Application layer DDoS attack detection method based on logistic regression
A logistic regression and attack detection technology, applied to electrical components, transmission systems, etc., can solve the problems that restrict the effectiveness of DDoS attack detection at the application layer, high computational complexity, low detection rate, etc., and achieve reduced overhead and accurate models Parameters, Model Simple Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0020] The present invention will be further described below through specific embodiments and accompanying drawings. This example is only intended to illustrate an implementation method of the present invention, and does not represent a limitation on the scope of coverage of the present invention.
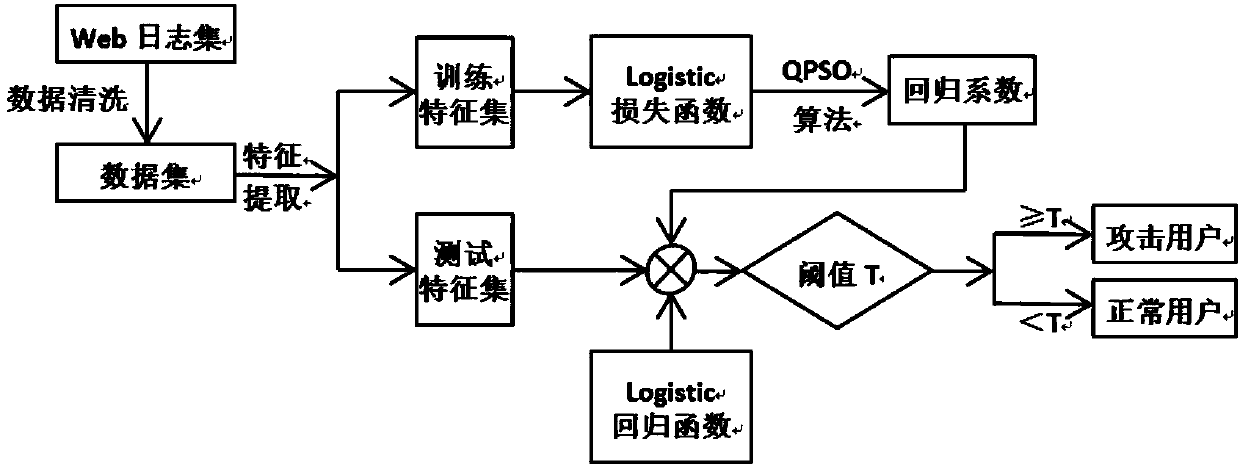
[0021] A kind of application layer DDoS attack detection method based on logistic regression of the present invention, the specific implementation process is described as follows:
[0022] The first step is to obtain the access log of the application layer server, and perform data cleaning on the obtained log.
[0023] Set the sliding time window to 1 hour, obtain user access logs within 1 hour, and then perform data cleaning on the obtained log set. The purpose of this is to remove redundant access records. When a user clicks on a page, they will also request static resources embedded in the page, such as: text, pictures, and page styles embedded in the page. Only keep user req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com