ARP spoofing fine-grained detecting method and system
A technology of ARP spoofing and detection methods, applied in the field of fine-grained detection methods and systems of ARP spoofing, can solve the problems of no system, easy to generate errors, large workload, etc., and achieve efficient dynamic ARP attacks and countermeasures, and detect ARP attacks and counteracting effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific embodiments of the invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
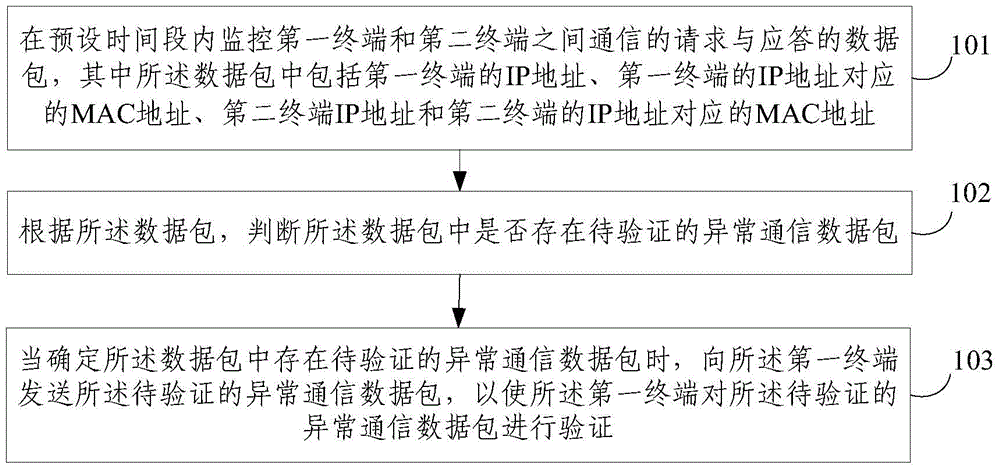
[0035] figure 1 A schematic flowchart of a fine-grained detection method for ARP spoofing provided by an embodiment of the present invention is shown, as shown in figure 1 As shown, the method includes:
[0036] 101. Monitor the data packets of requests and responses communicated between the first terminal and the second terminal within a preset period of time, wherein the data packets include the IP address of the first terminal and the MAC address corresponding to the IP address of the first terminal address, the IP address of the second terminal, and the MAC address corresponding to the IP address of the second terminal;
[0037] 102. According to the data packet, judge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com