Distributed denial-of-service attack detection method based on external connection behaviors of Web communication group
A technology of denial of service attack and detection method, applied in the field of network security, can solve the problems of unavoidable impact of basic network bandwidth and difficulty in distinguishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
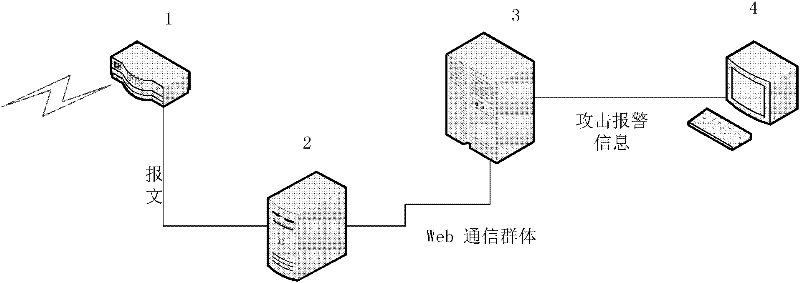
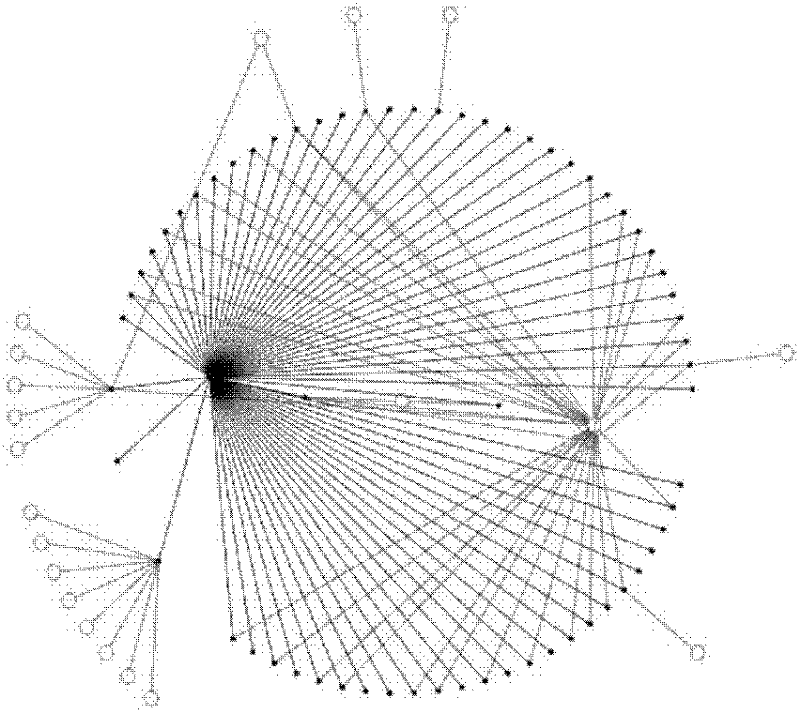
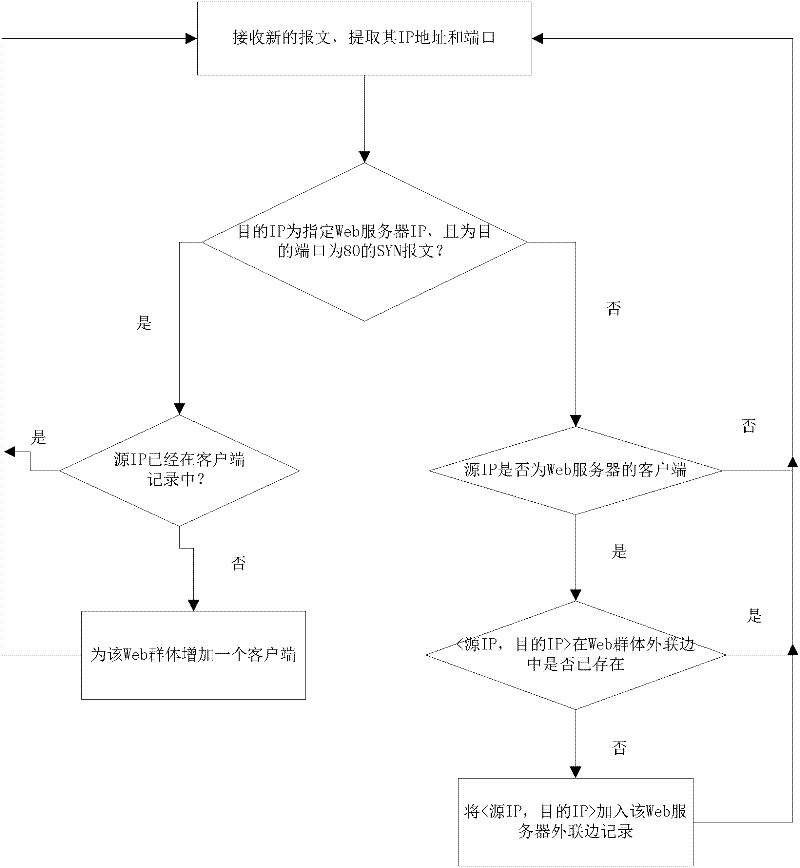
[0038] In order to deal with application-layer DDoS attacks more effectively, an application-layer DDoS attack detection method that can be deployed in the backbone network is designed. The application scenarios of this detection method are as follows: figure 1 Shown: Port mirroring is set up on network devices such as router 1 or switch, so that all network packets flowing through the device are copied and sent to the network monitoring front-end processor 2; the front-end processor constructs a Web communication group based on the communication relationship and sends it to the detection Server 3; the server 3 extracts the outreach behavior characteristics of the Web group, detects the deviation of the outreach behavior parameters, judges the application layer DDoS attack, and reports the occurrence of the attack to the network monitoring terminal 4.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com