Patents
Literature
35 results about "Attack response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Malicious Attack Response System and Associated Method
InactiveUS20120023572A1Memory loss protectionError detection/correctionTraffic capacityNetwork software
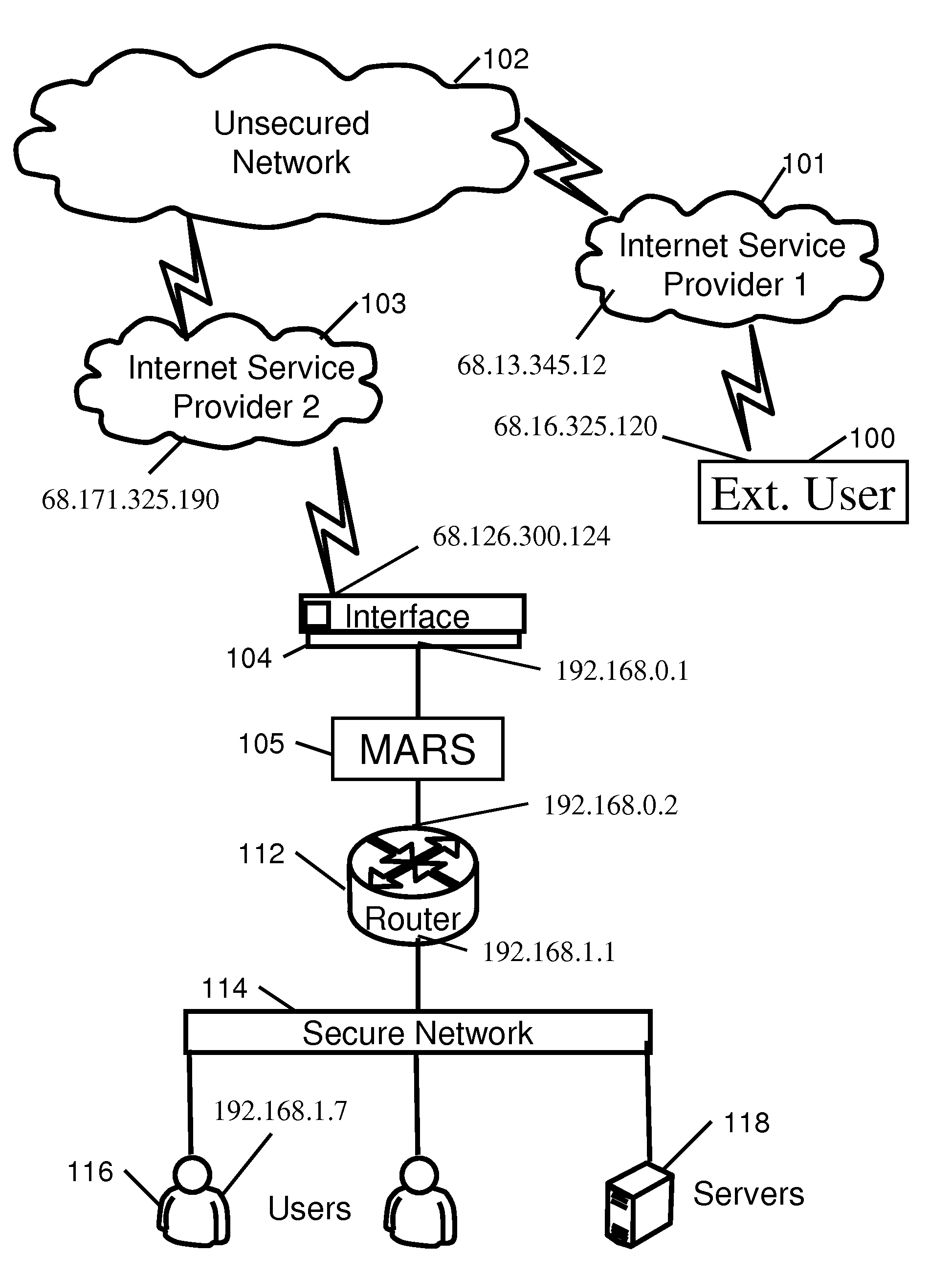
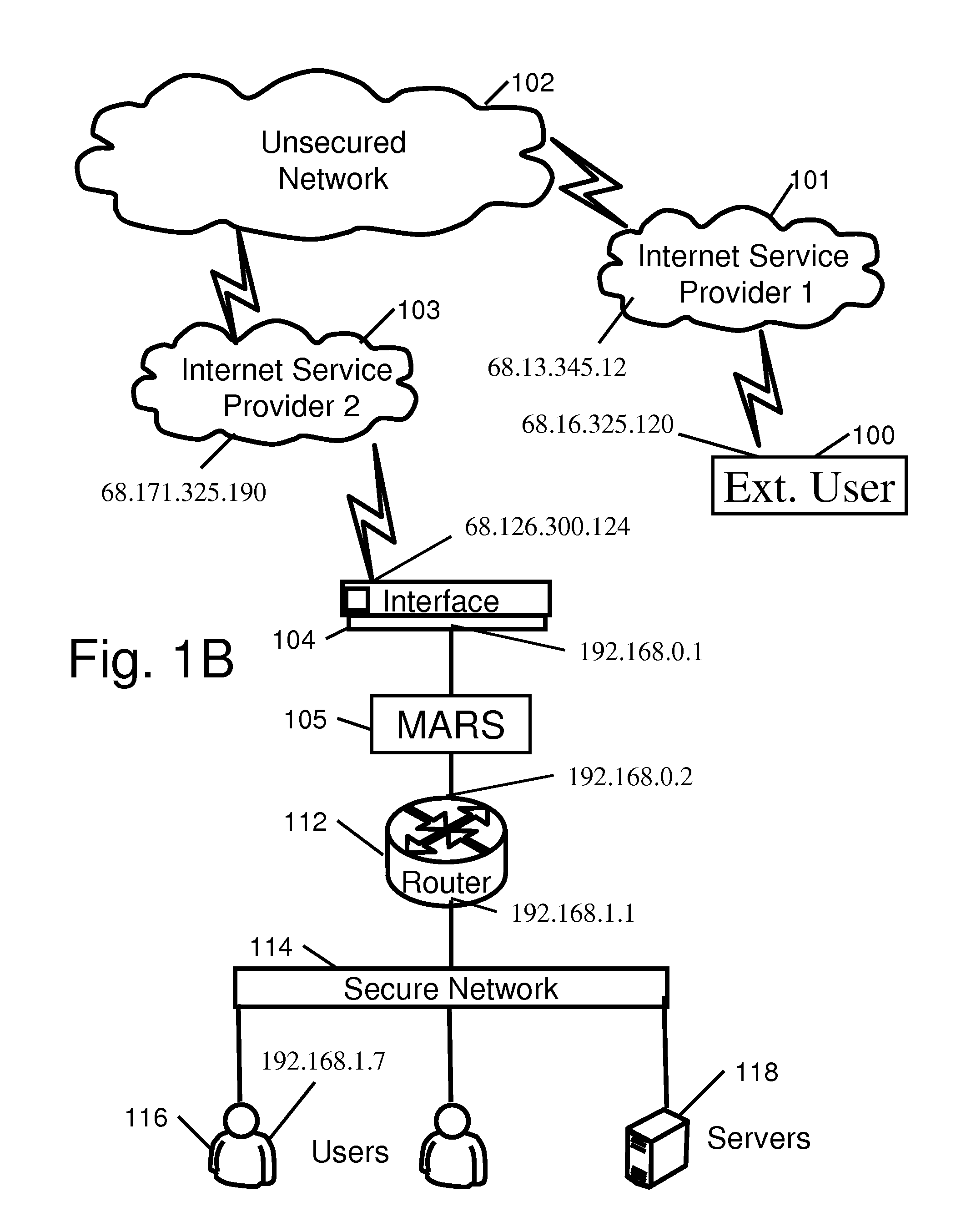
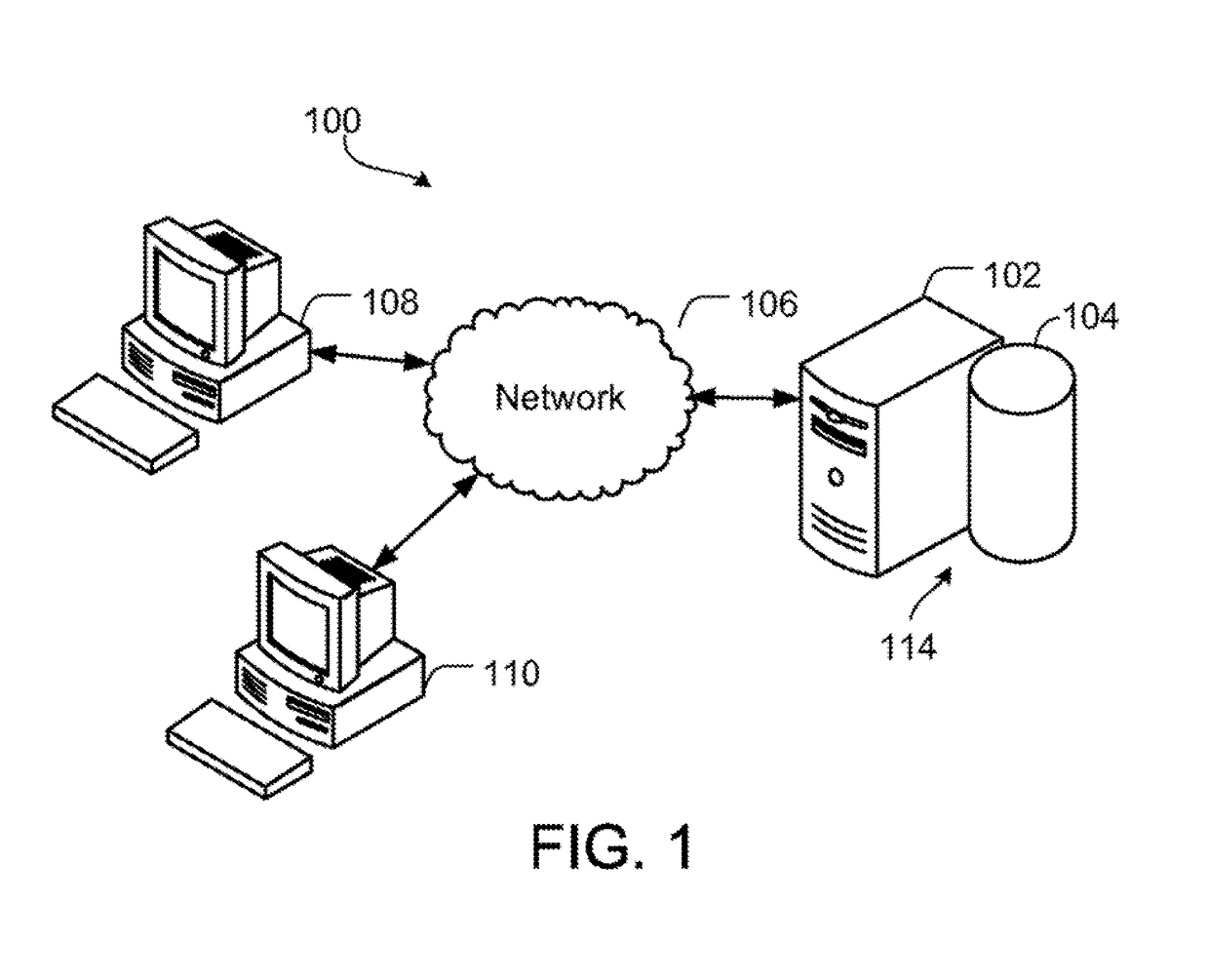
A system and method for detecting and identifying intruders in a computer network environment by providing a network traffic evaluation and simulation module at the interface between a protected network and external traffic source. The evaluation and simulation module identifies suspected intruders by observing intrusion pattern behavior and then presents a simulated network to the intruder. The simulated network appears to offer the intruder valuable information and provides the intruder with the appearance of success in breaking down the layers of the simulated network to keep the intruder engaged in the intrusion effort while information is gathered to trace and identify the source of the intrusion. Intrusion attempts are identified and categorized in an intrusion analysis module. The network traffic evaluation and simulated network may be provided as a self contained physical module that does not require modification of existing network software.
Owner:Q TRACK CORP
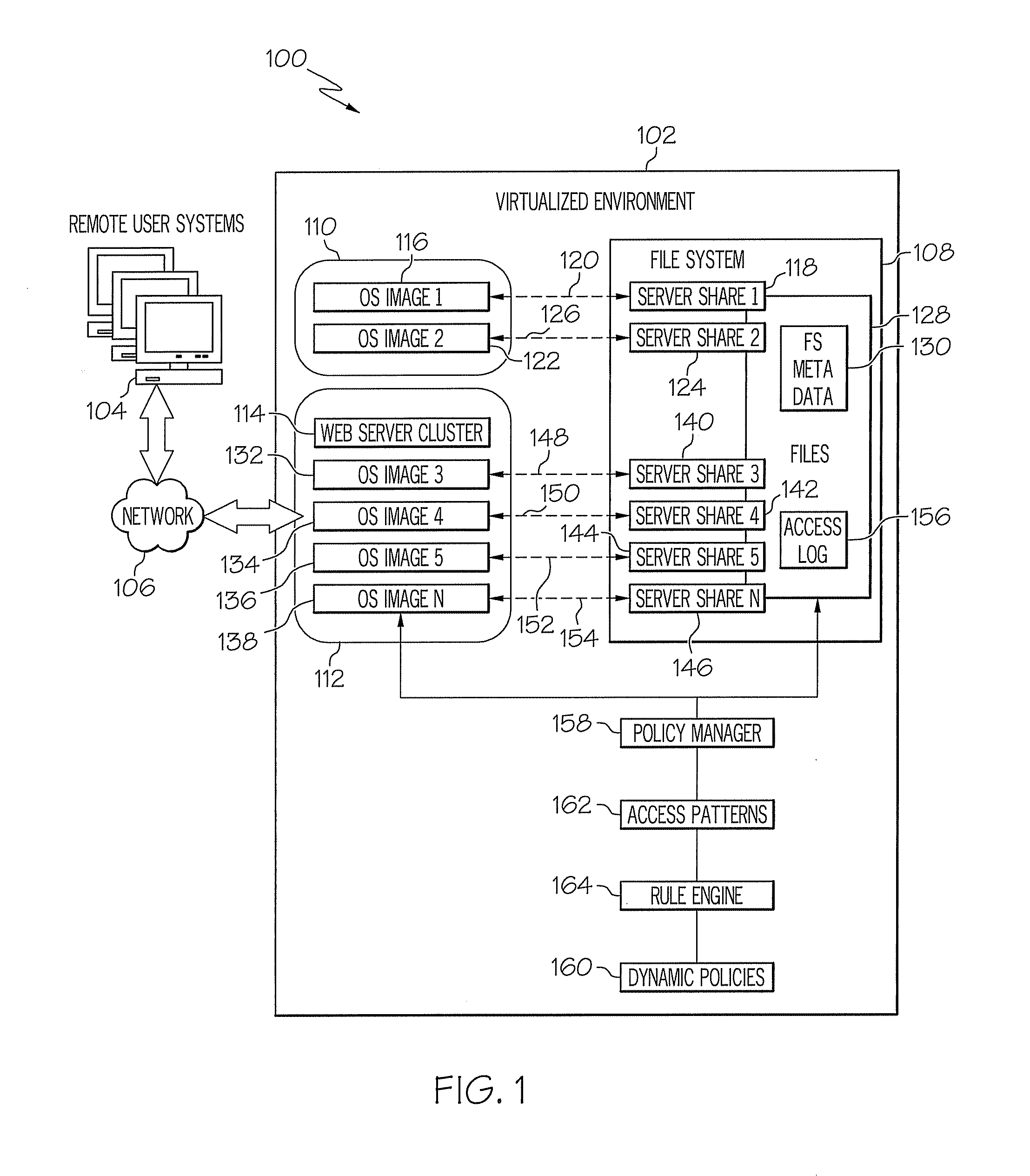
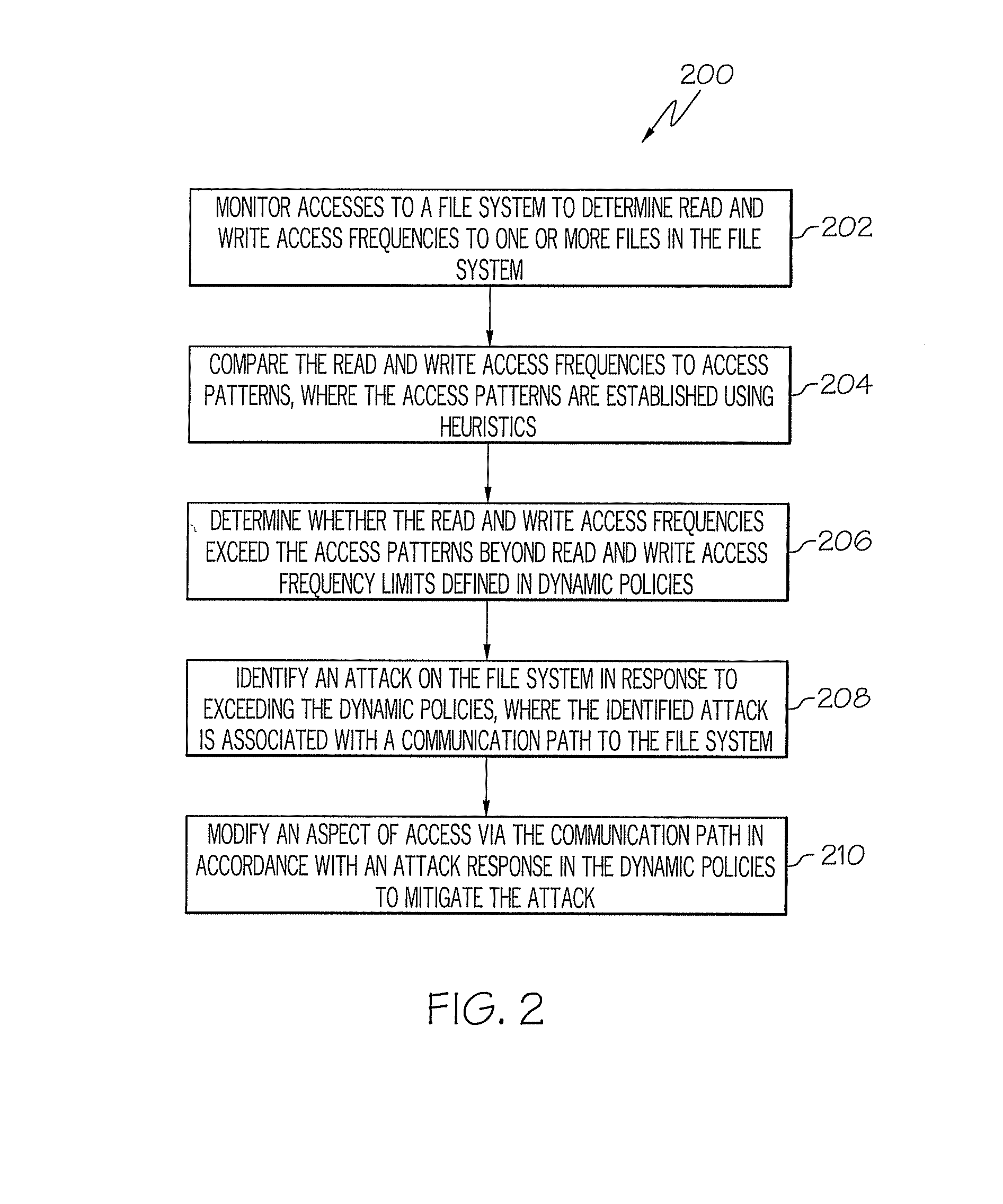
Computer system security using file system access pattern heuristics
InactiveUS20090144545A1Provide securityComputer security arrangementsSecuring communicationFile systemHeuristic
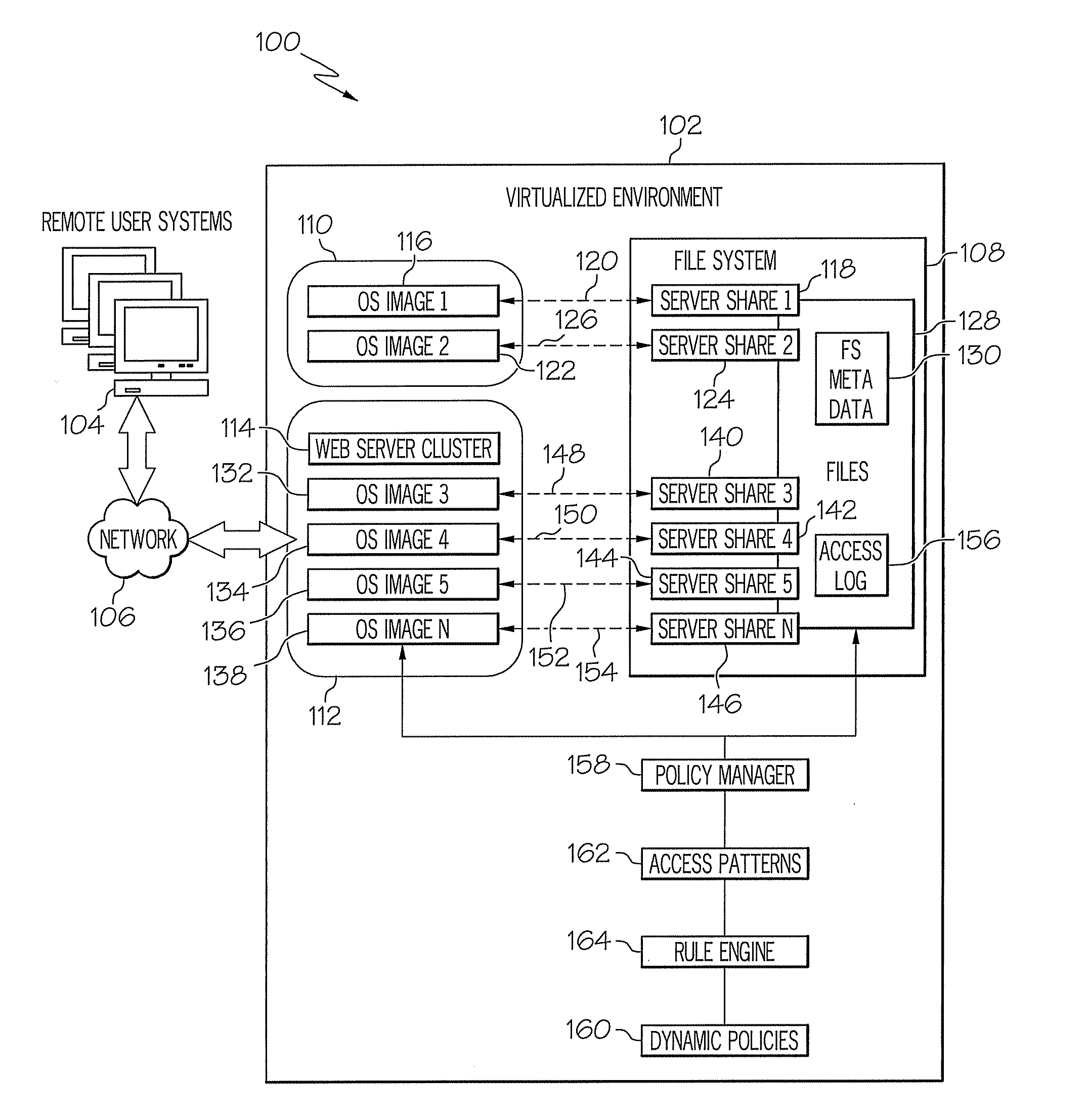
A system for computer system security using file system access pattern heuristics is provided. The system includes access patterns to establish nominal read and write frequencies to a file system using heuristics, dynamic policies, and a policy manager. The policy manager monitors accesses to the file system to determine read and write access frequencies to the file system. The policy manager also compares the read and write access frequencies to the access patterns, and determines whether the read and write access frequencies exceed the access patterns per the dynamic policies. The policy manager further identifies an attack on the file system in response to exceeding the dynamic policies, where the identified attack is associated with a communication path to the file system. The policy manager additionally modifies an aspect of access via the communication path in accordance with the attack response in the dynamic policies to mitigate the attack.
Owner:IBM CORP
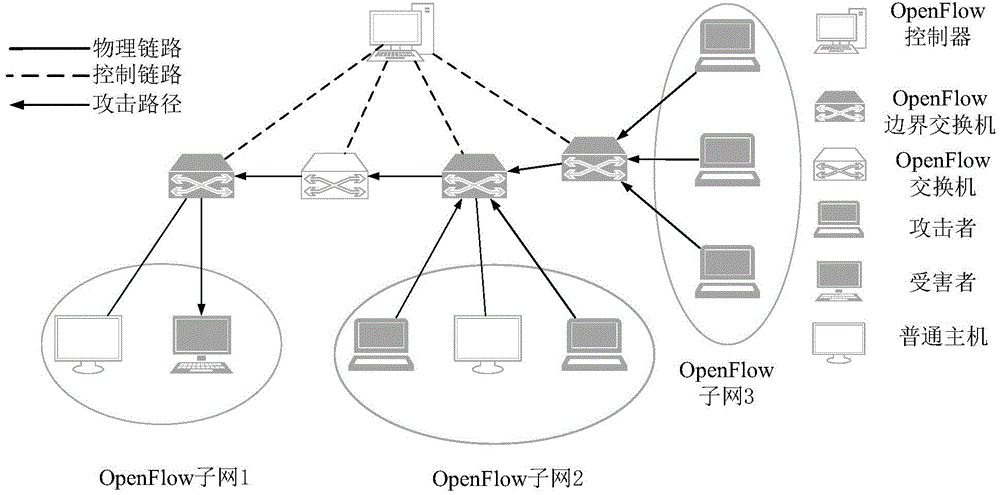
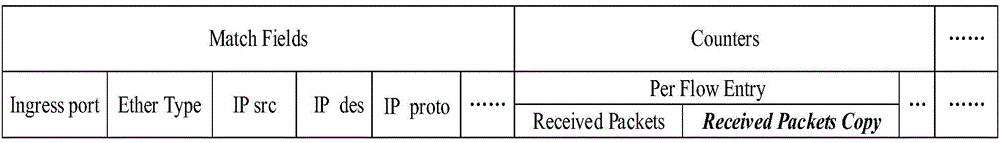
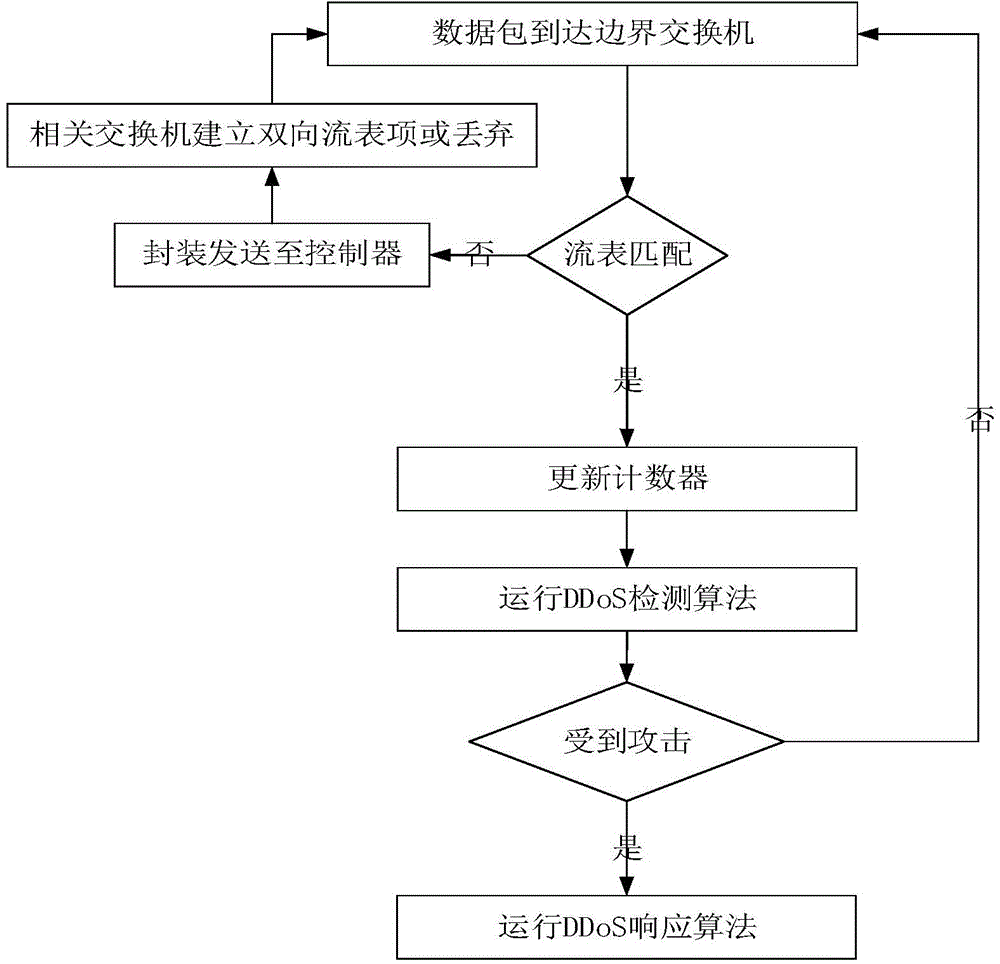
DDoS attack distributed detection and response system and method based on information entropy
InactiveCN104580222AReduce the monitoring burdenImprove detection accuracyTransmissionIp addressNetwork topology
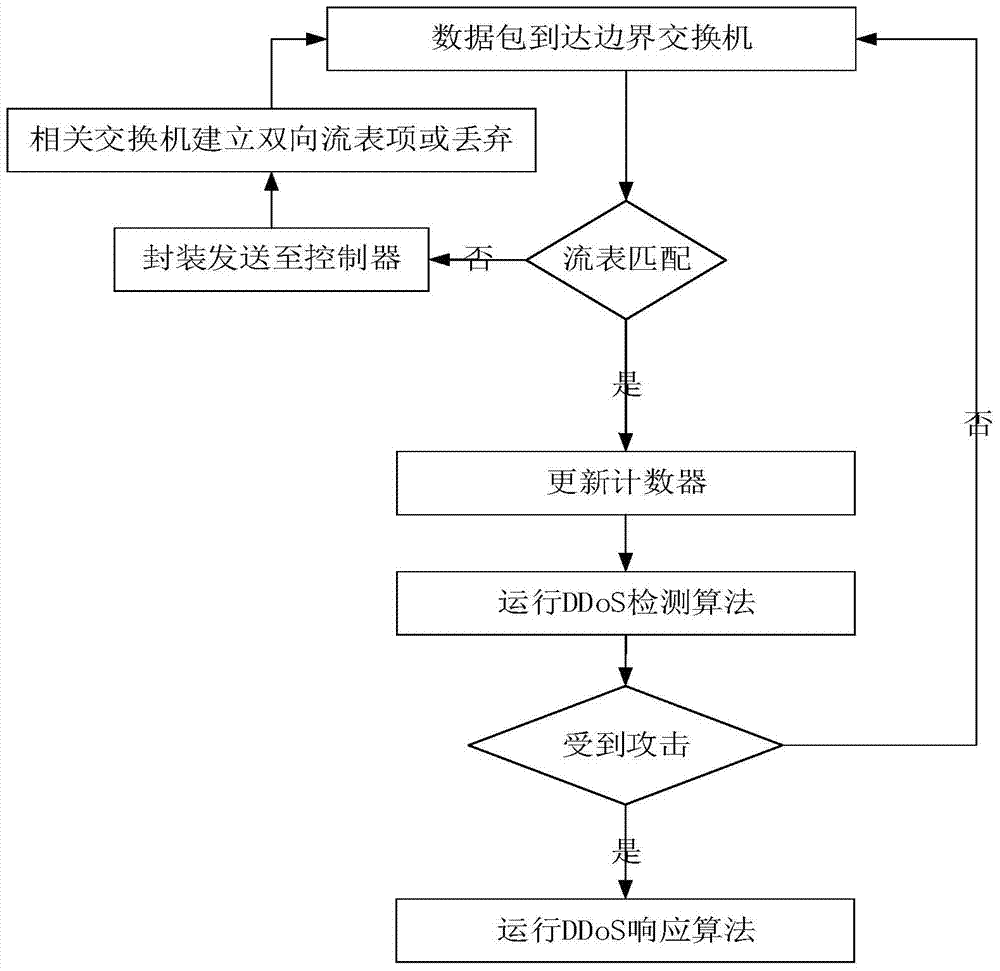
The invention discloses a DDoS attack distributed detection and response system and method based on information entropy. The system comprises a controller, the controller is connected with a plurality of exchangers, each exchanger is connected with a plurality of host computers, each exchanger is also connected with the other exchangers, and the controller is used for managing network topology, developing data forwarding strategies, and sending down the strategies to the exchangers; the exchangers are used for data forwarding; the exchangers comprise boundary exchangers and / or non-boundary exchangers; an attack detection algorithm and an attack response algorithm are operated by the boundary exchangers to achieve the attack detection and the attack response; the host computers are computers of users and each host computer corresponds to a certain IP address, and data of the host computers are forwarded by the boundary exchangers. The DDoS attack distributed detection and response system and method based on the information entropy has the advantages of being fast in detection speed, high in detection precision rate, rapid in attack response, and small in resource burden.
Owner:SHANDONG UNIV
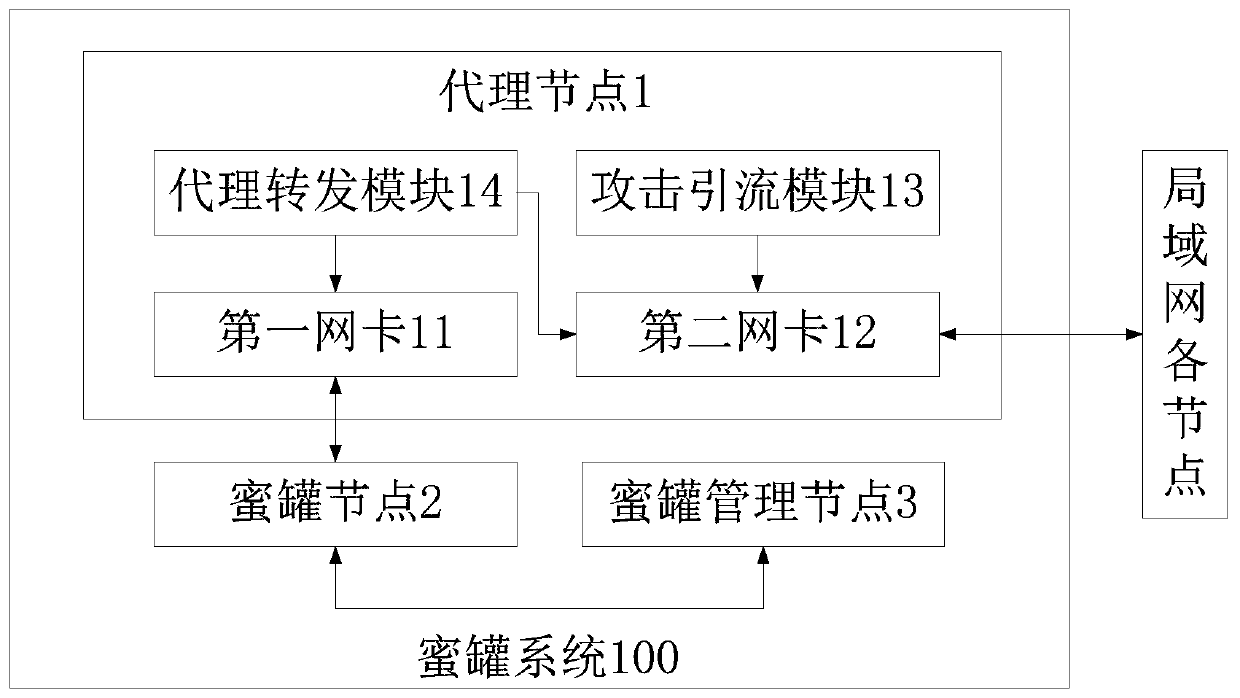
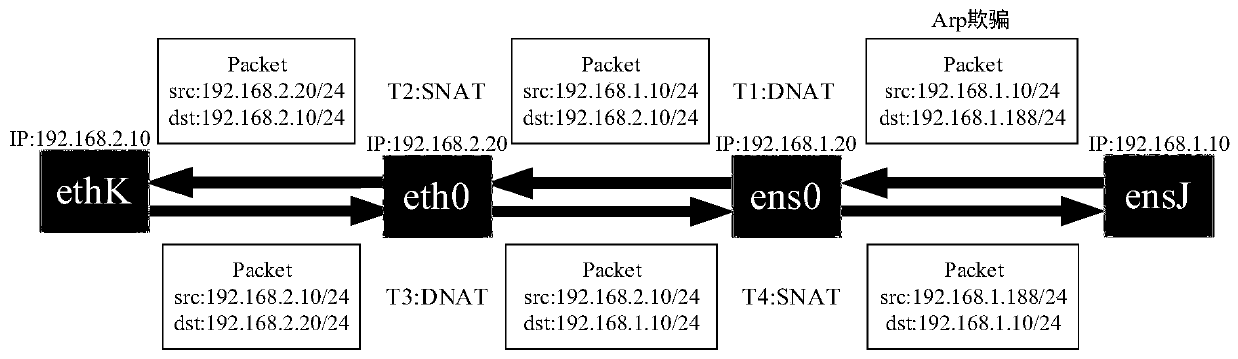
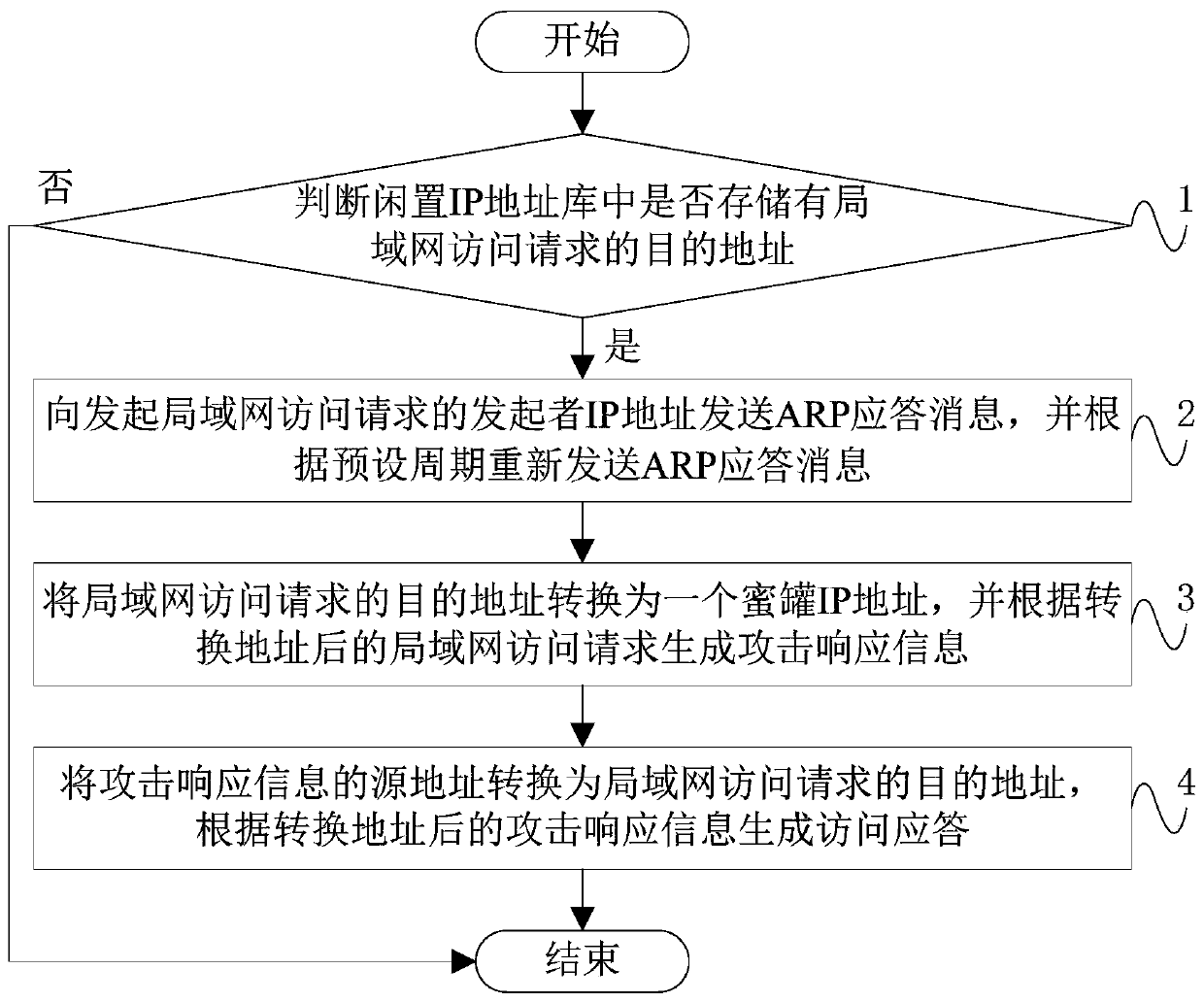
High-coverage intranet honeypot system
InactiveCN109768993AIncrease the chance of being attackedAvoid occupyingTransmissionIp addressARP spoofing
The invention discloses a high-coverage intranet honeypot system. The honeypot system comprises an agent node comprising an attack drainage module; a first network card, a second network card and a proxy forwarding module, the attack drainage module is used for passing ARP spoofing; guiding a local area network access request of which a destination address is an idle IP address in a network segment where the local area network is located to the agent node, the IP address of the first network card and the IP address of the honeypot are in the same network segment; the first network card is usedfor communicating with a honeypot node; the IP address of the second network card and the IP address of the protected device in the local area network are in the same network segment. The second network card is used for communicating with equipment in the local area network, and the agent forwarding module is used for sending the local area network access request guided to the agent node to the honeypot node and sending attack response information returned by the honeypot node to an initiator IP address of the local area network access request. Through the technical scheme provided by the invention, the IP address coverage rate of the honeypot in the honeypot system is improved while the IP address occupation of the honeypot is reduced.
Owner:中国人民解放军32082部队
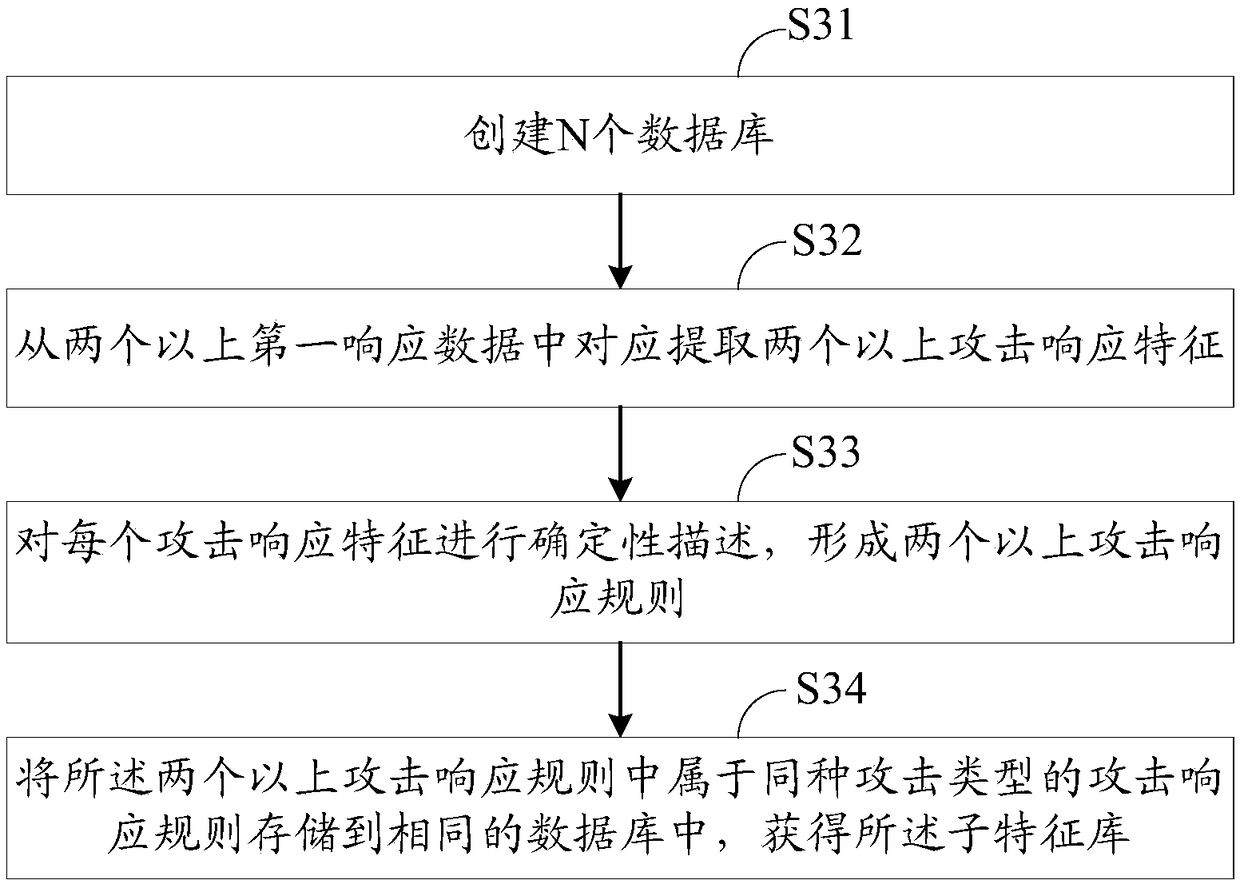
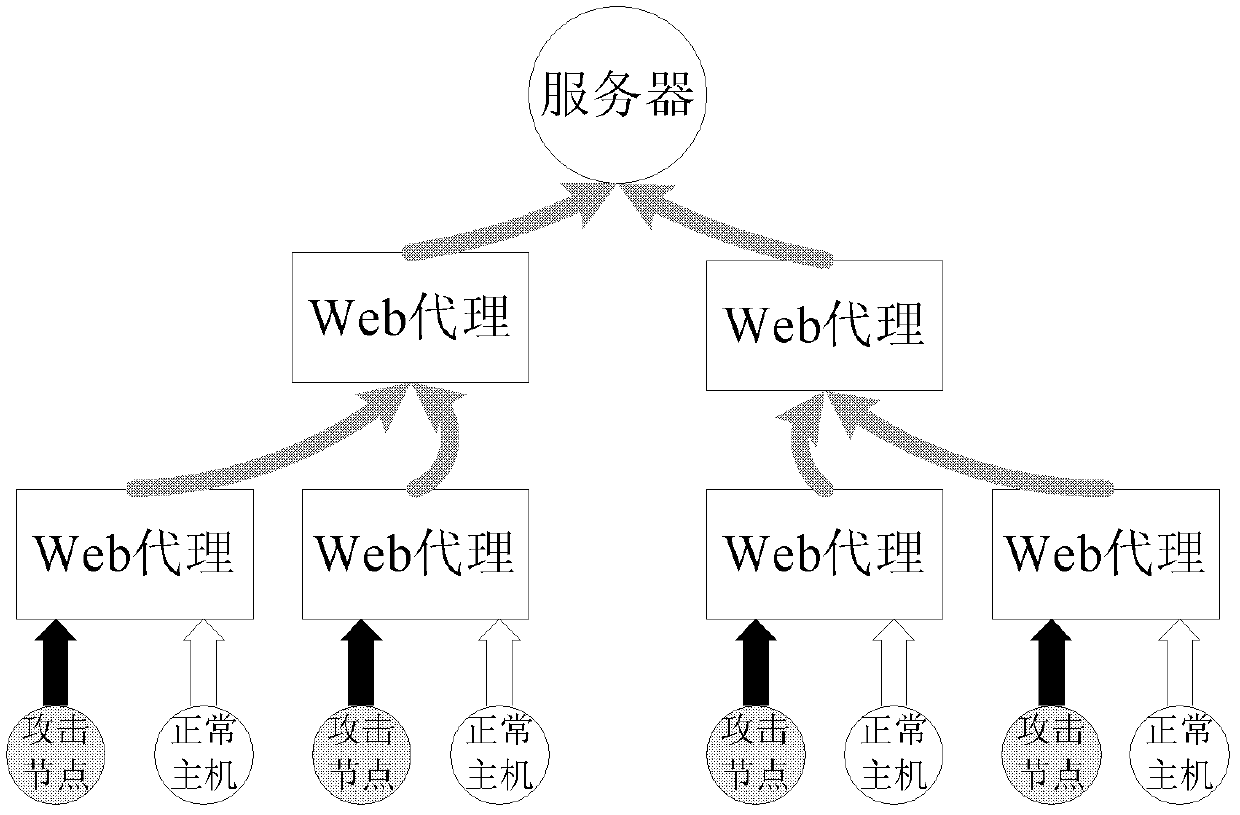
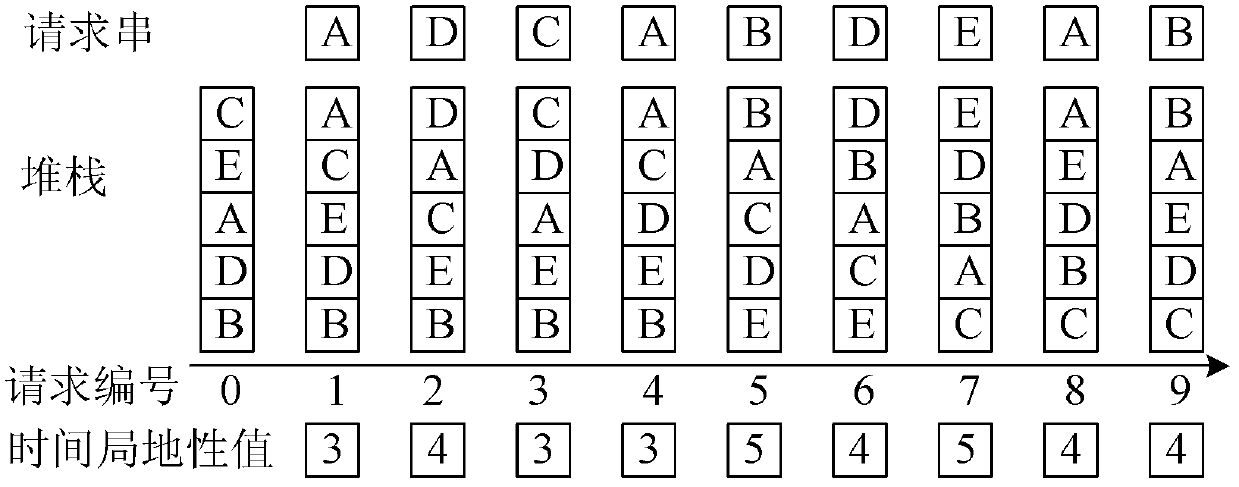
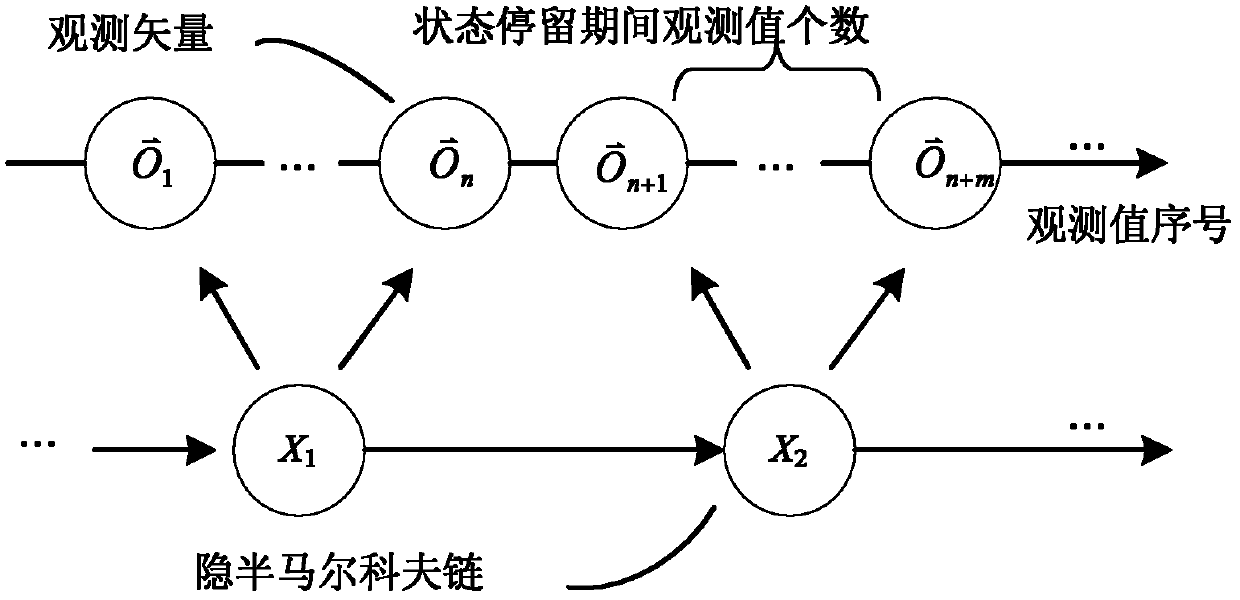
Indirect distributed denial of service attack defense method and system based on Web agency
InactiveCN102438025AAttack Response ImplementationEnable early detectionData switching networksSmall probabilityHidden semi-Markov model
The invention relates to an indirect distributed denial of service attack defense method and an indirect distributed denial of service attack defense system based on a Web agency. A behavior characteristic of a proxy-to-server network flow is described by extracting the space-time local property of the proxy-to-server network flow; the interference of a small-probability large value on an available signal is restrained by a nonlinear mapping function; a normal behavior model of the proxy-to-server network is constructed through a hidden semi-markov model (HsMM); normal degree estimation, namely long-time behavior estimation and short-time behavior estimation, under different time scales is performed by using behavior indexes acquired by the model; as to an abnormal behavior sequence (HTTP request sequence), an attack response is implemented by adopting a soft control method; and the basis of the soft control represents an HsMM model parameter and a structure index which are used for performing a normal behavior. The parameter for describing the proxy-to-server network is the space-time local property which is irrelevant to the change of the Web content on a target server; and the detection property of the method is the nature property based on the agent network flow and irrelevant to the size of the attack flow. By the method, the attack response can be realized before the resources of the target server are used by the attack flow, so that early detection can be realized effectively.
Owner:SUN YAT SEN UNIV
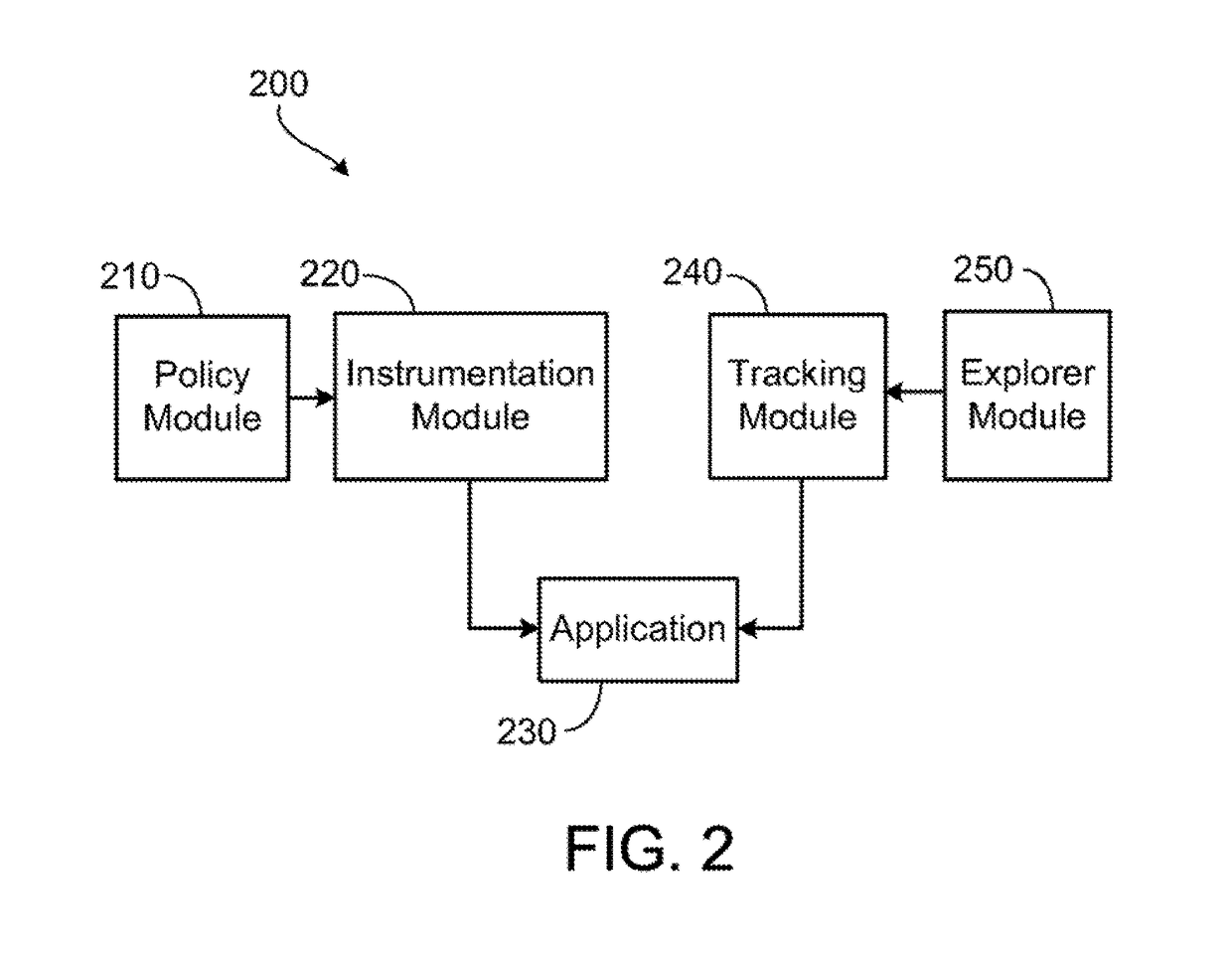
Method and system of attack detection and protection in computer systems
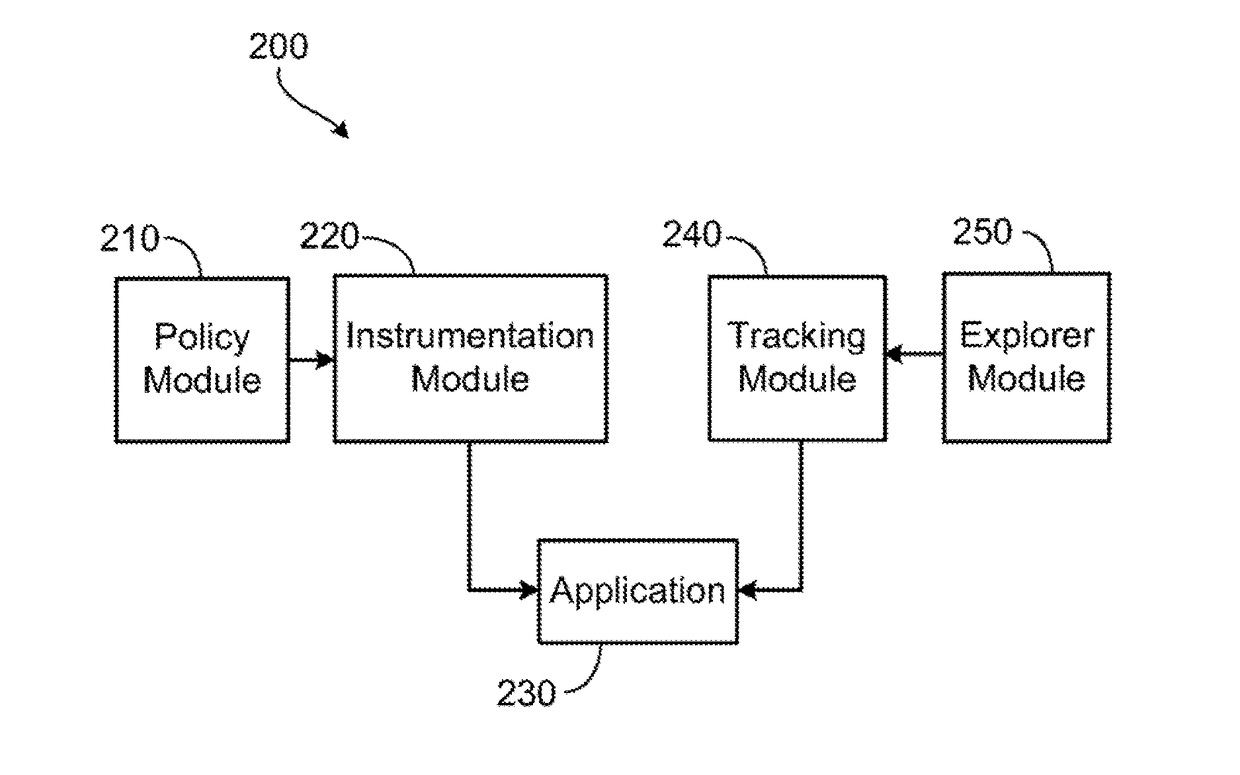
In one example aspect, a computerized method of automatically detecting and blocking at least one attack on an application includes the step of modifying instructions of the application to include at least one sensor. The at least one sensor generates a set of events related to detecting an attack on the application or a computing system implementing the application. The method includes the step of reviewing, from within the application, the set of events generated by the at least one sensor. The method includes the step of detecting a presence of at least one attack on the application based on the review of the set of events. The method includes the step of invoking an attack response action.
Owner:CONTRAST SECURITY
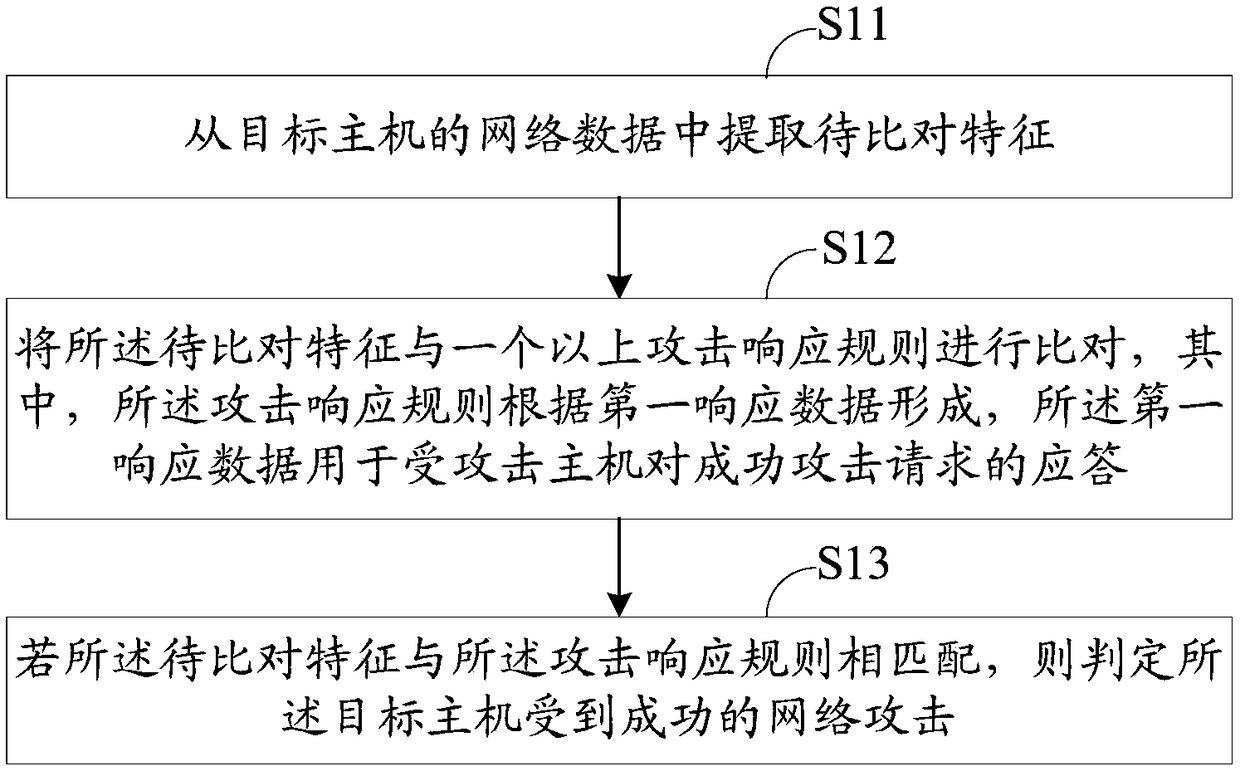
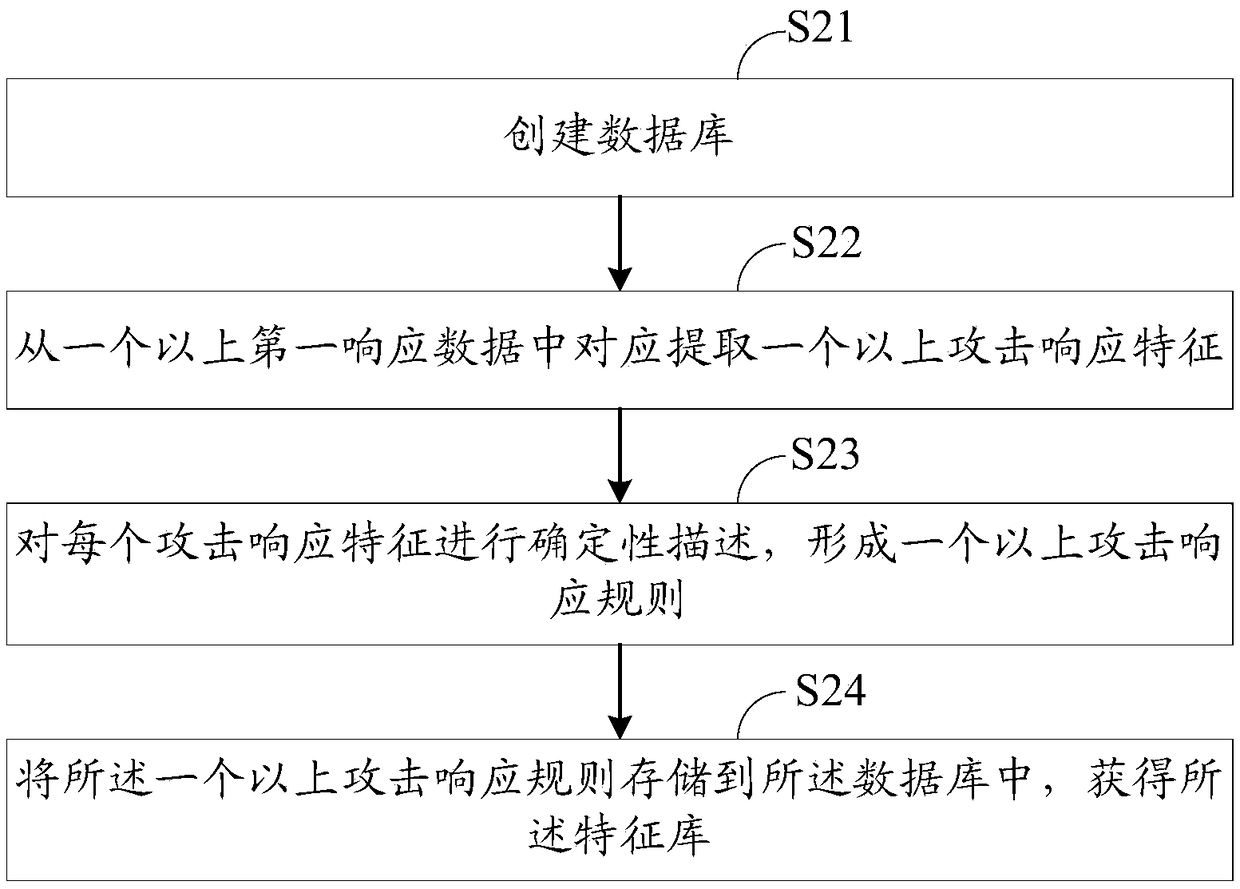
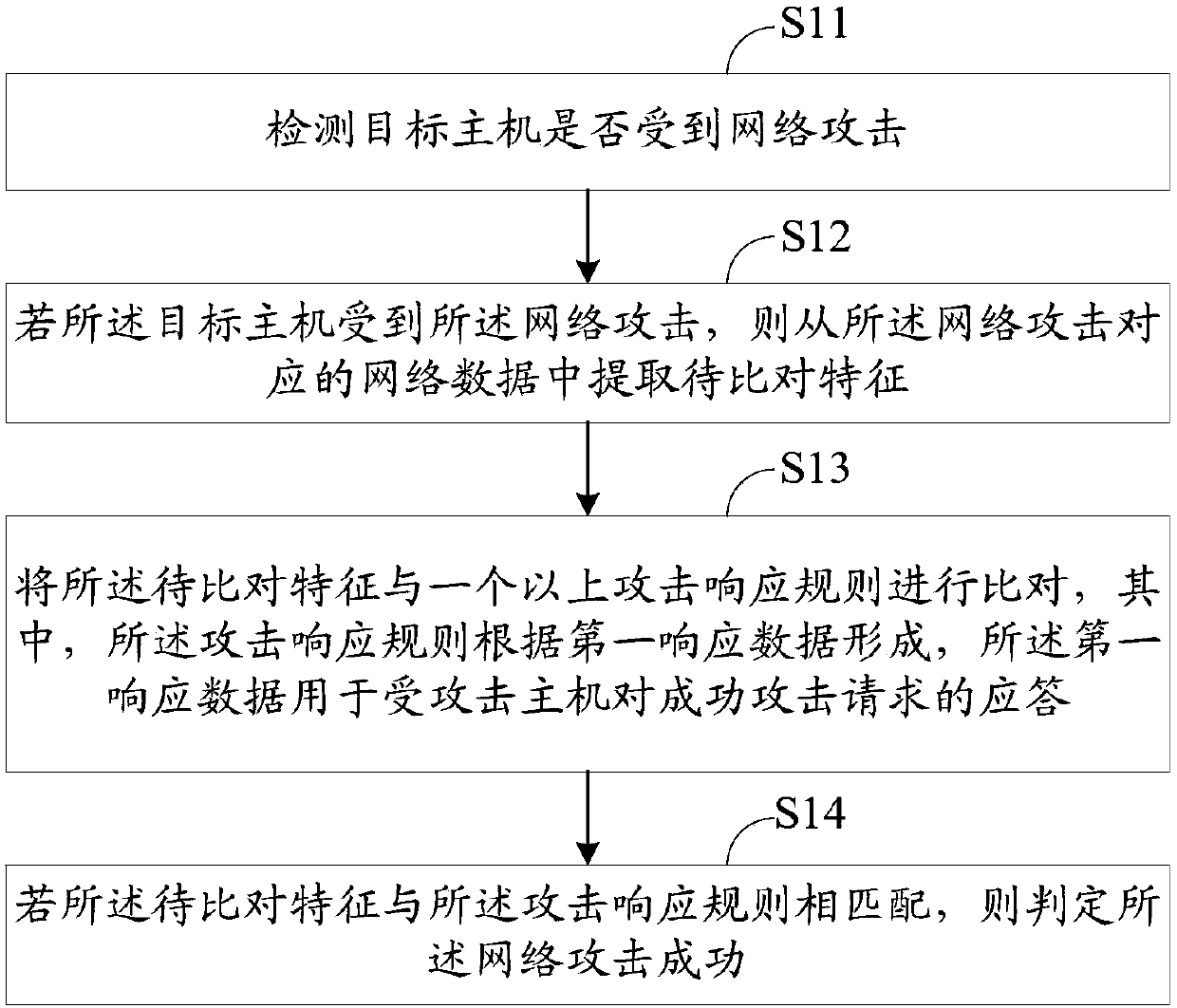
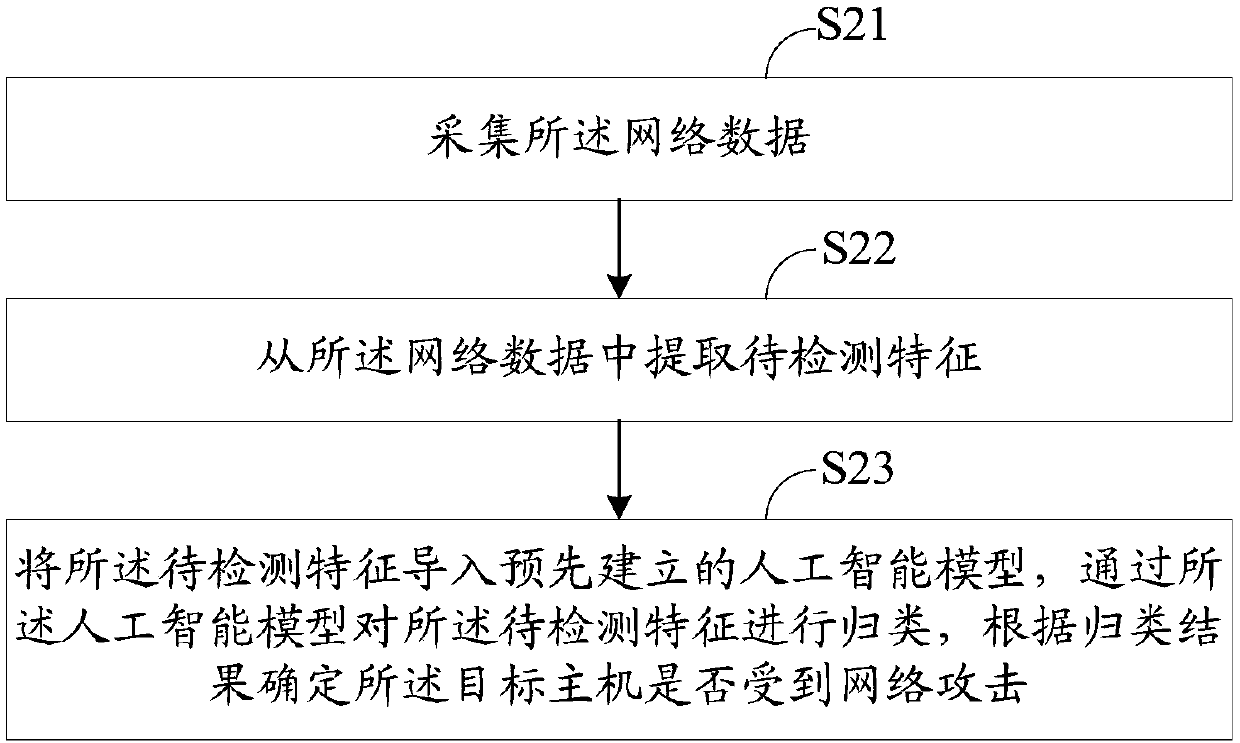
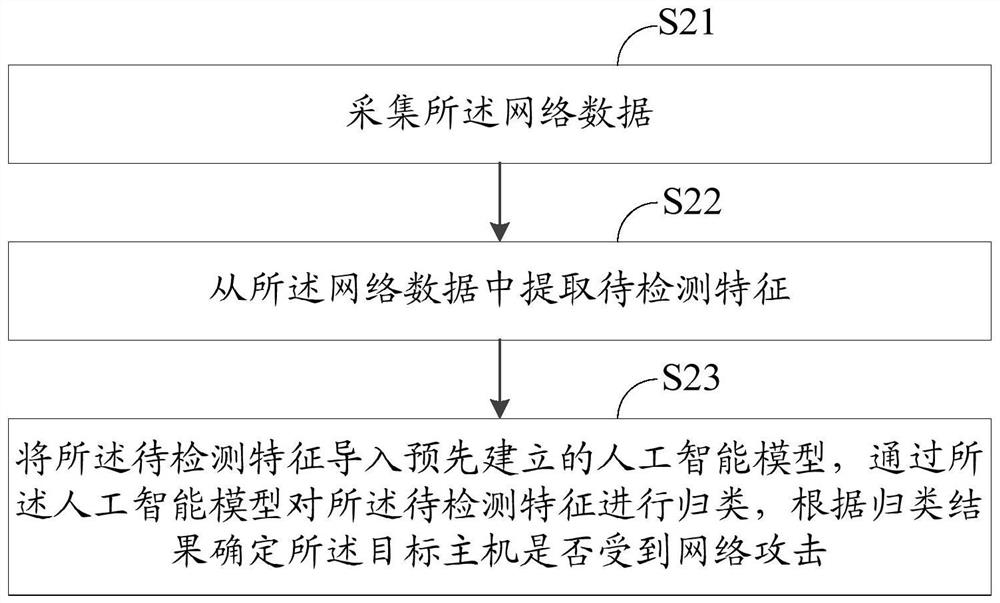
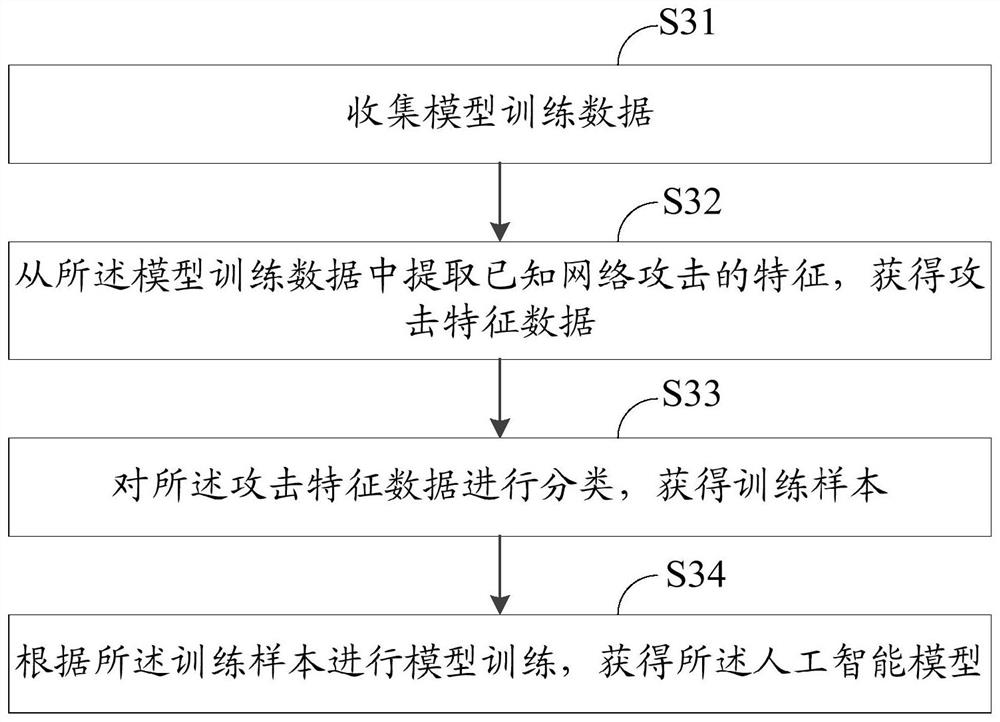
Network attack result detection method and system
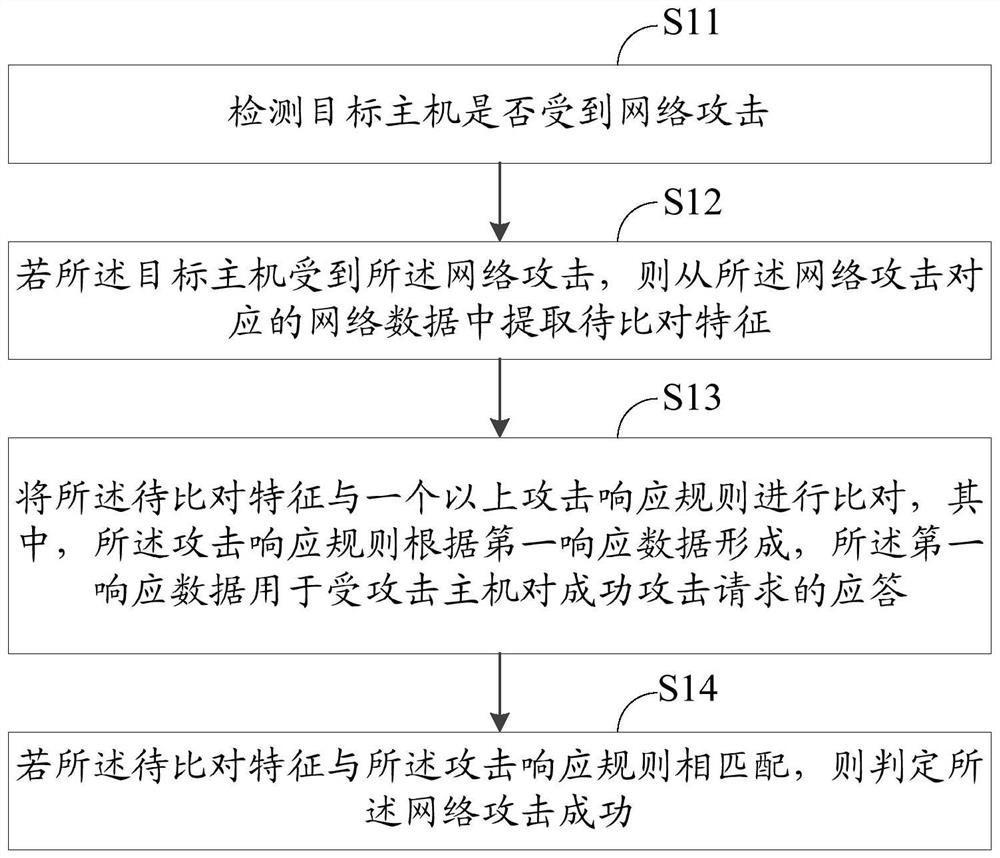
ActiveCN108881263AImprove operation and maintenance efficiencyTransmissionNetwork managementNetwork attack
The invention discloses a network attack result detection method and system. The network attack result detection method comprises the following steps: extracting to-be-contrasted features from networkdata of a target host; contrasting the to-be-contrasted features with more than one attack response rules, wherein the attack response rules are formed according to the first response data, and the first response data is used for responding to a successful attack request by the attacked host; and if the to-be-contrasted features are matched with the attack response rules, judging that the targethost suffers from successful network attack. Through the network attack result detection method and system disclosed by the invention, the successful network attack can be precisely identified, thereby providing effective network attack information for the network administrator.
Owner:北京鸿享技术服务有限公司
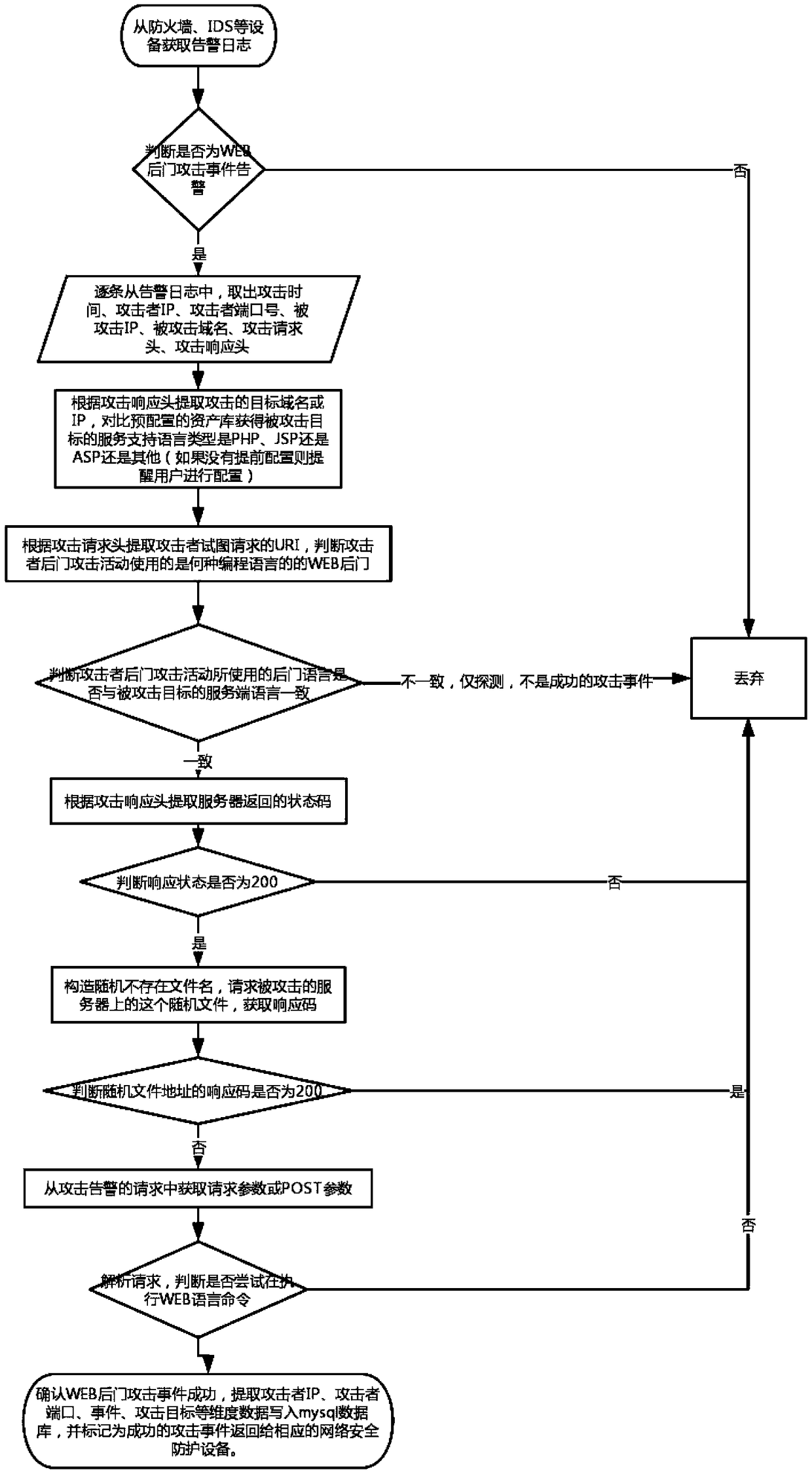
A method for confirming a WEB backdoor attack event
ActiveCN109040071AMeans of scientific confirmationEasy to identifyData switching networksDomain nameWeb service
The invention relates to a network security protection technology, aiming at providing a method for confirming a WEB backdoor attack event. The method comprises: parsing a firewall, IDS, IPS and related WEB server log, extracting the log record of WEB backdoor attack type, and judging whether the attack of WEB backdoor is successful or not according to the attack time, attacker IP, attacker port number, attacked IP, attacked domain name, attack request header and attack response header recorded in each alarm log; returning the confirmation result to the appropriate network protection device and marking the confirmed WEB backdoor attack event as a successful attack event to the user. The invention can provide a more scientific confirmation means for the WEB backdoor attack event, improve the recognition rate and accuracy of the network security protection equipment to the WEB backdoor attack, and reduce the alarm false alarm rate of the successful confirmation attack.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Network attack identification method and system
ActiveCN108683687AImprove operation and maintenance efficiencyImprove recognition efficiencyData switching networksNetwork managementNetwork attack
The invention discloses a network attack identification method and system. The network attack identification method comprises the steps of detecting whether a target host bears a network attack or not; extracting a to-be-compared feature from network data corresponding to the network attack if the target host bears the network attack; comparing the to-be-compared feature with more than one attackresponse rules, wherein the attack response rules are formed according to first response data, and the first response data is used for an attacked host to respond to a successful attack request; and judging that the network attack is successful if the to-be-compared feature matches the attack response rule. According to the network attack identification method and system provided by the invention,the successful network attack can be precisely identified, and the effective network attack information is provided for a network manager.
Owner:360 TECH GRP CO LTD
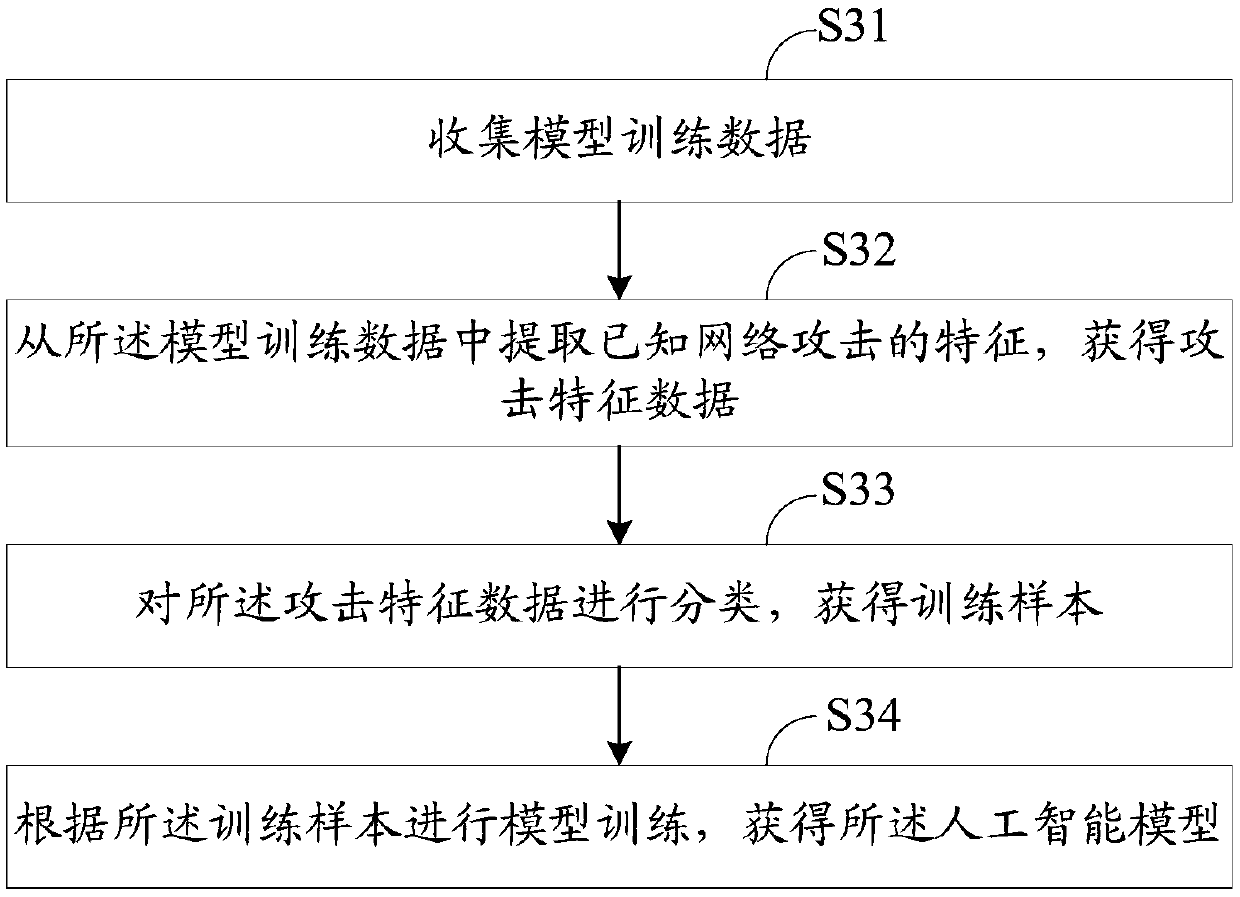
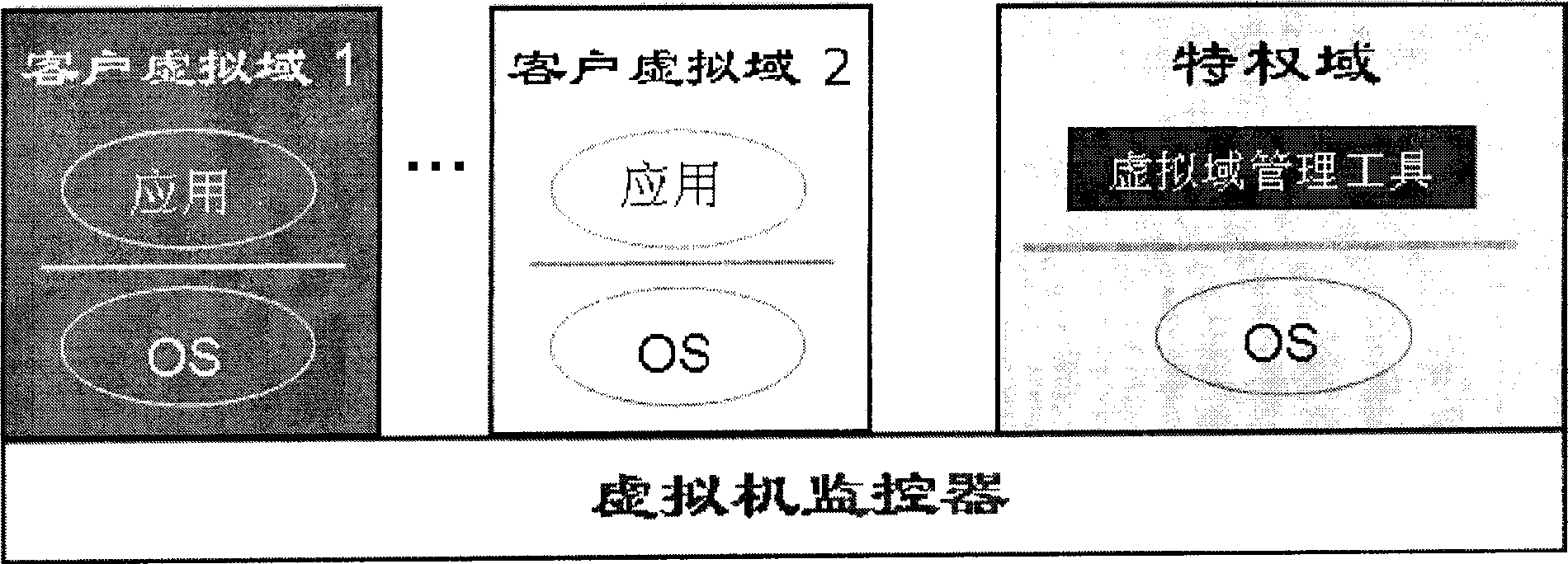
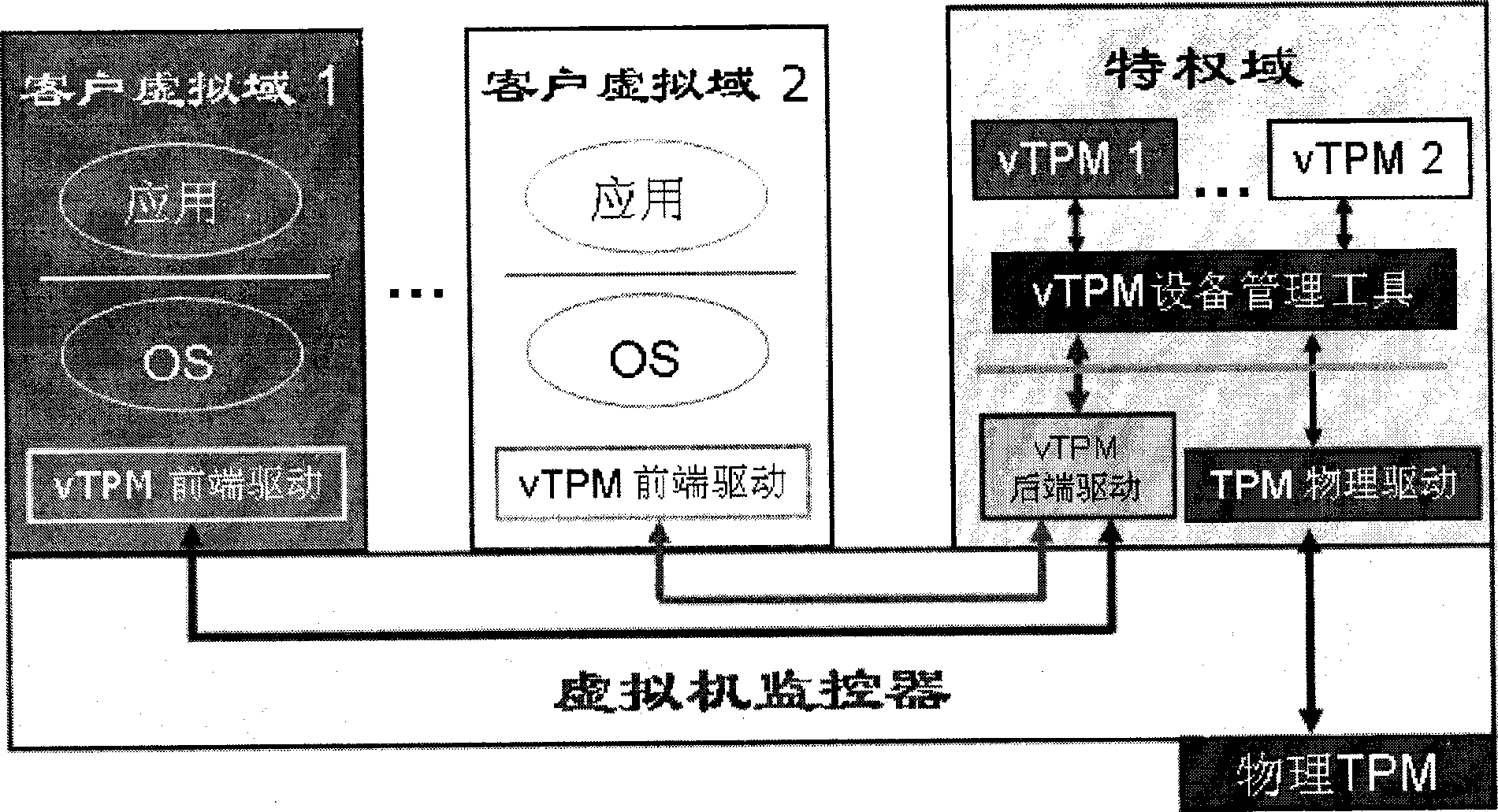
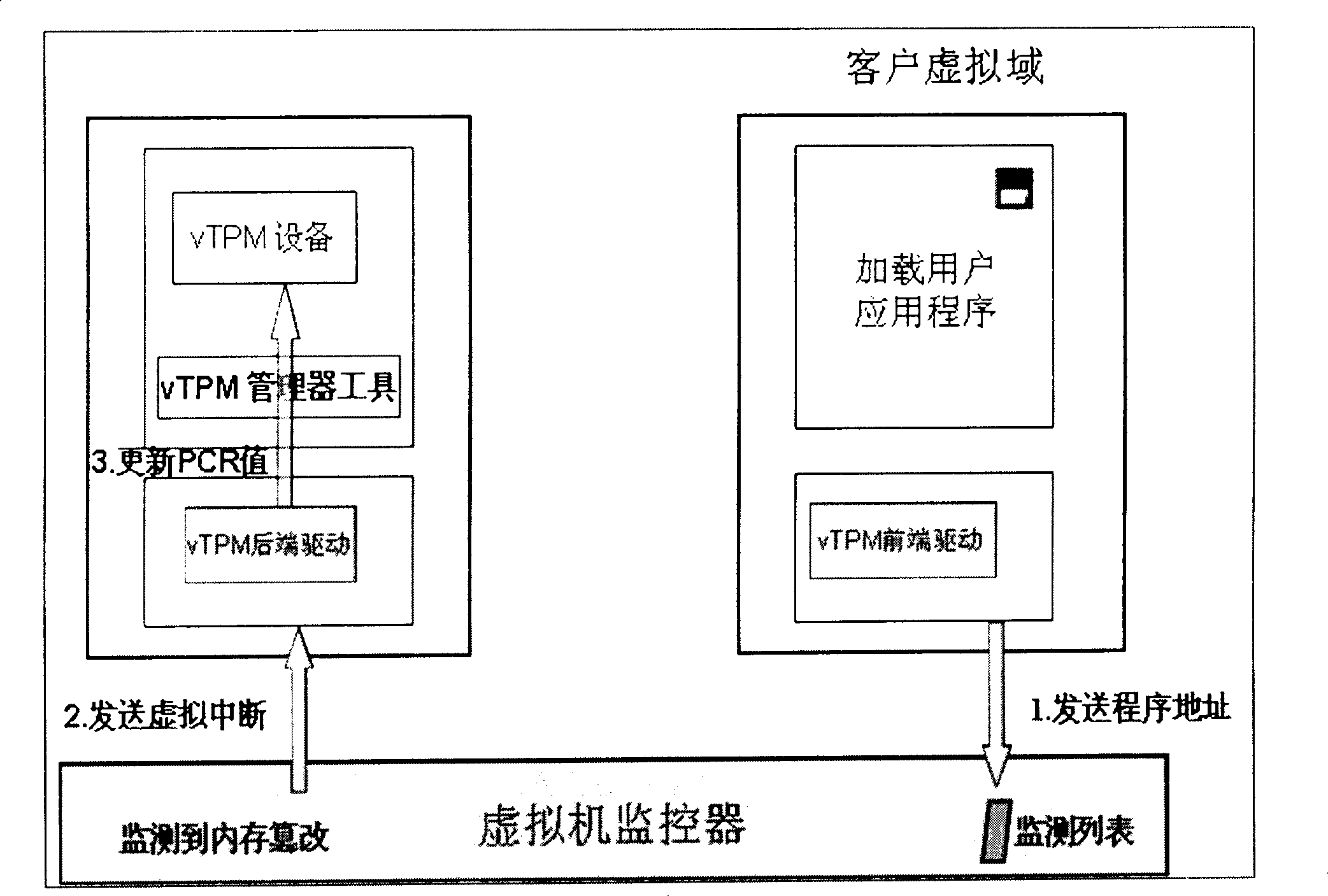
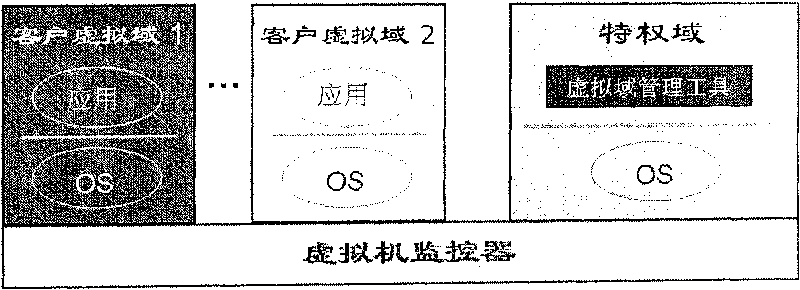
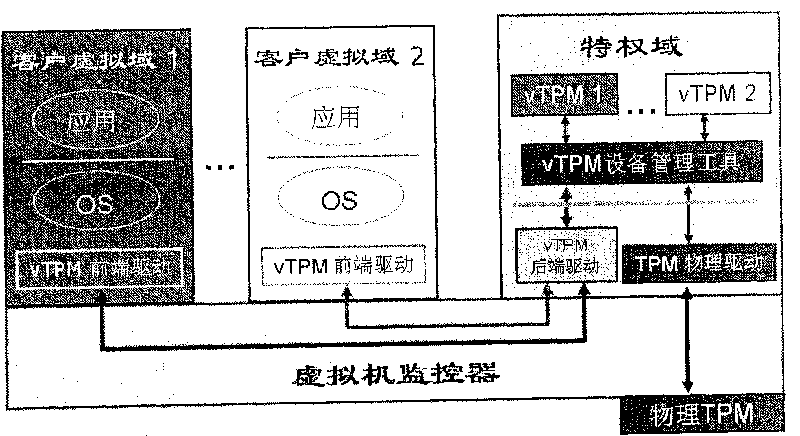
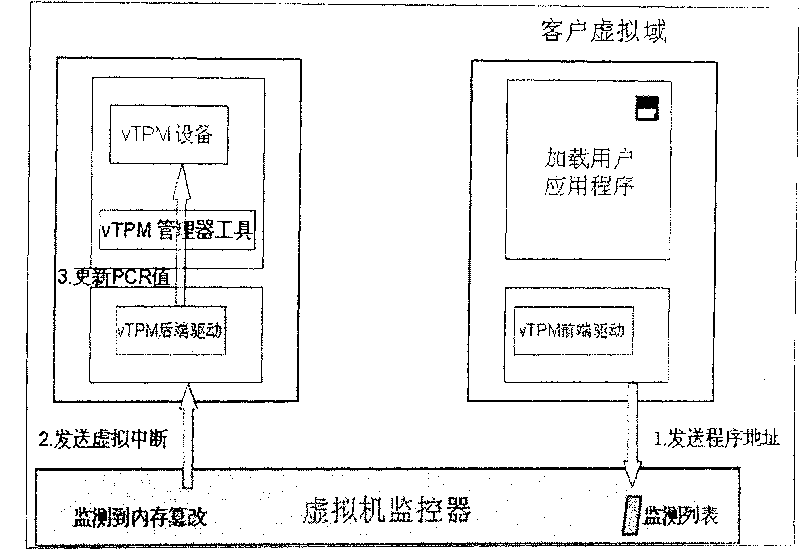
TOCTOU attack response method aiming at TPM trusted computation
InactiveCN101488176AAvoid attackAccurately reflectPlatform integrity maintainanceComputer hardwareExtensibility
The invention relates to a method for responding TOCTOU attack aiming at a TPM credible computer. The components of the method comprise a virtual TPM device program and a privileged domain proxy module which both have more powerful functions. Just as the prior methods, the method of the invention adopts a method of PCR register information updating, but the methods for enabling and executing event update is different from the prior methods so that a TPM command in the following two conditions can correctly indicate the current state of a client virtual domain platform: the first TPM command condition is that a TPM command processing result is not sent out of the virtual TPM device program when the TOCTOU attack is detected, and the second TPM command condition is that the TPM command is not received by the virtual TPM device program when the TOCTOU attack is detected. While considering the security, the invention also takes the system performance into full consideration and ensures the utilization effectiveness and the expandability of system resources by adopting event drive and avoiding process scheduling of an extra user space.
Owner:BEIJING JIAOTONG UNIV
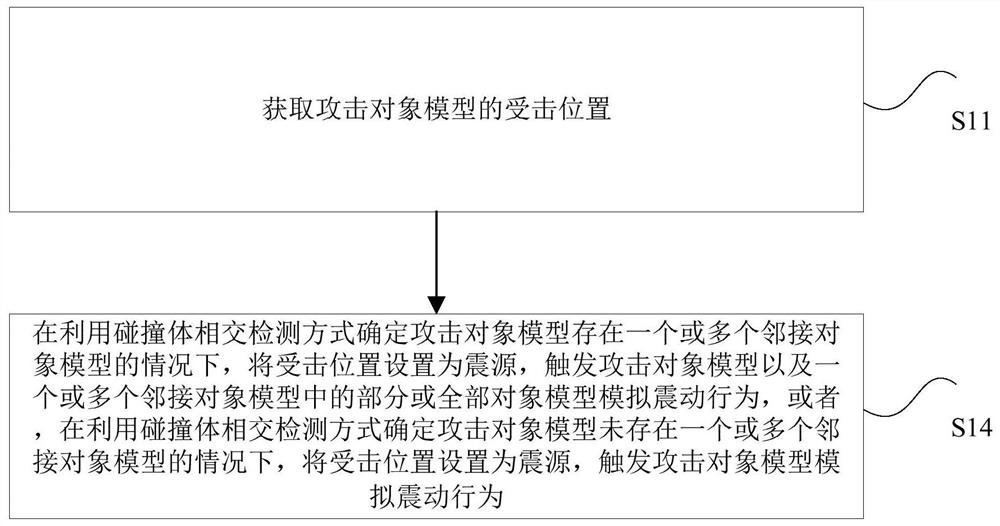
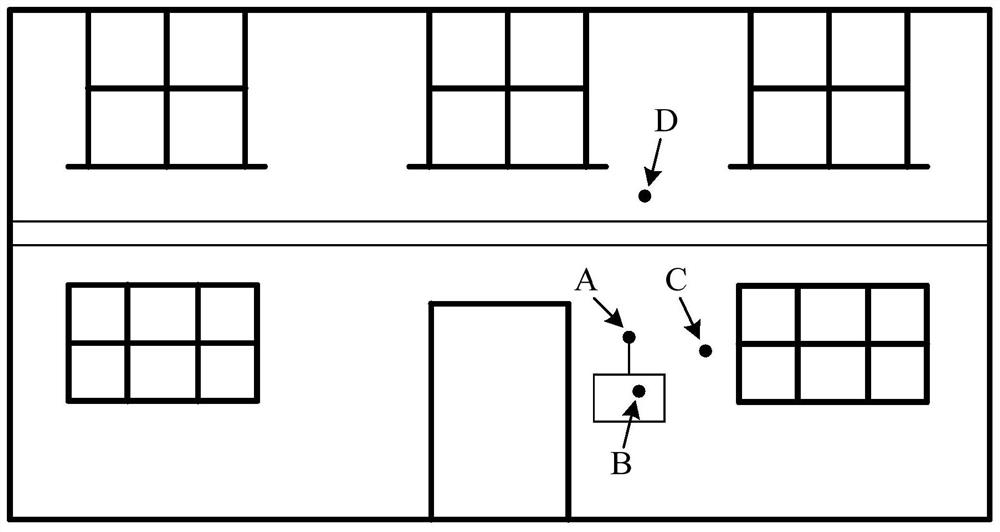
Simulation method, device, storage medium, processor and terminal for model vibration
ActiveCN108295471AImprove realismImprove gaming experienceInput/output for user-computer interactionVideo gamesSimulationComputer terminal
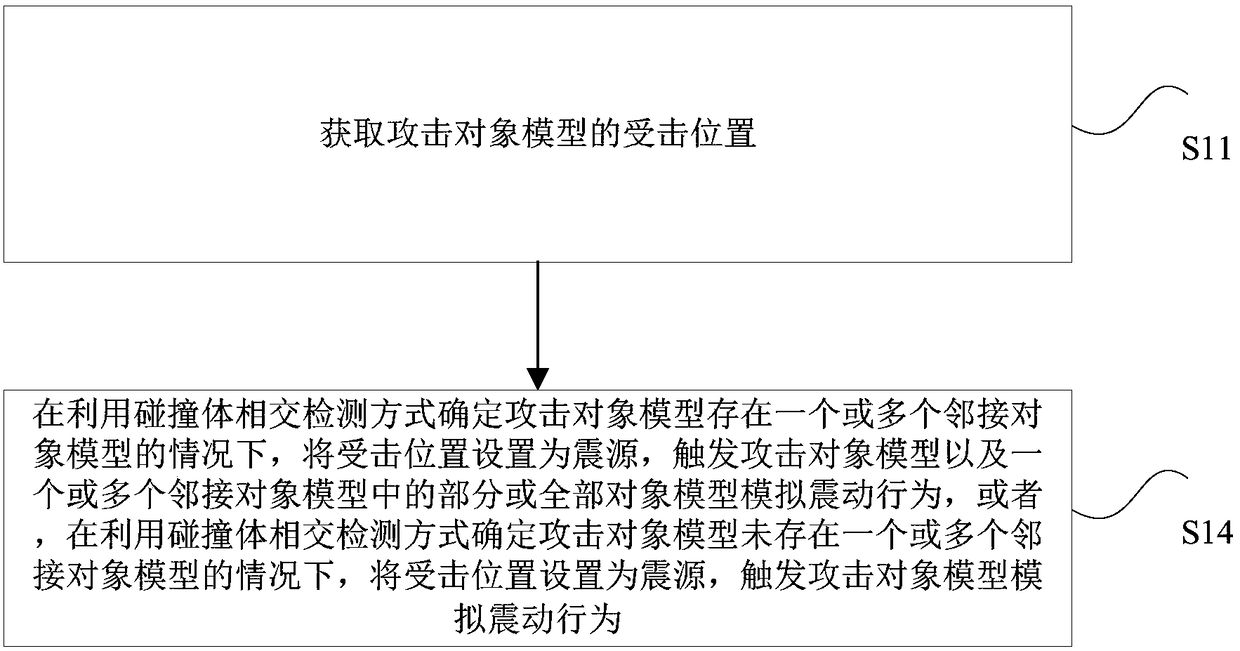
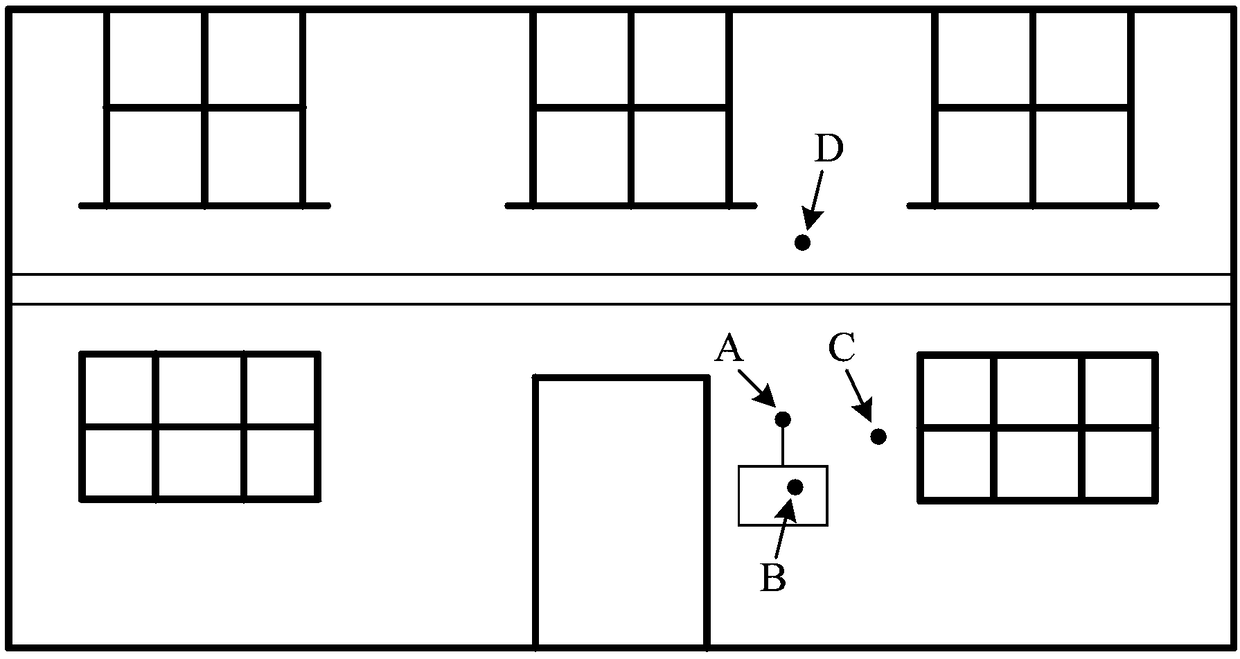
The invention discloses a simulation method, device, storage medium, processor and terminal for model vibration. The method comprises the steps that an attacked position of an attacking target model is obtained; under a condition that a crashing body intersectant detection method is used for determining that the attacking target model has one adjacent target model or multiple adjacent target models, the attacked position is taken as a centrum to trigger the attacking target model and partial or all target models of the one adjacent target model or more adjacent target models to simulate vibration behaviors, or under a condition that the crashing body intersectant detection method is used for determining that the attacking target model does not have one adjacent target model or multiple adjacent target models, the attacked position is taken as the centrum to trigger the attacking target model to simulate the vibration behaviors. The simulation method, device, storage medium, processor and terminal for the model vibration solve the technical problem that a mobile phone game scene in a related technology is lack of the simulation of attack responses.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
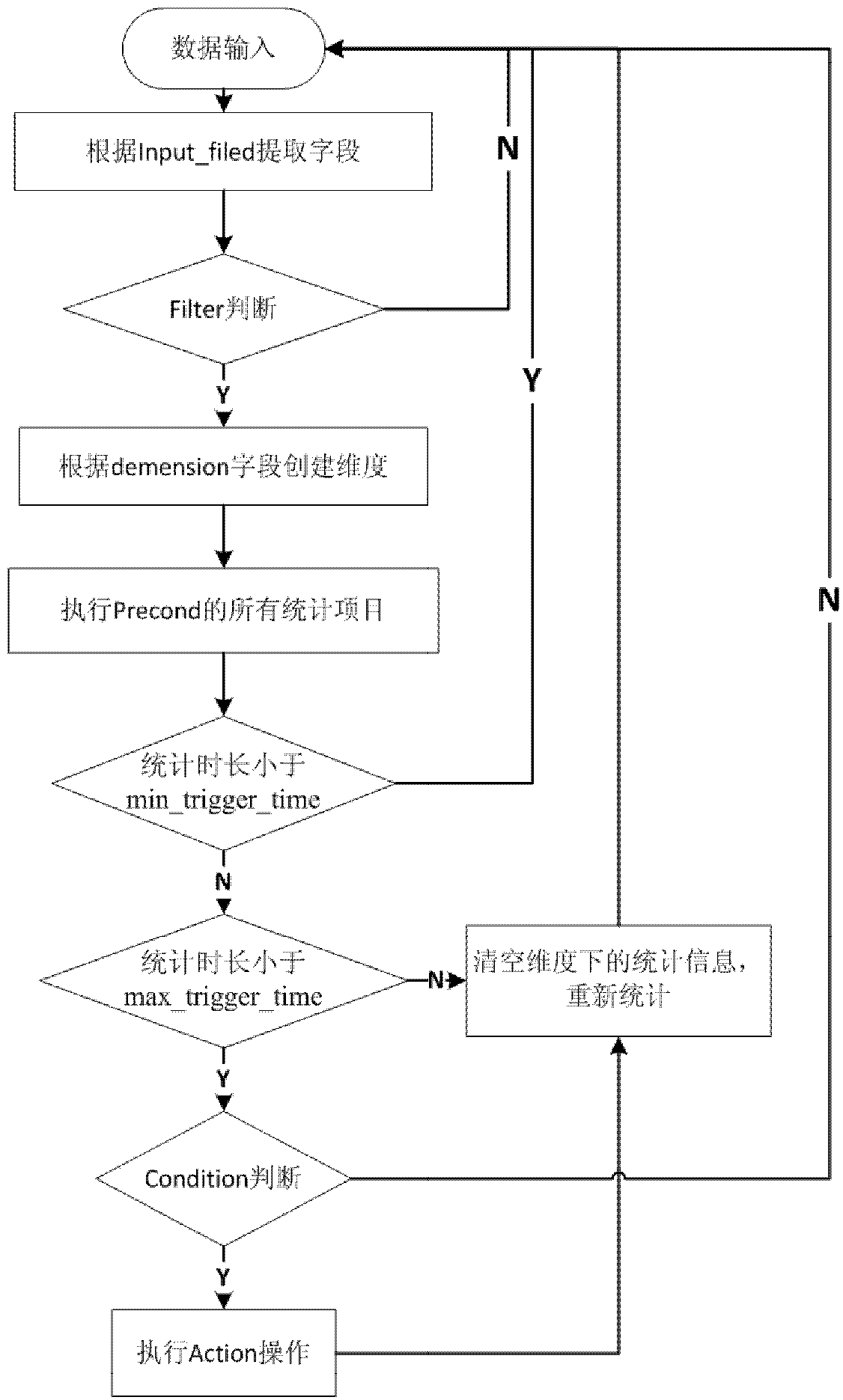
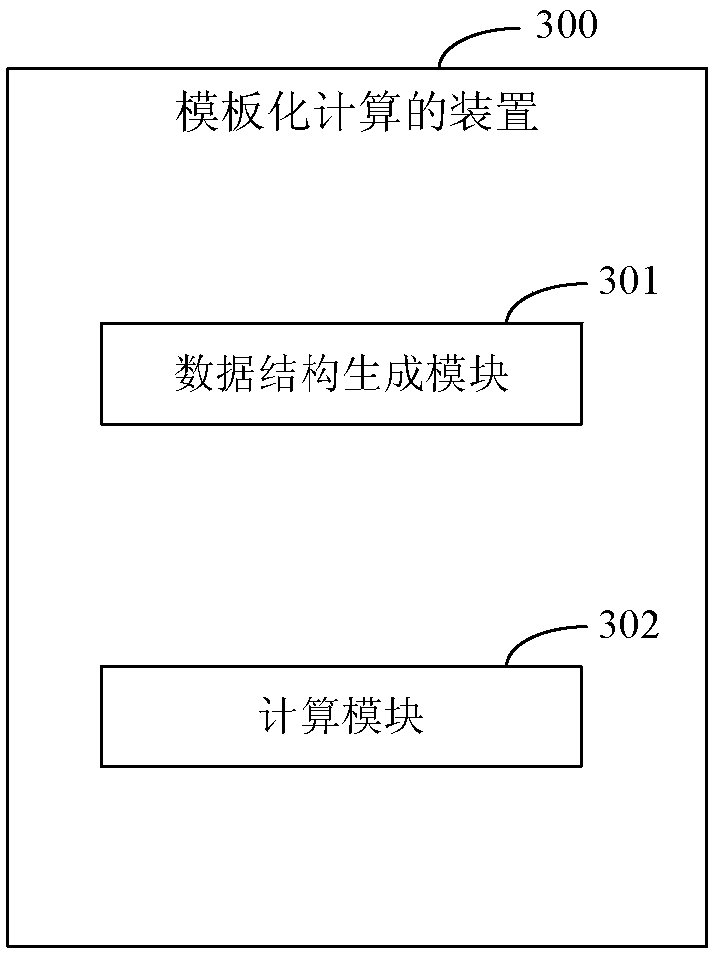
Template calculation method, device and system
PendingCN109992957AImprove quick response abilityIncrease flexibilityDigital data protectionSoftware maintainance/managementRisk ControlStrategy execution
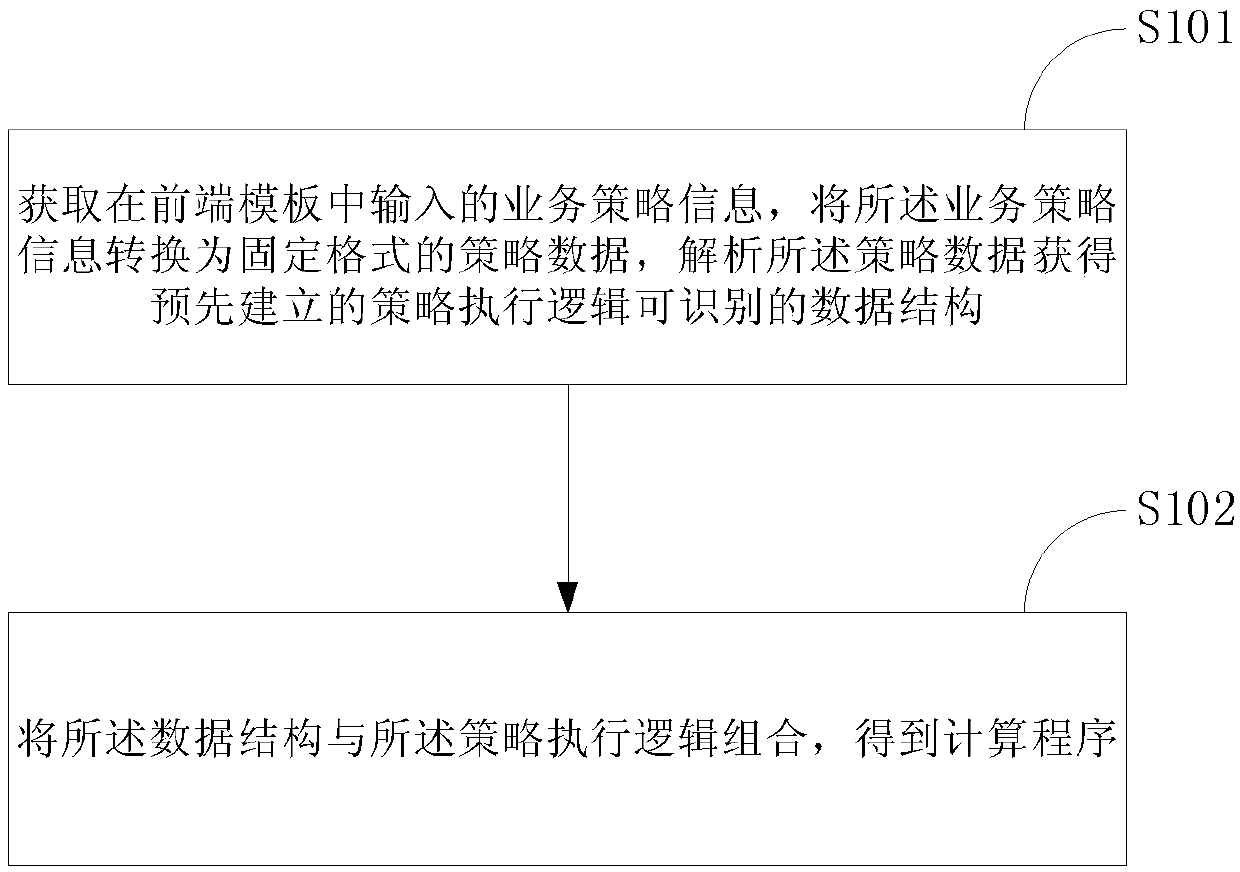
The invention discloses a templated computing method, device and system, and relates to the technical field of computers. A specific embodiment of the method comprises the steps of obtaining service strategy information input in a front-end template, converting the service strategy information into strategy data in a fixed format, and analyzing the strategy data to obtain a pre-established data structure which can be identified by strategy execution logic; and combining the data structure with the strategy execution logic to obtain a calculation program. According to the embodiment, the specific service strategy information can be separated from the strategy execution logic; therefore, a developer can conveniently input the service strategy information in the friendly front-end template, the calculation program responding to malicious access can be rapidly generated by combining the service strategy information with the pre-established strategy execution logic, and the response capability and the attack response capability of the risk control system are improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
DDoS attack detection and defense apparatus and method using packet data
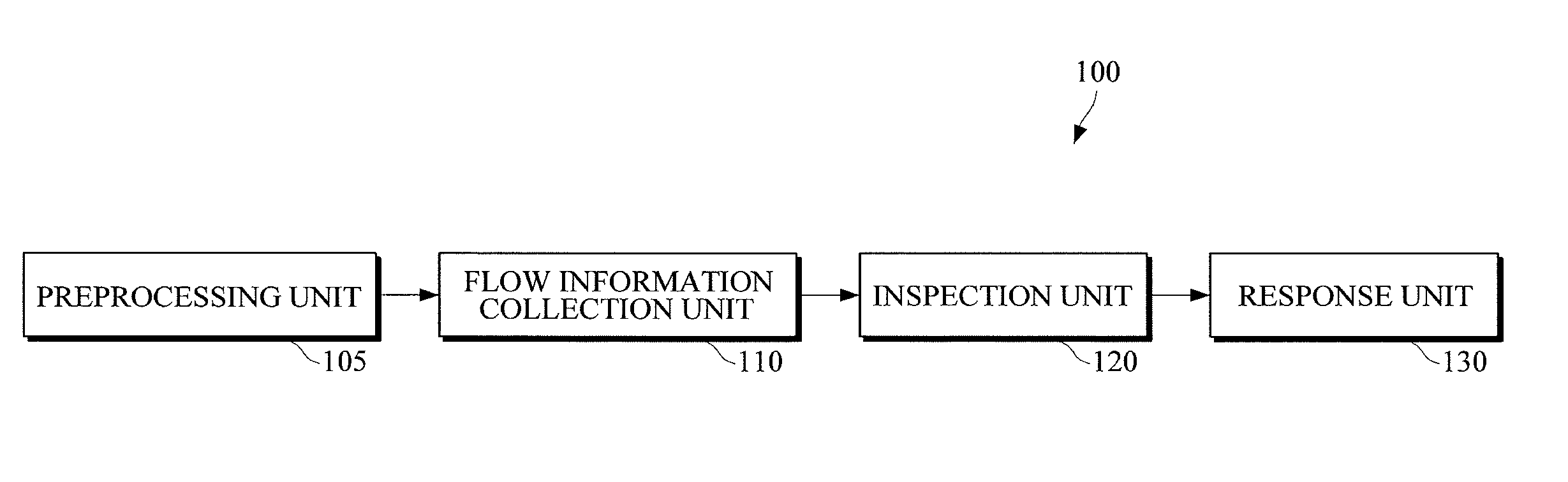
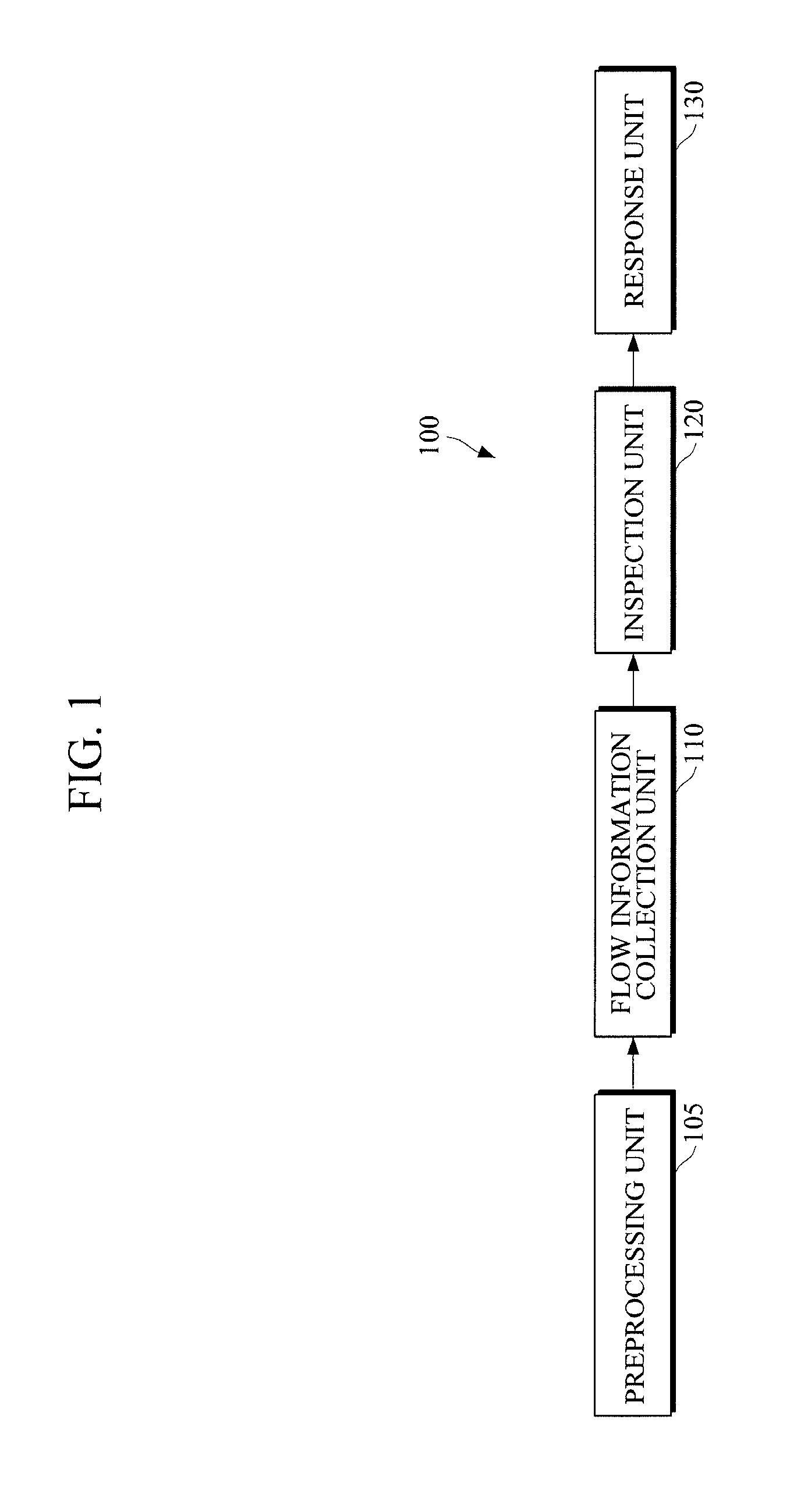
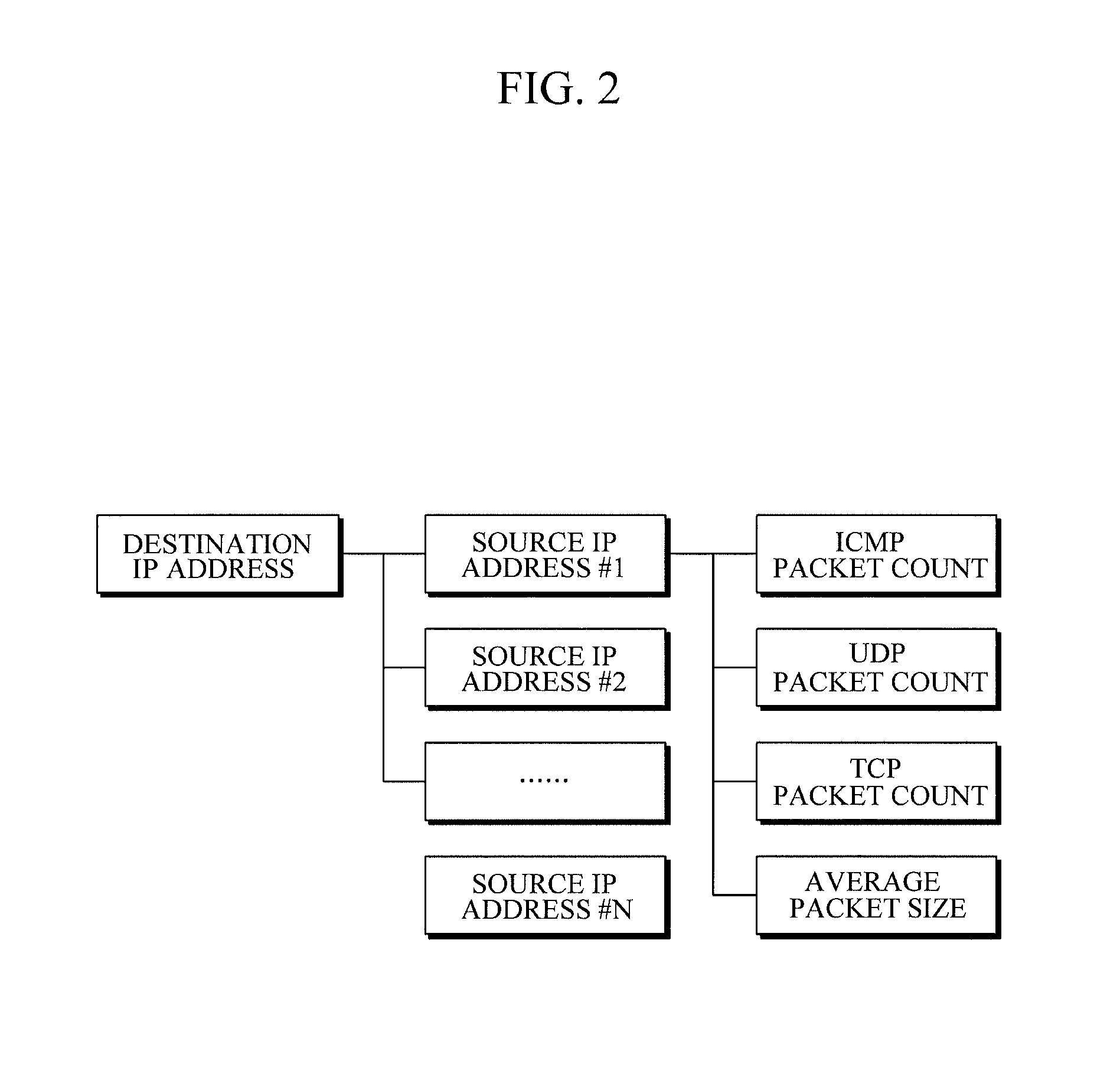
InactiveUS8634717B2Protection attackError preventionFrequency-division multiplex detailsIp addressInformation Harvesting
A Distributed Denial of Service (DDoS) attack detection and defense apparatus and method are provided. The Distributed Denial of Service (DDoS) attack detection and defense apparatus includes: a flow information collection unit to collect, from one or more input packets with an IP address of an attack target system as a destination IP address, flow information including source IP addresses of the input packets and packet counts of one or more flows that are classified for each of the source IP addresses and each of different protocol types; an inspection unit to calculate packets per second (PPS) values of the flows based on the packet counts; and a response unit to determine a DDoS attack response method for each of the flows based on the PPS value and the protocol type of a corresponding flow and to process the corresponding flow using the determined DDoS attack response method.
Owner:ELECTRONICS & TELECOMM RES INST
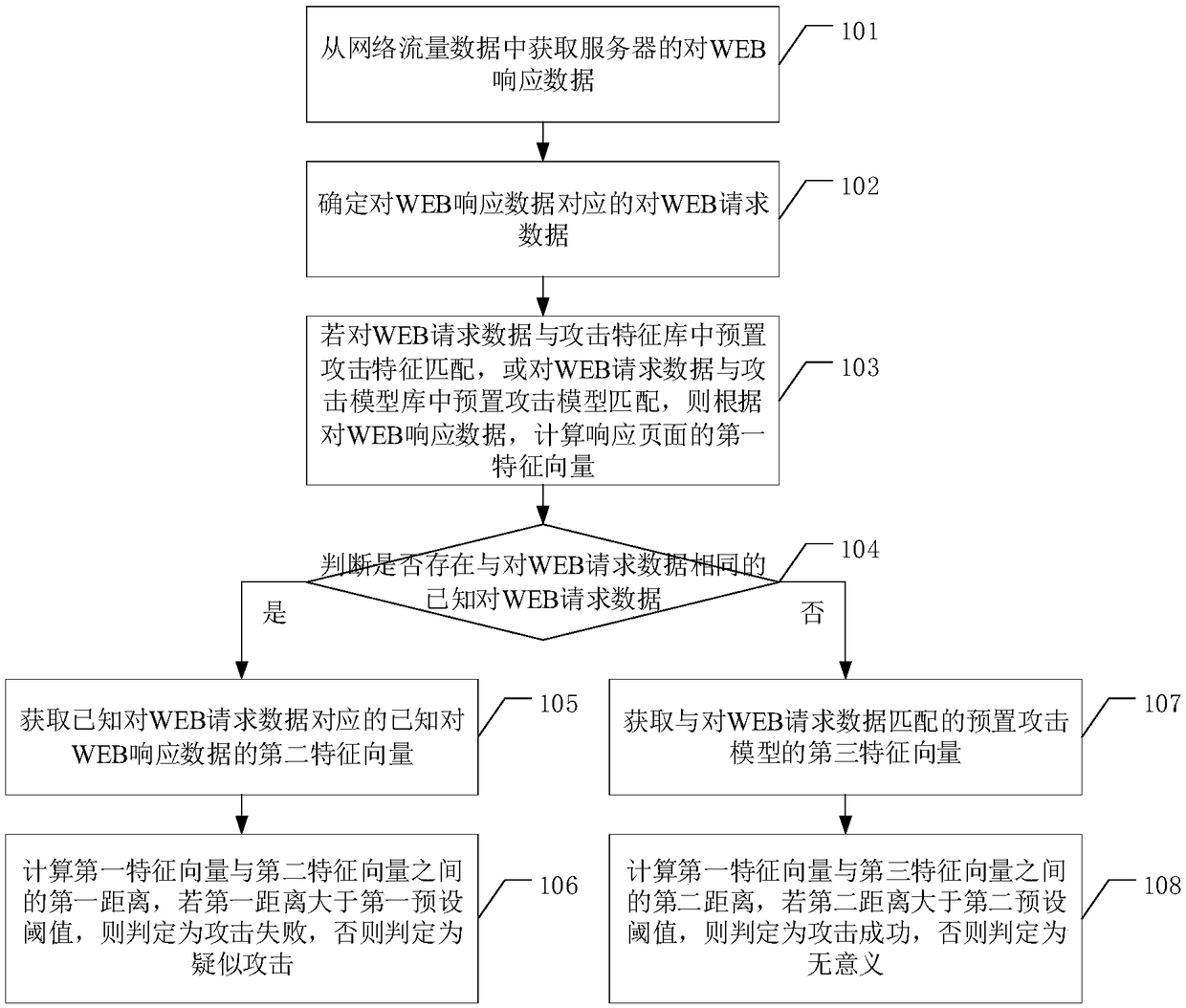
Method and device for determing WEB attack result, electronic device and readable storage medium
The embodiment of the invention discloses a method and device for determining a WEB attack result, and an electronic device and a readable storage medium. The attack result of the WEB request data corresponding to the WEB response data is determined by calculating the similarity between a response page corresponding to the WEB response data and a normal response page, and an attacked response page, respectively. Therefore, the technical problem that the existing detection systems usually only detect whether a WEB attack has occurred and cannot determine the result and the impact of the attacksis solved.
Owner:EASTCOMPEACE TECH
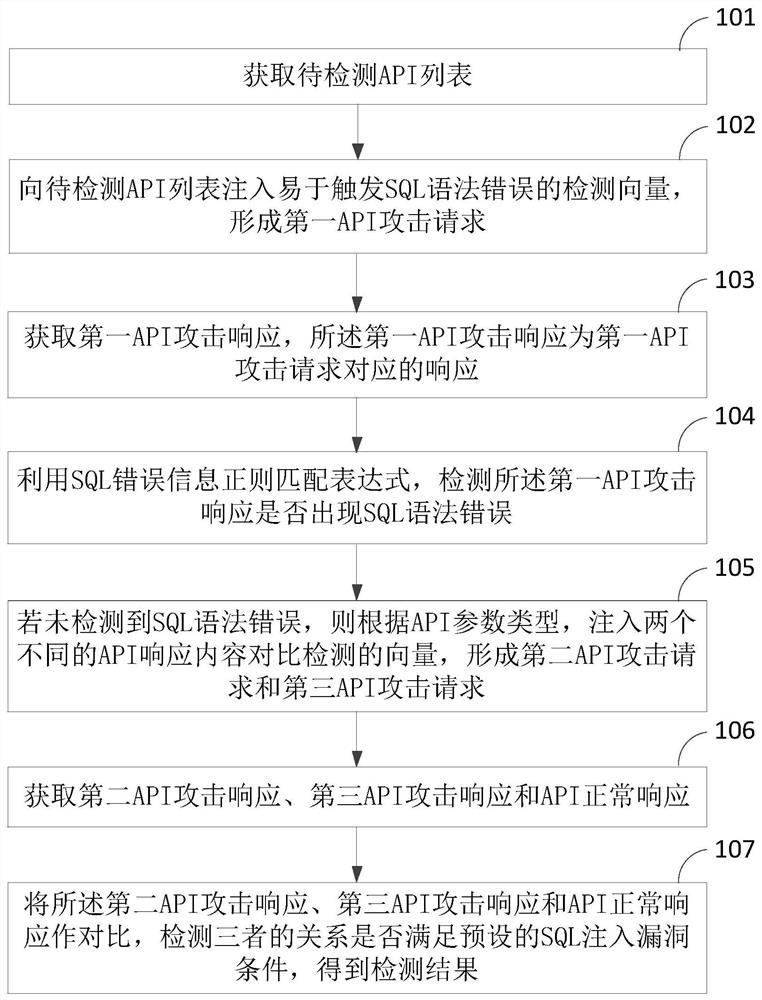
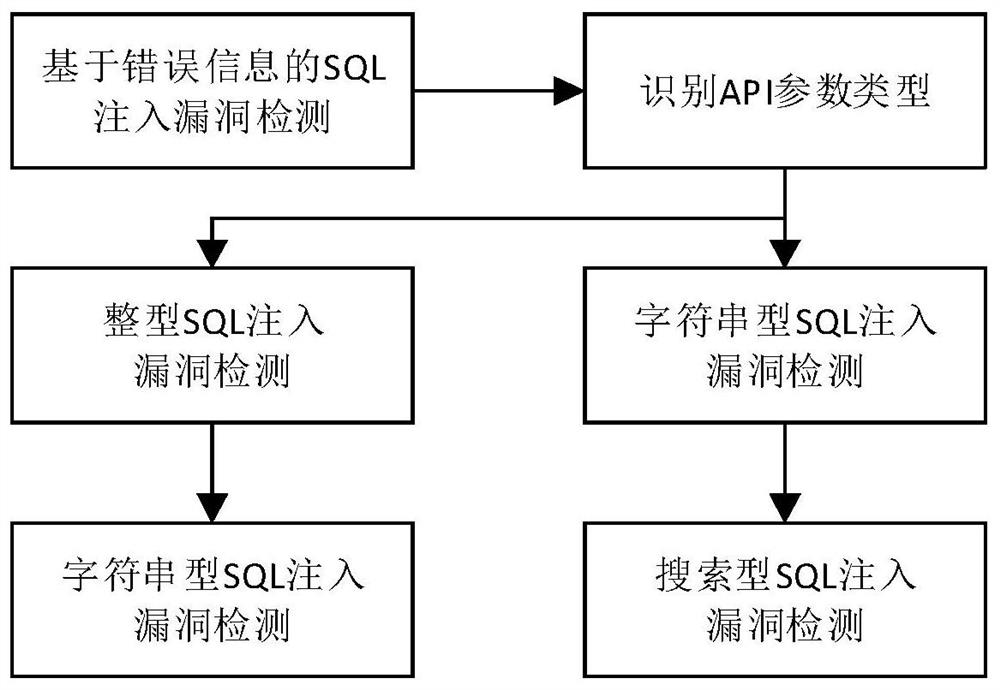
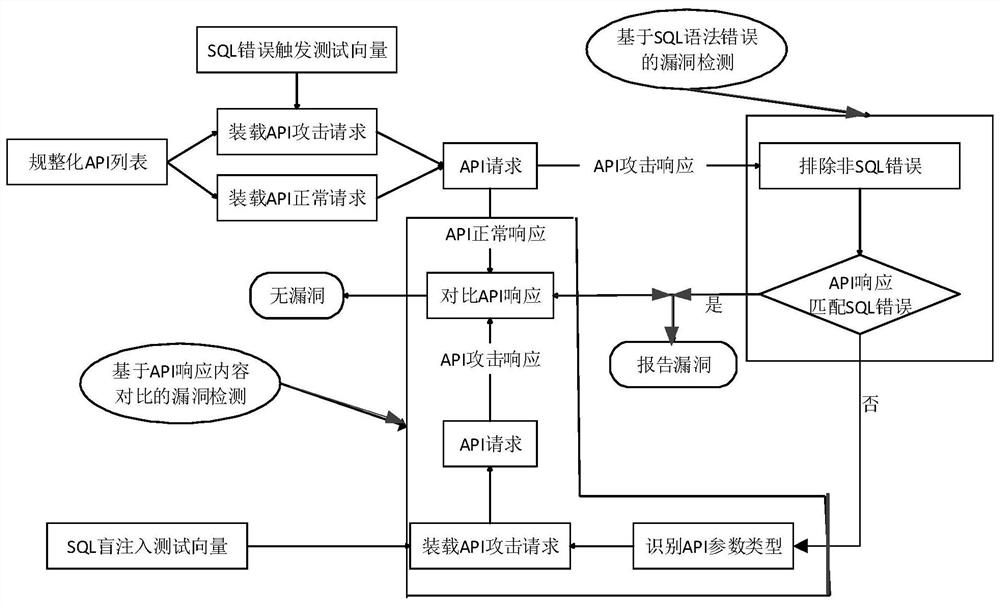
SQL injection vulnerability detection method and device for REST API
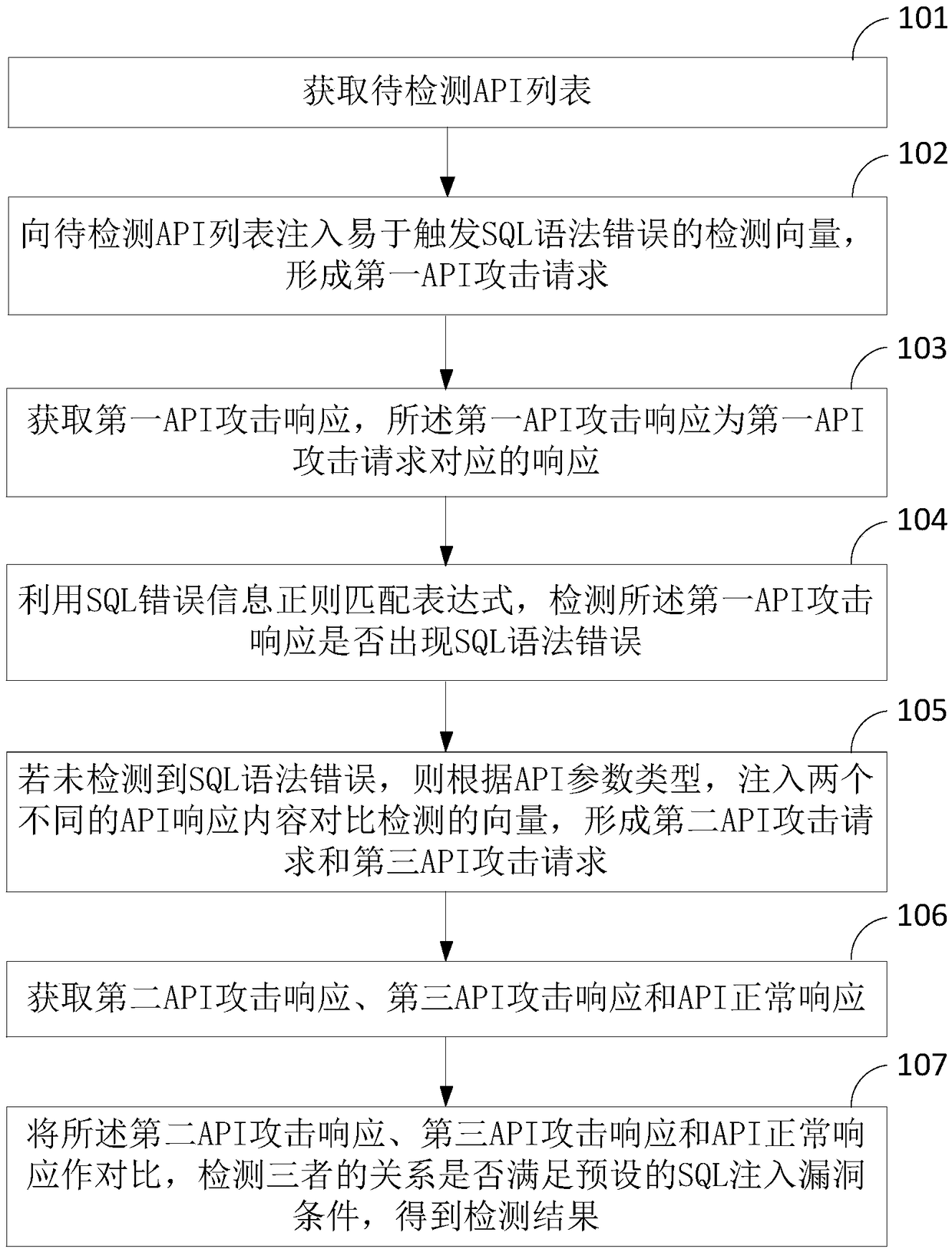
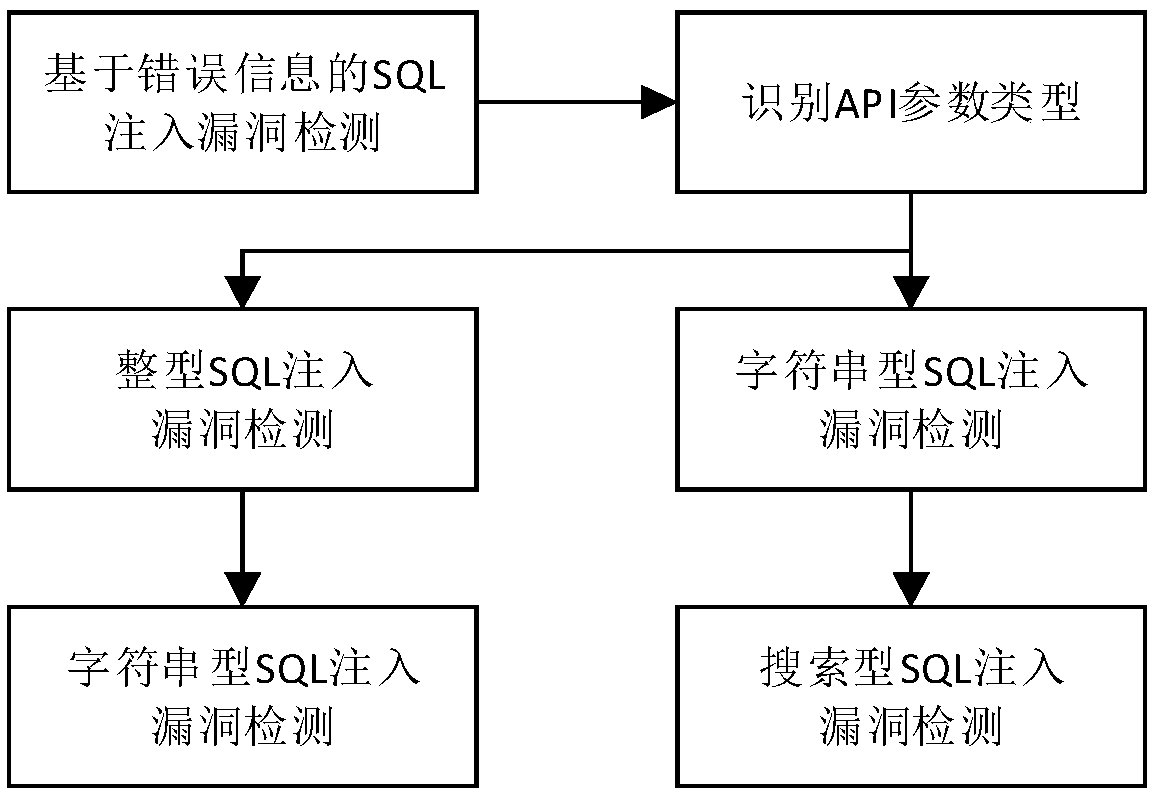
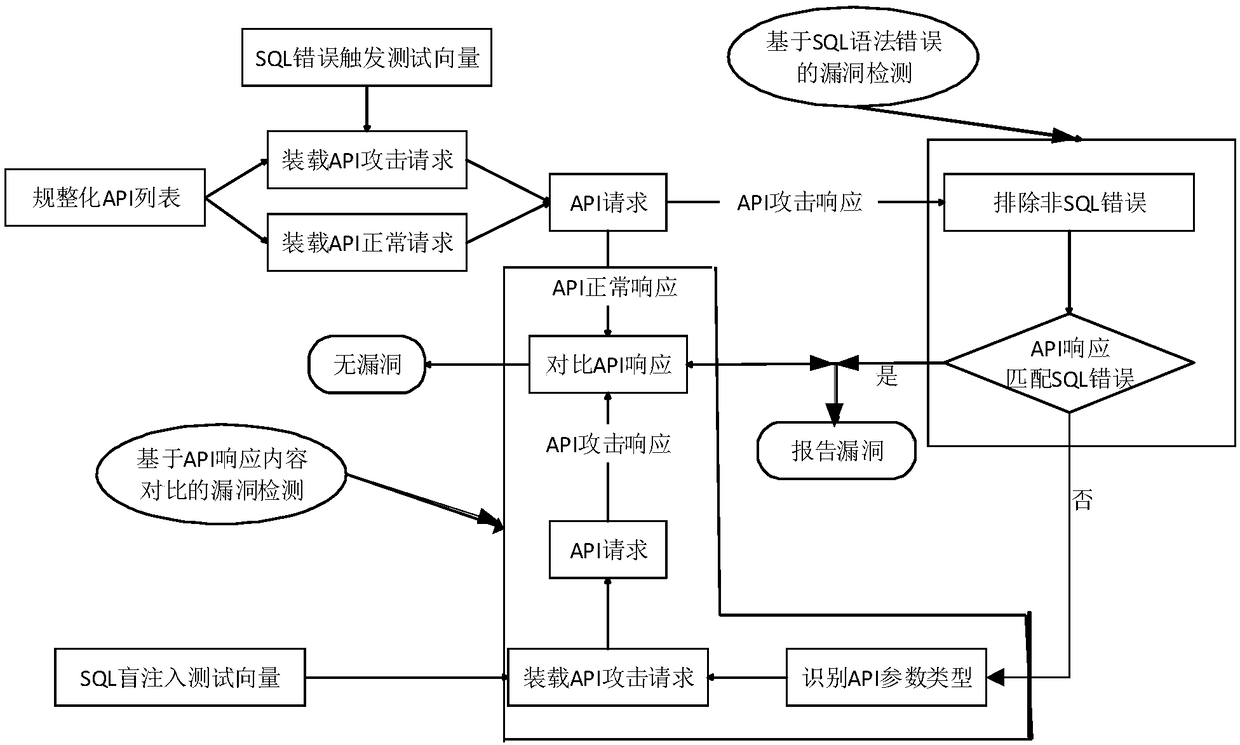
ActiveCN109246113AEfficient detectionImprove detection accuracyTransmissionSyntax errorSQL injection
The invention discloses an SQL injection vulnerability detection method and device for a REST API, and the method comprises the steps: injecting a detection vector that is easy to trigger a SQL syntaxerror into a to-be-detected API list to form a first API attack request, and then using a SQL error information regular matching expression to detect whether a first API attack response has a SQL syntax error or not; injecting two API response content comparison detection vectors according to the type of an API parameter if no SQL syntax error is detected, obtaining a second API attack response,a third API attack response and an API normal response to perform the comparison therebetween, detecting whether the relationship between the second API attack response, the third API attack responseand the API normal response meets a default SQL injection vulnerability condition and obtaining a detection result. Therefore, the detection vector that is easy to trigger the SQL syntax error and a vector for the API response content comparison detection are injected into the to-be-detected RESTful API, thereby detecting the mode of the corresponding API response, and achieving the effective detection of the SQL injection vulnerability of the RESTful API.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
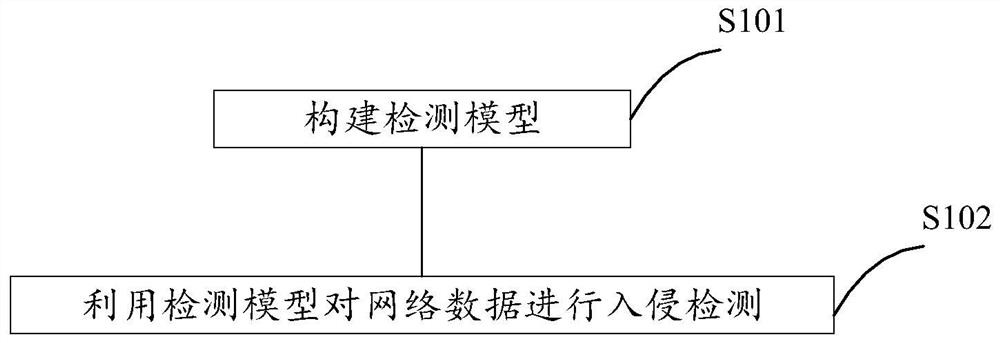
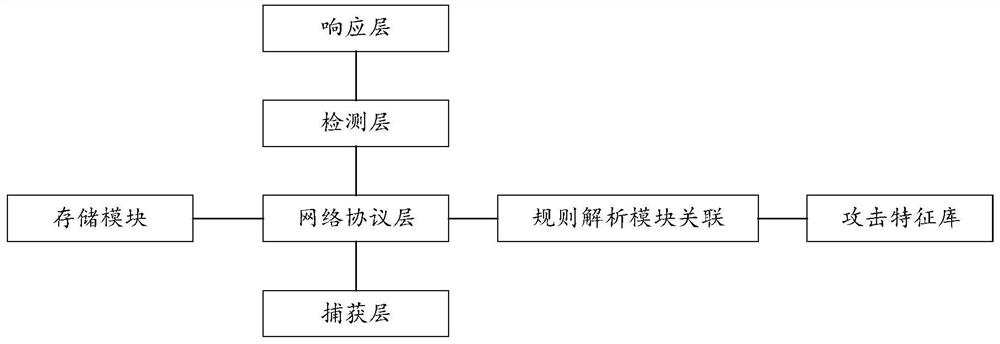
Intrusion detection method and detection equipment
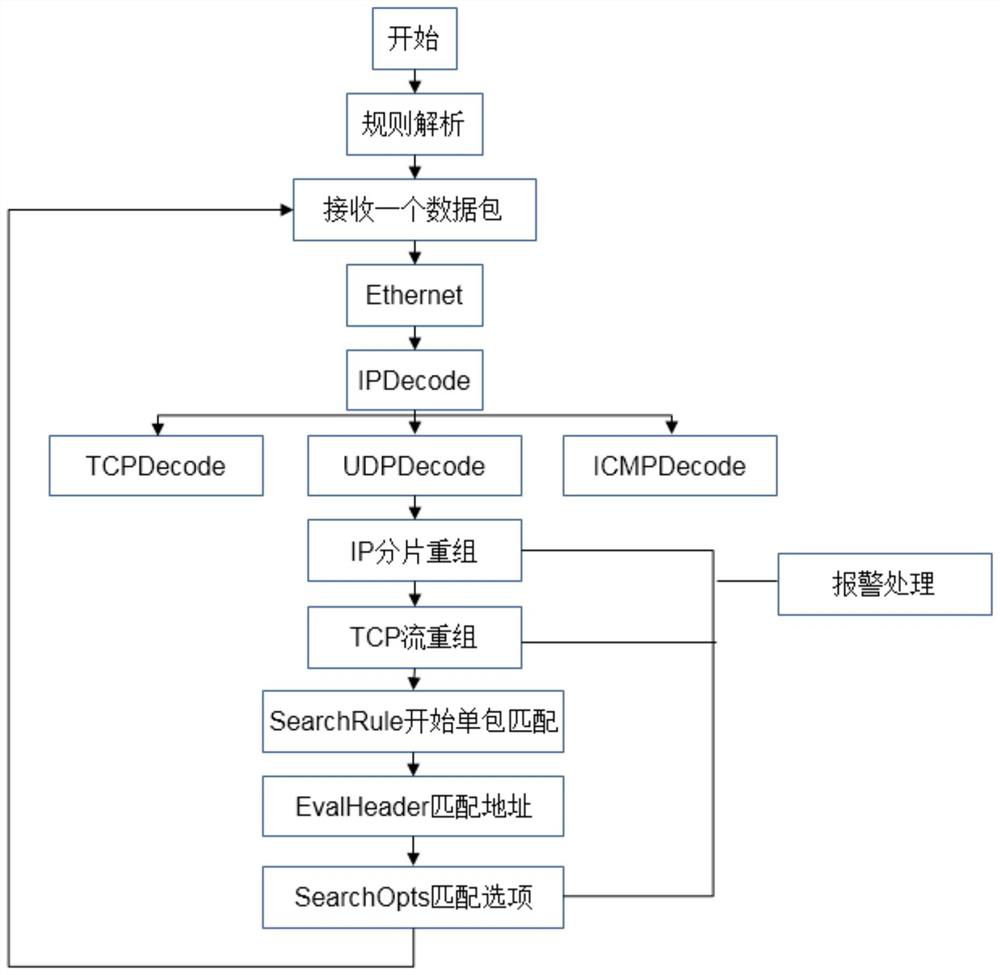
The invention provides an intrusion detection method and detection equipment, and the method comprises the steps: building a detection model which comprises a capture layer, a network protocol layer, a detection layer and a response layer; the capture layer is used for capturing a data packet; the network protocol layer is used for performing protocol analysis on the captured data packet to obtain an analysis result; the detection layer is used for determining whether the captured data packet is an attack event or not according to the analysis result; the response layer is used for performing attack response when the detection layer judges that the captured data packet is an attack event; and performing intrusion detection on the network data by using the detection model. Through the method, whether the data packet contains the attack event or not can be judged through protocol analysis of the data packet.
Owner:NEW H3C SECURITY TECH CO LTD
DDoS attack detection method based on network traffic application layer
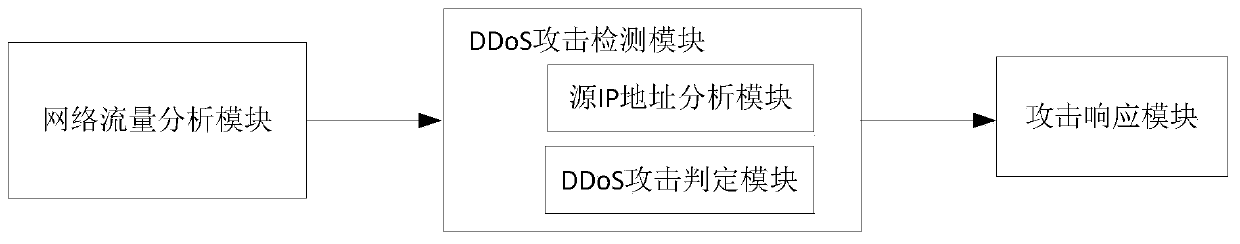
InactiveCN110493230AIdentify similaritiesReduce false alarm rateTransmissionIp addressProtocol Application
The invention discloses a DDoS attack detection method based on a network traffic application layer. The method comprises the following steps: selecting three parameters including a flow change rate,a new source IP address change rate and a source IP address request allocation rate to analyze network flow. Therefore, the DDoS attack traffic is distinguished from the FC traffic. The system is provided with a network flow analysis module, a DDoS attack detection module and an attack response module. When network flow changes suddenly, the network flow analysis module sends a warning signal to the DDoS attack detection module. The DDoS attack module is used for judging whether an FC attack or a DDoS attack occurs. When the DDoS attack is detected, the DDoS attack is detected. The attack response module is activated to filter malicious traffic and maintain uninterrupted service for a real user, the similarity between application layer DDoS attack traffic and FC traffic can be effectivelyrecognized, main characteristics of the application layer DDoS attack traffic and FC traffic are selected for distinguishing, the false alarm rate and the missing report rate are reduced, the cost islow, and application and popularization are facilitated.
Owner:北京云端智度科技有限公司
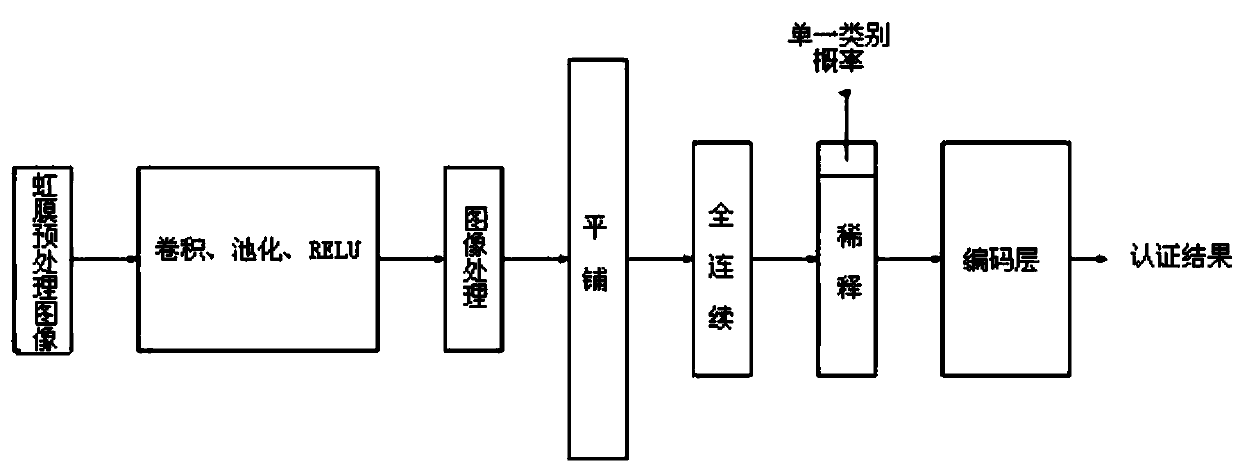
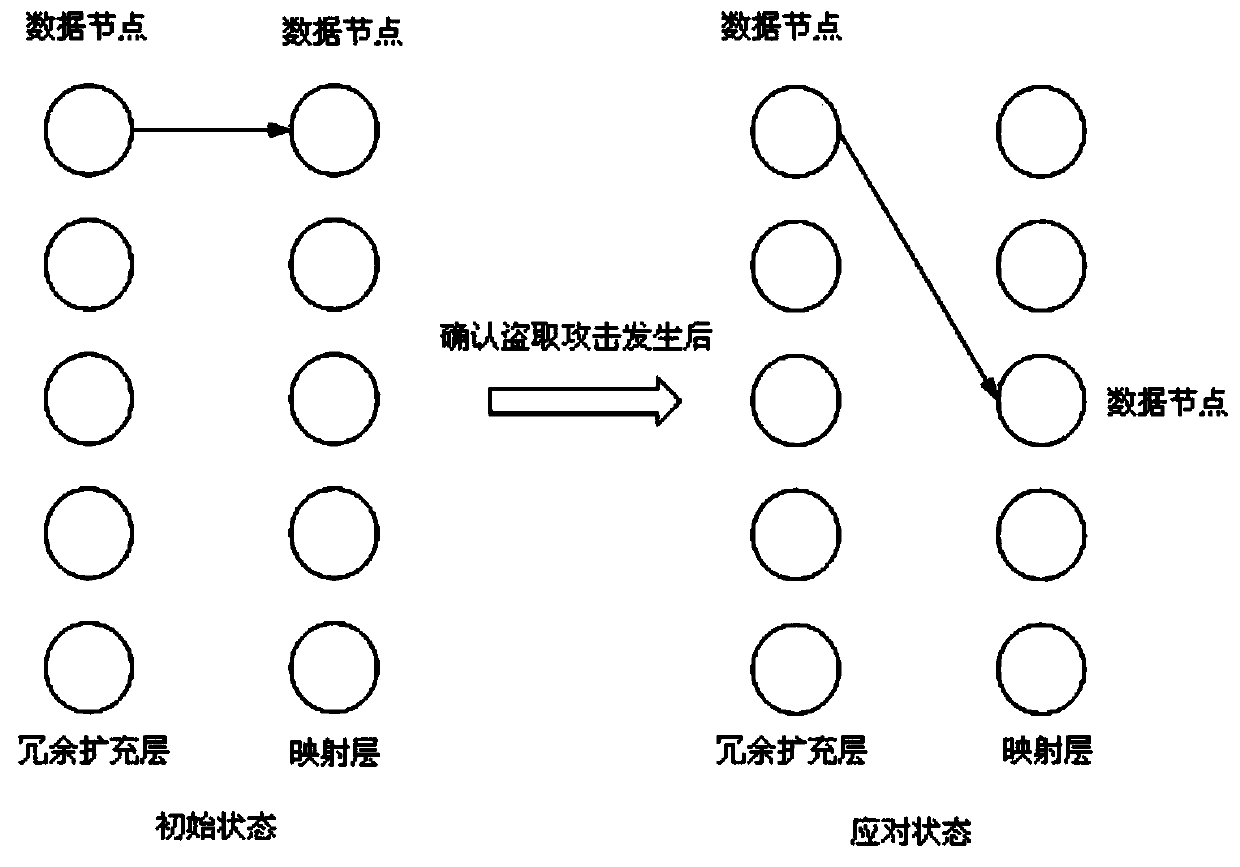
Heterogeneous iris authentication method with theft attack response mechanism
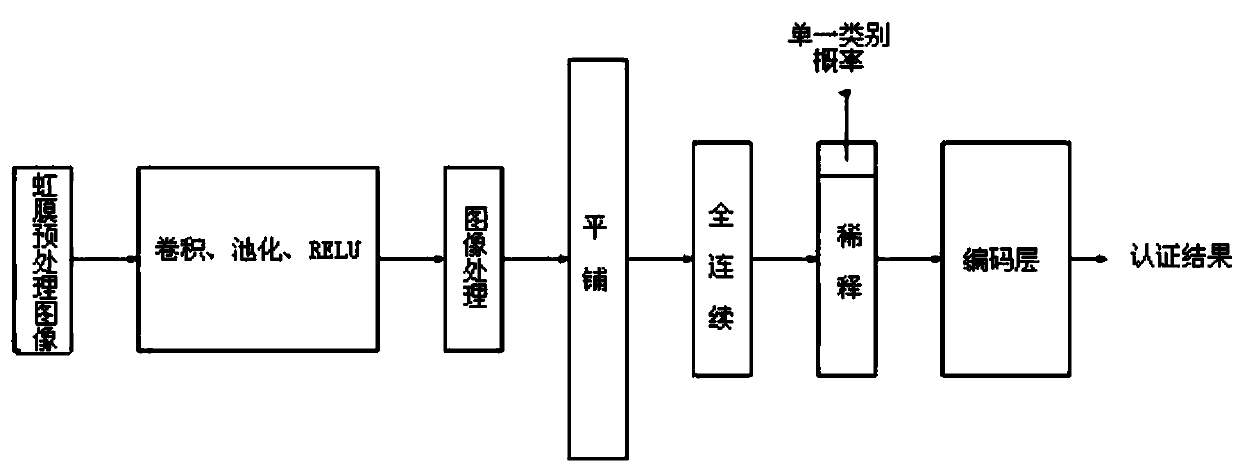
ActiveCN110046588AImprove fault toleranceImprove robustnessCharacter and pattern recognitionDigital data authenticationImaging processingAuthentication system
The invention discloses a heterogeneous iris authentication method with a theft attack response mechanism. The heterogeneous iris authentication method comprises the following steps of step 1, constructing a heterogeneous iris multi-class authentication system improved based on a convolutional neural network; 2, constructing the theft attack response mechanism; 3, starting the formal authentication; step 4, enabling the images to sequentially enter a full connection layer; step 5, obtaining a similarity probability with the iris to which the single classifier belongs; step 6, obtaining an accurate similarity probability; and step 7, through the mapping relation of the coding layer, outputting the iris type condition to which the tested iris belongs. The method has the beneficial effects that the traditional convolutional neural network is transformed, and the image processing layer and the dilution layer are added, so that the difference between different types of irises can be amplified in multi-type authentication, and the authentication accuracy is improved.
Owner:JILIN UNIV
Ddos attack distributed detection and response method based on information entropy
InactiveCN104580222BReduce the monitoring burdenImprove detection accuracyTransmissionResponse methodIp address
Owner:SHANDONG UNIV
Indirect distributed denial of service attack defense method and system based on Web agency
InactiveCN102438025BAttack Response ImplementationEnable early detectionData switching networksSmall probabilityHidden semi-Markov model
Owner:SUN YAT SEN UNIV
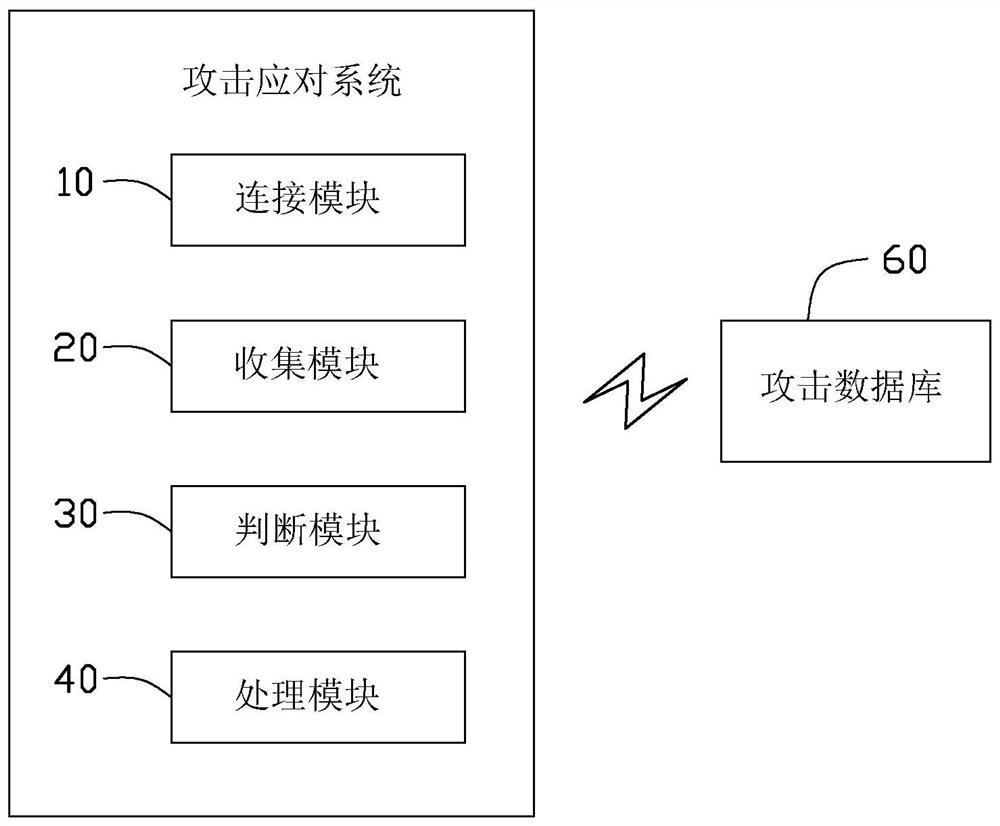
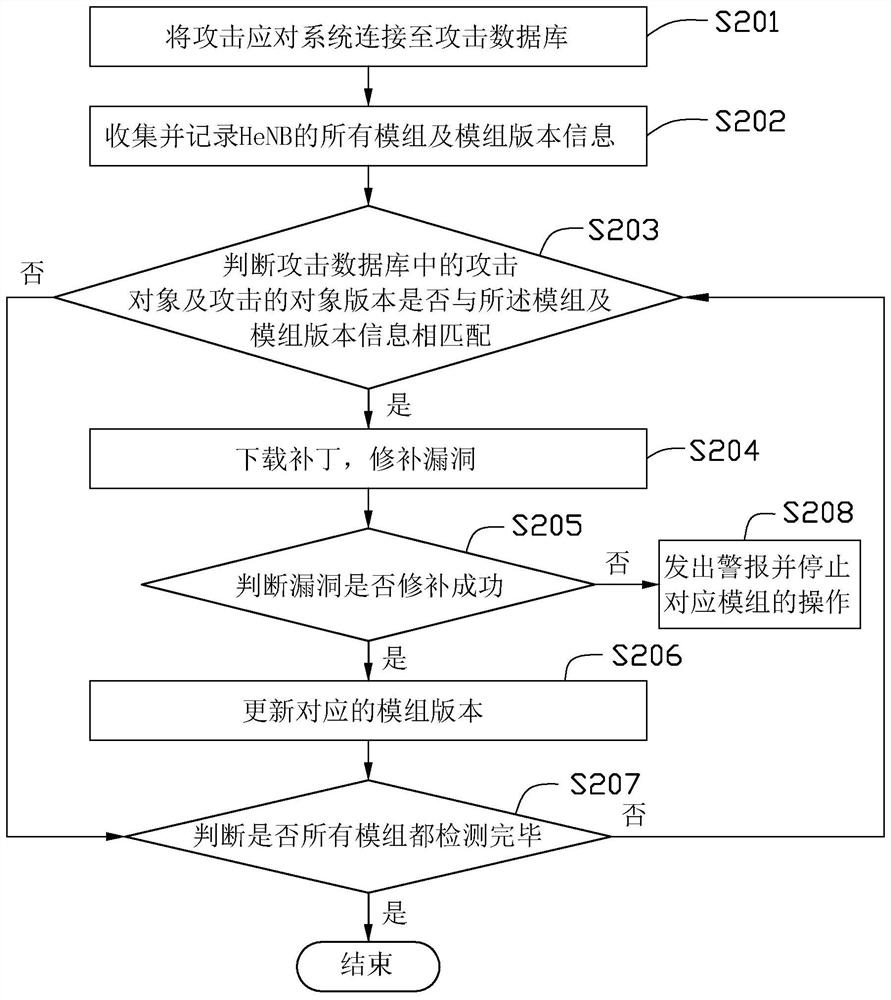
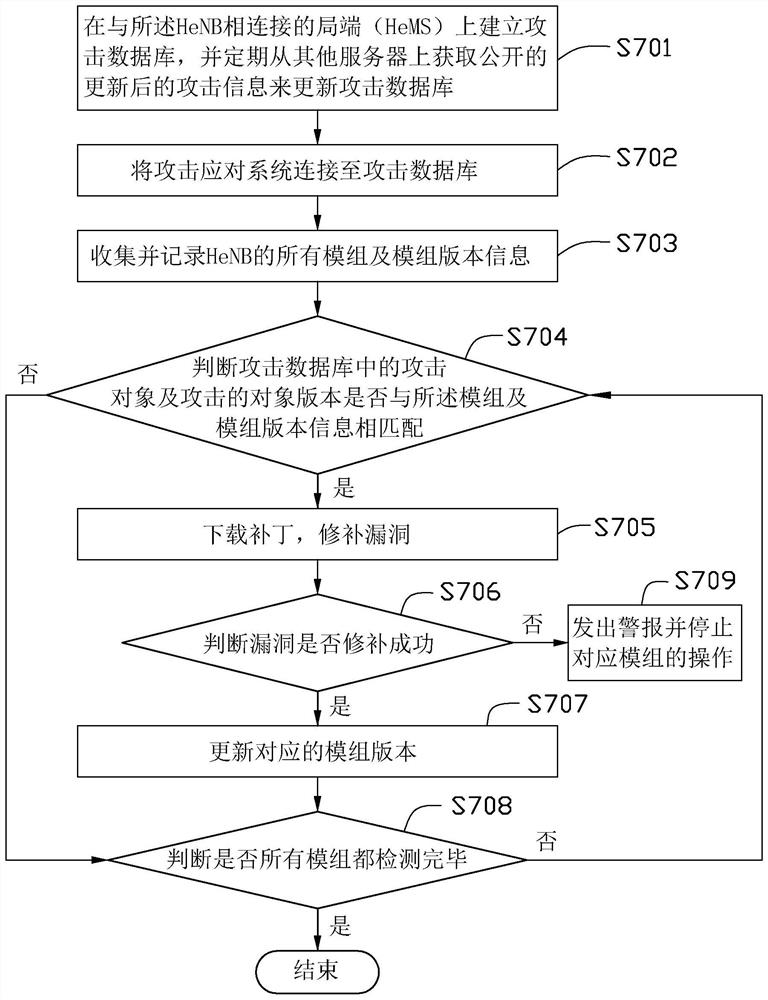
Attack Response Method and System
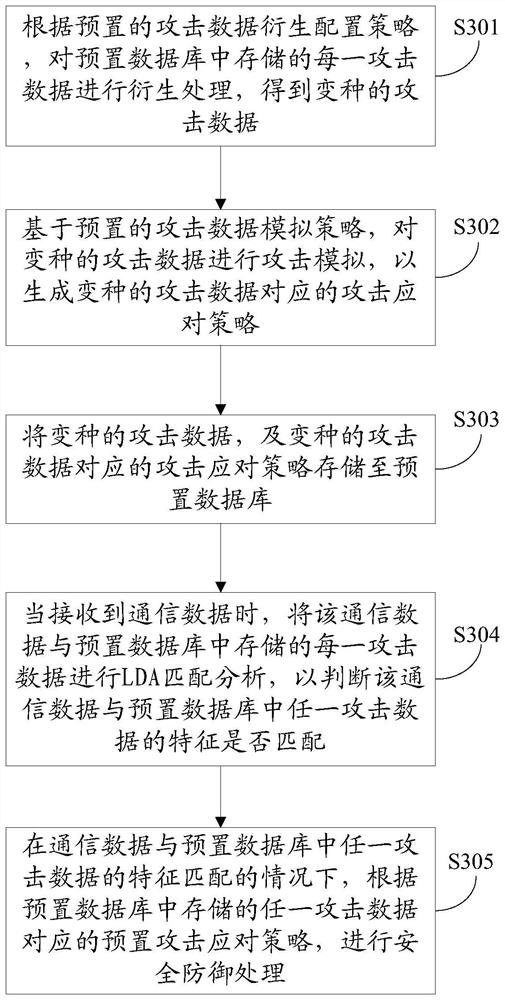
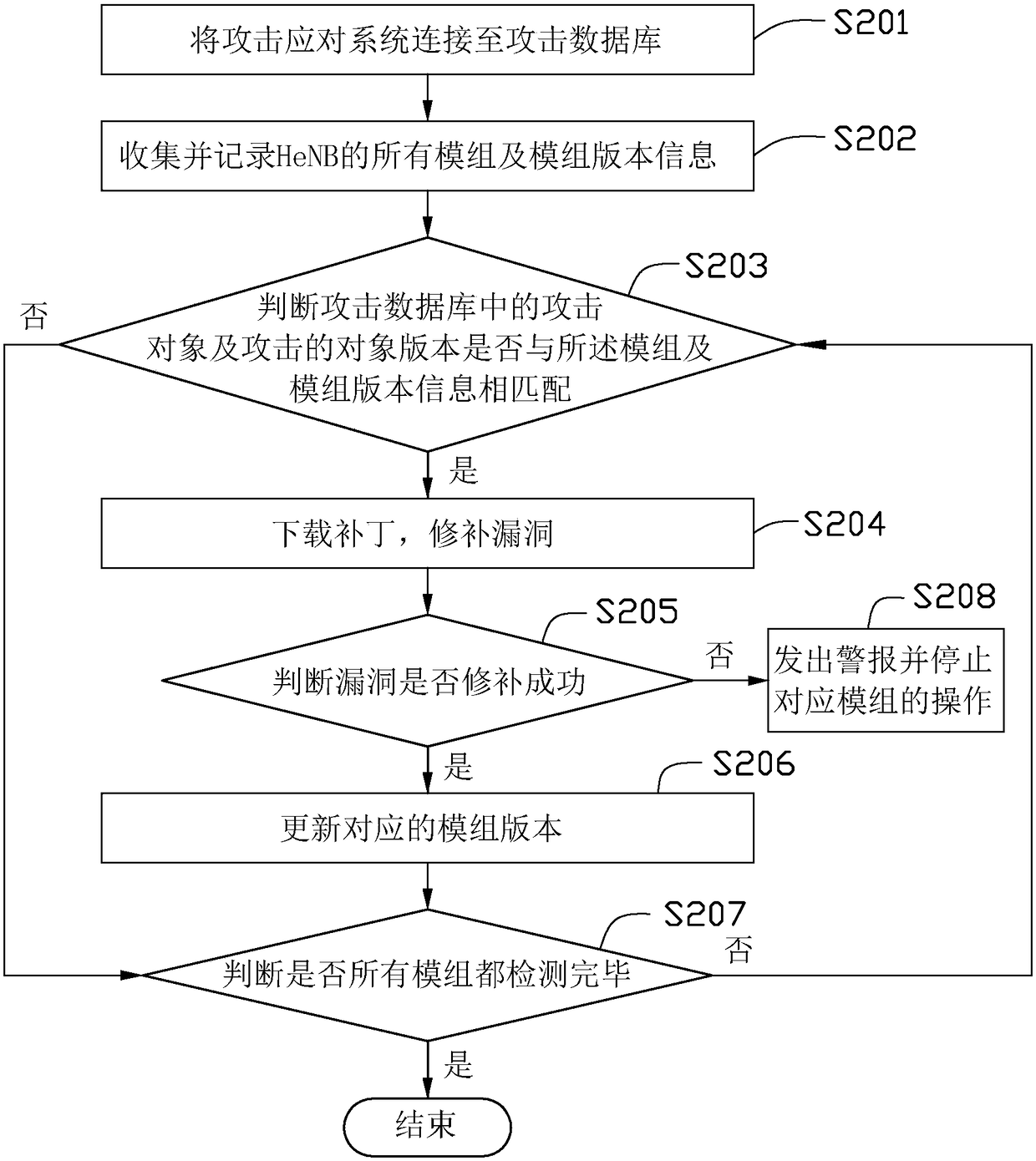
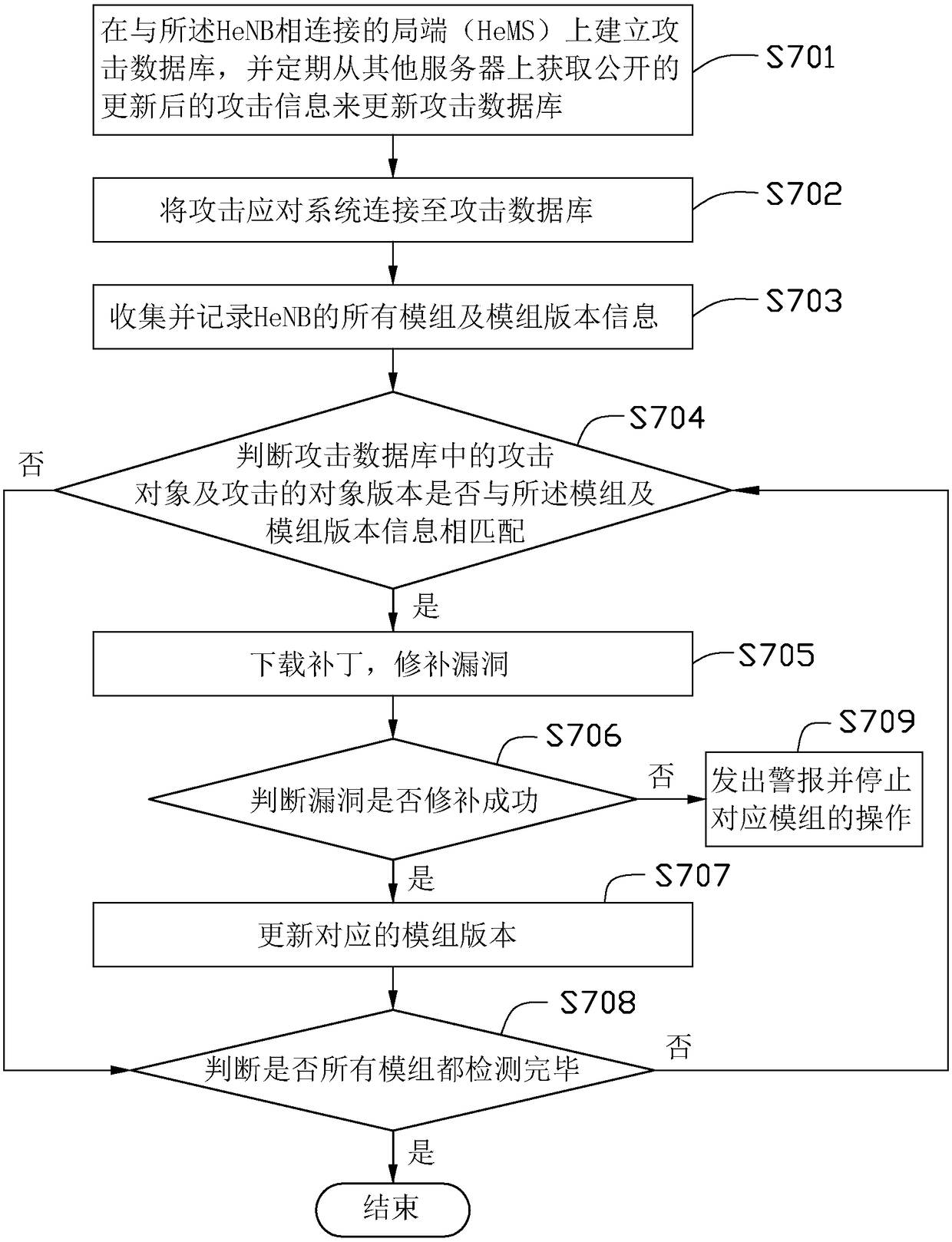
An attack response method, comprising: connecting an attack response system to an attack database; collecting and recording all modules and module version information of a Home evolved Node B (HeNB); judging the attack objects and Whether the target version of the attack matches the module and the module version information; download the patch of the attack target and the target version of the attack that matches the module and the module version information, and patch the vulnerability; and update and patch the vulnerability successfully version of the mod. The invention also discloses an attack response system. Through the above method and system, the potential risk of HeNB being attacked can be found and the risk can be eliminated in time, so as to prevent the HeNB from being attacked.
Owner:NANNING FUGUI PRECISION IND CO LTD
A SQL injection vulnerability detection method and device for rest API
ActiveCN109246113BEfficient detectionImprove detection accuracyTransmissionSyntax errorSQL injection
This application discloses a SQL injection vulnerability detection method and device for a REST API. The method includes: first injecting a detection vector that is easy to trigger SQL syntax errors into the API list to be detected to form a first API attack request, and then using SQL error information to regularize Match the expression to detect whether there is an SQL syntax error in the first API attack response; if no SQL syntax error is detected, according to the API parameter type, inject the vector of two API response content comparison detections, and obtain the second API attack response, After the third API attack response and API normal response, compare the three to detect whether the relationship between the three meets the preset SQL injection vulnerability conditions, and obtain the detection result. It can be seen that this application achieves effective detection of SQL injection vulnerabilities in RESTful APIs by injecting detection vectors that are likely to trigger SQL syntax errors and API response content comparison detection vectors into the RESTful API to be detected, and then detecting the corresponding API responses. .
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
TOCTOU attack response method aiming at TPM trusted computation
InactiveCN101488176BAvoid attackAccurately reflectPlatform integrity maintainanceExtensibilityComputer hardware
The invention relates to a method for responding TOCTOU attack aiming at a TPM credible computer. The components of the method comprise a virtual TPM device program and a privileged domain proxy module which both have more powerful functions. Just as the prior methods, the method of the invention adopts a method of PCR register information updating, but the methods for enabling and executing eventupdate is different from the prior methods so that a TPM command in the following two conditions can correctly indicate the current state of a client virtual domain platform: the first TPM command condition is that a TPM command processing result is not sent out of the virtual TPM device program when the TOCTOU attack is detected, and the second TPM command condition is that the TPM command is not received by the virtual TPM device program when the TOCTOU attack is detected. While considering the security, the invention also takes the system performance into full consideration and ensures theutilization effectiveness and the expandability of system resources by adopting event drive and avoiding process scheduling of an extra user space.
Owner:BEIJING JIAOTONG UNIV
Simulation method, device, storage medium, processor and terminal of model vibration
ActiveCN108295471BImprove realismImprove gaming experienceInput/output for user-computer interactionVideo gamesSimulationComputer engineering
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Audio dynamics processing control system with exponential release response
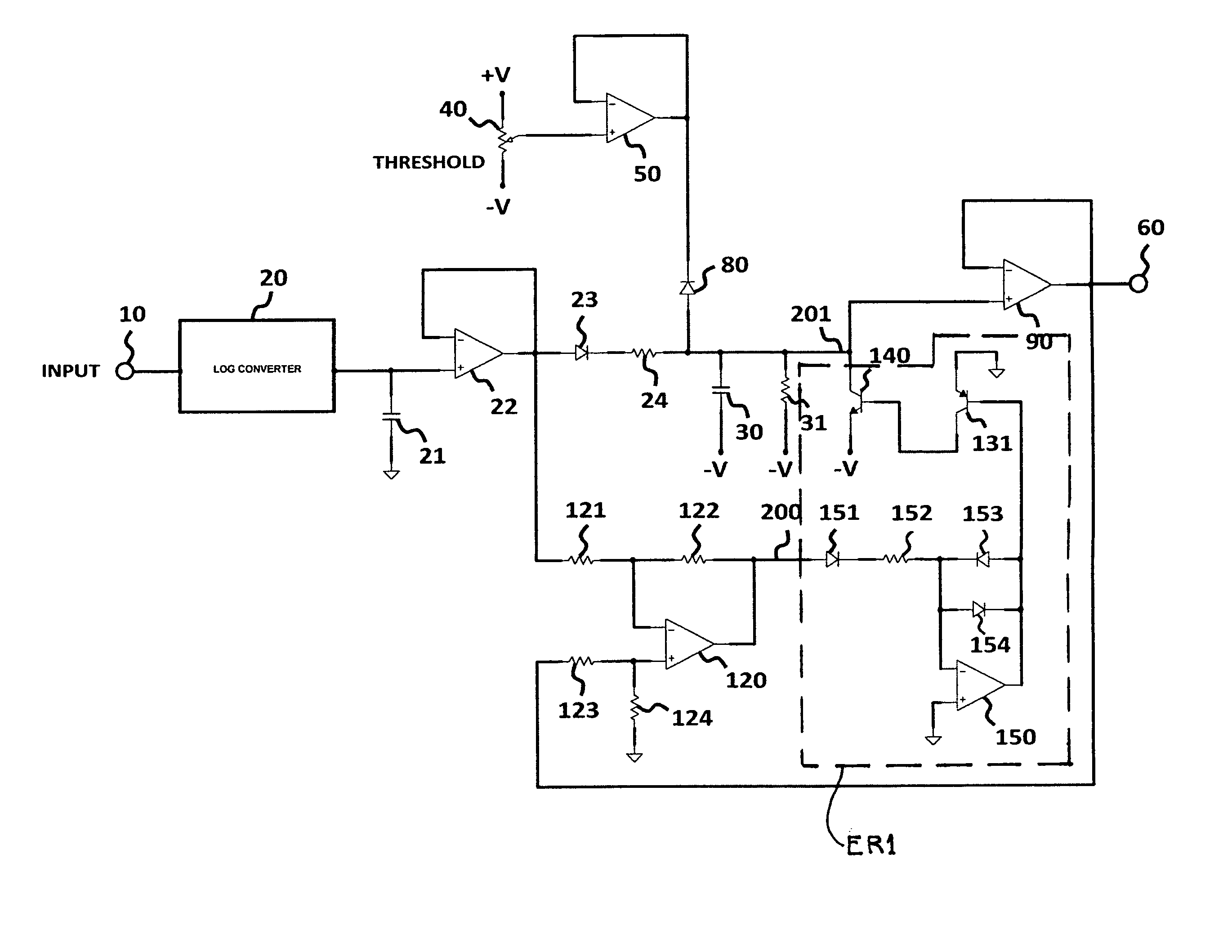
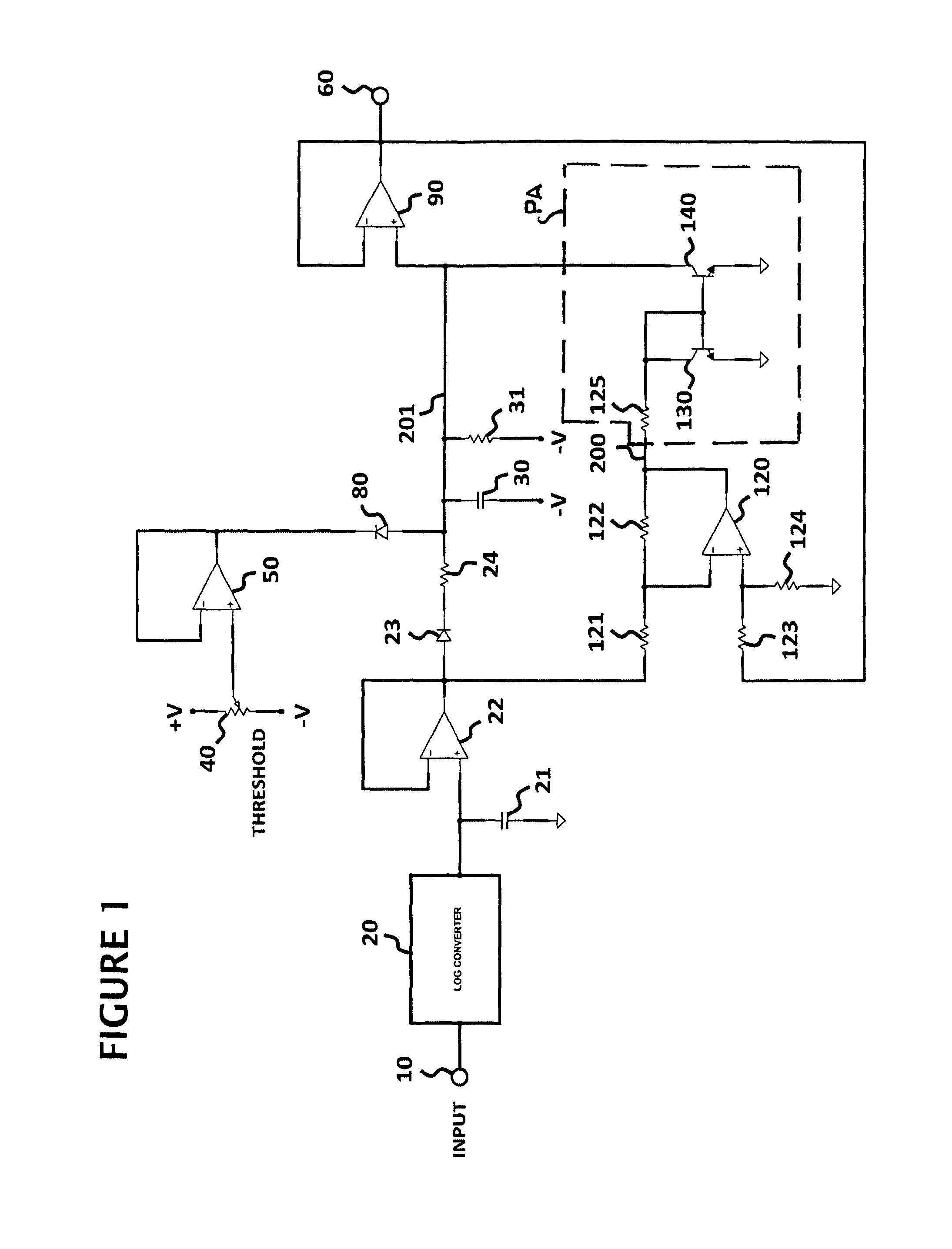
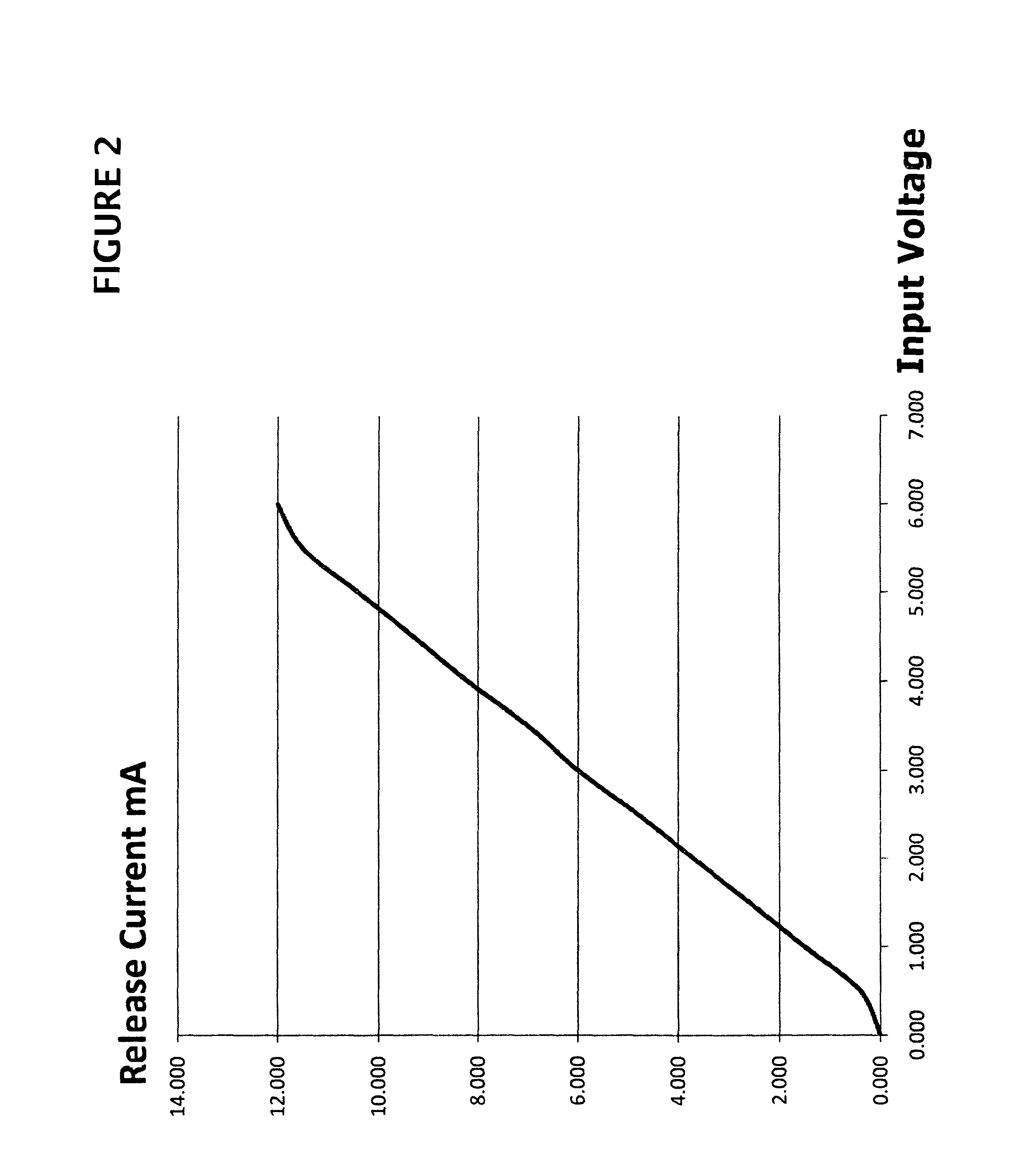
ActiveUS8842852B1Slow changeReduce control signalingGain controlVolume compression/expansion in untuned/low-frequency amplifiersRC time constantControl system
An input audio signal is detected to provide a fast time constant control signal which is clamped for immediate response when the input signal drops below a threshold level and filtered to provide a modified control signal with a slow time constant. As the modified control signal level decreases toward the control signal level, a time constant differential control signal decreases and slows the rate of change of the decreasing modified control signal which, as it nears the control signal level, reverts to a slow response. The resulting control signal has an exponential release response which can be applied to an audio dynamics processor. The time constant differential control signal may also be detected to provide an inverted output when it is significantly less than the modified control signal so as to result in the control signal also having an exponential attack response to be applied to the processor.
Owner:WALLER JR JAMES K
A network attack identification method and system
ActiveCN108683687BImprove operation and maintenance efficiencyImprove recognition efficiencyData switching networksAttackEngineering
The invention discloses a network attack identification method and system. The network attack identification method includes: detecting whether a target host is under a network attack; if the target host is under the network attack, obtaining network data corresponding to the network attack from the network Extract the features to be compared from the data; compare the features to be compared with one or more attack response rules, wherein the attack response rules are formed according to the first response data, and the first response data is used for the attacked host to The response to the successful attack request; if the feature to be compared matches the attack response rule, it is determined that the network attack is successful. The network attack identification method and system provided by the present invention can accurately identify successful network attacks and provide effective network attack information for network managers.
Owner:北京鸿享技术服务有限公司
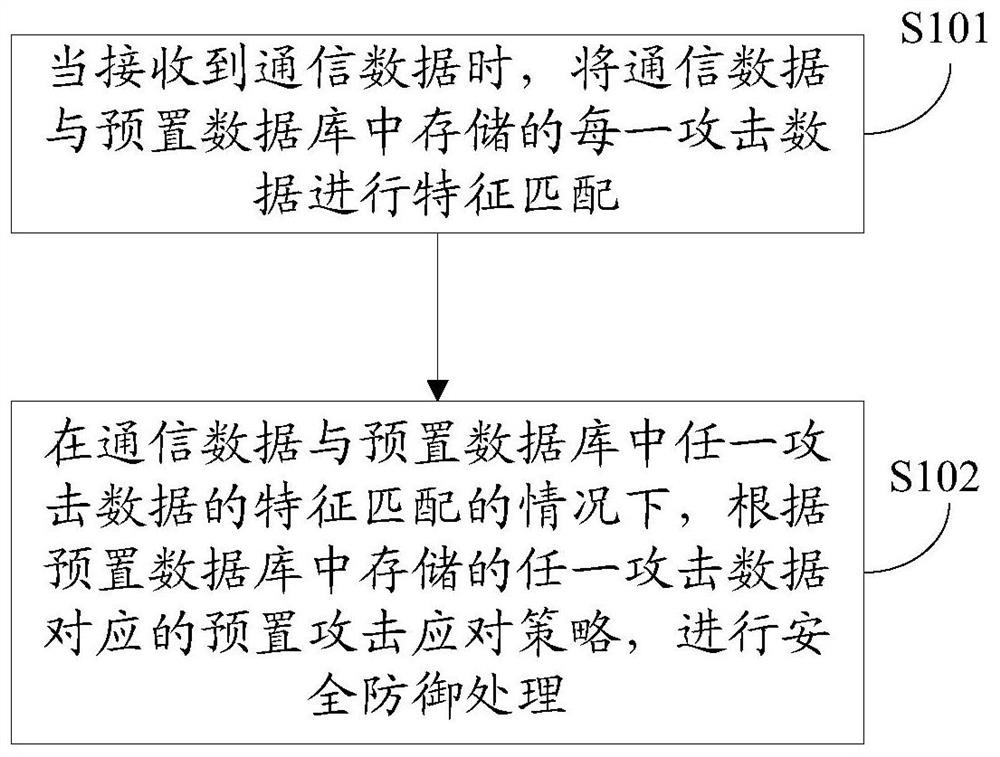
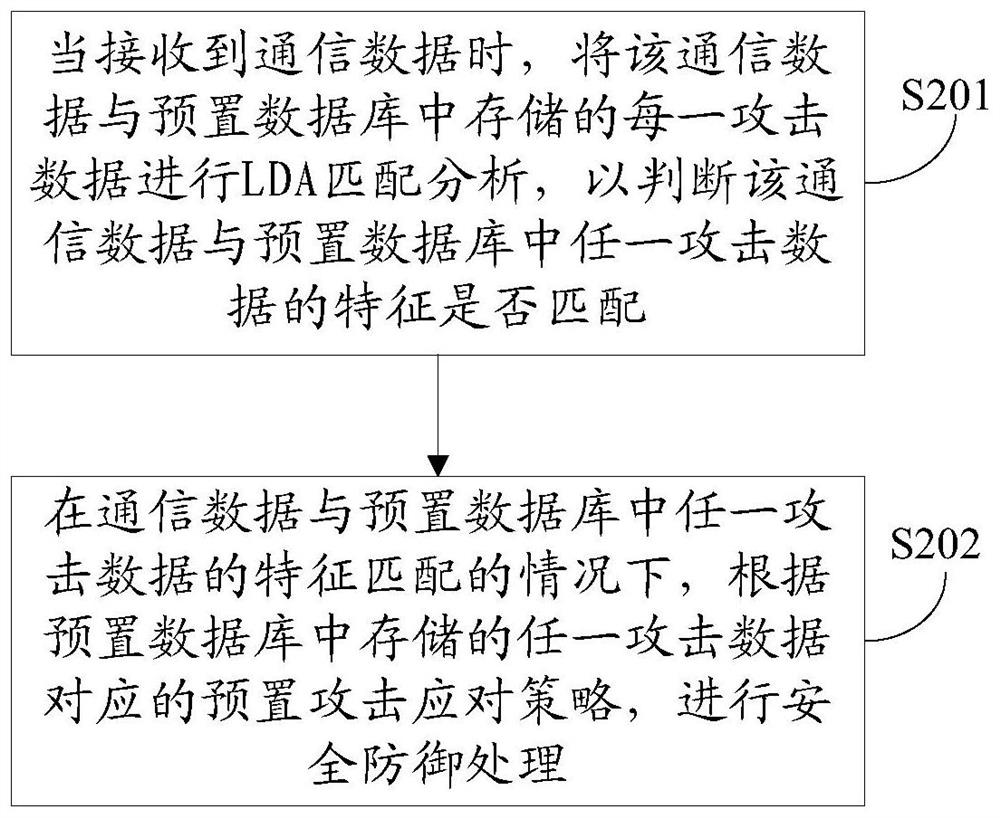
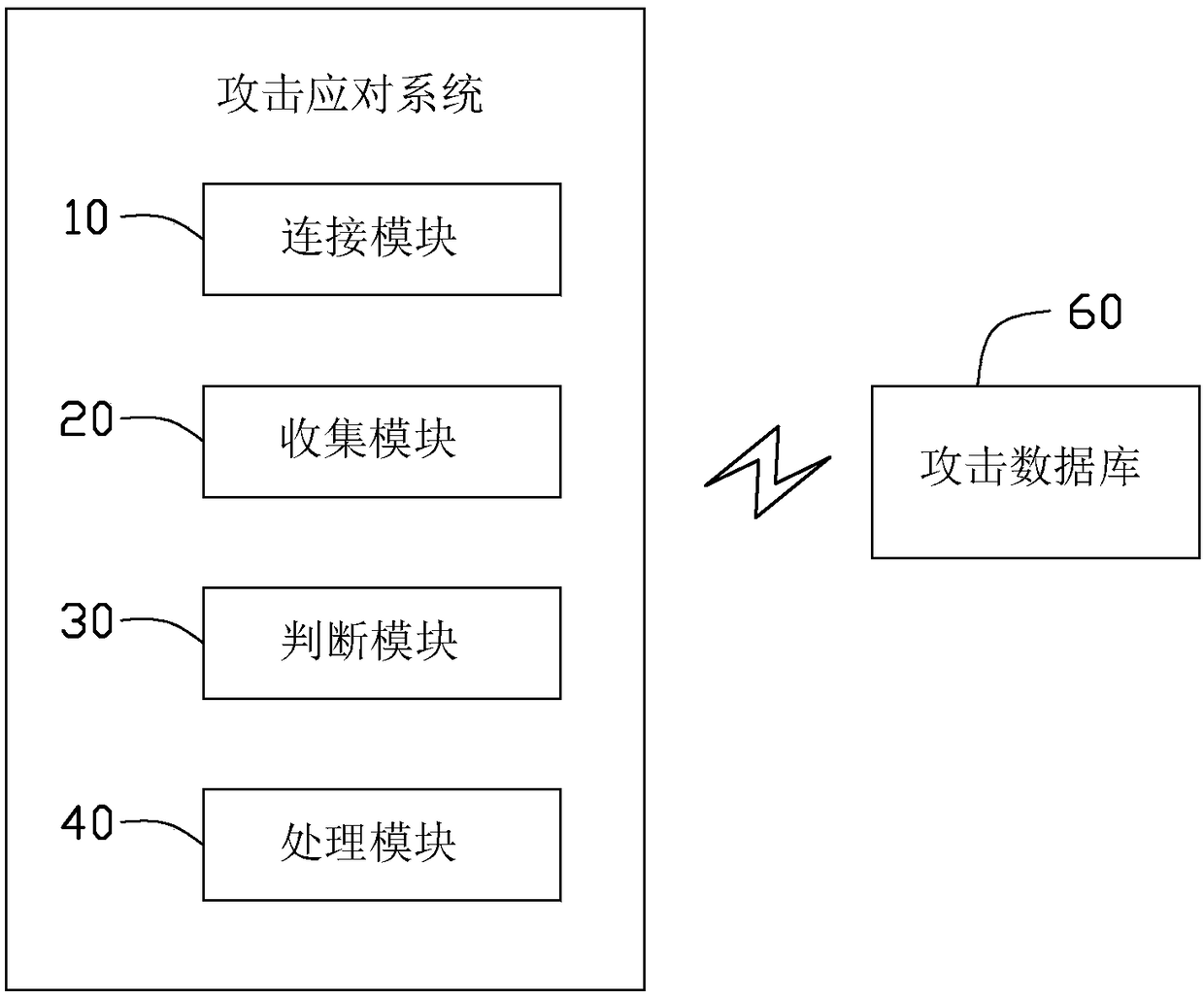
Attack defense method, device, Internet of Things device, and computer-readable storage medium
ActiveCN109246121BImproved ability to respond to attacksImprove self-healing abilityTransmissionComputer networkAttack
The present invention proposes an attack defense method, including: when receiving communication data, performing feature matching on the communication data and each attack data stored in a preset database; In the case of a matching feature, security defense processing is performed according to a preset attack response strategy corresponding to any attack data stored in the preset database. The invention also discloses an attack defense device, an Internet of Things device, and a computer-readable storage medium. By implementing the above scheme, the ability of the Internet of Things device to respond to attacks and the self-healing ability of the Internet of Things device after being attacked are effectively improved.
Owner:QINGDAO HAIER TECH
Attack response method and system
The invention provides an attack response method, which comprises the following steps: connecting an attack response system to an attack database; collecting and recording all modules and module version information of a home evolved node B (HeNB); judging whether attack objects in the attack database and the attacked object versions are matched with the modules and the module version information;downloading patches for the attack object and the attacked object version matched with the modules and the module version information to fix bugs; and updating the module version successful in bug fixing. The invention also discloses the attack response system. The method and system can find potential attack risks of the HeNB and can eliminate the risk timely, and prevent the HeNB from being attacked.
Owner:NANNING FUGUI PRECISION IND CO LTD
Active defense DDOS system based on SDWAN
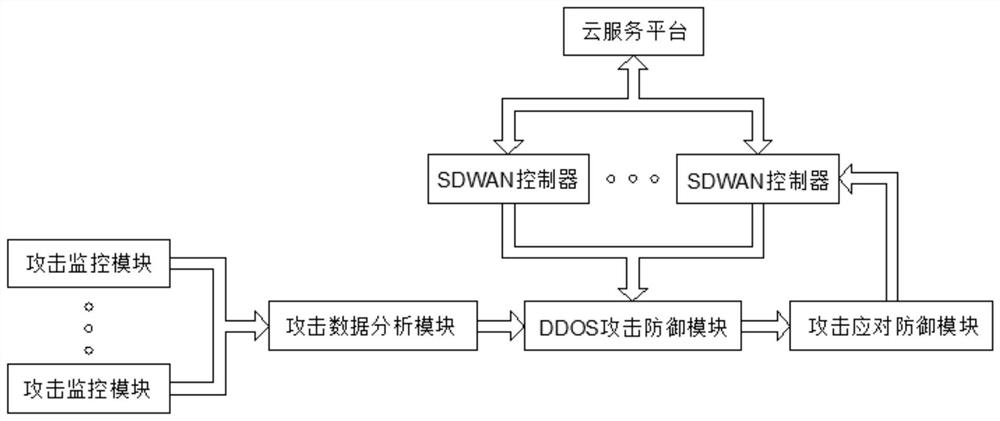
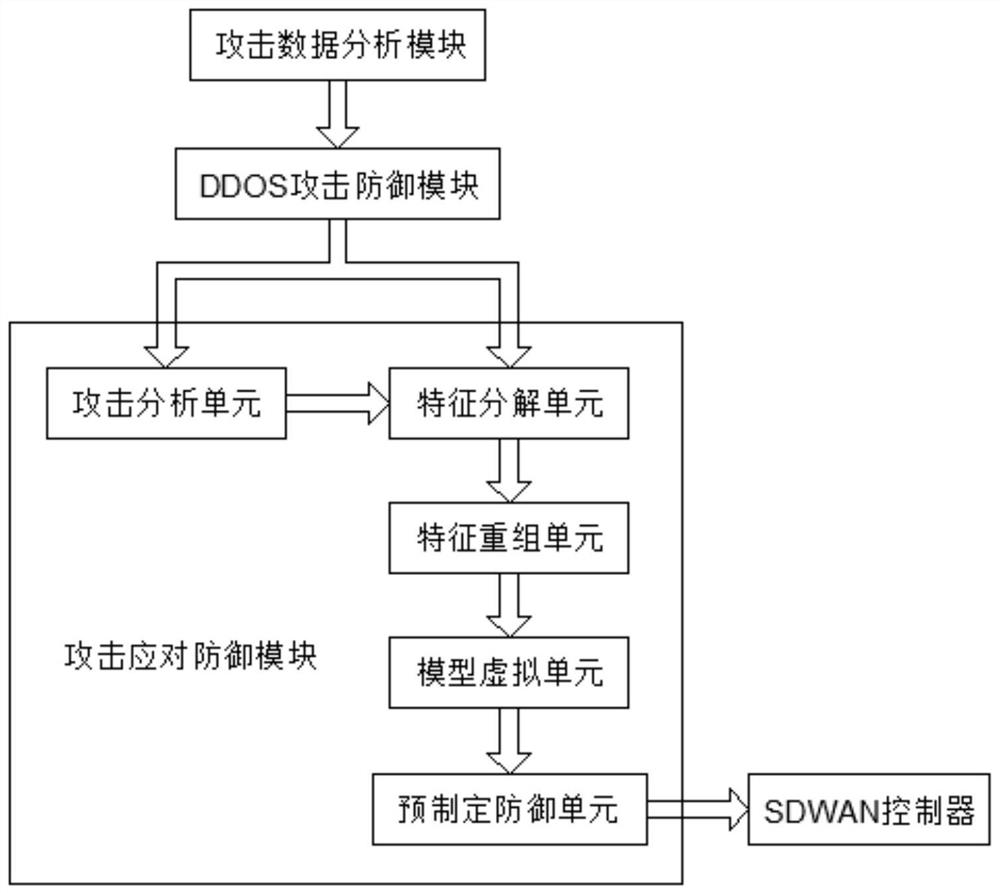
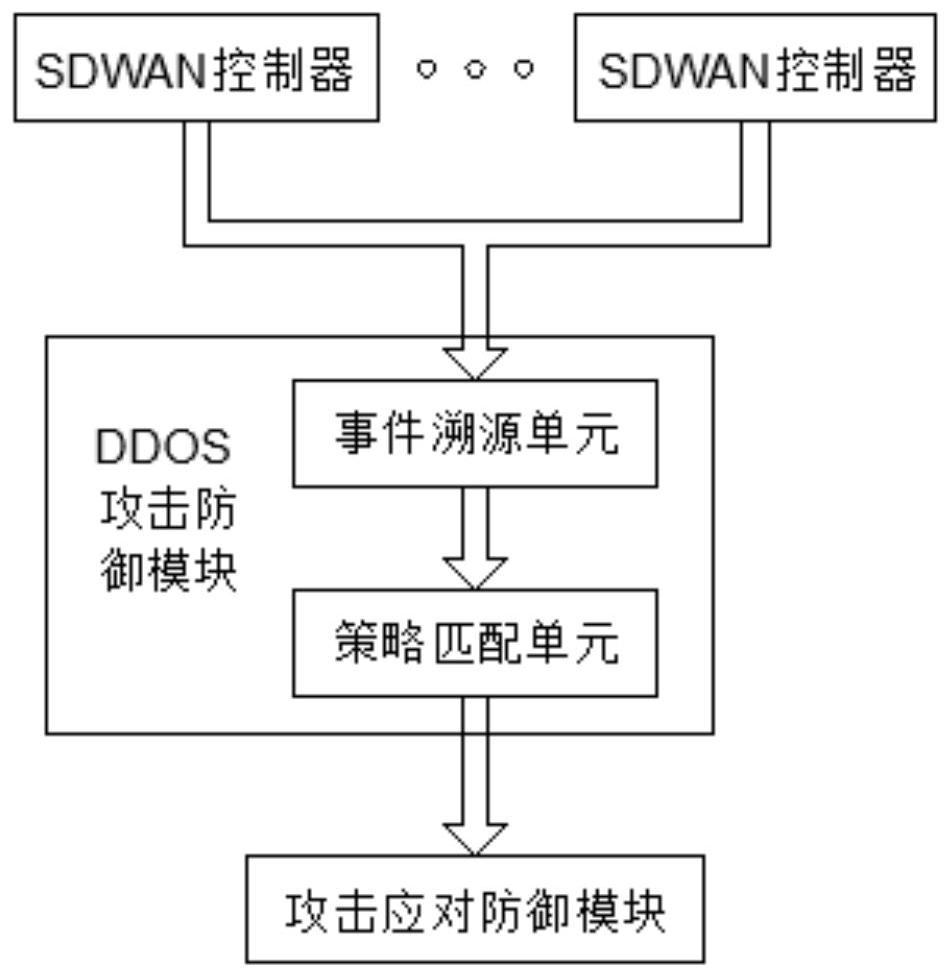
ActiveCN113395288ADefense is fast and accurateImprove response speedTransmissionFeature extractionAttack
The invention discloses an active defense DDOS system based on an SDWAN. The system comprises a cloud service platform; an SDWAN controller; an attack monitoring module is used for collecting attack data in a public network; an attack data analysis module is used for extracting attack features in the attack data; a DDOS attack defense module interacts attack characteristics through a plurality of SDWAN controllers and matches corresponding defense strategies; an attack response defense module is used for pre-formulating a defense strategy; when the attack monitoring module detects that a user is attacked, attack data is sent to an attack data analysis module for attack feature extraction, and a corresponding defense strategy is matched according to attack features in the cloud service platform through data interaction of the multiple SDWAN controllers so as to defend a previous attack event; Meanwhile, a pre-formulated defense strategy corresponding to a virtual feature approximate to the attack feature in the attack response defense module is called for active defense. According to the active defense DDOS system based on the SDWAN, the defense efficiency is relatively high when a DDOS attack event occurs.
Owner:浙江德迅网络安全技术有限公司
A Heterogeneous Iris Authentication Method with Stealing Attack Mechanism
ActiveCN110046588BImprove fault toleranceImprove robustnessCharacter and pattern recognitionDigital data authenticationImaging processingAuthentication system
The invention discloses a heterogeneous iris authentication method with a stealing attack coping mechanism. The method is as follows: step 1, constructing a heterogeneous iris multi-category authentication system improved based on a convolutional neural network; step 2, constructing a stealing attack Coping mechanism; step 3, start formal authentication; step 4, the image enters the fully connected layer in turn; step 5, obtain the similarity probability with the iris belonging to a single classifier; step 6, obtain the accurate similarity probability; step 7, pass the coding layer The mapping relationship, output the iris category to which the test iris belongs. Beneficial effects: The traditional convolutional neural network is transformed, and the image processing layer and the dilution layer are added, which helps to enlarge the difference between different types of irises in multi-category authentication and improves the accuracy of authentication.
Owner:JILIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com