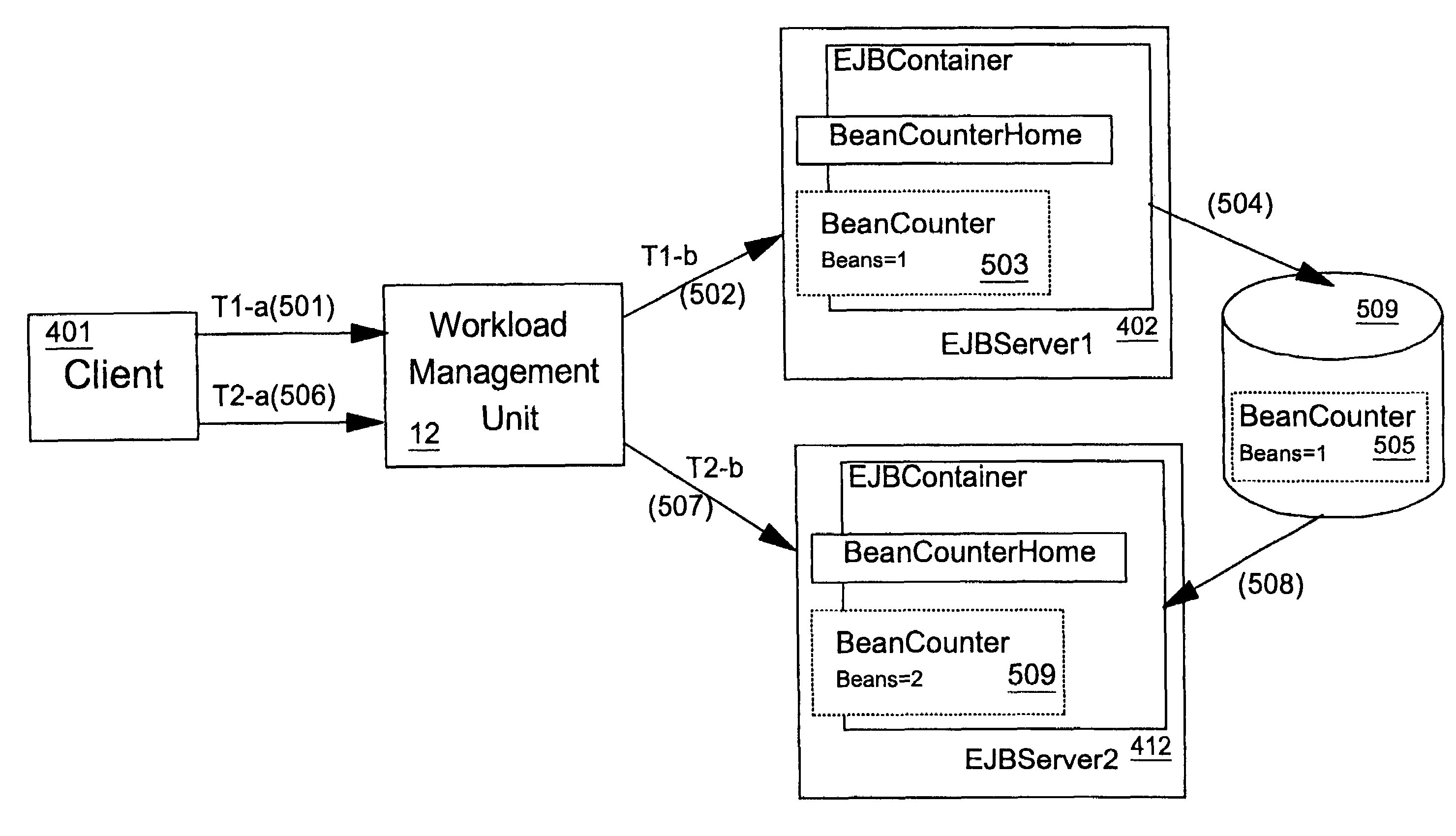
Workload management of stateful program entities
InactiveUS7349970B2Need be provideReduce accessResource allocationMultiple digital computer combinationsMass storageRouting table
In a workload managed system comprising a plurality of server processes each capable of supporting a given program entity, such as an Enterprise JavaBeans™ specified stateful session bean, a stateful session bean instance is passivated, by writing it to a bean store, on completion of a unit of work. On next use the session bean is reactivated, by reading it from the bean store, in any one of the plurality of servers thereby allowing workload management for stateful session beans. A routing table is maintained, in non-volatile mass storage, that contains location information for units of work and stateful session bean instances, used to maintain unit of work-server affinity for the lifetime of the unit of work Stateful session beans instances are associated with ID keys that include a flag that is used to indicate whether or not the routing table contains location information for the bean instance.
Owner:GOOGLE LLC
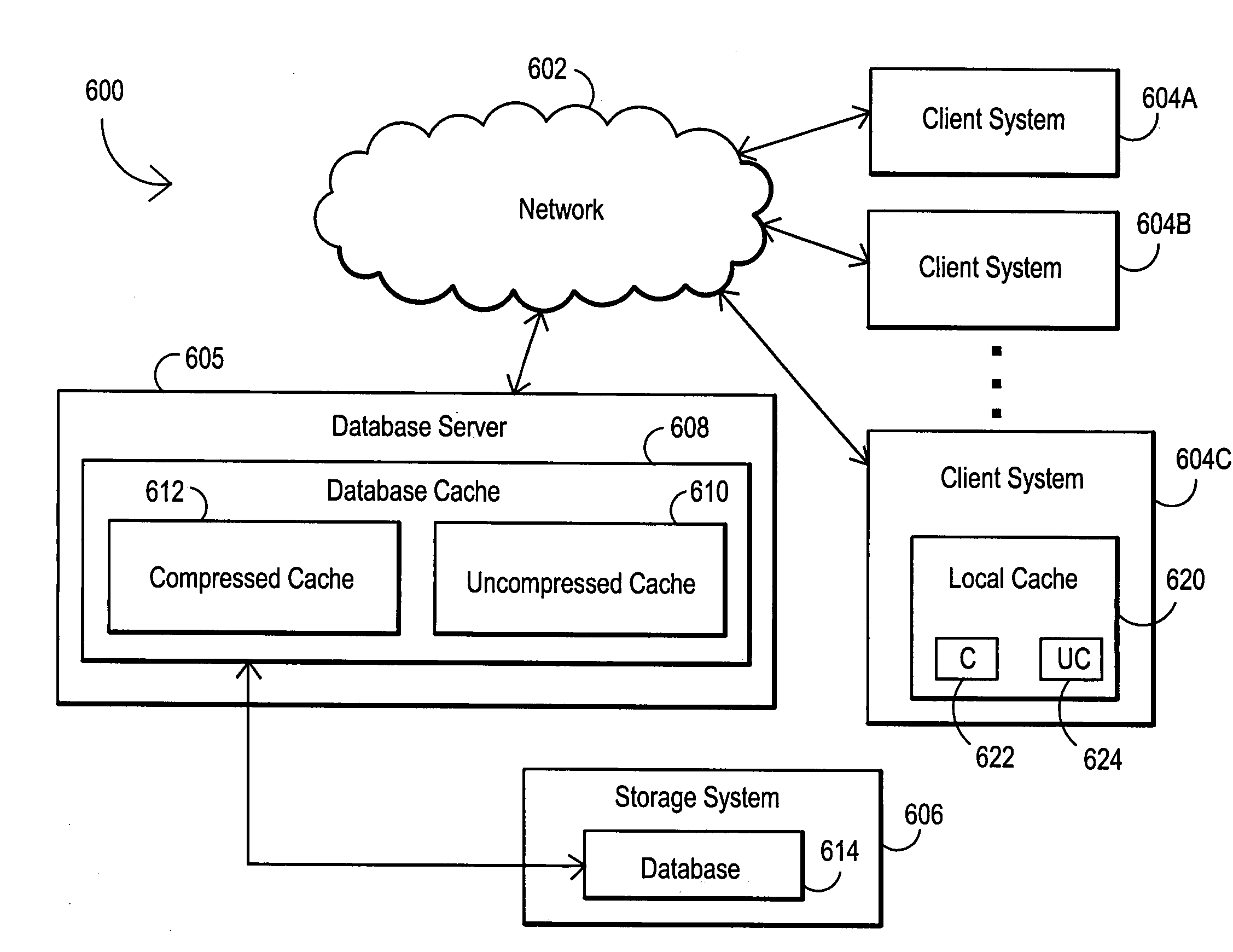
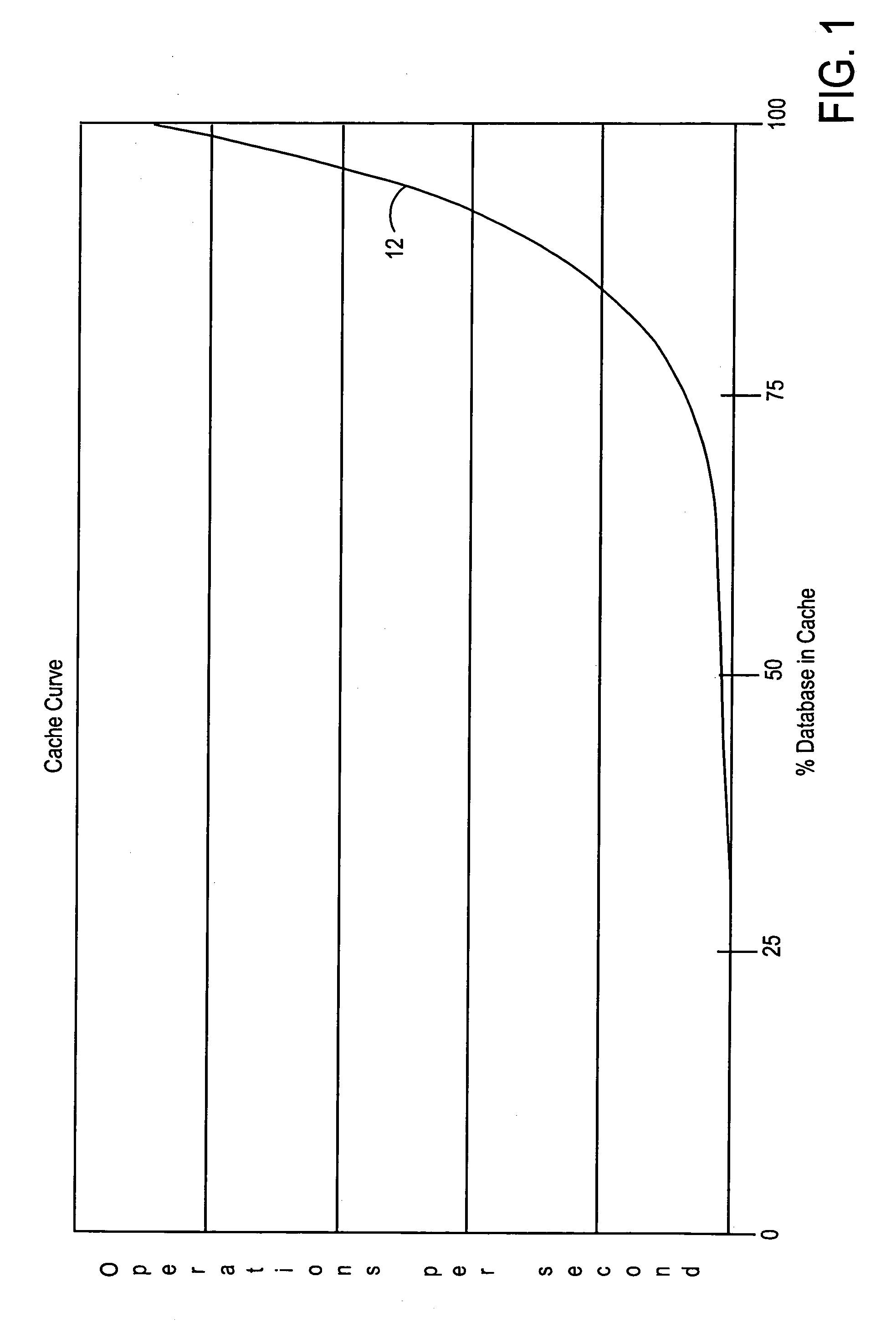
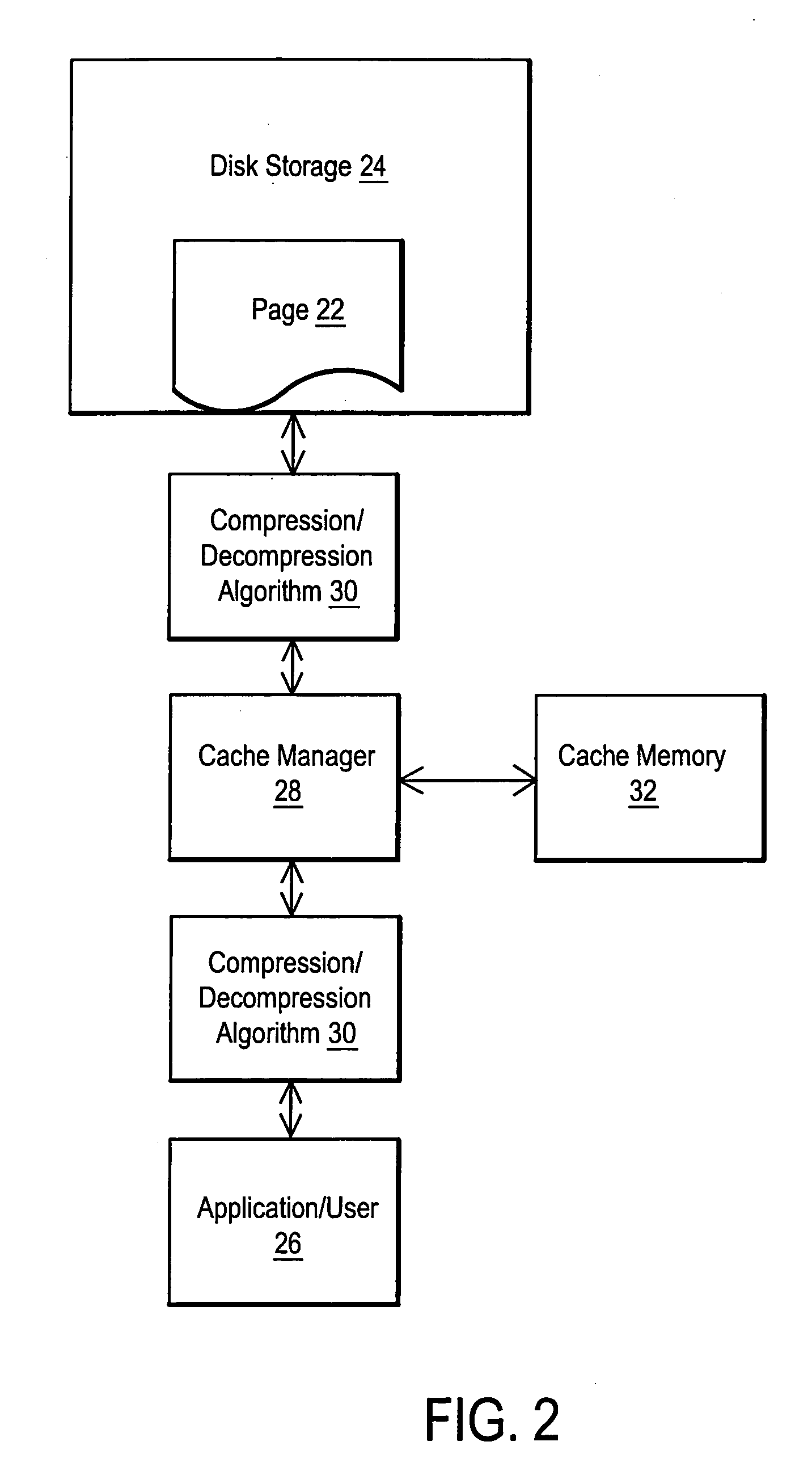
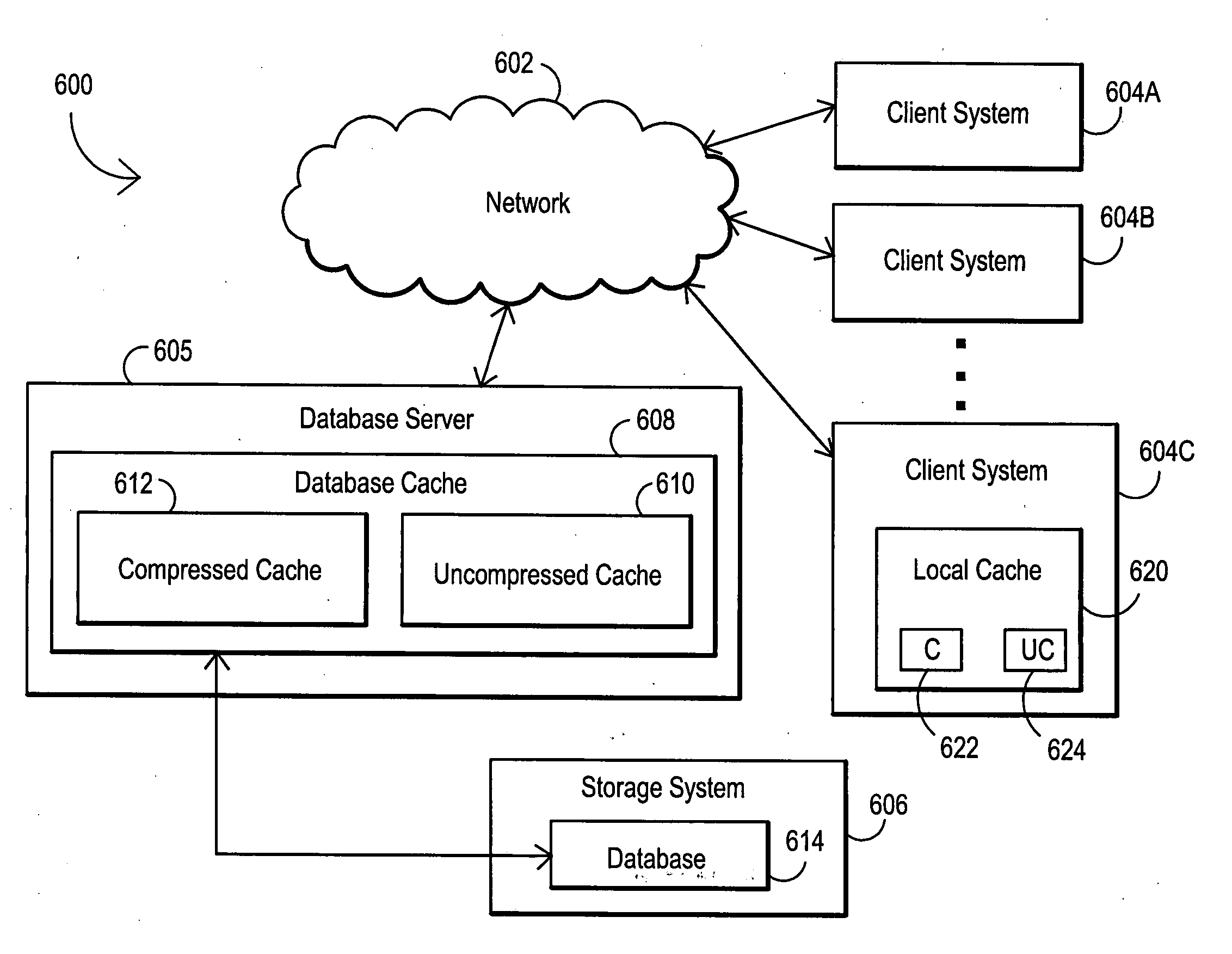
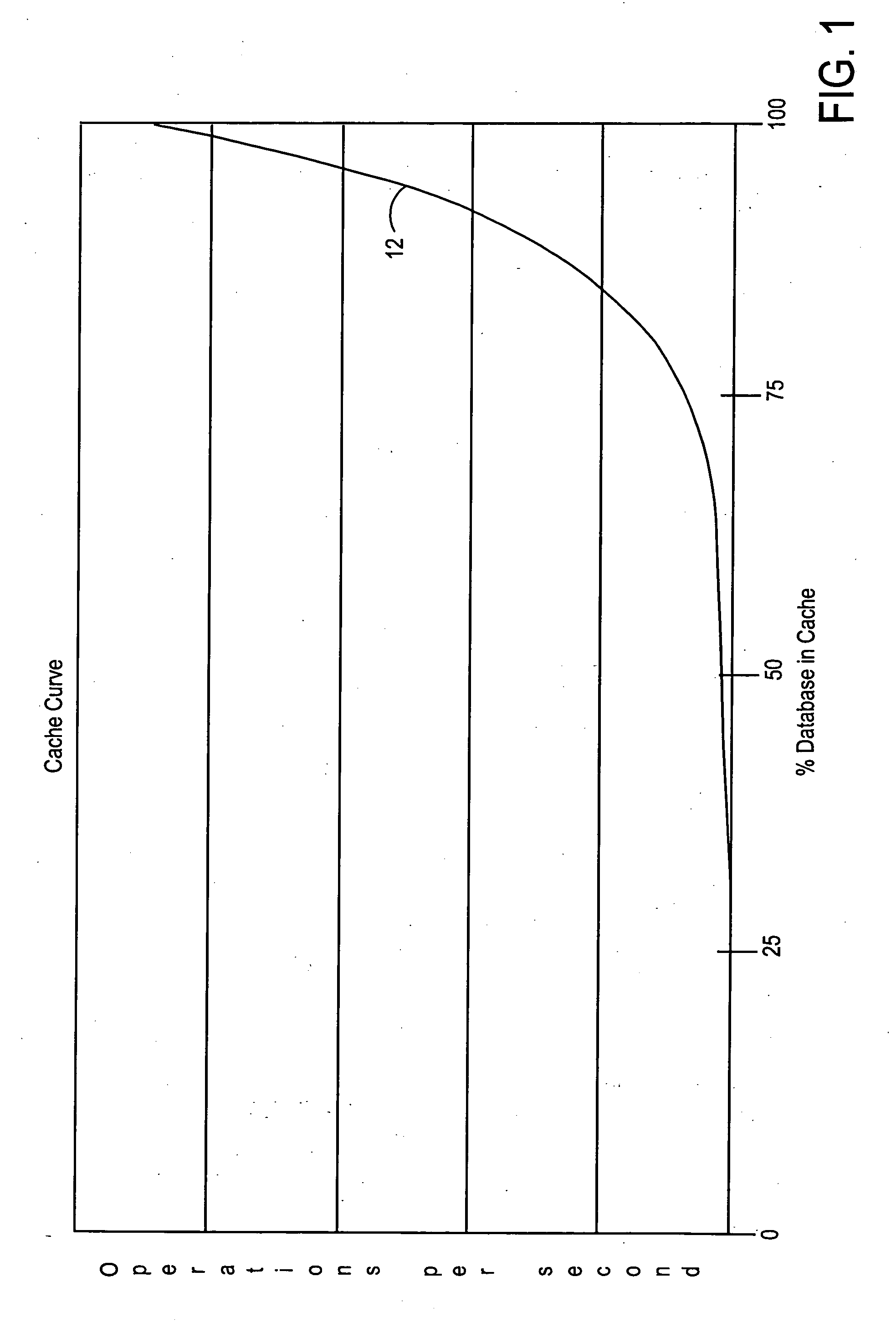
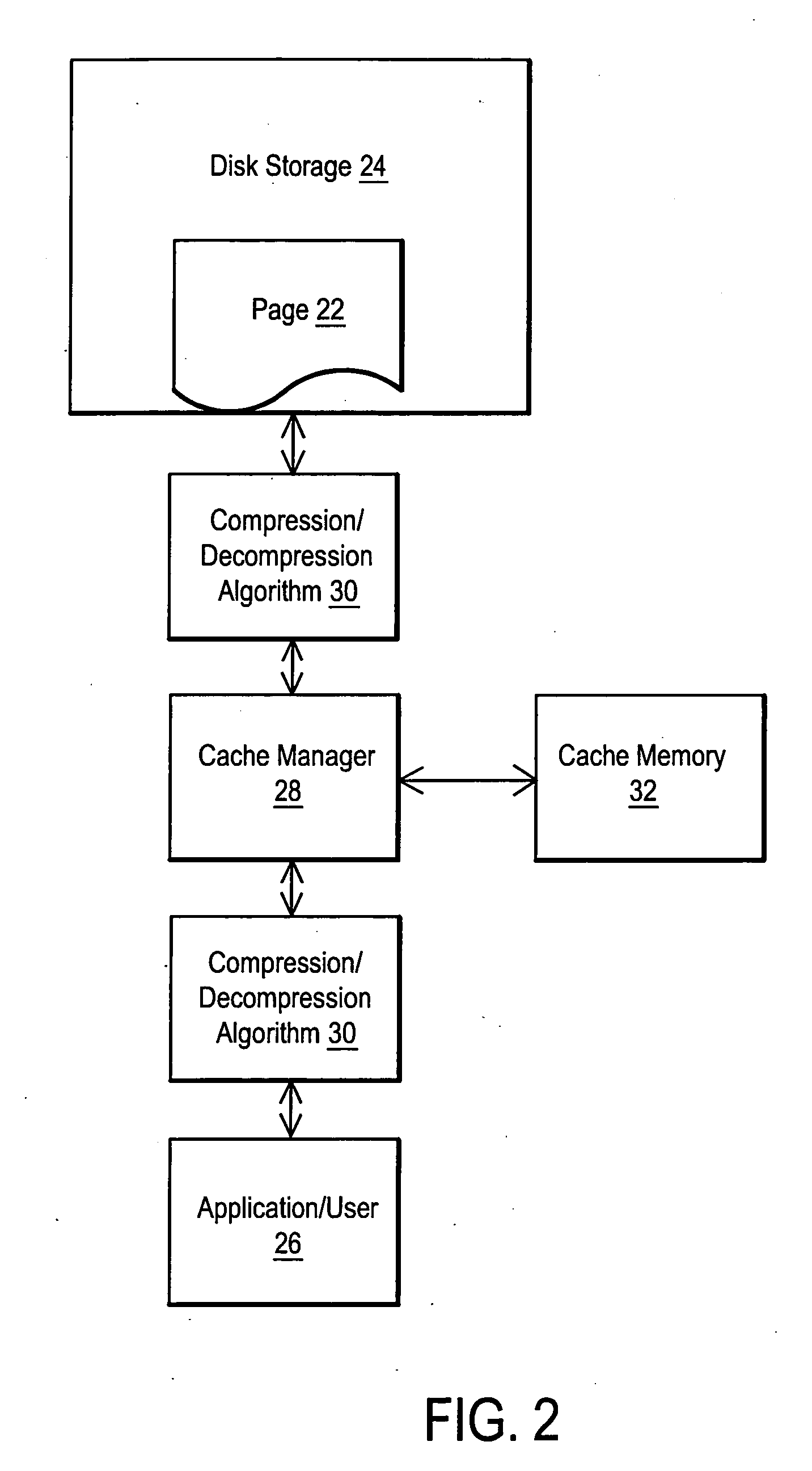
System and method for utilizing compression in database caches to facilitate access to database information
ActiveUS7181457B2Easy accessEnhance operations-per-second capabilityMemory architecture accessing/allocationData processing applicationsAccess timeData access
A system and method are disclosed for utilizing compression in database caches to facilitate access to database information. In contrast with applying compression to the database that is stored on disk, the present invention achieves performance advantages by using compression within the main memory database cache used by a database management system to manage data transfers to and from a physical database file stored on a storage system or stored on a networked attached device or node. The disclosed system and method thereby provide a significant technical advantage by increasing the effective database cache size. And this effective increase in database cache size can greatly enhance the operations-per-second capability of a database management system by reducing unnecessary disk or network accesses thereby reducing data access times.
Owner:ACTIAN CORP
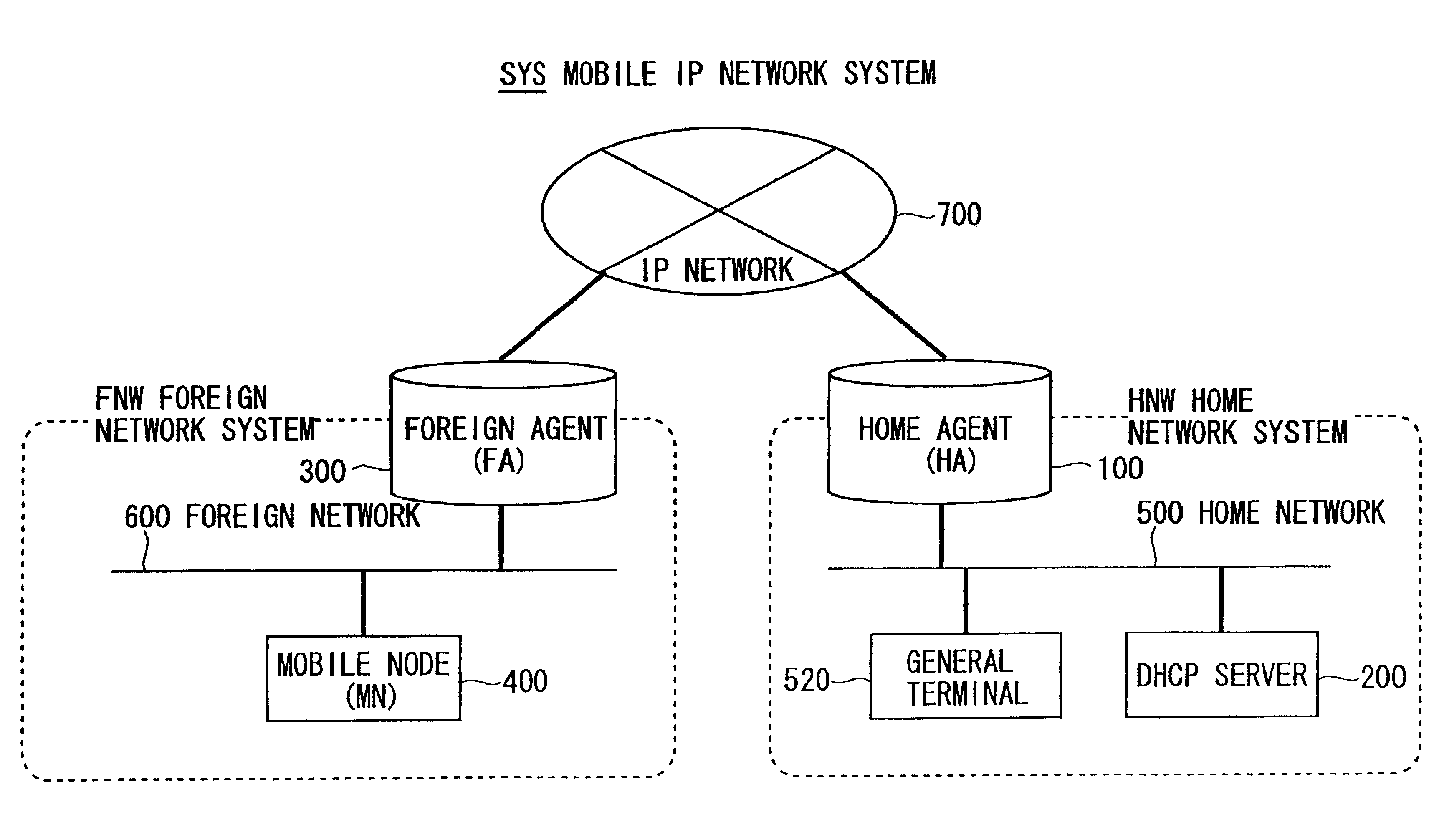
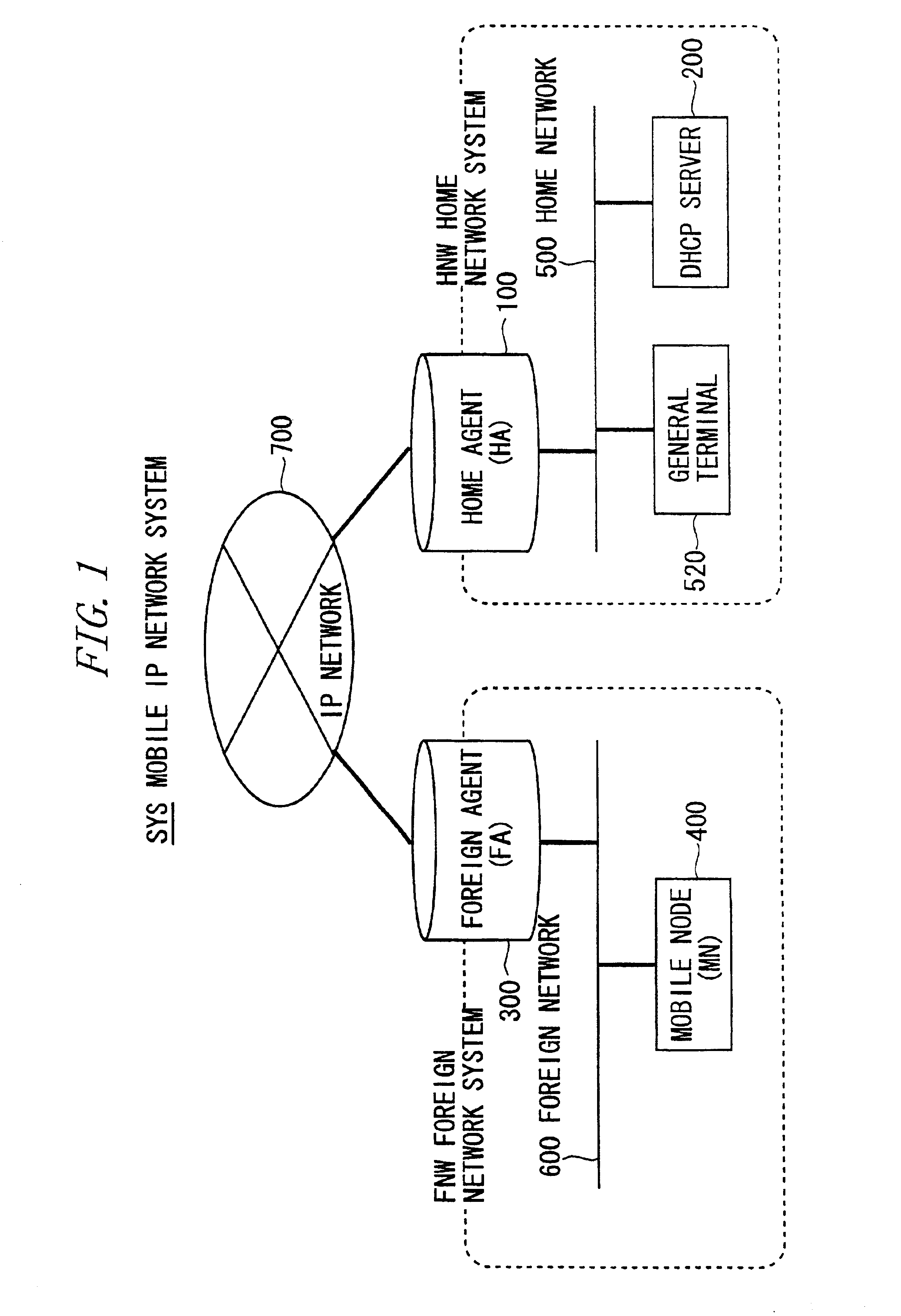
Mobile IP network system
InactiveUS6928282B2Good serviceShorten the counting processNetwork topologiesMultiple digital computer combinationsComputer networkMobile IP
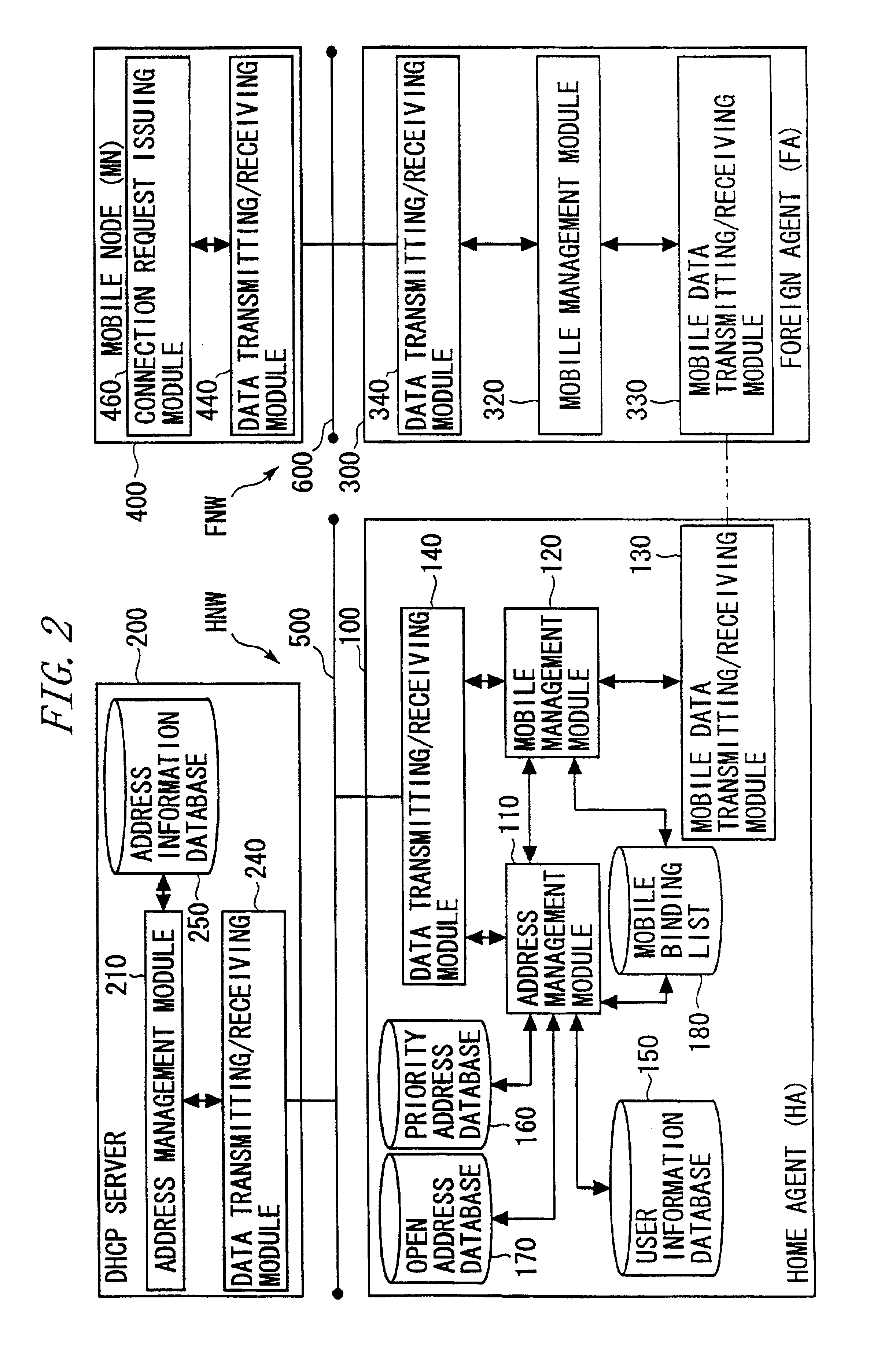
A home agent provides mobility transparent communications to a mobile node temporarily connected to a second network as a mobile destination different from a first network normally utilized. The home agent includes a module receiving a new registration request from the mobile node via the second network, a module detecting, when receiving the new registration request, that lease addresses of a DHCP server and addresses pooled beforehand are all occupied, and a module searching for, when detecting that all the addresses are occupied, an address on the basis of self-managed information and allocating the searched address to the mobile node.
Owner:FUJITSU LTD
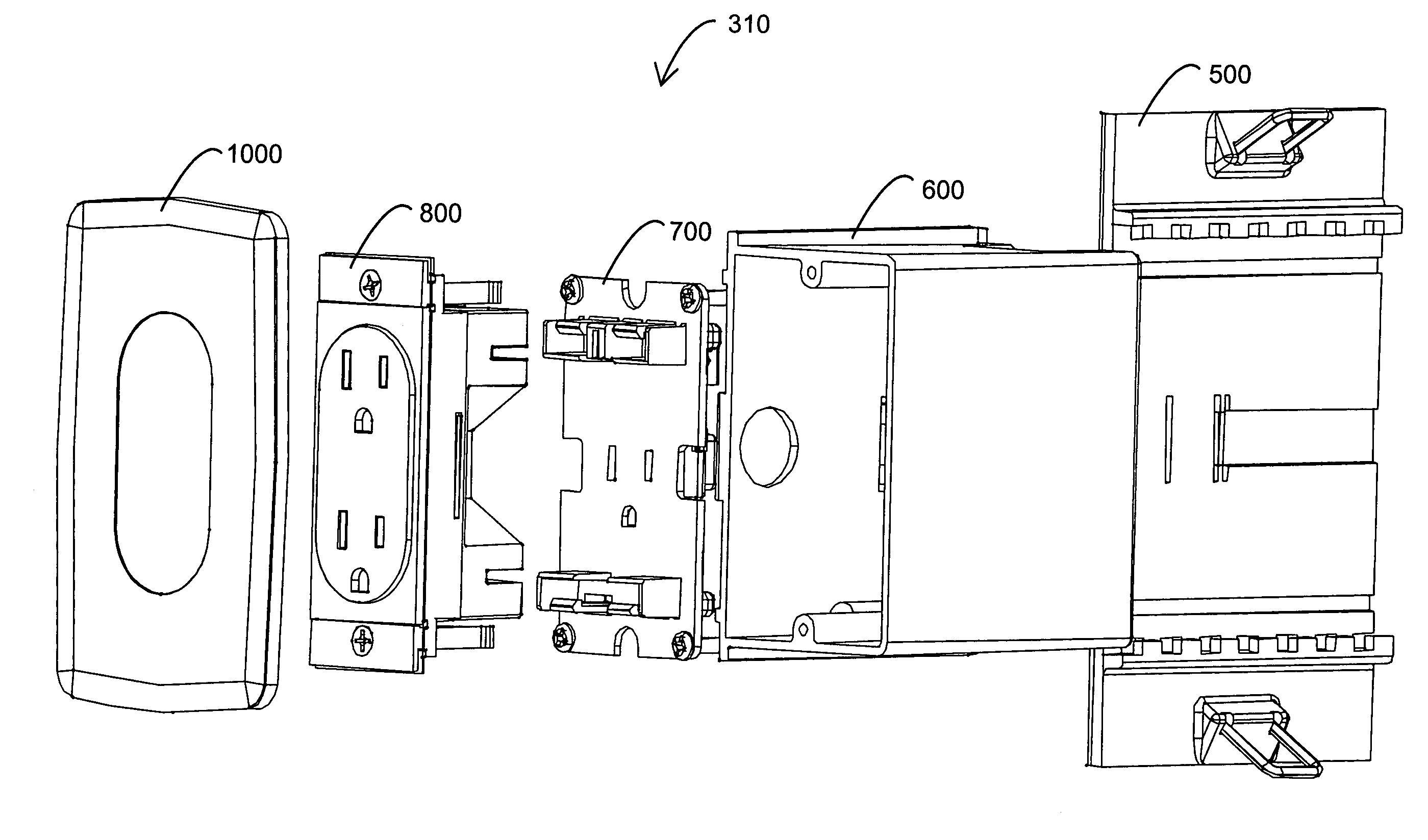
Safety outlet module
InactiveUS6894221B2Safe and easy replacementReduce exposureTwo pole connectionsInsulated cablesEngineeringMechanical engineering
A safety outlet module includes a housing, a receptacle defined by the housing, an aperture defined within the receptacle, a cover slidably retained within the receptacle and a plug retained at least partially within the housing. The receptacle has an opening, a bottom and a wall extending between the opening and the bottom. The aperture partially extends along the wall. The cover has a closed position proximate the opening and an open position proximate the bottom. The aperture is blocked in the closed position and exposed in the open position. The plug extends from a housing face and is adapted to removably connect to an electrical power source. A contact is retained by the housing outside of the receptacle and proximate to the aperture, and a buss internal to the housing connects the plug to the contact.
Owner:BAUM FAMILY TRUST DTD 1 11 2001 +143
System and method for utilizing compression in database caches to facilitate access to database information
ActiveUS20050015374A1Facilitate accessIncreasing effective database cache sizeMemory architecture accessing/allocationData processing applicationsSystem usageDatabase file
A system and method are disclosed for utilizing compression in database caches to facilitate access to database information. In contrast with applying compression to the database that is stored on disk, the present invention achieves performance advantages by using compression within the main memory database cache used by a database management system to manage data transfers to and from a physical database file stored on a storage system or stored on a networked attached device or node. The disclosed system and method thereby provide a significant technical advantage by increasing the effective database cache size. And this effective increase in database cache size can greatly enhance the operations-per-second capability of a database management system by reducing unnecessary disk or network accesses thereby reducing data access times.
Owner:ACTIAN CORP
Method, apparatus, and system for managing label of access network
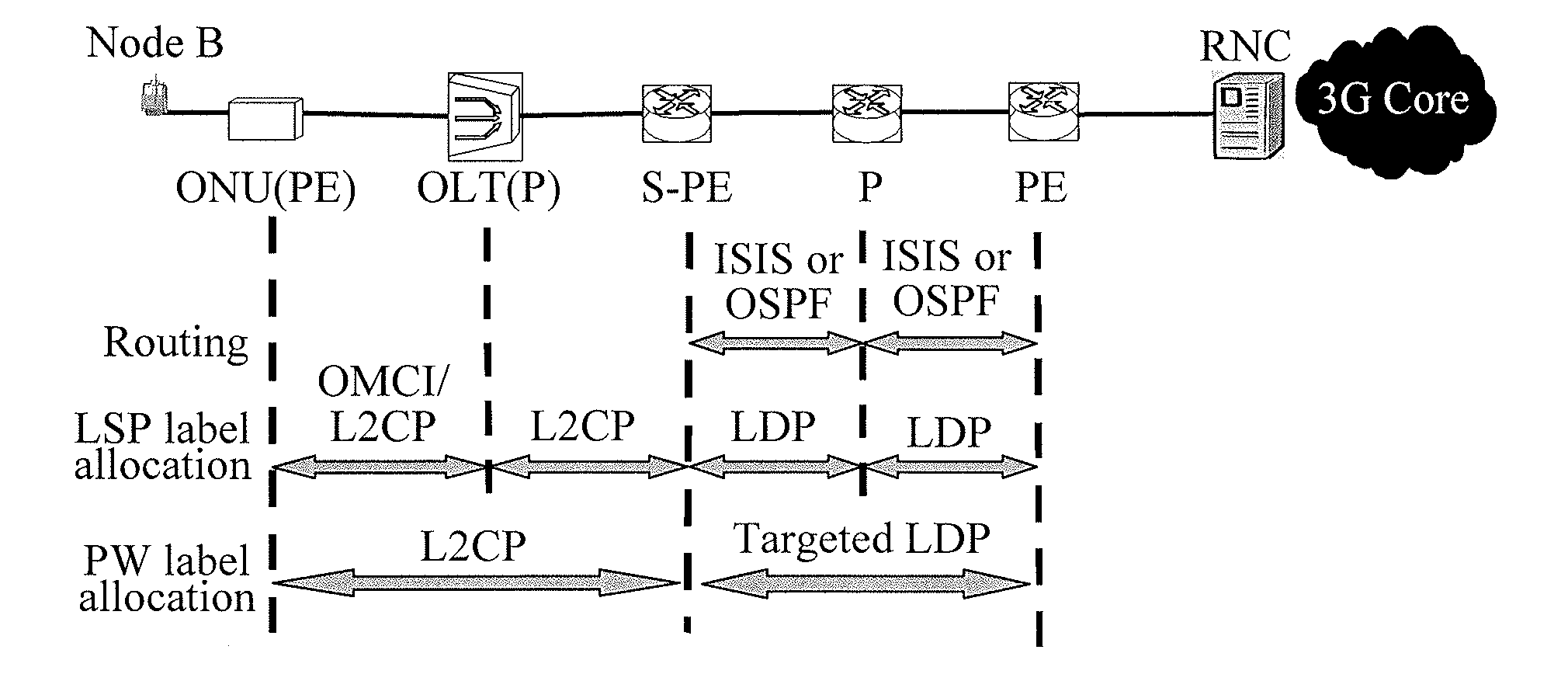
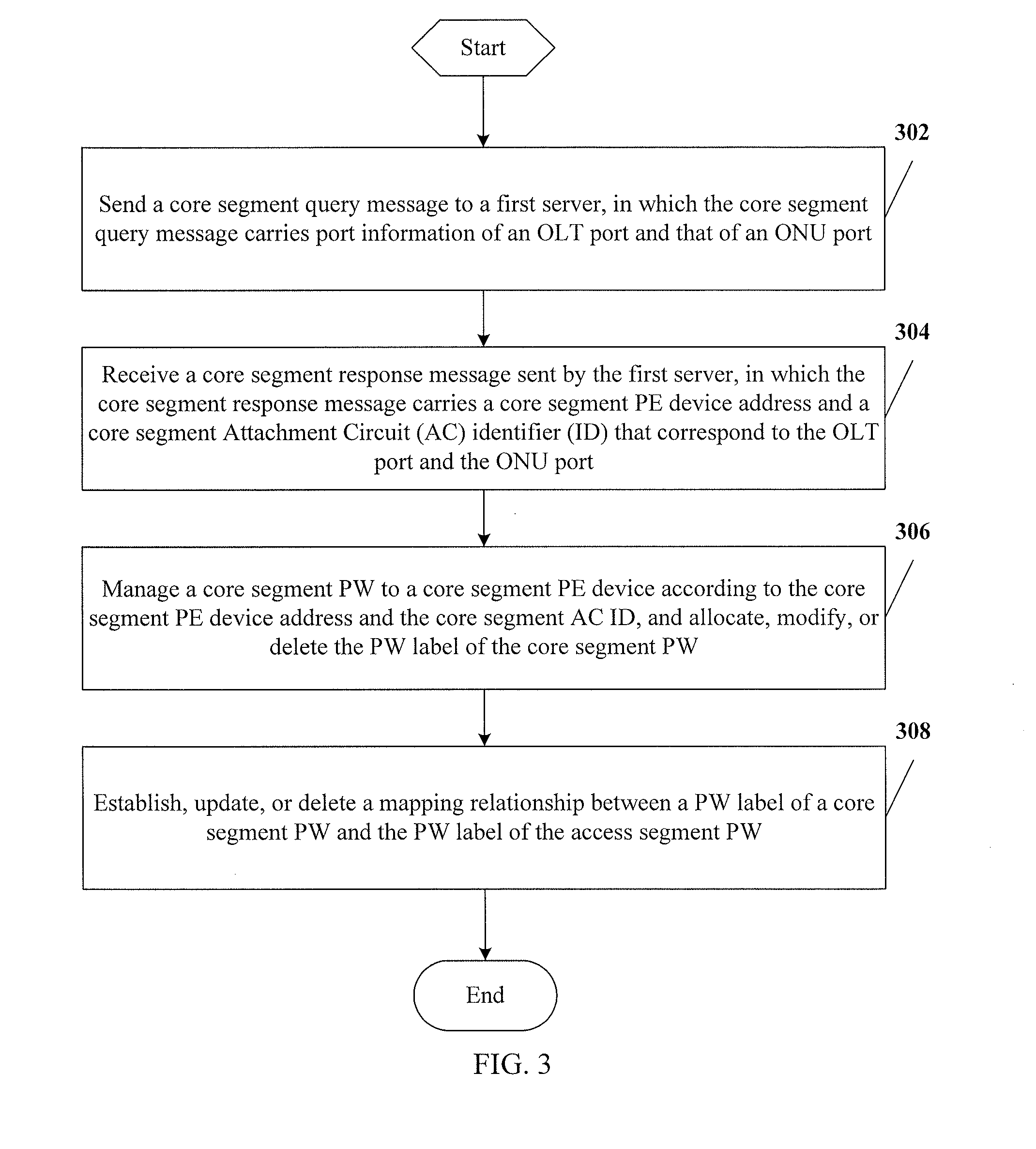
ActiveUS20120099861A1Reduce accessMultiplex system selection arrangementsOptical multiplexAccess networkNetwork communication
The present invention relates to the field of network communications. An Optical Line Terminal (OLT) allocates a Pseudo Wire (PW) label of an access segment PW for a port, and establishes a corresponding relationship between the port information and the PW label; and carries the corresponding relationship between the port information and the PW label in a label management message, and sends the label management message to an Optical Network Unit (ONU) so that the ONU updates a forwarding table, in which the label management message adopts an access network management protocol. As a consequence, a problem of supporting Pseudo Wire Emulation Edge-to-Edge (PWE3) on a data plane of an access segment of an access network is solved under the conditions that device complexity of the ONU is not increased and a configuration of the ONU is slightly changed.
Owner:HUAWEI TECH CO LTD
Valve port and method for vascular access
InactiveUS20070016162A1Reduce accessReduce riskInfusion syringesMedical devicesLocking mechanismBiomedical engineering
Owner:PROVIFLO A MISSISSIPPI CORP
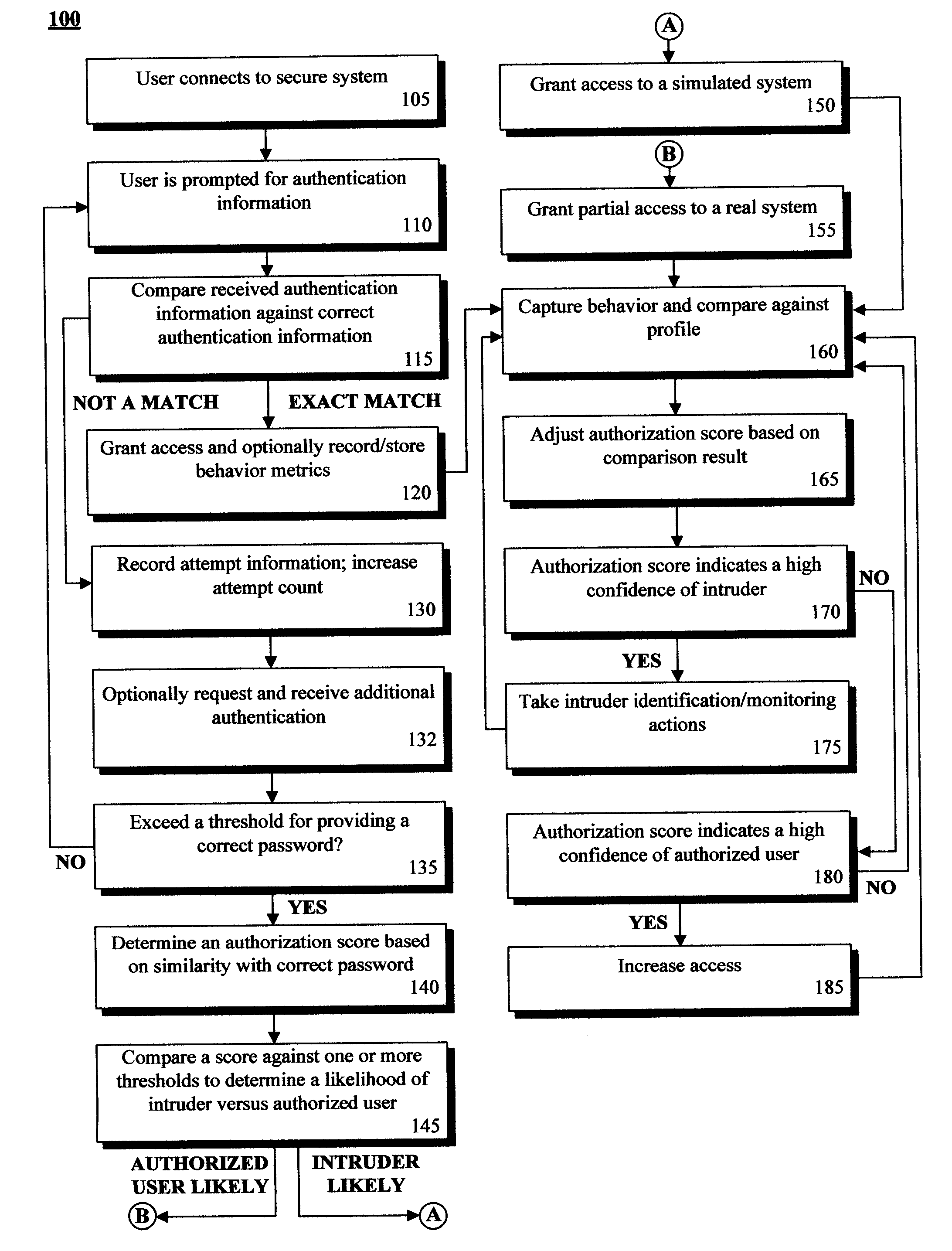
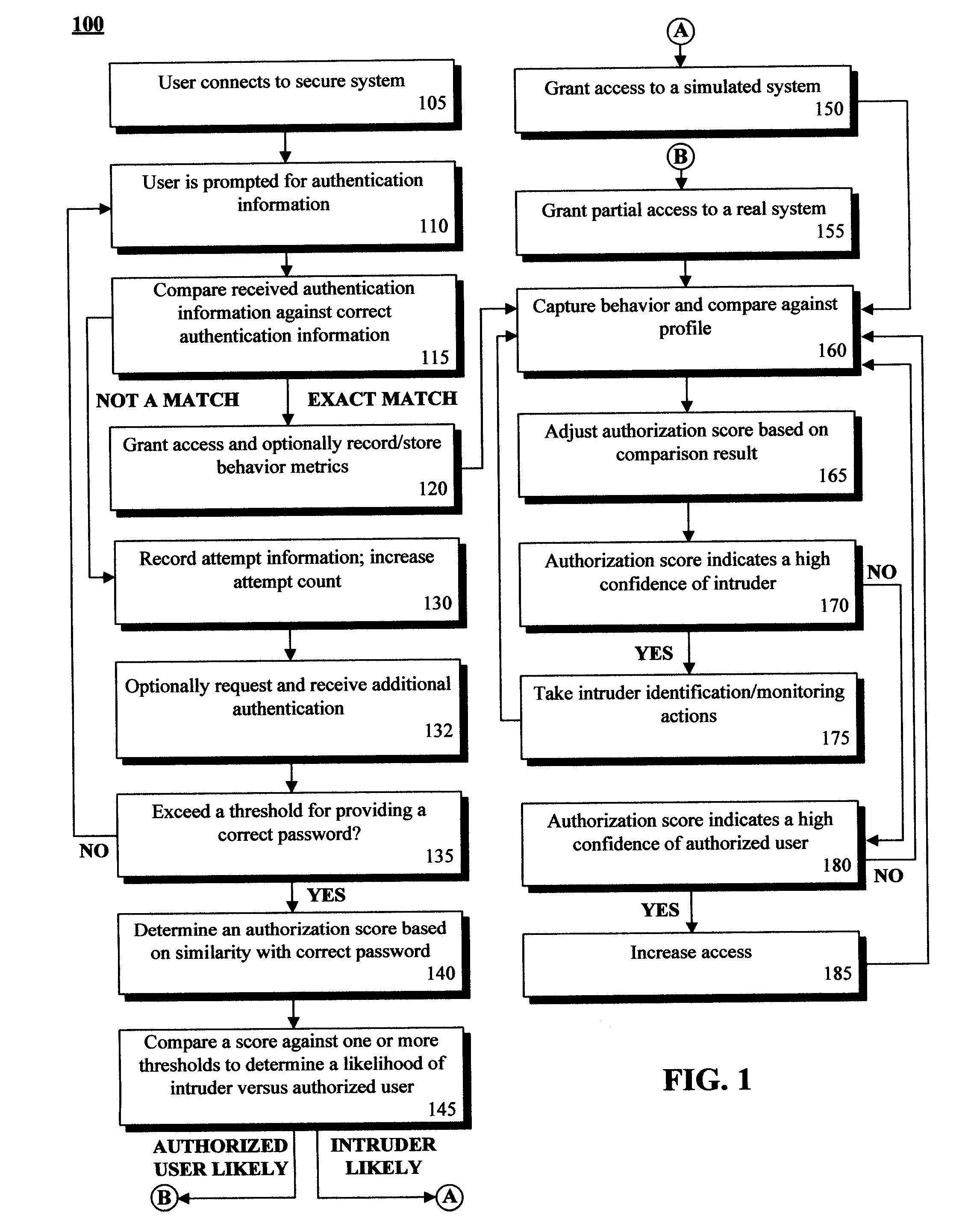
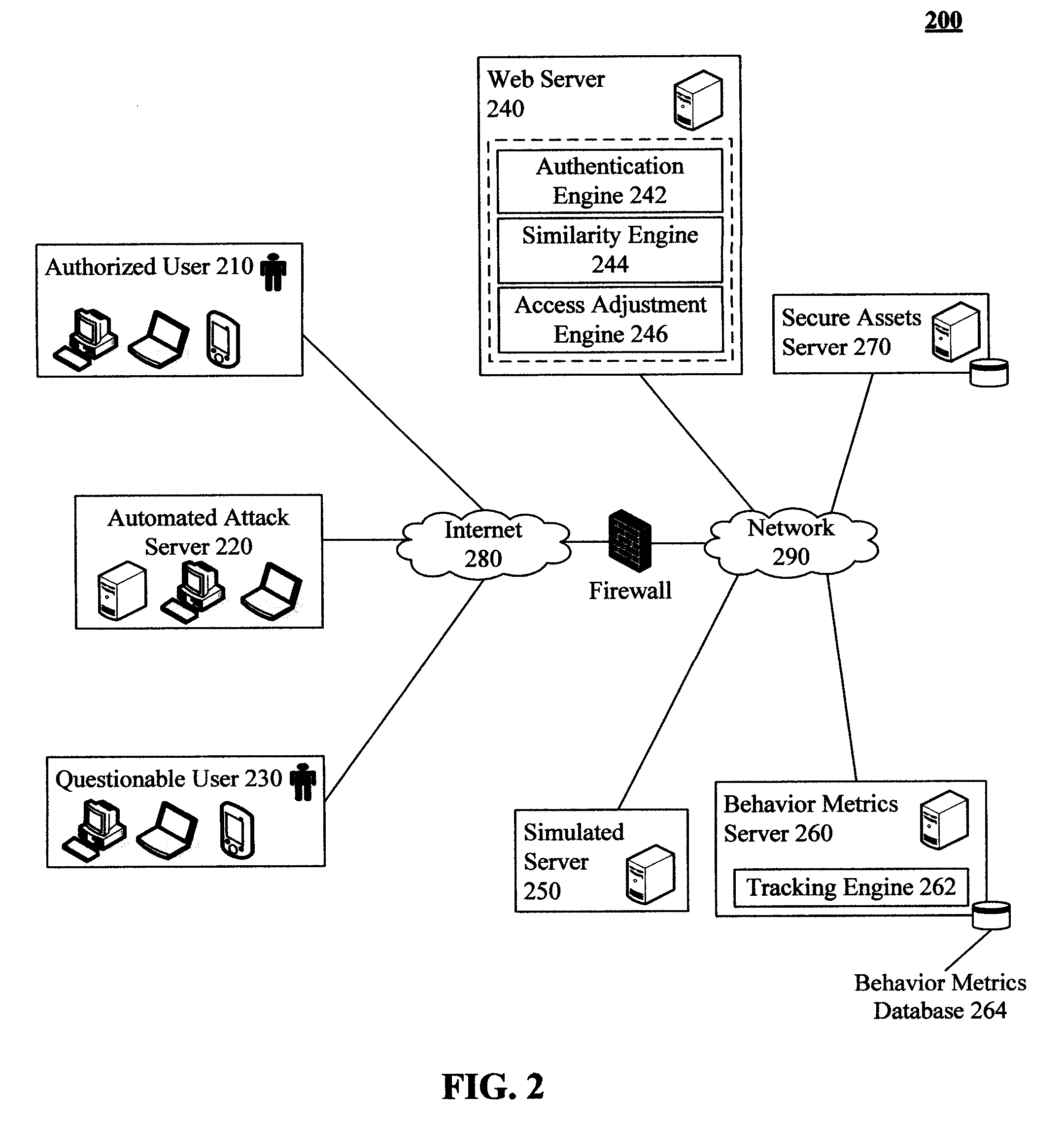
Adaptive authentication solution that rewards almost correct passwords and that simulates access for incorrect passwords
InactiveUS20090006856A1Reduce level of accessIncrease of access levelDigital data processing detailsAnalogue secracy/subscription systemsLimited accessPassword
In the invention, incorrect authentication information for accessing at least one secured computing asset can be received. A similarity score between the incorrect authentication information and correct authentication information can be determined. One of many different access levels can be assigned to a computing session based upon the similarity score. Access consistent with the assigned access level can be granted. One access level can be an emulation access level that grants access to at least one simulated asset designed to mimic the secured asset. Access to the simulated asset can be provided in a fashion so that a user, who is likely an intruder, is unaware that they are not receiving the secured asset information. A tracking action can he optionally initiated against the intruder. Further, user behavior with the simulated session or a limited access session can be compared against a behavior profile to dynamically increase or decrease session permissions.
Owner:IBM CORP
Semiconductor memory device comprising a plurality of static memory cells
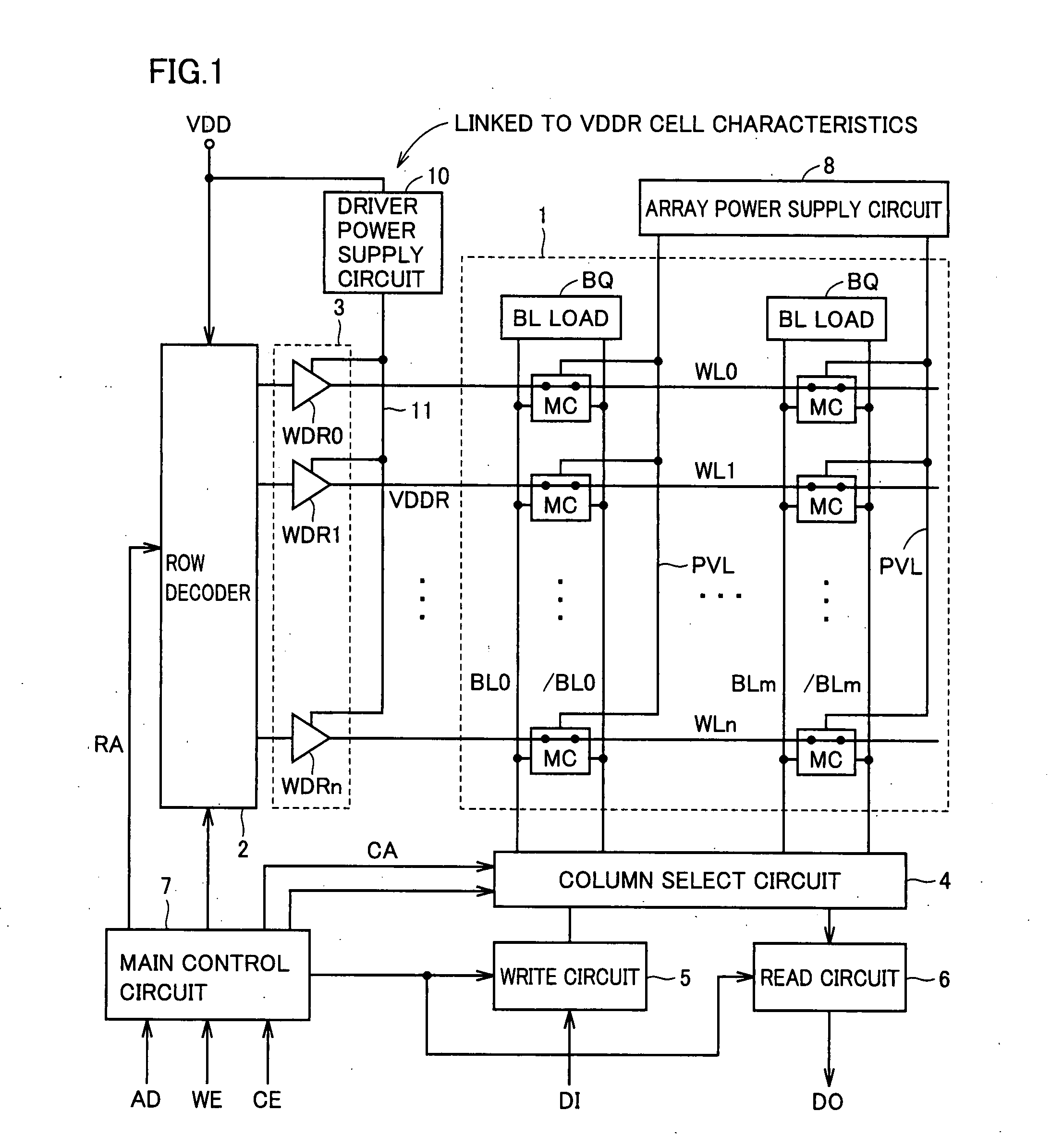
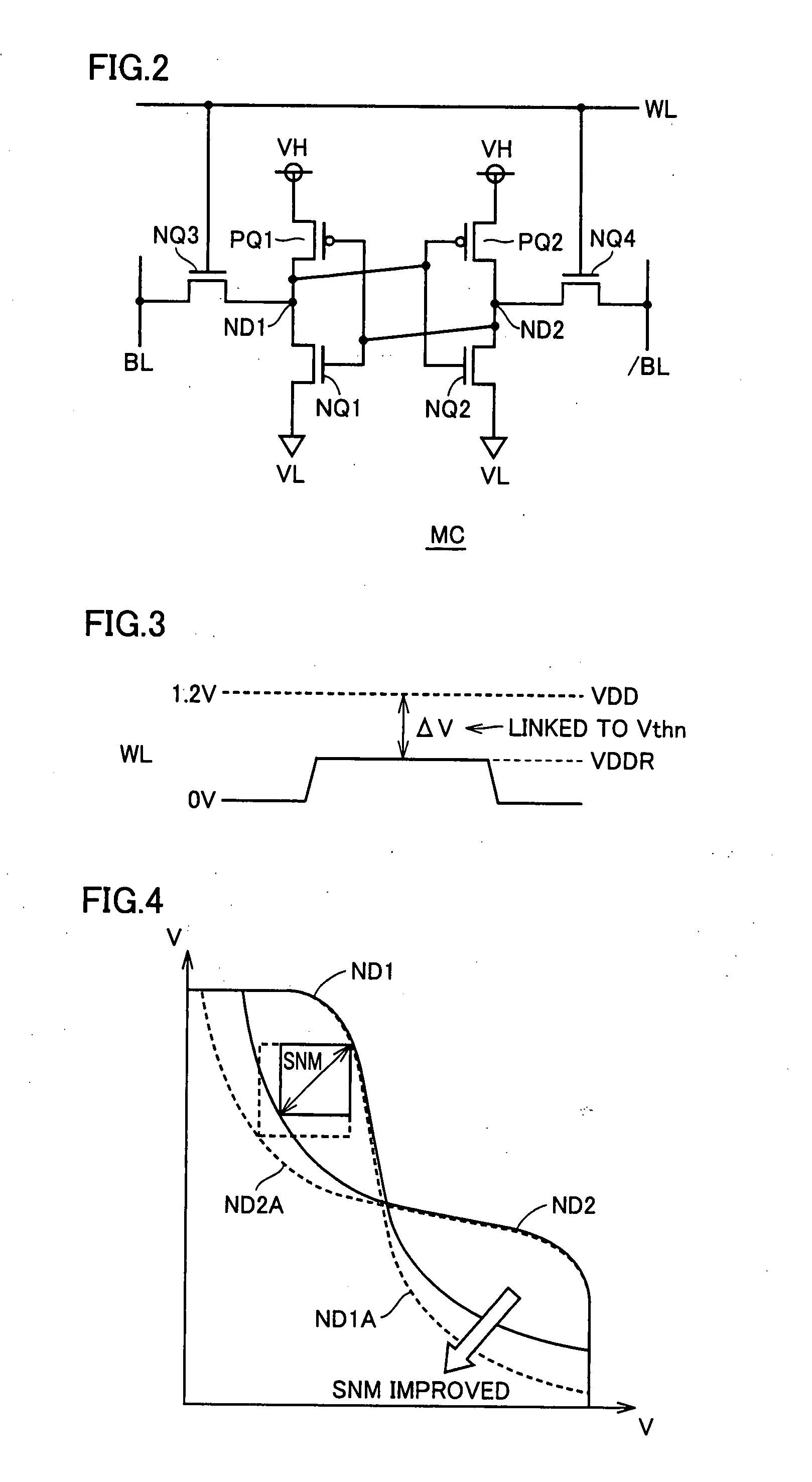
ActiveUS20080037358A1Simple circuit structureStable writing and reading of dataDigital storageHemt circuitsLine driver
A driver power supply circuit stepping down a power supply voltage is arranged at a power supply node of a word line driver. The driver power supply circuit includes a non-silicide resistance element of N+ doped polycrystalline silicon, and a pull-down circuit lowering a voltage level of the driver power supply node. The pull-down circuit includes a pull-down transistor having the same threshold voltage characteristics as a memory cell transistor pulling down a voltage level of the driver power supply node, and a gate control circuit adjusting at least a gate voltage of the pull-down transistor. The gate control circuit corrects the gate potential of the pull-down transistor in a manner linked to variations in threshold voltage of the memory cell transistor.
Owner:RENESAS ELECTRONICS CORP
Apparatus and method for reorganization of mapping information in flash memory
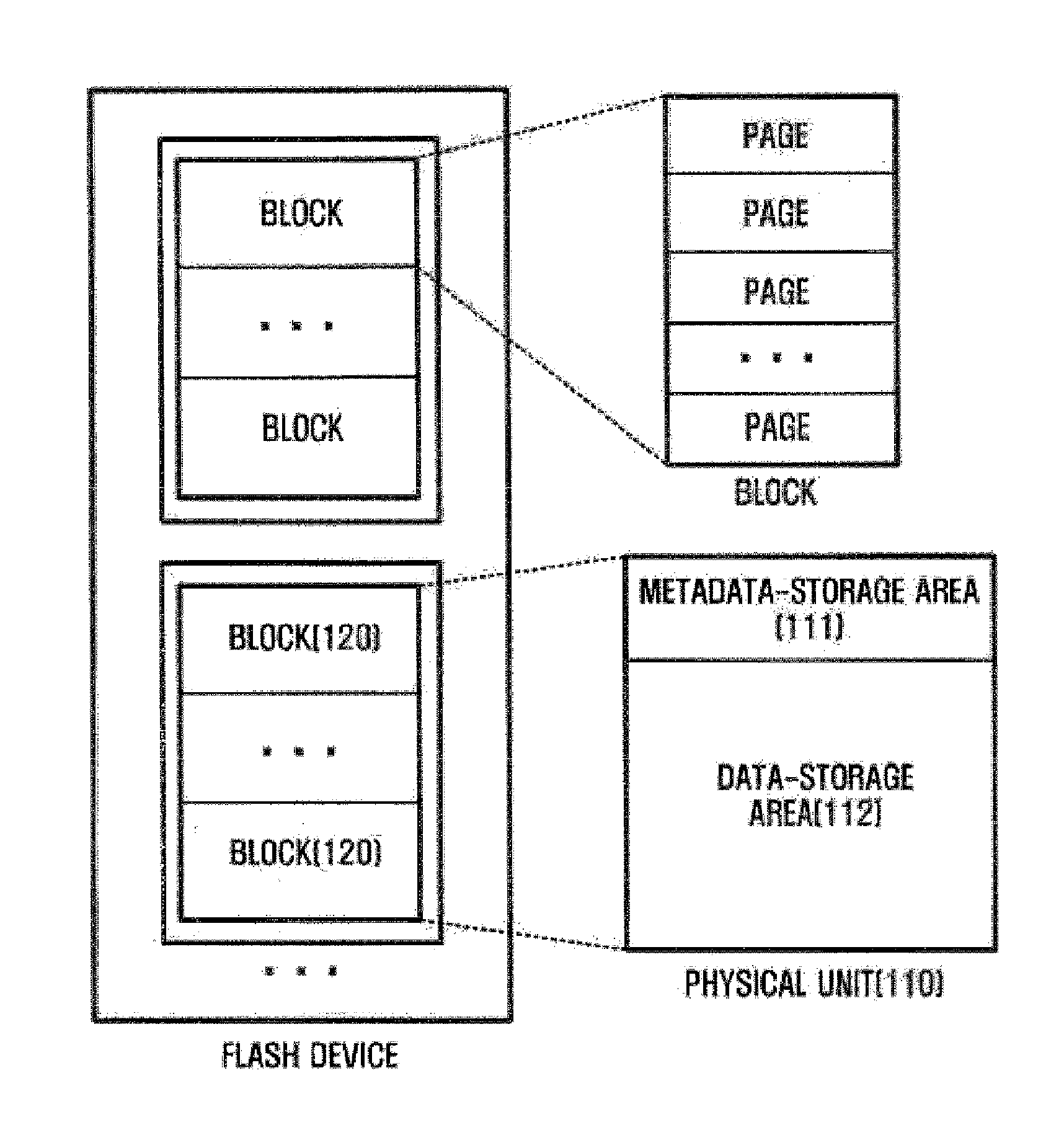
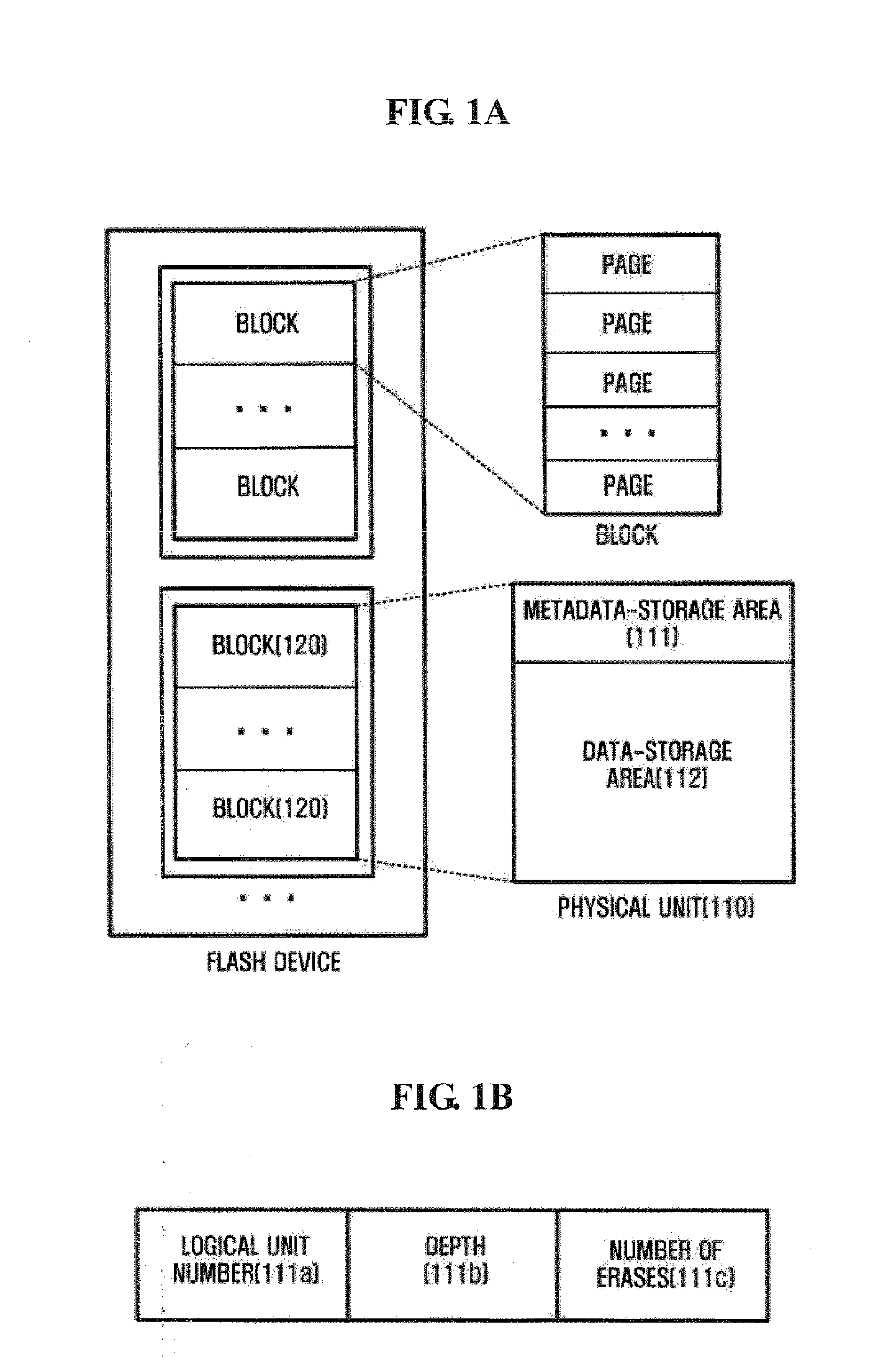
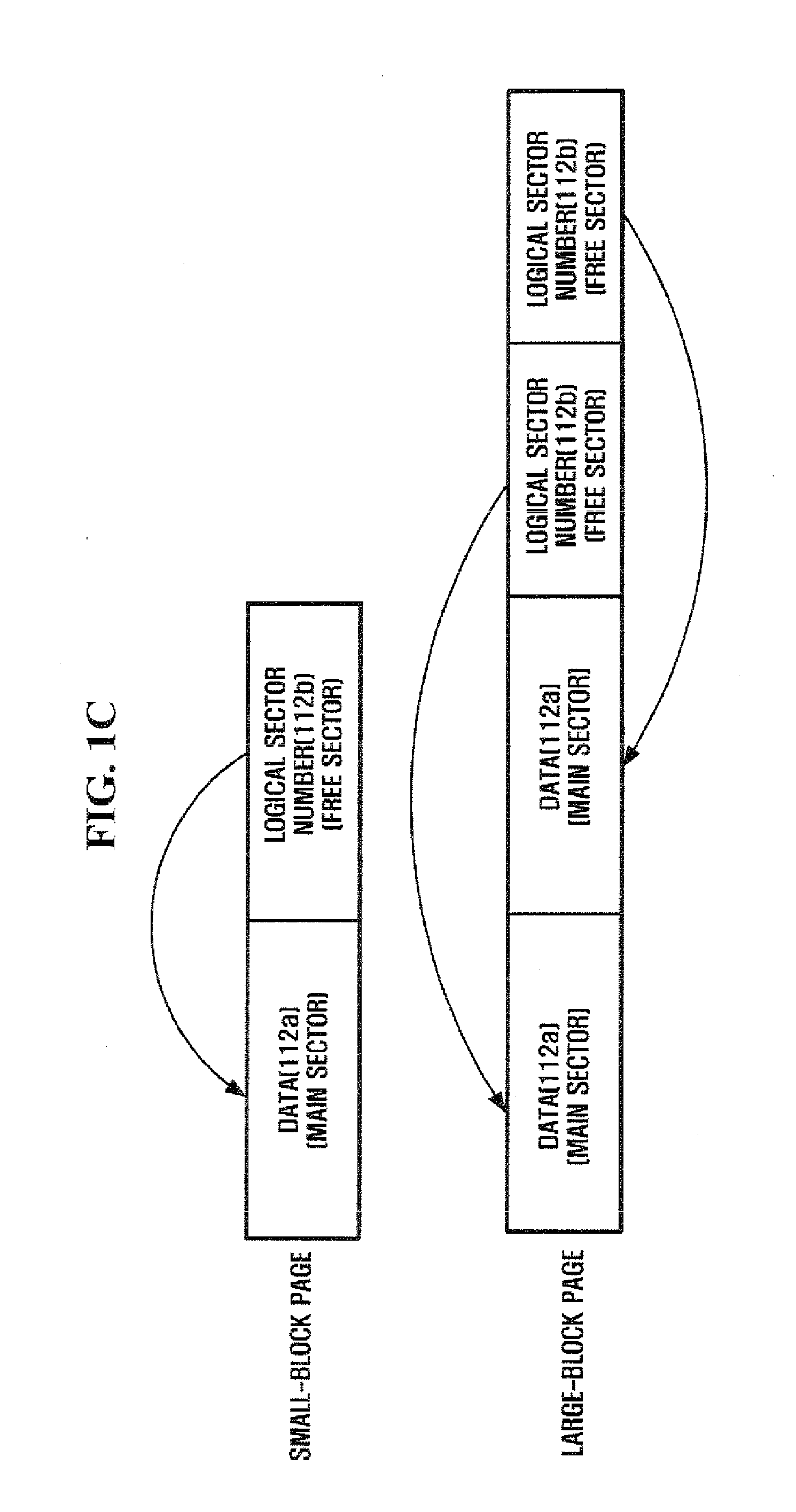
ActiveUS20080071971A1Shorten the timeReduce accessMemory adressing/allocation/relocationPhysical unitFlash memory
An apparatus and method for reorganizing mapping information in a flash memory are provided. The apparatus includes a sector-managing module that secures a mapping sector where mapping information is recorded in a physical unit, and determines whether user data is recorded up to a sector located in a predetermined position, and a mapping-information-recording module that records the mapping information in the mapping sector according to a result of the determination. Here, the mapping information includes a relation of a physical sector storing the user data and a logical sector corresponding to the physical sector.
Owner:SAMSUNG ELECTRONICS CO LTD
Motion compensation method, picture coding method and picture decoding method
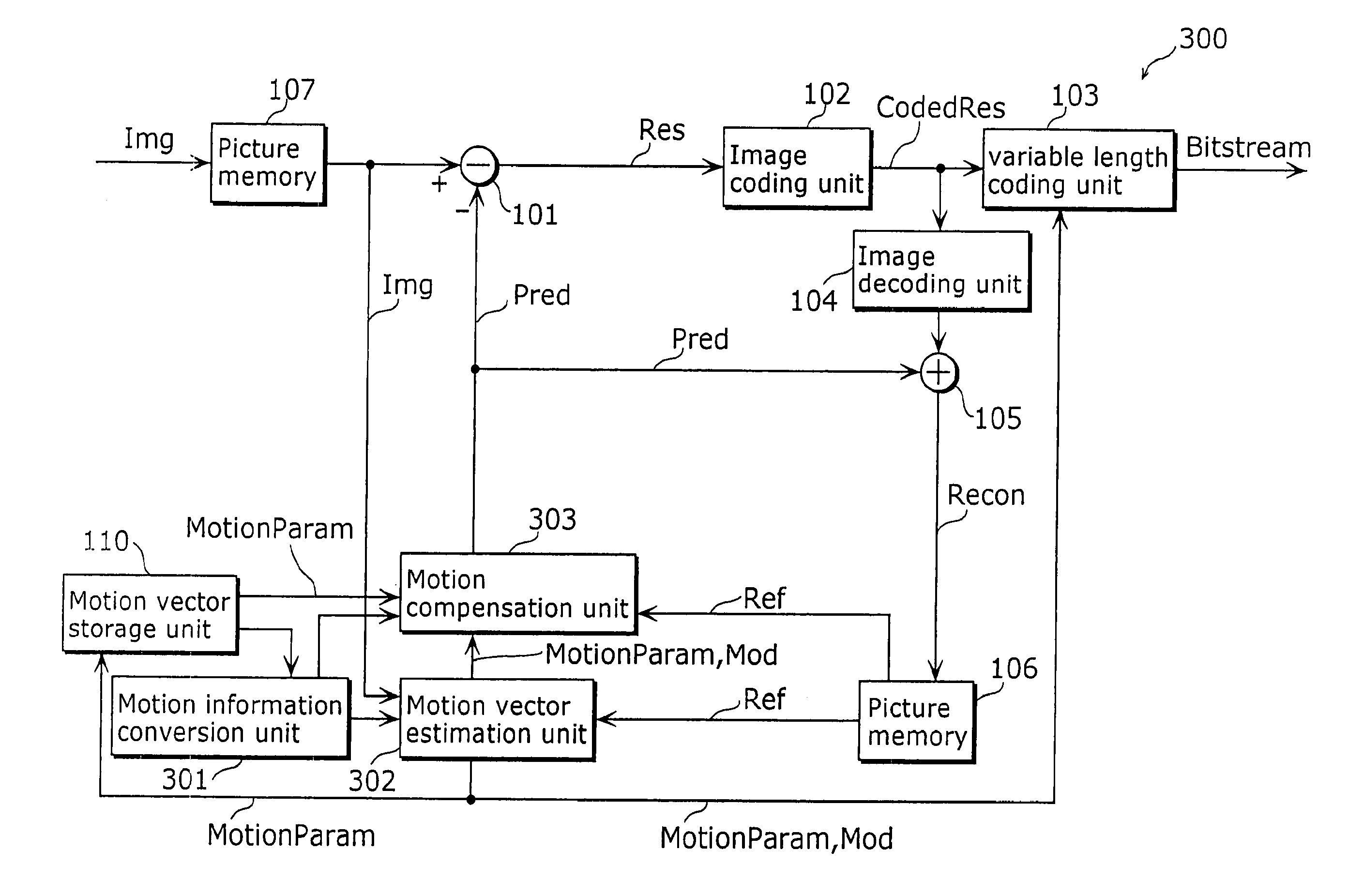
ActiveUS20110286527A1Reduce accessReduce overheadColor television with pulse code modulationColor television with bandwidth reductionPattern recognitionComputer graphics (images)
A picture coding apparatus (300) includes a motion vector estimation unit (302) and a motion compensation unit (303). The motion vector estimation unit (302) selects one method for deriving a motion vector of a block to be motion-compensated, depending on a motion vector of a block located in a corner of a decoded macroblock from among a group of blocks that compose the decoded macroblock corresponding to the current macroblock to be coded and determines the motion vector derived by the selected method for derivation to be a candidate of the motion vector of the current macroblock to be coded. The motion compensation unit (303) generates a predictive image of the block to be motion-compensated based on the estimated motion vector.
Owner:GK BRIDGE 1
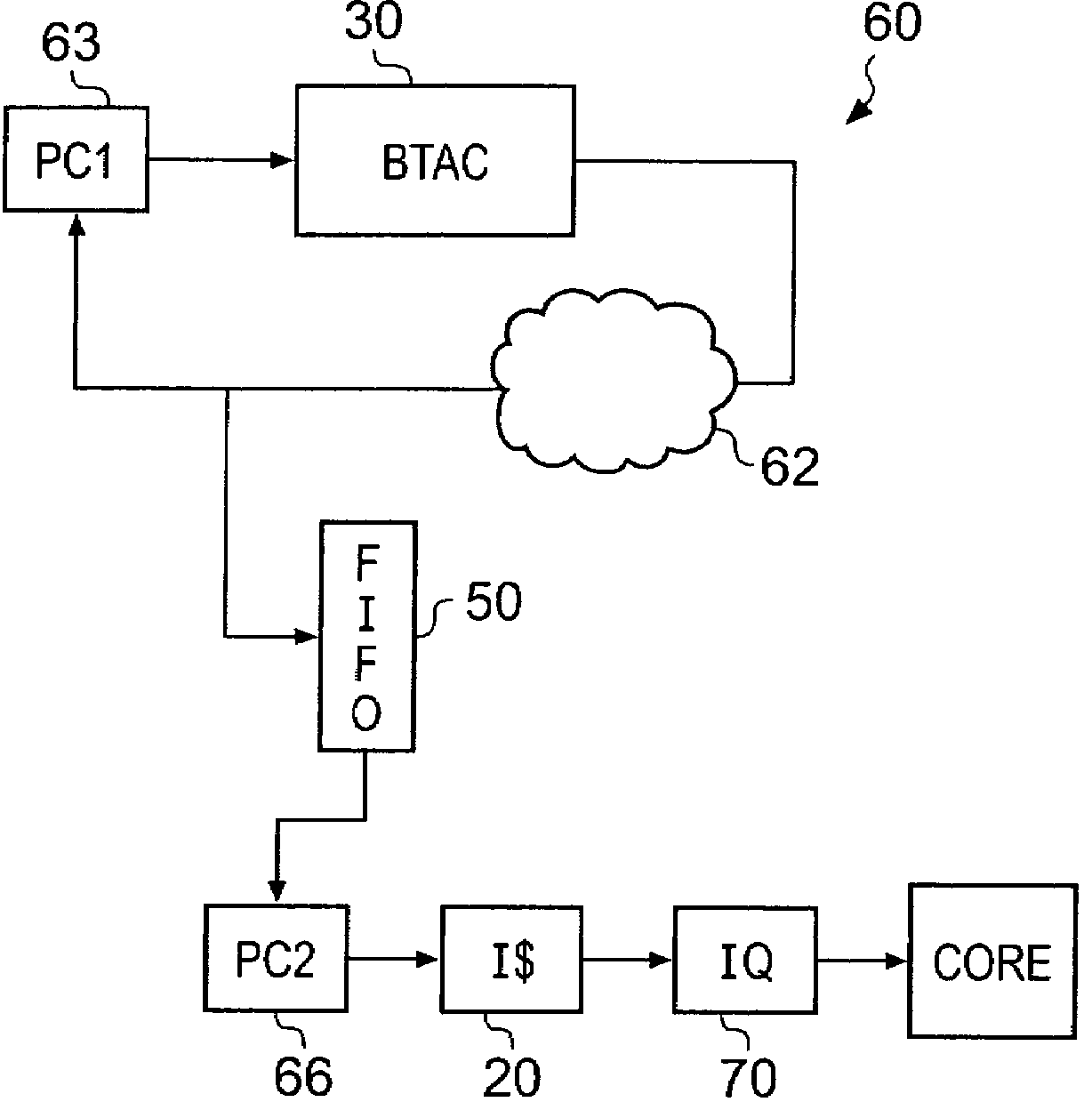
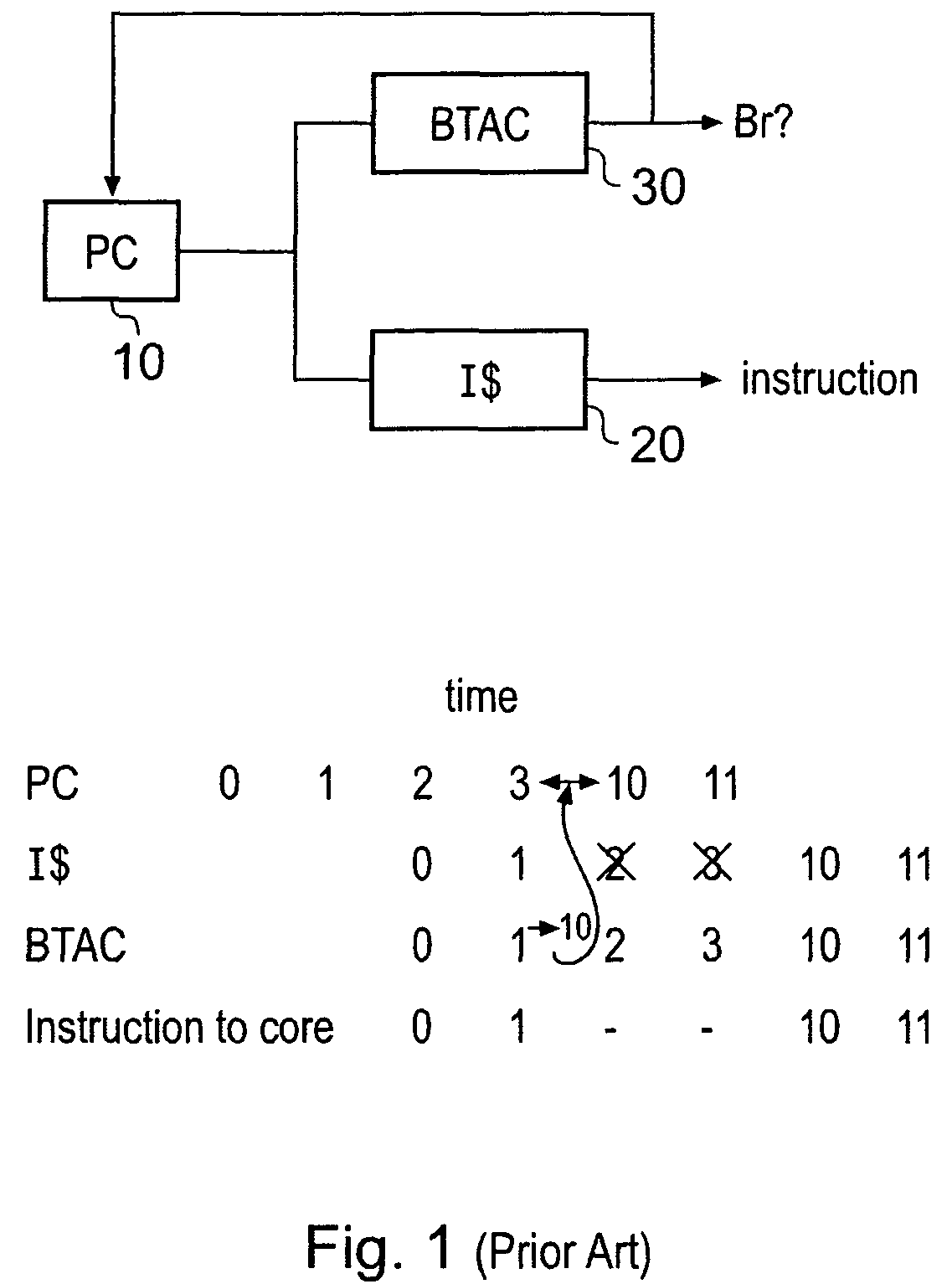
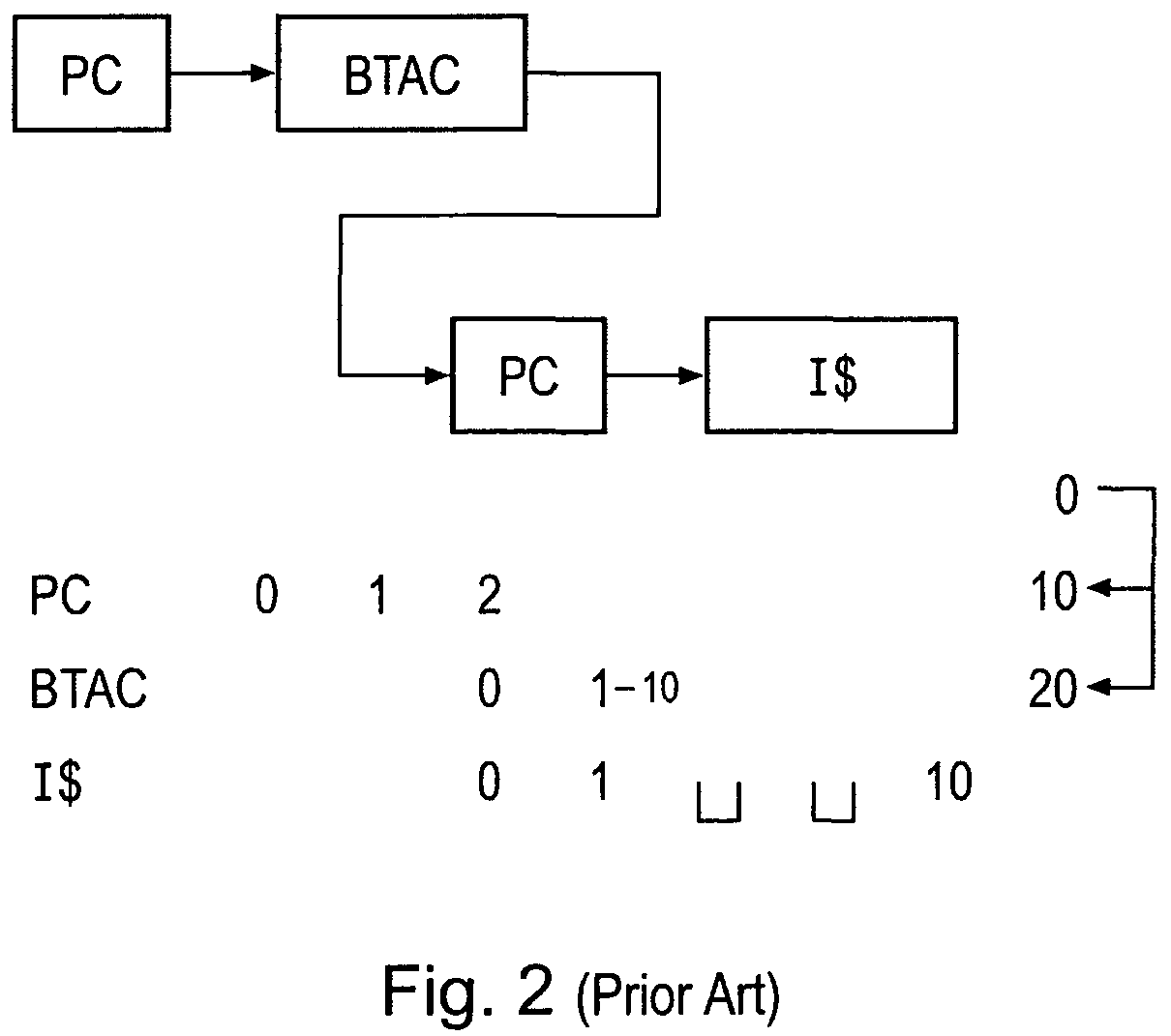
Accessing branch predictions ahead of instruction fetching
ActiveUS7783869B2Lower latencyReduce accessDigital computer detailsSpecific program execution arrangementsData memoryData store
A data processing apparatus is disclosed that comprises: a processor for processing a stream of decoded instructions; a prefetch unit for fetching instructions within a stream of instructions from a memory prior to sending said stream of instructions to said processor; branch prediction logic operable to predict a behaviour of a branch instruction; a branch target cache for storing predetermined information about branch operations executed by said processor, said predetermined information comprising: identification data for an instruction specifying a branch operation and data relating to whether said branch is taken or not; wherein said data processing apparatus is operable to access said branch target cache and to determine if there is data corresponding to instructions within said stream of instructions stored within said branch target cache and if there is to output said data; said data processing apparatus further comprising: a data store operable to store data indicative of a behaviour of a branch instruction; and said data processing apparatus is operable over a period of time to access predetermined information corresponding to more instructions within said branch target cache than instructions it prefetches from said memory such that said accesses to said branch target cache develop an advance in said instruction stream with respect to accesses to said memory; and said prefetch unit is operable to access said data store and to determine if there is data corresponding to an instruction within said data store that indicates that said instruction specifies a branch operation that will be taken and will cause a change in instruction flow.
Owner:ARM LTD
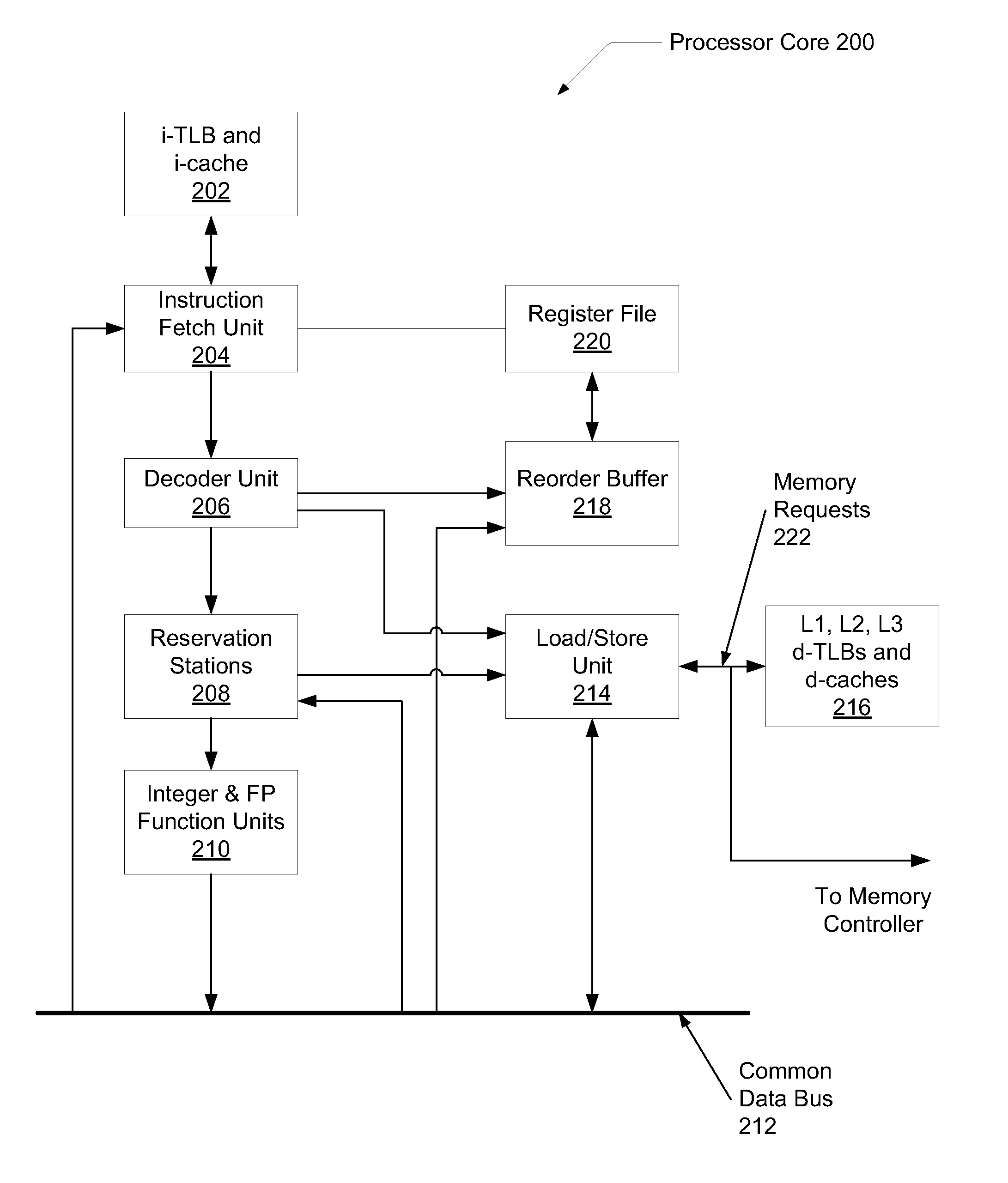
Speculative memory prefetch
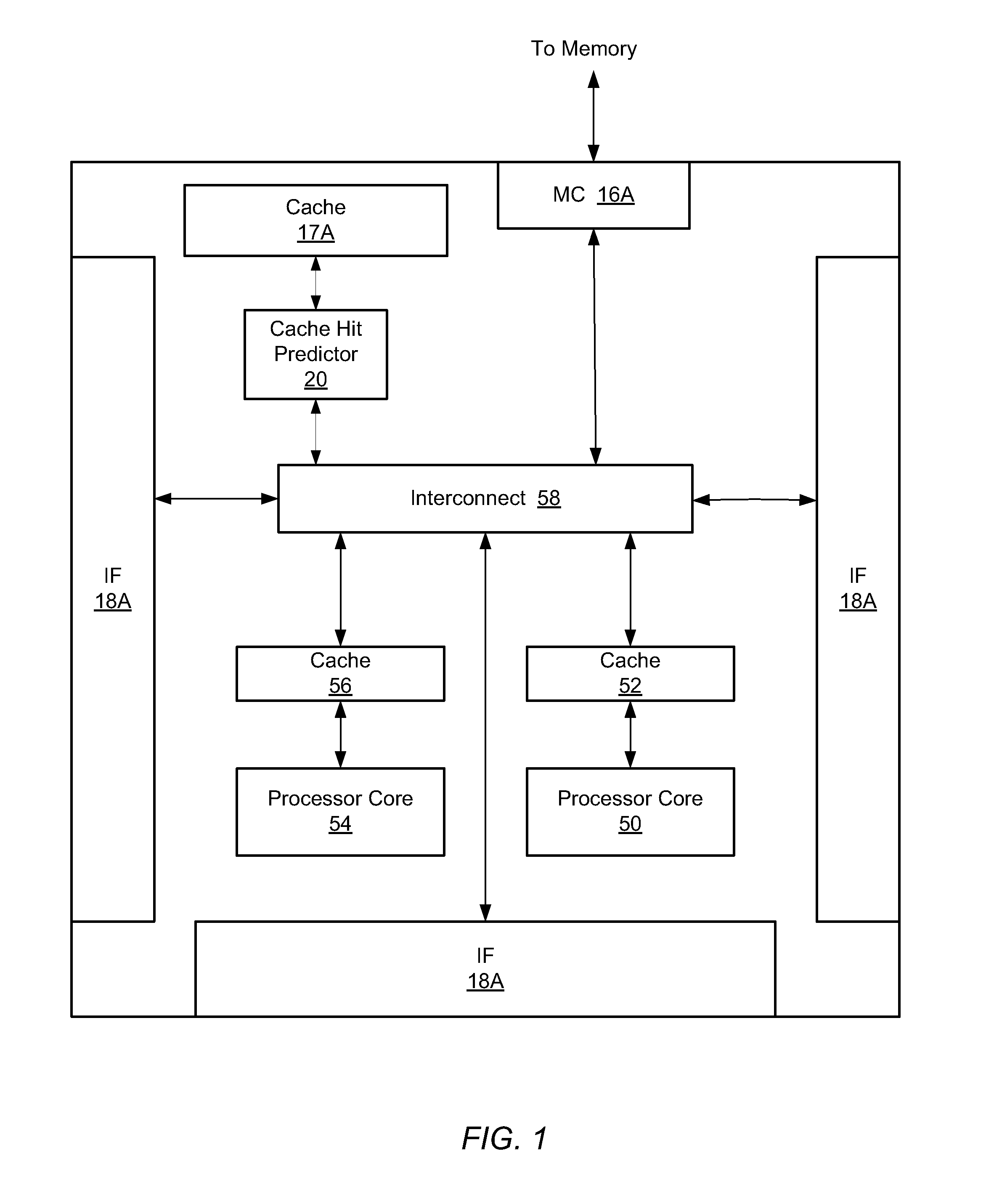
InactiveUS20090024835A1Data reductionReduce data latencyMemory architecture accessing/allocationDigital computer detailsMulti-core processorMemory address
A system and method for pre-fetching data from system memory. A multi-core processor accesses a cache hit predictor concurrently with sending a memory request to a cache subsystem. The predictor has two tables. The first table is indexed by a portion of a memory address and provides a hit prediction based on a first counter value. The second table is indexed by a core number and provides a hit prediction based on a second counter value. If neither table predicts a hit, a pre-fetch request is sent to memory. In response to detecting said hit prediction is incorrect, the pre-fetch is cancelled.
Owner:GLOBALFOUNDRIES INC
Technique for efficiently transferring moderate amounts of data across address space boundary
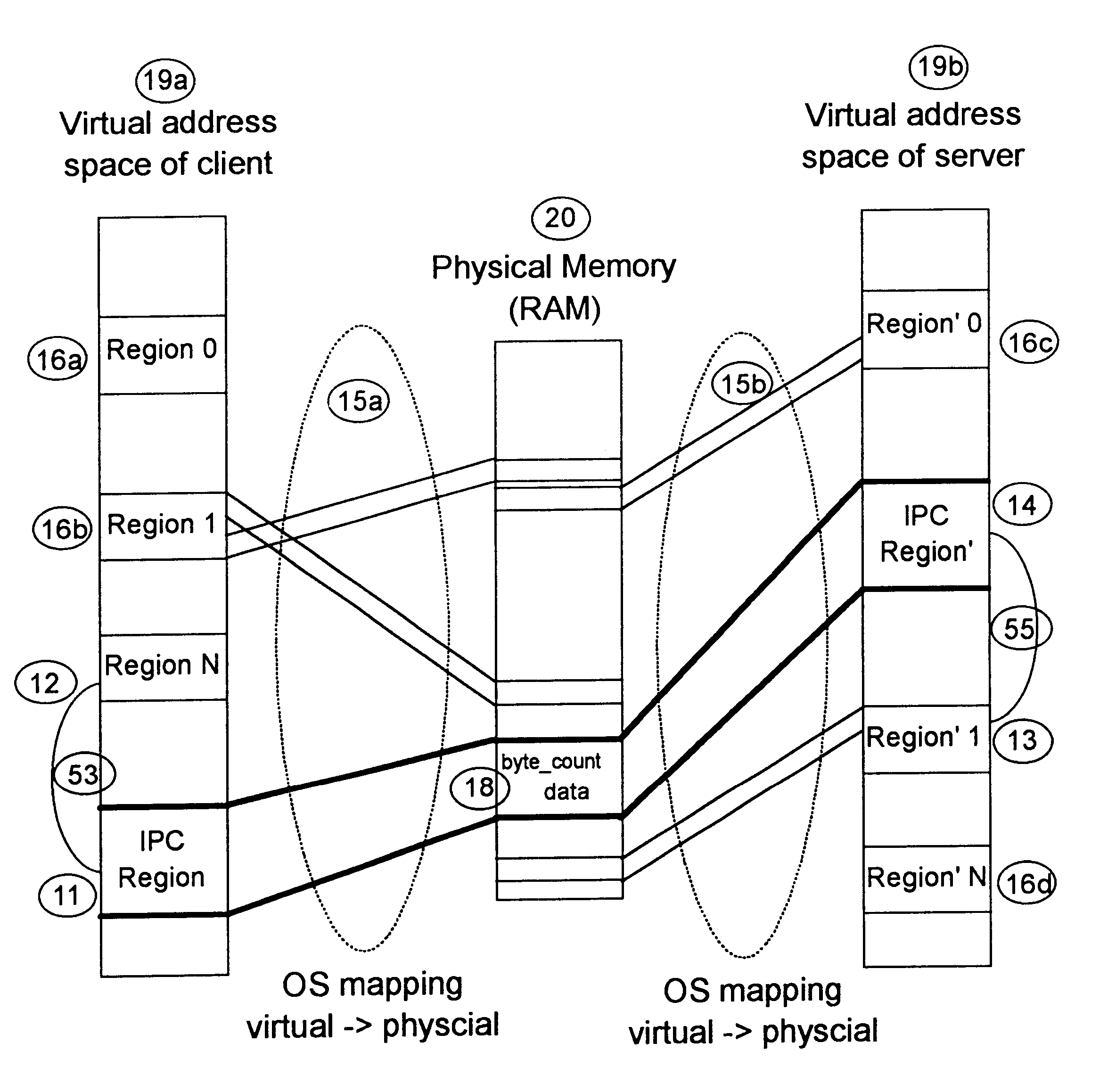
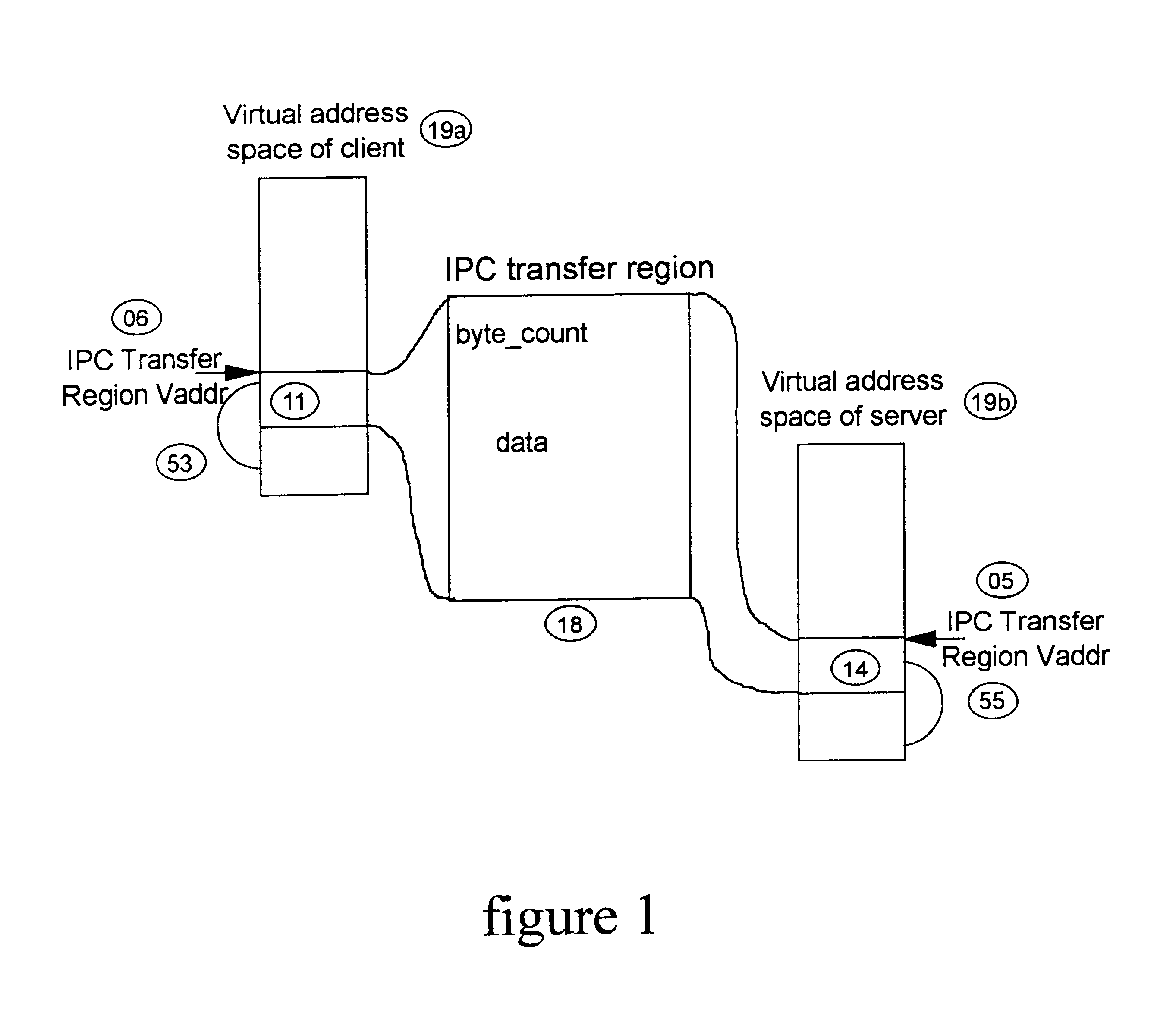
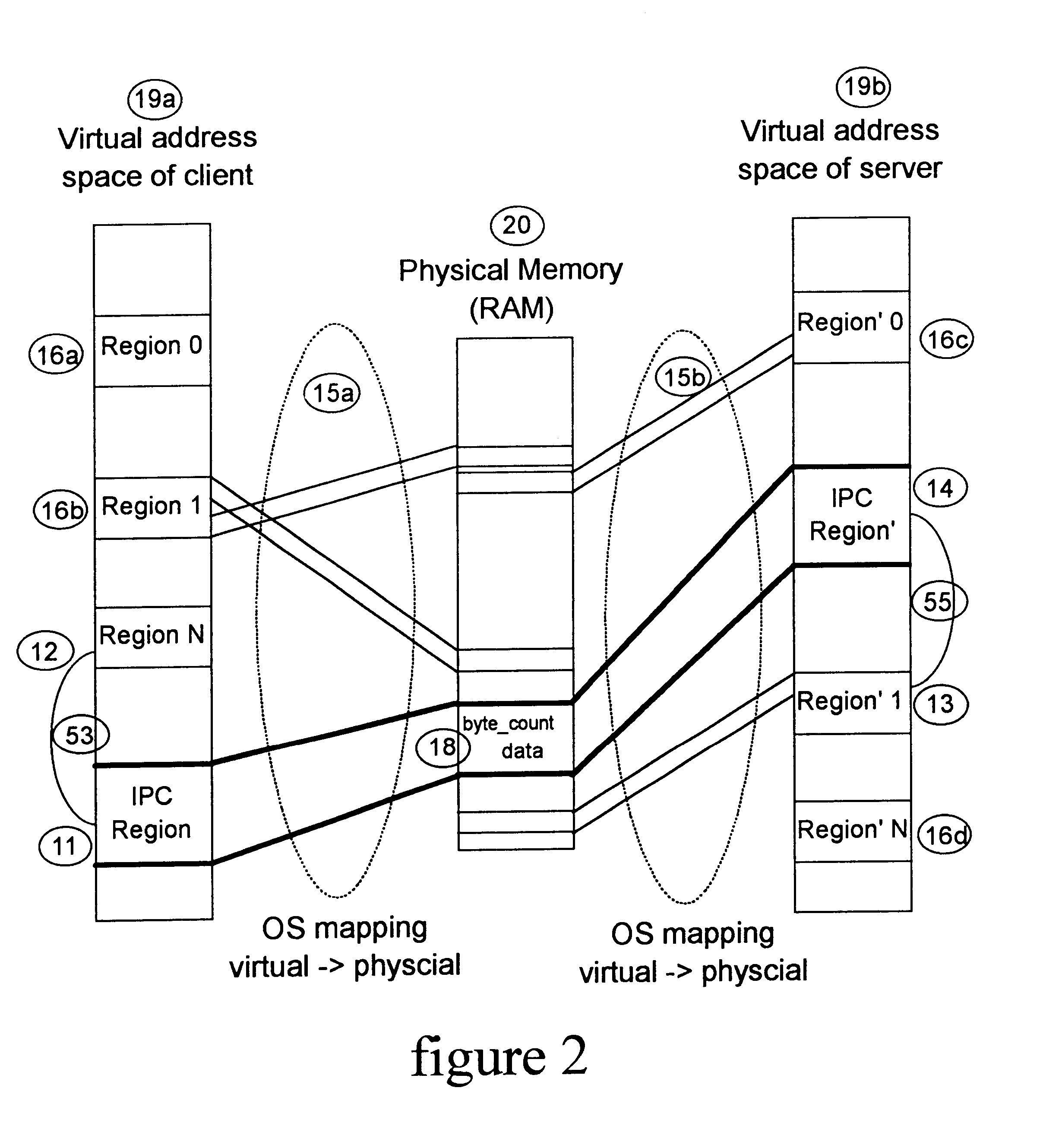
InactiveUS6601146B2Reduce accessAvoid overheadMultiprogramming arrangementsMemory systemsMostly TrueComputerized system
A method and apparatus for performing efficient interprocess communication (IPC) in a computer system. With this invention, a memory region called the IPC transfer region is shared among all processes of the system to enable more efficient IPC. The unique physical address of the region is mapped into a virtual address from each of the address spaces of the processes of the system. When one of the processes needs to transfer data to another of the processes, the first process stores arguments describing the data in the region using the virtual address in its address space that maps into the unique physical address. When the other or second process needs to receive the data, the second process reads the data from the second region using the virtual address in its memory space that maps into the unique physical address. With this invention, in most cases, control of the IPC transfer region occurs automatically without any kernel intervention.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com