DDoS attack detection method based on network traffic application layer
A network traffic and attack detection technology, applied in the Internet field, can solve problems such as the inability of servers to provide normal services, and achieve the effect of facilitating popularization and use, reducing false positive and false negative rates, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] A specific embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings, but it should be understood that the protection scope of the present invention is not limited by the specific embodiment.
[0019] There are some subtle differences between DDoS and FC, such as access intent, request rate of clients, distribution of source IP addresses, etc. The difference between DDoS and FC is shown in Table 1 below:
[0020]
[0021] Table 1 Comparison of DDoS attack and FC features
[0022] The embodiment of this patent application mainly selects three parameters: the rate of change of traffic, the rate of change of new source IP addresses, and the request allocation rate of source IP addresses to analyze network traffic, thereby distinguishing DDoS attack traffic from FC traffic.
[0023] Application layer DDoS attack detection model
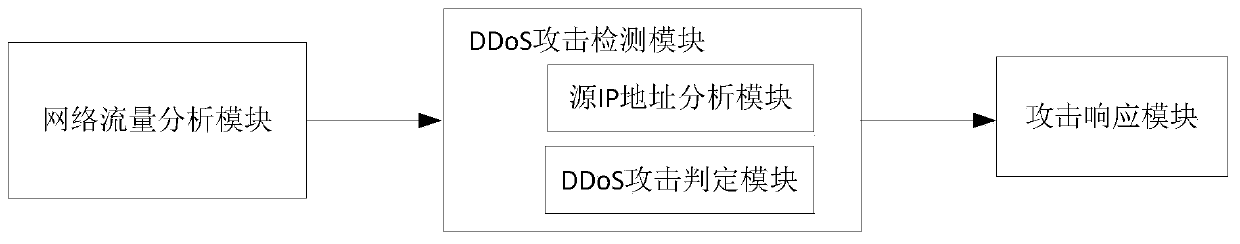
[0024] Application layer DDoS attack detection model such as figure 1 Shown: When ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com