Detection and protection method and system for application layer DDOS attack based on IP credibility
A DDOS and protection system technology, applied in the field of CDN network security, can solve the problems of not considering the characteristics of the request, the inability to model, and the limitations of the technical solution, so as to improve the experience, ensure the quality of access, and improve the accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Embodiments and examples of the present invention will be described in detail below with reference to the drawings.
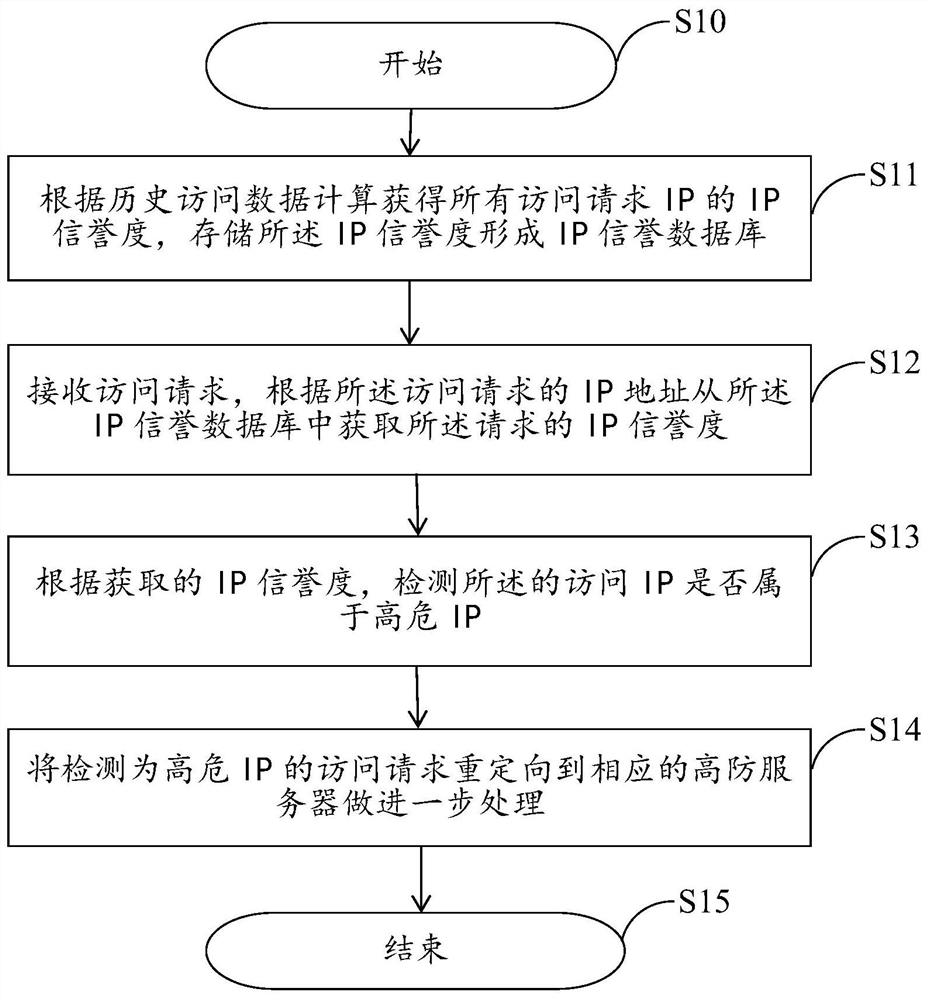
[0032] see figure 1 , figure 1 It shows a schematic diagram of the processing flow of an IP reputation-based application layer DDOS attack detection and protection method in an embodiment, specifically including steps S11-S14:
[0033] Step S11: Calculate and obtain the IP reputation of all access request IPs according to the historical record data, and store the IP reputation to form an IP reputation database.
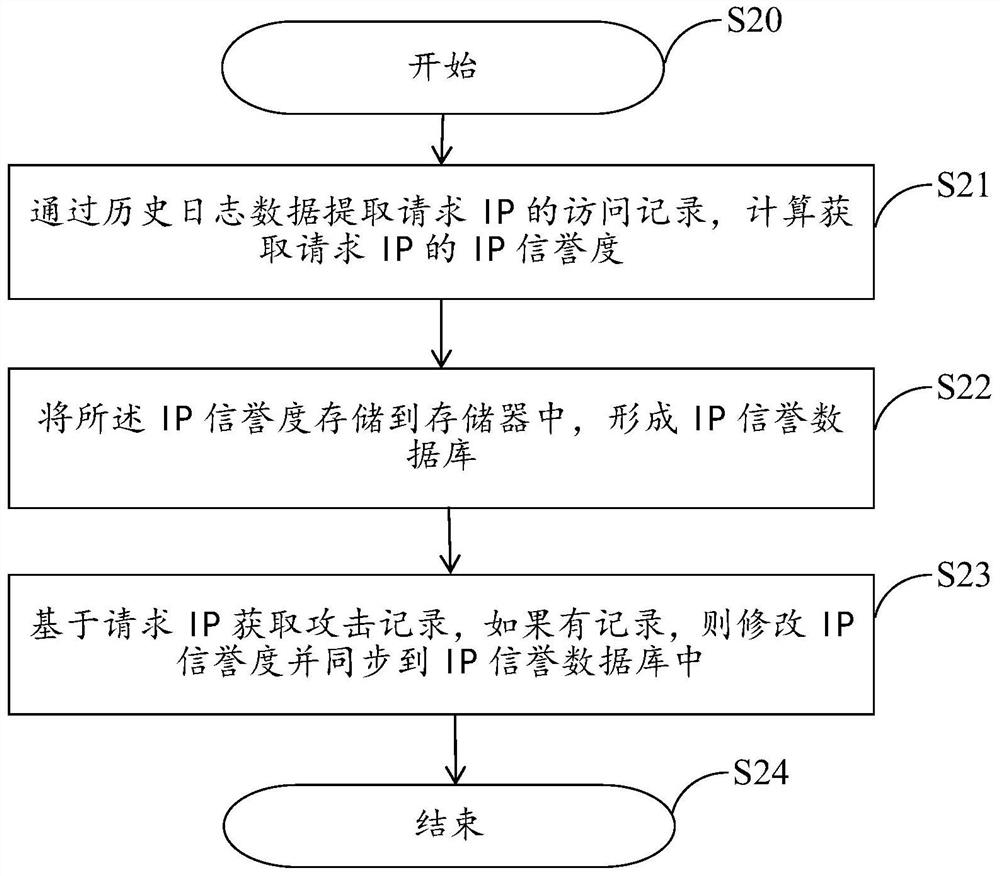
[0034] In this step, for the specific implementation steps of calculating and obtaining the IP reputation of all access request IPs, please refer to figure 2 The schematic diagram of the calculation flow of the IP reputation is shown.
[0035] The acquired IP reputation data is stored in a memory to form an IP reputation database. Specifically, the IP reputation data can be stored in a distributed NoSQL cluster. In one embodiment, the IP rep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com