Application layer distributed denial of service (DDoS) attack detection method and defensive system aimed at website
An attack detection and application layer technology, applied in the field of network security, can solve the problem that all types of users cannot access feature descriptions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
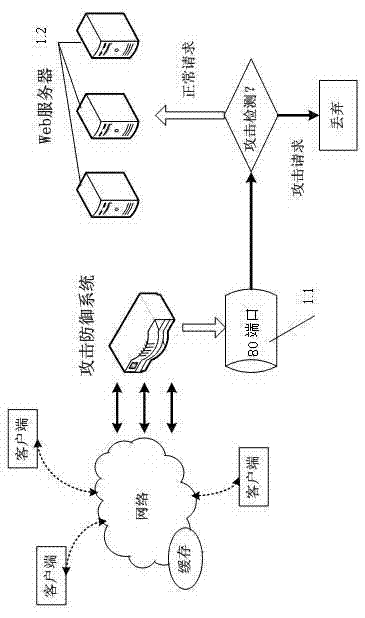
[0020] Such as figure 1 Shown is a schematic diagram of the deployment of the application layer DDoS attack defense system. The system is deployed at the front end of the web server 1.2 in the data center to protect all web servers 1.2 in the data center. The system detects the HTTP request to access port 1.1 of data center server 80, discards it if it is an attack request, and forwards it to the server if it is a normal request.
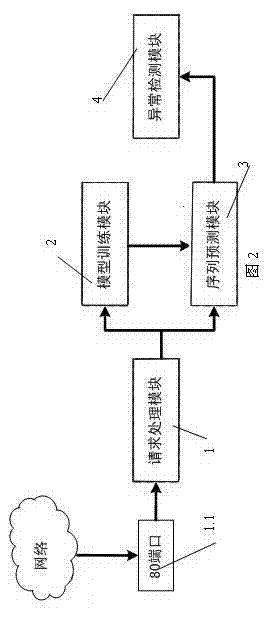
[0021] Such as figure 2 Shown is a schematic diagram of the application layer DDoS attack defense system architecture, the system is mainly composed of the following four modules:
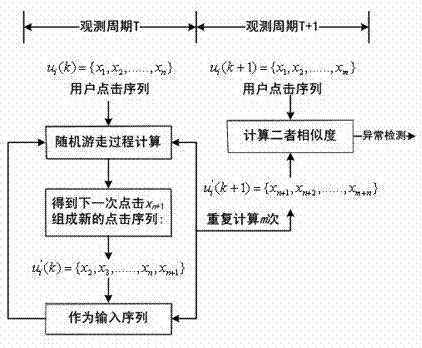
[0022] Request processing module 1, this module is responsible for preprocessing the HTTP request to access the server. First, according to the HTTP request, the K-means (distance-based clustering algorithm) clustering algorithm is used to classify the pages of a website to obtain a classification set V j ; j is the page type, and then according to the HTTP request a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com