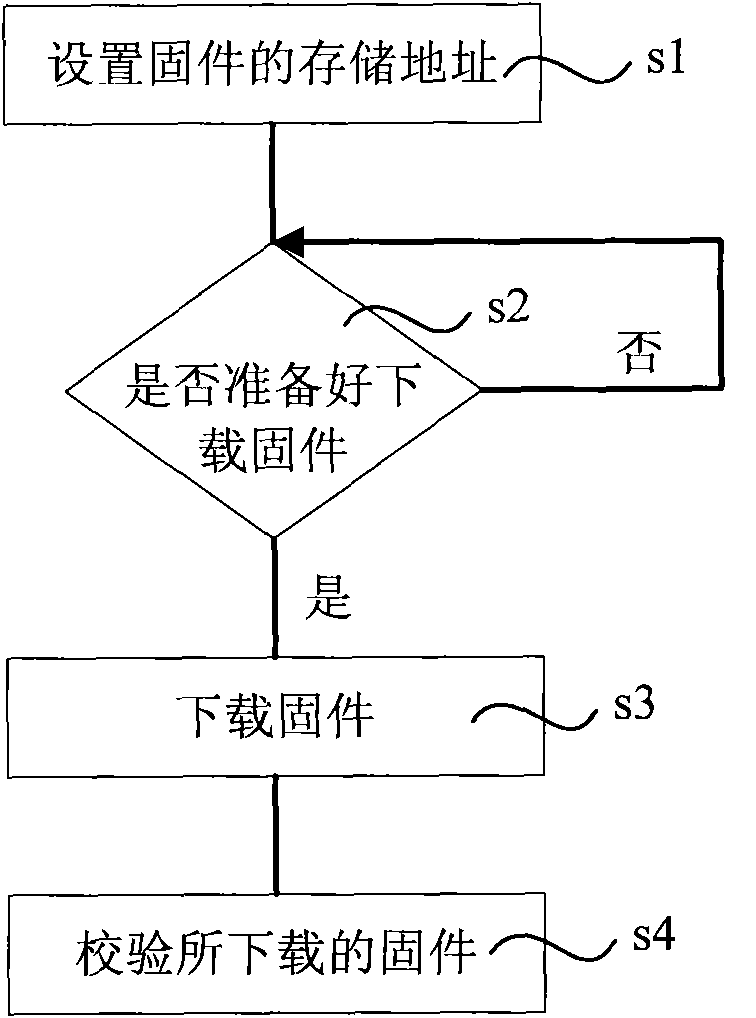
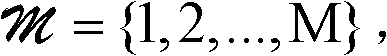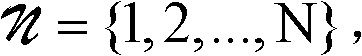Patents
Literature
49 results about "Application layer DDoS attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
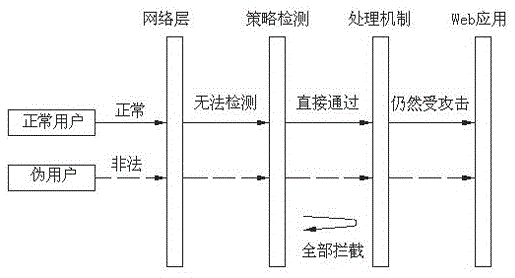
An application layer DDoS attack is a form of denial-of-service where attackers target the application layer of the OSI model. The attack disables specific functions or features as opposed to an entire network and often used against financial institutions to distract IT and security personnel from security breaches. As of 2013, application layer DDoS attacks represent 20% of all DDoS attacks.
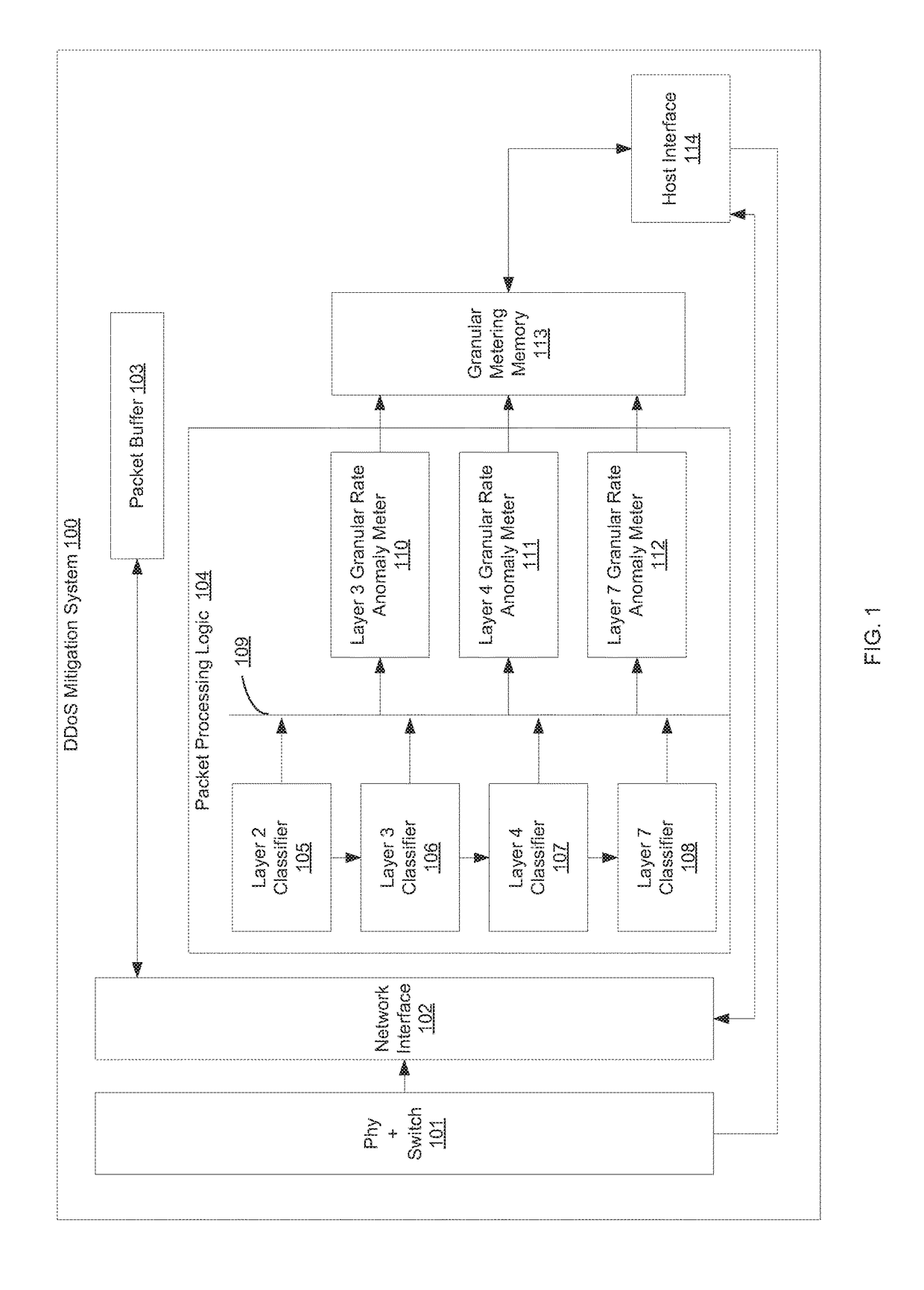
Apparatus for detecting and filtering application layer ddos attack of web service
InactiveUS20110099622A1Minimum arithmetic complexityMemory loss protectionError detection/correctionData packIp address
Owner:KOREA INTERNET & SECURITY AGENCY
Application layer distributed denial of service (DDoS) attack detection method and defensive system aimed at website
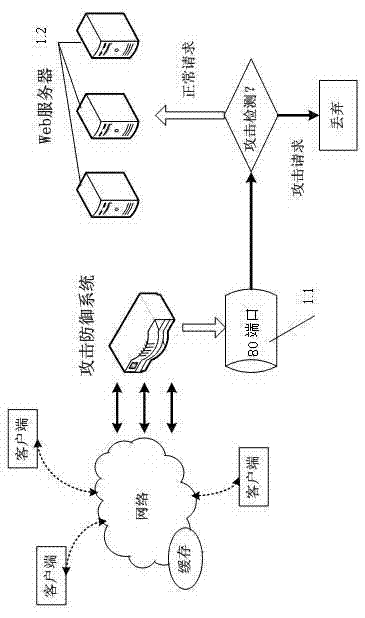
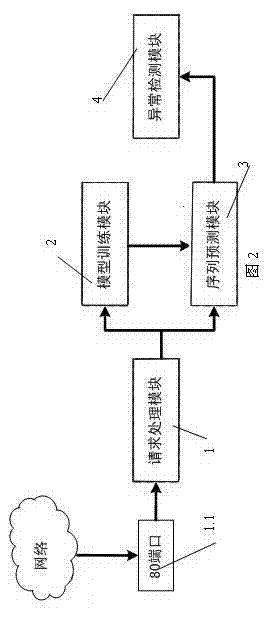
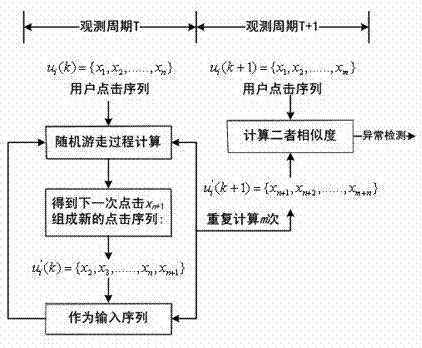
The invention relates to an application layer distributed denial of service (DDoS) attack detection method and defensive system and relates to network safety, in particular to application layer DDoS attack detection and defend. The invention provides a detection method and the defensive system based on user click sequence forecasting. Firstly, a page table uniform resource locator (URL) of a website is extracted, a clustering algorithm is utilized to conduct clustering, page table classification Vj and a user click sequence of the website are obtained, then the user click sequence is utilized to construct a random wandering image, a next observation period click sequence of a user is calculated through a process of random wandering, at last, similarity of a predict sequence and a click sequence is calculated, and abnormity of the user click sequence is judged through training threshold. The application layer DDoS attack detection method and defensive system can effectively detect attacking of an application layer, particularly stimulate an attack request of normal user behavior, and can be widely applied to safe defend of a data center website server.
Owner:深圳占领信息技术有限公司
Apparatus for detecting and filtering application layer DDoS attack of web service
InactiveUS8438639B2Minimum arithmetic complexityMemory loss protectionError detection/correctionWeb serviceIp address
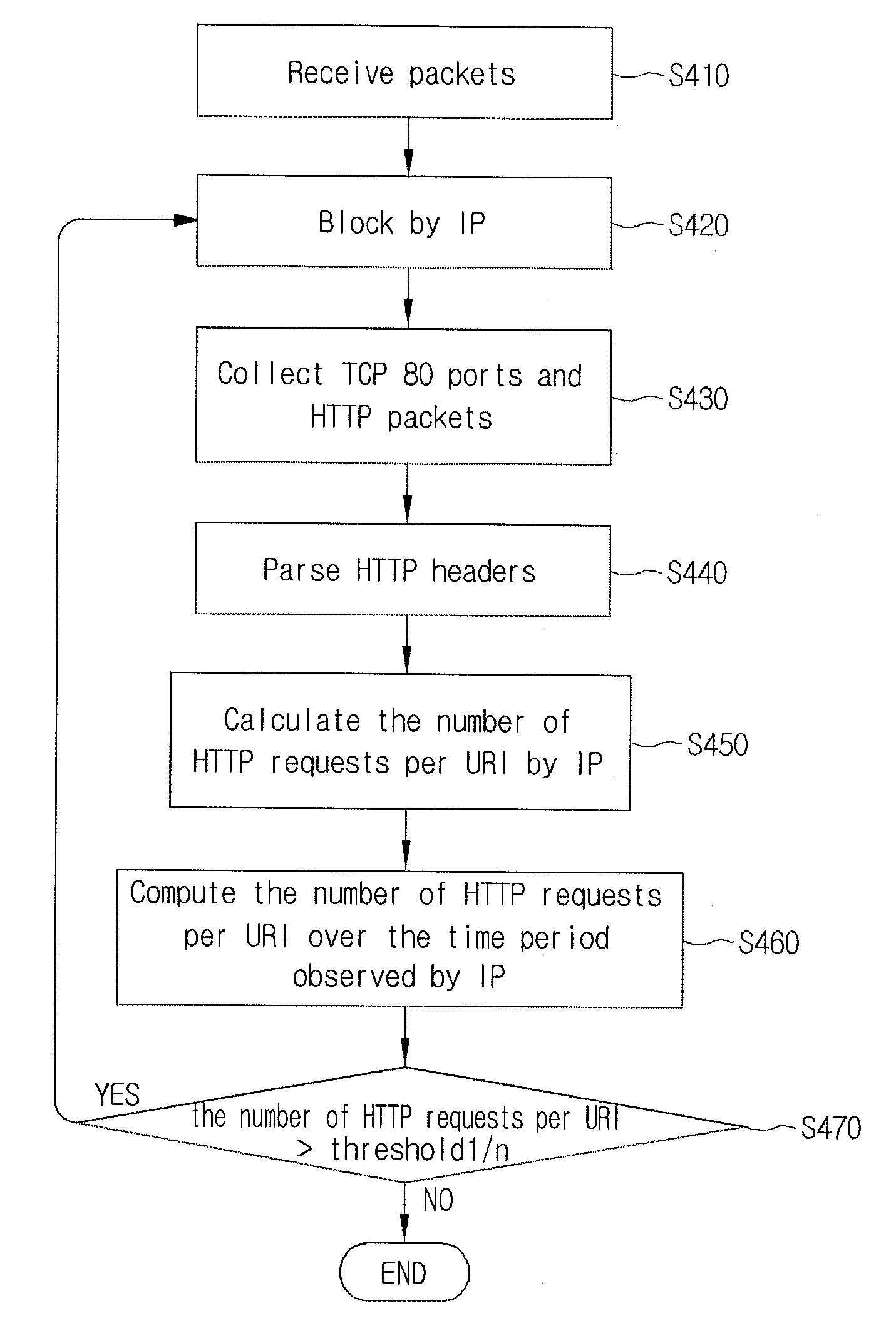
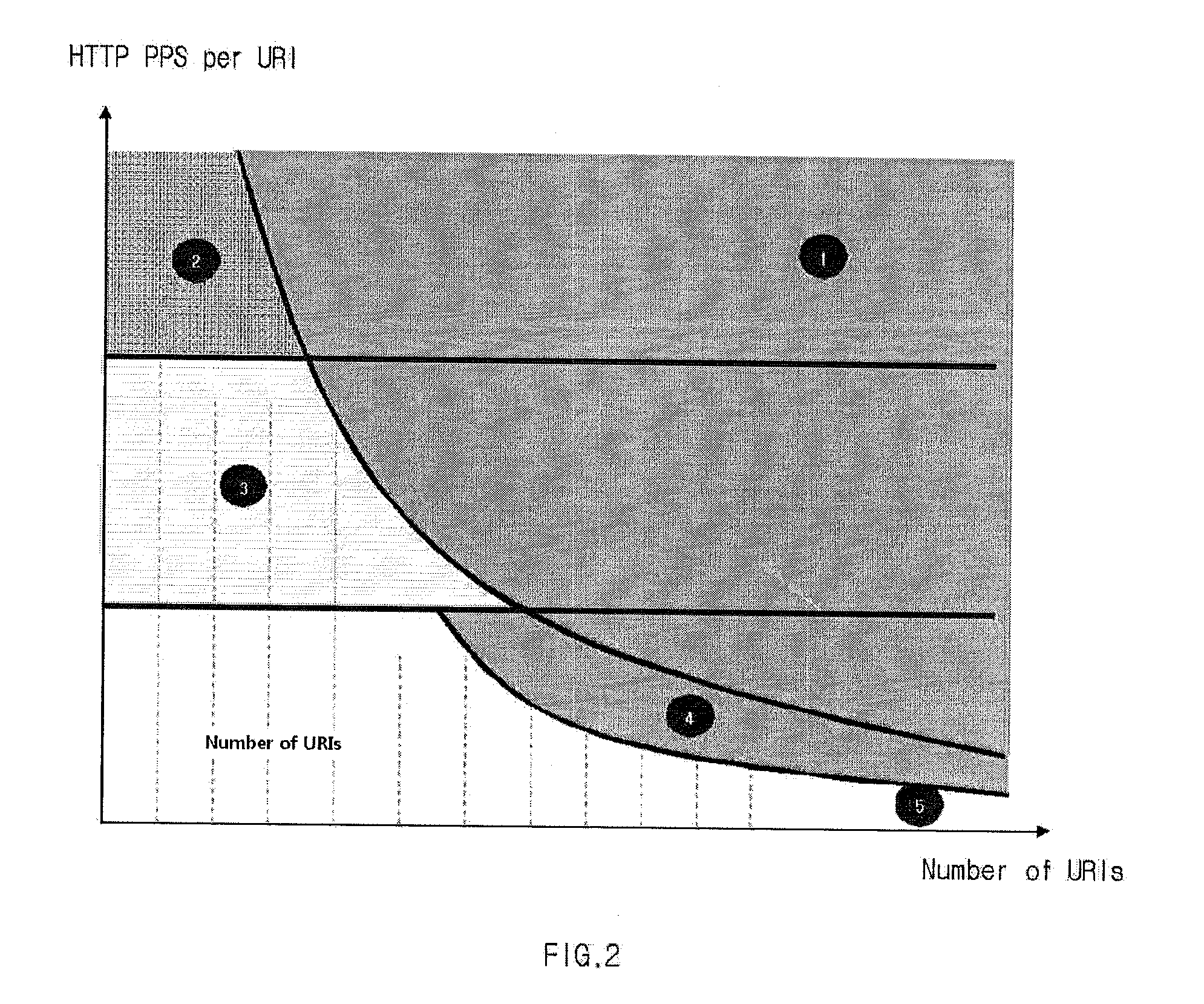
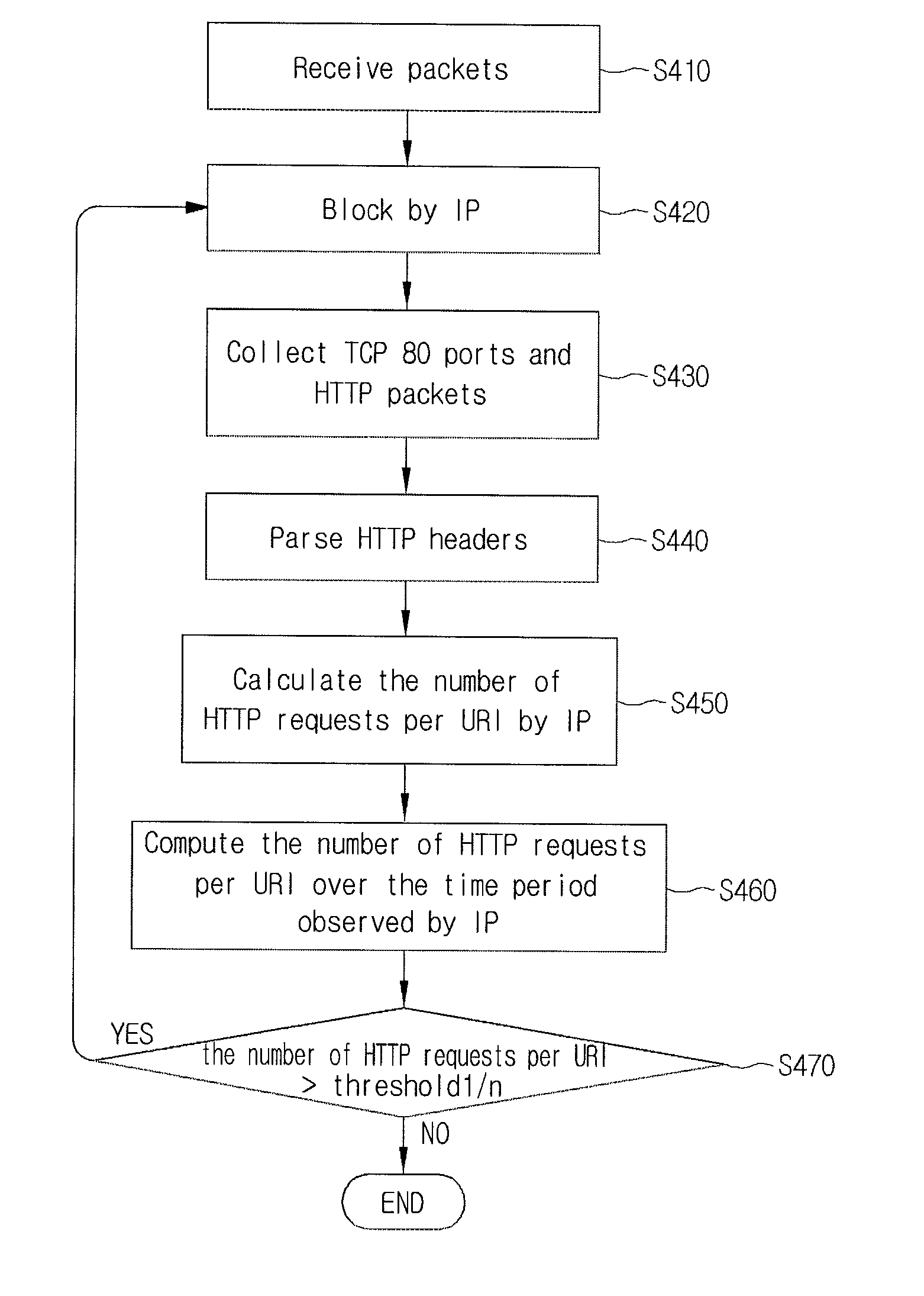
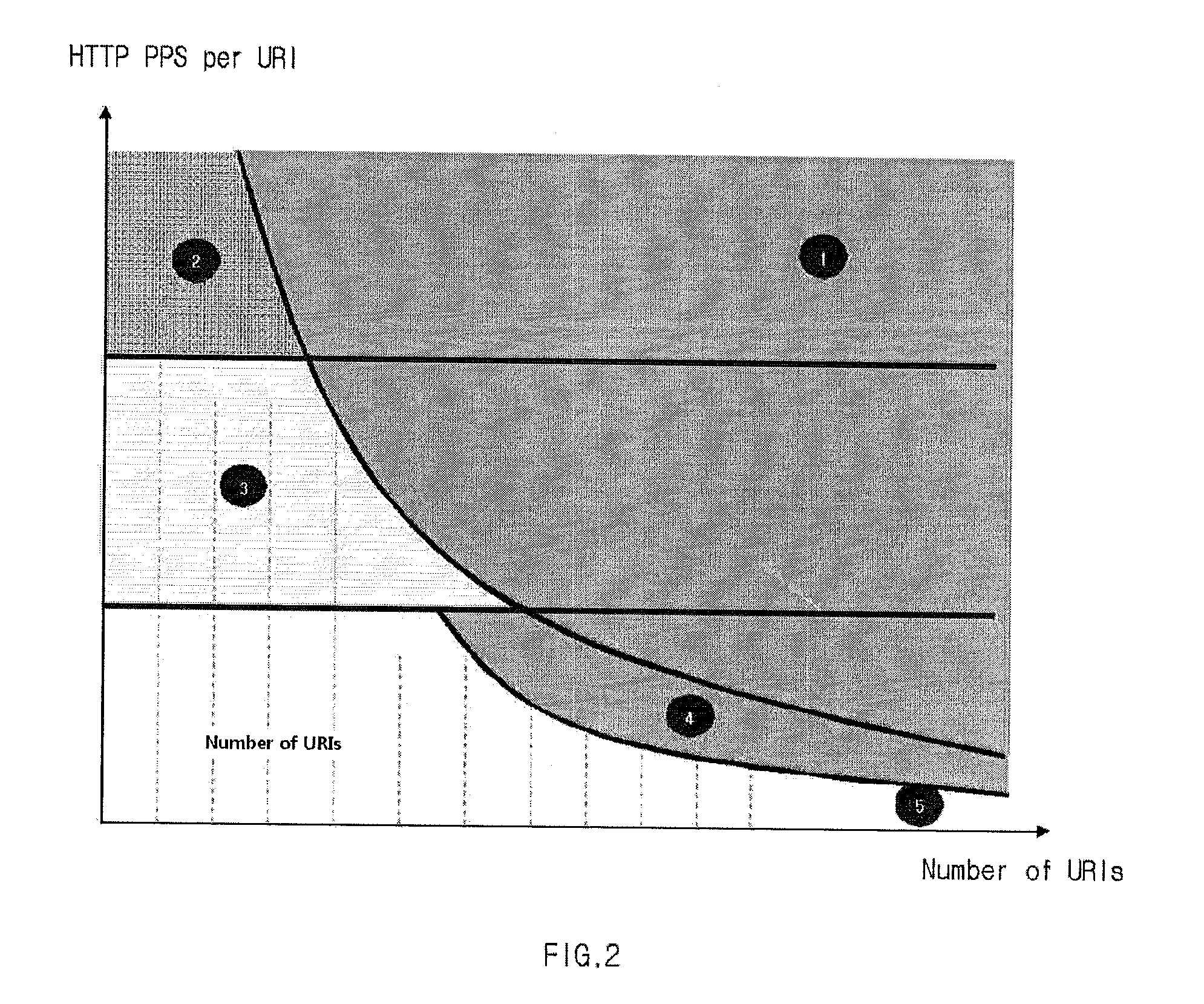
Disclosed is a DDoS attack detection and response apparatus. The DDoS attack detection and response apparatus comprises: a receiver unit receiving HTTP requests from a client terminal which is characterized as an IP address; a data measuring unit computing the number of HTTP requests by IP and the number of URIs per HTTP over a certain time period; a DDoS discrimination unit comparing the number of HTTPs per URI with a threshold value and defining an access of the client terminal having the IP address as a DDoS attack when the number of HTTPs per URI is larger than the threshold value; and a blocking unit blocking packets from the IP address when the DDoS discrimination unit detects a DDoS attack.
Owner:KOREA INTERNET & SECURITY AGENCY
Multiple detector methods and systems for defeating low and slow application ddos attacks
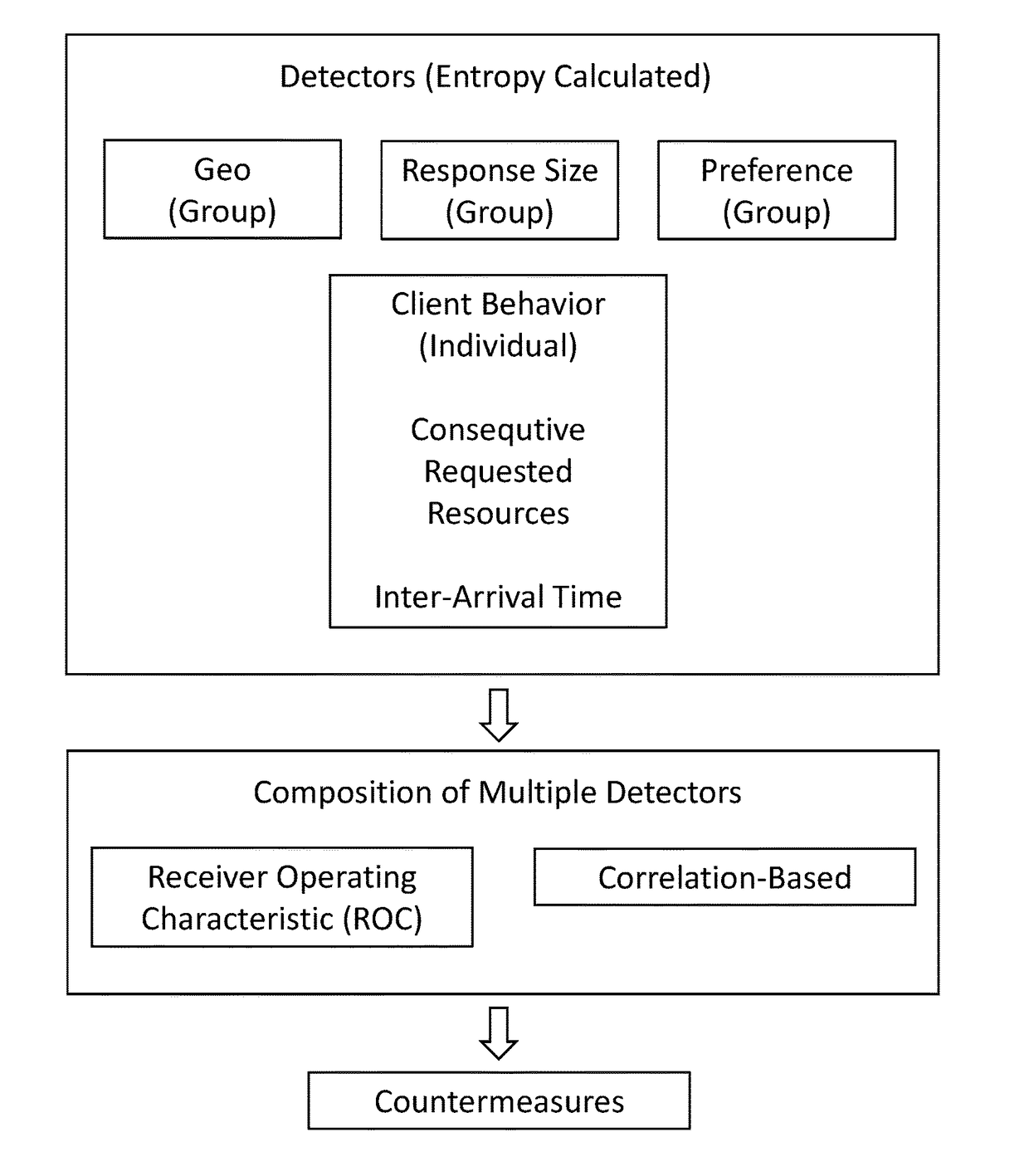
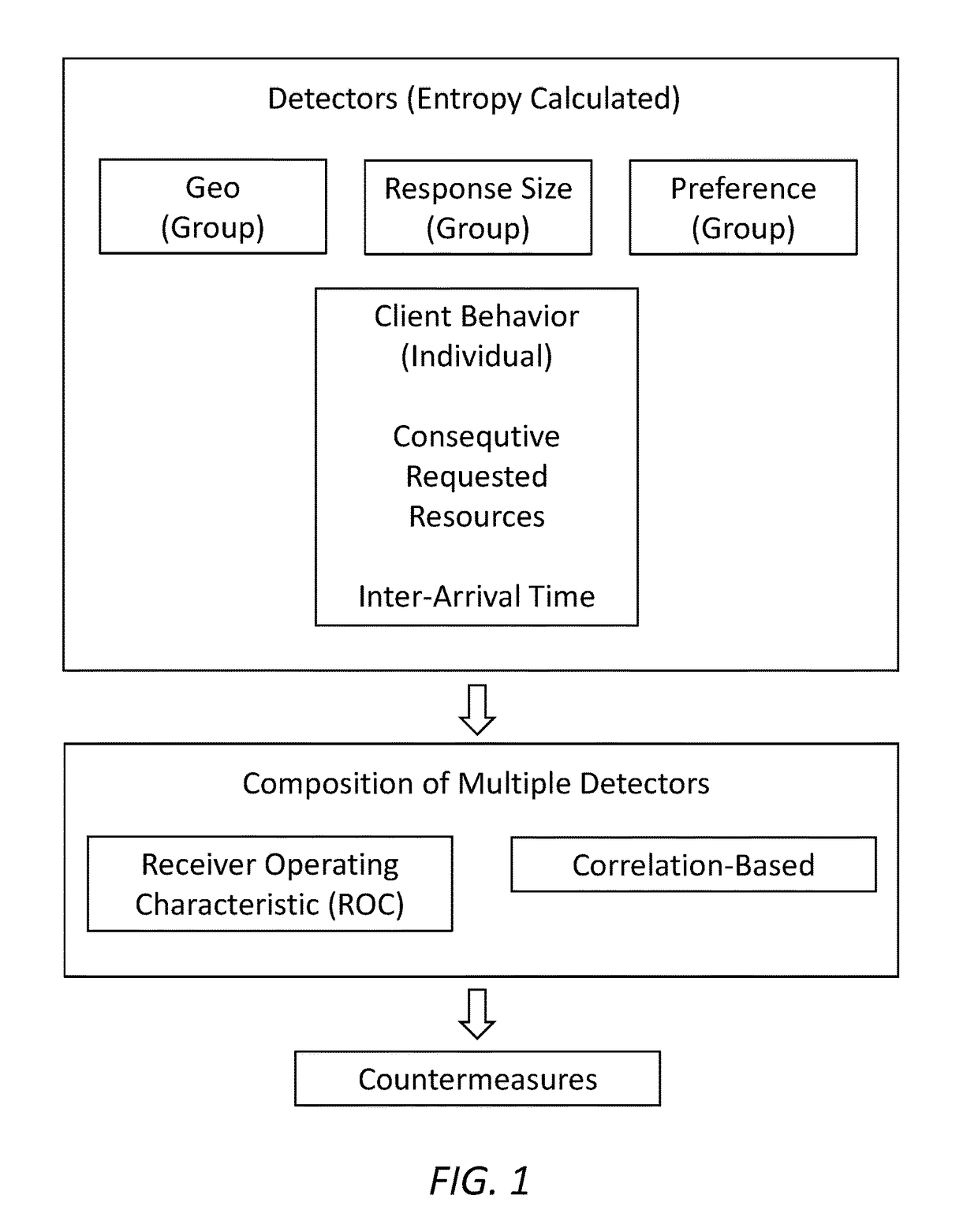
ActiveUS20170324757A1Reduce attackMitigate DDoS attackTransmissionCountermeasureReceiver operating characteristic
Methods and systems for detecting and defeating a low and slow application DDoS attack, comprising: computing the Entropy of a plurality of detectors, at least in part selected from a group Geo detector, a group response size detector, a group preference detector, and an individual client behavior detector, wherein the plurality of detectors each describe a feature of traffic affected by the DDoS attack; composing the plurality of detectors on one or more of a Receiver Operating Characteristic (ROC) curve basis and a correlation basis; and implementing a countermeasure to mitigate the DDoS attack.
Owner:JUNIVERSITI OF NORT KAROLINA EHT SHARLOTT
Data transmission method for wireless cooperative relay system
InactiveCN101969668AImprove erasure capabilityImprove throughputError preventionNetwork traffic/resource managementFountain codeSignal on
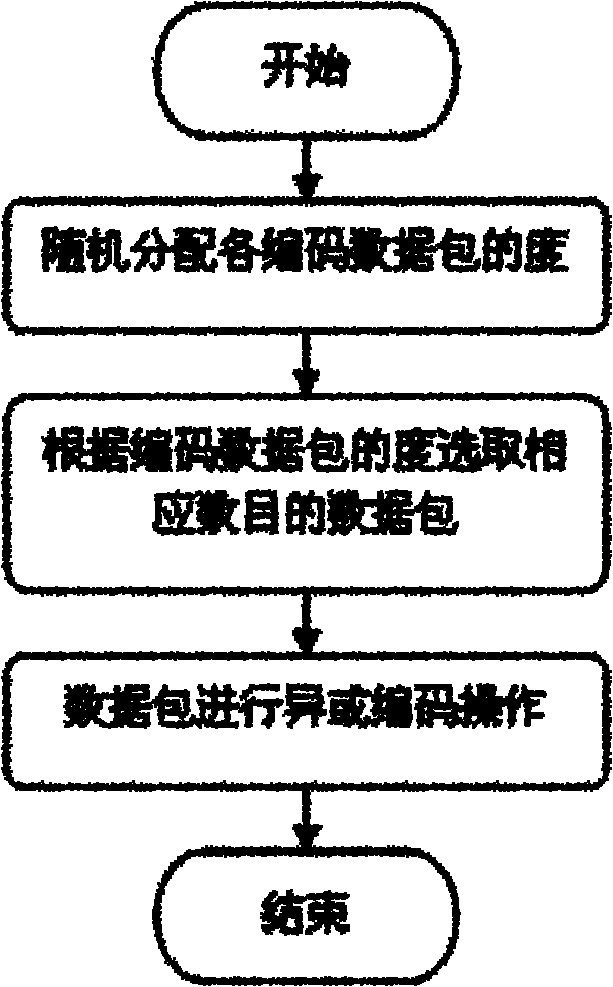
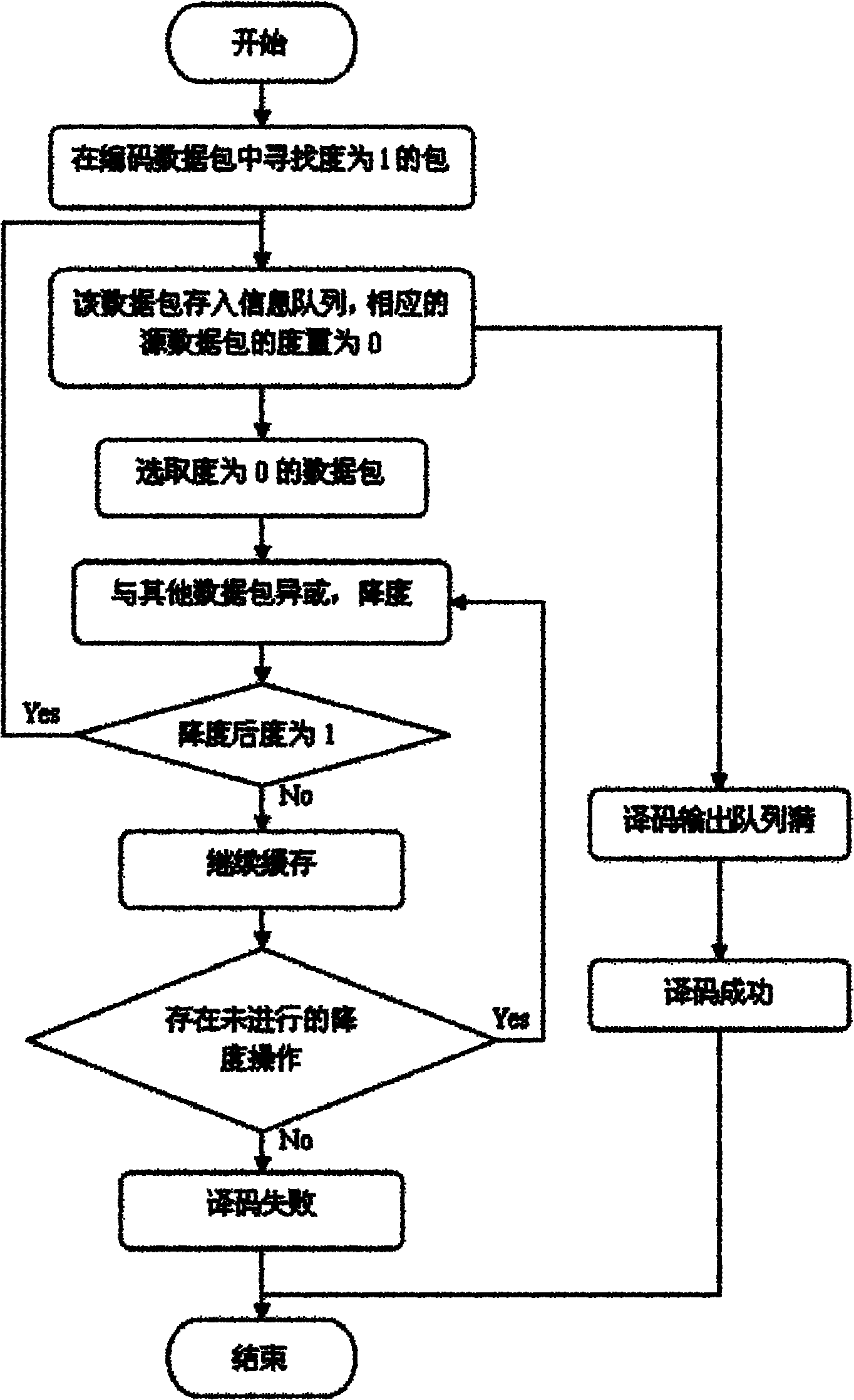
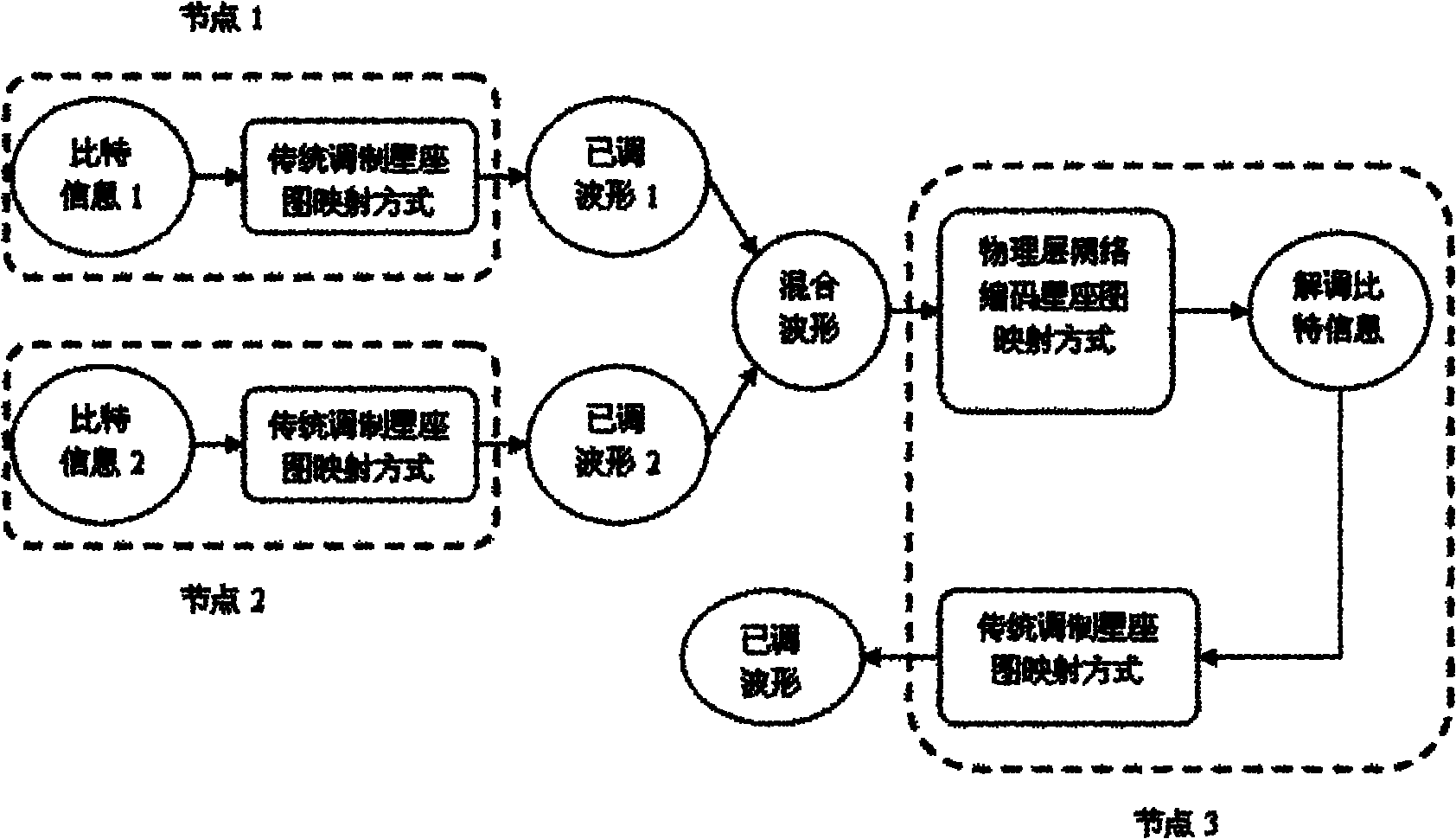
The invention belongs to the technical field of computer network communication, and relates to a data transmission method for a wireless cooperative relay system. The method comprises the following steps of: performing digital fountain code coding processing on application layer data of an information source node to acquire an application layer coding data packet; encapsulating head of each layer of a protocol stack of the acquired data packet, modulating and transmitting the data packet to a wireless channel for transmission; receiving a stacked electromagnetic wave signal on the wireless channel by a relay node, demodulating according to the mapping relationship of network coding in a physical layer, and demodulating and transmitting by a relay node; and detracting information per se from received information by a target node to acquire information of the opposite side, and decoding in the application layer by the digital fountain code decoding algorithm. The method can improve the erasing capability, throughput, packet delivery fraction and interference performance of the system.
Owner:TIANJIN UNIV
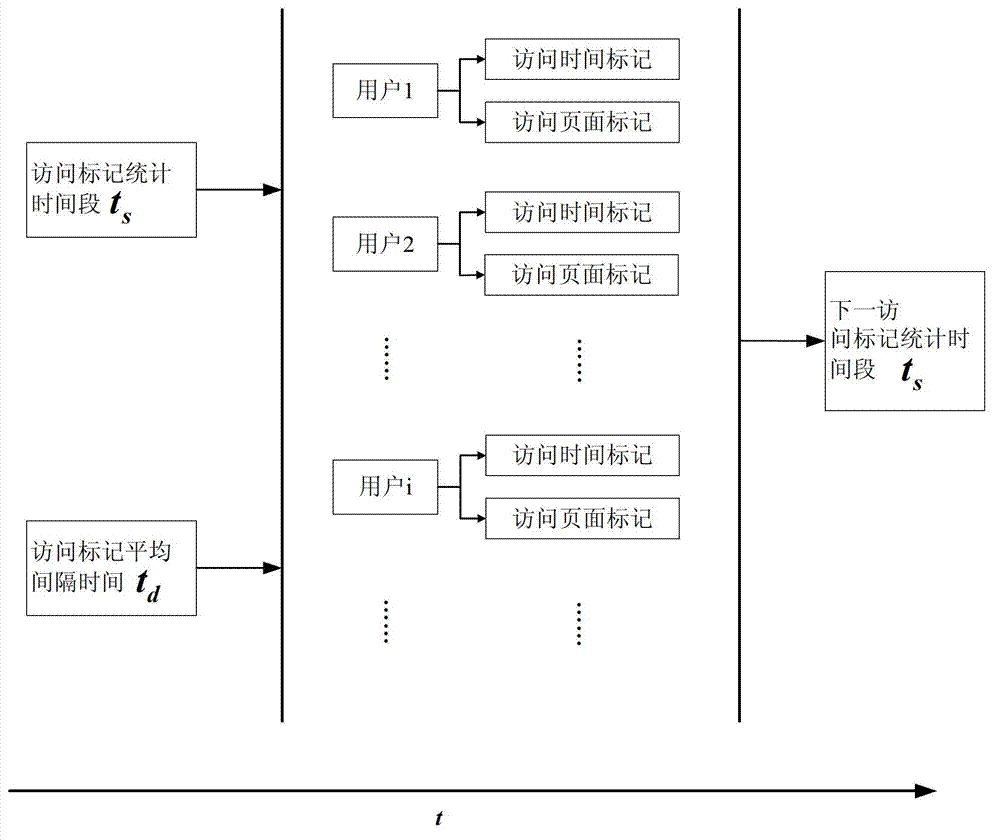
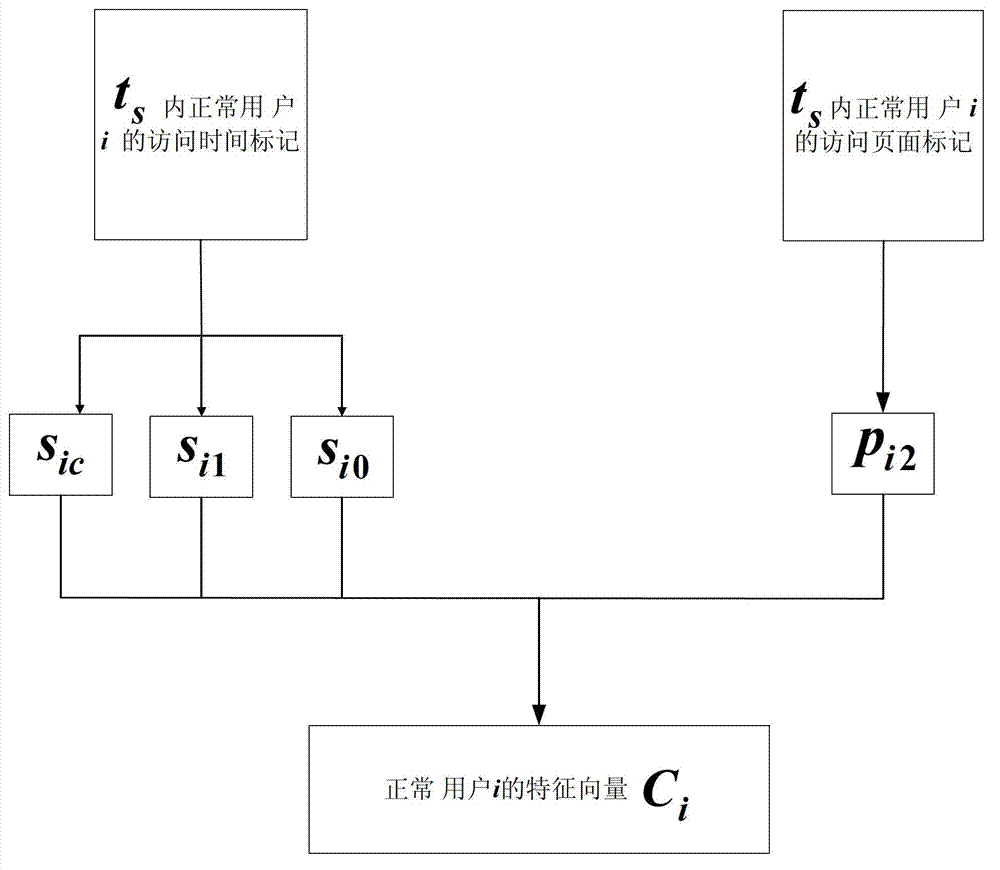
Method for detecting and filtering application layer DDoS (Distributed Denial of Service) attack on basis of access marking
InactiveCN103078856AImprove the ability to resist DDoS attacks at the application layerImplement synchronous filteringTransmissionFeature vectorFeature extraction
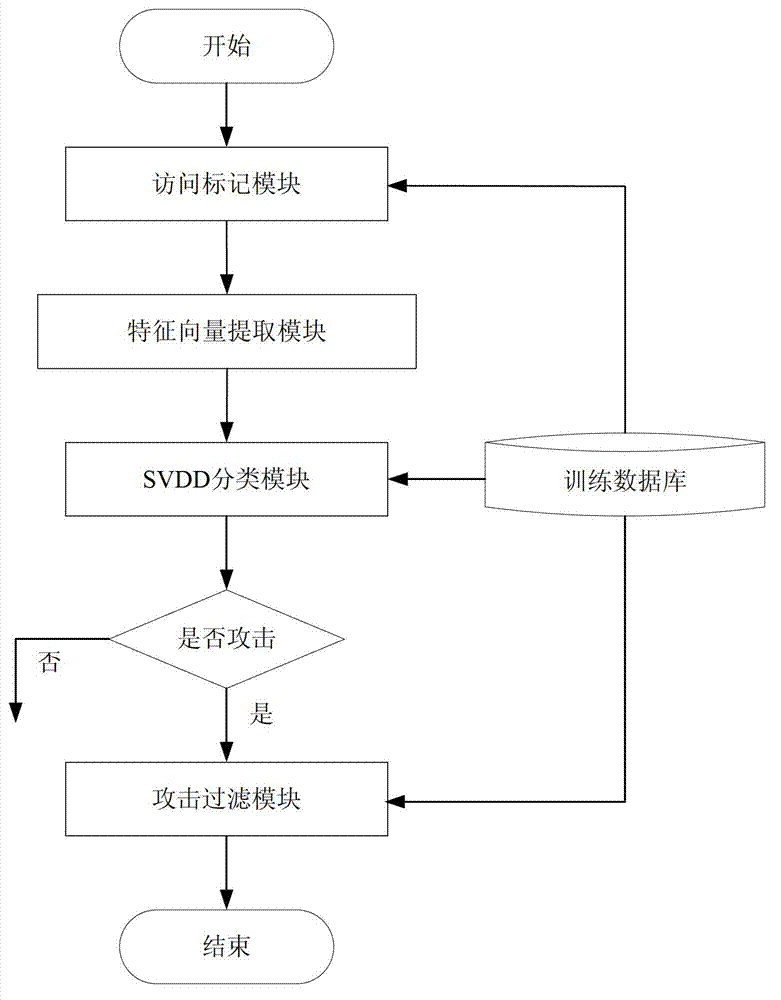
The invention discloses a method for detecting and filtering an application layer DDoS (Distributed Denial of Service) attack on the basis of access marking. The method comprises the following steps of: on the training phase, carrying out non-strategy marking on access behaviors of normal users; carrying out marking processing by adopting a marking strategy; extracting detection features by adopting a feature extraction strategy and representing access users as feature vectors; acquiring SVDD (Support Vector Data Description) supraspheres of the normal users and storing the SVDD supraspheres into a training database; carrying out marking on the basis of the marking strategy on access behaviors of users who enter a server and are to be detected; extracting effective detection features and expressing the access users into a feature vector form; and according to the SVDD supraspheres, carrying out detection classification and abnormity judgment on the feature vectors and when the access users are abnormal users, carrying out synchronous filtering. Implementation of the technical scheme adopted by the invention has the following beneficial effects that access marking and extraction of abnormal features are not limited to the specific server; synchronous filtering on attacking users can be implemented in the detecting process; and capability that the server resists to application layer DDoS attack is improved.
Owner:大连环宇移动科技有限公司 +1
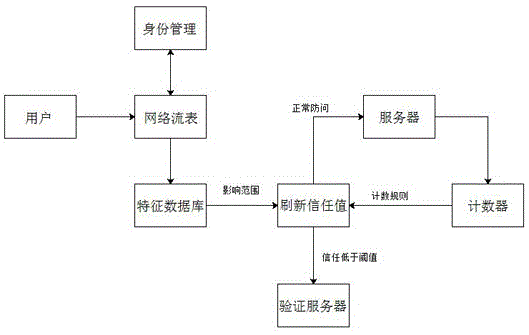
DDoS(Distributed Denial of Service)attack defensive system for application layer based on multiple feature recognition
The invention discloses a DDoS(Distributed Denial of Service) attack defensive system for an application layer based on multiple feature recognition. When a user initiates a request, the system stores information of a user data packet in a net-node network flow table, analyzes the user data packet, and judges whether the source of the user data packet is real and reliable or not; verification data is inserted when data is returned to the user; whether the source is real and reliable or not is detected again; afterthe fact that the source is real is determined, the credibility of the user is a threshold value credibility; the system distributes a cookie identity identifier to the source; then, a data database for recording the cookie identity identifier is established; access information of the cookie identity identifier within a certain time period is recorded and stored; the access information is used as the basis of identity verification management; and corresponding dispatching is carried out through analysis and treatment of a feature library. According to the invention, whether the long-term access behaviour of the user is normal or illegal can be analyzed and judged by establishing a blacklist and a whitelist ofaccess feature detection analysis; and the normal flow of the user cannot be intercepted when a DDoS attack occurs.
Owner:SHENZHEN YIKAYI NETWORK TECH
Method and system for network data analysis based on application layer data
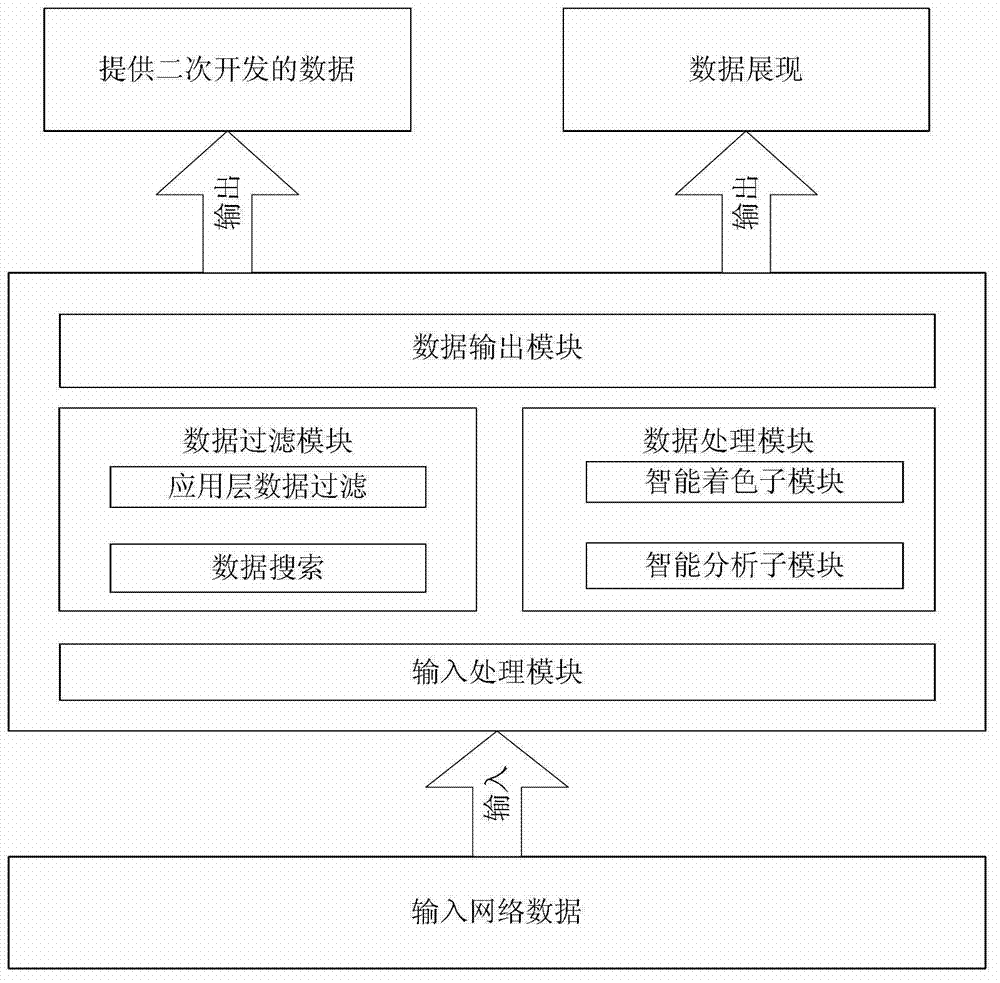
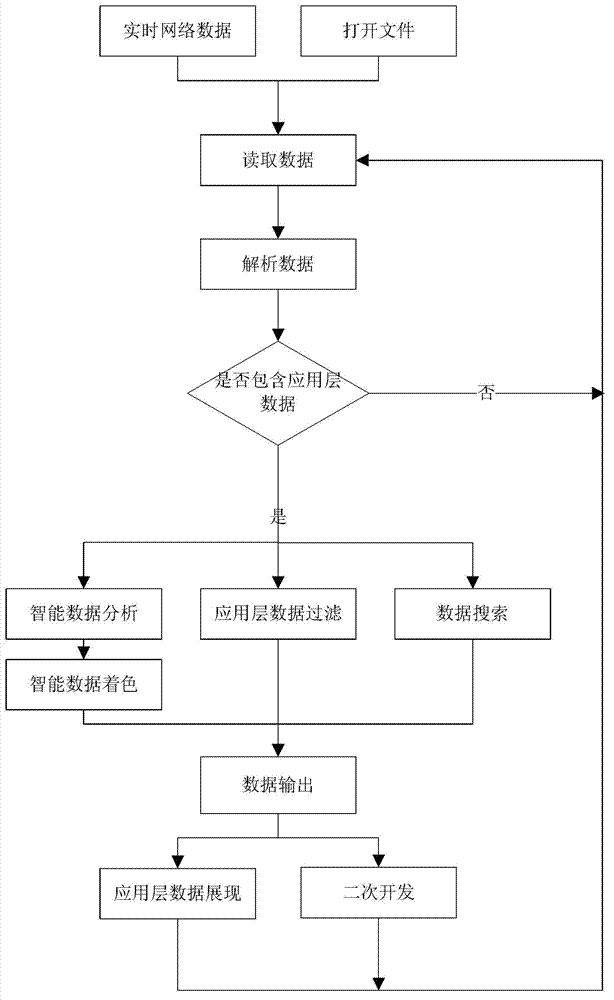
ActiveCN102970189AEasy to identifySee the law of changeData switching networksExtensibilityTransport layer
The invention discloses a method and a system for network data analysis based on application layer data. The method comprises the following steps of: reading network data and analysing that whether the present data packet is an application layer data packet or not at first; if not, then discarding the present data packet; or else, then analysing the quintuple (comprising a source IP (Internet protocol) address, a destination IP address, a source port, a destination port and a transport layer protocol) of each network data packet, and the application layer data; filtering the analysed application layer data according to set characteristics, so as to obtain application layer data meeting the set characteristics; or, displaying the application layer data satisfying the set characteristics to be set colours, and highlighting the application layer data meeting the set characteristics. With the adoption of the method and the system disclosed by the invention, the communication content of analysis software and audit network content become convenient, and the working efficiency can be increased; and moreover, an analysis function can be customized according to a specific network protocol, so that the analysis work becomes flexible and has extendibility.
Owner:RUN TECH CO LTD BEIJING
Network access system and method based on application layer data
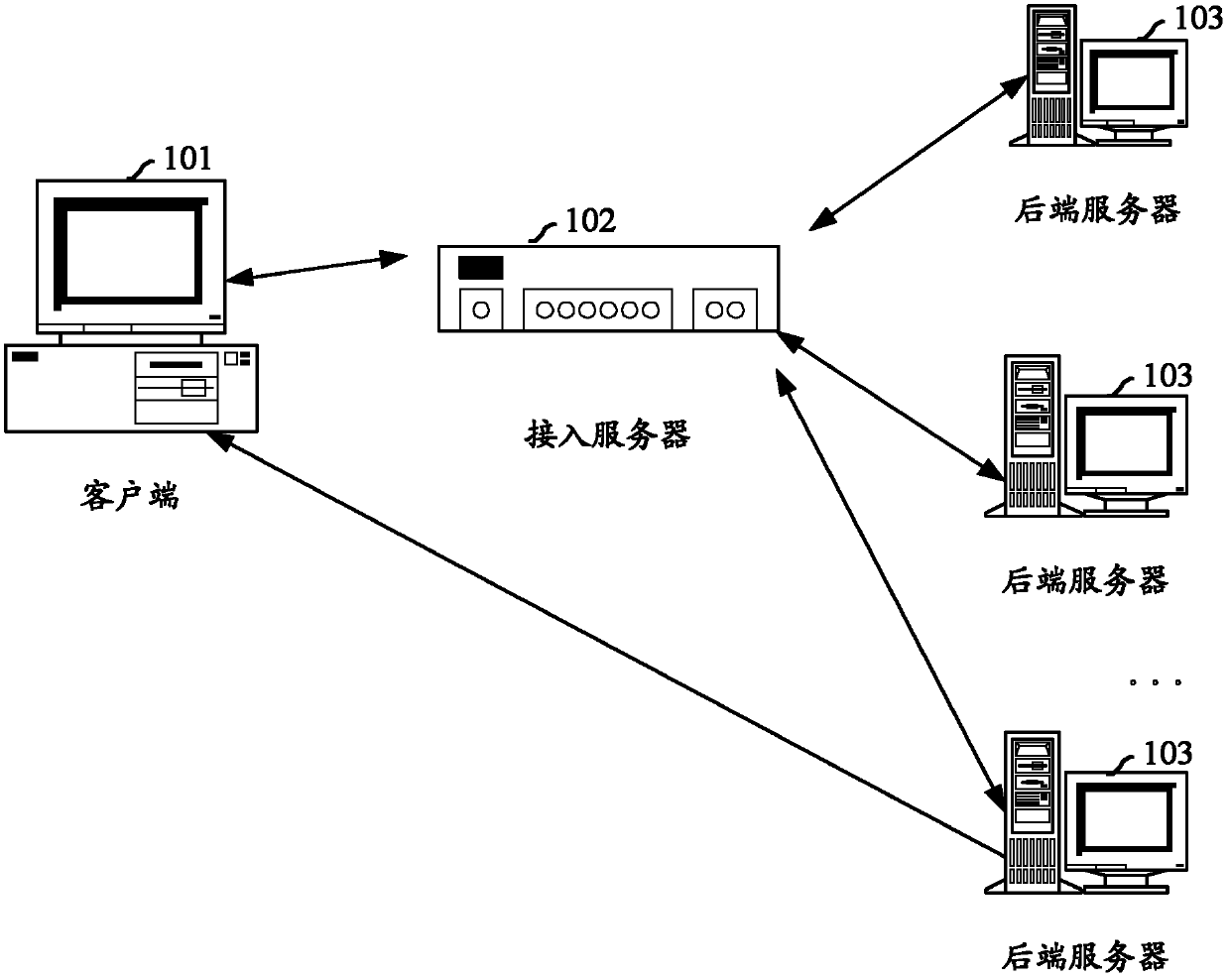
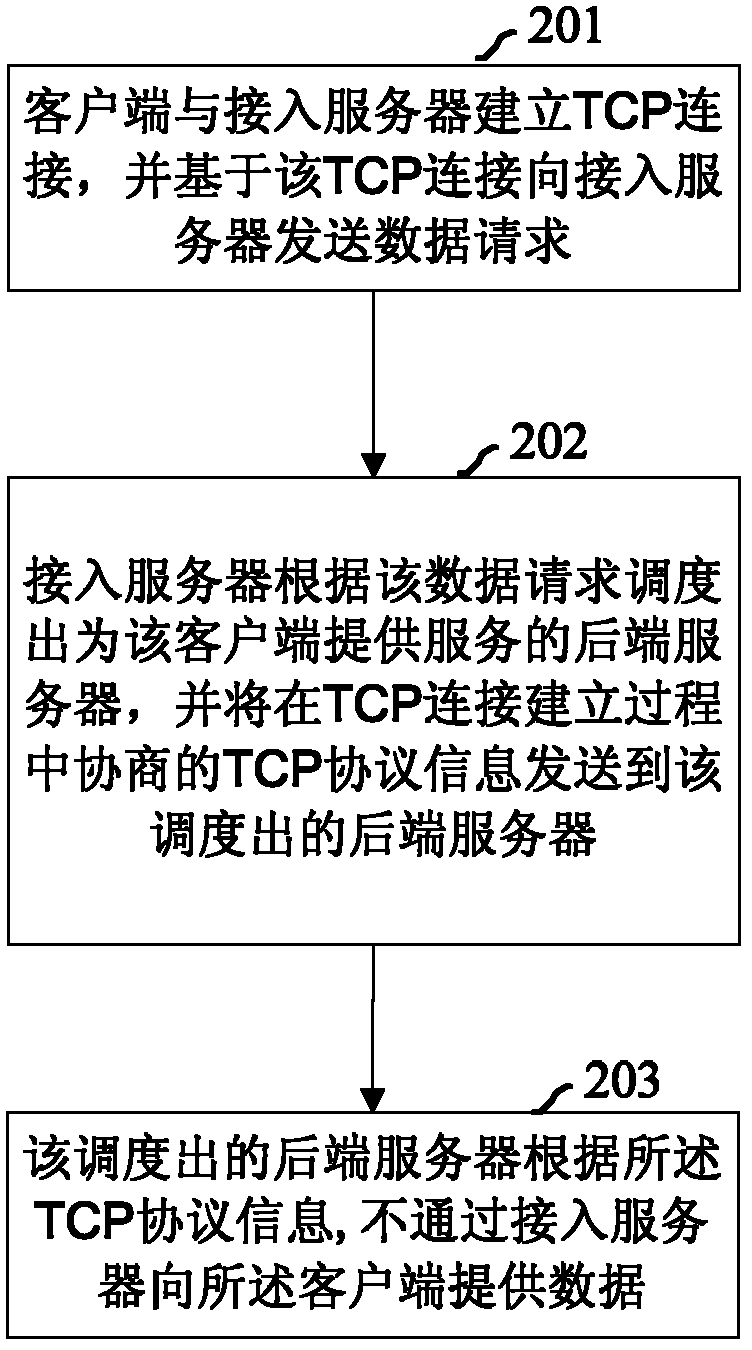
InactiveCN103379130AReduce implementation complexityReduce demandError prevention/detection by using return channelData switching by path configurationBack end serverClient-side
The embodiments of the invention propose a system for network access based on application layer data, including: a client, for establishing TCP connection with an access server, and sending a data request to the access server based on the TCP connection; an access server, for selecting a background server providing service to the client from a background server group according to the data request, and sending TCP protocol information negotiated in the TCP connection to the selected background server; the selected background server, for providing data directly to the client according to the TCP protocol information, without via the access server. The embodiments of the invention also propose a method for network access based on application layer data. By applying of the embodiments of the invention, the complexity is reduced, the implementation efficiency is enhanced, and the interactive process is simplified for the background server.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
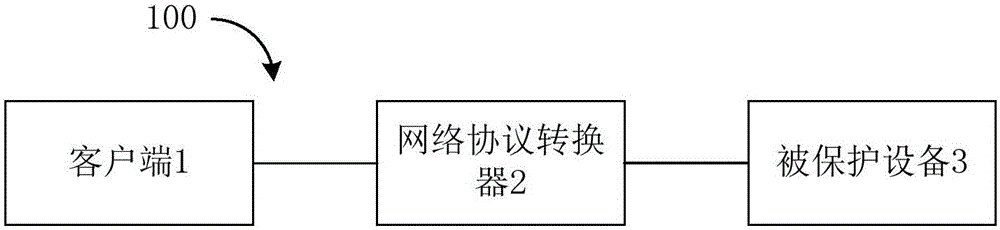
Network protocol conversion system, network protocol converter and network protocol conversion method
InactiveCN106357590AGuaranteed continuityReduced development effortTransmissionNetworking protocolClient-side
The invention discloses a network protocol conversion system, a network protocol converter and a network protocol conversion method. The network protocol converter comprises a first receiving unit, a content acquiring unit, an application layer extracting layer, a first packing unit and a first transmitting unit, wherein the first receiving unit is used for receiving data request information of a first network protocol of a client side, the content acquiring unit is used for connecting with protected equipment through a second network protocol so as to acquiring content of the protected equipment according to the data request information, the application layer extracting unit is used for extracting application layer data in the second network protocol, the first packing unit is used for packing the content of the protected equipment in a form of the first network protocol according to the application layer data and preset configuration information, and the first transmitting unit is used for transmitting the packed content to the client side. The network protocol conversion system, the network protocol converter and the network protocol conversion method have the advantages that through the externally connected network protocol converter, security conversion for an original product network protocol is realized transparently, development for special products one by one is not required, low developing workload is required, and application range is large.
Owner:VERTIV ENERGY SYST INC
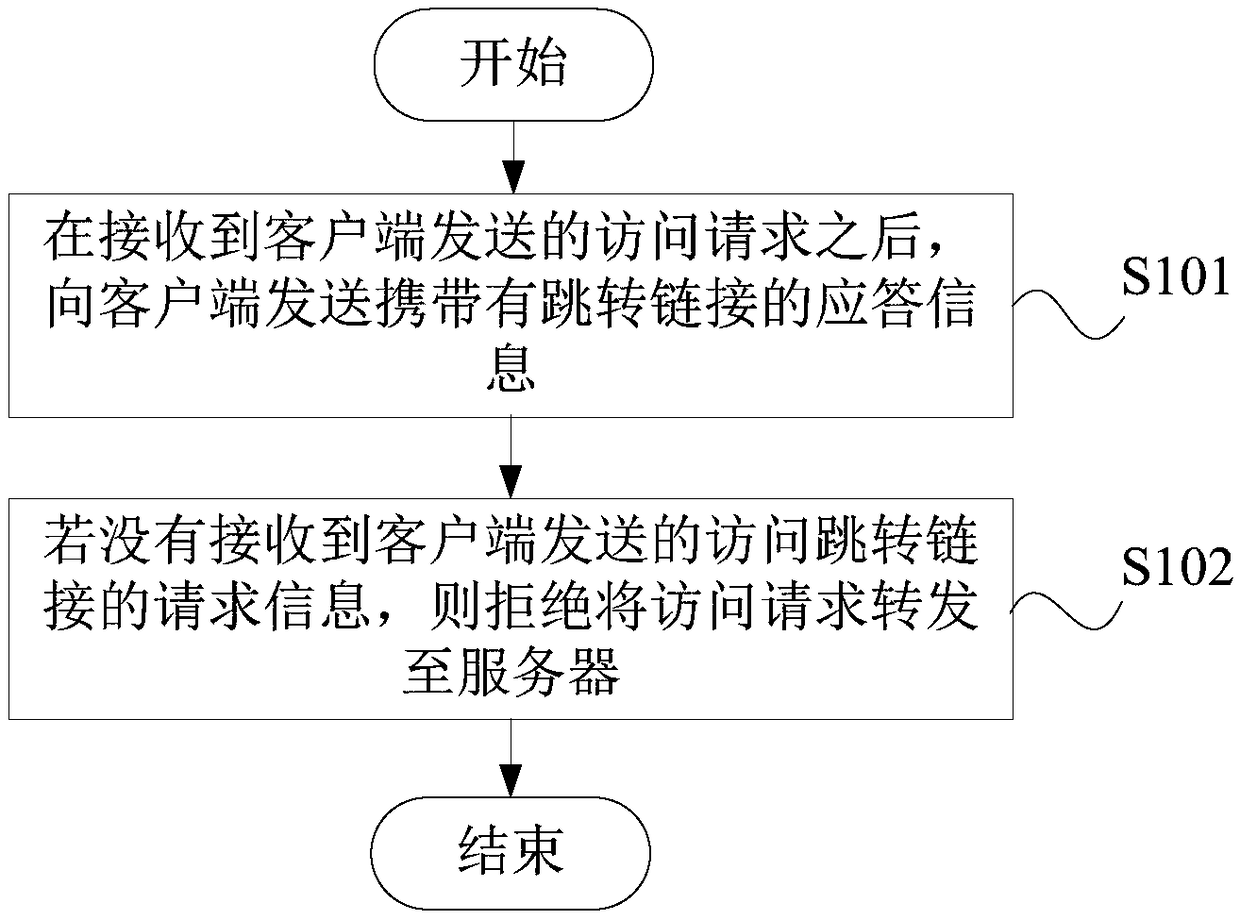
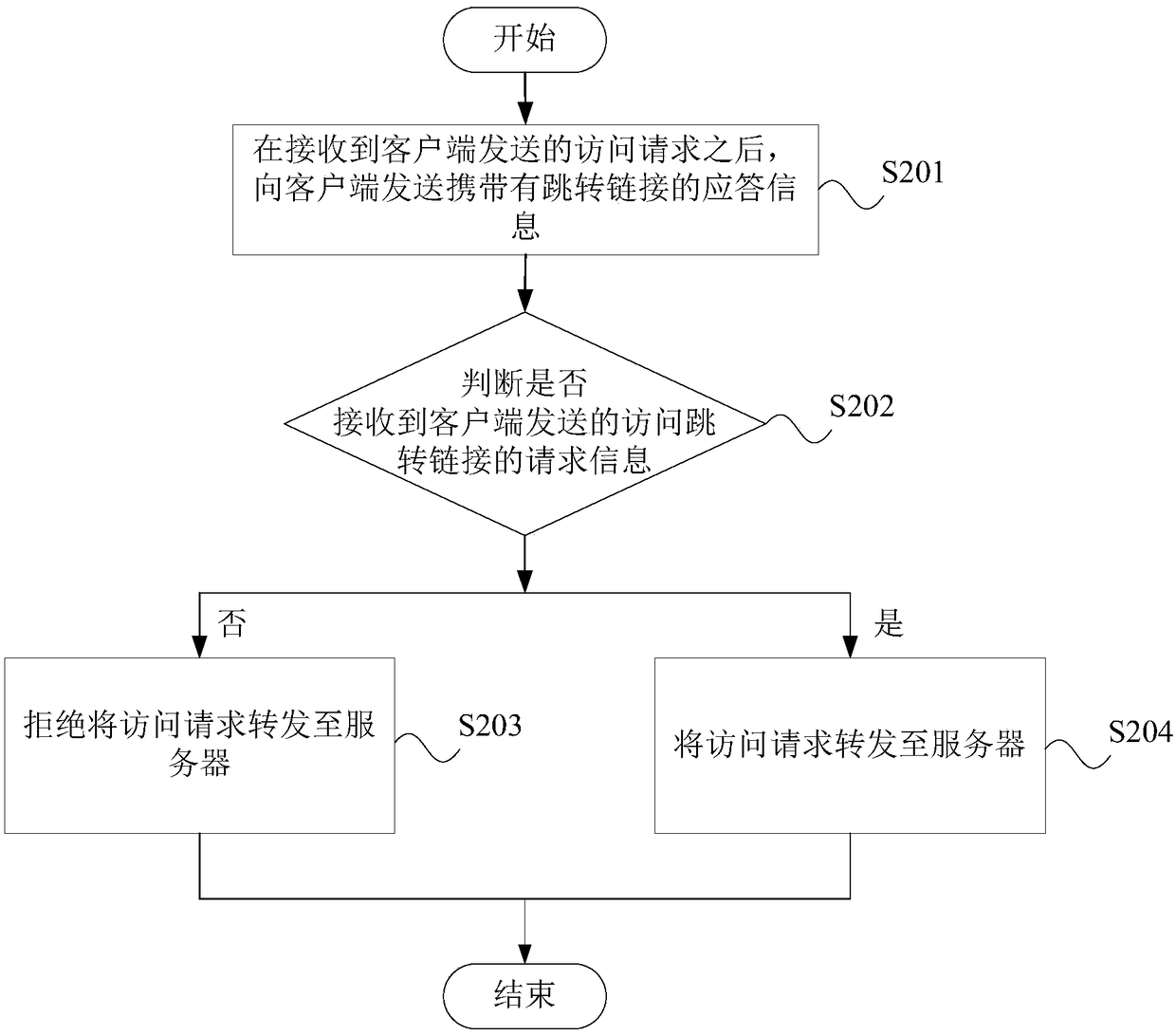
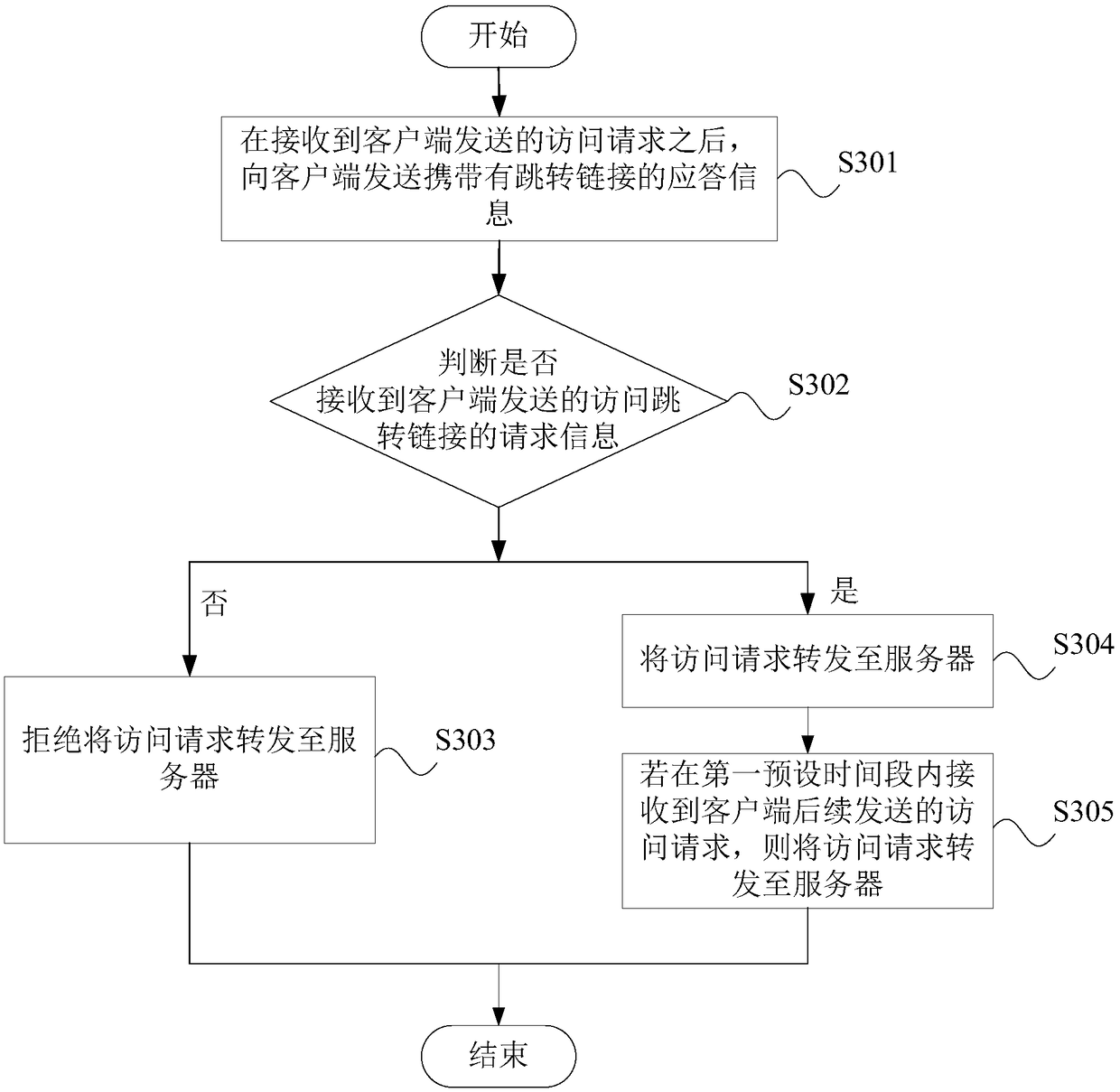
Protection method and protection device for application layer attacks and electronic equipment
InactiveCN108881226AAvoid attackTo achieve the purpose of cleaning attack trafficTransmissionClient-sideProtocol Application
The present application provides a protection method and a protection device for application layer attacks, electronic equipment and a computer readable storage medium. The protection method comprises: after an access request sent by a client is received, sending response information carrying a jump link to the client; and if request information of the access jump link sent by the client is not received, denying forwarding the access request to the server. A protection side sends response information carrying a jump link and verification request information to the client; and according to theresponse made by the client, whether the client is an abnormal client can be accurately judged, the access request from the abnormal client is denied to be forwarded to the server when the client is an abnormal client, and the abnormal client can be effectively prevented from attacking the application layer, so that the server can serve the normal client.
Owner:北京云枢网络科技有限公司
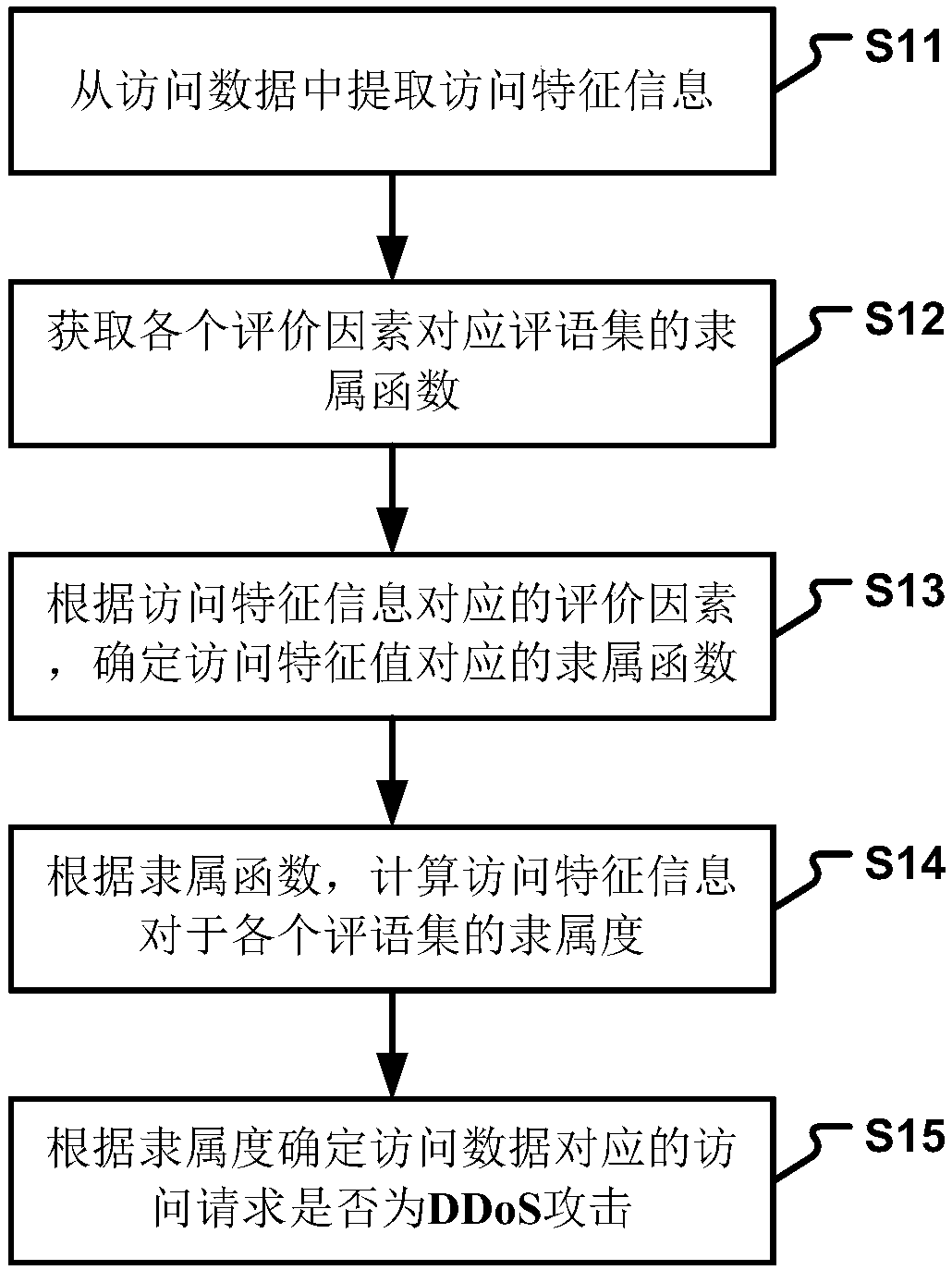
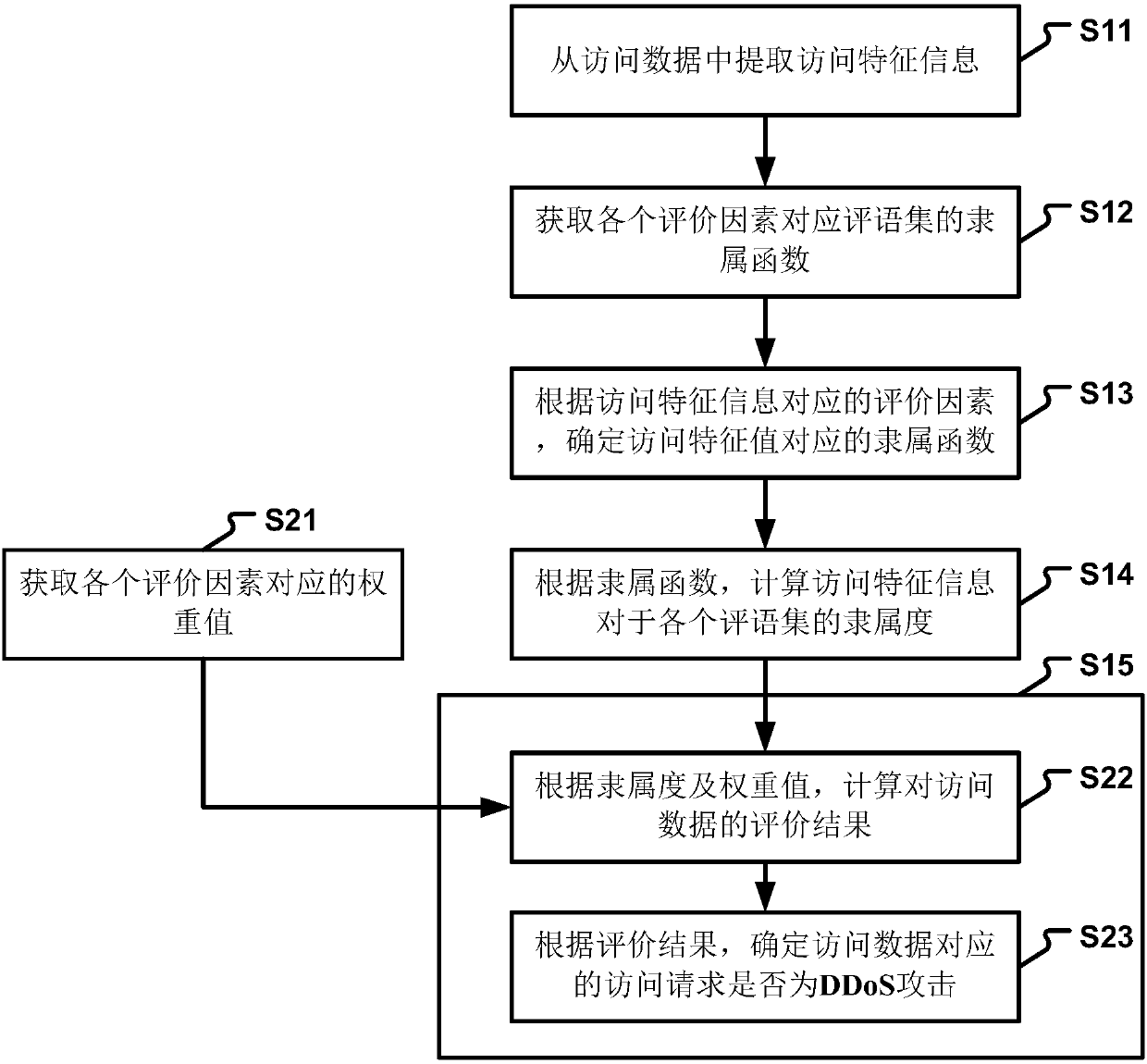
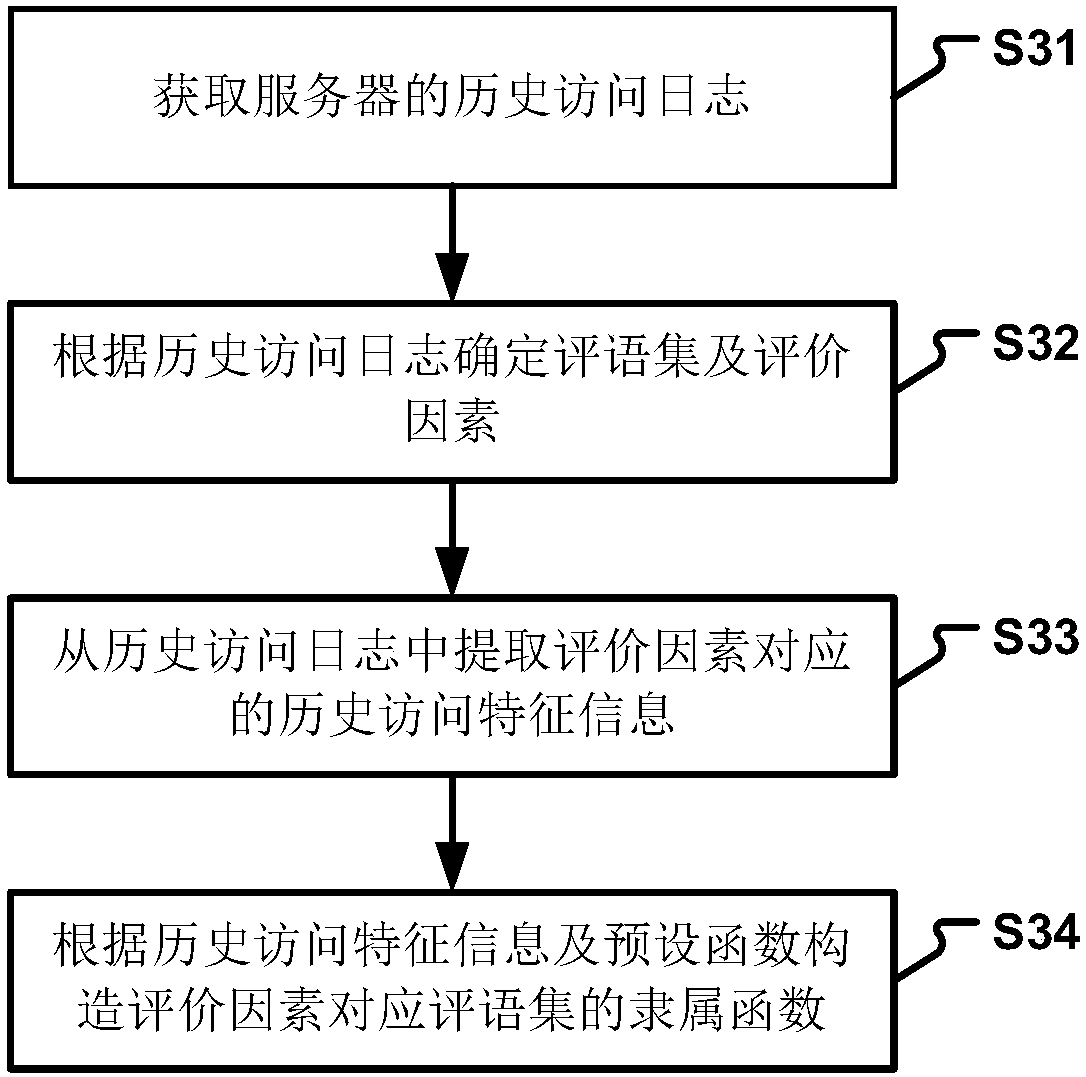
Application layer DDoS attack detection method and device
The invention relates to an application layer DDoS attack detection method and device. The method comprises the following steps: extracting access feature information from access data; obtaining a membership function of a comment set corresponding to each evaluation factor; determining a membership function corresponding to an access feature value according to the evaluation factor corresponding to the access feature information; calculating a membership degree of the access feature information for each comment set according to the membership function; and determining whether an access requestcorresponding to the access data is a DDoS attack. By adoption of the technical scheme, the accuracy and efficiency of detection are effectively improved, the false positive rate and the missed rateare reduced, and the security of the server is further improved.
Owner:BEIJING JIAOTONG UNIV
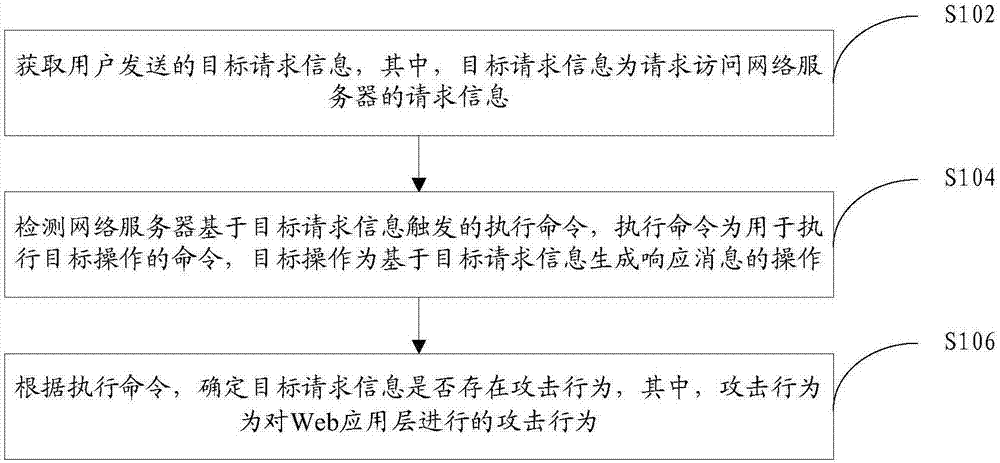
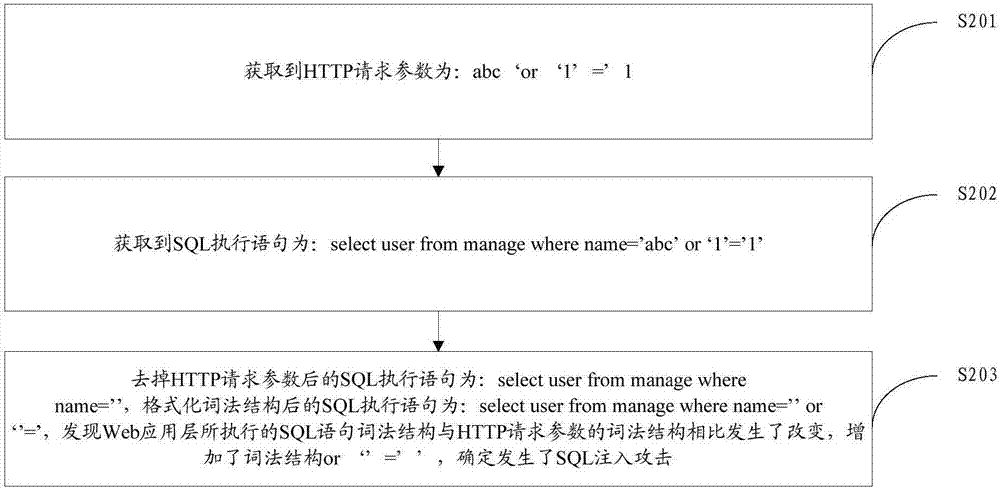
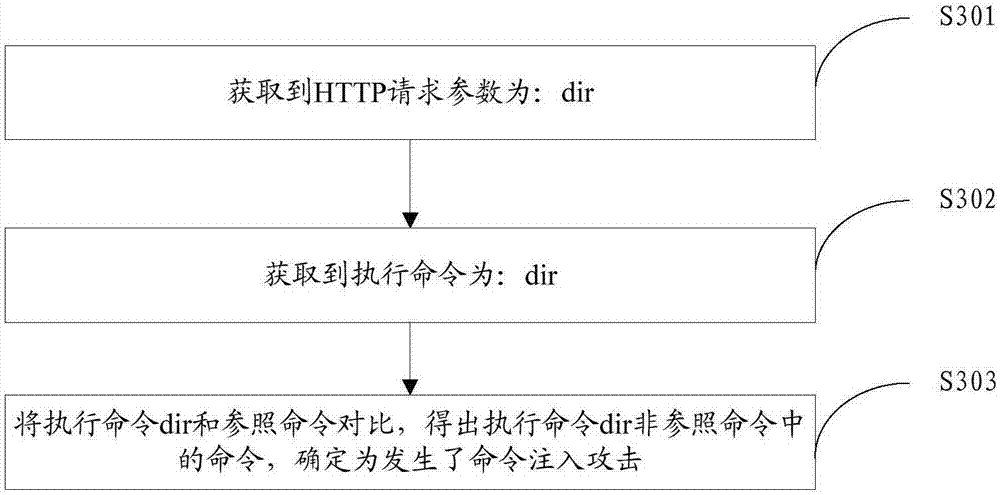
Method and device for improving detection accuracy of Web application layer attacks
ActiveCN107483510AMitigating technical issues with high false positive ratesTransmissionWeb applicationMisinformation
The invention provides a method and device for improving the detection accuracy of Web application layer attacks and relates to the technical field of network safety. The method comprises the steps that target request information sent by a user is acquired, wherein the target request information is request information for access to a network server; an execution command triggered by the network server based on the target request information is detected, wherein the execution command is a command used for executing a target operation, and the target operation is an operation of generating responding information based on the target request information; according to the execution command, whether or not an attack action exists in the target request information is determined, wherein the attack action is the attack action conducted on the Web application layer. The method and device solve the technical problem that a traditional application layer attack detection method is relatively high in misinformation rate.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
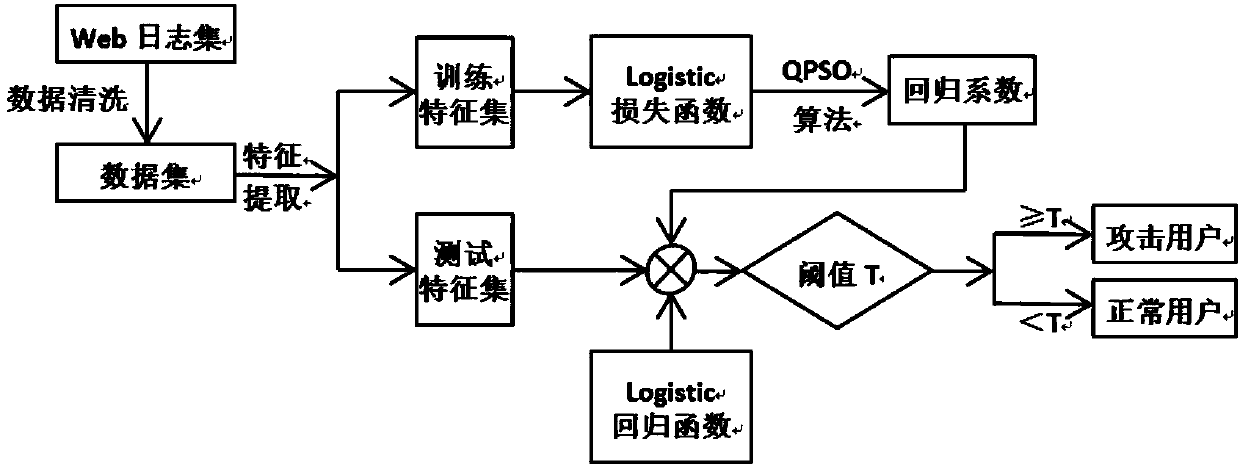
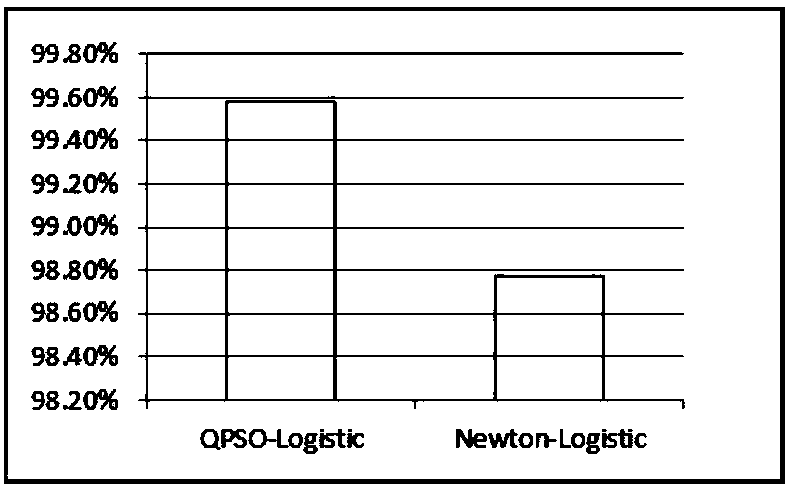
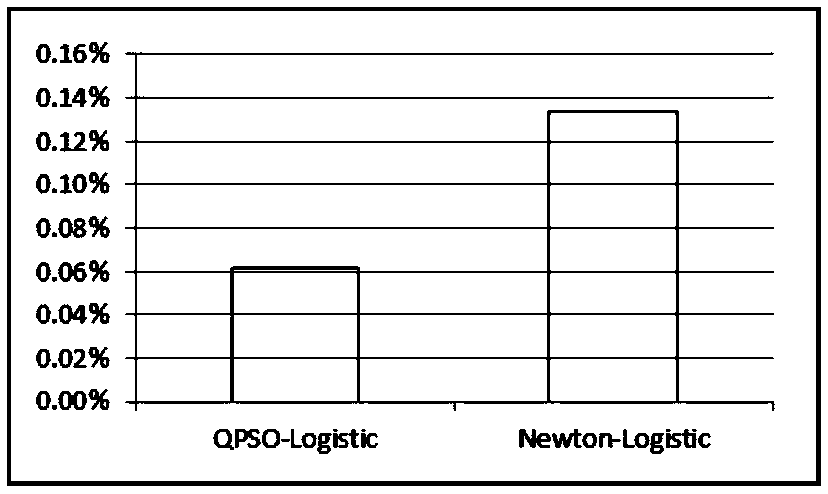
Application layer DDoS attack detection method based on logistic regression
The invention relates to an application layer DDoS attack detection method based on logistic regression. The method comprises the following steps: with the IP address of an access user as an identifier, extracting a feature set of user access behaviors; calculating a logistic regression function value of the user; obtaining the maximum likelihood function according to a logistic regression model,wherein the loss function of the logistic regression model is the opposite number of the maximum likelihood function; with the loss function as the target function, solving the target function by using a quantum particle swarm optimization algorithm to obtain the parameters of the logistic regression model, so that the target value of the loss function is the maximal; and predicting the unmarked user features by using the solved logistic regression model to obtain the category of the user.
Owner:TIANJIN UNIV
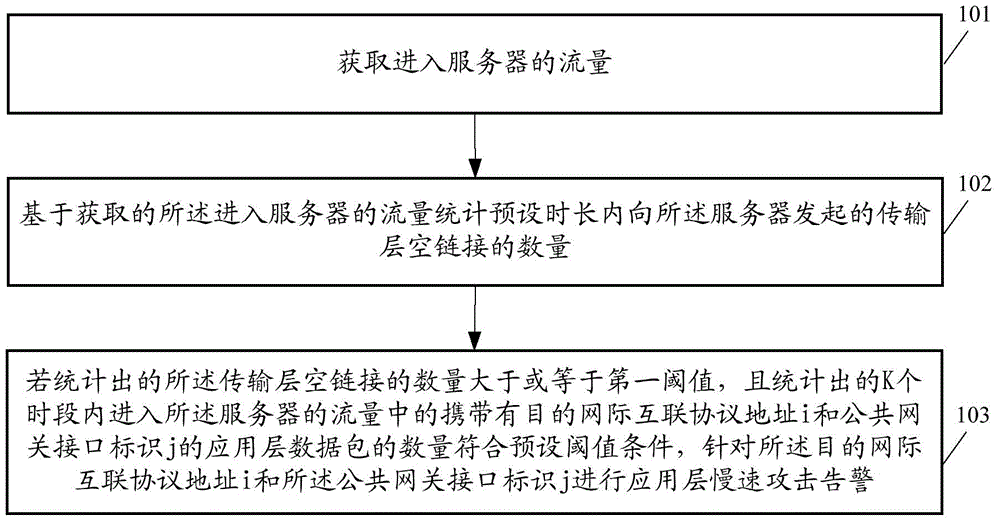
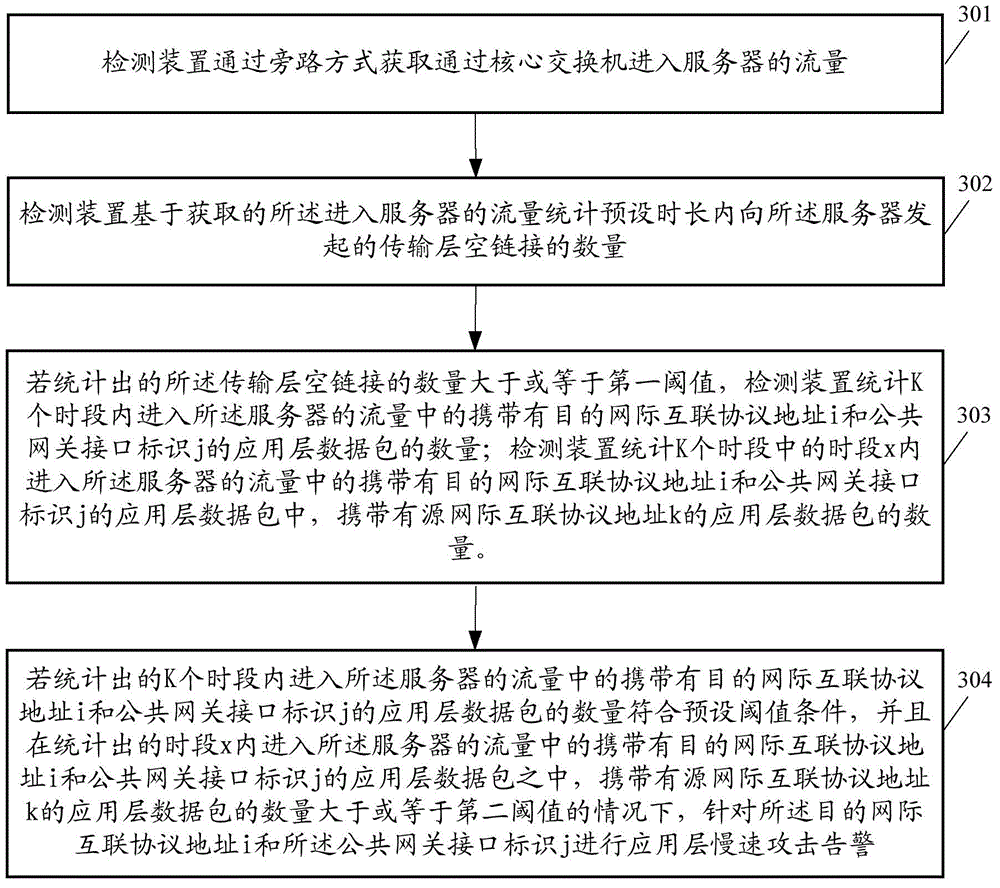
Application layer slow-speed attack detection method and correlation apparatus
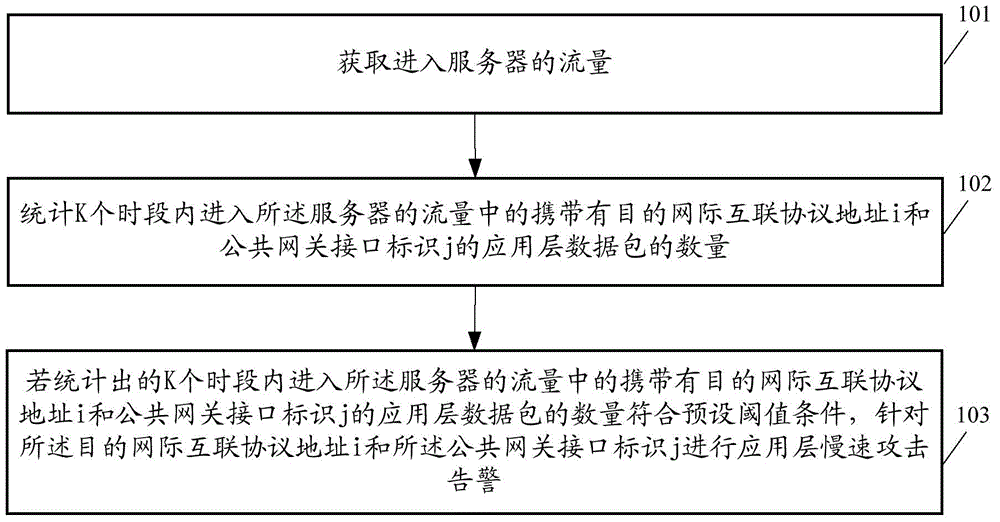
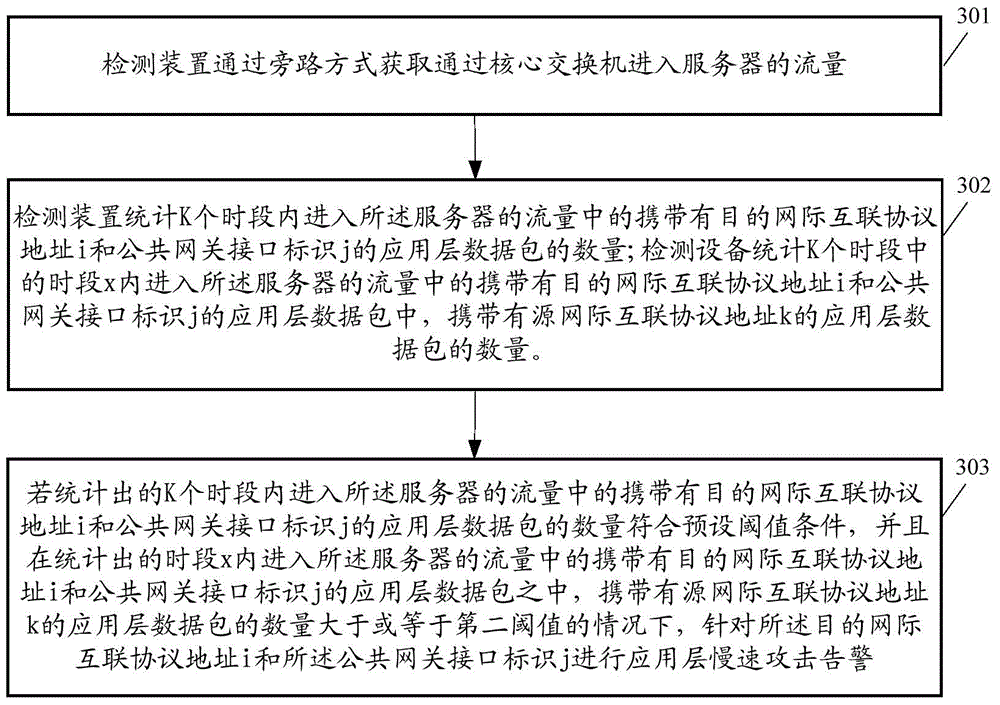
ActiveCN105591832AAccurate slow attack warningImprove accuracyData switching networksPublic networkProtocol for Carrying Authentication for Network Access
The embodiments of the invention disclose an application layer slow-speed attack detection method and a correlation apparatus. The application layer slow-speed attack detection method comprises the following steps: obtaining a flow entering a server; based on the obtained flow entering the server, counting the quantity of transmission layer empty chains initiated to the server within preset duration; and if the counted quantity of the transmission layer empty chains is greater than or equal to a first threshold and the quantity of application layer data packets carrying a destination internetworking protocol address i and a public network gateway interface identification j in the flow entering the server within k periods accords with a preset threshold condition, performing application layer slow-speed attack alarm on the destination internetworking protocol address i and the public network gateway interface identification j, wherein the destination internetworking protocol address i is one of internetworking protocol addresses of the server. According to the technical scheme provided by the embodiments of the invention, the accuracy of the application layer slow-speed attack alarm is improved.
Owner:TENCENT DIGITAL TIANJIN
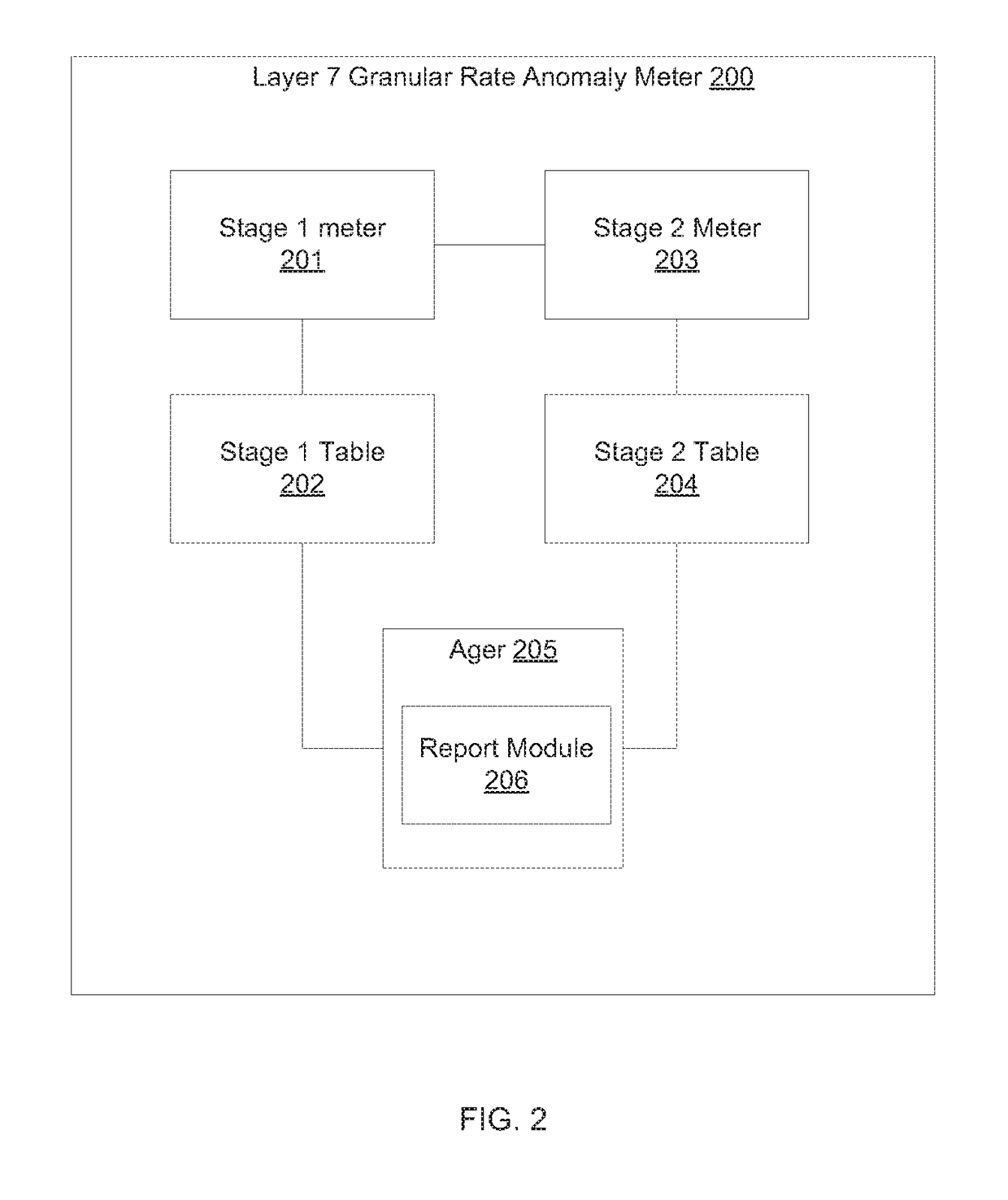
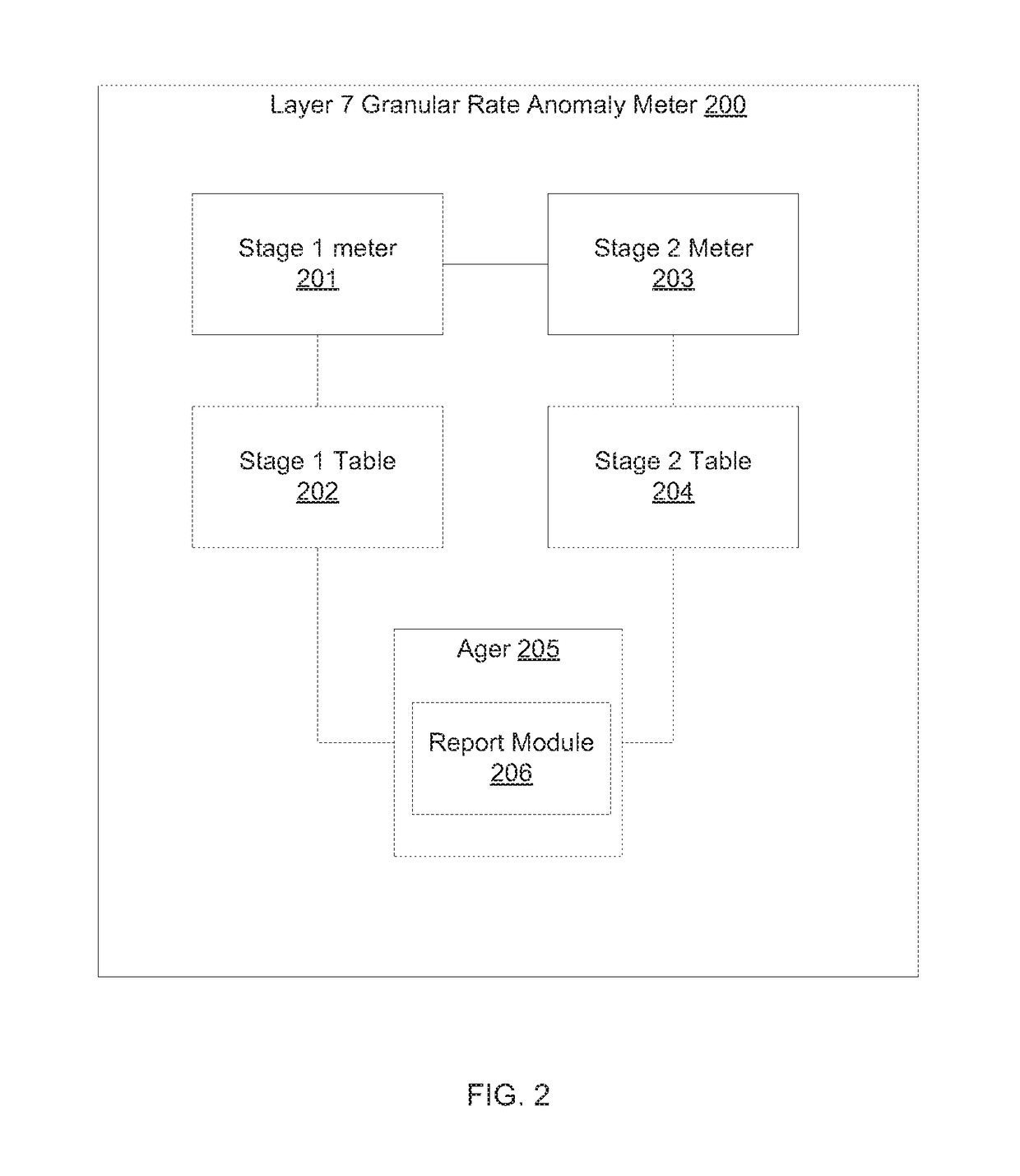
TWO-STAGE HASH BASED LOGIC FOR APPLICATION LAYER DISTRIBUTED DENIAL OF SERVICE (DDoS) ATTACK ATTRIBUTION
ActiveUS20170180415A1Improve attributesTransmissionProtocol ApplicationApplication layer DDoS attack
Methods and systems for a two-stage attribution of application layer DDoS attack are provided. In a first table just a hash index is maintained whereas the second stage table keeps the string parameter corresponding to the application layer attribute under attack. A linked list maintains a plurality of rows if there is hash collision in the first table. The second table is aged out and reported periodically with details of large strings.
Owner:FORTINET
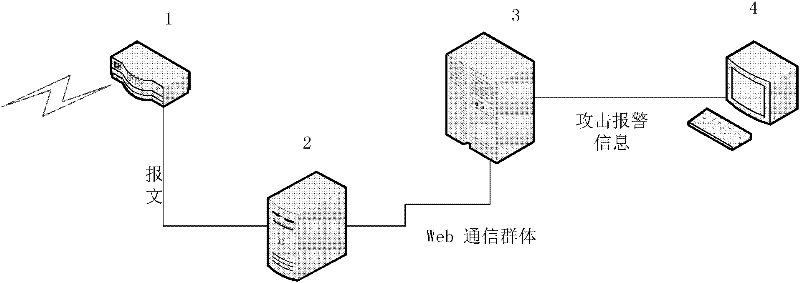
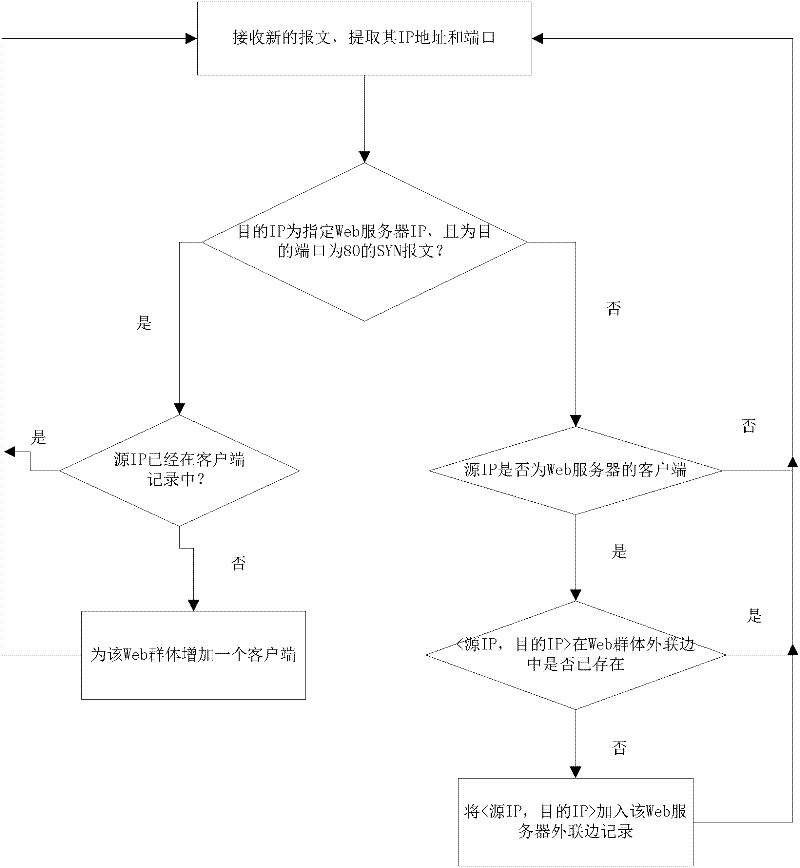
Distributed denial-of-service attack detection method based on external connection behaviors of Web communication group
The invention discloses a distributed denial-of-service attack detection method based on the external connection behaviors of a Web communication group. The method comprises the following steps of: 1) setting a port mirror image on network equipment, and copying and transmitting all network messages passing through the equipment to an attach detection front-end processor; 2) extracting the communication group of a given Web server and the external connection behaviors of the communication group, and transmitting the communication group and the external connection behaviors thereof to an attack detection server by using the attack detection front-end processor; 3) counting external connection behavior parameters comprising the number CN_MLN of clients connected with a plurality of external connection nodes and a total client number CN of the Web communication group, and monitoring the offset of ratio of the two parameters by using an improved cumulative sum (CUSUM) algorithm to judge the occurrence of an application layer distributed denial-of-service (DDoS) attack according to the offset by using the attack detection server; and 4) reporting whether the application layer DDoS attack occurs to the given Web server or not to a network monitoring terminal at the end of each time period.
Owner:SHANDONG UNIV
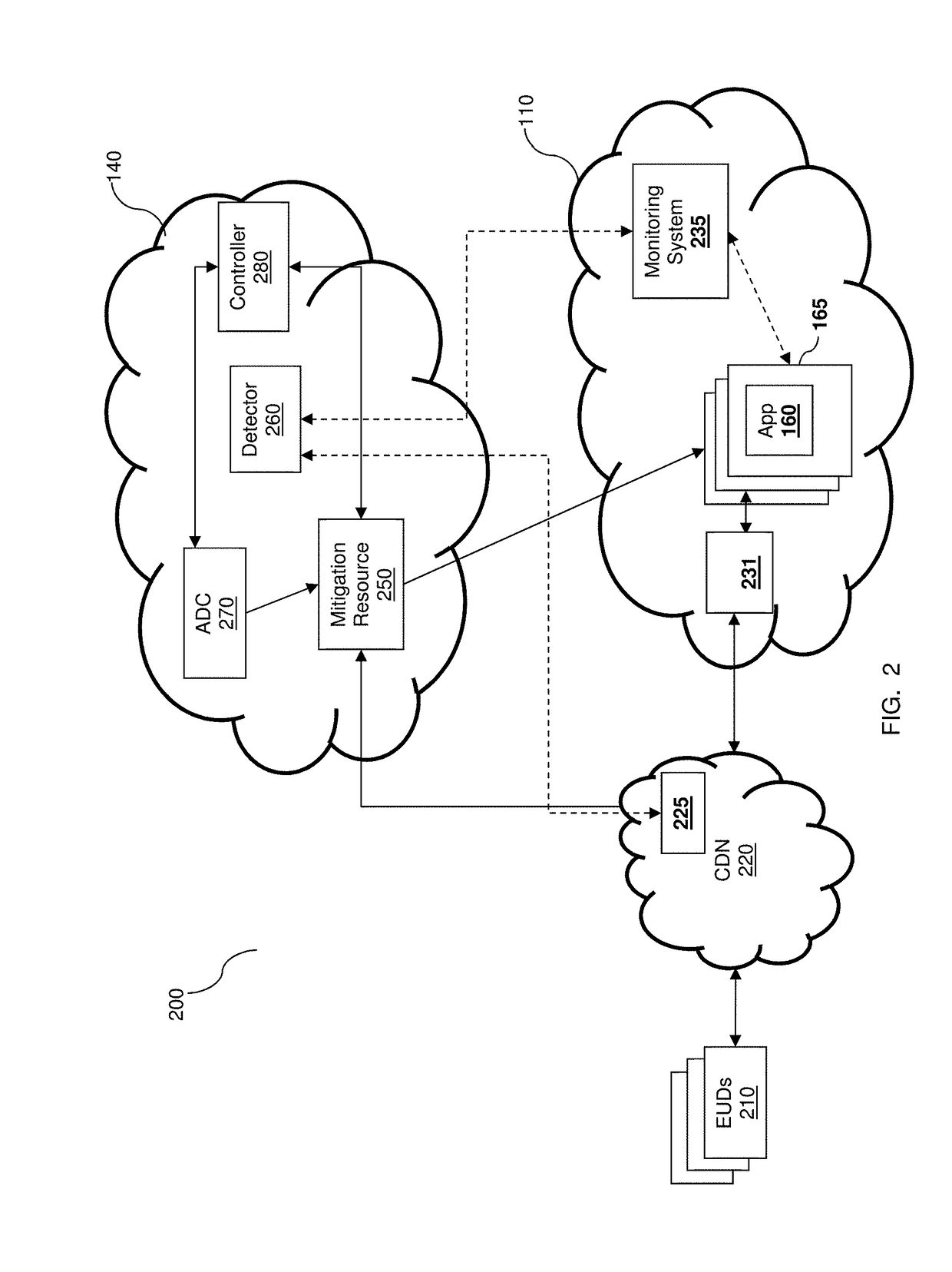
DETECTION AND MITIGATION OF SLOW APPLICATION LAYER DDoS ATTACKS
A method and system for protecting cloud-hosted applications against application-layer slow distributed denial-of-service (DDoS) attacks. The comprising collecting telemetries from a plurality of sources deployed in at least one cloud computing platform hosting a protected cloud-hosted application; providing a set of rate-based and rate-invariant features based on the collected telemetries; evaluating each feature in the set of rate-based and rate-invariant features to determine whether a behavior of each feature and a behavior of the set of rate-based and rate-invariant features indicate a potential application-layer slow DDoS attack; and causing execution of a mitigation action, when an indication of a potential application-layer slow DDoS attack is determined.
Owner:RADWARE
Cellular ad hoc network radio resource optimization and allocation method
InactiveCN102170700AReduce overheadImprove utilizationHigh level techniquesWireless communicationQuality of serviceDecomposition
The invention relates to a cellular ad hoc network radio resource optimization and allocation method which comprises the following steps: for a given system model and parameters, obtaining a performance objective function which can be realized under a cooperative relay protocol and can select a monotonic increasing function reflecting the generation speed of application layer data required by users; giving the following constraint conditions required to be met by realizing performance indexes: different QoS (quality of service) requirements of end-users, a flow conservation principle, maximum and minimum transmission power requirements and attainable speed requirements; carrying out Lagrangian dual decomposition according to the objective function and the constraint conditions, respectively decomposing to a physical layer, a network layer and an application layer of OSI (open system interconnection), and respectively carrying out the optimized solution on each layer by using a sub-gradient mathematical method; and after respectively solving the optimization sub-problems of the physical layer, the network layer and the application layer, obtaining the optimal flow distribution, relay selection, transmission power and data generation speed distribution of each sub-carrier. The method provided by the invention ensures better stability and reality, and is suitable for the next generation of cellular ad hoc cooperative networks.
Owner:GUANGZHOU UNIVERSITY
Method and related device for detecting quick attack of application layer
ActiveCN105656848AAttack alerts are accurateImprove accuracyTransmissionTraffic capacityProtocol Application
The embodiment of the invention discloses a method and related device for detecting a quick attack of an application layer. The method for detecting the quick attack of the application layer comprises the following steps of: obtaining the traffic entering a server; counting the number of application layer data packets carrying a target internetworking protocol address i and a public gateway interface identifier j in the traffic entering the server in K time intervals; and, if the counted number of the application layer data packets carrying the target internetworking protocol address i and the public gateway interface identifier j in the traffic entering the server in K time intervals accords with a threshold value condition, alarming the quick attack of the application layer for the target internetworking protocol address i and the public gateway interface identifier j, wherein the target internetworking protocol address i is one internetworking protocol address in the server; and the K is a positive integer, which is greater than or equal to 1. By means of the scheme in the embodiment of the invention, the quick attack alarm accuracy of the application layer is increased easily.
Owner:腾讯数码(深圳)有限公司
Security control method used for cloud platform network
ActiveCN105591928APrevent eavesdroppingPrevent tamperingUser identity/authority verificationData switching networksHash functionControl data
The invention provides a security control method used for a cloud platform network. The security control method comprises the steps that: a controller of the cloud network platform performs hash operation on application layer data in a control data message based on a preset security level value, a first currently valid secret key and a predetermined hash function when sending the control data message, so as to obtain an operation result; a first part of the operation result serves as authentication data and is attached to the control data message, and the second part of the operation result serves as a new first currently valid secret key to be used in the next hash operation; and the control data message with the authentication data is sent to a target node in the cloud network platform, and the target node adopts an algorithm corresponding to the hash operation adopted by the controller to authenticate the authentication data. The security control method used for the cloud platform network disclosed by the invention has high security level.
Owner:CHINA UNIONPAY
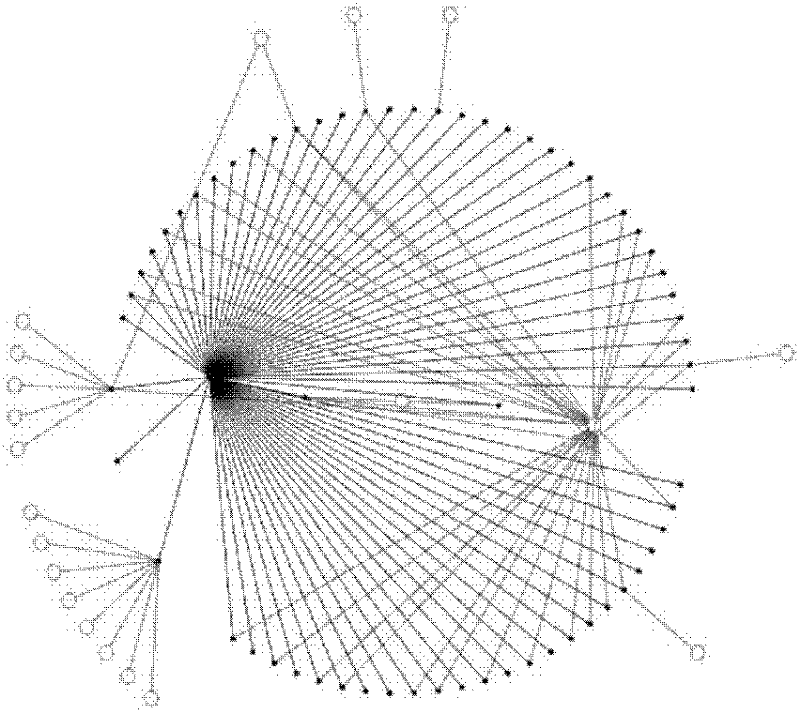
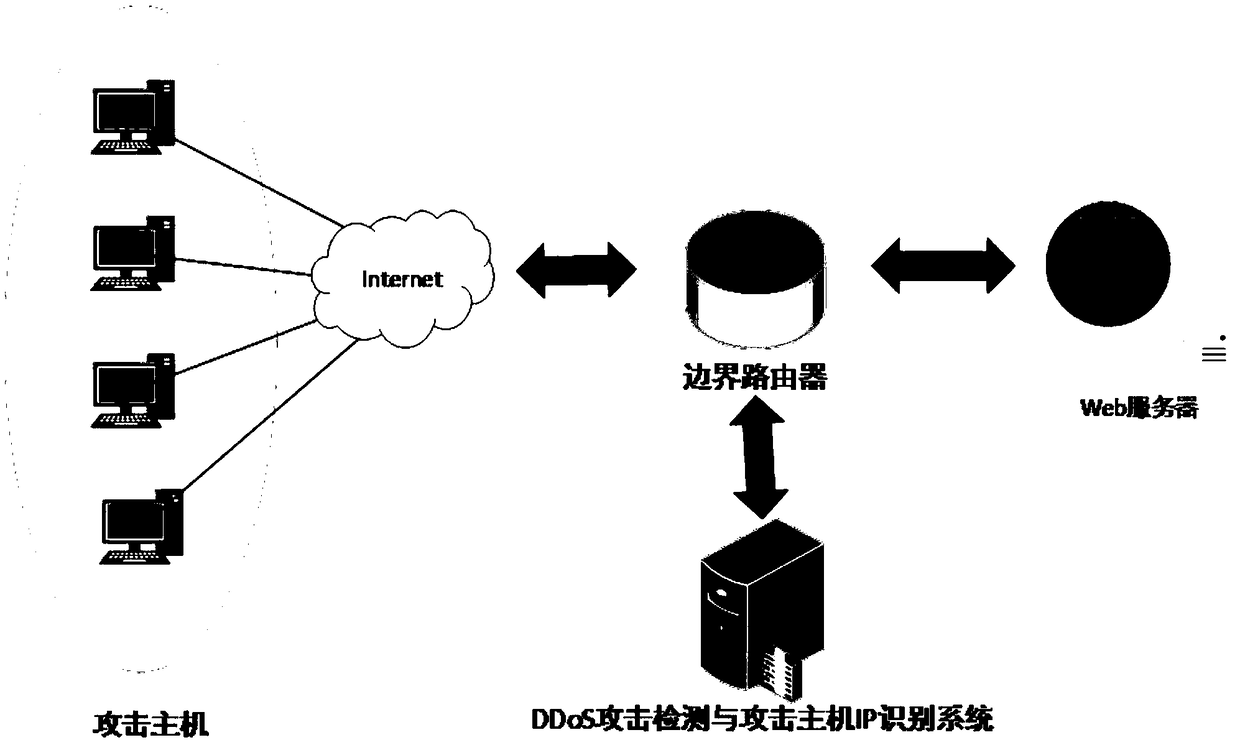
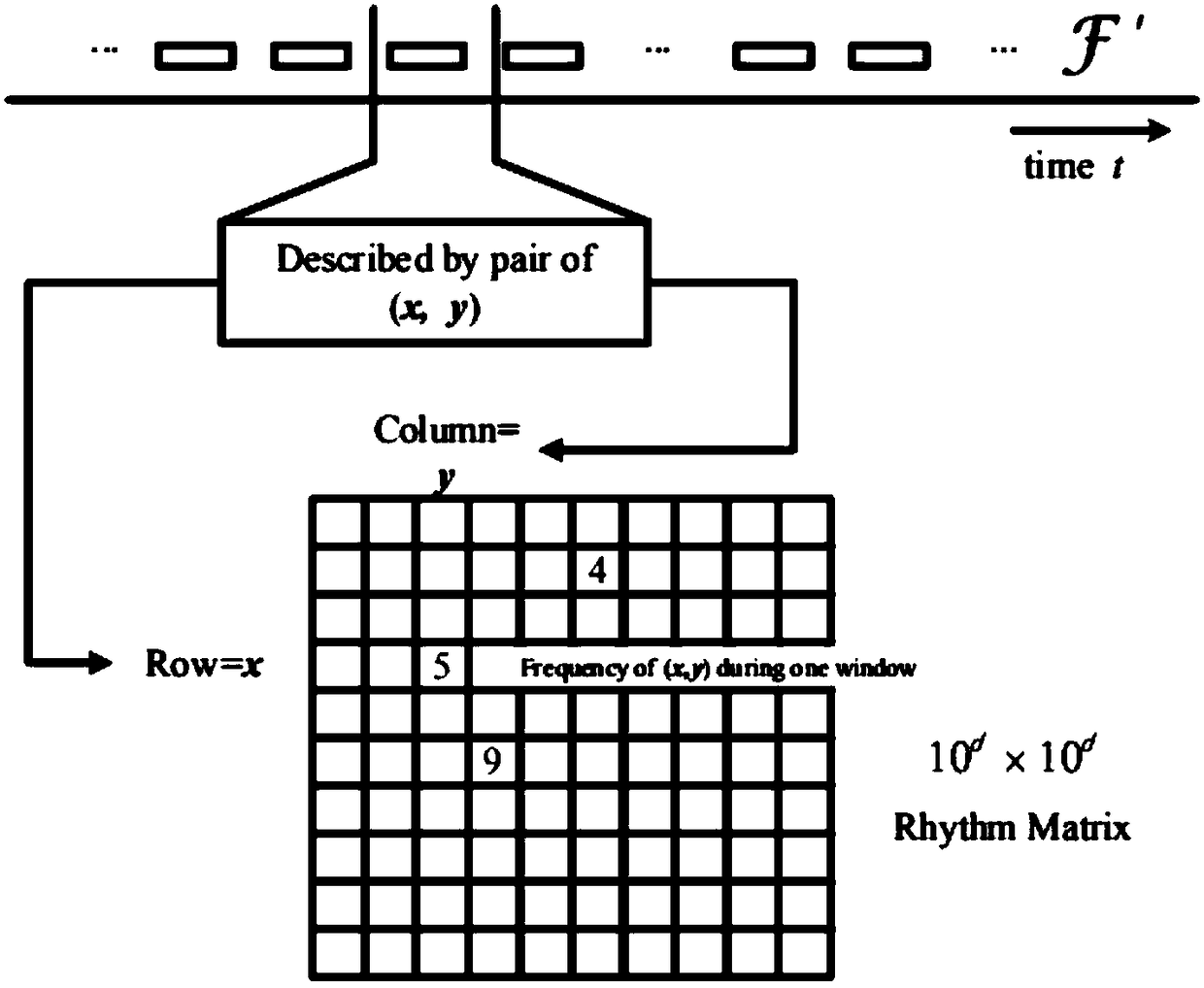
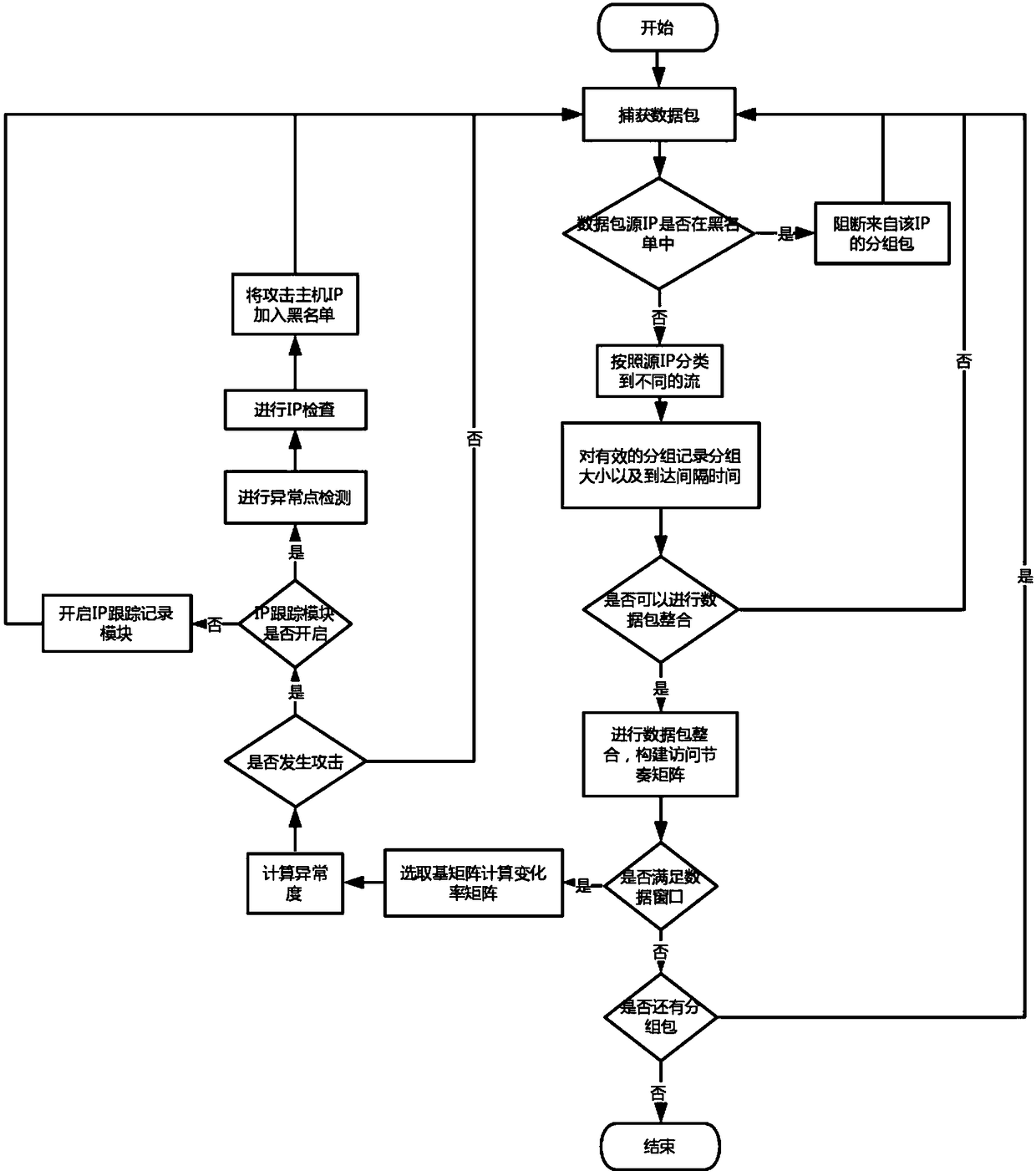
DDoS Attack Identification Method Based on Access Rhythm Matrix in Application Layer
ActiveCN109257384AReduce time and space complexityReduce time complexityTransmissionPort mirroringNetwork conditions
The invention discloses an application layer DDoS attack identification method based on an access rhythm matrix, which is based on a data structure of the access rhythm matrix, uses a variation anomaly degree to carry out attack detection, and uses an outlier point to identify an attack host IP. The time complexity and space complexity of the method are low, and the actual network condition will not be affected. The detection system integrated with the algorithm can be deployed between the nearest routing and the host. The inbound traffic packets can be obtained by port mirroring technology, and the access rhythm matrix can be constructed to detect DDoS attacks at the application layer and identify the attacking host IP.
Owner:济南百纳瑞信息技术有限公司
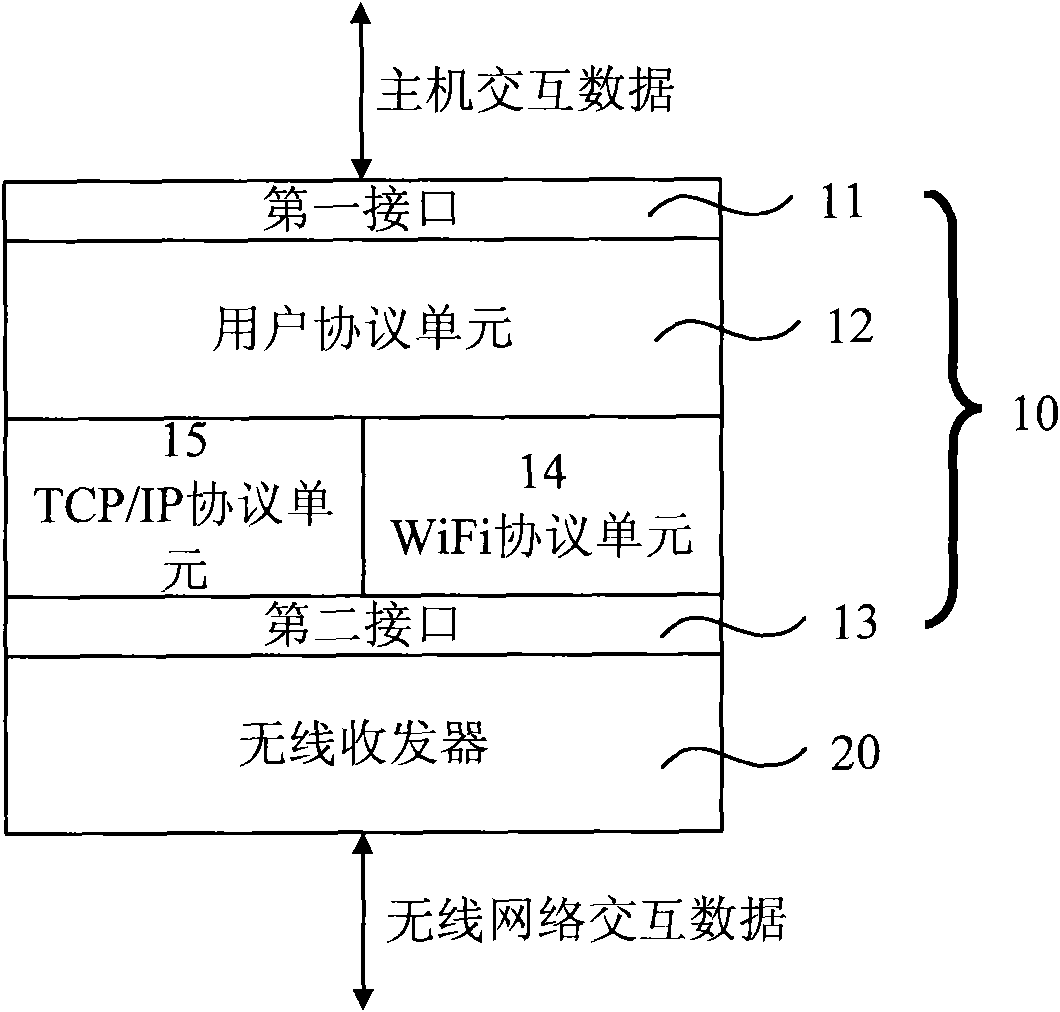
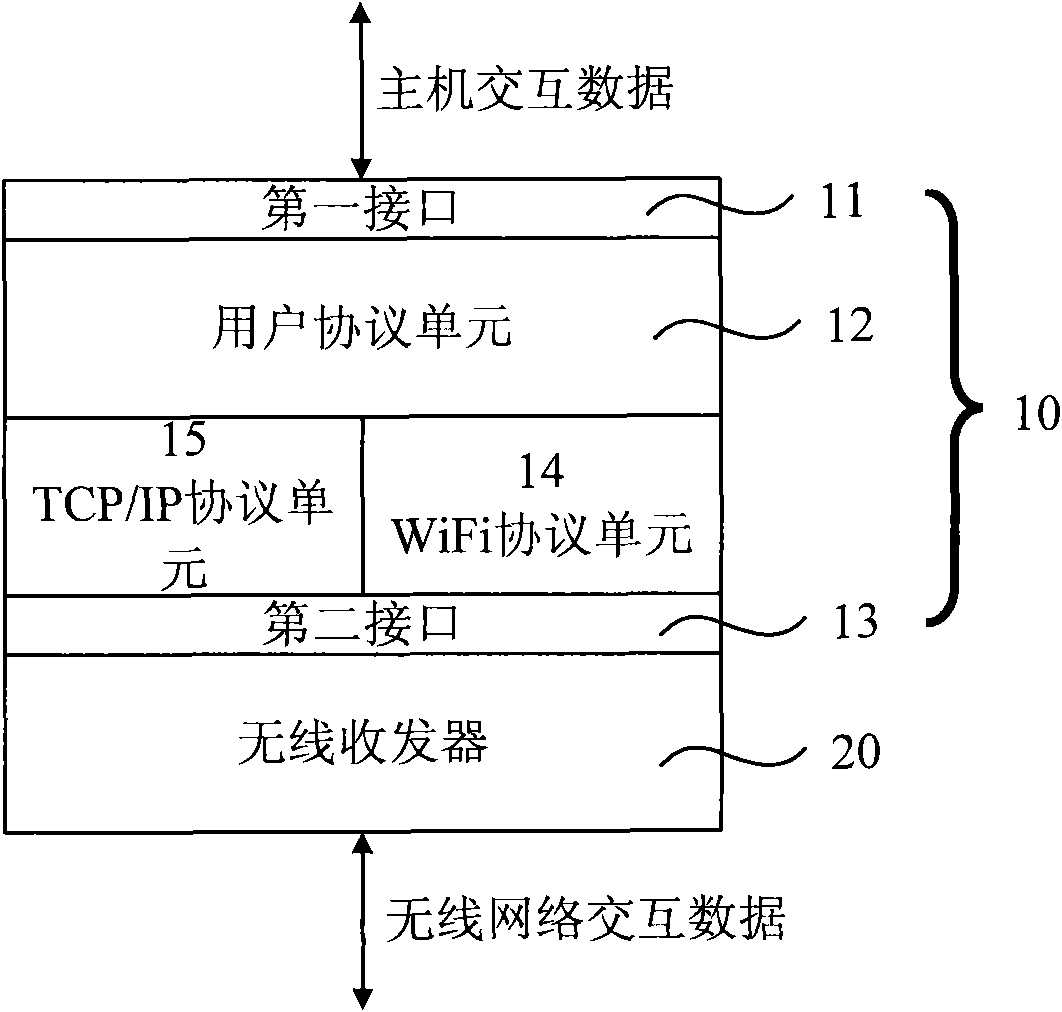
Wireless data transmission device
ActiveCN101784126AReduce complexityNetwork topologiesWireless network protocolsTransceiverWireless transceiver
The invention provides a wireless data transmission device. The wireless data transmission device comprises a microprocessor connected with a host and a wireless transceiver connected with the microprocessor, wherein the wireless transceiver transmits data received through a wireless local area network to the microprocessor or transmits the data transmitted by the microprocessor through the wireless local area network; the microprocessor comprises a first interface in data interaction with the host, a user protocol unit, a TCP / IP protocol unit, a WiFi protocol unit and a second interface connected with the wireless transceiver; the user protocol unit extracts application layer data in the data acquired through the second interface and transmits the application layer data to the host through the first interface or transmits the application layer data received through the first interface to the wireless transceiver through the second interface; the user protocol unit and the wireless transceiver are communicated with each other by using a TCP / IP protocol; and the wireless transceiver receives and transmits the data of the wireless local area network by using a WiFi protocol. The wireless data transmission device lowers the access complexity of the wireless local area network.
Owner:SHANGHAI MXCHIP INFORMATION TECHN
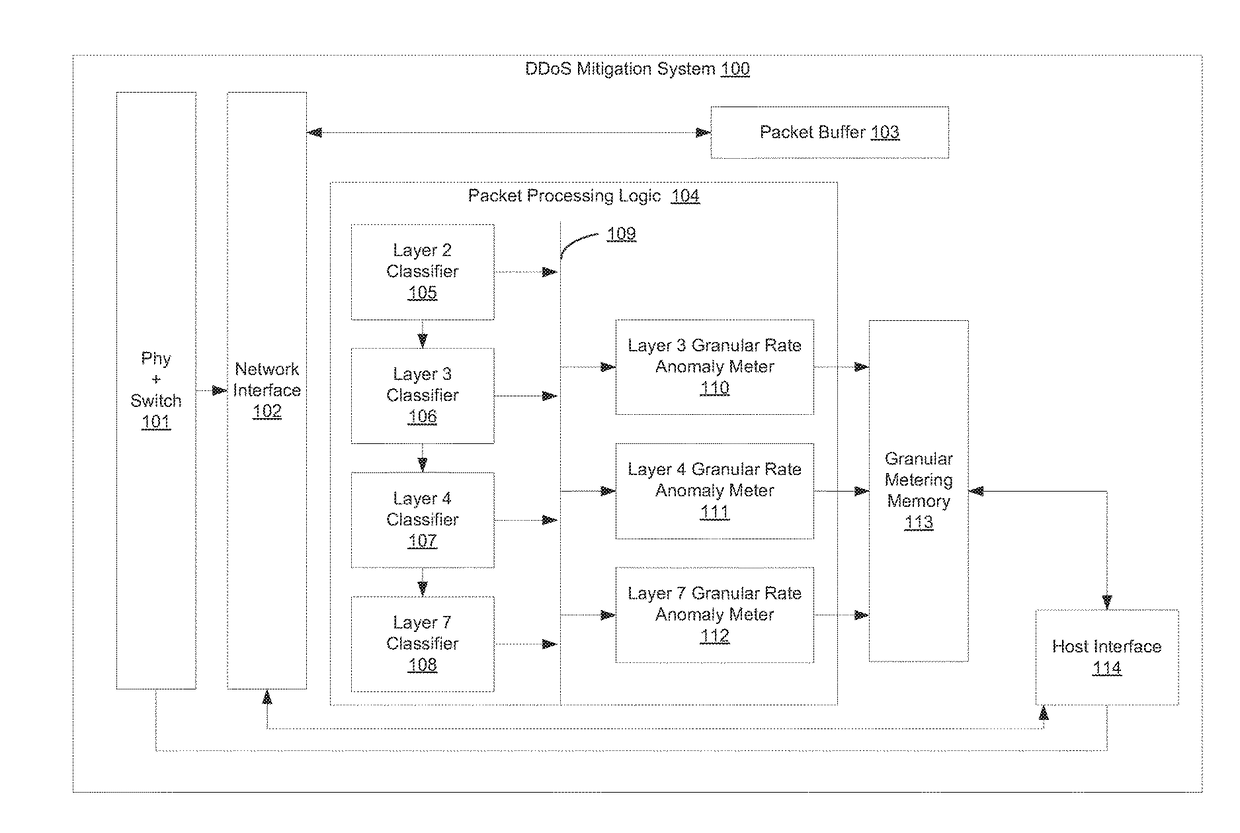
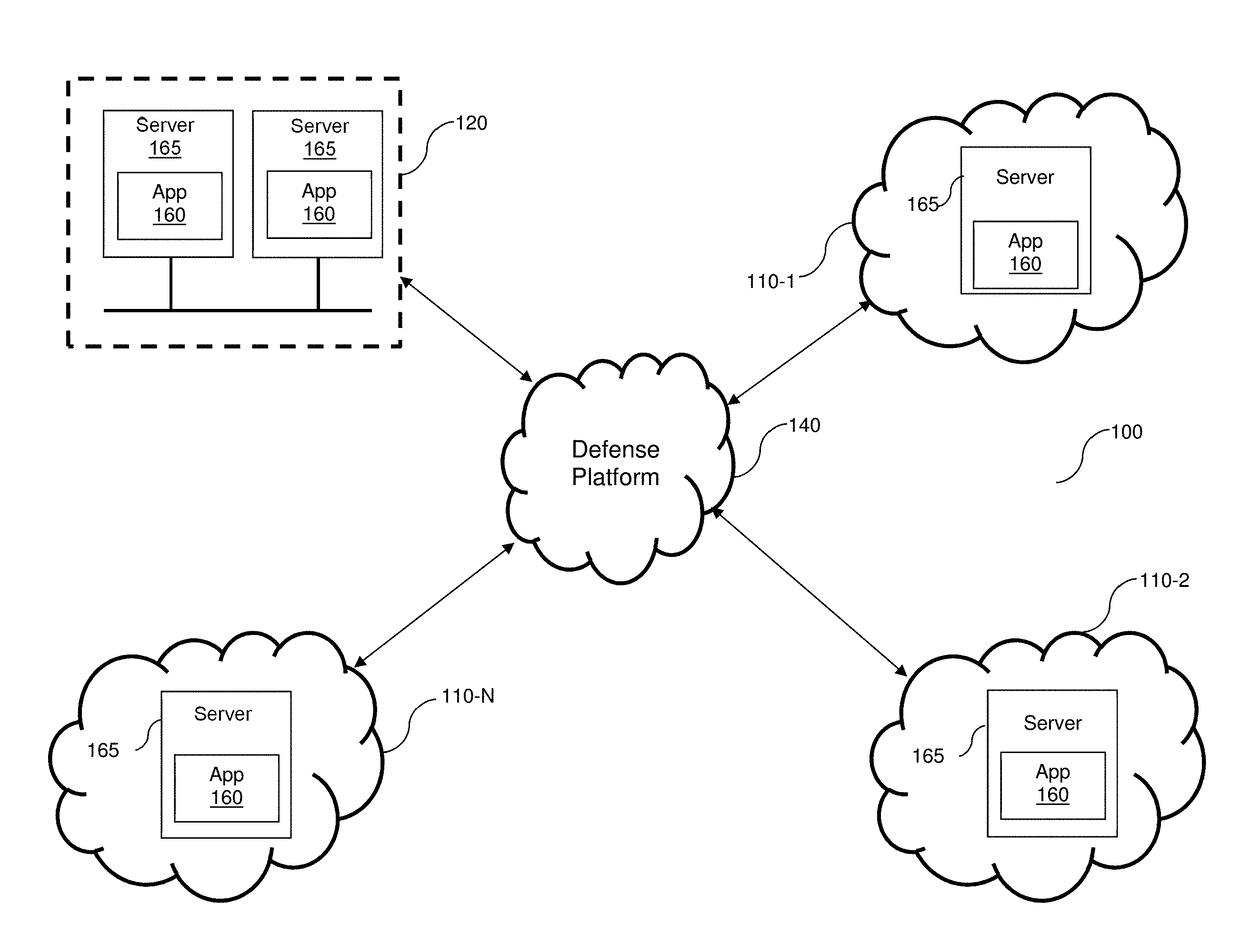
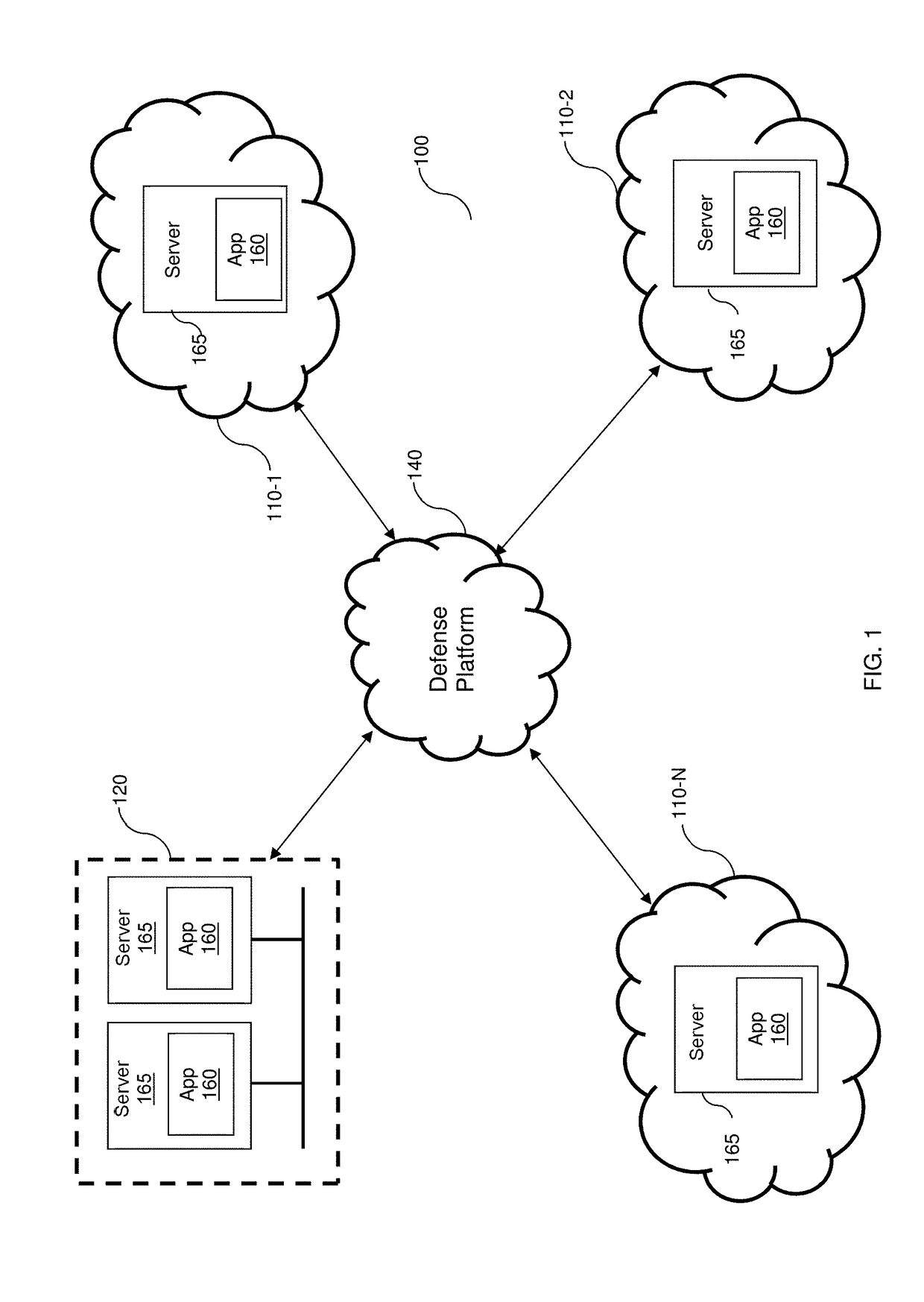
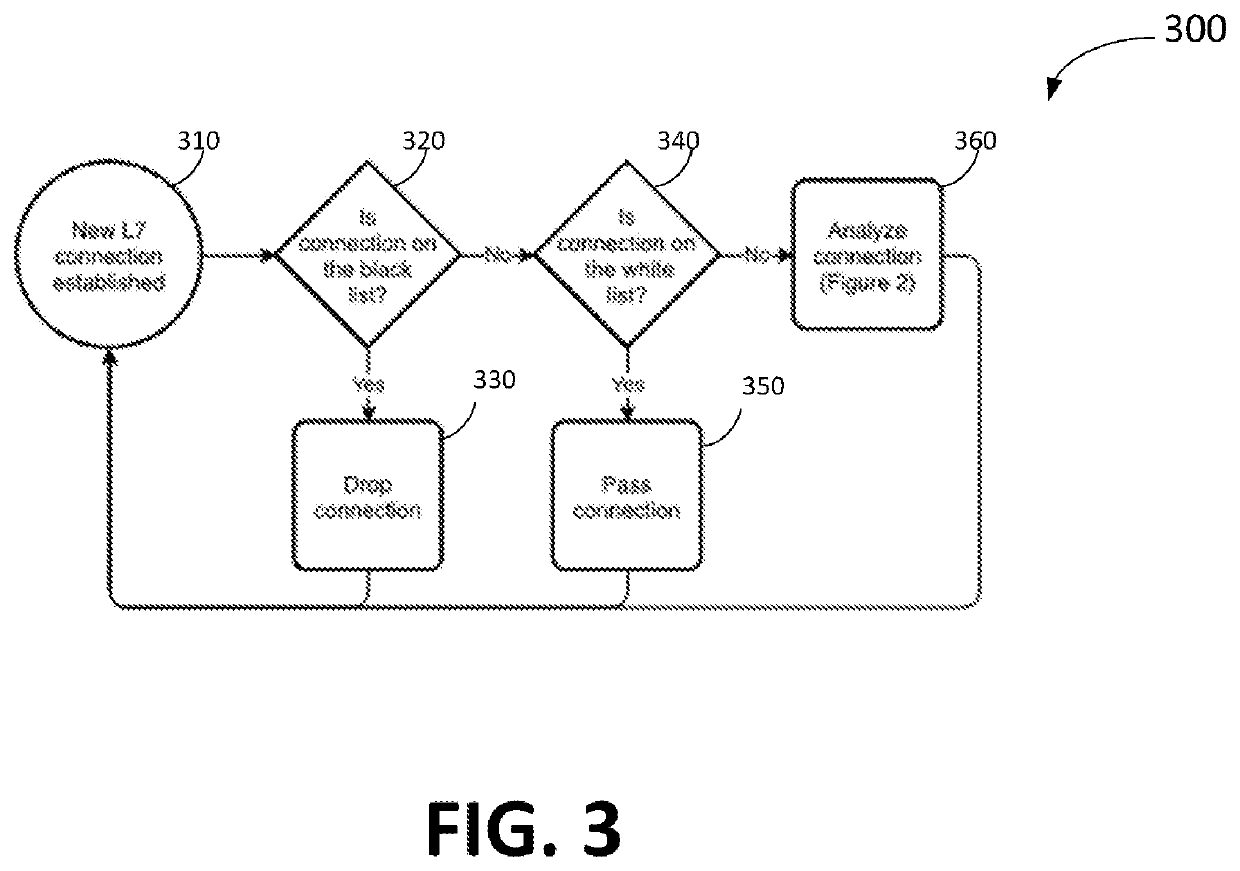
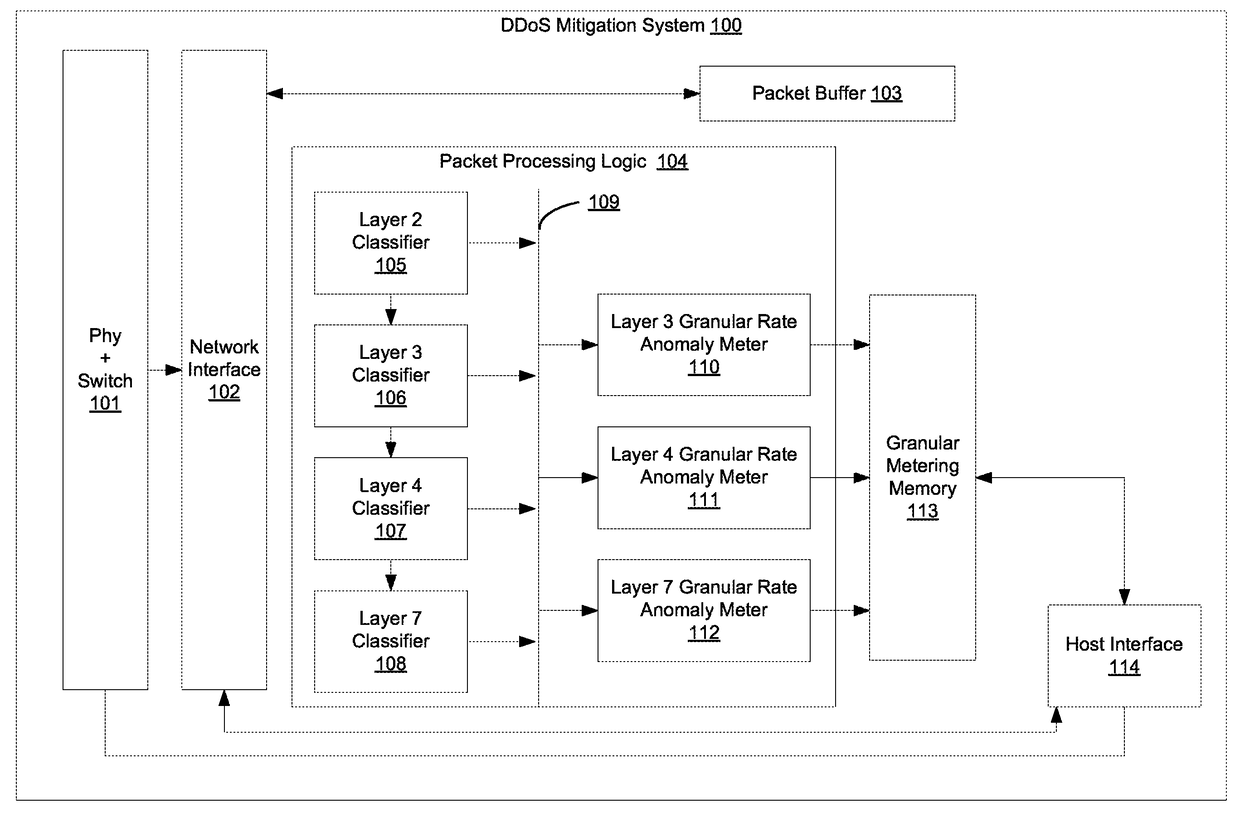
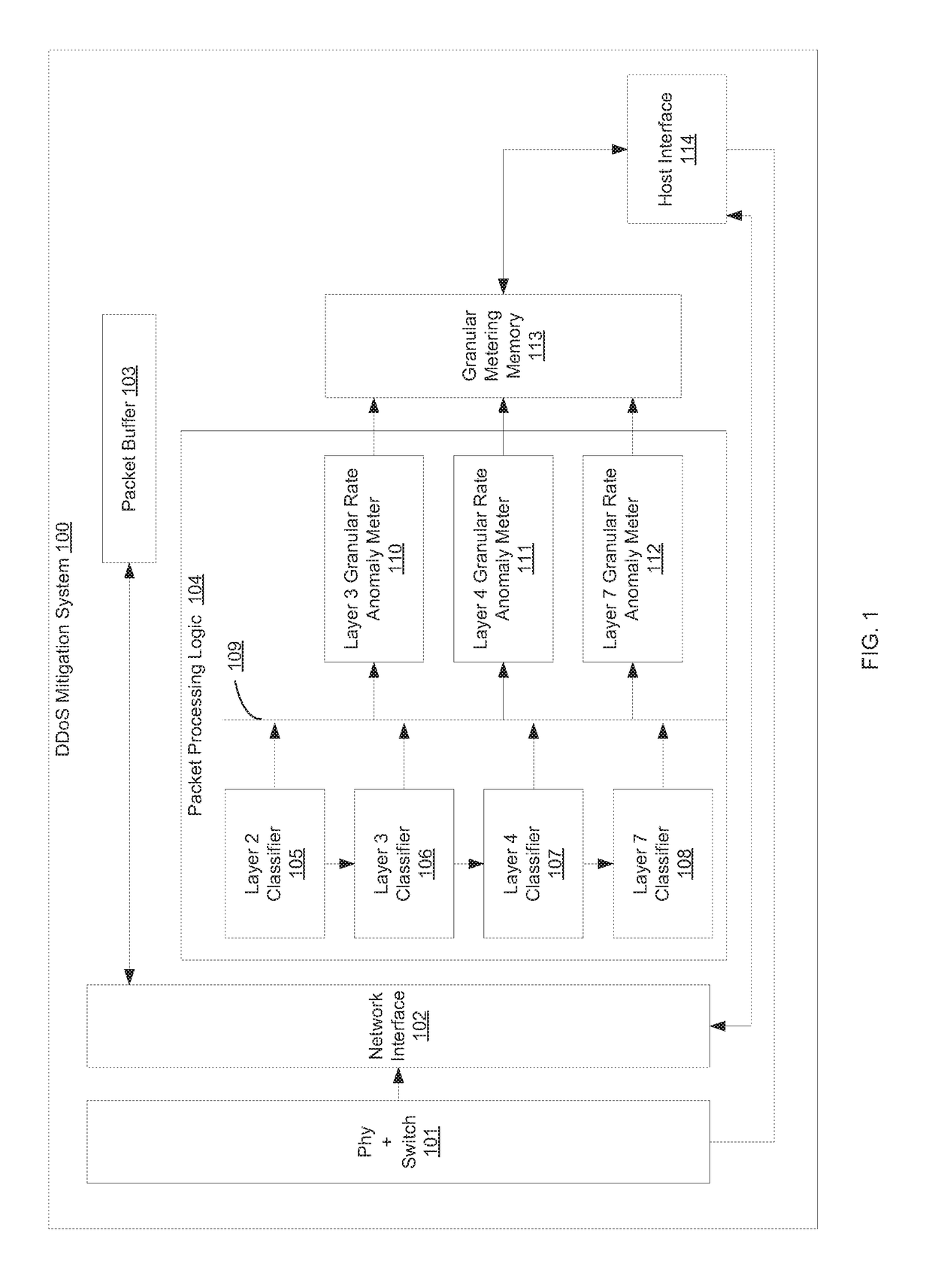
Detecting and mitigating application layer ddos attacks
A system and method for detecting a Denial of Service (DoS) attack. A number of evaluator elements (M) is determined for DoS analysis for network connection requests wherein each evaluator element is preferably associated with a component of the analyzed connection request. A DoS evaluator element score is determined for an evaluator element of the connection request by analyzing the evaluator element. DoS mitigation actions may be performed on the connection request if the determined evaluator element score is indicative of a DoS attack. An evaluator consolidated score (which may be weighted) is then calculated preferably consisting of one or more of the respective DoS evaluator element scores. Next, a determination is made as to whether each evaluator element of the M evaluator elements has been analyzed for determining a respective DoS evaluator element score. If no, a DoS evaluator element score for a succeeding evaluator element to be analyzed is then determined. And if yes, a determination is then made as to whether the value of the evaluator consolidated score is indicative of a DoS attack by the subject analyzed network connection request.
Owner:ARBOR NETWORKS
Application layer DDoS attack detection and defense method based on multiple feature entropies
InactiveCN110602109AReduce false positive rateFunction increaseTransmissionResource consumptionDecomposition
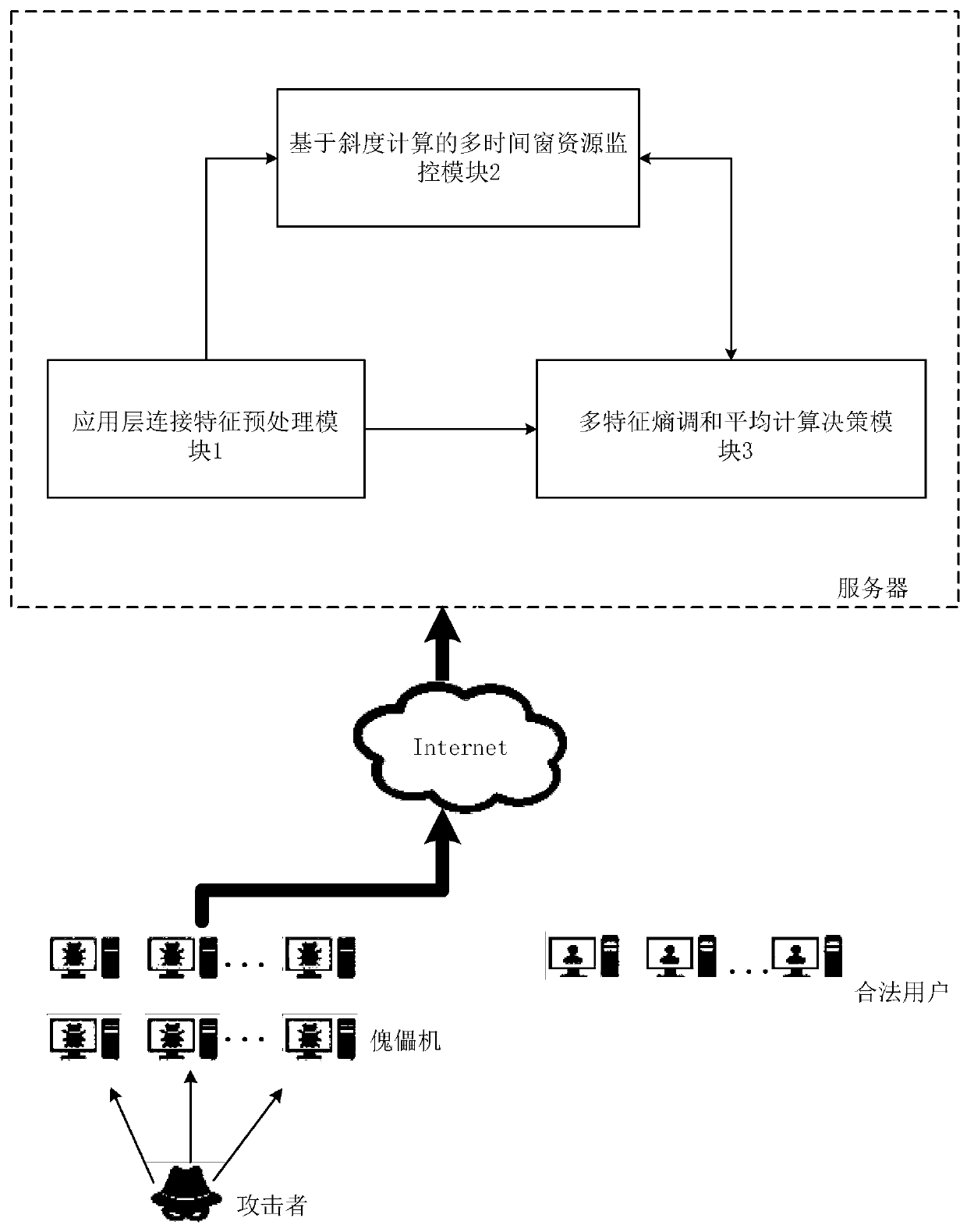
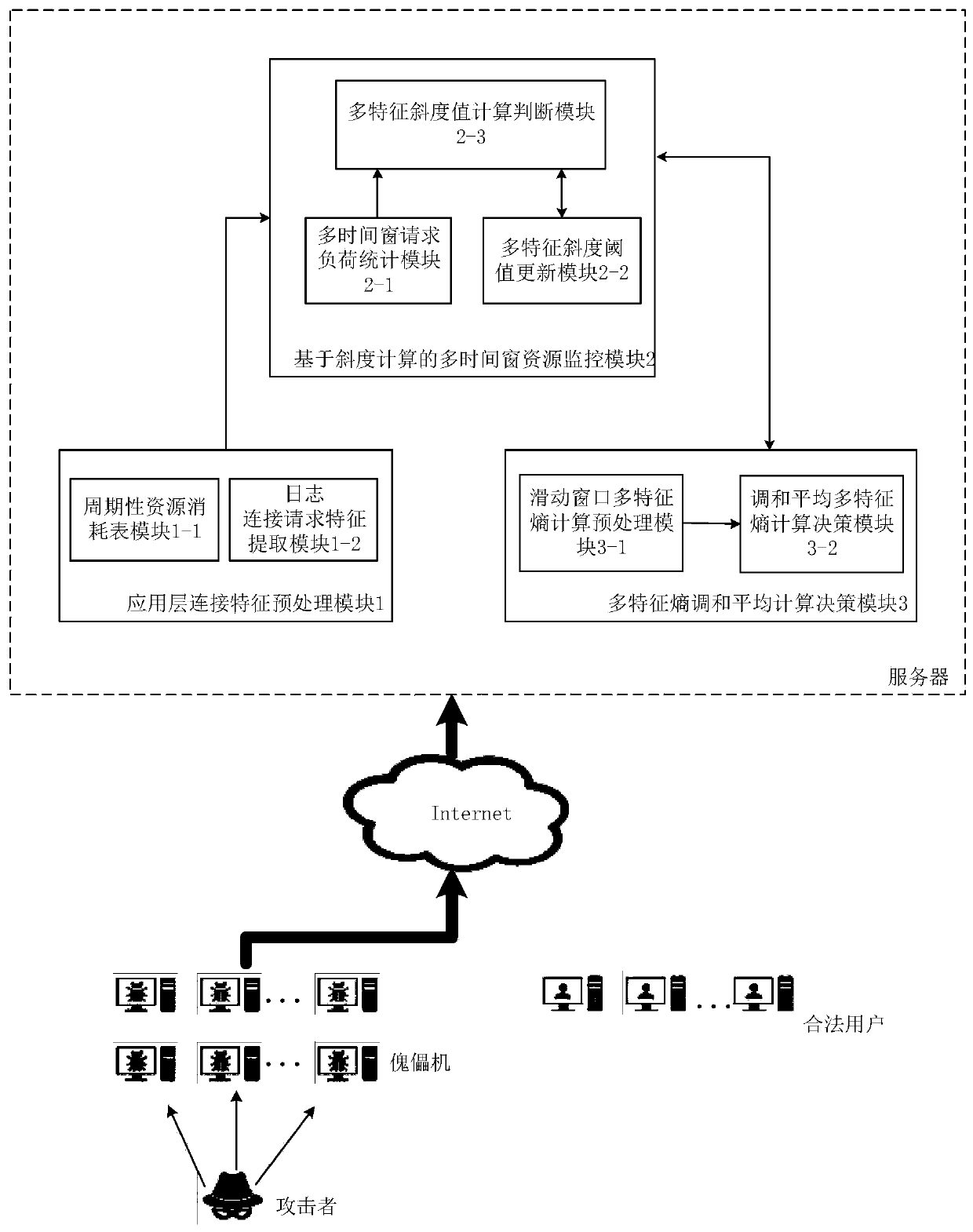
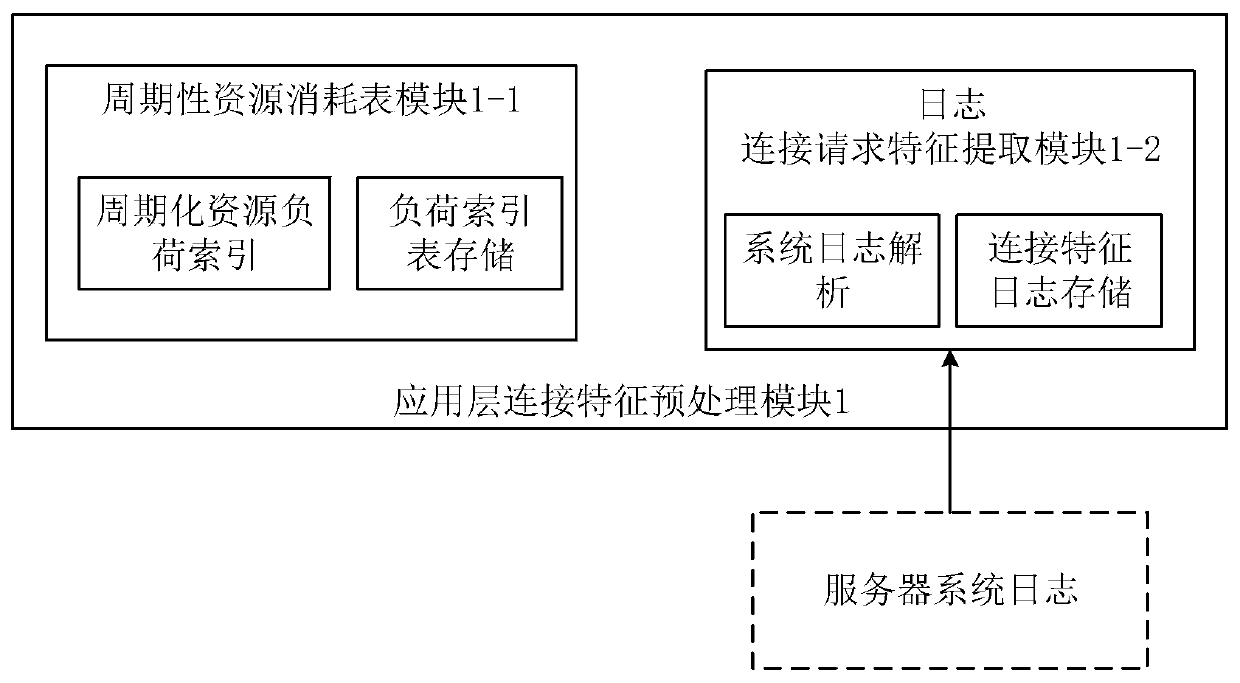
The invention discloses an application layer DDoS attack detection and defense method based on multiple feature entropies. The method comprises an application layer connection feature preprocessing module, a multi-time-window resource monitoring module based on inclination calculation, and a multi-feature-entropy harmonic average calculation decision module. The application layer connection feature preprocessing module counts URI resources and sets a resource consumption table, and performs multi-feature decomposition and preprocessing on the connection request in the log to generate a connection feature log; a multi-time-window resource monitoring module based on inclination calculation monitors the total connection and the total load capacity change of servers in a plurality of time windows in real time; and the multi-feature entropy harmonic average calculation decision module calculates a multi-feature entropy harmonic average vector norm, and judges whether an application layer DDoS attack exists or not by comparing an initial threshold value. The method has the advantages that real-time load monitoring and abnormal connection detection can be provided for the servers according to network servers of different scales, and it is guaranteed that the servers can effectively detect DDoS attacks on an application layer in real time.
Owner:SOUTHEAST UNIV +1
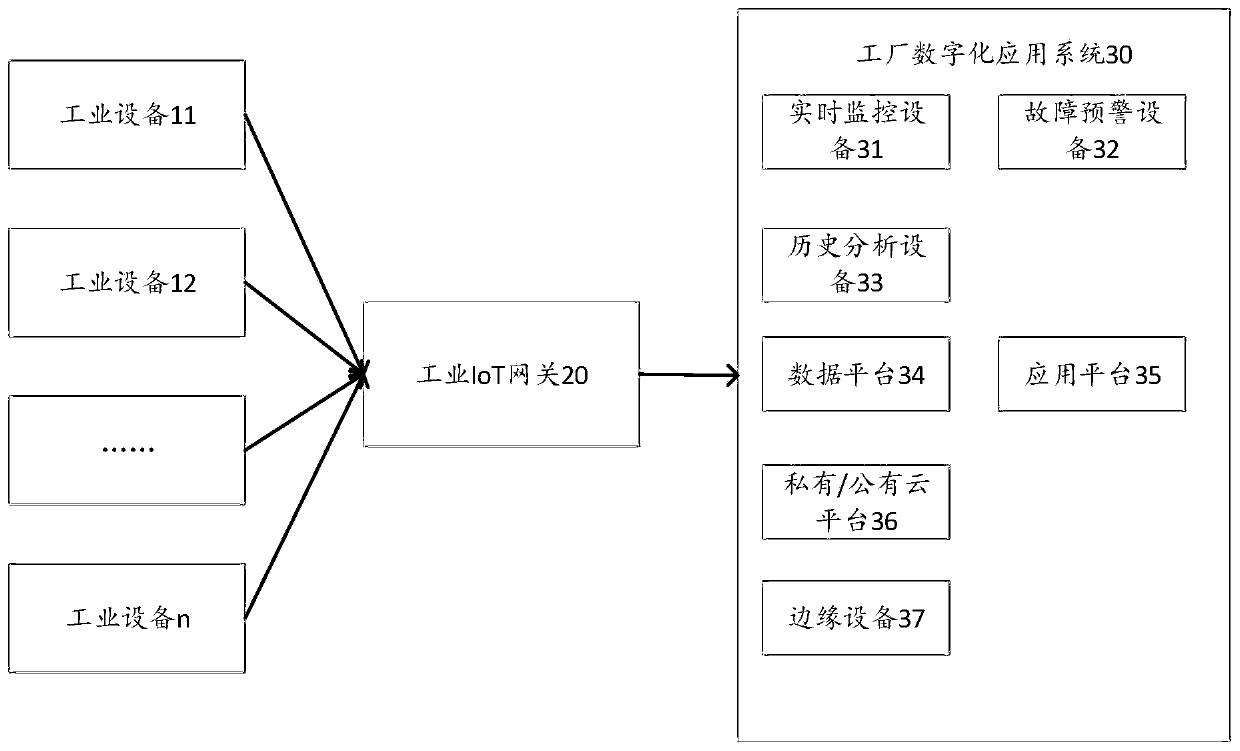
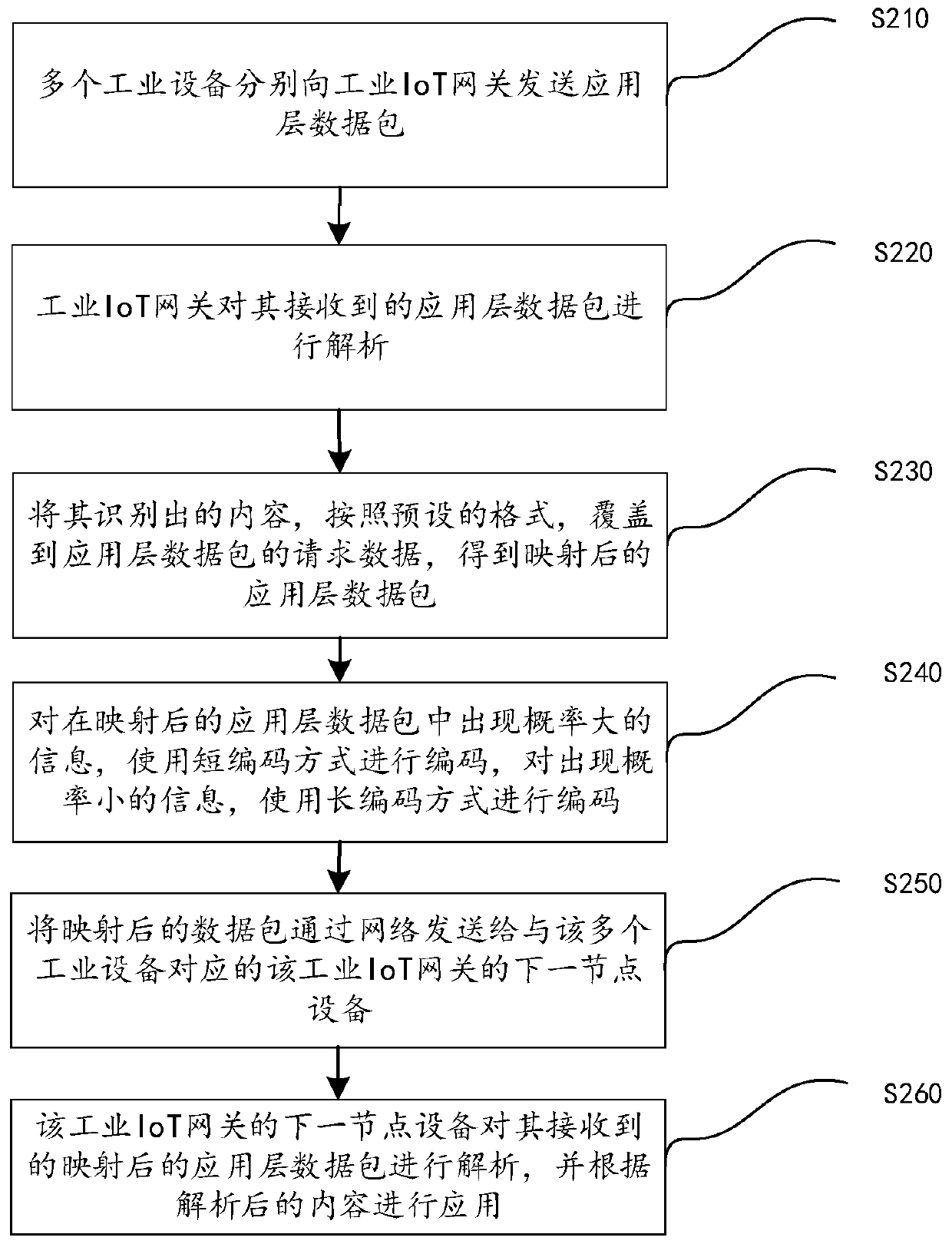
Data processing method in industrial Internet of Things gateway and industrial Internet of Things gateway
InactiveCN110535828AMeet the real-time requirements of data transmissionReduce flow pressureDatabase management systemsNetwork connectionsTraffic capacityIot gateway
The invention discloses a data processing method in an industrial Internet of Things gateway and the industrial Internet of Things gateway. The method comprises steps of enabling industrial Internet of Things gateway to receive corresponding first application layer data packets from a plurality of industrial devices; analyzing the first application layer data packet to obtain at least one or moreof the following contents: an equipment operation state, an alarm type of equipment, number information of products corresponding to the equipment, related information of a production cycle of the products corresponding to the equipment, and duration information of the state of the equipment; covering the content obtained by analyzing the first application layer data packet on the request data part of the first application layer data packet according to a preset format so as to obtain a second application layer data packet; and sending the second application layer data packet to a next node device of the industrial Internet of Things gateway corresponding to the plurality of industrial devices through a network. According to the invention, the standards of heterogeneous data sources are unified, and the flow pressure caused by data uplink is reduced.
Owner:华瑞新智科技(北京)有限公司 +1
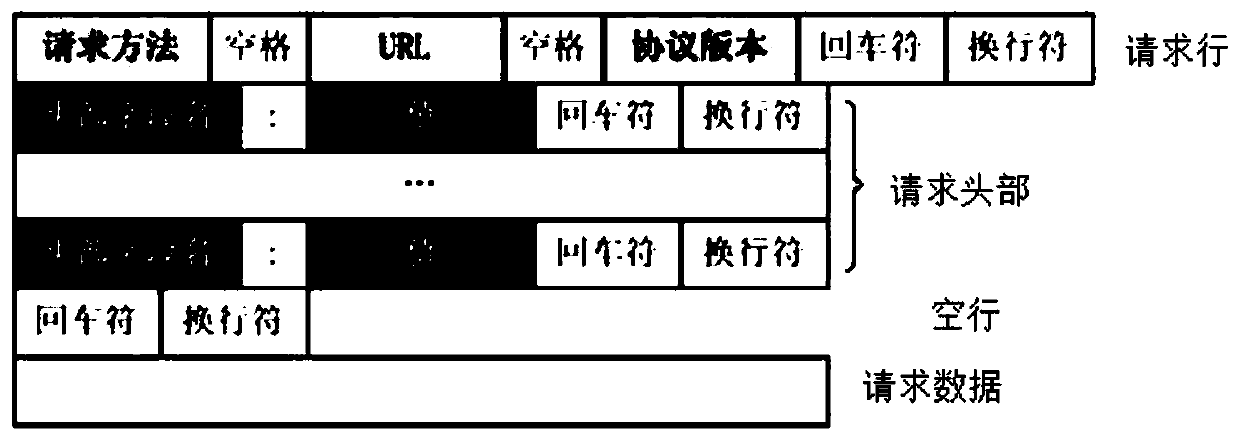
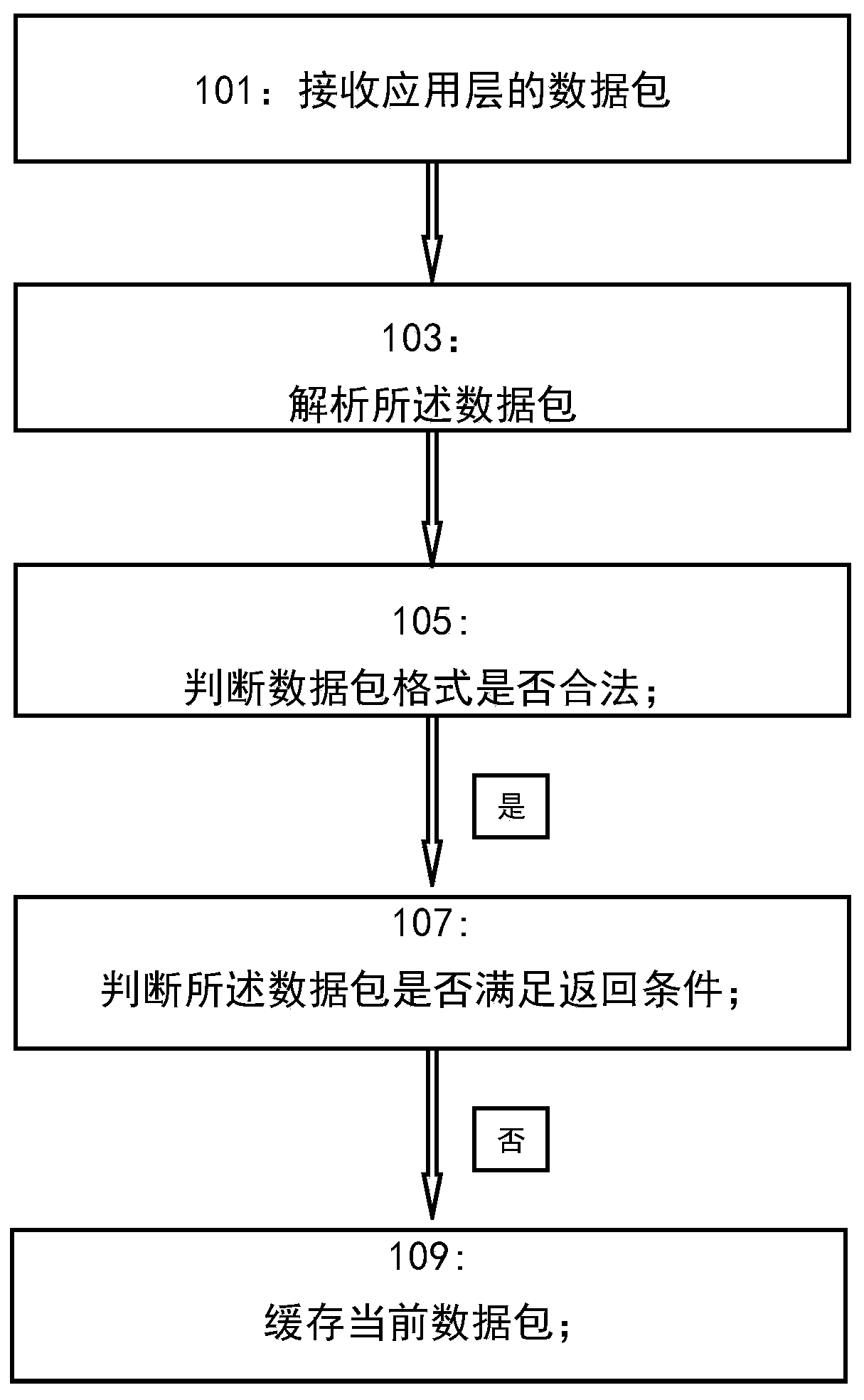
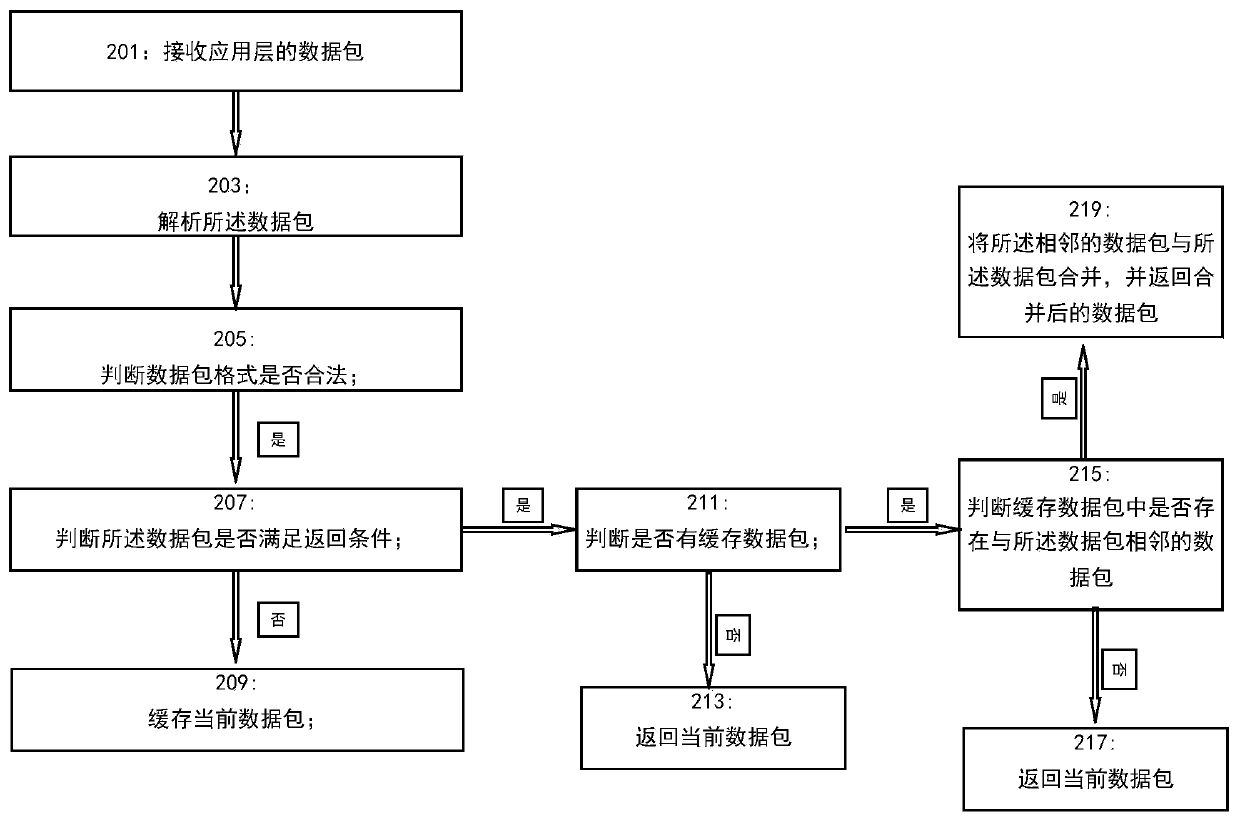
Application layer data sequential packing method, device and equipment and storage medium
InactiveCN109714326ASimplify the sorting processSimplified processing stepsTransmissionSystem stabilityProtocol Application
The invention discloses an application layer data sequential packing method and device, computer equipment and a readable storage medium. The application layer data sequential packing method comprisesthe following steps: receiving a data packet of an application layer; Analyzing the data packet; Judging whether the data packet format is legal; If the format of the data packet is legal, judging whether the data packet meets a return condition or not; And if the data packet does not meet the return condition, caching the current data packet. The sequential packing method includes packaging thereceived out-of-order data in an application layer; according to the serial number of the received data packet and the serial number of the data packet required in the current sequence, returning or caching the data packet; and further judging whether a data packet adjacent to the received data packet exists in the cache region or not before returning, and if yes, combining the received data packet with the adjacent data packet, thereby effectively simplifying the application layer data packet sorting process and processing steps, improving the efficiency, and improving the data sequence packaging success rate and system stability.
Owner:北京明朝万达科技股份有限公司
DDoS attack detection method based on network traffic application layer
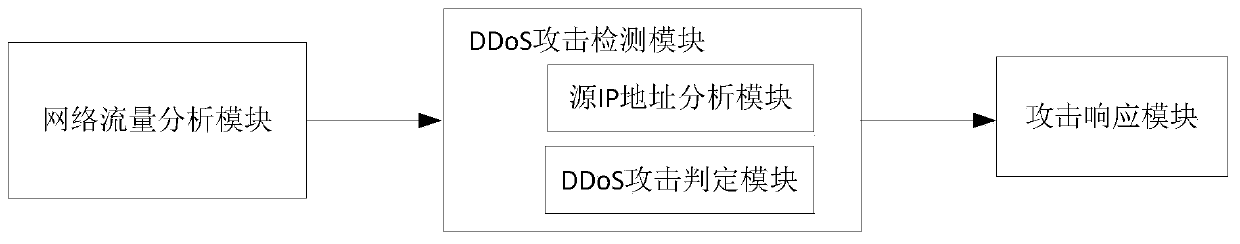
InactiveCN110493230AIdentify similaritiesReduce false alarm rateTransmissionIp addressProtocol Application
The invention discloses a DDoS attack detection method based on a network traffic application layer. The method comprises the following steps: selecting three parameters including a flow change rate,a new source IP address change rate and a source IP address request allocation rate to analyze network flow. Therefore, the DDoS attack traffic is distinguished from the FC traffic. The system is provided with a network flow analysis module, a DDoS attack detection module and an attack response module. When network flow changes suddenly, the network flow analysis module sends a warning signal to the DDoS attack detection module. The DDoS attack module is used for judging whether an FC attack or a DDoS attack occurs. When the DDoS attack is detected, the DDoS attack is detected. The attack response module is activated to filter malicious traffic and maintain uninterrupted service for a real user, the similarity between application layer DDoS attack traffic and FC traffic can be effectivelyrecognized, main characteristics of the application layer DDoS attack traffic and FC traffic are selected for distinguishing, the false alarm rate and the missing report rate are reduced, the cost islow, and application and popularization are facilitated.
Owner:北京云端智度科技有限公司
Detection and protection method and system for application layer DDOS attack based on IP credibility
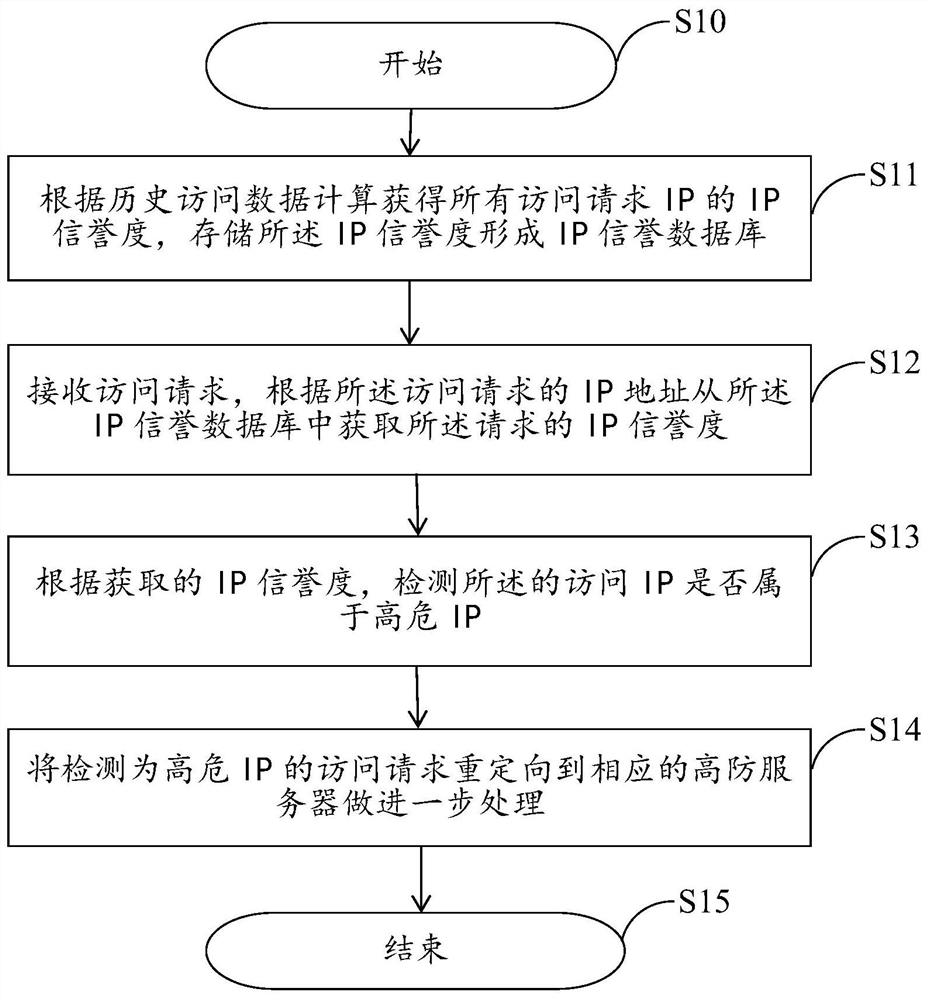
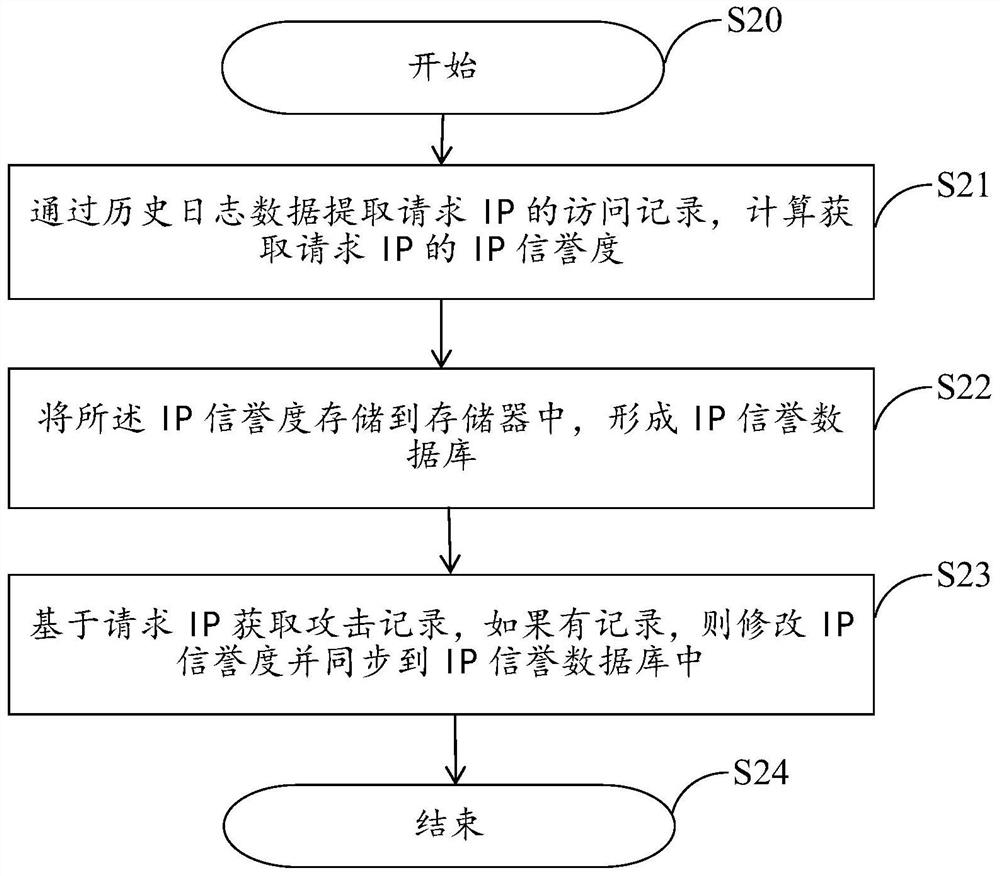
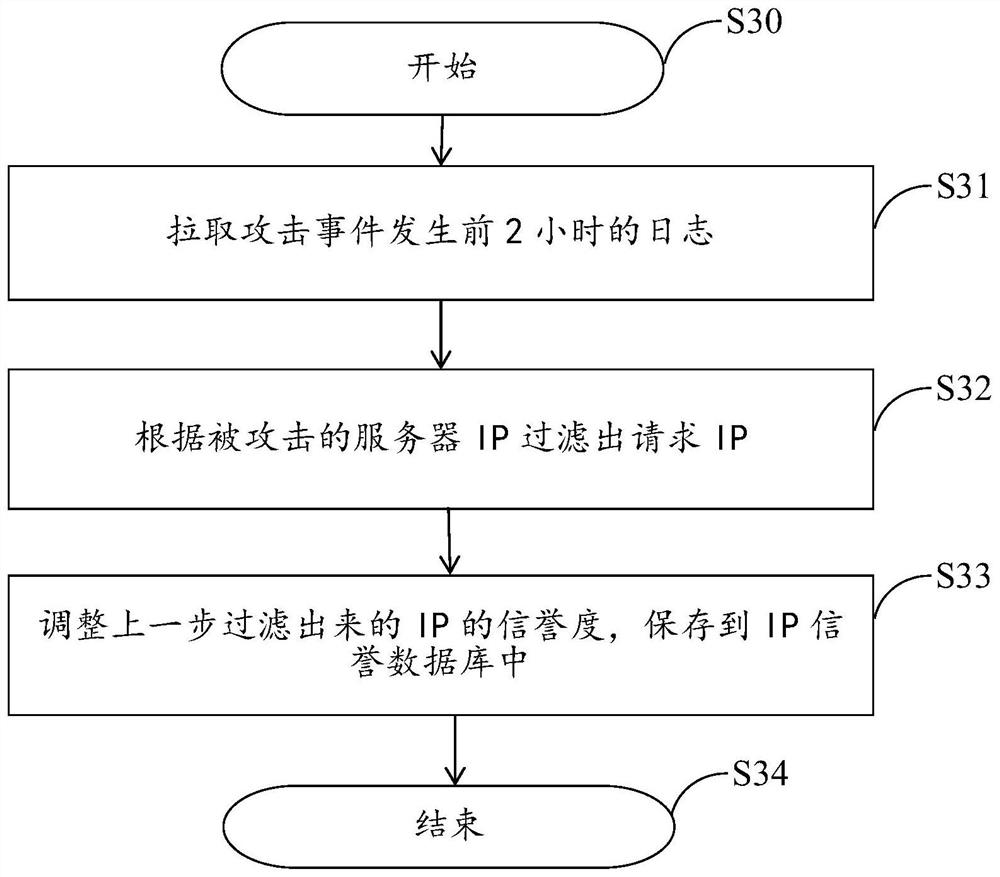
PendingCN112491869AEffectively distinguish abnormal trafficImprove accuracyTransmissionAttackThreat level
The embodiment of the invention provides an application layer DDOS attack detection and protection method and system based on IP credibility and electronic equipment, and the method comprises the steps: obtaining the IP credibility through combining an IP access log and a DDOS attack event record, carrying out the shunting of an access request according to the IP credibility, redirecting a high-risk access request to a corresponding high-protection server. Therefore, requests of different security threat levels are shunted and isolated, and detection and protection of application layer DDoS attacks are further realized. By utilizing the method disclosed by the invention, the abnormal traffic can be effectively distinguished, the accuracy of preventing and detecting the DDoS attack is improved, and meanwhile, when the service is attacked, the access quality of a normal user can be effectively ensured and the user experience is improved, so that the method disclosed by the invention hasobvious beneficial effects.
Owner:SHANGHAI QINIU INFORMATION TECH
Two-stage hash based logic for application layer distributed denial of service (DDoS) attack attribution
Methods and systems for a two-stage attribution of application layer DDoS attack are provided. In a first table just a hash index is maintained whereas the second stage table keeps the string parameter corresponding to the application layer attribute under attack. A linked list maintains a plurality of rows if there is hash collision in the first table. The second table is aged out and reported periodically with details of large strings.
Owner:FORTINET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com