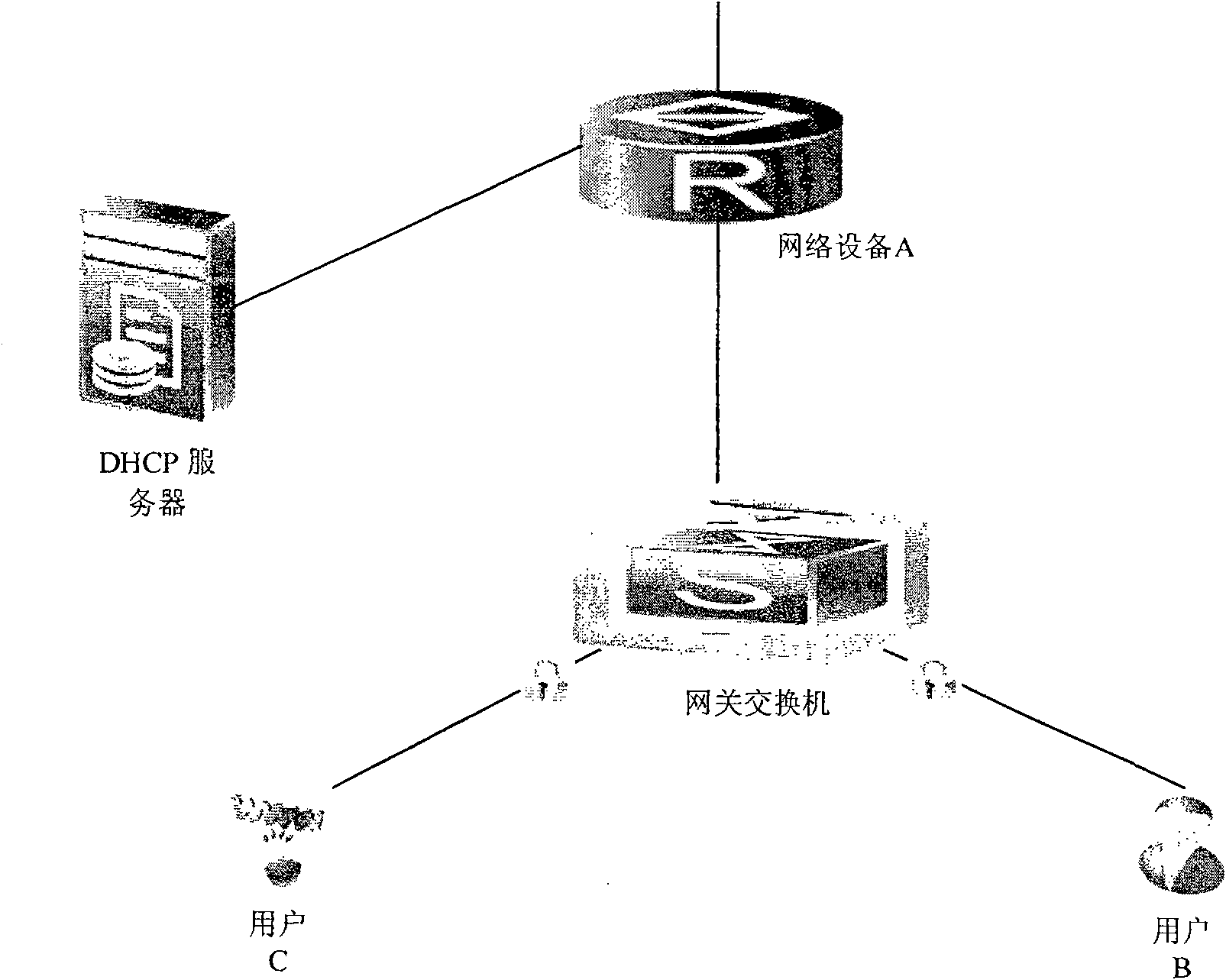
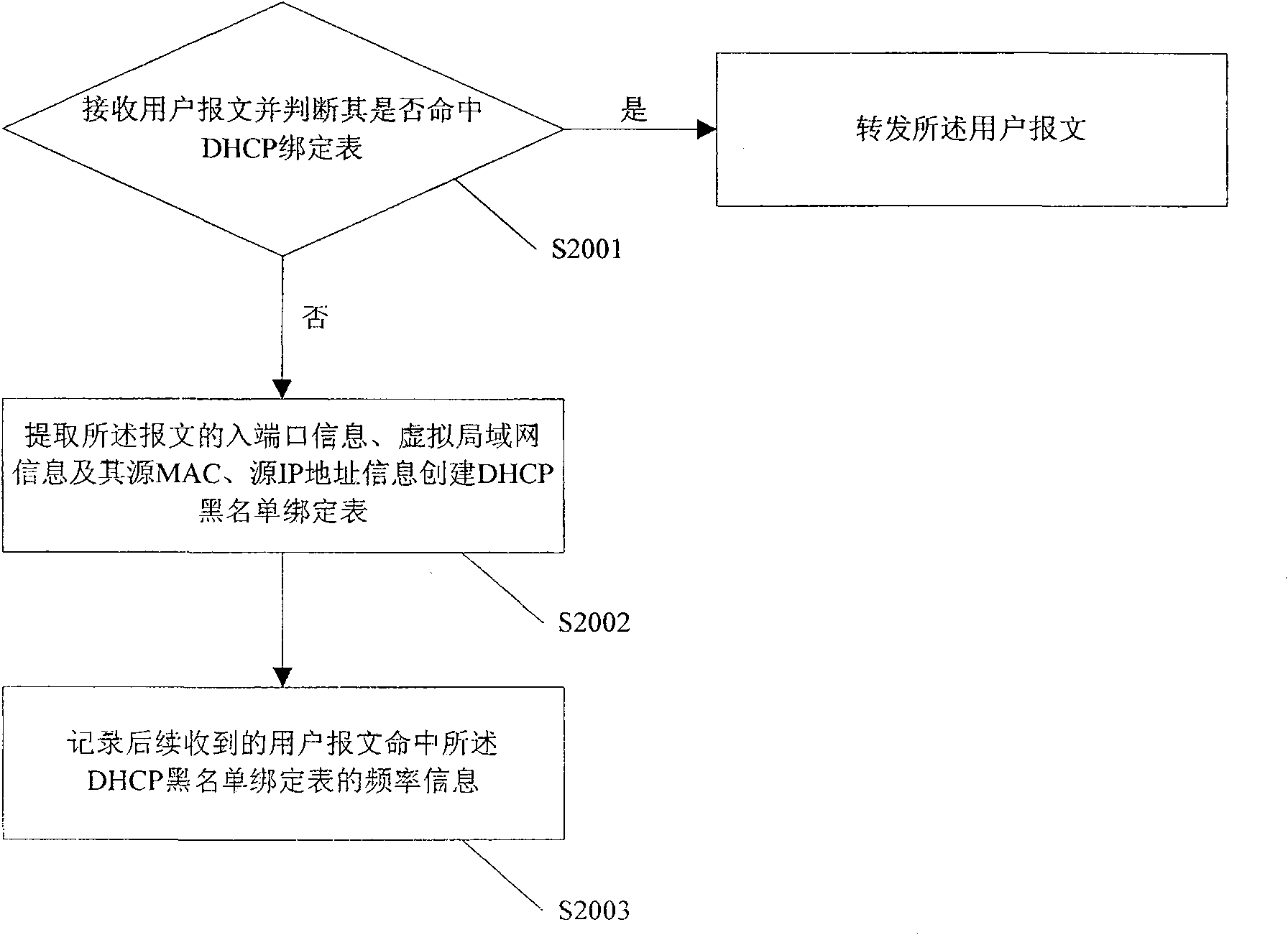
DHCP monitoring method and apparatus thereof
A monitoring method and technology of a monitoring device are applied in the field of communication networks and can solve problems such as inability to understand attacker information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 3
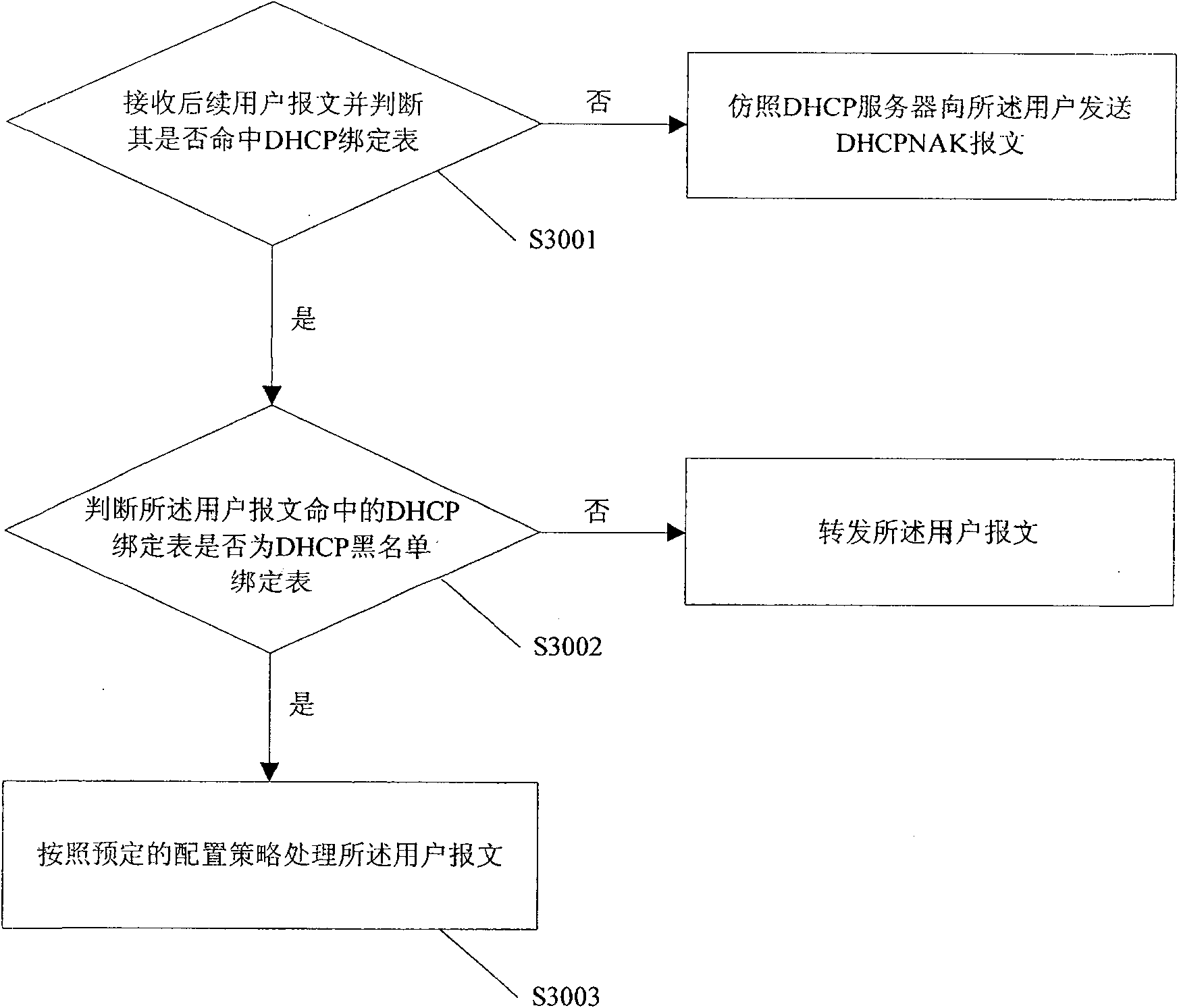
[0043] On the basis of embodiment one or embodiment two, after establishing the DHCP blacklist binding table and recording its hit frequency information, the monitoring method of the present invention can also be further improved, as image 3 Embodiment 3 of the monitoring method of the present invention is shown, including the following steps:
[0044] Step S3001: Receive a subsequent user message and judge whether it matches the DHCP binding table, if the judgment result is no, send a DHCPNAK message to the user in the same way as the DHCP server, otherwise, execute step S3002.
[0045] Step S3002: Determine whether the DHCP binding table hit by the user message is a DHCP blacklist binding table, if the judgment result is no, forward the user message according to the prior art, otherwise, execute step S3003.
[0046] Step S3003: Process the user message according to a predetermined configuration policy.
[0047] When the received user message cannot hit the DHCP binding tab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com