ARP message management method based on network equipment
A technology of ARP message and network equipment, which is applied in the field of ARP message management based on network equipment, which can solve the problems of message discarding, network administrator's workload in the early stage and management complexity in the later stage, and achieve the effect of reducing ARP spoofing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
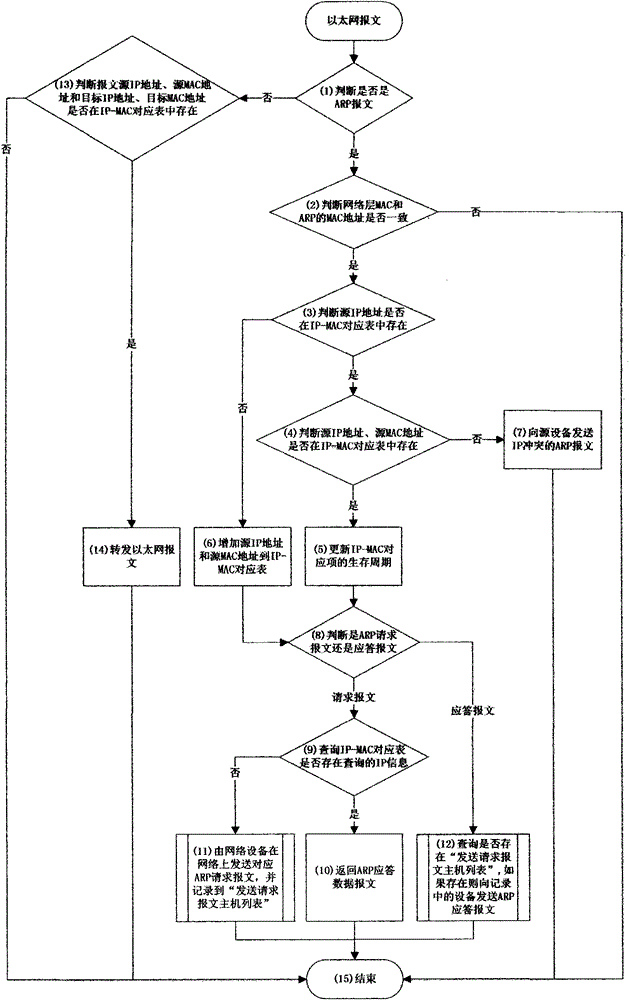
[0069] This embodiment is to simulate PC1 to send a data message to PC2, and the processing flow is as follows:
[0070] (1) PC1 (192.168.1.1) sends an ARP request message to PC2 (192.168.1.2) to the network.
[0071] (2) The network device verifies the legitimacy of PC1. The network device looks up the IP-MAC correspondence of PC1 from the local IP-MAC correspondence table: 192.168.1.1>>11-11-11-11-11-11. Because the IP-MAC corresponding item of PC1 is not found, the network device adds the corresponding corresponding relationship to the IP-MAC corresponding table.
[0072] (3) The network device responds to the ARP request message. The network device searches the corresponding item of PC2 (192.168.1.2) from the local IP-MAC correspondence table.
[0073] (4) Because the network device fails to find the corresponding item of PC2 in the IP-MAC correspondence table, the network device sends an ARP request packet to the network.
[0074] (5) PC2 sends an ARP response message...
Embodiment 2
[0081] This embodiment is to simulate PC3 to send data message to PC1, and the processing flow is as follows:
[0082] (1) PC3 (192.168.1.3) sends an ARP request message to PC1 (192.168.1.1) to the network.
[0083] (2) The network device verifies the legitimacy of PC3. The network device looks up the IP-MAC correspondence of PC3 from the local IP-MAC correspondence table: 192.168.1.3>>33-33-33-33-33-33. Because the IP-MAC corresponding item of PC3 is not found, the network device adds the corresponding corresponding relationship to the IP-MAC corresponding table.
[0084] (3) The network device responds to the ARP request. The network device finds out the corresponding item of PC1 from the local IP-MAC correspondence table.
[0085] (4) The network device returns an ARP response message to PC3.
[0086] (5) PC3 sends a data message to PC1.
[0087] (6) The network device verifies the legitimacy of PC3 and PC1 in the data message.
[0088] (7) The network device forwards...
Embodiment 3
[0090] In this embodiment, PC3 is simulated to send an ARP spoofing message to PC1, and PC3 is disguised as PC2. The process is as follows:
[0091] (1) PC3 sends an ARP response message to PC1, which indicates that the MAC address of PC2 is 33-33-33-33-33-33
[0092] (2) The network device verifies the legitimacy of PC3 and PC2. It is determined that the sending MAC address is inconsistent with the MAC address in the ARP packet, so the network device discards the ARP reply packet.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com